Generating vulnerability service reports
Communicate the exposure of RHEL systems to CVE security vulnerabilities
Abstract
Chapter 1. Overview of Red Hat Lightspeed vulnerability service reporting
The ability to convey the security exposure of your infrastructure to different stakeholders—DevOps team, security team, executive team—is vital. The vulnerability service enables you to download the following reports to analyze offline or share with others:
- Executive Reports. PDF summary and overview of the security vulnerability exposure your infrastructure, intended for executive audiences
- CVE reports. PDF report of selected, filtered CVEs to which your infrastructure is exposed, intended to highlight and share vulnerability data
- Vulnerability data export. Export of selected CVE data, based on filters you have in place when you perform the export, to a JSON or CSV file
Chapter 2. Executive reports
You can download a high-level executive report summarizing the security exposure of your infrastructure. Executive reports are two to three-page PDF files, designed for an executive audience, and include the following information:
On page 1
- Number of RHEL systems analyzed
- Number of individual CVEs to which your systems are currently exposed
- Number of security rules in your infrastructure
- List of CVEs that have advisories
On page 2
- Percentage of CVEs by severity (CVSS base score) range
- Number of CVEs published by 7, 30, and 90 day time frame
- Top three CVEs in your infrastructure, including security rules and known exploits
On page 3
- Security rule breakdown by severity
- Top 3 security rules, including severity and number of exposed systems
2.1. Downloading an executive report
Use the following steps to download an executive report for key stakeholders in your security organization:
Procedure
- Navigate to the Security > Vulnerability > Reports tab and log in if necessary.
- On the Executive report card, click Download PDF.
- Click Save File and click OK.
Verification
-
Verify that the PDF file is in your
Downloadsfolder or other specified location.
2.2. Downloading an executive report using the vulnerability service API
To download an executive report, use the vulnerability service API.
- Request URL: https://console.redhat.com/api/vulnerability/v1/report/executive
Curl:
curl -X GET "https://console.redhat.com/api/vulnerability/v1/report/executive" -H "accept: application/vnd.api+json"
curl -X GET "https://console.redhat.com/api/vulnerability/v1/report/executive" -H "accept: application/vnd.api+json"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 3. Reports by CVEs
You can create PDF reports showing a filtered list of CVEs your systems are exposed to. Give each report a relevant name, apply filters, and add user notes to present focused data to specific stakeholders.
You can apply the following filters when setting up the PDF report:
- Security rules. Show only CVEs with the security rules label.
- Known exploit. Show only CVEs with the Known exploit label.
- Severity. Select one or more values: Critical, Important, Moderate, Low, or Unknown.
- CVSS base score. Select one or more ranges: All, 0.0-3.9, 4.0-7.9, 8.0-10.0, N/A (not applicable)
- Business risk. Select one or more values: High, Medium, Low, Not defined.
- Status. Select one or more values: Not reviewed, In review, On-hold, Scheduled for patch, Resolved, No action - risk accepted, Resolved via mitigation.
- Publish date. Select from All, Last 7 days, Last 30 days, Last 90 days, Last year, or More than 1 year ago.
- Applies to OS. Select the RHEL minor version(s) of systems to filter and view.
- Tags. Select groups of tagged systems.
For more information about tags and system groups, see System tags and groups
- Advisory. Select whether to display only CVEs that have associated advisories (errata), only CVEs without advisories, or all CVEs.
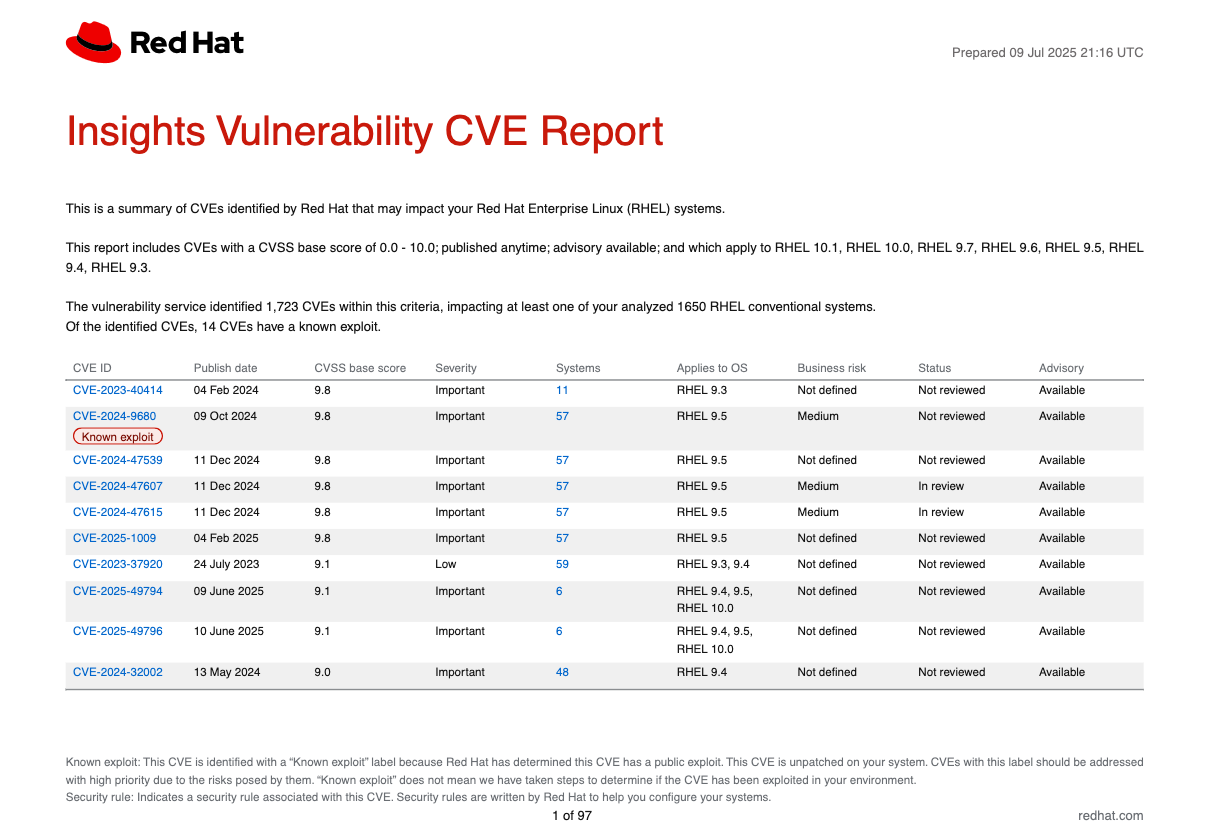
The CVE report lists the CVEs, linking each to the respective CVE page in the Red Hat CVE database so you can learn more about it. The list is ordered primarily by the publish date of the CVE, with the most recently published CVEs at the top of the list.
Example of a Red Hat Lightspeed Vulnerability CVE report
3.1. Creating a PDF report of CVEs
Use the following procedure to create a point-in-time snapshot of CVEs that potentially affect your systems.
Prerequisites
- You must be logged in to Red Hat Hybrid Cloud Console.
Procedure
- Navigate to the Security > Vulnerability > Reports page in the Red Hat Lightspeed application.
- On the Report by CVEs card, click Create report.
Make selections as needed in the pop-up card:
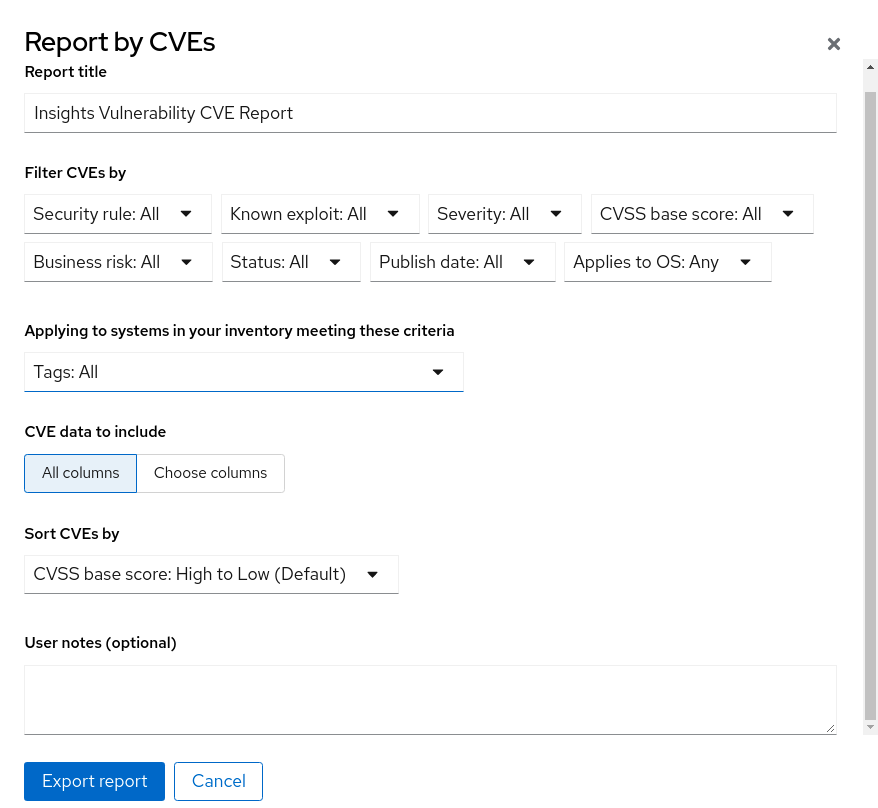
- Optionally, customize the report title.
- Under Filter CVEs by, click each filter dropdown and select a value.
- Select Tags to only include systems in a tagged group of systems.
- Under CVE data to include, Choose columns is activate by default, allowing you to deselect columns you do not want to include. Leave all boxes checked, or click All columns to show everything.
- Optionally, add notes to give the report context for the intended audience.
- Click Export report and allow the application a minute to generate the report.
- Select to open or save the PDF file, if your OS asks, and click OK.
Chapter 4. Reports by RHEL versions
The Vulnerability Exposure by OS report shows the the number of CVEs reported against up to five selected minor versions of RHEL. The report also includes a graph showing the number and severity of the CVEs for each selected RHEL version.
The report does not indicate actual CVEs on the systems registered to Red Hat Lightspeed in your environment. The comparison for each minor version is based on a generic system with the Base package list and with all errata for that minor version installed.
You can use the report to estimate the extent of vulnerability exposure for your systems within specific RHEL versions, and then use the information to make informed upgrade decisions.
The Vulnerability Exposure by OS report feature supports RHEL major and minor versions from RHEL 6.9 to RHEL 10.1 and later.
4.1. Creating a PDF report by RHEL versions
Prerequisites
- You have Vulnerability Viewer access to your environment in Red Hat Lightspeed.
Procedure
- From the Red Hat Lightspeed dashboard, navigate to Security > Vulnerability > Reports.
- Select Report by operating system versions.
- Click Create Report. The Vulnerability exposure by operating system dialog box displays.
- Select up to five versions of RHEL to compare in the report.
- Click Export PDF for a PDF report, or click Export CSV for a CSV-formatted file. The exported file downloads to your system automatically.
Chapter 5. Exporting vulnerability data as JSON, CSV, or PDF file
The vulnerability service enables you to export data for CVEs on systems in your RHEL infrastructure. After applying filters in the vulnerability service to view a specific set of CVEs or systems, you can export data based on those criteria.
These reports are accessible through the Red Hat Lightspeed service and can be exported and downloaded as .csv, .json, or PDF files.
5.1. Exporting CVE data from the vulnerability service
Perform the following steps to export select data from the vulnerability service.
Procedure
- Navigate to the Security > Vulnerability > CVEs page and log in if necessary.
- Apply filters and use the sorting functionality at the top of each column to locate specific CVEs.
-
Above the list of CVEs and to the right of the Filters menu, click the Export icon,
 , and select Export to JSON, Export to CSV, or Export as PDF based on your download preferences.
, and select Export to JSON, Export to CSV, or Export as PDF based on your download preferences.
- Select a download location and click Save.
Chapter 6. Enabling notifications and integrations
You can enable the notifications service in the Red Hat Hybrid Cloud Console to send notifications whenever a vulnerability event gets triggered. Using the notifications service frees you from having to continually check the Red Hat Lightspeed dashboard for event-triggered notifications. For example, you can configure the notifications service to:
- send an email message whenever a security issue affects systems in your installation
- send an email digest of all the vulnerability events that take place each day
In addition to sending email messages, you can configure the notifications service to send event data in other ways:
- Using an authenticated client to query Red Hat Lightspeed APIs for event data
- Using webhooks to send events to third-party applications that accept inbound requests
- Integrating notifications with applications such as Splunk to route event notifications to the application dashboard
Here are some of the ways administrators and users interact with the notifications service:
- A Notifications Administrator sets up behavior groups for events in the notifications service. Behavior groups specify the delivery method for each notification and whether the notifications are sent to all users, or just to Organization Administrators.
- An Organization Administrator creates a User access group with the Notifications Administrator role, and then adds account members to the group.
- Users who receive email notifications from events might set their user preferences so that they receive individual emails for each event, or a daily digest of events.
Additional resources
- For more information about how to set up notifications and integrations for Vulnerability events, see Configuring notifications on the Red Hat Hybrid Cloud Console and Integrating the Red Hat Hybrid Cloud Console with third-party applications.
Chapter 7. Reference materials
To learn more about the vulnerability service, or other Red Hat Lightspeed services and capabilities, the following resources might also be of interest:
Providing feedback on Red Hat documentation
We appreciate and prioritize your feedback regarding our documentation. Provide as much detail as possible, so that your request can be quickly addressed.
Prerequisites
- You are logged in to the Red Hat Customer Portal.
Procedure
To provide feedback, perform the following steps:
- Click the following link: Create Issue
- Describe the issue or enhancement in the Summary text box.
- Provide details about the issue or requested enhancement in the Description text box.
- Type your name in the Reporter text box.
- Click the Create button.
This action creates a documentation ticket and routes it to the appropriate documentation team. Thank you for taking the time to provide feedback.