Installation Guide
Installation and Configuration of Red Hat Update Infrastructure
Abstract
Chapter 1. Introduction to Red Hat Update Infrastructure
Important
- for Red Hat Enterprise Linux 5 —
redhat-release-5Server - for Red Hat Enterprise Linux 6 —
redhat-release-server
- Setting a storage volume mount point in the cloud to store installation or update packages synchronized from the Red Hat Customer Portal.
- Configuring network security for intra-cloud communications.
- Adding monitoring checks other than those offered by Red Hat.
Note
yum list command is run on an system using Red Hat Update Infrastructure, all package versions are returned. Despite this, Red Hat Update Infrastructure can only supply the latest available version of a package when clients are updated.
1.1. System Overview
- the Red Hat Update Appliance (RHUA). The Red Hat Update Appliance is a system instance that runs in the cloud by default. It
- synchronizes packages from an external source (such as the Red Hat Customer Portal).
- monitors status and provides both machine and human-readable update reports.
- manages one or more Content Delivery Servers.
- the Content Delivery Server (CDS). A CDS serves packages to cloud-based clients via HTTPS.
1.1.1. Communication
- The cloud provider accesses a central third-party content repository, such as Red Hat Customer Portal. Note: the Red Hat Update Appliance can connect to the content repository using a cloud provider’s network proxy server.
- The Red Hat Update Appliance synchronizes content to the CDS instances, and evenly distributes requests. Note: Each CDS serves as a load balancer. There is no need to install the load balancer either as a seperate instance or as part of the Red Hat Update Appliance.
- CDS instances distribute content via HTTPS to cloud-hosted Red Hat Enterprise Linux instances.
1.1.2. Certificates
- Content certificate
- The content certificate and its associated private key are given to the customer to allow access to Red Hat Customer Portal. This grants permission to the customer to download the Red Hat Update Infrastructure packages or ISO. Additionally, the Red Hat Update Appliance uses this certificate when authenticating with Red Hat Customer Portal to download updated packages into the Red Hat Update Infrastructure environment.Content certificates are signed by the Red Hat Certificate Authority (CA). This is the only certificate in the Red Hat Update Infrastructure public key infrastructure (PKI) that is not signed by the cloud provider.
- Entitlement certificate
- Clients use an entitlement certificate when connecting to CDS instances. The entitlement certificate contains entitlements for some or all of the products initially granted to the cloud provider in the content certificate. A client using an entitlement certificate can only get access to channels for which the certificate provides an entitlement.The entitlement certificate must be signed by a Certificate Authority (CA). This allows you to generate entitlement certificates for use in your environment without having to request them from Red Hat. All requests to the Red Hat Update Infrastructure that test the entitlement certificate will check that it was signed by the CA. This prevents users from spoofing the Red Hat Update Infrastructure with self-signed certificates.
- SSL Certificates
- SSL is used for communicating with CDS instances. SSL requires that a new SSL certificate is generated for each instance. For example, in an environment with three CDS instances, three separate certificates will need to be generated. The common name (CN) of the certificate must match the hostname of the instance.
Important
Chapter 2. Installation Requirements
2.1. Prerequisites
Cloud Provider Prerequisites
Note
- Complete a Cloud Provider Agreement with Red Hat. Cloud providers must be certified by Red Hat in order to be able to resell Red Hat Enterprise Linux.
- Ensure you have an entitlement for every Red Hat Update Appliance instance in the cloud. This grants access to:
- Red Hat Update Infrastructure (Red Hat Update Appliance and associated technologies).
- 32-bit and 64-bit Red Hat Enterprise Linux images. This is required to perform instantiation.
- Permission for the Red Hat Update Appliance to synchronize channel content from Red Hat Customer Portal.
- The ability to generate or obtain CA and SSL certificates. These are required for configuring SSL and signing client entitlement certificates.
- Employ a method of monitoring that includes some means of notification and the ability to run custom scripts and commands.
Red Hat Update Infrastructure has the following hardware and storage requirements:
- The latest version of Red Hat Enterprise Linux
- 64-bit architecture.
- At least 2 GB of available memory
- At least 4 GB of available swap space
/var/lib/pulp. Create this directory only if you need to create a new mount point for it; otherwise, it is automatically created during the installation process.
/var/lib/pulp requires at least 40 GB of storage for each binary package repository and approximately double the allocated storage for each debug-info repository during Full Support Phase of a major Red Hat Enterprise Linux version. Note that, after the period, the estimated annual growth rates of these repositories are 10 GB per binary package repository and 20 GB per debug-info repository.
/var/lib/pulp-cds.
Note
Red Hat Update Infrastructure uses various network protocols for communication between Red Hat Update Appliance, CDS, and client instances. The following table outlines each of the protocols used:
| Port | Protocol | Source | Destination | Notes |
|---|---|---|---|---|
| 443 | HTTPS | RHUA | Package Source | Third-party repository such as Red Hat Customer Portal |
| 443 | HTTPS | Client | CDS | Used by yum on the client to retrieve packages |
| 5674 | QPID | RHUA | CDS | Used for communication between the Red Hat Update Appliance and the CDS |
| 5674 | QPID | CDS | RHUA | Used for communication between the Red Hat Update Appliance and the CDS |
Important
2.2. Downloading Entitlements
Procedure 2.1. Downloading Entitlements from the customer portal
Note
- Go to the customer portal at http://access.redhat.com and click on the Subscriptions link.
- Scroll down to the Manage section and click the RHUI link.
- Click Register a RHUI.
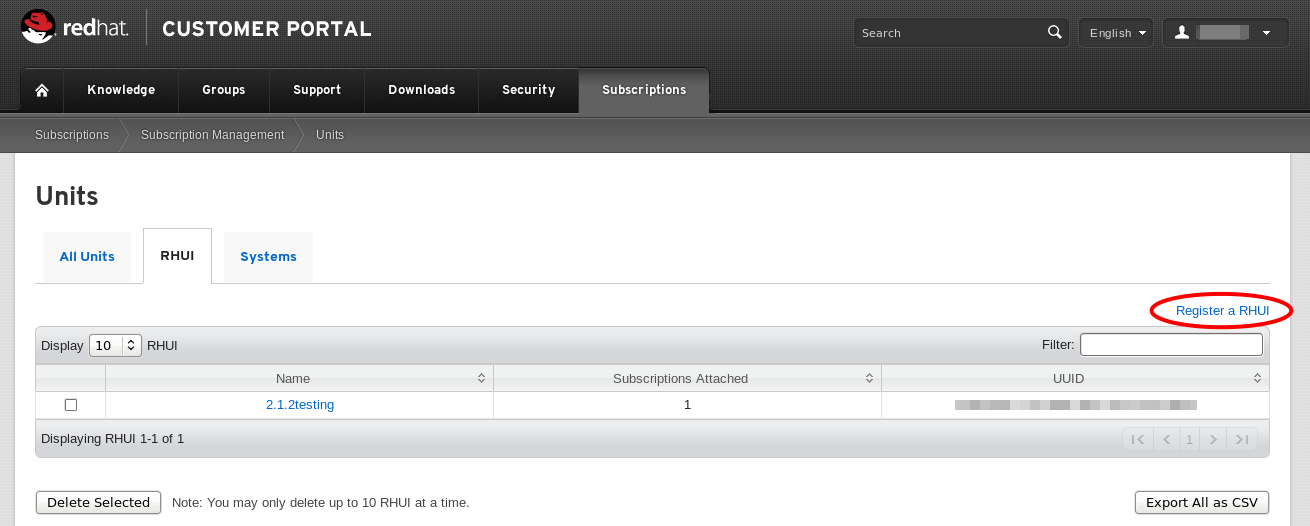
Figure 2.1. Create a New RHUI
- On the Register a New RHUI page, enter the name of the Red Hat Update Appliance instance, select a version, and click Register.
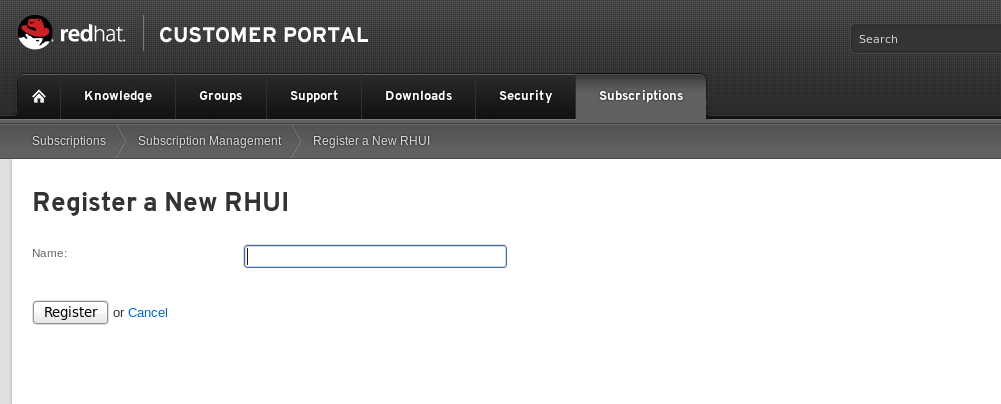
Figure 2.2. Register a New RHUI
- Your new Red Hat Update Appliance instance will not yet have any subscriptions applied to it. Add a subscription by clicking Attach a subscription in the bottom right corner. A list of available subscriptions will be displayed. Select the check box next to the desired subscription and click to add it to the instance.
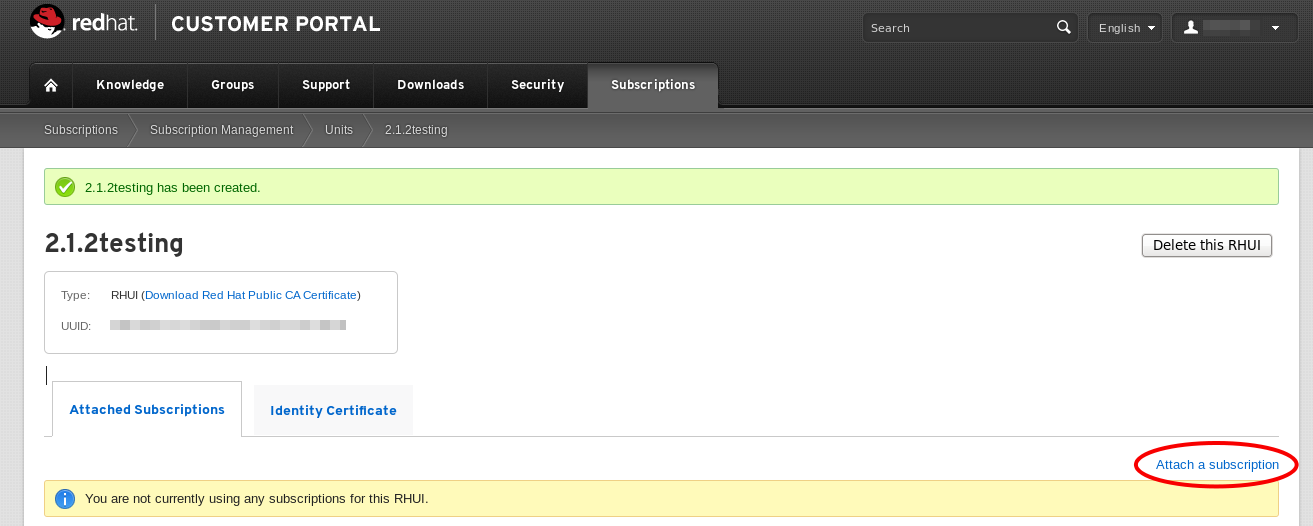
Figure 2.3. Adding Subscriptions
- Download the entitlement certificate by clicking Download in the Entitlement Certificate column of the subscriptions table. Save the entitlement certificate on your local machine and note down the location. You will need this information later when you install the Red Hat Update Infrastructure ISO.
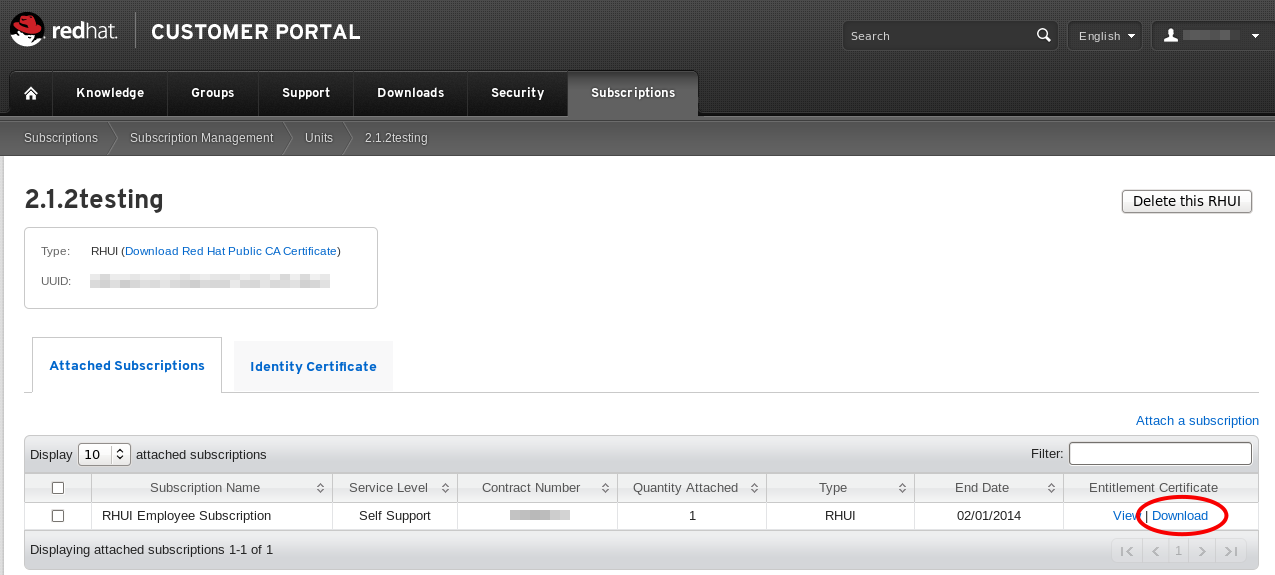
Figure 2.4. Download Entitlement Certificate
Note
The Entitlement Certificate downloaded here is used as a Content Certificate in the Red Hat Update Infrastructure package installation. - Download Red Hat Public CA Certificate by clicking Download Red Hat Public CA Certificate in the upper left corner. Save the Red Hat Public CA Certificate on your local machine and note down the location. You will need this information later when you install the Red Hat Update Infrastructure ISO.
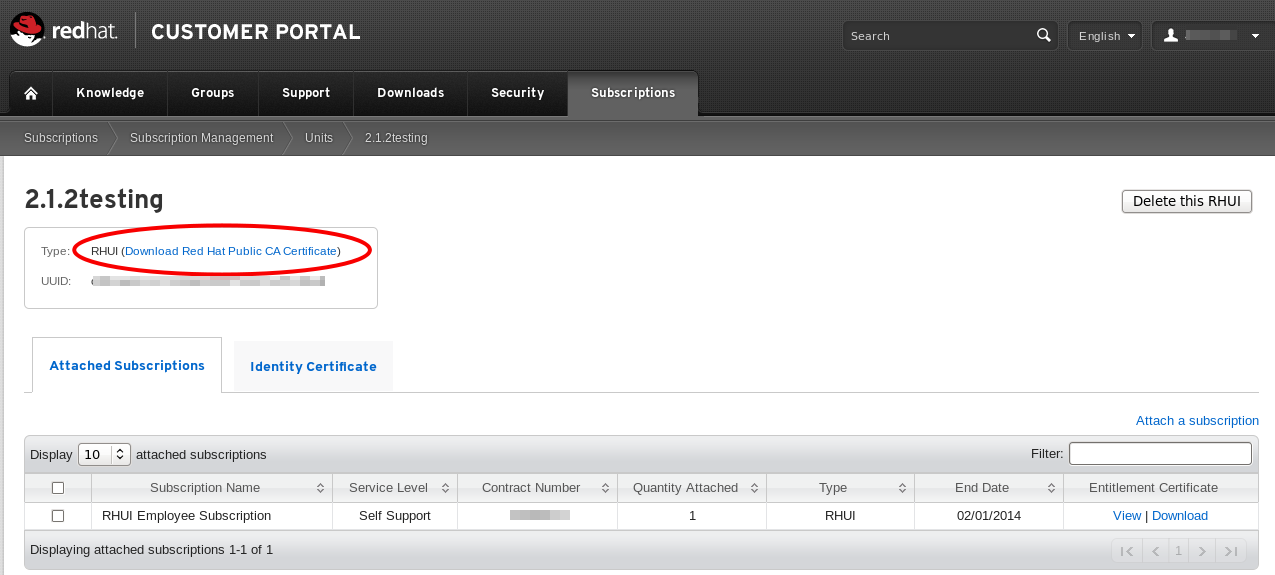
Figure 2.5. Download Red Hat Public CA Certificate
2.3. Package Installation
rhel-6-server-rpms. This requirement also means any third-party configurations or software that is not directly necessary for the direct operation of the server cannot be installed. This restriction includes hardening or other non-Red Hat security software.
Note
Procedure 2.2. Installing the Red Hat Update Infrastructure packages on the Red Hat Update Appliance Server
- Download the ISO from the Customer Portal.
- Change the hostname of the Red Hat Update Appliance Server and all CDS instances to a resolvable fully qualified domain name (FQDN).Change the hostname in your current session:
# hostname new_hostname
To make the hostname change persistent, edit/etc/sysconfig/networkusing your preferred text editor:NETWORKING=yes HOSTNAME=new_hostname ...
Important
If the hostname is unset and its value is reported aslocalhost.localdomainorlocalhost, you will not be able to proceed. In this guide, the example hostname for Red Hat Update Appliance is rhua.example.com, and the example hostname for the first CDS instance is cds01.example.com. - Mount the ISO:
# mkdir -p /mnt/example # mount -o loop <ISO> /mnt/example
- Change directory to /mnt/example.
# cd /mnt/example
- On the Red Hat Update Appliance Server, run
install_RHUA.shto install Red Hat Update Appliance packages.# ./install_RHUA.sh
Procedure 2.3. Installing the Red Hat Update Infrastructure packages on the Content Delivery Server (CDS)
- On the CDS instance, follow steps 1 to 4 in the previous procedure.
- Run the following commands to register the system to Red Hat Subscription Manager and give the system a basic Red Hat Enterprise Linux entitlement.
- Register the system to Red Hat Subscription Manager:
# subscription-manager register
- Attach the system:
# subscription-manager attach --auto
- Disable all existing repositories:
# subscription-manager repos --disable=*
- Enable the Red Hat Enterprise Linux repository:
# subscription-manager repos --enable=rhel-6-server-rpms
- Run
install_CDS.shto install CDS packages.# ./install_CDS.sh
Chapter 3. Red Hat Update Infrastructure Installer
- Configures
httpdon the Red Hat Update Appliance and any CDS instances with SSL certificates - Installs a custom CA certificate that is used for authentication of users
- Configures the Red Hat Update Appliance
- Configures secure communication between the Red Hat Update Appliance and the CDS instances
3.1. Setting Up SSL
Important
0100 to avoid conflicts within Red Hat Update Infrastructure.
3.1.1. Configuring SSL Certificates Manually
Procedure 3.1. Configuring Red Hat Update Appliance SSL Certificates
- Acquire your company's root certificate and private key. Alternatively you can purchase one from a certificate authority (CA), or generate your own using tools such as
opensslorgenkey.The CA key and certificate enables you to create SSL keys and certificates for the Red Hat Update Appliance and the CDS, as well as sign the entitlement certificates for the clients to access the CDS instances.Note
In this section, ca.key and ca.crt are the example names for the CA key and certificate. - Create a file with the same name and in the same location as the CA certificate you have but using a
.srlextension. The file should contain the text10only. This can be performed using the following command:# echo 10 > /home/example/certs/ca.srl
- Generate the Red Hat Update Appliance Server SSL key, using the following command:
# openssl genrsa -out ssl_RHUA.key 2048
- Generate a certificate request using the
opensslcommand:# openssl req -new -key ssl_RHUA.key -out ssl_RHUA.csr
The tool will prompt you for further information, and then create an output file calledssl_RHUA.csr. - Use the CSR file to create a SSL certificate for the Red Hat Update Appliance instance with the following command:
# openssl x509 -req -days 365 -CA ca.crt -CAkey ca.key -in ssl_RHUA.csr -out ssl_RHUA.crt
In this example,ssl_RHUA.csris the file created in the previous step,ca.crtis the certificate generated by the CA,ca.keyis the CA certificate private key, andssl_RHUA.crtis the name of the certificate file that will result from running this command.
Procedure 3.2. Configuring Content Delivery Server (CDS) SSL Certificates
- Generate the CDS SSL key, using the following command:
# openssl genrsa -out ssl_cds01.key 2048
- Generate a certificate request using the
opensslcommand:# openssl req -new -key ssl_cds01.key -out ssl_cds01.csr
The tool will prompt you for further information, and then create an output file calledssl_cds01.csr.Important
When entering the hostname for.csrfile, the hostname needs to be the same hostname clients will use to access the CDS. This is also the client hostname used in Procedure 3.3 Add a CDS Instance of the Administration guide. - Use the CSR file to create SSL certificates for each CDS instance with the following command:
# openssl x509 -req -days 365 -CA ca.crt -CAkey ca.key -in ssl_cds01.csr -out ssl_cds01.crt
Note
It is recommended that you name the output files correspondent with the hostname of the CDS instance for which the request was created. For example, if the hostname for the CDS iscds01.example.com, the output files could be namedssl-cds01.key,ssl_cds01.csr, andssl_cds01.crt. This will help avoiding confusion when creating multiple CDS instances.
3.1.2. Configuring SSL Certificates Using the Automated Script
Procedure 3.3. Configuring SSL Certificates Using the Automated Script
- Generate the SSL certificates required for the Red Hat Update Infrastructure installation using the following command:
# /usr/share/rh-rhua/rhui_certs/create_rhui_ssl_certs.sh RHUA_HOSTNAME CDS1_HOSTNAME
Note
If you do not wish to encrypt the keys use the--noencryptoption.Additional hostnames can be added to the end of the command if SSL certificates are required for more than one CDS. - You will be prompted for three separate passwords. These are for the root CA, the server CA and the client CA. Enter and confirm the passwords when prompted.
Important
Use different passwords for each CA and record the passwords in a secure location.
3.2. Editing the Answers File
/etc/rhui/answers.sample to use as a basis for creating your own answers file. There is also an example answers file at Example 3.1, “Example Answers File”.
Procedure 3.4. Editing the Answers File
- Copy
/etc/rhui/answers.sampleto another location on your local machine:# cp /etc/rhui/answers.sample /etc/rhui/myanswersfile
- Open the local copy of the file in your preferred text editor. The answers file is divided into three sections: General, RHUA, and CDS Instances.
General
The General section contains all the general configuration options for Red Hat Update Infrastructure.versionRed Hat Update Infrastructure Installer needs to generate configuration RPMs. These RPMs will be given the version number2.1by default. To make the RPMs use a different version number, enter it here:[general] version: 2.1
By default, this setting will apply to all the configuration RPMs that were created using this answers file. However, it can be overridden for specific sub-sections. For example, if in the General section version is set toversion: 2.1, all the CDS RPMs will be version 2.1. Similarly, if you set Red Hat Update Appliance section version toversion: 2.5, all the Red Hat Update Appliance RPMs will be version 2.5.dest_dirEnter the full path to the location where Red Hat Update Infrastructure Installer should create the configuration RPMs. Every RPM will be located in this directory after it runs and temporary files will be located in a sub-directory.dest_dir: /tmp/rhui
Red Hat Update Appliance
The Red Hat Update Appliance section contains configuration options for the Red Hat Update Appliance (RHUA). There must be only one Red Hat Update Appliance section on the answers file.rpm_nameEnter a name for the Red Hat Update Appliance configuration RPM. This name will have the version and architecture information added to it during the creation process, so there is no need to specify them here:rpm_name: rh-rhua-config
hostnameEnter the fully qualified domain name (FQDN) of the Red Hat Update Appliance instance. This must not be an IP address, but a resolvable DNS name. Ensure that your SSL certificate has been created for this DNS name, as they must match exactly:hostname: rhua.example.com
ssl_certandssl_keyEnter the full paths to the SSL certificate and its private key. These will be used to configure Apache on the Red Hat Update Appliance instance:ssl_cert: /path/to/ssl_RHUA.crt ssl_key: /path/to/ssl_RHUA.key
ca_certEnter the full path to the certificate authority (CA) certificate:ca_cert: /path/to/ca.crt
Optional Proxy Parameters
It is possible to specify optional parameters to be used as a proxy server when the Red Hat Update Appliance attempts to access the internet (external to the cloud) and download packages from Red Hat.proxy_server_host: proxy.example.com proxy_server_port: 443 proxy_server_username: admin proxy_server_password: password
For non-authenticating proxy servers, onlyproxy_server_hostandproxy_server_portneed to be defined.Important
When specifying theproxy_server_hostparameter, ensure you do not have a trailing slash in the URL, as resolution of the address will fail. For example, useproxy.example.comnotproxy.example.com/to avoid errors.
CDS Instances
The CDS section contains configuration options for each CDS instance. Create a new section under the CDS Instances heading for each CDS instance, giving each one a unique title with acds-prefix, for example:[cds-1] -- parameters for a CDS -- [cds-2] -- parameters for a different CDS --
rpm_nameEnter a name for the CDS configuration RPM. This name will have the version and architecture information added to it during the creation process, so there is no need to specify them here:rpm_name: rh-cds1-config
hostnameEnter the fully qualified domain name (FQDN) of the CDS instance. This must not be an IP address, but a resolvable DNS name. Ensure that your SSL certificate has been created for this DNS name as they must match exactly:hostname: cds01.example.com
ssl_certandssl_keyEnter the full paths to the SSL certificate and its private key. These will be used to configure Apache on the CDS instance:ssl_cert: /path/to/ssl_cds01.crt ssl_key: /path/to/ssl_cds01.key
Note
To create a new CDS after Red Hat Update Infrastructure is deployed, refer to Section 3.3, “Adding a Content Delivery Server”.- To execute the file and create the configuration RPMs, change to root user and run the
rhui-installercommand:# rhui-installer /etc/rhui/myanswersfile
The configuration RPMs will be saved to the location you specified in Step 3.b. There will be a configuration RPM for both the Red Hat Update Appliance and the CDS instances, using the names you gave for each. - Copy the Red Hat Update Appliance configuration RPM to the Red Hat Update Appliance and install it:
# yum install /tmp/rhui/rh-rhua-config-2.1-2.el6.noarch.rpm
- Copy the CDS configuration RPM for each CDS instance (as defined by the hostname in the
[cds-1]section) and install it:# yum install /tmp/rhui/rh-cds1-config-2.1-2.el6.noarch.rpm
Example 3.1. Example Answers File
# # RHUI Installer Sample Answers File # # This sample answers file can be found at /etc/rhui/answers.sample. # # This file is meant to be used as a template for creating an answers file for use with # the RHUI Installer. Once the appropriate values have been entered, the RHUI Installer # will generate RPMs based on these values through the following call: # # $ rhui-installer --answers <path to populated answers file> # # The results of running the above call will be found in the directory specified in the # dest_dir attribute under the [general] section. # == General =============================================== # The [general] section contains configuration options that apply to the RHUI installation # as a whole. [general] # This will be used as the version for all RPMs that are created by this answers file. # Individual components may override this value with the "rpm_version" attribute. version: 2.1 # Local directory into which RHUI tools will place any temporary files as well as the # built RPMs. If this directory exists prior to running RHUI tools, the user executing # it must have write permissions. dest_dir: /tmp/rhui # == RHUA =============================================== # The [rhua] section contains attributes describing a particular RHUA instance. [rhua] # Name of the RHUA configuration RPM created by RHUI tools. rpm_name: rh-rhua-config # Fully qualified hostname of the RHUA instance. hostname: rhua.example.com # SSL certificate and private key to be installed on the RHUA. The CN of this certificate # must match the hostname listed above. ssl_cert: ssl_key: # CA certificate used to sign the RHUA's SSL certificate. This is needed by the CDS # instances when connecting back to the RHUA to synchronize content to verify the # RHUA certificate during the handshake. ca_cert: # If a proxy server is needed for the RHUA to connect to the internet, this is the hostname # of that server. If this is not specified, no proxy server will be used. # proxy_server_host: proxy.example.com # Port to access on the proxy server. This value has no effect if proxy_server_host is # not specified. # proxy_server_port: 443 # Proxy server username. Omit if the proxy server does not require authentication. # proxy_server_username: admin # Proxy server password. # proxy_server_password: password # == CDS Instances =============================================== # There should be one [cds-*] section for each CDS to be used in the RHUI infrastructure. # The name between the [ ] must begin with "cds", however the remainder is arbitrary and must # only be unique with respect to other cds sections. There will be one CDS configuration RPM # generated for each section found. [cds-1] # Name of the RPM that will be created for this CDS configuration. rpm_name: rh-cds1-config # Fully qualified name of this CDS instance. hostname: cds01.example.com # SSL certificate and private key to be used by this CDS instance. The CN of this # certificate must match the hostname listed above. ssl_cert: ssl_key: # [cds-2] # rpm_name: rh-cds2-config # hostname: cds02.example.com # ssl_cert: # ssl_key:
3.3. Adding a Content Delivery Server
Note
Procedure 3.5. Generate SSL certificate for the new CDS
- Generate the CDS SSL key, using the following command:
# openssl genrsa -out ssl_cds02.key 2048
- Generate a certificate request using the
opensslcommand:# openssl req -new -key ssl_cds02.key -out ssl_cds02.csr
The tool will prompt you for further information, and then create an output file calledssl_cds02.csr. - Use the CSR file to create a SSL certificate for the new CDS instance with the following command:
# openssl x509 -req -days 365 -CA ca.crt -CAkey ca.key -in ssl_cds02.csr -out ssl_cds02.crt
Procedure 3.6. Prepare the answers file and generate RPM for the new CDS
- Change directory to the answers file created in Procedure 3.4, “Editing the Answers File”
# cd /etc/rhui/myanswersfile
- Edit the
/etc/rhui/myanswersfileanswers file using your preferred text editor to include the correct details under[cds-2].[cds-2] rpm_name: rh-cds2-config hostname: cds02.example.com ssl_cert: ssl_cds02.crt ssl_key: ssl_cds02.key
- To execute the file and create the configuration RPMs, change to root user and run the rhui-installer command:
# rhui-installer
/etc/rhui/myanswersfile - Finally, install
/tmp/rhui/rh-cds2-config-2.1-2.el6.noarch.rpmoncds02.example.com.# yum install /tmp/rhui/rh-cds2-config-2.1-2.el6.noarch.rpm
3.4. Updating Red Hat Update Infrastructure
yum command.
Appendix A. Revision History
| Revision History | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| Revision 0-65 | Tues Mar 13 2018 | ||||||||
| |||||||||
| Revision 0-64 | Thu Mar 23 2017 | ||||||||
| |||||||||
| Revision 0-63 | Tues Sep 1 2015 | ||||||||
| |||||||||
| Revision 0-62 | Tues Aug 25 2015 | ||||||||
| |||||||||
| Revision 0-61 | Wed Aug 19 2015 | ||||||||
| |||||||||
| Revision 0-60 | Mon Aug 3 2015 | ||||||||
| |||||||||
| Revision 0-59 | Fri July 31 2015 | ||||||||
| |||||||||
| Revision 0-58 | Thu July 30 2015 | ||||||||
| |||||||||
| Revision 0-57 | Thu Mar 26 2015 | ||||||||
| |||||||||
| Revision 0-56 | Thu Mar 26 2015 | ||||||||
| |||||||||
| Revision 0-55 | Wed Mar 25 2015 | ||||||||
| |||||||||
| Revision 0-54 | Tues Dec 16 2014 | ||||||||
| |||||||||
| Revision 0-53 | Wed Dec 10 2014 | ||||||||
| |||||||||
| Revision 0-52 | Thu Feb 20 2014 | ||||||||
| |||||||||
| Revision 0-51 | Tue Jan 28 2014 | ||||||||
| |||||||||
| Revision 0-50 | Wed Jan 22 2014 | ||||||||
| |||||||||
| Revision 0-49 | Tue Jan 21 2014 | ||||||||
| |||||||||
| Revision 0-48 | Mon Dec 16 2013 | ||||||||
| |||||||||
| Revision 0-47 | Mon Apr 22 2013 | ||||||||
| |||||||||
| Revision 0-46 | Tue Apr 16 2013 | ||||||||
| |||||||||
| Revision 0-45 | Tue Mar 26 2013 | ||||||||
| |||||||||
| Revision 0-44 | Mon Mar 18 2013 | ||||||||
| |||||||||
| Revision 0-43 | Thu Feb 07 2013 | ||||||||
| |||||||||
| Revision 0-42 | Mon Oct 29 2012 | ||||||||
| |||||||||
| Revision 0-41 | Fri Oct 26 2012 | ||||||||
| |||||||||
| Revision 0-40 | Fri Oct 26 2012 | ||||||||
| |||||||||
| Revision 0-39 | Wed Oct 24 2012 | ||||||||
| |||||||||
| Revision 0-38 | Wed Sep 19 2012 | ||||||||
| |||||||||
| Revision 0-37 | Tue Aug 28 2012 | ||||||||
| |||||||||
| Revision 0-36 | Wed Aug 22 2012 | ||||||||
| |||||||||
| Revision 0-35 | Tue Aug 21 2012 | ||||||||
| |||||||||
| Revision 0-34 | Tue Aug 21 2012 | ||||||||
| |||||||||
| Revision 0-33 | Mon Aug 20 2012 | ||||||||
| |||||||||
| Revision 0-32 | Thu Aug 16 2012 | ||||||||
| |||||||||
| Revision 0-31 | Tue Aug 14 2012 | ||||||||
| |||||||||
| Revision 0-30 | Mon Aug 13 2012 | ||||||||
| |||||||||
| Revision 0-29 | Tue Aug 07 2012 | ||||||||
| |||||||||
| Revision 0-28 | Mon Aug 06 2012 | ||||||||
| |||||||||
| Revision 0-27 | Wed Jul 25 2012 | ||||||||
| |||||||||
| Revision 0-26 | Tue Jul 24 2012 | ||||||||
| |||||||||
| Revision 0-25 | Tue Jul 24 2012 | ||||||||
| |||||||||
| Revision 0-24 | Mon Jul 23 2012 | ||||||||
| |||||||||
| Revision 0-23 | Fri Jul 20 2012 | ||||||||
| |||||||||
| Revision 0-22 | Thu Jul 19 2012 | ||||||||
| |||||||||
| Revision 0-21 | Wed Jul 18 2012 | ||||||||
| |||||||||
| Revision 0-20 | Tue Jul 17 2012 | ||||||||
| |||||||||
| Revision 0-19 | Sun Jul 15 2012 | ||||||||
| |||||||||
| Revision 0-18 | Mon Jul 09 2012 | ||||||||
| |||||||||
| Revision 0-17 | Mon Jul 09 2012 | ||||||||
| |||||||||
| Revision 0-16 | Tue Jul 5 2012 | ||||||||
| |||||||||
| Revision 0-15 | Tue Jul 3 2012 | ||||||||
| |||||||||
| Revision 0-14 | Tue Jun 26 2012 | ||||||||
| |||||||||
| Revision 0-13 | Mon Jun 25 2012 | ||||||||
| |||||||||
| Revision 0-12 | Mon Jun 25 2012 | ||||||||
| |||||||||
| Revision 0-11 | Thu Jun 21 2012 | ||||||||
| |||||||||
| Revision 0-10 | Tue Jun 19 2012 | ||||||||
| |||||||||
| Revision 0-9 | Mon Jun 18 2012 | ||||||||
| |||||||||
| Revision 0-8 | Fri Jun 15 2012 | ||||||||
| |||||||||
| Revision 0-7 | Tue Jun 12 2012 | ||||||||
| |||||||||
| Revision 0-6 | Wed Jun 06 2012 | ||||||||
| |||||||||
| Revision 0-5 | Tue May 29 2012 | ||||||||
| |||||||||
| Revision 0-4 | Fri May 25 2012 | ||||||||
| |||||||||
| Revision 0-3 | Fri May 25 2012 | ||||||||
| |||||||||
| Revision 0-2 | Fri May 25 2012 | ||||||||
| |||||||||
| Revision 0-1 | Thu May 24 2012 | ||||||||
| |||||||||
Index
C
- Certificates
- X.509, Certificates
I
- installation
- hardware, Prerequisites
- SSL, Configuring SSL Certificates Manually
- storage, Prerequisites
R
- Red Hat Update Appliance
- architecture, System Overview
- Red Hat Update Infrastructure, Introduction to Red Hat Update Infrastructure (see Red Hat Update Infrastructure)
- communications, Communication
- requirements, Installation Requirements
- Red Hat Update Infrastructure Installer
- answers file, Editing the Answers File
- configuration, Editing the Answers File
- requirements, Installation Requirements
- cloud provider, Prerequisites
- firewall, Prerequisites
- network, Prerequisites
U
- Using the Red Hat Update Infrastructure Installer
- overview, Red Hat Update Infrastructure Installer