Configuring plugins in Red Hat Developer Hub
Abstract
Preface
The Red Hat Developer Hub is an enterprise-grade, integrated developer platform, extended through plugins, that helps reduce the friction and frustration of developers while boosting their productivity.
Red Hat Developer Hub support
If you experience difficulty with a procedure described in this documentation, visit the Red Hat Customer Portal. You can use the Red Hat Customer Portal for the following purposes:
- To search or browse through the Red Hat Knowledgebase of technical support articles about Red Hat products.
- To create a support case for Red Hat Global Support Services (GSS). For support case creation, select Red Hat Developer Hub as the product and select the appropriate product version.
Chapter 1. Plugins in Red Hat Developer Hub
The Red Hat Developer Hub application offers a unified platform with various plugins. Using the plugin ecosystem within the Developer Hub application, you can access any kind of development infrastructure or software development tool.
The plugins in Developer Hub maximize the productivity and streamline the development workflows by maintaining the consistency in the overall user experience.
Chapter 2. Dynamic plugin installation
The dynamic plugin support is based on the backend plugin manager package, which is a service that scans a configured root directory (dynamicPlugins.rootDirectory in the app config) for dynamic plugin packages and loads them dynamically.
You can use the dynamic plugins that come preinstalled with Red Hat Developer Hub or install external dynamic plugins from a public NPM registry.
2.1. Viewing installed plugins
Using the Dynamic Plugins Info front-end plugin, you can view plugins that are currently installed in your Red Hat Developer Hub application. This plugin is enabled by default.
Procedure
- Open your Developer Hub application and click Administration.
- Go to the Plugins tab to view a list of installed plugins and related information.
2.2. Preinstalled dynamic plugins
Red Hat Developer Hub is preinstalled with a selection of dynamic plugins. The dynamic plugins that require custom configuration are disabled by default.
For a complete list of dynamic plugins that are preinstalled in this release of Developer Hub, see the Dynamic plugins support matrix.
Upon application startup, for each plugin that is disabled by default, the install-dynamic-plugins init container within the Developer Hub pod log displays a message similar to the following:
======= Skipping disabled dynamic plugin ./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-github-dynamic
To enable this plugin, add a package with the same name to the Helm chart and change the value in the disabled field to ‘false’. For example:
global:
dynamic:
includes:
- dynamic-plugins.default.yaml
plugins:
- package: ./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-github-dynamic
disabled: false
The default configuration for a plugin is extracted from the dynamic-plugins.default.yaml` file, however, you can use a pluginConfig entry to override the default configuration.
2.2.1. Preinstalled dynamic plugin descriptions and details
Technology Preview features are not supported with Red Hat production service level agreements (SLAs), might not be functionally complete, and Red Hat does not recommend using them for production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information on Red Hat Technology Preview features, see Technology Preview Features Scope.
Additional detail on how Red Hat provides support for bundled community dynamic plugins is available on the Red Hat Developer Support Policy page.
There are 60 plugins available in Red Hat Developer Hub. See the following table for more information:
| Name | Plugin | Role | Version | Support Level | Path | Required Variables | Default |
|---|---|---|---|---|---|---|---|
| 3scale | @janus-idp/backstage-plugin-3scale-backend | Backend | 1.5.15 | Red Hat Tech Preview | ./dynamic-plugins/dist/janus-idp-backstage-plugin-3scale-backend-dynamic |
| Disabled |
| AAP | @janus-idp/backstage-plugin-aap-backend | Backend | 1.6.15 | Red Hat Tech Preview | ./dynamic-plugins/dist/janus-idp-backstage-plugin-aap-backend-dynamic |
| Disabled |
| ACR | @janus-idp/backstage-plugin-acr | Frontend | 1.4.13 | Red Hat Tech Preview | ./dynamic-plugins/dist/janus-idp-backstage-plugin-acr | Disabled | |
| Analytics Provider Segment | @janus-idp/backstage-plugin-analytics-provider-segment | Frontend | 1.4.9 | Production | ./dynamic-plugins/dist/janus-idp-backstage-plugin-analytics-provider-segment |
| Enabled |
| Argo CD | @janus-idp/backstage-plugin-argocd | Frontend | 1.2.3 | Production | ./dynamic-plugins/dist/janus-idp-backstage-plugin-argocd | Disabled | |
| Argo CD | @roadiehq/backstage-plugin-argo-cd | Frontend | 2.6.5 | Production | ./dynamic-plugins/dist/roadiehq-backstage-plugin-argo-cd | Disabled | |
| Argo CD | @roadiehq/backstage-plugin-argo-cd-backend | Backend | 3.0.2 | Production | ./dynamic-plugins/dist/roadiehq-backstage-plugin-argo-cd-backend-dynamic |
| Disabled |
| Argo CD | @roadiehq/scaffolder-backend-argocd | Backend | 1.1.27 | Community Support | ./dynamic-plugins/dist/roadiehq-scaffolder-backend-argocd-dynamic |
| Disabled |
| Azure | @backstage/plugin-scaffolder-backend-module-azure | Backend | 0.1.9 | Community Support | ./dynamic-plugins/dist/backstage-plugin-scaffolder-backend-module-azure-dynamic | Enabled | |
| Azure Devops | @backstage/plugin-azure-devops | Frontend | 0.4.4 | Community Support | ./dynamic-plugins/dist/backstage-plugin-azure-devops | Disabled | |
| Azure Devops | @backstage/plugin-azure-devops-backend | Backend | 0.6.5 | Community Support | ./dynamic-plugins/dist/backstage-plugin-azure-devops-backend-dynamic |
| Disabled |
| Azure Repositories | @parfuemerie/douglas-scaffolder-backend-module-azure-repositories | Backend | 0.2.7 | Community Support | ./dynamic-plugins/dist/parfuemerie-douglas-scaffolder-backend-module-azure-repositories | Disabled | |
| Bitbucket Cloud | @backstage/plugin-catalog-backend-module-bitbucket-cloud | Backend | 0.2.4 | Community Support | ./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-bitbucket-cloud-dynamic |
| Disabled |
| Bitbucket Cloud | @backstage/plugin-scaffolder-backend-module-bitbucket-cloud | Backend | 0.1.7 | Community Support | ./dynamic-plugins/dist/backstage-plugin-scaffolder-backend-module-bitbucket-cloud-dynamic | Enabled | |
| Bitbucket Server | @backstage/plugin-catalog-backend-module-bitbucket-server | Backend | 0.1.31 | Community Support | ./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-bitbucket-server-dynamic |
| Disabled |
| Bitbucket Server | @backstage/plugin-scaffolder-backend-module-bitbucket-server | Backend | 0.1.7 | Community Support | ./dynamic-plugins/dist/backstage-plugin-scaffolder-backend-module-bitbucket-server-dynamic | Enabled | |
| Datadog | @roadiehq/backstage-plugin-datadog | Frontend | 2.2.8 | Community Support | ./dynamic-plugins/dist/roadiehq-backstage-plugin-datadog | Disabled | |
| Dynatrace | @backstage/plugin-dynatrace | Frontend | 10.0.4 | Community Support | ./dynamic-plugins/dist/backstage-plugin-dynatrace | Disabled | |
| Gerrit | @backstage/plugin-scaffolder-backend-module-gerrit | Backend | 0.1.9 | Community Support | ./dynamic-plugins/dist/backstage-plugin-scaffolder-backend-module-gerrit-dynamic | Enabled | |
| GitHub | @backstage/plugin-catalog-backend-module-github | Backend | 0.6.0 | Community Support | ./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-github-dynamic |
| Disabled |
| GitHub | @backstage/plugin-scaffolder-backend-module-github | Backend | 0.2.7 | Community Support | ./dynamic-plugins/dist/backstage-plugin-scaffolder-backend-module-github-dynamic | Enabled | |
| GitHub Actions | @backstage/plugin-github-actions | Frontend | 0.6.16 | Community Support | ./dynamic-plugins/dist/backstage-plugin-github-actions | Disabled | |
| GitHub Insights | @roadiehq/backstage-plugin-github-insights | Frontend | 2.3.29 | Community Support | ./dynamic-plugins/dist/roadiehq-backstage-plugin-github-insights | Disabled | |
| GitHub Issues | @backstage/plugin-github-issues | Frontend | 0.4.2 | Community Support | ./dynamic-plugins/dist/backstage-plugin-github-issues | Disabled | |
| GitHub Org | @backstage/plugin-catalog-backend-module-github-org | Backend | 0.1.12 | Community Support | ./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-github-org-dynamic |
| Disabled |
| GitHub Pull Requests | @roadiehq/backstage-plugin-github-pull-requests | Frontend | 2.5.26 | Community Support | ./dynamic-plugins/dist/roadiehq-backstage-plugin-github-pull-requests | Disabled | |
| GitLab | @immobiliarelabs/backstage-plugin-gitlab | Frontend | 6.5.0 | Community Support | ./dynamic-plugins/dist/immobiliarelabs-backstage-plugin-gitlab | Disabled | |
| GitLab | @backstage/plugin-catalog-backend-module-gitlab | Backend | 0.3.15 | Community Support | ./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-gitlab-dynamic | Disabled | |
| GitLab | @immobiliarelabs/backstage-plugin-gitlab-backend | Backend | 6.5.0 | Community Support | ./dynamic-plugins/dist/immobiliarelabs-backstage-plugin-gitlab-backend-dynamic |
| Disabled |
| GitLab | @backstage/plugin-scaffolder-backend-module-gitlab | Backend | 0.3.3 | Community Support | ./dynamic-plugins/dist/backstage-plugin-scaffolder-backend-module-gitlab-dynamic | Enabled | |
| GitLab Org | @backstage/plugin-catalog-backend-module-gitlab-org | Backend | 0.3.10 | Community Support | ./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-gitlab-org-dynamic | Disabled | |
| Http Request | @roadiehq/scaffolder-backend-module-http-request | Backend | 4.3.2 | Community Support | ./dynamic-plugins/dist/roadiehq-scaffolder-backend-module-http-request-dynamic | Enabled | |
| Jenkins | @backstage/plugin-jenkins | Frontend | 0.9.10 | Community Support | ./dynamic-plugins/dist/backstage-plugin-jenkins | Disabled | |
| Jenkins | @backstage/plugin-jenkins-backend | Backend | 0.4.5 | Community Support | ./dynamic-plugins/dist/backstage-plugin-jenkins-backend-dynamic |
| Disabled |
| JFrog Artifactory | @janus-idp/backstage-plugin-jfrog-artifactory | Frontend | 1.4.11 | Red Hat Tech Preview | ./dynamic-plugins/dist/janus-idp-backstage-plugin-jfrog-artifactory | Disabled | |
| Jira | @roadiehq/backstage-plugin-jira | Frontend | 2.5.8 | Community Support | ./dynamic-plugins/dist/roadiehq-backstage-plugin-jira | Disabled | |
| Keycloak | @janus-idp/backstage-plugin-keycloak-backend | Backend | 1.9.12 | Production | ./dynamic-plugins/dist/janus-idp-backstage-plugin-keycloak-backend-dynamic |
| Disabled |
| Kubernetes | @backstage/plugin-kubernetes | Frontend | 0.11.9 | Community Support | ./dynamic-plugins/dist/backstage-plugin-kubernetes | Disabled | |
| Kubernetes | @backstage/plugin-kubernetes-backend | Backend | 0.17.0 | Production | ./dynamic-plugins/dist/backstage-plugin-kubernetes-backend-dynamic |
| Disabled |
| Lighthouse | @backstage/plugin-lighthouse | Frontend | 0.4.20 | Community Support | ./dynamic-plugins/dist/backstage-plugin-lighthouse | Disabled | |
| Nexus Repository Manager | @janus-idp/backstage-plugin-nexus-repository-manager | Frontend | 1.6.10 | Red Hat Tech Preview | ./dynamic-plugins/dist/janus-idp-backstage-plugin-nexus-repository-manager | Disabled | |
| OCM | @janus-idp/backstage-plugin-ocm | Frontend | 4.1.8 | Production | ./dynamic-plugins/dist/janus-idp-backstage-plugin-ocm | Disabled | |
| OCM | @janus-idp/backstage-plugin-ocm-backend | Backend | 4.0.8 | Production | ./dynamic-plugins/dist/janus-idp-backstage-plugin-ocm-backend-dynamic |
| Disabled |
| PagerDuty | @pagerduty/backstage-plugin | Frontend | 0.12.0 | Community Support | ./dynamic-plugins/dist/pagerduty-backstage-plugin | Disabled | |
| Quay | @janus-idp/backstage-plugin-quay | Frontend | 1.7.8 | Production | ./dynamic-plugins/dist/janus-idp-backstage-plugin-quay | Disabled | |
| Quay | @janus-idp/backstage-scaffolder-backend-module-quay | Backend | 1.4.12 | Production | ./dynamic-plugins/dist/janus-idp-backstage-scaffolder-backend-module-quay-dynamic | Enabled | |
| RBAC | @janus-idp/backstage-plugin-rbac | Frontend | 1.24.1 | Production | ./dynamic-plugins/dist/janus-idp-backstage-plugin-rbac | Disabled | |
| Regex | @janus-idp/backstage-scaffolder-backend-module-regex | Backend | 1.4.12 | Production | ./dynamic-plugins/dist/janus-idp-backstage-scaffolder-backend-module-regex-dynamic | Enabled | |
| Scaffolder Relation Processor | @janus-idp/backstage-plugin-catalog-backend-module-scaffolder-relation-processor | Backend | 1.0.3 | Red Hat Tech Preview | ./dynamic-plugins/dist/janus-idp-backstage-plugin-catalog-backend-module-scaffolder-relation-processor-dynamic | Enabled | |
| Security Insights | @roadiehq/backstage-plugin-security-insights | Frontend | 2.3.17 | Community Support | ./dynamic-plugins/dist/roadiehq-backstage-plugin-security-insights | Disabled | |
| ServiceNow | @janus-idp/backstage-scaffolder-backend-module-servicenow | Backend | 1.4.14 | Red Hat Tech Preview | ./dynamic-plugins/dist/janus-idp-backstage-scaffolder-backend-module-servicenow-dynamic |
| Disabled |
| SonarQube | @backstage/plugin-sonarqube | Frontend | 0.7.17 | Community Support | ./dynamic-plugins/dist/backstage-plugin-sonarqube | Disabled | |
| SonarQube | @backstage/plugin-sonarqube-backend | Backend | 0.2.20 | Community Support | ./dynamic-plugins/dist/backstage-plugin-sonarqube-backend-dynamic |
| Disabled |
| SonarQube | @janus-idp/backstage-scaffolder-backend-module-sonarqube | Backend | 1.4.12 | Red Hat Tech Preview | ./dynamic-plugins/dist/janus-idp-backstage-scaffolder-backend-module-sonarqube-dynamic | Disabled | |
| TechDocs | @backstage/plugin-techdocs | Frontend | 1.10.4 | Production | ./dynamic-plugins/dist/backstage-plugin-techdocs | Enabled | |
| TechDocs | @backstage/plugin-techdocs-backend | Backend | 1.10.4 | Production | ./dynamic-plugins/dist/backstage-plugin-techdocs-backend-dynamic | Enabled | |
| Tech Radar | @backstage/plugin-tech-radar | Frontend | 0.7.4 | Community Support | ./dynamic-plugins/dist/backstage-plugin-tech-radar | Disabled | |
| Tekton | @janus-idp/backstage-plugin-tekton | Frontend | 3.7.7 | Production | ./dynamic-plugins/dist/janus-idp-backstage-plugin-tekton | Disabled | |
| Topology | @janus-idp/backstage-plugin-topology | Frontend | 1.21.10 | Production | ./dynamic-plugins/dist/janus-idp-backstage-plugin-topology | Disabled | |
| Utils | @roadiehq/scaffolder-backend-module-utils | Backend | 1.15.3 | Community Support | ./dynamic-plugins/dist/roadiehq-scaffolder-backend-module-utils-dynamic | Enabled |
- To configure Keycloak, see Installation and configuration of Keycloak.
- To configure Techdocs, see reference documentation. After experimenting with basic setup, use CI/CD to generate docs and an external cloud storage when deploying TechDocs for production use-case. See also this recommended deployment approach.
2.3. Configuring dynamic plugins with the Red Hat Developer Hub Operator
You can store the configuration for dynamic plugins in a ConfigMap object that your Backstage custom resource (CR) can reference.
If the pluginConfig field references environment variables, you must define the variables in your secrets-rhdh secret.
Procedure
- From the OpenShift Container Platform web console, select the ConfigMaps tab.
- Click Create ConfigMap.
From the Create ConfigMap page, select the YAML view option in Configure via and edit the file, if needed.
Example
ConfigMapobject using the GitHub dynamic pluginkind: ConfigMap apiVersion: v1 metadata: name: dynamic-plugins-rhdh data: dynamic-plugins.yaml: | includes: - dynamic-plugins.default.yaml plugins: - package: './dynamic-plugins/dist/backstage-plugin-catalog-backend-module-github-dynamic' disabled: false pluginConfig: catalog: providers: github: organization: "${GITHUB_ORG}" schedule: frequency: { minutes: 1 } timeout: { minutes: 1 } initialDelay: { seconds: 100 }- Click Create.
- Go to the Topology view.
Click on the overflow menu for the Red Hat Developer Hub instance that you want to use and select Edit Backstage to load the YAML view of the Red Hat Developer Hub instance.

Add the
dynamicPluginsConfigMapNamefield to yourBackstageCR. For example:apiVersion: rhdh.redhat.com/v1alpha1 kind: Backstage metadata: name: my-rhdh spec: application: # ... dynamicPluginsConfigMapName: dynamic-plugins-rhdh # ...- Click Save.
- Navigate back to the Topology view and wait for the Red Hat Developer Hub pod to start.
- Click the Open URL icon to start using the Red Hat Developer Hub platform with the new configuration changes.
Verification
Ensure that the dynamic plugins configuration has been loaded, by appending
/api/dynamic-plugins-info/loaded-pluginsto your Red Hat Developer Hub root URL and checking the list of plugins:Example list of plugins
[ { "name": "backstage-plugin-catalog-backend-module-github-dynamic", "version": "0.5.2", "platform": "node", "role": "backend-plugin-module" }, { "name": "backstage-plugin-techdocs", "version": "1.10.0", "role": "frontend-plugin", "platform": "web" }, { "name": "backstage-plugin-techdocs-backend-dynamic", "version": "1.9.5", "platform": "node", "role": "backend-plugin" }, ]
2.4. Installation of dynamic plugins using the Helm chart
You can deploy a Developer Hub instance using a Helm chart, which is a flexible installation method. With the Helm chart, you can sideload dynamic plugins into your Developer Hub instance without having to recompile your code or rebuild the container.
To install dynamic plugins in Developer Hub using Helm, add the following global.dynamic parameters in your Helm chart:
plugins: the dynamic plugins list intended for installation. By default, the list is empty. You can populate the plugins list with the following fields:-
package: a package specification for the dynamic plugin package that you want to install. You can use a package for either a local or an external dynamic plugin installation. For a local installation, use a path to the local folder containing the dynamic plugin. For an external installation, use a package specification from a public NPM repository. -
integrity(required for external packages): an integrity checksum in the form of<alg>-<digest>specific to the package. Supported algorithms includesha256,sha384andsha512. -
pluginConfig: an optional plugin-specificapp-configYAML fragment. See plugin configuration for more information. -
disabled: disables the dynamic plugin if set totrue. Default:false.
-
-
includes: a list of YAML files utilizing the same syntax.
The plugins list in the includes file is merged with the plugins list in the main Helm values. If a plugin package is mentioned in both plugins lists, the plugins fields in the main Helm values override the plugins fields in the includes file. The default configuration includes the dynamic-plugins.default.yaml file, which contains all of the dynamic plugins preinstalled in Developer Hub, whether enabled or disabled by default.
2.4.1. Obtaining the integrity checksum
To obtain the integrity checksum, enter the following command:
npm view <package name>@<version> dist.integrity
2.4.2. Example Helm chart configurations for dynamic plugin installations
The following examples demonstrate how to configure the Helm chart for specific types of dynamic plugin installations.
Configuring a local plugin and an external plugin when the external plugin requires a specific app-config
global:
dynamic:
plugins:
- package: <alocal package-spec used by npm pack>
- package: <external package-spec used by npm pack>
integrity: sha512-<some hash>
pluginConfig: ...
Disabling a plugin from an included file
global:
dynamic:
includes:
- dynamic-plugins.default.yaml
plugins:
- package: <some imported plugins listed in dynamic-plugins.default.yaml>
disabled: true
Enabling a plugin from an included file
global:
dynamic:
includes:
- dynamic-plugins.default.yaml
plugins:
- package: <some imported plugins listed in dynamic-plugins.custom.yaml>
disabled: false
Enabling a plugin that is disabled in an included file
global:
dynamic:
includes:
- dynamic-plugins.default.yaml
plugins:
- package: <some imported plugins listed in dynamic-plugins.custom.yaml>
disabled: false
2.4.3. Installing external dynamic plugins using a Helm chart
The NPM registry contains external dynamic plugins that you can use for demonstration purposes. For example, the following community plugins are available in the janus-idp organization in the NPMJS repository:
- Notifications (frontend and backend)
- Kubernetes actions (scaffolder actions)
To install the Notifications and Kubernetes actions plugins, include them in the Helm chart values in the global.dynamic.plugins list as shown in the following example:
global:
dynamic:
plugins:
- package: '@janus-idp/plugin-notifications-backend-dynamic@1.3.6'
# Integrity can be found at https://registry.npmjs.org/@janus-idp/plugin-notifications-backend-dynamic
integrity: 'sha512-Qd8pniy1yRx+x7LnwjzQ6k9zP+C1yex24MaCcx7dGDPT/XbTokwoSZr4baSSn8jUA6P45NUUevu1d629mG4JGQ=='
- package: '@janus-idp/plugin-notifications@1.1.12
'
# https://registry.npmjs.org/@janus-idp/plugin-notifications
integrity: 'sha512-GCdEuHRQek3ay428C8C4wWgxjNpNwCXgIdFbUUFGCLLkBFSaOEw+XaBvWaBGtQ5BLgE3jQEUxa+422uzSYC5oQ=='
pluginConfig:
dynamicPlugins:
frontend:
janus-idp.backstage-plugin-notifications:
appIcons:
- name: notificationsIcon
module: NotificationsPlugin
importName: NotificationsActiveIcon
dynamicRoutes:
- path: /notifications
importName: NotificationsPage
module: NotificationsPlugin
menuItem:
icon: notificationsIcon
text: Notifications
config:
pollingIntervalMs: 5000
- package: '@janus-idp/backstage-scaffolder-backend-module-kubernetes-dynamic@1.3.5'
# https://registry.npmjs.org/@janus-idp/backstage-scaffolder-backend-module-kubernetes-dynamic
integrity: 'sha512-19ie+FM3QHxWYPyYzE0uNdI5K8M4vGZ0SPeeTw85XPROY1DrIY7rMm2G0XT85L0ZmntHVwc9qW+SbHolPg/qRA=='
proxy:
endpoints:
/explore-backend-completed:
target: 'http://localhost:7017'
- package: '@dfatwork-pkgs/search-backend-module-explore-wrapped-dynamic@0.1.3-next.1'
# https://registry.npmjs.org/@dfatwork-pkgs/search-backend-module-explore-wrapped-dynamic
integrity: 'sha512-mv6LS8UOve+eumoMCVypGcd7b/L36lH2z11tGKVrt+m65VzQI4FgAJr9kNCrjUZPMyh36KVGIjYqsu9+kgzH5A=='
- package: '@dfatwork-pkgs/plugin-catalog-backend-module-test-dynamic@0.0.0'
# https://registry.npmjs.org/@dfatwork-pkgs/plugin-catalog-backend-module-test-dynamic
integrity: 'sha512-YsrZMThxJk7cYJU9FtAcsTCx9lCChpytK254TfGb3iMAYQyVcZnr5AA/AU+hezFnXLsr6gj8PP7z/mCZieuuDA=='2.5. Using a custom NPM registry for dynamic plugin packages
You can install external plugins in an air-gapped environment by setting up a custom NPM registry.
You can configure the NPM registry URL and authentication information for dynamic plugin packages using a Helm chart. For dynamic plugin packages obtained through npm pack, you can use a .npmrc file.
Using the Helm chart, add the .npmrc file to the NPM registry by creating a secret named dynamic-plugins-npmrc with the following content:
apiVersion: v1
kind: Secret
metadata:
name: dynamic-plugins-npmrc
type: Opaque
stringData:
.npmrc: |
registry=<registry-url>
//<registry-url>:_authToken=<auth-token>
...2.6. Basic configuration of dynamic plugins
Some dynamic plugins require environment variables to be set. If a mandatory environment variable is not set, and the plugin is enabled, then the application might fail at startup.
The mandatory environment variables for each plugin are listed in the Dynamic plugins support matrix.
Zib-bomb detection When installing some dynamic plugin containing large files, if the installation script considers the package archive to be a Zib-Bomb, the installation fails.
To increase the maximum permitted size of a file inside a package archive, you can increase the MAX_ENTRY_SIZE environment value of the deployment install-dynamic-plugins initContainer from the default size of 20000000 bytes.
2.7. Installing and using Ansibe plug-ins for Red Hat Developer Hub
Ansible plug-ins for Red Hat Developer Hub deliver an Ansible-specific portal experience with curated learning paths, push-button content creation, integrated development tools, and other opinionated resources.
The Ansible plug-ins are a Technology Preview feature only.
Technology Preview features are not supported with Red Hat production service level agreements (SLAs), might not be functionally complete, and Red Hat does not recommend using them for production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information on Red Hat Technology Preview features, see Technology Preview Features Scope.
Additional detail on how Red Hat provides support for bundled community dynamic plugins is available on the Red Hat Developer Support Policy page.
2.7.1. For administrators
To install and configure the Ansible plugins, see Installing Ansible plug-ins for Red Hat Developer Hub.
2.7.2. For users
To use the Ansible plugins, see Using Ansible plug-ins for Red Hat Developer Hub.
2.8. Installation and configuration of Keycloak
The Keycloak backend plugin, which integrates Keycloak into Developer Hub, has the following capabilities:
- Synchronization of Keycloak users in a realm.
- Synchronization of Keycloak groups and their users in a realm.
2.8.1. For administrators
2.8.1.1. Installation
The Keycloak plugin is pre-loaded in Developer Hub with basic configuration properties. To enable it, set the disabled property to false as follows:
global:
dynamic:
includes:
- dynamic-plugins.default.yaml
plugins:
- package: ./dynamic-plugins/dist/janus-idp-backstage-plugin-keycloak-backend-dynamic
disabled: false2.8.1.2. Basic configuration
To enable the Keycloak plugin, you must set the following environment variables:
-
KEYCLOAK_BASE_URL -
KEYCLOAK_LOGIN_REALM -
KEYCLOAK_REALM -
KEYCLOAK_CLIENT_ID -
KEYCLOAK_CLIENT_SECRET
2.8.1.3. Advanced configuration
Schedule configuration
You can configure a schedule in the app-config.yaml file, as follows:
catalog:
providers:
keycloakOrg:
default:
# ...
# highlight-add-start
schedule: # optional; same options as in TaskScheduleDefinition
# supports cron, ISO duration, "human duration" as used in code
frequency: { minutes: 1 }
# supports ISO duration, "human duration" as used in code
timeout: { minutes: 1 }
initialDelay: { seconds: 15 }
# highlight-add-end
If you have made any changes to the schedule in the app-config.yaml file, then restart to apply the changes.
Keycloak query parameters
You can override the default Keycloak query parameters in the app-config.yaml file, as follows:
catalog:
providers:
keycloakOrg:
default:
# ...
# highlight-add-start
userQuerySize: 500 # Optional
groupQuerySize: 250 # Optional
# highlight-add-endCommunication between Developer Hub and Keycloak is enabled by using the Keycloak API. Username and password, or client credentials are supported authentication methods.
The following table describes the parameters that you can configure to enable the plugin under catalog.providers.keycloakOrg.<ENVIRONMENT_NAME> object in the app-config.yaml file:
| Name | Description | Default Value | Required |
|---|---|---|---|
|
|
Location of the Keycloak server, such as | "" | Yes |
|
| Realm to synchronize |
| No |
|
| Realm used to authenticate |
| No |
|
| Username to authenticate | "" | Yes if using password based authentication |
|
| Password to authenticate | "" | Yes if using password based authentication |
|
| Client ID to authenticate | "" | Yes if using client credentials based authentication |
|
| Client Secret to authenticate | "" | Yes if using client credentials based authentication |
|
| Number of users to query at a time |
| No |
|
| Number of groups to query at a time |
| No |
When using client credentials, the access type must be set to confidential and service accounts must be enabled. You must also add the following roles from the realm-management client role:
-
query-groups -
query-users -
view-users
2.8.1.4. Limitations
If you have self-signed or corporate certificate issues, you can set the following environment variable before starting Developer Hub:
NODE_TLS_REJECT_UNAUTHORIZED=0
The solution of setting the environment variable is not recommended.
2.8.2. For users
2.8.2.1. Import of users and groups in Developer Hub using the Keycloak plugin
After configuring the plugin successfully, the plugin imports the users and groups each time when started.
If you set up a schedule, users and groups will also be imported.
After the first import is complete, you can select User to list the users from the catalog page:
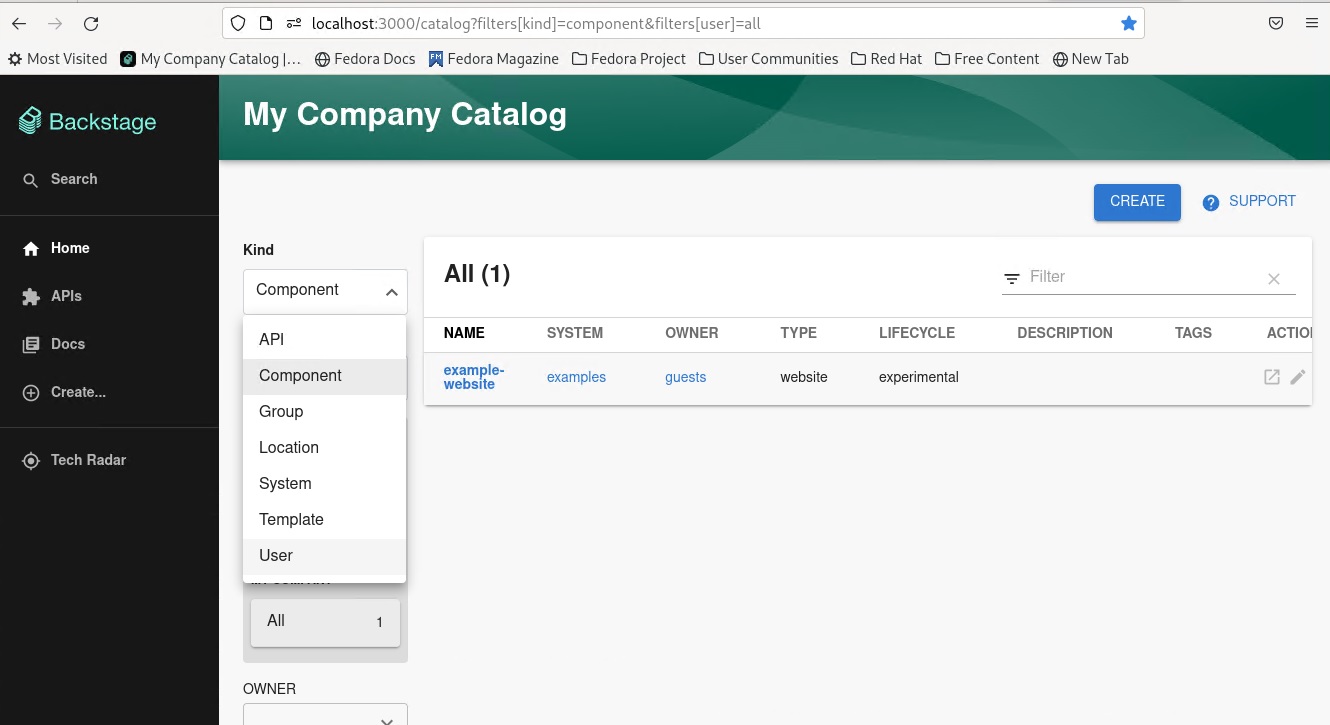
You can see the list of users on the page:
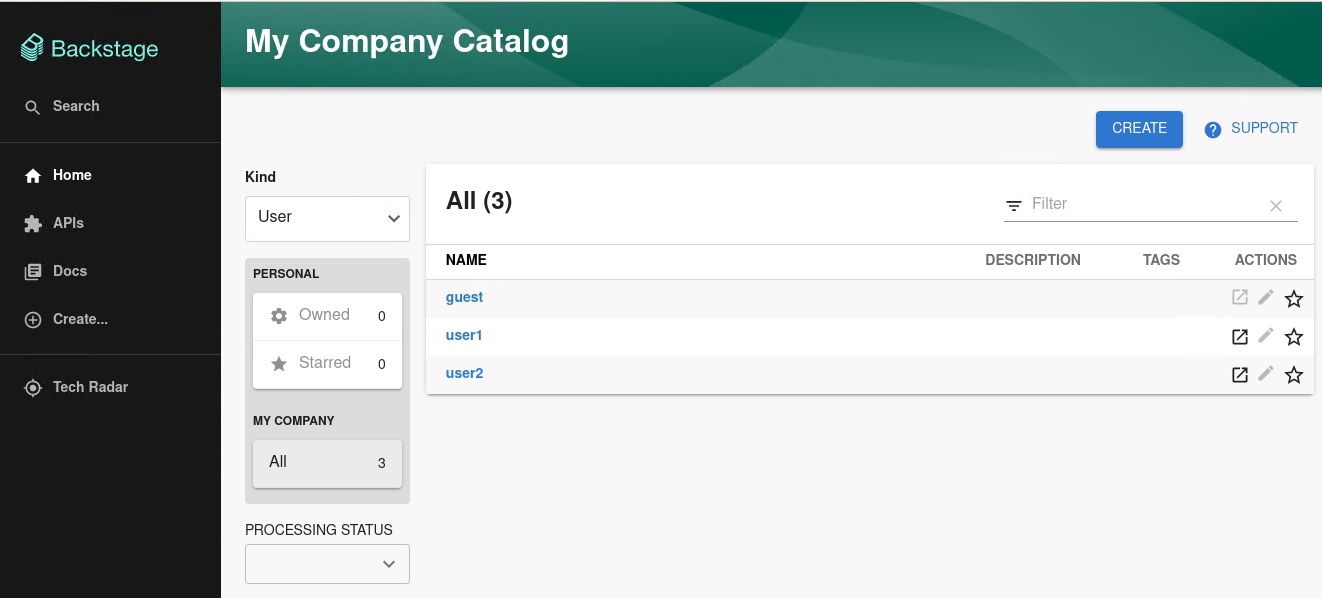
When you select a user, you can see the information imported from Keycloak:

You can also select a group, view the list, and select or view the information imported from Keycloak for a group:

2.9. Installation and configuration of Nexus Repository Manager
The Nexus Repository Manager plugin displays the information about your build artifacts in your Developer Hub application. The build artifacts are available in the Nexus Repository Manager.
The Nexus Repository Manager plugin is a Technology Preview feature only.
Technology Preview features are not supported with Red Hat production service level agreements (SLAs), might not be functionally complete, and Red Hat does not recommend using them for production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information on Red Hat Technology Preview features, see Technology Preview Features Scope.
Additional detail on how Red Hat provides support for bundled community dynamic plugins is available on the Red Hat Developer Support Policy page.
2.9.1. For administrators
2.9.1.1. Installing and configuring the Nexus Repository Manager plugin
Installation
The Nexus Repository Manager plugin is pre-loaded in Developer Hub with basic configuration properties. To enable it, set the disabled property to false as follows:
global:
dynamic:
includes:
- dynamic-plugins.default.yaml
plugins:
- package: ./dynamic-plugins/dist/janus-idp-backstage-plugin-nexus-repository-manager
disabled: falseConfiguration
Set the proxy to the desired Nexus Repository Manager server in the
app-config.yamlfile as follows:proxy: '/nexus-repository-manager': target: 'https://<NEXUS_REPOSITORY_MANAGER_URL>' headers: X-Requested-With: 'XMLHttpRequest' # Uncomment the following line to access a private Nexus Repository Manager using a token # Authorization: 'Bearer <YOUR TOKEN>' changeOrigin: true # Change to "false" in case of using self hosted Nexus Repository Manager instance with a self-signed certificate secure: trueOptional: Change the base URL of Nexus Repository Manager proxy as follows:
nexusRepositoryManager: # default path is `/nexus-repository-manager` proxyPath: /custom-pathOptional: Enable the following experimental annotations:
nexusRepositoryManager: experimentalAnnotations: trueAnnotate your entity using the following annotations:
metadata: annotations: # insert the chosen annotations here # example nexus-repository-manager/docker.image-name: `<ORGANIZATION>/<REPOSITORY>`,
2.9.2. For users
2.9.2.1. Using the Nexus Repository Manager plugin in Developer Hub
The Nexus Repository Manager is a front-end plugin that enables you to view the information about build artifacts.
Prerequisites
- Your Developer Hub application is installed and running.
- You have installed the Nexus Repository Manager plugin. For the installation process, see Section 2.9.1.1, “Installing and configuring the Nexus Repository Manager plugin”.
Procedure
- Open your Developer Hub application and select a component from the Catalog page.
Go to the BUILD ARTIFACTS tab.
The BUILD ARTIFACTS tab contains a list of build artifacts and related information, such as VERSION, REPOSITORY, REPOSITORY TYPE, MANIFEST, MODIFIED, and SIZE.

2.10. Installation and configuration of Tekton
You can use the Tekton plugin to visualize the results of CI/CD pipeline runs on your Kubernetes or OpenShift clusters. The plugin allows users to visually see high level status of all associated tasks in the pipeline for their applications.
2.10.1. For administrators
2.10.1.1. Installation
Prerequsites
-
You have installed and configured the
@backstage/plugin-kubernetesand@backstage/plugin-kubernetes-backenddynamic plugins. -
You have configured the Kubernetes plugin to connect to the cluster using a
ServiceAccount. The
ClusterRolemust be granted for custom resources (PipelineRuns and TaskRuns) to theServiceAccountaccessing the cluster.NoteIf you have the RHDH Kubernetes plugin configured, then the
ClusterRoleis already granted.-
To view the pod logs, you have granted permissions for
pods/log. You can use the following code to grant the
ClusterRolefor custom resources and pod logs:kubernetes: ... customResources: - group: 'tekton.dev' apiVersion: 'v1' plural: 'pipelineruns' - group: 'tekton.dev' apiVersion: 'v1' ... apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: backstage-read-only rules: - apiGroups: - "" resources: - pods/log verbs: - get - list - watch ... - apiGroups: - tekton.dev resources: - pipelineruns - taskruns verbs: - get - listYou can use the prepared manifest for a read-only
ClusterRole, which provides access for both Kubernetes plugin and Tekton plugin.Add the following annotation to the entity’s
catalog-info.yamlfile to identify whether an entity contains the Kubernetes resources:annotations: ... backstage.io/kubernetes-id: <BACKSTAGE_ENTITY_NAME>
You can also add the
backstage.io/kubernetes-namespaceannotation to identify the Kubernetes resources using the defined namespace.annotations: ... backstage.io/kubernetes-namespace: <RESOURCE_NS>
Add the following annotation to the
catalog-info.yamlfile of the entity to enable the Tekton related features in RHDH. The value of the annotation identifies the name of the RHDH entity:annotations: ... janus-idp.io/tekton : <BACKSTAGE_ENTITY_NAME>
Add a custom label selector, which RHDH uses to find the Kubernetes resources. The label selector takes precedence over the ID annotations.
annotations: ... backstage.io/kubernetes-label-selector: 'app=my-app,component=front-end'
Add the following label to the resources so that the Kubernetes plugin gets the Kubernetes resources from the requested entity:
labels: ... backstage.io/kubernetes-id: <BACKSTAGE_ENTITY_NAME>
NoteWhen you use the label selector, the mentioned labels must be present on the resource.
Procedure
The Tekton plugin is pre-loaded in RHDH with basic configuration properties. To enable it, set the disabled property to false as follows:
global: dynamic: includes: - dynamic-plugins.default.yaml plugins: - package: ./dynamic-plugins/dist/janus-idp-backstage-plugin-tekton disabled: false
2.10.2. For users
2.10.2.1. Using the Tekton plugin in RHDH
You can use the Tekton front-end plugin to view PipelineRun resources.
Prerequisites
- You have installed the Red Hat Developer Hub (RHDH).
- You have installed the Tekton plugin. For the installation process, see Installing and configuring the Tekton plugin.
Procedure
- Open your RHDH application and select a component from the Catalog page.
Go to the CI tab.
The CI tab displays the list of PipelineRun resources associated with a Kubernetes cluster. The list contains pipeline run details, such as NAME, VULNERABILITIES, STATUS, TASK STATUS, STARTED, and DURATION.
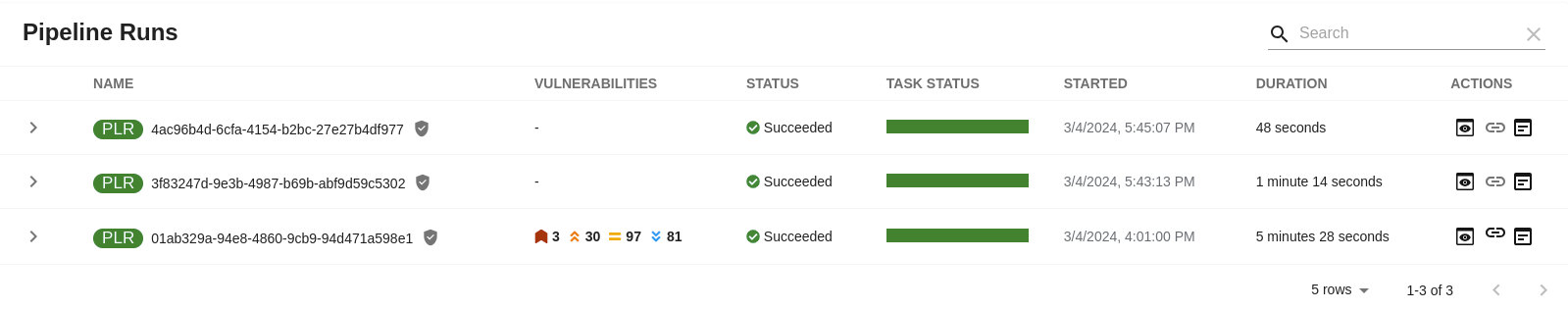
Click the expand row button besides PipelineRun name in the list to view the PipelineRun visualization. The pipeline run resource includes tasks to complete. When you hover the mouse pointer on a task card, you can view the steps to complete that particular task.

2.11. Enabling and configuring Argo CD plugin
You can use the Argo CD plugin to visualize the Continuous Delivery (CD) workflows in OpenShift GitOps. This plugin provides a visual overview of the application’s status, deployment details, commit message, author of the commit, container image promoted to environment and deployment history.
2.11.1. For administrators
2.11.1.1. Enabling Argo CD plugin
Prerequisites
Add Argo CD instance information to your
app-config.yamlconfigmap as shown in the following example:argocd: appLocatorMethods: - type: 'config' instances: - name: argoInstance1 url: https://argoInstance1.com username: ${ARGOCD_USERNAME} password: ${ARGOCD_PASSWORD} - name: argoInstance2 url: https://argoInstance2.com username: ${ARGOCD_USERNAME} password: ${ARGOCD_PASSWORD}Add the following annotation to the entity’s
catalog-info.yamlfile to identify the Argo CD applications.annotations: ... # The label that Argo CD uses to fetch all the applications. The format to be used is label.key=label.value. For example, rht-gitops.com/janus-argocd=quarkus-app. argocd/app-selector: '${ARGOCD_LABEL_SELECTOR}'(Optional) Add the following annotation to the entity’s
catalog-info.yamlfile to switch between Argo CD instances as shown in the following example:annotations: ... # The Argo CD instance name used in `app-config.yaml`. argocd/instance-name: '${ARGOCD_INSTANCE}'NoteIf you do not set this annotation, the Argo CD plugin defaults to the first Argo CD instance configured in
app-config.yaml.
Procedure
Add the following to your dynamic-plugins ConfigMap to enable the Argo CD plugin.
global: dynamic: includes: - dynamic-plugins.default.yaml plugins: - package: ./dynamic-plugins/dist/roadiehq-backstage-plugin-argo-cd-backend-dynamic disabled: false - package: ./dynamic-plugins/dist/janus-idp-backstage-plugin-argocd disabled: false
2.11.2. For Users
Prerequisites
- You have enabled the Argo CD plugin in Red Hat Developer Hub RHDH.
Procedures
- Select the Catalog tab and choose the component that you want to use.
Select the CD tab to view insights into deployments managed by Argo CD.

Select an appropriate card to view the deployment details (for example, commit message, author name, and deployment history).

-
Click the link icon (
 ) to open the deployment details in Argo CD.
) to open the deployment details in Argo CD.
-
Click the link icon (
Select the Overview tab and navigate to the Deployment summary section to review the summary of your application’s deployment across namespaces. Additionally, select an appropriate Argo CD app to open the deployment details in Argo CD, or select a commit ID from the Revision column to review the changes in GitLab or GitHub.

Additional resources
- For more information on dynamic plugins, see Dynamic plugin installation.