Server Developer Guide
Abstract
Chapter 1. Preface
In some of the example listings, what is meant to be displayed on one line does not fit inside the available page width. These lines have been broken up. A '\' at the end of a line means that a break has been introduced to fit in the page, with the following lines indented. So:
Let's pretend to have an extremely \ long line that \ does not fit This one is short
Let's pretend to have an extremely \
long line that \
does not fit
This one is shortIs really:
Let's pretend to have an extremely long line that does not fit This one is short
Let's pretend to have an extremely long line that does not fit
This one is shortChapter 2. Admin REST API
Red Hat build of Keycloak comes with a fully functional Admin REST API with all features provided by the Admin Console.
To invoke the API you need to obtain an access token with the appropriate permissions. The required permissions are described in the Server Administration Guide.
You can obtain a token by enabling authentication for your application using Red Hat build of Keycloak; see the Securing Applications and Services Guide. You can also use direct access grant to obtain an access token.
2.1. Examples of using CURL
2.1.1. Authenticating with a username and password
The following example assumes that you created the user admin with the password password in the master realm as shown in the Getting Started Guide tutorial.
Procedure
Obtain an access token for the user in the realm
masterwith usernameadminand passwordpassword:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteBy default this token expires in 1 minute
The result will be a JSON document.
-
Invoke the API you need by extracting the value of the
access_tokenproperty. Invoke the API by including the value in the
Authorizationheader of requests to the API.The following example shows how to get the details of the master realm:
curl \ -H "Authorization: bearer eyJhbGciOiJSUz..." \ "http://localhost:8080/admin/realms/master"
curl \ -H "Authorization: bearer eyJhbGciOiJSUz..." \ "http://localhost:8080/admin/realms/master"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.1.2. Authenticating with a service account
To authenticate against the Admin REST API using a client_id and a client_secret, perform this procedure.
Procedure
Make sure the client is configured as follows:
-
client_idis a confidential client that belongs to the realm master -
client_idhasService Accounts Enabledoption enabled client_idhas a custom "Audience" mapper-
Included Client Audience:
security-admin-console
-
Included Client Audience:
-
-
Check that
client_idhas the role 'admin' assigned in the "Service Account Roles" tab.
curl \ -d "client_id=<YOUR_CLIENT_ID>" \ -d "client_secret=<YOUR_CLIENT_SECRET>" \ -d "grant_type=client_credentials" \ "http://localhost:8080/realms/master/protocol/openid-connect/token"
curl \
-d "client_id=<YOUR_CLIENT_ID>" \
-d "client_secret=<YOUR_CLIENT_SECRET>" \
-d "grant_type=client_credentials" \
"http://localhost:8080/realms/master/protocol/openid-connect/token"2.2. Additional resources
Chapter 3. Themes
Red Hat build of Keycloak provides theme support for web pages and emails. This allows customizing the look and feel of end-user facing pages so they can be integrated with your applications.
Figure 3.1. Login page with sunrise example theme
3.1. Theme types
A theme can provide one or more types to customize different aspects of Red Hat build of Keycloak. The types available are:
- Account - Account Console
- Admin - Admin Console
- Email - Emails
- Login - Login forms
- Welcome - Welcome page
3.2. Configuring a theme
All theme types, except welcome, are configured through the Admin Console.
Procedure
- Log into the Admin Console.
- Select your realm from the drop-down box in the top left corner.
- Click Realm Settings from the menu.
Click the Themes tab.
NoteTo set the theme for the
masterAdmin Console you need to set the Admin Console theme for themasterrealm.- To see the changes to the Admin Console refresh the page.
-
Change the welcome theme by using the
spi-theme-welcome-themeoption. For example:
bin/kc.[sh|bat] start --spi-theme-welcome-theme=custom-theme
bin/kc.[sh|bat] start --spi-theme-welcome-theme=custom-themeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.3. Default themes
Red Hat build of Keycloak comes bundled with default themes in the JAR file keycloak-themes-26.0.17.redhat-00001.jar inside the server distribution. The server’s root themes directory does not contain any themes by default, but it contains a README file with some additional details about the default themes. To simplify upgrading, do not edit the bundled themes directly. Instead create your own theme that extends one of the bundled themes.
3.4. Creating a theme
A theme consists of:
- HTML templates (Freemarker Templates)
- Images
- Message bundles
- Stylesheets
- Scripts
- Theme properties
Unless you plan to replace every single page you should extend another theme. Most likely you will want to extend some existing theme. Alternatively, if you intend to provide your own implementation of the admin or account console, consider extending the base theme. The base theme consists of a message bundle and therefore such implementation needs to start from scratch, including implementation of the main index.ftl Freemarker template, but it can leverage existing translations from the message bundle.
When extending a theme you can override individual resources (templates, stylesheets, etc.). If you decide to override HTML templates bear in mind that you may need to update your custom template when upgrading to a new release.
While creating a theme it’s a good idea to disable caching as this makes it possible to edit theme resources directly from the themes directory without restarting Red Hat build of Keycloak.
Procedure
Run Keycloak with the following options:
bin/kc.[sh|bat] start --spi-theme-static-max-age=-1 --spi-theme-cache-themes=false --spi-theme-cache-templates=false
bin/kc.[sh|bat] start --spi-theme-static-max-age=-1 --spi-theme-cache-themes=false --spi-theme-cache-templates=falseCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a directory in the
themesdirectory.The name of the directory becomes the name of the theme. For example to create a theme called
mythemecreate the directorythemes/mytheme.Inside the theme directory, create a directory for each of the types your theme is going to provide.
For example, to add the login type to the
mythemetheme, create the directorythemes/mytheme/login.For each type create a file
theme.propertieswhich allows setting some configuration for the theme.For example, to configure the theme
themes/mytheme/loginto extend thebasetheme and import some common resources, create the filethemes/mytheme/login/theme.propertieswith following contents:parent=base import=common/keycloak
parent=base import=common/keycloakCopy to Clipboard Copied! Toggle word wrap Toggle overflow You have now created a theme with support for the login type.
- Log into the Admin Console to check out your new theme
- Select your realm
- Click Realm Settings from the menu.
- Click on the Themes tab.
- For Login Theme select mytheme and click Save.
Open the login page for the realm.
You can do this either by logging in through your application or by opening the Account Console (
/realms/{realm name}/account).-
To see the effect of changing the parent theme, set
parent=keycloakintheme.propertiesand refresh the login page.
Be sure to re-enable caching in production as it will significantly impact performance.
If you want to manually delete the content of the themes cache, you can do so by deleting the data/tmp/kc-gzip-cache directory of the server distribution. It can be useful for instance if you redeployed custom providers or custom themes without disabling themes caching in the previous server executions.
3.4.1. Theme properties
Theme properties are set in the file <THEME TYPE>/theme.properties in the theme directory.
- parent - Parent theme to extend
- import - Import resources from another theme
-
common - Override the common resource path. The default value is
common/keycloakwhen not specified. This value would be used as value of suffix of${url.resourcesCommonPath}, which is used typically in freemarker templates (prefix of${url.resoucesCommonPath}value is theme root uri). - styles - Space-separated list of styles to include
- locales - Comma-separated list of supported locales
There are a list of properties that can be used to change the css class used for certain element types. For a list of these properties look at the theme.properties file in the corresponding type of the keycloak theme (themes/keycloak/<THEME TYPE>/theme.properties).
You can also add your own custom properties and use them from custom templates.
When doing so, you can substitute system properties or environment variables by using these formats:
-
${some.system.property}- for system properties -
${env.ENV_VAR}- for environment variables.
A default value can also be provided in case the system property or the environment variable is not found with ${foo:defaultValue}.
If no default value is provided and there’s no corresponding system property or environment variable, then nothing is replaced and you end up with the format in your template.
Here’s an example of what is possible:
javaVersion=${java.version}
unixHome=${env.HOME:Unix home not found}
windowsHome=${env.HOMEPATH:Windows home not found}
javaVersion=${java.version}
unixHome=${env.HOME:Unix home not found}
windowsHome=${env.HOMEPATH:Windows home not found}3.4.2. Add a stylesheet to a theme
You can add one or more stylesheets to a theme.
Procedure
-
Create a file in the
<THEME TYPE>/resources/cssdirectory of your theme. Add this file to the
stylesproperty intheme.properties.For example, to add
styles.cssto themytheme, createthemes/mytheme/login/resources/css/styles.csswith the following content:.login-pf body { background: DimGrey none; }.login-pf body { background: DimGrey none; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit
themes/mytheme/login/theme.propertiesand add:styles=css/styles.css
styles=css/styles.cssCopy to Clipboard Copied! Toggle word wrap Toggle overflow To see the changes, open the login page for your realm.
You will notice that the only styles being applied are those from your custom stylesheet.
To include the styles from the parent theme, load the styles from that theme. Edit
themes/mytheme/login/theme.propertiesand changestylesto:styles=css/login.css css/styles.css
styles=css/login.css css/styles.cssCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteTo override styles from the parent stylesheets, ensure that your stylesheet is listed last.
3.4.3. Adding a script to a theme
You can add one or more scripts to a theme.
Procedure
-
Create a file in the
<THEME TYPE>/resources/jsdirectory of your theme. Add the file to the
scriptsproperty intheme.properties.For example, to add
script.jsto themytheme, createthemes/mytheme/login/resources/js/script.jswith the following content:alert('Hello');alert('Hello');Copy to Clipboard Copied! Toggle word wrap Toggle overflow Then edit
themes/mytheme/login/theme.propertiesand add:scripts=js/script.js
scripts=js/script.jsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.4.4. Adding an image to a theme
To make images available to the theme add them to the <THEME TYPE>/resources/img directory of your theme. These can be used from within stylesheets or directly in HTML templates.
For example to add an image to the mytheme copy an image to themes/mytheme/login/resources/img/image.jpg.
You can then use this image from within a custom stylesheet with:
body {
background-image: url('../img/image.jpg');
background-size: cover;
}
body {
background-image: url('../img/image.jpg');
background-size: cover;
}Or to use directly in HTML templates add the following to a custom HTML template:
<img src="${url.resourcesPath}/img/image.jpg" alt="My image description">
<img src="${url.resourcesPath}/img/image.jpg" alt="My image description">3.4.6. Adding an image to an email theme
To make images available to the theme add them to the <THEME TYPE>/email/resources/img directory of your theme. These can be used from within directly in HTML templates.
For example to add an image to the mytheme copy an image to themes/mytheme/email/resources/img/logo.jpg.
To use directly in HTML templates add the following to a custom HTML template:
<img src="${url.resourcesUrl}/img/image.jpg" alt="My image description">
<img src="${url.resourcesUrl}/img/image.jpg" alt="My image description">3.4.7. Messages
Text in the templates is loaded from message bundles. A theme that extends another theme will inherit all messages from the parent’s message bundle and you can override individual messages by adding <THEME TYPE>/messages/messages_en.properties to your theme.
For example to replace Username on the login form with Your Username for the mytheme create the file themes/mytheme/login/messages/messages_en.properties with the following content:
usernameOrEmail=Your Username
usernameOrEmail=Your Username
Within a message values like {0} and {1} are replaced with arguments when the message is used. For example {0} in Log in to {0} is replaced with the name of the realm.
Texts of these message bundles can be overwritten by realm-specific values. The realm-specific values are manageable via UI and API.
3.4.8. Adding a language to a realm
Prerequisites
- To enable internationalization for a realm, see the Server Administration Guide.
Procedure
-
Create the file
<THEME TYPE>/messages/messages_<LOCALE>.propertiesin the directory of your theme. Add this file to the
localesproperty in<THEME TYPE>/theme.properties. For a language to be available to users the realmslogin,accountandemail, the theme has to support the language, so you need to add your language for those theme types.For example, to add Norwegian translations to the
mythemetheme create the filethemes/mytheme/login/messages/messages_no.propertieswith the following content:usernameOrEmail=Brukernavn password=Passord
usernameOrEmail=Brukernavn password=PassordCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you omit a translation for messages, they will use English.
Edit
themes/mytheme/login/theme.propertiesand add:locales=en,no
locales=en,noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Add the same for the
accountandemailtheme types. To do this createthemes/mytheme/account/messages/messages_no.propertiesandthemes/mytheme/email/messages/messages_no.properties. Leaving these files empty will result in the English messages being used. -
Copy
themes/mytheme/login/theme.propertiestothemes/mytheme/account/theme.propertiesandthemes/mytheme/email/theme.properties. Add a translation for the language selector. This is done by adding a message to the English translation. To do this add the following to
themes/mytheme/account/messages/messages_en.propertiesandthemes/mytheme/login/messages/messages_en.properties:locale_no=Norsk
locale_no=NorskCopy to Clipboard Copied! Toggle word wrap Toggle overflow
By default, message properties files should be encoded using UTF-8. Keycloak falls back to ISO-8859-1 handling if it can’t read the contents as UTF-8. Unicode characters can be escaped as described in Java’s documentation for PropertyResourceBundle. Previous versions of Keycloak supported specifying the encoding in the first line with a comment like # encoding: UTF-8, which is no longer supported.
3.4.9. Adding custom Identity Providers icons
Red Hat build of Keycloak supports adding icons for custom Identity providers, which are displayed on the login screen.
Procedure
-
Define icon classes in your login
theme.propertiesfile (for example,themes/mytheme/login/theme.properties) with key patternkcLogoIdP-<alias>. For an Identity Provider with an alias
myProvider, you may add a line totheme.propertiesfile of your custom theme. For example:kcLogoIdP-myProvider = fa fa-lock
kcLogoIdP-myProvider = fa fa-lockCopy to Clipboard Copied! Toggle word wrap Toggle overflow
All icons are available on the official website of PatternFly4. Icons for social providers are already defined in base login theme properties (themes/keycloak/login/theme.properties), where you can inspire yourself.
3.4.10. Creating a custom HTML template
Red Hat build of Keycloak uses Apache Freemarker templates to generate HTML and render pages.
Although it is possible to create custom templates to change completely how pages are rendered, the recommendation is to leverage the built-in templates as much as possible. The reasons are:
- During upgrades, you might be forced to update your custom templates to get the latest updates from newer versions
- Configuring CSS styles to your themes allows you to adapt the UI to match your UI design standards and guidelines.
- User Profile allows you to support custom user attributes and configure how they are rendered.
In most cases, you won’t need to change templates to adapt Red Hat build of Keycloak to your needs, but you can override individual templates in your own theme by creating <THEME TYPE>/<TEMPLATE>.ftl. Admin and account console use a single template index.ftl for rendering the application.
For a list of templates in other theme types look at the theme/base/<THEME_TYPE> directory in the JAR file at $KEYCLOAK_HOME/lib/lib/main/org.keycloak.keycloak-themes-<VERSION>.jar.
Procedure
- Copy the template from the base theme to your own theme.
Apply the modifications you need.
For example, to create a custom login form for the
mythemetheme, copythemes/base/login/login.ftltothemes/mytheme/loginand open it in an editor.After the first line (<#import …>), add
<h1>HELLO WORLD!</h1>as shown here:<#import "template.ftl" as layout> <h1>HELLO WORLD!</h1> ...
<#import "template.ftl" as layout> <h1>HELLO WORLD!</h1> ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Back up the modified template. When upgrading to a new version of Red Hat build of Keycloak you may need to update your custom templates to apply changes to the original template if applicable.
3.4.11. Emails
To edit the subject and contents for emails, for example password recovery email, add a message bundle to the email type of your theme. There are three messages for each email. One for the subject, one for the plain text body and one for the html body.
To see all emails available take a look at themes/base/email/messages/messages_en.properties.
For example to change the password recovery email for the mytheme theme create themes/mytheme/email/messages/messages_en.properties with the following content:
passwordResetSubject=My password recovery
passwordResetBody=Reset password link: {0}
passwordResetBodyHtml=<a href="{0}">Reset password</a>
passwordResetSubject=My password recovery
passwordResetBody=Reset password link: {0}
passwordResetBodyHtml=<a href="{0}">Reset password</a>3.5. Deploying themes
Themes can be deployed to Red Hat build of Keycloak by copying the theme directory to themes or it can be deployed as an archive. During development you can copy the theme to the themes directory, but in production you may want to consider using an archive. An archive makes it simpler to have a versioned copy of the theme, especially when you have multiple instances of Red Hat build of Keycloak for example with clustering.
Procedure
- To deploy a theme as an archive, create a JAR archive with the theme resources.
Add a file
META-INF/keycloak-themes.jsonto the archive that lists the available themes in the archive as well as what types each theme provides.For example for the
mythemetheme createmytheme.jarwith the contents:- META-INF/keycloak-themes.json
- theme/mytheme/login/theme.properties
- theme/mytheme/login/login.ftl
- theme/mytheme/login/resources/css/styles.css
- theme/mytheme/login/resources/img/image.png
- theme/mytheme/login/messages/messages_en.properties
theme/mytheme/email/messages/messages_en.properties
The contents of
META-INF/keycloak-themes.jsonin this case would be:Copy to Clipboard Copied! Toggle word wrap Toggle overflow A single archive can contain multiple themes and each theme can support one or more types.
To deploy the archive to Red Hat build of Keycloak, add it to the providers/ directory of Red Hat build of Keycloak and restart the server if it is already running.
Chapter 4. Themes based on React
The admin console and account console are based on React. To fully customize these you can use the React based npm packages. There are two packages:
-
@keycloak/keycloak-admin-ui: This is the base theme for the admin console. -
@keycloak/keycloak-account-ui: This is the base theme for the account console.
Both packages are available on npm.
4.1. Installing the packages
To install the packages, run the following command:
pnpm install @keycloak/keycloak-account-ui
pnpm install @keycloak/keycloak-account-ui4.2. Using the packages
To use these pages you’ll need to add KeycloakProvider in your component hierarchy to setup what client, realm and url to use.
4.3. Translating the pages
The pages are translated using the i18next library. You can set it up as described on their [website](https://react.i18next.com/). If you want to use the translations that are provided then you need to add i18next-http-backend to your project and add:
4.4. Using the pages
All "pages" are React components that can be used in your application. To see what components are available, see the [source](https://github.com/keycloak/keycloak/blob/main/js/apps/account-ui/src/index.ts). Or have a look at the [quick start](https://github.com/keycloak/keycloak-quickstarts/tree/main/extension/extend-admin-console-node) to see how to use them.
4.5. Theme selector
By default the theme configured for the realm is used, with the exception of clients being able to override the login theme. This behavior can be changed through the Theme Selector SPI.
This could be used to select different themes for desktop and mobile devices by looking at the user agent header, for example.
To create a custom theme selector you need to implement ThemeSelectorProviderFactory and ThemeSelectorProvider.
4.6. Theme resources
When implementing custom providers in Red Hat build of Keycloak there may often be a need to add additional templates, resources and messages bundles.
The easiest way to load additional theme resources is to create a JAR with templates in theme-resources/templates resources in theme-resources/resources and messages bundles in theme-resources/messages.
If you want a more flexible way to load templates and resources that can be achieved through the ThemeResourceSPI. By implementing ThemeResourceProviderFactory and ThemeResourceProvider you can decide exactly how to load templates and resources.
4.7. Locale selector
By default, the locale is selected using the DefaultLocaleSelectorProvider which implements the LocaleSelectorProvider interface. English is the default language when internationalization is disabled.
With internationalization enabled, the locale is resolved according to the logic described in the Server Administration Guide.
This behavior can be changed through the LocaleSelectorSPI by implementing the LocaleSelectorProvider and LocaleSelectorProviderFactory.
The LocaleSelectorProvider interface has a single method, resolveLocale, which must return a locale given a RealmModel and a nullable UserModel. The actual request is available from the KeycloakSession#getContext method.
Custom implementations can extend the DefaultLocaleSelectorProvider in order to reuse parts of the default behavior. For example to ignore the Accept-Language request header, a custom implementation could extend the default provider, override it’s getAcceptLanguageHeaderLocale, and return a null value. As a result the locale selection will fall back on the realm’s default language.
Chapter 5. Identity Brokering APIs
Red Hat build of Keycloak can delegate authentication to a parent IDP for login. A typical example of this is the case where you want users to be able to log in through a social provider such as Facebook or Google. You can also link existing accounts to a brokered IDP. This section describes some APIs that your applications can use as it pertains to identity brokering.
5.1. Retrieving external IDP tokens
Red Hat build of Keycloak allows you to store tokens and responses from the authentication process with the external IDP. For that, you can use the Store Token configuration option on the IDP’s settings page.
Application code can retrieve these tokens and responses to pull in extra user information, or to securely invoke requests on the external IDP. For example, an application might want to use the Google token to invoke on other Google services and REST APIs. To retrieve a token for a particular identity provider you need to send a request as follows:
GET /realms/{realm}/broker/{provider_alias}/token HTTP/1.1
Host: localhost:8080
Authorization: Bearer <KEYCLOAK ACCESS TOKEN>
GET /realms/{realm}/broker/{provider_alias}/token HTTP/1.1
Host: localhost:8080
Authorization: Bearer <KEYCLOAK ACCESS TOKEN>
An application must have authenticated with Red Hat build of Keycloak and have received an access token. This access token will need to have the broker client-level role read-token set. This means that the user must have a role mapping for this role and the client application must have that role within its scope. In this case, given that you are accessing a protected service in Red Hat build of Keycloak, you need to send the access token issued by Red Hat build of Keycloak during the user authentication. In the broker configuration page you can automatically assign this role to newly imported users by turning on the Stored Tokens Readable switch.
These external tokens can be re-established by either logging in again through the provider, or using the client initiated account linking API.
5.2. Client initiated account linking
Some applications want to integrate with social providers like Facebook, but do not want to provide an option to login via these social providers. Red Hat build of Keycloak offers a browser-based API that applications can use to link an existing user account to a specific external IDP. This is called client-initiated account linking. Account linking can only be initiated by OIDC applications.
The way it works is that the application forwards the user’s browser to a URL on the Red Hat build of Keycloak server requesting that it wants to link the user’s account to a specific external provider (i.e. Facebook). The server initiates a login with the external provider. The browser logs in at the external provider and is redirected back to the server. The server establishes the link and redirects back to the application with a confirmation.
There are some preconditions that must be met by the client application before it can initiate this protocol:
- The desired identity provider must be configured and enabled for the user’s realm in the admin console.
- The user account must already be logged in as an existing user via the OIDC protocol
-
The user must have an
account.manage-accountoraccount.manage-account-linksrole mapping. - The application must be granted the scope for those roles within its access token
- The application must have access to its access token as it needs information within it to generate the redirect URL.
To initiate the login, the application must fabricate a URL and redirect the user’s browser to this URL. The URL looks like this:
/{auth-server-root}/realms/{realm}/broker/{provider}/link?client_id={id}&redirect_uri={uri}&nonce={nonce}&hash={hash}
/{auth-server-root}/realms/{realm}/broker/{provider}/link?client_id={id}&redirect_uri={uri}&nonce={nonce}&hash={hash}Here’s a description of each path and query param:
- provider
-
This is the provider alias of the external IDP that you defined in the
Identity Providersection of the admin console. - client_id
- This is the OIDC client id of your application. When you registered the application as a client in the admin console, you had to specify this client id.
- redirect_uri
- This is the application callback URL you want to redirect to after the account link is established. It must be a valid client redirect URI pattern. In other words, it must match one of the valid URL patterns you defined when you registered the client in the admin console.
- nonce
- This is a random string that your application must generate
- hash
-
This is a Base64 URL encoded hash. This hash is generated by Base64 URL encoding a SHA_256 hash of
nonce+token.getSessionState()+token.getIssuedFor()+provider. The token variable are obtained from the OIDC access token. Basically you are hashing the random nonce, the user session id, the client id, and the identity provider alias you want to access.
Here’s an example of Java Servlet code that generates the URL to establish the account link.
Why is this hash included? We do this so that the auth server is guaranteed to know that the client application initiated the request and no other rogue app just randomly asked for a user account to be linked to a specific provider. The auth server will first check to see if the user is logged in by checking the SSO cookie set at login. It will then try to regenerate the hash based on the current login and match it up to the hash sent by the application.
After the account has been linked, the auth server will redirect back to the redirect_uri. If there is a problem servicing the link request, the auth server may or may not redirect back to the redirect_uri. The browser may just end up at an error page instead of being redirected back to the application. If there is an error condition and the auth server deems it safe enough to redirect back to the client app, an additional error query parameter will be appended to the redirect_uri.
While this API guarantees that the application initiated the request, it does not completely prevent CSRF attacks for this operation. The application is still responsible for guarding against CSRF attacks target at itself.
5.2.1. Refreshing external tokens
If you are using the external token generated by logging into the provider (i.e. a Facebook or GitHub token), you can refresh this token by re-initiating the account linking API.
Chapter 6. Service Provider Interfaces (SPI)
Red Hat build of Keycloak is designed to cover most use-cases without requiring custom code, but we also want it to be customizable. To achieve this Red Hat build of Keycloak has a number of Service Provider Interfaces (SPI) for which you can implement your own providers.
6.1. Implementing an SPI
To implement an SPI you need to implement its ProviderFactory and Provider interfaces. You also need to create a service configuration file.
For example, to implement the Theme Selector SPI you need to implement ThemeSelectorProviderFactory and ThemeSelectorProvider and also provide the file META-INF/services/org.keycloak.theme.ThemeSelectorProviderFactory.
Example ThemeSelectorProviderFactory:
It is recommended that your provider factory implementation returns unique id by method getId(). However there can be some exceptions to this rule as mentioned below in the Overriding providers section.
Red Hat build of Keycloak creates a single instance of provider factories which makes it possible to store state for multiple requests. Provider instances are created by calling create on the factory for each request so these should be light-weight object.
Example ThemeSelectorProvider:
Example service configuration file (META-INF/services/org.keycloak.theme.ThemeSelectorProviderFactory):
org.acme.provider.MyThemeSelectorProviderFactory
org.acme.provider.MyThemeSelectorProviderFactoryTo configure your provider, see the Configuring Providers chapter.
For example, to configure a provider you can set options as follows:
bin/kc.[sh|bat] --spi-theme-selector-my-theme-selector-enabled=true --spi-theme-selector-my-theme-selector-theme=my-theme
bin/kc.[sh|bat] --spi-theme-selector-my-theme-selector-enabled=true --spi-theme-selector-my-theme-selector-theme=my-theme
Then you can retrieve the config in the ProviderFactory init method:
public void init(Config.Scope config) {
String themeName = config.get("theme");
}
public void init(Config.Scope config) {
String themeName = config.get("theme");
}Your provider can also look up other providers if needed. For example:
The pom.xml file for your SPI requires a dependencyManagement section with an import reference to the Red Hat build of Keycloak version that is intended for the SPI. In this example, replace the occurrence of VERSION with 26.0.17.redhat-00001, which is the current version of Red Hat build of Keycloak.
<.> Replace VERSION with the current version of Red Hat build of Keycloak
6.1.1. Override built-in providers
As mentioned above, it is recommended that your ProviderFactory implementations use unique ID. However at the same time, it can be useful to override one of the Red Hat build of Keycloak built-in providers. The recommended way for this is still ProviderFactory implementation with unique ID and then for instance set the default provider as specified in the Configuring Providers chapter. On the other hand, this may not be always possible.
For instance when you need some customizations to default OpenID Connect protocol behaviour and you want to override default Red Hat build of Keycloak implementation of OIDCLoginProtocolFactory you need to preserve same providerId. As for example admin console, OIDC protocol well-known endpoint and various other things rely on the ID of the protocol factory being openid-connect.
For this case, it is highly recommended to implement method order() of your custom implementation and make sure that it has higher order than the built-in implementation.
In case of multiple implementations with same provider ID, only the one with highest order will be used by Red Hat build of Keycloak runtime.
6.1.2. Show info from your SPI implementation in the Admin Console
Sometimes it is useful to show additional info about your Provider to a Red Hat build of Keycloak administrator. You can show provider build time information (for example, version of custom provider currently installed), current configuration of the provider (e.g. url of remote system your provider talks to) or some operational info (average time of response from remote system your provider talks to). Red Hat build of Keycloak Admin Console provides Server Info page to show this kind of information.
To show info from your provider it is enough to implement org.keycloak.provider.ServerInfoAwareProviderFactory interface in your ProviderFactory.
Example implementation for MyThemeSelectorProviderFactory from previous example:
6.2. Use available providers
In your provider implementation, you can use other providers available in Red Hat build of Keycloak. The existing providers can be typically retrieved with the usage of the KeycloakSession, which is available to your provider as described in the section Implementing an SPI.
Red Hat build of Keycloak has two provider types:
Single-implementation provider types - There can be only a single active implementation of the particular provider type in Red Hat build of Keycloak runtime.
For example
HostnameProviderspecifies the hostname to be used by Red Hat build of Keycloak and that is shared for the whole Red Hat build of Keycloak server. Hence there can be only single implementation of this provider active for the Red Hat build of Keycloak server. If there are multiple provider implementations available to the server runtime, one of them needs to be specified as the default one.
For example such as:
bin/kc.[sh|bat] build --spi-hostname-provider=default
bin/kc.[sh|bat] build --spi-hostname-provider=default
The value default used as the value of default-provider must match the ID returned by the ProviderFactory.getId() of the particular provider factory implementation. In the code, you can obtain the provider such as keycloakSession.getProvider(HostnameProvider.class)
Multiple implementation provider types - Those are provider types, that allow multiple implementations available and working together in the Red Hat build of Keycloak runtime.
For example
EventListenerprovider allows to have multiple implementations available and registered, which means that particular event can be sent to all the listeners (jboss-logging, sysout etc). In the code, you can obtain a specified instance of the provider for example such assession.getProvider(EventListener.class, "jboss-logging"). You need to specifyprovider_idof the provider as the second argument as there can be multiple instances of this provider type as described above.The provider ID must match the ID returned by the
ProviderFactory.getId()of the particular provider factory implementation. Some provider types can be retrieved with the usage ofComponentModelas the second argument and some (for exampleAuthenticator) even need to be retrieved with the usage ofKeycloakSessionFactory. It is not recommended to implement your own providers this way as it may be deprecated in the future.
6.3. Registering provider implementations
Providers are registered with the server by simply copying the JAR file to the providers directory.
If your provider needs additional dependencies not already provided by Keycloak copy these to the providers directory.
After registering new providers or dependencies Keycloak needs to be re-built with a non-optimized start or the kc.[sh|bat] build command.
Provider JARs are not loaded in isolated classloaders, so do not include resources or classes in your provider JARs that conflict with built-in resources or classes. In particular the inclusion of an application.properties file or overriding the commons-lang3 dependency will cause auto-build to fail if the provider JAR is removed. If you have included conflicting classes, you may see a split package warning in the start log for the server. Unfortunately not all built-in lib jars are checked by the split package warning logic, so you’ll need to check the lib directory JARs before bundling or including a transitive dependency. Should there be a conflict, that can be resolved by removing or repackaging the offending classes.
There is no warning if you have conflicting resource files. You should either ensure that your JAR’s resource files have path names that contain something unique to that provider, or you can check for the existence of some.file in the JAR contents under the "install root"/lib/lib/main directory with something like:
find . -type f -name "*.jar" -exec unzip -l {} \; | grep some.file
find . -type f -name "*.jar" -exec unzip -l {} \; | grep some.file
If you find that your server will not start due to a NoSuchFileException error related to a removed provider JAR, then run:
./kc.sh -Dquarkus.launch.rebuild=true --help
./kc.sh -Dquarkus.launch.rebuild=true --helpThis will force Quarkus to rebuild the classloading related index files. From there you should be able to perform a non-optimized start or build without an exception.
6.3.1. Disabling a provider
You can disable a provider by setting the enabled attribute for the provider to false. For example to disable the Infinispan user cache provider use:
bin/kc.[sh|bat] build --spi-user-cache-infinispan-enabled=false
bin/kc.[sh|bat] build --spi-user-cache-infinispan-enabled=false6.4. JavaScript providers
Scripts is Technology Preview and is not fully supported. This feature is disabled by default.
To enable start the server with --features=preview or --features=scripts
Red Hat build of Keycloak has the ability to execute scripts during runtime in order to allow administrators to customize specific functionalities:
- Authenticator
- JavaScript Policy
- OpenID Connect Protocol Mapper
- SAML Protocol Mapper
6.4.1. Authenticator
Authentication scripts must provide at least one of the following functions: authenticate(..), which is called from Authenticator#authenticate(AuthenticationFlowContext)action(..), which is called from Authenticator#action(AuthenticationFlowContext)
Custom Authenticator should at least provide the authenticate(..) function. You can use the javax.script.Bindings script within the code.
script-
the
ScriptModelto access script metadata realm-
the
RealmModel user-
the current
UserModel. Note thatuseris available when your script authenticator is configured in the authentication flow in a way that is triggered after another authenticator succeeded in establishing user identity and set the user into the authentication session. session-
the active
KeycloakSession authenticationSession-
the current
AuthenticationSessionModel httpRequest-
the current
org.jboss.resteasy.spi.HttpRequest LOG-
a
org.jboss.logging.Loggerscoped toScriptBasedAuthenticator
You can extract additional context information from the context argument passed to the authenticate(context) action(context) function.
6.4.1.1. Where to add script authenticator
A possible use of script authenticator is to do some checks at the end of the authentication. Note that if you want your script authenticator to be always triggered (even for instance during SSO re-authentication with the identity cookie), you may need to add it as REQUIRED at the end of the authentication flow and encapsulate the existing authenticators into a separate REQUIRED authentication subflow. This need is because the REQUIRED and ALTERNATIVE executions should not be at the same level. For example, the authentication flow configuration should appear as follows:
- User-authentication-subflow REQUIRED -- Cookie ALTERNATIVE -- Identity-provider-redirect ALTERNATIVE ... - Your-Script-Authenticator REQUIRED
- User-authentication-subflow REQUIRED
-- Cookie ALTERNATIVE
-- Identity-provider-redirect ALTERNATIVE
...
- Your-Script-Authenticator REQUIRED6.4.2. OpenID Connect Protocol Mapper
OpenID Connect Protocol Mapper scripts are javascript script that allow you to change the content of the ID Token and/or the Access Token.
You can use the javax.script.Bindings script within the code.
user-
the current
UserModel realm-
the
RealmModel token-
the current
IDToken. It is available only if the mapper is configured for the ID token. tokenResponse-
the current
AccessTokenResponse. It is available only if the mapper is configured for the Access token. userSession-
the active
UserSessionModel keycloakSession-
the active
KeycloakSession
The exports of the script will be used as the value of the token claim.
The above script allows to retrieve a user_input from the authorization request. This will be available to map in the Token Claim Name configured in the mapper.
6.4.3. Create a JAR with the scripts to deploy
JAR files are regular ZIP files with a .jar extension.
In order to make your scripts available to Red Hat build of Keycloak you need to deploy them to the server. For that, you should create a JAR file with the following structure:
META-INF/keycloak-scripts.json my-script-authenticator.js my-script-policy.js my-script-mapper.js
META-INF/keycloak-scripts.json
my-script-authenticator.js
my-script-policy.js
my-script-mapper.js
The META-INF/keycloak-scripts.json is a file descriptor that provides metadata information about the scripts you want to deploy. It is a JSON file with the following structure:
This file should reference the different types of script providers that you want to deploy:
authenticatorsFor OpenID Connect Script Authenticators. You can have one or multiple authenticators in the same JAR file
policiesFor JavaScript Policies when using Red Hat build of Keycloak Authorization Services. You can have one or multiple policies in the same JAR file
mappersFor OpenID Connect Script Protocol Mappers. You can have one or multiple mappers in the same JAR file
saml-mappersFor SAML Script Protocol Mappers. You can have one or multiple mappers in the same JAR file
For each script file in your JAR file, you need a corresponding entry in META-INF/keycloak-scripts.json that maps your scripts files to a specific provider type. For that you should provide the following properties for each entry:
nameA friendly name that will be used to show the scripts through the Red Hat build of Keycloak Administration Console. If not provided, the name of the script file will be used instead
descriptionAn optional text that better describes the intend of the script file
fileNameThe name of the script file. This property is mandatory and should map to a file within the JAR.
6.4.4. Deploy the script JAR
Once you have a JAR file with a descriptor and the scripts you want to deploy, you just need to copy the JAR to the Red Hat build of Keycloak providers/ directory, then run bin/kc.[sh|bat] build.
6.5. Available SPIs
If you want to see list of all available SPIs at runtime, you can check Server Info page in Admin Console as described in Admin Console section.
Chapter 7. User Storage SPI
You can use the User Storage SPI to write extensions to Red Hat build of Keycloak to connect to external user databases and credential stores. The built-in LDAP and ActiveDirectory support is an implementation of this SPI in action. Out of the box, Red Hat build of Keycloak uses its local database to create, update, and look up users and validate credentials. Often though, organizations have existing external proprietary user databases that they cannot migrate to Red Hat build of Keycloak’s data model. For those situations, application developers can write implementations of the User Storage SPI to bridge the external user store and the internal user object model that Red Hat build of Keycloak uses to log in users and manage them.
When the Red Hat build of Keycloak runtime needs to look up a user, such as when a user is logging in, it performs a number of steps to locate the user. It first looks to see if the user is in the user cache; if the user is found it uses that in-memory representation. Then it looks for the user within the Red Hat build of Keycloak local database. If the user is not found, it then loops through User Storage SPI provider implementations to perform the user query until one of them returns the user the runtime is looking for. The provider queries the external user store for the user and maps the external data representation of the user to Red Hat build of Keycloak’s user metamodel.
User Storage SPI provider implementations can also perform complex criteria queries, perform CRUD operations on users, validate and manage credentials, or perform bulk updates of many users at once. It depends on the capabilities of the external store.
User Storage SPI provider implementations are packaged and deployed similarly to (and often are) Jakarta EE components. They are not enabled by default, but instead must be enabled and configured per realm under the User Federation tab in the administration console.
If your user provider implementation is using some user attributes as the metadata attributes for linking/establishing the user identity, then please make sure that users are not able to edit the attributes and the corresponding attributes are read-only. The example is the LDAP_ID attribute, which the built-in Red Hat build of Keycloak LDAP provider is using for to store the ID of the user on the LDAP server side. See the details in the Threat model mitigation chapter.
There are two sample projects in Red Hat build of Keycloak Quickstarts Repository. Each quickstart has a README file with instructions on how to build, deploy, and test the sample project. The following table provides a brief description of the available User Storage SPI quickstarts:
| Name | Description |
|---|---|
| Demonstrates implementing a user storage provider using JPA. | |
| Demonstrates implementing a user storage provider using a simple properties file that contains username/password key pairs. |
7.1. Provider interfaces
When building an implementation of the User Storage SPI you have to define a provider class and a provider factory. Provider class instances are created per transaction by provider factories. Provider classes do all the heavy lifting of user lookup and other user operations. They must implement the org.keycloak.storage.UserStorageProvider interface.
You may be thinking that the UserStorageProvider interface is pretty sparse? You’ll see later in this chapter that there are other mix-in interfaces your provider class may implement to support the meat of user integration.
UserStorageProvider instances are created once per transaction. When the transaction is complete, the UserStorageProvider.close() method is invoked and the instance is then garbage collected. Instances are created by provider factories. Provider factories implement the org.keycloak.storage.UserStorageProviderFactory interface.
Provider factory classes must specify the concrete provider class as a template parameter when implementing the UserStorageProviderFactory. This is a must as the runtime will introspect this class to scan for its capabilities (the other interfaces it implements). So for example, if your provider class is named FileProvider, then the factory class should look like this:
The getId() method returns the name of the User Storage provider. This id will be displayed in the admin console’s User Federation page when you want to enable the provider for a specific realm.
The create() method is responsible for allocating an instance of the provider class. It takes a org.keycloak.models.KeycloakSession parameter. This object can be used to look up other information and metadata as well as provide access to various other components within the runtime. The ComponentModel parameter represents how the provider was enabled and configured within a specific realm. It contains the instance id of the enabled provider as well as any configuration you may have specified for it when you enabled through the admin console.
The UserStorageProviderFactory has other capabilities as well which we will go over later in this chapter.
7.2. Provider capability interfaces
If you have examined the UserStorageProvider interface closely you might notice that it does not define any methods for locating or managing users. These methods are actually defined in other capability interfaces depending on what scope of capabilities your external user store can provide and execute on. For example, some external stores are read-only and can only do simple queries and credential validation. You will only be required to implement the capability interfaces for the features you are able to. You can implement these interfaces:
| SPI | Description |
|---|---|
|
| This interface is required if you want to be able to log in with users from this external store. Most (all?) providers implement this interface. |
|
| Defines complex queries that are used to locate one or more users. You must implement this interface if you want to view and manage users from the administration console. |
|
| Implement this interface if your provider supports count queries. |
|
|
This interface is combined capability of |
|
| Implement this interface if your provider supports adding and removing users. |
|
| Implement this interface if your provider supports bulk update of a set of users. |
|
| Implement this interface if your provider can validate one or more different credential types (for example, if your provider can validate a password). |
|
| Implement this interface if your provider supports updating one or more different credential types. |
7.3. Model interfaces
Most of the methods defined in the capability interfaces either return or are passed in representations of a user. These representations are defined by the org.keycloak.models.UserModel interface. App developers are required to implement this interface. It provides a mapping between the external user store and the user metamodel that Red Hat build of Keycloak uses.
UserModel implementations provide access to read and update metadata about the user including things like username, name, email, role and group mappings, as well as other arbitrary attributes.
There are other model classes within the org.keycloak.models package that represent other parts of the Red Hat build of Keycloak metamodel: RealmModel, RoleModel, GroupModel, and ClientModel.
7.3.1. Storage Ids
One important method of UserModel is the getId() method. When implementing UserModel developers must be aware of the user id format. The format must be:
"f:" + component id + ":" + external id
"f:" + component id + ":" + external id
The Red Hat build of Keycloak runtime often has to look up users by their user id. The user id contains enough information so that the runtime does not have to query every single UserStorageProvider in the system to find the user.
The component id is the id returned from ComponentModel.getId(). The ComponentModel is passed in as a parameter when creating the provider class so you can get it from there. The external id is information your provider class needs to find the user in the external store. This is often a username or a uid. For example, it might look something like this:
f:332a234e31234:wburke
f:332a234e31234:wburke
When the runtime does a lookup by id, the id is parsed to obtain the component id. The component id is used to locate the UserStorageProvider that was originally used to load the user. That provider is then passed the id. The provider again parses the id to obtain the external id and it will use to locate the user in external user storage.
This format has the drawback that it can generate long IDs for the external storage users. This is specially important when combined with the WebAuthn authentication, which limits the user handle ID to 64 bytes. For that reason, if the storage users are going to use WebAuthn authentication, it is important to limit the full storage ID to 64 characters. The method validateConfiguration can be used to assign a short ID for the provider component on creation, giving some space to the user IDs within the 64 byte limitation.
7.4. Packaging and deployment
In order for Red Hat build of Keycloak to recognize the provider, you need to add a file to the JAR: META-INF/services/org.keycloak.storage.UserStorageProviderFactory. This file must contain a line-separated list of fully qualified classnames of the UserStorageProviderFactory implementations:
org.keycloak.examples.federation.properties.ClasspathPropertiesStorageFactory org.keycloak.examples.federation.properties.FilePropertiesStorageFactory
org.keycloak.examples.federation.properties.ClasspathPropertiesStorageFactory
org.keycloak.examples.federation.properties.FilePropertiesStorageFactory
To deploy this jar, copy it to the providers/ directory, then run bin/kc.[sh|bat] build.
7.5. Simple read-only, lookup example
To illustrate the basics of implementing the User Storage SPI let’s walk through a simple example. In this chapter you’ll see the implementation of a simple UserStorageProvider that looks up users in a simple property file. The property file contains username and password definitions and is hardcoded to a specific location on the classpath. The provider will be able to look up the user by ID and username and also be able to validate passwords. Users that originate from this provider will be read-only.
7.5.1. Provider class
The first thing we will walk through is the UserStorageProvider class.
Our provider class, PropertyFileUserStorageProvider, implements many interfaces. It implements the UserStorageProvider as that is a base requirement of the SPI. It implements the UserLookupProvider interface because we want to be able to log in with users stored by this provider. It implements the CredentialInputValidator interface because we want to be able to validate passwords entered in using the login screen. Our property file is read-only. We implement the CredentialInputUpdater because we want to post an error condition when the user attempts to update his password.
The constructor for this provider class is going to store the reference to the KeycloakSession, ComponentModel, and property file. We’ll use all of these later. Also notice that there is a map of loaded users. Whenever we find a user we will store it in this map so that we avoid re-creating it again within the same transaction. This is a good practice to follow as many providers will need to do this (that is, any provider that integrates with JPA). Remember also that provider class instances are created once per transaction and are closed after the transaction completes.
7.5.1.1. UserLookupProvider implementation
The getUserByUsername() method is invoked by the Red Hat build of Keycloak login page when a user logs in. In our implementation we first check the loadedUsers map to see if the user has already been loaded within this transaction. If it hasn’t been loaded we look in the property file for the username. If it exists we create an implementation of UserModel, store it in loadedUsers for future reference, and return this instance.
The createAdapter() method uses the helper class org.keycloak.storage.adapter.AbstractUserAdapter. This provides a base implementation for UserModel. It automatically generates a user id based on the required storage id format using the username of the user as the external id.
"f:" + component id + ":" + username
"f:" + component id + ":" + username
Every get method of AbstractUserAdapter either returns null or empty collections. However, methods that return role and group mappings will return the default roles and groups configured for the realm for every user. Every set method of AbstractUserAdapter will throw a org.keycloak.storage.ReadOnlyException. So if you attempt to modify the user in the Admin Console, you will get an error.
The getUserById() method parses the id parameter using the org.keycloak.storage.StorageId helper class. The StorageId.getExternalId() method is invoked to obtain the username embedded in the id parameter. The method then delegates to getUserByUsername().
Emails are not stored, so the getUserByEmail() method returns null.
7.5.1.2. CredentialInputValidator implementation
Next let’s look at the method implementations for CredentialInputValidator.
The isConfiguredFor() method is called by the runtime to determine if a specific credential type is configured for the user. This method checks to see that the password is set for the user.
The supportsCredentialType() method returns whether validation is supported for a specific credential type. We check to see if the credential type is password.
The isValid() method is responsible for validating passwords. The CredentialInput parameter is really just an abstract interface for all credential types. We make sure that we support the credential type and also that it is an instance of UserCredentialModel. When a user logs in through the login page, the plain text of the password input is put into an instance of UserCredentialModel. The isValid() method checks this value against the plain text password stored in the properties file. A return value of true means the password is valid.
7.5.1.3. CredentialInputUpdater implementation
As noted before, the only reason we implement the CredentialInputUpdater interface in this example is to forbid modifications of user passwords. The reason we have to do this is because otherwise the runtime would allow the password to be overridden in Red Hat build of Keycloak local storage. We’ll talk more about this later in this chapter.
The updateCredential() method just checks to see if the credential type is password. If it is, a ReadOnlyException is thrown.
7.5.2. Provider factory implementation
Now that the provider class is complete, we now turn our attention to the provider factory class.
First thing to notice is that when implementing the UserStorageProviderFactory class, you must pass in the concrete provider class implementation as a template parameter. Here we specify the provider class we defined before: PropertyFileUserStorageProvider.
If you do not specify the template parameter, your provider will not function. The runtime does class introspection to determine the capability interfaces that the provider implements.
The getId() method identifies the factory in the runtime and will also be the string shown in the admin console when you want to enable a user storage provider for the realm.
7.5.2.1. Initialization
The UserStorageProviderFactory interface has an optional init() method you can implement. When Red Hat build of Keycloak boots up, only one instance of each provider factory is created. Also at boot time, the init() method is called on each of these factory instances. There’s also a postInit() method you can implement as well. After each factory’s init() method is invoked, their postInit() methods are called.
In our init() method implementation, we find the property file containing our user declarations from the classpath. We then load the properties field with the username and password combinations stored there.
The Config.Scope parameter is factory configuration that configured through server configuration.
For example, by running the server with the following argument:
kc.[sh|bat] start --spi-storage-readonly-property-file-path=/other-users.properties
kc.[sh|bat] start --spi-storage-readonly-property-file-path=/other-users.properties
We can specify the classpath of the user property file instead of hardcoding it. Then you can retrieve the configuration in the PropertyFileUserStorageProviderFactory.init():
7.5.2.2. Create method
Our last step in creating the provider factory is the create() method.
@Override
public PropertyFileUserStorageProvider create(KeycloakSession session, ComponentModel model) {
return new PropertyFileUserStorageProvider(session, model, properties);
}
@Override
public PropertyFileUserStorageProvider create(KeycloakSession session, ComponentModel model) {
return new PropertyFileUserStorageProvider(session, model, properties);
}
We simply allocate the PropertyFileUserStorageProvider class. This create method will be called once per transaction.
7.5.3. Packaging and deployment
The class files for our provider implementation should be placed in a jar. You also have to declare the provider factory class within the META-INF/services/org.keycloak.storage.UserStorageProviderFactory file.
org.keycloak.examples.federation.properties.FilePropertiesStorageFactory
org.keycloak.examples.federation.properties.FilePropertiesStorageFactory
To deploy this jar, copy it to the providers/ directory, then run bin/kc.[sh|bat] build.
7.5.4. Enabling the provider in the Admin Console
You enable user storage providers per realm within the User Federation page in the Admin Console.
User Federation
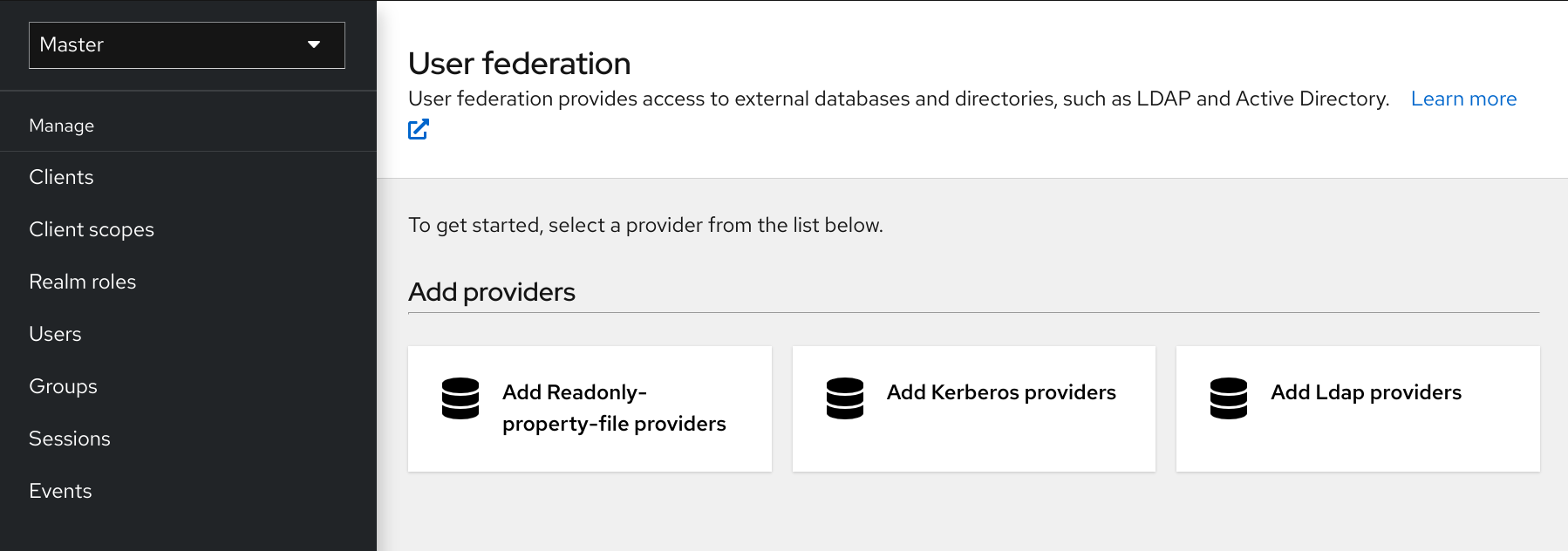
Procedure
Select the provider we just created from the list:
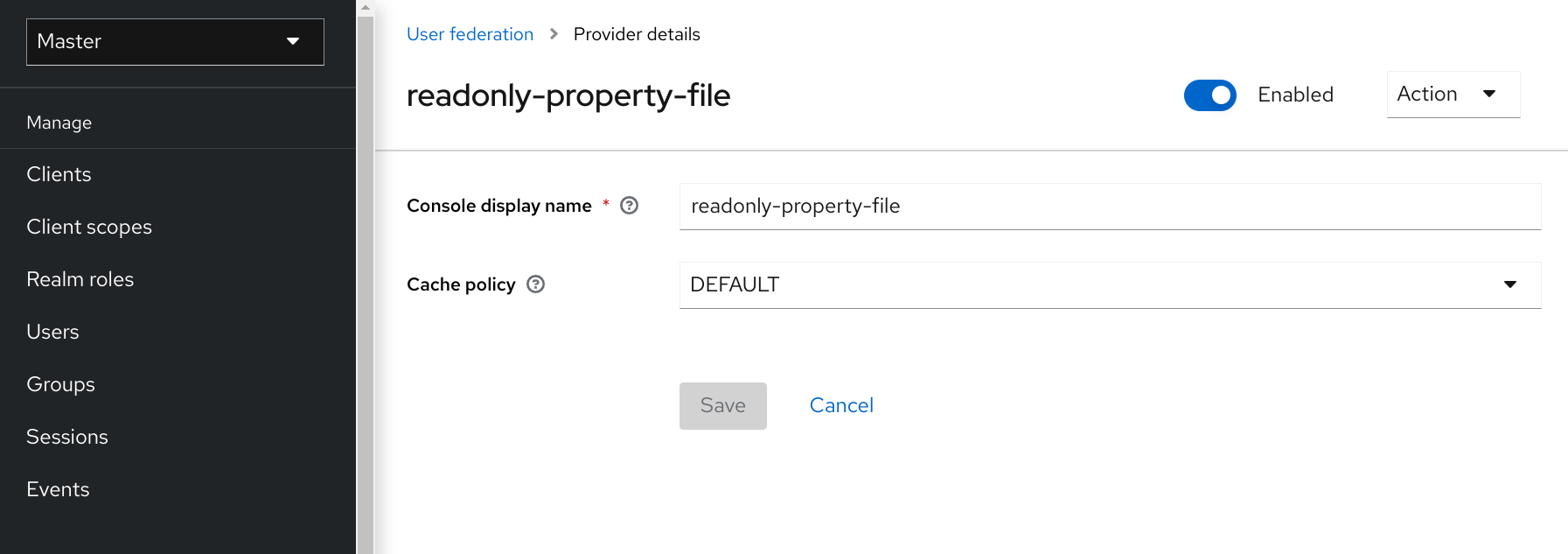
readonly-property-file.The configuration page for our provider displays.
Click Save because we have nothing to configure.
Configured Provider
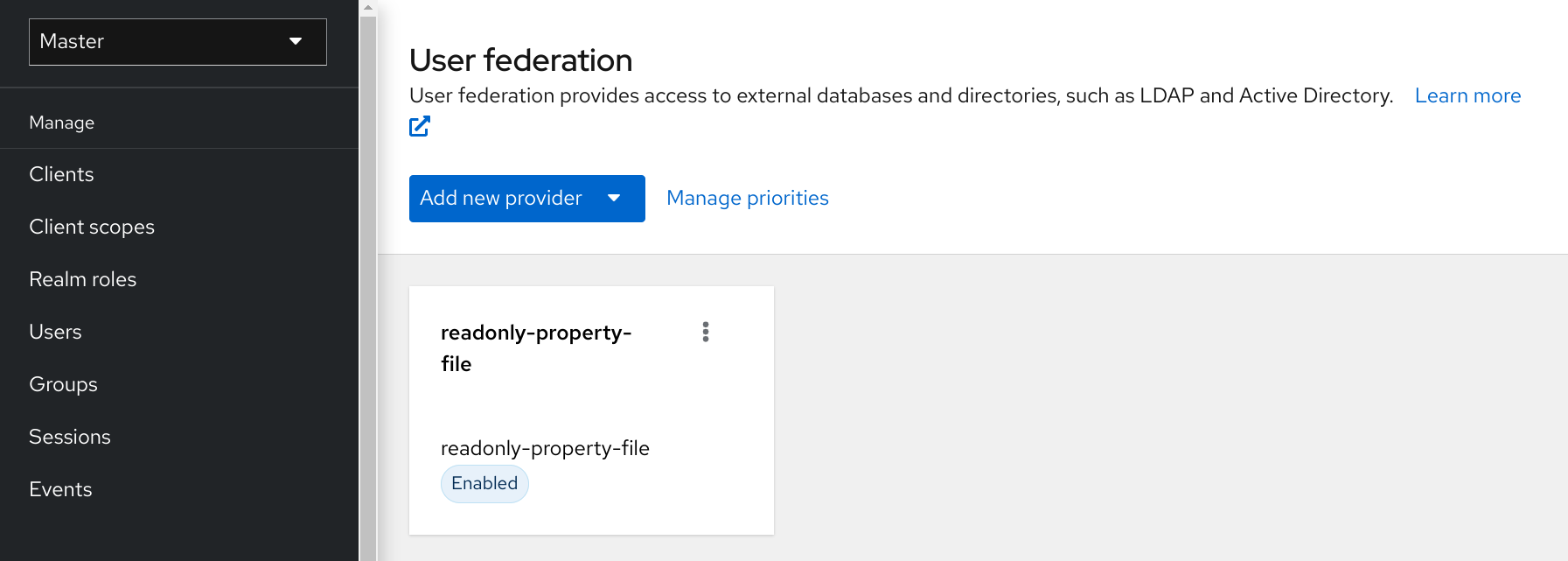
Return to the main User Federation page
You now see your provider listed.
User Federation
You will now be able to log in with a user declared in the users.properties file. This user will only be able to view the account page after logging in.
7.6. Configuration techniques
Our PropertyFileUserStorageProvider example is a bit contrived. It is hardcoded to a property file that is embedded in the jar of the provider, which is not terribly useful. We might want to make the location of this file configurable per instance of the provider. In other words, we might want to reuse this provider multiple times in multiple different realms and point to completely different user property files. We’ll also want to perform this configuration within the Admin Console UI.
The UserStorageProviderFactory has additional methods you can implement that handle provider configuration. You describe the variables you want to configure per provider and the Admin Console automatically renders a generic input page to gather this configuration. When implemented, callback methods also validate the configuration before it is saved, when a provider is created for the first time, and when it is updated. UserStorageProviderFactory inherits these methods from the org.keycloak.component.ComponentFactory interface.
The ComponentFactory.getConfigProperties() method returns a list of org.keycloak.provider.ProviderConfigProperty instances. These instances declare metadata that is needed to render and store each configuration variable of the provider.
7.6.1. Configuration example
Let’s expand our PropertyFileUserStorageProviderFactory example to allow you to point a provider instance to a specific file on disk.
PropertyFileUserStorageProviderFactory
The ProviderConfigurationBuilder class is a great helper class to create a list of configuration properties. Here we specify a variable named path that is a String type. On the Admin Console configuration page for this provider, this configuration variable is labeled as Path and has a default value of ${jboss.server.config.dir}/example-users.properties. When you hover over the tooltip of this configuration option, it displays the help text, File path to properties file.
The next thing we want to do is to verify that this file exists on disk. We do not want to enable an instance of this provider in the realm unless it points to a valid user property file. To do this, we implement the validateConfiguration() method.
The validateConfiguration() method provides the configuration variable from the ComponentModel to verify if that file exists on disk. Notice that the use of the org.keycloak.common.util.EnvUtil.replace() method. With this method any string that includes ${} will replace that value with a system property value. The ${jboss.server.config.dir} string corresponds to the conf/ directory of our server and is really useful for this example.
Next thing we have to do is remove the old init() method. We do this because user property files are going to be unique per provider instance. We move this logic to the create() method.
This logic is, of course, inefficient as every transaction reads the entire user property file from disk, but hopefully this illustrates, in a simple way, how to hook in configuration variables.
7.6.2. Configuring the provider in the Admin Console
Now that the configuration is enabled, you can set the path variable when you configure the provider in the Admin Console.
7.7. Add/Remove user and query capability interfaces
One thing we have not done with our example is allow it to add and remove users or change passwords. Users defined in our example are also not queryable or viewable in the Admin Console. To add these enhancements, our example provider must implement the UserQueryMethodsProvider (or UserQueryProvider) and UserRegistrationProvider interfaces.
7.7.1. Implementing UserRegistrationProvider
Use this procedure to implement adding and removing users from the particular store, we first have to be able to save our properties file to disk.
PropertyFileUserStorageProvider
Then, the implementation of the addUser() and removeUser() methods becomes simple.
PropertyFileUserStorageProvider
Notice that when adding a user we set the password value of the property map to be UNSET_PASSWORD. We do this as we can’t have null values for a property in the property value. We also have to modify the CredentialInputValidator methods to reflect this.
The addUser() method will be called if the provider implements the UserRegistrationProvider interface. If your provider has a configuration switch to turn off adding a user, returning null from this method will skip the provider and call the next one.
PropertyFileUserStorageProvider
Since we can now save our property file, it also makes sense to allow password updates.
PropertyFileUserStorageProvider
We can now also implement disabling a password.
PropertyFileUserStorageProvider
With these methods implemented, you’ll now be able to change and disable the password for the user in the Admin Console.
7.7.2. Implementing UserQueryProvider
UserQueryProvider is combination of UserQueryMethodsProvider and UserCountMethodsProvider. Without implementing UserQueryMethodsProvider the Admin Console would not be able to view and manage users that were loaded by our example provider. Let’s look at implementing this interface.
PropertyFileUserStorageProvider
The first declaration of searchForUserStream() takes a String parameter. In this example, the parameter represents a username that you want to search by. This string can be a substring, which explains the choice of the String.contains() method when doing the search. Notice the use of * to indicate to request a list of all users. The method iterates over the key set of the property file, delegating to getUserByUsername() to load a user. Notice that we are indexing this call based on the firstResult and maxResults parameter. If your external store does not support pagination, you will have to do similar logic.
PropertyFileUserStorageProvider
The searchForUserStream() method that takes a Map parameter can search for a user based on first, last name, username, and email. Only usernames are stored, so the search is based only on usernames except when the Map parameter does not contain the username attribute. In this case, all users are returned. In that situation, the searchForUserStream(realm, search, firstResult, maxResults) is used.
PropertyFileUserStorageProvider
Groups or attributes are not stored, so the other methods return an empty stream.
7.8. Augmenting external storage
The PropertyFileUserStorageProvider example is really limited. While we will be able to log in with users stored in a property file, we won’t be able to do much else. If users loaded by this provider need special role or group mappings to fully access particular applications there is no way for us to add additional role mappings to these users. You also can’t modify or add additional important attributes like email, first and last name.
For these types of situations, Red Hat build of Keycloak allows you to augment your external store by storing extra information in Red Hat build of Keycloak’s database. This is called federated user storage and is encapsulated within the org.keycloak.storage.federated.UserFederatedStorageProvider class.
UserFederatedStorageProvider
The UserFederatedStorageProvider instance is available on the UserStorageUtil.userFederatedStorage(KeycloakSession) method. It has all different kinds of methods for storing attributes, group and role mappings, different credential types, and required actions. If your external store’s datamodel cannot support the full Red Hat build of Keycloak feature set, then this service can fill in the gaps.
Red Hat build of Keycloak comes with a helper class org.keycloak.storage.adapter.AbstractUserAdapterFederatedStorage that will delegate every single UserModel method except get/set of username to user federated storage. Override the methods you need to override to delegate to your external storage representations. It is strongly suggested you read the javadoc of this class as it has smaller protected methods you may want to override. Specifically surrounding group membership and role mappings.
7.8.1. Augmentation example
In our PropertyFileUserStorageProvider example, we just need a simple change to our provider to use the AbstractUserAdapterFederatedStorage.
PropertyFileUserStorageProvider
We instead define an anonymous class implementation of AbstractUserAdapterFederatedStorage. The setUsername() method makes changes to the properties file and saves it.
7.9. Import implementation strategy
When implementing a user storage provider, there’s another strategy you can take. Instead of using user federated storage, you can create a user locally in the Red Hat build of Keycloak built-in user database and copy attributes from your external store into this local copy. There are many advantages to this approach.
- Red Hat build of Keycloak basically becomes a persistence user cache for your external store. Once the user is imported you’ll no longer hit the external store thus taking load off of it.
- If you are moving to Red Hat build of Keycloak as your official user store and deprecating the old external store, you can slowly migrate applications to use Red Hat build of Keycloak. When all applications have been migrated, unlink the imported user, and retire the old legacy external store.
There are some obvious disadvantages though to using an import strategy:
- Looking up a user for the first time will require multiple updates to Red Hat build of Keycloak database. This can be a big performance loss under load and put a lot of strain on the Red Hat build of Keycloak database. The user federated storage approach will only store extra data as needed and may never be used depending on the capabilities of your external store.
- With the import approach, you have to keep local Red Hat build of Keycloak storage and external storage in sync. The User Storage SPI has capability interfaces that you can implement to support synchronization, but this can quickly become painful and messy.
To implement the import strategy you simply check to see first if the user has been imported locally. If so return the local user, if not create the user locally and import data from the external store. You can also proxy the local user so that most changes are automatically synchronized.
This will be a bit contrived, but we can extend our PropertyFileUserStorageProvider to take this approach. We begin first by modifying the createAdapter() method.
PropertyFileUserStorageProvider
In this method we call the UserStoragePrivateUtil.userLocalStorage(session) method to obtain a reference to local Red Hat build of Keycloak user storage. We see if the user is stored locally, if not, we add it locally. Do not set the id of the local user. Let Red Hat build of Keycloak automatically generate the id. Also note that we call UserModel.setFederationLink() and pass in the ID of the ComponentModel of our provider. This sets a link between the provider and the imported user.
When a user storage provider is removed, any user imported by it will also be removed. This is one of the purposes of calling UserModel.setFederationLink().
Another thing to note is that if a local user is linked, your storage provider will still be delegated to for methods that it implements from the CredentialInputValidator and CredentialInputUpdater interfaces. Returning false from a validation or update will just result in Red Hat build of Keycloak seeing if it can validate or update using local storage.
Also notice that we are proxying the local user using the org.keycloak.models.utils.UserModelDelegate class. This class is an implementation of UserModel. Every method just delegates to the UserModel it was instantiated with. We override the setUsername() method of this delegate class to synchronize automatically with the property file. For your providers, you can use this to intercept other methods on the local UserModel to perform synchronization with your external store. For example, get methods could make sure that the local store is in sync. Set methods keep the external store in sync with the local one. One thing to note is that the getId() method should always return the id that was auto generated when you created the user locally. You should not return a federated id as shown in the other non-import examples.
If your provider is implementing the UserRegistrationProvider interface, your removeUser() method does not need to remove the user from local storage. The runtime will automatically perform this operation. Also note that removeUser() will be invoked before it is removed from local storage.
7.9.1. ImportedUserValidation interface
If you remember earlier in this chapter, we discussed how querying for a user worked. Local storage is queried first, if the user is found there, then the query ends. This is a problem for our above implementation as we want to proxy the local UserModel so that we can keep usernames in sync. The User Storage SPI has a callback for whenever a linked local user is loaded from the local database.
Whenever a linked local user is loaded, if the user storage provider class implements this interface, then the validate() method is called. Here you can proxy the local user passed in as a parameter and return it. That new UserModel will be used. You can also optionally do a check to see if the user still exists in the external store. If validate() returns null, then the local user will be removed from the database.
7.9.2. ImportSynchronization interface
With the import strategy you can see that it is possible for the local user copy to get out of sync with external storage. For example, maybe a user has been removed from the external store. The User Storage SPI has an additional interface you can implement to deal with this, org.keycloak.storage.user.ImportSynchronization:
This interface is implemented by the provider factory. Once this interface is implemented by the provider factory, the administration console management page for the provider shows additional options. You can manually force a synchronization by clicking a button. This invokes the ImportSynchronization.sync() method. Also, additional configuration options are displayed that allow you to automatically schedule a synchronization. Automatic synchronizations invoke the syncSince() method.
7.10. User caches
When a user object is loaded by ID, username, or email queries it is cached. When a user object is being cached, it iterates through the entire UserModel interface and pulls this information to a local in-memory-only cache. In a cluster, this cache is still local, but it becomes an invalidation cache. When a user object is modified, it is evicted. This eviction event is propagated to the entire cluster so that the other nodes' user cache is also invalidated.
7.10.1. Managing the user cache
You can access the user cache by calling KeycloakSession.getProvider(UserCache.class).
There are methods for evicting specific users, users contained in a specific realm, or the entire cache.
7.10.2. OnUserCache callback interface
You might want to cache additional information that is specific to your provider implementation. The User Storage SPI has a callback whenever a user is cached: org.keycloak.models.cache.OnUserCache.
public interface OnUserCache {
void onCache(RealmModel realm, CachedUserModel user, UserModel delegate);
}
public interface OnUserCache {
void onCache(RealmModel realm, CachedUserModel user, UserModel delegate);
}
Your provider class should implement this interface if it wants this callback. The UserModel delegate parameter is the UserModel instance returned by your provider. The CachedUserModel is an expanded UserModel interface. This is the instance that is cached locally in local storage.
This CachedUserModel interface allows you to evict the user from the cache and get the provider UserModel instance. The getCachedWith() method returns a map that allows you to cache additional information pertaining to the user. For example, credentials are not part of the UserModel interface. If you wanted to cache credentials in memory, you would implement OnUserCache and cache your user’s credentials using the getCachedWith() method.
7.10.3. Cache policies
On the administration console management page for your user storage provider, you can specify a unique cache policy.
7.11. Leveraging Jakarta EE
Since version 20, Keycloak relies only on Quarkus. Unlike WildFly, Quarkus is not an Application Server.
Therefore, the User Storage Providers cannot be packaged within any Jakarta EE component or make it an EJB as was the case when Keycloak ran over WildFly in previous versions.
Providers implementations are required to be plain java objects which implement the suitable User Storage SPI interfaces, as was explained in the previous sections. They must be packaged and deployed as stated in the Migration Guide. See Migrating custom providers.
You can still implement your custom UserStorageProvider class, which is able to integrate an external database by JPA Entity Manager, as shown in this example:
CDI is not supported.
7.12. REST management API
You can create, remove, and update your user storage provider deployments through the administrator REST API. The User Storage SPI is built on top of a generic component interface so you will be using that generic API to manage your providers.
The REST Component API lives under your realm admin resource.
/admin/realms/{realm-name}/components
/admin/realms/{realm-name}/components
We will only show this REST API interaction with the Java client. Hopefully you can extract how to do this from curl from this API.
To create a user storage provider, you must specify the provider id, a provider type of the string org.keycloak.storage.UserStorageProvider, as well as the configuration.
7.13. Migrating from an earlier user federation SPI
This chapter is only applicable if you have implemented a provider using the earlier (and now removed) User Federation SPI.
In Keycloak version 2.4.0 and earlier there was a User Federation SPI. Red Hat Single Sign-On version 7.0, although unsupported, had this earlier SPI available as well. This earlier User Federation SPI has been removed from Keycloak version 2.5.0 and Red Hat Single Sign-On version 7.1. However, if you have written a provider with this earlier SPI, this chapter discusses some strategies you can use to port it.
7.13.1. Import versus non-import
The earlier User Federation SPI required you to create a local copy of a user in the Red Hat build of Keycloak’s database and import information from your external store to the local copy. However, this is no longer a requirement. You can still port your earlier provider as-is, but you should consider whether a non-import strategy might be a better approach.
Advantages of the import strategy:
- Red Hat build of Keycloak basically becomes a persistence user cache for your external store. Once the user is imported you’ll no longer hit the external store, thus taking load off of it.
- If you are moving to Red Hat build of Keycloak as your official user store and deprecating the earlier external store, you can slowly migrate applications to use Red Hat build of Keycloak. When all applications have been migrated, unlink the imported user, and retire the earlier legacy external store.
There are some obvious disadvantages though to using an import strategy:
- Looking up a user for the first time will require multiple updates to Red Hat build of Keycloak database. This can be a big performance loss under load and put a lot of strain on the Red Hat build of Keycloak database. The user federated storage approach will only store extra data as needed and might never be used depending on the capabilities of your external store.
- With the import approach, you have to keep local Red Hat build of Keycloak storage and external storage in sync. The User Storage SPI has capability interfaces that you can implement to support synchronization, but this can quickly become painful and messy.
7.13.2. UserFederationProvider versus UserStorageProvider
The first thing to notice is that UserFederationProvider was a complete interface. You implemented every method in this interface. However, UserStorageProvider has instead broken up this interface into multiple capability interfaces that you implement as needed.
UserFederationProvider.getUserByUsername() and getUserByEmail() have exact equivalents in the new SPI. The difference between the two is how you import. If you are going to continue with an import strategy, you no longer call KeycloakSession.userStorage().addUser() to create the user locally. Instead you call KeycloakSession.userLocalStorage().addUser(). The userStorage() method no longer exists.
The UserFederationProvider.validateAndProxy() method has been moved to an optional capability interface, ImportedUserValidation. You want to implement this interface if you are porting your earlier provider as-is. Also note that in the earlier SPI, this method was called every time the user was accessed, even if the local user is in the cache. In the later SPI, this method is only called when the local user is loaded from local storage. If the local user is cached, then the ImportedUserValidation.validate() method is not called at all.
The UserFederationProvider.isValid() method no longer exists in the later SPI.
The UserFederationProvider methods synchronizeRegistrations(), registerUser(), and removeUser() have been moved to the UserRegistrationProvider capability interface. This new interface is optional to implement so if your provider does not support creating and removing users, you don’t have to implement it. If your earlier provider had switch to toggle support for registering new users, this is supported in the new SPI, returning null from UserRegistrationProvider.addUser() if the provider doesn’t support adding users.
The earlier UserFederationProvider methods centered around credentials are now encapsulated in the CredentialInputValidator and CredentialInputUpdater interfaces, which are also optional to implement depending on if you support validating or updating credentials. Credential management used to exist in UserModel methods. These also have been moved to the CredentialInputValidator and CredentialInputUpdater interfaces. One thing to note that if you do not implement the CredentialInputUpdater interface, then any credentials provided by your provider can be overridden locally in Red Hat build of Keycloak storage. So if you want your credentials to be read-only, implement the CredentialInputUpdater.updateCredential() method and return a ReadOnlyException.
The UserFederationProvider query methods such as searchByAttributes() and getGroupMembers() are now encapsulated in an optional interface UserQueryProvider. If you do not implement this interface, then users will not be viewable in the admin console. You’ll still be able to log in though.
7.13.3. UserFederationProviderFactory versus UserStorageProviderFactory
The synchronization methods in the earlier SPI are now encapsulated within an optional ImportSynchronization interface. If you have implemented synchronization logic, then have your new UserStorageProviderFactory implement the ImportSynchronization interface.
7.13.4. Upgrading to a new model
The User Storage SPI instances are stored in a different set of relational tables. Red Hat build of Keycloak automatically runs a migration script. If any earlier User Federation providers are deployed for a realm, they are converted to the later storage model as is, including the id of the data. This migration will only happen if a User Storage provider exists with the same provider ID (i.e., "ldap", "kerberos") as the earlier User Federation provider.
So, knowing this there are different approaches you can take.
- You can remove the earlier provider in your earlier Red Hat build of Keycloak deployment. This will remove the local linked copies of all users you imported. Then, when you upgrade Red Hat build of Keycloak, just deploy and configure your new provider for your realm.
-
The second option is to write your new provider making sure it has the same provider ID:
UserStorageProviderFactory.getId(). Make sure this provider is deployed to the server. Boot the server, and have the built-in migration script convert from the earlier data model to the later data model. In this case all your earlier linked imported users will work and be the same.
If you have decided to get rid of the import strategy and rewrite your User Storage provider, we suggest that you remove the earlier provider before upgrading Red Hat build of Keycloak. This will remove linked local imported copies of any user you imported.
7.14. Stream-based interfaces
Many of the user storage interfaces in Red Hat build of Keycloak contain query methods that can return potentially large sets of objects, which might lead to significant impacts in terms of memory consumption and processing time. This is especially true when only a small subset of the objects' internal state is used in the query method’s logic.
To provide developers with a more efficient alternative to process large data sets in these query methods, a Streams sub-interface has been added to user storage interfaces. These Streams sub-interfaces replace the original collection-based methods in the super-interfaces with stream-based variants, making the collection-based methods default. The default implementation of a collection-based query method invokes its Stream counterpart and collects the result into the proper collection type.
The Streams sub-interfaces allow for implementations to focus on the stream-based approach for processing sets of data and benefit from the potential memory and performance optimizations of that approach. The interfaces that offer a Streams sub-interface to be implemented include a few capability interfaces, all interfaces in the org.keycloak.storage.federated package and a few others that might be implemented depending on the scope of the custom storage implementation.
See this list of the interfaces that offer a Streams sub-interface to developers.
| Package | Classes |
|
|
|
|
|
|
|
| All interfaces |
|
|
|
(*) indicates the interface is a capability interface
Custom user storage implementation that want to benefit from the streams approach should simply implement the Streams sub-interfaces instead of the original interfaces. For example, the following code uses the Streams variant of the UserQueryProvider interface:
Chapter 8. Vault SPI
8.1. Vault provider
You can use a vault SPI from org.keycloak.vault package to write custom extension for Red Hat build of Keycloak to connect to arbitrary vault implementation.
The built-in files-plaintext provider is an example of the implementation of this SPI. In general the following rules apply:
-
To prevent a secret from leaking across realms, you may want to isolate or limit the secrets that can be retrieved by a realm. In that case, your provider should take into account the realm name when looking up secrets, for example by prefixing entries with the realm name. For example, an expression
${vault.key}would then evaluate generally to different entry names, depending on whether it was used in a realm A or realm B. To differentiate between realms, the realm needs to be passed to the createdVaultProviderinstance fromVaultProviderFactory.create()method where it is available from theKeycloakSessionparameter. -
The vault provider needs to implement a single method
obtainSecretthat returns aVaultRawSecretfor the given secret name. That class holds the representation of the secret either inbyte[]orByteBufferand is expected to convert between the two upon demand. Note that this buffer would be discarded after usage as explained below.
For details on how to package and deploy a custom provider refer to the Service Provider Interfaces chapter.
8.2. Consuming values from vault
The vault contains sensitive data and Red Hat build of Keycloak treats the secrets accordingly. When accessing a secret, the secret is obtained from the vault and retained in JVM memory only for the necessary time. Then all possible attempts to discard its content from JVM memory is done. This is achieved by using the vault secrets only within try-with-resources statement as outlined below:
The example uses KeycloakSession.vault() as the entrypoint for accessing the secrets. Using the VaultProvider.obtainSecret method directly is indeed also possible. However the vault() method has the benefit of ability to interpret the raw secret (which is generally a byte array) as a character array (via vault().getCharSecret()) or a String (via vault().getStringSecret()) in addition to obtaining the original uninterpreted value (via vault().getRawSecret() method).
Note that since String objects are immutable, their content cannot be discarded by overriding with random garbage. Even though measures have been taken in the default VaultStringSecret implementation to prevent internalizing Strings, the secrets stored in String objects would live at least to the next GC round. Thus using plain byte and character arrays and buffers is preferable.