Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 3. OpenShift Dedicated on Google Cloud architecture models
With OpenShift Dedicated on Google Cloud, you can create clusters that are accessible over public or private networks.
3.1. Private OpenShift Dedicated on Google Cloud architecture on public and private networks
You can customize the access patterns for your API server endpoint and Red Hat SRE management by choosing one of the following network configuration types:
- Private cluster with Private Service Connect (PSC).
- Private cluster without PSC
- Public cluster
Red Hat recommends using PSC when deploying a private OpenShift Dedicated cluster on Google Cloud. PSC ensures there is a secured, private connectivity between Red Hat infrastructure, Site Reliability Engineering (SRE), and private OpenShift clusters.
3.2. Understanding Private Service Connect
Private Service Connect (PSC), a capability of Google Cloud networking, enables private communication between services across different projects or organizations within Google Cloud. Users that implement PSC as part of their network connectivity can deploy OpenShift Dedicated clusters in a private and secured environment within Google Cloud without any public facing cloud resources.
For more information about PSC, see Private Service Connect.
PSC is only available on OpenShift Dedicated version 4.17 and later, and is only supported by the Customer Cloud Subscription (CCS) infrastructure type.
3.2.1. Private Service Connect architecture
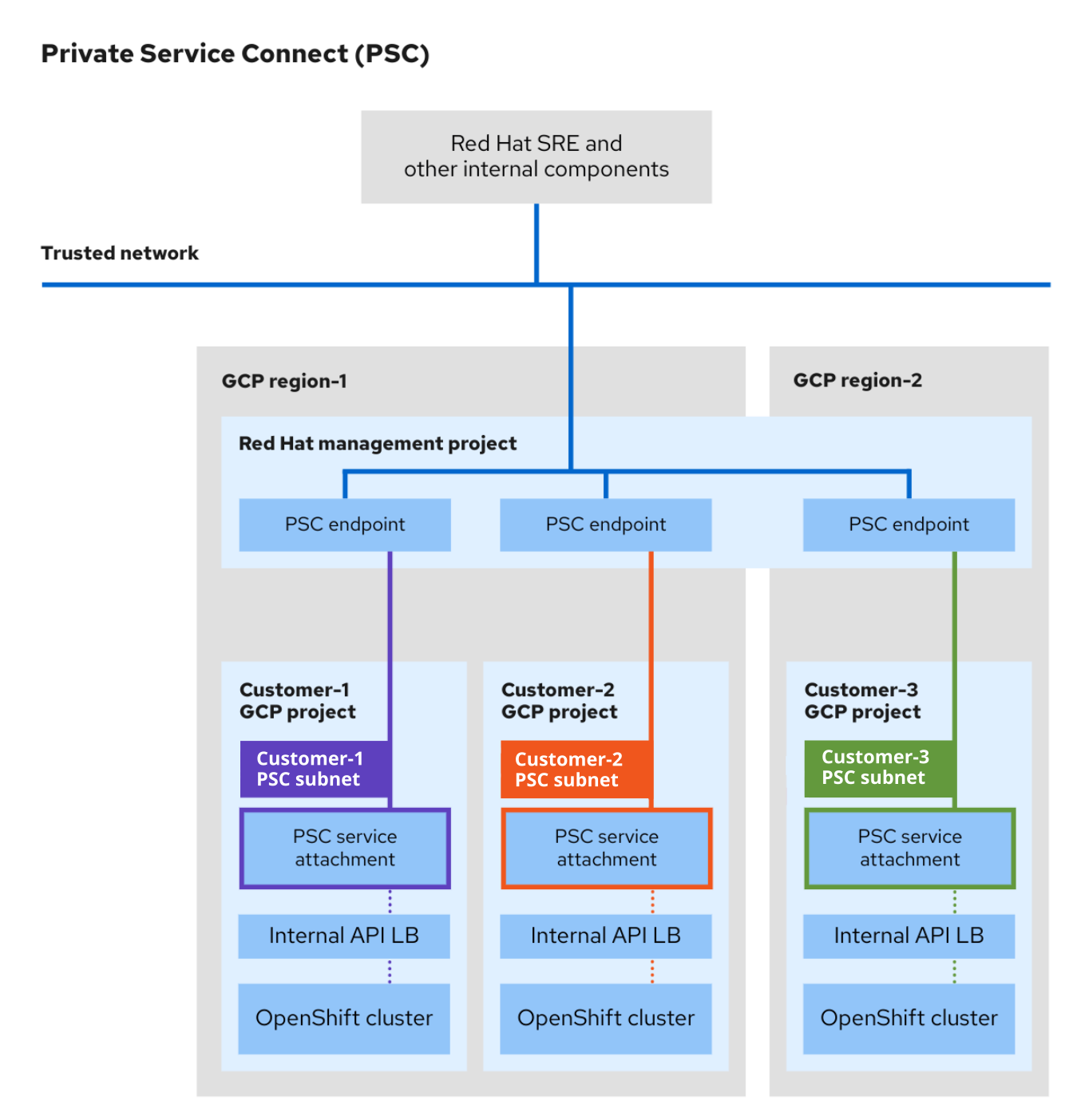
The Private Service Connect (PSC) architecture includes producer services and consumer services. Using PSC, the consumers can access producer services privately from inside their VPC network. Similarly, it allows producers to host services in their own separate VPC networks and offer a private connect to their consumers.
The following image depicts how Red HAT SREs and other internal resources access and support clusters created using PSC.
- A unique PSC service attachment is created for each OSD cluster in the customer Google Cloud project. The PSC service attachment points to the cluster API server load balancer created in the customer Google Cloud project.
- Similar to service attachments, a unique PSC endpoint is created in the Red Hat Management Google Cloud project for each OSD cluster.
- A dedicated subnet for Google Cloud Private Service Connect is created in the cluster’s network within the customer Google Cloud project. This is a special subnet type where the producer services are published via PSC service attachments. This subnet is used to Source NAT (SNAT) incoming requests to the cluster API server. Additionally, the PSC subnet must be within the Machine CIDR range and cannot be used in more than one service attachment.
- Red Hat internal resources and SREs access private OSD clusters using the connectivity between a PSC endpoint and service attachment. Even though the traffic transits multiple VPC networks, it remains entirely within Google Cloud.
- Access to PSC service attachments is possible only via the Red Hat Management project.
Figure 3.1. PSC architecture overview
3.3. Private OpenShift Dedicated on Google Cloud with Private Service Connect architecture model
With a private Google Cloud Private Service Connect (PSC) network configuration, your cluster API server endpoint and application routes are private. Public subnets or NAT gateways are not required in your VPC for egress. Red Hat SRE management access the cluster over the Google Cloud PSC-enabled private connectivity. The default ingress controller are private. Additional ingress controllers can be public or private. The following diagram shows network connectivity of a private cluster with PSC.
Figure 3.2. OpenShift Dedicated on Google Cloud deployed on a private network with PSC
3.4. Private OpenShift Dedicated on Google Cloud without Private Service Connect (PSC) architecture model
With a private network configuration, your cluster API server endpoint and application routes are private. Private OpenShift Dedicated on Google Cloud clusters use some public subnets, but no control plane or worker nodes are deployed in public subnets.
Red Hat recommends using Private Service Connect (PSC) when deploying a private OpenShift Dedicated cluster on Google Cloud. PSC ensures there is a secured, private connectivity between Red Hat infrastructure, Site Reliability Engineering (SRE), and private OpenShift clusters.
Red Hat SRE management access the cluster through a public load balancer endpoint that are restricted to Red Hat IPs. The API server endpoint is private. A separate Red Hat API server endpoint is public (but restricted to Red Hat trusted IP addresses). The default ingress controller can be public or private. The following image shows network connectivity of a private cluster without Private Service Connect (PSC).
Figure 3.3. OpenShift Dedicated on Google Cloud deployed on a private network without PSC
3.5. Public OpenShift Dedicated on Google Cloud architecture model
With a public network configuration, your cluster API server endpoint and application routes are internet-facing. The default ingress controller can be public or private. The following image shows the network connectivity of a public cluster.
Figure 3.4. OpenShift Dedicated on Google Cloud deployed on a public network