Installation Guide
Installing Red Hat Enterprise Linux 7 on all architectures
Abstract
Chapter 1. Getting Started
1.1. Graphical Installation
1.2. Remote Installation
Connect Mode can be used to perform a graphical installation completely remotely. For systems with a display and keyboard, but without the capacity to run the graphical interface, Direct Mode can instead be used to facilitate setup. For more information, see the Chapter 25, Using VNC.
1.3. Automated Installation
Chapter 2. Downloading Red Hat Enterprise Linux
- Binary DVD
- A full installation image that boots the installation program and performs the entire installation without additional package repositories.
Note
Binary DVDs are also available for IBM Z. They can be used to boot the installation program using a SCSI DVD drive or as installation sources. - Boot.iso
- A minimal boot image that boots the installation program but requires access to additional package repositories. Red Hat does not provide the repository; you must create it using the full installation ISO image.
Note
Procedure 2.1. Downloading Red Hat Enterprise Linux ISO Images
- Visit the Customer Portal at https://access.redhat.com/home. If you are not logged in, click LOG IN on the right side of the page. Enter your account credentials when prompted.
- Click DOWNLOADS at the top of the page.
- Click Red Hat Enterprise Linux.
- Ensure that you select the appropriate Product Variant and Architecture for your installation target. By default,
Red Hat Enterprise Linux Serverandx86_64are selected. If you are not sure which variant best suits your needs, see http://www.redhat.com/en/technologies/linux-platforms/enterprise-linux. Additionally, a list of packages available for every variant is available in the Red Hat Enterprise Linux 7 Package Manifest. - A list of available downloads is displayed; most notably, a minimal Boot ISO image and a full installation Binary DVD ISO image. These files are described above. Additional images can be available, such as preconfigured virtual machine images, which are beyond the scope of this document.
- Choose the image file that you want to use. You have two ways to download it from the Customer Portal:
- Click its name to begin downloading it to your computer using your web browser.
- Right-click the name and then click or a similar menu item, the exact wording of which depends on the browser that you are using. This action copies the URL of the file to your clipboard, which allows you to use an alternative application to download the file to your computer. This approach is especially useful if your Internet connection is unstable: in that case, you browser might fail to download the whole file, and an attempt to resume the interrupted download process fails because the download link contains an authentication key which is only valid for a short time. Specialized applications such as curl can, however, be used to resume interrupted download attempts from the Customer Portal, which means that you need not download the whole file again and thus you save your time and bandwidth consumption.
Procedure 2.2. Using curl to Download Installation Media
- Make sure the curl package is installed by running the following command as root:
yum install curl
# yum install curlCopy to Clipboard Copied! Toggle word wrap Toggle overflow If your Linux distribution does not use yum, or if you do not use Linux at all, download the most appropriate software package from the curl web site. - Open a terminal window, enter a suitable directory, and type the following command:
curl -o filename.iso 'copied_link_location'
$ curl -o filename.iso 'copied_link_location'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace filename.iso with the ISO image name as displayed in the Customer Portal, such asrhel-server-7.0-x86_64-dvd.iso. This is important because the download link in the Customer Portal contains extra characters which curl would otherwise use in the downloaded file name, too. Then, keep the single quotation mark in front of the next parameter, and replace copied_link_location with the link that you have copied from the Customer Portal; copy it again if you copied the commands above in the meantime. Note that in Linux, you can paste the content of the clipboard into the terminal window by middle-clicking anywhere in the window, or by pressing Shift+Insert. Finally, use another single quotation mark after the last parameter, and press Enter to run the command and start transferring the ISO image. The single quotation marks prevent the command line interpreter from misinterpreting any special characters that might be included in the download link.Example 2.1. Downloading an ISO image with curl
The following is an example of a curl command line:curl -o rhel-server-7.0-x86_64-dvd.iso 'https://access.cdn.redhat.com//content/origin/files/sha256/85/85a...46c/rhel-server-7.0-x86_64-dvd.iso?_auth_=141...7bf'
$ curl -o rhel-server-7.0-x86_64-dvd.iso 'https://access.cdn.redhat.com//content/origin/files/sha256/85/85a...46c/rhel-server-7.0-x86_64-dvd.iso?_auth_=141...7bf'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the actual download link is much longer because it contains complicated identifiers. - If your Internet connection does drop before the transfer is complete, refresh the download page in the Customer Portal; log in again if necessary. Copy the new download link, use the same basic
curlcommand line parameters as earlier but be sure to use the new download link, and add-C -to instruct curl to automatically determine where it should continue based on the size of the already downloaded file.Example 2.2. Resuming an interrupted download attempt
The following is an example of a curl command line that you use if you have only partially downloaded the ISO image of your choice:curl -o rhel-server-7.0-x86_64-dvd.iso 'https://access.cdn.redhat.com//content/origin/files/sha256/85/85a...46c/rhel-server-7.0-x86_64-dvd.iso?_auth_=141...963' -C -
$ curl -o rhel-server-7.0-x86_64-dvd.iso 'https://access.cdn.redhat.com//content/origin/files/sha256/85/85a...46c/rhel-server-7.0-x86_64-dvd.iso?_auth_=141...963' -C -Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Optionally, you can use a checksum utility such as sha256sum to verify the integrity of the image file after the download finishes. All downloads on the Download Red Hat Enterprise Linux page are provided with their checksums for reference:
sha256sum rhel-server-7.0-x86_64-dvd.iso 85a...46c rhel-server-7.0-x86_64-dvd.iso
$ sha256sum rhel-server-7.0-x86_64-dvd.iso 85a...46c rhel-server-7.0-x86_64-dvd.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Similar tools are available for Microsoft Windows and Mac OS X. You can also use the installation program to verify the media when starting the installation; see Section 23.2.2, “Verifying Boot Media” for details.
- Burn it to a CD or DVD as described in Section 3.1, “Making an Installation CD or DVD”.
- Use it to create a bootable USB drive; see Section 3.2, “Making Installation USB Media”.
- Place it on a server to prepare for a network installation. For specific directions, see Section 3.3.3, “Installation Source on a Network”.
- Place it on a hard drive to use the drive as an installation source. For specific instructions, see Section 3.3.2, “Installation Source on a Hard Drive”.
- Use it to prepare a Preboot Execution Environment (PXE) server, which allows you to boot the installation system over a network. See Chapter 24, Preparing for a Network Installation for instructions.
Chapter 3. Making Media
Note
inst.stage2= boot option is used on the installation media and set to a specific label (for example, inst.stage2=hd:LABEL=RHEL7\x20Server.x86_64). If you modify the default label of the file system containing the runtime image, or if using a customized procedure to boot the installation system, you must ensure this option is set to the correct value. See Specifying the Installation Source for details.
3.1. Making an Installation CD or DVD
Note
3.2. Making Installation USB Media
3.2.1. Making Installation USB Media on Linux
Warning
Procedure 3.1. Making USB Media on Linux
- Connect a USB flash drive to the system and execute the
dmesgcommand. A log detailing all recent events will be displayed. At the bottom of this log, you will see a set of messages caused by the USB flash drive you just connected. It will look like a set of lines similar to the following:[ 170.171135] sd 5:0:0:0: [sdb] Attached SCSI removable disk
[ 170.171135] sd 5:0:0:0: [sdb] Attached SCSI removable diskCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note the name of the connected device - in the above example, it issdb. - Log in as
root:su -
$ su -Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provide your root password when prompted. - Make sure that the device is not mounted. First, use the
findmnt devicecommand and the device name you found in the earlier steps. For example, if the device name issdb, use the following command:findmnt /dev/sdb
# findmnt /dev/sdbCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the command displays no output, you can proceed with the next step. However, if the command does provide output, it means that the device was automatically mounted and you must unmount it before proceeding. A sample output will look similar to the following:findmnt /dev/sdb TARGET SOURCE FSTYPE OPTIONS /mnt/iso /dev/sdb iso9660 ro,relatime
# findmnt /dev/sdb TARGET SOURCE FSTYPE OPTIONS /mnt/iso /dev/sdb iso9660 ro,relatimeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note theTARGETcolumn. Next, use theumount targetcommand to unmount the device:umount /mnt/iso
# umount /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
ddcommand to write the installation ISO image directly to the USB device:dd if=/image_directory/image.iso of=/dev/device bs=blocksize
# dd if=/image_directory/image.iso of=/dev/device bs=blocksizeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace /image_directory/image.iso with the full path to the ISO image file you downloaded, device with the device name as reported by thedmesgcommand earlier, and blocksize with a reasonable block size (for example,512k) to speed up the writing process. Thebsparameter is optional, but it can speed up the process considerably.Important
Make sure to specify the output as the device name (for example,/dev/sda), not as a name of a partition on the device (for example,/dev/sda1).For example, if the ISO image is located in/home/testuser/Downloads/rhel-server-7-x86_64-boot.isoand the detected device name issdb, the command will look like the following:dd if=/home/testuser/Downloads/rhel-server-7-x86_64-boot.iso of=/dev/sdb bs=512k
# dd if=/home/testuser/Downloads/rhel-server-7-x86_64-boot.iso of=/dev/sdb bs=512kCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Wait for
ddto finish writing the image to the device. Note that no progress bar is displayed; the data transfer is finished when the#prompt appears again. After the prompt is displayed, log out from therootaccount and unplug the USB drive.
Note
inst.stage2= boot option is specified. Refer to Section 23.1, “Configuring the Installation System at the Boot Menu” for information about the inst.stage2= boot option.
3.2.2. Making Installation USB Media on Windows
Note
Important
Procedure 3.2. Making USB Media on Windows
- Download and install Fedora Media Writer.
- Download the Red Hat Enterprise Linux ISO image you want to use to create the media. (See Chapter 2, Downloading Red Hat Enterprise Linux for instructions on obtaining ISO images.)
- Plug in the USB drive you will be using to create bootable media.
- Open Fedora Media Writer.
- In the main window, click Custom Image and select the downloaded Red Hat Enterprise Linux ISO image.
- From the drop-down menu, select the drive you want to use. If the drive does not appear, verify that the USB drive is connected and restart Fedora Media Writer.
- Click Write to disk. The boot media creation process will begin. Do not unplug the drive until the operation completes. Depending on the size of the ISO image and the write speed of the USB drive, writing the image can take several minutes.
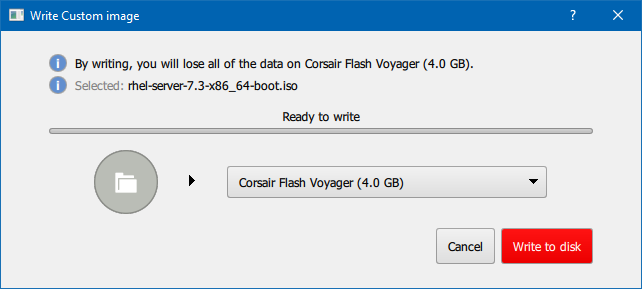
Figure 3.1. Fedora Media Writer
- When the creation process finishes and the
Complete!message appears, unmount the USB drive using the Safely remove hardware icon in the system's notification area.
3.2.3. Making Installation USB Media on Mac OS X
dd command line tool to write the installation image to a USB flash drive. Note that some steps involve use of the sudo command, which is only available when logged in with an administrator account that requires a password.
Warning
Procedure 3.3. Making USB Media on Mac OS X
- Connect a USB flash drive to the system and identify the device path with the
diskutil listcommand. The device path has the format of/dev/disknumber, where number is the number of the disk. The disks are numbered starting at zero (0). Disk 0 is likely to be the OS X recovery disk, and Disk 1 is likely to be your main OS X installation. In the following example, it isdisk2:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To identify your USB flash drive, compare theNAME,TYPEandSIZEcolumns to what you know about your flash drive. For example, theNAMEshould be the same as the title of the flash drive icon in the Finder. You can also compare these values to those in the flash drive's information panel; right-click on the drive icon and select Get Info. - Use the
diskutil unmountDiskcommand to unmount the flash drive's filesystem volumes:diskutil unmountDisk /dev/disknumber Unmount of all volumes on disknumber was successful
$ diskutil unmountDisk /dev/disknumber Unmount of all volumes on disknumber was successfulCopy to Clipboard Copied! Toggle word wrap Toggle overflow When you do this, the icon for the flash drive disappears from your desktop. If it does not, you might have identified the wrong disk. If you attempt to unmount the system disk accidentally, you get afailed to unmounterror. - Use the
ddcommand as a parameter of thesudocommand to write the ISO image to the flash drive:sudo dd if=/path/to/image.iso of=/dev/rdisknumber bs=1m>
$ sudo dd if=/path/to/image.iso of=/dev/rdisknumber bs=1m>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Mac OS X provides both a block (/dev/disk*) and character device (/dev/rdisk*) file for each storage device. Writing an image to the/dev/rdisknumbercharacter device is faster than to the/dev/disknumberblock device.Example 3.1. Writing an ISO Image to a Disk
To write the/Users/user_name/Downloads/rhel-server-7-x86_64-boot.isofile to the/dev/rdisk2device:sudo dd if=/Users/user_name/Downloads/rhel-server-7-x86_64-boot.iso of=/dev/rdisk2
$ sudo dd if=/Users/user_name/Downloads/rhel-server-7-x86_64-boot.iso of=/dev/rdisk2Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Wait for the command to finish. Note that no progress bar is displayed; however, to check the status of the operation while it is still running, press Ctrl+t in the terminal:
load: 1.02 cmd: dd 3668 uninterruptible 0.00u 1.91s 112+0 records in 111+0 records out 116391936 bytes transferred in 114.834860 secs (1013559 bytes/sec)
load: 1.02 cmd: dd 3668 uninterruptible 0.00u 1.91s 112+0 records in 111+0 records out 116391936 bytes transferred in 114.834860 secs (1013559 bytes/sec)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The speed of the data transfer depends on the speed of your USB ports and the flash drive. After the prompt is displayed again, the data transfer is finished. You can then unplug the flash drive.
3.3. Preparing Installation Sources
DVD: You can burn the binary DVD ISO image onto a DVD and configure the installation program to install packages from this disk.Hard drive: You can place the binary DVD ISO image on a hard drive and install packages from it.Network location: You can copy the binary DVD ISO image or the installation tree (extracted contents of the binary DVD ISO image) to a network location accessible from the installation system and perform the installation over the network using the following protocols:NFS: The binary DVD ISO image is placed into a Network File System (NFS) share.HTTPS,HTTPorFTP: The installation tree is placed on a network location accessible overHTTP,HTTPS, orFTP.
- In the installation program's graphical interface: After the graphical installation begins and you select your preferred language, the Installation Summary screen will appear. Navigate to the Installation Source screen and select the source you want to configure. For details, see:
- Section 8.11, “Installation Source” for 64-bit AMD, Intel, and ARM systems
- Section 13.12, “Installation Source” for IBM Power Systems servers
- Section 18.12, “Installation Source” for IBM Z
- Using a boot option: You can specify custom boot options to configure the installation program before it starts. One of these options allows you to specify the installation source to be used. See the
inst.repo=option in Section 23.1, “Configuring the Installation System at the Boot Menu” for details. - Using a Kickstart file: You can use the
installcommand in a Kickstart file and specify an installation source. See Section 27.3.1, “Kickstart Commands and Options” for details on theinstallKickstart command, and Chapter 27, Kickstart Installations for information about Kickstart installations in general.
3.3.1. Installation Source on a DVD
3.3.2. Installation Source on a Hard Drive
xfs, ext2, ext3, ext4, and vfat (FAT32). Note that on Microsoft Windows systems, the default file system used when formatting hard drives is NTFS, and the exFAT file system is also available; however, neither of these file systems can be mounted during the installation. If you are creating a hard drive or a USB drive to be used as an installation source on Microsoft Windows, make sure to format the drive as FAT32.
Important
FAT32 file system does not support files larger than 4 GiB. Some Red Hat Enterprise Linux 7 installation media can be larger than that, which means you cannot copy them to a drive with this file system.
3.3.3. Installation Source on a Network
3.3.3.1. Installation Source on an NFS Server
NFS installation method uses an ISO image of the Red Hat Enterprise Linux binary DVD placed in a Network File System server's exported directory, which the installation system must be able to read. To perform an NFS-based installation, you will need another running system which will act as the NFS host.
Procedure 3.4. Preparing for Installation Using NFS
- Install the nfs-utils package by running the following command as
root:yum install nfs-utils
# yum install nfs-utilsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the full Red Hat Enterprise Linux 7 binary DVD ISO image to a suitable directory on the NFS server. For example, you can create directory
/rhel7-install/for this purpose and save the ISO image here. - Open the
/etc/exportsfile using a text editor and add a line with the following syntax:/exported_directory/ clients
/exported_directory/ clientsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace /exported_directory/ with the full path to the directory holding the ISO image. Instead of clients, use the host name or IP address of the computer which is to be installed from this NFS server, the subnetwork from which all computers are to have access the ISO image, or the asterisk sign (*) if you want to allow any computer with network access to the NFS server to use the ISO image. See theexports(5)man page for detailed information about the format of this field.The following is a basic configuration which makes the/rhel7-install/directory available as read-only to all clients:/rhel7-install *
/rhel7-install *Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the
/etc/exportsfile after finishing the configuration and exit the text editor. - Start the
nfsservice:systemctl start nfs.service
# systemctl start nfs.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the service was already running before you changed the/etc/exportsfile, enter the following command instead, in order for the running NFS server to reload its configuration:systemctl reload nfs.service
# systemctl reload nfs.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow
NFS and ready to be used as an installation source.
nfs: as the protocol, the server's host name or IP address, the colon sign (:), and the directory holding the ISO image. For example, if the server's host name is myserver.example.com and you have saved the ISO image in /rhel7-install/, specify nfs:myserver.example.com:/rhel7-install/ as the installation source.
3.3.3.2. Installation Source on an HTTP, HTTPS or FTP Server
.treeinfo file. The installation source is accessed over HTTP, HTTPS, or FTP.
Procedure 3.5. Preparing Installation Using HTTP or HTTPS
- Install the httpd package by running the following command as
root:yum install httpd
# yum install httpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow AnHTTPSserver needs additional configuration. For detailed information, see section Setting Up an SSL Server in the Red Hat Enterprise Linux 7 System Administrator's Guide. However,HTTPSis not necessary in most cases, because no sensitive data is sent between the installation source and the installer, andHTTPis sufficient.Warning
If your Apache web server configuration enables SSL security, make sure to only enable theTLSv1protocol, and disableSSLv2andSSLv3. This is due to the POODLE SSL vulnerability (CVE-2014-3566). See https://access.redhat.com/solutions/1232413 for details.Important
If you decide to useHTTPSand the server is using a self-signed certificate, you must boot the installer with thenoverifyssloption. - Copy the full Red Hat Enterprise Linux 7 binary DVD ISO image to the HTTP(S) server.
- Mount the binary DVD ISO image, using the
mountcommand, to a suitable directory:mount -o loop,ro -t iso9660 /image_directory/image.iso /mount_point/
# mount -o loop,ro -t iso9660 /image_directory/image.iso /mount_point/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace /image_directory/image.iso with the path to the binary DVD ISO image, and /mount_point/ with the path to the directory in which you want the content of the ISO image to appear. For example, you can create directory/mnt/rhel7-install/for this purpose and use that as the parameter of themountcommand. - Copy the files from the mounted image to the HTTP server root.
cp -r /mnt/rhel7-install/ /var/www/html/
# cp -r /mnt/rhel7-install/ /var/www/html/Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates the/var/www/html/rhel7-install/directory with the content of the image. - Start the
httpdservice:systemctl start httpd.service
# systemctl start httpd.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow
http:// or https:// as the protocol, the server's host name or IP address, and the directory in which you have stored the files from the ISO image, relative to the HTTP server root. For example, if you are using HTTP, the server's host name is myserver.example.com, and you have copied the files from the image to /var/www/html/rhel7-install/, specify http://myserver.example.com/rhel7-install/ as the installation source.
Procedure 3.6. Preparing for Installation Using FTP
- Install the vsftpd package by running the following command as
root:yum install vsftpd
# yum install vsftpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, open the
/etc/vsftpd/vsftpd.confconfiguration file in a text editor, and edit any options you want to change. For available options, see thevsftpd.conf(5)man page. The rest of this procedure assumes that default options are used; notably, to follow the rest of the procedure, anonymous users of the FTP server must be permitted to download files.Warning
If you configured SSL/TLS security in yourvsftpd.conffile, make sure to only enable theTLSv1protocol, and disableSSLv2andSSLv3. This is due to the POODLE SSL vulnerability (CVE-2014-3566). See https://access.redhat.com/solutions/1234773 for details. - Copy the full Red Hat Enterprise Linux 7 binary DVD ISO image to the FTP server.
- Mount the binary DVD ISO image, using the
mountcommand, to a suitable directory:mount -o loop,ro -t iso9660 /image_directory/image.iso /mount_point
# mount -o loop,ro -t iso9660 /image_directory/image.iso /mount_pointCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace /image_directory/image.iso with the path to the binary DVD ISO image, and /mount_point with the path to the directory in which you want the content of the ISO image to appear. For example, you can create directory/mnt/rhel7-install/for this purpose and use that as the parameter of themountcommand. - Copy the files from the mounted image to the FTP server root:
cp -r /mnt/rhel7-install/ /var/ftp/
# cp -r /mnt/rhel7-install/ /var/ftp/Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates the/var/ftp/rhel7-install/directory with the content of the image. - Start the
vsftpdservice:systemctl start vsftpd.service
# systemctl start vsftpd.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the service was already running before you changed the/etc/vsftpd/vsftpd.conffile, restart it to ensure the edited file is loaded. To restart, execute the following command:systemctl restart vsftpd.service
# systemctl restart vsftpd.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow
ftp:// as the protocol, the server's host name or IP address, and the directory in which you have stored the files from the ISO image, relative to the FTP server root. For example, if the server's host name is myserver.example.com and you have copied the files from the image to /var/ftp/rhel7-install/, specify ftp://myserver.example.com/rhel7-install/ as the installation source.
3.3.3.3. Firewall Considerations for Network-based Installations
| Protocol used | Ports to open |
|---|---|
FTP | 21 |
HTTP | 80 |
HTTPS | 443 |
NFS | 2049, 111, 20048 |
TFTP | 69 |
Part I. AMD64, Intel 64, and ARM 64 - Installation and Booting
Chapter 4. Quick Installation Guide
4.1. Interactive Installation
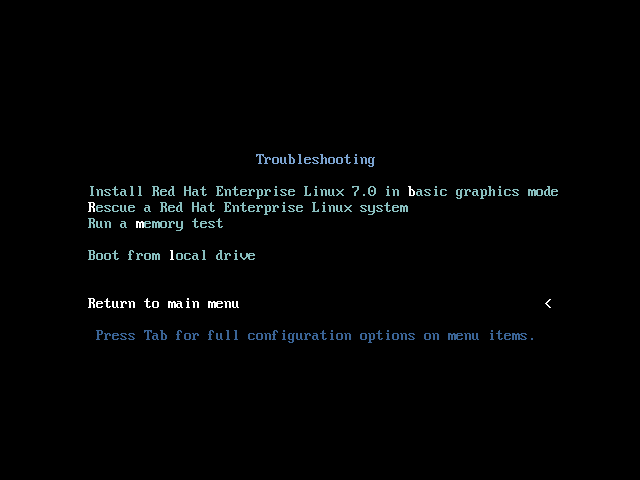
- Select Install Red Hat Enterprise Linux in the boot menu and press Enter.
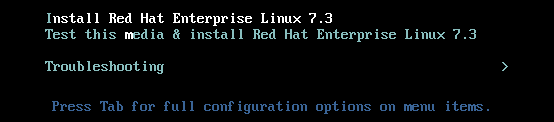
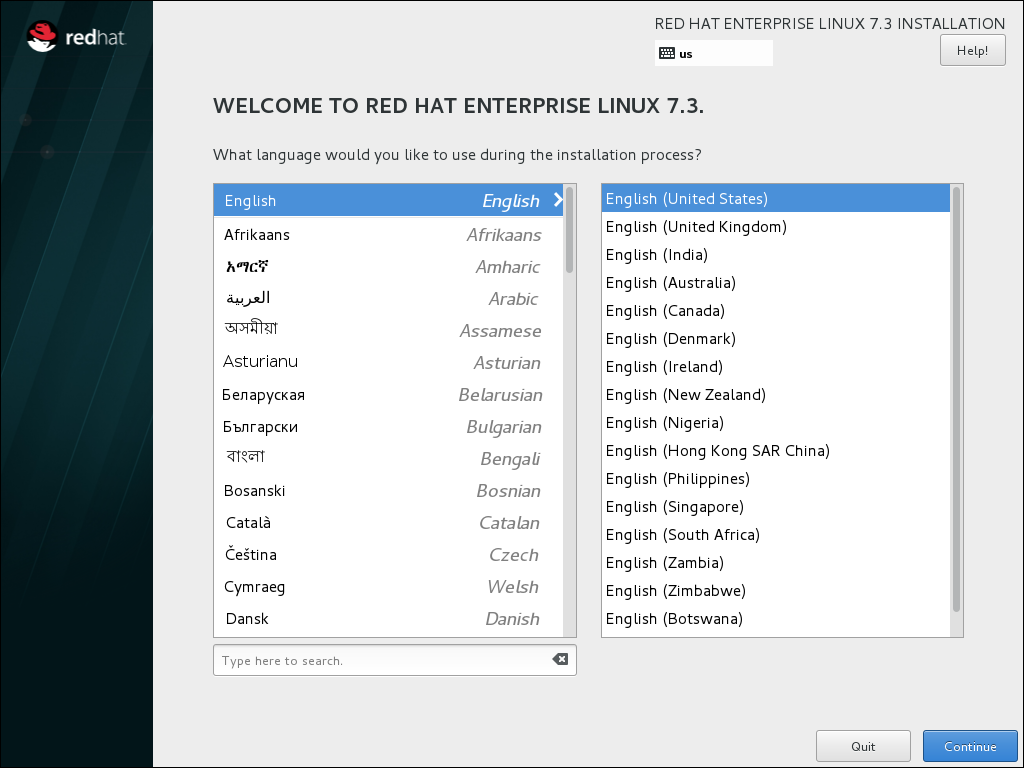
- After Anaconda, the Red Hat Enterprise Linux installer, started, select your language and region, and click Continue.
- The Installation Summary is the central screen to set configuration options:
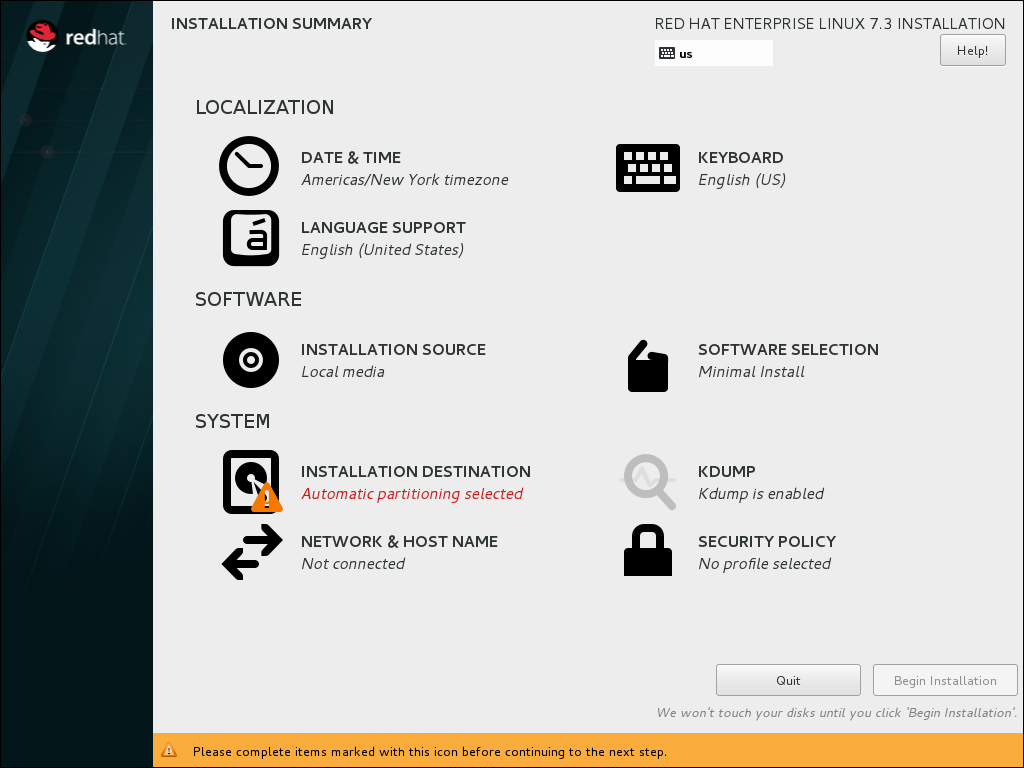 You can display and modify the individual options in any order. If a configuration option was automatically configured correctly, no further action is required. However, if items are marked with an exclamation point icon, you must complete the configuration for these items before you can begin the installation.
You can display and modify the individual options in any order. If a configuration option was automatically configured correctly, no further action is required. However, if items are marked with an exclamation point icon, you must complete the configuration for these items before you can begin the installation.Note
Nothing will be written to the disk until you click the button. - Select Date & Time:
- Set your region and the nearest city in your time zone.
- Click to return to the Installation Summary.
- Select :
- Use the and buttons to add and remove keyboard layouts.
- If you enable multiple keyboard layouts, move your preferred layout to the top of the list using the button to set it as default.
- Click to return to the Installation Summary.
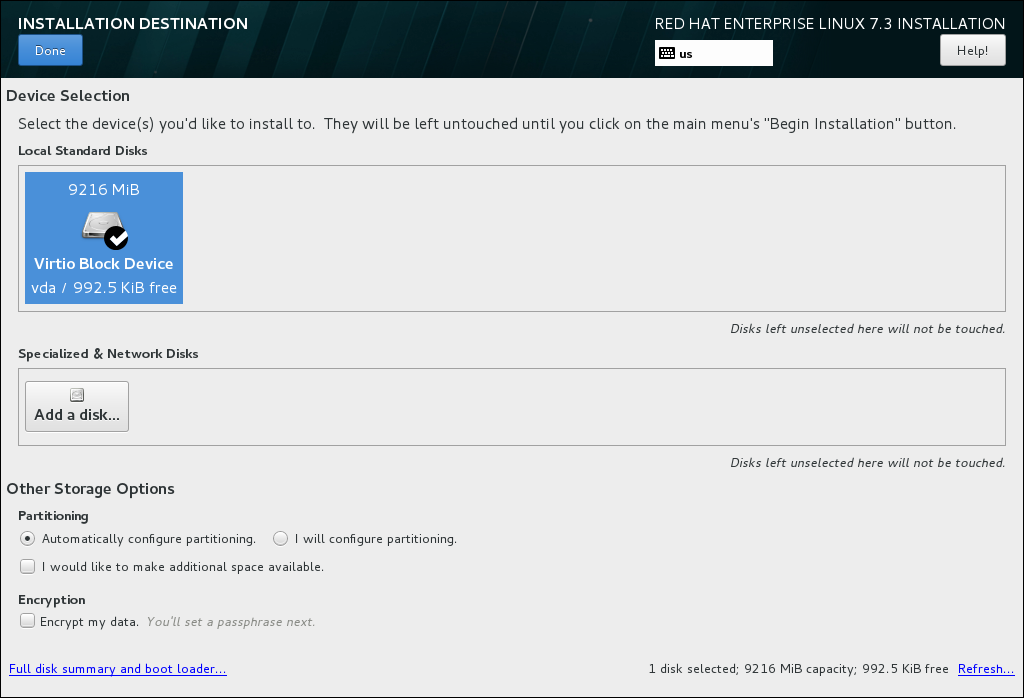
- Select Installation Destination:
- Select the target disk. A check mark is displayed next to the selected target.The selected disk is partitioned automatically.
- Click to return to the Installation Summary.
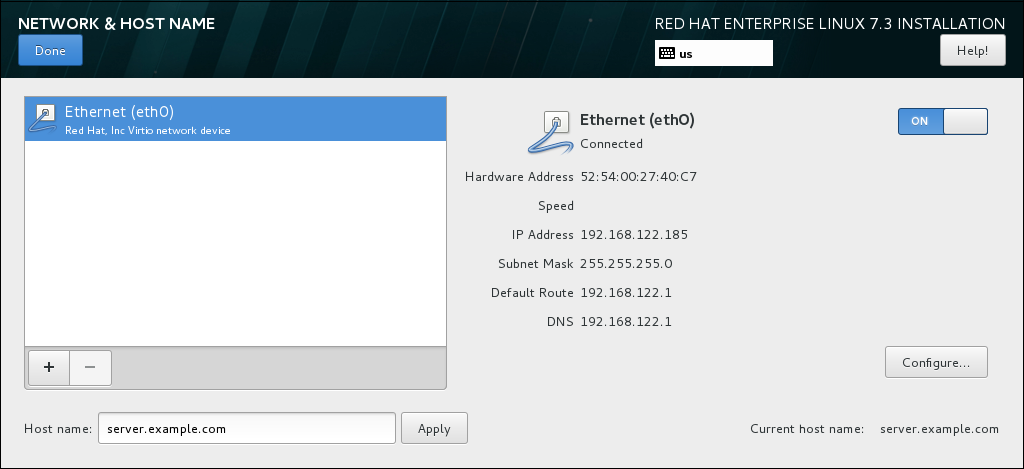
- Select Network and Hostname:
- Click the Ethernet sliding switch in the top right corner to enable the network configuration.
- Optional, select the device and click to update the network interface configuration.
- Click to return to the Installation Summary.
Note
Anaconda applies the network settings immediately. They are used during the setup and after the installation. - On the Installation Summary screen, click .
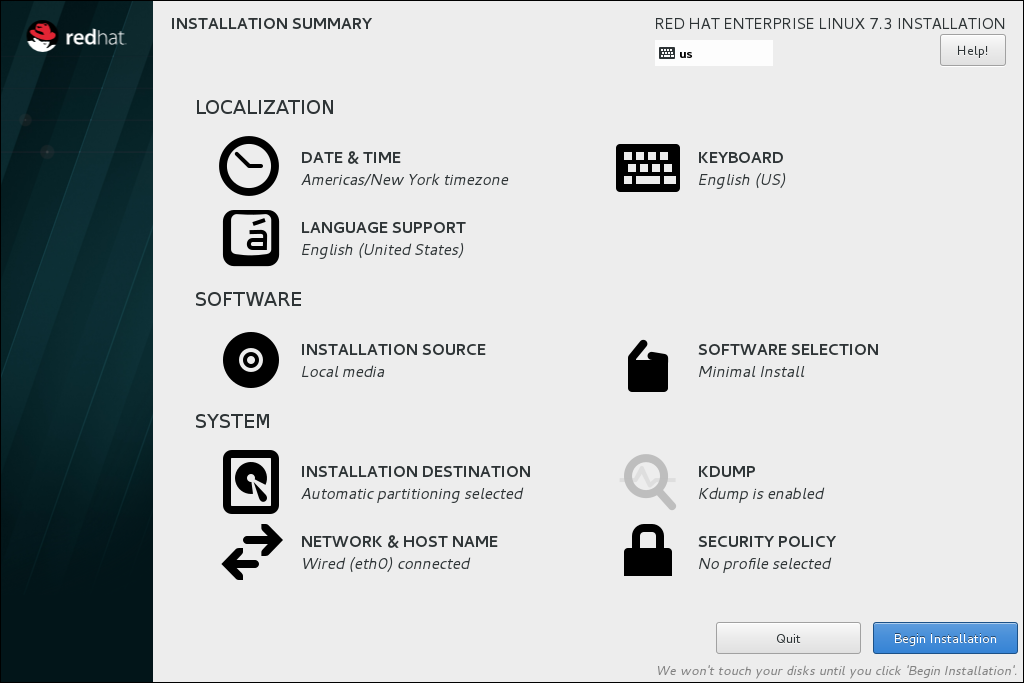
- The installation starts and the Configuration screen is displayed:
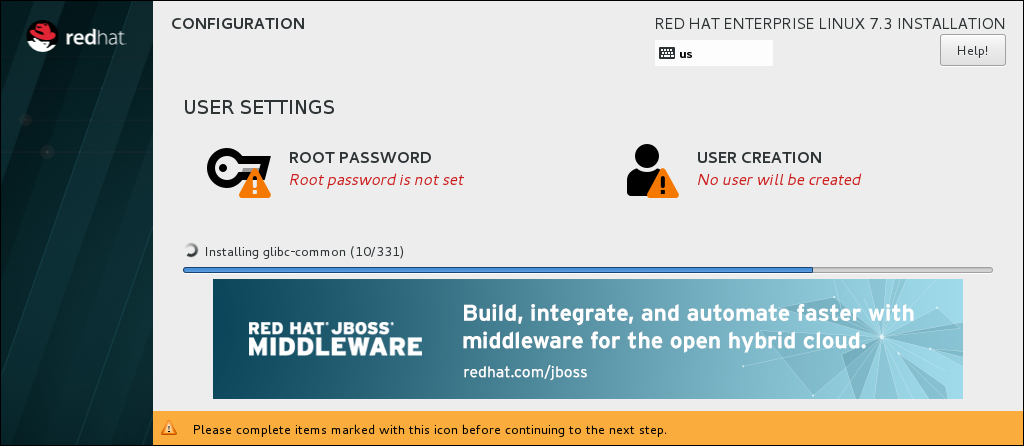 During the installation:
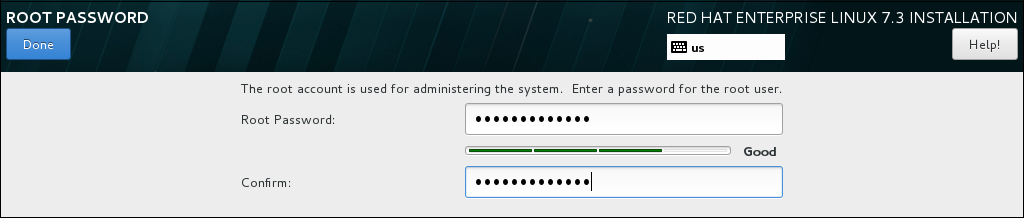
During the installation:- Select Root Password:
- Enter the password for the
rootuser and confirm it. - Click to return to the Configuration screen.
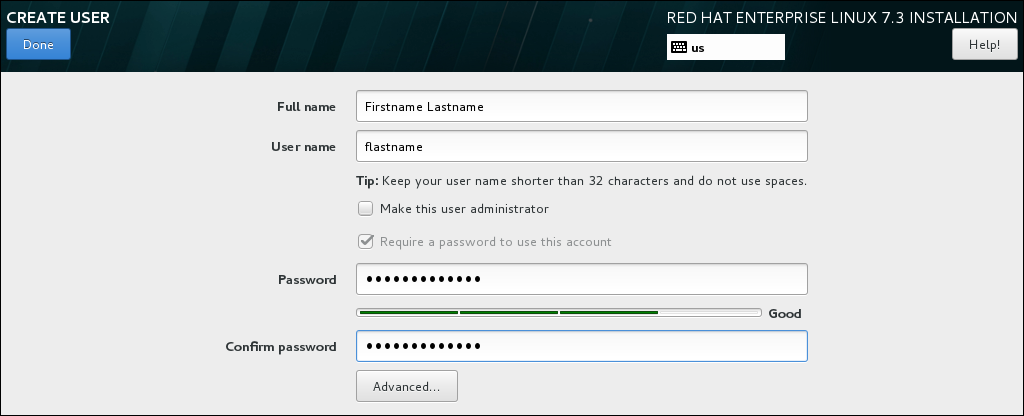
- Select User Creation:
- Enter the user's full name.
- Optionally, update the automatically generated user name.
- Set the password and confirm it.
- Optionally, check the Make this user administrator check box. This will add the user to the
wheelgroup and allow this account to usesudowithout any further configuration. - Click to return to the Configuration screen.
- Wait until the installation completes and click .
- After the installed system has been started:
- If you installed the server using the Server with GUI base environment, the Initial Setup application is started automatically:
- Accept the license agreement.
- Register the system.
For details, see Chapter 30, Initial Setup. - If you selected any other base environment during the installation:
- Log into the system as the
rootuser. - Register the system and automatically attach a subscription:
subscription-manager register --auto-attach \ --username=user_name --password=password
# subscription-manager register --auto-attach \ --username=user_name --password=passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.2. Automatic Installation
Generating the USB Boot Media
- Record an installation in a Kickstart file:
- Manually install Red Hat Enterprise Linux once. For details see Section 4.1, “Interactive Installation”.
- Boot the installed system. During the installation, Anaconda created a Kickstart file with the settings in the
/root/anaconda-ks.cfgfile.
- Download the Red Hat Enterprise Linux installation DVD ISO file to the
/tmp/directory. - Mount the installation ISO file to the
/mnt/directory. For example:mount -o loop /tmp/rhel-server-7.3-x86_64-dvd.iso /mnt/
# mount -o loop /tmp/rhel-server-7.3-x86_64-dvd.iso /mnt/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Create a working directory and copy the DVD content to it. For example:
mkdir /root/rhel-install/ shopt -s dotglob cp -avRf /mnt/* /root/rhel-install/
# mkdir /root/rhel-install/ # shopt -s dotglob # cp -avRf /mnt/* /root/rhel-install/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Unmount the ISO file:
umount /mnt/
# umount /mnt/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the Kickstart file generated during the installation to the working directory:
cp /root/anaconda-ks.cfg /root/rhel-install/
# cp /root/anaconda-ks.cfg /root/rhel-install/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To register Red Hat Enterprise Linux after the installation automatically and attach a subscription, append the following to the
/root/rhel-install/anaconda-ks.cfgfile:%post subscription-manager register --auto-attach --username=user_name --password=password %end
%post subscription-manager register --auto-attach --username=user_name --password=password %endCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Display the installation DVD volume name:
isoinfo -d -i rhel-server-7.3-x86_64-dvd.iso | grep "Volume id" | \ sed -e 's/Volume id: //' -e 's/ /\\x20/g' RHEL-7.3\x20Server.x86_64
# isoinfo -d -i rhel-server-7.3-x86_64-dvd.iso | grep "Volume id" | \ sed -e 's/Volume id: //' -e 's/ /\\x20/g' RHEL-7.3\x20Server.x86_64Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Add a new menu entry to the boot
/root/rhel-install/isolinux/isolinux.cfgfile that uses the Kickstart file. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Set theinst.stage2=hd:LABEL=andinst.ks=hd:LABEL=options to the DVD volume name retrieved in the previous step. - Before you create the
/root/rhel-ks.isofile from the working directory, execute the following steps for a USB UEFI boot or for a CDROM UEFI boot:- For a USB UEFI boot, follow the steps:
- Mount the volume:
mount /root/rhel-install/images/efiboot.img /mnt/
# mount /root/rhel-install/images/efiboot.img /mnt/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the file
/mnt/EFI/BOOT/grub.cfg: - Add a new menu entry:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Unmount the volume:
umount /mnt
# umount /mntCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- For a CDROM UEFI boot, follow the steps:
- Edit the file
/root/rhel-install/EFI/BOOT/grub.cfg: - Add a new menu entry to the file:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Create the
/root/rhel-ks.isofile from the working directory:mkisofs -untranslated-filenames -volid "RHEL-7.3 Server.x86_64" -J -joliet-long -rational-rock -translation-table -input-charset utf-8 -b isolinux/isolinux.bin -c isolinux/boot.cat -no-emul-boot -boot-load-size 4 -boot-info-table -eltorito-alt-boot -e images/efiboot.img -no-emul-boot -o /root/rhel-ks.iso -graft-points /root/rhel-install/
# mkisofs -untranslated-filenames -volid "RHEL-7.3 Server.x86_64" -J -joliet-long -rational-rock -translation-table -input-charset utf-8 -b isolinux/isolinux.bin -c isolinux/boot.cat -no-emul-boot -boot-load-size 4 -boot-info-table -eltorito-alt-boot -e images/efiboot.img -no-emul-boot -o /root/rhel-ks.iso -graft-points /root/rhel-install/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Set the-Voption to the DVD volume name retrieved in an earlier step and replace\x20in the string with a space. - Make the ISO image created by the command `mkisofs` bootable:
isohybrid --uefi /root/rhel-ks.iso
# isohybrid --uefi /root/rhel-ks.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Create an installation USB drive. For details, see Section 3.2.1, “Making Installation USB Media on Linux”.
Install Red Hat Enterprise Linux Using the Kickstart File
- Boot the installation USB drive. See Chapter 7, Booting the Installation on 64-bit AMD, Intel, and ARM systems.
- Select the entry with the Kickstart configuration that you created in Section 4.2, “Automatic Installation”.
Chapter 5. Planning for Installation on 64-bit AMD, Intel, and ARM Systems
5.1. Upgrade or Install?
- Clean Install
- A clean install is performed by backing up all data from the system, formatting disk partitions, performing an installation of Red Hat Enterprise Linux from installation media, and then restoring any user data.
Note
This is the recommended method for upgrading between major versions of Red Hat Enterprise Linux. - In-Place Upgrade
- An in-place upgrade is a way of upgrading your system without removing the older version first. The procedure requires installing the migration utilities available for your system and running them as any other software. In Red Hat Enterprise Linux, the Preupgrade Assistant assesses your current system and identifies potential problems you might encounter during or after the upgrade. It also performs minor fixes and modifications to the system. The Red Hat Upgrade Tool utility downloads the packages and performs the actual upgrade. An in-place upgrade requires a lot of troubleshooting and planning and should only be done if there is no other choice. For more information on the Preupgrade Assistant, see Chapter 29, Upgrading Your Current System.
Warning
Never perform an in-place upgrade on a production system without first testing it on a cloned backup copy of the system.
5.2. Is Your Hardware Compatible?
5.3. Supported Installation Targets
- Storage connected by a standard internal interface, such as SCSI, SATA, or SAS
- BIOS/firmware RAID devices
- NVDIMM devices in sector mode on the Intel64 and AMD64 architectures, supported by the
nd_pmemdriver. - Fibre Channel Host Bus Adapters and multipath devices. Some can require vendor-provided drivers.
- Xen block devices on Intel processors in Xen virtual machines.
- VirtIO block devices on Intel processors in KVM virtual machines.
5.4. System Specifications List
- If you plan to use a customized partition layout, record:
- The model numbers, sizes, types, and interfaces of the hard drives attached to the system. For example, Seagate ST3320613AS 320 GB on SATA0, Western Digital WD7500AAKS 750 GB on SATA1. This will allow you to identify specific hard drives during the partitioning process.
- If you are installing Red Hat Enterprise Linux as an additional operating system on an existing system, record:
- Information about the partitions used on the system. This information can include file system types, device node names, file system labels, and sizes. This will allow you to identify specific partitions during the partitioning process. Remember that different operating systems identify partitions and drives differently, therefore even if the other operating system is a Unix operating system, the device names can be reported by Red Hat Enterprise Linux differently. This information can usually be found by executing the equivalent of the
mountcommand andblkidcommand and in the/etc/fstabfile.If you have other operating systems already installed, the Red Hat Enterprise Linux 7 installation program attempts to automatically detect and configure to boot them. You can manually configure any additional operating systems if they are not detected properly. For more information, see Section 8.14.1, “Boot Loader Installation”.
- If you plan to install from an image on a local hard drive:
- The hard drive and directory that holds the image.
- If you plan to install from a network location:
- The make and model numbers of the network adapters on your system. For example, Netgear GA311. This will allow you to identify adapters when manually configuring the network.
- IP, DHCP, and BOOTP addresses
- Netmask
- Gateway IP address
- One or more name server IP addresses (DNS)
- The location of the installation source on an FTP server, HTTP (web) server, HTTPS (web) server, or NFS server.
If any of these networking requirements or terms are unfamiliar to you, contact your network administrator for assistance. - If you plan to install on an iSCSI target:
- The location of the iSCSI target. Depending on your network, you might also need a CHAP user name and password, and perhaps a reverse CHAP user name and password.
- If your computer is part of a domain:
- You should verify that the domain name will be supplied by the DHCP server. If not, you will need to input the domain name manually during installation.
5.5. Disk Space and Memory Requirements
Note
/ and swap) must be dedicated to Red Hat Enterprise Linux.
| Installation type | Minimum required RAM |
|---|---|
| Local media installation (USB, DVD) | 768 MiB |
| NFS network installation | 768 MiB |
| HTTP, HTTPS, or FTP network installation | 1.5 GiB |
Note
5.6. RAID and Other Disk Devices
5.6.1. Hardware RAID
5.6.2. Software RAID
Note
5.6.3. USB Disks
5.6.4. NVDIMM devices
- Version of Red Hat Enterprise Linux is 7.6 or later.
- The architecture of the system is Intel 64 or AMD64.
- The device is configured to sector mode. Anaconda can reconfigure NVDIMM devices to this mode.
- The device must be supported by the
nd_pmemdriver.
- The system uses UEFI.
- The device must be supported by firmware available on the system, or by a UEFI driver. The UEFI driver may be loaded from an option ROM of the device itself.
- The device must be made available under a namespace.
/boot and /boot/efi directories on the device. See Section 8.14.4, “Manual Partitioning” for more information. Note that the Execute-in-place (XIP) feature of NVDIMM devices is not supported during booting and the kernel is loaded into conventional memory.
5.6.5. Considerations for Intel BIOS RAID Sets
/etc/fstab, /etc/crypttab or other configuration files which refer to devices by their device node paths might not work in Red Hat Enterprise Linux 7. Therefore, you should replace device node paths (such as /dev/sda) with file system labels or device UUIDs instead. You can find the file system labels and device UUIDs using the blkid command.
5.6.6. Considerations for Intel BIOS iSCSI Remote Boot
5.7. Choose an Installation Boot Method
Note
%post section of a kickstart file.
- Full installation DVD or USB drive
- You can create bootable media from the full installation DVD ISO image. In this case, a single DVD or USB drive can be used to complete the entire installation - it will serve both as a boot device and as an installation source for installing software packages. See Chapter 3, Making Media for instructions on how to make a full installation DVD or USB drive.
- Minimal boot CD, DVD or USB Flash Drive
- A minimal boot CD, DVD or USB flash drive is created using a small ISO image, which only contains data necessary to boot the system and start the installation. If you use this boot media, you will need an additional installation source from which packages will be installed. See Section 3.2, “Making Installation USB Media” for instructions on making boot CDs, DVDs and USB flash drives.
- PXE Server
- A preboot execution environment (PXE) server allows the installation program to boot over the network. After you boot the system, you complete the installation from a different installation source, such as a local hard drive or a location on a network. For more information on PXE servers, see Chapter 24, Preparing for a Network Installation.
5.8. Automating the Installation with Kickstart
5.9. Using a Beta Release with UEFI Secure Boot
Note
Procedure 5.1. Adding a Custom Private Key for UEFI Secure Boot
- First, disable UEFI Secure Boot on the system, and install Red Hat Enterprise Linux 7 normally.
- After the installation finishes, the system will reboot. Secure Boot should still be disabled at this point. Reboot the system, log in and, if applicable, go through the Initial Setup screens as described in Chapter 30, Initial Setup.
- After finishing the first boot and going through Initial Setup, install the kernel-doc package if not installed already:
yum install kernel-doc
# yum install kernel-docCopy to Clipboard Copied! Toggle word wrap Toggle overflow This package provides a certificate file which contains the Red Hat CA public Beta key, located in/usr/share/doc/kernel-keys/kernel-version/kernel-signing-ca.cer, where kernel-version is the kernel version string without the platform architecture suffix - for example,3.10.0-686.el7. - Execute the following commands to enroll the public key into the system Machine Owner Key (MOK) list:
kr=$(uname -r) mokutil --import /usr/share/doc/kernel-keys/${kr%.$(uname -p)}/kernel-signing-ca.cer# kr=$(uname -r) # mokutil --import /usr/share/doc/kernel-keys/${kr%.$(uname -p)}/kernel-signing-ca.cerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enter a password of your choosing when prompted.Note
Make sure to remember the password. It is required to finish this procedure as well as to remove the imported key when it is no longer needed. - Reboot the system again. During startup you will be prompted to confirm that you want to complete the pending key enrollment request. Select yes, and provide the password which you set earlier using the
mokutilcommand in the previous step. The system will reboot again after you do so, and the key will be imported into the system firmware. You can turn on Secure Boot on this or any subsequent reboot.
Warning
mokutil --reset
# mokutil --resetChapter 6. Updating Drivers During Installation on AMD64 and Intel 64 Systems
Important
- place the ISO image file of the driver disc in a location accessible to the installation program, on a local hard drive, on a USB flash drive, or on a CD or DVD.
- create a driver disc by extracting the image file onto a CD or a DVD, or a USB flash drive. See the instructions for making installation discs in Section 3.1, “Making an Installation CD or DVD” for more information on burning ISO image files to a CD or DVD, and Section 3.2, “Making Installation USB Media” for instructions on writing ISO images to USB drives.
Warning
6.1. Limitations of Driver Updates During Installation
6.2. Preparing for a Driver Update During Installation
- Automatic driver update
- When starting the installation, the Anaconda installation program will attempt to detect all attached storage devices. If there is a storage device labeled
OEMDRVpresent when the installation begins, Anaconda will always treat it like a driver update disc and attempt to load drivers present on it. - Assisted driver update
- You can specify the
inst.ddboot option when starting the installation. If you use this option without any parameters, Anaconda will display a list of all storage devices connected to the system, and it will prompt you to select a device which contains a driver update. - Manual driver update
- You can specify the
inst.dd=locationboot option when starting the installation, where location is the path to a driver update disc or ISO image. When you specify this option, Anaconda will attempt to load any driver updates it finds at the specified location. With manual driver updates, you can specify either locally available storage devices, or a network location (anHTTP,HTTPSorFTPserver).
Note
inst.dd=location and inst.dd at the same time. However, what Anaconda does in this case depends on the type of location that you use. If it is a device, Anaconda prompts you to select drivers to update from the specified device and then it offers you additional devices. If location is a network location, Anaconda first prompts you to select a device containing a driver update and then it lets you update drivers from the specified network location.
OEMDRV, and it must be physically connected to the installation system. To use the assisted method, you can use any local storage device any label other than OEMDRV. To use the manual method, you can use any local storage with a different label, or a network location accessible from the installation system.
Important
ip= option when loading a driver update from a network location. See Section 23.1, “Configuring the Installation System at the Boot Menu” for details.
6.2.1. Preparing to Use a Driver Update Image File on Local Storage
- In order for the installation program to automatically recognize the driver disk, the volume label of the storage device must be
OEMDRV. Also, you will need to extract the contents of the ISO image file to the root directory of the storage device rather than copy the ISO image itself. See Section 6.3.1, “Automatic Driver Update”. Note that installation of a driver from a device labeledOEMDRVis always recommended and preferable to the manual installation. - For manual installation, simply copy the ISO image, as a single file, onto the storage device. You can rename the file if you find it helpful but you must not change the file name extension, which must remain
.iso, for exampledd.iso. See Section 6.3.3, “Manual Driver Update” to learn how to select the driver update manually during installation.
6.2.2. Preparing a Driver Disc
rhdd3, which is a signature file that contains the driver disc's description, and a directory named rpms, which contains the RPM packages with the actual drivers for various architectures.
.iso, then you have not created the disc correctly and should try again. Ensure that you choose an option similar to Burn from Image if you use a Linux desktop other than GNOME, or if you use a different operating system.
6.3. Performing a Driver Update During Installation
- let the installation program automatically find and offer a driver update for installation,
- let the installation program prompt you to locate a driver update,
- manually specify a path to a driver update image or an RPM package.
Important
6.3.1. Automatic Driver Update
OEMDRV volume label to your computer before starting the installation process.
Note
OEMDRV block device to automatically load a Kickstart file. This file must be named ks.cfg and placed in the root of the device to be loaded. See Chapter 27, Kickstart Installations for more information about Kickstart installations.
OEMDRV, it will treat it as a driver update disc and attempt to load driver updates from this device. You will be prompted to select which drivers to load:
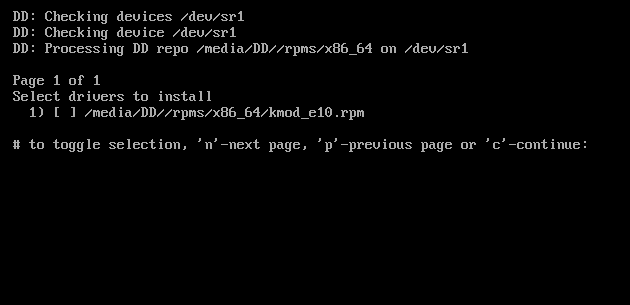
Figure 6.1. Selecting a Driver
6.3.2. Assisted Driver Update
OEMDRV volume label available to install a driver during installation. However, if no such device is detected and the inst.dd option was specified at the boot command line, the installation program lets you find the driver disk in interactive mode. In the first step, select a local disk partition from the list for Anaconda to scan for ISO files. Then, select one of the detected ISO files. Finally, select one or more available drivers. The image below demonstrates the process in the text user interface with individual steps highlighted.
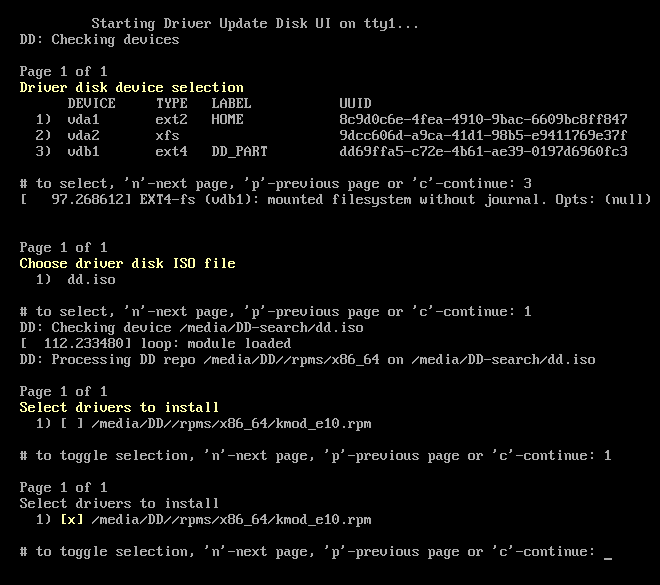
Figure 6.2. Selecting a Driver Interactively
Note
OEMDRV volume label, either use the inst.dd option with no arguments and use the menu to select the device, or use the following boot option for the installation program to scan the media for drivers:
inst.dd=/dev/sr0
inst.dd=/dev/sr06.3.3. Manual Driver Update
inst.dd=location to it, where location is a path to the driver update disc:
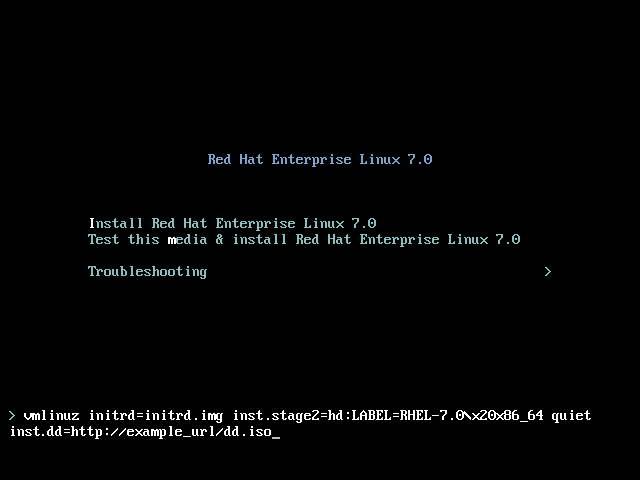
Figure 6.3. Specifying a Path to a Driver Update
6.3.4. Blacklisting a Driver
modprobe.blacklist=driver_name option to it. Replace driver_name with names of a driver or drivers you want to disable, for example:
modprobe.blacklist=ahci
modprobe.blacklist=ahcimodprobe.blacklist= boot option will remain disabled on the installed system and appear in the /etc/modprobe.d/anaconda-blacklist.conf file. See Chapter 23, Boot Options for more information about blacklisting drivers and other boot options.
Chapter 7. Booting the Installation on 64-bit AMD, Intel, and ARM systems
NFS, FTP, HTTP, or HTTPS methods. Booting and installing from the full installation DVD is the easiest method to get started with. Other methods require some additional setup but provide different advantages that might suit your needs better. For example, when installing Red Hat Enterprise Linux on a large number of computers at the same time, the best approach is booting from a PXE server and installing from a source in a shared network location.
| Boot method | Installation source |
|---|---|
| Full installation media (DVD or USB) | The boot media itself |
| Minimal boot media (CD or USB) | Full installation DVD ISO image or the installation tree extracted from this image, placed in a network location or on a hard drive |
| Network boot (PXE) | Full installation DVD ISO image or the installation tree extracted from this image, placed in a network location |
- Section 7.1.1, “Booting from Physical Media” describes how to boot the installation program using physical media (Red Hat Enterprise Linux DVD, Boot CD-ROM, USB flash drive).
- Section 7.1.2, “Booting from the Network Using PXE” describes how to boot the installation program using PXE.
- Section 7.2, “The Boot Menu” contains information on the boot menu.
7.1. Starting the Installation Program
Important
Note
7.1.1. Booting from Physical Media
Procedure 7.1. Booting the Installation from Physical Media
- Disconnect any drives which you do not need for the installation. See Section 5.6.3, “USB Disks” for more information.
- Power on your computer system.
- Insert the media in your computer.
- Power off your computer with the boot media still inside.
- Power on your computer system. Note that you might need to press a specific key or combination of keys to boot from the media or configure your system's Basic Input/Output System (BIOS) to boot from the media. For more information, see the documentation that came with your system.
7.1.2. Booting from the Network Using PXE
Network Boot or Boot Services. Also, ensure that the BIOS is configured to boot first from the correct network interface. Some BIOS systems specify the network interface as a possible boot device, but do not support the PXE standard. See your hardware's documentation for more information. Once you properly enable PXE booting, the computer can boot the Red Hat Enterprise Linux installation system without any other media.
Procedure 7.2. Booting the Installation from the Network Using PXE
- Ensure that the network cable is attached. The link indicator light on the network socket should be lit, even if the computer is not switched on.
- Switch on the computer.
- Depending on your hardware, some network setup and diagnostic information can be displayed before your computer connects to a PXE server. Once it connects, a menu is displayed according to the configuration of the PXE server. Press the number key that corresponds to the desired option. If you are not sure of which option to select, ask your server administrator.
Chapter 8. Installing Using Anaconda
- Use Kickstart to automate the installation as described in Chapter 27, Kickstart Installations
- Perform the graphical installation remotely by connecting to the installation system from another computer with a graphical display using the VNC (Virtual Network Computing) protocol - see Chapter 25, Using VNC
8.1. Introduction to Anaconda
8.2. Consoles and Logging During the Installation
8.2.1. Accessing Consoles
root privileges, unless this prompt was specifically disabled using a boot option or a Kickstart command.
Note
Note
| Shortcut | Contents |
|---|---|
| Ctrl+b 1 | Main installation program window. Contains text-based prompts (during text mode installation or if you use VNC Direct Mode), and also some debugging information. |
| Ctrl+b 2 | Interactive shell prompt with root privileges. |
| Ctrl+b 3 | Installation log; displays messages stored in /tmp/anaconda.log. |
| Ctrl+b 4 | Storage log; displays messages related storage devices from kernel and system services, stored in /tmp/storage.log. |
| Ctrl+b 5 | Program log; displays messages from other system utilities, stored in /tmp/program.log. |
8.2.2. Saving Screenshots
/tmp/anaconda-screenshots/.
autostep --autoscreenshot command in a Kickstart file to capture and save each step of the installation automatically. See Section 27.3.1, “Kickstart Commands and Options” for details.
8.3. Installing in Text Mode
Important
inst.xdriver=vesa option - see Chapter 23, Boot Options.
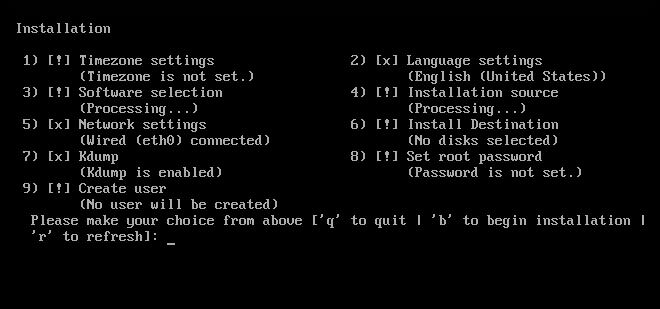
Figure 8.1. Text Mode Installation
[x], and screens which require your attention before the installation can begin are marked with [!]. Available commands are displayed below the list of available options.
Note
Processing... label. To refresh to the current status of text menu items, use the r option at the text mode prompt.
- The installer will always use the English language and the US English keyboard layout. You can configure your language and keyboard settings, but these settings will only apply to the installed system, not to the installation.
- You cannot configure any advanced storage methods (LVM, software RAID, FCoE, zFCP and iSCSI).
- It is not possible to configure custom partitioning; you must use one of the automatic partitioning settings. You also cannot configure where the boot loader will be installed.
- You cannot select any package add-ons to be installed; they must be added after the installation finishes using the Yum package manager.
inst.text boot option used either at the boot command line in the boot menu, or in your PXE server configuration. See Chapter 7, Booting the Installation on 64-bit AMD, Intel, and ARM systems for information about booting and using boot options.
8.4. Installing in the Graphical User Interface

Figure 8.2. The Installation Summary Screen
| Shortcut keys | Usage |
|---|---|
| Tab and Shift+Tab | Cycle through active control elements (buttons, check boxes, and so on.) on the current screen |
| Up and Down | Scroll through lists |
| Left and Right | Scroll through horizontal toolbars and table entries |
| Space and Enter | Select or remove a highlighted item from selection and expand and collapse drop-down menus |
8.5. Welcome Screen and Language Selection
Note
GeoIP module.

Figure 8.3. Language Configuration
8.6. The Installation Summary Screen

Figure 8.4. The Installation Summary Screen
Note
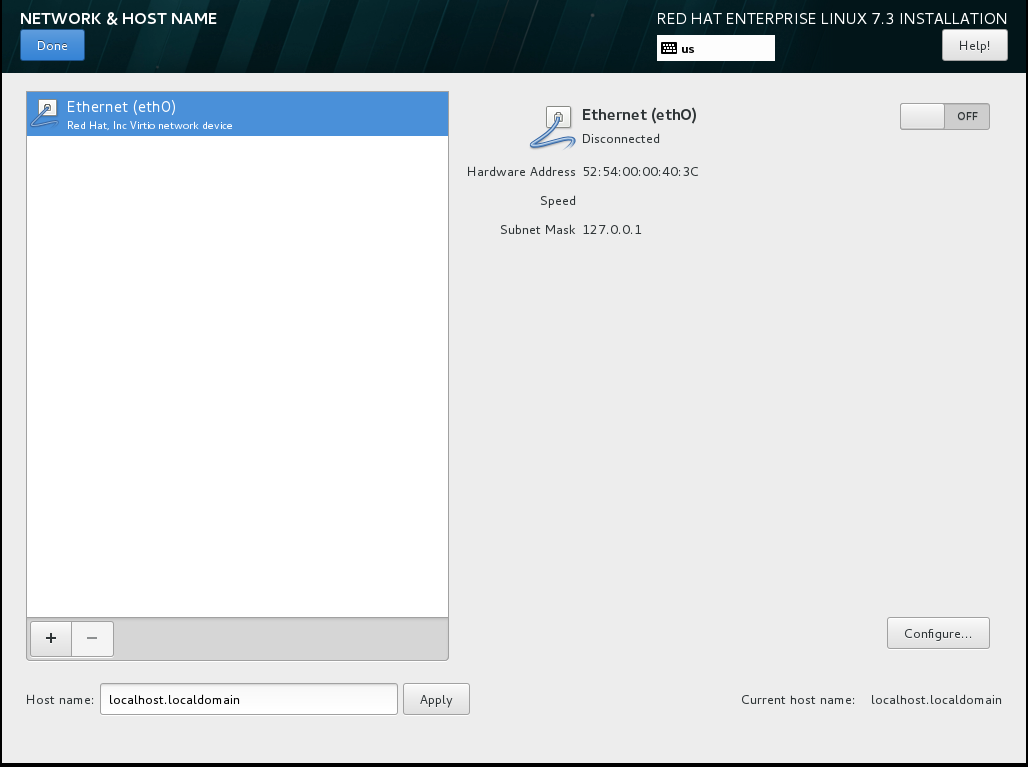
Figure 8.5. Network Configuration Screen When No Network Is Detected
8.7. Date & Time
- Using your mouse, click on the interactive map to select a specific city. A red pin appears indicating your selection.
- You can also scroll through the Region and City drop-down menus at the top of the screen to select your time zone.
- Select Etc at the bottom of the Region drop-down menu, then select your time zone in the next menu adjusted to GMT/UTC, for example
GMT+1.
timezone command in timezone (required) for details.
Note
Note
8.8. Language Support
Español. Then you can select a locale specific to your region in the right panel, for example Español (Costa Rica). You can select multiple languages and multiple locales. The selected languages are highlighted in bold in the left panel.
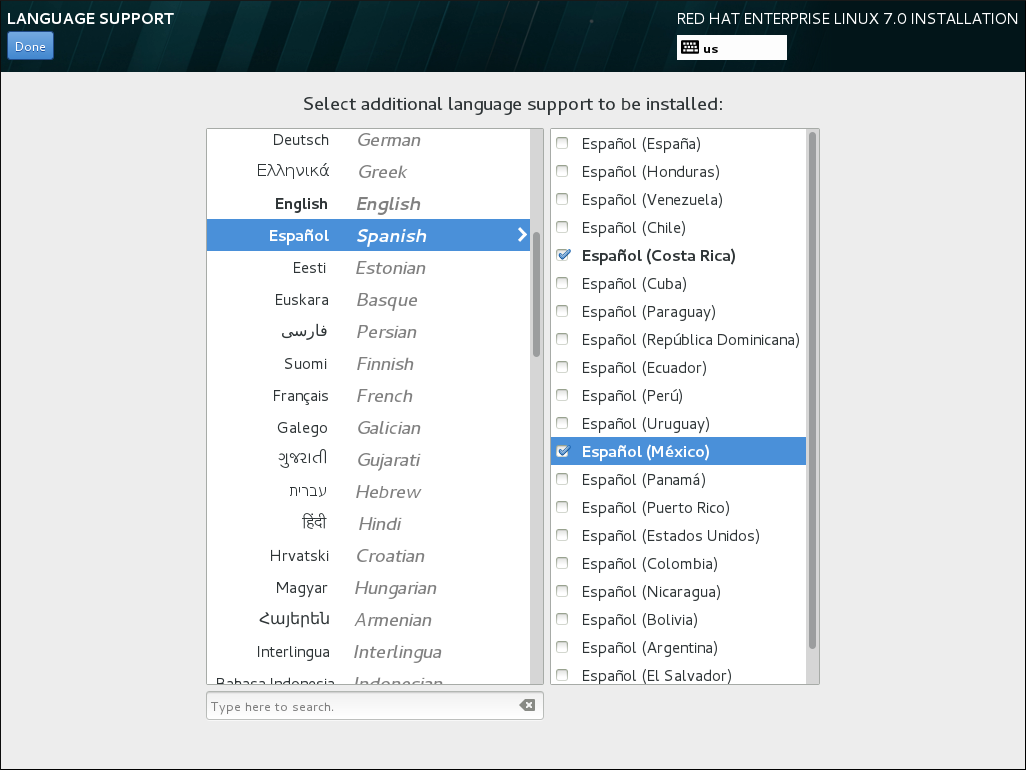
Figure 8.6. Configuring Language Support
Note
8.9. Keyboard Configuration

Figure 8.7. Keyboard Configuration
Important
Note
8.10. Security Policy
Important
/root/openscap_data directory on the installed system.
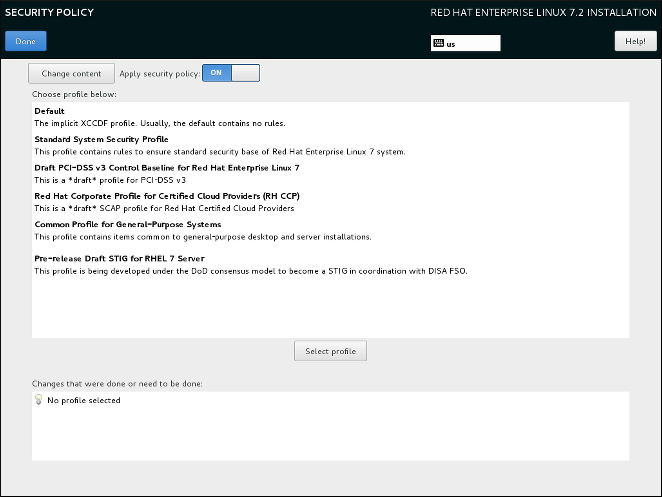
Figure 8.8. Security policy selection screen
Note
HTTP, HTTPS or FTP server. Use the full address of the content, including the protocol (such as http://). A network connection must be active (enabled in Section 8.12, “Network & Hostname”) before you can load a custom profile. The content type will be detected automatically by the installer.
8.11. Installation Source
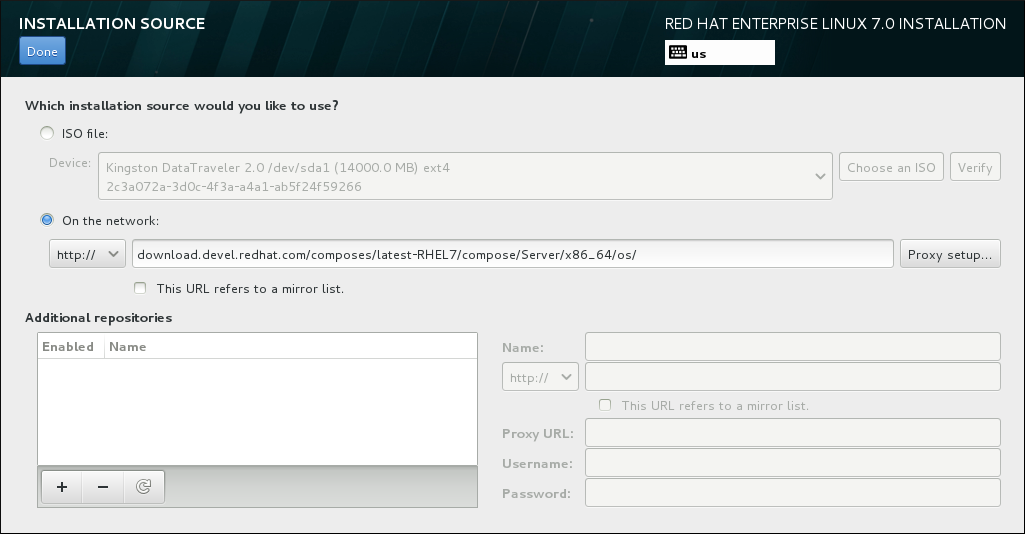
Figure 8.9. Installation Source Screen
- Auto-detected installation media
- If you started the installation using the full installation DVD or USB drive, the installation program will detect it and display basic information under this option. Click the button to ensure that the media is suitable for installation. This integrity test is the same as the one performed if you selected
Test this media & Install Red Hat Enterprise Linuxin the boot menu, or if you used therd.live.checkboot option. - ISO file
- This option will appear if the installation program detected a partitioned hard drive with mountable file systems. Select this option, click the button, and browse to the installation ISO file's location on your system. Then click to ensure that the file is suitable for installation.
- On the network
- To specify a network location, select this option and choose from the following options in the drop-down menu:
- http://
- https://
- ftp://
- nfs
Using your selection as the start of the location URL, type the rest into the address box. If you choose NFS, another box will appear for you to specify any NFS mount options.Important
When selecting an NFS-based installation source, you must specify the address with a colon (:) character separating the host name from the path. For example:server.example.com:/path/to/directory
server.example.com:/path/to/directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow To configure a proxy for an HTTP or HTTPS source, click the button. Check Enable HTTP proxy and type the URL into the Proxy URL box. If your proxy requires authentication, check Use Authentication and enter a user name and password. Click .If your HTTP or HTTPS URL refers to a repository mirror list, mark the check box under the input field.
8.12. Network & Hostname
Important
Note
em1 or wl3sp0. For information about these standards, see the Red Hat Enterprise Linux 7 Networking Guide.

Figure 8.10. Network & Hostname Configuration Screen
localhost.localdomain means that no specific static host name for target system is configured, and the actual host name of installed system will be configured during process of network configuration (for example, by NetworkManager using DHCP or DNS).
Important
Note
8.12.1. Edit Network Connections
- Mark the Automatically connect to this network when it is available check box if you want to use the connection every time the system boots. You can use more than one connection that will connect automatically. This setting will carry over to the installed system.
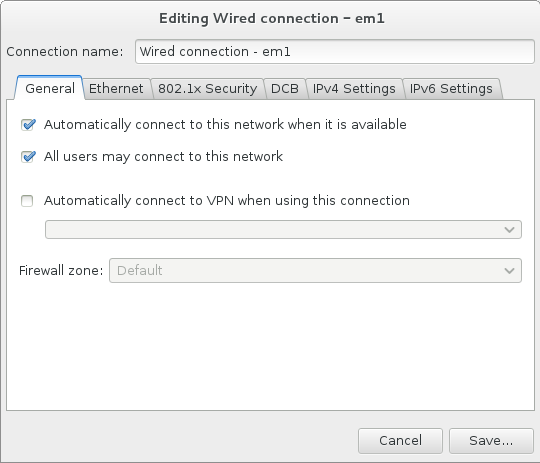
Figure 8.11. Network Auto-Connection Feature
- By default, IPv4 parameters are configured automatically by the DHCP service on the network. At the same time, the IPv6 configuration is set to the
Automaticmethod. This combination is suitable for most installation scenarios and usually does not require any changes.
Figure 8.12. IP Protocol Settings
8.12.2. Advanced Network Interfaces

Figure 8.13. Network & Hostname Configuration Screen
Bond- represents NIC (Network Interface Controller) Bonding, a method to bind multiple network interfaces together into a single, bonded, channel.Bridge- represents NIC Bridging, a method to connect multiple separate network into one aggregate network.Team- represents NIC Teaming, a new implementation to aggregate links, designed to provide a small kernel driver to implement the fast handling of packet flows, and various applications to do everything else in user space.VLAN- represents a method to create multiple distinct broadcast domains, which are mutually isolated.
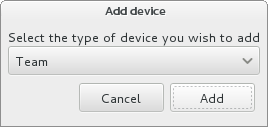
Figure 8.14. Advanced Network Interface Dialog
Note
8.13. Software Selection
- Add-ons listed above the horizontal line are specific to the environment you selected. If you select any add-ons in this part of the list and then select a different environment, your selection will be lost.
- Add-ons listed below the horizontal line are available for all environments. Selecting a different environment will not impact the selections made in this part of the list.
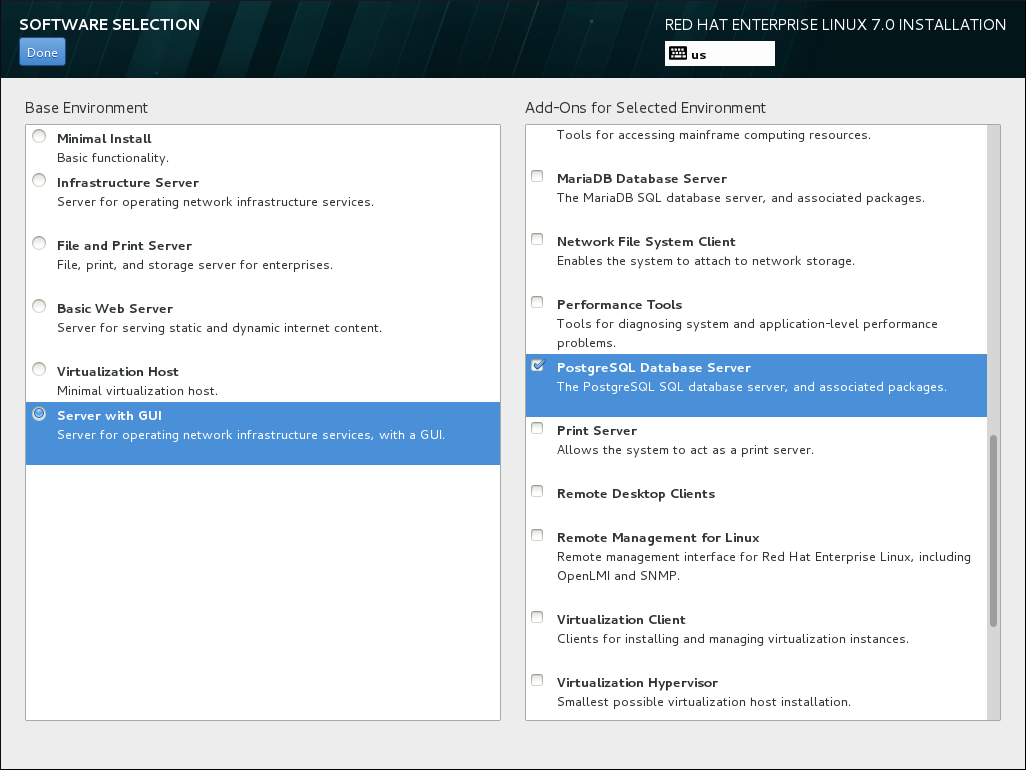
Figure 8.15. Example of a Software Selection for a Server Installation
server variant provides environments designed for servers, while the workstation variant has several choices for deployment as a developer workstation, and so on.
repodata/*-comps-variant.architecture.xml file on the Red Hat Enterprise Linux Installation DVD which you are using as the installation source. This file contains a structure describing available environments (marked by the <environment> tag) and add-ons (the <group> tag).
Important
%packages section of the Kickstart file. See Section 27.3.2, “Package Selection” for instructions on selecting packages to install in a Kickstart file, and Chapter 27, Kickstart Installations for general information about automating the installation with Kickstart.
8.13.1. Core Network Services
- centralized logging through the
rsyslogservice - email through SMTP (Simple Mail Transfer Protocol)
- network file sharing through NFS (Network File System)
- remote access through SSH (Secure SHell)
- resource advertising through mDNS (multicast DNS)
8.14. Installation Destination
Warning
Important
Important
Special cases
- If you have a RAID card, be aware that some BIOS types do not support booting from the RAID card. In such a case, the
/bootpartition must be created on a partition outside of the RAID array, such as on a separate hard drive. It is necessary to use an internal hard drive for partition creation with problematic RAID cards. A/bootpartition is also necessary for software RAID setups. If you have chosen to automatically partition your system, you should manually edit your/bootpartition; see Section 8.14.4, “Manual Partitioning” for more details. - To configure the Red Hat Enterprise Linux boot loader to chain load from a different boot loader, you must specify the boot drive manually by clicking the Full disk summary and bootloader link from the Installation Destination screen. See Section 8.14.1, “Boot Loader Installation” for instructions on specifying a boot drive.
- When you install Red Hat Enterprise Linux on a system with both multipath and non-multipath storage devices, the automatic partitioning layout in the installation program might create volume groups that contain a mix of multipath and non-multipath devices. This defeats the purpose of multipath storage. We advise that you select only multipath or only non-multipath devices on the Installation Destination screen. Alternatively, proceed to manual partitioning.

Figure 8.16. Storage Space Overview
- In the Partitioning section, you can select how storage devices are partitioned and how volumes are created. You can configure the partitions, manually or allow the installation program to do it automatically.Automatic partitioning is recommended if you are doing a clean installation on previously unused storage or do not need to keep any data that might be present on the storage. To proceed this way, leave the default selection of the Automatically configure partitioning radio button, and the installation program will create the necessary partitions and volumes on the storage space for you.For automatic partitioning, you can also select the I would like to make additional space available check box to choose how to reassign space from other file systems to this installation. After you click , there are two dialogs that can appear. If you selected automatic partitioning but there is not enough storage space to complete the installation using the recommended partitioning configuration, a dialog will appear:

Figure 8.17. Installation Options Dialog with Option to Reclaim Space
You can click to the Red Hat Enterprise Linux software selection link. The link will navigate you to the Software selection section, where you can change what software you want to install, and free some aditional storage space.Alternatively, you can click to return to the Installation Destination screen, where it is possible to add more storage devices, or to choose to configure partitioning manually. Click to free some storage space from existing file systems. See Section 8.14.3, “Reclaim Disk Space” for details.The second dialog appears if you cannot create enough free space. In this case, you have to add more disks on the initial storage screen or quit the installation.If you select the I will configure partitioning radio button for manual setup, you will be brought to the Manual Partitioning screen after clicking . See Section 8.14.4, “Manual Partitioning” for details. - In the Encryption section, you can select the Encrypt my data check box to encrypt all partitions except for the
/bootpartition. See the Red Hat Enterprise Linux 7 Security Guide for information on encryption.
8.14.1. Boot Loader Installation
Warning
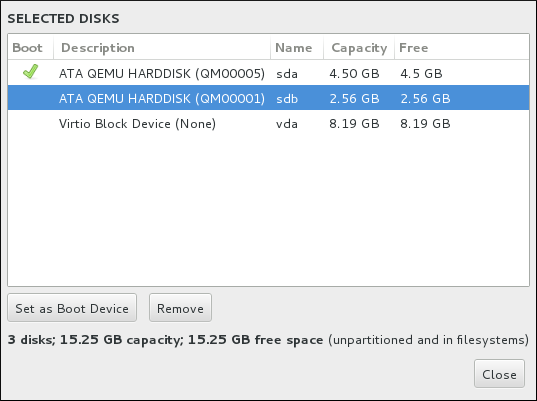
Figure 8.18. Summary of Selected Disks
Warning
8.14.1.1. MBR and GPT Considerations
- BIOS systems, and UEFI systems in BIOS compatibility mode
- If the disk is already formatted, the partitioning scheme is retained.If the disk is not formatted, or the user erased all partitions from the disk, Anaconda will use:
- MBR if the disk has less than 232 sectors. Most commonly, disks sectors are 512 bytes in size, in which case this would be equivalent to 2 TiB.
- GPT if the disk has 232 sectors or more.
Note
Append theinst.gptoption to the boot command line to override the default behavior and use GPT on a disk of less than 232 sectors in size. Note that you cannot manually override Anaconda to use MBR on a disk which is 232 sectors in size or larger.
You need to create a BIOS Boot (biosboot) partition to install on a BIOS system where the disk containing the boot loader uses GPT. Thebiosbootpartition should be 1 MiB in size. However, you do not need thebiosbootpartition if the disk containing the boot loader uses MBR. - UEFI systems
- Only GPT is allowed on UEFI systems. In order to install on a formatted disk with a MBR, you must first reformat it.You need to create an EFI System Partition (
/boot/efi), regardless of the partitioning scheme. The/boot/efipartition should be at least 50 MiB in size; its recommended size is 200 MiB.Note
Neither thebiosbootnorefipartition can reside on an LVM volume. Use standard physical partitions for them.
8.14.2. Encrypt Partitions
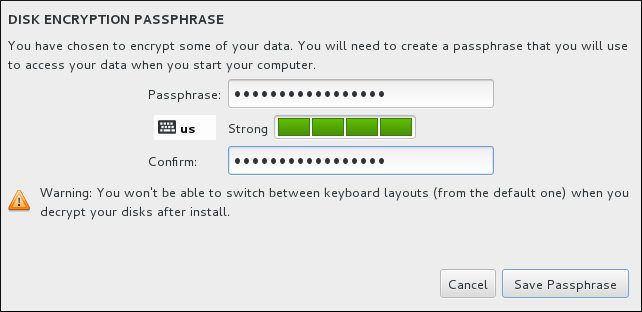
Figure 8.19. Enter Passphrase for an Encrypted Partition
Warning
8.14.3. Reclaim Disk Space
Warning
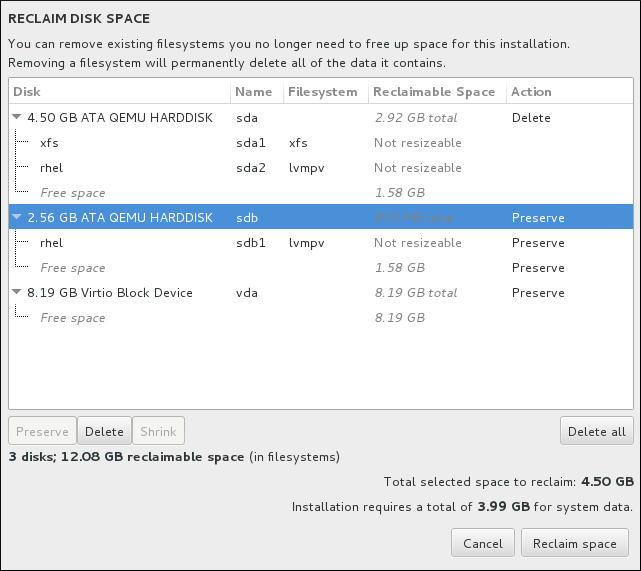
Figure 8.20. Reclaim Disk Space from Existing File Systems
- - leaves the file system untouched and no data will be deleted. This is the default action.
- - removes the file system entirely. All the space it takes up on the disk will be made available for the installation.
- - recovers free space from the file system and makes it available for this installation. Use the slider to set a new size for the selected partition. Can only be used on resizable partitions where LVM or RAID is not used.
- - this button, located on the right, marks all file systems for deletion by default. Upon clicking, it changes the label and allows you to mark all file systems to be preserved again.
8.14.4. Manual Partitioning
Warning
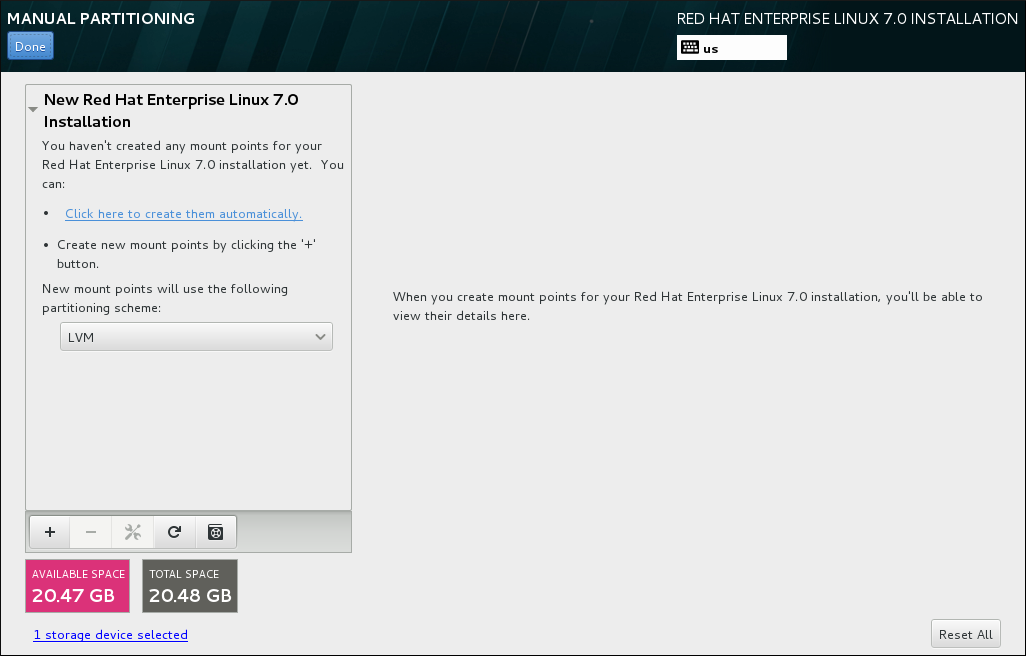
Figure 8.21. The Manual Partitioning Screen
Note
8.14.4.1. Adding File Systems and Configuring Partitions
/, /home, /boot, and swap. You can also create additional partitions and volumes as you require. See Section 8.14.4.4, “Recommended Partitioning Scheme” for further details.
Note
/boot partition, a / (root) volume, and a swap volume proportionate to the size of the available storage. These are the recommended file systems for a typical installation, but you can add additional file systems and mount points if you need to.
/ for the root partition or /boot for the boot partition. Then enter the size of the file system in the Desired Capacity text field; for example, 2GiB. If you leave the field empty or if you specify a size bigger than available space, all remaining free space is used instead. After entering these details, click the button to create the partition.
Note
/boot, and then create the rest of the partitions, letting the installation program allocate the remaining capacity to them.
Standard Partition, BTRFS, LVM, and LVM Thin Provisioning. Note that the /boot partition will always be located on a standard partition, regardless of the value selected in this menu.
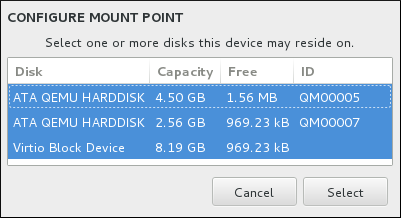
Figure 8.22. Configuring Mount Points
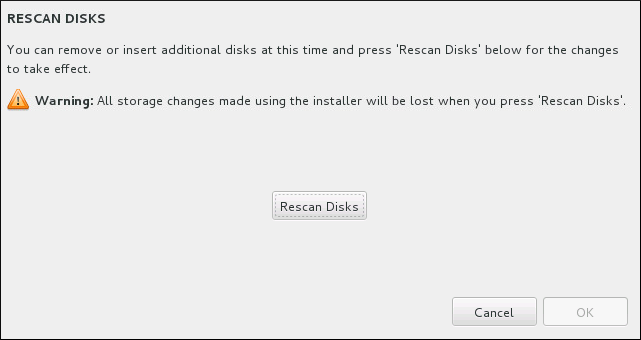
Figure 8.23. Rescanning Disks
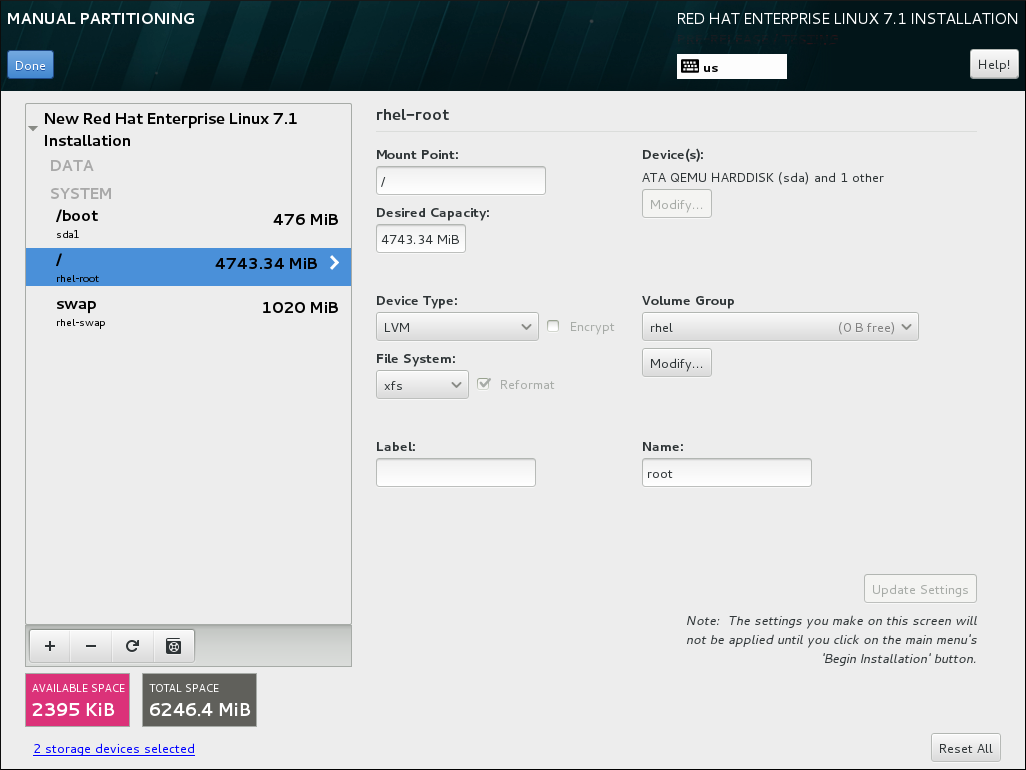
Figure 8.24. Customizing Partitions
- Mount Point - enter the file system's mount point. For example, if a file system should be the root file system, enter
/; enter/bootfor the/bootfile system, and so on. For a swap file system, the mount point should not be set - setting the file system type toswapis sufficient. - Desired Capacity - enter the desired size of the file system. You can use common size units such as KiB or GiB. The default is MiB if no other unit is specified.
- Device type - choose one of these types: Standard Partition, LVM, RAID, LVM Thin Provisioning, or BTRFS. Check the adjacent Encrypt box to encrypt the partition or volume. You will be prompted to set a password later. RAID is only available if two or more disks are selected for partitioning, and if you choose this type, you can also set the RAID Level. Similarly, if you select LVM, you can specify the Volume Group.
- File system - in the drop-down menu, select the appropriate file system type for this partition or volume. Check the adjacent Reformat box to format an existing partition, or leave it unchecked to retain your data. Note that newly created partitions and volumes must be reformatted, and the check box cannot be unchecked in this case.
- Label - assign a label to the partition. Labels are used for you to easily recognize and address individual partitions.
- Name - assign a name to an LVM or Btrfs volume. Note that standard partitions are named automatically when they are created and their name cannot be edited, such as
/homebeing assigned the namesda1.
Important
/usr or /var is partitioned separately from the rest of the root volume, the boot process becomes much more complex because these directories contain components critical to it. In some situations, such as when these directories are placed on an iSCSI drive or an FCoE location, the system can either be unable to boot, or hang with a Device is busy error when powering off or rebooting.
/usr or /var, not to directories below them. For example, a separate partition for /var/www will work without issues.
8.14.4.1.1. File System Types
Device Types
- standard partition - A standard partition can contain a file system or swap space, or it can provide a container for software RAID or an LVM physical volume.
- logical volume (LVM) - Creating an LVM partition automatically generates an LVM logical volume. LVM can improve performance when using physical disks. For information on how to create a logical volume, see Section 8.14.4.3, “Create LVM Logical Volume”. For more information regarding LVM, see the Red Hat Enterprise Linux 7 Logical Volume Manager Administration guide.
- LVM thin provisioning - Using thin provisioning, you can manage a storage pool of free space, known as a thin pool, which can be allocated to an arbitrary number of devices when needed by applications. The thin pool can be expanded dynamically when needed for cost-effective allocation of storage space. For more information regarding LVM, see the Red Hat Enterprise Linux 7 Logical Volume Manager Administration guide.
Warning
Anaconda does not support overprovisioned LVM thin pools.Note
The installer will automatically reserve 20% of any requested space for an LVM thin pool logical volume in the volume group containing it. This is a safety measure to ensure that you can extend either the metadata volume or the data volume of your thinly provisioned logical volume. - software RAID - Creating two or more software RAID partitions allows you to create a RAID device. One RAID partition is assigned to each disk on the system. To create a RAID device, see Section 8.14.4.2, “Create Software RAID”. For more information regarding RAID, see the Red Hat Enterprise Linux 7 Storage Administration Guide.
File Systems
- xfs - XFS is a highly scalable, high-performance file system that supports file systems up to 16 EiB (approximately 16 billion GiB), files up to 8 EiB (approximately 8 billion GiB), and directory structures containing tens of millions of entries. XFS supports metadata journaling, which facilitates quicker crash recovery. The XFS file system can also be defragmented and resized while mounted and active. This file system is selected by default and is highly recommended. For information on how to translate common commands from previously used ext4 file system to XFS, see Appendix F, Reference Table for ext4 and XFS Commands.The maximum supported size of an XFS file system in Red Hat Enterprise Linux is currently 500 TiB.
- ext4 - The ext4 file system is based on the ext3 file system and features a number of improvements. These include support for larger file systems and larger files, faster and more efficient allocation of disk space, no limit on the number of subdirectories within a directory, faster file system checking, and more robust journaling.The maximum supported size of an ext4 file system in Red Hat Enterprise Linux is currently 50 TiB.
- ext3 - The ext3 file system is based on the ext2 file system and has one main advantage - journaling. Using a journaling file system reduces time spent recovering a file system after a crash as there is no need to check the file system for metadata consistency by running the
fsckutility every time a crash occurs. - ext2 - An ext2 file system supports standard Unix file types, including regular files, directories, or symbolic links. It provides the ability to assign long file names, up to 255 characters.
- vfat - The VFAT file system is a Linux file system that is compatible with Microsoft Windows long file names on the FAT file system.
- swap - Swap partitions are used to support virtual memory. In other words, data is written to a swap partition when there is not enough RAM to store the data your system is processing.
- BIOS Boot - A very small partition required for booting a device with a GUID partition table (GPT) on a BIOS system. See Section 8.14.1, “Boot Loader Installation” for details.
- EFI System Partition - A small partition required for booting a device with a GUID partition table (GPT) on a UEFI system. See Section 8.14.1, “Boot Loader Installation” for details.
8.14.4.2. Create Software RAID
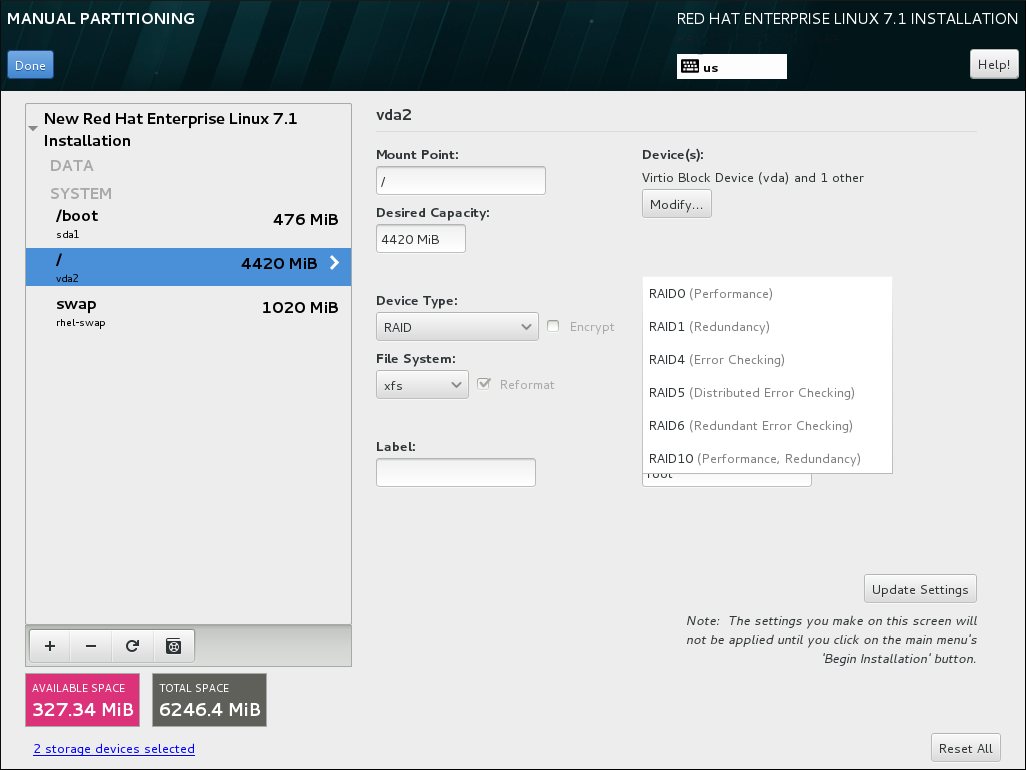
Figure 8.25. Creating a Software RAID Partition - the Device Type Menu Expanded
- Create a mount point as described in Section 8.14.4.1, “Adding File Systems and Configuring Partitions”. By configuring this mount point, you configure the RAID device.
- Keeping the partition selected in the left pane, select the configuration button below the pane to open the Configure Mount Point dialog. Select which disks will be included in the RAID device and click .
- Click the Device Type drop-down menu and select RAID.
- Click the File System drop-down menu and select your preferred file system type (see Section 8.14.4.1.1, “File System Types”.
- Click the RAID Level drop-down menu and select your preferred level of RAID.The available RAID levels are:
- RAID0 - Optimized performance (stripe)
- Distributes data across multiple disks. Level 0 RAIDs offer increased performance over standard partitions, and can be used to pool the storage of multiple disks into one large virtual device. Note that Level 0 RAIDs offer no redundancy, and that the failure of one device in the array destroys data in the entire array. RAID 0 requires at least two RAID partitions.
- RAID1 - Redundancy (mirror)
- Mirrors all data on one disk onto one or more other disks. Additional devices in the array provide increasing levels of redundancy. RAID 1 requires at least two RAID partitions.
- RAID4 - Error detection (parity)
- Distributes data across multiple disks, and uses one disk in the array to store parity information that safeguards the array in case any disk within the array fails. Because all parity information is stored on one disk, access to this disk creates a bottleneck in the performance of the array. RAID 4 requires at least three RAID partitions.
- RAID5 - Distributed error detection
- Distributes data and parity information across multiple disks. Level 5 RAIDs therefore offer the performance advantages of distributing data across multiple disks, but do not share the performance bottleneck of level 4 RAIDs because the parity information is also distributed through the array. RAID 5 requires at least three RAID partitions.
- RAID6 - Redundant
- Level 6 RAIDs are similar to level 5 RAIDs, but instead of storing only one set of parity data, they store two sets. RAID 6 requires at least four RAID partitions.
- RAID10 - Redundancy (mirror) and Optimized performance (stripe)
- Level 10 RAIDs are nested RAIDs or hybrid RAIDs. They are constructed by distributing data over mirrored sets of disks. For example, a level 10 RAID array constructed from four RAID partitions consists of two mirrored pairs of striped partitions. RAID 10 requires at least four RAID partitions.
- Click to save your changes, and either continue with another partition or click to return to the Installation Summary screen.
8.14.4.3. Create LVM Logical Volume
Important
lvm command. To return to the text-mode installation, press Ctrl+Alt+F1.
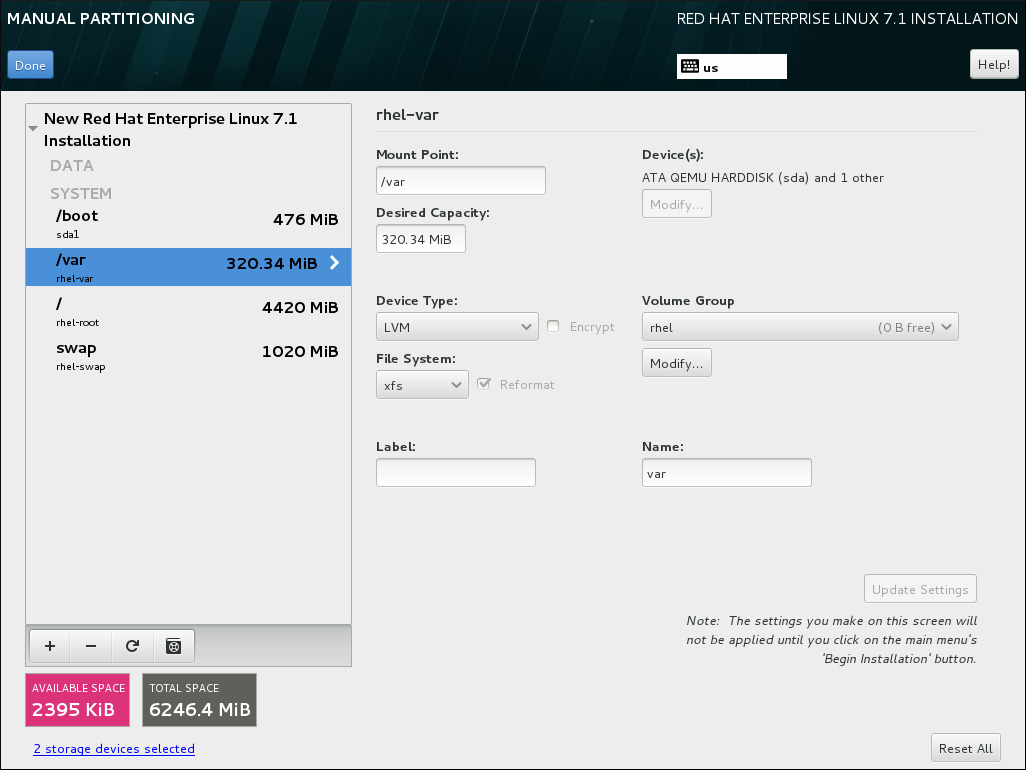
Figure 8.26. Configuring a Logical Volume
- Create a mount point for the LVM volume as described in Section 8.14.4.1, “Adding File Systems and Configuring Partitions”.
- Click the Device Type drop-down menu and select LVM. The Volume Group drop-down menu appears and displays the newly-created volume group name.
- Optionally, either click the menu and select Create a new volume group or click to configure the newly-created volume group, if you need to. Both the Create a new volume group option and the button lead to the Configure Volume Group dialog, where you can rename the logical volume group and select which disks will be included.
Note
The configuration dialog does not allow you to specify the size of the volume group's physical extents. The size will always be set to the default value of 4 MiB. If you want to create a volume group with different physical extents, create it manually by switching to an interactive shell and using thevgcreatecommand, or use a Kickstart file with thevolgroup --pesize=sizecommand.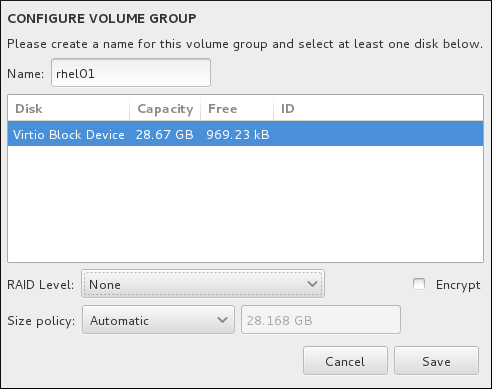
Figure 8.27. Customizing an LVM Volume Group
The available RAID levels are the same as with actual RAID devices. See Section 8.14.4.2, “Create Software RAID” for more information. You can also mark the volume group for encryption and set the size policy for it. The available policy options are:- Automatic - the size of the volume group is set automatically so that it is just large enough to contain the configured logical volumes. This is optimal if you do not need free space within the volume group.
- As large as possible - the volume group is created with maximum size, regardless of the size of the configured logical volumes it contains. This is optimal if you plan to keep most of your data on LVM and later need to increase the size of some existing logical volumes, or if you need to create additional logical volumes within this group.
- Fixed - with this option, you can set an exact size of the volume group. Any configured logical volumes must then fit within this fixed size. This is useful if you know exactly how large you would like the volume group to be.
Click when the group is configured. - Click to save your changes, and either continue with another partition or click to return to the Installation Summary screen.
Warning
/boot partition on an LVM volume is not supported.
8.14.4.4. Recommended Partitioning Scheme
/boot/(root)/homeswap
-
/bootpartition - recommended size at least 1 GiB - The partition mounted on
/bootcontains the operating system kernel, which allows your system to boot Red Hat Enterprise Linux, along with files used during the bootstrap process. Due to the limitations of most firmwares, creating a small partition to hold these is recommended. In most scenarios, a 1 GiB boot partition is adequate. Unlike other mount points, using an LVM volume for/bootis not possible -/bootmust be located on a separate disk partition.Warning
Normally, the/bootpartition is created automatically by the installation program. However, if the/(root) partition is larger than 2 TiB and (U)EFI is used for booting, you need to create a separate/bootpartition that is smaller than 2 TiB to boot the machine successfully.Note
If you have a RAID card, be aware that some BIOS types do not support booting from the RAID card. In such a case, the/bootpartition must be created on a partition outside of the RAID array, such as on a separate hard drive. root- recommended size of 10 GiB- This is where "
/", or the root directory, is located. The root directory is the top-level of the directory structure. By default, all files are written to this file system unless a different file system is mounted in the path being written to (for example,/bootor/home).While a 5 GiB root file system allows you to install a minimal installation, it is recommended to allocate at least 10 GiB so that you can install as many package groups as you want.Important
Do not confuse the/directory with the/rootdirectory. The/rootdirectory is the home directory of the root user. The/rootdirectory is sometimes referred to as slash root to distinguish it from the root directory. /home- recommended size at least 1 GiB- To store user data separately from system data, create a dedicated file system for the
/homedirectory. This file system should be sized based on the amount of data that will be stored locally, number of users, and so on. This will enable you to upgrade or reinstall Red Hat Enterprise Linux without erasing user data files. If you select automatic partitioning, it is recommended to have at least 55GiB of disk space available for the installation, to ensure that the/homefile system is created. swappartition - recommended size at least 1 GB- Swap file systems support virtual memory; data is written to a swap file system when there is not enough RAM to store the data your system is processing. Swap size is a function of system memory workload, not total system memory and therefore is not equal to the total system memory size. Therefore, it is important to analyze what applications a system will be running and the load those applications will serve in order to determine the system memory workload. Application providers and developers should be able to provide some guidance.When the system runs out of swap space, the kernel terminates processes as the system RAM memory is exhausted. Configuring too much swap space results in storage devices being allocated but idle and is a poor use of resources. Too much swap space can also hide memory leaks. The maximum size for a swap partition and other additional information can be found in the
mkswap(8)manual page.The following table provides the recommended size of a swap partition depending on the amount of RAM in your system and whether you want sufficient memory for your system to hibernate. If you let the installation program partition your system automatically, the swap partition size will be established using these guidelines. Automatic partitioning setup assumes hibernation is not in use. The maximum size of the swap partition is limited to 10% of the total size of the hard drive, and the installer cannot create swap partitions more than 128GB in size. If you want to set up enough swap space to allow for hibernation, or if you want to set the swap partition size to more than 10% of the system's storage space, or more than 128GB, you must edit the partitioning layout manually.Expand Table 8.3. Recommended System Swap Space Amount of RAM in the system Recommended swap space Recommended swap space if allowing for hibernation less than 2 GB 2 times the amount of RAM 3 times the amount of RAM 2 GB - 8 GB Equal to the amount of RAM 2 times the amount of RAM 8 GB - 64 GB 4GB to 0.5 times the amount of RAM 1.5 times the amount of RAM more than 64 GB workload dependent (at least 4GB) hibernation not recommended At the border between each range listed above (for example, a system with 2 GB, 8 GB, or 64 GB of system RAM), discretion can be exercised with regard to chosen swap space and hibernation support. If your system resources allow for it, increasing the swap space can lead to better performance.Distributing swap space over multiple storage devices - particularly on systems with fast drives, controllers and interfaces - also improves swap space performance.
Note
8.14.4.4.1. Advice on Partitions
- Consider encrypting any partitions that might contain sensitive data. Encryption prevents unauthorized people from accessing the data on the partitions, even if they have access to the physical storage device. In most cases, you should at least encrypt the
/homepartition. - Each kernel installed on your system requires approximately 56 MB on the
/bootpartition.- 32 MB initramfs
- 14 MB kdump initramfs
- 3.5 MB system map
- 6.6 MB vmlinuz
Note
For rescue mode,initramfsandvmlinuzrequire 80 MB.The default partition size of 1 GiB for/bootshould suffice for most common uses. However, it is recommended that you increase the size of this partition if you are planning on retaining multiple kernel releases or errata kernels. - The
/vardirectory holds content for a number of applications, including the Apache web server. It also is used to store downloaded update packages on a temporary basis. Ensure that the partition containing the/vardirectory has enough space to download pending updates and hold your other content. - The PackageKit update software downloads updated packages to
/var/cache/yum/by default. If you create a separate partition or volume for/var, ensure that it is at least 5 GB in size to accommodate downloaded package updates. - The
/usrdirectory holds the majority of software content on a Red Hat Enterprise Linux system. For an installation of the default set of software, allocate at least 5 GB of space. If the system will be used as a software development workstation, allocate at least 10GB. - If
/usror/varis partitioned separately from the rest of the root volume, the boot process becomes much more complex because these directories contain components critical to it. In some situations, such as when these directories are placed on an iSCSI drive or an FCoE location, the system can either be unable to boot, or it can hang with aDevice is busyerror when powering off or rebooting.This limitation only applies to/usror/var, not to directories below them. For example, a separate partition for/var/wwwwill work without issues. - Consider leaving a portion of the space in an LVM volume group unallocated. This unallocated space gives you flexibility if your space requirements change but you do not want to remove data from other partitions to reallocate storage. You can also select the Thin provisioning device type for the partition to have the unused space handled automatically by the volume.
- If you separate subdirectories into partitions, you can retain content in those subdirectories if you decide to install a new version of Red Hat Enterprise Linux over your current system. For instance, if you intend to run a MySQL database in
/var/lib/mysql/, make a separate partition for that directory in case you need to reinstall later. - On a BIOS system with its boot loader using GPT (GUID partition table), you need to create the
biosbootpartition of 1 MiB in size. See Section 8.14.1, “Boot Loader Installation” for more details. - UEFI systems need to contain a small partition with a mount point of
/boot/efi/containing an EFI System Partition file system. Its recommended size is 200 MiB, which is also the default value for automatic partitioning.
8.15. Storage Devices

Figure 8.28. Storage Space Overview
Note
dmeventd daemon is not performed during installation.
8.15.1. The Storage Devices Selection Screen
- Multipath Devices
- Storage devices accessible through more than one path, such as through multiple SCSI controllers or Fiber Channel ports on the same system.The installation program only detects multipath storage devices with serial numbers that are 16 or 32 characters long.
- Other SAN Devices
- Devices available on a Storage Area Network (SAN).
- NVDIMM Devices
- Non-Volatile Dual In-line Memory Module (NVDIMM) storage devices on the machine.
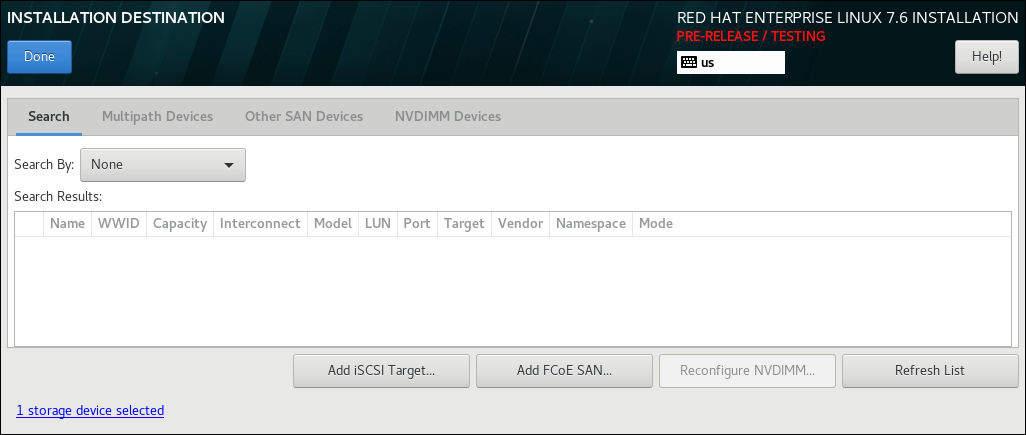
Figure 8.29. Tabbed Overview of Specialized Storage Devices
- - use to attach iSCSI devices; continue with Section 8.15.1.1.1, “Configuring iSCSI Parameters”
- - use to configure a Fibre Channel Over Internet storage device; continue with Section 8.15.1.1.2, “Configuring FCoE Parameters”
- - use to reconfigure a NVDIMM device into sector mode; continue with Section 8.15.1.1.3, “Configuring NVDIMM Devices”
- - use to reload the list when a device is added after the installer starts.
Figure 8.30. The Storage Devices Search Tab
/etc/fstab file.
Important
8.15.1.1. Advanced Storage Options

Figure 8.31. Advanced Storage Options
8.15.1.1.1. Configuring iSCSI Parameters
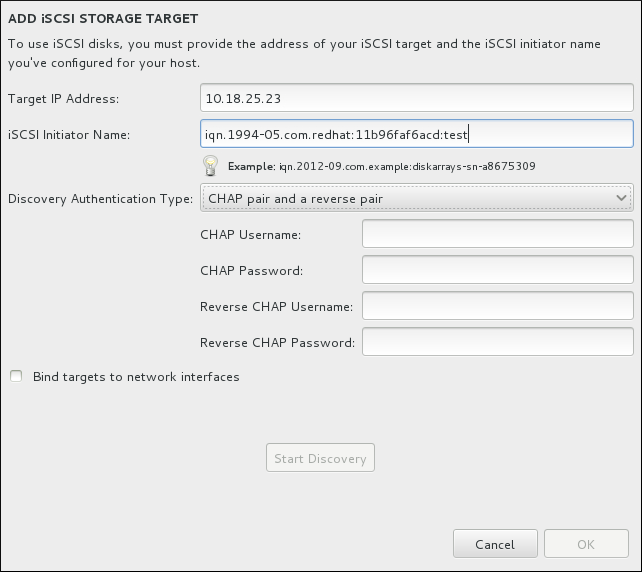
Figure 8.32. The iSCSI Discovery Details Dialog
Note
Procedure 8.1. iSCSI Discovery and Starting an iSCSI Session
- Enter the IP address of the iSCSI target in the Target IP Address field.
- Provide a name in the iSCSI Initiator Name field for the iSCSI initiator in iSCSI qualified name (IQN) format. A valid IQN entry contains:
- the string
iqn.(note the period) - a date code that specifies the year and month in which your organization's Internet domain or subdomain name was registered, represented as four digits for the year, a dash, and two digits for the month, followed by a period. For example, represent September 2010 as
2010-09. - your organization's Internet domain or subdomain name, presented in reverse order with the top-level domain first. For example, represent the subdomain
storage.example.comascom.example.storage - a colon followed by a string that uniquely identifies this particular iSCSI initiator within your domain or subdomain. For example,
:diskarrays-sn-a8675309
A complete IQN can therefore look as follows:iqn.2010-09.storage.example.com:diskarrays-sn-a8675309. Anaconda prepopulates the iSCSI Initiator Name field with a name in this format to help you with the structure.For more information on IQNs , see 3.2.6. iSCSI Names in RFC 3720 - Internet Small Computer Systems Interface (iSCSI) available from http://tools.ietf.org/html/rfc3720#section-3.2.6 and 1. iSCSI Names and Addresses in RFC 3721 - Internet Small Computer Systems Interface (iSCSI) Naming and Discovery available from http://tools.ietf.org/html/rfc3721#section-1. - Use the Discovery Authentication Type drop-down menu to specify the type of authentication to use for iSCSI discovery. The following options are available:
- no credentials
- CHAP pair
- CHAP pair and a reverse pair
- If you selected as the authentication type, provide the user name and password for the iSCSI target in the CHAP Username and CHAP Password fields.
- If you selected as the authentication type, provide the user name and password for the iSCSI target in the CHAP Username and CHAP Password field and the user name and password for the iSCSI initiator in the Reverse CHAP Username and Reverse CHAP Password fields.
- Optionally check the box labeled Bind targets to network interfaces.
- Click the button. Anaconda attempts to discover an iSCSI target based on the information that you provided. If discovery succeeds, the dialog displays a list of all iSCSI nodes discovered on the target.
- Each node is presented with a check box beside it. Click the check boxes to select the nodes to use for installation.

Figure 8.33. The Dialog of Discovered iSCSI Nodes
- The Node login authentication type menu provides the same options as the Discovery Authentication Type menu described in step 3. However, if you needed credentials for discovery authentication, it is typical to use the same credentials to log into a discovered node. To do that, use the additional option from the menu. When the proper credentials have been provided, the button becomes available.
- Click to initiate an iSCSI session.
8.15.1.1.2. Configuring FCoE Parameters
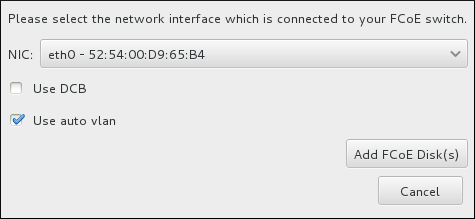
Figure 8.34. Configure FCoE Parameters
- Use DCB
- Data Center Bridging (DCB) is a set of enhancements to the Ethernet protocols designed to increase the efficiency of Ethernet connections in storage networks and clusters. Enable or disable the installation program's awareness of DCB with the check box in this dialog. This option should only be enabled for network interfaces that require a host-based DCBX client. Configurations on interfaces that implement a hardware DCBX client should leave this check box empty.
- Use auto vlan
- Auto VLAN indicates whether VLAN discovery should be performed. If this box is checked, then the FIP (FCoE Initiation Protocol) VLAN discovery protocol will run on the Ethernet interface once the link configuration has been validated. If they are not already configured, network interfaces for any discovered FCoE VLANs will be automatically created and FCoE instances will be created on the VLAN interfaces. This option is enabled by default.
8.15.1.1.3. Configuring NVDIMM Devices
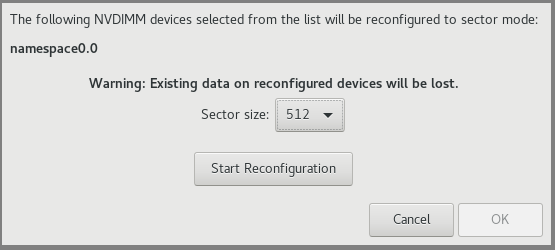
Figure 8.35. Reconfigure NVDIMM
Warning
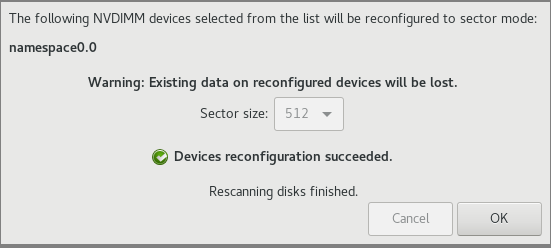
Figure 8.36. Successfully reconfigured NVDIMM
8.16. Kdump
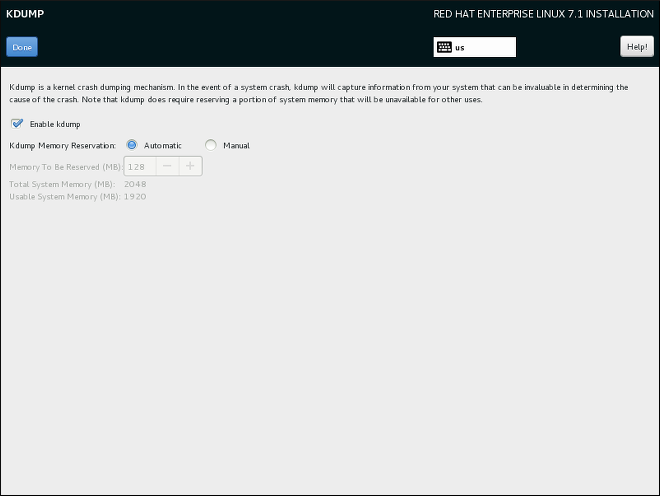
Figure 8.37. Kdump Enablement and Configuration
8.17. Begin Installation

Figure 8.38. Ready to Install
Warning
8.19. Installation Complete
login: prompt) appears.
Chapter 9. Troubleshooting Installation on 64-bit AMD, Intel, and ARM Systems
/tmp directory. These files are listed in the following table.
| Log file | Contents |
|---|---|
/tmp/anaconda.log | general Anaconda messages |
/tmp/program.log | all external programs run during the installation |
/tmp/storage.log | extensive storage module information |
/tmp/packaging.log | yum and rpm package installation messages |
/tmp/syslog | hardware-related system messages |
/tmp/anaconda-tb-identifier, where identifier is a random string.
/var/log/anaconda/. However, if installation is unsuccessful, or if the inst.nosave=all or inst.nosave=logs options are used when booting the installation system, these logs will only exist in the installation program's RAM disk. This means they are not saved permanently and will be lost once the system is powered down. To store them permanently, copy those files to another system on the network by using scp on the system running the installation program, or copy them to a mounted storage device (such as an USB flash drive). Details on how to transfer the log files over the network are below. Note that if you use an USB flash drive or other removable media, you should make sure to back up any data on it before starting the procedure.
Procedure 9.1. Transferring Log Files Onto a USB Drive
- On the system you are installing, press Ctrl+Alt+F2 to access a shell prompt. You will be logged into a root account and you will have access to the installation program's temporary file system.
- Connect a USB flash drive to the system and execute the
dmesgcommand. A log detailing all recent events will be displayed. At the bottom of this log, you will see a set of messages caused by the USB flash drive you just connected. It will look like a set of lines similar to the following:[ 170.171135] sd 5:0:0:0: [sdb] Attached SCSI removable disk
[ 170.171135] sd 5:0:0:0: [sdb] Attached SCSI removable diskCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note the name of the connected device - in the above example, it issdb. - Go to the
/mntdirectory and once there, create new directory which will serve as the mount target for the USB drive. The name of the directory does not matter; this example uses the nameusb.mkdir usb
# mkdir usbCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mount the USB flash drive onto the newly created directory. Note that in most cases, you do not want to mount the whole drive, but a partition on it. Therefore, do not use the name
sdb- use the name of the partition you want to write the log files to. In this example, the namesdb1is used.mount /dev/sdb1 /mnt/usb
# mount /dev/sdb1 /mnt/usbCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can now verify that you mounted the correct device and partition by accessing it and listing its contents - the list should match what you expect to be on the drive.cd /mnt/usb
# cd /mnt/usbCopy to Clipboard Copied! Toggle word wrap Toggle overflow ls
# lsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the log files to the mounted device.
cp /tmp/*log /mnt/usb
# cp /tmp/*log /mnt/usbCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Unmount the USB flash drive. If you get an error message saying that the target is busy, change your working directory to outside the mount (for example,
/).umount /mnt/usb
# umount /mnt/usbCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 9.2. Transferring Log Files Over the Network
- On the system you are installing, press Ctrl+Alt+F2 to access a shell prompt. You will be logged into a root account and you will have access to the installation program's temporary file system.
- Switch to the
/tmpdirectory where the log files are located:cd /tmp
# cd /tmpCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the log files onto another system on the network using the
scpcommand:scp *log user@address:path
# scp *log user@address:pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace user with a valid user name on the target system, address with the target system's address or host name, and path with the path to the directory you want to save the log files into. For example, if you want to log in asjohnto a system with an IP address of192.168.0.122and place the log files into the/home/john/logs/directory on that system, the command will have the following form:scp *log john@192.168.0.122:/home/john/logs/
# scp *log john@192.168.0.122:/home/john/logs/Copy to Clipboard Copied! Toggle word wrap Toggle overflow When connecting to the target system for the first time, the SSH client asks you to confirm that the fingerprint of the remote system is correct and that you want to continue:The authenticity of host '192.168.0.122 (192.168.0.122)' can't be established. ECDSA key fingerprint is a4:60:76:eb:b2:d0:aa:23:af:3d:59:5c:de:bb:c4:42. Are you sure you want to continue connecting (yes/no)?
The authenticity of host '192.168.0.122 (192.168.0.122)' can't be established. ECDSA key fingerprint is a4:60:76:eb:b2:d0:aa:23:af:3d:59:5c:de:bb:c4:42. Are you sure you want to continue connecting (yes/no)?Copy to Clipboard Copied! Toggle word wrap Toggle overflow Typeyesand press Enter to continue. Then, provide a valid password when prompted. The files will start transferring to the specified directory on the target system.
9.1. Trouble Beginning the Installation
9.1.1. System Does Not Boot When UEFI Secure Boot Is Enabled
9.1.2. Problems with Booting into the Graphical Installation
- Use the basic graphics mode
- You can attempt to perform the installation using the basic graphics driver. To do this, either select > in the boot menu, or edit the installation program's boot options and append
inst.xdriver=vesaat the end of the command line. - Specify the display resolution manually
- If the installation program fails to detect your screen resolution, you can override the automatic detection and specify it manually. To do this, append the
inst.resolution=xoption at the boot menu, where x is your display's resolution (for example,1024x768). - Use an alternate video driver
- You can also attempt to specify a custom video driver, overriding the installation program's automatic detection. To specify a driver, use the
inst.xdriver=xoption, where x is the device driver you want to use (for example,nouveau).Note
If specifying a custom video driver solves your problem, you should report it as a bug at https://bugzilla.redhat.com under theanacondacomponent. Anaconda should be able to detect your hardware automatically and use the appropriate driver without your intervention. - Perform the installation using VNC
- If the above options fail, you can use a separate system to access the graphical installation over the network, using the Virtual Network Computing (VNC) protocol. For details on installing using VNC, see Chapter 25, Using VNC.
9.1.3. Serial Console Not Detected
inst.text and console= boot options. See Chapter 23, Boot Options for more details.
9.2. Trouble During the Installation
9.2.1. No Disks Detected
9.2.2. Reporting Traceback Messages
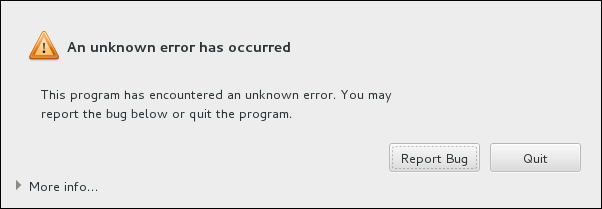
Figure 9.1. The Crash Reporting Dialog Box
tty1, where you can request more precise information that will enhance the bug report. To return to the graphical interface from tty1, use the continue command.
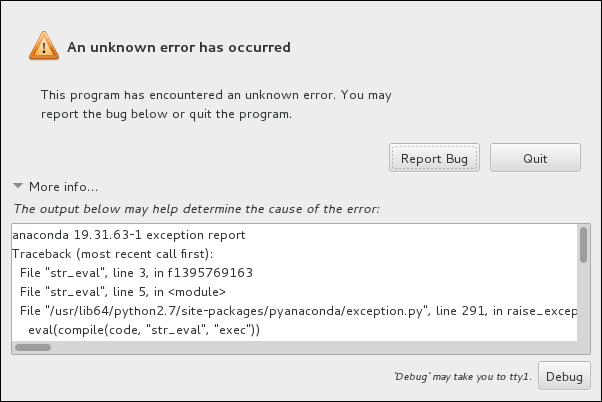
Figure 9.2. The Expanded Crash Reporting Dialog Box
Procedure 9.3. Reporting Errors to Red Hat Customer Support
- In the menu that appears, select Report a bug to Red Hat Customer Portal.
- To report the bug to Red Hat, you first need to provide your Customer Portal credentials. Click .

Figure 9.3. Customer Portal Credentials
- A new window is now open, prompting you to enter your Customer Portal user name and password. Enter your Red Hat Customer Portal credentials.
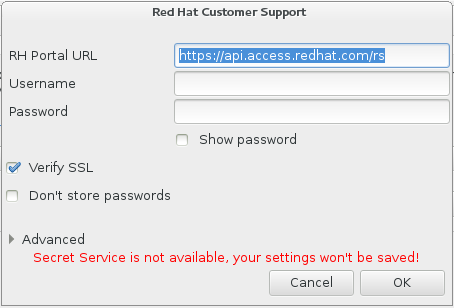
Figure 9.4. Configure Red Hat Customer Support
If your network settings require you to use aHTTPorHTTPSproxy, you can configure it by expanding the Advanced menu and entering the address of the proxy server.When you put in all required credentials, click OK to proceed. - A new window appears, containing a text field. Write down any useful information and comments here. Describe how the error can be reproduced by explaining each step you took before the crash reporting dialog appeared. Provide as much relevant detail as possible, including any information you acquired when debugging. Be aware that the information you provide here can become publicly visible on the Customer Portal.If you do not know what caused the error, check the box labeled I don't know what caused this problem at the bottom of the dialog.Then, click .
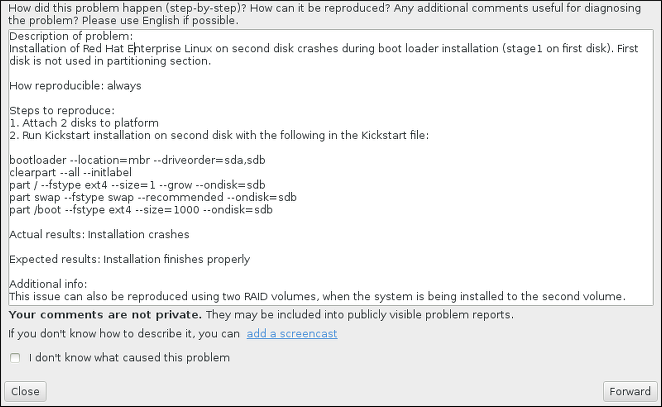
Figure 9.5. Describe the Problem
- Next, review the information that will be sent to the Customer Portal. The explanation you provided is in the comment tab. Other tabs include such information as your system's host name and other details about the installation environment. You can remove any items you do not want sent to Red Hat, but be aware that providing less detail can affect the investigation of the issue.Click when you finish reviewing the information to be sent.
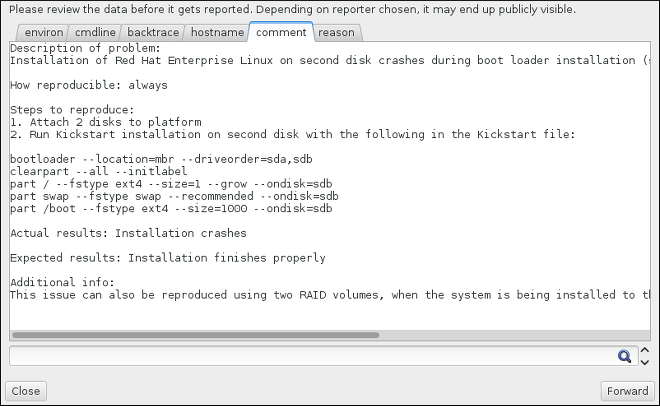
Figure 9.6. Review the Data to Be Sent
- Review the list of files that will be sent and included in the bug report as individual attachments. These files provide system information that will assist the investigation. If you do not want to send certain files, uncheck the box next to each one. To provide additional files that can help find the problem, click .Once you have reviewed the files to be sent, check the box labeled I have reviewed the data and agree with submitting it. Then, click to send the report and attachments to the Customer Portal.

Figure 9.7. Review the Files to Be Sent
- When the dialog reports that processing has finished, you can click Show log to view details of the reporting process or Close to return to the initial crash reporting dialog box. There, click Quit to exit the installation.
9.2.3. Creating Pre-installation Log Files
inst.debug option to create log files from the environment before the installation starts. These log files contain, for example, the current storage configuration.
- Select the entry.
- Press the Tab key to edit the boot options.
- Append
inst.debugto the options. For example:> vmlinuz ... inst.debug
> vmlinuz ... inst.debugCopy to Clipboard Copied! Toggle word wrap Toggle overflow For further details, see Chapter 23, Boot Options. - Press Enter to start the setup.
/tmp/pre-anaconda-logs/ directory before Anaconda starts. To access the log files:
- Switch to the console. See Section 8.2.1, “Accessing Consoles”.
- Change into the
/tmp/pre-anaconda-logs/directory:cd /tmp/pre-anaconda-logs/
# cd /tmp/pre-anaconda-logs/Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.3. Problems After Installation
9.3.1. Are You Unable to Boot With Your RAID Card?
grub>) and a flashing cursor might be all that appears. If this is the case, you must repartition your system and move your /boot partition and the boot loader outside the RAID array. The /boot partition and the boot loader must be on the same drive.
9.3.2. Trouble With the Graphical Boot Sequence
Procedure 9.4. Disabling Graphical Boot Temporarily
- Start your computer and wait until the boot loader menu appears. If you set your boot loader timeout period to 0, hold down the Esc key to access it.
- When the boot loader menu appears, use your cursor keys to highlight the entry you want to boot and press the e key to edit this entry's options.
- In the list of options, find the kernel line - that is, the line beginning with the keyword
linux(or, in some cases,linux16orlinuxefi). On this line, locate therhgboption and delete it. The option might not be immediately visible; use the cursor keys to scroll up and down. - Press F10 or Ctrl+X to boot your system with the edited options.
Procedure 9.5. Disabling Graphical Boot Permanently
- Log in to the
rootaccount using thesu -command:su -
$ su -Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the grubby tool to find the default GRUB2 kernel:
grubby --default-kernel /boot/vmlinuz-3.10.0-229.4.2.el7.x86_64
# grubby --default-kernel /boot/vmlinuz-3.10.0-229.4.2.el7.x86_64Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the grubby tool to remove the
rhgbboot option from the default kernel, identified in the last step, in your GRUB2 configuration. For example:grubby --remove-args="rhgb" --update-kernel /boot/vmlinuz-3.10.0-229.4.2.el7.x86_64
# grubby --remove-args="rhgb" --update-kernel /boot/vmlinuz-3.10.0-229.4.2.el7.x86_64Copy to Clipboard Copied! Toggle word wrap Toggle overflow
--remove-args="rhgb" parameter with the --args="rhgb" paramter. This will restore the rhgb boot option to the default kernel in your GRUB2 configuration.
9.3.3. Booting into a Graphical Environment
startx command. Note, however, that this is just a one-time fix and does not change the log in process for future log ins.
graphical.target. When you are finished, reboot the computer. You will presented with a graphical login prompt after the system restarts.
Procedure 9.6. Setting Graphical Login as Default
- Open a shell prompt. If you are in your user account, become root by typing the
su -command. - Change the default target to
graphical.target. To do this, execute the following command:systemctl set-default graphical.target
# systemctl set-default graphical.targetCopy to Clipboard Copied! Toggle word wrap Toggle overflow
root:
systemctl set-default multi-user.target
# systemctl set-default multi-user.target9.3.4. No Graphical User Interface Present
9.3.5. X Server Crashing After User Logs In
df -h
$ df -h/home partition. The following is a sample output of the df command:
/home partition is full, which causes the crash. You can make some room on the partition by removing unneeded files. After you free up some disk space, start X using the startx command.
df and an explanation of the options available (such as the -h option used in this example), see the df(1) man page.
9.3.6. Is Your RAM Not Being Recognized?
free -m command. If the displayed total amount of memory does not match your expectations, it is likely that at least one of your memory modules is faulty. On BIOS-based systems, you can use the Memtest86+ utility to test your system's memory - see Section 23.2.1, “Loading the Memory (RAM) Testing Mode” for details.
Note
free command. For details about kdump and its memory requirements, see the Red Hat Enterprise Linux 7 Kernel Crash Dump Guide.
mem= kernel option.
Procedure 9.7. Configuring the Memory Manually
- Start your computer and wait until the boot loader menu appears. If you set your boot loader timeout period to 0, hold down the Esc key to access it.
- When the boot loader menu appears, use your cursor keys to highlight the entry you want to boot and press the e key to edit this entry's options.
- In the list of options, find the kernel line - that is, the line beginning with the keyword
linux(or, in some cases,linux16). Append the following option to the end of this line:mem=xxM
mem=xxMCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace xx with the amount of RAM you have in MiB. - Press F10 or Ctrl+X to boot your system with the edited options.
- Wait for the system to boot and log in. Then, open a command line and execute the
free -mcommand again. If total amount of RAM displayed by the command matches your expectations, append the following to the line beginning withGRUB_CMDLINE_LINUXin the/etc/default/grubfile to make the change permanent:mem=xxM
mem=xxMCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace xx with the amount of RAM you have in MiB. - After you updated the file and saved it, refresh the boot loader configuration so that the change will take effect. Run the following command with root privileges:
grub2-mkconfig --output=/boot/grub2/grub.cfg
# grub2-mkconfig --output=/boot/grub2/grub.cfgCopy to Clipboard Copied! Toggle word wrap Toggle overflow
/etc/default/grub, the above example would look similar to the following:
9.3.7. Is Your System Displaying Signal 11 Errors?
rd.live.check boot option at the boot menu. See Section 23.2.2, “Verifying Boot Media” for details.
Part II. IBM Power Systems - Installation and Booting
Important
ppc and ppc64, respectively). Red Hat Enterprise Linux 7 supports only 64-bit Power Systems servers (ppc64).
Chapter 10. Planning for Installation on IBM Power Systems
10.1. Upgrade or Install?
10.2. Is Your Hardware Compatible?
10.3. IBM Installation Tools
- Install and configure Linux on a non-virtualized IBM Power Systems server.
- Install and configure Linux on servers with previously-configured logical partitions (LPARs, also known as virtualized servers).
- Install IBM service and productivity tools on a new or previously installed Linux system. The IBM service and productivity tools include dynamic logical partition (DLPAR) utilities.
- Upgrade system firmware level on IBM Power Systems servers.
- Perform diagnostics or maintenance operations on previously installed systems.
- Migrate a LAMP server (software stack) and application data from a System x to a System p system. A LAMP server is a bundle of open source software. LAMP is an acronym for Linux, Apache HTTP Server, MySQL relational database, and the PHP (or sometimes Perl, or Python) language.
10.4. Preparation for IBM Power Systems Servers
Important
c00000, otherwise you might see errors such as:
DEFAULT CATCH!, exception-handler=fff00300
DEFAULT CATCH!, exception-handler=fff0030010.5. Supported Installation Targets
- Storage connected by a standard internal interface, such as SCSI, SATA, or SAS
- Fibre Channel Host Bus Adapters and multipath devices. Some can require vendor-provided drivers.
- Virtualized installation on IBM Power Systems servers is also supported when using Virtual SCSI (vSCSI) adapters in virtual client LPARs
Important
10.6. System Specifications List
- If you plan to use a customized partition layout, record:
- The model numbers, sizes, types, and interfaces of the hard drives attached to the system. For example, Seagate ST3320613AS 320 GB on SATA0, Western Digital WD7500AAKS 750 GB on SATA1. This will allow you to identify specific hard drives during the partitioning process.
- If you are installing Red Hat Enterprise Linux as an additional operating system on an existing system, record:
- Information about the partitions used on the system. This information can include file system types, device node names, file system labels, and sizes. This will allow you to identify specific partitions during the partitioning process. Remember that different operating systems identify partitions and drives differently, therefore even if the other operating system is a Unix operating system, the device names can be reported by Red Hat Enterprise Linux differently. This information can usually be found by executing the equivalent of the
mountcommand andblkidcommand and in the/etc/fstabfile.If you have other operating systems already installed, the Red Hat Enterprise Linux 7 installation program attempts to automatically detect and configure to boot them. You can manually configure any additional operating systems if they are not detected properly. For more information, see Section 13.15.1, “Boot Loader Installation”.
- If you plan to install from an image on a local hard drive:
- The hard drive and directory that holds the image.
- If you plan to install from a network location:
- The make and model numbers of the network adapters on your system. For example, Netgear GA311. This will allow you to identify adapters when manually configuring the network.
- IP, DHCP, and BOOTP addresses
- Netmask
- Gateway IP address
- One or more name server IP addresses (DNS)
- The location of the installation source on an FTP server, HTTP (web) server, HTTPS (web) server, or NFS server.
If any of these networking requirements or terms are unfamiliar to you, contact your network administrator for assistance. - If you plan to install on an iSCSI target:
- The location of the iSCSI target. Depending on your network, you might also need a CHAP user name and password, and perhaps a reverse CHAP user name and password.
- If your computer is part of a domain:
- You should verify that the domain name will be supplied by the DHCP server. If not, you will need to input the domain name manually during installation.
10.7. Disk Space and Memory Requirements
Note
/, swap and a PReP boot partition) must be dedicated to Red Hat Enterprise Linux.
| Installation type | Minimum required RAM |
|---|---|
| Local media installation (USB, DVD) | 1,280 MiB |
| NFS network installation | 1,280 MiB |
| HTTP, HTTPS, or FTP network installation | 1,664 MiB |
10.8. RAID and Other Disk Devices
10.8.1. Hardware RAID
10.8.2. Software RAID
Note
10.8.3. USB Disks
10.9. Choose an Installation Boot Method
Note
%post section of a kickstart file.
- Full installation DVD or USB drive
- You can create bootable media from the full installation DVD ISO image. In this case, a single DVD or USB drive can be used to complete the entire installation - it will serve both as a boot device and as an installation source for installing software packages. See Chapter 3, Making Media for instructions on how to make a full installation DVD or USB drive.
- Minimal boot CD, DVD or USB Flash Drive
- A minimal boot CD, DVD or USB flash drive is created using a small ISO image, which only contains data necessary to boot the system and start the installation. If you use this boot media, you will need an additional installation source from which packages will be installed. See Chapter 3, Making Media for instructions on making boot CDs, DVDs and USB flash drives.
- PXE Server
- A preboot execution environment (PXE) server allows the installation program to boot over the network. After you boot the system, you complete the installation from a different installation source, such as a local hard drive or a location on a network. For more information on PXE servers, see Chapter 24, Preparing for a Network Installation.
10.10. Automating the Installation with Kickstart
Chapter 11. Updating Drivers During Installation on IBM Power Systems
Important
- place the ISO image file of the driver disc in a location accessible to the installation program, on a local hard drive, on a USB flash drive, or on a CD or DVD.
- create a driver disc by extracting the image file onto a CD or a DVD, or a USB flash drive. See the instructions for making installation discs in Section 3.1, “Making an Installation CD or DVD” for more information on burning ISO image files to a CD or DVD, and Section 3.2, “Making Installation USB Media” for instructions on writing ISO images to USB drives.
Warning
11.1. Preparing for a Driver Update During Installation
- Automatic driver update
- When starting the installation, the Anaconda installation program will attempt to detect all attached storage devices. If there is a storage device labeled
OEMDRVpresent when the installation begins, Anaconda will always treat it like a driver update disc and attempt to load drivers present on it. - Assisted driver update
- You can specify the
inst.ddboot option when starting the installation. If you use this option without any parameters, Anaconda will display a list of all storage devices connected to the system, and it will prompt you to select a device which contains a driver update. - Manual driver update
- You can specify the
inst.dd=locationboot option when starting the installation, where location is the path to a driver update disc or ISO image. When you specify this option, Anaconda will attempt to load any driver updates it finds at the specified location. With manual driver updates, you can specify either locally available storage devices, or a network location (anHTTP,HTTPSorFTPserver).
Note
inst.dd=location and inst.dd at the same time. However, what Anaconda does in this case depends on the type of location that you use. If it is a device, Anaconda prompts you to select drivers to update from the specified device and then it offers you additional devices. If location is a network location, Anaconda first prompts you to select a device containing a driver update and then it lets you update drivers from the specified network location.
OEMDRV, and it must be physically connected to the installation system. To use the assisted method, you can use any local storage device any label other than OEMDRV. To use the manual method, you can use any local storage with a different label, or a network location accessible from the installation system.
Important
ip= option when loading a driver update from a network location. See Section 23.1, “Configuring the Installation System at the Boot Menu” for details.
11.1.1. Preparing to Use a Driver Update Image File on Local Storage
- In order for the installation program to automatically recognize the driver disk, the volume label of the storage device must be
OEMDRV. Also, you will need to extract the contents of the ISO image file to the root directory of the storage device rather than copy the ISO image itself. See Section 11.2.1, “Automatic Driver Update”. Note that installation of a driver from a device labeledOEMDRVis always recommended and preferable to the manual installation. - For manual installation, simply copy the ISO image, as a single file, onto the storage device. You can rename the file if you find it helpful but you must not change the file name extension, which must remain
.iso, for exampledd.iso. See Section 11.2.2, “Assisted Driver Update” to learn how to select the driver update manually during installation.
11.1.2. Preparing a Driver Disc
rhdd3, which is a signature file that contains the driver disc's description, and a directory named rpms, which contains the RPM packages with the actual drivers for various architectures.
.iso, then you have not created the disc correctly and should try again. Ensure that you choose an option similar to Burn from Image if you use a Linux desktop other than GNOME, or if you use a different operating system.
11.2. Performing a Driver Update During Installation
- let the installation program automatically find and offer a driver update for installation,
- let the installation program prompt you to locate a driver update,
- manually specify a path to a driver update image or an RPM package.
Important
11.2.1. Automatic Driver Update
OEMDRV volume label to your computer before starting the installation process.
Note
OEMDRV block device to automatically load a Kickstart file. This file must be named ks.cfg and placed in the root of the device to be loaded. See Chapter 27, Kickstart Installations for more information about Kickstart installations.
OEMDRV, it will treat it as a driver update disc and attempt to load driver updates from this device. You will be prompted to select which drivers to load:

Figure 11.1. Selecting a Driver
11.2.2. Assisted Driver Update
OEMDRV volume label available to install a driver during installation. However, if no such device is detected and the inst.dd option was specified at the boot command line, the installation program lets you find the driver disk in interactive mode. In the first step, select a local disk partition from the list for Anaconda to scan for ISO files. Then, select one of the detected ISO files. Finally, select one or more available drivers. The image below demonstrates the process in the text user interface with individual steps highlighted.

Figure 11.2. Selecting a Driver Interactively
Note
OEMDRV volume label, either use the inst.dd option with no arguments and use the menu to select the device, or use the following boot option for the installation program to scan the media for drivers:
inst.dd=/dev/sr0
inst.dd=/dev/sr011.2.3. Manual Driver Update
inst.dd=location to it, where location is a path to the driver update disc:

Figure 11.3. Specifying a Path to a Driver Update
11.2.4. Blacklisting a Driver
modprobe.blacklist=driver_name option to it. Replace driver_name with names of a driver or drivers you want to disable, for example:
modprobe.blacklist=ahci
modprobe.blacklist=ahcimodprobe.blacklist= boot option will remain disabled on the installed system and appear in the /etc/modprobe.d/anaconda-blacklist.conf file. See Chapter 23, Boot Options for more information about blacklisting drivers and other boot options.
Chapter 12. Booting the Installation on IBM Power Systems
Figure 12.1. The SMS Console
Important
inst.vnc boot option (see Enabling Remote Access).
12.2. Installing from a Different Source
| Boot method | Installation source |
|---|---|
| Full installation media (DVD) | The boot media itself |
| Minimal boot media (CD or DVD) | Full installation DVD ISO image or the installation tree extracted from this image, placed in a network location or on a hard drive |
| Network boot | Full installation DVD ISO image or the installation tree extracted from this image, placed in a network location |
12.3. Booting from the Network Using an Installation Server
Select Boot Options in the SMS menu, then Select Boot/Install Device. Finally, select your network device from the list of available devices.
Procedure 12.1. How to Start the Installation Program from the Network
- Ensure that the network cable is attached. The link indicator light on the network socket should be lit, even if the computer is not switched on.
- Switch on the computer.
- Networking setup and diagnostic information usually appears before your computer connects to the server, although this depends on the hardware in use. Then you will see a menu with options specifying how the network boot server is setup. Press the number key that corresponds to the desired option. In case you are not sure which option you should select, ask your server administrator.
Important
vmlinuz and initrd.img images to boot your system over a network. You cannot use the ppc64.img image to boot over a network; the file is too large for TFTP.
Chapter 13. Installing Using Anaconda
- Use Kickstart to automate the installation as described in Chapter 27, Kickstart Installations
- Perform the graphical installation remotely by connecting to the installation system from another computer with a graphical display using the VNC (Virtual Network Computing) protocol - see Chapter 25, Using VNC
13.1. Introduction to Anaconda
13.2. Consoles and Logging During the Installation
13.2.1. Accessing Consoles
root privileges, unless this prompt was specifically disabled using a boot option or a Kickstart command.
Note
Note
| Shortcut | Contents |
|---|---|
| Ctrl+b 1 | Main installation program window. Contains text-based prompts (during text mode installation or if you use VNC Direct Mode), and also some debugging information. |
| Ctrl+b 2 | Interactive shell prompt with root privileges. |
| Ctrl+b 3 | Installation log; displays messages stored in /tmp/anaconda.log. |
| Ctrl+b 4 | Storage log; displays messages related storage devices from kernel and system services, stored in /tmp/storage.log. |
| Ctrl+b 5 | Program log; displays messages from other system utilities, stored in /tmp/program.log. |
13.2.2. Saving Screenshots
/tmp/anaconda-screenshots/.
autostep --autoscreenshot command in a Kickstart file to capture and save each step of the installation automatically. See Section 27.3.1, “Kickstart Commands and Options” for details.
13.3. Installing in Text Mode
Important
inst.xdriver=vesa option - see Chapter 23, Boot Options.

Figure 13.1. Text Mode Installation
[x], and screens which require your attention before the installation can begin are marked with [!]. Available commands are displayed below the list of available options.
Note
Processing... label. To refresh to the current status of text menu items, use the r option at the text mode prompt.
- The installer will always use the English language and the US English keyboard layout. You can configure your language and keyboard settings, but these settings will only apply to the installed system, not to the installation.
- You cannot configure any advanced storage methods (LVM, software RAID, FCoE, zFCP and iSCSI).
- It is not possible to configure custom partitioning; you must use one of the automatic partitioning settings. You also cannot configure where the boot loader will be installed.
- You cannot select any package add-ons to be installed; they must be added after the installation finishes using the Yum package manager.
inst.text boot option used either at the boot command line in the boot menu, or in your PXE server configuration. See Chapter 12, Booting the Installation on IBM Power Systems for information about booting and using boot options.
13.4. Using the HMC vterm
13.5. Installing in the Graphical User Interface

Figure 13.2. The Installation Summary Screen
| Shortcut keys | Usage |
|---|---|
| Tab and Shift+Tab | Cycle through active control elements (buttons, check boxes, and so on.) on the current screen |
| Up and Down | Scroll through lists |
| Left and Right | Scroll through horizontal toolbars and table entries |
| Space and Enter | Select or remove a highlighted item from selection and expand and collapse drop-down menus |
13.6. Welcome Screen and Language Selection
Note
GeoIP module.

Figure 13.3. Language Configuration
13.7. The Installation Summary Screen

Figure 13.4. The Installation Summary Screen
Note

Figure 13.5. Network Configuration Screen When No Network Is Detected
13.8. Date & Time
- Using your mouse, click on the interactive map to select a specific city. A red pin appears indicating your selection.
- You can also scroll through the Region and City drop-down menus at the top of the screen to select your time zone.
- Select Etc at the bottom of the Region drop-down menu, then select your time zone in the next menu adjusted to GMT/UTC, for example
GMT+1.
timezone command in timezone (required) for details.
Note
Note
13.9. Language Support
Español. Then you can select a locale specific to your region in the right panel, for example Español (Costa Rica). You can select multiple languages and multiple locales. The selected languages are highlighted in bold in the left panel.

Figure 13.6. Configuring Language Support
Note
13.10. Keyboard Configuration

Figure 13.7. Keyboard Configuration
Important
Note
13.11. Security Policy
Important
/root/openscap_data directory on the installed system.

Figure 13.8. Security policy selection screen
Note
HTTP, HTTPS or FTP server. Use the full address of the content, including the protocol (such as http://). A network connection must be active (enabled in Section 13.13, “Network & Hostname”) before you can load a custom profile. The content type will be detected automatically by the installer.
13.12. Installation Source

Figure 13.9. Installation Source Screen
- Auto-detected installation media
- If you started the installation using the full installation DVD or USB drive, the installation program will detect it and display basic information under this option. Click the button to ensure that the media is suitable for installation. This integrity test is the same as the one performed if you selected
Test this media & Install Red Hat Enterprise Linuxin the boot menu, or if you used therd.live.checkboot option. - ISO file
- This option will appear if the installation program detected a partitioned hard drive with mountable file systems. Select this option, click the button, and browse to the installation ISO file's location on your system. Then click to ensure that the file is suitable for installation.
- On the network
- To specify a network location, select this option and choose from the following options in the drop-down menu:
- http://
- https://
- ftp://
- nfs
Using your selection as the start of the location URL, type the rest into the address box. If you choose NFS, another box will appear for you to specify any NFS mount options.Important
When selecting an NFS-based installation source, you must specify the address with a colon (:) character separating the host name from the path. For example:server.example.com:/path/to/directory
server.example.com:/path/to/directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow To configure a proxy for an HTTP or HTTPS source, click the button. Check Enable HTTP proxy and type the URL into the Proxy URL box. If your proxy requires authentication, check Use Authentication and enter a user name and password. Click .If your HTTP or HTTPS URL refers to a repository mirror list, mark the check box under the input field.
13.13. Network & Hostname
Important
Note
em1 or wl3sp0. For information about these standards, see the Red Hat Enterprise Linux 7 Networking Guide.

Figure 13.10. Network & Hostname Configuration Screen
localhost.localdomain means that no specific static host name for target system is configured, and the actual host name of installed system will be configured during process of network configuration (for example, by NetworkManager using DHCP or DNS).
Important
Note
13.13.1. Edit Network Connections
- Mark the Automatically connect to this network when it is available check box if you want to use the connection every time the system boots. You can use more than one connection that will connect automatically. This setting will carry over to the installed system.

Figure 13.11. Network Auto-Connection Feature
- By default, IPv4 parameters are configured automatically by the DHCP service on the network. At the same time, the IPv6 configuration is set to the
Automaticmethod. This combination is suitable for most installation scenarios and usually does not require any changes.
Figure 13.12. IP Protocol Settings
13.13.2. Advanced Network Interfaces

Figure 13.13. Network & Hostname Configuration Screen
Bond- represents NIC (Network Interface Controller) Bonding, a method to bind multiple network interfaces together into a single, bonded, channel.Bridge- represents NIC Bridging, a method to connect multiple separate network into one aggregate network.Team- represents NIC Teaming, a new implementation to aggregate links, designed to provide a small kernel driver to implement the fast handling of packet flows, and various applications to do everything else in user space.VLAN- represents a method to create multiple distinct broadcast domains, which are mutually isolated.

Figure 13.14. Advanced Network Interface Dialog
Note
13.14. Software Selection
- Add-ons listed above the horizontal line are specific to the environment you selected. If you select any add-ons in this part of the list and then select a different environment, your selection will be lost.
- Add-ons listed below the horizontal line are available for all environments. Selecting a different environment will not impact the selections made in this part of the list.

Figure 13.15. Example of a Software Selection for a Server Installation
server variant provides environments designed for servers, while the workstation variant has several choices for deployment as a developer workstation, and so on.
repodata/*-comps-variant.architecture.xml file on the Red Hat Enterprise Linux Installation DVD which you are using as the installation source. This file contains a structure describing available environments (marked by the <environment> tag) and add-ons (the <group> tag).
Important
%packages section of the Kickstart file. See Section 27.3.2, “Package Selection” for instructions on selecting packages to install in a Kickstart file, and Chapter 27, Kickstart Installations for general information about automating the installation with Kickstart.
13.14.1. Core Network Services
- centralized logging through the
rsyslogservice - email through SMTP (Simple Mail Transfer Protocol)
- network file sharing through NFS (Network File System)
- remote access through SSH (Secure SHell)
- resource advertising through mDNS (multicast DNS)
13.15. Installation Destination
Warning
Important
Important
Special cases
- If you have a RAID card, be aware that some BIOS types do not support booting from the RAID card. In such a case, the
/bootpartition must be created on a partition outside of the RAID array, such as on a separate hard drive. It is necessary to use an internal hard drive for partition creation with problematic RAID cards. A/bootpartition is also necessary for software RAID setups. If you have chosen to automatically partition your system, you should manually edit your/bootpartition; see Section 13.15.4, “Manual Partitioning” for more details. - When you install Red Hat Enterprise Linux on a system with both multipath and non-multipath storage devices, the automatic partitioning layout in the installation program might create volume groups that contain a mix of multipath and non-multipath devices. This defeats the purpose of multipath storage. We advise that you select only multipath or only non-multipath devices on the Installation Destination screen. Alternatively, proceed to manual partitioning.
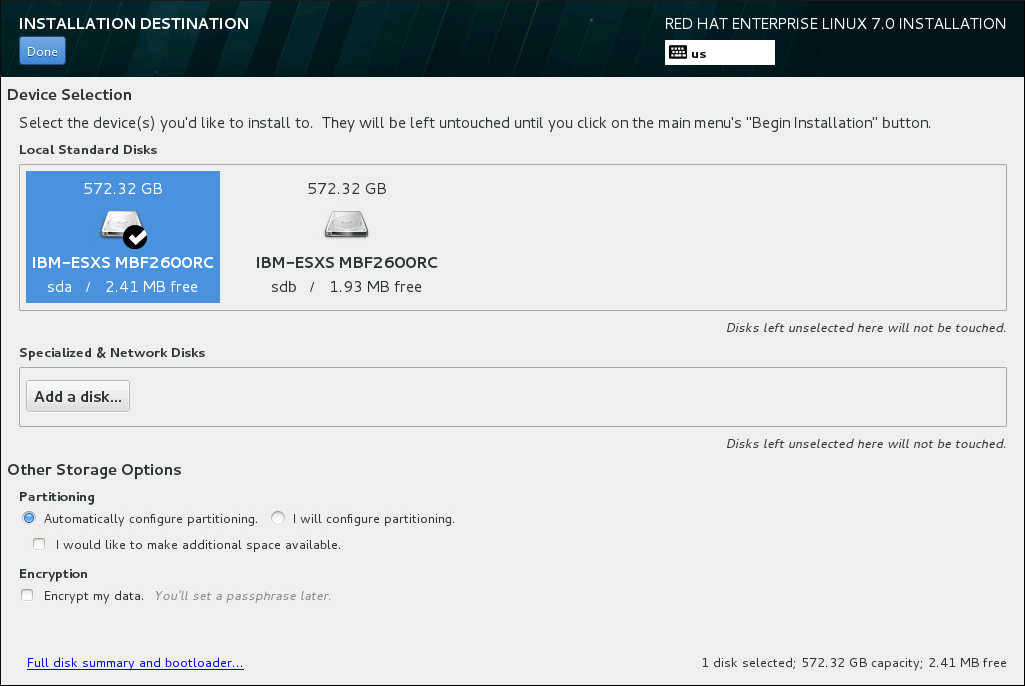
Figure 13.16. Storage Space Overview
- In the Partitioning section, you can select how storage devices are partitioned and how volumes are created. You can configure the partitions, manually or allow the installation program to do it automatically.Automatic partitioning is recommended if you are doing a clean installation on previously unused storage or do not need to keep any data that might be present on the storage. To proceed this way, leave the default selection of the Automatically configure partitioning radio button, and the installation program will create the necessary partitions and volumes on the storage space for you.For automatic partitioning, you can also select the I would like to make additional space available check box to choose how to reassign space from other file systems to this installation. After you click , there are two dialogs that can appear. If you selected automatic partitioning but there is not enough storage space to complete the installation using the recommended partitioning configuration, a dialog will appear:

Figure 13.17. Installation Options Dialog with Option to Reclaim Space
You can click to the Red Hat Enterprise Linux software selection link. The link will navigate you to the Software selection section, where you can change what software you want to install, and free some aditional storage space.Alternatively, you can click to return to the Installation Destination screen, where it is possible to add more storage devices or choose to configure partitioning manually. Click to free some storage space from existing file systems. See Section 13.15.3, “Reclaim Disk Space” for details.The second dialog appears if you cannot create enough free space. In this case, you have to add more disks on the initial storage screen or quit the installation.If you select the I will configure partitioning radio button for manual setup, you will be brought to the Manual Partitioning screen after clicking . See Section 13.15.4, “Manual Partitioning” for details. - In the Encryption section, you can select the Encrypt my data check box to encrypt all partitions except for the
/bootpartition. See the Red Hat Enterprise Linux 7 Security Guide for information on encryption.
13.15.1. Boot Loader Installation
Warning
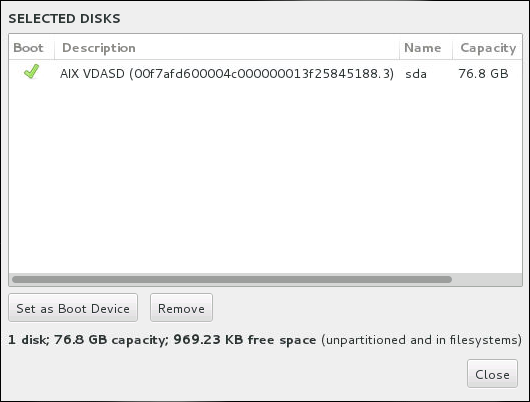
Figure 13.18. Summary of Selected Disks
Warning
13.15.2. Encrypt Partitions

Figure 13.19. Enter Passphrase for an Encrypted Partition
Warning
13.15.3. Reclaim Disk Space
Warning
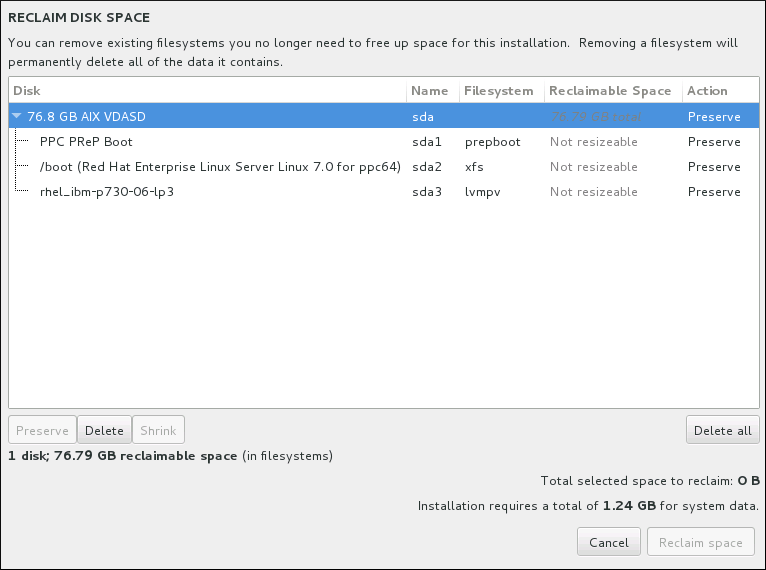
Figure 13.20. Reclaim Disk Space from Existing File Systems
- - leaves the file system untouched and no data will be deleted. This is the default action.
- - removes the file system entirely. All the space it takes up on the disk will be made available for the installation.
- - recovers free space from the file system and makes it available for this installation. Use the slider to set a new size for the selected partition. Can only be used on resizable partitions where LVM or RAID is not used.
- - this button, located on the right, marks all file systems for deletion by default. Upon clicking, it changes the label and allows you to mark all file systems to be preserved again.
13.15.4. Manual Partitioning
Warning

Figure 13.21. The Manual Partitioning Screen
Note
13.15.4.1. Adding File Systems and Configuring Partitions
PReP, /, /home, /boot, and swap. You can also create additional partitions you require. See Section 13.15.4.4, “Recommended Partitioning Scheme” for further details.
Note
/boot partition, a / (root) volume, and a swap volume proportionate to the size of the available storage. These are the recommended file systems for a typical installation, but you can add additional file systems and mount points if you need to.
/ for the root partition or /boot for the boot partition. Then enter the size of the file system in the Desired Capacity text field; for example, 2GiB. If you leave the field empty or if you specify a size bigger than available space, all remaining free space is used instead. After entering these details, click the button to create the partition.
Note
/boot, and then create the rest of the partitions, letting the installation program allocate the remaining capacity to them.
Standard Partition, BTRFS, LVM, and LVM Thin Provisioning. Note that the /boot partition will always be located on a standard partition, regardless of the value selected in this menu.
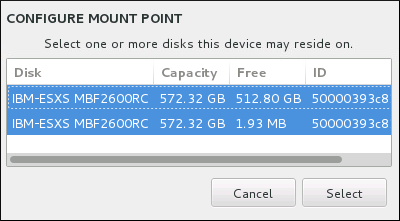
Figure 13.22. Configuring Mount Points

Figure 13.23. Rescanning Disks

Figure 13.24. Customizing Partitions
- Mount Point - enter the file system's mount point. For example, if a file system should be the root file system, enter
/; enter/bootfor the/bootfile system, and so on. For a swap file system, the mount point should not be set - setting the file system type toswapis sufficient. - Desired Capacity - enter the desired size of the file system. You can use common size units such as KiB or GiB. The default is MiB if no other unit is specified.
- Device type - choose one of these types: Standard Partition, LVM, RAID, LVM Thin Provisioning, or BTRFS. Check the adjacent Encrypt box to encrypt the partition or volume. You will be prompted to set a password later. RAID is only available if two or more disks are selected for partitioning, and if you choose this type, you can also set the RAID Level. Similarly, if you select LVM, you can specify the Volume Group.
- File system - in the drop-down menu, select the appropriate file system type for this partition or volume. Check the adjacent Reformat box to format an existing partition, or leave it unchecked to retain your data. Note that newly created partitions and volumes must be reformatted, and the check box cannot be unchecked in this case.
- Label - assign a label to the partition. Labels are used for you to easily recognize and address individual partitions.
- Name - assign a name to an LVM or Btrfs volume. Note that standard partitions are named automatically when they are created and their name cannot be edited, such as
/homebeing assigned the namesda1.
Important
/usr or /var is partitioned separately from the rest of the root volume, the boot process becomes much more complex because these directories contain components critical to it. In some situations, such as when these directories are placed on an iSCSI drive or an FCoE location, the system can either be unable to boot, or hang with a Device is busy error when powering off or rebooting.
/usr or /var, not to directories below them. For example, a separate partition for /var/www will work without issues.
13.15.4.1.1. File System Types
Device Types
- standard partition - A standard partition can contain a file system or swap space, or it can provide a container for software RAID or an LVM physical volume.
- logical volume (LVM) - Creating an LVM partition automatically generates an LVM logical volume. LVM can improve performance when using physical disks. For information on how to create a logical volume, see Section 13.15.4.3, “Create LVM Logical Volume”. For more information regarding LVM, see the Red Hat Enterprise Linux 7 Logical Volume Manager Administration guide.
- LVM thin provisioning - Using thin provisioning, you can manage a storage pool of free space, known as a thin pool, which can be allocated to an arbitrary number of devices when needed by applications. The thin pool can be expanded dynamically when needed for cost-effective allocation of storage space. For more information regarding LVM, see the Red Hat Enterprise Linux 7 Logical Volume Manager Administration guide.
Note
The installer will automatically reserve 20% of any requested space for an LVM thin pool logical volume in the volume group containing it. This is a safety measure to ensure that you can extend either the metadata volume or the data volume of your thinly provisioned logical volume. - software RAID - Creating two or more software RAID partitions allows you to create a RAID device. One RAID partition is assigned to each disk on the system. To create a RAID device, see Section 13.15.4.2, “Create Software RAID”. For more information regarding RAID, see the Red Hat Enterprise Linux 7 Storage Administration Guide.
File Systems
- xfs - XFS is a highly scalable, high-performance file system that supports file systems up to 16 EiB (approximately 16 billion GiB), files up to 8 EiB (approximately 8 billion GiB), and directory structures containing tens of millions of entries. XFS supports metadata journaling, which facilitates quicker crash recovery. The XFS file system can also be defragmented and resized while mounted and active. This file system is selected by default and is highly recommended. For information on how to translate common commands from previously used ext4 file system to XFS, see Appendix F, Reference Table for ext4 and XFS Commands.The maximum supported size of an XFS file system in Red Hat Enterprise Linux is currently 500 TiB.
- ext4 - The ext4 file system is based on the ext3 file system and features a number of improvements. These include support for larger file systems and larger files, faster and more efficient allocation of disk space, no limit on the number of subdirectories within a directory, faster file system checking, and more robust journaling.The maximum supported size of an ext4 file system in Red Hat Enterprise Linux is currently 50 TiB.
- ext3 - The ext3 file system is based on the ext2 file system and has one main advantage - journaling. Using a journaling file system reduces time spent recovering a file system after a crash as there is no need to check the file system for metadata consistency by running the
fsckutility every time a crash occurs. - ext2 - An ext2 file system supports standard Unix file types, including regular files, directories, or symbolic links. It provides the ability to assign long file names, up to 255 characters.
- vfat - The VFAT file system is a Linux file system that is compatible with Microsoft Windows long file names on the FAT file system.
- swap - Swap partitions are used to support virtual memory. In other words, data is written to a swap partition when there is not enough RAM to store the data your system is processing.
- PReP - this small boot partition is located on the first partition of the hard drive. The PReP boot partition contains the GRUB2 boot loader, which allows other IBM Power Systems servers to boot Red Hat Enterprise Linux.
13.15.4.2. Create Software RAID

Figure 13.25. Creating a Software RAID Partition - the Device Type Menu Expanded
- Create a mount point as described in Section 13.15.4.1, “Adding File Systems and Configuring Partitions”. By configuring this mount point, you configure the RAID device.
- Keeping the partition selected in the left pane, select the configuration button below the pane to open the Configure Mount Point dialog. Select which disks will be included in the RAID device and click .
- Click the Device Type drop-down menu and select RAID.
- Click the File System drop-down menu and select your preferred file system type (see Section 8.14.4.1.1, “File System Types”.
- Click the RAID Level drop-down menu and select your preferred level of RAID.The available RAID levels are:
- RAID0 - Optimized performance (stripe)
- Distributes data across multiple disks. Level 0 RAIDs offer increased performance over standard partitions, and can be used to pool the storage of multiple disks into one large virtual device. Note that Level 0 RAIDs offer no redundancy, and that the failure of one device in the array destroys data in the entire array. RAID 0 requires at least two RAID partitions.
- RAID1 - Redundancy (mirror)
- Mirrors all data on one disk onto one or more other disks. Additional devices in the array provide increasing levels of redundancy. RAID 1 requires at least two RAID partitions.
- RAID4 - Error detection (parity)
- Distributes data across multiple disks, and uses one disk in the array to store parity information that safeguards the array in case any disk within the array fails. Because all parity information is stored on one disk, access to this disk creates a bottleneck in the performance of the array. RAID 4 requires at least three RAID partitions.
- RAID5 - Distributed error detection
- Distributes data and parity information across multiple disks. Level 5 RAIDs therefore offer the performance advantages of distributing data across multiple disks, but do not share the performance bottleneck of level 4 RAIDs because the parity information is also distributed through the array. RAID 5 requires at least three RAID partitions.
- RAID6 - Redundant
- Level 6 RAIDs are similar to level 5 RAIDs, but instead of storing only one set of parity data, they store two sets. RAID 6 requires at least four RAID partitions.
- RAID10 - Redundancy (mirror) and Optimized performance (stripe)
- Level 10 RAIDs are nested RAIDs or hybrid RAIDs. They are constructed by distributing data over mirrored sets of disks. For example, a level 10 RAID array constructed from four RAID partitions consists of two mirrored pairs of striped partitions. RAID 10 requires at least four RAID partitions.
- Click to save your changes, and either continue with another partition or click to return to the Installation Summary screen.
13.15.4.3. Create LVM Logical Volume
Important
lvm command. To return to the text-mode installation, press Ctrl+Alt+F1.

Figure 13.26. Configuring a Logical Volume
- Create a mount point for the LVM volume as described in Section 13.15.4.1, “Adding File Systems and Configuring Partitions”.
- Click the Device Type drop-down menu and select LVM. The Volume Group drop-down menu appears and displays the newly-created volume group name.
- Optionally, either click the menu and select Create a new volume group or click to configure the newly-created volume group, if you need to. Both the Create a new volume group option and the button lead to the Configure Volume Group dialog, where you can rename the logical volume group and select which disks will be included.
Note
The configuration dialog does not allow you to specify the size of the volume group's physical extents. The size will always be set to the default value of 4 MiB. If you want to create a volume group with different physical extents, create it manually by switching to an interactive shell and using thevgcreatecommand, or use a Kickstart file with thevolgroup --pesize=sizecommand.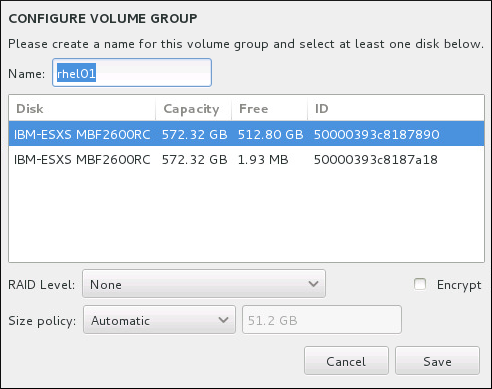
Figure 13.27. Customizing an LVM Volume Group
The available RAID levels are the same as with actual RAID devices. See Section 13.15.4.2, “Create Software RAID” for more information. You can also mark the volume group for encryption and set the size policy for it. The available policy options are:- Automatic - the size of the volume group is set automatically so that it is just large enough to contain the configured logical volumes. This is optimal if you do not need free space within the volume group.
- As large as possible - the volume group is created with maximum size, regardless of the size of the configured logical volumes it contains. This is optimal if you plan to keep most of your data on LVM and later need to increase the size of some existing logical volumes, or if you need to create additional logical volumes within this group.
- Fixed - with this option, you can set an exact size of the volume group. Any configured logical volumes must then fit within this fixed size. This is useful if you know exactly how large you would like the volume group to be.
Click when the group is configured. - Click to save your changes, and either continue with another partition or click to return to the Installation Summary screen.
Warning
/boot partition on an LVM volume is not supported.
13.15.4.4. Recommended Partitioning Scheme
- A PReP boot partition - recommended size of 4 to 8 MiB
- The first partition of the hard drive should include a PReP boot partition. This contains the GRUB2 boot loader, which allows other IBM Power Systems servers to boot Red Hat Enterprise Linux.
-
/bootpartition - recommended size at least 1 GiB - The partition mounted on
/bootcontains the operating system kernel, which allows your system to boot Red Hat Enterprise Linux, along with files used during the bootstrap process. Due to the limitations of most firmwares, creating a small partition to hold these is recommended. In most scenarios, a 1 GiB boot partition is adequate. Unlike other mount points, using an LVM volume for/bootis not possible -/bootmust be located on a separate disk partition.Note
If you have a RAID card, be aware that some BIOS types do not support booting from the RAID card. In such a case, the/bootpartition must be created on a partition outside of the RAID array, such as on a separate hard drive.Warning
If you have a RAID card, be aware that Red Hat Enterprise Linux does not support setting up hardware RAID on an IPR card. You can boot the standalone diagnostics CD prior to installation to create a RAID array and then install to that RAID array. root- recommended size of 10 GiB- This is where "
/", or the root directory, is located. The root directory is the top-level of the directory structure. By default, all files are written to this file system unless a different file system is mounted in the path being written to (for example,/bootor/home).While a 5 GiB root file system allows you to install a minimal installation, it is recommended to allocate at least 10 GiB so that you can install as many package groups as you want.Important
Do not confuse the/directory with the/rootdirectory. The/rootdirectory is the home directory of the root user. The/rootdirectory is sometimes referred to as slash root to distinguish it from the root directory. /home- recommended size at least 1 GiB- To store user data separately from system data, create a dedicated file system for the
/homedirectory. This file system should be sized based on the amount of data that will be stored locally, number of users, and so on. This will enable you to upgrade or reinstall Red Hat Enterprise Linux without erasing user data files. If you select automatic partitioning, it is recommended to have at least 55GiB of disk space available for the installation, to ensure that the/homefile system is created. swappartition - recommended size at least 1 GB- Swap file systems support virtual memory; data is written to a swap file system when there is not enough RAM to store the data your system is processing. Swap size is a function of system memory workload, not total system memory and therefore is not equal to the total system memory size. Therefore, it is important to analyze what applications a system will be running and the load those applications will serve in order to determine the system memory workload. Application providers and developers should be able to provide some guidance.When the system runs out of swap space, the kernel terminates processes as the system RAM memory is exhausted. Configuring too much swap space results in storage devices being allocated but idle and is a poor use of resources. Too much swap space can also hide memory leaks. The maximum size for a swap partition and other additional information can be found in the
mkswap(8)manual page.The following table provides the recommended size of a swap partition depending on the amount of RAM in your system. If you let the installation program partition your system automatically, the swap partition size will be established using these guidelines. Automatic partitioning setup assumes that the maximum size of the swap partition is limited to 10% of the total size of the hard drive, and the installer cannot create swap partitions more than 128GB in size. If you want to set the swap partition size to more than 10% of the system's storage space, or more than 128GB, you must edit the partitioning layout manually.Expand Table 13.3. Recommended System Swap Space Amount of RAM in the system Recommended swap space Recommended swap space if allowing for hibernation less than 2 GB 2 times the amount of RAM 3 times the amount of RAM 2 GB - 8 GB Equal to the amount of RAM 2 times the amount of RAM 8 GB - 64 GB 4GB to 0.5 times the amount of RAM 1.5 times the amount of RAM more than 64 GB workload dependent (at least 4GB) hibernation not recommended At the border between each range listed above (for example, a system with 2 GB, 8 GB, or 64 GB of system RAM), discretion can be exercised with regard to chosen swap space. If your system resources allow for it, increasing the swap space can lead to better performance.Distributing swap space over multiple storage devices - particularly on systems with fast drives, controllers and interfaces - also improves swap space performance.
Warning
/var/cache/yum/ by default. If you create a separate partition or volume for /var, ensure that it is at least 3GB in size to accommodate downloaded package updates.
13.16. Storage Devices

Figure 13.28. Storage Space Overview
13.16.1. The Storage Devices Selection Screen
- Multipath Devices
- Storage devices accessible through more than one path, such as through multiple SCSI controllers or Fiber Channel ports on the same system.The installation program only detects multipath storage devices with serial numbers that are 16 or 32 characters long.
- Other SAN Devices
- Devices available on a Storage Area Network (SAN).
- Firmware RAID
- Storage devices attached to a firmware RAID controller.

Figure 13.29. Tabbed Overview of Specialized Storage Devices
- - use to attach iSCSI devices; continue with Section 13.16.1.1.1, “Configure iSCSI Parameters”
- - use to configure a Fibre Channel Over Internet storage device; continue with Section 13.16.1.1.2, “Configure FCoE Parameters”

Figure 13.30. The Storage Devices Search Tab
/etc/fstab file.
Important
13.16.1.1. Advanced Storage Options

Figure 13.31. Advanced Storage Options
13.16.1.1.1. Configure iSCSI Parameters

Figure 13.32. The iSCSI Discovery Details Dialog
Note
Procedure 13.1. iSCSI Discovery and Starting an iSCSI Session
- Enter the IP address of the iSCSI target in the Target IP Address field.
- Provide a name in the iSCSI Initiator Name field for the iSCSI initiator in iSCSI qualified name (IQN) format. A valid IQN entry contains:
- the string
iqn.(note the period) - a date code that specifies the year and month in which your organization's Internet domain or subdomain name was registered, represented as four digits for the year, a dash, and two digits for the month, followed by a period. For example, represent September 2010 as
2010-09. - your organization's Internet domain or subdomain name, presented in reverse order with the top-level domain first. For example, represent the subdomain
storage.example.comascom.example.storage - a colon followed by a string that uniquely identifies this particular iSCSI initiator within your domain or subdomain. For example,
:diskarrays-sn-a8675309
A complete IQN can therefore look as follows:iqn.2010-09.storage.example.com:diskarrays-sn-a8675309. Anaconda prepopulates the iSCSI Initiator Name field with a name in this format to help you with the structure.For more information on IQNs , see 3.2.6. iSCSI Names in RFC 3720 - Internet Small Computer Systems Interface (iSCSI) available from http://tools.ietf.org/html/rfc3720#section-3.2.6 and 1. iSCSI Names and Addresses in RFC 3721 - Internet Small Computer Systems Interface (iSCSI) Naming and Discovery available from http://tools.ietf.org/html/rfc3721#section-1. - Use the Discovery Authentication Type drop-down menu to specify the type of authentication to use for iSCSI discovery. The following options are available:
- no credentials
- CHAP pair
- CHAP pair and a reverse pair
- If you selected as the authentication type, provide the user name and password for the iSCSI target in the CHAP Username and CHAP Password fields.
- If you selected as the authentication type, provide the user name and password for the iSCSI target in the CHAP Username and CHAP Password field and the user name and password for the iSCSI initiator in the Reverse CHAP Username and Reverse CHAP Password fields.
- Optionally check the box labeled Bind targets to network interfaces.
- Click the button. Anaconda attempts to discover an iSCSI target based on the information that you provided. If discovery succeeds, the dialog displays a list of all iSCSI nodes discovered on the target.
- Each node is presented with a check box beside it. Click the check boxes to select the nodes to use for installation.

Figure 13.33. The Dialog of Discovered iSCSI Nodes
- The Node login authentication type menu provides the same options as the Discovery Authentication Type menu described in step 3. However, if you needed credentials for discovery authentication, it is typical to use the same credentials to log into a discovered node. To do that, use the additional option from the menu. When the proper credentials have been provided, the button becomes available.
- Click to initiate an iSCSI session.
13.16.1.1.2. Configure FCoE Parameters

Figure 13.34. Configure FCoE Parameters
- Use DCB
- Data Center Bridging (DCB) is a set of enhancements to the Ethernet protocols designed to increase the efficiency of Ethernet connections in storage networks and clusters. Enable or disable the installation program's awareness of DCB with the check box in this dialog. This option should only be enabled for network interfaces that require a host-based DCBX client. Configurations on interfaces that implement a hardware DCBX client should leave this check box empty.
- Use auto vlan
- Auto VLAN indicates whether VLAN discovery should be performed. If this box is checked, then the FIP (FCoE Initiation Protocol) VLAN discovery protocol will run on the Ethernet interface once the link configuration has been validated. If they are not already configured, network interfaces for any discovered FCoE VLANs will be automatically created and FCoE instances will be created on the VLAN interfaces. This option is enabled by default.
13.17. Kdump

Figure 13.35. Kdump Enablement and Configuration
13.18. Begin Installation

Figure 13.36. Ready to Install
Warning
13.20. Installation Complete
login: prompt) appears.
Chapter 14. Troubleshooting Installation on IBM Power Systems
/tmp directory. These files are listed in the following table.
| Log file | Contents |
|---|---|
/tmp/anaconda.log | general Anaconda messages |
/tmp/program.log | all external programs run during the installation |
/tmp/storage.log | extensive storage module information |
/tmp/packaging.log | yum and rpm package installation messages |
/tmp/syslog | hardware-related system messages |
/tmp/anaconda-tb-identifier, where identifier is a random string.
/var/log/anaconda/. However, if installation is unsuccessful, or if the inst.nosave=all or inst.nosave=logs options are used when booting the installation system, these logs will only exist in the installation program's RAM disk. This means they are not saved permanently and will be lost once the system is powered down. To store them permanently, copy those files to another system on the network by using scp on the system running the installation program, or copy them to a mounted storage device (such as an USB flash drive). Details on how to transfer the log files over the network are below.
Note
ssh protocol.
Procedure 14.1. Transferring Log Files Over the Network
- On the system you are installing, press Ctrl+Alt+F2 to access a shell prompt. You will be logged into a root account and you will have access to the installation program's temporary file system.
- Switch to the
/tmpdirectory where the log files are located:cd /tmp
# cd /tmpCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the log files onto another system on the network using the
scpcommand:scp *log user@address:path
# scp *log user@address:pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace user with a valid user name on the target system, address with the target system's address or host name, and path with the path to the directory you want to save the log files into. For example, if you want to log in asjohnto a system with an IP address of192.168.0.122and place the log files into the/home/john/logs/directory on that system, the command will have the following form:scp *log john@192.168.0.122:/home/john/logs/
# scp *log john@192.168.0.122:/home/john/logs/Copy to Clipboard Copied! Toggle word wrap Toggle overflow When connecting to the target system for the first time, the SSH client asks you to confirm that the fingerprint of the remote system is correct and that you want to continue:The authenticity of host '192.168.0.122 (192.168.0.122)' can't be established. ECDSA key fingerprint is a4:60:76:eb:b2:d0:aa:23:af:3d:59:5c:de:bb:c4:42. Are you sure you want to continue connecting (yes/no)?
The authenticity of host '192.168.0.122 (192.168.0.122)' can't be established. ECDSA key fingerprint is a4:60:76:eb:b2:d0:aa:23:af:3d:59:5c:de:bb:c4:42. Are you sure you want to continue connecting (yes/no)?Copy to Clipboard Copied! Toggle word wrap Toggle overflow Typeyesand press Enter to continue. Then, provide a valid password when prompted. The files will start transferring to the specified directory on the target system.
14.1. Trouble Beginning the Installation
14.1.1. Problems with Booting into the Graphical Installation
- Use the basic graphics mode
- You can attempt to perform the installation using the basic graphics driver. To do this, edit the installation program's options at the
boot:prompt and appendinst.xdriver=vesaat the end of the command line. - Specify the display resolution manually
- If the installation program fails to detect your screen resolution, you can override the automatic detection and specify it manually. To do this, append the
inst.resolution=xoption at the boot menu, where x is your display's resolution (for example,1024x768).
14.1.2. Serial Console Not Detected
inst.text and console= boot options. See Chapter 23, Boot Options for more details.
14.2. Trouble During the Installation
14.2.1. No Disks Detected
14.2.2. Reporting Traceback Messages

Figure 14.1. The Crash Reporting Dialog Box
tty1, where you can request more precise information that will enhance the bug report. To return to the graphical interface from tty1, use the continue command.

Figure 14.2. The Expanded Crash Reporting Dialog Box
Procedure 14.2. Reporting Errors to Red Hat Customer Support
- In the menu that appears, select Report a bug to Red Hat Customer Portal.
- To report the bug to Red Hat, you first need to provide your Customer Portal credentials. Click .

Figure 14.3. Customer Portal Credentials
- A new window is now open, prompting you to enter your Customer Portal user name and password. Enter your Red Hat Customer Portal credentials.

Figure 14.4. Configure Red Hat Customer Support
If your network settings require you to use aHTTPorHTTPSproxy, you can configure it by expanding the Advanced menu and entering the address of the proxy server.When you put in all required credentials, click OK to proceed. - A new window appears, containing a text field. Write down any useful information and comments here. Describe how the error can be reproduced by explaining each step you took before the crash reporting dialog appeared. Provide as much relevant detail as possible, including any information you acquired when debugging. Be aware that the information you provide here can become publicly visible on the Customer Portal.If you do not know what caused the error, check the box labeled I don't know what caused this problem at the bottom of the dialog.Then, click .

Figure 14.5. Describe the Problem
- Next, review the information that will be sent to the Customer Portal. The explanation you provided is in the comment tab. Other tabs include such information as your system's host name and other details about the installation environment. You can remove any items you do not want sent to Red Hat, but be aware that providing less detail can affect the investigation of the issue.Click when you finish reviewing the information to be sent.

Figure 14.6. Review the Data to Be Sent
- Review the list of files that will be sent and included in the bug report as individual attachments. These files provide system information that will assist the investigation. If you do not want to send certain files, uncheck the box next to each one. To provide additional files that can help find the problem, click .Once you have reviewed the files to be sent, check the box labeled I have reviewed the data and agree with submitting it. Then, click to send the report and attachments to the Customer Portal.

Figure 14.7. Review the Files to Be Sent
- When the dialog reports that processing has finished, you can click Show log to view details of the reporting process or Close to return to the initial crash reporting dialog box. There, click Quit to exit the installation.
14.2.3. Creating Pre-installation Log Files
inst.debug option to create log files from the environment before the installation starts. These log files contain, for example, the current storage configuration.
- Select the entry.
- Press the Tab key to edit the boot options.
- Append
inst.debugto the options. For example:> vmlinuz ... inst.debug
> vmlinuz ... inst.debugCopy to Clipboard Copied! Toggle word wrap Toggle overflow For further details, see Chapter 23, Boot Options. - Press Enter to start the setup.
/tmp/pre-anaconda-logs/ directory before Anaconda starts. To access the log files:
- Switch to the console. See Section 8.2.1, “Accessing Consoles”.
- Change into the
/tmp/pre-anaconda-logs/directory:cd /tmp/pre-anaconda-logs/
# cd /tmp/pre-anaconda-logs/Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14.2.4. Other Partitioning Problems for IBM Power Systems Users
- A
/(root) partition - A
PReP Bootpartition - A
/bootpartition (only if the root partition is a LVM logical volume or Btrfs subvolume)
14.3. Problems After Installation
14.3.1. Trouble With the Graphical Boot Sequence
Procedure 14.3. Disabling Graphical Boot Temporarily
- Start your computer and wait until the boot loader menu appears. If you set your boot loader timeout period to 0, hold down the Esc key to access it.
- When the boot loader menu appears, use your cursor keys to highlight the entry you want to boot and press the e key to edit this entry's options.
- In the list of options, find the kernel line - that is, the line beginning with the keyword
linux. On this line, locate therhgboption and delete it. The option might not be immediately visible; use the cursor keys to scroll up and down. - Press F10 or Ctrl+X to boot your system with the edited options.
Procedure 14.4. Disabling Graphical Boot Permanently
- Log in to the
rootaccount using thesu -command:su -
$ su -Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the grubby tool to find the default GRUB2 kernel:
grubby --default-kernel /boot/vmlinuz-3.10.0-229.4.2.el7.ppc64
# grubby --default-kernel /boot/vmlinuz-3.10.0-229.4.2.el7.ppc64Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the grubby tool to remove the
rhgbboot option from the default kernel, identified in the last step, in your GRUB2 configuration. For example:grubby --remove-args="rhgb" --update-kernel /boot/vmlinuz-3.10.0-229.4.2.el7.ppc64
# grubby --remove-args="rhgb" --update-kernel /boot/vmlinuz-3.10.0-229.4.2.el7.ppc64Copy to Clipboard Copied! Toggle word wrap Toggle overflow
--remove-args="rhgb" parameter with the --args="rhgb" paramter. This will restore the rhgb boot option to the default kernel in your GRUB2 configuration.
14.3.2. Booting into a Graphical Environment
startx command. Note, however, that this is just a one-time fix and does not change the log in process for future log ins.
graphical.target. When you are finished, reboot the computer. You will presented with a graphical login prompt after the system restarts.
Procedure 14.5. Setting Graphical Login as Default
- Open a shell prompt. If you are in your user account, become root by typing the
su -command. - Change the default target to
graphical.target. To do this, execute the following command:systemctl set-default graphical.target
# systemctl set-default graphical.targetCopy to Clipboard Copied! Toggle word wrap Toggle overflow
root:
systemctl set-default multi-user.target
# systemctl set-default multi-user.target14.3.3. No Graphical User Interface Present
14.3.4. X Server Crashing After User Logs In
df -h
$ df -h/home partition. The following is a sample output of the df command:
/home partition is full, which causes the crash. You can make some room on the partition by removing unneeded files. After you free up some disk space, start X using the startx command.
df and an explanation of the options available (such as the -h option used in this example), see the df(1) man page.
14.3.5. Is Your System Displaying Signal 11 Errors?
rd.live.check boot option at the boot menu. See Section 23.2.2, “Verifying Boot Media” for details.
14.3.6. Unable to IPL from Network Storage Space (*NWSSTG)
PReP partition. In this case, you must reinstall the system and make sure to create this partition during the partitioning phase or in the Kickstart file.
14.3.7. The GRUB2 next_entry variable can behave unexpectedly in a virtualized environment
next_entry grub environment variable after a system reboot. The SLOF firmware does not support block writes at boot time by design thus the bootloader is unable to clear this variable at boot time.
Part III. IBM Z Architecture - Installation and Booting
Chapter 15. Planning for Installation on IBM Z
15.1. Pre-installation
- Decide whether you want to run the operating system on an LPAR or as a z/VM guest operating system.
- Decide if you need swap space and if so, how much. Although it is possible (and recommended) to assign enough memory to a z/VM guest virtual machine and let z/VM do the necessary swapping, there are cases where the amount of required RAM is hard to predict. Such instances should be examined on a case-by-case basis. See Section 18.15.3.4, “Recommended Partitioning Scheme”.
- Decide on a network configuration. Red Hat Enterprise Linux 7 for IBM Z supports the following network devices:
- Real and virtual Open Systems Adapter (OSA)
- Real and virtual HiperSockets
- LAN channel station (LCS) for real OSA
- Disk space. Calculate how much disk space you need and allocate sufficient disk space on DASDs[2] or SCSI[3] disks. You require at least 10 GB for a server installation, and 20 GB if you want to install all packages. You also require disk space for any application data. After the installation, you can add or delete more DASD or SCSI disk partitions.The disk space used by the newly installed Red Hat Enterprise Linux system (the Linux instance) must be separate from the disk space used by other operating systems you have installed on your system.For more information about disks and partition configuration, see Section 18.15.3.4, “Recommended Partitioning Scheme”.
- RAM. Acquire 1 GB (recommended) for the Linux instance. With some tuning, an instance might run with as little as 512 MB RAM.
Note
FBAPART option must be used.
15.2. Overview of the IBM Z Installation Procedure
Booting the Installation
Connect with the mainframe, then perform an initial program load (IPL), or boot, from the medium containing the installation program. See Chapter 16, Booting the Installation on IBM Z for details.Connecting to the installation system
From a local machine, connect to the remote IBM Z system to continue with the installation process. See Chapter 17, Connecting to the installation system for details.Anaconda
Use the Anaconda installation program to configure network, specify language support, installation source, software packages to be installed, and to perform the rest of the installation. See Chapter 18, Installing Using Anaconda for more information.
15.2.1. Booting the Installation
kernel.img) and initial RAM disk (initrd.img) with at least the parameters in the generic.prm file. Additionally, a generic.ins file is loaded which determines file names and memory addresses for the initrd, kernel and generic.prm.
- z/VM reader - see Section 16.3.1, “Using the z/VM Reader” for details.
- SE or HMC through a remote FTP server - see Section 16.4.1, “Using an FTP Server” for details.
- SE or HMC DVD - see Section 16.4.4, “Using an FCP-attached SCSI DVD Drive” for details.
- DASD - see Section 16.3.2, “Using a Prepared DASD” for z/VM or Section 16.4.2, “Using a Prepared DASD” for LPAR.
- SCSI device that is attached through an FCP channel - see Section 16.3.3, “Using a Prepared FCP-attached SCSI Disk” for z/VM or Section 16.4.3, “Using a Prepared FCP-attached SCSI Disk” for LPAR.
- FCP-attached SCSI DVD - see Section 16.3.4, “Using an FCP-attached SCSI DVD Drive” for z/VM or Section 16.4.4, “Using an FCP-attached SCSI DVD Drive” for LPAR
zipl boot loader.
15.2.2. Connecting to the installation system
15.2.3. Installation using Anaconda
- Graphical Mode
- Graphical installation is done through a VNC client. You can use your mouse and keyboard to navigate through the screens, click buttons, and type into text fields. For more information on performing a graphical installation using VNC, see Chapter 25, Using VNC.
- Text-based Mode
- This interface does not offer all interface elements of the GUI and does not support all settings. Use this for interactive installations if you cannot use a VNC client. For more information about text-based installations, see Section 18.4, “Installing in Text Mode”.
- Command-line Mode
- This is intended for automated and non-interactive installations on IBM Z. Note that if the installation program encounters an invalid or missing kickstart command, the system will reboot. For more information about automated installation, see Chapter 27, Kickstart Installations.
dasda can have partitions dasda1, dasda2, and dasda3.
zfcp device driver) and a switch, SCSI LUNs can be presented to Linux on IBM Z as if they were locally attached SCSI drives.
Chapter 16. Booting the Installation on IBM Z
16.1. Customizing boot parameters
generic.prm file. When installing on an LPAR, the rd.cmdline parameter is set to ask by default, meaning that you will be given a prompt on which you can enter these boot parameters. In both cases, the required parameters are the same.
Note
- Installation source
- An installation source must always be configured. Use the
inst.repo=option to specify the package source for the installation. See Specifying the Installation Source for details and syntax. - Network devices
- Network configuration must be provided if network access will be required during the installation. If you plan to perform an unattended (Kickstart-based) installation using only local media such as a hard drive, network configuration can be omitted.Use the
ip=option for basic network configuration, and other options listed in Network Boot Options as required.Also use therd.znet=kernel option, which takes a network protocol type, a comma delimited list of sub-channels, and, optionally, comma delimitedsysfsparameter and value pairs. This parameter can be specified multiple times to activate multiple network devices.For example:rd.znet=qeth,0.0.0600,0.0.0601,0.0.0602,layer2=1,portname=foo
rd.znet=qeth,0.0.0600,0.0.0601,0.0.0602,layer2=1,portname=fooCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Storage devices
- At least one storage device must always be configured.The
rd.dasd=option takes a Direct Access Storage Device (DASD) adapter device bus identifier. For multiple DASDs, specify the parameter multiple times, or use a comma separated list of bus IDs. To specify a range of DASDs, specify the first and the last bus ID. Example:rd.dasd=0.0.0200 rd.dasd=0.0.0202(ro),0.0.0203(ro:failfast),0.0.0205-0.0.0207
rd.dasd=0.0.0200 rd.dasd=0.0.0202(ro),0.0.0203(ro:failfast),0.0.0205-0.0.0207Copy to Clipboard Copied! Toggle word wrap Toggle overflow Therd.zfcp=option takes a SCSI over FCP (zFCP) adapter device bus identifier, a world wide port name (WWPN), and a FCP LUN, then activates the device. This parameter can be specified multiple times to activate multiple zFCP devices. Example:rd.zfcp=0.0.4000,0x5005076300C213e9,0x5022000000000000
rd.zfcp=0.0.4000,0x5005076300C213e9,0x5022000000000000Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Kickstart options
- If you are using a Kickstart file to perform an automatic installation, you must always specify the location of the Kickstart file using the
inst.ks=option. For an unattended, fully automatic Kickstart installation, theinst.cmdlineoption is also useful. See Section 21.4, “Parameters for Kickstart Installations” for additional information.
generic.prm file containing all mandatory parameters look similar to the following example:
Example 16.1. Customized generic.prm file
generic.ins, and contains file names for the initial RAM disk, kernel image, and parameter file (generic.prm) and a memory location for each file. An example generic.ins will look similar to the following example:
Example 16.2. Sample generic.ins file
images/kernel.img 0x00000000 images/initrd.img 0x02000000 images/genericdvd.prm 0x00010480 images/initrd.addrsize 0x00010408
images/kernel.img 0x00000000
images/initrd.img 0x02000000
images/genericdvd.prm 0x00010480
images/initrd.addrsize 0x00010408generic.ins file is provided by Red Hat along with all other files required to boot the installer. Modify this file only if you want to, for example, load a different kernel version than default.
16.2. Considerations for Hard Drive Installation on IBM Z
zipl -V -t /mnt/ -i /mnt/images/kernel.img -r /mnt/images/initrd.img -p /mnt/images/generic.prm
# zipl -V -t /mnt/ -i /mnt/images/kernel.img -r /mnt/images/initrd.img -p /mnt/images/generic.prmgeneric.prm configuration file.
16.3. Installing under z/VM
- the z/VM virtual reader
- a DASD or an FCP-attached SCSI device prepared with the zipl boot loader
- an FCP-attached SCSI DVD drive
Note
logon user here
logon user herecp ipl cms
cp ipl cmsquery disk
query disk- Query the available main memory, which is called storage in IBM Z terminology. Your guest should have at least 1 GB of main memory.
cp query virtual storage
cp query virtual storageCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Query available network devices by type:
osa- OSA - CHPID type OSD, real or virtual (VSWITCH or GuestLAN), both in QDIO mode
hsi- HiperSockets - CHPID type IQD, real or virtual (GuestLAN type Hipers)
lcs- LCS - CHPID type OSE
For example, to query all of the network device types mentioned above, run:cp query virtual osa
cp query virtual osaCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Query available DASDs. Only those that are flagged
RWfor read-write mode can be used as installation targets:cp query virtual dasd
cp query virtual dasdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Query available FCP channels:
cp query virtual fcp
cp query virtual fcpCopy to Clipboard Copied! Toggle word wrap Toggle overflow
16.3.1. Using the z/VM Reader
- If necessary, add the device containing the z/VM TCP/IP tools to your CMS disk list. For example:
cp link tcpmaint 592 592 acc 592 fm
cp link tcpmaint 592 592 acc 592 fmCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace fm with anyFILEMODEletter. - Execute the command:
ftp host
ftp hostCopy to Clipboard Copied! Toggle word wrap Toggle overflow Where host is the host name or IP address of the FTP server that hosts the boot images (kernel.imgandinitrd.img). - Log in and execute the following commands. Use the
(reploption if you are overwriting existingkernel.img,initrd.img,generic.prm, orredhat.execfiles:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, check whether the files were transferred correctly by using the CMS command
filelistto show the received files and their format. It is important thatkernel.imgandinitrd.imghave a fixed record length format denoted byFin the Format column and a record length of 80 in theLreclcolumn. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Press PF3 to quitfilelistand return to the CMS prompt. - Customize boot parameters in
generic.prmas necessary. See Section 16.1, “Customizing boot parameters” for details.Another way to configure storage and network devices is by using a CMS configuration file. In such a case, add theCMSDASD=andCMSCONFFILE=parameters togeneric.prm. See Section 21.2, “The z/VM Configuration File” for more details. - Finally, execute the REXX script
redhat.execto boot the installation program:redhat
redhatCopy to Clipboard Copied! Toggle word wrap Toggle overflow
16.3.2. Using a Prepared DASD
cp ipl DASD_device_number loadparm boot_entry_number
cp ipl DASD_device_number loadparm boot_entry_numbercp ipl eb1c loadparm 0
cp ipl eb1c loadparm 016.3.3. Using a Prepared FCP-attached SCSI Disk
- Configure the SCSI boot loader of z/VM to access the prepared SCSI disk in the FCP Storage Area Network. Select the prepared zipl boot menu entry referring to the Red Hat Enterprise Linux installation program. Use a command of the following form:
cp set loaddev portname WWPN lun LUN bootprog boot_entry_number
cp set loaddev portname WWPN lun LUN bootprog boot_entry_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace WWPN with the World Wide Port Name of the storage system and LUN with the Logical Unit Number of the disk. The 16-digit hexadecimal numbers must be split into two pairs of eight digits each. For example:cp set loaddev portname 50050763 050b073d lun 40204011 00000000 bootprog 0
cp set loaddev portname 50050763 050b073d lun 40204011 00000000 bootprog 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, confirm your settings with the command:
query loaddev
query loaddevCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Boot the FCP device connected with the storage system containing the disk with the following command:
cp ipl FCP_device
cp ipl FCP_deviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:cp ipl fc00
cp ipl fc00Copy to Clipboard Copied! Toggle word wrap Toggle overflow
16.3.4. Using an FCP-attached SCSI DVD Drive
- Insert your Red Hat Enterprise Linux for IBM Z DVD into the DVD drive.
- Configure the SCSI boot loader of z/VM to access the DVD drive in the FCP Storage Area Network and specify
1for the boot entry on the Red Hat Enterprise Linux for IBM Z DVD. Use a command of the following form:cp set loaddev portname WWPN lun FCP_LUN bootprog 1
cp set loaddev portname WWPN lun FCP_LUN bootprog 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace WWPN with the WWPN of the FCP-to-SCSI bridge and FCP_LUN with the LUN of the DVD drive. The 16-digit hexadecimal numbers must be split into two pairs of eight characters each. For example:cp set loaddev portname 20010060 eb1c0103 lun 00010000 00000000 bootprog 1
cp set loaddev portname 20010060 eb1c0103 lun 00010000 00000000 bootprog 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, confirm your settings with the command:
cp query loaddev
cp query loaddevCopy to Clipboard Copied! Toggle word wrap Toggle overflow - IPL on the FCP device connected with the FCP-to-SCSI bridge.
cp ipl FCP_device
cp ipl FCP_deviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:cp ipl fc00
cp ipl fc00Copy to Clipboard Copied! Toggle word wrap Toggle overflow
16.4. Installing in an LPAR
- an FTP server
- a DASD or an FCP-attached SCSI drive prepared with the zipl boot loader
- an FCP-attached SCSI DVD drive
- Log in on the IBM Z Hardware Management Console (HMC) or the Support Element (SE) as a user with sufficient privileges to install a new operating system to an LPAR. The
SYSPROGuser is recommended. - Select Images, then select the LPAR to which you want to install. Use the arrows in the frame on the right side to navigate to the menu.
- Double-click Operating System Messages to show the text console on which Linux boot messages will appear.
Note
16.4.1. Using an FTP Server
- Double-click Load from CD-ROM, DVD, or Server.
- In the dialog box that follows, select FTP Source, and enter the following information:
- Host Computer - Host name or IP address of the FTP server you want to install from, for example
ftp.redhat.com - User ID - Your user name on the FTP server. Or, specify
anonymous. - Password - Your password. Use your email address if you are logging in as
anonymous. - Account (optional) - Leave this field empty.
- File location (optional) - Directory on the FTP server holding the Red Hat Enterprise Linux for IBM Z, for example
/rhel/s390x/.
- Click Continue.
- In the dialog that follows, keep the default selection of
generic.insand click Continue.
16.4.2. Using a Prepared DASD
- Double-click Load.
- In the dialog box that follows, select
Normalas the Load type. - As Load address, fill in the device number of the DASD.
- As Load parameter, fill in the number corresponding the zipl boot menu entry that you prepared for booting the Red Hat Enterprise Linux installation program.
- Click the button.
16.4.3. Using a Prepared FCP-attached SCSI Disk
- Double-click Load.
- In the dialog box that follows, select
SCSIas the Load type. - As Load address, fill in the device number of the FCP channel connected with the SCSI disk.
- As World wide port name, fill in the WWPN of the storage system containing the disk as a 16-digit hexadecimal number.
- As Logical unit number, fill in the LUN of the disk as a 16-digit hexadecimal number.
- As Boot program selector, fill in the number corresponding the zipl boot menu entry that you prepared for booting the Red Hat Enterprise Linux installation program.
- Leave the Boot record logical block address as
0and the Operating system specific load parameters empty. - Click the button.
16.4.4. Using an FCP-attached SCSI DVD Drive
- Insert your Red Hat Enterprise Linux for IBM Z DVD into the DVD drive.
- Double-click Load.
- In the dialog box that follows, select
SCSIas the Load type. - As Load address, fill in the device number of the FCP channel connected with the FCP-to-SCSI bridge.
- As World wide port name, fill in the WWPN of the FCP-to-SCSI bridge as a 16-digit hexadecimal number.
- As Logical unit number, fill in the LUN of the DVD drive as a 16-digit hexadecimal number.
- As Boot program selector, fill in the number
1to select the boot entry on the Red Hat Enterprise Linux for IBM Z DVD. - Leave the Boot record logical block address as
0and the Operating system specific load parameters empty. - Click the button.
Chapter 17. Connecting to the installation system
17.1. Setting up remote connection using VNC
- The initial program boot is complete on the IBM Z system, and the command prompt displays:
Starting installer, one moment... Please ssh install@my-z-system (system ip address) to begin the install.Starting installer, one moment... Please ssh install@my-z-system (system ip address) to begin the install.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If you want to restrict VNC access to the installation system, then ensure
inst.vncpassword=PASSWORDboot parameter is configured.
- On the command prompt, run the following command:
$ssh install@my-z-system-domain-name
$ssh install@my-z-system-domain-nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow OR$ssh install@my-z-system-IP-address
$ssh install@my-z-system-IP-addressCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Depending on whether or not have you configured the
inst.vncparameter, the ssh session displays the following output:Wheninst.vncparameter is configured:Starting installer, one moment... Please manually connect your vnc client to my-z-system:1 (system-ip-address:1) to begin the install.
Starting installer, one moment... Please manually connect your vnc client to my-z-system:1 (system-ip-address:1) to begin the install.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Wheninst.vncparameter is not configured:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you have configured theinst.vncparameter, proceed to step 5. - Enter 1 to start VNC.
- Enter a password, if you have not set the
inst.vncpassword=boot option, but want to secure the server connection. - From a new command prompt, connect to the VNC server.
$vncviewer my-z-system-ip-address:display_number
$vncviewer my-z-system-ip-address:display_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you have secured the connection, use the password that you have entered in the previous step or the one that you had set forinst.vncpassword=boot option.The RHEL installer is launched in the VNC client.
Chapter 18. Installing Using Anaconda
18.1. Introduction to Anaconda
18.2. Consoles and Logging During the Installation
18.2.1. Accessing Consoles
root privileges, unless this prompt was specifically disabled using a boot option or a Kickstart command.
Note
Note
| Shortcut | Contents |
|---|---|
| Ctrl+b 1 | Main installation program window. Contains text-based prompts (during text mode installation or if you use VNC Direct Mode), and also some debugging information. |
| Ctrl+b 2 | Interactive shell prompt with root privileges. |
| Ctrl+b 3 | Installation log; displays messages stored in /tmp/anaconda.log. |
| Ctrl+b 4 | Storage log; displays messages related storage devices from kernel and system services, stored in /tmp/storage.log. |
| Ctrl+b 5 | Program log; displays messages from other system utilities, stored in /tmp/program.log. |
18.2.2. Saving Screenshots
/tmp/anaconda-screenshots/.
autostep --autoscreenshot command in a Kickstart file to capture and save each step of the installation automatically. See Section 27.3.1, “Kickstart Commands and Options” for details.
18.3. Installation in Non-Interactive Line Mode
inst.cmdline option was specified as a boot option in your parameter file (see Section 21.4, “Parameters for Kickstart Installations”) or the cmdline option was specified in your Kickstart file (see Chapter 27, Kickstart Installations), Anaconda starts with non-interactive text line mode. In this mode, all necessary information must be provided in the Kickstart file. The installation program will not allow user interaction and it will stop if any required commands are missing.
18.4. Installing in Text Mode

Figure 18.1. Text Mode Installation
[x], and screens which require your attention before the installation can begin are marked with [!]. Available commands are displayed below the list of available options.
Note
Processing... label. To refresh to the current status of text menu items, use the r option at the text mode prompt.
- The installer will always use the English language and the US English keyboard layout. You can configure your language and keyboard settings, but these settings will only apply to the installed system, not to the installation.
- You cannot configure any advanced storage methods (LVM, software RAID, FCoE, zFCP and iSCSI).
- It is not possible to configure custom partitioning; you must use one of the automatic partitioning settings. You also cannot configure where the boot loader will be installed.
- You cannot select any package add-ons to be installed; they must be added after the installation finishes using the Yum package manager.
inst.text boot option used in the parameter file (generic.prm). See Chapter 21, Parameter and Configuration Files on IBM Z for information about the parameter file.
18.5. Installing in the Graphical User Interface

Figure 18.2. The Installation Summary Screen
| Shortcut keys | Usage |
|---|---|
| Tab and Shift+Tab | Cycle through active control elements (buttons, check boxes, and so on.) on the current screen |
| Up and Down | Scroll through lists |
| Left and Right | Scroll through horizontal toolbars and table entries |
| Space and Enter | Select or remove a highlighted item from selection and expand and collapse drop-down menus |
18.6. Welcome Screen and Language Selection
Note
GeoIP module.

Figure 18.3. Language Configuration
18.7. The Installation Summary Screen

Figure 18.4. The Installation Summary Screen
Note
18.8. Date & Time
- Using your mouse, click on the interactive map to select a specific city. A red pin appears indicating your selection.
- You can also scroll through the Region and City drop-down menus at the top of the screen to select your time zone.
- Select Etc at the bottom of the Region drop-down menu, then select your time zone in the next menu adjusted to GMT/UTC, for example
GMT+1.
timezone command in timezone (required) for details.
Note
Note
18.9. Language Support
Español. Then you can select a locale specific to your region in the right panel, for example Español (Costa Rica). You can select multiple languages and multiple locales. The selected languages are highlighted in bold in the left panel.

Figure 18.5. Configuring Language Support
Note
18.10. Keyboard Configuration

Figure 18.6. Keyboard Configuration
Important
Note
18.11. Security Policy
Important
/root/openscap_data directory on the installed system.

Figure 18.7. Security policy selection screen
Note
HTTP, HTTPS or FTP server. Use the full address of the content, including the protocol (such as http://). A network connection must be active (enabled in Section 18.13, “Network & Hostname”) before you can load a custom profile. The content type will be detected automatically by the installer.
18.12. Installation Source

Figure 18.8. Installation Source Screen
- ISO file
- This option will appear if the installation program detected a partitioned hard drive with mountable file systems. Select this option, click the button, and browse to the installation ISO file's location on your system. Then click to ensure that the file is suitable for installation.
- On the network
- To specify a network location, select this option and choose from the following options in the drop-down menu:
- http://
- https://
- ftp://
- nfs
Using your selection as the start of the location URL, type the rest into the address box. If you choose NFS, another box will appear for you to specify any NFS mount options.Important
When selecting an NFS-based installation source, you must specify the address with a colon (:) character separating the host name from the path. For example:server.example.com:/path/to/directory
server.example.com:/path/to/directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow To configure a proxy for an HTTP or HTTPS source, click the button. Check Enable HTTP proxy and type the URL into the Proxy URL box. If your proxy requires authentication, check Use Authentication and enter a user name and password. Click .If your HTTP or HTTP URL refers to a repository mirror list, mark the check box under the input field.
18.13. Network & Hostname
Note
em1 or wl3sp0. For information about these standards, see the Red Hat Enterprise Linux 7 Networking Guide.

Figure 18.9. Network & Hostname Configuration Screen
localhost.localdomain means that no specific static host name for target system is configured, and the actual host name of installed system will be configured during process of network configuration (for example, by NetworkManager using DHCP or DNS).
Important
18.13.1. Edit Network Connections
enccwdevice_id, for example enccw0.0.0a00. Note that on IBM Z, you cannot add a new connection because the network subchannels need to be grouped and set online beforehand, and this is currently only done in the booting phase. See Chapter 16, Booting the Installation on IBM Z for details.
- Mark the Automatically connect to this network when it is available check box if you want to use the connection every time the system boots. You can use more than one connection that will connect automatically. This setting will carry over to the installed system.

Figure 18.10. Network Auto-Connection Feature
- By default, IPv4 parameters are configured automatically by the DHCP service on the network. At the same time, the IPv6 configuration is set to the
Automaticmethod. This combination is suitable for most installation scenarios and usually does not require any changes.
Figure 18.11. IP Protocol Settings
18.13.2. Advanced Network Interfaces
Bond- represents NIC (Network Interface Controller) Bonding, a method to bind multiple network interfaces together into a single, bonded, channel.Bridge- represents NIC Bridging, a method to connect multiple separate network into one aggregate network.Team- represents NIC Teaming, a new implementation to aggregate links, designed to provide a small kernel driver to implement the fast handling of packet flows, and various applications to do everything else in user space.VLAN- represents a method to create multiple distinct broadcast domains, which are mutually isolated.

Figure 18.12. Advanced Network Interface Dialog
Note
18.14. Software Selection
- Add-ons listed above the horizontal line are specific to the environment you selected. If you select any add-ons in this part of the list and then select a different environment, your selection will be lost.
- Add-ons listed below the horizontal line are available for all environments. Selecting a different environment will not impact the selections made in this part of the list.

Figure 18.13. Example of a Software Selection for a Server Installation
server variant provides environments designed for servers, while the workstation variant has several choices for deployment as a developer workstation, and so on.
repodata/*-comps-variant.architecture.xml file on the Red Hat Enterprise Linux Installation DVD which you are using as the installation source. This file contains a structure describing available environments (marked by the <environment> tag) and add-ons (the <group> tag).
Important
%packages section of the Kickstart file. See Section 27.3.2, “Package Selection” for instructions on selecting packages to install in a Kickstart file, and Chapter 27, Kickstart Installations for general information about automating the installation with Kickstart.
18.14.1. Core Network Services
- centralized logging through the
rsyslogservice - email through SMTP (Simple Mail Transfer Protocol)
- network file sharing through NFS (Network File System)
- remote access through SSH (Secure SHell)
- resource advertising through mDNS (multicast DNS)
18.15. Installation Destination
Warning
Important
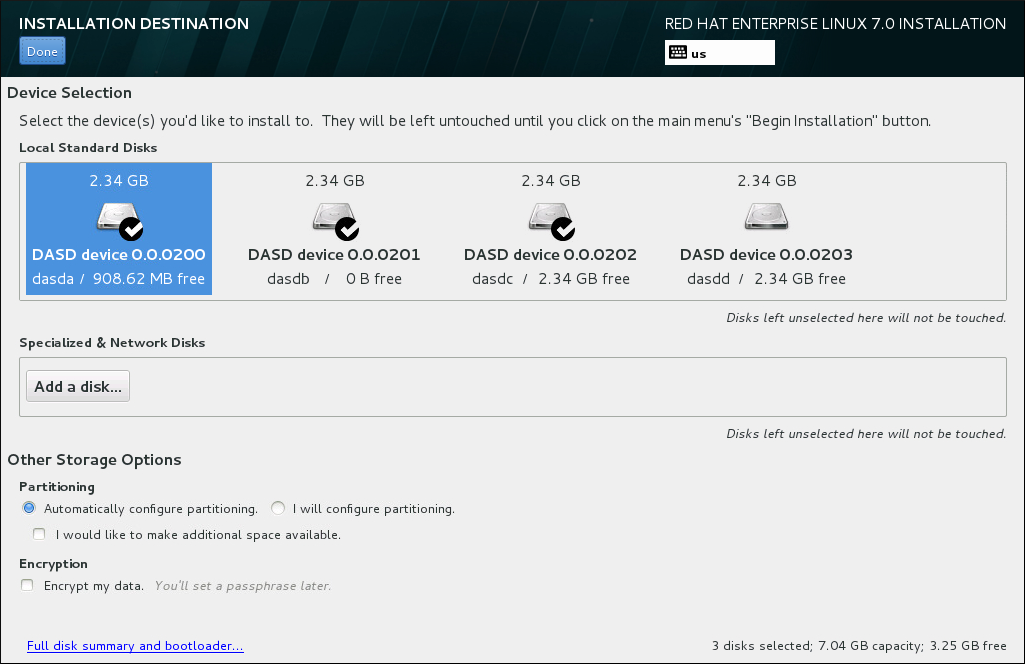
Figure 18.14. Storage Space Overview
Warning
/etc/dasd.conf configuration file as described in Section 20.1.3, “Persistently Setting DASDs Online”.
- In the Partitioning section, you can select how storage devices are partitioned and how volumes are created. You can configure the partitions, manually or allow the installation program to do it automatically.Automatic partitioning is recommended if you are doing a clean installation on previously unused storage or do not need to keep any data that might be present on the storage. To proceed this way, leave the default selection of the Automatically configure partitioning radio button, and the installation program will create the necessary partitions and volumes on the storage space for you.For automatic partitioning, you can also select the I would like to make additional space available check box to choose how to reassign space from other file systems to this installation. After you click , there are two dialogs that can appear. If you selected automatic partitioning but there is not enough storage space to complete the installation using the recommended partitioning configuration, a dialog will appear:

Figure 18.15. Installation Options Dialog with Option to Reclaim Space
You can click to the Red Hat Enterprise Linux software selection link. The link will navigate you to the Software selection section, where you can change what software you want to install, and free some aditional storage space.Alternatively, you can click to return to the Installation Destination screen, where it is possible to add more storage devices, or to choose to configure partitioning manually. Click to free some storage space from existing file systems. See Section 18.15.2, “Reclaim Disk Space” for details.The second dialog appears if you cannot create enough free space. In this case, you have to add more disks on the initial storage screen or quit the installation.If you select the I will configure partitioning radio button for manual setup, you will be brought to the Manual Partitioning screen after clicking . See Section 18.15.3, “Manual Partitioning” for details. - In the Encryption section, you can select the Encrypt my data check box to encrypt all partitions except for the
/bootpartition. See the Red Hat Enterprise Linux 7 Security Guide for information on encryption.
Important
18.15.1. Encrypt Partitions

Figure 18.16. Enter Passphrase for an Encrypted Partition
Warning
18.15.2. Reclaim Disk Space
Warning
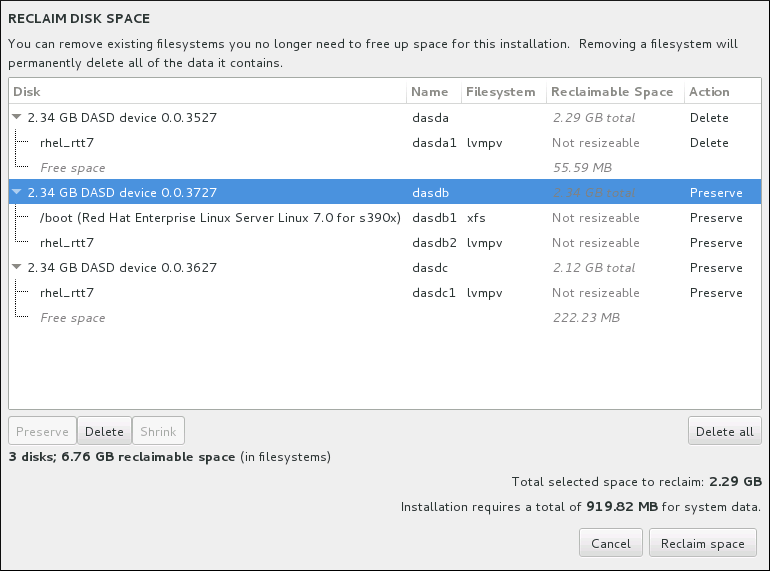
Figure 18.17. Reclaim Disk Space from Existing File Systems
- - leaves the file system untouched and no data will be deleted. This is the default action.
- - removes the file system entirely. All the space it takes up on the disk will be made available for the installation.
- - recovers free space from the file system and makes it available for this installation. Use the slider to set a new size for the selected partition. Can only be used on resizable partitions where LVM or RAID is not used.
- - this button, located on the right, marks all file systems for deletion by default. Upon clicking, it changes the label and allows you to mark all file systems to be preserved again.
18.15.3. Manual Partitioning
Warning

Figure 18.18. The Manual Partitioning Screen
Note
/boot. The kernel files and boot loader sector will be associated with this device. The first DASD or SCSI LUN will be used, and the device number will be used when re-IPLing the post-installed system.
18.15.3.1. Adding File Systems and Configuring Partitions
/, /home, /boot, and swap. You can also create additional partitions and volumes as you require. See Section 18.15.3.4, “Recommended Partitioning Scheme” for further details.
Note
/boot partition, a / (root) volume, and a swap volume proportionate to the size of the available storage. These are the recommended file systems for a typical installation, but you can add additional file systems and mount points if you need to.
/ for the root partition or /boot for the boot partition. Then enter the size of the file system in the Desired Capacity text field; for example, 2GiB. If you leave the field empty or if you specify a size bigger than available space, all remaining free space is used instead. After entering these details, click the button to create the partition.
Note
/boot, and then create the rest of the partitions, letting the installation program allocate the remaining capacity to them.
Standard Partition, BTRFS, LVM, and LVM Thin Provisioning. Note that the /boot partition will always be located on a standard partition, regardless of the value selected in this menu.
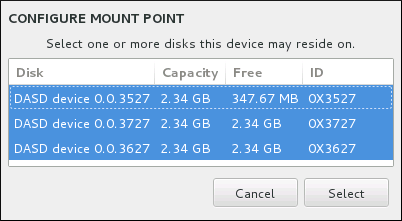
Figure 18.19. Configuring Mount Points

Figure 18.20. Rescanning Disks

Figure 18.21. Customizing Partitions
- Mount Point - enter the file system's mount point. For example, if a file system should be the root file system, enter
/; enter/bootfor the/bootfile system, and so on. For a swap file system, the mount point should not be set - setting the file system type toswapis sufficient. - Desired Capacity - enter the desired size of the file system. You can use common size units such as KiB or GiB. The default is MiB if no other unit is specified.
- Device type - choose one of these types: Standard Partition, LVM, RAID, LVM Thin Provisioning, or BTRFS. Check the adjacent Encrypt box to encrypt the partition or volume. You will be prompted to set a password later. RAID is only available if two or more disks are selected for partitioning, and if you choose this type, you can also set the RAID Level. Similarly, if you select LVM, you can specify the Volume Group.
- File system - in the drop-down menu, select the appropriate file system type for this partition or volume. Check the adjacent Reformat box to format an existing partition, or leave it unchecked to retain your data. Note that newly created partitions and volumes must be reformatted, and the check box cannot be unchecked in this case.
- Label - assign a label to the partition. Labels are used for you to easily recognize and address individual partitions.
- Name - assign a name to an LVM or Btrfs volume. Note that standard partitions are named automatically when they are created and their name cannot be edited, such as
/homebeing assigned the namesda1.
Important
/usr or /var is partitioned separately from the rest of the root volume, the boot process becomes much more complex because these directories contain components critical to it. In some situations, such as when these directories are placed on an iSCSI drive or an FCoE location, the system can either be unable to boot, or hang with a Device is busy error when powering off or rebooting.
/usr or /var, not to directories below them. For example, a separate partition for /var/www will work without issues.
18.15.3.1.1. File System Types
Device Types
- standard partition - A standard partition can contain a file system or swap space, or it can provide a container for software RAID or an LVM physical volume.
- logical volume (LVM) - Creating an LVM partition automatically generates an LVM logical volume. LVM can improve performance when using physical disks. For information on how to create a logical volume, see Section 18.15.3.3, “Create LVM Logical Volume”. For more information regarding LVM, see the Red Hat Enterprise Linux 7 Logical Volume Manager Administration guide.
- LVM thin provisioning - Using thin provisioning, you can manage a storage pool of free space, known as a thin pool, which can be allocated to an arbitrary number of devices when needed by applications. The thin pool can be expanded dynamically when needed for cost-effective allocation of storage space. For more information regarding LVM, see the Red Hat Enterprise Linux 7 Logical Volume Manager Administration guide.
Note
The installer will automatically reserve 20% of any requested space for an LVM thin pool logical volume in the volume group containing it. This is a safety measure to ensure that you can extend either the metadata volume or the data volume of your thinly provisioned logical volume. - software RAID - Creating two or more software RAID partitions allows you to create a RAID device. One RAID partition is assigned to each disk on the system. To create a RAID device, see Section 18.15.3.2, “Create Software RAID”. For more information regarding RAID, see the Red Hat Enterprise Linux 7 Storage Administration Guide.
File Systems
- xfs - XFS is a highly scalable, high-performance file system that supports file systems up to 16 EiB (approximately 16 billion GiB), files up to 8 EiB (approximately 8 billion GiB), and directory structures containing tens of millions of entries. XFS supports metadata journaling, which facilitates quicker crash recovery. The XFS file system can also be defragmented and resized while mounted and active. This file system is selected by default and is highly recommended. For information on how to translate common commands from previously used ext4 file system to XFS, see Appendix F, Reference Table for ext4 and XFS Commands.The maximum supported size of an XFS file system in Red Hat Enterprise Linux is currently 500 TiB.
- ext4 - The ext4 file system is based on the ext3 file system and features a number of improvements. These include support for larger file systems and larger files, faster and more efficient allocation of disk space, no limit on the number of subdirectories within a directory, faster file system checking, and more robust journaling.The maximum supported size of an ext4 file system in Red Hat Enterprise Linux is currently 50 TiB.
- ext3 - The ext3 file system is based on the ext2 file system and has one main advantage - journaling. Using a journaling file system reduces time spent recovering a file system after a crash as there is no need to check the file system for metadata consistency by running the
fsckutility every time a crash occurs. - ext2 - An ext2 file system supports standard Unix file types, including regular files, directories, or symbolic links. It provides the ability to assign long file names, up to 255 characters.
- vfat - The VFAT file system is a Linux file system that is compatible with Microsoft Windows long file names on the FAT file system.
- swap - Swap partitions are used to support virtual memory. In other words, data is written to a swap partition when there is not enough RAM to store the data your system is processing.
18.15.3.2. Create Software RAID
Note

Figure 18.22. Creating a Software RAID Partition - the Device Type Menu Expanded
- Create a mount point as described in Section 18.15.3.1, “Adding File Systems and Configuring Partitions”. By configuring this mount point, you configure the RAID device.
- Keeping the partition selected in the left pane, select the configuration button below the pane to open the Configure Mount Point dialog. Select which disks will be included in the RAID device and click .
- Click the Device Type drop-down menu and select RAID.
- Click the File System drop-down menu and select your preferred file system type (see Section 8.14.4.1.1, “File System Types”.
- Click the RAID Level drop-down menu and select your preferred level of RAID.The available RAID levels are:
- RAID0 - Optimized performance (stripe)
- Distributes data across multiple disks. Level 0 RAIDs offer increased performance over standard partitions, and can be used to pool the storage of multiple disks into one large virtual device. Note that Level 0 RAIDs offer no redundancy, and that the failure of one device in the array destroys data in the entire array. RAID 0 requires at least two RAID partitions.
- RAID1 - Redundancy (mirror)
- Mirrors all data on one disk onto one or more other disks. Additional devices in the array provide increasing levels of redundancy. RAID 1 requires at least two RAID partitions.
- RAID4 - Error detection (parity)
- Distributes data across multiple disks, and uses one disk in the array to store parity information that safeguards the array in case any disk within the array fails. Because all parity information is stored on one disk, access to this disk creates a bottleneck in the performance of the array. RAID 4 requires at least three RAID partitions.
- RAID5 - Distributed error detection
- Distributes data and parity information across multiple disks. Level 5 RAIDs therefore offer the performance advantages of distributing data across multiple disks, but do not share the performance bottleneck of level 4 RAIDs because the parity information is also distributed through the array. RAID 5 requires at least three RAID partitions.
- RAID6 - Redundant
- Level 6 RAIDs are similar to level 5 RAIDs, but instead of storing only one set of parity data, they store two sets. RAID 6 requires at least four RAID partitions.
- RAID10 - Redundancy (mirror) and Optimized performance (stripe)
- Level 10 RAIDs are nested RAIDs or hybrid RAIDs. They are constructed by distributing data over mirrored sets of disks. For example, a level 10 RAID array constructed from four RAID partitions consists of two mirrored pairs of striped partitions. RAID 10 requires at least four RAID partitions.
- Click to save your changes, and either continue with another partition or click to return to the Installation Summary screen.
18.15.3.3. Create LVM Logical Volume
Important
lvm command. To return to the text-mode installation, press Ctrl+Alt+F1.

Figure 18.23. Configuring a Logical Volume
- Create a mount point for the LVM volume as described in Section 18.15.3.1, “Adding File Systems and Configuring Partitions”.
- Click the Device Type drop-down menu and select LVM. The Volume Group drop-down menu appears and displays the newly-created volume group name.
- Optionally, either click the menu and select Create a new volume group or click to configure the newly-created volume group, if you need to. Both the Create a new volume group option and the button lead to the Configure Volume Group dialog, where you can rename the logical volume group and select which disks will be included.
Note
The configuration dialog does not allow you to specify the size of the volume group's physical extents. The size will always be set to the default value of 4 MiB. If you want to create a volume group with different physical extents, create it manually by switching to an interactive shell and using thevgcreatecommand, or use a Kickstart file with thevolgroup --pesize=sizecommand.
Figure 18.24. Customizing an LVM Volume Group
The available RAID levels are the same as with actual RAID devices. See Section 18.15.3.2, “Create Software RAID” for more information. You can also mark the volume group for encryption and set the size policy for it. The available policy options are:- Automatic - the size of the volume group is set automatically so that it is just large enough to contain the configured logical volumes. This is optimal if you do not need free space within the volume group.
- As large as possible - the volume group is created with maximum size, regardless of the size of the configured logical volumes it contains. This is optimal if you plan to keep most of your data on LVM and later need to increase the size of some existing logical volumes, or if you need to create additional logical volumes within this group.
- Fixed - with this option, you can set an exact size of the volume group. Any configured logical volumes must then fit within this fixed size. This is useful if you know exactly how large you would like the volume group to be.
Click when the group is configured. - Click to save your changes, and either continue with another partition or click to return to the Installation Summary screen.
Warning
/boot partition on an LVM volume is not supported.
18.15.3.4. Recommended Partitioning Scheme
- 'Chapter 7. Linux Swapping' in the IBM Redbooks publication Linux on IBM System z: Performance Measurement and Tuning [IBM Form Number SG24-6926-01], [ISBN 0738485586], available from http://www.redbooks.ibm.com/abstracts/sg246926.html
- Linux Performance when running under VM, available from http://www.vm.ibm.com/perf/tips/linuxper.html
18.16. Storage Devices
Warning
/etc/dasd.conf configuration file as described in Section 20.1.3, “Persistently Setting DASDs Online”.

Figure 18.25. Storage Space Overview
18.16.1. The Storage Devices Selection Screen
- Multipath Devices
- Storage devices accessible through more than one path, such as through multiple SCSI controllers or Fiber Channel ports on the same system.
Important
The installation program only detects multipath storage devices with serial numbers that are 16 or 32 characters long. - Other SAN Devices
- Any other devices available on a Storage Area Network (SAN) such as FCP LUNs attached over one single path.
- Firmware RAID
- Storage devices attached to a firmware RAID controller. This tab does not apply to IBM Z.
- System z Devices
- This tab contains storage devices, or Logical Units (LUNs), attached through the zSeries Linux FCP (Fiber Channel Protocol) driver.

Figure 18.26. Tabbed Overview of Specialized Storage Devices
- - press this button to add a zFCP storage device, and continue with Section 18.16.1.2.3, “FCP Devices”
- - press this to add additional DASD devices, and continue with Section 18.16.1.2.2, “DASD storage devices”
- - use to attach iSCSI devices; continue with Section 18.16.1.2.1, “Configuring iSCSI Parameters”
- - use to configure a Fibre Channel Over Internet storage device; continue with Section 18.16.1.2.4, “Configure FCoE Parameters”
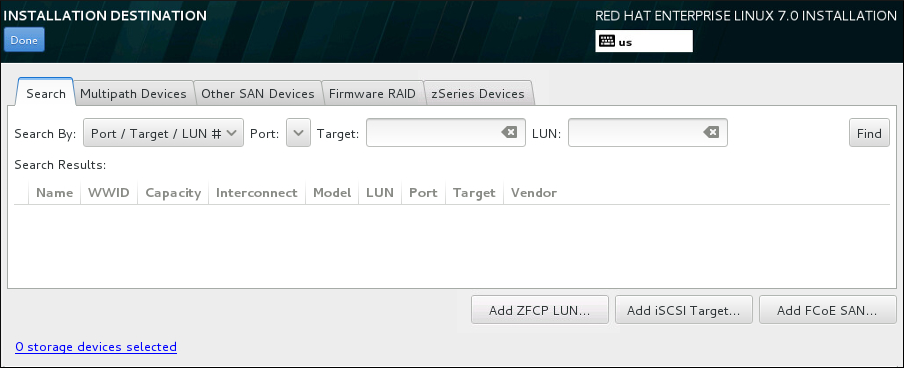
Figure 18.27. The Storage Devices Search Tab
/etc/fstab file.
18.16.1.1. DASD Low-level Formatting
Figure 18.28. Dialog for Formatting DASD Devices
zerombr. See zerombr (optional) for more details.
msdos partition table on the target DASD. The table does not allow more than three partitions on one DASD device. You can create the partitions manually or use the autopart --nohome Kickstart option, which ensures that the installer does not create a separate /home/ partition. The absence of the home directory keeps the number of partitions at three.
18.16.1.2. Advanced Storage Options

Figure 18.29. Advanced Storage Options
18.16.1.2.1. Configuring iSCSI Parameters

Figure 18.30. The iSCSI Discovery Details Dialog
Note
Procedure 18.1. iSCSI Discovery and Starting an iSCSI Session
- Enter the IP address of the iSCSI target in the Target IP Address field.
- Provide a name in the iSCSI Initiator Name field for the iSCSI initiator in iSCSI qualified name (IQN) format. A valid IQN entry contains:
- the string
iqn.(note the period) - a date code that specifies the year and month in which your organization's Internet domain or subdomain name was registered, represented as four digits for the year, a dash, and two digits for the month, followed by a period. For example, represent September 2010 as
2010-09. - your organization's Internet domain or subdomain name, presented in reverse order with the top-level domain first. For example, represent the subdomain
storage.example.comascom.example.storage - a colon followed by a string that uniquely identifies this particular iSCSI initiator within your domain or subdomain. For example,
:diskarrays-sn-a8675309
A complete IQN can therefore look as follows:iqn.2010-09.storage.example.com:diskarrays-sn-a8675309. Anaconda prepopulates the iSCSI Initiator Name field with a name in this format to help you with the structure.For more information on IQNs , see 3.2.6. iSCSI Names in RFC 3720 - Internet Small Computer Systems Interface (iSCSI) available from http://tools.ietf.org/html/rfc3720#section-3.2.6 and 1. iSCSI Names and Addresses in RFC 3721 - Internet Small Computer Systems Interface (iSCSI) Naming and Discovery available from http://tools.ietf.org/html/rfc3721#section-1. - Use the Discovery Authentication Type drop-down menu to specify the type of authentication to use for iSCSI discovery. The following options are available:
- no credentials
- CHAP pair
- CHAP pair and a reverse pair
- If you selected as the authentication type, provide the user name and password for the iSCSI target in the CHAP Username and CHAP Password fields.
- If you selected as the authentication type, provide the user name and password for the iSCSI target in the CHAP Username and CHAP Password field and the user name and password for the iSCSI initiator in the Reverse CHAP Username and Reverse CHAP Password fields.
- Optionally check the box labeled Bind targets to network interfaces.
- Click the button. Anaconda attempts to discover an iSCSI target based on the information that you provided. If discovery succeeds, the dialog displays a list of all iSCSI nodes discovered on the target.
- Each node is presented with a check box beside it. Click the check boxes to select the nodes to use for installation.

Figure 18.31. The Dialog of Discovered iSCSI Nodes
- The Node login authentication type menu provides the same options as the Discovery Authentication Type menu described in step 3. However, if you needed credentials for discovery authentication, it is typical to use the same credentials to log into a discovered node. To do that, use the additional option from the menu. When the proper credentials have been provided, the button becomes available.
- Click to initiate an iSCSI session.
18.16.1.2.2. DASD storage devices
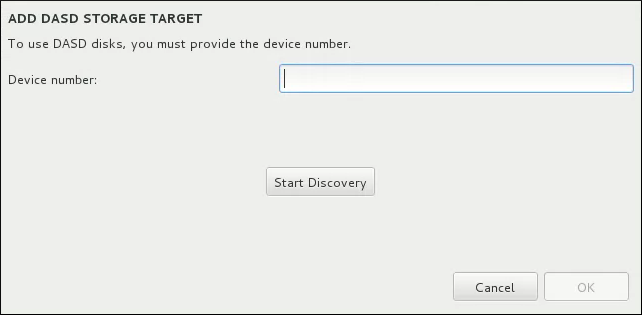
Figure 18.32. Add DASD Storage Target
0.0.0204. Enter the device number of the DASD you want to attach, and click .
18.16.1.2.3. FCP Devices
Notes
- Interactive creation of an FCP device is only possible in graphical mode. It is not possible to interactively configure an FCP device in a text mode installation.
- Use only lower-case letters in hex values. If you enter an incorrect value and hit the button, the installation program will display a warning and allow you to edit the configuration information and retry the discovery attempt.
- For more information on these values, consult the hardware documentation and check with the system administrator who set up the network for this system.
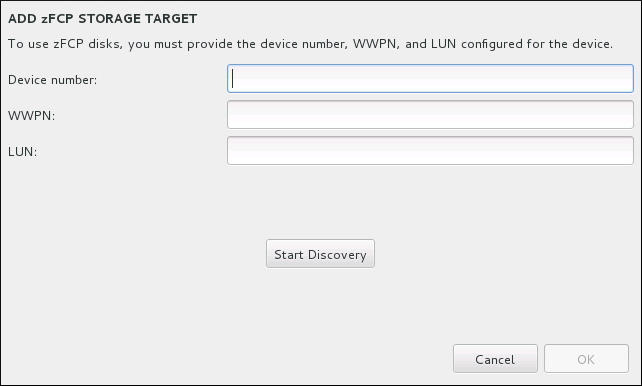
Figure 18.33. Add FCP Device
Important
DASD= from the parameter or CMS configuration file to indicate no DASD is present.
18.16.1.2.4. Configure FCoE Parameters

Figure 18.34. Configure FCoE Parameters
- Use DCB
- Data Center Bridging (DCB) is a set of enhancements to the Ethernet protocols designed to increase the efficiency of Ethernet connections in storage networks and clusters. Enable or disable the installation program's awareness of DCB with the check box in this dialog. This option should only be enabled for network interfaces that require a host-based DCBX client. Configurations on interfaces that implement a hardware DCBX client should leave this check box empty.
- Use auto vlan
- Auto VLAN indicates whether VLAN discovery should be performed. If this box is checked, then the FIP (FCoE Initiation Protocol) VLAN discovery protocol will run on the Ethernet interface once the link configuration has been validated. If they are not already configured, network interfaces for any discovered FCoE VLANs will be automatically created and FCoE instances will be created on the VLAN interfaces. This option is enabled by default.
18.17. Kdump

Figure 18.35. Kdump Enablement and Configuration
18.18. Begin Installation

Figure 18.36. Ready to Install
Warning
18.20. Installation Complete
/boot partition for Red Hat Enterprise Linux has been installed.
18.20.1. IPL under z/VM
#cp i 200
#cp i 200/boot partition is typically located.
/boot on an FCP LUN, you must provide the WWPN and LUN for the FCP-attached device from which to IPL.
- Provide FCP routing information to an FCP-attached device, for example, where
0x50050763050B073Dis the WWPN, and0x4020400100000000is the FCP LUN:#cp set loaddev portname 50050763 050B073D lun 40204001 00000000
#cp set loaddev portname 50050763 050B073D lun 40204001 00000000Copy to Clipboard Copied! Toggle word wrap Toggle overflow - IPL the FCP adapter, for example
FC00:#cp ipl FC00
#cp ipl FC00Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Note
#cp disconnect instead of #cp logoff. When your virtual machine is re-connected using the usual logon procedure, it might be placed in CP console function mode (CP READ). If so, to resume execution on your virtual machine, enter the BEGIN command.
18.20.2. IPL on an LPAR
/boot partition is located.
18.20.3. Continuing after Reboot (re-IPL)
/etc/securetty.
Chapter 19. Troubleshooting Installation on IBM Z
/tmp directory. These files are listed in the following table.
| Log file | Contents |
|---|---|
/tmp/anaconda.log | general Anaconda messages |
/tmp/program.log | all external programs run during the installation |
/tmp/storage.log | extensive storage module information |
/tmp/packaging.log | yum and rpm package installation messages |
/tmp/syslog | hardware-related system messages |
/tmp/anaconda-tb-identifier, where identifier is a random string.
/var/log/anaconda/. However, if installation is unsuccessful, or if the inst.nosave=all or inst.nosave=logs options are used when booting the installation system, these logs will only exist in the installation program's RAM disk. This means they are not saved permanently and will be lost once the system is powered down. To store them permanently, copy those files to another system on the network by using scp on the system running the installation program, or copy them to a mounted storage device (such as an USB flash drive). Details on how to transfer the log files over the network are below.
Note
ssh protocol.
Procedure 19.1. Transferring Log Files Over the Network
- Access the shell prompt on the installation system. This can be done in the following ways:
- In a running
tmuxsession on the installation system, press Ctrl+b p and Ctrl+b n to switch to the previous or next terminal, respectively, and find the terminal with a root shell. - Connect to the installation system over
ssh.
In both cases, you will be able to use the installation system's shell asroot. - Switch to the
/tmpdirectory where the log files are located:cd /tmp
# cd /tmpCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the log files onto another system on the network using the
scpcommand:scp *log user@address:path
# scp *log user@address:pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace user with a valid user name on the target system, address with the target system's address or host name, and path with the path to the directory you want to save the log files into. For example, if you want to log in asjohnto a system with an IP address of192.168.0.122and place the log files into the/home/john/logs/directory on that system, the command will have the following form:scp *log john@192.168.0.122:/home/john/logs/
# scp *log john@192.168.0.122:/home/john/logs/Copy to Clipboard Copied! Toggle word wrap Toggle overflow When connecting to the target system for the first time, the SSH client asks you to confirm that the fingerprint of the remote system is correct and that you want to continue:The authenticity of host '192.168.0.122 (192.168.0.122)' can't be established. ECDSA key fingerprint is a4:60:76:eb:b2:d0:aa:23:af:3d:59:5c:de:bb:c4:42. Are you sure you want to continue connecting (yes/no)?
The authenticity of host '192.168.0.122 (192.168.0.122)' can't be established. ECDSA key fingerprint is a4:60:76:eb:b2:d0:aa:23:af:3d:59:5c:de:bb:c4:42. Are you sure you want to continue connecting (yes/no)?Copy to Clipboard Copied! Toggle word wrap Toggle overflow Typeyesand press Enter to continue. Then, provide a valid password when prompted. The files will start transferring to the specified directory on the target system.
19.1. Trouble During the Installation
19.1.1. No Disks Detected
DASD=<disks> parameter to your parameter file or CMS configuration file (where disks is the DASD range reserved for installation) and start the installation again.
dasdfmt command within a Linux root shell, instead of formatting the DASDs using CMS. Anaconda automatically detects any DASD devices that are not yet formatted and asks you whether to format the devices.
19.1.2. Reporting Traceback Messages

Figure 19.1. The Crash Reporting Dialog Box
tty1, where you can request more precise information that will enhance the bug report. To return to the graphical interface from tty1, use the continue command.

Figure 19.2. The Expanded Crash Reporting Dialog Box
Procedure 19.2. Reporting Errors to Red Hat Customer Support
- In the menu that appears, select Report a bug to Red Hat Customer Portal.
- To report the bug to Red Hat, you first need to provide your Customer Portal credentials. Click .

Figure 19.3. Customer Portal Credentials
- A new window is now open, prompting you to enter your Customer Portal user name and password. Enter your Red Hat Customer Portal credentials.

Figure 19.4. Configure Red Hat Customer Support
If your network settings require you to use aHTTPorHTTPSproxy, you can configure it by expanding the Advanced menu and entering the address of the proxy server.When you put in all required credentials, click OK to proceed. - A new window appears, containing a text field. Write down any useful information and comments here. Describe how the error can be reproduced by explaining each step you took before the crash reporting dialog appeared. Provide as much relevant detail as possible, including any information you acquired when debugging. Be aware that the information you provide here can become publicly visible on the Customer Portal.If you do not know what caused the error, check the box labeled I don't know what caused this problem at the bottom of the dialog.Then, click .

Figure 19.5. Describe the Problem
- Next, review the information that will be sent to the Customer Portal. The explanation you provided is in the comment tab. Other tabs include such information as your system's host name and other details about the installation environment. You can remove any items you do not want sent to Red Hat, but be aware that providing less detail can affect the investigation of the issue.Click when you finish reviewing the information to be sent.

Figure 19.6. Review the Data to Be Sent
- Review the list of files that will be sent and included in the bug report as individual attachments. These files provide system information that will assist the investigation. If you do not want to send certain files, uncheck the box next to each one. To provide additional files that can help find the problem, click .Once you have reviewed the files to be sent, check the box labeled I have reviewed the data and agree with submitting it. Then, click to send the report and attachments to the Customer Portal.

Figure 19.7. Review the Files to Be Sent
- When the dialog reports that processing has finished, you can click Show log to view details of the reporting process or Close to return to the initial crash reporting dialog box. There, click Quit to exit the installation.
19.1.3. Creating Pre-installation Log Files
inst.debug option to create log files from the environment before the installation starts. These log files contain, for example, the current storage configuration.
- Select the entry.
- Press the Tab key to edit the boot options.
- Append
inst.debugto the options. For example:> vmlinuz ... inst.debug
> vmlinuz ... inst.debugCopy to Clipboard Copied! Toggle word wrap Toggle overflow For further details, see Chapter 23, Boot Options. - Press Enter to start the setup.
/tmp/pre-anaconda-logs/ directory before Anaconda starts. To access the log files:
- Switch to the console. See Section 8.2.1, “Accessing Consoles”.
- Change into the
/tmp/pre-anaconda-logs/directory:cd /tmp/pre-anaconda-logs/
# cd /tmp/pre-anaconda-logs/Copy to Clipboard Copied! Toggle word wrap Toggle overflow
19.2. Problems After Installation
19.2.1. Remote Graphical Desktops and XDMCP
Procedure 19.3. Enabling XDMCP on IBM Z
- Open the
/etc/gdm/custom.confconfiguration file in a plain text editor such as vi or nano. - In the
custom.conffile, locate the section starting with[xdmcp]. In this section, add the following line:Enable=true
Enable=trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the file, and exit the text editor.
- Restart the X Window System. To do this, either reboot the whole system, or restart the GNOME Display Manager using the following command as
root:systemctl restart gdm.service
# systemctl restart gdm.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait for the login prompt to appear again, and log in using your normal user name and password.
X command on the client workstation. For example:
X :1 -query address
$ X :1 -query address:1 of the X11 server system (usually accessible by pressing Ctrl-Alt-F8).
Xnest allows users to open a remote desktop nested within their local X11 session. For example, run Xnest using the following command, replacing address with the host name of the remote X11 server:
Xnest :1 -query address
$ Xnest :1 -query address19.2.2. Is Your System Displaying Signal 11 Errors?
rd.live.check boot option at the boot menu. See Section 23.2.2, “Verifying Boot Media” for details.
Chapter 20. Configuring an Installed Linux on IBM Z Instance
20.1. Adding DASDs
Note
CP ATTACH EB1C TO *
CP ATTACH EB1C TO *CP LINK RHEL7X 4B2E 4B2E MR DASD 4B2E LINKED R/W
CP LINK RHEL7X 4B2E 4B2E MR
DASD 4B2E LINKED R/W20.1.1. Dynamically Setting DASDs Online
- Use the
cio_ignoreutility to remove the DASD from the list of ignored devices and make it visible to Linux:cio_ignore -r device_number
# cio_ignore -r device_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace device_number with the device number of the DASD. For example:cio_ignore -r 4b2e
# cio_ignore -r 4b2eCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Set the device online. Use a command of the following form:
chccwdev -e device_number
# chccwdev -e device_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace device_number with the device number of the DASD. For example:chccwdev -e 4b2e
# chccwdev -e 4b2eCopy to Clipboard Copied! Toggle word wrap Toggle overflow As an alternative, you can set the device online using sysfs attributes:- Use the
cdcommand to change to the /sys/ directory that represents that volume:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Check to see if the device is already online:
cat online 0
# cat online 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If it is not online, enter the following command to bring it online:
echo 1 > online cat online 1
# echo 1 > online # cat online 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Verify which block devnode it is being accessed as:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow As shown in this example, device 4B2E is being accessed as /dev/dasdb.
/dev/disk/by-path/. See the chapter about persistent storage device naming in the Red Hat Enterprise Linux 7 Storage Administration Guide for more in-depth information about different ways to consistently refer to storage devices.
20.1.2. Preparing a New DASD with Low-level Formatting
/root directory and low-level format the device. This is only required once for a DASD during its entire lifetime:
Rereading the partition table... Exiting...
Rereading the partition table...
Exiting.../dev/disk/by-path/ccw-0.0.4b2e-part1. Never use the full DASD device (dev/dasdb) for anything but the commands dasdfmt and fdasd. If you want to use the entire DASD, create one partition spanning the entire drive as in the fdasd example above.
/etc/fstab, use the persistent device symbolic links under /dev/disk/by-path/.
20.1.3. Persistently Setting DASDs Online
initramfs to be able to mount the root file system.
cio_ignore commands are handled transparently for persistent device configurations and you do not need to free devices from the ignore list manually.
20.1.3.1. DASDs That Are Part of the Root File System
/etc/zipl.conf. Then run the zipl boot loader tool. There is no need to recreate the initramfs.
rd.dasd=. This option takes a Direct Access Storage Device (DASD) adapter device bus identifier. For multiple DASDs, specify the parameter multiple times, or use a comma separated list of bus IDs. To specify a range of DASDs, specify the first and the last bus ID.
zipl.conf for a system that uses physical volumes on partitions of two DASDs for an LVM volume group vg_devel1 that contains a logical volume lv_root for the root file system.
0.0.202b. To do this, add rd.dasd=0.0.202b to the parameters line of your boot kernel in zipl.conf:
Warning
/etc/zipl.conf does not exceed 896 bytes. Otherwise, the boot loader cannot be saved, and the installation fails.
zipl to apply the changes of /etc/zipl.conf for the next IPL:
20.1.3.2. DASDs That Are Not Part of the Root File System
/etc/dasd.conf. It contains one DASD per line. Each line begins with the device bus ID of a DASD. Optionally, each line can continue with options separated by space or tab characters. Options consist of key-value-pairs, where the key and value are separated by an equals sign.
sysfs attribute a DASD can have. The value will be written to the key's sysfs attribute. Entries in /etc/dasd.conf are activated and configured by udev when a DASD is added to the system. At boot time, all DASDs visible to the system get added and trigger udev.
/etc/dasd.conf:
0.0.0207 0.0.0200 use_diag=1 readonly=1
0.0.0207
0.0.0200 use_diag=1 readonly=1/etc/dasd.conf only become effective after a reboot of the system or after the dynamic addition of a new DASD by changing the system's I/O configuration (that is, the DASD is attached under z/VM). Alternatively, you can trigger the activation of a new entry in /etc/dasd.conf for a DASD which was previously not active, by executing the following commands:
- Use the
cio_ignoreutility to remove the DASD from the list of ignored devices and make it visible to Linux:cio_ignore -r device_number
# cio_ignore -r device_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:cio_ignore -r 021a
# cio_ignore -r 021aCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Trigger the activation by writing to the
ueventattribute of the device:echo add > /sys/bus/ccw/devices/device-bus-ID/uevent
# echo add > /sys/bus/ccw/devices/device-bus-ID/ueventCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:echo add > /sys/bus/ccw/devices/0.0.021a/uevent
# echo add > /sys/bus/ccw/devices/0.0.021a/ueventCopy to Clipboard Copied! Toggle word wrap Toggle overflow
20.2. Adding FCP-attached Logical Units (LUNs)
Note
CP ATTACH FC00 TO * CP ATTACH FCD0 TO *
CP ATTACH FC00 TO *
CP ATTACH FCD0 TO *20.2.1. Dynamically Activating an FCP LUN
- Use the
cio_ignoreutility to remove the FCP adapter from the list of ignored devices and make it visible to Linux:cio_ignore -r device_number
# cio_ignore -r device_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace device_number with the device number of the FCP adapter. For example: - To bring the FCP adapter device online, use the following command:
chccwdev -e fc00
# chccwdev -e fc00Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Verify that the required WWPN was found by the automatic port scanning of the zfcp device driver:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Activate the FCP LUN by adding it to the port (WWPN) through which you would like to access the LUN:
echo 0x4020400100000000 > /sys/bus/ccw/drivers/zfcp/0.0.fc00/0x50050763050b073d/unit_add
# echo 0x4020400100000000 > /sys/bus/ccw/drivers/zfcp/0.0.fc00/0x50050763050b073d/unit_addCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Find out the assigned SCSI device name:
lszfcp -DV /sys/devices/css0/0.0.0015/0.0.fc00/0x50050763050b073d/0x4020400100000000 /sys/bus/ccw/drivers/zfcp/0.0.fc00/host0/rport-0:0-21/target0:0:21/0:0:21:1089355792
# lszfcp -DV /sys/devices/css0/0.0.0015/0.0.fc00/0x50050763050b073d/0x4020400100000000 /sys/bus/ccw/drivers/zfcp/0.0.fc00/host0/rport-0:0-21/target0:0:21/0:0:21:1089355792Copy to Clipboard Copied! Toggle word wrap Toggle overflow
20.2.2. Persistently activating FCP LUNs
initramfs to be able to mount the root file system. The cio_ignore commands are handled transparently for persistent device configurations and you do not need to free devices from the ignore list manually.
20.2.2.1. FCP LUNs That Are Part of the Root File System
/etc/zipl.conf followed by a run of the zipl boot loader tool. There is no more need to recreate the initramfs.
rd.zfcp=. The value is a comma-separated list containing the device bus ID, the WWPN as 16 digit hexadecimal number prefixed with 0x, and the FCP LUN prefixed with 0x and padded with zeroes to the right to have 16 hexadecimal digits.
zipl.conf is for a system that uses physical volumes on partitions of two FCP LUNs for an LVM volume group vg_devel1 that contains a logical volume lv_root for the root file system. For simplicity, the example shows a configuration without multipathing.
rd.zfcp=0.0.fc00,0x5105074308c212e9,0x401040a300000000 to the parameters line of your boot kernel in zipl.conf. For example:
Warning
/etc/zipl.conf does not exceed 896 bytes. Otherwise, the boot loader cannot be saved, and the installation fails.
/etc/zipl.conf for the next IPL:
20.2.2.2. FCP LUNs That Are Not Part of the Root File System
/etc/zfcp.conf. It contains one FCP LUN per line. Each line contains the device bus ID of the FCP adapter, the WWPN as 16 digit hexadecimal number prefixed with 0x, and the FCP LUN prefixed with 0x and padded with zeroes to the right to have 16 hexadecimal digits, separated by a space or tab. Entries in /etc/zfcp.conf are activated and configured by udev when an FCP adapter is added to the system. At boot time, all FCP adapters visible to the system are added and trigger udev.
/etc/zfcp.conf:
/etc/zfcp.conf only become effective after a reboot of the system or after the dynamic addition of a new FCP channel by changing the system's I/O configuration (for example, a channel is attached under z/VM). Alternatively, you can trigger the activation of a new entry in /etc/zfcp.conf for an FCP adapter which was previously not active, by executing the following commands:
- Use the
cio_ignoreutility to remove the FCP adapter from the list of ignored devices and make it visible to Linux:cio_ignore -r device_number
# cio_ignore -r device_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace device_number with the device number of the FCP adapter. For example:cio_ignore -r fcfc
# cio_ignore -r fcfcCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To trigger the uevent that activates the change, issue:
echo add > /sys/bus/ccw/devices/device-bus-ID/uevent
# echo add > /sys/bus/ccw/devices/device-bus-ID/ueventCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:echo add > /sys/bus/ccw/devices/0.0.fcfc/uevent
# echo add > /sys/bus/ccw/devices/0.0.fcfc/ueventCopy to Clipboard Copied! Toggle word wrap Toggle overflow
20.3. Adding a Network Device
- Dynamically
- Load the device driver
- Remove the network devices from the list of ignored devices.
- Create the group device.
- Configure the device.
- Set the device online.
- Persistently
- Create a configuration script.
- Activate the interface.
20.3.1. Adding a qeth Device
qeth network device driver supports IBM Z OSA-Express features in QDIO mode, HiperSockets, z/VM guest LAN, and z/VM VSWITCH.
qeth device driver assigns the same interface name for Ethernet and Hipersockets devices: enccwbus_ID. The bus ID is composed of the channel subsystem ID, subchannel set ID, and device number, for example enccw0.0.0a00.
20.3.1.1. Dynamically Adding a qeth Device
qeth device dynamically, follow these steps:
- Determine whether the
qethdevice driver modules are loaded. The following example shows loadedqethmodules:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the output of thelsmodcommand shows that theqethmodules are not loaded, run themodprobecommand to load them:modprobe qeth
# modprobe qethCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
cio_ignoreutility to remove the network channels from the list of ignored devices and make them visible to Linux:cio_ignore -r read_device_bus_id,write_device_bus_id,data_device_bus_id
# cio_ignore -r read_device_bus_id,write_device_bus_id,data_device_bus_idCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace read_device_bus_id,write_device_bus_id,data_device_bus_id with the three device bus IDs representing a network device. For example, if the read_device_bus_id is0.0.f500, the write_device_bus_id is0.0.f501, and the data_device_bus_id is0.0.f502:cio_ignore -r 0.0.f500,0.0.f501,0.0.f502
# cio_ignore -r 0.0.f500,0.0.f501,0.0.f502Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the znetconf utility to sense and list candidate configurations for network devices:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Select the configuration you want to work with and use znetconf to apply the configuration and to bring the configured group device online as network device.
znetconf -a f500 Scanning for network devices... Successfully configured device 0.0.f500 (enccw0.0.f500)
# znetconf -a f500 Scanning for network devices... Successfully configured device 0.0.f500 (enccw0.0.f500)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, you can also pass arguments that are configured on the group device before it is set online:
znetconf -a f500 -o portname=myname Scanning for network devices... Successfully configured device 0.0.f500 (enccw0.0.f500)
# znetconf -a f500 -o portname=myname Scanning for network devices... Successfully configured device 0.0.f500 (enccw0.0.f500)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Now you can continue to configure theenccw0.0.f500network interface.
sysfs attributes to set the device online as follows:
- Create a
qethgroup device:echo read_device_bus_id,write_device_bus_id,data_device_bus_id > /sys/bus/ccwgroup/drivers/qeth/group
# echo read_device_bus_id,write_device_bus_id,data_device_bus_id > /sys/bus/ccwgroup/drivers/qeth/groupCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:echo 0.0.f500,0.0.f501,0.0.f502 > /sys/bus/ccwgroup/drivers/qeth/group
# echo 0.0.f500,0.0.f501,0.0.f502 > /sys/bus/ccwgroup/drivers/qeth/groupCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Next, verify that the
qethgroup device was created properly by looking for the read channel:ls /sys/bus/ccwgroup/drivers/qeth/0.0.f500
# ls /sys/bus/ccwgroup/drivers/qeth/0.0.f500Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can optionally set additional parameters and features, depending on the way you are setting up your system and the features you require, such as:portnolayer2portname
- Bring the device online by writing
1to the onlinesysfsattribute:echo 1 > /sys/bus/ccwgroup/drivers/qeth/0.0.f500/online
# echo 1 > /sys/bus/ccwgroup/drivers/qeth/0.0.f500/onlineCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Then verify the state of the device:
cat /sys/bus/ccwgroup/drivers/qeth/0.0.f500/online 1
# cat /sys/bus/ccwgroup/drivers/qeth/0.0.f500/online 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow A return value of1indicates that the device is online, while a return value0indicates that the device is offline. - Find the interface name that was assigned to the device:
cat /sys/bus/ccwgroup/drivers/qeth/0.0.f500/if_name enccw0.0.f500
# cat /sys/bus/ccwgroup/drivers/qeth/0.0.f500/if_name enccw0.0.f500Copy to Clipboard Copied! Toggle word wrap Toggle overflow Now you can continue to configure theenccw0.0.f500network interface.The following command from the s390utils package shows the most important settings of yourqethdevice:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
20.3.1.2. Dynamically Removing a qeth Device
qeth device, use the znetconf utility. For example:
- Use the
znetconfutility to show you all configured network devices:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Select the network device to be removed and run
znetconfto set the device offline and ungroup theccw> group device.znetconf -r f500 Remove network device 0.0.f500 (0.0.f500,0.0.f501,0.0.f502)? Warning: this may affect network connectivity! Do you want to continue (y/n)?y Successfully removed device 0.0.f500 (enccw0.0.f500)
# znetconf -r f500 Remove network device 0.0.f500 (0.0.f500,0.0.f501,0.0.f502)? Warning: this may affect network connectivity! Do you want to continue (y/n)?y Successfully removed device 0.0.f500 (enccw0.0.f500)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Verify the success of the removal:
znetconf -c Device IDs Type Card Type CHPID Drv. Name State -------------------------------------------------------------------------------------- 0.0.8036,0.0.8037,0.0.8038 1731/05 HiperSockets FB qeth hsi1 online 0.0.f5f0,0.0.f5f1,0.0.f5f2 1731/01 OSD_1000 76 qeth enccw0.0.09a0 online
# znetconf -c Device IDs Type Card Type CHPID Drv. Name State -------------------------------------------------------------------------------------- 0.0.8036,0.0.8037,0.0.8038 1731/05 HiperSockets FB qeth hsi1 online 0.0.f5f0,0.0.f5f1,0.0.f5f2 1731/01 OSD_1000 76 qeth enccw0.0.09a0 onlineCopy to Clipboard Copied! Toggle word wrap Toggle overflow
20.3.1.3. Persistently Adding a qeth Device
qeth device persistent, you need to create the configuration file for your new interface. The network interface configuration files are placed in the /etc/sysconfig/network-scripts/ directory.
ifcfg-device, where device is the value found in the if_name file in the qeth group device that was created earlier, for example enccw0.0.09a0. The cio_ignore commands are handled transparently for persistent device configurations and you do not need to free devices from the ignore list manually.
cd /etc/sysconfig/network-scripts cp ifcfg-enccw0.0.09a0 ifcfg-enccw0.0.0600
# cd /etc/sysconfig/network-scripts
# cp ifcfg-enccw0.0.09a0 ifcfg-enccw0.0.0600lsqeth -p devices CHPID interface cardtype port chksum prio-q'ing rtr4 rtr6 lay'2 cnt -------------------------- ----- ---------------- -------------- ---- ------ ---------- ---- ---- ----- ----- 0.0.09a0/0.0.09a1/0.0.09a2 x00 enccw0.0.09a0 Virt.NIC QDIO 0 sw always_q_2 n/a n/a 1 64 0.0.0600/0.0.0601/0.0.0602 x00 enccw0.0.0600 Virt.NIC QDIO 0 sw always_q_2 n/a n/a 1 64
# lsqeth -p
devices CHPID interface cardtype port chksum prio-q'ing rtr4 rtr6 lay'2 cnt
-------------------------- ----- ---------------- -------------- ---- ------ ---------- ---- ---- ----- -----
0.0.09a0/0.0.09a1/0.0.09a2 x00 enccw0.0.09a0 Virt.NIC QDIO 0 sw always_q_2 n/a n/a 1 64
0.0.0600/0.0.0601/0.0.0602 x00 enccw0.0.0600 Virt.NIC QDIO 0 sw always_q_2 n/a n/a 1 64/etc/sysconfig/network-scripts/ifcfg-0.0.09a0 as a template:
ifcfg-0.0.0600 file as follows:
- Modify the
DEVICEstatement to reflect the contents of theif_namefile from yourccwgroup. - Modify the
IPADDRstatement to reflect the IP address of your new interface. - Modify the
NETMASKstatement as needed. - If the new interface is to be activated at boot time, then make sure
ONBOOTis set toyes. - Make sure the
SUBCHANNELSstatement matches the hardware addresses for your qeth device. Please, note that the IDs must be specified in lowercase. - Modify the
PORTNAMEstatement or leave it out if it is not necessary in your environment. - You can add any valid
sysfsattribute and its value to theOPTIONSparameter. The Red Hat Enterprise Linux installation program currently uses this to configure the layer mode (layer2) and the relative port number (portno) ofqethdevices.Theqethdevice driver default for OSA devices is now layer 2 mode. To continue using oldifcfgdefinitions that rely on the previous default of layer 3 mode, addlayer2=0to theOPTIONSparameter.
/etc/sysconfig/network-scripts/ifcfg-0.0.0600
ifcfg file only become effective after rebooting the system or after the dynamic addition of new network device channels by changing the system's I/O configuration (for example, attaching under z/VM). Alternatively, you can trigger the activation of a ifcfg file for network channels which were previously not active yet, by executing the following commands:
- Use the
cio_ignoreutility to remove the network channels from the list of ignored devices and make them visible to Linux:cio_ignore -r read_device_bus_id,write_device_bus_id,data_device_bus_id
# cio_ignore -r read_device_bus_id,write_device_bus_id,data_device_bus_idCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace read_device_bus_id,write_device_bus_id,data_device_bus_id with the three device bus IDs representing a network device. For example, if the read_device_bus_id is0.0.0600, the write_device_bus_id is0.0.0601, and the data_device_bus_id is0.0.0602:cio_ignore -r 0.0.0600,0.0.0601,0.0.0602
# cio_ignore -r 0.0.0600,0.0.0601,0.0.0602Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To trigger the uevent that activates the change, issue:
echo add > /sys/bus/ccw/devices/read-channel/uevent
# echo add > /sys/bus/ccw/devices/read-channel/ueventCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:echo add > /sys/bus/ccw/devices/0.0.0600/uevent
# echo add > /sys/bus/ccw/devices/0.0.0600/ueventCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Check the status of the network device:
lsqeth
# lsqethCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Now start the new interface:
ifup enccw0.0.0600
# ifup enccw0.0.0600Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Check the status of the interface:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Check the routing for the new interface:
ip route default via 10.85.1.245 dev enccw0.0.0600 proto static metric 1024 12.34.4.95/24 dev enp0s25 proto kernel scope link src 12.34.4.201 12.38.4.128 via 12.38.19.254 dev enp0s25 proto dhcp metric 1 192.168.122.0/24 dev virbr0 proto kernel scope link src 192.168.122.1
# ip route default via 10.85.1.245 dev enccw0.0.0600 proto static metric 1024 12.34.4.95/24 dev enp0s25 proto kernel scope link src 12.34.4.201 12.38.4.128 via 12.38.19.254 dev enp0s25 proto dhcp metric 1 192.168.122.0/24 dev virbr0 proto kernel scope link src 192.168.122.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Verify your changes by using the
pingutility to ping the gateway or another host on the subnet of the new device:ping -c 1 192.168.70.8 PING 192.168.70.8 (192.168.70.8) 56(84) bytes of data. 64 bytes from 192.168.70.8: icmp_seq=0 ttl=63 time=8.07 ms
# ping -c 1 192.168.70.8 PING 192.168.70.8 (192.168.70.8) 56(84) bytes of data. 64 bytes from 192.168.70.8: icmp_seq=0 ttl=63 time=8.07 msCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If the default route information has changed, you must also update
/etc/sysconfig/networkaccordingly.
20.3.2. Adding an LCS Device
LCS device driver assigns the following interface name for OSA-Express Fast Ethernet and Gigabit Ethernet devices: enccwbus_ID. The bus ID is composed of the channel subsystem ID, subchannel set ID, and device number, for example enccw0.0.0a00.
20.3.2.1. Dynamically Adding an LCS Device
- Load the device driver:
modprobe lcs
# modprobe lcsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
cio_ignoreutility to remove the network channels from the list of ignored devices and make them visible to Linux:cio_ignore -r read_device_bus_id,write_device_bus_id
# cio_ignore -r read_device_bus_id,write_device_bus_idCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace read_device_bus_id and write_device_bus_id with the two device bus IDs representing a network device. For example:cio_ignore -r 0.0.09a0,0.0.09a1
# cio_ignore -r 0.0.09a0,0.0.09a1Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Create the group device:
echo read_device_bus_id,write_device_bus_id > /sys/bus/ccwgroup/drivers/lcs/group
# echo read_device_bus_id,write_device_bus_id > /sys/bus/ccwgroup/drivers/lcs/groupCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the device. OSA cards can provide up to 16 ports for a single CHPID. By default, the LCS group device uses port
0. To use a different port, issue a command similar to the following:echo portno > /sys/bus/ccwgroup/drivers/lcs/device_bus_id/portno
# echo portno > /sys/bus/ccwgroup/drivers/lcs/device_bus_id/portnoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace portno with the port number you want to use. - Set the device online:
echo 1 > /sys/bus/ccwgroup/drivers/lcs/read_device_bus_id/online
# echo 1 > /sys/bus/ccwgroup/drivers/lcs/read_device_bus_id/onlineCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To find out what network device name has been assigned, enter the command:
ls -l /sys/bus/ccwgroup/drivers/lcs/read_device_bus_ID/net/ drwxr-xr-x 4 root root 0 2010-04-22 16:54 enccw0.0.0600
# ls -l /sys/bus/ccwgroup/drivers/lcs/read_device_bus_ID/net/ drwxr-xr-x 4 root root 0 2010-04-22 16:54 enccw0.0.0600Copy to Clipboard Copied! Toggle word wrap Toggle overflow
20.3.2.2. Persistently Adding an LCS Device
cio_ignore commands are handled transparently for persistent device configurations and you do not need to free devices from the ignore list manually.
- Create a configuration script as file in
/etc/sysconfig/network-scripts/with a name likeifcfg-device, where device is the value found in theif_namefile in theqethgroup device that was created earlier, for exampleenccw0.0.09a0. The file should look similar to the following:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Modify the value of
PORTNAMEto reflect the LCS port number (portno) you would like to use. You can add any valid lcs sysfs attribute and its value to the optionalOPTIONSparameter. See Section 20.3.1.3, “Persistently Adding a qeth Device” for the syntax. - Set the
DEVICEparameter as follows:DEVICE=enccwbus_ID
DEVICE=enccwbus_IDCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Issue an
ifupcommand to activate the device:ifup enccwbus_ID
# ifup enccwbus_IDCopy to Clipboard Copied! Toggle word wrap Toggle overflow
ifcfg file only become effective after rebooting the system. You can trigger the activation of a ifcfg file for network channels by executing the following commands:
- Use the
cio_ignoreutility to remove the LCS device adapter from the list of ignored devices and make it visible to Linux:cio_ignore -r read_device_bus_id,write_device_bus_id
# cio_ignore -r read_device_bus_id,write_device_bus_idCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace read_device_bus_id and write_device_bus_id with the device bus IDs of the LCS device. For example:cio_ignore -r 0.0.09a0,0.0.09a1
# cio_ignore -r 0.0.09a0,0.0.09a1Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To trigger the uevent that activates the change, issue:
echo add > /sys/bus/ccw/devices/read-channel/uevent
# echo add > /sys/bus/ccw/devices/read-channel/ueventCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:echo add > /sys/bus/ccw/devices/0.0.09a0/uevent
# echo add > /sys/bus/ccw/devices/0.0.09a0/ueventCopy to Clipboard Copied! Toggle word wrap Toggle overflow
20.3.3. Configuring a IBM Z Network Device for Network Root File System
zipl.conf on a DASD or FCP-attached SCSI LUN prepared with the zipl boot loader. There is no need to recreate the initramfs.
rd.znet=.
NETTYPE (qeth, lcs, ctc), two (lcs, ctc) or three (qeth) device bus IDs, and optional additional parameters consisting of key-value pairs corresponding to network device sysfs attributes. This parameter configures and activates the IBM Z network hardware. The configuration of IP addresses and other network specifics works the same as for other platforms. See the dracut documentation for more details.
root=10.16.105.196:/nfs/nfs_root cio_ignore=all,!condev rd.znet=qeth,0.0.0a00,0.0.0a01,0.0.0a02,layer2=1,portno=0,portname=OSAPORT ip=10.16.105.197:10.16.105.196:10.16.111.254:255.255.248.0:nfs‑server.subdomain.domain:enccw0.0.09a0:none rd_NO_LUKS rd_NO_LVM rd_NO_MD rd_NO_DM LANG=en_US.UTF-8 SYSFONT=latarcyrheb-sun16 KEYTABLE=us
root=10.16.105.196:/nfs/nfs_root cio_ignore=all,!condev rd.znet=qeth,0.0.0a00,0.0.0a01,0.0.0a02,layer2=1,portno=0,portname=OSAPORT ip=10.16.105.197:10.16.105.196:10.16.111.254:255.255.248.0:nfs‑server.subdomain.domain:enccw0.0.09a0:none rd_NO_LUKS rd_NO_LVM rd_NO_MD rd_NO_DM LANG=en_US.UTF-8 SYSFONT=latarcyrheb-sun16 KEYTABLE=usChapter 21. Parameter and Configuration Files on IBM Z
- install unattended with Kickstart.
- choose non-default installation settings that are not accessible through the installation program"s interactive user interface, such as rescue mode.
ro, and parameters for the installation process, such as vncpassword=test or vnc.
21.1. Required Parameters
generic.prm in directory images/ of the installation DVD:
ro- mounts the root file system, which is a RAM disk, read-only.
ramdisk_size=size- modifies the memory size reserved for the RAM disk to ensure that the Red Hat Enterprise Linux installation program fits within it. For example:
ramdisk_size=40000.
generic.prm file also contains the additional parameter cio_ignore=all,!condev. This setting speeds up boot and device detection on systems with many devices. The installation program transparently handles the activation of ignored devices.
Important
cio_ignore support not being implemented throughout the entire stack, adapt the cio_ignore= parameter value to your system or remove the parameter entirely from your parameter file used for booting (IPL) the installation program.
21.2. The z/VM Configuration File
variable=value .
CMSDASD and CMSCONFFILE parameters to the parameter file. These parameters point the installation program to the configuration file:
CMSDASD=cmsdasd_address- Where cmsdasd_address is the device number of a CMS-formatted disk that contains the configuration file. This is usually the CMS user"s
Adisk.For example:CMSDASD=191 CMSCONFFILE=configuration_file- Where configuration_file is the name of the configuration file. This value must be specified in lower case. It is specified in a Linux file name format:
CMS_file_name.CMS_file_type.The CMS fileREDHAT CONFis specified asredhat.conf. The CMS file name and the file type can each be from one to eight characters that follow the CMS conventions.For example:CMSCONFFILE=redhat.conf
21.3. Installation Network Parameters
NETTYPE="type"- Where type must be one of the following:
qeth,lcs, orctc. The default isqeth.Chooselcsfor:- OSA-2 Ethernet/Token Ring
- OSA-Express Fast Ethernet in non-QDIO mode
- OSA-Express High Speed Token Ring in non-QDIO mode
- Gigabit Ethernet in non-QDIO mode
Chooseqethfor:- OSA-Express Fast Ethernet
- Gigabit Ethernet (including 1000Base-T)
- High Speed Token Ring
- HiperSockets
- ATM (running Ethernet LAN emulation)
SUBCHANNELS="device_bus_IDs"- Where device_bus_IDs is a comma-separated list of two or three device bus IDs. The IDs must be specified in lowercase.Provides required device bus IDs for the various network interfaces:
qeth: SUBCHANNELS="read_device_bus_id,write_device_bus_id,data_device_bus_id" lcs or ctc: SUBCHANNELS="read_device_bus_id,write_device_bus_id"
qeth: SUBCHANNELS="read_device_bus_id,write_device_bus_id,data_device_bus_id" lcs or ctc: SUBCHANNELS="read_device_bus_id,write_device_bus_id"Copy to Clipboard Copied! Toggle word wrap Toggle overflow For example (a sample qeth SUBCHANNEL statement):SUBCHANNELS="0.0.f5f0,0.0.f5f1,0.0.f5f2"
SUBCHANNELS="0.0.f5f0,0.0.f5f1,0.0.f5f2"Copy to Clipboard Copied! Toggle word wrap Toggle overflow PORTNAME="osa_portname",PORTNAME="lcs_portnumber"- This variable supports OSA devices operating in qdio mode or in non-qdio mode.When using qdio mode (
NETTYPE="qeth"), osa_portname is the portname specified on the OSA device when operating in qeth mode.When using non-qdio mode (NETTYPE="lcs"), lcs_portnumber is used to pass the relative port number as a decimal integer in the range of 0 through 15. PORTNO="portnumber"- You can add either
PORTNO="0"(to use port 0) orPORTNO="1"(to use port 1 of OSA features with two ports per CHPID) to the CMS configuration file to avoid being prompted for the mode. LAYER2="value"- Where value can be
0or1.UseLAYER2="0"to operate an OSA or HiperSockets device in layer 3 mode (NETTYPE="qeth"). UseLAYER2="1"for layer 2 mode. For virtual network devices under z/VM this setting must match the definition of the GuestLAN or VSWITCH to which the device is coupled.To use network services that operate on layer 2 (the Data Link Layer or its MAC sublayer) such as DHCP, layer 2 mode is a good choice.The qeth device driver default for OSA devices is now layer 2 mode. To continue using the previous default of layer 3 mode, setLAYER2="0"explicitly. VSWITCH="value"- Where value can be
0or1.SpecifyVSWITCH="1"when connecting to a z/VM VSWITCH or GuestLAN, orVSWITCH="0"(or nothing at all) when using directly attached real OSA or directly attached real HiperSockets. MACADDR="MAC_address"- If you specify
LAYER2="1"andVSWITCH="0", you can optionally use this parameter to specify a MAC address. Linux requires six colon-separated octets as pairs lower case hex digits - for example,MACADDR=62:a3:18:e7:bc:5f. Note that this is different from the notation used by z/VM.If you specifyLAYER2="1"andVSWITCH="1", you must not specify theMACADDR, because z/VM assigns a unique MAC address to virtual network devices in layer 2 mode. CTCPROT="value"- Where value can be
0,1, or3.Specifies the CTC protocol forNETTYPE="ctc". The default is0. HOSTNAME="string"- Where string is the host name of the newly-installed Linux instance.
IPADDR="IP"- Where IP is the IP address of the new Linux instance.
NETMASK="netmask"- Where netmask is the netmask.The netmask supports the syntax of a prefix integer (from 1 to 32) as specified in IPv4 classless interdomain routing (CIDR). For example, you can specify
24instead of255.255.255.0, or20instead of255.255.240.0. GATEWAY="gw"- Where gw is the gateway IP address for this network device.
MTU="mtu"- Where mtu is the Maximum Transmission Unit (MTU) for this network device.
DNS="server1:server2:additional_server_terms:serverN"- Where "server1:server2:additional_server_terms:serverN" is a list of DNS servers, separated by colons. For example:
DNS="10.1.2.3:10.3.2.1"
DNS="10.1.2.3:10.3.2.1"Copy to Clipboard Copied! Toggle word wrap Toggle overflow SEARCHDNS="domain1:domain2:additional_dns_terms:domainN"- Where "domain1:domain2:additional_dns_terms:domainN" is a list of the search domains, separated by colons. For example:
SEARCHDNS="subdomain.domain:domain"
SEARCHDNS="subdomain.domain:domain"Copy to Clipboard Copied! Toggle word wrap Toggle overflow You only need to specifySEARCHDNS=if you specify theDNS=parameter. DASD=- Defines the DASD or range of DASDs to configure for the installation.The installation program supports a comma-separated list of device bus IDs or of ranges of device bus IDs with the optional attributes
ro,diag,erplog, andfailfast. Optionally, you can abbreviate device bus IDs to device numbers with leading zeros stripped. Any optional attributes should be separated by colons and enclosed in parentheses. Optional attributes follow a device bus ID or a range of device bus IDs.The only supported global option isautodetect. This does not support the specification of non-existent DASDs to reserve kernel device names for later addition of DASDs. Use persistent DASD device names (for example/dev/disk/by-path/...) to enable transparent addition of disks later. Other global options such asprobeonly,nopav, ornofcxare not supported by the installation program.Only specify those DASDs that you really need to install your system. All unformatted DASDs specified here must be formatted after a confirmation later on in the installation program (see Section 18.16.1.1, “DASD Low-level Formatting”). Add any data DASDs that are not needed for the root file system or the/bootpartition after installation as described in Section 20.1.3.2, “DASDs That Are Not Part of the Root File System”.For example:DASD="eb1c,0.0.a000-0.0.a003,eb10-eb14(diag),0.0.ab1c(ro:diag)"
DASD="eb1c,0.0.a000-0.0.a003,eb10-eb14(diag),0.0.ab1c(ro:diag)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow For FCP-only environments, remove theDASD=option from the CMS configuration file to indicate no DASD is present. FCP_n="device_bus_ID WWPN FCP_LUN"- Where:
- n is typically an integer value (for example
FCP_1orFCP_2) but could be any string with alphabetic or numeric characters or underscores. - device_bus_ID specifies the device bus ID of the FCP device representing the host bus adapter (HBA) (for example
0.0.fc00for device fc00). - WWPN is the world wide port name used for routing (often in conjunction with multipathing) and is as a 16-digit hex value (for example
0x50050763050b073d). - FCP_LUN refers to the storage logical unit identifier and is specified as a 16-digit hexadecimal value padded with zeroes to the right (for example
0x4020400100000000).
These variables can be used on systems with FCP devices to activate FCP LUNs such as SCSI disks. Additional FCP LUNs can be activated during the installation interactively or by means of a Kickstart file. An example value looks similar to the following:FCP_1="0.0.fc00 0x50050763050b073d 0x4020400100000000"
FCP_1="0.0.fc00 0x50050763050b073d 0x4020400100000000"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Important
Each of the values used in the FCP parameters (for exampleFCP_1orFCP_2) are site-specific and are normally supplied by the FCP storage administrator.
21.4. Parameters for Kickstart Installations
inst.ks=URL- References a Kickstart file, which usually resides on the network for Linux installations on IBM Z. Replace URL with the full path including the file name of the Kickstart file. This parameter activates automatic installation with Kickstart. See Kickstart Boot Options and Section 27.2.5, “Starting the Kickstart Installation” for more details.
RUNKS=valueImportant
This parameter is deprecated. If you use it in a Kickstart file, it will be ignored. Only theinst.ks=parameter is necessary to start a Kickstart installation on IBM Z.Where value is defined as 1 if you want to run the loader automatically on the Linux console without having to log in over the network with SSH. To useRUNKS=1, the console must either support full-screen or theinst.cmdlineoption (below) should be used. The latter applies for the 3270 terminal under z/VM or the operating system messages console for LPAR. We recommendRUNKS=1for fully automatic installations with Kickstart. WhenRUNKS=1is set, the installation program automatically continues in case of parameter errors and does not interrupt unattended installations by prompting for user interaction.Leave out the parameter or specifyRUNKS=0otherwise.inst.cmdline- When this option is specified, output on line-mode terminals (such as 3270 under z/VM or operating system messages for LPAR) becomes readable, as the installation program disables escape terminal sequences that are only applicable to UNIX-like consoles. This requires installation with a Kickstart file that answers all questions, because the installation program does not support interactive user input in cmdline mode.
inst.cmdline option. If a required command is missing, the installation will fail. See Chapter 27, Kickstart Installations for details.
21.5. Miscellaneous Parameters
rd.live.check- Turns on testing of an ISO-based installation source; for example, when booted from an FCP-attached DVD or using
inst.repo=with an ISO on local hard disk or mounted with NFS. nompath- Disables support for multipath devices.
proxy=[protocol://][username[:password]@]host[:port]- Specify a proxy to use with installation over HTTP, HTTPS, or FTP.
inst.rescue- Boot into a rescue system running from a RAM disk that can be used to fix and restore an installed system.
inst.stage2=URL- Specifies a path to an
install.imgfile instead of to an installation source. Otherwise, follows the same syntax asinst.repo=. Ifinst.stage2is specified, it typically takes precedence over other methods of findinginstall.img. However, if Anaconda findsinstall.imgon local media, theinst.stage2URL will be ignored.Ifinst.stage2is not specified andinstall.imgcannot be found locally, Anaconda looks to the location given byinst.repo=ormethod=.If onlyinst.stage2=is given withoutinst.repo=ormethod=, Anaconda uses whatever repos the installed system would have enabled by default for installation.Use the option multiple times to specify multiple HTTP, HTTPS or FTP sources. The HTTP, HTTPS or FTP paths are then tried sequentially until one succeeds:inst.stage2=host1/install.img inst.stage2=host2/install.img inst.stage3=host3/install.img
inst.stage2=host1/install.img inst.stage2=host2/install.img inst.stage3=host3/install.imgCopy to Clipboard Copied! Toggle word wrap Toggle overflow inst.syslog=IP/hostname[:port]- Sends log messages to a remote syslog server.
21.6. Sample Parameter File and CMS Configuration File
generic.prm file.
generic.prm file:
ro ramdisk_size=40000 cio_ignore=all,!condev CMSDASD="191" CMSCONFFILE="redhat.conf" vnc inst.repo=http://example.com/path/to/repository
ro ramdisk_size=40000 cio_ignore=all,!condev
CMSDASD="191" CMSCONFFILE="redhat.conf"
vnc
inst.repo=http://example.com/path/to/repositoryredhat.conf file configuring a QETH network device (pointed to by CMSCONFFILE in generic.prm):
Chapter 22. IBM Z References
22.1. IBM Z Publications
Linux on System z - How to use FC-attached SCSI devices with Linux on System z9 and zSeries. 2008. SC33-8413.
Linux on System z - How to Improve Performance with PAV. 2008. SC33-8414.
z/VM - Getting Started with Linux on System z. 2009. SC24-6194.
22.2. IBM Redbooks Publications for IBM Z
Introductory publications
Introduction to the New Mainframe: z/VM Basics. 2007. SG24-7316.
Practical Migration to Linux on System z. 2009. SG24-7727.
Performance and high availability
Linux on IBM System z: Performance Measurement and Tuning. 2011. SG24-6926.
Achieving High Availability on Linux for System z with Linux-HA Release 2. 2009. SG24-7711.
Security
Security for Linux on System z. 2013. SG24-7728.
Networking
IBM System z Connectivity Handbook. 2013. SG24-5444.
OSA Express Implementation Guide. 2009. SG24-5948.
HiperSockets Implementation Guide. 2007. SG24-6816.
Fibre Channel Protocol for Linux and z/VM on IBM System z. 2007. SG24-7266.
22.3. Online Resources
For z/VM publications, refer to http://www.vm.ibm.com/library/ .
For IBM Z I/O connectivity information, refer to http://www.ibm.com/systems/z/hardware/connectivity/index.html .
For IBM Z cryptographic coprocessor information, refer to http://www.ibm.com/security/cryptocards/ .
For IBM Z DASD storage information, refer to http://www-01.ibm.com/support/knowledgecenter/linuxonibm/com.ibm.linux.z.lgdd/lgdd_t_dasd_wrk.html .
Part IV. Advanced Installation Options
- customizing the installation program's behavior by specifying boot options
- setting up a PXE server to boot the installation program over a network
- installing with remote access through VNC
- using a Kickstart file to automate the installation process
- installing into a disk image instead of a physical drive
- upgrading a previous release of Red Hat Enterprise Linux to the current version
Chapter 23. Boot Options
- Options presented as ending with an "equals" sign (
=) require a value to be specified - they cannot be used on their own. For example, theinst.vncpassword=option must also contain a value (in this case, a password). The correct form is thereforeinst.vncpassword=password. On its own, without a password specified, the option is invalid. - Options presented without the "
=" sign do not accept any values or parameters. For example, therd.live.checkoption forces Anaconda to verify the installation media before starting the installation; if this option is present, the check will be performed, and if it is not present, the check will be skipped.
23.1. Configuring the Installation System at the Boot Menu
Note
- Section 7.2, “The Boot Menu” for 64-bit AMD, Intel and ARM systems
- Section 12.1, “The Boot Menu” for IBM Power Systems servers
- The
boot:prompt, accessed by pressing the Esc key anywhere in the boot menu. When using this prompt, the first option must always specify the installation program image file to be loaded. In most cases, the image can be specified using thelinuxkeyword. After that, additional options can be specified as needed.Pressing the Tab key at this prompt will display help in the form of usable commands where applicable. To start the installation with your options, press the Enter key. To return from theboot:prompt to the boot menu, restart the computer and boot from the installation media again. - The
>prompt on BIOS-based AMD64 and Intel 64 systems, accessed by highlighting an entry in the boot menu and pressing the Tab key. Unlike theboot:prompt, this prompt allows you to edit a predefined set of boot options. For example, if you highlight the entry labeled , a full set of options used by this menu entry will be displayed on the prompt, allowing you to add your own options.Pressing Enter will start the installation using the options you specified. To cancel editing and return to the boot menu, press the Esc key at any time. - The GRUB2 menu on UEFI-based 64-bit AMD, Intel and ARM systems. If your system uses UEFI, you can edit boot options by highlighting an entry and pressing the e key. When you finish editing, press F10 or Ctrl+X to start the installation using the options you specified.
dracut.cmdline(7) man page.
Note
inst. in this guide. Currently, this prefix is optional, for example, resolution=1024x768 will work exactly the same as inst.resolution=1024x768. However, it is expected that the inst. prefix will be mandatory in future releases.
Specifying the Installation Source
inst.repo=- Specifies the installation source - that is, a location where the installation program can find the images and packages it requires. For example:
inst.repo=cdrom
inst.repo=cdromCopy to Clipboard Copied! Toggle word wrap Toggle overflow The target must be either:- an installable tree, which is a directory structure containing the installation program's images, packages and repodata as well as a valid
.treeinfofile - a DVD (a physical disk present in the system's DVD drive)
- an ISO image of the full Red Hat Enterprise Linux installation DVD, placed on a hard drive or a network location accessible from the installation system (requires specifying NFS Server as the installation source)
This option allows for the configuration of different installation methods using different formats. The syntax is described in the table below.Expand Table 23.1. Installation Sources Installation source Option format Any CD/DVD drive inst.repo=cdromSpecific CD/DVD drive inst.repo=cdrom:deviceHard Drive inst.repo=hd:device:/pathHMC inst.repo=hmcHTTP Server inst.repo=http://host/pathHTTPS Server inst.repo=https://host/pathFTP Server inst.repo=ftp://username:password@host/pathNFS Server inst.repo=nfs:[options:]server:/path[a][a] This option uses NFS protocol version 3 by default. To use a different version, addnfsvers=Xto options, replacing X with the version number that you want to use.Note
In previous releases of Red Hat Enterprise Linux, there were separate options for an installable tree accessible by NFS (thenfsoption) and an ISO image located on an NFS source (thenfsisooption). In Red Hat Enterprise Linux 7, the installation program can automatically detect whether the source is an installable tree or a directory containing an ISO image, and thenfsisooption is deprecated.Disk device names can be set using the following formats:- Kernel device name, for example
/dev/sda1orsdb2 - File system label, for example
LABEL=FlashorLABEL=RHEL7 - File system UUID, for example
UUID=8176c7bf-04ff-403a-a832-9557f94e61db
Non-alphanumeric characters must be represented as\xNN, where NN is the hexadecimal representation of the character. For example,\x20is a white space (" inst.stage2=- Specifies the location of the installation program runtime image to be loaded. The syntax is the same as in Specifying the Installation Source. This option expects a path to a directory containing a valid
.treeinfofile; the location of the runtime image will be read from this file if found. If a.treeinfofile is not available, Anaconda will try to load the image fromLiveOS/squashfs.img.Use the option multiple times to specify multiple HTTP, HTTPS or FTP sources.inst.stage2=host1/install.img inst.stage2=host2/install.img inst.stage2=host3/install.img
inst.stage2=host1/install.img inst.stage2=host2/install.img inst.stage2=host3/install.imgCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
By default, theinst.stage2=boot option is used on the installation media and set to a specific label (for example,inst.stage2=hd:LABEL=RHEL7\x20Server.x86_64). If you modify the default label of the file system containing the runtime image, or if you use a customized procedure to boot the installation system, you must ensure this option is set to the correct value. inst.dd=- If you need to perform a driver update during the installation, use the
inst.dd=option. It can be used multiple times. The location of a driver RPM package can be specified using any of the formats detailed in Specifying the Installation Source. With the exception of theinst.dd=cdromoption, the device name must always be specified. For example:inst.dd=/dev/sdb1
inst.dd=/dev/sdb1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Using this option without any parameters (only asinst.dd) will prompt the installation program to ask you for a driver update disk with an interactive menu.Driver disks can also be loaded from a hard disk drive or a similar device instead of being loaded over the network or frominitrd. Follow this procedure:- Load the driver disk on a hard disk drive, a USB or any similar device.
- Set the label, for example, DD, to this device.
- Start the installation with:as the boot argument.
inst.dd=hd:LABEL=DD:/dd.rpm
inst.dd=hd:LABEL=DD:/dd.rpmCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Replace DD with a specific label and replace dd.rpm with a specific name. Use anything supported by theinst.repocommand instead of LABEL to specify your hard disk drive.For more information about driver updates during the installation, see Chapter 6, Updating Drivers During Installation on AMD64 and Intel 64 Systems for AMD64 and Intel 64 systems and Chapter 11, Updating Drivers During Installation on IBM Power Systems for IBM Power Systems servers.
Kickstart Boot Options
inst.ks=- Gives the location of a Kickstart file to be used to automate the installation. Locations can be specified using any of the formats valid for
inst.repo. See Specifying the Installation Source for details.Use the option multiple times to specify multiple HTTP, HTTPS and FTP sources. If multiple HTTP, HTTPS and FTP locations are specified, the locations are tried sequentially until one succeeds:inst.ks=host1/directory/ks.cfg inst.ks=host2/directory/ks.cfg inst.ks=host3/directory/ks.cfg
inst.ks=host1/directory/ks.cfg inst.ks=host2/directory/ks.cfg inst.ks=host3/directory/ks.cfgCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you only specify a device and not a path, the installation program will look for the Kickstart file in/ks.cfgon the specified device. If you use this option without specifying a device, the installation program will use the following:inst.ks=nfs:next-server:/filename
inst.ks=nfs:next-server:/filenameCopy to Clipboard Copied! Toggle word wrap Toggle overflow In the above example, next-server is the DHCPnext-serveroption or the IP address of the DHCP server itself, and filename is the DHCPfilenameoption, or/kickstart/. If the given file name ends with the/character,ip-kickstartis appended. For example:Expand Table 23.2. Default Kickstart File Location DHCP server address Client address Kickstart file location 192.168.122.1192.168.122.100192.168.122.1:/kickstart/192.168.122.100-kickstartAdditionally, starting with Red Hat Enterprise Linux 7.2, the installer will attempt to load a Kickstart file namedks.cfgfrom a volume with a label ofOEMDRVif present. If your Kickstart file is in this location, you do not need to use theinst.ks=boot option at all. inst.ks.sendmac- Adds headers to outgoing
HTTPrequests with the MAC addresses of all network interfaces. For example:X-RHN-Provisioning-MAC-0: eth0 01:23:45:67:89:ab
X-RHN-Provisioning-MAC-0: eth0 01:23:45:67:89:abCopy to Clipboard Copied! Toggle word wrap Toggle overflow This can be useful when usinginst.ks=httpto provision systems. inst.ks.sendsn- Adds a header to outgoing
HTTPrequests. This header will contain the system's serial number, read from/sys/class/dmi/id/product_serial. The header has the following syntax:X-System-Serial-Number: R8VA23D
X-System-Serial-Number: R8VA23DCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Console, Environment and Display Options
console=- This kernel option specifies a device to be used as the primary console. For example, to use a console on the first serial port, use
console=ttyS0. This option should be used along with theinst.textoption.You can use this option multiple times. In that case, the boot message will be displayed on all specified consoles, but only the last one will be used by the installation program afterwards. For example, if you specifyconsole=ttyS0 console=ttyS1, the installation program will usettyS1. noshell- Disables access to the root shell during the installation. This is useful with automated (Kickstart) installations - if you use this option, a user can watch the installation progress, but they cannot interfere with it by accessing the root shell by pressing Ctrl+Alt+F2.
inst.lang=- Sets the language to be used during the installation. Language codes are the same as the ones used in the
langKickstart command as described in Section 27.3.1, “Kickstart Commands and Options”. On systems where the system-config-language package is installed, a list of valid values can also be found in/usr/share/system-config-language/locale-list. inst.geoloc=- Configures geolocation usage in the installation program. Geolocation is used to preset the language and time zone, and uses the following syntax:
inst.geoloc=valueThe value parameter can be any of the following:Expand Table 23.3. Valid Values for the inst.geoloc Option Disable geolocation inst.geoloc=0Use the Fedora GeoIP API inst.geoloc=provider_fedora_geoipUse the Hostip.info GeoIP API inst.geoloc=provider_hostipIf this option is not specified, Anaconda will useprovider_fedora_geoip. inst.keymap=- Specifies the keyboard layout to be used by the installation program. Layout codes are the same as the ones used in the
keyboardKickstart command as described in Section 27.3.1, “Kickstart Commands and Options”. inst.text- Forces the installation program to run in text mode instead of graphical mode. The text user interface is limited, for example, it does not allow you to modify the partition layout or set up LVM. When installing a system on a machine with a limited graphical capabilities, it is recommended to use VNC as described in Enabling Remote Access.
inst.cmdline- Forces the installation program to run in command line mode. This mode does not allow any interaction, all options must be specified in a Kickstart file or on the command line.
inst.graphical- Forces the installation program to run in graphical mode. This mode is the default.
inst.resolution=- Specifies the screen resolution in graphical mode. The format is NxM, where N is the screen width and M is the screen height (in pixels). The lowest supported resolution is
800x600. inst.headless- Specifies that the machine being installed onto does not have any display hardware. In other words, this option prevents the installation program from trying to detect a screen.
inst.xdriver=- Specifies the name of the
Xdriver to be used both during the installation and on the installed system. inst.usefbx- Tells the installation program to use the frame buffer
Xdriver instead of a hardware-specific driver. This option is equivalent toinst.xdriver=fbdev. modprobe.blacklist=- Blacklists (completely disables) one or more drivers. Drivers (mods) disabled using this option will be prevented from loading when the installation starts, and after the installation finishes, the installed system will keep these settings. The blacklisted drivers can then be found in the
/etc/modprobe.d/directory.Use a comma-separated list to disable multiple drivers. For example:modprobe.blacklist=ahci,firewire_ohci
modprobe.blacklist=ahci,firewire_ohciCopy to Clipboard Copied! Toggle word wrap Toggle overflow inst.sshd=0- By default,
sshdis only automatically started on IBM Z, and on other architectures,sshdis not started unless theinst.sshdoption is used. This option preventssshdfrom starting automatically on IBM Z. inst.sshd- Starts the
sshdservice during the installation, which allows you to connect to the system during the installation usingSSHand monitor its progress. For more information on SSH, see thessh(1)man page and the corresponding chapter in the Red Hat Enterprise Linux 7 System Administrator's Guide. By default,sshdis only automatically started on IBM Z, and on other architectures,sshdis not started unless theinst.sshdoption is used.Note
During the installation, therootaccount has no password by default. You can set a root password to be used during the installation with thesshpwKickstart command as described in Section 27.3.1, “Kickstart Commands and Options”. inst.kdump_addon=- Enables or disables the Kdump configuration screen (add-on) in the installer. This screen is enabled by default; use
inst.kdump_addon=offto disable it. Note that disabling the add-on will disable the Kdump screens in both the graphical and text-based interface as well as the%addon com_redhat_kdumpKickstart command.
Network Boot Options
dracut.cmdline(7) man page. Additional information on networking is also available in Red Hat Enterprise Linux 7 Networking Guide.
ip=- Configures one or more network interfaces. To configure multiple interfaces, you can use the
ipoption multiple times - once for each interface. If multiple interfaces are configured, you must also use the optionrd.neednet=1, and you must specify a primary boot interface using thebootdevoption, described below. Alternatively, you can use theipoption once, and then use Kickstart to set up further interfaces.This option accepts several different formats. The most common are described in Table 23.4, “Network Interface Configuration Formats”.Expand Table 23.4. Network Interface Configuration Formats Configuration Method Option format Automatic configuration of any interface ip=methodAutomatic configuration of a specific interface ip=interface:methodStatic configuration ip=ip::gateway:netmask:hostname:interface:noneAutomatic configuration of a specific interface with an override [a] ip=ip::gateway:netmask:hostname:interface:method:mtu[a] Brings up the specified interface using the specified method of automatic configuration, such asdhcp, but overrides the automatically obtained IP address, gateway, netmask, host name or other specified parameter. All parameters are optional; only specify the ones you want to override and automatically obtained values will be used for the others.Themethodparameter can be any the following:Expand Table 23.5. Automatic Interface Configuration Methods Automatic configuration method Value DHCP dhcpIPv6 DHCP dhcp6IPv6 automatic configuration auto6iBFT (iSCSI Boot Firmware Table) ibftNote
If you use a boot option which requires network access, such asinst.ks=http://host/path, without specifying theipoption, the installation program will useip=dhcp.Important
To connect automatically to an iSCSI target, a network device for accessing the target needs to be activated. The recommended way to do so is to useip=ibftboot option.In the above tables, the ip parameter specifies the client's IP address.IPv6addresses can be specified by putting them in square brackets, for example,[2001:DB8::1].The gateway parameter is the default gateway. IPv6 addresses are accepted here as well.The netmask parameter is the netmask to be used. This can either be a full netmask for IPv4 (for example255.255.255.0) or a prefix for IPv6 (for example64).The hostname parameter is the host name of the client system. This parameter is optional. nameserver=- Specifies the address of the name server. This option can be used multiple times.
rd.neednet=- You must use the option
rd.neednet=1if you use more than oneipoption. Alternatively, to set up multiple network interfaces you can use theiponce, and then set up further interfaces using Kickstart. bootdev=- Specifies the boot interface. This option is mandatory if you use more than one
ipoption. ifname=- Assigns a given interface name to a network device with a given MAC address. Can be used multiple times. The syntax is
ifname=interface:MAC. For example:ifname=eth0:01:23:45:67:89:ab
ifname=eth0:01:23:45:67:89:abCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Using theifname=option is the only supported way to set custom network interface names during installation. inst.dhcpclass=- Specifies the DHCP vendor class identifier. The
dhcpdservice will see this value asvendor-class-identifier. The default value isanaconda-$(uname -srm). inst.waitfornet=- Using the inst.waitfornet=SECONDS boot option causes the installation system to wait for network connectivity before installation. The value given in the SECONDS argument specifies maximum amount of time to wait for network connectivity before timing out and continuing the installation process even if network connectivity is not present.
vlan=- Sets up a Virtual LAN (VLAN) device on a specified interface with a given name. The syntax is
vlan=name:interface. For example:vlan=vlan5:em1
vlan=vlan5:em1Copy to Clipboard Copied! Toggle word wrap Toggle overflow The above will set up a VLAN device namedvlan5on theem1interface. The name can take the following forms:Expand Table 23.6. VLAN Device Naming Conventions Naming scheme Example VLAN_PLUS_VID vlan0005VLAN_PLUS_VID_NO_PAD vlan5DEV_PLUS_VID em1.0005.DEV_PLUS_VID_NO_PAD em1.5. bond=- Set up a bonding device with the following syntax:
bond=name[:slaves][:options]. Replace name with the bonding device name, slaves with a comma-separated list of physical (ethernet) interfaces, and options with a comma-separated list of bonding options. For example:bond=bond0:em1,em2:mode=active-backup,tx_queues=32,downdelay=5000
bond=bond0:em1,em2:mode=active-backup,tx_queues=32,downdelay=5000Copy to Clipboard Copied! Toggle word wrap Toggle overflow For a list of available options, execute themodinfo bondingcommand.Using this option without any parameters will assumebond=bond0:eth0,eth1:mode=balance-rr. team=- Set up a team device with the following syntax:
team=master:slaves. Replace master with the name of the master team device and slaves with a comma-separated list of physical (ethernet) devices to be used as slaves in the team device. For example:team=team0:em1,em2
team=team0:em1,em2Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Advanced Installation Options
inst.kexec- If this option is specified, the installer will use the kexec system call at the end of the installation, instead of performing a reboot. This loads the new system immediately, and bypasses the hardware initialization normally performed by the BIOS or firmware.
Important
Due to the complexities involved with booting systems using kexec, it cannot be explicitly tested and guaranteed to function in every situation.When kexec is used, device registers (which would normally be cleared during a full system reboot) might stay filled with data, which could potentially create issues for some device drivers. inst.gpt- Force the installation program to install partition information into a GUID Partition Table (GPT) instead of a Master Boot Record (MBR). This option is meaningless on UEFI-based systems, unless they are in BIOS compatibility mode.Normally, BIOS-based systems and UEFI-based systems in BIOS compatibility mode will attempt to use the MBR schema for storing partitioning information, unless the disk is 232 sectors in size or larger. Most commonly, disk sectors are 512 bytes in size, meaning that this is usually equivalent to 2 TiB. Using this option will change this behavior, allowing a GPT to be written to disks smaller than this.See Section 8.14.1.1, “MBR and GPT Considerations” for more information about GPT and MBR, and Section A.1.4, “GUID Partition Table (GPT)” for more general information about GPT, MBR and disk partitioning in general.
inst.multilib- Configure the system for multilib packages (that is, to allow installing 32-bit packages on a 64-bit AMD64 or Intel 64 system) and install packages specified in this section as such.Normally, on an AMD64 or Intel 64 system, only packages for this architecture (marked as
x86_64) and packages for all architectures (marked asnoarchwould be installed. When you use this option, packages for 32-bit AMD or Intel systems (marked asi686) will be automatically installed as well if available.This only applies to packages directly specified in the%packagessection. If a package is only installed as a dependency, only the exact specified dependency will be installed. For example, if you are installing package bash which depends on package glibc, the former will be installed in multiple variants, while the latter will only be installed in variants specifically required. selinux=0- By default, SELinux operates in
permissivemode in the installer, and inenforcingmode in the installed system. This option disables the use of SELinux in the installer and the installed system entirely.Note
Theselinux=0andinst.selinux=0options are not the same. Theselinux=0option disables the use of SELinux in the installer and the installed system, whereasinst.selinux=0disables SELinux only in the installer. By default, SELinux is set to operate inpermissivemode in the installer, so disabling it has little effect. inst.nosave=- This option, introduced in Red Hat Enterprise Linux 7.3, controls which Kickstart files and installation logs are saved to the installed system. It can be especially useful to disable saving such data when performing OEM operating system installations, or when generating images using sensitive resources (such as internal repository URLs), as these resources might otherwise be mentioned in kickstart files, or in logs on the image, or both. Possible values for this option are:
input_ks- disables saving of the input Kickstart file (if any).output_ks- disables saving of the output Kickstart file generated by Anaconda.all_ks- disables saving of both input and output Kickstart files.logs- disables saving of all installation logs.all- disables saving of all Kickstart files and all installation logs.Multiple values can be combined as a comma separated list, for example:input_ks,logs inst.zram- This option controls the usage of zRAM swap during the installation. It creates a compressed block device inside the system RAM and uses it for swap space instead of the hard drive. This allows the installer to essentially increase the amount of memory available, which makes the installation faster on systems with low memory.By default, swap on zRAM is enabled on systems with 2 GiB or less RAM, and disabled on systems with more than 2 GiB of memory. You can use this option to change this behavior - on a system with more than 2 GiB RAM, use
inst.zram=1to enable it, and on systems with 2 GiB or less memory, useinst.zram=0to disable this feature.
Enabling Remote Access
inst.vnc- Specifies that the installation program's graphical interface should be run in a
VNCsession. If you specify this option, you will need to connect to the system using a VNC client application to be able to interact with the installation program. VNC sharing is enabled, so multiple clients can connect to the system at the same time.Note
A system installed using VNC will start in text mode by default. inst.vncpassword=- Sets a password on the VNC server used by the installation program. Any VNC client attempting to connecting to the system will have to provide the correct password to gain access. For example,
inst.vncpassword=testpwdwill set the password totestpwd. The VNC password must be between 6 and 8 characters long.Note
If you specify an invalid password (one that is too short or too long), you will be prompted to specify a new one by a message from the installation program:VNC password must be six to eight characters long. Please enter a new one, or leave blank for no password. Password:
VNC password must be six to eight characters long. Please enter a new one, or leave blank for no password. Password:Copy to Clipboard Copied! Toggle word wrap Toggle overflow inst.vncconnect=- Connect to a listening VNC client at a specified host and port once the installation starts. The correct syntax is
inst.vncconnect=host:port, where host is the address to the VNC client's host, and port specifies which port to use. The port parameter is optional, if you do not specify one, the installation program will use5900.
Debugging and Troubleshooting
inst.updates=- Specifies the location of the
updates.imgfile to be applied to the installation program runtime. The syntax is the same as in theinst.repooption - see Table 23.1, “Installation Sources” for details. In all formats, if you do not specify a file name but only a directory, the installation program will look for a file namedupdates.img. inst.loglevel=- Specifies the minimum level for messages to be logged on a terminal. This only concerns terminal logging; log files will always contain messages of all levels.Possible values for this option from the lowest to highest level are:
debug,info,warning,errorandcritical. The default value isinfo, which means that by default, the logging terminal will display messages ranging frominfotocritical. inst.syslog=- Once the installation starts, this option sends log messages to the syslog process on the specified host. The remote syslog process must be configured to accept incoming connections. For information on how to configure a syslog service to accept incoming connections, see the Red Hat Enterprise Linux 7 System Administrator's Guide.
inst.virtiolog=- Specifies a
virtioport (a character device at/dev/virtio-ports/name) to be used for forwarding logs. The default value isorg.fedoraproject.anaconda.log.0; if this port is present, it will be used. rd.live.ram- If this option is specified, the stage 2 image will be copied into RAM. When the stage2 image on NFS repository is used, this option may make the installation proceed smoothly, since the installation is sometimes affected by reconfiguring network in an environment built upon the stage 2 image on NFS.Note that using this option when the stage 2 image is on an NFS server will increase the minimum required memory by the size of the image - roughly 500 MiB.
inst.nokill- A debugging option that prevents anaconda from and rebooting when a fatal error occurs or at the end of the installation process. This allows you to capture installation logs which would be lost upon reboot.
23.1.1. Deprecated and Removed Boot Options
Deprecated Boot Options
Note
inst. prefix. For example, the vnc= option is considered deprecated and replaced by the inst.vnc= option. These changes are not listed here.
method=- Configured the installation method. Use the
inst.repo=option instead. repo=nfsiso:server:/path- In NFS installations, specified that the target is an ISO image located on an NFS server instead of an installable tree. The difference is now detected automatically, which means this option is the same as
inst.repo=nfs:server:/path. dns=- Configured the Domain Name Server (DNS). Use the
nameserver=option instead. netmask=,gateway=,hostname=,ip=,ipv6=- These options have been consolidated under the
ip=option. ksdevice=- Select network device to be used at early stage of installation. Different values have been replaced with different options; see the table below.
Expand Table 23.7. Automatic Interface Configuration Methods Value Current behavior Not present Activation of all devices is attempted using dhcp, unless the desired device and configuration is specified by theip=option or theBOOTIFoption.ksdevice=linkSimilar to the above, with the difference that network will always be activated in the initramfs, whether it is needed or not. The supported rd.neednetdracut option should be used to achieve the same result.ksdevice=bootifIgnored (the BOOTIF= option is used by default when specified) ksdevice=ibftReplaced with the ip=ibftdracut optionksdevice=MACReplaced with BOOTIF=MACksdevice=deviceReplaced by specifying the device name using the ip=dracut option. blacklist=- Used to disable specified drivers. This is now handled by the
modprobe.blacklist=option. nofirewire=- Disabled support for the FireWire interface. You can disable the FireWire driver (
firewire_ohci) by using themodprobe.blacklist=option instead:modprobe.blacklist=firewire_ohci
modprobe.blacklist=firewire_ohciCopy to Clipboard Copied! Toggle word wrap Toggle overflow nicdelay=- Used to indicate the delay after which the network was considered active; the system waited until either the gateway was successfully pinged, or until the amount of seconds specified in this parameter passed. In RHEL 7, network devices are configured and activated during the early stage of installation by the dracut modules which ensure that the gateway is accessible before proceeding. For more information about dracut, see the
dracut.cmdline(7)man page. linksleep=- Used to configure how long anaconda should wait for a link on a device before activating it. This functionality is now available in the dracut modules where specific
rd.net.timeout.*options can be configured to handle issues caused by slow network device initialization. For more information about dracut, see thedracut.cmdline(7)man page.
Removed Boot Options
askmethod,asknetwork- The installation program's
initramfsis now completely non-interactive, which means that these options are not available anymore. Instead, use theinst.repo=to specify the installation method andip=to configure network settings. serial- This option forced Anaconda to use the
/dev/ttyS0console as the output. Use theconsole=/dev/ttyS0(or similar) instead. updates=- Specified the location of updates for the installation program. Use the
inst.updates=option instead. essid=,wepkey=,wpakey=- Configured wireless network access. Network configuration is now being handled by dracut, which does not support wireless networking, rendering these options useless.
ethtool=- Used in the past to configure additional low-level network settings. All network settings are now handled by the
ip=option. gdb- Allowed you to debug the loader. Use
rd.debuginstead. mediacheck- Verified the installation media before starting the installation. Replaced with the
rd.live.checkoption. ks=floppy- Specified a 3.5 inch diskette as the Kickstart file source. These drives are not supported anymore.
display=- Configured a remote display. Replaced with the
inst.vncoption. utf8- Added UTF8 support when installing in text mode. UTF8 support now works automatically.
noipv6- Used to disable IPv6 support in the installation program. IPv6 is now built into the kernel so the driver cannot be blacklisted; however, it is possible to disable IPv6 using the
ipv6.disabledracut option. upgradeany- Upgrades are done in a different way in Red Hat Enterprise Linux 7. For more information about upgrading your system, see Chapter 29, Upgrading Your Current System.
vlanid=- Used to configure Virtual LAN (802.1q tag) devices. Use the
vlan=dracut option instead.
23.2. Using the Maintenance Boot Modes
23.2.1. Loading the Memory (RAM) Testing Mode
Note
Figure 23.1. Memory Check Using Memtest86+
- The upper left corner shows information about your system's memory configuration - the amount of detected memory and processor cache and their throughputs and processor and chipset information. This information is detected when Memtest86+ starts.
- The upper right corner displays information about the tests - progress of the current pass and the currently running test in that pass as well as a description of the test.
- The central part of the screen is used to display information about the entire set of tests from the moment when the tool has started, such as the total time, the number of completed passes, number of detected errors and your test selection. On some systems, detailed information about the installed memory (such as the number of installed modules, their manufacturer, frequency and latency) will be also displayed here. After the each pass completes, a short summary will appear in this location. For example:
** Pass complete, no errors, press Esc to exit **
** Pass complete, no errors, press Esc to exit **Copy to Clipboard Copied! Toggle word wrap Toggle overflow If Memtest86+ detects an error, it will also be displayed in this area and highlighted red. The message will include detailed information such as which test detected a problem, the memory location which is failing, and others.
Note
README file is also located in /usr/share/doc/memtest86+-version/ on Red Hat Enterprise Linux systems with the memtest86+ package installed.
23.2.2. Verifying Boot Media
rd.live.check to the boot loader command line. Note that this option is used automatically if you select the default installation option from the boot menu ().
23.2.3. Booting Your Computer in Rescue Mode
inst.rescue boot option.
/mnt/sysimage/.
Chapter 24. Preparing for a Network Installation
Note
- A server - a system running a DHCP server, a TFTP server to provide boot files, and an HTTP, FTP or NFS server which hosts the installation image. Theoretically, each of the servers can run on a different physical system; procedures in this section assume a single system runs all of them for simplicity.
- A client - the system which you are installing Red Hat Enterprise Linux to. When the installation begins, the client will query the DHCP server, obtain boot files from the TFTP server, and download the installation image from the HTTP, FTP or NFS server.
- Configure the network server (
NFS,HTTPS,HTTP, orFTP) to export the installation tree or the installation ISO image. For procedures describing the configuration, see Section 3.3.3, “Installation Source on a Network”. - Configure the files on the tftp server necessary for network boot, configure
DHCP, and start thetftpservice on the PXE server. See Section 24.1, “Configuring Network Boot Services” for details.Important
The GRUB2 boot loader supports network boot fromHTTPin addition to a tftp server. However, obtaining boot files (the kernel and initial ram disk for the installer) over this protocol is very slow and suffers a risk of timeout failures. Using a tftp server to provide the boot files is recommended.This warning only applies to the kernel and initial ram disk (vmlinuzandinitrd). Obtaining the installation source from anHTTPserver does not carry this risk. - Boot the client (the system you want to install Red Hat Enterprise Linux on) and start the installation.
Note
24.1. Configuring Network Boot Services
DHCP server must be configured, and all necessary services must be enabled and started.
Note
24.1.1. Configuring a TFTP Server for BIOS-based AMD64 and Intel 64 Clients
Procedure 24.1. Configuring a TFTP Boot Server for BIOS-based Systems
- Install the tftp-server package. To do this, enter the following command as
root:yum install tftp-server
# yum install tftp-serverCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Allow incoming connections to the
tftpservice in the firewall:firewall-cmd --add-service=tftp
# firewall-cmd --add-service=tftpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
The above command only enables access until the next server reboot. To allow access permanently, add the--permanentoption. For more information about firewall configuration, see the Red Hat Enterprise Linux 7 Security Guide. - Configure your
DHCPserver to use the boot images packaged with SYSLINUX. If you do not have one installed, see the Red Hat Enterprise Linux 7 Networking Guide for instructions.A sample configuration in the/etc/dhcp/dhcpd.conffile might look like:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - You now need the
pxelinux.0file from the SYSLINUX package in the ISO image file of the full installation DVD. To access it, enter the following commands as root:mount -t iso9660 /path_to_image/name_of_image.iso /mount_point -o loop,ro
# mount -t iso9660 /path_to_image/name_of_image.iso /mount_point -o loop,roCopy to Clipboard Copied! Toggle word wrap Toggle overflow cp -pr /mount_point/Packages/syslinux-version-architecture.rpm /publicly_available_directory
# cp -pr /mount_point/Packages/syslinux-version-architecture.rpm /publicly_available_directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mount_point
# umount /mount_pointCopy to Clipboard Copied! Toggle word wrap Toggle overflow Extract the package:rpm2cpio syslinux-version-architecture.rpm | cpio -dimv
# rpm2cpio syslinux-version-architecture.rpm | cpio -dimvCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Create a
pxelinux/directory withintftpboot/and copy thepxelinux.0file into it:mkdir /var/lib/tftpboot/pxelinux
# mkdir /var/lib/tftpboot/pxelinuxCopy to Clipboard Copied! Toggle word wrap Toggle overflow cp publicly_available_directory/usr/share/syslinux/pxelinux.0 /var/lib/tftpboot/pxelinux
# cp publicly_available_directory/usr/share/syslinux/pxelinux.0 /var/lib/tftpboot/pxelinuxCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Create the directory
pxelinux.cfg/in thepxelinux/directory:mkdir /var/lib/tftpboot/pxelinux/pxelinux.cfg
# mkdir /var/lib/tftpboot/pxelinux/pxelinux.cfgCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a configuration file nameddefaultto thepxelinux.cfg/directory.A sample configuration file at/var/lib/tftpboot/pxelinux/pxelinux.cfg/defaultmight look like:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Important
Theinst.repo=Anaconda option, shown in the example above, must always be used to specify the installation program's image as well as the installation source. Without this option, the installation program will be unable to boot. For more information about boot options for Anaconda, see Section 23.1, “Configuring the Installation System at the Boot Menu”. - Create a subdirectory to store the boot image files within the
/var/lib/tftpboot/directory, and copy the boot image files to it. In this example, we use the directory/var/lib/tftpboot/pxelinux/images/RHEL-release_number/:mkdir -p /var/lib/tftpboot/pxelinux/images/RHEL-7.1/ cp /path_to_x86_64_images/pxeboot/{vmlinuz,initrd.img} /var/lib/tftpboot/pxelinux/images/RHEL-release_number/# mkdir -p /var/lib/tftpboot/pxelinux/images/RHEL-7.1/ # cp /path_to_x86_64_images/pxeboot/{vmlinuz,initrd.img} /var/lib/tftpboot/pxelinux/images/RHEL-release_number/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Finally, start and enable the services:
- The
dhcpdservice:systemctl start dhcpd systemctl enable dhcpd
# systemctl start dhcpd # systemctl enable dhcpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - The
xinetdservice, that manages the tftpd service:systemctl start xinetd systemctl enable xinetd
# systemctl start xinetd # systemctl enable xinetdCopy to Clipboard Copied! Toggle word wrap Toggle overflow
24.1.2. Configuring a TFTP Server for UEFI-based AMD64/Intel 64 and ARM Clients
Procedure 24.2. Configuring TFTP Boot for UEFI-based Systems
Note
grub.cfg-01-aa-bb-cc-dd-ee-ff
- Install the tftp-server package. To do this, enter the following command as
root:yum install tftp-server
# yum install tftp-serverCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Allow incoming connections to the
tftpservice in the firewall:firewall-cmd --add-service=tftp
# firewall-cmd --add-service=tftpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
The above command only enables access until the next server reboot. To allow access permanently, add the--permanentoption. For more information about firewall configuration, see the Red Hat Enterprise Linux 7 Security Guide. - Configure your
DHCPserver to use the EFI boot images packaged with shim. If you do not have one installed, see the Red Hat Enterprise Linux 7 Networking Guide for instructions.A sample configuration in the/etc/dhcp/dhcpd.conffile might look like:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - You now need the
shim.efifile from the shim package and thegrubx64.efifile from the grub2-efi package in the ISO image file. To access them, enter the following commands as root:mount -t iso9660 /path_to_image/name_of_image.iso /mount_point -o loop,ro
# mount -t iso9660 /path_to_image/name_of_image.iso /mount_point -o loop,roCopy to Clipboard Copied! Toggle word wrap Toggle overflow cp -pr /mount_point/Packages/shim-version-architecture.rpm /publicly_available_directory
# cp -pr /mount_point/Packages/shim-version-architecture.rpm /publicly_available_directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow cp -pr /mount_point/Packages/grub2-efi-version-architecture.rpm /publicly_available_directory
# cp -pr /mount_point/Packages/grub2-efi-version-architecture.rpm /publicly_available_directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mount_point
# umount /mount_pointCopy to Clipboard Copied! Toggle word wrap Toggle overflow Extract the packages:rpm2cpio shim-version-architecture.rpm | cpio -dimv
# rpm2cpio shim-version-architecture.rpm | cpio -dimvCopy to Clipboard Copied! Toggle word wrap Toggle overflow rpm2cpio grub2-efi-version-architecture.rpm | cpio -dimv
# rpm2cpio grub2-efi-version-architecture.rpm | cpio -dimvCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the EFI boot images from your boot directory:
cp publicly_available_directory/boot/efi/EFI/redhat/shim.efi /var/lib/tftpboot/
# cp publicly_available_directory/boot/efi/EFI/redhat/shim.efi /var/lib/tftpboot/Copy to Clipboard Copied! Toggle word wrap Toggle overflow cp publicly_available_directory/boot/efi/EFI/redhat/grubx64.efi /var/lib/tftpboot/
# cp publicly_available_directory/boot/efi/EFI/redhat/grubx64.efi /var/lib/tftpboot/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Add a configuration file named
grub.cfgto thetftpboot/directory. A sample configuration file at/var/lib/tftpboot/grub.cfgmight look like:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Important
Theinst.repo=Anaconda option, shown in the example above, must always be used to specify the installation program's image as well as the installation source. Without this option, the installation program will be unable to boot. For more information about boot options for Anaconda, see Section 23.1, “Configuring the Installation System at the Boot Menu”. - Create a subdirectory to store the boot image files within the
/var/lib/tftpboot/directory, and copy the boot image files to it. In this example, we use the directory/var/lib/tftpboot/images/RHEL-7.1/:mkdir -p /var/lib/tftpboot/images/RHEL-7.1/# cp /path_to_x86_64_images/pxeboot/{vmlinuz,initrd.img} /var/lib/tftpboot/images/RHEL-7.1/# mkdir -p /var/lib/tftpboot/images/RHEL-7.1/# cp /path_to_x86_64_images/pxeboot/{vmlinuz,initrd.img} /var/lib/tftpboot/images/RHEL-7.1/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Finally, start and enable the services:
- The
dhcpdservice:systemctl start dhcpd systemctl enable dhcpd
# systemctl start dhcpd # systemctl enable dhcpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - The
xinetdservice, that manages the tftpd service:systemctl start xinetd systemctl enable xinetd
# systemctl start xinetd # systemctl enable xinetdCopy to Clipboard Copied! Toggle word wrap Toggle overflow
24.1.3. Configuring Network Boot for IBM Power Systems Using GRUB2
Procedure 24.3. Configuring a Network Boot Server for IBM Power Systems Using GRUB2
- Install the tftp-server package. To do this, enter the following command as
root:yum install tftp-server
# yum install tftp-serverCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Allow incoming connections to the
tftpservice in the firewall:firewall-cmd --add-service=tftp
# firewall-cmd --add-service=tftpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
The above command only enables access until the next server reboot. To allow access permanently, add the--permanentoption. For more information about firewall configuration, see the Red Hat Enterprise Linux 7 Security Guide. - Create a GRUB2 network boot directory inside the tftp root:
grub2-mknetdir --net-directory=/var/lib/tftpboot Netboot directory for powerpc-ieee1275 created. Configure your DHCP server to point to /boot/grub2/powerpc-ieee1275/core.elf
# grub2-mknetdir --net-directory=/var/lib/tftpboot Netboot directory for powerpc-ieee1275 created. Configure your DHCP server to point to /boot/grub2/powerpc-ieee1275/core.elfCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note the command's output, which informs you about which file needs to be configured as thefilenamein yourDHCPconfiguration. This will become important further in the procedure. - Create a GRUB2 configuration file:
/var/lib/tftpboot/boot/grub2/grub.cfg. Thegrub.cfgsyntax is described in the Red Hat Enterprise Linux 7 System Administrator's Guide.Below is an example configuration file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Important
Theinst.repo=Anaconda option, shown in the example above, must always be used to specify the installation program's image as well as the installation source. Without this option, the installation program will be unable to boot. For more information about boot options for Anaconda, see Section 23.1, “Configuring the Installation System at the Boot Menu”. - Configure your
DHCPserver to use the boot images packaged with GRUB2. If you do not have one installed, see the Red Hat Enterprise Linux 7 Networking Guide for instructions.A sample configuration in the/etc/dhcp/dhcpd.conffile might look like:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Adjust the sample parameters (subnet,netmask,routers,fixed-addressandhardware ethernet) to fit your network configuration. Also note thefilenameparameter; this is the file name which was output by thegrub2-mknetdircommand earlier in the procedure. - Finally, start and enable the services:
- The
dhcpdservice:systemctl start dhcpd systemctl enable dhcpd
# systemctl start dhcpd # systemctl enable dhcpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - The
xinetdservice that manages the tftpd service:systemctl start xinetd systemctl enable xinetd
# systemctl start xinetd # systemctl enable xinetdCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 25. Using VNC
25.1. Installing a VNC Viewer
- TigerVNC - A basic viewer independent of your desktop environment. Installed as the tigervnc package.
- Vinagre - A viewer for the GNOME desktop environment. Installed as the vinagre package.
- KRDC - A viewer integrated with the KDE desktop environment. Installed as the kdenetwork-krdc package.
root:
yum install package
# yum install packageNote
25.2. Performing a VNC Installation
- Direct Mode
- In this mode, Anaconda is configured to start the installation and wait for a VNC viewer before proceeding. The IP address and port are displayed on the system being installed. Using this information, you can connect to the installation system from a different computer. For this reason you must have visual and interactive access to the system being installed.
- Connect Mode
- In this mode, the VNC viewer is started on the remote system in listening mode. The VNC viewer waits for an incoming connection on a specified port. Then, Anaconda is started and the host name and port number are provided using a boot option or a Kickstart command. When the installation begins, the installation program establishes a connection with the listening VNC viewer using the specified host name and port number. For this reason, your remote system must be able to accept incoming network connections.
Considerations for choosing a VNC installation mode
- Visual and Interactive access to the system
- If visual and interactive access to the system being installed is not available, then you must use Connect Mode.
- Network Connection Rules and Firewalls
- If the system being installed is not allowed inbound connections by a firewall, then you must use Connect Mode or disable the firewall. Disabling a firewall can have security implications.
- If the remote system running the VNC viewer is not allowed incoming connections by a firewall, then you must use Direct Mode, or disable the firewall. Disabling a firewall can have security implications. See the Red Hat Enterprise Linux 7 Security Guide for information about configuring the firewall.
Note
- Section 7.2, “The Boot Menu” for 64-bit AMD, Intel, and ARM systems
- Section 12.1, “The Boot Menu” for IBM Power Systems servers
25.2.1. Installing in VNC Direct Mode
Procedure 25.1. Starting VNC in Direct Mode
- Run the VNC viewer of your choice on the workstation you are using to connect to the system being installed. For example, if you use TigerVNC:
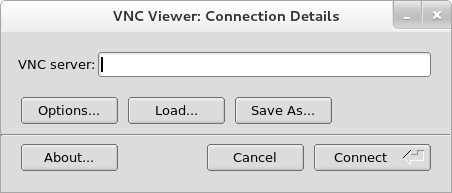
Figure 25.1. TigerVNC Connection Details
- Boot the installation system and wait for the boot menu to appear. In the menu, press the Tab key to edit boot options. Append the
inst.vncoption to the end of the command line.Optionally, if you want to restrict VNC access to the installation system, add theinst.vncpassword=PASSWORDboot option as well. Replace PASSWORD with the password you want to use for the installation. The VNC password must be between 6 and 8 characters long.Important
Use a temporary password for theinst.vncpassword=option. It should not be a real or root password you use on any system.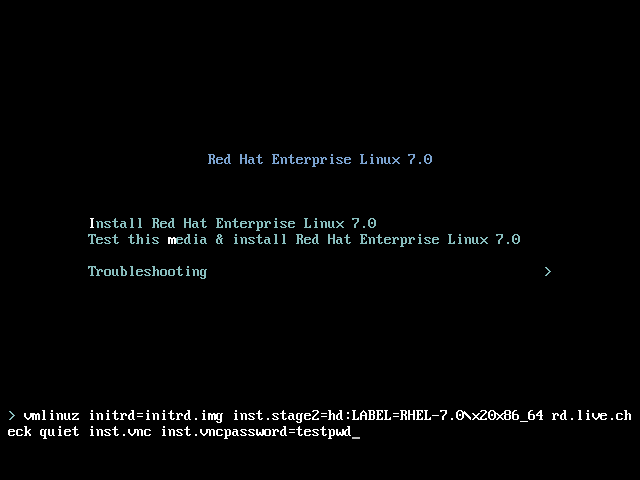
Figure 25.2. Adding VNC Boot Options on AMD, Intel, and ARM Systems
- Press Enter to start the installation. The system initializes the installation program and starts the necessary services. When the system is ready, you get a message on the screen similar to the following:
13:14:47 Please manually connect your VNC viewer to 192.168.100.131:1 to begin the install.
13:14:47 Please manually connect your VNC viewer to 192.168.100.131:1 to begin the install.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note the IP address and port number (in the above example,192.168.100.131:1). - On the system running the VNC Viewer, enter the IP address and port number obtained in the previous step into the Connection Details dialog in the same format as it was displayed on the screen by Anaconda. Then, click Connect. The VNC viewer connects to the installation system. If you set up a VNC password, enter it when prompted and click OK.For further details about using a VNC client, see the corresponding section in the Red Hat Enterprise Linux 7 System Administrator's Guide.
- Chapter 8, Installing Using Anaconda for 64-bit AMD, Intel, and ARM systems
- Chapter 13, Installing Using Anaconda for IBM Power Systems servers
- Chapter 18, Installing Using Anaconda for IBM Z
25.2.2. Installing in VNC Connect Mode
Procedure 25.2. Starting VNC in Connect Mode
- Start the VNC viewer on the client system in listening mode. For example, on Red Hat Enterprise Linux using TigerVNC, execute the following command:
vncviewer -listen PORT
$ vncviewer -listen PORTCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace PORT with the port number you want to use for the connection.The terminal displays a message similar to the following example:Example 25.1. TigerVNC Viewer Listening
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The VNC viewer is now ready and waiting for an incoming connection from the installation system. - Boot the system being installed and wait for the boot menu to appear. In the menu, press the Tab key to edit boot options. Append the following options to the command line:
inst.vnc inst.vncconnect=HOST:PORT
$ inst.vnc inst.vncconnect=HOST:PORTCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace HOST with the IP address of the system running the listening VNC viewer, and PORT with the port number that the VNC viewer is listening on. - Press Enter to start the installation. The system initializes the installation program and starts the necessary services. Once the initialization is finished, Anaconda attempts to connect to the IP address and port you provided in the previous step.When the connection is successfully established, a new window opens on the system running the VNC viewer, displaying the installation menu. In this window, you can use the Anaconda graphical interface the same way you would use it when installing directly on the system.
- Chapter 8, Installing Using Anaconda for 64-bit AMD, Intel, and ARM systems
- Chapter 13, Installing Using Anaconda for IBM Power Systems servers
- Chapter 18, Installing Using Anaconda for IBM Z
25.3. Kickstart Considerations
vnc command results in an installation using Direct Mode. Additional options are available to set up an installation using Connect Mode. For more information about the vnc command and options used in Kickstart files, see Section 27.3.1, “Kickstart Commands and Options”.
Chapter 26. Headless Systems
- Set up a network boot server to start the installation. Information about installing and performing basic configurating of a network boot server can be found in Chapter 24, Preparing for a Network Installation.
- Configure the server to use the boot options for a Connect Mode VNC installation. For information on these boot options, see Section 25.2.2, “Installing in VNC Connect Mode”.
- Follow the procedure for VNC Installation using Connect Mode as described in the procedure Procedure 25.2, “Starting VNC in Connect Mode”. However, when directed to boot the system, boot it from the network server instead of local media.
Chapter 27. Kickstart Installations
27.1. What are Kickstart Installations?
/tmp directory to assist with debugging installation failures.
Note
27.2. How Do You Perform a Kickstart Installation?
- Create a Kickstart file.
- Make the Kickstart file available on removable media, a hard drive or a network location.
- Create boot media, which will be used to begin the installation.
- Make the installation source available.
- Start the Kickstart installation.
27.2.1. Creating a Kickstart File
anaconda-ks.cfg, located in the /root/ directory on the installed system. You can then copy this file, make any changes you need, and use the resulting configuration file in further installations.
Important
- Sections must be specified in order. Items within the sections do not have to be in a specific order unless otherwise specified. The section order is:
- Command section - See Section 27.3.1, “Kickstart Commands and Options” for a list of Kickstart options. You must include the required options.Add-ons for Anaconda which expand the functionality of the installer can also be used in the command section by using the
%addon addon_namecommand. See Section 27.3.7, “Kickstart Add-ons” for details. - The
%packagessection - See Section 27.3.2, “Package Selection” for details. - The
%preand%postsections, and the%onerrorsection - these sections can be in any order and are not required. See Section 27.3.3, “Pre-installation Script”, Section 27.3.5, “Post-installation Script” and Section 27.3.6, “Kickstart error handling” for details.
Important
Sections%addon,%packages,%onerror,%preand%postmust end with%end, otherwise the installation program will refuse the Kickstart file. - Items that are not required can be omitted.
- Omitting any required item results in the installation program prompting the user for an answer to the related item, just as the user would be prompted during a typical installation. Once the answer is given, the installation continues unattended (unless it finds another missing item).
- Lines starting with a pound (also known as number) sign (
#) are treated as comments and are ignored.
27.2.2. Maintaining the Kickstart File
27.2.2.1. Verifying the Kickstart File
root:
yum install pykickstart
# yum install pykickstartksvalidator /path/to/kickstart.ks
$ ksvalidator /path/to/kickstart.ksksvalidator(1) man page.
Important
%pre, %post and %packages sections of the Kickstart file.
27.2.2.2. Changes in Kickstart Syntax
ksverdiff command to display the differences between two versions of the Kickstart syntax. This is useful when updating an existing Kickstart file to be used with a new release. To display a list of changes in syntax between Red Hat Enterprise Linux 6 and 7, use the following command:
ksverdiff -f RHEL6 -t RHEL7
$ ksverdiff -f RHEL6 -t RHEL7-f option specifies the release to start the comparison with, and the -t option to specify the release to end with. For additional information, see the ksverdiff(1) man page.
27.2.3. Making the Kickstart File Available
- On removable media, such as a DVD or USB flash drive
- On a hard drive connected to the installation system
- On a network share reachable from the installation system
27.2.4. Making the Installation Source Available
27.2.5. Starting the Kickstart Installation
Note
inst.ks= boot option, name the file ks.cfg and place it on a storage volume labeled OEMDRV.
inst.ks=location when booting the installation system, replacing location with the location of your Kickstart file. The exact way to specify the boot option depends on your system's architecture - see Chapter 23, Boot Options for details.
27.2.5.1. Starting the Kickstart Installation Manually
boot: prompt) will be required.
Procedure 27.1. Starting the Kickstart Installation Using a Boot Option
- Boot the system using either local media (a CD, DVD, or a USB flash drive). For architecture-specific instructions, see:
- Chapter 7, Booting the Installation on 64-bit AMD, Intel, and ARM systems for 64-bit AMD, Intel, and ARM systems
- Chapter 12, Booting the Installation on IBM Power Systems for IBM Power Systems servers
- At the boot prompt, specify the
inst.ks=boot option and the location of the Kickstart file. If the Kickstart file is in a network location, you must also configure the network using theip=option. In some cases, theinst.repo=option is also necessary in order to access a software source from which necessary packages will be installed.For details about boot options and valid syntax, see Chapter 23, Boot Options. - Start the installation by confirming your added boot options.
27.2.5.2. Starting the Kickstart Installation Automatically
Note
Procedure 27.2. Starting the Kickstart Installation by Editing Boot Loader Configuration
- Open the boot loader configuration file on your PXE server, and add the
inst.ks=boot option to the appropriate line. The name of the file and its syntax depends on your system's architecture and hardware:- On AMD64 and Intel 64 systems with BIOS, the file name can be either
defaultor based on your system's IP address. In this case, add theinst.ks=option to theappendline in the installation entry. A sampleappendline in the configuration file looks similar to the following:append initrd=initrd.img inst.ks=http://10.32.5.1/mnt/archive/RHEL-7/7.x/Server/x86_64/kickstarts/ks.cfg
append initrd=initrd.img inst.ks=http://10.32.5.1/mnt/archive/RHEL-7/7.x/Server/x86_64/kickstarts/ks.cfgCopy to Clipboard Copied! Toggle word wrap Toggle overflow - On systems using the GRUB2 boot loader (64-bit AMD, Intel, and ARM systems with UEFI firmware and IBM Power Systems servers), the file name will be
grub.cfg. In this file, append theinst.ks=option to thekernelline in the installation entry. A samplekernelline in the configuration file will look similar to the following:kernel vmlinuz inst.ks=http://10.32.5.1/mnt/archive/RHEL-7/7.x/Server/x86_64/kickstarts/ks.cfg
kernel vmlinuz inst.ks=http://10.32.5.1/mnt/archive/RHEL-7/7.x/Server/x86_64/kickstarts/ks.cfgCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Boot the installation from the network server. For architecture-specific instructions, see:
- Section 7.1.2, “Booting from the Network Using PXE” for 64-bit AMD, Intel, and ARM systems
- Section 12.3, “Booting from the Network Using an Installation Server” for IBM Power Systems servers
27.3. Kickstart Syntax Reference
27.3.1. Kickstart Commands and Options
Note
=), a value must be specified after it. In the example commands, options in square brackets ([ ]) are optional arguments for the command.
-
authorauthconfig(optional) - Sets up the authentication options for the system using the
authconfigcommand, which can also be run on the command line after the installation finishes. See theauthconfig(8)manual page and theauthconfig --helpcommand for more details. Passwords are shadowed by default.Warning
When using OpenLDAP with theSSLprotocol for security, make sure that theSSLv2andSSLv3protocols are disabled in the server configuration. This is due to the POODLE SSL vulnerability (CVE-2014-3566). See https://access.redhat.com/solutions/1234843 for details.--enablenis- Turns on NIS support. By default,--enablenisuses whatever domain it finds on the network. A domain should almost always be set by hand with the--nisdomain=option.--nisdomain=- NIS domain name to use for NIS services.--nisserver=- Server to use for NIS services (broadcasts by default).--useshadowor--enableshadow- Use shadow passwords.--enableldap- Turns on LDAP support in/etc/nsswitch.conf, allowing your system to retrieve information about users (for example, their UIDs, home directories, and shells) from an LDAP directory. To use this option, you must install the nss-pam-ldapd package. You must also specify a server and a base DN (distinguished name) with--ldapserver=and--ldapbasedn=.--enableldapauth- Use LDAP as an authentication method. This enables thepam_ldapmodule for authentication and changing passwords, using an LDAP directory. To use this option, you must have the nss-pam-ldapd package installed. You must also specify a server and a base DN with--ldapserver=and--ldapbasedn=. If your environment does not use TLS (Transport Layer Security), use the--disableldaptlsswitch to ensure that the resulting configuration file works.--ldapserver=- If you specified either--enableldapor--enableldapauth, use this option to specify the name of the LDAP server to use. This option is set in the/etc/ldap.conffile.--ldapbasedn=- If you specified either--enableldapor--enableldapauth, use this option to specify the DN in your LDAP directory tree under which user information is stored. This option is set in the/etc/ldap.conffile.--enableldaptls- Use TLS (Transport Layer Security) lookups. This option allows LDAP to send encrypted user names and passwords to an LDAP server before authentication.--disableldaptls- Do not use TLS (Transport Layer Security) lookups in an environment that uses LDAP for authentication.--enablekrb5- Use Kerberos 5 for authenticating users. Kerberos itself does not know about home directories, UIDs, or shells. If you enable Kerberos, you must make users' accounts known to this workstation by enabling LDAP, NIS, or Hesiod or by using theuseraddcommand. If you use this option, you must have the pam_krb5 package installed.--krb5realm=- The Kerberos 5 realm to which your workstation belongs.--krb5kdc=- The KDC (or KDCs) that serve requests for the realm. If you have multiple KDCs in your realm, use a comma-separated list without spaces.--krb5adminserver=- The KDC in your realm that is also running kadmind. This server handles password changing and other administrative requests. This server must be run on the master KDC if you have more than one KDC.--enablehesiod- Enables Hesiod support for looking up user home directories, UIDs, and shells. More information on setting up and using Hesiod on your network is in/usr/share/doc/glibc-2.x.x/README.hesiod, which is included in the glibc package. Hesiod is an extension of DNS that uses DNS records to store information about users, groups, and various other items.--hesiodlhsand--hesiodrhs- TheHesiodLHS (left-hand side) and RHS (right-hand side) values, set in/etc/hesiod.conf. TheHesiodlibrary uses these values to search DNS for a name, similar to the way thatLDAPuses a base DN.To look up user information for the user namejim, the Hesiod library looks upjim.passwdLHSRHS, which should resolve to a TXT record that contains a string identical to an entry for that user in thepasswdfile:jim:*:1001:1001:Jungle Jim:/home/jim:/bin/bash. To look up groups, the Hesiod library looks upjim.groupLHSRHSinstead.To look up users and groups by number, make1001.uida CNAME forjim.passwd, and1001.gida CNAME forjim.group. Note that the library does not place a period (.) in front of the LHS and RHS values when performing a search. Therefore, if the LHS and RHS values need to have a period placed in front of them, you must include the period in the values you set for--hesiodlhsand--hesiodrhs.--enablesmbauth- Enables authentication of users against an SMB server (typically a Samba or Windows server). SMB authentication support does not know about home directories, UIDs, or shells. If you enable SMB, you must make users' accounts known to the workstation by enabling LDAP, NIS, or Hesiod or by using theuseraddcommand.--smbservers=- The name of the servers to use for SMB authentication. To specify more than one server, separate the names with commas (,).--smbworkgroup=- The name of the workgroup for the SMB servers.--enablecache- Enables thenscdservice. Thenscdservice caches information about users, groups, and various other types of information. Caching is especially helpful if you choose to distribute information about users and groups over your network usingNIS,LDAP, orHesiod.--passalgo=- Specifysha256to set up the SHA-256 hashing algorithm orsha512to set up the SHA-512 hashing algorithm.
-
autopart(optional) - Automatically creates partitions: a root (
/) partition (1 GB or larger), aswappartition, and an appropriate/bootpartition for the architecture. On large enough drives (50 GB and larger), this also creates a/homepartition.Important
Theautopartoption cannot be used together with thepart/partition,raid,logvol, orvolgroupoptions in the same Kickstart file.--type=- Selects one of the predefined automatic partitioning schemes you want to use. Accepts the following values:lvm: The LVM partitioning scheme.btrfs: The Btrfs partitioning scheme.plain: Regular partitions with no LVM or Btrfs.thinp: The LVM Thin Provisioning partitioning scheme.
For a description of the available partition schemes, see Section 8.14.4.1.1, “File System Types”.--fstype=- Selects one of the available file system types. The available values areext2,ext3,ext4,xfs, andvfat. The default file system isxfs. For information about these file systems, see Section 8.14.4.1.1, “File System Types”.--nohome- Disables automatic creation of the/homepartition.--nolvm- Do not use LVM or Btrfs for automatic partitioning. This option is equal to--type=plain.--encrypted- Encrypts all partitions. This is equivalent to checking the Encrypt partitions check box on the initial partitioning screen during a manual graphical installation.Note
When encrypting one or more partitions, Anaconda attempts to gather 256 bits of entropy to ensure the partitions are encrypted securely. Gathering entropy can take some time - the process will stop after a maximum of 10 minutes, regardless of whether sufficient entropy has been gathered.The process can be sped up by interacting with the installation system (typing on the keyboard or moving the mouse). If you are installing in a virtual machine, you can also attach a virtio-rng device (a virtual random number generator) to the guest as described in the Red Hat Enterprise Linux 7 Virtualization Deployment and Administration Guide.--passphrase=- Provides a default system-wide passphrase for all encrypted devices.--escrowcert=URL_of_X.509_certificate- Stores data encryption keys of all encrypted volumes as files in/root, encrypted using the X.509 certificate from the URL specified with URL_of_X.509_certificate. The keys are stored as a separate file for each encrypted volume. This option is only meaningful if--encryptedis specified.--backuppassphrase- Adds a randomly-generated passphrase to each encrypted volume. Store these passphrases in separate files in/root, encrypted using the X.509 certificate specified with--escrowcert. This option is only meaningful if--escrowcertis specified.--cipher=- Specifies the type of encryption to use if the Anaconda defaultaes-xts-plain64is not satisfactory. You must use this option together with the--encryptedoption; by itself it has no effect. Available types of encryption are listed in the Red Hat Enterprise Linux 7 Security Guide, but Red Hat strongly recommends using eitheraes-xts-plain64oraes-cbc-essiv:sha256.Note
It is recommended to use theautopart --nohomeKickstart option when installing on a single FBA DASD of the CMS type. This ensures that the installer does not create a separate/homepartition. The installation then proceeds successfully.
-
autostep(optional) - Normally, Kickstart installations skip unnecessary screens. This option makes the installation program step through every screen, displaying each briefly. This option should not be used when deploying a system because it can disrupt package installation.
--autoscreenshot- Take a screenshot at every step during installation. These screenshots are stored in/tmp/anaconda-screenshots/during the installation, and after the installation finishes you can find them in/root/anaconda-screenshots.Each screen is only captured right before the installer switches to the next one. This is important, because if you do not use all required Kickstart options and the installation therefore does not begin automatically, you can go to the screens which were not automatically configured, perform any configuration you want. Then, when you click Done to continue, the screen is captured including the configuration you just provided.
-
bootloader(required) - Specifies how the boot loader should be installed.
Important
Red Hat recommends setting up a boot loader password on every system. An unprotected boot loader can allow a potential attacker to modify the system's boot options and gain unauthorized access to the system.Important
Device names in thesdX(or/dev/sdX) format are not guaranteed to be consistent across reboots, which can complicate usage of some Kickstart commands. When a command calls for a device node name, you can instead use any item from/dev/disk. For example, instead of:part / --fstype=xfs --onpart=sda1
part / --fstype=xfs --onpart=sda1Copy to Clipboard Copied! Toggle word wrap Toggle overflow You could use an entry similar to one of the following:part / --fstype=xfs --onpart=/dev/disk/by-path/pci-0000:00:05.0-scsi-0:0:0:0-part1
part / --fstype=xfs --onpart=/dev/disk/by-path/pci-0000:00:05.0-scsi-0:0:0:0-part1Copy to Clipboard Copied! Toggle word wrap Toggle overflow part / --fstype=xfs --onpart=/dev/disk/by-id/ata-ST3160815AS_6RA0C882-part1
part / --fstype=xfs --onpart=/dev/disk/by-id/ata-ST3160815AS_6RA0C882-part1Copy to Clipboard Copied! Toggle word wrap Toggle overflow This way the command will always target the same storage device. This is especially useful in large storage environments. See the chapter about persistent storage device naming in the Red Hat Enterprise Linux 7 Storage Administration Guide for more in-depth information about different ways to consistently refer to storage devices.Note
In some cases, a special partition is required to install the boot loader on 64-bit AMD, Intel, and ARM systems. The type and size of this partition depends on whether the disk you are installing the boot loader to uses the Master Boot Record (MBR) or a GUID Partition Table (GPT) schema. For more information, see Section 8.14.1, “Boot Loader Installation”.--append=- Specifies additional kernel parameters. To specify multiple parameters, separate them with spaces. For example:bootloader --location=mbr --append="hdd=ide-scsi ide=nodma"
bootloader --location=mbr --append="hdd=ide-scsi ide=nodma"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Therhgbandquietparameters are always used, even if you do not specify them here or do not use the--append=command at all.This option is useful for disabling mechanisms which were implemented to mitigate the Meltdown and Spectre speculative execution vulnerabilities found in most modern processors (CVE-2017-5754, CVE-2017-5753, and CVE-2017-5715). In some cases, these mechanisms may be unnecessary, and keeping them enabled causes decreased performance with no improvement in security. To disable these mechanisms, add the options to do so into your Kickstart file - for example,bootloader --append="nopti noibrs noibpb"on AMD64/Intel 64 systems.Warning
Ensure your system is not at risk of attack before disabling any of the vulnerability mitigation mechanisms. See the Red Hat vulnerability response article for information about the Meltdown and Spectre vulnerabilities.--boot-drive=- Specifies which drive the boot loader should be written to, and therefore which drive the computer will boot from. If you use a multipath device as the boot drive, specify the device using its disk/by-id/dm-uuid-mpath-WWID name.Important
The--boot-drive=option is currently being ignored in Red Hat Enterprise Linux installations on IBM Z systems using the zipl boot loader. When zipl is installed, it determines the boot drive on its own.--leavebootorder- The installer will add Red Hat Enterprise Linux 7 to the top of the list of installed systems in the boot loader, and preserve all existing entries as well as their order.--driveorder=- Specifies which drive is first in the BIOS boot order. For example:bootloader --driveorder=sda,hda
bootloader --driveorder=sda,hdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow --location=- Specifies where the boot record is written. Valid values are the following:mbr- The default option. Depends on whether the drive uses the Master Boot Record (MBR) or GUID Partition Table (GPT) scheme:- On a GPT-formatted disk, this option installs stage 1.5 of the boot loader into the BIOS boot partition.
- On an MBR-formatted disk, stage 1.5 is installed into the empty space between the MBR and the first partition.
partition- Install the boot loader on the first sector of the partition containing the kernel.none- Do not install the boot loader.
In most cases, this option does not need to be specified.--password=- If using GRUB2, sets the boot loader password to the one specified with this option. This should be used to restrict access to the GRUB2 shell, where arbitrary kernel options can be passed.If a password is specified, GRUB2 also asks for a user name. The user name is alwaysroot.--iscrypted- Normally, when you specify a boot loader password using the--password=option, it is stored in the Kickstart file in plain text. If you want to encrypt the password, use this option and an encrypted password.To generate an encrypted password, use thegrub2-mkpasswd-pbkdf2command, enter the password you want to use, and copy the command's output (the hash starting withgrub.pbkdf2) into the Kickstart file. An examplebootloaderKickstart entry with an encrypted password looks similar to the following:bootloader --iscrypted --password=grub.pbkdf2.sha512.10000.5520C6C9832F3AC3D149AC0B24BE69E2D4FB0DBEEDBD29CA1D30A044DE2645C4C7A291E585D4DC43F8A4D82479F8B95CA4BA4381F8550510B75E8E0BB2938990.C688B6F0EF935701FF9BD1A8EC7FE5BD2333799C98F28420C5CC8F1A2A233DE22C83705BB614EA17F3FDFDF4AC2161CEA3384E56EB38A2E39102F5334C47405E
bootloader --iscrypted --password=grub.pbkdf2.sha512.10000.5520C6C9832F3AC3D149AC0B24BE69E2D4FB0DBEEDBD29CA1D30A044DE2645C4C7A291E585D4DC43F8A4D82479F8B95CA4BA4381F8550510B75E8E0BB2938990.C688B6F0EF935701FF9BD1A8EC7FE5BD2333799C98F28420C5CC8F1A2A233DE22C83705BB614EA17F3FDFDF4AC2161CEA3384E56EB38A2E39102F5334C47405ECopy to Clipboard Copied! Toggle word wrap Toggle overflow --timeout=- Specifies the amount of time the boot loader waits before booting the default option (in seconds).--default=- Sets the default boot image in the boot loader configuration.--extlinux- Use the extlinux boot loader instead of GRUB2. This option only works on systems supported by extlinux.--disabled— This option is a stronger version of--location=none. While--location=nonesimply disables boot loader installation,--disableddisables boot loader installation and also disables installation of the package containing the boot loader, thus saving space.
-
btrfs(optional) - Create a Btrfs volume or subvolume. For a volume, the syntax is:
btrfs mntpoint --data=level --metadata=level --label=label partitions
btrfs mntpoint --data=level --metadata=level --label=label partitionsCopy to Clipboard Copied! Toggle word wrap Toggle overflow One or more partitions can be specified in partitions. When specifying more than one partitions, the entries must be separated by a single space. See Example 27.1, “Creating Btrfs Volumes and Subvolumes” for a demonstration.For a subvolume, the syntax is:btrfs mntpoint --subvol --name=path parent
btrfs mntpoint --subvol --name=path parentCopy to Clipboard Copied! Toggle word wrap Toggle overflow parent should be the identifier of the subvolume's parent volume and mntpoint is the location where the file system is mounted.--data=- RAID level to use for file system data (such as 0, 1, or 10). This parameter is optional, has no meaning for subvolumes, and requires more than one physical disk.--metadata=- RAID level to use for file system/volume metadata (such as0,1, or10). Optional. This option has no meaning for subvolumes and requires more than one physical disk.--label=- Specify a label for the Btrfs file system. If the given label is already in use by another file system, a new label is created. This option has no meaning for subvolumes.--noformator--useexisting- Use an existing Btrfs volume (or subvolume) and do not reformat the file system.--mkfsoptions=- Specifies additional parameters to be passed to the program that makes a filesystem on this partition. No processing is done on the list of arguments, so they must be supplied in a format that can be passed directly to the mkfs program. This means multiple options should be comma-separated or surrounded by double quotes, depending on the filesystem.
The following example shows how to create a Btrfs volume from member partitions on three disks with subvolumes for/and/home. The main volume is not mounted or used directly in this example.Example 27.1. Creating Btrfs Volumes and Subvolumes
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
clearpart(optional) - Removes partitions from the system, prior to creation of new partitions. By default, no partitions are removed.
Important
Device names in thesdX(or/dev/sdX) format are not guaranteed to be consistent across reboots, which can complicate usage of some Kickstart commands. When a command calls for a device node name, you can instead use any item from/dev/disk. For example, instead of:part / --fstype=xfs --onpart=sda1
part / --fstype=xfs --onpart=sda1Copy to Clipboard Copied! Toggle word wrap Toggle overflow You could use an entry similar to one of the following:part / --fstype=xfs --onpart=/dev/disk/by-path/pci-0000:00:05.0-scsi-0:0:0:0-part1
part / --fstype=xfs --onpart=/dev/disk/by-path/pci-0000:00:05.0-scsi-0:0:0:0-part1Copy to Clipboard Copied! Toggle word wrap Toggle overflow part / --fstype=xfs --onpart=/dev/disk/by-id/ata-ST3160815AS_6RA0C882-part1
part / --fstype=xfs --onpart=/dev/disk/by-id/ata-ST3160815AS_6RA0C882-part1Copy to Clipboard Copied! Toggle word wrap Toggle overflow This way the command will always target the same storage device. This is especially useful in large storage environments. See the chapter about persistent storage device naming in the Red Hat Enterprise Linux 7 Storage Administration Guide for more in-depth information about different ways to consistently refer to storage devices.Note
If theclearpartcommand is used, then thepart --onpartcommand cannot be used on a logical partition.For a detailed example of partitioning including theclearpartcommand, see Section 27.4.1, “Advanced Partitioning Example”.--all- Erases all partitions from the system.Warning
This option will erase all disks which can be reached by the installer, including any attached network storage. Use this option with caution.You can preventclearpartfrom wiping storage you want to preserve by using the--drives=option and specifying only the drives you want to clear, by attaching network storage later (for example, in the%postsection of the Kickstart file), or by blacklisting the kernel modules used to access network storage.--drives=- Specifies which drives to clear partitions from. For example, the following clears all the partitions on the first two drives on the primary IDE controller:clearpart --drives=hda,hdb --all
clearpart --drives=hda,hdb --allCopy to Clipboard Copied! Toggle word wrap Toggle overflow To clear a multipath device, use the formatdisk/by-id/scsi-WWID, where WWID is the world-wide identifier for the device. For example, to clear a disk with WWID58095BEC5510947BE8C0360F604351918, use:clearpart --drives=disk/by-id/scsi-58095BEC5510947BE8C0360F604351918
clearpart --drives=disk/by-id/scsi-58095BEC5510947BE8C0360F604351918Copy to Clipboard Copied! Toggle word wrap Toggle overflow This format is preferable for all multipath devices, but if errors arise, multipath devices that do not use logical volume management (LVM) can also be cleared using the formatdisk/by-id/dm-uuid-mpath-WWID, where WWID is the world-wide identifier for the device. For example, to clear a disk with WWID2416CD96995134CA5D787F00A5AA11017, use:clearpart --drives=disk/by-id/dm-uuid-mpath-2416CD96995134CA5D787F00A5AA11017
clearpart --drives=disk/by-id/dm-uuid-mpath-2416CD96995134CA5D787F00A5AA11017Copy to Clipboard Copied! Toggle word wrap Toggle overflow Warning
Never specify multipath devices by device names likempatha. Device names such as this are not specific to a particular disk. The disk named/dev/mpathaduring installation might not be the one that you expect it to be. Therefore, theclearpartcommand could target the wrong disk.--initlabel- Initializes a disk (or disks) by creating a default disk label for all disks in their respective architecture that have been designated for formatting (for example, msdos for x86). Because--initlabelcan see all disks, it is important to ensure only those drives that are to be formatted are connected.clearpart --initlabel --drives=names_of_disks
clearpart --initlabel --drives=names_of_disksCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:clearpart --initlabel --drives=dasda,dasdb,dasdc
clearpart --initlabel --drives=dasda,dasdb,dasdcCopy to Clipboard Copied! Toggle word wrap Toggle overflow --list=- Specifies which partitions to clear. This option overrides the--alland--linuxoptions if used. Can be used across different drives. For example:clearpart --list=sda2,sda3,sdb1
clearpart --list=sda2,sda3,sdb1Copy to Clipboard Copied! Toggle word wrap Toggle overflow --linux- Erases all Linux partitions.--none(default) - Do not remove any partitions.
Note
Using theclearpart --allcommand in a Kickstart file to remove all existing partitions during the installation can cause Anaconda to pause and prompt you for a confirmation in certain cases. If you need to perform the installation automatically with no interaction, add thezerombrcommand to your Kickstart file. -
cmdline(optional) - Perform the installation in a completely non-interactive command line mode. Any prompt for interaction halts the installation. This mode is useful on IBM Z systems with the x3270 terminal. See Section 21.4, “Parameters for Kickstart Installations”.
Important
For a fully automatic installation, you must either specify one of the available modes (graphical,text, orcmdline) in the Kickstart file, or you must use theconsole=boot option as described in Console, Environment and Display Options. If no mode is specified, the system will prompt you to choose one before continuing. -
device(optional) - On most PCI systems, the installation program automatically detects Ethernet and SCSI cards. However, on older systems and some PCI systems, Kickstart requires a hint to find the proper devices. The
devicecommand, which tells the installation program to install extra modules, uses the following format:device moduleName --opts=options
device moduleName --opts=optionsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - moduleName - Replace with the name of the kernel module which should be installed.
--opts=- Options to pass to the kernel module. For example:device --opts="aic152x=0x340 io=11"
device --opts="aic152x=0x340 io=11"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
-
driverdisk(optional) - Driver disks can be used during Kickstart installations to provide additional drivers not included by default. You must copy the driver disks's contents to the root directory of a partition on the system's hard drive. Then, you must use the
driverdiskcommand to specify that the installation program should look for a driver disk and its location.driverdisk [partition|--source=url|--biospart=biospart]
driverdisk [partition|--source=url|--biospart=biospart]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, a network location can be specified for the driver disk:driverdisk --source=ftp://path/to/dd.img driverdisk --source=http://path/to/dd.img driverdisk --source=nfs:host:/path/to/img
driverdisk --source=ftp://path/to/dd.img driverdisk --source=http://path/to/dd.img driverdisk --source=nfs:host:/path/to/imgCopy to Clipboard Copied! Toggle word wrap Toggle overflow - partition - Partition containing the driver disk. Note that the partition must be specified as a full path (for example,
/dev/sdb1), not just the partition name (for example,sdb1). --source=- URL for the driver disk. NFS locations can be given in the form ofnfs:host:/path/to/img.--biospart=- BIOS partition containing the driver disk (for example,82p2).
Driver disks can also be loaded from a hard disk drive or a similar device instead of being loaded over the network or frominitrd. Follow this procedure:- Load the driver disk on a hard disk drive, a USB or any similar device.
- Set the label, for example, DD, to this device.
- Add the following line to your Kickstart file:
driverdisk LABEL=DD:/e1000.rpm
driverdisk LABEL=DD:/e1000.rpmCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Replace DD with a specific label and replace dd.rpm with a specific name. Use anything supported by theinst.repocommand instead of LABEL to specify your hard disk drive. -
eula(optional) - Use this option to accept the End User License Agreement (EULA) without user interaction. Specifying this option prevents Initial Setup from prompting you to accept the license agreement after you finish the installation and reboot the system for the first time. See Chapter 30, Initial Setup for more information.
--agreed(required) - Accept the EULA. This option must always be used, otherwise theeulacommand is meaningless.
-
fcoe(optional) - Specify which FCoE devices should be activated automatically in addition to those discovered by Enhanced Disk Drive Services (EDD).
fcoe --nic=name [options]
fcoe --nic=name [options]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --nic=(required) - The name of the device to be activated.--dcb=- Establish Data Center Bridging (DCB) settings.--autovlan- Discover VLANs automatically.
-
firewall(optional) - Specify the firewall configuration for the installed system.
firewall --enabled|--disabled device [options]
firewall --enabled|--disabled device [options]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --enabledor--enable- Reject incoming connections that are not in response to outbound requests, such as DNS replies or DHCP requests. If access to services running on this machine is needed, you can choose to allow specific services through the firewall.--remove-service- Do not allow services through the firewall.--disabledor--disable- Do not configure any iptables rules.--trust=- Listing a device here, such as em1, allows all traffic coming to and from that device to go through the firewall. To list more than one device, use--trust em1 --trust em2. Do NOT use a comma-separated format such as--trust em1, em2.- incoming - Replace with one or more of the following to allow the specified services through the firewall.
--ssh--smtp--http--ftp
--port=- You can specify that ports be allowed through the firewall using the port:protocol format. For example, to allow IMAP access through your firewall, specifyimap:tcp. Numeric ports can also be specified explicitly; for example, to allow UDP packets on port 1234 through, specify1234:udp. To specify multiple ports, separate them by commas.--service=- This option provides a higher-level way to allow services through the firewall. Some services (likecups,avahi, and so on.) require multiple ports to be open or other special configuration in order for the service to work. You can specify each individual port with the--portoption, or specify--service=and open them all at once.Valid options are anything recognized by the firewall-offline-cmd program in the firewalld package. Iffirewalldis running,firewall-cmd --get-servicesprovides a list of known service names.
-
firstboot(optional) - Determine whether the Initial Setup application starts the first time the system is booted. If enabled, the initial-setup package must be installed. If not specified, this option is disabled by default.
--enableor--enabled- Initial Setup is started the first time the system boots.--disableor--disabled- Initial Setup is not started the first time the system boots.--reconfig- Enable the Initial Setup to start at boot time in reconfiguration mode. This mode enables the language, mouse, keyboard, root password, security level, time zone and networking configuration options in addition to the default ones.
-
group(optional) - Creates a new user group on the system. If a group with the given name or GID already exists, this command fails. In addition, the
usercommand can be used to create a new group for the newly created user.group --name=name [--gid=gid]
group --name=name [--gid=gid]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --name=- Provides the name of the group.--gid=- The group's GID. If not provided, defaults to the next available non-system GID.
-
graphical(optional) - Perform the installation in graphical mode. This is the default.
Important
For a fully automatic installation, you must either specify one of the available modes (graphical,text, orcmdline) in the Kickstart file, or you must use theconsole=boot option as described in Console, Environment and Display Options. If no mode is specified, the system will prompt you to choose one before continuing. -
halt(optional) - Halt the system after the installation has successfully completed. This is similar to a manual installation, where Anaconda displays a message and waits for the user to press a key before rebooting. During a Kickstart installation, if no completion method is specified, this option is used as the default.The
haltcommand is equivalent to theshutdown -hcommand.For other completion methods, see thepoweroff,reboot, andshutdowncommands. -
ignoredisk(optional) - Causes the installation program to ignore the specified disks. This is useful if you use automatic partitioning and want to be sure that some disks are ignored. For example, without
ignoredisk, attempting to deploy on a SAN-cluster the Kickstart would fail, as the installation program detects passive paths to the SAN that return no partition table.ignoredisk --drives=drive1,drive2,...
ignoredisk --drives=drive1,drive2,...Copy to Clipboard Copied! Toggle word wrap Toggle overflow where driveN is one ofsda,sdb,...,hda,... and so on.Important
Device names in thesdX(or/dev/sdX) format are not guaranteed to be consistent across reboots, which can complicate usage of some Kickstart commands. When a command calls for a device node name, you can instead use any item from/dev/disk. For example, instead of:part / --fstype=xfs --onpart=sda1
part / --fstype=xfs --onpart=sda1Copy to Clipboard Copied! Toggle word wrap Toggle overflow You could use an entry similar to one of the following:part / --fstype=xfs --onpart=/dev/disk/by-path/pci-0000:00:05.0-scsi-0:0:0:0-part1
part / --fstype=xfs --onpart=/dev/disk/by-path/pci-0000:00:05.0-scsi-0:0:0:0-part1Copy to Clipboard Copied! Toggle word wrap Toggle overflow part / --fstype=xfs --onpart=/dev/disk/by-id/ata-ST3160815AS_6RA0C882-part1
part / --fstype=xfs --onpart=/dev/disk/by-id/ata-ST3160815AS_6RA0C882-part1Copy to Clipboard Copied! Toggle word wrap Toggle overflow This way the command will always target the same storage device. This is especially useful in large storage environments. See the chapter about persistent storage device naming in the Red Hat Enterprise Linux 7 Storage Administration Guide for more in-depth information about different ways to consistently refer to storage devices.To ignore a multipath device that does not use logical volume management (LVM), use the formatdisk/by-id/dm-uuid-mpath-WWID, where WWID is the world-wide identifier for the device. For example, to ignore a disk with WWID2416CD96995134CA5D787F00A5AA11017, use:ignoredisk --drives=disk/by-id/dm-uuid-mpath-2416CD96995134CA5D787F00A5AA11017
ignoredisk --drives=disk/by-id/dm-uuid-mpath-2416CD96995134CA5D787F00A5AA11017Copy to Clipboard Copied! Toggle word wrap Toggle overflow Warning
Never specify multipath devices by device names likempatha. Device names such as this are not specific to a particular disk. The disk named/dev/mpathaduring installation might not be the one that you expect it to be. Therefore, theclearpartcommand could target the wrong disk.--only-use- Specifies a list of disks for the installation program to use. All other disks are ignored. For example, to use disksdaduring installation and ignore all other disks:ignoredisk --only-use=sda
ignoredisk --only-use=sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow To include a multipath device that does not use LVM:ignoredisk --only-use=disk/by-id/dm-uuid-mpath-2416CD96995134CA5D787F00A5AA11017
ignoredisk --only-use=disk/by-id/dm-uuid-mpath-2416CD96995134CA5D787F00A5AA11017Copy to Clipboard Copied! Toggle word wrap Toggle overflow To include a multipath device that uses LVM:ignoredisk --only-use=/dev/disk/by-id/dm-uuid-mpath-
ignoredisk --only-use=/dev/disk/by-id/dm-uuid-mpath-Copy to Clipboard Copied! Toggle word wrap Toggle overflow bootloader --location=mbr
bootloader --location=mbrCopy to Clipboard Copied! Toggle word wrap Toggle overflow --interactive- Allows you to manually navigate the advanced storage screen.
-
install(optional) - The default installation mode. You must specify the type of installation from
cdrom,harddrive,nfs,liveimg, orurl(for FTP, HTTP, or HTTPS installations). Theinstallcommand and the installation method command must be on separate lines. For example:install liveimg --url=file:///images/install/squashfs.img --noverifyssl
install liveimg --url=file:///images/install/squashfs.img --noverifysslCopy to Clipboard Copied! Toggle word wrap Toggle overflow cdrom- Install from the first optical drive on the system.harddrive- Install from a Red Hat installation tree or full installation ISO image on a local drive. The drive must contain a file system the installation program can mount:ext2,ext3,ext4,vfat, orxfs.--biospart=- BIOS partition to install from (such as82).--partition=- Partition to install from (such assdb2).--dir=- Directory containing thevariantdirectory of the installation tree, or the ISO image of the full installation DVD.
For example:harddrive --partition=hdb2 --dir=/tmp/install-tree
harddrive --partition=hdb2 --dir=/tmp/install-treeCopy to Clipboard Copied! Toggle word wrap Toggle overflow liveimg- Install from a disk image instead of packages. The image can be thesquashfs.imgfile from a live ISO image, a compressed tar file (.tar,.tbz,.tgz,.txz,.tar.bz2,.tar.gz, or.tar.xz.), or any file system that the installation media can mount. Supported file systems areext2,ext3,ext4,vfat, andxfs.Note
When using theliveimginstallation mode with a driver disk, drivers on the disk will not automatically be included in the installed system. If necessary, these drivers should be installed manually, or in the%postsection of a kickstart script.--url=- The location to install from. Supported protocols areHTTP,HTTPS,FTP, andfile.--proxy=- Specify anHTTP,HTTPSorFTPproxy to use while performing the installation.--checksum=- An optional argument with theSHA256checksum of the image file, used for verification.--noverifyssl- Disable SSL verification when connecting to anHTTPSserver.
For example:liveimg --url=file:///images/install/squashfs.img --checksum=03825f567f17705100de3308a20354b4d81ac9d8bed4bb4692b2381045e56197 --noverifyssl
liveimg --url=file:///images/install/squashfs.img --checksum=03825f567f17705100de3308a20354b4d81ac9d8bed4bb4692b2381045e56197 --noverifysslCopy to Clipboard Copied! Toggle word wrap Toggle overflow nfs- Install from the NFS server specified.--server=- Server from which to install (host name or IP).--dir=- Directory containing thevariantdirectory of the installation tree.--opts=- Mount options to use for mounting the NFS export. (optional)
For example:nfs --server=nfsserver.example.com --dir=/tmp/install-tree
nfs --server=nfsserver.example.com --dir=/tmp/install-treeCopy to Clipboard Copied! Toggle word wrap Toggle overflow url- Install from an installation tree on a remote server using theFTP,HTTP, orHTTPSprotocol. You can only specify one URL.--url=- Specifies theHTTP,HTTPS,FTP, orfilelocation to install from.--mirrorlist=- Specifies the mirror URL to install from.--proxy=- Specifies anHTTP,HTTPS, orFTPproxy to use during the installation.--noverifyssl- Disables SSL verification when connecting to anHTTPSserver.
For example:url --url http://server/path
url --url http://server/pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow or:url --url ftp://username:password@server/path
url --url ftp://username:password@server/pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
-
iscsi(optional) iscsi --ipaddr=address [options]
iscsi --ipaddr=address [options]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Specifies additional iSCSI storage to be attached during installation. If you use theiscsicommand, you must also assign a name to the iSCSI node, using theiscsinamecommand. Theiscsinamecommand must appear before theiscsicommand in the Kickstart file.We recommend that wherever possible you configure iSCSI storage in the system BIOS or firmware (iBFT for Intel systems) rather than use theiscsicommand. Anaconda automatically detects and uses disks configured in BIOS or firmware and no special configuration is necessary in the Kickstart file.If you must use theiscsicommand, ensure that networking is activated at the beginning of the installation, and that theiscsicommand appears in the Kickstart file before you refer to iSCSI disks with commands such asclearpartorignoredisk.--ipaddr=(required) - the IP address of the target to connect to.--port=(required) - the port number (typically,--port=3260)--target=- the target IQN (iSCSI Qualified Name).--iface=- bind the connection to a specific network interface instead of using the default one determined by the network layer. Once used, it must be specified in all instances of theiscsicommand in the entire Kickstart file.--user=- the user name required to authenticate with the target--password=- the password that corresponds with the user name specified for the target--reverse-user=- the user name required to authenticate with the initiator from a target that uses reverse CHAP authentication--reverse-password=- the password that corresponds with the user name specified for the initiator
-
iscsiname(optional) - Assigns a name to an iSCSI node specified by the iscsi parameter. If you use the
iscsiparameter in your Kickstart file, you must specifyiscsinameearlier in the Kickstart file.iscsiname iqn
iscsiname iqnCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
%addon com_redhat_kdump(optional) - This command configures the kdump kernel crash dumping mechanism.
Note
The syntax for this command is unusual because it is an add-on rather than a built-in Kickstart command. For more information about add-ons, see Section 27.3.7, “Kickstart Add-ons”.Kdump is a kernel crash dumping mechanism that allows you to save the contents of the system's memory for later analysis. It relies on kexec, which can be used to boot a Linux kernel from the context of another kernel without rebooting the system, and preserve the contents of the first kernel's memory that would otherwise be lost.In case of a system crash, kexec boots into a second kernel (a capture kernel). This capture kernel resides in a reserved part of the system memory that is inaccessible to the first kernel. Kdump then captures the contents of the crashed kernel's memory (a crash dump) and saves it to a specified location. The location cannot be configured using this Kickstart command; it must be configured after the installation by editing the/etc/kdump.confconfiguration file.For more information about Kdump, see the Red Hat Enterprise Linux 7 Kernel Crash Dump Guide.Available options are:--enable- Enable kdump on the installed system.--disable- Disable kdump on the installed system.--reserve-mb=- The amount of memory you want to reserve for kdump, in MiB. For example:%addon com_redhat_kdump --enable --reserve-mb=128 %end
%addon com_redhat_kdump --enable --reserve-mb=128 %endCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can also specifyautoinstead of a numeric value. In that case, the installer will determine the amount of memory automatically based on the criteria described in the Red Hat Enterprise Linux 7 Kernel Crash Dump Guide.If you enable kdump and do not specify a--reserve-mb=option, the valueautowill be used.--enablefadump- Enable firmware-assisted dumping on systems which allow it (notably, IBM Power Systems servers).
-
keyboard(required) - Sets one or more available keyboard layouts for the system.
--vckeymap=- Specify aVConsolekeymap which should be used. Valid names correspond to the list of files in the/usr/lib/kbd/keymaps/directory, without the.map.gzextension.--xlayouts=- Specify a list of X layouts that should be used as a comma-separated list without spaces. Accepts values in the same format assetxkbmap(1), either in thelayoutformat (such ascz), or in thelayout (variant)format (such ascz (qwerty)).All available layouts can be viewed on thexkeyboard-config(7)man page underLayouts.--switch=- Specify a list of layout-switching options (shortcuts for switching between multiple keyboard layouts). Multiple options must be separated by commas without spaces. Accepts values in the same format assetxkbmap(1).Available switching options can be viewed on thexkeyboard-config(7)man page underOptions.
The following example sets up two keyboard layouts (English (US)andCzech (qwerty)) using the--xlayouts=option, and allows to switch between them using Alt+Shift:keyboard --xlayouts=us,'cz (qwerty)' --switch=grp:alt_shift_toggle
keyboard --xlayouts=us,'cz (qwerty)' --switch=grp:alt_shift_toggleCopy to Clipboard Copied! Toggle word wrap Toggle overflow Important
Either the--vckeymap=or the--xlayouts=option must be used. -
lang(required) - Sets the language to use during installation and the default language to use on the installed system. For example, to set the language to English, the Kickstart file should contain the following line:
lang en_US
lang en_USCopy to Clipboard Copied! Toggle word wrap Toggle overflow The file/usr/share/system-config-language/locale-listprovides a list of the valid language codes in the first column of each line and is part of the system-config-language package.Certain languages (for example, Chinese, Japanese, Korean, and Indic languages) are not supported during text-mode installation. If you specify one of these languages with thelangcommand, the installation process continues in English, but the installed system uses your selection as its default language.--addsupport=- Add support for additional languages. Takes the form of comma-separated list without spaces. For example:lang en_US --addsupport=cs_CZ,de_DE,en_UK
lang en_US --addsupport=cs_CZ,de_DE,en_UKCopy to Clipboard Copied! Toggle word wrap Toggle overflow
-
logging(optional) - Controls the error logging of Anaconda during installation. It has no effect on the installed system.
logging [--host=host] [--port=port] [--level=debug|info|error|critical]
logging [--host=host] [--port=port] [--level=debug|info|error|critical]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --host=- Send logging information to the given remote host, which must be running a syslogd process configured to accept remote logging.--port=- If the remote syslogd process uses a port other than the default, set it using this option.--level=- Specify the minimum level of messages that appear on tty3. All messages are still sent to the log file regardless of this level, however. Possible values aredebug,info,warning,error, orcritical.
-
logvol(optional) - Create a logical volume for Logical Volume Management (LVM). For more information regarding LVM, see the Red Hat Enterprise Linux 7 Logical Volume Manager Administration guide. This command uses the following syntax:
logvol mntpoint --vgname=name --name=name [options]
logvol mntpoint --vgname=name --name=name [options]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Do not use the dash (-) character in logical volume and volume group names when installing Red Hat Enterprise Linux using Kickstart. If this character is used, the installation finishes normally, but the/dev/mapper/directory will list these volumes and volume groups with every dash doubled. For example, a volume group namedvolgrp-01containing a logical volume namedlogvol-01will be listed as/dev/mapper/volgrp--01-logvol--01.This limitation only applies to newly created logical volume and volume group names. If you are reusing existing ones using the--noformatoption, their names will not be changed.For a detailed example oflogvolin action, see Section 27.4.1, “Advanced Partitioning Example”.- The mntpoint is where the partition is mounted and must be of one of the following forms:
/pathFor example,/or/homeswapThe partition is used as swap space.To determine the size of the swap partition automatically, use the--recommendedoption:swap --recommended
swap --recommendedCopy to Clipboard Copied! Toggle word wrap Toggle overflow To determine the size of the swap partition automatically and also allow extra space for your system to hibernate, use the--hibernationoption:swap --hibernation
swap --hibernationCopy to Clipboard Copied! Toggle word wrap Toggle overflow The size assigned will be equivalent to the swap space assigned by--recommendedplus the amount of RAM on your system.For the swap sizes assigned by these commands, see Section 8.14.4.4, “Recommended Partitioning Scheme” for 64-bit AMD, Intel, and ARM systems, Section 13.15.4.4, “Recommended Partitioning Scheme” for IBM Power Systems servers, and Section 18.15.3.4, “Recommended Partitioning Scheme” for IBM Z.
The options are as follows:--noformat- Use an existing logical volume and do not format it.--useexisting- Use an existing logical volume and reformat it.--fstype=- Sets the file system type for the logical volume. Valid values arexfs,ext2,ext3,ext4,swap, andvfat.--fsoptions=- Specifies a free form string of options to be used when mounting the filesystem. This string will be copied into the/etc/fstabfile of the installed system and should be enclosed in quotes.--mkfsoptions=- Specifies additional parameters to be passed to the program that makes a filesystem on this partition. No processing is done on the list of arguments, so they must be supplied in a format that can be passed directly to the mkfs program. This means multiple options should be comma-separated or surrounded by double quotes, depending on the filesystem.--label=- Sets a label for the logical volume.--grow- Tells the logical volume to grow to fill available space (if any), or up to the maximum size setting, if one is specified. A minimum size must be given, using either the--percent=option or the--size=option.Note
For more information about allocating space when writing to an image file, see section3.5.4.Host StoragedescribingImage filesin the Red Hat Enterprise Linux 7 Storage Administration Guide.--size=- The size of the logical volume in MiB. This option cannot be used together with the--percent=option.--percent=- The size of the logical volume, as a percentage of the free space in the volume group after any statically-sized logical volumes are taken into account. This option cannot be used together with the--size=option.Important
When creating a new logical volume, you must either specify its size statically using the--size=option, or as a percentage of remaining free space using the--percent=option. You cannot use both of these options on the same logical volume.Note that this behavior is only applies to Red Hat Enterprise Linux 7.1 and later. In Red Hat Enterprise Linux 7.0, these two options interacted differently.--maxsize=- The maximum size in MiB when the logical volume is set to grow. Specify an integer value here such as500(do not include the unit).--recommended- Use this option when creating aswaplogical volume to determine the size of this volume automatically, based on your system's hardware. For details about the recommended scheme, see Section 8.14.4.4, “Recommended Partitioning Scheme” for 64-bit AMD, Intel, and ARM systems, Section 13.15.4.4, “Recommended Partitioning Scheme” for IBM Power Systems, and Section 18.15.3.4, “Recommended Partitioning Scheme” for IBM Z.--resize- Resize a logical volume. If you use this option, you must also specify--useexistingand--size.--encrypted- Specifies that this logical volume should be encrypted, using the passphrase provided in the--passphrase=option. If you do not specify a passphrase, the installation program uses the default, system-wide passphrase set with theautopart --passphrasecommand, or stops the installation and prompts you to provide a passphrase if no default is set.Note
When encrypting one or more partitions, Anaconda attempts to gather 256 bits of entropy to ensure the partitions are encrypted securely. Gathering entropy can take some time - the process will stop after a maximum of 10 minutes, regardless of whether sufficient entropy has been gathered.The process can be sped up by interacting with the installation system (typing on the keyboard or moving the mouse). If you are installing in a virtual machine, you can also attach a virtio-rng device (a virtual random number generator) to the guest as described in the Red Hat Enterprise Linux 7 Virtualization Deployment and Administration Guide.--passphrase=- Specifies the passphrase to use when encrypting this logical volume. You must use this option together with the--encryptedoption; it has no effect by itself.--cipher=- Specifies which type of encryption will be used if the Anaconda default aes-xts-plain64 is not satisfactory. You must use this option together with the--encryptedoption; by itself it has no effect. Available types of encryption are listed in the Red Hat Enterprise Linux 7 Security Guide, but Red Hat strongly recommends using either aes-xts-plain64 or aes-cbc-essiv:sha256.--escrowcert=URL_of_X.509_certificate- Store data encryption keys of all encrypted volumes as files in/root, encrypted using the X.509 certificate from the URL specified with URL_of_X.509_certificate. The keys are stored as a separate file for each encrypted volume. This option is only meaningful if--encryptedis specified.--backuppassphrase- Add a randomly-generated passphrase to each encrypted volume. Store these passphrases in separate files in/root, encrypted using the X.509 certificate specified with--escrowcert. This option is only meaningful if--escrowcertis specified.--thinpool- Creates a thin pool logical volume. (Use a mount point ofnone)--metadatasize=size- Specify the metadata area size (in MiB) for a new thin pool device.--chunksize=size- Specify the chunk size (in KiB) for a new thin pool device.--thin- Create a thin logical volume. (Requires use of--poolname)--poolname=name- Specify the name of the thin pool in which to create a thin logical volume. Requires the--thinoption.--profile=name- Specify the configuration profile name to use with thin logical volumes. If used, the name will also be included in the metadata for the given logical volume. By default, the available profiles aredefaultandthin-performanceand are defined in the/etc/lvm/profile/directory. See thelvm(8)man page for additional information.--cachepvs=- A comma-separated list of physical volumes which should be used as a cache for this volume.--cachemode=- Specify which mode should be used to cache this logical volume - eitherwritebackorwritethrough.Note
For more information about cached logical volumes and their modes, see thelvmcache(7)man page.--cachesize=- Size of cache attached to the logical volume, specified in MiB. This option requires the--cachepvs=option.
Create the partition first, create the logical volume group, and then create the logical volume. For example:part pv.01 --size 3000 volgroup myvg pv.01 logvol / --vgname=myvg --size=2000 --name=rootvol
part pv.01 --size 3000 volgroup myvg pv.01 logvol / --vgname=myvg --size=2000 --name=rootvolCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the partition first, create the logical volume group, and then create the logical volume to occupy 90% of the remaining space in the volume group. For example:part pv.01 --size 1 --grow volgroup myvg pv.01 logvol / --vgname=myvg --name=rootvol --percent=90
part pv.01 --size 1 --grow volgroup myvg pv.01 logvol / --vgname=myvg --name=rootvol --percent=90Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
mediacheck(optional) - If given, this command forces the installation program to perform a media check (
rd.live.check) before starting the installation. This command requires that installations be attended, so it is disabled by default. -
mount(optional) - Assigns a mount point to an existing block device, and optionally reformats it to a given format.
mount [--reformat [REFORMAT]] [--mkfsoptions MKFS_OPTS] [--mountoptions MOUNT_OPTS] device mntpoint
mount [--reformat [REFORMAT]] [--mkfsoptions MKFS_OPTS] [--mountoptions MOUNT_OPTS] device mntpointCopy to Clipboard Copied! Toggle word wrap Toggle overflow Unlike most other storage configuration commands in Kickstart,mountdoes not require you to describe the entire storage configuration in the Kickstart file. You only need to ensure that the described block device exists on the system. However, if you want to create the storage stack with all the devices mounted, you must use other commands such aspartto do so.Important
You can not usemounttogether with other storage-related commands such aspart,logvol, orautopartin the same Kickstart file.Mandatory arguments:device- The block device to mount.mntpoint- Where to mount thedevice. It must be a valid mount point, such as/or/usr, ornoneif the device is unmountable (for exampleswap).
Optional arguments:--reformat=- Specifies a new format (such asext4) to which the device should be reformatted.--mkfsoptions=- Specifies additional argument to be passed to the command which creates the new file system specified in--reformat=. The list of arguments provided here is not processed, so they must be specified in a format that can be passed directly to themkfsprogram. The list of options should be either comma-separated or surrounded by double quotes, depending on the file system. Check themkfsman page for the file system you want to create (for examplemkfs.ext4(8)ormkfs.xfs(8)) for specific details.--mountoptions=- Specifies a free form string that contains options to be used when mounting the file system. The string will be copied to the/etc/fstabfile on the installed system and should be enclosed in double quotes. See themount(8)man page for a full list of mount options, andfstab(5)for basics.
-
network(optional) - Configures network information for the target system and activates network devices in the installation environment. The device specified in the first
networkcommand is activated automatically. Activation of the device can be also explicitly required by the--activateoption.Note
There are several types of network device naming standards used to identify network devices with persistent names such asem1orwl3sp0. For information about these standards, see the Red Hat Enterprise Linux 7 Networking Guide.--activate- activate this device in the installation environment.If you use the--activateoption on a device that has already been activated (for example, an interface you configured with boot options so that the system could retrieve the Kickstart file) the device is reactivated to use the details specified in the Kickstart file.Use the--nodefrouteoption to prevent the device from using the default route.--no-activate- do not activate this device in the installation environment.By default, Anaconda activates the first network device in the Kickstart file regardless of the--activateoption. You can disable the default setting by using the--no-activateoption.--bootproto=- One ofdhcp,bootp,ibft, orstatic. The default option isdhcp; thedhcpandbootpoptions are treated the same. To disableipv4configuration of the device, use--noipv4option.Note
This option configures ipv4 configuration of the device. For ipv6 configuration use --ipv6 and --ipv6gateway options.The DHCP method uses a DHCP server system to obtain its networking configuration. The BOOTP method is similar, requiring a BOOTP server to supply the networking configuration. To direct a system to use DHCP:network --bootproto=dhcp
network --bootproto=dhcpCopy to Clipboard Copied! Toggle word wrap Toggle overflow To direct a machine to use BOOTP to obtain its networking configuration, use the following line in the Kickstart file:network --bootproto=bootp
network --bootproto=bootpCopy to Clipboard Copied! Toggle word wrap Toggle overflow To direct a machine to use the configuration specified in iBFT, use:network --bootproto=ibft
network --bootproto=ibftCopy to Clipboard Copied! Toggle word wrap Toggle overflow Thestaticmethod requires that you specify at least the IP address and netmask in the Kickstart file. This information is static and is used during and after the installation.All static networking configuration information must be specified on one line; you cannot wrap lines using a backslash (\) as you can on a command line.network --bootproto=static --ip=10.0.2.15 --netmask=255.255.255.0 --gateway=10.0.2.254 --nameserver=10.0.2.1
network --bootproto=static --ip=10.0.2.15 --netmask=255.255.255.0 --gateway=10.0.2.254 --nameserver=10.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can also configure multiple nameservers at the same time. To do so, use the--nameserver=option once, and specify each of their IP addresses, separated by commas.network --bootproto=static --ip=10.0.2.15 --netmask=255.255.255.0 --gateway=10.0.2.254 --nameserver=192.168.2.1,192.168.3.1
network --bootproto=static --ip=10.0.2.15 --netmask=255.255.255.0 --gateway=10.0.2.254 --nameserver=192.168.2.1,192.168.3.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow --device=- specifies the device to be configured (and eventually activated in Anaconda) with thenetworkcommand.If the--device=option is missing on the first use of thenetworkcommand, the value of theksdevice=Anaconda boot option is used, if available. Note that this is considered deprecated behavior; in most cases, you should always specify a--device=for everynetworkcommand.The behavior of any subsequentnetworkcommand in the same Kickstart file is unspecified if its--device=option is missing. Make sure you specify this option for anynetworkcommand beyond the first.You can specify a device to be activated in any of the following ways:- the device name of the interface, for example,
em1 - the MAC address of the interface, for example,
01:23:45:67:89:ab - the keyword
link, which specifies the first interface with its link in theupstate - the keyword
bootif, which uses the MAC address that pxelinux set in theBOOTIFvariable. SetIPAPPEND 2in yourpxelinux.cfgfile to have pxelinux set theBOOTIFvariable.
For example:network --bootproto=dhcp --device=em1
network --bootproto=dhcp --device=em1Copy to Clipboard Copied! Toggle word wrap Toggle overflow --ip=- IP address of the device.--ipv6=- IPv6 address of the device, in the form of address[/prefix length] - for example,3ffe:ffff:0:1::1/128. If prefix is omitted,64is used. You can also useautofor automatic configuration, ordhcpfor DHCPv6-only configuration (no router advertisements).--gateway=- Default gateway as a single IPv4 address.--ipv6gateway=- Default gateway as a single IPv6 address.--nodefroute- Prevents the interface being set as the default route. Use this option when you activate additional devices with the--activate=option, for example, a NIC on a separate subnet for an iSCSI target.--nameserver=- DNS name server, as an IP address. To specify more than one name server, use this option once, and separate each IP address with a comma.--nodns- Do not configure any DNS server.--netmask=- Network mask for the installed system.--hostname=- The host name for the installed system. The host name can either be a fully-qualified domain name (FQDN) in the formathost_name.domainname, or a short host name with no domain. Many networks have a Dynamic Host Configuration Protocol (DHCP) service which automatically supplies connected systems with a domain name; to allow DHCP to assign the domain name, only specify a short host name.Important
If your network does not provide a DHCP service, always use the FQDN as the system's host name.--ethtool=- Specifies additional low-level settings for the network device which will be passed to the ethtool program.--essid=- The network ID for wireless networks.--wepkey=- The WEP encryption key for wireless networks.--wpakey=- The WPA encryption key for wireless networks.--onboot=- Whether or not to enable the device at boot time.--dhcpclass=- The DHCP class.--mtu=- The MTU of the device.--noipv4- Disable IPv4 on this device.--noipv6- Disable IPv6 on this device.--bondslaves=- When this option is used, the network device specified in the--device=option is created using slaves defined in the--bondslaves=option. For example:network --device=mynetwork --bondslaves=em1,em2
network --device=mynetwork --bondslaves=em1,em2Copy to Clipboard Copied! Toggle word wrap Toggle overflow The above command creates a bond device namedmynetworkusing theem1andem2interfaces as its slaves.--bondopts=- a list of optional parameters for a bonded interface, which is specified using the--bondslaves=and--device=options. Options in this list must be separated by commas (",") or semicolons (";"). If an option itself contains a comma, use a semicolon to separate the options. For example:network --bondopts=mode=active-backup,balance-rr;primary=eth1
network --bondopts=mode=active-backup,balance-rr;primary=eth1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Available optional parameters are listed in the Working with Kernel Modules chapter of the Red Hat Enterprise Linux 7 System Administrator's Guide.Important
The--bondopts=mode=parameter only supports full mode names such asbalance-rrorbroadcast, not their numerical representations such as0or3.--vlanid=- Specifies virtual LAN (VLAN) ID number (802.1q tag) for the device created using the device specified in--device=as a parent. For example,network --device=em1 --vlanid=171creates a virtual LAN deviceem1.171.--interfacename=- Specify a custom interface name for a virtual LAN device. This option should be used when the default name generated by the--vlanid=option is not desirable. This option must be used along with--vlanid=. For example:network --device=em1 --vlanid=171 --interfacename=vlan171
network --device=em1 --vlanid=171 --interfacename=vlan171Copy to Clipboard Copied! Toggle word wrap Toggle overflow The above command creates a virtual LAN interface namedvlan171on theem1device with an ID of171.The interface name can be arbitrary (for example,my-vlan), but in specific cases, the following conventions must be followed:- If the name contains a dot (
.), it must take the form ofNAME.ID. The NAME is arbitrary, but the ID must be the VLAN ID. For example:em1.171ormy-vlan.171. - Names starting with
vlanmust take the form ofvlanID- for example,vlan171.
--teamslaves=- Team device specified by the--device=option will be created using slaves specified in this option. Slaves are separated by commas. A slave can be followed by its configuration, which is a single-quoted JSON string with double quotes escaped by the\character. For example:network --teamslaves="p3p1'{\"prio\": -10, \"sticky\": true}',p3p2'{\"prio\": 100}'"network --teamslaves="p3p1'{\"prio\": -10, \"sticky\": true}',p3p2'{\"prio\": 100}'"Copy to Clipboard Copied! Toggle word wrap Toggle overflow See also the--teamconfig=option.--teamconfig=- Double-quoted team device configuration which is a single-quoted JSON string with double quotes escaped by the\character. The device name is specified by--device=option and its slaves and their configuration by--teamslaves=option. For example:network --device team0 --activate --bootproto static --ip=10.34.102.222 --netmask=255.255.255.0 --gateway=10.34.102.254 --nameserver=10.34.39.2 --teamslaves="p3p1'{\"prio\": -10, \"sticky\": true}',p3p2'{\"prio\": 100}'" --teamconfig="{\"runner\": {\"name\": \"activebackup\"}}"network --device team0 --activate --bootproto static --ip=10.34.102.222 --netmask=255.255.255.0 --gateway=10.34.102.254 --nameserver=10.34.39.2 --teamslaves="p3p1'{\"prio\": -10, \"sticky\": true}',p3p2'{\"prio\": 100}'" --teamconfig="{\"runner\": {\"name\": \"activebackup\"}}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow --bridgeslaves=- When this option is used, the network bridge with device name specified using the--device=option will be created and devices defined in the--bridgeslaves=option will be added to the bridge. For example:network --device=bridge0 --bridgeslaves=em1
network --device=bridge0 --bridgeslaves=em1Copy to Clipboard Copied! Toggle word wrap Toggle overflow --bridgeopts=- An optional comma-separated list of parameters for the bridged interface. Available values arestp,priority,forward-delay,hello-time,max-age, andageing-time. For information about these parameters, see the bridge setting table in thenm-settings(5)man page or at https://developer.gnome.org/NetworkManager/0.9/ref-settings.html.Also see the Red Hat Enterprise Linux 7 Networking Guide for general information about network bridging.--bindto=mac- Bind the device configuration (ifcfg) file on the installed system to the device MAC address (HWADDR) instead of the default binding to the interface name (DEVICE). Note that this option is independent of the--device=option ---bindto=macwill be applied even if the samenetworkcommand also specifies a device name,link, orbootif.
-
nvdimm(optional) - Performs an action on Non-Volatile Dual In-line Memory Module (NVDIMM) devices. This command uses the following format:
nvdimm action [options]
nvdimm action [options]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
By default, all NVDIMM devices are ignored by the installer. You must use thenvdimmcommand to enable installation on these devices.The following actions are available:reconfigure- Reconfigure a specific NVDIMM device into a given mode. Additionally, the specified device is implicitly marked as to be used, so a subsequentnvdimm usecommand for the same device is redundant. This action uses the following format:nvdimm reconfigure [--namespace=NAMESPACE] [--mode=MODE] [--sectorsize=SECTORSIZE]
nvdimm reconfigure [--namespace=NAMESPACE] [--mode=MODE] [--sectorsize=SECTORSIZE]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --namespace=- The device specification by namespace. For example:nvdimm reconfigure --namespace=namespace0.0 --mode=sector --sectorsize=512
nvdimm reconfigure --namespace=namespace0.0 --mode=sector --sectorsize=512Copy to Clipboard Copied! Toggle word wrap Toggle overflow --mode=- The mode specification. Currently, only the valuesectoris available.--sectorsize=- Size of a sector for sector mode. For example:nvdimm reconfigure --namespace=namespace0.0 --mode=sector --sectorsize=512
nvdimm reconfigure --namespace=namespace0.0 --mode=sector --sectorsize=512Copy to Clipboard Copied! Toggle word wrap Toggle overflow The supported sector sizes are 512 and 4096 bytes.
use- Specify a NVDIMM device as a target for installation. The device must be already configured to the sector mode by thenvdimm reconfigurecommand. This action uses the following format:nvdimm use [--namespace=NAMESPACE|--blockdevs=DEVICES]
nvdimm use [--namespace=NAMESPACE|--blockdevs=DEVICES]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --namespace=- Specifies the device by namespace. For example:nvdimm use --namespace=namespace0.0
nvdimm use --namespace=namespace0.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow --blockdevs=- Specifies a comma-separated list of block devices corresponding to the NVDIMM devices to be used. The asterisk*wildcard is supported. For example:nvdimm use --blockdevs=pmem0s,pmem1s nvdimm use --blockdevs=pmem*
nvdimm use --blockdevs=pmem0s,pmem1s nvdimm use --blockdevs=pmem*Copy to Clipboard Copied! Toggle word wrap Toggle overflow
-
%addon org_fedora_oscap(optional) - The OpenSCAP installer add-on is used to apply SCAP (Security Content Automation Protocol) content - security policies - on the installed system. This add-on has been enabled by default since Red Hat Enterprise Linux 7.2. When enabled, the packages necessary to provide this functionality will automatically be installed. However, by default, no policies are enforced, meaning that no checks are performed during or after installation unless specifically configured.
Important
Applying a security policy is not necessary on all systems. This screen should only be used when a specific policy is mandated by your organization rules or government regulations.Unlike most other commands, this add-on does not accept regular options, but uses key-value pairs in the body of the%addondefinition instead. These pairs are whitespace-agnostic. Values can be optionally enclosed in single quotes (') or double quotes (").The following keys are recognized by the add-on:content-type- Type of the security content. Possible values aredatastream,archive,rpm, andscap-security-guide.If thecontent-typeisscap-security-guide, the add-on will use content provided by the scap-security-guide package, which is present on the boot media. This means that all other keys exceptprofilewill have no effect.content-url- Location of the security content. The content must be accessible using HTTP, HTTPS, or FTP; local storage is currently not supported. A network connection must be available to reach content definitions in a remote location.datastream-id- ID of the data stream referenced in thecontent-urlvalue. Used only ifcontent-typeisdatastream.xccdf-id- ID of the benchmark you want to use.xccdf-path- Path to the XCCDF file which should be used; given as a relative path in the archive.profile- ID of the profile to be applied. Usedefaultto apply the default profile.fingerprint- A MD5, SHA1 or SHA2 checksum of the content referenced bycontent-url.tailoring-path- Path to a tailoring file which should be used, given as a relative path in the archive.
The following is an example%addon org_fedora_oscapsection which uses content from the scap-security-guide on the installation media:Example 27.2. Sample OpenSCAP Add-on Definition Using SCAP Security Guide
%addon org_fedora_oscap content-type = scap-security-guide profile = xccdf_org.ssgproject.content_profile_pci-dss %end
%addon org_fedora_oscap content-type = scap-security-guide profile = xccdf_org.ssgproject.content_profile_pci-dss %endCopy to Clipboard Copied! Toggle word wrap Toggle overflow The following is a more complex example which loads a custom profile from a web server:Example 27.3. Sample OpenSCAP Add-on Definition Using a Datastream
Copy to Clipboard Copied! Toggle word wrap Toggle overflow For more information about the profiles available in the SCAP Security Guide and what they do, see Red Hat Enterprise Linux 7 Security Guide. -
partorpartition(required) - Creates a partition on the system.
Warning
All partitions created are formatted as part of the installation process unless--noformatand--onpartare used.Important
Device names in thesdX(or/dev/sdX) format are not guaranteed to be consistent across reboots, which can complicate usage of some Kickstart commands. When a command calls for a device node name, you can instead use any item from/dev/disk. For example, instead of:part / --fstype=xfs --onpart=sda1
part / --fstype=xfs --onpart=sda1Copy to Clipboard Copied! Toggle word wrap Toggle overflow You could use an entry similar to one of the following:part / --fstype=xfs --onpart=/dev/disk/by-path/pci-0000:00:05.0-scsi-0:0:0:0-part1
part / --fstype=xfs --onpart=/dev/disk/by-path/pci-0000:00:05.0-scsi-0:0:0:0-part1Copy to Clipboard Copied! Toggle word wrap Toggle overflow part / --fstype=xfs --onpart=/dev/disk/by-id/ata-ST3160815AS_6RA0C882-part1
part / --fstype=xfs --onpart=/dev/disk/by-id/ata-ST3160815AS_6RA0C882-part1Copy to Clipboard Copied! Toggle word wrap Toggle overflow This way the command will always target the same storage device. This is especially useful in large storage environments. See the chapter about persistent storage device naming in the Red Hat Enterprise Linux 7 Storage Administration Guide for more in-depth information about different ways to consistently refer to storage devices.For a detailed example ofpartin action, see Section 27.4.1, “Advanced Partitioning Example”.part|partition mntpoint [options]
part|partition mntpoint [options]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - mntpoint - Where the partition is mounted. The value must be of one of the following forms:
/pathFor example,/,/usr,/homeswapThe partition is used as swap space.To determine the size of the swap partition automatically, use the--recommendedoption:swap --recommended
swap --recommendedCopy to Clipboard Copied! Toggle word wrap Toggle overflow The size assigned will be effective but not precisely calibrated for your system.To determine the size of the swap partition automatically but also allow extra space for your system to hibernate, use the--hibernationoption:swap --hibernation
swap --hibernationCopy to Clipboard Copied! Toggle word wrap Toggle overflow The size assigned will be equivalent to the swap space assigned by--recommendedplus the amount of RAM on your system.For the swap sizes assigned by these commands, see Section 8.14.4.4, “Recommended Partitioning Scheme” for 64-bit AMD, Intel, and ARM systems, Section 13.15.4.4, “Recommended Partitioning Scheme” for IBM Power Systems servers, and Section 18.15.3.4, “Recommended Partitioning Scheme” for IBM Z.raid.idThe partition is used for software RAID (seeraid).pv.idThe partition is used for LVM (seelogvol).biosbootThe partition will be used for a BIOS Boot partition. A 1 MiB BIOS boot partition is necessary on BIOS-based AMD64 and Intel 64 systems using a GUID Partition Table (GPT); the boot loader will be installed into it. It is not necessary on UEFI systems. See also thebootloadercommand./boot/efiAn EFI System Partition. A 50 MiB EFI partition is necessary on UEFI-based AMD, Intel, and ARM; the recommended size is 200 MiB. It is not necessary on BIOS systems. See also thebootloadercommand.
--size=- The minimum partition size in MiB. Specify an integer value here such as500(do not include the unit).Important
If the--sizevalue is too small, the installation fails. Set the--sizevalue as the minimum amount of space you require. For size recommendations, see Section 8.14.4.4, “Recommended Partitioning Scheme”.--grow- Tells the partition to grow to fill available space (if any), or up to the maximum size setting, if one is specified.Note
If you use--grow=without setting--maxsize=on a swap partition, Anaconda limits the maximum size of the swap partition. For systems that have less than 2 GB of physical memory, the imposed limit is twice the amount of physical memory. For systems with more than 2 GB, the imposed limit is the size of physical memory plus 2GB.--maxsize=- The maximum partition size in MiB when the partition is set to grow. Specify an integer value here such as500(do not include the unit).--noformat- Specifies that the partition should not be formatted, for use with the--onpartcommand.--onpart=or--usepart=- Uses existing blank device and format it to the new specified type. For example:partition /home --onpart=hda1
partition /home --onpart=hda1Copy to Clipboard Copied! Toggle word wrap Toggle overflow puts/homeon/dev/hda1.These options can also add a partition to a logical volume. For example:partition pv.1 --onpart=hda2
partition pv.1 --onpart=hda2Copy to Clipboard Copied! Toggle word wrap Toggle overflow The device must already exist on the system; the--onpartoption will not create it.It is also possible to specify an entire drive, rather than a partition, in which case Anaconda will format and use the drive without creating a partition table. Note, however, that installation of GRUB2 is not supported on a device formatted in this way, and must be placed on a drive with a partition table.--ondisk=or--ondrive=- Creates a partition (specified by the part command) on an existing disk. This command always creates a partition. For example,--ondisk=sdbputs the partition on the second SCSI disk on the system.To specify a multipath device that does not use logical volume management (LVM), use the formatdisk/by-id/dm-uuid-mpath-WWID, where WWID is the world-wide identifier for the device. For example, to specify a disk with WWID2416CD96995134CA5D787F00A5AA11017, use:part / --fstype=xfs --grow --asprimary --size=8192 --ondisk=disk/by-id/dm-uuid-mpath-2416CD96995134CA5D787F00A5AA11017
part / --fstype=xfs --grow --asprimary --size=8192 --ondisk=disk/by-id/dm-uuid-mpath-2416CD96995134CA5D787F00A5AA11017Copy to Clipboard Copied! Toggle word wrap Toggle overflow Warning
Never specify multipath devices by device names likempatha. Device names such as this are not specific to a particular disk. The disk named/dev/mpathaduring installation might not be the one that you expect it to be. Therefore, theclearpartcommand could target the wrong disk.--asprimary- Forces the partition to be allocated as a primary partition. If the partition cannot be allocated as primary (usually due to too many primary partitions being already allocated), the partitioning process fails. This option only makes sense when the disk uses a Master Boot Record (MBR); for GUID Partition Table (GPT)-labeled disks this option has no meaning. For information about primary (and extended) partitions, see Section A.1.2, “Partitions: Turning One Drive Into Many”.--fsprofile=- Specifies a usage type to be passed to the program that makes a filesystem on this partition. A usage type defines a variety of tuning parameters to be used when making a filesystem. For this option to work, the filesystem must support the concept of usage types and there must be a configuration file that lists valid types. Forext2,ext3,ext4, this configuration file is/etc/mke2fs.conf.--mkfsoptions=- Specifies additional parameters to be passed to the program that makes a filesystem on this partition. This is similar to--fsprofilebut works for all filesystems, not just the ones that support the profile concept. No processing is done on the list of arguments, so they must be supplied in a format that can be passed directly to the mkfs program. This means multiple options should be comma-separated or surrounded by double quotes, depending on the filesystem.--fstype=- Sets the file system type for the partition. Valid values arexfs,ext2,ext3,ext4,swap,vfat,efiandbiosboot.--fsoptions- Specifies a free form string of options to be used when mounting the filesystem. This string will be copied into the/etc/fstabfile of the installed system and should be enclosed in quotes.--label=- assign a label to an individual partition.--recommended- Determine the size of the partition automatically. For details about the recommended scheme, see Section 8.14.4.4, “Recommended Partitioning Scheme” for 64-bit AMD, Intel, and ARM, Section 13.15.4.4, “Recommended Partitioning Scheme” for IBM Power Systems, and Section 18.15.3.4, “Recommended Partitioning Scheme” for IBM Z.Important
This option can only be used for partitions which result in a file system such as the/bootpartition andswapspace. It cannot be used to create LVM physical volumes or RAID members.--onbiosdisk- Forces the partition to be created on a particular disk as discovered by the BIOS.--encrypted- Specifies that this partition should be encrypted, using the passphrase provided in the--passphraseoption. If you do not specify a passphrase, Anaconda uses the default, system-wide passphrase set with theautopart --passphrasecommand, or stops the installation and prompts you to provide a passphrase if no default is set.Note
When encrypting one or more partitions, Anaconda attempts to gather 256 bits of entropy to ensure the partitions are encrypted securely. Gathering entropy can take some time - the process will stop after a maximum of 10 minutes, regardless of whether sufficient entropy has been gathered.The process can be sped up by interacting with the installation system (typing on the keyboard or moving the mouse). If you are installing in a virtual machine, you can also attach a virtio-rng device (a virtual random number generator) to the guest as described in the Red Hat Enterprise Linux 7 Virtualization Deployment and Administration Guide.--passphrase=- Specifies the passphrase to use when encrypting this partition. You must use this option together with the--encryptedoption; by itself it has no effect.--cipher=- Specifies which type of encryption will be used if the Anaconda defaultaes-xts-plain64is not satisfactory. You must use this option together with the--encryptedoption; by itself it has no effect. Available types of encryption are listed in the Red Hat Enterprise Linux 7 Security Guide, but Red Hat strongly recommends using eitheraes-xts-plain64oraes-cbc-essiv:sha256.--escrowcert=URL_of_X.509_certificate- Store data encryption keys of all encrypted partitions as files in/root, encrypted using the X.509 certificate from the URL specified with URL_of_X.509_certificate. The keys are stored as a separate file for each encrypted partition. This option is only meaningful if--encryptedis specified.--backuppassphrase- Add a randomly-generated passphrase to each encrypted partition. Store these passphrases in separate files in/root, encrypted using the X.509 certificate specified with--escrowcert. This option is only meaningful if--escrowcertis specified.--resize=- Resize an existing partition. When using this option, specify the target size (in MiB) using the--size=option and the target partition using the--onpart=option.
Note
If partitioning fails for any reason, diagnostic messages appear on virtual console 3. -
poweroff(optional) - Shut down and power off the system after the installation has successfully completed. Normally during a manual installation, Anaconda displays a message and waits for the user to press a key before rebooting. During a Kickstart installation, if no completion method is specified, the
haltoption is used as default.Thepoweroffoption is equivalent to theshutdown -pcommand.Note
Thepoweroffcommand is highly dependent on the system hardware in use. Specifically, certain hardware components such as the BIOS, APM (advanced power management), and ACPI (advanced configuration and power interface) must be able to interact with the system kernel. Consult your hardware documentation for more information on you system's APM/ACPI abilities.For other completion methods, see thehalt,reboot, andshutdownKickstart commands. -
raid(optional) - Assembles a software RAID device. This command is of the form:
raid mntpoint --level=level --device=device-name partitions*
raid mntpoint --level=level --device=device-name partitions*Copy to Clipboard Copied! Toggle word wrap Toggle overflow - mntpoint - Location where the RAID file system is mounted. If it is
/, the RAID level must be 1 unless a boot partition (/boot) is present. If a boot partition is present, the/bootpartition must be level 1 and the root (/) partition can be any of the available types. The partitions* (which denotes that multiple partitions can be listed) lists the RAID identifiers to add to the RAID array.Important
On IBM Power Systems, if a RAID device has been prepared and has not been reformatted during the installation, ensure that the RAID metadata version is0.90if you intend to put the/bootandPRePpartitions on the RAID device.The default Red Hat Enterprise Linux 7 mdadm metadata version is not supported for the boot device.For a detailed example ofraidin action, see Section 27.4.1, “Advanced Partitioning Example”. --level=- RAID level to use (0, 1, 4, 5, 6, or 10). See Section 8.14.4.2, “Create Software RAID” for information about various available RAID levels.--device=- Name of the RAID device to use - for example,--device=root.Important
Do not usemdraidnames in the form ofmd0- these names are not guaranteed to be persistent. Instead, use meaningful names such asrootorswap. Using meaningful names creates a symbolic link from/dev/md/nameto whichever/dev/mdXnode is assigned to the array.If you have an old (v0.90 metadata) array that you cannot assign a name to, you can specify the array by a filesystem label or UUID (for example,--device=rhel7-root --label=rhel7-root).--chunksize=- Sets the chunk size of a RAID storage in KiB. In certain situations, using a different chunk size than the default (512 Kib) can improve the performance of the RAID.--spares=- Specifies the number of spare drives allocated for the RAID array. Spare drives are used to rebuild the array in case of drive failure.--fsprofile=- Specifies a usage type to be passed to the program that makes a filesystem on this partition. A usage type defines a variety of tuning parameters to be used when making a filesystem. For this option to work, the filesystem must support the concept of usage types and there must be a configuration file that lists valid types. For ext2, ext3, and ext4, this configuration file is/etc/mke2fs.conf.--fstype=- Sets the file system type for the RAID array. Valid values arexfs,ext2,ext3,ext4,swap, andvfat.--fsoptions=- Specifies a free form string of options to be used when mounting the filesystem. This string will be copied into the/etc/fstabfile of the installed system and should be enclosed in quotes.--mkfsoptions=- Specifies additional parameters to be passed to the program that makes a filesystem on this partition. No processing is done on the list of arguments, so they must be supplied in a format that can be passed directly to the mkfs program. This means multiple options should be comma-separated or surrounded by double quotes, depending on the filesystem.--label=- Specify the label to give to the filesystem to be made. If the given label is already in use by another filesystem, a new label will be created.--noformat- Use an existing RAID device and do not format the RAID array.--useexisting- Use an existing RAID device and reformat it.--encrypted- Specifies that this RAID device should be encrypted, using the passphrase provided in the--passphraseoption. If you do not specify a passphrase, Anaconda uses the default, system-wide passphrase set with theautopart --passphrasecommand, or stops the installation and prompts you to provide a passphrase if no default is set.Note
When encrypting one or more partitions, Anaconda attempts to gather 256 bits of entropy to ensure the partitions are encrypted securely. Gathering entropy can take some time - the process will stop after a maximum of 10 minutes, regardless of whether sufficient entropy has been gathered.The process can be sped up by interacting with the installation system (typing on the keyboard or moving the mouse). If you are installing in a virtual machine, you can also attach a virtio-rng device (a virtual random number generator) to the guest as described in the Red Hat Enterprise Linux 7 Virtualization Deployment and Administration Guide.--cipher=- Specifies which type of encryption will be used if the Anaconda default aes-xts-plain64 is not satisfactory. You must use this option together with the--encryptedoption; by itself it has no effect. Available types of encryption are listed in the Red Hat Enterprise Linux 7 Security Guide, but Red Hat strongly recommends using either aes-xts-plain64 or aes-cbc-essiv:sha256.--passphrase=- Specifies the passphrase to use when encrypting this RAID device. You must use this option together with the--encryptedoption; by itself it has no effect.--escrowcert=URL_of_X.509_certificate- Store the data encryption key for this device in a file in/root, encrypted using the X.509 certificate from the URL specified with URL_of_X.509_certificate. This option is only meaningful if--encryptedis specified.--backuppassphrase- Add a randomly-generated passphrase to this device. Store the passphrase in a file in/root, encrypted using the X.509 certificate specified with--escrowcert. This option is only meaningful if--escrowcertis specified.
The following example shows how to create a RAID level 1 partition for/, and a RAID level 5 for/home, assuming there are three SCSI disks on the system. It also creates three swap partitions, one on each drive.Example 27.4. Using the raid Kickstart command
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
realm(optional) - Join an Active Directory or IPA domain. For more information about this command, see the
joinsection of therealm(8)man page.realm join [options] domain
realm join [options] domainCopy to Clipboard Copied! Toggle word wrap Toggle overflow --computer-ou=OU=- Provide the distinguished name of an organizational unit in order to create the computer account. The exact format of the distinguished name depends on the client software and membership software. The root DSE portion of the distinguished name can usually be left out.--no-password- Join automatically without a password.--one-time-password=- Join using a one-time password. This is not possible with all types of realm.--client-software=- Only join realms which can run this client software. Valid values includesssdandwinbind. Not all realms support all values. By default, the client software is chosen automatically.--server-software=- Only join realms which can run this server software. Possible values includeactive-directoryorfreeipa.--membership-software=- Use this software when joining the realm. Valid values includesambaandadcli. Not all realms support all values. By default, the membership software is chosen automatically.
-
reboot(optional) - Reboot after the installation is successfully completed (no arguments). Normally, Kickstart displays a message and waits for the user to press a key before rebooting.The
rebootoption is equivalent to theshutdown -rcommand.Specifyrebootto automate installation fully when installing in command line mode on IBM Z.For other completion methods, see thehalt,poweroff, andshutdownKickstart options.Thehaltoption is the default completion method if no other methods are explicitly specified in the Kickstart file.Note
Use of therebootoption might result in an endless installation loop, depending on the installation media and method.--eject- Attempt to eject the bootable media (DVD, USB, or other media) before rebooting.--kexec- Uses the kexec system call instead of performing a full reboot, which immediately loads the installed system into memory, bypassing the hardware initialization normally performed by the BIOS or firmware.Important
Due to the complexities involved with booting systems using kexec, it cannot be explicitly tested and guaranteed to function in every situation.When kexec is used, device registers (which would normally be cleared during a full system reboot) might stay filled with data, which could potentially create issues for some device drivers.
-
repo(optional) - Configures additional yum repositories that can be used as sources for package installation. You can add multiple
repolines.repo --name=repoid [--baseurl=<url>|--mirrorlist=url] [options]
repo --name=repoid [--baseurl=<url>|--mirrorlist=url] [options]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --name=- The repository id. This option is required. If a repository has a name which conflicts with another previously added repository, it is ignored. Because the installation program uses a list of preset repositories, this means that you cannot add repositories with the same names as the preset ones.--baseurl=- The URL to the repository. The variables that can be used in yum repo config files are not supported here. This option cannot be used together with the--mirrorlistoption in the same repository definition.--mirrorlist=- The URL pointing at a list of mirrors for the repository. The variables that can be used in yum repository configuration files are not supported here. This option cannot be used together with the--baseurloption in the same repository definition.--install- Save the provided repository configuration on the installed system in the/etc/yum.repos.d/directory. Without using this option, a repository configured in a Kickstart file will only be available during the installation process, not on the installed system.--cost=- An integer value to assign a cost to this repository. If multiple repositories provide the same packages, this number is used to prioritize which repository will be used before another. Repositories with a lower cost take priority over repositories with higher cost.--excludepkgs=- A comma-separated list of package names that must not be pulled from this repository. This is useful if multiple repositories provide the same package and you want to make sure it comes from a particular repository. Both full package names (such aspublican) and globs (such asgnome-*) are accepted.--includepkgs=- A comma-separated list of package names and globs that must be pulled from this repository. This is useful if multiple repositories provide the same package and you want to make sure it comes from this repository.--proxy=[protocol://][username[:password]@]host[:port]- Specify an HTTP/HTTPS/FTP proxy to use just for this repository. This setting does not affect any other repositories, nor how theinstall.imgis fetched on HTTP installations.--ignoregroups=true- This option is used when composing installation trees and has no effect on the installation process itself. It tells the compose tools to not look at the package group information when mirroring trees so as to avoid mirroring large amounts of unnecessary data.--noverifyssl- Disable SSL verification when connecting to anHTTPSserver.
Important
Repositories used for installation must be stable. The installation can fail if a repository is modified before the installation concludes. -
rescue(optional) - Automatically enters the installation program's rescue mode. This gives you a chance to repair the system in case of any problems.
rescue [--nomount|--romount]
rescue [--nomount|--romount]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --nomountor--romount- Controls how the installed system is mounted in the rescue environment. By default, the installation program finds your system and mount it in read-write mode, telling you where it has performed this mount. You can optionally select to not mount anything (the--nomountoption) or mount in read-only mode (the--romountoption). Only one of these two options can be used.
-
reqpart(optional) - Automatically creates partitions required by your hardware platform. These include a
/boot/efipartition for systems with UEFI firmware, abiosbootpartition for systems with BIOS firmware and GPT, and aPRePBootpartition for IBM Power Systems.reqpart [--add-boot]
reqpart [--add-boot]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --add-boot- Creates a separate/bootpartition in addition to the platform-specific partition created by the base command.
Note
This command cannot be used toegether withautopart, becauseautopartdoes everything thereqpartcommand does and, in addition, creates other partitions or logical volumes such as/andswap. In contrast withautopart, this command only creates platform-specific partitions and leaves the rest of the drive empty, allowing you to create a custom layout. -
rootpw(required) - Sets the system's root password to the password argument.
rootpw [--iscrypted|--plaintext] [--lock] password
rootpw [--iscrypted|--plaintext] [--lock] passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow --iscrypted- If this option is present, the password argument is assumed to already be encrypted. This option is mutually exclusive with--plaintext. To create an encrypted password, you can use python:python -c 'import crypt,getpass;pw=getpass.getpass();print(crypt.crypt(pw) if (pw==getpass.getpass("Confirm: ")) else exit())'$ python -c 'import crypt,getpass;pw=getpass.getpass();print(crypt.crypt(pw) if (pw==getpass.getpass("Confirm: ")) else exit())'Copy to Clipboard Copied! Toggle word wrap Toggle overflow This generates a sha512 crypt-compatible hash of your password using a random salt.--plaintext- If this option is present, the password argument is assumed to be in plain text. This option is mutually exclusive with--iscrypted.--lock- If this option is present, the root account is locked by default. This means that the root user will not be able to log in from the console. This option will also disable the Root Password screens in both the graphical and text-based manual installation.
-
selinux(optional) - Sets the state of SELinux on the installed system. The default SELinux policy is
enforcing.selinux [--disabled|--enforcing|--permissive]
selinux [--disabled|--enforcing|--permissive]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --enforcing- Enables SELinux with the default targeted policy beingenforcing.--permissive- Outputs warnings based on the SELinux policy, but does not actually enforce the policy.--disabled- Disables SELinux completely on the system.
For more information regarding SELinux, see the Red Hat Enterprise Linux 7 SELinux User's and Administrator's Guide. -
services(optional) - Modifies the default set of services that will run under the default systemd target. The list of disabled services is processed before the list of enabled services. Therefore, if a service appears on both lists, it will be enabled.
services [--disabled=list] [--enabled=list]
services [--disabled=list] [--enabled=list]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --disabled=- Disable the services given in the comma separated list.--enabled=- Enable the services given in the comma separated list.
Important
Do not include spaces in the list of services. If you do, Kickstart will enable or disable only the services up to the first space. For example:services --disabled=auditd, cups,smartd, nfslock
services --disabled=auditd, cups,smartd, nfslockCopy to Clipboard Copied! Toggle word wrap Toggle overflow disables only theauditdservice. To disable all four services, this entry should include no spaces:services --disabled=auditd,cups,smartd,nfslock
services --disabled=auditd,cups,smartd,nfslockCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
shutdown(optional) - Shut down the system after the installation has successfully completed. During a Kickstart installation, if no completion method is specified, the
haltcommand is used.TheshutdownKickstart option is equivalent to theshutdowncommand.For other completion methods, see thehalt,poweroff, andrebootKickstart options. -
skipx(optional) - If present, X is not configured on the installed system.
Important
If you install a display manager among your package selection options, this package creates an X configuration, and the installed system defaults tographical.target. The effect of theskipxoption is overridden. -
snapshot(optional) - Using the
snapshotcommand, you can create LVM thin volume snapshots during the installation process. This enables you to back up a logical volume before or after the installation.To create multiple snapshots, add thesnaphostKickstart command multiple times.snapshots vg_name/lv_name --name=snapshot_name --when=pre-install|post-install
snapshots vg_name/lv_name --name=snapshot_name --when=pre-install|post-installCopy to Clipboard Copied! Toggle word wrap Toggle overflow vg_name/lv_name- Sets the name of the volume group and logical volume to create the snapshot from.--name=snapshot_name- Sets the name of the snapshot. This name must be unique within the volume group.--when=pre-install|post-install- Sets if the snapshot is created before the installation begins or after the installation is completed.
-
sshpw(optional) - During the installation, you can interact with the installation program and monitor its progress over an
SSHconnection. Use thesshpwcommand to create temporary accounts through which to log on. Each instance of the command creates a separate account that exists only in the installation environment. These accounts are not transferred to the installed system.sshpw --username=name password [--iscrypted|--plaintext] [--lock]
sshpw --username=name password [--iscrypted|--plaintext] [--lock]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --username- Provides the name of the user. This option is required.--iscrypted- If this option is present, the password argument is assumed to already be encrypted. This option is mutually exclusive with--plaintext. To create an encrypted password, you can use python:python -c 'import crypt,getpass;pw=getpass.getpass();print(crypt.crypt(pw) if (pw==getpass.getpass("Confirm: ")) else exit())'$ python -c 'import crypt,getpass;pw=getpass.getpass();print(crypt.crypt(pw) if (pw==getpass.getpass("Confirm: ")) else exit())'Copy to Clipboard Copied! Toggle word wrap Toggle overflow This generates a sha512 crypt-compatible hash of your password using a random salt.--plaintext- If this option is present, the password argument is assumed to be in plain text. This option is mutually exclusive with--iscrypted--lock- If this option is present, this account is locked by default. This means that the user will not be able to log in from the console.--ssh- If this is option is present, then the password string is interpreted as an ssh key value.
Important
By default, thesshserver is not started during the installation. To makesshavailable during the installation, boot the system with the kernel boot optioninst.sshd. See Console, Environment and Display Options for details.Note
If you want to disable rootsshaccess, while allowing another usersshaccess, use the following:sshpw --username=example_username example_password --plaintext sshpw --username=root example_password --lock
sshpw --username=example_username example_password --plaintext sshpw --username=root example_password --lockCopy to Clipboard Copied! Toggle word wrap Toggle overflow To simply disable rootsshaccess, use the following:sshpw --username=root example_password --lock
sshpw --username=root example_password --lockCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
text(optional) - Perform the Kickstart installation in text mode. Kickstart installations are performed in graphical mode by default.
Important
For a fully automatic installation, you must either specify one of the available modes (graphical,text, orcmdline) in the Kickstart file, or you must use theconsole=boot option as described in Console, Environment and Display Options. If no mode is specified, the system will prompt you to choose one before continuing. -
timezone(required) - Sets the system time zone to timezone.
timezone timezone [options]
timezone timezone [options]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --utc- If present, the system assumes the hardware clock is set to UTC (Greenwich Mean) time.--nontp- Disable the NTP service automatic starting.--ntpservers=- Specify a list of NTP servers to be used as a comma-separated list without spaces.
Starting with Red Hat Entrerprise Linux 7.5, time zone names are validated using thepytz.all_timezoneslist, provided by the pytz package. In previous releases, the names were validated againstpytz.common_timezones, which is a subset of the currently used list. Note that the graphical and text mode interfaces still use the more restrictedpytz.common_timezoneslist; you must use a Kickstart file to use additional time zone definitions. -
unsupported_hardware(optional) - Tells the installation program to suppress the Unsupported Hardware Detected alert. If this command is not included and unsupported hardware is detected, the installation stalls at this alert.
-
user(optional) - Creates a new user on the system.
user --name=username [options]
user --name=username [options]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --name=- Provides the name of the user. This option is required.--gecos=- Provides the GECOS information for the user. This is a string of various system-specific fields separated by a comma. It is frequently used to specify the user's full name, office number, and so on. See thepasswd(5)man page for more details.--groups=- In addition to the default group, a comma separated list of group names the user should belong to. The groups must exist before the user account is created. See thegroupcommand.--homedir=- The home directory for the user. If not provided, this defaults to/home/username.--lock- If this option is present, this account is locked by default. This means that the user will not be able to log in from the console. This option will also disable the Create User screens in both the graphical and text-based manual installation.--password=- The new user's password. If not provided, the account will be locked by default.--iscrypted- If this option is present, the password argument is assumed to already be encrypted. This option is mutually exclusive with--plaintext. To create an encrypted password, you can use python:python -c 'import crypt,getpass;pw=getpass.getpass();print(crypt.crypt(pw) if (pw==getpass.getpass("Confirm: ")) else exit())'$ python -c 'import crypt,getpass;pw=getpass.getpass();print(crypt.crypt(pw) if (pw==getpass.getpass("Confirm: ")) else exit())'Copy to Clipboard Copied! Toggle word wrap Toggle overflow This generates a sha512 crypt-compatible hash of your password using a random salt.--plaintext- If this option is present, the password argument is assumed to be in plain text. This option is mutually exclusive with--iscrypted--shell=- The user's login shell. If not provided, the system default is used.--uid=- The user's UID (User ID). If not provided, this defaults to the next available non-system UID.--gid=- The GID (Group ID) to be used for the user's group. If not provided, this defaults to the next available non-system group ID.Note
Consider using the--uidand--gidoptions to set IDs of regular users and their default groups at range starting at5000instead of1000. That is because the range reserved for system users and groups,0-999, might increase in the future and thus overlap with IDs of regular users.For changing the minimum UID and GID limits after the installation, which ensures that your chosen UID and GID ranges are applied automatically on user creation, see the Users and Groups chapter of the System Administrator's Guide.
Note
Files and directories are created with various permissions, dictated by the application used to create the file or directory. For example, themkdircommand creates directories with all permissions enabled. However, applications are prevented from granting certain permissions to newly created files, as specified by theuser file-creation masksetting.Theuser file-creation maskcan be controlled with theumaskcommand. The default setting of theuser file-creation maskfor new users is defined by theUMASKvariable in the/etc/login.defsconfiguration file on the installed system. If unset, it defaults to022. This means that by default when an application creates a file, it is prevented from granting write permission to users other than the owner of the file. However, this can be overridden by other settings or scripts. More information can be found in the Red Hat Enterprise Linux 7 System Administrator's Guide. -
vnc(optional) - Allows the graphical installation to be viewed remotely through VNC. This method is usually preferred over text mode, as there are some size and language limitations in text installations. With no additional options, this command starts a VNC server on the installation system with no password and displays the details required to connect to it.
vnc [--host=host_name] [--port=port] [--password=password]
vnc [--host=host_name] [--port=port] [--password=password]Copy to Clipboard Copied! Toggle word wrap Toggle overflow --host=- Connect to the VNC viewer process listening on the given host name.--port=- Provide a port that the remote VNC viewer process is listening on. If not provided, Anaconda uses the VNC default port of 5900.--password=- Set a password which must be provided to connect to the VNC session. This is optional, but recommended.
For more information about VNC installations, including instructions on how to connect to the installation system, see Chapter 25, Using VNC. -
volgroup(optional) - Creates a Logical Volume Management (LVM) group.
volgroup name partition [options]
volgroup name partition [options]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Important
Do not use the dash (-) character in logical volume and volume group names when installing Red Hat Enterprise Linux using Kickstart. If this character is used, the installation finishes normally, but the/dev/mapper/directory will list these volumes and volume groups with every dash doubled. For example, a volume group namedvolgrp-01containing a logical volume namedlogvol-01will be listed as/dev/mapper/volgrp--01-logvol--01.This limitation only applies to newly created logical volume and volume group names. If you are reusing existing ones using the--noformatoption, their names will not be changed.For a detailed partitioning example includingvolgroup, see Section 27.4.1, “Advanced Partitioning Example”.The options are as follows:--noformat- Use an existing volume group and do not format it.--useexisting- Use an existing volume group and reformat it. If you use this option, do not specify a partition. For example:volgroup rhel00 --useexisting --noformat
volgroup rhel00 --useexisting --noformatCopy to Clipboard Copied! Toggle word wrap Toggle overflow --pesize=- Set the size of the volume group's physical extents in KiB. The default value is 4096 (4 MiB), and the minimum value is 1024 (1 MiB).--reserved-space=- Specify an amount of space to leave unused in a volume group in MiB. Applicable only to newly created volume groups.--reserved-percent=- Specify a percentage of total volume group space to leave unused. Applicable only to newly created volume groups.
Create the partition first, then create the logical volume group, and then create the logical volume. For example:part pv.01 --size 10000 volgroup volgrp pv.01 logvol / --vgname=volgrp --size=2000 --name=root
part pv.01 --size 10000 volgroup volgrp pv.01 logvol / --vgname=volgrp --size=2000 --name=rootCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
xconfig(optional) - Configures the X Window System. If you install the X Window System with a Kickstart file that does not include the
xconfigcommand, you must provide the X configuration manually during installation.Do not use this command in a Kickstart file that does not install the X Window System.--defaultdesktop=- Specify eitherGNOMEorKDEto set the default desktop (assumes that the chosen environment, either the GNOME Desktop Environment or the KDE Desktop Environment, has been installed in the%packagessection).Important
It is currently not possible to specify KDE as your default desktop environment using this option. This is a known issue. See https://access.redhat.com/solutions/1125833 for a workaround. The workaround can be used as a Kickstart post-installation script as described in Section 27.3.5, “Post-installation Script”.--startxonboot- Use a graphical login on the installed system.
-
zerombr(optional) - The
zerombrinitializes any invalid partition tables that are found on disks and destroys all of the contents of disks with invalid partition tables. This command is required when performing an installation on an IBM Z system with unformatted Direct Access Storage Device (DASD) disks, otherwise the unformatted disks are not formatted and used during the installation.Warning
On IBM Z, ifzerombris specified, any Direct Access Storage Device (DASD) visible to the installation program which is not already low-level formatted is automatically low-level formatted with dasdfmt. The command also prevents user choice during interactive installations.Ifzerombris not specified and there is at least one unformatted DASD visible to the installation program, a non-interactive Kickstart installation exits unsuccessfully.Ifzerombris not specified and there is at least one unformatted DASD visible to the installation program, an interactive installation exits if the user does not agree to format all visible and unformatted DASDs. To circumvent this, only activate those DASDs that you will use during installation. You can always add more DASDs after installation is complete. -
zfcp(optional) - Define a Fibre channel device. This option only applies on IBM Z. All of the options described below must be specified.
zfcp --devnum=devnum --wwpn=wwpn --fcplun=lun
zfcp --devnum=devnum --wwpn=wwpn --fcplun=lunCopy to Clipboard Copied! Toggle word wrap Toggle overflow --devnum- The device number (zFCP adapter device bus ID).--wwpn- The device's World Wide Port Name (WWPN). Takes the form of a 16-digit number, preceded by0x.--fcplun- The device's Logical Unit Number (LUN). Takes the form of a 16-digit number, preceded by0x.
For example:zfcp --devnum=0.0.4000 --wwpn=0x5005076300C213e9 --fcplun=0x5022000000000000
zfcp --devnum=0.0.4000 --wwpn=0x5005076300C213e9 --fcplun=0x5022000000000000Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
%include(optional) - Use the
%include /path/to/filecommand to include the contents of another file in the Kickstart file as though the contents were at the location of the%includecommand in the Kickstart file.
27.3.2. Package Selection
%packages command to begin a Kickstart section which describes the software packages to be installed.
repodata/*-comps-variant.architecture.xml file on the Red Hat Enterprise Linux 7 Installation DVD for a list of environments and groups.
*-comps-variant.architecture.xml file contains a structure describing available environments (marked by the <environment> tag) and groups (the <group> tag). Each entry has an ID, user visibility value, name, description, and package list. If the group is selected for installation, the packages marked mandatory in the package list are always installed, the packages marked default are installed if they are not specifically excluded elsewhere, and the packages marked optional must be specifically included elsewhere even when the group is selected.
<id> tag) or name (the <name> tag).
Important
Important
--multilib option also must be specified in the Kickstart file; see the available options below.
Important
root are created. You can either create a user with the user option in the Kickstart file before installing additional systems from it (see Section 27.3.1, “Kickstart Commands and Options” for details) or log into the installed system with a virtual console as root and add users with the useradd command.
%packages section must end with the %end command.
- Specifying an Environment
- In addition to groups, you specify an entire environment to be installed:
%packages @^Infrastructure Server %end
%packages @^Infrastructure Server %endCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command installs all packages which are part of the Infrastracture Server environment. All available environments are described in therepodata/*-comps-variant.architecture.xmlfile on the Red Hat Enterprise Linux 7 Installation DVD. Only a single environment can be specified in the Kickstart file. - Specifying Groups
- Specify groups, one entry to a line, starting with an
@symbol, and then the full group name or group id as given in the*-comps-variant.architecture.xmlfile. For example:%packages @X Window System @Desktop @Sound and Video %end
%packages @X Window System @Desktop @Sound and Video %endCopy to Clipboard Copied! Toggle word wrap Toggle overflow TheCoregroup is always selected - it is not necessary to specify it in the%packagessection.The*-comps-variant.architecture.xmlfile also defines groups calledConflicts (variant)for each variant of Red Hat Enterprise Linux. This group contains all packages which are known to cause file conflicts, and is intended to be excluded. - Specifying Individual Packages
- Specify individual packages by name, one entry to a line. You can use the asterisk character (
*) as a wildcard in package names. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Thedocbook*entry includes the packages docbook-dtds, docbook-simple, docbook-slides and others that match the pattern represented with the wildcard. - Excluding Environments, Groups, or Packages
- Use a leading dash (
-) to specify packages or groups to exclude from the installation. For example:%packages -@Graphical Internet -autofs -ipa*fonts %end
%packages -@Graphical Internet -autofs -ipa*fonts %endCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Important
* in a Kickstart file is not supported, even if you exclude the @Conflicts (variant) group.
%packages section by using several options. Some options work for the entire package selection, others are used with only specific groups.
Common Package Selection Options
%packages. To use an option, append it to the start of the package selection section. For example:
%packages --multilib --ignoremissing
%packages --multilib --ignoremissing-
--default - Install the default set of packages. This corresponds to the package set which would be installed if no other selections were made in the Package Selection screen during an interactive installation.
-
--excludedocs - Do not install any documentation contained within packages. In most cases, this excludes any files normally installed in the
/usr/share/docdirectory, but the specific files to be excluded depend on individual packages. -
--ignoremissing - Ignore any packages, groups and environments missing in the installation source, instead of halting the installation to ask if the installation should be aborted or continued.
-
--instLangs= - Specify a list of languages to install. Note that this is different from package group level selections. This option does not describe which package groups should be installed; instead, it sets RPM macros controlling which translation files from individual packages should be installed.Red Hat Enterprise Linux packages use the ISO 639 language codes. Running the
locale -acommand provides you with a comprehensive list of language codes applicable with%packages --instLangs=arguments.Example 27.5. Specifying a list of languages to install
- A colon separated list of language codes installs specified locales:
%packages --instLangs=es:fr:it
%packages --instLangs=es:fr:itCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Omitting the
--instLangs=option installs all locales:%packages
%packagesCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Omitting language codes installs no locales:
%packages --instLangs=
%packages --instLangs=Copy to Clipboard Copied! Toggle word wrap Toggle overflow
-
--multilib - Configure the installed system for multilib packages, to allow installing 32-bit packages on a 64-bit system, and install packages specified in this section as such.Normally, on an AMD64 and Intel 64 system, you can install only the
x86_64and thenoarchpackages. However, with the --multilib option, you can automatically install the 32-bit AMD and the i686 Intel system packages available, if any.This only applies to packages explicitly specified in the%packagessection. Packages which are only being installed as dependencies without being specified in the Kickstart file are only installed in architecture versions in which they are needed, even if they are available for more architectures.This option works both during the installation and on the running system using the `yum` command. -
--nocore - Disables installation of the
@Corepackage group which is otherwise always installed by default. Disabling the@Corepackage group with--nocoreshould be only used for creating lightweight containers; installing a desktop or server system with--nocorewill result in an unusable system.Note
- Using
-@Coreto exclude packages in the@Corepackage group does not work. The only way to exclude the@Corepackage group is with the--nocoreoption. - The
@Corepackage group is defined as a minimal set of packages needed for installing a working system. It is not related in any way to core packages as defined in the Package Manifest and Scope of Coverage Details.
--retries=- Sets the number of times Yum will attempt to download packages (retries). The default value is
10. This option only applies during the installation, and will not affect Yum configuration on the installed system. --timeout=- Sets the Yum timeout in seconds. The default value is
30. This option only applies during the installation, and will not affect Yum configuration on the installed system.
Options for Specific Package Groups
%packages command in the Kickstart file, append them to the group name. For example:
%packages @Graphical Internet --optional %end
%packages
@Graphical Internet --optional
%end-
--nodefaults - Only install the group's mandatory packages, not the default selections.
-
--optional - Install packages marked as optional in the group definition in the
*-comps-variant.architecture.xmlfile, in addition to installing the default selections.Note that some package groups, such asScientific Support, do not have any mandatory or default packages specified - only optional packages. In this case the--optionaloption must always be used, otherwise no packages from this group will be installed.
27.3.3. Pre-installation Script
%pre script is run on the system immediately after the Kickstart file has been parsed, but before installation begins. This section must be placed towards the end of the Kickstart file, after the Kickstart commands described in Section 27.3.1, “Kickstart Commands and Options”, and must start with %pre and end with %end. If your Kickstart file also includes a %post section, the order in which the %pre and %post sections are included does not matter.
%pre script can be used for activation and configuration of networking and storage devices. It is also possible to run scripts, using interpreters available in the installation environment. Adding a %pre script can be useful if you have networking and storage that needs special configuration before proceeding with the installation, or have a script that, for example, sets up additional logging parameters or environment variables. Debugging problems with %pre scripts can be difficult, so it is recommended only to use a %pre script when necessary.
Important
%pre section of Kickstart is executed at the stage of installation which happens after the installer image (inst.stage2) is fetched: it means after root switches to the installer environment (the installer image) and after the Anaconda installer itself starts. Then the configuration in %pre is applied and can be used to fetch packages from installation repositories configured, for example, by URL in Kickstart. However, it cannot be used to configure network to fetch the image (inst.stage2) from network.
%pre script, in addition to most of the utilities in the installation environment's /sbin and /bin directories.
%pre section. However, the name service has not been configured at this point, so only IP addresses work, not URLs.
Note
chroot environment.
%pre line at the beginning of the script. For example:
%pre --interpreter=/usr/bin/python --- Python script omitted -- %end
%pre --interpreter=/usr/bin/python
--- Python script omitted --
%end--interpreter=- Allows you to specify a different scripting language, such as Python. Any scripting language available on the system can be used; in most cases, these are
/usr/bin/sh,/usr/bin/bash, and/usr/bin/python. --erroronfail- Display an error and halt the installation if the script fails. The error message will direct you to where the cause of the failure is logged.
--log=- Logs the script's output into the specified log file. For example:
%pre --log=/mnt/sysimage/root/ks-pre.log
%pre --log=/mnt/sysimage/root/ks-pre.logCopy to Clipboard Copied! Toggle word wrap Toggle overflow
%pre section:
Example 27.6. Sample %pre Script
%include /tmp/part-include
%include /tmp/part-include27.3.4. Anaconda configuration
%anaconda section of your Kickstart file. This section controls the behavior of the user interface of the installation system.
%anaconda and end with %end.
%anaconda section is pwpolicy. See Section 27.3.1, “Kickstart Commands and Options” for more details.
%anaconda section:
Example 27.7. Sample %anaconda Script
%anaconda pwpolicy root --minlen=10 --strict %end
%anaconda
pwpolicy root --minlen=10 --strict
%end%anaconda section sets a password policy which requires that the root password be at least 10 characters long, and strictly forbids passwords which do not match this requirement.
27.3.5. Post-installation Script
%post and end with %end. If your Kickstart file also includes a %pre section, the order of the %pre and %post sections does not matter.
--nochroot option as described below.
systemctl commands will refuse to perform any action. For more information, see the "Behavior of systemctl in a chroot Environment" section of System Administrator's Guide for Red Hat Enterprise Linux 7.
Important
%post section. If you configured the network for DHCP, the /etc/resolv.conf file has not been completed when the installation executes the %post section. You can access the network, but you cannot resolve IP addresses. Thus, if you are using DHCP, you must specify IP addresses in the %post section.
%post line at the beginning of the script. For example:
%post --interpreter=/usr/bin/python --- Python script omitted -- %end
%post --interpreter=/usr/bin/python
--- Python script omitted --
%end--interpreter=- Allows you to specify a different scripting language, such as Python. For example:
%post --interpreter=/usr/bin/python
%post --interpreter=/usr/bin/pythonCopy to Clipboard Copied! Toggle word wrap Toggle overflow Any scripting language available on the system can be used; in most cases, these are/usr/bin/sh,/usr/bin/bash, and/usr/bin/python. --nochroot- Allows you to specify commands that you would like to run outside of the chroot environment.The following example copies the file
/etc/resolv.confto the file system that was just installed.%post --nochroot cp /etc/resolv.conf /mnt/sysimage/etc/resolv.conf %end
%post --nochroot cp /etc/resolv.conf /mnt/sysimage/etc/resolv.conf %endCopy to Clipboard Copied! Toggle word wrap Toggle overflow --erroronfail- Display an error and halt the installation if the script fails. The error message will direct you to where the cause of the failure is logged.
--log=- Logs the script's output into the specified log file. Note that the path of the log file must take into account whether or not you use the
--nochrootoption. For example, without--nochroot:%post --log=/root/ks-post.log
%post --log=/root/ks-post.logCopy to Clipboard Copied! Toggle word wrap Toggle overflow with--nochroot:%post --nochroot --log=/mnt/sysimage/root/ks-post.log
%post --nochroot --log=/mnt/sysimage/root/ks-post.logCopy to Clipboard Copied! Toggle word wrap Toggle overflow
%post section:
Example 27.8. Sample %post Script
runme located at /usr/new-machines/ on the share. Note that NFS file locking is not supported while in Kickstart mode, therefore the -o nolock option is required.
%post script:
Example 27.9. Running subscription-manager as a Post-Install Script
%post --log=/root/ks-post.log /usr/sbin/subscription-manager register --username=admin@example.com --password=secret --serverurl=sam-server.example.com --org="Admin Group" --environment="Dev" --servicelevel=standard --release="7.0" %end
%post --log=/root/ks-post.log
/usr/sbin/subscription-manager register --username=admin@example.com --password=secret --serverurl=sam-server.example.com --org="Admin Group" --environment="Dev" --servicelevel=standard --release="7.0"
%endsubscription-manager command-line script registers a system to a Red Hat Subscription Management server (Customer Portal Subscription Management, Subscription Asset Manager, or CloudForms System Engine). This script can also be used to assign or attach subscriptions automatically to the system that best-match that system.
subscription-manager in a Kickstart %post section.
27.3.6. Kickstart error handling
%onerror scripts in the order they are provided in the Kickstart file. In addition, %onerror scripts will be run in the event of a traceback.
%onerror script is required to end with %end.
--erroronfail- Display an error and halt the installation if the script fails. The error message will direct you to where the cause of the failure is logged.
--interpreter=- Allows you to specify a different scripting language, such as Python. For example:
%post --interpreter=/usr/bin/python
%post --interpreter=/usr/bin/pythonCopy to Clipboard Copied! Toggle word wrap Toggle overflow Any scripting language available on the system can be used; in most cases, these are/usr/bin/sh,/usr/bin/bash, and/usr/bin/python. --log=- Logs the script's output into the specified log file.
27.3.7. Kickstart Add-ons
%addon addon_name options command, and finish the command with an %end statement, similar to pre-installation and post-installation scripts described in previous sections. For example, if you want to use the Kdump add-on, which is distributed with Anaconda by default, use the following commands:
%addon com_redhat_kdump --enable --reserve-mb=auto %end
%addon com_redhat_kdump --enable --reserve-mb=auto
%end%addon command does not include any options of its own - all options are dependent on the actual add-on. For more information about add-ons, see the Red Hat Enterprise Linux 7 Anaconda Customization Guide.
27.4. Sample Kickstart Configurations
27.4.1. Advanced Partitioning Example
clearpart, zerombr, part, raid, volgroup, and logvol Kickstart options in action:
Example 27.10. Advanced Partitioning Example
clearpart command is used on drives hda and hdc to wipe them. The zerombr command initializes unused partition tables.
/ (root), /safe, swap and /usr. The fifth, largest pair of partitions is named pv.01 and will be used in the following part as a physical volume for LVM.
sysvg on the pv.01 physical volume. Then, three logical volumes (/var, /var/freespace and /usr/local) are created and added to the sysvg volume group. The /var and /var/freespace volumes have a set size of 8 GB, and the /usr/local volume uses the --grow option to fill all remaining available space.
27.4.2. User Input Example
Example 27.11. User Input Example
exec < /dev/tty6 > /dev/tty6 2> /dev/tty6 and chvt 6 commands. The read USERINPUT reads input from the user until enter is pressed, and stores it in the variable USERINPUT. The echo -n "You entered:" "$USERINPUT" command displays the text You entered: followed by the user's input. Finally, the chvt 1 and exec < /dev/tty1 > /dev/tty1 2> /dev/tty1 commands switch back to the original terminal and allow Kickstart to continue installation.
27.4.3. Example Kickstart file for installing and starting the RNG daemon
Example 27.12. Example Kickstart file for installing and starting the RNG daemon
services --enabled=rngd %packages rng-tools %end
services --enabled=rngd
%packages
rng-tools
%endservices --enabled=rngd command instructs the installed system to start the RNG daemon each time the system starts. The rng-tools package, which contains the RNG daemon, is then designated for installation.
Chapter 28. Installing into a Disk Image
Note
Important
28.1. Manual Disk Image Installation
anaconda -h command.
Warning
28.1.1. Preparing a Disk Image
fallocate -l size name
$ fallocate -l size name10G or 5000M), and name with the file name of the image to be created. For example, to create a disk image file named myimage.raw with the size of 30GB, use the following command:
fallocate -l 30G myimage.raw
$ fallocate -l 30G myimage.rawNote
fallocate command allows you to specify the size of the file to be created in different ways, depending on the suffix used. For details about specifying the size, see the fallocate(1) man page.
- Section 8.14.4.4, “Recommended Partitioning Scheme” for 64-bit AMD, Intel, and ARM systems
- Section 13.15.4.4, “Recommended Partitioning Scheme” for IBM Power Systems servers
28.1.2. Installing Red Hat Enterprise Linux into a Disk Image
Important
SELinux) to permissive (or disabled) mode before creating custom images with Anaconda. See Red Hat Enterprise Linux 7 SELinux User's and Administrator's Guide for information on setting SELinux modes.
root:
anaconda --image=/path/to/image/file
# anaconda --image=/path/to/image/fileanaconda command. You can view the full list of supported commands by executing anaconda -h on a command line.
--repo=, which allows you to specify an installation source. This option uses the same syntax as the inst.repo= boot option. See Section 23.1, “Configuring the Installation System at the Boot Menu” for more information.
--image= option, only the disk image file specified will be available as the installation target. No other devices will be visible in the Installation Destination dialog. If you want to use multiple disk images, you must specify the --image= option separately for each image file separately. For example:
anaconda --image=/home/testuser/diskinstall/image1.raw --image=/home/testuser/diskinstall/image2.raw
# anaconda --image=/home/testuser/diskinstall/image1.raw --image=/home/testuser/diskinstall/image2.raw:name to the end of the disk image file name. For example, to use a disk image file located in /home/testuser/diskinstall/image1.raw and assign the name myimage to it, execute the following command:
anaconda --image=/home/testuser/diskinstall/image1.raw:myimage
# anaconda --image=/home/testuser/diskinstall/image1.raw:myimage28.2. Automatic Disk Image Installation
28.2.1. Overview of livemedia-creator
livemedia-creator --help command. Additional documentation is also installed along with the lorax package: the livemedia-creator(1) man page and the README.livemedia-creator file located in the /usr/share/doc/lorax-version/ directory, where version is the version of the lorax package you have installed.
28.2.2. Installing livemedia-creator
root:
yum install lorax
# yum install lorax- virt-install: a package providing tools to build new virtual machines, used in the first stage of live media creation unless the
--no-virtoption is specified. - libvirt, qemu-kvm, libvirt-client and other virtualization tools: when using virt-install, your system must be prepared to create, run and manage a virtual machine. See the Red Hat Enterprise Linux 7 Virtualization Deployment and Administration Guide for information on virtualization in Red Hat Enterprise Linux and for documentation about installing and working with virtualization tools.
- anaconda: the Red Hat Enterprise Linux installation program, used in the first stage instead of virt-install if the
--no-virtoption is used.
28.2.3. Sample Kickstart Files
/usr/share/doc/lorax-version/ directory, where version is the version number of the lorax package installed on your system.
rhel7-minimal.ks: a configuration file which provides only a minimal installation (the@coregroup) and other essentials such as the kernel and the GRUB2 boot loader. No users apart fromrootare created, and no graphical interface or additional packages are installed.rhel7-livemedia.ks: a more advanced configuration file which creates a live system with a graphical interface. A user namedliveuseris created along withroot.
Important
Note
Note
%include statement as they are not supported by livemedia-creator. All Kickstart files must be flattened either manually or using the ksflatten tool before they can be used.
28.2.4. Creating Custom Images
livemedia-creator --help or see the livemedia-creator(1) man page. For more information about lorax, see https://weldr.io/lorax/.
28.2.4.1. Using lorax to create a boot.iso file
Note
boot.iso will exist in the results/images directory. The --repo= command loads a Yum repository configuration file, in this case the default one, and use it to download package from Red Hat's content delivery network the same way they would be downloaded during a system update.
yum install lorax setenforce 0 lorax -p RHEL -v 7.4 -r 7.4 --repo=/etc/yum.repos.d/redhat.repo ./results/ setenforce 1
# yum install lorax
# setenforce 0
# lorax -p RHEL -v 7.4 -r 7.4 --repo=/etc/yum.repos.d/redhat.repo ./results/
# setenforce 1Note
28.2.4.2. Creating a Live Image Using virt-install
livemedia-creator --make-iso --iso=/path/to/boot.iso --ks=/path/to/valid/kickstart.ks
# livemedia-creator --make-iso --iso=/path/to/boot.iso --ks=/path/to/valid/kickstart.ks--vnc vnc: this option allows you to watch the installation process using a VNC client such as TigerVNC. The option is passed to virt-install's--graphicsoption. See Chapter 25, Using VNC for more information.--ram x: allows you to specify the amount of RAM for the temporary virtual machine in MiB.--vcpus x: the amount of the virtual machine's processors.
28.2.4.3. Creating a Live Image Using Anaconda's Image Install
Warning
--no-virt option is therefore only recommended on virtual machines (guests) specifically reserved for this purpose.
Important
SELinux) to permissive (or disabled) mode before creating custom images with Anaconda. See Red Hat Enterprise Linux 7 SELinux User's and Administrator's Guide for information on setting SELinux modes.
--no-virt option. For example:
livemedia-creator --make-iso --ks=/path/to/valid/kickstart.ks --no-virt
# livemedia-creator --make-iso --ks=/path/to/valid/kickstart.ks --no-virt28.2.4.4. Creating a Disk or File System Image
Note
--no-virt option in all examples in this section.
--image-only option as illustrated in the following example:
livemedia-creator --make-iso --ks=/path/to/valid/kickstart.ks --iso=/path/to/boot.iso --image-only
# livemedia-creator --make-iso --ks=/path/to/valid/kickstart.ks --iso=/path/to/boot.iso --image-only--make-disk option instead of --make-iso:
livemedia-creator --make-disk --ks=/path/to/valid/kickstart.ks --iso=/path/to/boot.iso
# livemedia-creator --make-disk --ks=/path/to/valid/kickstart.ks --iso=/path/to/boot.iso--make-fsimage option:
livemedia-creator --make-fsimage --ks=/path/to/valid/kickstart.ks --iso=/path/to/boot.iso
# livemedia-creator --make-fsimage --ks=/path/to/valid/kickstart.ks --iso=/path/to/boot.iso/var/tmp/ directory by default. To change the location of the result, use the --tmp /path/to/temporary/directory/ option, where /path/to/temporary/directory/ is the path to the target directory.
28.2.4.5. Using a Previously Created Disk or File System Image
--disk-image option. For example:
livemedia-creator --make-iso --disk-image=/path/to/disk/image.img
# livemedia-creator --make-iso --disk-image=/path/to/disk/image.img--fs-image option instead:
livemedia-creator --make-iso --fs-image=/path/to/filesystem/image.img
# livemedia-creator --make-iso --fs-image=/path/to/filesystem/image.img28.2.4.6. Creating an Appliance
--make-appliance option instead of --make-iso. For example:
livemedia-creator --make-appliance --ks=/path/to/valid/kickstart.ks --iso=/path/to/boot.iso
# livemedia-creator --make-appliance --ks=/path/to/valid/kickstart.ks --iso=/path/to/boot.iso/var/tmp/ directory unless a different one is specified using the --resultdir option.
--app-name name: specifies the name of the appliance, which will appear in the XML description file marked by the<name>tag. The default value isNone.--app-template /path/to/template.tmpl: specifies the template to be used. The default is/usr/share/lorax/appliance/libvirt.tmpl.--app-file /path/to/app/file.xml: specifies name of the generated description XML file. The default value isappliance.xml.
28.2.4.7. Creating an Amazon Machine Image (AMI)
--make-ami option. Virtualized and image installations are both supported.
livemedia-creator --make-ami --ks=/path/to/valid/kickstart.ks --iso=/path/to/boot.iso
# livemedia-creator --make-ami --ks=/path/to/valid/kickstart.ks --iso=/path/to/boot.isoami-root.img, located in the /var/tmp/ directory, unless you used the --resultdir option to specify a different one.
28.2.4.8. Additional Arguments
--keep-image: when you specify this option, the temporary disk image file used in the first stage of the installation will not be deleted. It will be located in the/var/tmp/directory and it will have a randomly generated name such asdiskgU42Cq.img.--image-only: using this option means that only the first stage of the image creation process will be executed. Instead of producing the final bootable ISO image, livemedia-creator will only create the temporary disk image file and perform an installation on it. This option allows you to save time when testing modifications to your Kickstart file, because you can skip the time-consuming second stage and inspect the temporary disk image file.--image-name name: allows you to specify a custom name for the temporary disk image file. The default name is randomly generated (for example,disk1Fac8G.img).--tmp /path/to/temporary/directory/: specifies the top level temporary directory. The default value is/var/tmp/. When using this option, you must specify a directory which already exists.--resultdir /path/to/results/directory/: specifies the directory where the results (the bootable ISO image) will appear after livemedia-creator finishes. An already existing directory cannot be specified. The default is/var/tmp/. This option only applies to the final ISO image; if you are creating a disk or file system image and want it to be saved at a specific location, use the--tmpoption.--logfile /path/to/log/file/: specifies the location of the program's log file.
28.2.5. Troubleshooting livemedia-creator Problems
--logfile option. The log files will be different based on the options you used - for example, virt-install.log will not be generated when you use the --no-virt option (instead, you will get log files from Anaconda, located in the anaconda/ directory). Other files, namely livemedia.log and program.log, are generated every time.
--image-only option when running the utility. This option will stop the program after the first stage, so only a disk image file will be generated instead of the final bootable ISO. You can then mount the disk image file and examine its contents without having to wait for the second stage to finish. Alternatively, you can use the --keep-image option, which will execute both stages, but keep the temporary disk image for later analysis.
--vnc option is recommended when testing changes to the Kickstart file. This option will allow you to use a VNC client to connect to the virtual machine and watch the installation progress. See Chapter 25, Using VNC for details.
28.2.5.1. Stuck Virtual Machine Installation
Procedure 28.1. Stopping the Temporary Virtual Machine
- Use virsh to list all virtual machines (guests) currently available on the system. The output will be similar to the following:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Identify the temporary virtual machine. Its name will always start withLiveOS, followed by a string of random numbers and characters. - Once you have identified the temporary virtual machine, stop it using the
virsh destroy namecommand, where name is the virtual machine's name:virsh destroy LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 Domain LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 destroyed
# virsh destroy LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 Domain LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 destroyedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
28.2.5.2. Failed installation using a Virtual Machine
virsh undefine name command. You can also use steps 4 and 5 if you only want to clean up temporary files created by livemedia-creator and nothing else.
Procedure 28.2. Removing Temporary Guests And Disk Image Files
- Use virsh to list all virtual machines (guests) currently available on the system. The output will be similar to the following:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Identify the temporary virtual machine. Its name will always start withLiveOS, followed by a string of random numbers and characters. - Once you have identified the temporary virtual machine, stop it using the
virsh destroy namecommand, where name is the virtual machine's name:virsh destroy LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 Domain LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 destroyed
# virsh destroy LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 Domain LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 destroyedCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Delete the temporary virtual machine using
virsh undefine name, using the same name as in the previous step.virsh undefine LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 Domain LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 has been undefined
# virsh undefine LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 Domain LiveOS-2a198971-ba97-454e-a056-799f453e1bd7 has been undefinedCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Find the temporary file system's mount. It will be targeted to the
/var/tmp/directory and its name will belorax.imgutilsfollowed by six random numbers or characters.findmnt -T /var/tmp/lorax.imgutils* TARGET SOURCE FSTYPE OPTIONS /var/tmp/lorax.imgutils.bg6iPJ /dev/loop1 iso9660 ro,relatime
# findmnt -T /var/tmp/lorax.imgutils* TARGET SOURCE FSTYPE OPTIONS /var/tmp/lorax.imgutils.bg6iPJ /dev/loop1 iso9660 ro,relatimeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Then, unmount it using theumountcommand:umount /var/tmp/lorax.imgutils.bg6iPJ
# umount /var/tmp/lorax.imgutils.bg6iPJCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Find the temporary disk image created by virt-install in the
/var/tmp/directory. The name of this file is printed to command line at the beginning of the installation process and is randomly generated, unless you specify a name using the--image-nameoption. For example:2013-10-30 09:53:03,161: disk_size = 5GB 2013-10-30 09:53:03,161: disk_img = /var/tmp/diskQBkzRz.img 2013-10-30 09:53:03,161: install_log = /home/pbokoc/lorax/virt-install.log mount: /dev/loop1 is write-protected, mounting read-only
2013-10-30 09:53:03,161: disk_size = 5GB 2013-10-30 09:53:03,161: disk_img = /var/tmp/diskQBkzRz.img 2013-10-30 09:53:03,161: install_log = /home/pbokoc/lorax/virt-install.log mount: /dev/loop1 is write-protected, mounting read-onlyCopy to Clipboard Copied! Toggle word wrap Toggle overflow In the above example, the temporary disk image is/var/tmp/diskQBkzRz.img.If you cannot find the initial messages, you can identify the temporary files manually. List all contents of the/var/tmp/directory using thelscommand and filter the output for files containingdiskin their names:ls /var/tmp/ | grep disk diskQBkzRz.img
# ls /var/tmp/ | grep disk diskQBkzRz.imgCopy to Clipboard Copied! Toggle word wrap Toggle overflow Then, delete the temporary disk image:rm -f /var/tmp/diskQBkzRz.img
# rm -f /var/tmp/diskQBkzRz.imgCopy to Clipboard Copied! Toggle word wrap Toggle overflow
28.2.5.3. Failed Installation Using Anaconda
--no-virt option) can be achieved by executing the anaconda-cleanup script, which is installed along with the anaconda package. This script is located in the /usr/bin/ directory.
anaconda-cleanup
# anaconda-cleanupChapter 29. Upgrading Your Current System
- The Preupgrade Assistant, which is a diagnostics utility that assesses your current system and identifies potential problems you might encounter during or after the upgrade.
- The Red Hat Upgrade Tool utility, which is used to upgrade a system from Red Hat Enterprise Linux version 6 to version 7.
Note
x86_64) systems and on IBM Z (s390x). Additionally, only the Server variant can be upgraded with Red Hat Upgrade Tool.
Part V. After Installation
- performing common post-installation tasks, such as registering the system to Red Hat Subscription Management services
- using a Red Hat Enterprise Linux installation disc to rescue a damaged system
- removing Red Hat Enterprise Linux from your computer
Chapter 30. Initial Setup
- Using the base environment in the Red Hat Enterprise Linux setup.
- Using a Kickstart file that contains one of the following entries in the
%packagessection:- the initial-setup-gui package for graphical mode
- the initial-setup package for text mode
- the x11 group
- the gnome-desktop group
- the kde-desktop group
Note
Options in the Initial Setup
| Option | Graphical User Interface | Text User Interface |
|---|---|---|
| License agreement [a] | Yes | Yes |
| Language settings [b] | No | Yes |
| Date & time [b] | Yes | Yes [c] |
| Subscription Manager | Yes | No |
| Network & host name [b] | Yes | No |
| Root password [b] | Yes | Yes [c] |
| User creation [b] | Yes | Yes |
[a]
This option is only displayed if you did not previously agreed to the license.
[b]
This option is only displayed if you did not previously set it.
[c]
This option is only available if you run Initial Setup in reconfiguration mode
| ||
Important
firstboot --enable --reconfig
firstboot --enable --reconfig--reconfig option specifies that all options should be displayed. For further details about Kickstart installations, see Chapter 27, Kickstart Installations.
30.1. Graphical Mode
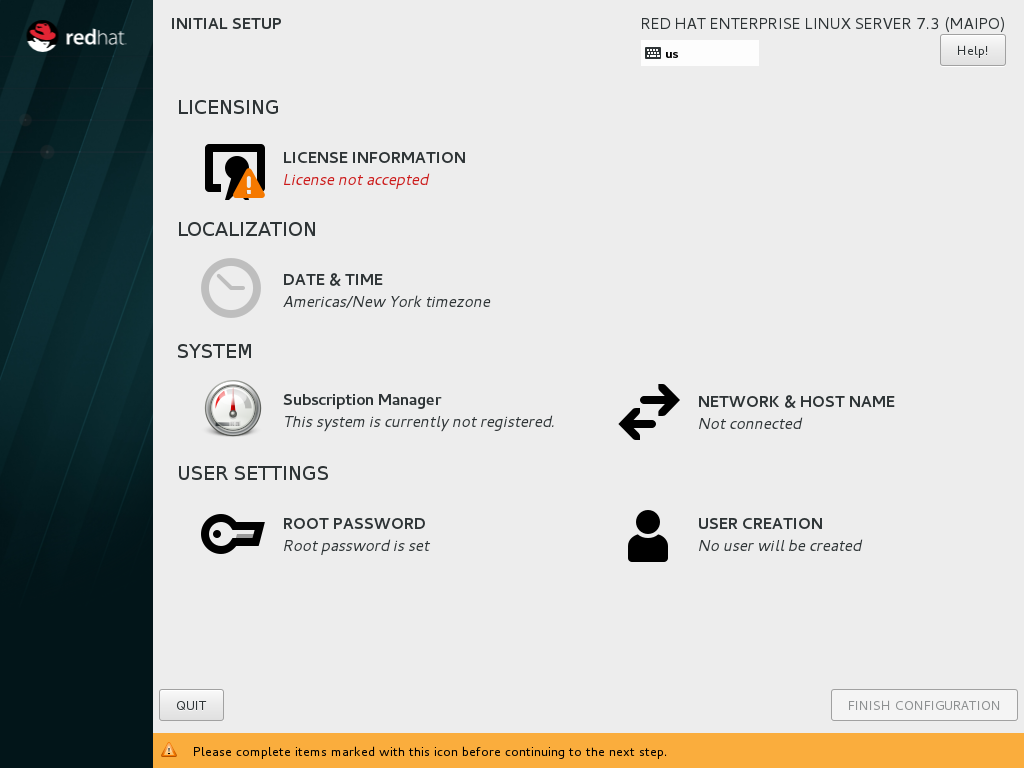
Figure 30.1. Main Initial Setup Screen
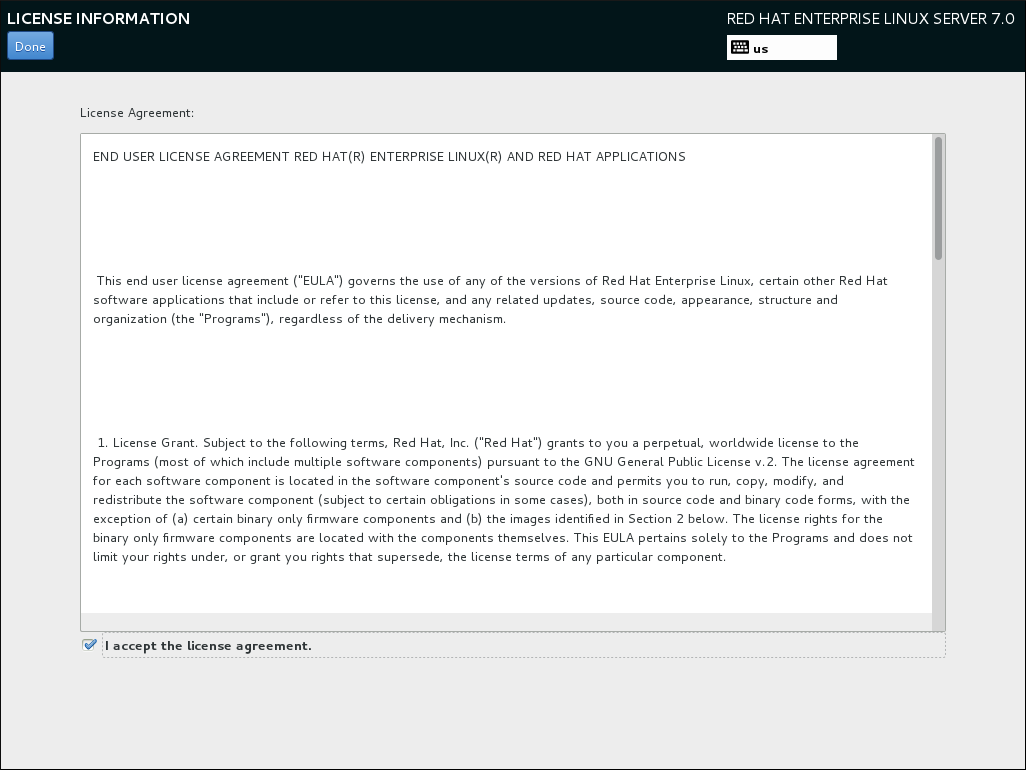
Figure 30.2. License Information Screen
30.1.1. Subscription Manager
Note
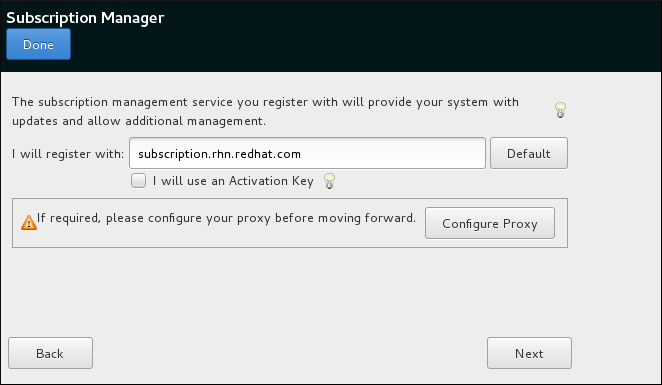
Figure 30.3. Subscription Manager Screen
- Customer Portal Subscription Management, hosted services from Red Hat (the default)
- Subscription Asset Manager, an on-premise subscription server which proxies content delivery back to the Customer Portal's services
- CloudForms System Engine, an on-premise service which handles both subscription services and content delivery
30.2. Text Mode
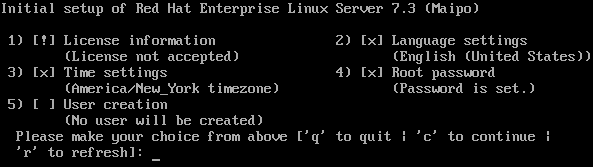
Figure 30.4. Initial Setup in text mode
- q to close the application. Until you accepted the license agreement, closing the application causes the system to reboot.
- c to continue. Pressing this key in a submenu returns you to the main menu. In the main menu, pressing the c key stores the settings and closes the application. Note that you cannot continue without accepting the license agreement.
- r to refresh the menu.
[x]: This setting is already configured. However, you can change the setting.[!]: This setting is mandatory but not yet set.[ ]: This setting is optional and not yet set.
30.3. Starting Initial Setup Manually
- Enable the service:
systemctl enable initial-setup.service
# systemctl enable initial-setup.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, to display all menu options, including the ones previously set, create an empty
/.unconfiguredfile to start Initial Setup in reconfiguration mode:touch /.unconfigured
# touch /.unconfiguredCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that, regardless of this setting, the license agreement entry is not displayed again if you previously accepted it. - Reboot the system.
Note
Chapter 31. Your Next Steps
- Find help, answers, and utilize diagnostic services
- Red Hat Access is a GUI application which allows you to conveniently access Red Hat knowledge and solutions. It can be used to search for error codes, messages, or any topic of interest, and view related knowledge from the Red Hat Customer Portal. More information about Red Hat Access can be found in the Red Hat Access GUI article on the Red Hat Customer Portal.
- Recover a lost root password
- The root password, which is configured during the installation, is required for accessing the system as the root user. Without the root password you will not be able to configure your system or install additional software. If you lost or forgot your root password, you can reset it by following the steps described in Section 32.1.3, “Resetting the Root Password”.
- Install driver updates
- Usually, drivers for system devices are already supported in the kernel provided by Red Hat Enterprise Linux. However, occasionally, support for devices that have been released recently can be missing. In these cases, a driver update enabling your device might be available.Devices necessary to complete the installation can have driver updates provided before the installation begins. If a device is missing a driver, but it is not essential during the installation, it is recommended to wait until after the installation completes, and install additional drivers afterwards. For instructions on installing and enabling additional drivers on the installed system using RPM and Yum, see the Red Hat Enterprise Linux 7 System Administrator's Guide.
- Configure the network
- In most cases network access is configured during the installation process, either in the installation program or in a Kickstart file. For information on configuring the network after the installation, see the Red Hat Enterprise Linux 7 Networking Guide.
- Set up Kdump
- Kdump is a kernel crash dumping mechanism. If your system encounters a significant error, Kdump can save the contents of the system's memory into a kernel crash dump, which can then be analyzed to find the cause of the error.Kdump can be enabled during the installation process (see Section 8.16, “Kdump”). It can also be configured at any time afterwards. Red Hat Enterprise Linux 7 Kernel Crash Dump Guide provides all information necessary to understand how Kdump works and how to configure it on your system.
- Register the system
- The products installed on a system (including the operating system itself) are covered by subscriptions. A subscription service is used to track registered systems, the products installed on those systems, and the subscriptions attached to those products. Registration is a part of the Initial Setup configuration process (see Section 30.1.1, “Subscription Manager”).However, if you have not registered your system during Initial Setup, you can register it afterwards. See Using and Configuring Red Hat Subscription Manager and Red Hat Satellite Quick Start Guide for more information.
Note
You can also use the Registration Assistant application to guide you through the registration process. - Automate the initial configuration of cloud instances using cloud-init
- For the initial configuration of cloud instances, you can use the cloud-init package. On a new cloud instance, cloud-init can automatically:
- set the default locale
- configure the host name
- configure network interfaces
- generate private SSH keys
- add SSH keys to the user's
.ssh/authorized_keysfile - set up ephemeral mount points
Cloud-init is used with Red Hat's cloud products. See documentation on using cloud-init with Red Hat products:- Red Hat Enterprise Linux Atomic Host 7 Installation and Configuration Guide
- Red Hat OpenStack Platform 8 Instances and Images Guide
- Red Hat Enterprise Virtualization Virtual Machine Management Guide
- Red Hat CloudForms Provisioning Virtual Machines and Hosts Guide
See also upstream cloud-init documentation - Perform an initial system update
- After the installation is complete, Red Hat recommends that you perform an initial system update. During this process, all installed packages are updated to their latest available versions. Updates to packages provide security fixes, bug fixes and enhancements.In Red Hat Enterprise Linux, the Yum package manager is used for updating the installed packages. For more information about updating your system with Yum, see the Red Hat Enterprise Linux 7 System Administrator's Guide.
- Configure additional repositories
- New software is installed from package repositories. Package repositories are organized sets of software and metadata that can be accessed by the Yum package manager. If you registered your system with Red Hat, update repositories are configured automatically and you can install updates and additional software from those. However, if you want to set up additional repositories, for example containing your own software, some extra steps are needed.For information about configuring additional software repositories, see the Red Hat Enterprise Linux 7 System Administrator's Guide.
- Install additional packages
- You can control which packages will be installed by selecting an environment in the
Software Selectiondialog in the graphical installation. This dialog does not provide a way to choose individual packages, only predefined sets. However, you can use the Yum packages manager to install additional packages after the installation. See the Red Hat Enterprise Linux 7 System Administrator's Guide for more information. - Switch to a graphical login
- Depending on the options you chose during the installation process, it is possible that your system does not have a graphical interface, instead offering only a text-based prompt. If this is the case and you want to enable a graphical desktop after the installation, you must install the X Window System and your preferred desktop environment (either GNOME or KDE).As with all other software, these packages can be installed using the Yum package manager. For information about using Yum to install new packages, see the Red Hat Enterprise Linux 7 System Administrator's Guide. For information on how to enable graphical login by default, see Section 9.3.3, “Booting into a Graphical Environment”.
- Enable or disable GNOME 3 extensions
- The default desktop environment in Red Hat Enterprise Linux 7 is GNOME 3 which provides GNOME Shell and GNOME Classic user interfaces. It is possible to customize these interfaces by enabling and disabling GNOME 3 extensions. See the Red Hat Enterprise Linux 7 Desktop Migration and Administration Guide for more information.
Chapter 32. Basic System Recovery
32.1. Common Problems
- You are unable to boot into Red Hat Enterprise Linux normally.
- You are having hardware or software problems, and you want to recover data from your system's hard drive.
- You forgot the root password.
32.1.1. Unable to Boot into Red Hat Enterprise Linux
/ partition changes, the boot loader might not be able to find it to mount the partition. To fix this problem, you will need to reinstall the boot loader. See Section 32.2.2, “Reinstalling the Boot Loader” for instructions on how to do this.
32.1.2. Hardware and Software Problems
32.1.3. Resetting the Root Password
32.2. Anaconda Rescue Mode
Note
- Chapter 7, Booting the Installation on 64-bit AMD, Intel, and ARM systems for 64-bit AMD, Intel, and ARM systems
- Chapter 12, Booting the Installation on IBM Power Systems for IBM Power Systems servers
Important
dracut boot options (such as rd.zfcp= or root=iscsi:options), or in the CMS configuration file on IBM Z. It is not possible to configure these storage devices interactively after booting into rescue mode.
dracut boot options, see the dracut.cmdline(7) man page. For information about the CMS configuration file, see Chapter 21, Parameter and Configuration Files on IBM Z.
Procedure 32.1. Booting into Anaconda Rescue Mode
- Boot the system from either minimal boot media, or a full installation DVD or USB drive, and wait for the boot menu to appear.
- From the boot menu, either select the option from the submenu, or append the
inst.rescueoption to the boot command line. To enter the boot command line, press the Tab key on BIOS-based systems or the e key on the UEFI-based systems. - If your system requires a third-party driver provided on a driver disc to boot, append the
inst.dd=driver_nameto the boot command line:inst.rescue inst.dd=driver_name
inst.rescue inst.dd=driver_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information on using a driver disc at boot time, see Section 6.3.3, “Manual Driver Update” for AMD64 and Intel 64 systems or Section 11.2.3, “Manual Driver Update” for IBM Power Systems servers. - If a driver that is part of the Red Hat Enterprise Linux 7 distribution prevents the system from booting, append the
modprobe.blacklist=option to the boot command line:inst.rescue modprobe.blacklist=driver_name
inst.rescue modprobe.blacklist=driver_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information about blacklisting drivers, see Section 6.3.4, “Blacklisting a Driver”. - When ready, press Enter (BIOS-based systems) or Ctrl+X (UEFI-based systems) to boot the modified option. Then wait until the following message is displayed:
The rescue environment will now attempt to find your Linux installation and mount it under the /mnt/sysimage/ directory. You can then make any changes required to your system. If you want to proceed with this step choose 'Continue'. You can also choose to mount your file systems read-only instead of read-write by choosing 'Read-only'. If for some reason this process fails you can choose 'Skip' and this step will be skipped and you will go directly to a command line.
The rescue environment will now attempt to find your Linux installation and mount it under the /mnt/sysimage/ directory. You can then make any changes required to your system. If you want to proceed with this step choose 'Continue'. You can also choose to mount your file systems read-only instead of read-write by choosing 'Read-only'. If for some reason this process fails you can choose 'Skip' and this step will be skipped and you will go directly to a command line.Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you select , it attempts to mount your file system under the directory/mnt/sysimage/. If it fails to mount a partition, you will be notified. If you select , it attempts to mount your file system under the directory/mnt/sysimage/, but in read-only mode. If you select , your file system is not mounted. Choose if you think your file system is corrupted. - Once you have your system in rescue mode, a prompt appears on VC (virtual console) 1 and VC 2 (use the Ctrl+Alt+F1 key combination to access VC 1 and Ctrl+Alt+F2 to access VC 2):
sh-4.2#
sh-4.2#Copy to Clipboard Copied! Toggle word wrap Toggle overflow
multi-user.target or graphical.target). If you selected to mount your file system and it mounted successfully, you can change the root partition of the Anaconda rescue mode environment to the root partition of your file system by executing the following command:
chroot /mnt/sysimage
sh-4.2# chroot /mnt/sysimagerpm, that require your root partition to be mounted as /. To exit the chroot environment, type exit to return to the prompt.
/directory/, and typing the following command:
mount -t xfs /dev/mapper/VolGroup00-LogVol02 /directory
sh-4.2# mount -t xfs /dev/mapper/VolGroup00-LogVol02 /directory/directory/ is a directory that you have created and /dev/mapper/VolGroup00-LogVol02 is the LVM2 logical volume you want to mount. If the partition is a different type than XFS, replace the xfs string with the correct type (such as ext4).
fdisk -l
sh-4.2# fdisk -lpvdisplay, vgdisplay or lvdisplay commands, respectively.
ssh,scp, andpingif the network is startedFor details, see the Red Hat Enterprise Linux 7 System Administrator's Guide.dumpandrestorefor users with tape drivesFor details, see the RHEL Backup and Restore Assistant.partedandfdiskfor managing partitionsFor details, see the Red Hat Enterprise Linux 7 Storage Administration Guide.yumfor installing or upgrading softwareFor details, see the Red Hat Enterprise Linux 7 Administrator's Guide
32.2.1. Capturing an sosreport
sosreport command-line utility collects configuration and diagnostic information, such as the running kernel version, loaded modules, and system and service configuration files, from the system. The utility output is stored in a tar archive in the /var/tmp/ directory.
sosreport utility is useful for analyzing the system errors and can make troubleshooting easier. The following procedure describes how to capture an sosreport output in Anaconda rescue mode:
Procedure 32.2. Using sosreport in Anaconda Rescue Mode
- Follow steps in Procedure 32.1, “Booting into Anaconda Rescue Mode” to boot into Anaconda rescue mode. Ensure that you mount the installed system
/(root) partition in read-write mode. - Change the root directory to the
/mnt/sysimage/directory:chroot /mnt/sysimage/
sh-4.2# chroot /mnt/sysimage/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Execute
sosreportto generate an archive with system configuration and diagnostic information:sosreport
sh-4.2# sosreportCopy to Clipboard Copied! Toggle word wrap Toggle overflow Important
When running,sosreportwill prompt you to enter your name and case number that you get when you contact Red Hat Support service and open a new support case. Use only letters and numbers because adding any of the following characters or spaces could render the report unusable:% & { } \ < > > * ? / $ ~ ' " : @ + ` | =# % & { } \ < > > * ? / $ ~ ' " : @ + ` | =Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Optional. If you want to transfer the generated archive to a new location using the network, it is necessary to have a network interface configured. In case you use the dynamic IP addressing, there are no other steps required. However, when using the static addressing, enter the following command to assign an IP address (for example 10.13.153.64/23) to a network interface (for example dev eth0):
bash-4.2# ip addr add 10.13.153.64/23 dev eth0
bash-4.2# ip addr add 10.13.153.64/23 dev eth0Copy to Clipboard Copied! Toggle word wrap Toggle overflow See the Red Hat Enterprise Linux 7 Networking Guide for additional information about static addressing. - Exit the chroot environment:
exit
sh-4.2# exitCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Store the generated archive in a new location, from where it can be easily accessible:
cp /mnt/sysimage/var/tmp/sosreport new_location
sh-4.2# cp /mnt/sysimage/var/tmp/sosreport new_locationCopy to Clipboard Copied! Toggle word wrap Toggle overflow For transferring the archive through the network, use thescputility:scp /mnt/sysimage/var/tmp/sosreport username@hostname:sosreport
sh-4.2# scp /mnt/sysimage/var/tmp/sosreport username@hostname:sosreportCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- For general information about
sosreport, see What is a sosreport and how to create one in Red Hat Enterprise Linux 4.6 and later?. - For information about using
sosreportwithin Anaconda rescue mode, see How to generate sosreport from the rescue environment. - For information about generating an
sosreportto a different location than/tmp, see How do I make sosreport write to an alternative location?. - For information about collecting an
sosreportmanually, see Sosreport fails. What data should I provide in its place?.
32.2.2. Reinstalling the Boot Loader
Procedure 32.3. Reinstalling the GRUB2 Boot Loader
- Follow instructions in Procedure 32.1, “Booting into Anaconda Rescue Mode” to boot into Anaconda rescue mode. Ensure that you mount the installed system's
/(root) partition in read-write mode. - Change the root partition:
chroot /mnt/sysimage/
sh-4.2# chroot /mnt/sysimage/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the following command to reinstall the GRUB2 boot loader, where install_device is the boot device (typically, /dev/sda):
/sbin/grub2-install install_device
sh-4.2# /sbin/grub2-install install_deviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot the system.
32.2.3. Using RPM to Add, Remove, or Replace a Driver
Note
Procedure 32.4. Using RPM to Remove a Driver
- Boot the system into Anaconda rescue mode. Follow the instructions in Procedure 32.1, “Booting into Anaconda Rescue Mode”. Ensure that you mount the installed system in read-write mode.
- Change the root directory to
/mnt/sysimage/:chroot /mnt/sysimage/
sh-4.2# chroot /mnt/sysimage/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
rpm -ecommand to remove the driver package. For example, to remove the xorg-x11-drv-wacom driver package, run:rpm -e xorg-x11-drv-wacom
sh-4.2# rpm -e xorg-x11-drv-wacomCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Exit the chroot environment:
exit
sh-4.2# exitCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 32.5. Installing a Driver from an RPM package
- Boot the system into Anaconda rescue mode. Follow the instructions in Procedure 32.1, “Booting into Anaconda Rescue Mode”. Do not choose to mount the installed system as read only.
- Make the RPM package that contains the driver available. For example, mount a CD or USB flash drive and copy the RPM package to a location of your choice under
/mnt/sysimage/, for example:/mnt/sysimage/root/drivers/ - Change the root directory to
/mnt/sysimage/:chroot /mnt/sysimage/
sh-4.2# chroot /mnt/sysimage/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
rpm -ivhcommand to install the driver package. For example, to install the xorg-x11-drv-wacom driver package from/root/drivers/, run:rpm -ivh /root/drivers/xorg-x11-drv-wacom-0.23.0-6.el7.x86_64.rpm
sh-4.2# rpm -ivh /root/drivers/xorg-x11-drv-wacom-0.23.0-6.el7.x86_64.rpmCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
The/root/drivers/directory in this chroot environment is the/mnt/sysimage/root/drivers/directory in the original rescue environment. - Exit the chroot environment:
exit
sh-4.2# exitCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 33. Unregistering from Red Hat Subscription Management Services
33.1. Systems Registered with Red Hat Subscription Management
unregister command as root without any additional parameters:
subscription-manager unregister
# subscription-manager unregister33.2. Systems Registered with Red Hat Satellite
Chapter 34. Uninstalling Red Hat Enterprise Linux
34.1. Removing Red Hat Enterprise Linux from 64-bit AMD, Intel, and ARM Systems
- In certain situations you need the install media for any non-Red Hat Enterprise Linux operating system you are going to be using on the system after you complete this process.
- If you have multiple operating systems installed, ensure that you can boot each one separately and have all administrator passwords, including any passwords that might have been set automatically by your computer manufacturer or the manufacturer of the operating system.
- If you want to retain any data from the installation of Red Hat Enterprise Linux that you are going to remove, it will need to be backed up to a different location. If you are deleting an installation that contains sensitive data, ensure that you destroy the data according to your security policy. Ensure that any backup medium is readable on the operating system where you will restore the data. For example, without extra third-party software, Microsoft Windows cannot read an external hard drive that you have formatted with Red Hat Enterprise Linux to use the ext2, ext3, ext4 or XFS file system.
Warning
As a precaution, back up all data from any operating systems, including Red Hat Enterprise Linux, that are installed on the same computer. Unforeseen circumstances can result in loss of all your data. - If you are only uninstalling Red Hat Enterprise Linux and not reinstalling the entire computer, you should familiarize yourself with your partition layout. In particular, the output of the mount command can be helpful. It can also be helpful to note which
menuitemis used to boot your Red Hat Enterprise Linux installation ingrub.cfg.
- Remove the Red Hat Enterprise Linux boot loader information from your master boot record (MBR).
- Remove any partitions that contain the Red Hat Enterprise Linux operating system.
- only Red Hat Enterprise Linux
- Red Hat Enterprise Linux and different Linux Distribution
- Red Hat Enterprise Linux and Windows 2000, Windows Server 2000, Windows XP, Windows Vista, Windows Server 2003 and Windows Server 2008
34.1.1. Only Red Hat Enterprise Linux is Installed
- Back up any data that you want to keep.
- Shut down the computer.
- Boot your computer with the installation disc for the replacement operating system.
- Follow the prompts presented during the installation process. Windows, OS X, and most Linux installation discs allow you to manually partition your hard drive during the installation process, or will offer you the option to remove all partitions and start with a fresh partition scheme. At this point, remove any existing partitions that the installation software detects or allow the installation program to remove the partitions automatically. "System restore" media for computers pre-installed with Microsoft Windows might create a default partition layout automatically without input from you.
Warning
If your computer has system restore software stored on a partition on a hard drive, take care when removing partitions while installing an operating system from other media. Under these circumstances, you could destroy the partition holding the system restore software.
34.1.2. Red Hat Enterprise Linux installed with a Different Linux Distribution
Important
- Remove Red Hat Enterprise Linux Entries from Your Boot Loader
- Boot the Linux Distribution you are keeping on your computer, not Red Hat Enterprise Linux.
- At the command line, type
su -and press Enter. When the system prompts you for the root password, type the password and press Enter. - Use a text editor such as vim to open the
/boot/grub2/grub.cfgconfiguration file. In this file, find the entry of the system you are removing. A typical Red Hat Enterprise Linux entry in thegrub.cfgfile looks similar to the following example:Example 34.1. A Red Hat Enterprise Linux Entry in
grub.cfgCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Delete the entire entry, starting with the menuentry keyword and ending with }.Depending on the configuration of your system, there might be multiple Red Hat Enterprise Linux entries in
grub.cfg, each corresponding to a different version of the Linux kernel. Delete each of the Red Hat Enterprise Linux entries from the file. - Save the updated
grub.cfgfile and close vim
- Remove Red Hat Enterprise Linux partitions on multi-boot environments:
Note
Be careful not to remove partitions that are still in use by the other installations.- Boot the Linux Distribution you are keeping on your computer, not Red Hat Enterprise Linux.
- Remove any unwanted and unnecessary partitions, for example, using:, for example, with fdisk for standard partitions, or lvremove and vgremove to remove logical volumes and volume groups. Additional information on these utilities can be found in their respective man pages, or the Red Hat Enterprise Linux 7 System Administrator's Guide.
- fdisk for standard partitions. For details, see How do you use fdisk to delete a partition?
- lvremove and vgremove to remove logical volumes and volume groups. For details, see the Red Hat Storage Administration Guide.
34.1.3. Red Hat Enterprise Linux installed with a Microsoft Windows Operating System
Warning
- Remove the Red Hat Enterprise Linux partitions
- Boot your computer into your Microsoft Windows environment.
- Click Start>Run, type
diskmgmt.mscand press Enter. The Disk Management tool opens.The tool displays a graphical representation of your disk, with bars representing each partition. The first partition is usually labeledNTFSand corresponds to yourC:drive. At least two Red Hat Enterprise Linux partitions will be visible. Windows will not display a file system type for these partitions, but can allocate drive letters to some of them. - Right-click on one of the Red Hat Enterprise Linux partitions, then click Delete Partition and click Yes to confirm the deletion. Repeat this process for the other Red Hat Enterprise Linux partitions on your system. As you delete partitions, Windows labels the space on the hard drive previously occupied by those partitions as
unallocated.You can add this unallocated space to an existing Windows partition or to use this space in some other way. Directions for doing this can be found in the manuals for your non-Red Hat Enterprise Linux operating system.
- Restore the Windows boot loader
- On Windows 2000, Windows Server 2000, Windows XP, and Windows Server 2003:
- Insert the Windows installation disk and restart your computer. As your computer starts, the following message will appear on the screen for a few seconds:
Press any key to boot from CD
Press any key to boot from CDCopy to Clipboard Copied! Toggle word wrap Toggle overflow Press any key while the message is still showing and the Windows installation software will load. - When the
Welcome to Setupscreen appears, you can start the Windows Recovery Console. The procedure is slightly different on different versions of Windows:- On Windows 2000 and Windows Server 2000, press the R key, then the C key.
- On Windows XP and Windows Server 2003, press the R key.
- The Windows Recovery Console scans your hard drives for Windows installations, and assigns a number to each one. It displays a list of Windows installations and prompts you to select one. Type the number corresponding to the Windows installation that you want to restore.
- The Windows Recovery Console prompts you for the Administrator password for your Windows installation. Type the Administrator password and press the Enter key. If there is no administrator password for this system, press only the Enter key.
- At the prompt, type the command
fixmbrand press the Enter. The fixmbr tool now restores the Master Boot Record for the system. - When the prompt reappears, type
exitand press the Enter key. - Your computer will restart and boot your Windows operating system.
- On Windows Vista and Windows Server 2008:
- Insert the Windows installation disk and restart your computer. As your computer starts, the following message will appear on the screen for a few seconds:
Press any key to boot from CD or DVD
Press any key to boot from CD or DVDCopy to Clipboard Copied! Toggle word wrap Toggle overflow Press any key while the message is still showing and the Windows installation software will load. - In the Install Windows dialog, select a language, time and currency format, and keyboard type. Click Next
- Click Repair your computer.
- The Windows Recovery Environment (WRE) shows you the Windows installations that it can detect on your system. Select the installation that you want to restore, then click Next.
- Click Command prompt. A command window will open.
- Type
bootrec /fixmbrand press Enter. - When the prompt reappears, close the command window, then click Restart.
- Your computer will restart and boot your Windows operating system.
34.2. Removing Red Hat Enterprise Linux from IBM Z
- Overwrite the disks with a new installation.
- Make the DASD or SCSI disk where Linux was installed visible from another system, then delete the data. However, this might require special privileges. Ask your system administrator for advice. You can use Linux commands such as
dasdfmt(DASD only),parted,mke2fsordd. For more details about the commands, see the respective man pages.
34.2.1. Running a Different Operating System on Your z/VM Guest or LPAR
Part VI. Technical Appendixes
Appendix A. An Introduction to Disk Partitions
Note
Note
A.1. Hard Disk Basic Concepts

Figure A.1. An Unused Disk Drive
A.1.1. File Systems

Figure A.2. Disk Drive with a File System
- A small percentage of the driver's available space is used to store file system-related data and can be considered as overhead.
- A file system splits the remaining space into small, consistently-sized segments. For Linux, these segments are known as blocks. [4]

Figure A.3. Disk Drive with a Different File System

Figure A.4. Disk Drive with Data Written to It
A.1.2. Partitions: Turning One Drive Into Many
- Logical separation of the operating system data from the user data
- Ability to use different file systems
- Ability to run multiple operating systems on one machine
Note
Figure A.5. Disk Drive with Partition Table
- The points on the disk where the partition starts and ends
- Whether the partition is "active"
- The partition's type
Figure A.6. Disk Drive With Single Partition
DOS. This label shows the partition type, with DOS being one of the most common ones. The table below shows a list of some of the commonly used partition types and hexadecimal numbers used to represent them.
| Partition Type | Value | Partition Type | Value |
|---|---|---|---|
| Empty | 00 | Novell Netware 386 | 65 |
| DOS 12-bit FAT | 01 | PIC/IX | 75 |
| XENIX root | 02 | Old MINIX | 80 |
| XENIX usr | 03 | Linux/MINUX | 81 |
| DOS 16-bit <=32M | 04 | Linux swap | 82 |
| Extended | 05 | Linux native | 83 |
| DOS 16-bit >=32 | 06 | Linux extended | 85 |
| OS/2 HPFS | 07 | Amoeba | 93 |
| AIX | 08 | Amoeba BBT | 94 |
| AIX bootable | 09 | BSD/386 | a5 |
| OS/2 Boot Manager | 0a | OpenBSD | a6 |
| Win95 FAT32 | 0b | NEXTSTEP | a7 |
| Win95 FAT32 (LBA) | 0c | BSDI fs | b7 |
| Win95 FAT16 (LBA) | 0e | BSDI swap | b8 |
| Win95 Extended (LBA) | 0f | Syrinx | c7 |
| Venix 80286 | 40 | CP/M | db |
| Novell | 51 | DOS access | e1 |
| PReP Boot | 41 | DOS R/O | e3 |
| GNU HURD | 63 | DOS secondary | f2 |
| Novell Netware 286 | 64 | BBT | ff |
A.1.3. Partitions Within Partitions - An Overview of Extended Partitions
Figure A.7. Disk Drive With Extended Partition
A.1.4. GUID Partition Table (GPT)
- To preserve backward compatibility with MBR disks, the first sector (LBA 0) of GPT is reserved for MBR data and it is called “protective MBR”.
- The primary GPT header begins on the second logical block (LBA 1) of the device. The header contains the disk GUID, the location of the primary partition table, the location of the secondary GPT header, and CRC32 checksums of itself and the primary partition table. It also specifies the number of partition entries of the table.
- The primary GPT table includes, by default, 128 partition entries, each with an entry size 128 bytes, its partition type GUID and unique partition GUID.
- The secondary GPT table is identical to the primary GPT table. It is used mainly as a backup table for recovery in case the primary partition table is corrupted.
- The secondary GPT header is located on the last logical sector of the disk and it can be used to recover GPT information in case the primary header is corrupted. It contains the disk GUID, the location of the secondary partition table and the primary GPT header, CRC32 checksums of itself and the secondary partition table, and the number of possible partition entries.
Important
A.2. Strategies for Disk Repartitioning
- Unpartitioned free space is available
- An unused partition is available
- Free space in an actively used partition is available
Note
A.2.1. Using Unpartitioned Free Space
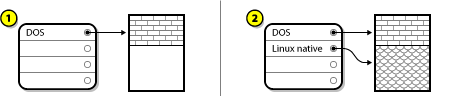
Figure A.8. Disk Drive with Unpartitioned Free Space
A.2.2. Using Space from an Unused Partition
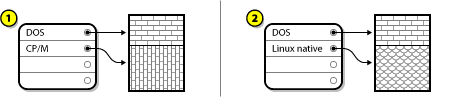
Figure A.9. Disk Drive with an Unused Partition
A.2.3. Using Free Space from an Active Partition
- Destructive Repartitioning
- In this case, the single large partition is deleted and several smaller ones are created instead. Any data held in the original partition is destroyed. This means that making a complete backup is necessary. It is highly recommended to make two backups, use verification (if available in your backup software), and try to read data from the backup before deleting the partition.
Warning
If an operating system was installed on that partition, it must be reinstalled if you want to use that system as well. Be aware that some computers sold with pre-installed operating systems might not include the installation media to reinstall the original operating system. You should check whether this applies to your system is before you destroy your original partition and its operating system installation.After creating a smaller partition for your existing operating system, you can reinstall software, restore your data, and start your Red Hat Enterprise Linux installation.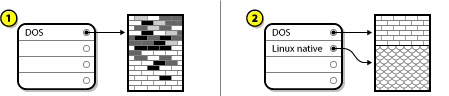
Figure A.10. Disk Drive Being Destructively Repartitioned
In the above example, 1 represents before and 2 represents after.Warning
Any data previously present in the original partition is lost. - Non-Destructive Repartitioning
- With non-destructive repartitioning you execute a program that makes a big partition smaller without losing any of the files stored in that partition. This method is usually reliable, but can be very time-consuming on large drives.While the process of non-destructive repartitioning is rather straightforward, there are three steps involved:
- Compress and backup existing data
- Resize the existing partition
- Create new partition(s)
A.2.3.1. Compress Existing Data
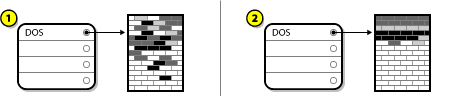
Figure A.11. Disk Drive Being Compressed
A.2.3.2. Resize the Existing Partition
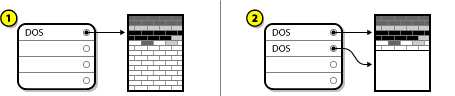
Figure A.12. Disk Drive with Partition Resized
A.2.3.3. Create new partitions
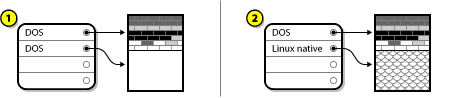
Figure A.13. Disk Drive with Final Partition Configuration
A.3. Partition Naming Schemes and Mount Points
A.3.1. Partition Naming Scheme
/dev/xxyN.
/dev/- This is the name of the directory in which all device files reside. Because partitions reside on hard disks, and hard disks are devices, the files representing all possible partitions reside in
/dev/. xx- The first two letters of the partition name indicate the type of device on which the partition resides, usually
sd. y- This letter indicates which device the partition is on. For example,
/dev/sdafor the first hard disk,/dev/sdbfor the second, and so on. N- The final number denotes the partition. The first four (primary or extended) partitions are numbered
1through4. Logical partitions start at5. So, for example,/dev/sda3is the third primary or extended partition on the first hard disk, and/dev/sdb6is the second logical partition on the second hard disk.
Note
A.3.2. Disk Partitions and Mount Points
/dev/sda5 is mounted on /usr/, that would mean that all files and directories under /usr/ physically reside on /dev/sda5. So the file /usr/share/doc/FAQ/txt/Linux-FAQ would be stored on /dev/sda5, while the file /etc/gdm/custom.conf would not.
/usr/ would be mount points for other partitions. For instance, a partition (say, /dev/sda7) could be mounted on /usr/local/, meaning that /usr/local/man/whatis would then reside on /dev/sda7 rather than /dev/sda5.
A.3.3. How Many Partitions?
swap, /boot/, and / (root).
Appendix B. iSCSI Disks
B.1. iSCSI Disks in Anaconda
- When Anaconda starts, it checks if the BIOS or add-on boot ROMs of the system support iSCSI Boot Firmware Table (iBFT), a BIOS extension for systems which can boot from iSCSI. If the BIOS supports iBFT, Anaconda will read the iSCSI target information for the configured boot disk from the BIOS and log in to this target, making it available as an installation target.
Important
To connect automatically to an iSCSI target, a network device for accessing the target needs to be activated. The recommended way to do so is to useip=ibftboot option. - You can discover and add iSCSI targets manually in the graphical user interface in anaconda. From the main menu, the Installation Summary screen, click the Installation Destination option. Then click the in the Specialized & Network Disks section of the screen. A tabbed list of available storage devices appears. In the lower right corner, click the button and proceed with the discovery process. See Section 8.15.1, “The Storage Devices Selection Screen” for more information.
Important
Restriction: The/bootpartition cannot be placed on iSCSI targets that have been manually added using this method - an iSCSI target containing a/bootpartition must be configured for use with iBFT.However, in instances where the installed system is expected to boot from iSCSI with iBFT configuration provided by a method other than firmware iBFT, for example using iPXE, the/bootpartition restriction can be disabled using theinst.nonibftiscsibootinstaller boot option.
/ so that the system will automatically log in to them when it starts. If / is placed on an iSCSI target, initrd will log into this target and Anaconda does not include this target in start up scripts to avoid multiple attempts to log into the same target.
B.2. iSCSI Disks During Start Up
- The init script in the initrd will log into iSCSI targets used for
/, if any. This is done using the iscsistart utility, without requiring iscsid to run.Note
If the root file system is on an iSCSI disk connected using IPv6, ensure that the installed system is using the correctip=boot option, for exampleip=eth0:auto6. If this option is not set, the installed system can spend up to 20 minutes at boot time attempting to establish a connection, before eventually succeeding. Using the correctip=option eliminates this delay. - When the root file system has been mounted and the various service init scripts are running, the iscsi init script will get called. This script then starts the iscsid daemon if any iSCSI targets are used for
/, or if any targets in the iSCSI database are marked to be logged into automatically. - After the classic network service script has been run, the iscsi init script will run. If the network is accessible, this will log into any targets in the iSCSI database that are marked to be logged into automatically. If the network is not accessible, this script will exit quietly.
- When using NetworkManager to access the network, instead of the classic network service script, NetworkManager will call the iscsi init script. Also see the
/etc/NetworkManager/dispatcher.d/04-iscsifile for further reference.Important
Because NetworkManager is installed in the/usrdirectory, you cannot use it to configure network access if/usris on network-attached storage such as an iSCSI target.
Appendix C. Anaconda UI specific commands
C.1. Commands used in Anaconda
-
pwpolicy(optional) - This command can be used to enforce a custom password policy, which specifies requirements for passwords created during installation, based on factors such as password length and strength.
pwpolicy name [--minlen=length] [--minquality=quality] [--strict|--nostrict] [--emptyok|--noempty] [--changesok|--nochanges]
pwpolicy name [--minlen=length] [--minquality=quality] [--strict|--nostrict] [--emptyok|--noempty] [--changesok|--nochanges]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace name with eitherroot,userorluksto enforce the policy for therootpassword, user passwords, or LUKS passphrase, respectively.Thelibpwqualitylibrary is used to check minimum password requirements (length and quality). You can use thepwscoreandpwmakecommands provided by the libpwquality package to check the quality score of a password, or to create a random password with a given score. See thepwscore(1)andpwmake(1)man page for details about these commands.Important
This command can only be used inside the%anacondasection.--minlen=- Sets the minimum allowed password length, in characters. The default is6.--minquality=- Sets the minimum allowed password quality as defined by thelibpwqualitylibrary. The default value is1.--strict- Enables strict password enforcement. Passwords which do not meet the requirements specified in--minquality=and--minlen=will not be accepted. This option is disabled by default.--notstrict- Passwords which do not meet the minimum quality requirements specified by the--minquality=and-minlen=options will be allowed, after Done is clicked twice.--emptyok- Allows the use of empty passwords. Enabled by default for user passwords.--notempty- Disallows the use of empty passwords. Enabled by default for the root password and the LUKS passphrase.--changesok- Allows changing the password in the user interface, even if the Kickstart file already specifies a password. Disabled by default.--nochanges- Disallows changing passwords which are already set in the Kickstart file. Enabled by default.
Appendix D. Understanding LVM
xfs, and a mount point.
Important
/boot partition.
/boot on LVM logical volumes with linear mapping.
/ and swap partitions within LVM volumes, with a separate /boot partition on a physical volume.
Appendix E. Other Technical Documentation
- Boot Loader
- Red Hat Enterprise Linux uses the
GRUB2boot loader. See the corresponding chapter in the RRed Hat Enterprise Linux 7 System Administrator's Guide. - Storage Management
- Logical Volume Management (LVM) provides administrators with a range of facilities to manage storage. By default, the Red Hat Enterprise Linux installation process formats drives as LVM volumes. For further details about LVM, see the Red Hat Enterprise Linux 7 Logical Volume Manager Administration Guide.
- Remote Displays
- Red Hat Enterprise Linux and Anaconda include VNC (Virtual Network Computing) software to enable remote access to graphical displays. For more information about VNC, see the TigerVNC chapter in the Red Hat Enterprise Linux 7 System Administrator's Guide.You can also use the VNC Configurator application on the Red Hat Customer Portal to guide you through VNC server and client setup.
- Remote System Access
- Red Hat Enterprise Linux incorporates the OpenSSH suite to provide remote access to the system. The SSH service enables a number of functions, which include access to the command-line from other systems, remote command execution, and network file transfers. During the installation process,
Anacondamight use thescpfeature of OpenSSH to transfer crash reports to remote systems. For further details about OpenSSH, see the corresponding section in the Red Hat Enterprise Linux 7 System Administrator's Guide. - Access Control
- SELinux provides Mandatory Access Control (MAC) capabilities that supplement the standard Linux security features. See the Red Hat Enterprise Linux 7 SELinux User's and Administrator's Guide for further information.
- Firewall
- Red Hat Enterprise Linux uses firewalld to provide firewall features. For further information, see the corresponding chapter in the Red Hat Enterprise Linux 7 Security Guide.
- Software Installation
- Red Hat Enterprise Linux uses
yumto manage the RPM packages that make up the system. See the corresponding chapter in the Red Hat Enterprise Linux 7 Administrator's Guide for further information. - Virtualization
- Virtualization provides the capability to simultaneously run multiple operating systems on the same computer. Red Hat Enterprise Linux also includes tools to install and manage the secondary systems on a Red Hat Enterprise Linux host. You can select virtualization support during the installation process, or at any time thereafter. See the Red Hat Enterprise Linux 7 Virtualization Deployment and Administration Guide for more information.
Appendix F. Reference Table for ext4 and XFS Commands
| Task | ext4 | XFS |
|---|---|---|
| Creating a file system | mkfs.ext4 | mkfs.xfs |
| Mounting a file system | mount | mount |
| Resizing a file system | resize2fs | xfs_growfs [a] |
| Repairing a file system | e2fsck | xfs_repair |
| Changing the label on a file system | e2label | xfs_admin -L |
| Reporting on disk space and file usage | quota | quota |
| Debugging a file system | debugfs | xfs_db |
| Saving critical file system metadata to a file | e2image | xfs_metadump |
[a]
The size of XFS file systems cannot be reduced; the command is used only to increase the size.
| ||
Appendix G. Data Size Terminology Reference Table
| Term | Abbreviation | Size (in bytes) |
|---|---|---|
| Binary (Bytes) | ||
| Kibibyte | KiB | 1024 |
| Mebibyte | MiB | 10242 |
| Gibibyte | GiB | 10243 |
| Tebibyte | TiB | 10244 |
| Pebibyte | PiB | 10245 |
| Exbibyte | EiB | 10246 |
| Zebibyte | ZiB | 10247 |
| Yobibyte | YiB | 10248 |
| Decimal (Bytes) | ||
| Kilobyte | KB | 1000 |
| Megabyte | MB | 10002 |
| Gigabyte | GB | 10003 |
| Terabyte | TB | 10004 |
| Petabyte | PB | 10005 |
| Exabyte | EB | 10006 |
| Zettabyte | ZB | 10007 |
| Yottabyte | YB | 10008 |
| Decimal (Bits) | ||
| Kilobit | Kb | 125 |
| Megabit | Mb | 125,000 |
| Gigabit | Gb | 125,000,000 |
Appendix H. Revision History
| Revision History | |||
|---|---|---|---|
| Revision 1.5-6 | Wed Aug 07 2019 | ||
| Revision 1.5-5 | Thu Jul 11 2019 | ||
| |||
| Revision 1.5-4 | Fri May 24 2019 | ||
| |||
| Revision 1.5-3 | Tue Oct 30 2018 | ||
| |||
| Revision 1.5-2 | Tue Aug 21 2018 | ||
| |||
| Revision 1.5-1 | Fri Apr 6 2018 | ||
| |||
| Revision 1.5-0 | Fri Dec 15 2017 | ||
| |||
| Revision 1.4-2 | Thu Nov 23 2017 | ||
| |||
| Revision 1.4-1 | Fri Oct 13 2017 | ||
| |||
| Revision 1.4-0 | Tue Aug 1 2017 | ||
| |||
| Revision 1.3-9 | Mon May 15 2017 | ||
| |||
| Revision 1.3-8 | Tue Apr 4 2017 | ||
| |||
| Revision 1.3-7 | Sun Nov 6 2016 | ||
| |||
| Revision 1.3-4 | Mon Nov 16 2015 | ||
| |||
| Revision 1.2-2 | Wed Feb 18 2015 | ||
| |||
| Revision 1.0-0 | Tue Jun 03 2014 | ||
| |||
Index
Symbols
- /boot partition
- recommended partitioning, Recommended Partitioning Scheme, Recommended Partitioning Scheme
- /var/ partition
- recommended partitioning, Recommended Partitioning Scheme, Recommended Partitioning Scheme
A
- adding partitions
- anaconda.log
- AMD64 and Intel 64, Troubleshooting Installation on 64-bit AMD, Intel, and ARM Systems
- IBM Power Systems, Troubleshooting Installation on IBM Power Systems
- IBM Z, Troubleshooting Installation on IBM Z
- anaconda.packaging.log
- array (see RAID)
- automatic partitioning, Installation Destination, Installation Destination, Installation Destination
B
- BIOS (Basic Input/Output System), Booting the Installation on 64-bit AMD, Intel, and ARM systems
- boot loader, Boot Loader Installation, Boot Loader Installation
- GRUB2, Boot Loader Installation, Boot Loader Installation
- installation, Boot Loader Installation, Boot Loader Installation
- boot menu
- options, Boot Options
- boot options, Boot Options
- console, Configuring the Installation System at the Boot Menu
- debugging, Configuring the Installation System at the Boot Menu
- disk device names, Configuring the Installation System at the Boot Menu
- driver updates, Configuring the Installation System at the Boot Menu
- gpt, Configuring the Installation System at the Boot Menu
- GUID Partition Table, Configuring the Installation System at the Boot Menu
- installation program runtime image, Configuring the Installation System at the Boot Menu
- installation source, Configuring the Installation System at the Boot Menu
- kexec, Configuring the Installation System at the Boot Menu
- logging, Configuring the Installation System at the Boot Menu
- media verification, Verifying Boot Media
- memory testing mode, Loading the Memory (RAM) Testing Mode
- multilib, Configuring the Installation System at the Boot Menu
- network, Configuring the Installation System at the Boot Menu
- remote access, Configuring the Installation System at the Boot Menu
- rescue mode, Booting Your Computer in Rescue Mode
- selinux, Configuring the Installation System at the Boot Menu
- text mode, Configuring the Installation System at the Boot Menu
- troubleshooting, Configuring the Installation System at the Boot Menu
- VNC, Configuring the Installation System at the Boot Menu
- zram, Configuring the Installation System at the Boot Menu
- zRAM, Configuring the Installation System at the Boot Menu
- booting
- installation program
- AMD64 and Intel 64, Booting from Physical Media
- rescue mode, Anaconda Rescue Mode
- booting the installation program
- IBM Power Systems, Booting the Installation on IBM Power Systems
C
- CD/DVD media
- booting, Booting the Installation on 64-bit AMD, Intel, and ARM systems, Booting the Installation on IBM Power Systems
- making, Making an Installation CD or DVD
- (see also ISO images)
- Chain loading, The Storage Devices Selection Screen, The Storage Devices Selection Screen
- clock, Date & Time, Date & Time, Date & Time
- CMS configuration files, Parameter and Configuration Files on IBM Z
- sample CMS configuration file, Sample Parameter File and CMS Configuration File
- configuration
- hardware, System Specifications List, System Specifications List
- time, Date & Time, Date & Time, Date & Time
- time zone, Date & Time, Date & Time, Date & Time
- configuration files
- CMS configuration files, Parameter and Configuration Files on IBM Z
- the z/VM configuration file, The z/VM Configuration File
- custom image
- creating, Installing into a Disk Image
D
- DASD, DASD storage devices
- DHCP (Dynamic Host Configuration Protocol), Network & Hostname, Network & Hostname, Network & Hostname
- Disk Partitioner
- adding partitions
- disk partitioning, Installation Destination, Installation Destination, Installation Destination
- disk space, Disk Space and Memory Requirements, Disk Space and Memory Requirements
- DVD media
- downloading, Downloading Red Hat Enterprise Linux
- (see also ISO images)
E
- extended partitions, Partitions Within Partitions - An Overview of Extended Partitions
F
- FCoE
- installation, Advanced Storage Options, Advanced Storage Options, Advanced Storage Options
- fcoe
- via Kickstart, Kickstart Commands and Options
- FCP devices, FCP Devices
- file system
- formats, overview of, File Systems
- file system types, File System Types, File System Types, File System Types
- firewall
- documentation, Other Technical Documentation
G
- GRUB2, Boot Loader Installation, Boot Loader Installation
- documentation, Other Technical Documentation
- installation, Boot Loader Installation, Boot Loader Installation
- GUID Partition Table
- specifying as a boot option, Configuring the Installation System at the Boot Menu
H
- hard disk
- basic concepts, Hard Disk Basic Concepts
- extended partitions, Partitions Within Partitions - An Overview of Extended Partitions
- file system formats, File Systems
- partition introduction, Partitions: Turning One Drive Into Many
- partition types, Partitions: Turning One Drive Into Many
- partitioning of, An Introduction to Disk Partitions
- hardware
- compatibility, Is Your Hardware Compatible?, Is Your Hardware Compatible?
- configuration, System Specifications List, System Specifications List
- support, Supported Installation Targets, Supported Installation Targets
- hardware preparation, IBM Power Systems servers, Preparation for IBM Power Systems Servers
- HMC vterm, Using the HMC vterm
- hostname, Network & Hostname, Network & Hostname, Network & Hostname
I
- Initial Setup
- subscriptions, Subscription Manager
- via Kickstart, Kickstart Commands and Options
- install log file
- installation
- disk space, Disk Space and Memory Requirements, Disk Space and Memory Requirements
- getting started, Getting Started
- GRUB2, Boot Loader Installation, Boot Loader Installation
- Kickstart (see Kickstart installations)
- memory requirements, Disk Space and Memory Requirements, Disk Space and Memory Requirements
- partitioning, Manual Partitioning, Manual Partitioning, Manual Partitioning
- program
- starting, Starting the Installation Program
- text mode, Configuring the Installation System at the Boot Menu
- using VNC, Using VNC
- Installation media
- downloading, Downloading Red Hat Enterprise Linux
- installation program
- AMD64 and Intel 64
- booting, Booting from Physical Media
- installation program rescue mode
- definition of, Anaconda Rescue Mode
- utilities available, Anaconda Rescue Mode
- installing packages, Software Selection, Software Selection, Software Selection
- IPv4, Network & Hostname, Network & Hostname, Network & Hostname
- iscsi
- installation, Advanced Storage Options, Advanced Storage Options, Advanced Storage Options
- ISO images
- downloading, Downloading Red Hat Enterprise Linux
K
- kdump, Kdump, Kdump, Kdump
- kexec
- keyboard
- configuration, Keyboard Configuration, Keyboard Configuration, Keyboard Configuration
- keymap
- selecting language, Welcome Screen and Language Selection, Welcome Screen and Language Selection, Welcome Screen and Language Selection
- selecting type of keyboard, Keyboard Configuration, Keyboard Configuration, Keyboard Configuration
- Kickstart
- how the file is found, Starting the Kickstart Installation
- parameters for IBM Z parameter files, Parameters for Kickstart Installations
- subscriptions, Post-installation Script
- Kickstart file
- %anaconda, Anaconda configuration
- %include, Kickstart Commands and Options
- %post, Post-installation Script
- %pre, Pre-installation Script
- anaconda configuration, Anaconda configuration
- auth, Kickstart Commands and Options
- authconfig, Kickstart Commands and Options
- autopart, Kickstart Commands and Options
- autostep, Kickstart Commands and Options
- bootloader, Kickstart Commands and Options
- btrfs, Kickstart Commands and Options
- changes in syntax, Changes in Kickstart Syntax
- clearpart, Kickstart Commands and Options
- cmdline, Kickstart Commands and Options
- creating, Kickstart Commands and Options
- creating required partitions, Kickstart Commands and Options
- device, Kickstart Commands and Options
- driverdisk, Kickstart Commands and Options
- eula, Kickstart Commands and Options
- fcoe, Kickstart Commands and Options
- firewall, Kickstart Commands and Options
- firstboot, Kickstart Commands and Options
- format of, Creating a Kickstart File
- graphical, Kickstart Commands and Options
- group, Kickstart Commands and Options
- halt, Kickstart Commands and Options
- ignoredisk, Kickstart Commands and Options
- include contents of another file, Kickstart Commands and Options
- install, Kickstart Commands and Options
- installation methods, Kickstart Commands and Options
- installation source, Kickstart Commands and Options
- iscsi, Kickstart Commands and Options
- iscsiname, Kickstart Commands and Options
- kdump, Kickstart Commands and Options
- keyboard, Kickstart Commands and Options
- lang, Kickstart Commands and Options
- logging, Kickstart Commands and Options
- logvol, Kickstart Commands and Options
- mediacheck, Kickstart Commands and Options
- mount, Kickstart Commands and Options
- network, Kickstart Commands and Options
- network-based, Making the Installation Source Available
- nvdimm, Kickstart Commands and Options
- options, Kickstart Commands and Options
- partitioning examples, Advanced Partitioning Example
- user input, User Input Example
- org_fedora_oscap, Kickstart Commands and Options
- package selection specification, Package Selection
- part, Kickstart Commands and Options
- partition, Kickstart Commands and Options
- post-installation configuration, Post-installation Script
- poweroff, Kickstart Commands and Options
- pre-installation configuration, Pre-installation Script
- pwpolicy, Commands used in Anaconda
- raid , Kickstart Commands and Options
- realm, Kickstart Commands and Options
- reboot, Kickstart Commands and Options
- repository configuration, Kickstart Commands and Options
- rescue, Kickstart Commands and Options
- rootpw, Kickstart Commands and Options
- selinux, Kickstart Commands and Options
- services , Kickstart Commands and Options
- shutdown, Kickstart Commands and Options
- skipx, Kickstart Commands and Options
- snapshot, Kickstart Commands and Options
- sshpw, Kickstart Commands and Options
- text, Kickstart Commands and Options
- timezone, Kickstart Commands and Options
- unsupported_hardware, Kickstart Commands and Options
- user, Kickstart Commands and Options
- vnc, Kickstart Commands and Options
- volgroup, Kickstart Commands and Options
- what it looks like, Creating a Kickstart File
- xconfig, Kickstart Commands and Options
- zerombr, Kickstart Commands and Options
- zfcp, Kickstart Commands and Options
- Kickstart installations, Kickstart Installations
- file format, Creating a Kickstart File
- file locations, Making the Kickstart File Available
- installation source, Making the Installation Source Available
- LVM, Kickstart Commands and Options
- network-based, Making the Installation Source Available
- starting, Starting the Kickstart Installation
- kickstart installations
- validation, Verifying the Kickstart File
- verification, Verifying the Kickstart File
- KRDC, Installing a VNC Viewer
L
- language
- live image
- creating, Installing into a Disk Image
- livemedia-creator, Installing into a Disk Image
- additional packages, Installing livemedia-creator
- examples, Creating Custom Images
- installation, Installing livemedia-creator
- Kickstart files, Sample Kickstart Files
- log files, Troubleshooting livemedia-creator Problems
- troubleshooting, Troubleshooting livemedia-creator Problems
- usage, Creating Custom Images
- log files
- AMD64 and Intel 64, Troubleshooting Installation on 64-bit AMD, Intel, and ARM Systems
- IBM Power Systems, Troubleshooting Installation on IBM Power Systems
- IBM Z, Troubleshooting Installation on IBM Z
- Kickstart installations, What are Kickstart Installations?
- LVM
- documentation, Other Technical Documentation
- logical volume, Understanding LVM
- physical volume, Understanding LVM
- understanding, Understanding LVM
- volume group, Understanding LVM
- with Kickstart, Kickstart Commands and Options
M
- master boot record, Boot Loader Installation, Boot Loader Installation
- Master Boot Record, Unable to Boot into Red Hat Enterprise Linux
- reinstalling, Reinstalling the Boot Loader
- memory
- minimum requirements, Disk Space and Memory Requirements, Disk Space and Memory Requirements
- memory testing mode, Loading the Memory (RAM) Testing Mode
- mount points
- partitions and, Disk Partitions and Mount Points
- multilib
- enabling during installation, Configuring the Installation System at the Boot Menu
- Multipath devices
- Mixing with non-multipath devices, Installation Destination
N
- Network boot installations
- configuration, Configuring Network Boot Services
- overview, Preparing for a Network Installation
- NTP (Network Time Protocol), Date & Time, Date & Time, Date & Time
- NVDIMM
- hardware, RAID and Other Disk Devices
O
- OpenSSH, Other Technical Documentation
- (see also SSH)
P
- packages
- groups, Software Selection, Software Selection, Software Selection
- selecting, Software Selection, Software Selection, Software Selection
- installing, Software Selection, Software Selection, Software Selection
- selecting, Software Selection, Software Selection, Software Selection
- packaging.log
- AMD64 and Intel 64, Troubleshooting Installation on 64-bit AMD, Intel, and ARM Systems
- IBM Power Systems, Troubleshooting Installation on IBM Power Systems
- IBM Z, Troubleshooting Installation on IBM Z
- parameter files, Parameter and Configuration Files on IBM Z
- installation network parameters, Installation Network Parameters
- Kickstart parameters, Parameters for Kickstart Installations
- required parameters, Required Parameters
- sample parameter file, Sample Parameter File and CMS Configuration File
- parm files (see parameter files)
- partition
- partitioning, Manual Partitioning, Manual Partitioning, Manual Partitioning
- automatic, Installation Destination, Installation Destination, Installation Destination
- basic concepts, An Introduction to Disk Partitions
- creating new, Adding File Systems and Configuring Partitions, Adding File Systems and Configuring Partitions, Adding File Systems and Configuring Partitions
- file system type, File System Types, File System Types, File System Types
- destructive, Using Free Space from an Active Partition
- extended partitions, Partitions Within Partitions - An Overview of Extended Partitions
- how many partitions, Partitions: Turning One Drive Into Many, How Many Partitions?
- introduction to, Partitions: Turning One Drive Into Many
- making room for partitions, Strategies for Disk Repartitioning
- mount points and, Disk Partitions and Mount Points
- naming partitions, Partition Naming Scheme
- non-destructive, Using Free Space from an Active Partition
- numbering partitions, Partition Naming Scheme
- primary partitions, Partitions: Turning One Drive Into Many
- recommended, Recommended Partitioning Scheme, Recommended Partitioning Scheme
- types of partitions, Partitions: Turning One Drive Into Many
- using free space, Using Unpartitioned Free Space
- using in-use partition, Using Free Space from an Active Partition
- using unused partition, Using Space from an Unused Partition
- Partitioning , Manual Partitioning, Manual Partitioning, Manual Partitioning
- adding partitions
- file system type, File System Types, File System Types, File System Types
- password
- setting root, Set the Root Password, Set the Root Password, Set the Root Password
- Planning for Installation
- IBM Z, Pre-installation
- program.log
- AMD64 and Intel 64, Troubleshooting Installation on 64-bit AMD, Intel, and ARM Systems
- IBM Power Systems, Troubleshooting Installation on IBM Power Systems
- IBM Z, Troubleshooting Installation on IBM Z
- PXE (Pre-boot eXecution Environment), Booting from the Network Using PXE
R
- RAID
- hardware, RAID and Other Disk Devices, RAID and Other Disk Devices
- Kickstart installations, Kickstart Commands and Options
- software, RAID and Other Disk Devices, RAID and Other Disk Devices
- trouble booting from drive attached to RAID card
- AMD64 and Intel 64, Are You Unable to Boot With Your RAID Card?
- registration
- with Initial Setup, Subscription Manager
- with Kickstart, Post-installation Script
- remote installation
- using VNC, Using VNC
- removing
- Red Hat Enterprise Linux
- from IBM Z, Removing Red Hat Enterprise Linux from IBM Z
- from x86_64-based systems, Removing Red Hat Enterprise Linux from 64-bit AMD, Intel, and ARM Systems
- rescue mode, Booting Your Computer in Rescue Mode
- using the installation program, Anaconda Rescue Mode
- root / partition
- recommended partitioning, Recommended Partitioning Scheme, Recommended Partitioning Scheme
- root password, Set the Root Password, Set the Root Password, Set the Root Password
S
- scp, Other Technical Documentation
- (see also SSH)
- selecting
- packages, Software Selection, Software Selection, Software Selection
- SELinux
- documentation, Other Technical Documentation
- SSH (Secure SHell)
- documentation, Other Technical Documentation
- starting
- installation, Starting the Installation Program
- steps
- booting with CD-ROM or DVD, Choose an Installation Boot Method, Choose an Installation Boot Method
- disk space, Disk Space and Memory Requirements, Disk Space and Memory Requirements
- hardware compatibility, Is Your Hardware Compatible?, Is Your Hardware Compatible?
- IBM Power Systems servers hardware preparation, Preparation for IBM Power Systems Servers
- supported hardware, Supported Installation Targets, Supported Installation Targets
- storage devices
- basic storage devices, Storage Devices, Storage Devices, Storage Devices
- specialized storage devices, Storage Devices, Storage Devices, Storage Devices
- storage.log
- AMD64 and Intel 64, Troubleshooting Installation on 64-bit AMD, Intel, and ARM Systems
- IBM Power Systems, Troubleshooting Installation on IBM Power Systems
- IBM Z, Troubleshooting Installation on IBM Z
- subscription
- with Kickstart, Post-installation Script
- subscription service, Unregistering from Red Hat Subscription Management Services
- subscriptions
- after the installation, Subscription Manager
- in Initial Setup, Subscription Manager
- swap partition
- recommended partitioning, Recommended Partitioning Scheme, Recommended Partitioning Scheme
- syslog
- AMD64 and Intel 64, Troubleshooting Installation on 64-bit AMD, Intel, and ARM Systems
- IBM Power Systems, Troubleshooting Installation on IBM Power Systems
- IBM Z, Troubleshooting Installation on IBM Z
- system recovery, Basic System Recovery
- common problems, Common Problems
- hardware and software problems, Hardware and Software Problems
- reinstalling the boot loader, Reinstalling the Boot Loader
- sosreport, Capturing an sosreport
- unable to boot into Red Hat Enterprise Linux, Unable to Boot into Red Hat Enterprise Linux
T
- text mode
- installation, Configuring the Installation System at the Boot Menu
- TigerVNC, Installing a VNC Viewer
- time zone
- configuration, Date & Time, Date & Time, Date & Time
- traceback messages
- saving traceback messages without removable media
- AMD64 and Intel 64, Reporting Traceback Messages
- IBM Power Systems, Reporting Traceback Messages
- IBM Z, Reporting Traceback Messages
- troubleshooting
- after the installation
- AMD64 and Intel 64, Problems After Installation
- IBM Power Systems, Problems After Installation
- IBM Z, Problems After Installation
- AMD64 and Intel 64, Troubleshooting Installation on 64-bit AMD, Intel, and ARM Systems
- beginning the installation
- AMD64 and Intel 64, Trouble Beginning the Installation
- IBM Power Systems, Trouble Beginning the Installation
- booting
- RAID cards, Are You Unable to Boot With Your RAID Card?
- booting into a graphical environment
- AMD64 and Intel 64, Booting into a Graphical Environment
- IBM Power Systems, Booting into a Graphical Environment
- booting into GNOME or KDE
- AMD64 and Intel 64, Booting into a Graphical Environment
- IBM Power Systems, Booting into a Graphical Environment
- booting into the X Window System
- AMD64 and Intel 64, Booting into a Graphical Environment
- IBM Power Systems, Booting into a Graphical Environment
- completing partitions
- IBM Power Systems, Other Partitioning Problems for IBM Power Systems Users
- Console unavailable
- AMD64 and Intel 64, Serial Console Not Detected
- IBM Power Systems, Serial Console Not Detected
- during the installation
- AMD64 and Intel 64, Trouble During the Installation
- IBM Power Systems, Trouble During the Installation
- IBM Z, Trouble During the Installation
- graphical boot
- AMD64 and Intel 64, Trouble With the Graphical Boot Sequence
- IBM Power Systems, Trouble With the Graphical Boot Sequence
- graphical login
- GRUB2
- GUI installation method unavailable
- AMD64 and Intel 64, Problems with Booting into the Graphical Installation
- IBM Power Systems, Problems with Booting into the Graphical Installation
- IBM Power Systems, Troubleshooting Installation on IBM Power Systems
- IBM Z, Troubleshooting Installation on IBM Z
- IPL NWSSTG
- IBM Power Systems, Unable to IPL from Network Storage Space (*NWSSTG)
- no disks detected
- AMD64 and Intel 64, No Disks Detected
- IBM Power Systems, No Disks Detected
- IBM Z, No Disks Detected
- RAM not recognized
- AMD64 and Intel 64, Is Your RAM Not Being Recognized?
- remote desktop
- saving traceback messages without removable media
- AMD64 and Intel 64, Reporting Traceback Messages
- IBM Power Systems, Reporting Traceback Messages
- IBM Z, Reporting Traceback Messages
- signal 11 error
- AMD64 and Intel 64, Is Your System Displaying Signal 11 Errors?
- IBM Power Systems, Is Your System Displaying Signal 11 Errors?
- IBM Z, Is Your System Displaying Signal 11 Errors?
- X (X Window System)
- AMD64 and Intel 64, No Graphical User Interface Present
- IBM Power Systems, No Graphical User Interface Present
- X server crashes
- AMD64 and Intel 64, X Server Crashing After User Logs In
- IBM Power Systems, X Server Crashing After User Logs In
U
- UEFI (Unified Extensible Firmware Interface), Booting the Installation on 64-bit AMD, Intel, and ARM systems
- uninstalling
- from IBM Z, Removing Red Hat Enterprise Linux from IBM Z
- from x86_64-based systems, Removing Red Hat Enterprise Linux from 64-bit AMD, Intel, and ARM Systems
- unregister, Unregistering from Red Hat Subscription Management Services
- upgrade
- from Red Hat Enterprise Linux 6, Upgrading Your Current System
- using Preupgrade Assistant, Upgrading Your Current System
- using Red Hat Upgrade, Upgrading Your Current System
- USB boot media
- creating
- on Linux, Making Installation USB Media on Linux
- on Mac OS X, Making Installation USB Media on Mac OS X
- on Windows, Making Installation USB Media on Windows
- USB flash media
- creating, Making Installation USB Media
- downloading, Downloading Red Hat Enterprise Linux
- USB media
V
- Vinagre, Installing a VNC Viewer
- Virtualization
- documentation, Other Technical Documentation
- VNC
- Connect Mode, Installing in VNC Connect Mode
- Direct Mode, Installing in VNC Direct Mode
- usage during installation, Using VNC
- viewer, Installing a VNC Viewer
- VNC (Virtual Network Computing)
- documentation, Other Technical Documentation
X
- XDMCP
- enabling
Y
- yum
- documentation, Other Technical Documentation
Z
- zRAM
- using as swap space, Configuring the Installation System at the Boot Menu