Configuration and schema reference
Core server configuration attributes and server schema reference
Abstract
Providing feedback on Red Hat Directory Server
We appreciate your input on our documentation and products. Please let us know how we could make it better. To do so:
For submitting feedback on the Red Hat Directory Server documentation through Jira (account required):
- Go to the Red Hat Issue Tracker.
- Enter a descriptive title in the Summary field.
- Enter your suggestion for improvement in the Description field. Include links to the relevant parts of the documentation.
- Click Create at the bottom of the dialogue.
For submitting feedback on the Red Hat Directory Server product through Jira (account required):
- Go to the Red Hat Issue Tracker.
- On the Create Issue page, click .
- Fill in the Summary field.
- Select the component in the Component field.
Fill in the Description field including:
- The version number of the selected component.
- Steps to reproduce the problem or your suggestion for improvement.
- Click Create.
Chapter 1. File locations overview
Red Hat Directory Server is compatible with the Filesystem Hierarchy Standards (FHS). For further details about the FHS, see FHS Specification.
1.1. Directory Server instance-independent files and directories
The instance-independent default files and directory locations for the Directory Server include:
| Type | Location |
|---|---|
| Command-line utilities |
|
| Systemd unit files |
|
| Self-Signed Certificate Authority |
|
1.2. Directory Server instance-specific files and directories
To separate multiple instances running on the same host, certain files and directories contain the name of the instance. You set the instance name during the Directory Server setup. By default, this is the host name without domain name. For example, if your fully-qualified domain name is server.example.com, the default instance name is server.
The instance-independent default file and directory locations for the Directory Server include:
| Type | Location |
|---|---|
| Backup files |
|
| Configuration files |
|
| Certificate and key databases |
|
| Database files |
|
| LDIF files |
|
| Lock files |
|
| Log files |
|
| PID file |
|
| Systemd unit files |
|
1.2.1. Configuration files
Each Directory Server instance stores its configuration files in the /etc/dirsrv/slapd-instance_name_/ directory.
The configuration information for Red Hat Directory Server is stored as LDAP entries in the directory. Therefore, you must change the server configuration through the server instead of editing configuration files. The principal advantage of configuration storage is that a directory administrator can reconfigure the server using LDAP while the server is still running, avoiding the need to shut the server down for most configuration changes.
1.2.2. Overview of the Directory Server configuration
When the Directory Server is set up, the server stores the default configuration as a series of LDAP entries within the directory, under the cn=config sub-tree. When you start the server, the server reads the contents of the cn=config sub-tree from the dse.ldif file that is in the LDIF format. The dse.ldif file contains all of the server configuration information and has the following names:
-
dse.ldif. The latest version of this file. -
dse.ldif.bak. The version prior to the last modification. -
dse.ldif.startOK. The latest file with which the server successfully started.
Most features of the Directory Server are designed as discrete modules that plug into the core server. The details of the internal configuration for each plug-in are contained in separate entries under cn=plugins,cn=config sub-tree. For example, the configuration of the Telephone Syntax plug-in is contained in the cn=Telephone Syntax,cn=plugins,cn=config.
Similarly, database-specific configuration is stored under cn=ldbm database,cn=plugins,cn=config for local databases and cn=chaining database,cn=plugins,cn=config for database links.
The following diagram shows where the configuration data is placed under the cn=config directory tree.
Figure 1.1. Configuration data sub-tree
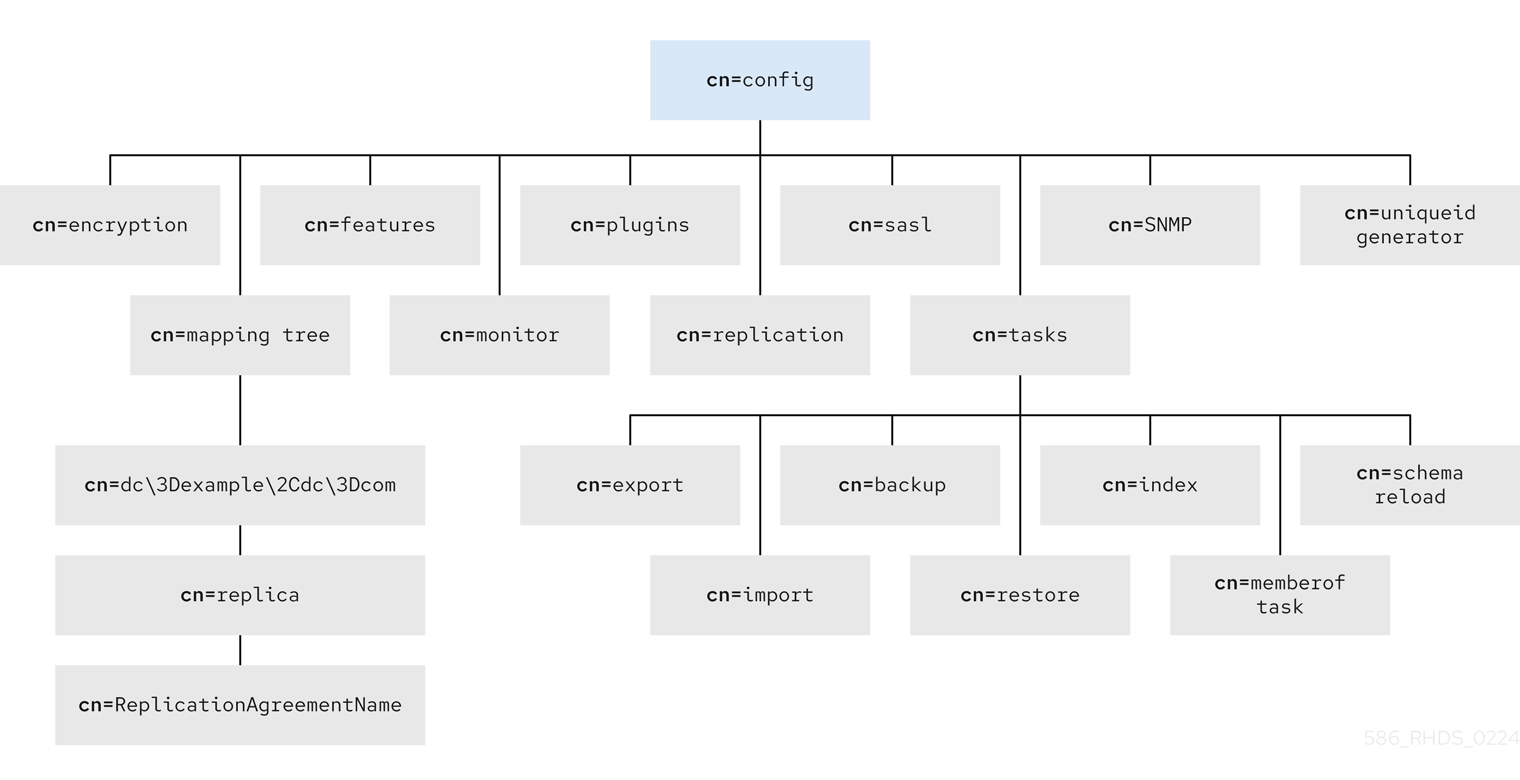
The dc\3Dexample\2Cdc\3Dcom value represents the dc=example,dc=com DN with escaped characters.
1.2.2.1. LDIF and schema configuration files
Directory Server stores configuration data in LDIF files in the /etc/dirsrv/slapd-instance_name directory. If a server name is phonebook, then for a Directory Server, the configuration LDIF files are all stored under /etc/dirsrv/slapd-phonebook.
This directory also contains other server instance-specific configuration files.
Schema configuration is also stored in LDIF format in the following directories:
-
/etc/dirsrv/instance_name/schema/for instance-specific schema. -
/usr/share/dirsrv/schema/for default schema. -
/etc/dirsrv/schema/for schema that overrides the default schema.
Previously, schema configuration files were stored in the /etc/dirsrv/schema directory only.
The following table lists the configuration files that are supplied with the Directory Server, including those for the compatible servers schema. Each file is preceded by a number which indicates the order in which they should be loaded (ascending numerically, then alphabetically).
| Configuration Filename | Purpose |
|---|---|
| dse.ldif |
Contains front-end directory-specific entries (DSE) created by the directory at the server startup. The entries include the Root DSE ( |
| 00core.ldif |
Contains schema definitions, such as
The rest of the schema used by users, features, and applications is located in the |
| 02common.ldif |
The
Modifying the file causes interoperability problems. You must add user-defined attributes through the Directory Server web console. |
| 05rfc2247.ldif | Schema from RFC 2247, Using Domains in LDAP/X500 Distinguished Names, and the related pilot schema. |
| 05rfc2927.ldif |
Schema from RFC 2927, MIME Directory Profile for LDAP Schema. Contains the |
| 06inetorgperson.ldif |
Contains |
| 10presence.ldif | Legacy. Schema for instant messaging presence (online) information. The file lists the default object classes with the allowed attributes that must be added to a user entry in order for instant-messaging presence information to be available for that user. |
| 10rfc2307.ldif | Schema from RFC 2307, An Approach for Using LDAP as a Network Information Service.
The |
| 20subscriber.ldif |
Contains new schema elements and the Nortel subscriber interoperability specification. Also contains the |
| 25java-object.ldif | Schema from RFC 2713, Schema for Representing Java® Objects in an LDAP Directory. |
| 28pilot.ldif |
Contains pilot directory schema from RFC 1274, which is no longer recommended for new deployments. Future RFCs that succeed RFC 1274 may deprecate some or all of |
| 30ns-common.ldif | Schema that contains objects classes and attributes common to the Directory Server web console framework. |
| 50ns-admin.ldif | Schema used by Red Hat Administration Server. |
| 50ns-certificate.ldif | Schema for Red Hat Certificate Management System. |
| 50ns-directory.ldif | Contains additional configuration schema used by Directory Server 4.12 and earlier versions of the directory, which is no longer applicable to the current releases of Directory Server. This schema is required for replication between Directory Server 4.12 and the current releases. |
| 50ns-mail.ldif | Schema used by Netscape Messaging Server to define mail users and mail groups. |
| 50ns-value.ldif | Schema for servers value item attributes. |
| 50ns-web.ldif | Schema for Netscape Web Server. |
| 60pam-plugin.ldif | Reserved for future use. |
| 99user.ldif | User-defined schema that Directory Server replication consumers maintain. The schema contains the attributes and object classes from the suppliers. |
1.2.2.2. The dse.ldif server configuration file
The dse.ldif file contains all configuration information including directory-specific entries (DSE) created by the directory at server startup, such as entries related to the database. The file includes the root Directory Server entry (or Root DSE, named by "") and the contents of the cn=config sub-tree.
When the server generates the dse.ldif file, the server lists the entries in the order that the entries appear in the directory under cn=config, which is usually the same order in which an LDAP search of sub-tree scope for the cn=config base returns the entries.
The dse.ldif file also contains the cn=monitor entry, which is mostly read-only, but can have ACIs set on it.
The dse.ldif file does not contain every attribute in cn=config entry. If the administrator did not set the attribute and it has a default value, the server does not write this attribute to the dse.ldif file. To see every attribute in the cn=config entry, use the ldapsearch utility.
Configuration attributes
Each configuration entry, such as cn=config, contains attribute-value pairs set for this entry.
The following example part of the dse.ldif file shows that schema checking was enabled by setting the nsslapd-schemacheck attribute to on.
Configuration of plug-in functionality
The configuration for each part of Directory Server plug-in functionality has its own separate entry and set of attributes under the cn=plugins,cn=config sub-tree.
The following example shows the example configuration for the Telephone Syntax plug-in.
A plug-in configuration contains attributes that are common to all plug-ins and attributes that are specific to this plug-in. To check which attributes Directory Server currently uses, run the ldapsearch command on the cn=config sub-tree.
For more information about supported plug-ins and their configuration information, see Plug-in implemented server functionality reference.
Configuration of databases
The cn=UserRoot,cn=ldbm database,cn=plugins,cn=config sub-tree contains configuration data for the databases that contains the default suffix Directory Server creates during setup.
The cn=UserRoot sub-tree and its children have many attributes used to configure different database settings, like the cache sizes, the paths to the index files and transaction logs, entries and attributes for monitoring and statistics, and database indexes.
Configuration of indexes
Indexes configuration information is stored as entries in the Directory Server under the following sub-directories:
-
cn=index,cn=UserRoot,cn=ldbm database,cn=plugins,cn=config -
cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config
For general information about indexes, see Managing indexes documentation.
For information about the index configuration attributes, see Section 6.4.1, “Database attributes under cn=config,cn=ldbm database,cn=plugins,cn=config”.
1.2.3. Database files
Every Directory Server instance contains the /var/lib/dirsrv/slapd-instance/db directory for storing all of the database files. A sample listing of the /var/lib/dirsrv/slapd-instance/db directory contents is illustrated below.
Database directory contents
db.001 db.002 __db.003 DBVERSION log.0000000001 userroot/
db.001 db.002 __db.003 DBVERSION log.0000000001 userroot/-
db.00xfiles. Used internally by the database and you must not move, delete, or modify these files in any way. -
log.xxxxxxxxxxfiles. Used for storing the transaction logs per database. -
DBVERSION. Used for storing the version of the database. -
userRoot. Stores the user-defined suffixs (user-defined databases) created at setup, for example,dc=example,dc=com.
When you create a new database, for example testRoot, to store the directory tree under a new suffix, the directory named testRoot also appears in the /var/lib/dirsrv/slapd-instance/db directory.
The following example lists of the userRoot directory contents.
The userroot database directory contents
The userroot sub-directory contains the following files:
-
ancestorid.db. Contains a list of IDs to find the ID of the entry ancestor. -
entrydn.db. Contains a list of full DNs to find any ID. -
id2entry.db. Contains the actual directory database entries. All other database files can be recreated from this one, if necessary. -
nsuniqueid.db. Contains a list of unique IDs to find any ID. -
numsubordinates.db. Contains IDs that have child entries. -
objectclass.db. Contains a list of IDs which have a particular object class. -
parentid.db. Contains a list of IDs to find the ID of the parent.
1.3. LDIF files
Directory Server stores LDIF-related files in the /usr/share/dirsrv/data/ directory.
LDIF directory contents
European.ldif Example.ldif Example-roles.ldif Example-views.ldif
European.ldif
Example.ldif
Example-roles.ldif
Example-views.ldifThe example contains the following files:
-
European.ldif. Contains European character examples. -
Example.ldif. Is an example LDIF file. -
Example-roles.ldif. Is an example LDIF file similar toExample.ldif, except that it uses roles and class of service instead of groups for setting access control and resource limits for directory administrators.
The LDIF files exported by db2ldif or db2ldif.pl scripts in the instance directory are stored in /var/lib/dirsrv/slapd-instance_name/ldif/.
1.4. Lock files
Every Directory Server instance contains a /var/lock/dirsrv/slapd-instance_name/ directory for storing lock-related files.
The following example lists the locks directory contents.
Lock directory contents
exports/ imports/ server/
exports/ imports/ server/The lock mechanisms control how many copies of the Directory Server process can be running at once:
-
If the server performs an import, a lock is placed in the
imports/directory to prevent any otherns-slapd(normal),ldif2db(another import), ordb2ldif(export) operations from running. -
If the server is running as normal, the lock is placed in the
server/directory, which prevents only import operations. -
If the server performs an export, the lock is placed in the
exports/directory. This allows normal server operations, but prevents imports.
The number of available locks can affect overall Directory Server performance. The number of locks is set in the nsslapd-db-locks attribute. For more details, see The nsslapd-db-locks attribute description.
1.5. Log files
Every Directory Server instance stores log files in the /var/log/dirsrv/slapd-instance_name/ directory.
Log directory contents
The content of the access, audit, error, security log files depends on the log configuration. The stats file is located at the /var/run/dirsrv/slapd-instance_name.stats/ directory.
The stats file is a memory-mapped file that cannot be read by an editor. It contains data that the Directory Server SNMP data collection component collect. This data is read by the SNMP sub-agent in response to SNMP attribute queries and is communicated to the SNMP master agent responsible for handling Directory Server SNMP requests.
For overview of all log files, refer to Log files reference chapter.
1.6. PID files
When the server is up and running, the slapd-serverID.pid and slapd-serverID.startpid files are created in the /var/run/dirsrv/ directory. Both files store the server process ID.
1.7. Backup files
Every Directory Server instance contains the following directories to store backup-related files:
-
/var/lib/dirsrv/slapd-instance_name/bak/. Contains backup copies of the database. Each backup is dated with the instance name, time and date of the database backup, for example,instance_name-2023_05_04_18_01_23. -
/var/lib/dirsrv/slapd-instance_name/bak/config_files/. Contains backed up configuration files, the certificate database, and custom schema files.
Chapter 2. Core server configuration attributes
This section contains reference information on the configuration attributes that are relevant to the core server functionality. For information on changing server configuration, see Section 2.2.1.2, "Accessing and Modifying Server Configuration". For a list of server features that are implemented as plug-ins, see Section 4.1, "Server Plug-in Functionality Reference". For help with implementing custom server functionality, contact Directory Server support.
The configuration information stored in the dse.ldif file is organized as an information tree under the general configuration entry cn=config.
Most of these configuration tree nodes are covered in the following sections.
The cn=plugins node is covered in Chapter 4, Plug-in Implemented Server Functionality Reference. The description of each attribute contains details such as the DN of its directory entry, its default value, the valid range of values, and an example of its use.
Some of the entries and attributes described in this chapter may change in future releases of the product.
2.1. cn=config
Directory Server stores general configuration entries in the cn=config entry. This entry is an instance of the nsslapdConfig object class, which in turn inherits from the extensibleObject object class.
2.1.1. nsslapd-accesslog
This attribute specifies the path and filename of the log used to record each LDAP access. The following information is recorded by default in the log file:
- IP address (IPv4 or IPv6) of the client machine that accessed the database.
- Operations performed (for example, search, add, and modify).
- Result of the access (for example, the number of entries returned or an error code).
For access logging to be enabled, this attribute must have a valid path and parameter, and the nsslapd-accesslog-logging-enabled configuration attribute must be switched to on. The table lists the four possible combinations of values for these two configuration attributes and their outcome in terms of disabling or enabling of access logging.
| Attribute | Value | Logging enabled or disabled |
|---|---|---|
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | on empty string | Disabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | on filename | Enabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | off empty string | Disabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | off filename | Disabled |
The nsslapd-accesslog parameters description:
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid filename. |
| Default Value | /var/log/dirsrv/slapd-instance/access |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog: /var/log/dirsrv/slapd-instance/access |
2.1.2. nsslapd-accesslog-compress
Directory Server does not compress the access log by default. Set nsslapd-accesslog-compress to on to enable the access log compression when Directory Server rotates the log.
You do not need to restart the server to apply changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-compress: on |
2.1.3. nsslapd-accesslog-level
This attribute controls what is logged to the access log.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | * 0 - No access logging * 4 - Logging for internal access operations * 256 - Logging for connections, operations, and results * 512 - Logging for access to an entry and referrals
* These values can be added together to provide the exact type of logging required; for example, |
| Default Value | 256 |
| Syntax | Integer |
| Example | nsslapd-accesslog-level: 256 |
2.1.4. nsslapd-accesslog-list
This read-only attribute, which cannot be set, provides a list of access log files used in access log rotation.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-list: accesslog2,accesslog3 |
2.1.5. nsslapd-accesslog-logbuffering
When set to off, the server writes all access log entries directly to disk. Buffering allows the server to use access logging even when under a heavy load without impacting performance. However, when debugging, it is sometimes useful to disable buffering in order to see the operations and their results right away instead of having to wait for the log entries to be flushed to the file. Disabling log buffering can severely impact performance in heavily loaded servers.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-logbuffering: off |
2.1.6. nsslapd-accesslog-logexpirationtime
This attribute specifies the maximum age that a log file is allowed to reach before it is deleted. This attribute supplies only the number of units. The units are provided by the nsslapd-accesslog-logexpirationtimeunit attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) A value of -1 or 0 means that the log never expires. |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logexpirationtime: 2 |
2.1.7. nsslapd-accesslog-logexpirationtimeunit
This attribute specifies the units for nsslapd-accesslog-logexpirationtime attribute. If the unit is unknown by the server, then the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day |
| Default Value | month |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-logexpirationtimeunit: week |
2.1.8. nsslapd-accesslog-logging-enabled
Disables and enables accesslog logging but only in conjunction with the nsslapd-accesslog attribute that specifies the path and parameter of the log used to record each database access.
For access logging to be enabled, this attribute must be switched to on, and the nsslapd-accesslog configuration attribute must have a valid path and parameter. The table lists the four possible combinations of values for these two configuration attributes and their outcome in terms of disabling or enabling of access logging.
| Attribute | Value | Logging Enabled or Disabled |
|---|---|---|
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | on empty string | Disabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | on filename | Enabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | off empty string | Disabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | off filename | Disabled |
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-logging-enabled: off |
2.1.9. nsslapd-accesslog-logmaxdiskspace
This attribute specifies the maximum amount of disk space in megabytes that the access logs are allowed to consume. If this value is exceeded, the oldest access log is deleted.
When setting a maximum disk space, consider the total number of log files that can be created due to log file rotation. Also, remember that there are three different log files (access log, audit log, and error log) maintained by Directory Server, each of which consumes disk space. Compare these considerations to the total amount of disk space for the access log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the disk space allowed to the access log is unlimited in size. |
| Default Value | 500 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logmaxdiskspace: 500 |
2.1.10. nsslapd-accesslog-logminfreediskspace
This attribute sets the minimum allowed free disk space in megabytes. When the amount of free disk space falls below the value specified on this attribute, the oldest access logs are deleted until enough disk space is freed to satisfy this attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logminfreediskspace: -1 |
2.1.11. nsslapd-accesslog-logrotationsync-enabled
This attribute sets whether access log rotation is to be synchronized with a particular time of the day. Synchronizing log rotation this way can generate log files at a specified time during a day, such as midnight to midnight every day. This makes analysis of the log files much easier because they then map directly to the calendar.
For access log rotation to be synchronized with time-of-day, this attribute must be enabled with the nsslapd-accesslog-logrotationsynchour and nsslapd-accesslog-logrotationsyncmin attribute values set to the hour and minute of the day for rotating log files.
For example, to rotate access log files every day at midnight, enable this attribute by setting its value to on, and then set the values of the nsslapd-accesslog-logrotationsynchour and nsslapd-accesslog-logrotationsyncmin attributes to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-logrotationsync-enabled: on |
2.1.12. nsslapd-accesslog-logrotationsynchour
This attribute sets the hour of the day for rotating access logs. This attribute must be used in conjunction with nsslapd-accesslog-logrotationsync-enabled and nsslapd-accesslog-logrotationsyncmin attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 23 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logrotationsynchour: 23 |
2.1.13. nsslapd-accesslog-logrotationsyncmin
This attribute sets the minute of the day for rotating access logs. This attribute must be used in conjunction with nsslapd-accesslog-logrotationsync-enabled and nsslapd-accesslog-logrotationsynchour attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 59 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logrotationsyncmin: 30 |
2.1.14. nsslapd-accesslog-logrotationtime
This attribute sets the time between access log file rotations. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-accesslog-logrotationtimeunit attribute.
Directory Server rotates the log at the first write operation after the configured interval has expired, regardless of the size of the log.
Although it is not recommended for performance reasons to specify no log rotation since the log grows indefinitely, there are two ways of specifying this. Either set the nsslapd-accesslog-maxlogsperdir attribute value to 1 or set the nsslapd-accesslog-logrotationtime attribute to -1. The server checks the nsslapd-accesslog-maxlogsperdir attribute first, and, if this attribute value is larger than 1, the server then checks the nsslapd-accesslog-logrotationtime attribute. See Section 2.1.17, “nsslapd-accesslog-maxlogsperdir” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the time between access log file rotation is unlimited. |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logrotationtime: 100 |
2.1.15. nsslapd-accesslog-logrotationtimeunit
This attribute sets the units for the nsslapd-accesslog-logrotationtime attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day | hour | minute |
| Default Value | day |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-logrotationtimeunit: week |
2.1.16. nsslapd-accesslog-maxlogsize
This attribute sets the maximum access log size in megabytes. When this value is reached, the access log is rotated. That means the server starts writing log information to a new log file. If the nsslapd-accesslog-maxlogsperdir attribute is set to 1, the server ignores this attribute.
When setting a maximum log size, take into consideration the following:
- The total number of log files that can be created due to the log file rotation.
- The Directory Server maintains five different log files: access log, audit log, audit fail log, error log, security log. Each log file consumes disk space.
Compare these considerations to the total amount of disk space you want to set for the access log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means the log file is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-accesslog-maxlogsize: 100 |
2.1.17. nsslapd-accesslog-maxlogsperdir
This attribute sets the total number of access logs that can be contained in the directory where the access log is stored. Each time the access log is rotated, a new log file is created. When the number of files contained in the access log directory exceeds the value stored in this attribute, then the oldest version of the log file is deleted. For performance reasons, do not set this value to 1 because the server does not rotate the log, and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-accesslog-logrotationtime attribute to establish whether log rotation is specified. If the nsslapd-accesslog-logrotationtime attribute has a value of -1, then there is no log rotation. See Section 2.1.14, “nsslapd-accesslog-logrotationtime” for more information.
Depending on the values set in nsslapd-accesslog-logminfreediskspace and nsslapd-accesslog-maxlogsize, the actual number of logs could be less than what you configure in nsslapd-accesslog-maxlogsperdir. For example, if nsslapd-accesslog-maxlogsperdir uses the default (10 files) and you set nsslapd-accesslog-logminfreediskspace to 500 MB and nsslapd-accesslog-maxlogsize to 100 MB, Directory Server keeps only 5 access log files.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 10 |
| Syntax | Integer |
| Example | nsslapd-accesslog-maxlogsperdir: 10 |
2.1.18. nsslapd-accesslog-mode
This attribute sets the access mode or file permission with which access log files are to be created. The valid values are any combination of 000 to 777 (these mirror the numbered or absolute UNIX file permissions). The value must be a 3-digit number, the digits varying from 0 through 7:
-
0- None -
1- Execute only -
2- Write only -
3- Write and execute -
4- Read only -
5- Read and execute -
6- Read and write -
7- Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the second digit represents the group’s permissions, and the third digit represents everyone’s permissions. When changing the default value, remember that 000 does not allow access to the logs and that allowing write permissions to everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log rotates to a new file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 000 through 777 |
| Default Value | 600 |
| Syntax | Integer |
| Example | nsslapd-accesslog-mode: 600 |
2.1.19. nsslapd-allow-anonymous-access
If a user attempts to connect to Directory Server without supplying any bind DN or password, this is an anonymous bind. Anonymous binds simplify common search and read operations, like checking the directory for a phone number or email address, by not requiring users to authenticate to the directory first.
However, there are risks with anonymous binds. Adequate ACIs must be in place to restrict access to sensitive information and to disallow actions like modifies and deletes. Additionally, anonymous binds can be used for denial of service attacks or for malicious people to gain access to the server.
Anonymous binds can be disabled to increase security (off). By default, anonymous binds are allowed (on) for search and read operations. This allows access to regular directory entries, which includes user and group entries as well as configuration entries like the root DSE. A third option, rootdse, allows anonymous search and read access to search the root DSE itself, but restricts access to all other directory entries.
Optionally, resource limits can be placed on anonymous binds using the nsslapd-anonlimitsdn attribute as described in Section 2.1.23, “nsslapd-anonlimitsdn”.
Changes to this value will not take effect until the server is restarted.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off | rootdse |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-allow-anonymous-access: on |
2.1.20. nsslapd-allowed-sasl-mechanisms
Per default, the root DSE lists all mechanisms the SASL library supports. However in some environments only certain ones are preferred. The nsslapd-allowed-sasl-mechanisms attribute allows you to enable only some defined SASL mechanisms.
The mechanism names must consist of uppercase letters, numbers, and underscores. Each mechanism can be separated by commas or spaces.
The EXTERNAL mechanism is actually not used by any SASL plug-in. It is internal to the server, and is mainly used for TLS client authentication. Hence, the EXTERNAL mechanism cannot be restricted or controlled. It will always appear in the supported mechanisms list, regardless what is set in the nsslapd-allowed-sasl-mechanisms attribute.
This setting does not require a server restart to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid SASL mechanism |
| Default Value | None (all SASL mechanisms allowed) |
| Syntax | DirectoryString |
| Example | nsslapd-allowed-sasl-mechanisms: GSSAPI, DIGEST-MD5, OTP |
2.1.21. nsslapd-allow-hashed-passwords
This parameter disables the pre-hashed password checks. By default, the Directory Server does not allow pre-hashed passwords to be set by anyone other than the Directory Manager. You can delegate this privilege to other users when you add them to the Password Administrators group. However in some scenarios, like when the replication partner already controls the pre-hashed passwords checking, this feature has to be disabled on the Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-allow-hashed-passwords: off |
2.1.22. nsslapd-allow-unauthenticated-binds
Unauthenticated binds are connections to Directory Server where a user supplies an empty password. Using the default settings, Directory Server denies access in this scenario for security reasons.
Red Hat recommends not enabling unauthenticated binds. This authentication method enables users to bind without supplying a password as any account, including the Directory Manager. After the bind, the user can access all data with the permissions of the account used to bind.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-allow-unauthenticated-binds: off |
2.1.23. nsslapd-anonlimitsdn
Resource limits can be set on authenticated binds. The resource limits can set a cap on how many entries can be searched in a single operation (nsslapd-sizeLimit), a time limit (nsslapd-timelimit) and time out period (nsslapd-idletimeout) for searches, and the total number of entries that can be searched (nsslapd-lookthroughlimit). These resource limits prevent denial of service attacks from tying up directory resources and improve overall performance.
Resource limits are set on a user entry. An anonymous bind, obviously, does not have a user entry associated with it. This means that resource limits usually do not apply to anonymous operations.
To set resource limits for anonymous binds, a template entry can be created, with the appropriate resource limits. The nsslapd-anonlimitsdn configuration attribute can then be added that points to this entry and applies the resource limits to anonymous binds.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-anonlimitsdn: cn=anon template,ou=people,dc=example,dc=com |
2.1.24. nsslapd-attribute-name-exceptions
This attribute allows non-standard characters in attribute names to be used for backwards compatibility with older servers, such as "_" in schema-defined attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-attribute-name-exceptions: on |
2.1.25. nsslapd-auditfaillog
This attribute sets the path and filename of the log used to record failed LDAP modifications.
If nsslapd-auditfaillog-logging-enabled is enabled, and nsslapd-auditfaillog is not set, the audit fail events are logged to the file specified in nsslapd-auditlog.
If you set the nsslapd-auditfaillog parameter to the same path as nsslapd-auditlog, both are logged in the same file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid filename |
| Default Value | /var/log/dirsrv/slapd-instance/audit |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog: /var/log/dirsrv/slapd-instance/audit |
To enable the audit fail log, this attribute must have a valid path and the nsslapd-auditfaillog-logging-enabled attribute must be set to on
2.1.26. nsslapd-auditfaillog-compress
Directory Server does not compress audit fail log by default. Set nsslapd-auditfaillog-compress to on to enable audit fail log compression when Directory Server rotates the log.
You do not need to restart the server to apply changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-compress: on |
2.1.27. nsslapd-auditfaillog-list
Provides a list of audit fail log files.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-list: auditfaillog2,auditfaillog3 |
2.1.28. nsslapd-auditfaillog-logexpirationtime
This attribute sets the maximum age of a log file before it is removed. It supplies to the number of units. Specify the units, such as day, week, month, and so forth in the nsslapd-auditfaillog-logexpirationtimeunit attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) A value of -1 or 0 means that the log never expires. |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logexpirationtime: 1 |
2.1.29. nsslapd-auditfaillog-logexpirationtimeunit
This attribute sets the units for the nsslapd-auditfaillog-logexpirationtime attribute. If the unit is unknown by the server, the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day |
| Default Value | week |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-logexpirationtimeunit: day |
2.1.30. nsslapd-auditfaillog-logging-enabled
Turns on and off logging of failed LDAP modifications.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-logging-enabled: off |
2.1.31. nsslapd-auditfaillog-logmaxdiskspace
This attribute sets the maximum amount of disk space in megabytes the audit fail logs are can consume. If the size exceed the limit, the oldest audit fail log is deleted.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the disk space allowed to the audit fail log is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logmaxdiskspace: 10000 |
2.1.32. nsslapd-auditfaillog-logminfreediskspace
This attribute sets the minimum permissible free disk space in megabytes. When the amount of free disk space is lower than the specified value, the oldest audit fail logs are deleted until enough disk space is freed.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 (unlimited) | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logminfreediskspace: -1 |
2.1.33. nsslapd-auditfaillog-logrotationsync-enabled
This attribute sets whether audit fail log rotation is to be synchronized with a particular time of the day. Synchronizing log rotation this way can generate log files at a specified time during a day, such as midnight to midnight every day. This makes analysis of the log files much easier because they then map directly to the calendar.
For audit fail log rotation to be synchronized with time-of-day, this attribute must be enabled with the nsslapd-auditfaillog-logrotationsynchour and nsslapd-auditfaillog-logrotationsyncmin attribute values set to the hour and minute of the day for rotating log files.
For example, to rotate audit fail log files every day at midnight, enable this attribute by setting its value to on, and then set the values of the nsslapd-auditfaillog-logrotationsynchour and nsslapd-auditfaillog-logrotationsyncmin attributes to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-logrotationsync-enabled: on |
2.1.34. nsslapd-auditfaillog-logrotationsynchour
This attribute sets the hour of the day the audit fail log is rotated. This attribute must be used in conjunction with nsslapd-auditfaillog-logrotationsync-enabled and nsslapd-auditfaillog-logrotationsyncmin attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 23 |
| Default Value |
None (because |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logrotationsynchour: 23 |
2.1.35. nsslapd-auditfaillog-logrotationsyncmin
This attribute sets the minute the audit fail log is rotated. This attribute must be used in conjunction with nsslapd-auditfaillog-logrotationsync-enabled and nsslapd-auditfaillog-logrotationsynchour attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 59 |
| Default Value |
None (because |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logrotationsyncmin: 30 |
2.1.36. nsslapd-auditfaillog-logrotationtime
This attribute sets the time between audit fail log file rotations. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-auditfaillog-logrotationtimeunit attribute. If the nsslapd-auditfaillog-maxlogsperdir attribute is set to 1, the server ignores this attribute.
Directory Server rotates the log at the first write operation after the configured interval has expired, regardless of the size of the log.
Although it is not recommended for performance reasons to specify no log rotation, as the log grows indefinitely, there are two ways of specifying this. Either set the nsslapd-auditfaillog-maxlogsperdir attribute value to 1 or set the nsslapd-auditfaillog-logrotationtime attribute to -1. The server checks the nsslapd-auditfaillog-maxlogsperdir attribute first, and, if this attribute value is larger than 1, the server then checks the nsslapd-auditfaillog-logrotationtime attribute. See Section 2.1.25, “nsslapd-auditfaillog” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means the time between audit fail log file rotation is unlimited. |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logrotationtime: 100 |
2.1.37. nsslapd-auditfaillog-logrotationtimeunit
This attribute sets the units for the nsslapd-auditfaillog-logrotationtime attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day | hour | minute |
| Default Value | week |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-logrotationtimeunit: day |
2.1.38. nsslapd-auditfaillog-maxlogsize
This attribute sets the maximum audit fail log size in megabytes. When this value is reached, the audit fail log is rotated. That means the server starts writing log information to a new log file. If the nsslapd-auditfaillog-maxlogsperdir parameter is set to 1, the server ignores this attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means the log file is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-maxlogsize: 50 |
2.1.39. nsslapd-auditfaillog-maxlogsperdir
This attribute sets the total number of audit fail logs that can be contained in the directory where the audit log is stored. Each time the audit fail log is rotated, a new log file is created. When the number of files contained in the audit log directory exceeds the value stored on this attribute, then the oldest version of the log file is deleted. The default is 1 log. If this default is accepted, the server will not rotate the log, and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-auditfaillog-logrotationtime attribute to establish whether log rotation is specified. If the nsslapd-auditfaillog-logrotationtime attribute has a value of -1, then there is no log rotation. See Section 2.1.28, “nsslapd-auditfaillog-logexpirationtime” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-maxlogsperdir: 10 |
2.1.40. nsslapd-auditfaillog-mode
This attribute sets the access mode or file permissions with which audit fail log files are to be created. The valid values are any combination of 000 to 777 since they mirror numbered or absolute UNIX file permissions. The value must be a combination of a 3-digit number, the digits varying from 0 through 7:
- 0 - None
- 1 - Execute only
- 2 - Write only
- 3 - Write and execute
- 4 - Read only
- 5 - Read and execute
- 6 - Read and write
- 7 - Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the second digit represents the group’s permissions, and the third digit represents everyone’s permissions. When changing the default value, remember that 000 does not allow access to the logs and that allowing write permissions to everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log rotates to a new file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 000 through 777 |
| Default Value | 600 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-mode: 600 |
2.1.41. nsslapd-auditlog
This attribute sets the path and filename of the log used to record changes made to each database.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid filename |
| Default Value | /var/log/dirsrv/slapd-instance/audit |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog: /var/log/dirsrv/slapd-instance/audit |
For audit logging to be enabled, this attribute must have a valid path and parameter, and the nsslapd-auditlog-logging-enabled configuration attribute must be switched to on. The table lists the four possible combinations of values for these two configuration attributes and their outcome in terms of disabling or enabling of audit logging.
| Attributes in dse.ldif | Value | Logging enabled or disabled |
|---|---|---|
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | on empty string | Disabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | on filename | Enabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | off empty string | Disabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | off filename | Disabled |
2.1.42. nsslapd-auditlog-display-attrs
With the nsslapd-auditlog-display-attrs attribute you can set attributes that Directory Server displays in the audit log to provide useful identifying information about the entry being modified. By adding attributes to the audit log, you can check the current state of certain attributes in the entry and details of the entry update.
You can display attributes in the log by choosing one of the following options:
- To display a certain attribute of the entry that Directory Server modifies, provide the attribute name as a value.
- To display more than one attribute, provide the space separated list of attribute names as a value.
- To display all attributes of the entry, use an asterisk (*) as a value.
Provide the space separated list of attributes that Directory Server must display in the audit log, or use an asterisk (*) as a value to display all attributes of an entry being modified.
For example, to add the cn attribute to the audit log output, set the nsslapd-auditlog-display-attrs attribute to cn. The audit log contains then entries similar to the following:
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values |
Any valid attribute name and asterisk ( |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-display-attrs: cn ou |
2.1.43. nsslapd-auditlog-compress
Directory Server does not compress the audit log by default. Set nsslapd-auditlog-compress to on to enable the audit log compression when Directory Server rotates the log.
You do not need to restart the server to apply changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-compress: on |
2.1.44. nsslapd-auditlog-list
Provides a list of audit log files.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-list: auditlog2,auditlog3 |
2.1.45. nsslapd-auditlog-logbuffering
When the nsslapd-auditlog-logbuffering attribute is set to off, the server writes all audit and auditfail log entries directly to a disk. When nsslapd-auditlog-logbuffering is set to on, Directory Server can use audit and auditfail logging even under a heavy load without an impact on the server performance. However, when debugging, disable buffering in order to see the operations and their results right away instead of having to wait for the log entries to be flushed to the file. Disabling log buffering can severely impact performance in heavily loaded servers.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-logbuffering: off |
2.1.46. nsslapd-auditlog-logexpirationtime
This attribute sets the maximum age that a log file is allowed to be before it is deleted. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-auditlog-logexpirationtimeunit attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) A value of -1 or 0 means that the log never expires. |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-auditlog-logexpirationtime: 1 |
2.1.47. nsslapd-auditlog-logexpirationtimeunit
This attribute sets the units for the nsslapd-auditlog-logexpirationtime attribute. If the unit is unknown by the server, then the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day |
| Default Value | week |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-logexpirationtimeunit: day |
2.1.48. nsslapd-auditlog-logging-enabled
Turns audit logging on and off.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-logging-enabled: off |
For audit logging to be enabled, this attribute must have a valid path and parameter and the nsslapd-auditlog-logging-enabled configuration attribute must be switched to on. The table lists the four possible combinations of values for these two configuration attributes and their outcome in terms of disabling or enabling of audit logging.
| Attribute | Value | Logging enabled or disabled |
|---|---|---|
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | on empty string | Disabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | on filename | Enabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | off empty string | Disabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | off filename | Disabled |
2.1.49. nsslapd-auditlog-logmaxdiskspace
This attribute sets the maximum amount of disk space in megabytes that the audit logs are allowed to consume. If this value is exceeded, the oldest audit log is deleted.
When setting a maximum disk space, consider the total number of log files that can be created due to log file rotation. Also remember that there are three different log files (access log, audit log, and error log) maintained by Directory Server, each of which consumes disk space. Compare these considerations with the total amount of disk space for the audit log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the disk space allowed to the audit log is unlimited in size. |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-auditlog-logmaxdiskspace: 10000 |
2.1.50. nsslapd-auditlog-logminfreediskspace
This attribute sets the minimum permissible free disk space in megabytes. When the amount of free disk space falls below the value specified by this attribute, the oldest audit logs are deleted until enough disk space is freed to satisfy this attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 (unlimited) | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-auditlog-logminfreediskspace: -1 |
2.1.51. nsslapd-auditlog-logrotationsync-enabled
This attribute sets whether audit log rotation is to be synchronized with a particular time of the day. Synchronizing log rotation this way can generate log files at a specified time during a day, such as midnight to midnight every day. This makes analysis of the log files much easier because they then map directly to the calendar.
For audit log rotation to be synchronized with time-of-day, this attribute must be enabled with the nsslapd-auditlog-logrotationsynchour and nsslapd-auditlog-logrotationsyncmin attribute values set to the hour and minute of the day for rotating log files.
For example, to rotate audit log files every day at midnight, enable this attribute by setting its value to on, and then set the values of the nsslapd-auditlog-logrotationsynchour and nsslapd-auditlog-logrotationsyncmin attributes to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-logrotationsync-enabled: on |
2.1.52. nsslapd-auditlog-logrotationsynchour
This attribute sets the hour of the day for rotating audit logs. This attribute must be used in conjunction with nsslapd-auditlog-logrotationsync-enabled and nsslapd-auditlog-logrotationsyncmin attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 23 |
| Default Value |
None (because |
| Syntax | Integer |
| Example | nsslapd-auditlog-logrotationsynchour: 23 |
2.1.53. nsslapd-auditlog-logrotationsyncmin
This attribute sets the minute of the day for rotating audit logs. This attribute must be used in conjunction with nsslapd-auditlog-logrotationsync-enabled and nsslapd-auditlog-logrotationsynchour attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 59 |
| Default Value |
None (because |
| Syntax | Integer |
| Example | nsslapd-auditlog-logrotationsyncmin: 30 |
2.1.54. nsslapd-auditlog-logrotationtime
This attribute sets the time between audit log file rotations. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-auditlog-logrotationtimeunit attribute. If the nsslapd-auditlog-maxlogsperdir attribute is set to 1, the server ignores this attribute.
Directory Server rotates the log at the first write operation after the configured interval has expired, regardless of the size of the log.
Although it is not recommended for performance reasons to specify no log rotation, as the log grows indefinitely, there are two ways of specifying this. Either set the nsslapd-auditlog-maxlogsperdir attribute value to 1 or set the nsslapd-auditlog-logrotationtime attribute to -1. The server checks the nsslapd-auditlog-maxlogsperdir attribute first, and, if this attribute value is larger than 1, the server then checks the nsslapd-auditlog-logrotationtime attribute. See Section 2.1.39, “nsslapd-auditfaillog-maxlogsperdir” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the time between audit log file rotation is unlimited. |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-auditlog-logrotationtime: 100 |
2.1.55. nsslapd-auditlog-logrotationtimeunit
This attribute sets the units for the nsslapd-auditlog-logrotationtime attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day | hour | minute |
| Default Value | week |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-logrotationtimeunit: day |
2.1.56. nsslapd-auditlog-maxlogsize
This attribute sets the maximum audit log size in megabytes. When this value is reached, the audit log is rotated. That means the server starts writing log information to a new log file. If nsslapd-auditlog-maxlogsperdir to 1, the server ignores this attribute.
When setting a maximum log size, consider the total number of log files that can be created due to log file rotation. Also, remember that Directory Server maintains five different log files (access log, audit log, audit fail log, error log, security log), each of which consumes disk space. Compare these considerations to the total amount of disk space for the audit log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means the log file is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-auditlog-maxlogsize: 50 |
2.1.57. nsslapd-auditlog-maxlogsperdir
This attribute sets the total number of audit logs that can be contained in the directory where the audit log is stored. Each time the audit log is rotated, a new log file is created. When the number of files contained in the audit log directory exceeds the value stored on this attribute, then the oldest version of the log file is deleted. The default is 1 log. If this default is accepted, the server will not rotate the log, and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-auditlog-logrotationtime attribute to establish whether log rotation is specified. If the nsslapd-auditlog-logrotationtime attribute has a value of -1, then there is no log rotation. See Section 2.1.14, “nsslapd-accesslog-logrotationtime” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-auditlog-maxlogsperdir: 10 |
2.1.58. nsslapd-auditlog-mode
This attribute sets the access mode or file permissions with which audit log files are to be created. The valid values are any combination of 000 to 777 since they mirror numbered or absolute UNIX file permissions. The value must be a combination of a 3-digit number, the digits varying from 0 through 7:
- 0 - None
- 1 - Execute only
- 2 - Write only
- 3 - Write and execute
- 4 - Read only
- 5 - Read and execute
- 6 - Read and write
- 7 - Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the second digit represents the group’s permissions, and the third digit represents everyone’s permissions. When changing the default value, remember that 000 does not allow access to the logs and that allowing write permissions to everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log rotates to a new file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 000 through 777 |
| Default Value | 600 |
| Syntax | Integer |
| Example | nsslapd-auditlog-mode: 600 |
2.1.59. nsslapd-bakdir
This parameter sets the path to the default backup directory. The Directory Server user must have write permissions in the configured directory.
This setting does not require a server restart to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any local directory path. |
| Default Value | /var/lib/dirsrv/slapd-instance/bak |
| Syntax | DirectoryString |
| Example | nsslapd-bakdir: /var/lib/dirsrv/slapd-instance/bak |
2.1.60. nsslapd-certdir
This parameter defines the full path to the directory that Directory Server uses to store the Network Security Services (NSS) database of the instance. This database contains the private keys and certificates of the instance.
As a fallback, Directory Server extracts the private key and certificates to this directory, if the server cannot extract them to the /tmp/ directory in a private name space. For details about private name spaces, see the PrivateTmp parameter description in the systemd.exec(5) man page.
The directory specified in nsslapd-certdir must be owned by the user ID of the server, and only this user ID must have read-write permissions in this directory. For security reasons, no other users should have permissions to read or write to this directory.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | An absolute path |
| Default Value | /etc/dirsrv/slapd-instance_name/ |
| Syntax | DirectoryString |
| Example | nsslapd-certdir: /etc/dirsrv/slapd-instance_name/ |
2.1.61. nsslapd-certmap-basedn
This attribute can be used when client authentication is performed using TLS certificates in order to avoid limitations of the security subsystem certificate mapping, configured in the /etc/dirsrv/slapd-instance_name/certmap.conf file. Depending on the configuration in this file, the certificate mapping may be done using a directory subtree search based at the root DN. If the search is based at the root DN, then the nsslapd-certmap-basedn attribute may force the search to be based at some entry other than the root. The valid value for this attribute is the DN of the suffix or subtree to use for certificate mapping.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-certmap-basedn: ou=People,dc=example,dc=com |
2.1.62. nsslapd-close-on-failed-bind
Use the nsslapd-close-on-failed-bind configuration attribute to close a client connection from the server side if a BIND operation fails.
Enabling this parameter helps to reduce the load from Directory Server if applications ignore the BIND return code and continue sending requests.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-close-on-failed-bind: off |
2.1.63. nsslapd-cn-uses-dn-syntax-in-dns
This parameter allows you to enable a DN inside a CN value.
The Directory Server DN normalizer follows RFC4514 and keeps a white space if the RDN attribute type is not based on the DN syntax. However the Directory Server’s configuration entry sometimes uses a cn attribute to store a DN value. For example in dn: cn="dc=A,dc=com", cn=mapping tree,cn=config, the cn should be normalized following the DN syntax.
If this configuration is required, enable the nsslapd-cn-uses-dn-syntax-in-dns parameter.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-cn-uses-dn-syntax-in-dns: off |
2.1.64. nsslapd-config
This read-only attribute is the config DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid configuration DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-config: cn=config |
2.1.65. nsslapd-connection-buffer
This attribute sets the connection buffering behavior. Possible values:
-
0: Disable buffering. Only single Protocol Data Units (PDU) are read at a time. -
1: Regular fixed sizeLDAP_SOCKET_IO_BUFFER_SIZEof512bytes. -
2: Adaptable buffer size.
The value 2 provides a better performance if the client sends a large amount of data at once. This is, for example, the case for large add and modify operations, or when many asynchronous requests are received over a single connections like during a replication.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 | 1 | 2 |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-connection-buffer: 1 |
2.1.66. nsslapd-connection-nocanon
This option allows you to enable or disable the SASL NOCANON flag. Disabling avoids Directory Server looking up DNS reverse entries for outgoing connections.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-connection-nocanon: on |
2.1.67. nsslapd-counters
The nsslapd-counters attribute enables and disables Directory Server database and server performance counters.
There can be a performance impact by keeping track of the larger counters. Turning off 64-bit integers for counters can have a minimal improvement on performance, although it negatively affects long term statistics tracking.
This parameter is enabled by default. To disable counters, stop Directory Server, edit the dse.ldif file directly, and restart the server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-counters: on |
2.1.68. nsslapd-csnlogging
This attribute sets whether change sequence numbers (CSNs), when available, are to be logged in the access log. By default, CSN logging is turned on.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-csnlogging: on |
2.1.69. nsslapd-defaultnamingcontext
This attribute gives the naming context, of all configured naming contexts, which clients should use by default as a search base. This value is copied over to the root DSE as the defaultNamingContext attribute, which allows clients to query the root DSE to obtain the context and then to initiate a search with the appropriate base.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any root suffix DN |
| Default Value | The default user suffix |
| Syntax | DN |
| Example | nsslapd-defaultnamingcontext: dc=example,dc=com |
2.1.70. nsslapd-disk-monitoring
This attribute enables a thread which runs every ten (10) seconds to check the available disk space on the disk or mount where the Directory Server database is running. If the available disk space drops below a configured threshold, then the server begins reducing logging levels, disabling access or audit logs, and deleting rotated logs. If that does not free enough available space, then the server shuts down gracefully (after a wanring and grace period).
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-disk-monitoring: on |
2.1.71. nsslapd-disk-monitoring-grace-period
Sets a grace period to wait before shutting down the server after it hits half of the disk space limit set in Section 2.1.74, “nsslapd-disk-monitoring-threshold”. This gives the administrator time to clean out the disk and prevent a shutdown.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any integer (sets value in minutes) |
| Default Value | 60 |
| Syntax | Integer |
| Example | nsslapd-disk-monitoring-grace-period: 45 |
2.1.72. nsslapd-disk-monitoring-logging-critical
Sets whether to shut down the server if the log directories pass the halfway point set in the disk space limit, Section 2.1.74, “nsslapd-disk-monitoring-threshold”.
If this is enabled, then logging is not disabled and rotated logs are not deleted as means of reducing disk usage by the server. The server simply goes toward a shutdown process.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-disk-monitoring-logging-critical: on |
2.1.73. nsslapd-disk-monitoring-readonly-on-threshold
If the free disk space reaches half of the value you set in the nsslapd-disk-monitoring-threshold parameter, Directory Server shuts down the instance after the grace period set in nsslapd-disk-monitoring-grace-period is reached. However, if the disk runs out of space before the instance is down, data can be corrupted. To prevent this problem, enable the nsslapd-disk-monitoring-readonly-on-threshold parameter, and Directory Server sets the instance to read-only mode when the threshold is reached.
With this setting, Directory Server does not start if the free disk space is below half of the threshold configured in the nsslapd-disk-monitoring-threshold.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-disk-monitoring-readonly-on-threshold: off |
2.1.74. nsslapd-disk-monitoring-threshold
Sets the threshold, in bytes, to use to evaluate whether the server has enough available disk space. Once the space reaches half of this threshold, then the server begins a shut down process.
For example, if the threshold is 2MB (the default), then once the available disk space reaches 1MB, the server will begin to shut down.
By default, the threshold is evaluated backs on the disk space used by the configuration, transaction, and database directories for the Directory Server instance. If the Section 2.1.72, “nsslapd-disk-monitoring-logging-critical” attribute is enabled, then the log directory is included in the evaluation.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | * 0 to the maximum 32-bit integer value (2147483647) on 32-bit systems * 0 to the maximum 64-bit integer value (9223372036854775807) on 64-bit systems |
| Default Value | 2000000 (2MB) |
| Syntax | DirectoryString |
| Example | nsslapd-disk-monitoring-threshold: 2000000 |
2.1.75. nsslapd-dn-validate-strict
The nsslapd-syntaxcheck attribute enables the server to verify that any new or modified attribute value matches the required syntax for that attribute.
However, the syntax rules for DNs have grown increasingly strict. Attempting to enforce DN syntax rules in RFC 4514 could break many servers using older syntax definitions. By default, then nsslapd-syntaxcheck validates DNs using RFC 1779 or RFC 2253.
The nsslapd-dn-validate-strict attribute explicitly enables strict syntax validation for DNs, according to section 3 in RFC 4514. If this attribute is set to off (the default), the server normalizes the value before checking it for syntax violations.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-dn-validate-strict: off |
2.1.76. nsslapd-ds4-compatible-schema
Makes the schema in cn=schema compatible with 4.x versions of Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-ds4-compatible-schema: off |
2.1.77. nsslapd-enable-turbo-mode
The Directory Server turbo mode is a feature that enables a worker thread to be dedicated to a connection and continuously read incoming operations from that connection. This can improve the performance on very active connections, and the feature is enabled by default.
Worker threads are processing the LDAP operation received by the server. The number of worker threads is defined in the nsslapd-threadnumber parameter. Every five seconds, each worker thread evaluates if the activity level of its current connection is one of the highest among all established connections. Directory Server measures the activity as the number of operations initiated since the last check, and switches a worker thread in turbo mode if the activity of the current connection is one of the highest.
If you encounter long execution times (etime value in log files) for bind operations, such as one second or longer, deactivating the turbo mode can improve the performance. However, in some cases, long bind times are a symptom of networking or hardware issues. In these situations, disabling the turbo mode does not result in improved performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-enable-turbo-mode: on |
2.1.78. nsslapd-enable-upgrade-hash
During a simple bind, Directory Server has access to the plain text password due to the nature of bind operations. If the nsslapd-enable-upgrade-hash parameter is enabled and a user authenticates, Directory Server checks if the userPassword attribute of the user uses the hashing algorithm set in the passwordStorageScheme attribute. If the algorithm is different, the server hashes the plain text password with the algorithm from passwordStorageScheme and updates the value of the user’s userPassword attribute.
For example, if you import a user entry with a password that is hashed using a weak algorithm, the server automatically re-hashes the passwords on the first login of the user using the algorithm set in passwordStorageScheme, which is, by default, PBKDF2_SHA256.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-enable-upgrade-hash: on |
2.1.79. nsslapd-enquote-sup-oc
This attribute is deprecated and will be removed in a future version of Directory Server.
This attribute controls whether quoting in the objectclass attributes contained in the cn=schema entry conforms to the quoting specified by Internet draft RFC 2252. By default, Directory Server conforms to RFC 2252, which indicates that this value should not be quoted. Only very old clients need this value set to on, so leave it off.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-enquote-sup-oc: off |
2.1.80. nsslapd-entryusn-global
The nsslapd-entryusn-global parameter defines if the USN plug-in assigns unique update sequence numbers (USN) across all back end databases or to each database individually. For unique USNs across all back end databases, set this parameter to on.
For further details, see Section 10.8, “entryusn”.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-entryusn-global: off |
2.1.81. nsslapd-entryusn-import-initval
Entry update sequence numbers (USNs) are not preserved when entries are exported from one server and imported into another, including when initializing a database for replication. By default, the entry USNs for imported entries are set to zero.
It is possible to configure a different initial value for entry USNs using nsslapd-entryusn-import-initval. This sets a starting USN which is used for all imported entries.
There are two possible values for nsslapd-entryusn-import-initval:
- An integer, which is the explicit start number used for every imported entry.
- next, which means that every imported entry uses whatever the highest entry USN value was on the server before the import operation, incremented by one.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any integer | next |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-entryusn-import-initval: next |
2.1.82. nsslapd-errorlog
This attribute sets the path and filename of the log used to record error messages generated by Directory Server. These messages can describe error conditions, but more often they contain informative conditions, such as:
- Server startup and shutdown times.
- The port number that the server uses.
This log contains differing amounts of information depending on the current setting of the Log Level attribute. See Section 2.1.84, “nsslapd-errorlog-level” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid filename |
| Default Value | /var/log/dirsrv/slapd-instance/errors |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog: /var/log/dirsrv/slapd-instance/errors |
For error logging to be enabled, this attribute must have a valid path and filename, and the nsslapd-errorlog-logging-enabled configuration attribute must be switched to on. The table lists the four possible combinations of values for these two configuration attributes and their outcome in terms of disabling or enabling of error logging.
| Attributes in dse.ldif | Value | Logging enabled or disabled |
|---|---|---|
| nsslapd-errorlog-logging-enabled nsslapd-errorlog | on empty string | Disabled |
| nsslapd-errorlog-logging-enabled nsslapd-errorlog | on filename | Enabled |
| nsslapd-errorlog-logging-enabled nsslapd-errorlog | off empty string | Disabled |
| nsslapd-errorlog-logging-enabled nsslapd-errorlog | off filename | Disabled |
2.1.83. nsslapd-errorlog-compress
Directory Server does not compress error log by default. Set nsslapd-errorlog-compress to on to enable the error log compression when Directory Server rotates the log.
You do not need to restart the server to apply changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-compress: on |
2.1.84. nsslapd-errorlog-level
This attribute sets the level of logging for Directory Server. The log level is additive; that is, specifying a value of 3 includes both levels 1 and 2.
The default value for nsslapd-errorlog-level is 16384.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | For the full list of the error log logging levels, see Error logging levels. |
| Default Value | 16384 |
| Syntax | Integer |
| Example | nsslapd-errorlog-level: 8192 |
2.1.85. nsslapd-errorlog-list
This read-only attribute provides a list of error log files.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-list: errorlog2,errorlog3 |
:_content-type: REFERENCE
:_content-type: REFERENCE2.1.86. nsslapd-errorlog-logbuffering
When the nsslapd-errorlog-logbuffering attribute is set to off, the server writes all error log entries directly to a disk. When nsslapd-errorlog-logbuffering is set to on, Directory Server can use error logging even under a heavy load without an impact on the server performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-logbuffering: on |
2.1.87. nsslapd-errorlog-logexpirationtime
This attribute sets the maximum age that a log file is allowed to reach before it is deleted. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-errorlog-logexpirationtimeunit attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) A value of -1 or 0 means that the log never expires. |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logexpirationtime: 1 |
2.1.88. nsslapd-errorlog-logexpirationtimeunit
This attribute sets the units for the nsslapd-errorlog-logexpirationtime attribute. If the unit is unknown by the server, then the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day |
| Default Value | month |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-logexpirationtimeunit: week |
2.1.89. nsslapd-errorlog-logging-enabled
Turns error logging on and off.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-logging-enabled: on |
2.1.90. nsslapd-errorlog-logmaxdiskspace
This attribute sets the maximum amount of disk space in megabytes that the error logs are allowed to consume. If this value is exceeded, the oldest error log is deleted.
When setting a maximum disk space, consider the total number of log files that can be created due to log file rotation. Also, remember that there are three different log files (access log, audit log, and error log) maintained by Directory Server, each of which consumes disk space. Compare these considerations to the total amount of disk space for the error log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the disk space allowed to the error log is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logmaxdiskspace: 10000 |
2.1.91. nsslapd-errorlog-logminfreediskspace
This attribute sets the minimum allowed free disk space in megabytes. When the amount of free disk space falls below the value specified on this attribute, the oldest error log is deleted until enough disk space is freed to satisfy this attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 (unlimited) | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logminfreediskspace: -1 |
2.1.92. nsslapd-errorlog-logrotationsync-enabled
This attribute sets whether error log rotation is to be synchronized with a particular time of the day. Synchronizing log rotation this way can generate log files at a specified time during a day, such as midnight to midnight every day. This makes analysis of the log files much easier because they then map directly to the calendar.
For error log rotation to be synchronized with time-of-day, this attribute must be enabled with the nsslapd-errorlog-logrotationsynchour and nsslapd-errorlog-logrotationsyncmin attribute values set to the hour and minute of the day for rotating log files.
For example, to rotate error log files every day at midnight, enable this attribute by setting its value to on, and then set the values of the nsslapd-errorlog-logrotationsynchour and nsslapd-errorlog-logrotationsyncmin attributes to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-logrotationsync-enabled: on |
2.1.93. nsslapd-errorlog-logrotationsynchour
This attribute sets the hour of the day for rotating error logs. This attribute must be used in conjunction with nsslapd-errorlog-logrotationsync-enabled and nsslapd-errorlog-logrotationsyncmin attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 23 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logrotationsynchour: 23 |
2.1.94. nsslapd-errorlog-logrotationsyncmin
This attribute sets the minute of the day for rotating error logs. This attribute must be used in conjunction with nsslapd-errorlog-logrotationsync-enabled and nsslapd-errorlog-logrotationsynchour attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 59 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logrotationsyncmin: 30 |
2.1.95. nsslapd-errorlog-logrotationtime
This attribute sets the time between error log file rotations. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-errorlog-logrotationtimeunit (Error Log Rotation Time Unit) attribute.
Directory Server rotates the log at the first write operation after the configured interval has expired, regardless of the size of the log.
Although it is not recommended for performance reasons to specify no log rotation, as the log grows indefinitely, there are two ways of specifying this. Either set the nsslapd-errorlog-maxlogsperdir attribute value to 1 or set the nsslapd-errorlog-logrotationtime attribute to -1. The server checks the nsslapd-errorlog-maxlogsperdir attribute first, and, if this attribute value is larger than 1, the server then checks the nsslapd-errorlog-logrotationtime attribute. See Section 2.1.98, “nsslapd-errorlog-maxlogsperdir” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the time between error log file rotation is unlimited). |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logrotationtime: 100 |
2.1.96. nsslapd-errorlog-logrotationtimeunit
This attribute sets the units for nsslapd-errorlog-logrotationtime (Error Log Rotation Time). If the unit is unknown by the server, then the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day | hour | minute |
| Default Value | week |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-logrotationtimeunit: day |
2.1.97. nsslapd-errorlog-maxlogsize
This attribute sets the maximum error log size in megabytes. When this value is reached, the error log is rotated, and the server starts writing log information to a new log file. If nsslapd-errorlog-maxlogsperdir is set to 1, the server ignores this attribute.
When setting a maximum log size, consider the total number of log files that can be created due to log file rotation. Also, remember that Directory Server maintains five different log files (access log, audit log, audit fail log, error log, security log), each of which consumes disk space. Compare these considerations to the total amount of disk space for the error log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647) where a value of -1 means the log file is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-errorlog-maxlogsize: 100 |
2.1.98. nsslapd-errorlog-maxlogsperdir
This attribute sets the total number of error logs that can be contained in the directory where the error log is stored. Each time the error log is rotated, a new log file is created. When the number of files contained in the error log directory exceeds the value stored on this attribute, then the oldest version of the log file is deleted. The default is 1 log. If this default is accepted, the server does not rotate the log, and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-errorlog-logrotationtime attribute to establish whether log rotation is specified. If the nsslapd-errorlog-logrotationtime attribute has a value of -1, then there is no log rotation. See Section 2.1.95, “nsslapd-errorlog-logrotationtime” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-errorlog-maxlogsperdir: 10 |
2.1.99. nsslapd-errorlog-mode
This attribute sets the access mode or file permissions with which error log files are to be created. The valid values are any combination of 000 to 777 since they mirror numbered or absolute UNIX file permissions. That is, the value must be a combination of a 3-digit number, the digits varying from 0 through 7:
- 0 - None
- 1 - Execute only
- 2 - Write only
- 3 - Write and execute
- 4 - Read only
- 5 - Read and execute
- 6 - Read and write
- 7 - Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the second digit represents the group’s permissions, and the third digit represents everyone’s permissions. When changing the default value, remember that 000 does not allow access to the logs and that allowing write permissions to everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log rotates to a new file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 000 through 777 |
| Default Value | 600 |
| Syntax | Integer |
| Example | nsslapd-errorlog-mode: 600 |
2.1.100. nsslapd-external-libs-debug-enabled
To enable the third-party logging in Directory Server, use the nsslapd-external-libs-debug-enabled attribute.
Libraries, such as libldap and libber, perform error and debug logging, however these records are not available in the Directory Server logs. When the nsslapd-external-libs-debug-enabled attribute is set to on, Directory Server can use all log levels that libldap and libber packages provide.
Enable the nsslapd-external-libs-debug-enabled attribute only for debugging purposes because it produces verbose logging for all operations.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-external-libs-debug-enabled: off |
2.1.101. nsslapd-force-sasl-external
When establishing a TLS connection, a client sends its certificate first and then issues a BIND request using the SASL/EXTERNAL mechanism. Using SASL/EXTERNAL tells Directory Server to use the credentials in the certificate for the TLS handshake. However, some clients do not use SASL/EXTERNAL when they send their BIND request, so the Directory Server processes the bind as a simple authentication request or an anonymouse request and the TLS connection fails.
The nsslapd-force-sasl-external attribute forces clients in certificate-based authentication to send the BIND request using the SASL/EXTERNAL method.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | String |
| Example | nsslapd-force-sasl-external: on |
2.1.102. nsslapd-groupevalnestlevel
This attribute is deprecated, and documented here only for historical purposes.
The Access Control Plug-in does not use the value specified by the nsslapd-groupevalnestlevel attribute to set the number of levels of nesting that access control performs for group evaluation. Instead, the number of levels of nesting is hardcoded as 5.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 5 |
| Default Value | 5 |
| Syntax | Integer |
| Example | nsslapd-groupevalnestlevel: 5 |
2.1.103. nsslapd-haproxy-trusted-ip
The nsslapd-haproxy-trusted-ip attribute configures the list of trusted proxy servers. When you set nsslapd-haproxy-trusted-ip, Directory Server uses HAProxy protocol to receive client IP addresses via an additional TCP header to evaluate access control instructions (ACIs) correctly and log the client traffic.
If an untrusted proxy server initiates a bind request, Directory Server rejects the request and records the following message to the error log file:
[time_stamp] conn=5 op=-1 fd=64 Disconnect - Protocol error - Unknown Proxy - P4
[time_stamp] conn=5 op=-1 fd=64 Disconnect - Protocol error - Unknown Proxy - P4
To set the list of trusted proxy servers, use the dsconf utility. For example, if you want Directory Server to trust the 127.0.0.1, 127.0.0.2, 127.0.0.3 IP addresses, run:
dsconf instance_name config replace nsslapd-haproxy-trusted-ip=127.0.0.1 nsslapd-haproxy-trusted-ip=127.0.0.2 nsslapd-haproxy-trusted-ip=127.0.0.3
# dsconf instance_name config replace nsslapd-haproxy-trusted-ip=127.0.0.1 nsslapd-haproxy-trusted-ip=127.0.0.2 nsslapd-haproxy-trusted-ip=127.0.0.3| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | IPv4 or IPv6 addresses |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-haproxy-trusted-ip: 127.0.0.1 |
2.1.104. nsslapd-idletimeout
This attribute sets the amount of time in seconds after which an idle LDAP client connection is closed by the server. A value of 0 means that the server never closes idle connections. This setting applies to all connections and all users. Idle timeout is enforced when the connection table is walked, when poll() does not return zero. Therefore, a server with a single connection never enforces the idle timeout.
Use the nsIdleTimeout operational attribute, which can be added to user entries, to override the value assigned to this attribute.
For very large databases, with millions of entries, this attribute must have a high enough value that the online initialization process can complete or replication will fail when the connection to the server times out. Alternatively, the nsIdleTimeout attribute can be set to a high value on the entry used as the supplier bind DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | 3600 |
| Syntax | Integer |
| Example | nsslapd-idletimeout: 3600 |
2.1.105. nsslapd-ignore-virtual-attrs
This parameter allows to disable the virtual attribute lookup in a search entry.
If you do not require virtual attributes, you can disable virtual attribute lookups in search results to increase the speed of searches.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-ignore-virtual-attrs: on |
2.1.106. nsslapd-instancedir
This attribute is deprecated. There are now separate configuration parameters for instance-specific paths, such as nsslapd-certdir and nsslapd-lockdir. See the documentation for the specific directory path that is set.
2.1.107. nsslapd-ioblocktimeout
This attribute sets the amount of time in milliseconds after which the connection to a stalled LDAP client is closed. An LDAP client is considered to be stalled when it has not made any I/O progress for read or write operations.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to the maximum 32 bit integer value (2147483647) in ticks |
| Default Value | 10000 |
| Syntax | Integer |
| Example | nsslapd-ioblocktimeout: 10000 |
2.1.108. nsslapd-lastmod
This attribute sets whether Directory Server maintains the creatorsName, createTimestamp, modifiersName, and modifyTimestamp operational attributes for newly created or updated entries.
Red Hat recommends not disabling tracking these attributes. If disabled, entries do not get a unique ID assigned in the nsUniqueID attribute and replication does not work.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-lastmod: on |
2.1.109. nsslapd-ldapiautobind
The nsslapd-ldapiautobind sets whether the server will allow users to autobind to Directory Server using LDAPI. Autobind maps the UID or GUID number of a system user to a Directory Server user, and automatically authenticates the user to Directory Server based on those credentials. The Directory Server connection occurs over UNIX socket.
Along with enabling autobind, configuring autobind requires configuring mapping entries. The nsslapd-ldapimaprootdn maps a root user on the system to the Directory Manager. The nsslapd-ldapimaptoentries maps regular users to Directory Server users, based on the parameters defined in the nsslapd-ldapiuidnumbertype, nsslapd-ldapigidnumbertype, and nsslapd-ldapientrysearchbase attributes.
Autobind can only be enabled if LDAPI is enabled, meaning the nsslapd-ldapilisten is on and the nsslapd-ldapifilepath attribute is set to an LDAPI socket.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-ldapiautobind: off |
2.1.110. nsslapd-ldapientrysearchbase
With autobind, it is possible to map system users to Directory Server user entries, based on the system user’s UID and GUID numbers. This requires setting Directory Server parameters for which attribute to use for the UID number (nsslapd-ldapiuidnumbertype) and GUID number (nsslapd-ldapigidnumbertype) and setting the search base to use to search for matching user entries.
The nsslapd-ldapientrysearchbase gives the subtree to search for user entries to use for autobind.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | DN |
| Default Value |
The suffix created when the server instance was created, such as |
| Syntax | DN |
| Example | nsslapd-ldapientrysearchbase: ou=people,dc=example,dc=om |
2.1.111. nsslapd-ldapifilepath
LDAPI connects a user to an LDAP server over a UNIX socket rather than TCP. In order to configure LDAPI, the server must be configured to communicate over a UNIX socket. The UNIX socket to use is set in the nsslapd-ldapifilepath attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any directory path |
| Default Value | /var/run/dirsrv/slapd-example.socket |
| Syntax | Case-exact string |
| Example | nsslapd-ldapifilepath: /var/run/slapd-example.socket |
2.1.112. nsslapd-ldapigidnumbertype
Autobind can be used to authenticate system users to the server automatically and connect to the server using a UNIX socket. To map the system user to a Directory Server user for authentication, the system user’s UID and GUID numbers should be mapped to be a Directory Server attribute. The nsslapd-ldapigidnumbertype attribute points to the Directory Server attribute to map system GUIDs to user entries.
Users can only connect to the server with autobind if LDAPI is enabled (nsslapd-ldapilisten and nsslapd-ldapifilepath), autobind is enabled (nsslapd-ldapiautobind), and autobind mapping is enabled for regular users (nsslapd-ldapimaptoentries).
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any Directory Server attribute |
| Default Value | gidNumber |
| Syntax | DirectoryString |
| Example | nsslapd-ldapigidnumbertype: gidNumber |
2.1.113. nsslapd-ldapilisten
The nsslapd-ldapilisten enables LDAPI connections to Directory Server. LDAPI allows users to connect to Directory Server over a UNIX socket rather than a standard TCP port. Along with enabling LDAPI by setting nsslapd-ldapilisten to on, there must also be a UNIX socket set for LDAPI in the nsslapd-ldapifilepath attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-ldapilisten: on |
2.1.114. nsslapd-ldapimaprootdn
The nsslapd-ldapimaprootdn attribute is deprecated. Use the nsslapd-rootdn parameter to map a system root entry to a root DN entry.
With autobind, a system user is mapped to a Directory Server user and then automatically authenticated to Directory Server over a UNIX socket.
The root system user (the user with a UID of 0) is mapped to whatever Directory Server entry is specified in the nsslapd-ldapimaprootdn attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any DN |
| Default Value | cn=Directory Manager |
| Syntax | DN |
| Example | nsslapd-ldapimaprootdn: cn=Directory Manager |
2.1.115. nsslapd-ldapimaptoentries
With autobind, a system user is mapped to a Directory Server user and then automatically authenticated to Directory Server over a UNIX socket. This mapping is automatic for root users, but it must be enabled for regular system users through the nsslapd-ldapimaptoentries attribute. Setting this attribute to on enables mapping for regular system users to Directory Server entries. If this attribute is not enabled, then only root users can use autobind to authenticate to Directory Server, and all other users connect anonymously.
The mappings themselves are configured through the nsslapd-ldapiuidnumbertype and nsslapd-ldapigidnumbertype attributes, which map Directory Server attributes to the user’s UID and GUID numbers.
Users can only connect to the server with autobind if LDAPI is enabled (nsslapd-ldapilisten and nsslapd-ldapifilepath) and autobind is enabled (nsslapd-ldapiautobind).
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-ldapimaptoentries: on |
2.1.116. nsslapd-ldapiuidnumbertype
Autobind can be used to authenticate system users to the server automatically and connect to the server using a UNIX socket. To map the system user to a Directory Server user for authentication, the system user’s UID and GUID numbers must be mapped to be a Directory Server attribute. The nsslapd-ldapiuidnumbertype attribute points to the Directory Server attribute to map system UIDs to user entries.
Users can only connect to the server with autobind if LDAPI is enabled (nsslapd-ldapilisten and nsslapd-ldapifilepath), autobind is enabled (nsslapd-ldapiautobind), and autobind mapping is enabled for regular users (nsslapd-ldapimaptoentries).
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any Directory Server attribute |
| Default Value | uidNumber |
| Syntax | DirectoryString |
| Example | nsslapd-ldapiuidnumbertype: uidNumber |
2.1.117. nsslapd-ldifdir
Directory Server exports files in LDAP Data Interchange Format (LDIF) format to the directory set in this parameter when using the db2ldif or db2ldif.pl. The directory must be owned by the Directory Server user and group. Only this user and group must have read and write access in this directory.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any directory writable by the Directory Server user |
| Default Value | /var/lib/dirsrv/slapd-instance_name/ldif/ |
| Syntax | DirectoryString |
| Example | nsslapd-ldifdir: /var/lib/dirsrv/slapd-instance_name/ldif/ |
2.1.118. nsslapd-listen-backlog-size
This attribute sets the maximum of the socket connection backlog. The listen service sets the number of sockets available to receive incoming connections. The backlog setting sets a maximum length for how long the queue for the socket (sockfd) can grow before refusing connections.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | The maximum 64-bit integer value (9223372036854775807) |
| Default Value | 128 |
| Syntax | Integer |
| Example | nsslapd-listen-backlog-size: 128 |
2.1.119. nsslapd-listenhost
This attribute allows multiple Directory Server instances to run on a multihomed machine (or makes it possible to limit listening to one interface of a multihomed machine). There can be multiple IP addresses associated with a single hos tname, and these IP addresses can be a mix of both IPv4 and IPv6. This parameter can be used to restrict the Directory Server instance to a single IP interface.
If a host name is given as the nsslapd-listenhost value, then Directory Server responds to requests for every interface associated with the host name. If a single IP interface (either IPv4 or IPv6) is given as the nsslapd-listenhost value, Directory Server only responds to requests sent to that specific interface. Either an IPv4 or IPv6 address can be used.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any local host name, IPv4 or IPv6 address |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-listenhost: ldap.example.com |
2.1.120. nsslapd-localhost
This attribute specifies the host machine on which Directory Server runs. This attribute creates the referral URL that forms part of the MMR protocol. In a high-availability configuration with failover nodes, that referral should point to the virtual name of the cluster, not the local host name.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any fully qualified host name. |
| Default Value | Hostname of installed machine. |
| Syntax | DirectoryString |
| Example | nsslapd-localhost: phonebook.example.com |
2.1.121. nsslapd-localssf
The nsslapd-localssf parameter sets the security strength factor (SSF) for LDAPI connections. Directory Server allows LDAPI connections only if the value set in nsslapd-localssf is greater or equal than the value set in the nsslapd-minssf parameter. Therefore, LDAPI connections meet the minimum SSF set in nsslapd-minssf.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 to the maximum 32-bit integer value (2147483647) |
| Default Value | 71 |
| Syntax | Integer |
| Example | nsslapd-localssf: 71 |
2.1.122. nsslapd-localuser
This attribute sets the user as whom Directory Server runs. The group as which the user runs is derived from this attribute by examining the user’s primary group. Should the user change, then all of the instance-specific files and directories for this instance need to be changed to be owned by the new user, using a tool such as chown.
The value for the nsslapd-localuser is set initially when the server instance is configured.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid user |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-localuser: dirsrv |
2.1.123. nsslapd-lockdir
This is the full path to the directory the server uses for lock files. The default value is /var/lock/dirsrv/slapd-instance. Changes to this value will not take effect until the server is restarted.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Absolute path to a directory owned by the server user ID with write access to the server ID |
| Default Value | /var/lock/dirsrv/slapd-instance |
| Syntax | DirectoryString |
| Example | nsslapd-lockdir: /var/lock/dirsrv/slapd-instance |
2.1.124. nsslapd-malloc-mmap-threshold
If a Directory Server instance is started as a service using the systemctl utility, environment variables are not passed to the server unless you set them in the /etc/sysconfig/dirsrv or /etc/sysconfig/dirsrv-instance_name file. For further details, see the systemd.exec(3) man page.
Instead of manually editing the service files to set the M_MMAP_THRESHOLD environment variable, the nsslapd-malloc-mmap-threshold parameter enables you to set the value in the Directory Server configuration. For further details, see the M_MMAP_THRESHOLD parameter description in the mallopt(3) man page.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 - 33554432 |
| Default Value |
See the |
| Syntax | Integer |
| Example | nsslapd-malloc-mmap-threshold: 33554432 |
2.1.125. nsslapd-malloc-mxfast
If a Directory Server instance is started as a service using the systemctl utility, environment variables are not passed to the server unless you set them in the /etc/sysconfig/dirsrv or /etc/sysconfig/dirsrv-instance_name file. For further details, see the systemd.exec(3) man page.
Instead of manually editing the service files to set the M_MXFAST environment variable, the nsslapd-malloc-mxfast parameter enables you to set the value in the Directory Server configuration. For further details, see the M_MXFAST parameter description in the mallopt(3) man page.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 - 80 * (sizeof(size_t) / 4) |
| Default Value |
See the |
| Syntax | Integer |
| Example | nsslapd-malloc-mxfast: 1048560 |
2.1.126. nsslapd-malloc-trim-threshold
If a Directory Server instance is started as a service using the systemctl utility, environment variables are not passed to the server unless you set them in the /etc/sysconfig/dirsrv or /etc/sysconfig/dirsrv-instance_name file. For further details, see the systemd.exec(3) man page.
Instead of manually editing the service files to set the M_TRIM_THRESHOLD environment variable, the nsslapd-malloc-trim-threshold parameter enables you to set the value in the Directory Server configuration. For further details, see the M_TRIM_THRESHOLD parameter description in the mallopt(3) man page.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 2^31-1 |
| Default Value |
See the |
| Syntax | Integer |
| Example | nsslapd-malloc-trim-threshold: 131072 |
2.1.127. nsslapd-maxbersize
Defines the maximum size in bytes allowed for an incoming message. This limits the size of LDAP requests that can be handled by Directory Server. Limiting the size of requests prevents some kinds of denial of service attacks.
The limit applies to the total size of the LDAP request. For example, if the request is to add an entry and if the entry in the request is larger than the configured value or the default, then the add request is denied. However, the limit is not applied to replication processes. Be cautious before changing this attribute.
This setting does not require a server restart to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 - 2 gigabytes (2,147,483,647 bytes)
Zero |
| Default Value | 2097152 |
| Syntax | Integer |
| Example | nsslapd-maxbersize: 2097152 |
2.1.128. nsslapd-maxdescriptors
The nsslapd-maxdescriptors attribute sets the maximum platform-dependent number of file descriptors that Directory Server can use. A file descriptor is used whenever a client connects to the server and for some server activities, such as index maintenance. File descriptors are also used by log files, database files (indexes and transaction logs), and as sockets for outgoing connections to other servers for replication and chaining.
The number of descriptors available for TCP/IP to serve client connections is equal to the nsslapd-maxdescriptors attribute minus the number of file descriptors for non-client connections that the nsslapd-reservedescriptors attribute determines. For more details, see nsslapd-reservedescriptors.
The number you set for the nsslapd-maxdescriptors attribute must not be greater than the total number of file descriptors that the operating system allows the ns-slapd process to use. This number differs depending on the operating system. For details about file descriptor limits and configuration, see the operating system documentation. You can use the dsktune program to suggest changes to the system kernel or TCP/IP tuning attributes.
If you set value of the nsslapd-maxdescriptors attribute too high, Directory Server queries the operating system for the maximum allowable value, and then uses this value. Directory Server also issues a warning in the error log. If you set an invalid value remotely by using ldapmodify, the server rejects the new value, keeps the old value, and responds with an error.
Increase the nsslapd-maxdescriptors attribute value if Directory Server refuses connections because it is out of file descriptors and writes the following message to the Directory Server error log file:
Not listening for new connections -- too many fds open
Not listening for new connections -- too many fds open
UNIX shells usually have configurable limits on the number of file descriptors. See the operating system documentation for further information about limit and ulimit, as these limits can often cause problems.
You must restart the server to apply changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | Operating-system dependent |
| Default Value | 1048576. The file descriptor limit of the operating system the server is running on |
| Syntax | Integer |
| Example | nsslapd-maxdescriptors: 64000 |
2.1.129. nsslapd-maxsasliosize
When a user is authenticated to Directory Server over SASL GSS-API, the server must allocate a certain amount of memory to the client to perform LDAP operations, according to how much memory the client requests. It is possible for an attacker to send such a large packet size that it crashes Directory Server or ties it up indefinitely as part of a denial of service attack.
The packet size which Directory Server will allow for SASL clients can be limited using the nsslapd-maxsasliosize attribute. This attribute sets the maximum allowed SASL IO packet size that the server will accept.
When an incoming SASL IO packet is larger than the nsslapd-maxsasliosize limit, the server immediately disconnects the client and logs a message to the error log, so that an administrator can adjust the setting if necessary.
This attribute value is specified in bytes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | * -1 (unlimited) to the maximum 32-bit integer value (2147483647) on 32-bit systems * -1 (unlimited) to the maximum 64-bit integer value (9223372036854775807) on 64-bit systems |
| Default Value | 2097152 (2MB) |
| Syntax | Integer |
| Example | nsslapd-maxsasliosize: 2097152 |
2.1.130. nsslapd-maxthreadsperconn
Defines the maximum number of threads that a connection should use. For normal operations where a client binds and only performs one or two operations before unbinding, use the default value. For situations where a client binds and simultaneously issues many requests, increase this value to allow each connection enough resources to perform all the operations. This attribute is not available from the server console.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to maximum threadnumber |
| Default Value | 5 |
| Syntax | Integer |
| Example | nsslapd-maxthreadsperconn: 5 |
2.1.131. nsslapd-minssf
A security strength factor is a relative measurement of how strong a connection is according to its key strength. The SSF determines how secure an TLS or SASL connection is. The nsslapd-minssf attribute sets a minimum SSF requirement for any connection to the server; any connection attempts that are weaker than the minimum SSF are rejected.
TLS and SASL connections can be mixed in a connection to Directory Server. These connections generally have different SSFs. The higher of the two SSFs is used to compare to the minimum SSF requirement.
Setting the SSF value to 0 means that there is no minimum setting.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any positive integer |
| Default Value | 0 (off) |
| Syntax | DirectoryString |
| Example | nsslapd-minssf: 128 |
2.1.132. nsslapd-minssf-exclude-rootdse
A security strength factor is a relative measurement of how strong a connection is according to its key strength. The SSF determines how secure an TLS or SASL connection is.
The nsslapd-minssf-exclude-rootdse attribute sets a minimum SSF requirement for any connection to the server except for queries for the root DSE. This enforces appropriate SSF values for most connections, while still allowing clients to get required information about the server configuration from the root DSE without having to establish a secure connection first.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any positive integer |
| Default Value | 0 (off) |
| Syntax | DirectoryString |
| Example | nsslapd-minssf-exclude-rootdse: 128 |
2.1.133. nsslapd-moddn-aci
This parameter controls the ACI checks when directory entries are moved from one subtree to another and using source and target restrictions in moddn operations. For backward compatibility, you can disable the ACI checks.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-moddn-aci: on |
2.1.134. nsslapd-nagle
When the value of this attribute is off, the TCP_NODELAY option is set so that LDAP responses (such as entries or result messages) are sent back to a client immediately. When the attribute is turned on, default TCP behavior applies; specifically, sending data is delayed so that additional data can be grouped into one packet of the underlying network MTU size, typically 1500 bytes for Ethernet.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-nagle: off |
2.1.135. nsslapd-ndn-cache-enabled
Normalizing distinguished names (DN) is a resource intensive task. If the nsslapd-ndn-cache-enabled parameter is enabled, Directory Server caches normalized DNs in memory. Update the nsslapd-ndn-cache-max-size parameter to set the maximum size of this cache.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-ndn-cache-enabled: on |
2.1.136. nsslapd-ndn-cache-max-size
Normalizing distinguished names (DN) is a resource intensive task. If the nsslapd-ndn-cache-enabled parameter is enabled, Directory Server caches normalized DNs in memory. The nsslapd-ndn-cache-max-size parameter sets the maximum size of this cache.
If a DN requested is not cached already, it is normalized and added. When the cache size limit is exceeded, Directory Server removes the least recently used 10,000 DNs from the cache. However, a minimum of 10,000 DNs is always kept cached.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 to the maximum 32-bit integer value (2147483647) |
| Default Value | 20971520 |
| Syntax | Integer |
| Example | nsslapd-ndn-cache-max-size: 20971520 |
2.1.137. nsslapd-outbound-ldap-io-timeout
This attribute limits the I/O wait time for all outbound LDAP connections. The default is 300000 milliseconds (5 minutes). A value of 0 means that the server does not impose a limit on I/O wait time.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to the maximum 32-bit integer value (2147483647) |
| Default Value | 300000 |
| Syntax | DirectoryString |
| Example | nsslapd-outbound-ldap-io-timeout: 300000 |
2.1.138. nsslapd-pagedsizelimit
This attribute sets the maximum number of entries to return from a search operation specifically which uses the simple paged results control. This overrides the nsslapd-sizelimit attribute for paged searches.
If this value is set to zero, then the nsslapd-sizelimit attribute is used for paged searches as well as non-paged searches.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) |
| Default Value | |
| Syntax | Integer |
| Example | nsslapd-pagedsizelimit: 10000 |
2.1.139. nsslapd-plug-in
This read-only attribute lists the DNs of the plug-in entries for the syntax and matching rule plug-ins loaded by the server.
2.1.140. nsslapd-plugin-binddn-tracking
Sets the bind DN used for an operation as the modifier of an entry, even if the operation itself was initiated by a server plug-in. The specific plug-in which performed the operation is listed in a separate operational attribute, internalModifiersname.
One change can trigger other, automatic changes in the directory tree. When a user is deleted, for example, that user is automatically removed from any groups it belonged to by the Referential Integrity Plug-in. The initial deletion of the user is performed by whatever user account is bound to the server, but the updates to the groups (by default) are shown as being performed by the plug-in, with no information about which user initiated that update. The nsslapd-plugin-binddn-tracking attribute allows the server to track which user originated an update operation, as well as the internal plug-in which actually performed it. For example:
dn: cn=my_group,ou=groups,dc=example,dc=com modifiersname: uid=jsmith,ou=people,dc=example,dc=com internalModifiersname: cn=referential integrity plugin,cn=plugins,cn=config
dn: cn=my_group,ou=groups,dc=example,dc=com
modifiersname: uid=jsmith,ou=people,dc=example,dc=com
internalModifiersname: cn=referential integrity plugin,cn=plugins,cn=configThis attribute is disabled by default.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-plugin-binddn-tracking: on |
2.1.141. nsslapd-plugin-logging
By default, even if access logging is set to record internal operations, plug-in internal operations are not logged in the access log file. Instead of enabling the logging in each plug-in’s configuration, you can control it globally with this parameter.
When enabled, plug-ins use this global setting and log access and audit events if enabled.
If nsslapd-plugin-logging is enabled and nsslapd-accesslog-level is set to record internal operations, unindexed searches and other internal operations are logged into the access log file.
In case nsslapd-plugin-logging is not set, unindexed searches from plug-ins are still logged in the Directory Server error log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-plugin-logging: off |
2.1.142. nsslapd-port
This attribute gives the TCP/IP port number used for standard LDAP communications. To run TLS over this port, use the Start TLS extended operation. This selected port must be unique on the host system; make sure no other application is attempting to use the same port number. Specifying a port number of less than 1024 means Directory Server has to be started as root.
The server sets its uid to the nsslapd-localuser value after startup. When changing the port number for a configuration directory, the corresponding server instance entry in the configuration directory must be updated.
The server has to be restarted for the port number change to be taken into account.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 65535 |
| Default Value | 389 |
| Syntax | Integer |
| Example | nsslapd-port: 389 |
Set the port number to zero (0) to disable the LDAP port if the LDAPS port is enabled.
2.1.143. nsslapd-privatenamespaces
This read-only attribute contains the list of the private naming contexts cn=config, cn=schema, and cn=monitor.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | cn=config, cn=schema, and cn=monitor |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-privatenamespaces: cn=config |
2.1.144. nsslapd-pwpolicy-inherit-global
When the fine-grained password syntax is not set, new or updated passwords are not checked even though the global password syntax is configured. To inherit the global fine-grained password syntax, set this attribute to on.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-pwpolicy-inherit-global: off |
2.1.145. nsslapd-pwpolicy-local
Turns fine-grained (subtree- and user-level) password policy on and off.
If this attribute has a value of off, all entries (except for cn=Directory Manager) in the directory are subjected to the global password policy; the server ignores any defined subtree/user level password policy.
If this attribute has a value of on, the server checks for password policies at the subtree- and user-level and enforce those policies.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-pwpolicy-local: off |
2.1.146. nsslapd-readonly
This attribute sets whether the whole server is in read-only mode, meaning that neither data in the databases nor configuration information can be modified. Any attempt to modify a database in read-only mode returns an error indicating that the server is unwilling to perform the operation.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-readonly: off |
2.1.147. nsslapd-referral
This multi-valued attribute specifies the LDAP URLs to be returned by the suffix when the server receives a request for an entry not belonging to the local tree; that is, an entry whose suffix does not match the value specified on any of the suffix attributes. For example, assume the server contains only entries:
ou=People,dc=example,dc=com
ou=People,dc=example,dc=combut the request is for this entry:
ou=Groups,dc=example,dc=com
ou=Groups,dc=example,dc=comIn this case, the referral would be passed back to the client in an attempt to allow the LDAP client to locate a server that contains the requested entry. Although only one referral is allowed per Directory Server instance, this referral can have multiple values.
To use TLS communications, the referral attribute should be in the form ldaps://server-location.
Start TLS does not support referrals.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid LDAP URL |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-referral: ldap://ldap.example.com/dc=example,dc=com |
2.1.148. nsslapd-referralmode
When set, this attribute sends back the referral for any request on any suffix.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid LDAP URL |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-referralmode: ldap://ldap.example.com |
2.1.149. nsslapd-require-secure-binds
This parameter requires that a user authenticate to the directory over a protected connection such as TLS, StartTLS, or SASL, rather than a regular connection.
This only applies to authenticated binds. Anonymous binds and unauthenticated binds can still be completed over a standard channel, even if nsslapd-require-secure-binds is turned on.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-require-secure-binds: on |
2.1.150. nsslapd-requiresrestart
This parameter lists what other core configuration attributes require that the server be restarted after a modification. This means that if any attribute listed in nsslapd-requiresrestart is changed, the new setting does not take effect until after the server is restarted. The list of attributes can be returned in an ldapsearch:
ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -b "cn=config" -s sub -x "(objectclass=*)" | grep nsslapd-requiresrestart
ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -b "cn=config" -s sub -x "(objectclass=*)" | grep nsslapd-requiresrestartThis attribute is multi-valued.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any core server configuration attribute |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-requiresrestart: nsslapd-cachesize |
2.1.151. nsslapd-reservedescriptors
The nsslapd-reservedescriptors attribute specifies the number of file descriptors that Directory Server reserves for managing non-client connections, such as index management and managing replication.
You do not need to change the nsslapd-reservedescriptors attribute value for most Directory Server installations. However, consider increasing the value on this attribute if all of the following is true:
- The server replicates to a large number of consumer servers (more than 10), or the server is maintaining a large number of index files (more than 30).
- The server serves a large number of LDAP connections.
- Error messages report that the server is unable to open file descriptors (the actual error message differs depending on the operation that the server is attempting to perform), but these error messages are not related to managing client LDAP connections.
If you increase the value for this attribute then more LDAP clients might not be able to access the directory. Along with increasing the nsslapd-reservedescriptors value, you must also increase the value of the nsslapd-maxdescriptors attribute. It might not be possible to increase the nsslapd-maxdescriptors value if the server is already using the maximum number of file descriptors that the operating system allows a process to use. If this is the case, reduce the load on the server by causing LDAP clients to search alternative directory replicas. For details, see the operating system documentation and nsslapd-maxdescriptors attribute description.
To assist in computing the number of file descriptors set for the nsslapd-reservedescriptors attribute, use the following formula:
nsslapd-reservedescriptor = 20 + (pass:quotes[NldbmBackends] * 4) + pass:quotes[NglobalIndex] + pass:quotes[ReplicationDescriptor] + pass:quotes[ChainingBackendDescriptors] + pass:quotes[PTADescriptors] + pass:quotes[SSLDescriptors]
nsslapd-reservedescriptor = 20 + (pass:quotes[NldbmBackends] * 4) + pass:quotes[NglobalIndex] +
pass:quotes[ReplicationDescriptor] + pass:quotes[ChainingBackendDescriptors] + pass:quotes[PTADescriptors] + pass:quotes[SSLDescriptors]- NldbmBackends is the number of ldbm databases.
- NglobalIndex is the total number of configured indexes for all databases including system indexes. (By default 8 system indexes and 17 additional indexes per database).
- ReplicationDescriptor is eight (8) plus the number of replicas in the server that can act as a supplier or hub (NSupplierReplica).
-
ChainingBackendDescriptors is NchainingBackend times the nsOperationConnectionsLimit (a chaining or database link configuration attribute;
10by default). -
PTADescriptors is
3if PTA is configured and0if PTA is not configured. -
SSLDescriptors is
5(4 files + 1 listensocket) if TLS is configured and0if TLS is not configured.
Restart the server to apply changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to 65535 |
| Default Value | 64 |
| Syntax | Integer |
| Example | nsslapd-reservedescriptors: 64 |
2.1.152. nsslapd-return-exact-case
Returns the exact case of attribute type names as requested by the client. Although LDAPv3-compliant clients must ignore the case of attribute names, some client applications require attribute names to match exactly the case of the attribute as it is listed in the schema when the attribute is returned by Directory Server as the result of a search or modify operation. However, most client applications ignore the case of attributes; therefore, by default, this attribute is disabled. Do not modify it unless there are legacy clients that can check the case of attribute names in results returned from the server.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-return-exact-case: off |
2.1.153. nsslapd-return-original-entrydn
Use the nsslapd-return-original-entrydn parameter to manage how Directory Server returns the distinguished name (DN) of entries to client applications during search operations.
When the nsslapd-return-original-entrydn parameter is set to on, Directory Server returns the DN exactly how it was originally added to the database by taking the value from the operational attribute dsEntryDN. As a result, if you added or modified an entry uid=User,ou=PEople,dc=ExaMPlE,DC=COM, Directory Server returns the same DN uid=User,ou=PEople,dc=ExaMPlE,DC=COM for the entry.
When the nsslapd-return-original-entrydn parameter is set to off, Directory Server generates the entry DN by putting together a Relative DN (RDN) of the entry and the base DN. Directory Server stores the base DN of the entry in the database suffix configuration under cn=userroot,cn=ldbm database,cn=plugins,cn=config in the operational attribute nsslapd-suffix. As a result, if you added an entry uid=User,ou=PEople,dc=ExaMPlE,DC=COM, but the base DN is ou=people,dc=example,dc=com, then Directory Server returns uid=User,ou=people,dc=example,dc=com during searches.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-return-original-entrydn: on |
2.1.154. nsslapd-rewrite-rfc1274
This attribute is deprecated and will be removed in a later version.
This attribute is used only for LDAPv2 clients that require attribute types to be returned with their RFC 1274 names. Set the value to on for those clients. The default is off.
2.1.155. nsslapd-rootdn
This attribute sets the distinguished name (DN) of an entry that is not subject to access control restrictions, administrative limit restrictions for operations on the directory, or resource limits in general. There does not have to be an entry corresponding to this DN, and by default there is not an entry for this DN, thus values like cn=Directory Manager are acceptable.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid distinguished name |
| Default Value | |
| Syntax | DN |
| Example | nsslapd-rootdn: cn=Directory Manager |
2.1.156. nsslapd-rootpw
This attribute sets the password associated with the Manager DN. When the root password is provided, it is encrypted according to the encryption method selected for the nsslapd-rootpwstoragescheme attribute. When viewed from the server console, this attribute shows the value *. When viewed from the dse.ldif file, this attribute shows the encryption method followed by the encrypted string of the password. The example shows the password as displayed in the dse.ldif file, not the actual password.
When the root DN is configred at server setup, a root password is required. However, it is possible for the root password to be deleted from dse.ldif by directly editing the file. In this situation, the root DN can only obtain the same access to the directory is allowed for anonymous access. Always make sure that a root password is defined in dse.ldif when a root DN is configured for the database. The pwdhash command-line utility can create a new root password.
When resetting the Directory Manager’s password from the command line, do not use curly braces ({}) in the password. The root password is stored in the format {password-storage-scheme}hashed_password. Any characters in curly braces are interpreted by the server as the password storage scheme for the root password. If that text is not a valid storage scheme or if the password that follows is not properly hashed, then the Directory Manager cannot bind to the server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid password, encrypted by any one of the encryption methods which are described in Section 6.3.44, “Password Storage Schemes”. |
| Default Value | |
| Syntax | DirectoryString {encryption_method }encrypted_Password |
| Example | nsslapd-rootpw: {SSHA}9Eko69APCJfF |
2.1.157. nsslapd-rootpwstoragescheme
This attribute sets the method used to encrypt the Directory Server’s manager password stored in the nsslapd-rootpw attribute. For further details, such as recommended strong password storage schemes, see Section 6.3.44, “Password Storage Schemes”.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | PBKDF2-SHA512 |
| Syntax | DirectoryString |
| Example | nsslapd-rootpwstoragescheme: PBKDF2-SHA512 |
2.1.158. nsslapd-rundir
This parameter sets the absolute path to the directory in which Directory Server stores run-time information, such as the PID file. The directory must be owned by the Directory Server user and group. Only this user and group must have read and write access in this directory.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any directory writable by the Directory Server user |
| Default Value | /var/run/dirsrv/ |
| Syntax | DirectoryString |
| Example | nsslapd-rundir: /var/run/dirsrv/ |
2.1.159. nsslapd-sasl-mapping-fallback
By default, only first matching SASL mapping is checked. If this mapping fails, the bind operation will fail even if there are other matching mappings that might have worked. SASL mapping fallback will keep checking all of the matching mappings.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-sasl-mapping-fallback: off |
2.1.160. nsslapd-sasl-max-buffer-size
This attribute sets the maximum SASL buffer size.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | 2097152 (2 MB) |
| Syntax | Integer |
| Example | nsslapd-sasl-max-buffer-size: 2097152 |
2.1.161. nsslapd-saslpath
Sets the absolute path to the directory containing the Cyrus-SASL SASL2 plug-ins. Setting this attribute allows the server to use custom or non-standard SASL plug-in libraries. This is usually set correctly during installation, and Red Hat strongly recommends not changing this attribute. If the attribute is not present or the value is empty, this means Directory Server is using the system provided SASL plug-in libraries which are the correct version.
If this parameter is set, the server uses the specified path for loading SASL plug-ins. If this parameter is not set, the server uses the SASL_PATH environment variable. If neither nsslapd-saslpath or SASL_PATH are set, the server attempts to load SASL plug-ins from the default location, /usr/lib/sasl2.
Changes made to this attribute will not take effect until the server is restarted.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Path to plug-ins directory. |
| Default Value | Platform dependent |
| Syntax | DirectoryString |
| Example | nsslapd-saslpath: /usr/lib/sasl2 |
2.1.162. nsslapd-schemacheck
This attribute sets whether the database schema is enforced when entries are added or modified. When this attribute has a value of on, Directory Server will not check the schema of existing entries until they are modified. The database schema defines the type of information allowed in the database. The default schema can be extended using the object classes and attribute types.
Red Hat strongly discourages turning off schema checking. This can lead to severe interoperability problems. This is typically used for very old or non-standard LDAP data that must be imported into Directory Server. If there are not a lot of entries that have this problem, consider using the extensibleObject object class in those entries to disable schema checking on a per entry basis.
Schema checking works by default when database modifications are made using an LDAP client, such as ldapmodify or when importing a database from LDIF using ldif2db. If schema checking is turned off, every entry has to be verified manually to see that they conform to the schema. If schema checking is turned on, the server sends an error message listing the entries which do not match the schema. Ensure that the attributes and object classes created in the LDIF statements are both spelled correctly and identified in dse.ldif. Either create an LDIF file in the schema directory or add the elements to 99user.ldif.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-schemacheck: on |
2.1.163. nsslapd-schemadir
This is the absolute path to the directory containing Directory Server instance-specific schema files. When the server starts up, it reads the schema files from this directory, and when the schema is modified through LDAP tools, the schema files in this directory are updated. This directory must be owned by the server user ID, and that user must have read and write permissions to the directory.
Changes made to this attribute will not take effect until the server is restarted.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid path |
| Default Value | /etc/dirsrv/instance_name/schema |
| Syntax | DirectoryString |
| Example | nsslapd-schemadir: /etc/dirsrv/instance_name/schem |
2.1.164. nsslapd-schema-ignore-trailing-spaces
Ignores trailing spaces in object class names. By default, the attribute is turned off. If the directory contains entries with object class values that end in one or more spaces, turn this attribute on. It is preferable to remove the trailing spaces because the LDAP standards do not allow them.
For performance reasons, server restart is required for changes to take effect.
An error is returned by default when object classes that include trailing spaces are added to an entry. Additionally, during operations such as add, modify, and import (when object classes are expanded and missing superiors are added) trailing spaces are ignored, if appropriate. This means that even when nsslapd-schema-ignore-trailing-spaces is on, a value such as top is not added if top is already there. An error message is logged and returned to the client if an object class is not found and it contains trailing spaces.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-schema-ignore-trailing-spaces: on |
2.1.165. nsslapd-schemamod
Online schema modifications require a lock protection that are impacting the performance. If schema modifications are disabled, setting this parameter to off can increase the performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-schemamod: on |
2.1.166. nsslapd-schemareplace
Determines whether modify operations that replace attribute values are allowed on the cn=schema entry.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off | replication-only |
| Default Value | replication-only |
| Syntax | DirectoryString |
| Example | nsslapd-schemareplace: replication-only |
2.1.167. nsslapd-scheme-list-no-upgrade-hash
The nsslapd-scheme-list-no-upgrade-hash attribute defines the list of password storage schemes that must be excluded from password updates after a successful bind. For example, if you add the MD5 password storage scheme to nsslapd-scheme-list-no-upgrade-hash, then when a user successfully binds to the server, the stored hash of the user password will not be updated if the password is hashed with MD5.
For details about supported password storage schemes, see Section 6.3.44, “Password Storage Schemes”
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any password storage scheme that Directory Server supports |
| Default Value | CRYPT, CLEAR |
| Syntax | DirectoryString |
| Example | nsslapd-scheme-list-no-upgrade-hash: CRYPT, CLEAR, MD5 |
2.1.168. nsslapd-search-return-original-type-switch
If the attribute list passed to a search contains a space followed by other characters, the same string is returned to the client. For example:
ldapsearch -b <basedn> "(filter)" "sn someothertext" dn: <matched dn> sn someothertext: <sn>
# ldapsearch -b <basedn> "(filter)" "sn someothertext"
dn: <matched dn>
sn someothertext: <sn>This behavior is disabled by default, but can be enabled using this configuration parameter.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-search-return-type-switch: off |
2.1.169. nsslapd-securelistenhost
This attribute allows multiple Directory Server instances to run on a multihomed machine (or makes it possible to limit listening to one interface of a multihomed machine). There can be multiple IP addresses associated with a single host name, and these IP addresses can be a mix of both IPv4 and IPv6. This parameter can be used to restrict the Directory Server instance to a single IP interface; this parameter also specifically sets what interface to use for TLS traffic rather than regular LDAP connections.
If a host name is given as the nsslapd-securelistenhost value, then Directory Server responds to requests for every interface associated with the host name. If a single IP interface (either IPv4 or IPv6) is given as the nsslapd-securelistenhost value, Directory Server only responds to requests sent to that specific interface. Either an IPv4 or IPv6 address can be used.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any secure host name, IPv4 or IPv6 address |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-securelistenhost: ldaps.example.com |
2.1.170. nsslapd-securePort
This attribute sets the TCP/IP port number used for TLS communications. This selected port must be unique on the host system; make sure no other application is attempting to use the same port number. Specifying a port number of less than 1024 requires that Directory Server be started as root. The server sets its uid to the nsslapd-localuser value after startup.
The server only listens to this port if it has been configured with a private key and a certificate, and nsslapd-security is set to on; otherwise, it does not listen on this port.
The server has to be restarted for the port number change to be taken into account.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to 65535 |
| Default Value | 636 |
| Syntax | Integer |
| Example | nsslapd-securePort: 636 |
2.1.171. nsslapd-securitylog-compress
Directory Server compresses the rotated security log by default. Use nsslapd-securitylog-compress attribute to manage security log file compression.
You do not need to restart the server to apply changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-securitylog-compress: on |
2.1.172. nsslapd-security
This attribute sets whether Directory Server is to accept TLS communications on its encrypted port. This attribute should be set to on for secure connections. To run with security on, the server must be configured with a private key and server certificate in addition to the other TLS configuration.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-security: off |
2.1.173. nsslapd-securitylog
The nsslapd-securitylog attribute sets the path and filename of the specialized security log that records authentication attacks, authorization issues, DOS/TCP attacks, and other security events.
To enable security logging, the nsslapd-securitylog attribute must have a valid path and the nsslapd-securitylog-logging-enabled configuration attribute must be set to on.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid filename |
| Default Value | /var/log/dirsrv/slapd-instance_name/security |
| Syntax | DirectoryString |
| Example | nsslapd-securitylog: /var/log/dirsrv/slapd-instance_name/security |
2.1.174. nsslapd-securitylog-list
The nsslapd-securitylog-list attribute provides a list of security log files.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-securitylog-list: securitylog2,securitylog3 |
2.1.175. nsslapd-securitylog-logbuffering
When set to off, the server writes all security log entries directly to the disk. With buffering, the server uses security logging even under a heavy load without impacting performance. However, when debugging, disable buffering to see the operations and their results right away instead of having to wait for the log entries to be flushed to the file. Disabling log buffering can severely impact performance in heavily loaded servers.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-security-logbuffering: on |
2.1.176. nsslapd-securitylog-logging-enabled
The nsslapd-securitylog-logging-enabled attribute turns security logging on and off.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-security-logging-enabled: on |
2.1.177. nsslapd-securitylog-logexpirationtime
The nsslapd-securitylog-logexpirationtime attribute sets the maximum age of a security log file before it is deleted.
The nsslapd-securitylog-logexpirationtime attribute provides only the number of units, when the nsslapd-securitylog-logexpirationtimeunit attribute provides the units, such as day, week, month, and so on, used for the log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) A value of -1 or 0 means that the log never expires. |
| Default Value | 12 |
| Syntax | Integer |
| Example | nsslapd-securitylog-logexpirationtime: 12 |
2.1.178. nsslapd-securitylog-logexpirationtimeunit
The nsslapd-securitylog-logexpirationtimeunit attribute sets the units for the nsslapd-securitylog-logexpirationtime attribute. If you do not specify the units for the security log maximum age or the server does not recognize the units then the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day |
| Default Value | month |
| Syntax | DirectoryString |
| Example | nsslapd-securitylog-logexpirationtimeunit: week |
2.1.179. nsslapd-securitylog-logminfreediskspace
The nsslapd-securitylog-logminfreediskspace attribute sets the minimum allowed free disk space in megabytes. When the amount of free disk space falls below the value specified on this attribute, the server deletes the oldest security logs until enough disk space appears.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 5 |
| Syntax | Integer |
| Example | nsslapd-securitylog-logminfreediskspace: 5 |
2.1.180. nsslapd-securitylog-logrotationsync-enabled
The nsslapd-securitylog-logrotationsync-enabled attribute sets whether security log rotation must be synchronized with a particular time of the day. Synchronizing log rotation this way can generate log files at a specified time during a day, such as midnight to midnight every day. This makes the analysis of the log files much easier because they then map directly to the calendar.
For security log rotation synchronization with time-of-day, you must enable the nsslapd-securitylog-logrotationsync-enabled attribute together with configured nsslapd-securitylog-logrotationsynchour and nsslapd-securitylog-logrotationsyncmin attributes.
For example, to rotate security log files every day at midnight, enable this attribute by setting its value to on, and then set the values of the nsslapd-securitylog-logrotationsynchour and nsslapd-securitylog-logrotationsyncmin attributes to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-securitylog-logrotationsync-enabled: off |
2.1.181. nsslapd-securitylog-logrotationsynchour
The nsslapd-securitylog-logrotationsynchour attribute sets the hour of the day for the security log rotation. You must use the attribute together with nsslapd-securitylog-logrotationsync-enabled and nsslapd-securitylog-logrotationsyncmin attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 23 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-securitylog-logrotationsynchour: 23 |
2.1.182. nsslapd-securitylog-logrotationsyncmin
The nsslapd-securitylog-logrotationsyncmin attribute sets the minute of the day for rotating security logs. You must use the attribute in conjunction with nsslapd-securitylog-logrotationsync-enabled and nsslapd-securitylog-logrotationsynchour attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 59 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-securitylog-logrotationsyncmin: 30 |
2.1.183. nsslapd-securitylog-logrotationtime
The nsslapd-securitylog-logrotationtime attribute sets the number of units of the time between security log file rotations. Use another configuration attribute nsslapd-securitylog-logrotationtimeunit to set the units (day, week, month, and other).
If the nsslapd-securitylog-maxlogsperdir attribute is set to 1, the server ignores the nsslapd-securitylog-logrotationtime attribute.
Directory Server rotates the log at the first write operation after the configured interval has expired regardless of the size of the log.
You can use two ways to specify the no log rotation policy. Either set the nsslapd-securitylog-maxlogsperdir attribute value to 1 or set the nsslapd-securitylog-logrotationtime attribute to -1. The server checks the nsslapd-securitylog-maxlogsperdir attribute first, and, if the attribute value is larger than 1, the server then checks the nsslapd-securitylog-logrotationtime attribute. See Section 2.1.173, “nsslapd-securitylog” for more information.
Using no log rotation policy makes the log grow indefinitely and may impact the server performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647). The -1 value means the time between security log file rotation is unlimited. |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-securitylog-logrotationtime: 5 |
2.1.184. nsslapd-securitylog-logrotationtimeunit
The nsslapd-securitylog-logrotationtimeunit attribute sets the units for nsslapd-securitylog-logrotationtime (Security log rotation time). If you do not specify the units for the security log rotation policy or the server does not recognize the units then the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day | hour | minute |
| Default Value | month |
| Syntax | DirectoryString |
| Example | nsslapd-securitylog-logrotationtimeunit: week |
2.1.185. nsslapd-securitylog-maxlogsize
The nsslapd-securitylog-maxlogsize attribute sets the maximum security log size in megabytes. When the attribute value is reached, Directory Server rotates the security log and starts writing log information to a new log file. If nsslapd-securitylog-maxlogsperdir is set to 1, the server ignores the nsslapd-securitylog-maxlogsize attribute.
When setting a maximum log size, take into consideration the following:
- The total number of log files that can be created due to the log file rotation.
- The Directory Server maintains five different log files: access log, audit log, audit fail log, error log, security log. Each log file consumes disk space.
Compare these considerations to the total amount of disk space you want to set for the security log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647). The -1 value means the log file is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-securitylog-maxlogsize: 100 |
2.1.186. nsslapd-securitylog-maxlogsperdir
The nsslapd-securitylog-maxlogsperdir attribute sets the total number of security logs that Directory Server stores in the log file directory. Each time the security log is rotated, a new log file is created. When the number of files contained in the security log directory exceeds the value of the nsslapd-securitylog-maxlogsperdir attribute, then Directory Server deletes the oldest version of the log file.
If the value of the nsslapd-securitylog-maxlogsperdir attribute is higher than 1, then check the nsslapd-securitylog-logrotationtime attribute to understand whether log rotation is set. If the nsslapd-securitylog-logrotationtime attribute has a value of -1, then no log rotation occurs. See Section 2.1.183, “nsslapd-securitylog-logrotationtime” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 10 |
| Syntax | Integer |
| Example | nsslapd-securitylog-maxlogsperdir: 5 |
2.1.187. nsslapd-securitylog-mode
The nsslapd-securitylog-mode attribute sets the access mode or file permissions with which Directory Server creates security log files. The valid values are any combination of 000 to 777 since they mirror numbered or absolute UNIX file permissions. The value must be a combination of a 3-digit number, the digits varying from 0 through 7:
- 0 - None
- 1 - Execute only
- 2 - Write only
- 3 - Write and execute
- 4 - Read only
- 5 - Read and execute
- 6 - Read and write
- 7 - Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the second digit represents the group’s permissions, and the third digit represents everyone’s permissions. When changing the default value, remember that 000 does not allow access to the logs and that allowing write permissions to everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that the server creates. The mode is set when the log rotates to a new file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 000 through 777 |
| Default Value | 600 |
| Syntax | Integer |
| Example | nsslapd-securitylog-mode: 600 |
2.1.188. nsslapd-sizelimit
This attribute sets the maximum number of entries to return from a search operation. If this limit is reached, ns-slapd returns any entries it has located that match the search request, as well as an exceeded size limit error.
When no limit is set, ns-slapd returns every matching entry to the client regardless of the number found. To set a no limit value whereby Directory Server waits indefinitely for the search to complete, specify a value of -1 for this attribute in the dse.ldif file.
This limit applies to everyone, regardless of their organization.
A value of -1 on this attribute in dse.ldif file is the same as leaving the attribute blank in the server console, in that it causes no limit to be used. This cannot have a null value in dse.ldif file, as it is not a valid integer. It is possible to set it to 0, which returns size limit exceeded for every search.
The corresponding user-level attribute is nsSizeLimit.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 2000 |
| Syntax | Integer |
| Example | nsslapd-sizelimit: 2000 |
2.1.189. nsslapd-snmp-index
This parameter controls the SNMP index number of Directory Server instance.
If you have multiple Directory Server instances on the same host listening all on port 389 but on different network interfaces, this parameter allows you to set different SNMP index numbers for each instance.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-snmp-index: 0 |
2.1.190. nsslapd-ssl-check-hostname
This attribute sets whether an TLS-enabled Directory Server should verify authenticity of a request by matching the host name against the value assigned to the common name (cn) attribute of the subject name (subjectDN field) in the certificate being presented. By default, the attribute is set to on. If it is on and if the host name does not match the cn attribute of the certificate, appropriate error and audit messages are logged.
For example, in a replicated environment, messages similar to the following are logged in the supplier server’s log files if it finds that the peer server’s host name does not match the name specified in its certificate:
Red Hat recommends turning this attribute on to protect Directory Server’s outbound TLS connections against a man in the middle (MITM) attack.
DNS and reverse DNS must be set up correctly in order for this to work; otherwise, the server cannot resolve the peer IP address to the host name in the subject DN in the certificate.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-ssl-check-hostname: on |
2.1.191. nsslapd-SSLclientAuth
The nsslapd-SSLclientAuth parameter will be deprecated in a future release and is currently maintained for backward compatibility. Use the new parameter nsSSLClientAuth, stored under cn=encryption,cn=config, instead. See Section 2.3.5, “nsSSLClientAuth”.
2.1.192. nsslapd-statlog-level
Use the nsslapd-statlog-level parameter to enable logging of statistics per an operation in the access log without the impact on the Directory Server performance.
Directory Server supports collection of statistics related to indexes used during search operations. When you set nsslapd-statlog-level to 1, the access log starts to collect the number of index lookups (database read operations) for each key in the index.
For example, a directory has one million uid entries which values start with user_ and the search operation uses the filter (uid=user_*). Directory Server creates ^us, use, ser, and er_ index keys. With the setting nsslapd-statlog-level=1, the access log shows the following information:
STAT read index: attribute=uid key(sub)=er_ count 1000000 STAT read index: attribute=uid key(sub)=ser count 1000000 STAT read index: attribute=uid key(sub)=use count 1000000 STAT read index: attribute=uid key(sub)=^us count 1000000 STAT read index: duration 0.001010276
STAT read index: attribute=uid key(sub)=er_ count 1000000
STAT read index: attribute=uid key(sub)=ser count 1000000
STAT read index: attribute=uid key(sub)=use count 1000000
STAT read index: attribute=uid key(sub)=^us count 1000000
STAT read index: duration 0.001010276
Knowing the number of lookups and the overall duration of an index lookups helps to diagnose why filters, such as (uid=user_*), are expensive.
You need to restart the server to apply changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values |
|
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-statlog-level: 1 |
2.1.193. nsslapd-syntaxcheck
This attribute validates all modifications to entry attributes to make sure that the new or changed values conform to the required syntax for that attribute type. Any changes which do not conform to the proper syntax are rejected, when this attribute is enabled. All attribute values are validated against the syntax definitions in RFC 4514.
By default, this is turned on.
Syntax validation is only run against new or modified attributes; it does not validate the syntax of existing attribute values. Syntax validation is triggered for LDAP operations such as adds and modifies; it does not happen after operations like replication, since the validity of the attribute syntax should be checked on the originating supplier.
This validates all supported attribute types for Directory Server, with the exception of binary syntaxes (which cannot be verified) and non-standard syntaxes, which do not have a defined required format. The unvalidated syntaxes are as follows:
- Fax (binary)
- OctetString (binary)
- JPEG (binary)
- Binary (non-standard)
- Space Insensitive String (non-standard)
- URI (non-standard)
The nsslapd-syntaxcheck attribute sets whether to validate and reject attribute modifications. This can be used with the nsslapd-syntaxlogging attribute to write warning messages about invalid attribute values to the error logs.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nnsslapd-syntaxcheck: on |
2.1.194. nsslapd-syntaxlogging
This attribute sets whether to log syntax validation failures to the errors log. By default, this is turned off.
If the nsslapd-syntaxcheck attribute is enabled (the default) and the nsslapd-syntaxlogging attribute is also enabled, then any invalid attribute change is rejected and written to the errors log. If only nsslapd-syntaxlogging is enabled and nsslapd-syntaxcheck is disabled, then invalid changes are allowed to proceed, but a warning message is written to the error log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nnsslapd-syntaxlogging: off |
2.1.195. nsslapd-threadnumber
This performance tuning-related value sets the number of threads, Directory Server creates at startup. If the value is set to -1 (default), Directory Server enables the optimized auto-tuning based on the available hardware. Note that if auto-tuning is enabled, the nsslapd-threadnumber shows the auto-generated number of threads while Directory Server is running.
Red Hat recommends to use the auto-tuning setting for optimized performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum number of threads supported by the system’s thread and processor. limits |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-threadnumber: -1 |
2.1.196. nsslapd-timelimit
This attribute sets the maximum number of seconds allocated for a search request. If this limit is reached, Directory Server returns any entries it has located that match the search request, as well as an exceeded time limit error.
When no limit is set, ns-slapd returns every matching entry to the client regardless of the time it takes. To set a no limit value whereby Directory Server waits indefinitely for the search to complete, specify a value of -1 for this attribute in the dse.ldif file. A value of zero (0) causes no time to be allowed for searches. The smallest time limit is 1 second.
A value of -1 on this attribute in thedse.ldif is the same as leaving the attribute blank in the server console in that it causes no limit to be used. However, a negative integer cannot be set in this field in the server console, and a null value cannot be used in the dse.ldif entry, as it is not a valid integer.
The corresponding user-level attribute is nsTimeLimit.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) in seconds |
| Default Value | 3600 |
| Syntax | Integer |
| Example | nsslapd-timelimit: 3600 |
2.1.197. nsslapd-tmpdir
This is the absolute path of the directory the server uses for temporary files. The directory must be owned by the server user ID and the user must have read and write access. No other user ID should have read or write acces to the directory. The default value is /tmp.
Changes made to this attribute will not take effect until the server is restarted.
2.1.198. nsslapd-unhashed-pw-switch
When you update the userPassword attribute, Directory Server encrypts the password and stores it in userPassword. However, in certain situations, for example, when synchronizing passwords with Active Directory (AD), Directory Server must pass the unencrypted password to a plug-in. In this case, the server stores the unencrypted password in the temporary unhashed#user#password attribute in the so-called entry extension and, depending on the scenario, also in the changelog. Note that Directory Server does not store the temporary unhashed#user#password attribute on the server’s hard disk.
The nsslapd-unhashed-pw-switch parameter controls whether and how Directory Server stores the unencrypted password. For example, you must set nsslapd-unhashed-pw-switch to on to synchronize passwords from Directory Server to Active Directory.
You can set the parameter to one of the following values:
-
off: Directory Server neither stores the unencrypted password in the entry extension nor in the changelog. Set this value if you do not use password synchronization with AD or any plug-ins that requires access to the unencrypted password. -
on: Directory Server stores the unencrypted password in the entry extension and in the changelog. Set this value if you configure password synchronization with AD. -
nolog: Directory Server stores the unencrypted password only in the entry extension but not in the changelog. Set this value if local Directory Server plug-ins require access to the unencrypted password, but no password synchronization with AD is configured.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | off | on | nolog |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-unhashed-pw-switch: off |
2.1.199. nsslapd-validate-cert
If Directory Server is configured to run in TLS and its certificate expires, then Directory Server cannot be started. The nsslapd-validate-cert parameter sets how Directory Server should respond when it attempts to start with an expired certificate:
-
warnallows Directory Server to start successfully with an expired certificate, but it sends a warning message that the certificate has expired. This is the default setting. -
onvalidates the certificate and will prevent the server from restarting if the certificate is expired. This sets a hard failure for expired certificates. -
offdisables all certificate expiration validation, so the server can start with an expired certificate without logging a warning.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | warn | on | off |
| Default Value | warn |
| Syntax | DirectoryString |
| Example | nsslapd-validate-cert: warn |
2.1.200. nsslapd-verify-filter-schema
The nsslapd-verify-filter-schema parameter defines how Directory Server verifies search filters with attributes that are not specified in the schema.
You can set nsslapd-verify-filter-schema to one of the following options:
-
reject-invalid: Directory Server rejects the filter with an error if it contains any unknown element. process-safe: Directory Server replaces unknown components with an empty set, and logs a warning with thenotes=Fflag in the/var/log/dirsrv/slapd-instance_name/accesslog file.Before you switch
nsslapd-verify-filter-schemafromwarn-invalidorofftoprocess-safe, monitor the access log and fix queries from applications that cause log entries withnotes=Fflag. Otherwise, the operation result changes and Directory Server might not return all the matching entries.-
warn-invalid: Directory Server logs a warning with thenotes=Fflag in the/var/log/dirsrv/slapd-instance_name/accesslog file, and continues scanning the full database. -
off: Directory Server does not verify filters.
Note that, for example, if you set nsslapd-verify-filter-schema to warn-invalid or off, a filter, such as (&(non_exististent_attribute=example)(uid=user_name)) evaluates the uid=user_name entry and returns it only if it contains contains non_exististent_attribute=example. If you set nsslapd-verify-filter-schema to process-safe, Directory Server does not evaluate that entry and does not return it.
Setting nsslapd-verify-filter-schema to reject-invalid or process-safe can prevent high load due to unindexed searches for attributes that are not specified in the schema.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | reject-invalid, process-safe, warn-invalid, off |
| Default Value | process-safe |
| Syntax | DirectoryString |
| Example | nsslapd-verify-filter-schema: process-safe |
2.1.201. nsslapd-versionstring
This attribute sets the server version number. The build data is automatically appended when the version string is displayed.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid server version number. |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-versionstring: Red Hat-Directory/{VER} |
2.1.202. nsslapd-workingdir
This is the absolute path of the directory that the server uses as its current working directory after startup. This is the value that the server would return as the value of the getcwd() function, and the value that the system process table shows as its current working directory. This is the directory a core file is generated in. The server user ID must have read and write access to the directory, and no other user ID should have read or write access to it. The default value for this attribute is the same directory containing the error log, which is usually /var/log/dirsrv/slapd-instance.
Changes made to this attribute will not take effect until the server is restarted.
2.1.203. nsslapd-numlisteners
The nsslapd-numlisteners attribute specifies the number of listener threads the Directory Server can use to monitor established connections. You can improve the response times when the server experiences a large number of client connections by increasing the attribute value.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 1 - 4 |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-numlisteners: 2 |
You must restart the server after you change the value of the nsslapd-numlisteners attribute.
2.1.204. passwordAdminSkipInfoUpdate
With a new passwordAdminSkipInfoUpdate: on/off setting under the cn=config entry, you can perform a fine grained control over password updates that password administrators manage. When you set this setting to on, Directory Server updates only the the password and does not update attributes, such as passwordHistory,passwordExpirationTime,passwordRetryCount, pwdReset, and passwordExpWarned.
Password administrators can use this setting to bypass password syntax checks and password expiration settings configured in the global and local login policies that use passwordExpirationTime and pwdMustChange attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordAdminSkipInfoUpdate: on |
2.1.205. passwordAllowChangeTime
This attribute specifies the length of time that must pass before the user is allowed to change his password.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any integer |
| Default Value | |
| Syntax | DirectoryString |
| Example | passwordAllowChangeTime: 5h |
2.1.206. passwordBadWords
The passwordBadWords parameter defines a comma-separated list of strings that users are not allowed to use in a password.
Note that Directory Server does a case-insensitive comparison of the strings.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any string |
| Default Value | "" |
| Syntax | DirectoryString |
| Example | passwordBadWords: example |
2.1.207. passwordChange
Indicates whether users may change their passwords.
This can be abbreviated to pwdAllowUserChange.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | passwordChange: on |
2.1.208. passwordCheckSyntax
This attribute sets whether the password syntax is checked before the password is saved. The password syntax checking mechanism checks that the password meets or exceeds the password minimum length requirement and that the string does not contain any trivial words, such as the user’s name or user ID or any attribute value stored in the uid, cn, sn, givenName, ou, or mail attributes of the user’s directory entry.
Password syntax includes several different categories for checking:
- The length of string or tokens to use to compare when checking for trivial words in the password (for example, if the token length is three, then no string of three sequential characters in the user’s UID, name, email address, or other parameters can be used in the password)
- Minimum number of number characters (0-9)
- Minimum number of uppercase ASCII alphabetic characters
- Minimum number of lowercase ASCII alphabetic characters
-
Minimum number of special ASCII characters, such as
!@#$ - Minimum number of 8-bit characters
- Minimum number of character categories required per password; a category can be upper- or lower-case letters, special characters, digits, or 8-bit characters
This can be abbreviated to pwdCheckSyntax.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordCheckSyntax: off |
2.1.209. passwordDictCheck
If set to on, the passwordDictCheck parameter checks the password against the CrackLib dictionary. Directory Server rejects the password if the new password contains a dictionary word.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordDictCheck: off |
2.1.210. passwordExp
Indicates whether user passwords expire after a given number of seconds. By default, user passwords do not expire. Once password expiration is enabled, set the number of seconds after which the password expires using the passwordMaxAge attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordExp: on |
2.1.211. passwordExpirationTime
This attribute specifies the length of time that passes before the user’s password expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any date, in integers |
| Default Value | none |
| Syntax | GeneralizedTime |
| Example | passwordExpirationTime: 202009011953 |
2.1.212. passwordExpWarned
This attribute indicates that a password expiration warning has been sent to the user.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | true | false |
| Default Value | none |
| Syntax | DirectoryString |
| Example | passwordExpWarned: true |
2.1.213. passwordGraceLimit
This attribute is only applicable if password expiration is enabled. After the user’s password has expired, the server allows the user to connect for the purpose of changing the password. This is called a grace login. The server allows only a certain number of attempts before completely locking out the user. This attribute is the number of grace logins allowed. A value of 0 means the server does not allow grace logins.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 (off) to any reasonable integer |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordGraceLimit: 3 |
2.1.214. passwordHistory
Enables password history. Password history refers to whether users are allowed to reuse passwords. By default, password history is disabled, and users can reuse passwords. If this attribute is set to on, the directory stores a given number of old passwords and prevents users from reusing any of the stored passwords. Set the number of old passwords the Directory Server stores using the passwordInHistory attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordHistory: on |
2.1.215. passwordInHistory
Indicates the number of passwords Directory Server stores in history. Passwords that are stored in history cannot be reused by users. By default, the password history feature is disabled, meaning that Directory Server does not store any old passwords, and so users can reuse passwords. Enable password history using the passwordHistory attribute.
To prevent users from rapidly cycling through the number of passwords that are tracked, use the passwordMinAge attribute.
This can be abbreviated to pwdInHistory.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range |
0 to 24 passwords. |
| Default Value | 6 |
| Syntax | Integer |
| Example | passwordInHistory: 7 |
2.1.216. passwordIsGlobalPolicy
This attribute controls whether password policy attributes are replicated.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordIsGlobalPolicy: off |
2.1.217. passwordLegacyPolicy
Enables legacy password behavior. Older LDAP clients expected to receive an error to lock a user account once the maximum failure limit was exceeded. For example, if the limit were three failures, then the account was locked at the fourth failed attempt. Newer clients, however, expect to receive the error message when the failure limit is reached. For example, if the limit is three failures, then the account should be locked at the third failed attempt.
Because locking the account when the failure limit is exceeded is the older behavior, it is considered legacy behavior. It is enabled by default, but can be disabled to allow the new LDAP clients to receive the error at the expected time.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | passwordLegacyPolicy: on |
2.1.218. passwordLockout
Indicates whether users are locked out of the directory after a given number of failed bind attempts. By default, users are not locked out of the directory after a series of failed bind attempts. If account lockout is enabled, set the number of failed bind attempts after which the user is locked out using the passwordMaxFailure attribute.
This can be abbreviated to pwdLockOut.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordLockout: off |
2.1.219. passwordLockoutDuration
Indicates the amount of time in seconds during which users are locked out of the directory after an account lockout. The account lockout feature protects against hackers who try to break into the directory by repeatedly trying to guess a user’s password. Enable and disable the account lockout feature using the passwordLockout attribute.
This can be abbreviated to pwdLockoutDuration.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) in seconds |
| Default Value | 3600 |
| Syntax | Integer |
| Example | passwordLockoutDuration: 3600 |
2.1.220. passwordMaxAge
Indicates the number of seconds after which user passwords expire. To use this attribute, password expiration has to be enabled using the passwordExp attribute.
This can be abbreviated to pwdMaxAge.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) in seconds |
| Default Value | 8640000 (100 days) |
| Syntax | Integer |
| Example | passwordMaxAge: 100 |
2.1.221. passwordMaxClassChars
If you set the passwordMaxClassChars parameter to a value higher than 0, Directory Server prevents setting a password that has more consecutive characters from the same category than the value set in the parameter. If enabled, Directory Server checks for consecutive characters of the following categories:
- digits
- alpha characters
- lower case
- upper case
For example, if you set passwordMaxClassChars to 3, passwords containing, for example, jdif or 1947 are not allowed.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 (disabled) to maximum 32-bit integer (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMaxClassChars: 0 |
2.1.222. passwordMaxFailure
Indicates the number of failed bind attempts after which a user is locked out of the directory. By default, account lockout is disabled. Enable account lockout by modifying the passwordLockout attribute.
This can be abbreviated to pwdMaxFailure.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to maximum integer bind failures |
| Default Value | 3 |
| Syntax | Integer |
| Example | passwordMaxFailure: 3 |
2.1.223. passwordMaxRepeats
Maximum number of times the same character can appear sequentially in the password. Zero (0) is off. Integer values reject any password which used a character more than that number of times; for example, 1 rejects characters that are used more than once (aa) and 2 rejects characters used more than twice (aaa).
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMaxRepeats: 1 |
2.1.224. passwordMaxSeqSets
If you set the passwordMaxSeqSets parameter to a value higher than 0, Directory Server rejects passwords with duplicate monotonic sequences exceeding the length set in the parameter. For example, if you set passwordMaxSeqSets to 2, setting the password to azXYZ_XYZ-g is not allowed, because XYZ appears twice in the password.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 (disabled) to the maximum 32 bit integer value (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMaxSeqSets: 0 |
2.1.225. passwordMaxSequence
If you set the passwordMaxSequence parameter to a value higher than 0, Directory Server rejects new passwords with a monotonic sequence longer than the value set in passwordMaxSequence. For example, if you set the parameter to 3, Directory Server rejects passwords containing strings such as 1234 or dcba.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 (disabled) to the maximum 32 bit integer value (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMaxSequence: 0 |
2.1.226. passwordMin8Bit
This sets the minimum number of 8-bit characters the password must contain.
The 7-bit checking for userPassword must be disabled to use this.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMin8Bit: 0 |
2.1.227. passwordMinAge
Indicates the number of seconds that must pass before a user can change their password. Use this attribute in conjunction with the passwordInHistory (number of passwords to remember) attribute to prevent users from quickly cycling through passwords so that they can use their old password again. A value of zero (0) means that the user can change the password immediately.
This can be abbreviated to pwdMaxFailure.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to valid maximum integer |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinAge: 150 |
2.1.228. passwordMinAlphas
This attribute sets the minimum number of alphabetic characters password must contain.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinAlphas: 4 |
2.1.229. passwordMinCategories
This sets the minimum number of character categories that are represented in the password. The categories are:
- Lowercase alphabetic characters
- Uppercase alphabetic characters
- Numbers
- Special ASCII charactes, such as $ and punctuation marks
- 8-bit characters
For example, if the value of this attribute were set to 2, and the user tried to change the password to aaaaa, the server would reject the password because it contains only lower case characters, and therefore contains characters from only one category. A password of aAaAaA would pass because it contains characters from two categories, uppercase and lowercase.
The default is 3, which means that if password syntax checking is enabled, valid passwords have to have three categories of characters.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 5 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinCategories: 2 |
2.1.230. PasswordMinDigits
This sets the minimum number of digits a password must contain.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinDigits: 3 |
2.1.231. passwordMinLength
This attribute specifies the minimum number of characters that must be used in Directory Server user password attributes. In general, shorter passwords are easier to crack. Directory Server enforces a minimum password of eight characters. This is long enough to be difficult to crack but short enough that users can remember the password without writing it down.
This can be abbreviated to pwdMinLength.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 2 to 512 characters |
| Default Value | 8 |
| Syntax | Integer |
| Example | passwordMinLength: 8 |
2.1.232. PasswordMinLowers
This attribute sets the minimum number of lower case letters password must contain.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinLowers: 1 |
2.1.233. PasswordMinSpecials
This attribute sets the minimum number of special, or not alphanumeric, characters a password must contain.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinSpecials: 1 |
2.1.234. PasswordMinTokenLength
This attribute sets the smallest attribute value length that is used for trivial words checking. For example, if the PasswordMinTokenLength is set to 3, then a givenName of DJ does not result in a policy that rejects DJ from being in the password, but the policy rejects a password comtaining the givenName of Bob.
Directory Server checks the minimum token length against values in the following attributes:
-
uid -
cn -
sn -
givenName -
mail -
ou
If Directory Server should check additional attributes, you can set them in the passwordUserAttributes parameter. For details, see Section 2.1.246, “passwordUserAttributes”.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to 64 |
| Default Value | 3 |
| Syntax | Integer |
| Example | passwordMinTokenLength: 3 |
2.1.235. PasswordMinUppers
This sets the minimum number of uppercase letters password must contain.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinUppers: 2 |
2.1.236. passwordMustChange
Indicates whether users must change their passwords when they first bind to Directory Server or when the password has been reset by the Manager DN.
This can be abbreviated to pwdMustChange.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordMustChange: off |
2.1.237. passwordPalindrome
If you enable the passwordPalindrome parameter, Directory Server rejects a password if the new password contains a palindrome.
A palindrome is a string which reads the same forward as backward, such as abc11cba.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordPalindrome: off |
2.1.238. passwordResetFailureCount
Indicates the amount of time in seconds after which the password failure counter resets. Each time an invalid password is sent from the user’s account, the password failure counter is incremented. If the passwordLockout attribute is set to on, users are locked out of the directory when the counter reaches the number of failures specified by the passwordMaxFailure attribute (within 600 seconds by default). After the amount of time specified by the passwordLockoutDuration attribute, the failure counter is reset to zero (0).
This can be abbreviated to pwdFailureCountInterval.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) in seconds |
| Default Value | 600 |
| Syntax | Integer |
| Example | passwordResetFailureCount: 600 |
2.1.239. passwordSendExpiringTime
When a client requests the password expiring control, Directory Server returns the "time to expire" value only if the password is within the warning period. To provide compatibility with existing clients that always expect this value to be returned - regardless if the password expiration time is within the warning period - the passwordSendExpiringTime parameter can be set to on.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordSendExpiringTime: off |
2.1.240. passwordStorageScheme
This attribute sets the method used to encrypt user passwords stored in userPassword attributes. For further details, such as recommended strong password storage schemes, see Section 6.3.44, “Password Storage Schemes”.
Red Hat recommends not setting this attribute. I the value is not set, Directory Server automatically uses the strongest supported password storage scheme available. If a future Directory Server update changes the default value to increase security, passwords will be automatically encrypted using the new storage scheme if a user set a passwords.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | PBKDF2-SHA512 |
| Syntax | DirectoryString |
| Example | passwordStorageScheme: PBKDF2-SHA512 |
2.1.241. passwordTPRDelayExpireAt
The passwordTPRDelayExpireAt attribute is part of the password policy. After the administrator sets a temporary password to a user account, passwordTPRDelayExpireAt defines the time in seconds before the temporary password expires.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | -1 (disabled) to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | passwordTPRDelayExpireAt: 3600 |
2.1.242. passwordTPRDelayValidFrom
The passwordTPRDelayValidFrom attribute is part of the password policy. After the administrator sets a temporary password to a user account, passwordTPRDelayValidFrom defines the time in seconds before a temporary password can be used.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | -1 (disabled) to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | passwordTPRDelayValidFrom: 60 |
2.1.243. passwordTPRMaxUse
The passwordTPRMaxUse attribute is part of the password policy. The attribute sets the number of times a user can authenticate successfully or not before the temporary password expires. If the authentication is successful, Directory Server only allows the user to change the password before other operations are possible. If the user does not change the password, the operation is terminated. The counter of the number of authentication attempts is increased regardless whether the authentication was successful or not.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | -1 (disabled) to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | passwordTPRMaxUse: 5 |
2.1.244. passwordTrackUpdateTime
Sets whether to record a separate timestamp specifically for the last time that the password for an entry was changed. If this is enabled, then it adds the pwdUpdateTime operational attribute to the user account entry (separate from other update times, like modifyTime).
Using this timestamp can make it easier to synchronize password changes between different LDAP stores, such as Active Directory.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordTrackUpdateTime: off |
2.1.245. passwordUnlock
Indicates whether users are locked out of the directory for a specified amount of time or until the administrator resets the password after an account lockout. The account lockout feature protects against malicious actors who try to break into the directory by repeatedly trying to guess a user’s password. If this passwordUnlock attribute is set to off and the operational attribute accountUnlockTime has a value of 0, then the account is locked indefinitely.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | passwordUnlock: off |
2.1.246. passwordUserAttributes
By default, if you set a minimum token length in the passwordMinTokenLength parameter, Directory Server checks the tokens only against certain attributes. For details, see Section 2.1.234, “PasswordMinTokenLength”.
The passwordUserAttributes parameter enables you to set a comma-separated list of additional attributes that Directory Server should check.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any string |
| Default Value | "" |
| Syntax | DirectoryString |
| Example | passwordUserAttributes: telephoneNumber, l |
2.1.247. passwordWarning
Indicates the number of seconds before a user’s password is due to expire that the user receives a password expiration warning control on their next LDAP operation. Depending on the LDAP client, the user may also be prompted to change their password at the time the warning is sent.
This can be abbreviated to pwdExpireWarning.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) in seconds |
| Default Value | 86400 (1 day) |
| Syntax | Integer |
| Example | passwordWarning: 86400 |
2.1.248. retryCountResetTime
The retryCountResetTime attribute contains the date and time in UTC-format after which the passwordRetryCount attribute will be reset to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | Any valid time stamp in UTC format |
| Default Value | none |
| Syntax | Generalized Time |
| Example | retryCountResetTime: 20190618094419Z |
2.2. Changelog attributes
The changelog attributes contain the changes logged in the changelog.
2.2.1. changeLog
This attribute contains the distinguished name of the entry which contains the set of entries comprising the server’s changelog.
| OID | 2.16.840.1.113730.3.1.35 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
2.2.2. changeNumber
This attribute is always present. It contains an integer which uniquely identifies each change made to a directory entry. This number is related to the order in which the change occurred. The higher the number, the later the change.
| OID | 2.16.840.1.113730.3.1.5 |
| Syntax | Integer |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
2.2.3. changes
This attribute contains the changes made to the entry for add and modify operations in LDIF format.
| OID | 2.16.840.1.113730.3.1.8 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
2.2.4. changeTime
This attribute defines a time, in a YYMMDDHHMMSS format, when the entry was added.
| OID | 2.16.840.1.113730.3.1.77 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
2.2.5. changeType
This attribute specifies the type of LDAP operation, add, delete, modify, or modrdn. For example:
changeType: modify
changeType: modify| OID | 2.16.840.1.113730.3.1.7 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
2.2.6. deleteOldRdn
In the case of modrdn operations, this attribute specifies whether the old RDN was deleted.
A value of zero (0) will delete the old RDN. Any other non-zero value will keep the old RDN. (Non-zero values can be negative or positive integers.)
| OID | 2.16.840.1.113730.3.1.10 |
| Syntax | Boolean |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
2.2.7. filterInfo
This is used by the changelog for processing replication.
| OID | 2.16.840.1.113730.3.1.206 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
2.2.8. newRdn
In the case of modrdn operations, this attribute specifies the new RDN of the entry.
| OID | 2.16.840.1.113730.3.1.9 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
2.2.9. newSuperior
In the case of modrdn operations, this attribute specifies the new parent (superior) entry for the moved entry.
| OID | 2.16.840.1.113730.3.1.11 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
2.2.10. targetDn
This attribute contains the DN of the entry that was affected by the LDAP operation. In the case of a modrdn operation, the targetDn attribute contains the DN of the entry before it was modified or moved.
| OID | 2.16.840.1.113730.3.1.6 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
2.3. cn=encryption,cn=config
Encryption related attributes are stored under the cn=encryption,cn=config entry. The cn=encryption,cn=config entry is an instance of the nsslapdEncryptionConfig object class.
2.3.1. allowWeakCipher
This attribute controls whether weak ciphers are allowed or rejected. The default depends on the value set in the nsSSL3Ciphers parameter.
Ciphers are considered weak, if:
They are exportable.
Exportable ciphers are labeled
EXPORTin the cipher name. For example, inTLS_RSA_EXPORT_WITH_RC4_40_MD5.They are symmetrical and weaker than the 3DES algorithm.
Symmetrical ciphers use the same cryptographic keys for both encryption and decryption.
- The key length is shorter than 128 bits.
The server has to be restarted for changes to this attribute to take effect.
| Entry DN | cn=encryption,cn=config |
| Valid Values | on | off |
| Default Value |
|
| Syntax | DirectoryString |
| Example | allowWeakCipher: on |
2.3.2. allowWeakDHParam
The network security services (NSS) libraries linked with Directory Server requires minimum of 2048-bit Diffie-Hellman (DH) parameters. However, some clients connecting to Directory Server, such as Java 1.6 and 1.7 clients, only support 1024-bit DH parameters. The allowWeakDHParam parameter allows you to enable support for weak 1024-bit DH parameters in Directory Server.
The server has to be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=encryption,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | allowWeakDHParam: off |
2.3.3. nsSSL3Ciphers
This attribute specifies the set of TLS encryption ciphers Directory Server uses during encrypted communications.
The value set in this parameter influences the default value of the allowWeakCipher parameter. For details, see Section 2.3.1, “allowWeakCipher”.
| Parameter | Description |
|---|---|
| Entry DN | cn=encryption,cn=config |
| Valid Values | Comma separated list of NSS supported ciphers. Additionally, the following parameters are possible: * default: Enables the default ciphers advertised by NSS except weak ciphers. For further information, see List supported cipher suites for SSL connections.
* +all: All ciphers are enabled. This includes weak ciphers, if the * -all: All ciphers are disabled. |
| Default Value | default |
| Syntax | DirectoryString
Use the plus (
To enable all ciphers — except |
| Example | nsSSL3Ciphers: +TLS_RSA_AES_128_SHA,+TLS_RSA_AES_256_SHA,+TLS_RSA_WITH_AES_128_GCM_SHA256,-RSA_NULL_SHA |
2.3.4. nsSSLActivation
This attribute shows whether an TLS cipher family is enabled for a given security module.
| Entry DN | cn=encryptionType,cn=encryption,cn=config |
| Valid Values | on | off |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsSSLActivation: on |
2.3.5. nsSSLClientAuth
This attribute shows how Directory Server enforces client authentication. It accepts the following values:
-
off- Directory Server will not accept client authentication -
allowed(default) - Directory Server will accept client authentication, but not require it -
required- all clients must use client authentication.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | off | allowed | required |
| Default Value | allowed |
| Syntax | DirectoryString |
| Example | nsSSLClientAuth: allowed |
2.3.6. nsSSLEnabledCiphers
Directory Server generates the multi-valued nsSSLEnabledCiphers attribute automatically. The attribute is read-only and displays the ciphers Directory Server currently uses. The list might not be the same as you set in the nsSSL3Ciphers attribute. For example, if you set weak ciphers in the nsSSL3Ciphers attribute, but allowWeakCipher is disabled, the nsSSLEnabledCiphers attribute neither lists the weak ciphers nor does Directory Server use them.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | The values of this attribute are auto-generated and read-only. |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsSSLClientAuth: TLS_RSA_WITH_AES_256_CBC_SHA::AES::SHA1::256 |
2.3.7. nsSSLPersonalitySSL
This attribute contains the certificate name to use for SSL.
| Entry DN | cn=encryption,cn=config |
| Valid Values | A certificate nickname |
| Default Value | |
| Syntax | DirectoryString |
| Example: | nsSSLPersonalitySSL: Server-Cert |
2.3.8. nsSSLSessionTimeout
This attribute sets the lifetime duration of a TLS connection. The minimum timeout value is 5 seconds. If a smaller value is set, then it is automatically replaced by 5 seconds. A value greater than the maximum value in the valid range below is replaced by the maximum value in the range.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=encryption,cn=config |
| Valid Range | 5 seconds to 24 hours |
| Default Value | 0, which means use the maximum value in the valid range above. |
| Syntax | Integer |
| Example | nsSSLSessionTimeout: 5 |
2.3.9. nsSSLSupportedCiphers
This attribute contains the supported ciphers for the server.
| Entry DN | cn=encryption,cn=config |
| Valid Values | A specific family, cipher, and strength string |
| Default Value | |
| Syntax | DirectoryString |
| Example: | nsSSLSupportedCiphers: TLS_RSA_WITH_AES_256_CBC_SHA::AES::SHA1::256 |
2.3.10. nsSSLToken
This attribute contains the name of the token (security module) used by the server.
| Entry DN | cn=encryption,cn=config |
| Valid Values | A module name |
| Default Value | |
| Syntax | DirectoryString |
| Example: | nsSSLToken: internal (software) |
2.3.11. nsTLS1
Enables TLS version 1. The ciphers used with TLS are defined in the nsSSL3Ciphers attribute.
If the sslVersionMin and sslVersionMax parameters are set in conjunction with nsTLS1, Directory Server selects the most secure settings from these parameters.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=encryption,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsTLS1: on |
2.3.12. nsTLSAllowClientRenegotiation
Directory Server uses the SSL_OptionSet() network security services (NSS) function with the SSL_ENABLE_RENEGOTIATION option to control the TLS renegotiation behavior of NSS.
The nsTLSAllowClientRenegotiation attribute controls which values Directory Server passes to the SSL_ENABLE_RENEGOTIATION option:
-
If you set
nsTLSAllowClientRenegotiation: on, Directory Server passesSSL_RENEGOTIATE_REQUIRES_XTNto theSSL_ENABLE_RENEGOTIATIONoption. In this case, NSS allows secure renegotiations attempts using RFC 5746. -
If you set
nsTLSAllowClientRenegotiation: off, Directory Server passesSSL_RENEGOTIATE_NEVERto theSSL_ENABLE_RENEGOTIATIONoption. In this case, NSS denies all renegotiations attempts, even secure ones.
For further details about the NSS TLS renegotiation behavior, see the The RFC 5746 implementation in NSS (Network Security Services) section in the Is Red Hat affected by TLS renegotiation MITM attacks (CVE-2009-3555)? article.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=encryption,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsTLSAllowClientRenegotiation: on |
2.3.13. sslVersionMax
Sets the maximum version of the TLS protocol to be used. By default this value is set to the newest available protocol version in the NSS library installed on the system.
The server has to be restarted for changes to this attribute to go into effect.
If the sslVersionMin and sslVersionMax parameters are set in conjunction with nsTLS1, Directory Server selects the most secure settings from these parameters.
| Entry DN | cn=encryption,cn=config |
| Valid Values |
TLS protocol version such as |
| Default Value | Newest available protocol version in the NSS library installed on the system |
| Syntax | DirectoryString |
| Example: | sslVersionMax: TLS1.2 |
2.3.14. sslVersionMin
The sslVersionMin parameter sets the minimum version of the TLS protocol Directory Server uses. However, by default, Directory Server sets this parameter automatically based on the system-wide crypto policy. If you set the crypto policy profile in the /etc/crypto-policies/config file to:
-
DEFAULT,FUTURE, orFIPS, Directory Server setssslVersionMintoTLS1.2 -
LEGACY, Directory Server setssslVersionMintoTLS1.0
Alternatively, you can manually set sslVersionMin to higher value than the one defined in the crypto policy.
The service must be restarted for changes to this attribute to take effect.
| Entry DN | cn=encryption,cn=config |
| Valid Values |
TLS protocol versions, such as |
| Default Value | Depends on the system-wide crypto policy profile you set. |
| Syntax | DirectoryString |
| Example: | sslVersionMin: TLS1.2 |
2.4. cn=features,cn=config
There are not attributes for the cn=features entry itself. This entry is only used as a parent container entry, with the nsContainer object class.
The child entries contain an oid attribute to identify the feature and the directoryServerFeature object class, plus optional identifying information about the feature, such as specific ACLs. For example:
2.4.1. oid
The oid attribute contains an object identifier assigned to a directory service feature. oid is used as the naming attribute for these directory features.
| OID | 2.16.840.1.113730.3.1.215 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
2.5. cn=mapping tree,cn=config
Configuration attributes for suffixes, replication, and Windows synchronization are stored under
cn=mapping tree,cn=config. Configuration attributes related to suffixes are found under the suffix subentrycn=suffix,cn=mapping tree,cn=config.For example, a suffix is the root entry in the directory tree, such as
dc=example,dc=com.-
Replication configuration attributes are stored under
cn=replica,cn=suffix,cn=mapping tree,cn=config. -
Replication agreement attributes are stored under
cn=replicationAgreementName,cn=replica,cn=suffix,cn=mapping tree,cn=config. -
Windows synchronization agreement attributes are stored under
cn=syncAgreementName,cn=replica,cn=suffix,cn=mapping tree,cn=config.
2.6. cn=suffix_DN,cn=mapping tree,cn=config
Suffix configurations are stored under the cn-suffix_DN,cn-mapping tree,cn-config entry. These entries are instances of the nsMappingTree object class. The extensibleObject object class enables entries that belong to it to hold any user attribute. For suffix configuration attributes to be taken into account by the server, these object classes, in addition to the top object class, must be present in the entry.
You must write the suffix DN in quotes because it contains characters such as equals signs (=), commas (,), and space characters. By using quotes, the DN appears correctly as a value in another DN. For example: cn-"dc=example,dc=com",cn-mapping tree,cn-config
2.6.1. cn
This mandatory attribute sets the relative distinguished name (RDN) of a new suffix.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid LDAP DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | cn: dn=example,dc=com |
2.6.2. nsslapd-backend
This parameter sets the name of the database or database link used to process requests. It is multi-valued, with one database or database link per value. This attribute is required when the value of the nsslapd-state attribute is set to backend or referral on update.
Set the value to the name of the back-end database entry instance under cn=ldbm database,cn=plugins,cn=config. For example: o=userroot,cn=ldbm database,cn=plugins,cn=config
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid partition name |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-backend: userRoot |
2.6.3. nsslapd-distribution-function
The nssldap-distribution-function parameter sets the name of the custom distribution function. You must set this attribute when you set more than one database in the nsslapd-backend attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid distribution function |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-distribution-plugin: distribution_function_name |
2.6.4. nsslapd-distribution-plugin
The nssldap-distribution-plugin sets the shared library to be used with the custom distribution function. You must set this attribute when you set more than one database in the nsslapd-backend attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid distribution plug-in |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-distribution-plugin: /path/to/shared/library |
2.6.5. nsslapd-parent
If you want to create a sub suffix, use the nsslapd-parent attribute to define the parent suffix.
If the attribute is not set, the new suffix is created as a root suffix.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid partition name |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-parent-suffix: dc=example,dc=com |
2.6.6. nsslapd-referral
This attribute sets the LDAP URL of the referral to be returned by the suffix. You can add the nssldap-referral attribute multiple times to set multiple referral URLs.
You must set this attribute if you set the nsslapd-state parameter to referral or on update.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid LDAP URL |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssldap-referral: ldap://example.com/ |
2.6.7. nsslapd-state
This parameter determines how a suffix handles operations. The attribute takes the following values:
-
backend: The back-end database processes all operations. -
disabled: The database is not available for processing operations. The server returns aNo such search objecterror in response to requests made by client applications. -
referral: Directory Server returns a referral URL for requests to this suffix. -
referral on update: The database is used for all operations. Only for update requests is a referral sent.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | backend | disabled | referral | referral on update |
| Default Value | backend |
| Syntax | DirectoryString |
| Example | nsslapd-state: backend |
2.7. cn=replica,cn=suffix_DN,cn=mapping tree,cn=config
Replication configuration attributes are stored under cn-replica,cn-suffix,cn-mapping tree,cn-config. The cn-replica entry is an instance of the nsDS5Replica object class. For replication configuration attributes to be taken into account by the server, this object class (in addition to the top object class) must be present in the entry.
The cn-replica,cn-suffix,cn-mapping tree,cn-config entry must contain the following object classes:
-
top -
extensibleObject -
nsds5replica
2.7.1. cn
Sets the naming attribute for the replica. The cn attribute must be set to replica.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
The value must be set to |
| Default Value | replica |
| Syntax | DirectoryString |
| Example | cn=replica |
2.7.2. nsds5DebugReplicaTimeout
This attribute gives an alternate timeout period to use when the replication is run with debug logging. This can set only the time or both the time and the debug level:
nsds5debugreplicatimeout: seconds[:debuglevel]
nsds5debugreplicatimeout: seconds[:debuglevel]| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any numeric string |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5debugreplicatimeout: 60:8192 |
2.7.3. nsDS5Flags
This attribute sets replica properties that were previously defined in flags. At present only one flag exists, which sets whether the log changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 * 0: The replica does not write to the changelog; this is the default for consumers. * 1: The replica writes to the changelog; this is the default for hubs and suppliers. |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsDS5Flags: 0 |
2.7.4. nsDS5ReplConflict
Although this attribute is not in the cn=replica entry, it is used in conjunction with replication. This multi-valued attribute is included on entries that have a change conflict that cannot be resolved automatically by the synchronization process. To check for replication conflicts requiring administrator intervention, perform an LDAP search for (nsDS5ReplConflict=*). For example:
ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -x -s sub -b dc=example,dc=com "(|(objectclass=nsTombstone)(nsDS5ReplConflict=*))" dn nsDS5ReplConflict nsUniqueID
# ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -x -s sub -b dc=example,dc=com "(|(objectclass=nsTombstone)(nsDS5ReplConflict=*))" dn nsDS5ReplConflict nsUniqueID
Using the search filter "(objectclass=nsTombstone)" also shows tombstone (deleted) entries. The value of the nsDS5ReplConflict contains more information about which entries are in conflict, usually by referring to them by their nsUniqueID. It is possible to search for a tombstone entry by its nsUniqueID. For example:
ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -x -s sub -b dc=example,dc=com "(|(objectclass=nsTombstone)(nsUniqueID=66a2b699-1dd211b2-807fa9c3-a58714648))"
# ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -x -s sub -b dc=example,dc=com "(|(objectclass=nsTombstone)(nsUniqueID=66a2b699-1dd211b2-807fa9c3-a58714648))"2.7.5. nsDS5ReplicaAbortCleanRUV
This read-only attribute specifies whether the background task that removes old RUV entries for obsolete or missing suppliers is being terminated. See Section 2.26, “cn=task_name,cn=abort cleanallruv,cn=tasks,cn=config” for more information about this task. A value of 0 means that the task is inactive, and a value of 1 means that the task is active.
This attribute helps to resume the termination task after a server restart. When the task completes, Directory Server deletes the attribute.
The server ignores the modify request if you set this value manually.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 |
| Default Value | None |
| Syntax | Integer |
| Example | nsDS5ReplicaAbortCleanRUV: 1 |
2.7.6. nsDS5ReplicaAutoReferral
This attribute sets whether Directory Server follows configured referrals for the database.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | on | off |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaAutoReferral: on |
2.7.7. nsds5ReplicaBackoffMin and nsds5ReplicaBackoffMax
These attributes are used in environments with heavy replication traffic, where updates need to be sent as fast as possible.
By default, if a remote replica is busy, the replication protocol will go into a "back off" state, and it will retry to send it updates at the next interval of the back-off timer. By default, the timer starts at 3 seconds, and has a maximum wait period of 5 minutes. As these default settings maybe not be sufficient under certain circumstances, you can use nsds5ReplicaBackoffMin and nsds5ReplicaBackoffMax to configure the minimum and maximum wait times.
The configuration settings can be applied while the server is online, and do not require a server restart. If invalid settings are used, then the default values are used instead. The configuration must be handled through CLI tools.
2.7.8. nsDS5ReplicaBindDN
This multi-valued attribute specifies the DN to use when binding. Although there can be more than one value in this cn=replica entry, there can only be one supplier bind DN per replication agreement. Each value should be the DN of a local entry on the consumer server. If replication suppliers are using client certificate-based authentication to connect to the consumers, configure the certificate mapping on the consumer to map the subjectDN in the certificate to a local entry.
For security reasons, do not set this attribute to cn=Directory Manager.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaBindDN: cn=replication manager,cn=config |
2.7.9. nsDS5ReplicaBindDNGroup
The nsDS5ReplicaBindDNGroup attribute specifies a group DN. This group is then expanded and its members, including the members of its subgroups, are added to the replicaBindDNs attribute at startup or when the replica object is modified. This extends the current functionality provided by the nsDS5ReplicaBindDN attribute, as it allows to set a group DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid group DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaBindDNGroup: cn=sample_group,ou=groups,dc=example,dc=com |
2.7.10. nsDS5ReplicaBindDNGroupCheckInterval
Directory Server checks for any changes in the groups specified in the nsDS5ReplicaBindDNGroup attribute and automatically rebuilds the list for the replicaBindDN parameter accordingly. These operations have a negative effect on performance and are therefore performed only at a specified interval set in the nsDS5ReplicaBindDNGroupCheckInterval attribute.
This attribute accepts the following values:
-
-1: Disables the dynamic check at runtime. The administrator must restart the instance when thensDS5ReplicaBindDNGroupattribute changes. -
0: Directory Server rebuilds the lists immediately after the groups are changed. - Any positive 32-bit integer value: Minimum number of seconds that are required to pass since the last rebuild.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | -1 to maximum 32-bit integer (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsDS5ReplicaBindDNGroupCheckInterval: 0 |
2.7.11. nsDS5ReplicaChangeCount
This read-only attribute shows the total number of entries in the changelog and whether they still remain to be replicated. When the changelog is purged, only the entries that are still to be replicated remain.
For more information about purge operation properties, see the following attributes:
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | -1 to maximum 32-bit integer (2147483647) |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaChangeCount: 675 |
2.7.12. nsDS5ReplicaCleanRUV
This read-only attribute specifies whether the background task that removes old RUV entries for obsolete or missing suppliers is active. See Section 2.25, “cn=task_name,cn=cleanallruv,cn=tasks,cn=config” for more information about this task. A value of 0 means that the task is inactive, and a value of 1 means that the task is active.
This attribute is present to allow the cleanup task to be resumed after a server restart. When the task completes, the attribute is deleted.
The server ignores the modify request if this value is set manually.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 |
| Default Value | None |
| Syntax | Integer |
| Example | nsDS5ReplicaCleanRUV: 0 |
2.7.13. nsDS5ReplicaId
This attribute sets the unique ID for suppliers in a given replication environment.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range |
For suppliers:
For consumers and hubs: |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaId: 1 |
2.7.14. nsDS5ReplicaLegacyConsumer
If this attribute is absent or has a value of false, then it means that the replica is not a legacy consumer.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | true | false |
| Default Value | false |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaLegacyConsumer: false |
2.7.15. nsDS5ReplicaName
This attribute specifies the name of the replica with a unique identifier for internal operations. If it is not specified, this unique identifier is allocated by the server when the replica is created.
It is recommended that the server be permitted to generate this name. However, in certain circumstances, for example, in replica role changes (supplier to hub etc.), this value needs to be specified. Otherwise, the server will not use the correct changelog database, and replication fails.
This attribute is destined for internal use only.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | |
| Default Value | |
| Syntax | DirectoryString (a UID identifies the replica) |
| Example | nsDS5ReplicaName: 66a2b699-1dd211b2-807fa9c3-a58714648 |
2.7.16. nsds5ReplicaProtocolTimeout
When stopping the server, disabling replication, or removing a replication agreement, there is a timeout on how long to wait before stopping replication when the server is under load. The nsds5ReplicaProtocolTimeout attribute can be used to configure this timeout and its default value is 120 seconds.
There may be scenarios where a timeout of 2 minutes is too long, or not long enough. For example, a particular replication agreement may need more time before ending a replication session during a shutdown.
This attribute can be added to the main replication configuration entry for a back end:
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=dc\3Dexample\2Cdc\3Dcom,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) in seconds |
| Default value | 120 |
| Syntax | Integer |
| Example | nsds5ReplicaProtocolTimeout: 120 |
The nsds5ReplicaProtocolTimeout attribute can also be added to a replication agreement. The replication agreement protocol timeout overrides the timeout set in the main replica configuration entry. This allows different timeouts for different replication agreements. If a replication session is in progress, a new timeout will abort that session and allow the server to shutdown.
2.7.17. nsDS5ReplicaPurgeDelay
This attribute controls the maximum age of deleted entries (tombstone entries) and state information.
The Directory Server stores tombstone entries and state information so that when a conflict occurs in a multi-supplier replication process, the server resolves the conflicts based on the timestamp and replica ID stored in the change sequence numbers.
An internal Directory Server housekeeping operation periodically removes tombstone entries which are older than the value of this attribute (in seconds). State information which is older than the nsDS5ReplicaPurgeDelay value is removed when an entry which contains the state information is modified.
Not every tombstone and state information may be removed because, with multi-supplier replication, the server may need to keep a small number of the latest updates to prime replication, even if they are older than the value of the attribute.
This attribute specifies the interval, in seconds, to perform internal purge operations on an entry. When setting this attribute, ensure that the purge delay is longer than the longest replication cycle in the replication policy to preserve enough information to resolve replication conflicts and to prevent the copies of data stored in different servers from diverging.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | 0 (keep forever) to maximum 32-bit integer (2147483647) |
| Default Value | 604800 [1 week (60x60x24x7)] |
| Syntax | Integer |
| Example | nsDS5ReplicaPurgeDelay: 604800 |
2.7.18. nsDS5ReplicaReapActive
This read-only attribute specifies whether the background task that removes old tombstones (deleted entries) from the database is active. See Section 2.7.22, “nsDS5ReplicaTombstonePurgeInterval” for more information about this task. A value of 0 means that the task is inactive, and a value of 1 means that the task is active. The server ignores the modify request if this value is set manually.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaReapActive: 0 |
2.7.19. nsDS5ReplicaReferral
This multi-valued attribute specifies the user-defined referrals. This should only be defined on a consumer. User referrals are only returned when a client attempts to modify data on a read-only consumer. This optional referral overrides the referral that is automatically configured by the consumer by the replication protocol.
The URL can use the format ldap://host_name:port_number or ldap://IP_address:port_number, with an IPv4 or IPv6 address.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid LDAP URL |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaReferral: ldap://server.example.com:389 |
2.7.20. nsDS5ReplicaReleaseTimeout
This attribute, when used on suppliers and hubs in multi-supplier scenarios, determines a timeout period (in seconds) after which a supplier will release a replica. This is useful in situations when problems such as a slow network connection causes one supplier to acquire access to a replica and hold it for a long time, preventing all other suppliers from accessing it and sending updates. If this attribute is set, replicas are released by suppliers after the specified period, resulting in improved replication performance.
Setting this attribute to 0 disables the timeout. Any other value determines the length of the timeout in seconds.
Avoid setting this attribute to values between 1 and 30. In most scenarios, short timeouts decrease the replication performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 to maximum 32-bit integer (2147483647) in seconds |
| Default Value | 60 |
| Syntax | Integer |
| Example | nsDS5ReplicaReleaseTimeout: 60 |
2.7.21. nsDS5ReplicaRoot
This attribute sets the DN at the root of a replicated area. This attribute must have the same value as the suffix of the database being replicated and cannot be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Suffix of the database being replicated, which is the suffix DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaRoot: "dc=example,dc=com" |
2.7.22. nsDS5ReplicaTombstonePurgeInterval
This attribute specifies the time interval in seconds between purge operation cycles.
Periodically, the server runs an internal housekeeping operation to purge old update and state information from the changelog and the main database. See Section 2.7.17, “nsDS5ReplicaPurgeDelay”.
When setting this attribute, remember that the purge operation is time-consuming, especially if the server handles many delete operations from clients and suppliers.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) in seconds |
| Default Value | 86400 (1 day) |
| Syntax | Integer |
| Example | nsDS5ReplicaTombstonePurgeInterval: 86400 |
2.7.23. nsDS5ReplicaType
Defines the type of replication relationship that exists between this replica and the others.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 | 2 | 3 * 0 means unknown * 1 means primary (not yet used) * 2 means consumer (read-only) * 3 consumer/supplier (updateable) |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaType: 2 |
2.7.24. nsds5Task
This attribute launches a replication task, such as dumping the database contents to an LDIF file or removing obsolete suppliers from the replication topology.
You can set the nsds5Task attribute to one of the following values:
-
cl2ldif: Exports the changelog to an LDIF file in the/var/lib/dirsrv/slapd-instance_name/changelogdb/directory. -
ldif2cl: Imports the changelog from an LDIF file stored in the/var/lib/dirsrv/slapd-instance_name/changelogdb/directory. -
cleanruv: Removes a Replica Update Vector (RUV) from the suppliers where you run the operation. -
cleanallruv: Removes RUVs from all servers in a replication topology.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
*
*
*
* |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5Task: cleanallruv |
2.7.25. nsState
This attribute stores information on the state of the clock. It is designed only for internal use to ensure that the server cannot generate a change sequence number (csn) inferior to existing ones required for detecting backward clock errors.
2.8. cn=ReplicationAgreementName,cn=replica,cn=suffix_DN,cn=mapping tree,cn=config
The replication attributes that concern the replication agreement are stored under cn=ReplicationAgreementName,cn=replica,cn=suffix_DN,cn=mapping tree,cn=config. The cn=ReplicationAgreementName entry is an instance of the nsDS5ReplicationAgreement object class. Replication agreements are configured only on supplier replicas.
2.8.1. cn
This attribute is used for naming. Once this attribute has been set, it cannot be modified. This attribute is required for setting up a replication agreement.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
Any valid |
| Default Value | |
| Syntax | DirectoryString |
| Example | cn: SupplierAtoSupplierB |
2.8.2. description
Free form text description of the replication agreement. This attribute can be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | DirectoryString |
| Example | description: Replication Agreement between Server A and Server B. |
2.8.3. nsDS50ruv
This attribute stores the last replica update vector (RUV) read from the consumer of this replication agreement. It is always present and must not be changed.
2.8.4. nsDS5BeginReplicaRefresh
Initializes the replica. This attribute is absent by default. However, if this attribute is added with a value of start, then the server initializes the replica and removes the attribute value. To monitor the status of the initialization procedure, poll for this attribute. When initialization is finished, the attribute is removed from the entry, and the other monitoring attributes can be used for detailed status inquiries.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | stop | start |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5BeginReplicaRefresh: start |
2.8.5. nsDS5ReplicaBindDN
This attribute sets the DN to use when binding to the consumer during replication. The value of this attribute must be the same as the one in cn=replica on the consumer replica. This may be empty if certificate-based authentication is used, in which case the DN used is the subject DN of the certificate, and the consumer must have appropriate client certificate mapping enabled. This can also be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid DN (can be empty if client certificates are used) |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaBindDN: cn=replication manager,cn=config |
2.8.6. nsDS5ReplicaBindMethod
This attribute sets the method for the server to use to bind to the consumer server.
The nsDS5ReplicaBindMethod supports the following values:
-
Empty or
SIMPLE: The server uses password-based authentication. When using this bind method, additionally, set thensds5ReplicaBindDNandnsds5ReplicaCredentialsparameters to provide a user name and password. -
SSLCLIENTAUTH: Enables certificate-based authentication between the supplier and consumer. For this, the consumer server must have a certificate mapping configured to map the supplier’s certificate to the replication manager entry. -
SASL/GSSAPI: Enables Kerberos authentication using SASL. This requires that the supplier server have a Kerberos keytab, and the consumer server a SASL mapping entry configured to map the supplier’s Kerberos principal to the replication manager entry. -
SASL/DIGEST-MD5: Enables password-based authentication using SASL with theDIGEST-MD5mechanism. When using this bind method, additionally, set thensds5ReplicaBindDNandnsds5ReplicaCredentialsparameters to provide a user name and password.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | SIMPLE | SSLCLIENTAUTH | SASL/GSSAPI | SASL/DIGEST |
| Default Value | SIMPLE |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaBindMethod: SIMPLE |
2.8.7. nsds5ReplicaBootstrapBindDN
The nsds5ReplicaBootstrapBindDN parameter sets the fall-back bind distinguished name (DN) that Directory Server uses when the supplier fails to bind to a consumer due to an LDAP_INVALID_CREDENTIALS (err=49), LDAP_INAPPROPRIATE_AUTH (err=48), or LDAP_NO_SUCH_OBJECT (err=32) error.
In these cases, Directory Server uses the information from the nsds5ReplicaBootstrapBindDN, nsds5ReplicaBootstrapCredentials, nsds5ReplicaBootstrapBindMethod, and nsds5ReplicaBootstrapTransportInfo parameters to establish the connection. If the server also fails to establish the connection using these bootstrap settings, the server stops trying to connect.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5ReplicaBootstrapBindDN: cn=replication manager,cn=config |
2.8.8. nsds5ReplicaBootstrapBindMethod
The nsds5ReplicaBootstrapBindMethod parameter sets the password for the fall-back login mechanism that Directory Server uses when the supplier fails to bind to a consumer due to an LDAP_INVALID_CREDENTIALS (err=49), LDAP_INAPPROPRIATE_AUTH (err=48), or LDAP_NO_SUCH_OBJECT (err=32) error.
In these cases, Directory Server uses the information from the nsds5ReplicaBootstrapBindDN, nsds5ReplicaBootstrapCredentials, nsds5ReplicaBootstrapBindMethod, and nsds5ReplicaBootstrapTransportInfo parameters to establish the connection. If the server also fails to establish the connection using these bootstrap settings, the server stops trying to connect.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | SIMPLE | SSLCLIENTAUTH | SASL/GSSAPI | SASL/DIGEST |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5ReplicaBootstrapBindMethod: SIMPLE |
2.8.9. nsds5ReplicaBootstrapCredentials
The nsds5ReplicaBootstrapCredentials parameter sets the password for the fall-back bind distinguished name (DN) that Directory Server uses when the supplier fails to bind to a consumer due to an LDAP_INVALID_CREDENTIALS (err=49), LDAP_INAPPROPRIATE_AUTH (err=48), or LDAP_NO_SUCH_OBJECT (err=32) error.
In these cases, Directory Server uses the information from the nsds5ReplicaBootstrapBindDN, nsds5ReplicaBootstrapCredentials, nsds5ReplicaBootstrapBindMethod, and nsds5ReplicaBootstrapTransportInfo parameters to establish the connection. If the server also fails to establish the connection using these bootstrap settings, the server stops trying to connect.
Directory Server automatically hashes the password using the AES reversible password encryption algorithm when you set the parameter in clear text.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid string. |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5ReplicaBootstrapCredentials: password |
2.8.10. nsds5ReplicaBootstrapTransportInfo
The nsds5ReplicaBootstrapTransportInfo parameter sets the encryption method for the connection to and from the replica for the fall-back connection that Directory Server uses when the supplier fails to bind to a consumer due to an LDAP_INVALID_CREDENTIALS (err=49), LDAP_INAPPROPRIATE_AUTH (err=48), or LDAP_NO_SUCH_OBJECT (err=32) error.
In these cases, Directory Server uses the information from the nsds5ReplicaBootstrapBindDN, nsds5ReplicaBootstrapCredentials, nsds5ReplicaBootstrapBindMethod, and nsds5ReplicaBootstrapTransportInfo parameters to establish the connection. If the server also fails to establish the connection using these bootstrap settings, the server stops trying to connect.
The attribute takes the following values:
-
TLS: The connection uses theStartTLScommand to start the encryption. -
SSL: The connection uses LDAPS with TLS encryption. -
LDAP: The connection is not encrypted.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | TLS | SSL | LDAP |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5ReplicaBootstrapTransportInfo: SSL |
2.8.11. nsDS5ReplicaBusyWaitTime
This attribute sets the amount of time in seconds a supplier should wait after a consumer sends back a busy response before making another attempt to acquire access. The default value is three (3) seconds. If the attribute is set to a negative value, Directory Server sends the client a message and an LDAP_UNWILLING_TO_PERFORM error code.
The nsDS5ReplicaBusyWaitTime attribute works in conjunction with the nsDS5ReplicaSessionPauseTime attribute. The two attributes are designed so that the nsDS5ReplicaSessionPauseTime interval is always at least one second longer than the interval specified for nsDS5ReplicaBusyWaitTime. The longer interval gives waiting suppliers a better chance to gain consumer access before the previous supplier can re-access the consumer.
Set the nsDS5ReplicaBusyWaitTime attribute at any time by using changetype:modify with the replace operation. The change takes effect for the next update session if one is already in progress.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid integer |
| Default Value | 3 |
| Syntax | Integer |
| Example | nsDS5ReplicaBusyWaitTime: 3 |
2.8.12. nsDS5ReplicaChangesSentSinceStartup
This read-only attribute shows the number of changes sent to this replica since the server started. The actual value in the attribute is stored as a binary blob.
In the command line, the attribute value is shown in a binary form. For example:
nsds5replicaChangesSentSinceStartup:: MToxLzAg
nsds5replicaChangesSentSinceStartup:: MToxLzAg| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) |
| Default Value | |
| Syntax | Integer |
| Example | nsds5replicaChangesSentSinceStartup:: MToxLzAg |
2.8.13. nsDS5ReplicaCredentials
This attribute sets the credentials for the bind DN specified in the nsDS5ReplicaBindDN attribute. Directory Server uses this password to connect to the consumer.
The example below shows the encrypted value, as stored in the /etc/dirsrv/slapd-instance_name/dse.ldif file and not the actual password. To set a value, set it in clear text, for example nsDS5ReplicaCredentials: password. Directory Server then encrypts the password using the AES reversible password encryption schema when it stores the value.
When you use certificate-based authentication, this attribute does not have a value set.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid password |
| Default Value | |
| Syntax | DirectoryString {AES-Base64-algorithm-id}encoded_password |
| Example | nsDS5ReplicaCredentials: {AES-TUhNR0NT…}VoglUB8GG5A… |
2.8.14. nsds5ReplicaEnabled
This attribute sets whether a replication agreement is active, meaning whether replication is occurring per that agreement. The default is on, so that replication is enabled.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsds5ReplicaEnabled: off |
2.8.15. nsds5ReplicaFlowControlPause
This parameters sets the time in milliseconds to pause after reaching the number of entries and updates set in the nsds5ReplicaFlowControlWindow parameter is reached. Updating both the nsds5ReplicaFlowControlWindow and nsds5ReplicaFlowControlPause parameters enables you to fine-tune the replication throughput. For further details, see Section 2.8.16, “nsds5ReplicaFlowControlWindow”.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=replication_agreement_name,cn=replica,cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | 0 to maximum 64-bit long |
| Default Value | 2000 |
| Syntax | Integer |
| Example | nsds5ReplicaFlowControlPause: 2000 |
2.8.16. nsds5ReplicaFlowControlWindow
This attribute sets the maximum number of entries and updates sent by a supplier, which are not acknowledged by the consumer. After reaching the limit, the supplier pauses the replication agreement for the time set in the nsds5ReplicaFlowControlPause parameter. Updating both the nsds5ReplicaFlowControlWindow and nsds5ReplicaFlowControlPause parameters enables you to fine-tune the replication throughput.
Update this setting if the supplier sends entries and updates faster than the consumer can import or update, and acknowledge the data. In this case, the following message is logged in the supplier’s error log file:
Total update flow control gives time (2000 msec) to the consumer before sending more entries [ msgid sent: xxx, rcv: yyy]) If total update fails you can try to increase nsds5ReplicaFlowControlPause and/or decrease nsds5ReplicaFlowControlWindow in the replica agreement configuration
Total update flow control gives time (2000 msec) to the consumer before sending more entries [ msgid sent: xxx, rcv: yyy])
If total update fails you can try to increase nsds5ReplicaFlowControlPause and/or decrease nsds5ReplicaFlowControlWindow in the replica agreement configurationThis setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=replication_agreement_name,cn=replica,cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | 0 to maximum 64-bit long |
| Default Value | 1000 |
| Syntax | Integer |
| Example | nsds5ReplicaFlowControlWindow: 1000 |
2.8.17. nsDS5ReplicaHost
This attribute sets the host name for the remote server containing the consumer replica. Once this attribute has been set, it cannot be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid host server name |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaHost: ldap2.example.com |
2.8.18. nsDS5ReplicaLastInitEnd
This optional, read-only attribute states when the initialization of the consumer replica ended.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
YYYYMMDDhhmmssZ is the date/time in Generalized Time form at which the connection was opened. This value gives the time in relation to Greenwich Mean Time. The hours are set with a 24-hour clock. The |
| Default Value | |
| Syntax | GeneralizedTime |
| Example | nsDS5ReplicaLastInitEnd: 20200504121603Z |
2.8.19. nsDS5ReplicaLastInitStart
This optional, read-only attribute states when the initialization of the consumer replica started.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
YYYYMMDDhhmmssZ is the date/time in Generalized Time form at which the connection was opened. This value gives the time in relation to Greenwich Mean Time. The hours are set with a 24-hour clock. The |
| Default Value | |
| Syntax | GeneralizedTime |
| Example | nsDS5ReplicaLastInitStart: 20200503030405 |
2.8.20. nsDS5ReplicaLastInitStatus
This optional, read-only attribute provides status for the initialization of the consumer. There is typically a numeric code followed by a short string explaining the status. Zero (0) means success.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 (Consumer Initialization Succeeded), followed by any other status message. |
| Default Value | |
| Syntax | String |
| Example | nsDS5ReplicaLastInitStatus: 0 Consumer Initialization Succeeded |
2.8.21. nsDS5ReplicaLastUpdateEnd
This read-only attribute states when the most recent replication schedule update ended.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
YYYYMMDDhhmmssZ is the date/time in Generalized Time form at which the connection was opened. This value gives the time in relation to Greenwich Mean Time. The hours are set with a 24-hour clock. The |
| Default Value | |
| Syntax | GeneralizedTime |
| Example | nsDS5ReplicaLastUpdateEnd: 20200502175801Z |
2.8.22. nsDS5ReplicaLastUpdateStart
This read-only attribute states when the most recent replication schedule update started.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
YYYYMMDDhhmmssZ is the date/time in Generalized Time form at which the connection was opened. This value gives the time in relation to Greenwich Mean Time. The hours are set with a 24-hour clock. The |
| Default Value | |
| Syntax | GeneralizedTime |
| Example | nsDS5ReplicaLastUpdateStart: 20200504122055Z |
2.8.23. nsds5replicaLastUpdateStatus
In the read-only nsds5replicaLastUpdateStatus attribute of each replication agreement, Directory Server displays the latest status of the agreement.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid replication agreement status |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5replicaLastUpdateStatus: Error (0) Replica acquired successfully: Incremental update succeeded |
2.8.24. nsDS5ReplicaPort
This attribute sets the port number for the remote server containing the replica. Once this attribute has been set, it cannot be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Port number for the remote server containing the replica |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaPort:389 |
2.8.25. nsds5ReplicaProtocolTimeout
When stopping the server, disabling replication, or removing a replication agreement, there is a timeout on how long to wait before stopping replication when the server is under load. The nsds5ReplicaProtocolTimeout attribute can be used to configure this timeout and its default value is 120 seconds.
There may be scenarios where a timeout of 2 minutes is too long, or not long enough. For example, a particular replication agreement may need more time before ending a replication session during a shutdown.
This attribute can be added to the main replication configuration entry for a back end:
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=dc\3Dexample\2Cdc\3Dcom,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) in seconds |
| Default value | 120 |
| Syntax | Integer |
| Example | nsds5ReplicaProtocolTimeout: 120 |
The nsds5ReplicaProtocolTimeout attribute can also be added to a replication agreement. The replication agreement protocol timeout overrides the timeout set in the main replica configuration entry. This allows different timeouts for different replication agreements. If a replication session is in progress, a new timeout will abort that session and allow the server to shutdown.
2.8.26. nsDS5ReplicaReapActive
This read-only attribute specifies whether the background task that removes old tombstones (deleted entries) from the database is active. See Section 2.7.22, “nsDS5ReplicaTombstonePurgeInterval” for more information about this task. A value of zero (0) means that the task is inactive, and a value of 1 means that the task is active. If this value is set manually, the server ignores the modify request.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaReapActive: 0 |
2.8.27. nsDS5ReplicaRoot
This attribute sets the DN at the root of a replicated area. This attribute must have the same value as the suffix of the database being replicated and cannot be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Suffix of the database being replicated - same as suffixDN above |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaRoot: "dc=example,dc=com" |
2.8.28. nsDS5ReplicaSessionPauseTime
This attribute sets the amount of time in seconds a supplier should wait between update sessions. The default value is 0. If the attribute is set to a negative value, Directory Server sends the client a message and an LDAP_UNWILLING_TO_PERFORM error code.
The nsDS5ReplicaSessionPauseTime attribute works in conjunction with the nsDS5ReplicaBusyWaitTime attribute. The two attributes are designed so that the nsDS5ReplicaSessionPauseTime interval is always at least one second longer than the interval specified for nsDS5ReplicaBusyWaitTime. The longer interval gives waiting suppliers a better chance to gain consumer access before the previous supplier can re-access the consumer.
-
If either attribute is specified but not both,
nsDS5ReplicaSessionPauseTimeis set automatically to1second more thannsDS5ReplicaBusyWaitTime. -
If both attributes are specified, but
nsDS5ReplicaSessionPauseTimeis less than or equal tonsDS5ReplicaBusyWaitTime,nsDS5ReplicaSessionPauseTimeis set automatically to1second more thannsDS5ReplicaBusyWaitTime.
When setting the values, ensure that the nsDS5ReplicaSessionPauseTime interval is at least 1 second longer than the interval specified for nsDS5ReplicaBusyWaitTime. Increase the interval as needed until there is an acceptable distribution of consumer access among the suppliers.
Set the nsDS5ReplicaSessionPauseTime attribute at any time by using changetype:modify with the replace operation. The change takes effect for the next update session if one is already in progress.
If Directory Server has to reset the value of nsDS5ReplicaSessionPauseTime automatically, the value is changed internally only. The change is not visible to clients, and it is not saved to the configuration file. From an external viewpoint, the attribute value appears as originally set.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid integer |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsDS5ReplicaSessionPauseTime: 0 |
2.8.29. nsds5ReplicaStripAttrs
Fractional replication allows a list of attributes which are removed from replication updates (nsDS5ReplicatedAttributeList). However, a change to an excluded attribute still triggers a modify event and generates an empty replication update.
The nsds5ReplicaStripAttrs attribute adds a list of attributes which cannot be sent in an empty replication event and are stripped from the update sequence. This logically includes operational attribtes like modifiersName.
If a replication event is not empty, the stripped attributes are replicated. These attributes are removed from updates only if the event would otherwise be emtpy.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | A space-separated list of any supported directory attribute |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5ReplicaStripAttrs: modifiersname modifytimestamp |
2.8.30. nsDS5ReplicatedAttributeList
This allowed attribute specifies any attributes that are not replicated to a consumer server. Fractional replication allows databases to be replicated across slow connections or to less secure consumers while still protecting sensitive information. By default, all attributes are replicated, and this attribute is not present.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicatedAttributeList: (objectclass=*) $ EXCLUDE accountlockout memberof |
2.8.31. nsDS5ReplicatedAttributeListTotal
This allowed attribute specifies any attributes that are not replicated to a consumer server during a total update.
Fractional replication only replicates specified attributes. This improves the overall network performance. However, there may be times when administrators want to restrict some attributes using fractional replication during an incremental update but allow those attributes to be replicated during a total update (or vice versa).
By default, all attributes are replicated. nsDS5ReplicatedAttributeList sets the incremental replication list; if only nsDS5ReplicatedAttributeList is set, then this list applies to total updates as well.
nsDS5ReplicatedAttributeListTotal sets the list of attributes to exclude only from a total update.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicatedAttributeListTotal: (objectclass=*) $ EXCLUDE accountlockout |
2.8.32. nsDS5ReplicaTimeout
This allowed attribute specifies the number of seconds outbound LDAP operations waits for a response from the remote replica before timing out and failing. If the server writes Warning: timed out waiting messages in the error log file, then increase the value of this attribute.
Find out the amount of time the operation actually lasted by examining the access log on the remote machine, and then set the nsDS5ReplicaTimeout attribute accordingly to optimize performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer value (2147483647) in seconds |
| Default Value | 120 |
| Syntax | Integer |
| Example | nsDS5ReplicaTimeout: 120 |
2.8.33. nsDS5ReplicaTransportInfo
This attribute sets the type of transport used for transporting data to and from the replica. This attribute cannot be modified once it is set.
The attribute takes the following values:
-
StartTLS: The connection uses encryption using theStartTLScommand. -
LDAPS: The connection uses TLS encryption. -
LDAP: The connection uses the unencrypted LDAP protocol. This value is also used, if thensDS5ReplicaTransportInfoattribute is not set.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | StartTLS | LDAPS | LDAP |
| Default Value | absent |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaTransportInfo: StartTLS |
2.8.34. nsDS5ReplicaUpdateInProgress
This read-only attribute states whether or not a replication update is in progress.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | true | false |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaUpdateInProgress: true |
2.8.35. nsDS5ReplicaUpdateSchedule
This multi-valued attribute specifies the replication schedule and can be modified. Changes made to this attribute take effect immediately. Modifying this value can be useful to pause replication and resume it later. For example, if this value to 0000-0001 0, this in effect causes the server to stop sending updates for this replication agreement. The server continues to store them for replay later. If the value is later changed back to 0000-2359 0123456, this makes replication immediately resume and sends all pending changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | Time schedule presented as XXXX-YYYY 0123456, where XXXX is the starting hour, YYYY is the finishing hour, and the numbers 0123456 are the days of the week starting with Sunday. |
| Default Value | 0000-2359 0123456 (all the time) |
| Syntax | Integer |
| Example | nsDS5ReplicaUpdateSchedule: 0000-2359 0123456 |
2.8.36. nsDS5ReplicaWaitForAsyncResults
In a replication environment, the nsDS5ReplicaWaitForAsyncResults parameter sets the time in milliseconds for which a supplier waits if the consumer is not ready before resending data.
Note that if you set the parameter to 0, the default value is used.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsDS5ReplicaWaitForAsyncResults: 100 |
2.8.37. nsruvReplicaLastModified
This attribute contains the most recent time that an entry in the replica was modified and the changelog was updated.
2.9. cn=syncAgreementName,cn=replica,cn=suffix_DN,cn=mapping tree,cn=config
The synchronization attributes that concern the synchronization agreement are stored under cn=syncAgreementName,cn=suffix_DN,cn=mapping tree,cn=config. The cn=syncAgreementName entry is an instance of the nsDSWindowsReplicationAgreement object class.
For synchronization agreement configuration attributes to be taken into account by the server, this object class (in addition to the top object class) must be present in the entry. Synchronization agreements are configured only on databases that are enabled to synchronize with Windows Active Directory servers.
| cn | nsDS5ReplicaLastUpdateEnd |
| description | nsDS5ReplicaLastUpdateStart |
| nsDS5ReplicaBindDN (the Windows sync manager ID) | nsDS5ReplicaLastUpdateStatus |
| nsDS5ReplicaBindMethod | nsDS5ReplicaPort |
| nsDS5ReplicaBusyWaitTime | nsDS5ReplicaRoot |
| nsDS5ReplicaChangesSentSinceStartup | nsDS5ReplicaSessionPauseTime |
| nsDS5ReplicaCredentials (the Windows sync manager password) | nsDS5ReplicaTimeout |
| nsDS5ReplicaHost (the Windows host) | nsDS5ReplicaTransportInfo |
| nsDS5ReplicaLastInitEnd | nsDS5ReplicaUpdateInProgress |
| nsDS5ReplicaLastInitStart | nsDS5ReplicaUpdateSchedule |
| nsDS5ReplicaLastInitStatus | nsDS50ruv |
| winSyncMoveAction | winSyncInterval |
| nsds5ReplicaStripAttrs |
2.9.1. nsds7DirectoryReplicaSubtree
The suffix or DN of the Directory Server subtree that is being synchronized.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid suffix or subsuffix |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7DirectoryReplicaSubtree: ou=People,dc=example,dc=com |
2.9.2. nsds7DirsyncCookie
This string is created by Active Directory DirSync and gives the state of the Active Directory Server at the time of the last synchronization. The old cookie is sent to Active Directory with each Directory Server update; a new cookie is returned along with the Windows directory data. This means only entries which have changed since the last synchronization are retrieved.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7DirsyncCookie::khDKJFBZsjBDSCkjsdhIU74DJJVBXDhfvjmfvbhzxj |
2.9.3. nsds7NewWinGroupSyncEnabled
This attribute sets whether a new group created in the Windows sync peer is automatically synchronized by creating a new group on Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | on | off |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7NewWinGroupSyncEnabled: on |
2.9.4. nsds7NewWinUserSyncEnabled
This attribute sets whether a new entry created in the Windows sync peer is automatically synchronized by creating a new entry on Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | on | off |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7NewWinUserSyncEnabled: on |
2.9.5. nsds7WindowsDomain
This attribute sets the name of the Windows domain to which the Windows sync peer belongs.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid domain name |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7WinndowsDomain: DOMAINWORLD |
2.9.6. nsds7WindowsReplicaSubtree
The suffix or DN of the Windows subtree that is being synchronized.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid suffix or subsuffix |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7WindowsReplicaSubtree: cn=Users,dc=domain,dc=com |
2.9.7. oneWaySync
This attribute sets which direction to perform synchronization. This can either be from the Active Directory server to Directory Server or from Directory Server to the Active Directory server.
If this attribute is absent (the default), then the synchronization agreement is bi-directional, so changes made in both domains are synchronized.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | toWindows | fromWindows | null |
| Default Value | |
| Syntax | DirectoryString |
| Example | oneWaySync: fromWindows |
2.9.8. winSyncInterval
This attribute sets how frequently, in seconds, Directory Server polls the Windows sync peer to look for changes in the Active Directory entries. If this entry is not set, Directory Server checks the Windows server every five (5) minutes, meaning the default value is 300 (300 seconds).
This value can be set lower to write Active Directory changes over to Directory Server faster or raised if the directory searches are taking too long.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 1 to the maximum 32-bit integer value (2147483647) |
| Default Value | 300 |
| Syntax | Integer |
| Example | winSyncInterval: 600 |
2.9.9. winSyncMoveAction
The synchronization process starts at the root DN to begin evaluating entries for synchronization. Entries are correlated based on the samAccount in the Active Directory and the uid attribute in Directory Server. The synchronization plug-in notes if a previously synced entry (based on the samAccount/uid relationship) is removed from the synced subtree either because it is deleted or moved, then the synchronization plug-in recognizes that the entry is no longer to be synced.
The winSyncMoveAction attribute for the synchronization agreement sets instructions on how to handle these moved entries:
-
nonetakes no action, so if a synced Directory Server entry exists, it may be synced over to or create an Active Directory entry within scope. If no synced Directory Server entry exists, nothing happens at all (this is the default behavior). unsyncremoves any sync-related attributes (ntUserorntGroup) from the Directory Server entry but otherwise leaves the Directory Server entry intact. The Active Directory and Directory Server entries exist in tandem.ImportantThere is a risk when unsyncing entries that the Active Directory entry may be deleted at a later time, and the Directory Server entry will be left intact. This can create data inconsistency issues, especially if the Directory Server entry is ever used to recreate the entry on the Active Directory side later.
deletedeletes the corresponding entry on the Directory Server side, regardless of whether it was ever synced with Active Directory (this was the default behavior in 9.0).ImportantYou almost never want to delete a Directory Server entry without deleting the corresponding Active Directory entry. This option is available only for compatibility with Directory Server 9.0 systems.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | none | delete | unsync |
| Default Value | none |
| Syntax | DirectoryString |
| Example | winSyncMoveAction: unsync |
2.10. cn=replication,cn=config
This entry has no attributes. When configuring legacy replication, those entries are stored under this cn=replication,cn=replication node, which serves as a placeholder.
2.11. cn=sasl,cn=config
Entries which contain SASL mapping configurations are stored under cn=mapping,cn=sasl,cn=config. The cn=sasl entry is an instance of the nsContainer object class. Each mapping underneath it is an instance of the nsSaslMapping object class.
2.11.1. nsSaslMapBaseDNTemplate
This attribute contains the search base DN template used in SASL identity mapping.
| Parameter | Description |
|---|---|
| Entry DN | cn=mapping_name,cn=mapping,cn=sasl,cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | IA5String |
| Example | nsSaslMapBaseDNTemplate: ou=People,dc=example,dc=com |
2.11.2. nsSaslMapFilterTemplate
This attribute contains the search filter template used in SASL identity mapping.
| Parameter | Description |
|---|---|
| Entry DN | cn=mapping_name,cn=mapping,cn=sasl,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | IA5String |
| Example | nsSaslMapFilterTemplate: (cn=\1) |
2.11.3. nsSaslMapPriority
Directory Server enables you to set multiple simple authentication and security layer (SASL) mappings. If SASL fallback is enabled by the nsslapd-sasl-mapping-fallback parameter, you can set the nsSaslMapPriority attribute to prioritize the individual SASL mappings.
This setting does not require a server restart to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=mapping_name,cn=mapping,cn=sasl,cn=config |
| Valid Values | 1 (highest priority) - 100 (lowest priority) |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsSaslMapPriority: 100 |
2.11.4. nsSaslMapRegexString
This attribute contains a regular expression used to map SASL identity strings.
| Parameter | Description |
|---|---|
| Entry DN | cn=mapping_name,cn=mapping,cn=sasl,cn=config |
| Valid Values | Any valid regular expression |
| Default Value | |
| Syntax | IA5String |
| Example | nsSaslMapRegexString: \(.*\) |
2.12. cn=SNMP,cn=config
SNMP configuration attributes are stored under cn=SNMP,cn=config. The cn=SNMP entry is an instance of the nsSNMP object class.
2.12.1. nssnmpcontact
This attribute sets the email address of the person responsible for maintaining Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | Contact email address |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssnmpcontact: jerome@example.com |
2.12.2. nssnmpdescription
Provides a unique description of the Directory Server instance.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | Description |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssnmpdescription: Employee directory instance |
2.12.3. nssnmpenabled
This attribute sets whether SNMP is enabled.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nssnmpenabled: off |
2.12.4. nssnmplocation
This attribute sets the location within the company or organization where Directory Server resides.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | Location |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssnmplocation: B14 |
2.12.5. nssnmpmasterhost
nssnmpmasterhost is deprecated. This attribute is deprecated with the introduction of net-snmp. The attribute still appears in dse.ldif but without a default value.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | machine host name or localhost |
| Default Value | <blank> |
| Syntax | DirectoryString |
| Example | nssnmpmasterhost: localhost |
2.12.6. nssnmpmasterport
The nssnmpmasterport attribute was deprecated with the introduction of net-snmp. The attribute still appears in dse.ldif but without a default value.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | Operating system dependent port number. See the operating system documentation for further information. |
| Default Value | <blank> |
| Syntax | Integer |
| Example | nssnmpmasterport: 199 |
2.12.7. nssnmporganization
This attribute sets the organization to which Directory Server belongs.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | Organization name |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssnmporganization: Red Hat, Inc. |
2.12.8. SNMP statistic attributes
The table below contains read-only attributes from cn=monitoring which list the statistics available for LDAP and SNMP clients. Unless otherwise noted, the value for the given attribute is the number of requests received by the server or results returned by the server since startup. Some of these attributes are not used by or are not applicable to Directory Server but are still required to be present by SNMP clients.
If the nsslapd-counters attribute in cn=config is set to on (the default setting), then all of the counters kept by the Directory Server instance increment using 64-bit integers, even on 32-bit machines or with a 32-bit version of Directory Server. All of the SNMP statistics attributes use the 64-bit integers, if it is configured.
The nsslapd-counters attribute enables 64-bit integers for these specific database and server counters. The counters which use 64-bit integers are not configurable; 64-bit integers are either enabled for all the allowed counters or disabled for all allowed counters.
| Attribute | Description |
|---|---|
| AnonymousBinds | This shows the number of anonymous bind requests. |
| UnAuthBinds | This shows the number of unauthenticated (anonymous) binds. |
| SimpleAuthBinds | This shows the number of LDAP simple bind requests (DN and password). |
| StrongAuthBinds | This shows the number of LDAP SASL bind requests, for all SASL mechanisms. |
| BindSecurityErrors | This shows the number of number of times an invalid password was given in a bind request. |
| InOps | This shows the total number of all requests received by the server. |
| ReadOps |
Not used. This value is always |
| CompareOps | This shows the number of LDAP compare requests. |
| AddEntryOps | This shows the number of LDAP add requests. |
| RemoveEntryOps | This shows the number of LDAP delete requests. |
| ModifyEntryOps | This shows the number of LDAP modify requests. |
| ModifyRDNOps | This shows the number of LDAP modify RDN (modrdn) requests. |
| ListOps |
Not used. This value is always |
| SearchOps | This shows the number of LDAP search requests. |
| OneLevelSearchOps | This shows the number of one-level search operations. |
| WholeSubtreeSearchOps | This shows the number of subtree-level search operations. |
| Referrals | This shows the number of LDAP referrals returned. |
| Chainings |
Not used. This value is always |
| SecurityErrors | This shows the number of errors returned that were security related, such as invalid passwords, unknown or invalid authentication methods, or stronger authentication required. |
| Errors | This shows the number of errors returned. |
| Connections | This shows the number of currently open connections. |
| ConnectionSeq | This shows the total number of connections opened, including both currently open and closed connections. |
| BytesRecv | This shows the number of bytes received. |
| BytesSent | This shows the number of bytes sent. |
| EntriesReturned | This shows the number of entries returned as search results. |
| ReferralsReturned | This provides information on referrals returned as search results (continuation references). |
| MasterEntries |
Not used. This value is always |
| CopyEntries |
Not used. This value is always |
| CacheEntries[a] |
If the server has only one database back end, this is the number of entries cached in the entry cache. If the server has more than one database back end, this value is |
| CacheHits |
If the server has only one database back end, this is the number of entries returned from the entry cache, rather than from the database, for search results. If the server has more than one database back end, this value is |
| SlaveHits |
Not used. This value is always |
[a]
CacheEntries and CacheHits are updated every ten (10) seconds. Red Hat strongly encourages using the database back end specific monitor entries for this and other database information.
| |
2.13. cn=uniqueid generator,cn=config
The unique ID generator configuration attributes are stored under cn=uniqueid generator,cn=config. The cn=uniqueid generator entry is an instance of the extensibleObject object class.
2.13.1. nsstate
This attribute saves the state of the unique ID generator across server restarts. This attribute is maintained by the server. Do not edit it.
| Parameter | Description |
|---|---|
| Entry DN | cn=uniqueid generator,cn=config |
| Valid Values | |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsstate: AbId0c3oMIDUntiLCyYNGgAAAAAAAAAA |
2.14. Common task invocation attributes for entries under cn=tasks,cn=config
Some core Directory Server, tasks can be initiated by editing a directory entry using LDAP tools. These task entries are contained in cn=tasks,cn=config. Each task can be invoked by updating an entry such as the following:
dn: cn=task_id,cn=task_type,cn=tasks,cn=config ...
dn: cn=task_id,cn=task_type,cn=tasks,cn=config
...This section lists the common attributes of all task types.
Task entries are not permanent configuration entries. They only exist in the configuration file for as long as the task operation is running or until the ttl period expires. Then, the entry is deleted automatically by the server.
2.14.1. cn
The cn attribute identifies a new task operation to initiate. The cn attribute value can be anything, as long as it defines a new task.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | DirectoryString |
| Example | cn: example task entry name |
2.14.2. nsTaskCancel
This attribute allows a task to be aborted while in progress. This attribute can be modified by users.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | |
| Syntax | Case-insensitive string |
| Example | nsTaskCancel: true |
2.14.3. nsTaskCurrentItem
This attribute shows the number of subtask which the task operation has completed, assuming the task can be broken down into subtasks. If there is only one task, then nsTaskCurrentItem is 0 while the task is running, and 1 when the task is complete. In this way, the attribute is analogous to a progress bar. When the nsTaskCurrentItem attribute has the same value as nsTaskTotalItems, then the task is completed.
This attribute value is set by the server and should not be edited.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | |
| Syntax | Integer |
| Example | nsTaskCurrentItem: 148 |
2.14.4. nsTaskExitCode
This attribute contains the exit code for the task. This attribute only exists after the task is completed and any value is only valid if the task is complete. The result code can be any LDAP exit code, but only a 0 value equals success; any other result code is an error.
This attribute value is set by the server and should not be edited.
2.14.5. nsTaskLog
This entry contains all of the log messages for the task, including both warning and information messages. New messages are appended to the end of the entry value, so this attribute value grows larger, without erasing the original contents, by default.
Successful task operations, which have an nsTaskExitCode of 0, are only recorded in the nsTaskLog attribute. Any non-zero response, which indicates an error, may be recorded in the error log as an error, but the error message is only recorded in the nsTaskLog attribute. For this reason, use the information in the nsTaskLog attribute to find out what errors actuall occurred.
This attribute value is set by the server and should not be edited.
2.14.6. nsTaskStatus
This attribute contains changing information about the status of the task, such as cumulative statistics or its current output message. The entire contents of the attribute may be updated periodically for as long as the process is running.
This attribute value is set by the server and should not be edited.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | case-exact string |
| Example | nsTaskStatus: Loading entries…. |
2.14.7. nsTaskTotalItems
This attribute shows the total number of subtasks that must be completed for the task operation. When the nsTaskCurrentItem attribute has the same value as nsTaskTotalItems, then the task is completed.
This attribute value is set by the server and should not be edited.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | |
| Syntax | Integer |
| Example | nsTaskTotalItems: 152 |
2.14.8. ttl
This attribute sets the amount of time (in seconds) the task entry will remain in the DSE after the task has finished or aborted. Setting a ttl attribute allows the task entry to be polled for new status information without missing the exit code. Setting the ttl attribute to 0 means that the entry is not cached.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | 0 (cannot be cached) to the maximum 32 bit integer value (2147483647) |
| Default Value | |
| Syntax | DirectoryString |
| Example | ttl: 120 |
2.15. cn=task_name,cn=import,cn=tasks,cn=config
An LDIF file or multiple LDIF files can be imported through the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory.
The cn=import entry is a container entry for import task operations. The cn=import entry itself has no attributes, but each of the task entries within this entry, such as cn=task_name,cn=import,cn=tasks,cn=config, uses the following attributes to define the import task.
An import task entry under cn=import must contain the LDIF file to import (in the nsFilename attribute) and the name of the instance into which to import the file (in the nsInstance attribute). Additionally, it must contain a unique cn to identify the task. For example:
dn: cn=example import,cn=import,cn=tasks,cn=config objectclass: extensibleObject cn: example import nsFilename: /home/files/example.ldif nsInstance: userRoot
dn: cn=example import,cn=import,cn=tasks,cn=config
objectclass: extensibleObject
cn: example import
nsFilename: /home/files/example.ldif
nsInstance: userRootAs the import operation runs, the task entry will contain all of the server-generated task attributes listed in Common task invocation attributes for entries under cn=tasks.
2.15.1. nsExcludeSuffix
This attribute identifies suffixes or subtrees in the LDIF file to exclude from the import.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | |
| Syntax | DN, multi-valued |
| Example | nsExcludeSuffix: ou=machines,dc=example,dc=com |
2.15.2. nsFilename
The nsFilename attribute contains the path and filenames of the LDIF files to import into Directory Server instance. To import multiple files, add multiple instances of this attribute. For example:
nsFilename: file1.ldif nsFilename: file2.ldif
nsFilename: file1.ldif
nsFilename: file2.ldif| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | Case-exact string, multi-valued |
| Example | nsFilename: /home/jsmith/example.ldif |
2.15.3. nsImportChunkSize
This attribute defines the number of chunks to have during the import operation, which overrides the server’s detection during the import of when to start a new pass and merges the chunks.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsImportChunkSize: 10 |
2.15.4. nsImportIndexAttrs
This attribute sets whether to index the attributes that are imported into database instance.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | true |
| Syntax | Case-insensitive string |
| Example | nsImportIndexAttrs: true |
2.15.5. nsIncludeSuffix
This attribute identifies a specific suffix or subtree to import from the LDIF file.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | |
| Syntax | DN, multi-valued |
| Example | nsIncludeSuffix: ou=people,dc=example,dc=com |
2.15.6. nsInstance
This attribute supplies the name of the database instance into which to import the files, such as userRoot or slapd-example.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | The name of a Directory Server instance database (any string) |
| Default Value | |
| Syntax | Case-exact string |
| Example | nsInstance: userRoot |
2.15.7. nsUniqueIdGenerator
This attribute defines how to generate name-based IDs; the attribute sets the namespace to use to generate the IDs. This option is useful to import the same LDIF file into two Directory Server instances when the entries need to have the same IDs.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | Case-insensitive string |
| Example | nsUniqueIdGeneratorNamespace: example |
2.15.8. nsUniqueIdGeneratorNamespace
This attribute defines how to generate name-based IDs; the attribute sets the namespace to use to generate the IDs. This option is useful to import the same LDIF file into two Directory Server instances when the entries need to have the same IDs.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | Case-insensitive string |
| Example | nsUniqueIdGeneratorNamespace: example |
2.16. cn=task_name,cn=export,cn=tasks,cn=config
A database or multiple databases can be exported through the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory.
The cn=export,cn=tasks,cn=config entry is a container for export task operations. These tasks are stored within this container and named cn=task_name,cn=export,cn=tasks,cn=config.
While the export operation is running, the task entry contains all of the server-generated task attributes listed in Common task invocation attributes for entries under cn=tasks.
2.16.1. nsDumpUniqId
This attribute sets that the unique IDs for the exported entries are not exported.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | true |
| Syntax | Case-insensitive string |
| Example | nsDumpUniqId: true |
2.16.2. nsExcludeSuffix
This attribute identifies suffixes or subtrees in the database to exclude from the exported LDIF file.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | |
| Syntax | DN, multi-valued |
| Example | nsExcludeSuffix: ou=machines,dc=example,dc=com |
2.16.3. nsExportReplica
This attribute identifies whether the exported database will be used in replication. For replicas, the proper attributes and settings will be included with the entry to initialize the replica automatically.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | false |
| Syntax | Case-insensitive string |
| Example | nsExportReplica: true |
2.16.4. nsFilename
The nsFilename attribute contains the path and filenames of the LDIF files to which to export the Directory Server instance database.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | Case-exact string, multi-valued |
| Example | nsFilename: /home/jsmith/example.ldif |
2.16.5. nsIncludeSuffix
This attribute identifies a specific suffix or subtree to export to an LDIF file.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | |
| Syntax | DN, multi-valued |
| Example | nsIncludeSuffix: ou=people,dc=example,dc=com |
2.16.6. nsInstance
This attribute supplies the name of the database instance from which to export the database, such as userRoot or userRoot.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | The name of a Directory Server instance (any string) |
| Default Value | |
| Syntax | Case-exact string, multi-valued |
| Example | nsInstance: userRoot |
2.16.7. nsNoWrap
This attribute sets whether to wrap long lines in the LDIF file.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | false |
| Syntax | Case-insensitive string |
| Example | nsNoWrap: false |
2.16.8. nsPrintKey
This attribute sets whether to print the entry ID number as the entry is processed by the export task.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | true |
| Syntax | Case-insensitive string |
| Example | nsPrintKey: false |
2.16.9. nsUseId2Entry
The nsUseId2Entry attribute uses the main database index, id2entry, to define the exported LDIF entries.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | false |
| Syntax | Case-insensitive string |
| Example | nsUseId2Entry: true |
2.16.10. nsUseOneFile
This attribute sets whether to export all Directory Server instances to a single LDIF file or separate LDIF files.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | true |
| Syntax | Case-insensitive string |
| Example | nsUseOneFile: true |
2.17. cn=task_name,cn=backup,cn=tasks,cn=config
A database can be backed up through the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory.
The cn=backup entry is a container entry for backup task operations. The cn=backup entry itself has no attributes, but each of the task entries within this entry, such as cn=task_ID,cn=backup,cn=tasks,cn=config, uses the following attributes to define the backup task.
A backup task entry under cn=backup must contain the location of the directory to which to copy the archive copy (in the backup-nsArchiveDir attribute) and the type of database being backed up (in the backup-nsDatabaseType attribute). Additionally, it must contain a unique cn to identify the task. For example:
dn: cn=example backup,cn=backup,cn=tasks,cn=config objectclass: extensibleObject cn: example backup nsArchiveDir: /export/backups/_ nsDatabaseType: ldbm database__
dn: cn=example backup,cn=backup,cn=tasks,cn=config
objectclass: extensibleObject
cn: example backup
nsArchiveDir: /export/backups/_ nsDatabaseType: ldbm database__As the backup operation runs, the task entry will contain all of the server-generated task attributes listed in Common task invocation attributes for entries under cn=tasks.
2.17.1. nsArchiveDir
This attribute gives the location of the directory to which to write the backup.
The backup directory here should usually be the same as the one configured in the nsslapd-bakdir attribute.
If this attribute is not included with the cn=backup task, the task will fail with an LDAP object class violation error (65).
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=backup,cn=tasks,cn=config |
| Valid Values | Any local directory location |
| Default Value | |
| Syntax | Case-exact string |
| Example | nsArchiveDir: /export/backups |
2.17.2. nsDatabaseType
This attribute gives the kind of database being archived. Setting the database types signals what kind of backup plug-in Directory Server should use to archive the database.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=backup,cn=tasks,cn=config |
| Valid Values | ldbm database |
| Default Value | ldbm database |
| Syntax | Case-exact string |
| Example | nsDatabaseType: ldbm database |
2.18. cn=task_name,cn=restore,cn=tasks,cn=config
A database can be restored through the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory.
The cn=restore entry is a container entry for task operations to restore a database. The cn=restore entry itself has no attributes, but each of the task entries within this entry, such as cn=task_ID,cn=restore,cn=tasks,cn=config, uses the following attributes to define the restore task.
A restore task entry under cn=restore must contain the location of the directory from which to retrieve the archive copy (in the restore-nsArchiveDir attribute) and the type of database being restored (in the restore-nsDatabaseType attribute). Additionally, it must contain a unique cn to identify the task. For example:
dn: cn=example restore,cn=restore,cn=tasks,cn=config objectclass: extensibleObject cn: example restore nsArchiveDir: /export/backups/ nsDatabaseType: ldbm database
dn: cn=example restore,cn=restore,cn=tasks,cn=config
objectclass: extensibleObject
cn: example restore
nsArchiveDir: /export/backups/
nsDatabaseType: ldbm databaseAs the restore operation runs, the task entry will contain all of the server-generated task attributes listed in Common task invocation attributes for entries under cn=tasks.
2.18.1. nsArchiveDir
This attribute gives the location of the directory to which to write the backup.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=restore,cn=tasks,cn=config |
| Valid Values | Any local directory location |
| Default Value | |
| Syntax | Case-exact string |
| Example | nsArchiveDir: /export/backups |
2.18.2. nsDatabaseType
This attribute gives the kind of database being archived. Setting the database types signals what kind of backup plug-in Directory Server should use to archive the database.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=restore,cn=tasks,cn=config |
| Valid Values | ldbm database |
| Default Value | ldbm database |
| Syntax | Case-exact string |
| Example | nsDatabaseType: ldbm database |
2.19. cn=task_name,cn=index,cn=tasks,cn=config
Directory attributes can be indexed though the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory.
The cn=index entry is a container entry for index task operations. The cn=index entry itself has no attributes, but each of the task entries within this entry, such as cn=task_ID,cn=index,cn=tasks,cn=config, uses the following attributes to define the backup task.
An index task entry under cn=index can create a standard index by identifying the attribute to be indexed and the type of index to create, both defined in the nsIndexAttribute attribute.
Alternatively, the index task can be used to generate virtual list view (VLV) indexes for an attribute using the nsIndexVLVAttribute attribute. This is the same as running the vlvindex script.
For example:
As the index operation runs, the task entry will contain all of the server-generated task attributes listed in Common task invocation attributes for entries under cn=tasks.
2.19.1. nsIndexAttribute
This attribute gives the name of the attribute to index and the types of indexes to apply. The format of the attribute value is the attribute name and a comma-separated list of index types, enclosed in double quotation marks. For example:
nsIndexAttribute: attribute:index1,index2
nsIndexAttribute: attribute:index1,index2| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=index,cn=tasks,cn=config |
| Valid Values | * Any attribute
* The index type, which can be |
| Default Value | |
| Syntax | Case-insensitive string, multi-valued |
| Example | * nsIndexAttribute: cn:pres,eq * nsIndexAttribute: description:sub |
2.19.2. nsIndexVLVAttribute
This attribute gives the name of the target entry for a VLV index. A virtual list view is based on a browsing index entry, which defines the virtual list base DN, scope, and filter. The nsIndexVLVAttribute value is the browsing index entry, and the VLV creation task is run according to the browsing index entry parameters.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=index,cn=tasks,cn=config |
| Valid Values | RDN of the subentry of the VLV entry definition |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsIndexVLVAttribute: "browsing index sort identifier" |
2.20. cn=task_name,cn=schema reload task,cn=tasks,cn=config
The directory schema is loaded when the directory instance is started or restarted. Any changes to the directory schema, including adding custom schema elements, are not loaded automatically and available to the instance until the server is restarted or by initiating a schema reload task.
Custom schema changes can be reloaded dynamically, without having to restart the Directory Server instance. This is done by initiating a schema reload task through creating a new task entry under the cn=tasks entry.
The custom schema file can be located in any directory; if not specified with the schemadir attribute, the server reloads the schema from the default /etc/dirsrv/slapd-instance_name/schema/ directory.
Any schema loaded from another directory must be copied into the schema directory or the schema will be lost when the server.
The schema reload task is initiated though the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory. For example:
dn: cn=example schema reload,cn=schema reload task,cn=tasks,cn=config objectclass: extensibleObject cn:example schema reload schemadir: /export/schema
dn: cn=example schema reload,cn=schema reload task,cn=tasks,cn=config
objectclass: extensibleObject
cn:example schema reload
schemadir: /export/schema
The cn=schema reload task entry is a container entry for schema reload operations. The cn=schema reload task entry itself has no attributes, but each of the task entries within this entry, such as cn=task_ID,cn=schema reload task,cn=tasks,cn=config, uses the schema reload attributes to define the individual reload task.
2.20.1. cn
The cn attribute identifies a new task operation to initiate. The cn attribute value can be anything, as long as it defines a new task.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=schema reload task,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | DirectoryString |
| Example | cn: example reload task ID |
2.20.2. schemadir
This contains the full path to the directory containing the custom schema file.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=schema reload task,cn=tasks,cn=config |
| Valid Values | Any local directory path |
| Default Value | /etc/dirsrv/schema |
| Syntax | DirectoryString |
| Example | schemadir: /export/schema/ |
2.21. cn=task_name,cn=memberof task,cn=tasks,cn=config
The memberOf attribute is created and managed by Directory Server automatically to display group membership on the members' user entries. When the member attribute on a group entry is changed, all of the members' associated directory entries are automatically updated with their corresponding memberOf attributes.
The cn=memberof task is used to create the initial memberOf attributes on the member’s user entries in the directory. After the memberOf attributes are created, then the MemberOf Plug-in manages the memberOf attributes automatically.
The memberOf update task must give the DN of the entry or subtree to run the update task against (set in the memberof-basdn attribute). Optionally, the task can include a filter to identify the members' user entries to update (set in the memberof-filter attribute). For example:
dn: cn=example memberOf,cn=memberof task,cn=tasks,cn=config objectclass: extensibleObject cn:example memberOf basedn: ou=people,dc=example,dc=com filter: (objectclass=groupofnames)
dn: cn=example memberOf,cn=memberof task,cn=tasks,cn=config
objectclass: extensibleObject
cn:example memberOf
basedn: ou=people,dc=example,dc=com
filter: (objectclass=groupofnames)When the task is complete, the task entry is removed from the directory.
The cn=memberof task entry is a container entry for memberOf update operations. The cn=memberof task entry itself has no attributes, but each of the task entries beneath this entry, such as cn=task_ID,cn=memberof task,cn=tasks,cn=config, uses its attributes to define the individual update task.
2.21.1. basedn
This attribute gives the base DN to use to search for the user entries to update the memberOf attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=memberof task,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | |
| Syntax | DN |
| Example | basedn: ou=people,dc=example,dc=com |
2.21.2. filter
This attribute gives an optional LDAP filter to use to select which user entries to update the memberOf attribute. Each member of a group has a corresponding user entry in the directory.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=memberof task,cn=tasks,cn=config |
| Valid Values | Any LDAP filter |
| Default Value | (objectclass=*) |
| Syntax | DirectoryString |
| Example | filter: (l=Sunnyvale) |
2.22. cn=task_name,cn=fixup linked attributes task,cn=tasks,cn=config
Directory Server has a Linked Attributes Plug-in which allows one attribute, set in one entry, to update another attribute in another entry automatically. Both entries have DNs for values. The DN value in the first entry points to the entry for the plug-in to update; the attribute in the second entry contains a DN back-pointer to the first entry.
This is similar to the way that the MemberOf Plug-in uses the member attribute in group entries to set memberOf attribute in user entries. With linked attributes, any attribute can be defined as a "link," and then another attribute is "managed" in affected entries.
The cn=fixup linked attributes creates the managed attributes — based on link attributes that already exist in the database — in the user entries once the linking plug-in instance is created. After the linked and managed attributes are set, the Linked Attributes Plug-in maintains the managed attributes dynamically, as users change the link attributes.
The linked attributes update task can specify which linked attribute plug-in instance to update, set in the optional cn-fixup-linked-attributes-linkdn attribute. If this attribute is not set on the task entry, then all configured linked attributes are updated.
dn: cn=example,cn=fixup linked attributes,cn=tasks,cn=config objectclass: extensibleObject cn:example linkdn: cn=Example Link,cn=Linked Attributes,cn=plugins,cn=config
dn: cn=example,cn=fixup linked attributes,cn=tasks,cn=config
objectclass: extensibleObject
cn:example
linkdn: cn=Example Link,cn=Linked Attributes,cn=plugins,cn=configWhen the task is complete, the task entry is removed from the directory.
The cn=fixup linked attributes entry is a container entry for any linked attribute update operation. The cn=fixup linked attributes entry itself has no attributes related to individual tasks, but each of the task entries beneath this entry, such as cn=task_ID,cn=fixup linked attributes,cn=tasks,cn=config, uses its attributes to define the individual update task.
2.22.1. linkdn
Each linked-managed attribute pair is configured in a linked attributes plug-in instance. The linkdn attribute sets the specific linked attribute plug-in used to update the entries by giving the plug-in instance DN. For example:
linkdn: cn=Manager Attributes,cn=Linked Attributes,cn=plugins,cn=config
linkdn: cn=Manager Attributes,cn=Linked Attributes,cn=plugins,cn=configIf no plug-in instance is given, then all linked attributes are updated.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=fixup linked attributes,cn=tasks,cn=config |
| Valid Values | A DN (for an instance of the Linked Attributes plug-in) |
| Default Value | None |
| Syntax | DN |
| Example | linkdn: cn=Manager Links,cn=Linked Attributes,cn=plugins,cn=config |
2.23. cn=task_name,cn=syntax validate,cn=tasks,cn=config
Syntax validation checks every modification to attributes to make sure that the new value has the required syntax for that attribute type. Attribute syntaxes are validated against the definitions in RFC 4514.
Syntax validation is enabled by default. However, syntax validation only audits changes to attribute values, such as when an attribute is added or modified. It does not validate the syntax of existing attribute values.
Validation of the existing syntax can be done with the syntax validation task. This task checks entries under a specified subtree (in the syntax-validation-basedn attribute) and, optionally, only entries which match a specified filter (in the syntax-validation-filter attribute).
dn: cn=example,cn=syntax validate,cn=tasks,cn=config objectclass: extensibleObject cn:example basedn: ou=people,dc=example,dc=com filter: "(objectclass=inetorgperson)"
dn: cn=example,cn=syntax validate,cn=tasks,cn=config
objectclass: extensibleObject
cn:example
basedn: ou=people,dc=example,dc=com
filter: "(objectclass=inetorgperson)"When the task is complete, the task entry is removed from the directory.
If syntax validation is disabled or if a server is migrated, then there may be data in the server which does not conform to attribute syntax requirements. The syntax validation task can be run to evaluate those existing attribute values before enabling syntax validation.
The cn=syntax validate entry is a container entry for any syntax validation operation. The cn=syntax validate entry itself has no attributes that are specific to any task. Each of the task entries beneath this entry, such as cn=task_ID,cn=syntax validate,cn=tasks,cn=config, uses its attributes to define the individual update task.
2.23.1. basedn
Gives the subtree against which to run the syntax validation task. For example:
basedn: ou=people,dc=example,dc=com
basedn: ou=people,dc=example,dc=com| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=syntax validate,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | None |
| Syntax | DN |
| Example | basedn: dc=example,dc=com |
2.23.2. filter
Contains an optional LDAP filter which can be used to identify specific entries beneath the given basedn against which to run the syntax validation task. If this attribute is not set on the task, then every entry within the basedn is audited. For example:
filter: "(objectclass=person)"
filter: "(objectclass=person)"| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=syntax validate,cn=tasks,cn=config |
| Valid Values | Any LDAP filter |
| Default Value | "(objectclass=*)" |
| Syntax | DirectoryString |
| Example | filter: "(objectclass=*)" |
2.24. cn=task_name,cn=USN tombstone cleanup task,cn=tasks,cn=config
If the USN Plug-in is enabled, then update sequence numbers (USNs) are set on every entry whenever a directory write operation, like add or modify, occurs on that entry. This is reflected in the entryUSN operational attribute. This USN is set even when an entry is deleted, and the tombstone entries are maintained by the Directory Server instance.
The cn=USN tombstone cleanup task deletes the tombstone entries maintained by the instance according to the back end database (in the backend attribute) or the suffix (in the suffix attribute). Optionally, only a subset of tombstone entries can be deleted by specifying a maximum USN to delete (in the max-usn-to-delete attribute), which preserves the most recent tombstone entries.
dn: cn=example,cn=USN tombstone cleanup task,cn=tasks,cn=config objectclass: extensibleObject cn:example backend: userroot max_usn_to_delete: 500
dn: cn=example,cn=USN tombstone cleanup task,cn=tasks,cn=config
objectclass: extensibleObject
cn:example
backend: userroot
max_usn_to_delete: 500This task can only be launched if replication is not enabled. Replication maintains its own tombstone store, and these tombstone entries cannot be deleted by the USN Plug-in; they must be maintained by the replication processes. Thus, Directory Server prevents users from running the cleanup task for replicated databases.
Attempting to create this task entry for a replicated back end will return this error in the command line:
ldap_add: DSA is unwilling to perform
ldap_add: DSA is unwilling to performIn the error log, there is a more explicit message that the suffix cannot have tombstone removed because it is replicated.
[...] usn-plugin - Suffix dc=example,dc=com is replicated. Unwilling to perform cleaning up tombstones.
[...] usn-plugin - Suffix dc=example,dc=com is replicated. Unwilling to perform cleaning up tombstones.When the task is complete, the task entry is removed from the directory.
The cn=USN tombstone cleanup task entry is a container entry for all USN tombstone delete operations. The cn=USN tombstone cleanup task entry itself has no attributes related to any individual task, but each of the task entries beneath this entry, such as cn=task_ID,cn=USN tombstone cleanup task,cn=tasks,cn=config, uses its attributes to define the individual update task.
2.24.1. backend
This gives the Directory Server instance back end, or database, to run the cleanup operation against. If the back end is not specified, then the suffix must be specified.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=USN tombstone cleanup task,cn=tasks,cn=config |
| Valid Values | Database name |
| Default Value | None |
| Syntax | DirectoryString |
| Example | backend: userroot |
2.24.2. max_usn_to_delete
This gives the highest USN value to delete when removing tombstone entries. All tombstone entries up to and including that number are deleted. Tombstone entries with higher USN values (that means more recent entries) are not deleted.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=USN tombstone cleanup task,cn=tasks,cn=config |
| Valid Values | Any integer |
| Default Value | None |
| Syntax | Integer |
| Example | max_usn_to_delete: 500 |
2.24.3. suffix
This gives the suffix or subtree in Directory Server to run the cleanup operation against. If the suffix is not specified, then the back end must be given.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=USN tombstone cleanup task,cn=tasks,cn=config |
| Valid Values | Any subtree DN |
| Default Value | None |
| Syntax | DN |
| Example | suffix: dc=example,dc=com |
2.25. cn=task_name,cn=cleanallruv,cn=tasks,cn=config
Information about the replication topology - all of the suppliers which are supplying updates to each other and other replicas within the same replication group - is contained in a set of metadata called the replica update vector (RUV). The RUV contains information about the supplier like its ID and URL, its latest change state number for changes made on the local server, and the CSN of the first change. Both suppliers and consumers store RUV information, and they use it to control replication updates.
When one supplier is removed from the replication topology, it may remain in another replica’s RUV. When the other replica is restarted, it can record errors in its log that the replication plug-in does not recognize the (removed) supplier.
When the supplier is permanently removed from the topology, then any lingering metadata about that supplier should be purged from every other supplier’s RUV entry.
The cn=cleanallruv task propagates through all servers in the replication topology and removes the RUV entries associated with the specified missing or obsolete supplier.
When the task is complete, the task entry is removed from the directory.
The cn=cleanallruv entry is a container entry for all clean RUV operations. The cn=cleanallruv entry itself has no attributes related to any individual task, but each of the task entries beneath this entry, such as cn=task_ID,cn=cleanallruv,cn=tasks,cn=config, uses its attributes to define the individual update task.
Each clean RUV task must specify the replica ID number of the replica RUV entries to remove, the based DN of the replicated database, and whether remaining updates from the missing supplier should be applied before removing the RUV data.
2.25.1. replica-base-dn
This gives the Directory Server base DN associated with the replicated database. This is the base DN for the replicated suffix.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=cleanallruv,cn=tasks,cn=config |
| Valid Values | Directory suffix DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | replica-base-dn: dc=example,dc=com |
2.25.2. replica-force-cleaning
This sets whether any outstanding updates from the replica to be removed should be applied (no) or whether the clean RUV operation should force-continue and lose any remaining updates (yes).
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=cleanallruv,cn=tasks,cn=config |
| Valid Values | no | yes |
| Default Value | None |
| Syntax | DirectoryString |
| Example | replica-force-cleaning: no |
2.25.3. replica-id
This gives the replica ID (defined in the nsDS5ReplicaId attribute for the replica configuration entry) of the replica to be removed from the replication topology.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=cleanallruv,cn=tasks,cn=config |
| Valid Values | 0 to 65534 |
| Default Value | None |
| Syntax | Integer |
| Example | replica-id: 55 |
2.26. cn=task_name,cn=abort cleanallruv,cn=tasks,cn=config
The cleanallruv task can take several minutes to propagate among all servers in the replication topology, even longer if the task processes all updates first. For performance or other maintenance considerations, it is possible to terminate a clean RUV task, and that termination is also propagated across all servers in the replication topology.
The termination task is a subentry of the cn=abort cleanallruv entry. When Directory Server completes the task, the task entry is removed from the directory.
The cn=abort cleanallruv entry is a container entry for all termination operations of the cleanallruv tasks. The cn=abort cleanallruv entry itself has no attributes related to any individual task, but each of the task entries beneath this entry, such as cn=task_ID,cn=abort cleanallruv,cn=tasks,cn=config, uses its attributes to define the individual update task.
Each abort cleanallruv task must specify the replica ID number of the replica RUV entries for which Directory Server runs the cleanallruv task, the base DN of the replicated database, and whether the terminate task should complete when it has completed on all servers in the topology or just locally.
2.26.1. replica-base-dn
This gives the Directory Server base DN associated with the replicated database. This is the base DN for the replicated suffix.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=abort cleanallruv,cn=tasks,cn=config |
| Valid Values | Directory suffix DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | replica-base-dn: dc=example,dc=com |
2.26.2. replica-certify-all
This sets whether the task should complete successfully on all servers in the replication topology before completing the task locally (yes) or whether the task should show complete as soon as it completes locally (no).
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=abort cleanallruv,cn=tasks,cn=config |
| Valid Values | no | yes |
| Default Value | None |
| Syntax | DirectoryString |
| Example | replica-certify-all: yes |
2.26.3. replica-id
This gives the replica ID (defined in the nsDS5ReplicaId attribute for the replica configuration entry) of the replica in the process of being removed from the replication topology.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=abort cleanallruv,cn=tasks,cn=config |
| Valid Values | 0 to 65534 |
| Default Value | None |
| Syntax | Integer |
| Example | replica-id: 55 |
2.27. cn=task_name,cn=automember rebuild membership,cn=tasks,cn=config
If autoMemberProcessModifyOps is set to off, the Auto Membership plugin runs only when new entries are added to the directory. The plugin ignores existing entries or entries that are edited to match an Auto Membership definition entry filter.
The cn=automember rebuild membership task runs the current Auto Membership rules against existing entries to update or rebuild group membership. All configured Auto Membership rules are run against the identified entries. However, not all rules might apply to a given entry.
2.27.1. basedn
This gives the Directory Server base DN to use to search for user entries. The entries in the specified DN are then updated according to the automembership rules.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember rebuild membership,cn=tasks,cn=config |
| Valid Values | Directory suffix DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | basedn: dc=example,dc=com |
2.27.2. filter
This attribute gives an LDAP filter to use to identify which user entries to update according to the configured automembership rules.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember rebuild membership,cn=tasks,cn=config |
| Valid Values | Any LDAP filter |
| Default Value | None |
| Syntax | DirectoryString |
| Example | filter: (uid=*) |
2.27.3. scope
This attribute gives an LDAP search scope to use when searching the given base DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember rebuild membership,cn=tasks,cn=config |
| Valid Values | sub | base | one |
| Default Value | None |
| Syntax | DirectoryString |
| Example | scope: sub |
2.28. cn=task_name,cn=automember export updates,cn=tasks,cn=config
This task runs against existing entries in the directory and exports the results of what users would have been added to what groups, based on the rules. This is useful for testing existing rules against existing users to see how your real deployment are performing.
The automembership-related changes are not executed. The proposed changes are written to a specified LDIF file.
2.28.1. basedn
This gives the Directory Server base DN to use to search for user entries. A test-run of the automembership rules will be run against the identified entries.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember export updates,cn=tasks,cn=config |
| Valid Values | Directory suffix DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | basedn: dc=example,dc=com |
2.28.2. filter
This attribute gives an LDAP filter to use to identify which user entries to test-run the automembership rules.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember export updates,cn=tasks,cn=config |
| Valid Values | Any LDAP filter |
| Default Value | None |
| Syntax | DirectoryString |
| Example | filter: (uid=*) |
2.28.3. ldif
This attribute sets the full path and filename of an LDIF file to which to write the proposed changes from the test-run of the automembership rules. This file must be local to the system from which the task is initiated.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember export updates,cn=tasks,cn=config |
| Valid Values | Local path and filename |
| Default Value | None |
| Syntax | DirectoryString |
| Example | ldif: /tmp/automember-results.ldif |
2.28.4. scope
This attribute gives an LDAP search scope to use when searching the given base DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember export updates,cn=tasks,cn=config |
| Valid Values | sub | base | one |
| Default Value | None |
| Syntax | DirectoryString |
| Example | scope: sub |
2.29. cn=task_name,cn=automember map updates,cn=tasks,cn=config
This task runs against entries within an LDIF file (new entries or, potentially, test entries) and then writes the proposed changes to those user entries to an LDIF file. This can be very useful for testing a new rule, before applying it to (real) new or existing user entries.
The automembership-related changes are not executed. The proposed changes are written to a specified LDIF file.
2.29.1. ldif_in
This attribute sets the full path and filename of an LDIF file from which to import entries to test with the configured automembership rules. These entries are not imported into the directory and the changes are not performed. The entries are loaded and used by the test-run only.
This file must be local to the system from which the task is initiated.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember map updates,cn=tasks,cn=config |
| Valid Values | Local path and filename |
| Default Value | None |
| Syntax | DirectoryString |
| Example | ldif_in: /tmp/automember-test-users.ldif |
2.29.2. ldif_out
This attribute sets the full path and filename of an LDIF file to which to write the proposed changes from the test-run of the automembership rules. This file must be local to the system from which the task is initiated.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember map updates,cn=tasks,cn=config |
| Valid Values | Local path and filename |
| Default Value | None |
| Syntax | DirectoryString |
| Example | ldif_out: /tmp/automember-results.ldif |
2.30. cn=task_name,cn=des2aes,cn=tasks,cn=config
This task searches for all reversible password entries in the specified user database which are encoded using the outdated DES cipher, and converts them to the more secure AES cipher.
Previously, this task was being performed automatically on all suffixes during Directory Server startup. However, since the search for DES passwords was typically unindexed, it could take a very long time to perform on suffixes containing large amounts of entries, which in turn caused Directory Server to time out and fail to start. For that reason, the search is now performed only on cn=config, but to convert passwords in any other database you must run this task manually.
2.30.1. suffix
This multivalued attribute specifies a suffix to check for DES passwords and convert them to AES. If this attribute is omitted then all the back ends/suffixes are checked.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=des2aes,cn=tasks,cn=config |
| Valid Values | Directory suffix DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | suffix: dc=example,dc=com |
2.31. Root DSE configuration parameters
2.31.1. nsslapd-return-default-opattr
Directory Server does not display the operational attributes in Root DSE searches. For example, if you are running the ldapsearch utility with the -s base -b "" parameters, only the user attributes are displayed. For clients expecting operational attributes in Root DSE search output, you can enable this behavior to provide backward compatibility:
- Stop the Directory Server instance.
Edit the
/etc/dirsrv/slapd-instance_name/dse.ldiffile and add the following parameters to thedn:section:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Start the Directory Server instance.
| Parameter | Description |
|---|---|
| Entry DN | Root DSE |
| Valid Values | supportedsaslmechanisms | nsBackendSuffix | subschemasubentry | supportedldapversion | supportedcontrol | ref | vendorname | vendorVersion |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-return-default-opattr: supportedsaslmechanisms |
Chapter 3. Configuration object classes
Many configuration entries simply use the extensibleObject object class, but some require other object classes. These configuration object classes are listed here.
3.1. changeLogEntry
This object class is used for entries which store changes made to the Directory Server entries.
To configure Directory Server to maintain a changelog that is compatible with the changelog implemented in Directory Server 4.1x, enable the Retro Changelog plug-in. Each entry in the changelog has the changeLogEntry object class.
This object class is defined in Changelog Internet Draft.
Superior Class
top
OID
2.16.840.1.113730.3.2.1
| objectClass | Defines the object classes for the entry. |
| Contains a number assigned arbitrarily to the changelog. | |
| The time at which a change took place. | |
| The type of change performed on an entry. | |
| The distinguished name of an entry added, modified or deleted on a supplier server. |
| Changes made to the Directory Server. | |
| A flag that defines whether the old Relative Distinguished Name (RDN) of the entry should be kept as a distinguished attribute of the entry or should be deleted. | |
| New RDN of an entry that is the target of a modRDN or modDN operation. | |
| Name of the entry that becomes the immediate superior of the existing entry when processing a modDN operation. |
3.2. directoryServerFeature
This object class is used specifically for entries which identify a feature of the directory service. This object class is defined by Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.40
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| cn | Specifies the common name of the entry. |
| multiLineDescription | Gives a text description of the entry. |
| oid | Specifies the OID of the feature. |
3.3. nsBackendInstance
This object class is used for the Directory Server back end, or database, instance entry. This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.109
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| cn | Gives the common name of the entry. |
3.4. nsDS5Replica
This object class is for entries which define a replica in database replication. Many of these attributes are set within the back end and cannot be modified.
Information on the attributes for this object class are listed with the core configuration attributes in chapter 2 of the Directory Server Configuration, Command, and File Reference.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.108
| objectClass | Defines the object classes for the entry. |
| nsDS5ReplicaId | Specifies the unique ID for suppliers in a replication environment. |
| nsDS5ReplicaRoot | Specifies the suffix DN at the root of a replicated area. |
| cn | Gives the name for the replica. |
| nsDS5Flags | Specifies information that has been previously set in flags. |
| nsDS5ReplicaAutoReferral | Sets whether the server will follow configured referrals for the Directory Server database. |
| nsDS5ReplicaBindDN | Specifies the DN to use when a supplier server binds to a consumer. |
| nsDS5ReplicaChangeCount | Gives the total number of entries in the changelog and whether they have been replicated. |
| nsDS5ReplicaLegacyConsumer | Specifies whether the replica is a legacy consumer. |
| nsDS5ReplicaName | Specifies the unique ID for the replica for internal operations. |
| nsDS5ReplicaPurgeDelay | Specifies the time in seconds before the changelog is purged. |
| nsDS5ReplicaReferral | Specifies the URLs for user-defined referrals. |
| nsDS5ReplicaReleaseTimeout | Specifies a timeout after which a supplier will release a replica, whether or not it has finished sending its updates. |
| nsDS5ReplicaTombstonePurgeInterval | Specifies the time interval in seconds between purge operation cycles. |
| nsDS5ReplicaType | Defines the type of replica, such as a read-only consumer. |
| nsDS5Task | Launches a replication task, such as dumping the database contents to LDIF; this is used internally by the Directory Server supplier. |
| nsState | Stores information on the clock so that proper change sequence numbers are generated. |
3.5. nsDS5ReplicationAgreement
Entries with the nsDS5ReplicationAgreement object class store the information set in a replication agreement. Information on the attributes for this object class are in chapter 2 of the Directory Server Configuration, Command, and File Reference.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.103
| objectClass | Defines the object classes for the entry. |
| cn | Used for naming the replication agreement. |
| description | Contains a free text description of the replication agreement. |
| nsDS5BeginReplicaRefresh | Initializes a replica manually. |
| nsds5debugreplicatimeout | Gives an alternate timeout period to use when the replication is run with debug logging. |
| nsDS5ReplicaBindDN | Specifies the DN to use when a supplier server binds to a consumer. |
| nsDS5ReplicaBindMethod | Specifies the method (SSL or simple authentication) to use for binding. |
| nsDS5ReplicaBusyWaitTime | Specifies the amount of time in seconds a supplier should wait after a consumer sends back a busy response before making another attempt to acquire access. |
| nsDS5ReplicaChangesSentSinceStartup | The number of changes sent to this replica since the server started. |
| nsDS5ReplicaCredentials | Specifies the password for the bind DN. |
| nsDS5ReplicaHost | Specifies the host name for the consumer replica. |
| nsDS5ReplicaLastInitEnd | States when the initialization of the consumer replica ended. |
| nsDS5ReplicaLastInitStart | States when the initialization of the consumer replica started. |
| nsDS5ReplicaLastInitStatus | The status for the initialization of the consumer. |
| nsDS5ReplicaLastUpdateEnd | States when the most recent replication schedule update ended. |
| nsDS5ReplicaLastUpdateStart | States when the most recent replication schedule update started. |
| nsDS5ReplicaLastUpdateStatus | Provides the status for the most recent replication schedule updates. |
| nsDS5ReplicaPort | Specifies the port number for the remote replica. |
| nsDS5ReplicaRoot | Specifies the suffix DN at the root of a replicated area. |
| nsDS5ReplicaSessionPauseTime | Specifies the amount of time in seconds a supplier should wait between update sessions. |
| nsDS5ReplicatedAttributeList | Specifies any attributes that will not be replicated to a consumer server. |
| nsDS5ReplicaTimeout | Specifies the number of seconds outbound LDAP operations will wait for a response from the remote replica before timing out and failing. |
| nsDS5ReplicaTransportInfo | Specifies the type of transport used for transporting data to and from the replica. |
| nsDS5ReplicaUpdateInProgress | States whether a replication schedule update is in progress. |
| nsDS5ReplicaUpdateSchedule | Specifies the replication schedule. |
| nsDS50ruv | Manages the internal state of the replica using the replication update vector. |
| nsruvReplicaLastModified | Contains the most recent time that an entry in the replica was modified and the changelog was updated. |
| nsds5ReplicaStripAttrs |
With fractional replication, an update to an excluded attribute still triggers a replication event, but that event is empty. This attribute sets attributes to strip from the replication update. This prevents changes to attributes like |
3.6. nsDSWindowsReplicationAgreement
Stores the synchronization attributes that concern the synchronization agreement. Information on the attributes for this object class are in chapter 2 of the Red Hat Directory Server Configuration, Command, and File Reference.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.503
| objectClass | Defines the object classes for the entry. |
| cn | Gives the name of the synchronization agreement. |
| description | Contains a text description of the synchronization agreement. |
| nsDS5BeginReplicaRefresh | Initiates a manual synchronization. |
| nsds5debugreplicatimeout | Gives an alternate timeout period to use when the synchronization is run with debug logging. |
| nsDS5ReplicaBindDN | Specifies the DN to use when Directory Server binds to the Windows server. |
| nsDS5ReplicaBindMethod | Specifies the method (SSL or simple authentication) to use for binding. |
| nsDS5ReplicaBusyWaitTime | Specifies the amount of time in seconds Directory Server should wait after the Windows server sends back a busy response before making another attempt to acquire access. |
| nsDS5ReplicaChangesSentSinceStartup | Shows the number of changes sent since Directory Server started. |
| nsDS5ReplicaCredentials | Specifies the credentials for the bind DN. |
| nsDS5ReplicaHost | Specifies the host name for the Windows domain controller of the Windows server being synchronized. |
| nsDS5ReplicaLastInitEnd | States when the last total update (resynchronization) of the Windows server ended. |
| nsDS5ReplicaLastInitStart | States when the last total update (resynchronization) of the Windows server started. |
| nsDS5ReplicaLastInitStatus | The status for the total update (resynchronization) of the Windows server. |
| nsDS5ReplicaLastUpdateEnd | States when the most recent update ended. |
| nsDS5ReplicaLastUpdateStart | States when the most recent update started. |
| nsDS5ReplicaLastUpdateStatus | Provides the status for the most recent updates. |
| nsDS5ReplicaPort | Specifies the port number for the Windows server. |
| nsDS5ReplicaRoot | Specifies the root suffix DN of Directory Server. |
| nsDS5ReplicaSessionPauseTime | Specifies the amount of time in seconds Directory Server should wait between update sessions. |
| nsDS5ReplicaTimeout | Specifies the number of seconds outbound LDAP operations will wait for a response from the Windows server before timing out and failing. |
| nsDS5ReplicaTransportInfo | Specifies the type of transport used for transporting data to and from the Windows server. |
| nsDS5ReplicaUpdateInProgress | States whether an update is in progress. |
| nsDS5ReplicaUpdateSchedule | Specifies the synchronization schedule. |
| nsDS50ruv | Manages the internal state of Directory Server sync peer using the replication update vector (RUV). |
| nsds7DirectoryReplicaSubtree | Specifies Directory Server suffix (root or sub) that is synced. |
| nsds7DirsyncCookie | Contains a cookie set by the sync service that functions as an RUV. |
| nsds7NewWinGroupSyncEnabled | Specifies whether new Windows group accounts are automatically created on Directory Server. |
| nsds7NewWinUserSyncEnabled | Specifies whether new Windows user accounts are automatically created on Directory Server. |
| nsds7WindowsDomain |
Identifies the Windows domain being synchronized; analogous to |
| nsds7WindowsReplicaSubtree | Specifies the Windows server suffix (root or sub) that is synced. |
| nsruvReplicaLastModified | Contains the most recent time that an entry in Directory Server sync peer was modified and the changelog was updated. |
| winSyncInterval |
Sets how frequently, in seconds, Directory Server polls the Windows server for updates to write over. If this is not set, the default is |
| winSyncMoveAction | Sets how the sync plug-in handles corresponding entries that are discovered in Active Directory outside of the synced subtree. The sync process can ignore these entries (none, the default) or it can assume that the entries were moved intentionally to remove them from synchronization, and it can then either delete the corresponding Directory Server entry (delete) or remove the synchronization attributes and no longer sync the entry (unsync). |
3.7. nsEncryptionConfig
The nsEncryptionConfig object class stores the configuration information for allowed encryption options, such as protocols and cipher suites. This is defined in the Administrative Services.
Superior Class
top
OID
nsEncryptionConfig-oid
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| cn (commonName) | Gives the common name of the device. |
| Attribute | Definition |
|---|---|
| nsSSL3SessionTimeout | Sets the timeout period for an SSLv3 cipher session. |
| nsSSLClientAuth | Sets how the server handles client authentication. There are three possible values: allow, disallow, or require. |
| nsSSLSessionTimeout | Sets the timeout period for a cipher session. |
| nsSSLSupportedCiphers | Contains a list of all ciphers available to be used with secure connections to the server. |
| nsTLS1 | Sets whether TLS version 1 is enabled for the server. |
3.8. nsEncryptionModule
The nsEncryptionModule object class stores the encryption module information. This is defined in the Administrative Services.
Superior Class
top
OID
nsEncryptionModule-oid
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| cn (commonName) | Gives the common name of the device. |
| Attribute | Definition |
|---|---|
| nsSSLActivation | Sets whether to enable a cipher family. |
| nsSSLPersonalitySSL | Contains the name of the certificate used by the server for SSL. |
| nsSSLToken | Identifies the security token used by the server. |
3.9. nsMappingTree
A mapping tree maps a suffix to the back end. Each mapping tree entry uses the nsMappingTree object class. This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.110
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| cn | Gives the common name of the entry. |
3.10. nsSaslMapping
This object class is used for entries which contain an identity mapping configuration for mapping SASL attributes to Directory Server attributes.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.317
| objectClass | Defines the object classes for the entry. |
| cn | Gives the name of the SASL mapping entry. |
| Contains the search base DN template. | |
| Contains the search filter template. | |
| Contains a regular expression to match SASL identity strings. |
3.11. nsslapdConfig
The nsslapdConfig object class defines the configuration object, cn=config, for the Directory Server instance.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.39
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| cn | Gives the common name of the entry. |
3.12. passwordPolicy
Both local and global password policies take the passwordPolicy object class. This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.13
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| Sets the number of seconds after which user passwords expire. | |
|
Identifies whether the user’s password expires after an interval given by the | |
| Sets the minimum number of characters that must be used in passwords. | |
| Sets the number of passwords the directory stores in the history. | |
| Identifies whether or not users is allowed to change their own password. | |
| Sets the number of seconds before a warning message is sent to users whose password is about to expire. | |
| Identifies whether or not users are locked out of the directory after a given number of failed bind attempts. | |
| Sets the number of failed bind attempts after which a user will be locked out of the directory. | |
| Identifies whether a user is locked out until the password is reset by an administrator or whether the user can log in again after a given lockout duration. The default is to allow a user to log back in after the lockout period. | |
| Sets the time, in seconds, that users will be locked out of the directory. | |
| Identifies whether the password syntax is checked by the server before the password is saved. | |
| Identifies whether or not to change their passwords when they first login to the directory or after the password is reset by the Directory Manager. | |
| Sets the type of encryption used to store Directory Server passwords. | |
| Sets the number of seconds that must pass before a user can change their password. | |
| Sets the time, in seconds, after which the password failure counter will be reset. Each time an invalid password is sent from the user’s account, the password failure counter is incremented. | |
| Sets the number of grace logins permitted when a user’s password is expired. | |
| Sets the minimum number of numeric characters (0 through 9) which must be used in the password. | |
| Sets the minimum number of alphabetic chracters that must be used in the password. | |
| Sets the minimum number of upper case alphabetic characters, A to Z, which must be used in the password. | |
| Sets the minimum number of lower case alphabetic characters, a to z, which must be used in the password. | |
|
Sets the minimum number of special ASCII characters, such as | |
| Sets the minimum number of 8-bit chracters used in the password. | |
| Sets the maximum number of times that the same character can be used in row. | |
| Sets the minimum number of categories which must be used in the password. | |
| Sets the length to check for trivial words. | |
| Sets a delay when temporary passwords become valid. | |
| Sets the number of seconds a temporary password is valid. | |
| Sets the maximum number off attempts a temporary password can be used. |
Chapter 4. cn=monitor
Information used to monitor the server is stored under cn=monitor. This entry and its children are read-only; clients cannot directly modify them. The server updates this information automatically. This section describes the cn=monitor attributes. The only attribute that can be changed by a user to set access control is the aci attribute.
If the nsslapd-counters attribute in cn=config is set to on (the default setting), then all of the counters kept by Directory Server instance increment using 64-bit integers, even on 32-bit machines or with a 32-bit version of Directory Server. For the cn=monitor entry, the 64-bit integers are used with the opsinitiated, opscompleted, entriessent, and bytessent counters.
The nsslapd-counters attribute enables 64-bit support for these specific database and server counters. The counters which use 64-bit integers are not configurable; the 64-bit integers are either enabled for all the allowed counters or disabled for all allowed counters.
4.1. backendMonitorDN
This attribute shows the DN for each Directory Server database backend. For further information on monitoring the database, see the following sections:
- Section 6.4.11, “Database attributes under cn=attribute_name,cn=encrypted attributes,cn=database_name,cn=ldbm database,cn=plugins,cn=config”
- Section 6.4.6, “Database attributes under cn=database,cn=monitor,cn=ldbm database,cn=plugins,cn=config”
- Section 6.5.4, “Database link attributes under cn=monitoring,cn=database_link_name,cn=chaining database,cn=plugins,cn=config”
4.2. bytesSent
This attribute shows the number of bytes sent by Directory Server.
4.3. connection
This attribute lists open connections and associated status and performance related information and values. These are given in the following format:
connection: pass:quotes[A:YYYYMMDDhhmmssZ:B:C:D:E:F:G:H:I:IP_address]
connection: pass:quotes[A:YYYYMMDDhhmmssZ:B:C:D:E:F:G:H:I:IP_address]For example:
connection: pass:quotes[69:20200604081953Z:6086:6086:-:cn=proxy,ou=special_users,dc=example,dc=test:0:11:27:7448846:ip=192.0.2.1]
connection: pass:quotes[69:20200604081953Z:6086:6086:-:cn=proxy,ou=special_users,dc=example,dc=test:0:11:27:7448846:ip=192.0.2.1]-
A is the connection number, which is the number of the slot in the connection table associated with this connection. This is the number logged as
slot=A in the access log message when this connection was opened, and usually corresponds to the file descriptor associated with the connection. The attributedTableSizeshows the total size of the connection table. - YYYYMMDDhhmmssZ is the date and time, in GeneralizedTime form, at which the connection was opened. This value gives the time in relation to Greenwich Mean Time.
- B is the number of operations received on this connection.
- C is the number of completed operations.
-
D is
rif the server is in the process of reading BER from the network, empty otherwise. This value is usually empty (as in the example). -
E this is the bind DN. This may be empty or have value of
NULLDNfor anonymous connections. -
F is the connection maximum threads state:
1is in max threads,0is not. - G is the number of times this thread has hit the maximum threads value.
- H is the number of operations attempted that were blocked by the maximum number of threads.
-
I is the connection ID as reported in the logs as
conn=connection_ID. - IP_address is the IP address of the LDAP client.
B and C for the initiated and completed operations should ideally be equal.
4.4. currentConnections
This attribute shows the number of currently open and active Directory Server connections
4.5. currentTime
This attribute shows the current time, given in Greenwich Mean Time (indicated by generalizedTime syntax Z notation; for example, 20220202131102Z).
4.6. dTableSize
The dTableSize attribute shows the size of Directory Server connection table. Each connection is associated with a slot in this table and usually corresponds to the file descriptor used by this connection. For more information, see nsslapd-maxdescriptors and nsslapd-reservedescriptors.
4.7. entriesSent
This attribute shows the number of entries sent by Directory Server.
4.8. nbackEnds
This attribute shows the number of Directory Server database back ends.
4.9. opsInitiated
This attribute shows the number of Directory Server operations completed.
4.10. readWaiters
This attribute shows the number of connections where some requests are pending and not currently being serviced by a thread in Directory Server.
4.11. startTime
This attribute shows Directory Server start time given in Greenwich Mean Time, indicated by generalizedTime syntax Z notation. For example, 20220202131102Z.
4.12. threads
This attribute shows the number of threads used by Directory Server. This should correspond to nsslapd-threadnumber in cn=config.
4.13. totalConnections
This attribute shows the total number of Directory Server connections. This number includes connections that have been opened and closed since the server was last started in addition to the currentConnections.
4.14. version
This attribute shows Directory Server vendor, version, and build number. For example, 389-Directory/2.0.14 B2022.082.0000.
Chapter 5. Root DSE attributes
The attributes in this section are used to define the root directory server entry (DSE) for the server instance. The information defined in the DSE relates to the actual configuration of the server instance, such as the controls, mechanisms, or features supported in that version of the server software. It also contains information specific to the instance, like its build number and installation date.
The DSE is a special entry, outside the normal DIT, and can be returned by searching with a null search base. For example:
ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -x -s base -b "" "objectclass=*"
# ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -x -s base -b "" "objectclass=*"5.1. dataversion
This attribute contains a timestamp which shows the most recent edit time for any data in the directory.
dataversion: 020090923175302020090923175302
dataversion: 020090923175302020090923175302| OID | |
| Syntax | GeneralizedTime |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
5.2. defaultNamingContext
Corresponds to the naming context, out of all configured naming contexts, which clients should use by default.
| OID | |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
5.3. lastusn
The USN Plug-in assigns a sequence number to every entry whenever a write operation — add, modify, delete, and modrdn — is performed for that entry. The USN is assigned in the entryUSN operational attribute for the entry.
The USN Plug-in has two modes: local and global.
In local mode, each database maintained for a server instance has its own instance of the USN Plug-in with a separate USN counter per back end database. The most recent USN assigned for any entry in the database is displayed in the lastusn attribute. When the USN Plug-in is set to local mode, the lastUSN attribute shows both the database which assigned the USN and the USN:
lastusn;pass:quotes[database_name]:pass:quotes[USN]
lastusn;pass:quotes[database_name]:pass:quotes[USN]For example:
lastusn;example1: 213 lastusn;example2: 207
lastusn;example1: 213
lastusn;example2: 207
In global mode, when the database uses a shared USN counter, the lastUSN value shows the latest USN assigned by any database:
lastusn: 420
lastusn: 4205.4. namingContexts
Corresponds to a naming context the server is controlling or shadowing. When Directory Server does not control any information (such as when it is an LDAP gateway to a public X.500 directory), this attribute is absent. When Directory Server believes it contains the entire directory, the attribute has a single value, and that value is the empty string (indicating the null DN of the root).This attribute permits a client contacting a server to choose suitable base objects for searching.
| OID | 1.3.6.1.4.1.1466.101.120.5 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
5.5. netscapemdsuffix
This attribute contains the DN for the top suffix of the directory tree for machine data maintained in the server. The DN itself points to an LDAP URL. For example:
cn=ldap://dc=pass:quotes[server_name],dc=example,dc=com:389
cn=ldap://dc=pass:quotes[server_name],dc=example,dc=com:389| OID | 2.16.840.1.113730.3.1.212 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
5.6. supportedControl
The values of this attribute are the object identifiers (OIDs) that identify the controls supported by the server. When the server does not support controls, this attribute is absent.
| OID | 1.3.6.1.4.1.1466.101.120.13 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
5.7. supportedExtension
The values of this attribute are the object identifiers (OIDs) that identify the extended operations supported by the server. When the server does not support extended operations, this attribute is absent.
| OID | 1.3.6.1.4.1.1466.101.120.7 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
5.8. supportedFeatures
This attribute contains features supported by the current version of Red Hat Directory Server.
| OID | 1.3.6.1.4.1.4203.1.3.5 |
| Syntax | OID |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
5.9. supportedLDAPVersion
This attribute identifies the versions of the LDAP protocol implemented by the server.
| OID | 1.3.6.1.4.1.1466.101.120.15 |
| Syntax | Integer |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
5.10. supportedSASLMechanisms
This attribute identifies the names of the SASL mechanisms supported by the server. When the server does not support SASL attributes, this attribute is absent.
| OID | 1.3.6.1.4.1.1466.101.120.14 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
5.11. vendorName
This attribute contains the name of the server vendor.
| OID | 1.3.6.1.1.4 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
5.12. vendorVersion
This attribute shows the vendor’s version number for the server.
| OID | 1.3.6.1.1.5 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
config-schema-reference-title
Chapter 6. Plug-in implemented server functionality reference
This chapter contains reference information on plug-ins.
The configuration for each part of Directory Server plug-in functionality has its own separate entry and set of attributes under the subtree cn=plugins,cn=config.
Some of these attributes are common to all plug-ins while others may be particular to a specific plug-in. You can check which attributes a given plug-in uses by performing an ldapsearch on the cn=config subtree.
All plug-ins are instances of the nsSlapdPlugin object class inherited from the extensibleObject object class. Server takes into account plug-in configuration attributes when both object classes (in addition to the top object class) are present in the entry, as shown in the following example:
dn:cn=ACL Plugin,cn=plugins,cn=config objectclass:top objectclass:nsSlapdPlugin objectclass:extensibleObject
dn:cn=ACL Plugin,cn=plugins,cn=config
objectclass:top
objectclass:nsSlapdPlugin
objectclass:extensibleObject6.1. List of attributes common to all plug-ins
This list provides a brief attribute description, the entry DN, valid range, default value, syntax, and an example for each attribute.
Each Directory Server plug-in belongs to the nsslapdPlugin object class.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.41
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| cn | Gives the common name of the entry. |
| Identifies the plugin library name (without the library suffix). | |
| Identifies an initialization function of the plugin. | |
| Identifies the type of plugin. | |
| Identifies the plugin ID. | |
| Identifies the version of plugin. | |
| Identifies the vendor of plugin. | |
| Identifies the description of the plugin. | |
| Identifies whether or not the plugin is enabled. | |
| Sets the priority for the plug-in in the execution order. |
6.1.1. nsslapd-logAccess
This attribute enables you to log search operations run by the plug-in to the file set in the nsslapd-accesslog parameter in cn=config.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-logAccess: Off |
6.1.2. nsslapd-logAudit
This attribute enables you to log and audit modifications to the database originated from the plug-in.
Successful modification events are logged in the audit log, if the nsslapd-auditlog-logging-enabled parameter is enabled in cn=config. To log failed modification database operations by a plug-in, enable the nsslapd-auditfaillog-logging-enabled attribute in cn=config.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-logAudit: Off |
6.1.3. nsslapd-pluginDescription
This attribute provides a description of the plug-in.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-pluginDescription: acl access check plug-in |
6.1.4. nsslapd-pluginEnabled
This attribute specifies whether the plug-in is enabled. This attribute can be changed over protocol but will only take effect when the server is next restarted.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-pluginEnabled: on |
6.1.5. nsslapd-pluginId
This attribute specifies the plug-in ID.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | Any valid plug-in ID |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-pluginId: chaining database |
6.1.6. nsslapd-pluginInitfunc
This attribute specifies the plug-in function to be initiated.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | Any valid plug-in function |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-pluginInitfunc: NS7bitAttr_Init |
6.1.7. nsslapd-pluginPath
This attribute specifies the full path to the plug-in.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | Any valid path |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-pluginPath: uid-plugin |
6.1.8. nsslapd-pluginPrecedence
This attribute sets the precedence or priority for the execution order of a plug-in. Precedence defines the execution order of plug-ins, which allows more complex environments or interactions since it can enable a plug-in to wait for a completed operation before being executed. This is more important for pre-operation and post-operation plug-ins.
Plug-ins with a value of 1 have the highest priority and are run first; plug-ins with a value of 99 have the lowest priority. The default is 50.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | 1 to 99 |
| Default Value | 50 |
| Syntax | Integer |
| Example | nsslapd-pluginPrecedence: 3 |
6.1.9. nsslapd-pluginType
This attribute specifies the plug-in type. See Section 6.2.4, “nsslapd-plugin-depends-on-type” for further information.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | Any valid plug-in type |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-pluginType: preoperation |
6.1.10. nsslapd-pluginVendor
This attribute specifies the vendor of the plug-in.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | Any approved plug-in vendor |
| Default Value | Red Hat, Inc. |
| Syntax | DirectoryString |
| Example | nsslapd-pluginVendor: Red Hat, Inc. |
6.1.11. nsslapd-pluginVersion
This attribute specifies the plug-in version.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | Any valid plug-in version |
| Default Value | Product version number |
| Syntax | DirectoryString |
| Example | nsslapd-pluginVersion: {VER} |
6.2. Optional attributes of certain plug-ins
6.2.1. nsslapd-dynamic-plugins
You can enable some Directory Server plug-ins dynamically without the instance restart. Enable the nsslapd-dynamic-plugins attribute in Directory Server to allow the dynamic plug-ins. By default, dynamic plug-ins are disabled.
Red Hat Directory Server does not support dynamic plug-ins. Use it only for testing and debugging purposes.
You cannot configure some plug-ins as dynamic. To enable such plug-ins, restart the instance.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-dynamic-plugins: on |
6.2.2. nsslapd-pluginConfigArea
Some plug-in entries are container entries, and multiple instances of the plug-in are created beneath this container in cn=plugins,cn=config. However, the cn=plugins,cn=config is not replicated, which means that the plug-in configurations beneath those container entries must be configured manually, in some way, on every Directory Server instance.
The nsslapd-pluginConfigArea attribute points to another container entry, in the main database area, which contains the plug-in instance entries. This container entry can be in a replicated database, which allows the plug-in configuration to be replicated.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | DN |
| Example | nsslapd-pluginConfigArea: cn=managed entries container,ou=containers,dc=example,dc=com |
6.2.3. nsslapd-plugin-depends-on-named
Multi-valued attribute used to ensure that plug-ins are called by the server in the correct order. Takes a value which corresponds to the cn value of a plug-in. The plug-in with a cn value matching one of the following values will be started by the server prior to this plug-in. If the plug-in does not exist, the server fails to start. The following postoperation Referential Integrity Plug-in example shows that the Views plug-in is started before Roles. If Views is missing, the server is not going to start.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=referential integrity postoperation,cn=plugins,cn=config |
| Valid Values | Class of Service |
| Default Value | |
| Syntax | DirectoryString |
| Example | * nsslapd-plugin-depends-on-named: Views * nsslapd-pluginId: roles |
6.2.4. nsslapd-plugin-depends-on-type
Multi-valued attribute used to ensure that plug-ins are called by the server in the correct order. Takes a value which corresponds to the type number of a plug-in, contained in the attribute nsslapd-pluginType. See Section 6.1.9, “nsslapd-pluginType” for further information. All plug-ins with a type value which matches one of the values in the following valid range will be started by the server prior to this plug-in. The following postoperation Referential Integrity Plug-in example shows that the database plug-in will be started prior to the postoperation Referential Integrity Plug-in.
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=referential integrity postoperation,cn=plugins,cn=config |
| Valid Values | database |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-plugin-depends-on-type: database |
6.2.5. nsslapd-pluginLoadGlobal
This attribute specifies whether the symbols in dependent libraries are made visible locally (false) or to the executable and to all shared objects (true).
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | true | false |
| Default Value | false |
| Syntax | DirectoryString |
| Example | nsslapd-pluginLoadGlobal: false |
6.2.6. nsslapd-pluginLoadNow
This attribute specifies whether to load all of the symbols used by a plug-in immediately (true), as well as all symbols references by those symbols, or to load the symbol the first time it is used (false).
| Plug-in Parameter | Description |
|---|---|
| Entry DN | cn=plug-in name,cn=plugins,cn=config |
| Valid Values | true | false |
| Default Value | false |
| Syntax | DirectoryString |
| Example | nsslapd-pluginLoadNow: false |
6.3. Server plug-in functionality reference
This section provides an overview of the plug-ins provided with Directory Server, along with their configurable options, configurable arguments, default setting, dependencies, general performance-related information, and further reading.
6.3.1. 7-bit Check plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | NS7bitAtt |
| DN of Configuration Entry | cn=7-bit check,cn=plugins,cn=config |
| Description | Checks certain attributes are 7-bit clean |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments |
List of attributes ( |
| Dependencies | Database |
| Performance-Related Information | None |
| Further Information | If Directory Server uses non-ASCII characters, such as Japanese, turn this plug-in off. |
6.3.2. Account Policy plug-in
Account policies can be set that automatically lock an account after a certain amount of time has elapsed. This can be used to create temporary accounts that are only valid for a preset amount of time or to lock users which have been inactive for a certain amount of time.
The Account Policy Plug-in itself only accept on argument, which points to a plug-in configuration entry.
dn: cn=Account Policy Plugin,cn=plugins,cn=config ... nsslapd-pluginarg0: cn=config,cn=Account Policy Plugin,cn=plugins,cn=config
dn: cn=Account Policy Plugin,cn=plugins,cn=config
...
nsslapd-pluginarg0: cn=config,cn=Account Policy Plugin,cn=plugins,cn=configThe account policy configuration entry defines, for the entire server, what attributes to use for account policies. Most of the configuration defines attributes to use to evaluate account policies and expiration times, but the configuration also defines what object class to use to identify subtree-level account policy definitions.
One the plug-in is configured globally, account policy entries can be created within the user subtrees, and then these policies can be applied to users and to roles through classes of service.
Example 6.1. Account Policy Definition
Any entry, both individual users and roles or CoS templates, can be an account policy subentry. Every account policy subentry has its creation and login times tracked against any expiration policy.
Example 6.2. User Account with Account Policy
dn: uid=scarter,ou=people,dc=example,dc=com ... lastLoginTime: 20060527001051Z acctPolicySubentry: cn=AccountPolicy,dc=example,dc=com
dn: uid=scarter,ou=people,dc=example,dc=com
...
lastLoginTime: 20060527001051Z
acctPolicySubentry: cn=AccountPolicy,dc=example,dc=com| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | none |
| DN of Configuration Entry | cn=Account Policy Plugin,cn=plugins,cn=config |
| Description | Defines a policy to lock user accounts after a certain expiration period or inactivity period. |
| Type | object |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | A pointer to a configuration entry which contains the global account policy settings. |
| Dependencies | Database |
| Performance-Related Information | None |
| Further Information |
This plug-in configuration points to a configuration entry which is used for server-wide settings on account inactivity and expiration data. Individual (subtree-level or user-level) account policies can be defined as directory entries, as instances of the |
6.3.2.1. altstateattrname
Account expiration policies are based on some timed criteria for the account. For example, for an inactivity policy, the primary criteria may be the last login time, lastLoginTime. However, there may be instances where that attribute does not exist on an entry, such as a user who never logged into his account. The altstateattrname attribute provides a backup attribute for the server to reference to evaluate the expiration time.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=Account Policy Plugin,cn=plugins,cn=config |
| Valid Range | Any time-based entry attribute |
| Default Value | None |
| Syntax | DirectoryString |
| Example | altstateattrname: createTimeStamp |
6.3.2.2. alwaysRecordLogin
By default, only entries which have an account policy directly applied to them — meaning, entries with the acctPolicySubentry attribute — have their login times tracked. If account policies are applied through classes of service or roles, then the acctPolicySubentry attribute is on the template or container entry, not the user entries themselves.
The alwaysRecordLogin attribute sets that every entry records its last login time. This allows CoS and roles to be used to apply account policies.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=Account Policy Plugin,cn=plugins,cn=config |
| Valid Range | yes | no |
| Default Value | no |
| Syntax | DirectoryString |
| Example | alwaysRecordLogin: no |
6.3.2.3. alwaysRecordLoginAttr
The Account Policy plug-in uses the attribute name set in the alwaysRecordLoginAttr parameter to store the time of the last successful login in this attribute in the user’s directory entry.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=Account Policy Plugin,cn=plugins,cn=config |
| Valid Range | Any valid attribute name |
| Default Value | stateAttrName |
| Syntax | DirectoryString |
| Example | alwaysRecordLoginAttr: lastLoginTime |
6.3.2.4. lastLoginHistSize
To maintain a history of successful logins, you can use the lastLoginHistSize attribute that determines the number of logins to store and stores the last five successful logins by default.
For the lastLoginHistSize attribute to stores the last logins, you must enable the alwaysRecordLogin attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=Account Policy Plugin,cn=plugins,cn=config |
| Valid Range | 0 (Disable) to the maximum 32 bit integer value (2147483647) |
| Default Value | 5 |
| Syntax | Integer |
| Example | lastloginhistorysize: 10 |
6.3.2.5. limitattrname
The account policy entry in the user directory defines the time limit for the account lockout policy. This time limit can be set in any time-based attribute, and a policy entry could have multiple time-based attributes in ti. The attribute within the policy to use for the account inactivation limit is defined in the limitattrname attribute in the Account Policy Plug-in, and it is applied globally to all account policies.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=Account Policy Plugin,cn=plugins,cn=config |
| Valid Range | Any time-based entry attribute |
| Default Value | None |
| Syntax | DirectoryString |
| Example | limitattrname: accountInactivityLimit |
6.3.2.6. specattrname
There are really two configuration entries for an account policy: the global settings in the plug-in configuration entry and then yser- or subtree-level settings in an entry within the user directory. An account policy can be set directly on a user entry or it can be set as part of a CoS or role configuration. The way that the plug-in identifies which entries are account policy configuration entries is by identifying a specific attribute on the entry which flags it as an account policy. This attribute in the plug-in configuration is is specattrname; its will usually be set to acctPolicySubentry.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=Account Policy Plugin,cn=plugins,cn=config |
| Valid Range | Any time-based entry attribute |
| Default Value | None |
| Syntax | DirectoryString |
| Example | specattrname: acctPolicySubentry |
6.3.2.7. stateattrname
Account expiration policies are based on some timed criteria for the account. For example, for an inactivity policy, the primary criteria may be the last login time, lastLoginTime. The primary time attribute used to evaluate an account policy is set in the stateattrname attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=Account Policy Plugin,cn=plugins,cn=config |
| Valid Range | Any time-based entry attribute |
| Default Value | None |
| Syntax | DirectoryString |
| Example | stateattrname: lastLoginTime |
6.3.3. Account Usability plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | acctusability |
| DN of Configuration Entry | cn=Account Usability Plugin,cn=plugins,cn=config |
| Description | Checks the authentication status, or usability, of an account without actually authenticating as the given user |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | on |
| Dependencies | Database |
| Performance-Related Information | None |
6.3.4. ACL plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | acl |
| DN of Configuration Entry | cn=ACL Plugin,cn=plugins,cn=config |
| Description | ACL access check plug-in |
| Type | accesscontrol |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | Database |
| Performance-Related Information | Access control incurs a minimal performance hit. Leave this plug-in enabled since it is the primary means of access control for the server. |
6.3.5. ACL Preoperation plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | acl |
| DN of Configuration Entry | cn=ACL preoperation,cn=plugins,cn=config |
| Description | ACL access check plug-in |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | Database |
| Performance-Related Information | Access control incurs a minimal performance hit. Leave this plug-in enabled since it is the primary means of access control for the server. |
6.3.6. AD DN plug-in
The AD DN plug-in supports multiple domain configurations. Create one configuration entry for each domain.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | addn |
| DN of Configuration Entry | cn=addn,cn=plugins,cn=config |
| Description |
Enables the usage of Active Directory-formatted user names, such as |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments |
|
| Dependencies | None |
| Performance-Related Information | None |
6.3.6.1. addn_base
Sets the base DN under which Directory Server searches the user’s DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=domain_name,cn=addn,cn=plugins,cn=config |
| Valid Entry | Any valid DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | addn_base: ou=People,dc=example,dc=com |
6.3.6.2. addn_filter
Sets the search filter. Directory Server replaces the %s variable automatically with the non-domain part of the authenticating user. For example, if the user name in the bind is user_name@example.com, the filter searches the corresponding DN which is (&(objectClass=account)(uid=user_name)).
| Parameter | Description |
|---|---|
| Entry DN | cn=domain_name,cn=addn,cn=plugins,cn=config |
| Valid Entry | Any valid DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | addn_filter: (&(objectClass=account)(uid=%s)) |
6.3.6.3. cn
Sets the domain name of the configuration entry. The plug-in uses the domain name from the authenticating user name to select the corresponding configuration entry.
| Parameter | Description |
|---|---|
| Entry DN | cn=domain_name,cn=addn,cn=plugins,cn=config |
| Valid Entry | Any string |
| Default Value | None |
| Syntax | DirectoryString |
| Example | cn: example.com |
6.3.7. Alias Entries plug-in
The Alias Entries plug-in checks the base entry for the object class alias and the aliasedObjectName attribute that contains a DN to another entry (an alias to another entry). During a search, the plug-in modifies the search base DN to this aliased DN.
The Alias Entries plug-in supports only base level searches. Use the ldapsearch -a find command to retrieve entries with aliases.
For the plug-in to return the aliased entry, the base entry must contain the following information:
-
The
aliasobject class. -
The
aliasedObjectNameattribute (known as thealiasedEntryNameattribute in X.500) with a DN value pointing to another entry.
Directory Server can return to the client the following errors:
-
Error 32 (no such object)if the alias DN is missing. -
Error 53 (unwilling to perform)if the search is a non-base level search.
Dereferencing is the conversion of an alias name to an object name. The process may require the examination of more than one alias entry. An alias entry may point to an entry that is not a leaf entry. An entry in the DIT may have multiple alias names, and several alias entries may point to the same entry.
Example 6.3. An Entry with an alias
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | Alias Entries |
| DN of Configuration Entry | cn=Alias Entries, cn=plugins, cn=config |
| Description |
Checks the base entry for |
| Type | object |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments |
Alias entries belong to the
The |
| Dependencies | Database |
| Performance-Related Information |
Every alias entry must belong to the |
| Further Information |
The
The |
6.3.8. Attribute Uniqueness plug-in
The Attribute Uniqueness plug-in ensures that the value of an attribute is unique across the directory or subtree.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | NSUniqueAttr |
| DN of Configuration Entry | cn=Attribute Uniqueness,cn=plugins,cn=config |
| Description | Checks that the values of specified attributes are unique each time a modification occurs on an entry. For example, most sites require that a user ID and email address be unique. |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments |
To check for UID attribute uniqueness in all listed subtrees, enter |
| Dependencies | Database |
| Performance-Related Information | Directory Server provides the UID Uniqueness Plug-in by default. To ensure unique values for other attributes, create instances of the Attribute Uniqueness Plug-in for those attributes. The UID Uniqueness Plug-in is off by default due to operation restrictions that need to be addressed before enabling the plug-in in a multi-supplier replication environment. Turning the plug-in on may slow down Directory Server performance. |
6.3.8.1. cn
Sets the name of the Attribute Uniqueness plug-in configuration record. You can use any string, but Red Hat recommends naming the configuration record attribute_name Attribute Uniqueness.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_uniqueness_configuration_record_name,cn=plugins,cn=config |
| Valid Values | Any valid string |
| Default Value | None |
| Syntax | DirectoryString |
| Example | cn: mail Attribute Uniqueness |
6.3.8.2. uniqueness-across-all-subtrees
If enabled (on), the plug-in checks that the attribute is unique across all subtrees set. If you set the attribute to off, uniqueness is only enforced within the subtree of the updated entry.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_uniqueness_configuration_entry_name,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | uniqueness-across-all-subtrees: off |
6.3.8.3. uniqueness-attribute-name
Sets the name of the attribute whose values must be unique. This attribute is multi-valued.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_uniqueness_configuration_entry_name,cn=plugins,cn=config |
| Valid Values | Any valid attribute name |
| Default Value | None |
| Syntax | DirectoryString |
| Example | uniqueness-attribute-name: mail |
6.3.8.4. uniqueness-exclude-subtrees
Sets the DN under which the plug-in skips uniqueness verification of the attribute’s value. This attribute is multi-valued.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_uniqueness_configuration_entry_name,cn=plugins,cn=config |
| Valid Values | Any valid subtree DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | uniqueness-exclude-subtrees: dc=private,dc=people,dc=example,dc=com |
6.3.8.5. uniqueness-subtree-entries-oc
Optionally, when using the uniqueness-top-entry-oc parameter, you can configure that the Attribute Uniqueness plug-in only verifies if an attribute is unique, if the entry contains the object class set in this parameter.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_uniqueness_configuration_entry_name,cn=plugins,cn=config |
| Valid Values | Any valid object class |
| Default Value | None |
| Syntax | DirectoryString |
| Example | uniqueness-subtree-entries-oc: inetOrgPerson |
6.3.8.6. uniqueness-subtrees
Sets the DN under which the plug-in checks for uniqueness of the attribute’s value. This attribute is multi-valued.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_uniqueness_configuration_entry_name,cn=plugins,cn=config |
| Valid Values | Any valid subtree DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | uniqueness-subtrees: ou=Sales,dc=example,dc=com |
6.3.8.7. uniqueness-top-entry-oc
Directory Server searches this object class in the parent entry of the updated object. If it was not found, the search continues at the next higher level entry up to the root of the directory tree. If the object class was found, Directory Server verifies that the value of the attribute set in uniqueness-attribute-name is unique in this subtree.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_uniqueness_configuration_entry_name,cn=plugins,cn=config |
| Valid Values | Any valid object class |
| Default Value | None |
| Syntax | DirectoryString |
| Example | uniqueness-top-entry-oc: nsContainer |
6.3.9. Auto Membership plug-in
Automembership essentially allows a static group to act like a dynamic group. Different automembership definitions create searches that are automatically run on all new directory entries. The automembership rules search for and identify matching entries — much like the dynamic search filters — and then explicitly add those entries as members to the specified static group.
The Auto Membership Plug-in itself is a container entry. Each automember definition is a child of the Auto Membership Plug-in. The automember definition defines the LDAP search base and filter to identify entries and a default group to add them to.
Each automember definition can have its own child entry that defines additional conditions for assigning the entry to group. Regular expressions can be used to include or exclude entries and assign them to specific groups based on those conditions.
If the entry matches the main definition and not any of the regular expression conditions, then it uses the group in the main definition. If it matches a regular expression condition, then it is added to the regular expression condition group.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | Auto Membership |
| DN of Configuration Entry | cn=Auto Membership,cn=plugins,cn=config |
| Description | Container entry for automember definitions. Automember definitions search new entries and, if they match defined LDAP search filters and regular expression conditions, add the entry to a specified group automatically. |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | None for the main plug-in entry. The definition entry must specify an LDAP scope, LDAP filter, default group, and member attribute format. The optional regular expression child entry can specify inclusive and exclusive expressions and a different target group. |
| Dependencies | Database |
| Performance-Related Information | None. |
6.3.9.1. autoMemberDefaultGroup
This attribute sets a default or fallback group to add the entry to as a member. If only the definition entry is used, then this is the group to which all matching entries are added. If regular expression conditions are used, then this group is used as a fallback if an entry which matches the LDAP search filter do not match any of the regular expressions.
| Parameter | Description |
|---|---|
| Entry DN | cn=Auto Membership Plugin,cn=plugins,cn=config |
| Valid Range | Any existing Directory Server group |
| Default Value | None |
| Single- or Multi-Valued | Single |
| Syntax | DirectoryString |
| Example | autoMemberDefaultGroup: cn=hostgroups,ou=groups,dc=example,dc=com |
6.3.9.2. autoMemberDefinition (object class)
This attribute identifies the entry as an automember definition. This entry must be a child of the Auto Membership Plug-in, cn=Auto Membership Plugin,cn=plugins,cn=config.
Allowed Attributes
- autoMemberScope
- autoMemberFilter
- autoMemberDefaultGroup
- autoMemberGroupingAttr
6.3.9.3. autoMemberExclusiveRegex
This attribute sets a single regular expression to use to identify entries to exclude. If an entry matches the exclusion condition, then it is not included in the group. Multiple regular expressions could be used, and if an entry matches any one of those expressions, it is excluded in the group.
The format of the expression is a Perl-compatible regular expression (PCRE). For more information on PCRE patterns, see the pcresyntax(3) man page.
Exclude conditions are evaluated first and take precedence over include conditions.
| Parameter | Description |
|---|---|
| Entry DN | cn=Auto Membership Plugin,cn=plugins,cn=config |
| Valid Range | Any regular expression |
| Default Value | None |
| Single- or Multi-Valued | Multi-valued |
| Syntax | DirectoryString |
| Example | autoMemberExclusiveRegex: fqdn=^www\.web[0-9]+\.example\.com |
6.3.9.4. autoMemberFilter
This attribute sets a standard LDAP search filter to use to search for matching entries.
| Parameter | Description |
|---|---|
| Entry DN | cn=Auto Membership Plugin,cn=plugins,cn=config |
| Valid Range | Any valid LDAP search filter |
| Default Value | None |
| Single- or Multi-Valued | Single |
| Syntax | DirectoryString |
| Example | autoMemberFilter:objectclass=ntUser |
6.3.9.5. autoMemberGroupingAttr
This attribute gives the name of the member attribute in the group entry and the attribute in the object entry that supplies the member attribute value, in the format group_member_attr:entry_attr.
This structures how the Automembership Plug-in adds a member to the group, depending on the group configuration. For example, for a groupOfUniqueNames user group, each member is added as a uniqueMember attribute. The value of uniqueMember is the DN of the user entry. In essence, each group member is identified by the attribute-value pair of uniqueMember: user_entry_DN. The member entry format, then, is uniqueMember:dn.
| Parameter | Description |
|---|---|
| Entry DN | cn=Auto Membership Plugin,cn=plugins,cn=config |
| Valid Range | Any Directory Server attribute |
| Default Value | None |
| Single- or Multi-Valued | Single |
| Syntax | DirectoryString |
| Example | autoMemberGroupingAttr: member:dn |
6.3.9.6. autoMemberInclusiveRegex
This attribute sets a single regular expression to use to identify entries to include. Multiple regular expressions could be used, and if an entry matches any one of those expressions, it is included in the group (assuming it does not match an exclude expression).
The format of the expression is a Perl-compatible regular expression (PCRE). For more information on PCRE patterns, see the pcresyntax(3) man page.
| Parameter | Description |
|---|---|
| Entry DN | cn=Auto Membership Plugin,cn=plugins,cn=config |
| Valid Range | Any regular expression |
| Default Value | None |
| Single- or Multi-Valued | Multi-valued |
| Syntax | DirectoryString |
| Example | autoMemberInclusiveRegex: fqdn=^www\.web[0-9]+\.example\.com |
6.3.9.7. autoMemberProcessModifyOps
By default, Directory Server invokes the Automembership plug-in for add and modify operations. With this setting, the plug-in changes groups when you add a group entry to a user or modify a group entry of a user. If you set the autoMemberProcessModifyOps to off, Directory Server only invokes the Automembership plug-in when you add a group entry to a user. In this case, if an administrator changes a user entry, and that entry impactes what Automembership groups the user belongs to, the plug-in does not remove the user from the old group and only adds the new group. To update the old group, you must then manually run a fix-up task.
| Parameter | Description |
|---|---|
| Entry DN | cn=Auto Membership Plugin,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Single- or Multi-Valued | Single |
| Syntax | DirectoryString |
| Example | autoMemberProcessModifyOps: on |
6.3.9.8. autoMemberRegexRule (object class)
This attribute identifies the entry as a regular expression rule. This entry must be a child of an automember definition (objectclass: autoMemberDefinition).
Allowed Attributes
- autoMemberInclusiveRegex
- autoMemberExclusiveRegex
- autoMemberTargetGroup
6.3.9.9. autoMemberScope
This attribute sets the subtree DN to search for entries. This is the search base.
| Parameter | Description |
|---|---|
| Entry DN | cn=Auto Membership Plugin,cn=plugins,cn=config |
| Valid Range | Any Directory Server subtree |
| Default Value | None |
| Single- or Multi-Valued | Single |
| Syntax | DirectoryString |
| Example | autoMemberScope: dc=example,dc=com |
6.3.9.10. autoMemberTargetGroup
This attribute sets which group to add the entry to as a member, if it meets the regular expression conditions.
| Parameter | Description |
|---|---|
| Entry DN | cn=Auto Membership Plugin,cn=plugins,cn=config |
| Valid Range | Any Directory Server group |
| Default Value | None |
| Single- or Multi-Valued | Single |
| Syntax | DirectoryString |
| Example | autoMemberTargetGroup: cn=webservers,cn=hostgroups,ou=groups,dc=example,dc=com |
6.3.10. Binary Syntax plug-in
Binary syntax is deprecated. Use Octet String syntax instead.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | bin-syntax |
| DN of Configuration Entry | cn=Binary Syntax,cn=plugins,cn=config |
| Description | Syntax for handling binary data. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
6.3.11. Bit String Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | bitstring-syntax |
| DN of Configuration Entry | cn=Bit String Syntax,cn=plugins,cn=config |
| Description | Supports bit string syntax values and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.12. Bitwise plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | bitwise |
| DN of Configuration Entry | cn=Bitwise Plugin,cn=plugins,cn=config |
| Description | Matching rule for performing bitwise operations against the LDAP server |
| Type | matchingrule |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
6.3.13. Boolean Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | boolean-syntax |
| DN of Configuration Entry | cn=Boolean Syntax,cn=plugins,cn=config |
| Description | Supports boolean syntax values (TRUE or FALSE) and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.14. Case Exact String Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | ces-syntax |
| DN of Configuration Entry | cn=Case Exact String Syntax,cn=plugins,cn=config |
| Description | Supports case-sensitive matching or Directory String, IA5 String, and related syntaxes. This is not a case-exact syntax; this plug-in provides case-sensitive matching rules for different string syntaxes. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
6.3.15. Case Ignore String Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | directorystring-syntax |
| DN of Configuration Entry | cn=Case Ignore String Syntax,cn=plugins,cn=config |
| Description | Supports case-insensitive matching rules for Directory String, IA5 String, and related syntaxes. This is not a case-insensitive syntax; this plug-in provides case-sensitive matching rules for different string syntaxes. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
6.3.16. Chaining Database plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | chaining database |
| DN of Configuration Entry | cn=Chaining database,cn=plugins,cn=config |
| Description | Enables back end databases to be linked |
| Type | database |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | There are many performance related tuning parameters involved with the chaining database. |
| Further Information | A chaining database is also known as a database link. |
6.3.17. Class of Service plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | cos |
| DN of Configuration Entry | cn=Class of Service,cn=plugins,cn=config |
| Description | Allows for sharing of attributes between entries |
| Type | object |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | * Type: Database * Named: State Change Plug-in * Named: Views Plug-in |
| Performance-Related Information | Do not modify the configuration of this plug-in. Leave this plug-in running at all times. |
6.3.18. Content Synchronization plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | content-sync-plugin |
| DN of Configuration Entry | cn=Content Synchronization,cn=plugins,cn=config |
| Description |
Enables support for the |
| Type | object |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | None |
| Dependencies | Retro Changelog plug-in |
| Performance-Related Information |
If you know which back end or subtree clients access to synchronize data, limit the scope of the |
6.3.19. Country String Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | countrystring-syntax |
| DN of Configuration Entry | cn=Country String Syntax,cn=plugins,cn=config |
| Description | Supports country naming syntax values and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.20. Delivery Method Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | delivery-syntax |
| DN of Configuration Entry | cn=Delivery Method Syntax,cn=plugins,cn=config |
| Description | Supports values that are lists of preferred deliver methods and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.21. deref plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | Dereference |
| DN of Configuration Entry | cn=deref,cn=plugins,cn=config |
| Description | For dereference controls in directory searches |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | Database |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
6.3.22. Distinguished Name Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | dn-syntax |
| DN of Configuration Entry | cn=Distinguished Name Syntax,cn=plugins,cn=config |
| Description | Supports DN value syntaxes and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.23. Distributed Numeric Assignment plug-in
The Distributed Numeric Assignment Plug-in manages ranges of numbers and assigns unique numbers within that range to entries. By breaking number assignments into ranges, the Distributed Numeric Assignment Plug-in allows multiple servers to assign numbers without conflict. The plug-in also manages the ranges assigned to servers, so that if one instance runs through its range quickly, it can request additional ranges from the other servers.
Distributed numeric assignment can be configured to work with single attribute types or multiple attribute types, and is only applied to specific suffixes and specific entries within the subtree.
Distributed numeric assignment is handled per-attribute and is only applied to specific suffixes and specific entries within the subtree.
| Plug-in Information | Description |
|---|---|
| Plug-in ID | Distributed Numeric Assignment |
| Configuration Entry DN | cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Description | Distributed Numeric Assignment plugin |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | |
| Dependencies | Database |
| Performance-Related Information | None |
6.3.23.1. dnaFilter
This attribute sets an LDAP filter to use to search for and identify the entries to which to apply the distributed numeric assignment range.
The dnaFilter attribute is required to set up distributed numeric assignment for an attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | Any valid LDAP filter |
| Default Value | None |
| Syntax | DirectoryString |
| Example | dnaFilter: (objectclass=person) |
6.3.23.2. dnaHostname
This attribute identifies the host name of a server in a shared range, as part of the DNA range configuration for that specific host in multi-supplier replication. Available ranges are tracked by host and the range information is replicated among all suppliers so that if any supplier runs low on available numbers, it can use the host information to contact another supplier and request an new range.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Syntax | DirectoryString |
| Valid Range | Any valid host name |
| Default Value | None |
| Example | dnahostname: ldap1.example.com |
6.3.23.3. dnaInterval
This attribute sets an interval to use to increment through numbers in a range. Essentially, this skips numbers at a predefined rate. If the interval is 3 and the first number in the range is 1, the next number used in the range is 4, then 7, then 10, incrementing by three for every new number assignment.
In a replication environment, the dnaInterval enables multiple servers to share the same range. However, when you configure different servers that share the same range, set the dnaInterval and dnaNextVal parameters accordingly so that the different servers do not generate the same values. You must also consider this if you add new servers to the replication topology.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | Any integer |
| Default Value | 1 |
| Syntax | Integer |
| Example | dnaInterval: 1 |
6.3.23.4. dnaMagicRegen
This attribute sets a user-defined value that instructs the plug-in to assign a new value for the entry. The magic value can be used to assign new unique numbers to existing entries or as a standard setting when adding new entries.
The magic entry should be outside of the defined range for the server so that it cannot be triggered by accident. Note that this attribute does not have to be a number when used on a DirectoryString or other character type. However, in most cases the DNA plug-in is used on attributes which only accept integer values, and in such cases the dnamagicregen value must also be an integer.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | Any string |
| Default Value | None |
| Syntax | DirectoryString |
| Example | dnaMagicRegen: -1 |
6.3.23.5. dnaMaxValue
This attribute sets the maximum value that can be assigned for the range. The default is -1, which is the same as setting the highest 64-bit integer.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | 1 to the maximum 32-bit integer on 32-bit systems and to the maximum 64-bit integer on 64-bit systems; -1 is unlimited |
| Default Value | -1 |
| Syntax | Integer |
| Example | dnaMaxValue: 1000 |
6.3.23.6. dnaNextRange
This attribute defines the next range to use when the current range is exhausted. This value is automatically set when range is transferred between servers, but it can also be manually set to add a range to a server if range requests are not used.
The dnaNextRange attribute should be set explicitly only if a separate, specific range has to be assigned to other servers. Any range set in the dnaNextRange attribute must be unique from the available range for the other servers to avoid duplication. If there is no request from the other servers and the server where dnaNextRange is set explicitly has reached its set dnaMaxValue, the next set of values (part of the dnaNextRange) is allocated from this deck.
The dnaNextRange allocation is also limited by the dnaThreshold attribute that is set in the DNA configuration. Any range allocated to another server for dnaNextRange cannot violate the threshold for the server, even if the range is available on the deck of dnaNextRange.
If the dnaNextRange attribute is handled internally if it is not set explicitly. When it is handled automatically, the dnaMaxValue attribute serves as upper limit for the next range.
The attribute sets the range in the format lower_range-upper_range.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | 1 to the maximum 32-bit integer on 32-bit systems and to the maximum 64-bit integer on 64-bit systems for the lower and upper ranges |
| Default Value | None |
| Syntax | DirectoryString |
| Example | dnaNextRange: 100-500 |
6.3.23.7. dnaNextValue
This attribute gives the next available number which can be assigned. After being initially set in the configuration entry, this attribute is managed by the Distributed Numeric Assignment Plug-in.
The dnaNextValue attribute is required to set up distributed numeric assignment for an attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | 1 to the maximum 32-bit integer on 32-bit systems and to the maximum 64-bit integer on 64-bit systems |
| Default Value | -1 |
| Syntax | Integer |
| Example | dnaNextValue: 1 |
6.3.23.8. dnaPluginConfig (object class)
This object class is used for entries which configure the DNA plug-in and numeric ranges to assign to entries.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.324
Allowed Attributes
- dnaType
- dnaPrefix
- dnaNextValue
- dnaMaxValue
- dnaInterval
- dnaMagicRegen
- dnaFilter
- dnaScope
- dnaSharedCfgDN
- dnaThreshold
- dnaNextRange
- dnaRangeRequestTimeout
- cn
6.3.23.9. dnaPortNum
This attribute gives the standard port number to use to connect to the host identified in dnaHostname.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Syntax | Integer |
| Valid Range | 0 to 65535 |
| Default Value | 389 |
| Example | dnaPortNum: 389 |
6.3.23.10. dnaPrefix
This attribute defines a prefix that can be prepended to the generated number values for the attribute. For example, to generate a user ID such as user1000, the dnaPrefix setting would be user.
dnaPrefix can hold any kind of string. However, some possible values for dnaType (such as uidNumber and gidNumber) require only integer values. To use a prefix string, consider using a custom attribute for dnaType which allows strings.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | Any string |
| Default Value | None |
| Example | dnaPrefix: id |
6.3.23.11. dnaRangeRequestTimeout
One potential situation with the Distributed Numeric Assignment Plug-in is that one server begins to run out of numbers to assign. The dnaThreshold attribute sets a threshold of available numbers in the range, so that the server can request an additional range from the other servers before it is unable to perform number assignments.
The dnaRangeRequestTimeout attribute sets a timeout period, in seconds, for range requests so that the server does not stall waiting on a new range from one server and can request a range from a new server.
For range requests to be performed, the dnaSharedCfgDN attribute must be set.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | 1 to the maximum 32-bit integer on 32-bit systems and to the maximum 64-bit integer on 64-bit systems |
| Default Value | 10 |
| Syntax | Integer |
| Example | dnaRangeRequestTimeout: 15 |
6.3.23.12. dnaRemainingValues
This attribute contains the number of values that are remaining and available to a server to assign to entries.
| Parameter | Description |
|---|---|
| Entry DN | dnaHostname=host_name+dnaPortNum=port_number,ou=ranges,dc=example,dc=com |
| Syntax | Integer |
| Valid Range | Any integer |
| Default Value | None |
| Example | dnaRemainingValues: 1000 |
6.3.23.13. dnaRemoteBindCred
Specifies the Replication Manager’s password. If you set a bind method in the dnaRemoteBindMethod attribute that requires authentication, additionally set the dnaRemoteBindDN and dnaRemoteBindCred parameter for every server in the replication deployment in the plug-in configuration entry under the cn=config entry.
Set the parameter in plain text. The value is automatically AES-encrypted before it is stored.
A server restart is required for the change to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Syntax | DirectoryString {AES} encrypted_password |
| Valid Values | Any valid AES-encrypted password. |
| Default Value | |
| Example | dnaRemoteBindCred: {AES-TUhNR0NTcUdTSWIzRFFFRkRUQm1NRVVHQ1NxR1NJYjNEUUVGRERBNEJDUmxObUk0WXpjM1l5MHdaVE5rTXpZNA0KTnkxaE9XSmhORGRoT0MwMk1ESmpNV014TUFBQ0FRSUNBU0F3Q2dZSUtvWklodmNOQWdjd0hRWUpZSVpJQVdVRA0KQkFFcUJCQk5KbUFDUWFOMHlITWdsUVp3QjBJOQ==}bBR3On6cBmw0DdhcRx826g== |
6.3.23.14. dnaRemoteBindDN
Specifies the Replication Manager DN. If you set a bind method in the dnaRemoteBindMethod attribute that requires authentication, additionally set the dnaRemoteBindDN and dnaRemoteBindCred parameter for every server in the replication deployment in the plug-in configuration under the cn=config entry.
A server restart is required for the change to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Syntax | DirectoryString |
| Valid Values | Any valid Replication Manager DN. |
| Default Value | |
| Example | dnaRemoteBindDN: cn=replication manager,cn=config |
6.3.23.15. dnaRemoteBindMethod
Specifies the remote bind method. If you set a bind method in this attribute that requires authentication, additionally set the dnaRemoteBindDN and dnaRemoteBindCred parameter for every server in the replication deployment in the plug-in configuration entry under the cn=config entry.
A server restart is required for the change to take effect.
| Parameter | Description |
|---|---|
| Entry DN | dnaHostname=host_name+dnaPortNum=port_number,ou=ranges,dc=example,dc=com |
| Syntax | DirectoryString |
| Valid Values |
|
| Default Value | |
| Example | dnaRemoteBindMethod: SIMPLE |
6.3.23.16. dnaRemoteConnProtocol
Specifies the remote connection protocol.
A server restart is required for the change to take effect.
| Parameter | Description |
|---|---|
| Entry DN | dnaHostname=host_name+dnaPortNum=port_number,ou=ranges,dc=example,dc=com |
| Syntax | DirectoryString |
| Valid Values |
|
| Default Value | |
| Example | dnaRemoteConnProtocol: LDAP |
6.3.23.17. dnaScope
This attribute sets the base DN to search for entries to which to apply the distributed numeric assignment. This is analogous to the base DN in an ldapsearch.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | Any Directory Server entry |
| Default Value | None |
| Syntax | DirectoryString |
| Example | dnaScope: ou=people,dc=example,dc=com |
6.3.23.18. dnaSecurePortNum
This attribute gives the secure (TLS) port number to use to connect to the host identified in dnaHostname.
| Parameter | Description |
|---|---|
| Entry DN | dnaHostname=host_name+dnaPortNum=port_number,ou=ranges,dc=example,dc=com |
| Syntax | Integer |
| Valid Range | 0 to 65535 |
| Default Value | 636 |
| Example | dnaSecurePortNum: 636 |
6.3.23.21. dnaThreshold
One potential situation with the Distributed Numeric Assignment Plug-in is that one server begins to run out of numbers to assign, which can cause problems. The Distributed Numeric Assignment Plug-in allows the server to request a new range from the available ranges on other servers.
So that the server can recognize when it is reaching the end of its assigned range, the dnaThreshold attribute sets a threshold of remaining available numbers in the range. When the server hits the threshold, it sends a request for a new range.
For range requests to be performed, the dnaSharedCfgDN attribute must be set.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | 1 to the maximum 32-bit integer on 32-bit systems and to the maximum 64-bit integer on 64-bit systems |
| Default Value | 100 |
| Syntax | Integer |
| Example | dnaThreshold: 100 |
6.3.23.22. dnaType
This attribute sets which attributes have unique numbers being generated for them. In this case, whenever the attribute is added to the entry with the magic number, an assigned value is automatically supplied.
This attribute is required to set a distributed numeric assignment for an attribute.
If the dnaPrefix attribute is set, then the prefix value is prepended to whatever value is generated by dnaType. The dnaPrefix value can be any kind of string, but some reasonable values for dnaType (such as uidNumber and gidNumber) require only integer values. To use a prefix string, consider using a custom attribute for dnaType which allows strings.
| Parameter | Description |
|---|---|
| Entry DN | cn=DNA_config_entry,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config |
| Valid Range | Any Directory Server attribute |
| Default Value | None |
| Example | dnaType: uidNumber |
6.3.24. Enhanced Guide Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | enhancedguide-syntax |
| DN of Configuration Entry | cn=Enhanced Guide Syntax,cn=plugins,cn=config |
| Description | Supports syntaxes and related matching rules for creating complex criteria, based on attributes and filters, to build searches; from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.25. Facsimile Telephone Number Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | facsimile-syntax |
| DN of Configuration Entry | cn=Facsimile Telephone Number Syntax,cn=plugins,cn=config |
| Description | Supports syntaxes and related matching rules for fax numbers; from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.26. Fax Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | fax-syntax |
| DN of Configuration Entry | cn=Fax Syntax,cn=plugins,cn=config |
| Description | Supports syntaxes and related matching rules for storing images of faxed objects; from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.27. Generalized Time Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | time-syntax |
| DN of Configuration Entry | cn=Generalized Time Syntax,cn=plugins,cn=config |
| Description | Supports syntaxes and related matching rules for dealing with dates, times and time zones; from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information | The Generalized Time String consists of a four digit year, two digit month (for example, 01 for January), two digit day, two digit hour, two digit minute, two digit second, an optional decimal part of a second, and a time zone indication. Red Hat strongly recommends using the Z time zone indication, which indicates Greenwich Mean Time. See also RFC 4517. |
6.3.28. Guide Syntax plug-in
This syntax is deprecated. Use Enhanced Guide syntax instead.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | guide-syntax |
| DN of Configuration Entry | cn=Guide Syntax,cn=plugins,cn=config |
| Description | Syntax for creating complex criteria, based on attributes and filters, to build searches |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information | This syntax is obsolete. The Enhanced Guide Syntax should be used instead. |
6.3.29. HTTP Client plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | http-client |
| DN of Configuration Entry | cn=HTTP Client,cn=plugins,cn=config |
| Description | HTTP client plug-in |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | Database |
| Performance-Related Information |
6.3.30. Integer Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | int-syntax |
| DN of Configuration Entry | cn=Integer Syntax,cn=plugins,cn=config |
| Description | Supports integer syntaxes and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.31. Internationalization plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | orderingrule |
| DN of Configuration Entry | cn=Internationalization Plugin,cn=plugins,cn=config |
| Description | Enables internationalized strings to be ordered in the directory |
| Type | matchingrule |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments |
The Internationalization Plug-in has one argument, which must not be modified, which specifies the location of the |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
6.3.32. JPEG Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | jpeg-syntax |
| DN of Configuration Entry | cn=JPEG Syntax,cn=plugins,cn=config |
| Description | Supports syntaxes and related matching rules for JPEG image data; from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.33. ldbm database plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | ldbm-backend |
| DN of Configuration Entry | cn=ldbm database,cn=plugins,cn=config |
| Description | Implements local databases |
| Type | database |
| Configurable Options | |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | * Syntax * matchingRule |
| Performance-Related Information | See Section 6.4, “Database plug-in attributes” for further information on database configuration. |
6.3.34. Linked Attributes plug-in
Many times, entries have inherent relationships to each other (such as managers and employees, document entries and their authors, or special groups and group members). While attributes exist that reflect these relationships, these attributes have to be added and updated on each entry manually. That can lead to a whimsically inconsistent set of directory data, where these entry relationships are unclear, outdated, or missing.
The Linked Attributes Plug-in allows one attribute, set in one entry, to update another attribute in another entry automatically. The first attribute has a DN value, which points to the entry to update; the second entry attribute also has a DN value which is a back-pointer to the first entry. The link attribute which is set by users and the dynamically-updated "managed" attribute in the affected entries are both defined by administrators in the Linked Attributes Plug-in instance.
Conceptually, this is similar to the way that the MemberOf Plug-in uses the member attribute in group entries to set memberOf attribute in user entries. Only with the Linked Attributes Plug-in, all of the link/managed attributes are user-defined and there can be multiple instances of the plug-in, each reflecting different link-managed relationships.
There are a couple of caveats for linking attributes:
- Both the link attribute and the managed attribute must have DNs as values. The DN in the link attribute points to the entry to add the managed attribute to. The managed attribute contains the linked entry DN as its value.
- The managed attribute must be multi-valued. Otherwise, if multiple link attributes point to the same managed entry, the managed attribute value would not be updated accurately.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | Linked Attributes |
| DN of Configuration Entry | cn=Linked Attributes,cn=plugins,cn=config |
| Description |
Container entry for linked-managed attribute configuration entries. Each configuration entry under the container links one attribute to another, so that when one entry is updated (such as a manager entry), then any entry associated with that entry (such as a custom |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | None for the main plug-in entry. Each plug-in instance has three possible attributes: * linkType, which sets the primary attribute for the plug-in to monitor * managedType, which sets the attribute which will be managed dynamically by the plug-in whenever the attribute in linkType is modified * linkScope, which restricts the plug-in activity to a specific subtree within the directory tree |
| Dependencies | Database |
| Performance-Related Information | Any attribute set in linkType must only allow values in a DN format. Any attribute set in managedType must be multi-valued. |
6.3.34.1. linkScope
This restricts the scope of the plug-in, so it operates only in a specific subtree or suffix. If no scope is given, then the plug-in will update any part of the directory tree.
| Parameter | Description |
|---|---|
| Entry DN | cn=plugin_instance,cn=Linked Attributes,cn=plugins,cn=config |
| Valid Range | Any DN |
| Default Value | None |
| Syntax | DN |
| Example | linkScope: ou=People,dc=example,dc=com |
6.3.34.2. linkType
This sets the user-managed attribute. This attribute is modified and maintained by users, and then when this attribute value changes, the linked attribute is automatically updated in the targeted entries.
| Parameter | Description |
|---|---|
| Entry DN | cn=plugin_instance,cn=Linked Attributes,cn=plugins,cn=config |
| Valid Range | Any Directory Server attribute |
| Default Value | None |
| Syntax | DirectoryString |
| Example | linkType: directReport |
6.3.34.3. managedType
This sets the managed, or plug-in maintained, attribute. This attribute is managed dynamically by the Linked Attributes Plug-in instance. Whenever a change is made to the managed attribute, then the plug-in updates all of the linked attributes on the targeted entries.
| Parameter | Description |
|---|---|
| Entry DN | cn=plugin_instance,cn=Linked Attributes,cn=plugins,cn=config |
| Valid Range | Any Directory Server attribute |
| Default Value | None |
| Syntax | DN |
| Example | managedType: manager |
6.3.35. Managed Entries plug-in
In some unique circumstances, it is useful to have an entry created automatically when another entry is created. For example, this can be part of Posix integration by creating a specific group entry when a new user is created. Each instance of the Managed Entries Plug-in identifies two areas:
- The scope of the plug-in, meaning the subtree and the search filter to use to identify entries which require a corresponding managed entry
- A template entry that defines what the managed entry should look like
| Plug-in Information | Description |
|---|---|
| Plug-in ID | Managed Entries |
| Configuration Entry DN | cn=Managed Entries,cn=plugins,cn=config |
| Description | Container entry for automatically generated directory entries. Each configuration entry defines a target subtree and a template entry. When a matching entry in the target subtree is created, then the plug-in automatically creates a new, related entry based on the template. |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | None for the main plug-in entry. Each plug-in instance has four possible attributes: * originScope, which sets the search base * originFilter, which sets the search base for matching entries * managedScope, which sets the subtree under which to create new managed entries * managedTemplate, which is the template entry used to create the managed entries |
| Dependencies | Database |
| Performance-Related Information | None |
6.3.35.1. managedBase
This attribute sets the subtree under which to create the managed entries. This can be any entry in the directory tree.
| Parameter | Description |
|---|---|
| Entry DN | cn=instance_name,cn=Managed Entries Plugin,cn=plugins,cn=config |
| Valid Values | Any Directory Server subtree |
| Default Value | None |
| Syntax | DirectoryString |
| Example | managedBase: ou=groups,dc=example,dc=com |
6.3.35.2. managedTemplate
This attribute identifies the template entry to use to create the managed entry. This entry can be located anywhere in the directory tree; however, it is recommended that this entry is in a replicated suffix so that all suppliers and consumers in replication are using the same template.
The attributes used to create the managed entry template are described in the Red Hat Directory Server Configuration, Command, and File Reference.
| Parameter | Description |
|---|---|
| Entry DN | cn=instance_name,cn=Managed Entries Plugin,cn=plugins,cn=config |
| Valid Values |
Any Directory Server entry of the |
| Default Value | None |
| Syntax | DirectoryString |
| Example | managedTemplate: cn=My Template,ou=Templates,dc=example,dc=com |
6.3.35.3. originFilter
This attribute sets the search filter to use to search for and identify the entries within the subtree which require a managed entry. The filter allows the managed entries behavior to be limited to a specific type of entry or subset of entries. The syntax is the same as a regular search filter.
| Parameter | Description |
|---|---|
| Entry DN | cn=instance_name,cn=Managed Entries Plugin,cn=plugins,cn=config |
| Valid Values | Any valid LDAP filter |
| Default Value | None |
| Syntax | DirectoryString |
| Example | originFilter: objectclass=posixAccount |
6.3.35.4. originScope
This attribute sets the scope of the search to use to see which entries the plug-in monitors. If a new entry is created within the scope subtree, then the Managed Entries Plug-in creates a new managed entry that corresponds to it.
| Parameter | Description |
|---|---|
| Entry DN | cn=instance_name,cn=Managed Entries Plugin,cn=plugins,cn=config |
| Valid Values | Any Directory Server subtree |
| Default Value | None |
| Syntax | DirectoryString |
| Example | originScope: ou=people,dc=example,dc=com |
6.3.36. MemberOf plug-in
Group membership is defined within group entries using attributes such as member. Searching for the member attribute makes it easy to list all of the members for the group. However, group membership is not reflected in the member’s user entry, so it is impossible to tell to what groups a person belongs by looking at the user’s entry.
The MemberOf Plug-in synchronizes the group membership in group members with the members' individual directory entries by identifying changes to a specific member attribute (such as member) in the group entry and then working back to write the membership changes over to a specific attribute in the members' user entries.
| Plug-in Information | Description |
|---|---|
| Plug-in ID | memberOf |
| Configuration Entry DN | cn=MemberOf Plugin,cn=plugins,cn=config |
| Description |
Manages the |
| Type | postoperation |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments |
*
* |
| Dependencies | Database |
| Performance-Related Information | None |
6.3.36.1. cn
Sets the name of the plug-in instance.
| Parameter | Description |
|---|---|
| Entry DN | cn=MemberOf Plugin,cn=plugins,cn=config |
| Valid Values | Any valid string |
| Default Value | |
| Syntax | DirectoryString |
| Example | cn: Example MemberOf Plugin Instance |
6.3.36.2. memberOfAllBackends
This attribute specifies whether to search the local suffix for user entries or all available suffixes. This can be desirable in directory trees where users may be distributed across multiple databases so that group membership is evaluated comprehensively and consistently.
| Parameter | Description |
|---|---|
| Entry DN | cn=MemberOf Plugin,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | memberOfAllBackends: on |
6.3.36.3. memberOfAttr
This attribute specifies the attribute in the user entry for Directory Server to manage to reflect group membership. The MemberOf Plug-in generates the value of the attribute specified here in the directory entry for the member. There is a separate attribute for every group to which the user belongs.
| Parameter | Description |
|---|---|
| Entry DN | cn=MemberOf Plugin,cn=plugins,cn=config |
| Valid Range | Any Directory Server attribute that supports DN syntax |
| Default Value | memberOf |
| Syntax | DirectoryString |
| Example | memberOfAttr: memberOf |
6.3.36.4. memberOfAutoAddOC
To enable the memberOf plug-in to add the memberOf attribute to a user, the user object must contain an object class that allows this attribute. If an entry does not have an object class that allows the memberOf attribute then the memberOf plugin will automatically add the object class listed in the memberOfAutoAddOC parameter.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=MemberOf Plugin,cn=plugins,cn=config |
| Valid Values | Any Directory Server object class |
| Default Value | nsMemberOf |
| Syntax | DirectoryString |
| Example | memberOfAutoAddOC: nsMemberOf |
6.3.36.5. memberOfDeferredUpdate
On instances with Berkeley Database (BDB), if a change to a static group impacts many members, such as adding more than 10,000 members to the group, this change triggers a large number of internal updates of all group members. Directory Server processes all updates in one transaction that can hold sensitive database pages and block other searches waiting for the update completion.
Set the memberOfDeferredUpdate attribute to on to defer the update of the members. In this case, Directory Server performs the members update in a separate transaction improving server responsiveness.
| Parameter | Description |
|---|---|
| Entry DN | cn=MemberOf Plugin,cn=plugins,cn=config |
| Valid range | on | off |
| Default value | off |
| Syntax | DirectoryString |
| Example | memberOfDeferredUpdate: off |
6.3.36.6. memberOfEntryScope
If you configured several back ends or multiple-nested suffixes, the multi-valued memberOfEntryScope parameter enables you to set what suffixes the MemberOf plug-in works on. If the parameter is not set, the plug-in works on all suffixes. The value set in the memberOfEntryScopeExcludeSubtree parameter has a higher priority than values set in memberOfEntryScope.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=MemberOf Plugin,cn=plugins,cn=config |
| Valid Range | Any Directory Server entry DN. |
| Default Value | |
| Syntax | DirectoryString |
| Example | memberOfEntryScope: ou=people,dc=example,dc=com |
6.3.36.7. memberOfEntryScopeExcludeSubtree
If you configured several back ends or multiple-nested suffixes, the multi-valued memberOfEntryScopeExcludeSubtree parameter enables you to set what suffixes the MemberOf plug-in excludes. The value set in the memberOfEntryScopeExcludeSubtree parameter has a higher priority than values set in memberOfEntryScope. If the scopes set in both parameters overlap, the MemberOf plug-in only works on the non-overlapping directory entries.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=MemberOf Plugin,cn=plugins,cn=config |
| Valid Range | Any Directory Server entry DN. |
| Default Value | |
| Syntax | DirectoryString |
| Example | memberOfEntryScopeExcludeSubtree: ou=sample,dc=example,dc=com |
6.3.36.8. memberOfGroupAttr
This attribute specifies the attribute in the group entry to use to identify the DNs of group members. By default, this is the member attribute, but it can be any membership-related attribute that contains a DN value, such as uniquemember or member.
Any attribute can be used for the memberOfGroupAttr value, but the MemberOf Plug-in only works if the value of the target attribute contains the DN of the member entry. For example, the member attribute contains the DN of the member’s user entry:
member: uid=jsmith,ou=People,dc=example,dc=com
member: uid=jsmith,ou=People,dc=example,dc=com
Some member-related attributes do not contain a DN, like the memberURL attribute. That attribute will not work as a value for memberOfGroupAttr. The memberURL value is a URL, and a non-DN value cannot work with the MemberOf Plug-in.
| Parameter | Description |
|---|---|
| Entry DN | cn=MemberOf Plugin,cn=plugins,cn=config |
| Valid Range | Any Directory Server attribute |
| Default Value | member |
| Syntax | DirectoryString |
| Example | memberOfGroupAttr: member |
6.3.36.9. memberOfSkipNested
If you do not use nested groups in the directory, set the memberOfSkipNested attribute to on to skip the nested group check. It significantly improves response time of update operations when Directory Server needs to compute membership in more that 10000 entries.
You do not need to restart the server to apply changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=MemberOf Plugin,cn=plugins,cn=config |
| Valid range | on | off |
| Default value | off |
| Syntax | DirectoryString |
| Example | memberOfSkipNested: off |
6.3.37. Multi-supplier Replication plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | replication-multisupplier |
| DN of Configuration Entry | cn=Multisupplier Replication Plugin,cn=plugins,cn=config |
| Description | Enables replication between two current Directory Server |
| Type | object |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | * Named: ldbm database * Named: DES * Named: Class of Service |
| Performance-Related Information | |
| Further Information | Turn this plug-in off if one server will never replicate. |
6.3.38. Name and Optional UID Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | nameoptuid-syntax |
| DN of Configuration Entry | cn=Name And Optional UID Syntax,cn=plugins,cn=config |
| Description | Supports syntaxes and related matching rules to store and search for a DN with an optional unique ID; from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information | The optional UID is used to distinguish between entries which may have identical DNs or naming attributes. See also RFC 4517. |
6.3.39. Numeric String Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | numstr-syntax |
| DN of Configuration Entry | cn=Numeric String Syntax,cn=plugins,cn=config |
| Description | Supports syntaxes and related matching rules for strings of numbers and spaces; from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.40. Octet String Syntax plug-in
Use the Octet String syntax instead of Binary, which is deprecated.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | octetstring-syntax |
| DN of Configuration Entry | cn=Octet String Syntax,cn=plugins,cn=config |
| Description | Supports octet string syntaxes and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.41. OID Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | oid-syntax |
| DN of Configuration Entry | cn=OID Syntax,cn=plugins,cn=config |
| Description | Supports object identifier (OID) syntaxes and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.42. PAM Pass Through Auth plug-in
Local PAM configurations on Unix systems can leverage an external authentication store for LDAP users. This is a form of pass-through authentication which allows Directory Server to use the externally-stored user credentials for directory access.
PAM pass-through authentication is configured in child entries beneath the PAM Pass Through Auth Plug-in container entry. All of the possible configuration attributes for PAM authentication (defined in the 60pam-plugin.ldif schema file) are available to a child entry; the child entry must be an instance of the PAM configuration object class.
Example 6.4. Example PAM Pass Through Auth Configuration Entries
The PAM configuration, at a minimum, must define a mapping method (a way to identify what the PAM user ID is from the Directory Server entry), the PAM server to use, and whether to use a secure connection to the service.
pamIDMapMethod: RDN pamSecure: FALSE pamService: ldapserver
pamIDMapMethod: RDN
pamSecure: FALSE
pamService: ldapserverThe configuration can be expanded for special settings, such as to exclude or specifically include subtrees or to map a specific attribute value to the PAM user ID.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | pam_passthruauth |
| DN of Configuration Entry | cn=PAM Pass Through Auth,cn=plugins,cn=config |
| Description | Enables pass-through authentication for PAM, meaning that a PAM service can use the Directory Server as its user authentication store. |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | Database |
| Performance-Related Information |
6.3.42.1. pamConfig (object class)
This object class is used to define the PAM configuration to interact with the directory service. This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.318
Allowed Attributes
-
pamExcludeSuffix -
pamIncludeSuffix -
pamMissingSuffix -
pamFilter -
pamIDAttr -
pamIDMapMethod -
pamFallback -
pamSecure -
pamService -
nsslapd-pluginConfigArea
6.3.42.2. pamExcludeSuffix
This attribute specifies a suffix to exclude from PAM authentication.
| OID | 2.16.840.1.113730.3.1.2068 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
6.3.42.3. pamFallback
Sets whether to fallback to regular LDAP authentication if PAM authentication fails.
| OID | 2.16.840.1.113730.3.1.2072 |
| Syntax | Boolean |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
6.3.42.4. pamFilter
Sets an LDAP filter to use to identify specific entries within the included suffixes for which to use PAM pass-through authentication. If not set, all entries within the suffix are targeted by the configuration entry.
| OID | 2.16.840.1.113730.3.1.2131 |
| Syntax | Boolean |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
6.3.42.5. pamIDAttr
This attribute contains the attribute name which is used to hold the PAM user ID.
| OID | 2.16.840.1.113730.3.1.2071 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
6.3.42.6. pamIDMapMethod
Gives the method to use to map the LDAP bind DN to a PAM identity.
Directory Server user account inactivation is only validated using the ENTRY mapping method. With RDN or DN, a Directory Server user whose account is inactivated can still bind to the server successfully.
| OID | 2.16.840.1.113730.3.1.2070 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
6.3.42.7. pamIncludeSuffix
This attribute sets a suffix to include for PAM authentication.
| OID | 2.16.840.1.113730.3.1.2067 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
6.3.42.8. pamMissingSuffix
Identifies how to handle missing include or exclude suffixes. The options are ERROR (which causes the bind operation to fail); ALLOW, which logs an error but allows the operation to proceed; and IGNORE, which allows the operation and does not log any errors.
| OID | 2.16.840.1.113730.3.1.2069 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
6.3.42.9. pamModuleIsThreadSafe
By default, Directory Server serializes the Pluggable Authentication Module (PAM) authentications. If you set the pamModuleIsThreadSafe attribute to on, Directory Server starts to perform PAM authentications in parallel. However, ensure that the PAM module you are using is a thread-safe module.
Currently, you can use the ldapmodify utility to configure the pamModuleIsThreadSafe attribute:
ldapmodify -D "cn=Directory Manager" -W -H ldap://server.example.com -x dn: cn=Example PAM config entry,cn=PAM Pass Through Auth,cn=plugins,cn=config changetype: modify add: pamModuleIsThreadSafe pamModuleIsThreadSafe: on
# ldapmodify -D "cn=Directory Manager" -W -H ldap://server.example.com -x
dn: cn=Example PAM config entry,cn=PAM Pass Through Auth,cn=plugins,cn=config
changetype: modify
add: pamModuleIsThreadSafe
pamModuleIsThreadSafe: onTo apply changes, restart the server.
| OID | 2.16.840.1.113730.3.1.2399 |
| Syntax | Boolean |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
6.3.42.10. pamSecure
Requires secure TLS connection for PAM authentication.
| OID | 2.16.840.1.113730.3.1.2073 |
| Syntax | Boolean |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
6.3.42.11. pamService
Contains the service name to pass to PAM. This assumes that the service specified has a configuration file in the /etc/pam.d/ directory.
The pam_fprintd.so module cannot be in the configuration file referenced by the pamService attribute of the PAM Pass-Through Authentication Plug-in configuration. Using the PAM pam_fprintd.so module causes Directory Server to hit the max file descriptor limit and can cause Directory Server process to abort.
The pam_fprintd.so module cannot be in the configuration file referenced by the pamService attribute of the PAM Pass-Through Authentication Plug-in configuration. Using the PAM fprintd module causes Directory Server to hit the max file descriptor limit and can cause the Directory Server process to abort.
| OID | 2.16.840.1.113730.3.1.2074 |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
6.3.43. Pass Through Authentication plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | passthruauth |
| DN of Configuration Entry | cn=Pass Through Authentication,cn=plugins,cn=config |
| Description | Enables pass-through authentication, the mechanism which allows one directory to consult another to authenticate bind requests. |
| Type | preoperation |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | ldap://example.com:389/o=example |
| Dependencies | Database |
| Performance-Related Information | Pass-through authentication slows down bind requests a little because they have to make an extra hop to the remote server. |
6.3.44. Password Storage Schemes
Directory Server implements the password storage schemes as plug-ins. However, the cn=Password Storage Schemes,cn=plugins,cn=config entry itself is just a container, not a plug-in entry. All password storage scheme plug-ins are stored as a subentry of this container.
To display all password storage schemes plug-ins, enter:
dsconf <instance_name> pwpolicy list-schemes
# dsconf <instance_name> pwpolicy list-schemesDo not disable the password scheme plug-ins or change the configurations of the plug-ins to prevent unpredictable authentication behavior.
Strong Password Storage Schemes
Use only the following strong password storage schemes (strongest first):
-
PBKDF2-SHA512(default). ThePBKDF2-SHA512is more secure thanPBKDF2_SHA256.
The password-based key derivation function 2 (PBKDF2) is designed to expend resources to counter brute force attacks. PBKDF2 supports a variable number of iterations to apply the hashing algorithm. Higher iterations improve security but require more hardware resources. To apply the PBKDF2-SHA512 algorithm, Directory Server uses 10,000 iterations.
The network security service (NSS) database in Red Hat Enterprise Linux 6 does not support PBKDF2. Therefore you cannot use this password scheme in a replication topology with Directory Server 9.
-
SSHA512
The salted secure hashing algorithm (SSHA) implements an enhanced version of the secure hashing algorithm (SHA), that uses a randomly generated salt to increase the security of the hashed password. SSHA512 implements the hashing algorithm using 512 bits.
Weak Password Storage Schemes
Besides the recommended strong password storage schemes, Directory Server supports the following weak schemes for backward compatibility:
-
AES -
CLEAR -
CRYPT -
CRYPT-MD5 -
CRYPT-SHA256,CRYPT-SHA512 -
GOST_YESCRYPT -
MD5 -
NS-MTA-MD5. Directory Server only supports authentication using this scheme. You can no longer use it to encrypt passwords. -
SHA(160 bit),SHA256,SHA384,SHA512 -
SMD5 -
SSHA,SSHA256,SSHA384
Only continue using a weak scheme over a short time frame, as it increases security risks.
6.3.45. Posix Winsync API plug-in
By default, Posix-related attributes are not synchronized between Active Directory and Red Hat Directory Server. On Linux systems, system users and groups are identified as Posix entries, and LDAP Posix attributes contain that required information. However, when Windows users are synced over, they have ntUser and ntGroup attributes automatically added which identify them as Windows accounts, but no Posix attributes are synced over (even if they exist on the Active Directory entry) and no Posix attributes are added on the Directory Server side.
The Posix Winsync API Plug-in synchronizes POSIX attributes between Active Directory and Directory Server entries.
All POSIX attributes (such as uidNumber, gidNumber, and homeDirectory) are synchronized between Active Directory and Directory Server entries. However, if a new POSIX entry or POSIX attributes are added to an existing entry in Directory Server, only the POSIX attributes are synchronized over to the Active Directory corresponding entry. The POSIX object class (posixAccount for users and posixGroup for groups) is not added to the Active Directory entry.
This plug-in is disabled by default and must be enabled before any Posix attributes will be synchronized from the Active Directory entry to the Directory Server entry.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | posix-winsync-plugin |
| DN of Configuration Entry | cn=Posix Winsync API,cn=plugins,cn=config |
| Description | Enables and configures Windows synchronization for Posix attributes set on Active Directory user and group entries. |
| Type | preoperation |
| Configurable Arguments | * on | off * memberUID mapping (groups) * converting and sorting memberUID values in lower case (groups) * memberOf fix-up tasks with sync operations * use Windows 2003 Posix schema |
| Default Setting | off |
| Configurable Arguments | None |
| Dependencies | database |
6.3.45.1. posixWinsyncCreateMemberOfTask
This attribute sets whether to run the memberOf fix-up task immediately after a sync run in order to update group memberships for synced users. This is disabled by default because the memberOf fix-up task can be resource-intensive and cause performance issues if it is run too frequently.
| Parameter | Description |
|---|---|
| Entry DN | cn=Posix Winsync API Plugin,cn=plugins,cn=config |
| Valid Range | true | false |
| Default Value | false |
| Example | posixWinsyncCreateMemberOfTask: false |
6.3.45.2. posixWinsyncLowerCaseUID
This attribute sets whether to store (and, if necessary, convert) the UID value in the memberUID attribute in lower case.
| Parameter | Description |
|---|---|
| Entry DN | cn=Posix Winsync API Plugin,cn=plugins,cn=config |
| Valid Range | true | false |
| Default Value | false |
| Example | posixWinsyncLowerCaseUID: false |
6.3.45.3. posixWinsyncMapMemberUID
This attribute sets whether to map the memberUID attribute in an Active Directory group to the uniqueMember attribute in a Directory Server group.
| Parameter | Description |
|---|---|
| Entry DN | cn=Posix Winsync API Plugin,cn=plugins,cn=config |
| Valid Range | true | false |
| Default Value | true |
| Example | posixWinsyncMapMemberUID: false |
6.3.45.4. posixWinsyncMapNestedGrouping
The posixWinsyncMapNestedGrouping parameter manages if nested groups are updated when memberUID attributes in an Active Directory POSIX group change. Updating nested groups is supported up a depth of five levels.
| Parameter | Description |
|---|---|
| Entry DN | cn=Posix Winsync API Plugin,cn=plugins,cn=config |
| Valid Range | true | false |
| Default Value | false |
| Example | posixWinsyncMapNestedGrouping: false |
6.3.45.5. posixWinsyncMsSFUSchema
This attribute sets whether to the older Microsoft System Services for Unix 3.0 (msSFU30) schema when syncing Posix attributes from Active Directory. By default, the Posix Winsync API Plug-in uses Posix schema for modern Active Directory servers: 2005, 2008, and later versions. There are slight differences between the modern Active Directory Posix schema and the Posix schema used by Windows Server 2003 and older Windows servers. If an Active Directory domain is using the older-style schema, then the older-style schema can be used instead.
| Parameter | Description |
|---|---|
| Entry DN | cn=Posix Winsync API Plugin,cn=plugins,cn=config |
| Valid Range | true | false |
| Default Value | false |
| Example | posixWinsyncMsSFUSchema: true |
6.3.46. Postal Address String Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | postaladdress-syntax |
| DN of Configuration Entry | cn=Postal Address Syntax,cn=plugins,cn=config |
| Description | Supports postal address syntaxes and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.47. Printable String Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | printablestring-syntax |
| DN of Configuration Entry | cn=Printable String Syntax,cn=plugins,cn=config |
| Description | Supports syntaxes and matching rules for alphanumeric and select punctuation strings (for strings which conform to printable strings as defined in RFC 4517). |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.48. Referential Integrity plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | referint |
| DN of Configuration Entry | cn=Referential Integrity Postoperation,cn=plugins,cn=config |
| Description | Enables the server to ensure referential integrity |
| Type | postoperation |
| Configurable Options | All configuration and on | off |
| Default Setting | off |
| Configurable Arguments |
When enabled, the post-operation Referential Integrity plug-in performs integrity updates on the |
| Dependencies | Database |
| Performance-Related Information | The Referential Integrity plug-in should be enabled on all suppliers in multi-supplier replication environment. When enabling the plug-in on chained servers, be sure to analyze the performance resource and time needs as well as integrity needs; integrity checks can be time consuming and demanding on memory and CPU. All attributes specified must be indexed for both presence and equality. |
6.3.49. Retro Changelog plug-in
Two different types of changelogs are maintained by Directory Server. The first type, referred to as simply a changelog, is used by multi-supplier replication, and the second changelog, a plug-in referred to as the retro changelog, is intended for use by LDAP clients for maintaining application compatibility with Directory Server 4.x versions.
This Retro Changelog Plug-in is used to record modifications made to a supplier server. When the supplier server’s directory is modified, an entry is written to the Retro Changelog that contains both of the following:
- A number that uniquely identifies the modification. This number is sequential with respect to other entries in the changelog.
- The modification action; that is, exactly how the directory was modified.
It is through the Retro Changelog Plug-in that the changes performed to Directory Server are accessed using searches to cn=changelog suffix.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | retrocl |
| DN of Configuration Entry | cn=Retro Changelog Plugin,cn=plugins,cn=config |
| Description |
Used by LDAP clients for maintaining application compatibility with Directory Server 4.x versions. Maintains a log of all changes occurring in Directory Server. The retro changelog offers the same functionality as the changelog in the 4.x versions of Directory Server. This plug-in exposes the |
| Type | object |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | See Section 6.3.49, “Retro Changelog plug-in” for further information on the configuration attributes for this plug-in. |
| Dependencies | * Type: Database * Named: Class of Service |
| Performance-Related Information | May slow down Directory Server update performance. |
6.3.49.1. isReplicated
This optional attribute sets a flag to indicate on a change in the changelog whether the change is newly made on that server or whether it was replicated over from another server.
| Parameter | Description |
|---|---|
| OID | 2.16.840.1.113730.3.1.2085 |
| Entry DN | cn=Retro Changelog Plugin,cn=plugins,cn=config |
| Valid Values | true | false |
| Default Value | None |
| Syntax | Boolean |
| Example | isReplicated: true |
6.3.49.2. nsslapd-attribute
This attribute explicitly specifies another Directory Server attribute which must be included in the retro changelog entries.
Many operational attributes and other types of attributes are commonly excluded from the retro changelog, but these attributes may need to be present for a third-party application to use the changelog data. This is done by listing the attribute in the retro changelog plug-in configuration using the nsslapd-attribute parameter.
It is also possible to specify an optional alias for the specified attribute within the nsslapd-attribute value.
nsslapd-attribute: attribute:pass:attributes[{blank}]alias
nsslapd-attribute: attribute:pass:attributes[{blank}]aliasUsing an alias for the attribute can help avoid conflicts with other attributes in an external server or application which may use the retro changelog records.
Setting the value of the nsslapd-attribute attribute to isReplicated is a way of indicating, in the retro changelog entry itself, whether the modification was done on the local server (that is, whether the change is an original change) or whether the change was replicated over to the server.
| Parameter | Description |
|---|---|
| Entry DN | cn=Retro Changelog Plugin,cn=plugins,cn=config |
| Valid Values | Any valid directory attribute (standard or custom) |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-attribute: nsUniqueId: uniqueID |
6.3.49.3. nsslapd-changelogdir
This attribute specifies the name of the directory in which the changelog database is created the first time the plug-in is run. By default, the database is stored with all the other databases under /var/lib/dirsrv/slapd-instance/changelogdb.
For performance reasons, store this database on a different physical disk.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=Retro Changelog Plugin,cn=plugins,cn=config |
| Valid Values | Any valid path to the directory |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-changelogdir: /var/lib/dirsrv/slapd-instance/changelogdb |
6.3.49.4. nsslapd-changelogmaxage
The nsslapd-changelogmaxage attribute sets the maximum age of any entry in the changelog. The changelog contains records of each directory modification and is used when synchronizing consumer servers. Each record contains a timestamp. Any record with a timestamp that is older than the value specified in this attribute is removed. By default, Directory Server removes records that are older than seven days. If you set this attribute to 0, there is no age limit on changelog records, and Directory Server keeps all records.
The size of the retro changelog is automatically reduced when you set a lower value.
Expired changelog records will not be removed if there is an agreement that has fallen behind further than the maximum age.
| Parameter | Description |
|---|---|
| Entry DN | cn=Retro Changelog Plugin,cn=plugins,cn=config |
| Valid Range | 0 (meaning that entries are not removed according to their age) to the maximum 32 bit integer value (2147483647) |
| Default Value | 7d |
| Syntax | DirectoryString IntegerAgeID, where AgeID is:
If you set only the integer value without the AgeID then Directory Server takes it as seconds. |
| Example | nsslapd-changelogmaxage: 30d |
6.3.49.5. nsslapd-exclude-attrs
The nsslapd-exclude-attrs parameter stores an attribute name to exclude from the retro changelog database. To exclude multiple attributes, add one nsslapd-exclude-attrs parameter for each attribute to exclude.
| Parameter | Description |
|---|---|
| Entry DN | cn=Retro Changelog Plugin,cn=plugins,cn=config |
| Valid Values | Any valid attribute name |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-exclude-attrs: example |
6.3.49.6. nsslapd-exclude-suffix
The nsslapd-exclude-suffix parameter stores a suffix to exclude from the retro changelog database. You can add the parameter multiple times to exclude multiple suffixes.
| Parameter | Description |
|---|---|
| Entry DN | cn=Retro Changelog Plugin,cn=plugins,cn=config |
| Valid Values | Any valid attribute name |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-exclude-suffix: ou=demo,dc=example,dc=com |
6.3.50. Roles plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | roles |
| DN of Configuration Entry | cn=Roles Plugin,cn=plugins,cn=config |
| Description | Enables the use of roles in Directory Server |
| Type | object |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | * Type: Database * Named: State Change Plug-in * Named: Views Plug-in |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
6.3.51. RootDN Access Control plug-in
The root DN, cn=Directory Manager, is a special user entry that is defined outside the normal user database. Normal access control rules are not applied to the root DN, but because of the powerful nature of the root user, it can be beneficial to apply some kind of access control rules to the root user.
The RootDN Access Control Plug-in sets normal access controls — host and IP address restrictions, time-of-day restrictions, and day of week restrictions — on the root user.
This plug-in is disabled by default.
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | rootdn-access-control |
| DN of Configuration Entry | cn=RootDN Access Control,cn=plugins,cn=config |
| Description | Enables and configures access controls to use for the root DN entry. |
| Type | internalpreoperation |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Attributes | * rootdn-open-time and rootdn-close-time for time-based access controls * rootdn-days-allowed for day-based access controls * rootdn-allow-host, rootdn-deny-host, rootdn-allow-ip, and rootdn-deny-ip for host-based access controls |
| Dependencies | None |
6.3.51.1. rootdn-allow-host
This sets what hosts, by fully-qualified domain name, the root user is allowed to use to access Directory Server. Any hosts not listed are implicitly denied.
Wild cards are allowed.
This attribute can be used multiple times to specify multiple hosts, domains, or subdomains.
| Parameter | Description |
|---|---|
| Entry DN | cn=RootDN Access Control Plugin,cn=plugins,cn=config |
| Valid Range | Any valid host name or domain, including asterisks (*) for wildcards |
| Default Value | None |
| Syntax | DirectoryString |
| Example | rootdn-allow-host: *.example.com |
6.3.51.2. rootdn-allow-ip
This sets what IP addresses, either IPv4 or IPv6, for machines the root user is allowed to use to access Directory Server. Any IP addresses not listed are implicitly denied.
Wild cards are allowed.
This attribute can be used multiple times to specify multiple addresses, domains, or subnets.
| Parameter | Description |
|---|---|
| Entry DN | cn=RootDN Access Control Plugin,cn=plugins,cn=config |
| Valid Range | Any valid IPv4 or IPv6 address, including asterisks (*) for wildcards |
| Default Value | None |
| Syntax | DirectoryString |
| Example | rootdn-allow-ip: 192.168.. |
6.3.51.3. rootdn-close-time
This sets part of a time period or range when the root user is allowed to access Directory Server. This sets when the time-based access ends, when the root user is no longer allowed to access Directory Server.
This is used in conjunction with the rootdn-open-time attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=RootDN Access Control Plugin,cn=plugins,cn=config |
| Valid Range | Any valid time, in a 24-hour format |
| Default Value | None |
| Syntax | Integer |
| Example | rootdn-close-time: 1700 |
6.3.51.4. rootdn-days-allowed
This gives a comma-separated list of what days the root user is allowed to use to access Directory Server. Any days listed are implicitly denied. This can be used with rootdn-close-time and rootdn-open-time to combine time-based access and days-of-week or it can be used by itself (with all hours allowed on allowed days).
| Parameter | Description |
|---|---|
| Entry DN | cn=RootDN Access Control Plugin,cn=plugins,cn=config |
| Valid Values | * Sun * Mon * Tue * Wed * Thu * Fri * Sat |
| Default Value | None |
| Syntax | DirectoryString |
| Example | rootdn-days-allowed: Mon, Tue, Wed, Thu, Fri |
6.3.51.5. rootdn-deny-ip
This sets what IP addresses, either IPv4 or IPv6, for machines the root user is not allowed to use to access Directory Server. Any IP addresses not listed are implicitly allowed.
Deny rules supercede allow rules, so if an IP address is listed in both the rootdn-allow-ip and rootdn-deny-ip attributes, it is denied access.
Wild cards are allowed.
This attribute can be used multiple times to specify multiple addresses, domains, or subnets.
| Parameter | Description |
|---|---|
| Entry DN | cn=RootDN Access Control Plugin,cn=plugins,cn=config |
| Valid Range | Any valid IPv4 or IPv6 address, including asterisks (*) for wildcards |
| Default Value | None |
| Syntax | DirectoryString |
| Example | rootdn-deny-ip: 192.168.0.0 |
6.3.51.6. rootdn-open-time
This sets part of a time period or range when the root user is allowed to access Directory Server. This sets when the time-based access begins.
This is used in conjunction with the rootdn-close-time attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=RootDN Access Control Plugin,cn=plugins,cn=config |
| Valid Range | Any valid time, in a 24-hour format |
| Default Value | None |
| Syntax | Integer |
| Example | rootdn-open-time: 0800 |
6.3.52. Schema Reload plug-in
| Plug-in Information | Description |
|---|---|
| Plug-in ID | schemareload |
| Configuration Entry DN | cn=Schema Reload,cn=plugins,cn=config |
| Description | Task plug-in to reload schema files |
| Type | object |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information |
6.3.53. Space Insensitive String Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | none |
| DN of Configuration Entry | cn=Space Insensitive String Syntax,cn=plugins,cn=config |
| Description | Syntax for handling space-insensitive values |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information | This plug-in enables the Directory Server to support space and case insensitive values. This allows applications to search the directory using entries with ASCII space characters.
For example, a search or compare operation that uses |
6.3.54. State Change plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | statechange |
| DN of Configuration Entry | cn=State Change Plugin,cn=plugins,cn=config |
| Description | Enables state-change-notification service |
| Type | postoperation |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information |
6.3.55. Syntax Validation Task plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | none |
| DN of Configuration Entry | cn=Syntax Validation Task,cn=plugins,cn=config |
| Description | Enables syntax validation for attribute values |
| Type | object |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | |
| Further Information | This plug-in implements syntax validation tasks. The actual process that carries out syntax validation is performed by each specific syntax plug-in. |
6.3.56. Telephone Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | tele-syntax |
| DN of Configuration Entry | cn=Telephone Syntax,cn=plugins,cn=config |
| Description | Supports telephone number syntaxes and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.57. Teletex Terminal Identifier Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | teletextermid-syntax |
| DN of Configuration Entry | cn=Teletex Terminal Identifier Syntax,cn=plugins,cn=config |
| Description | Supports international telephone number syntaxes and related matching rules from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.58. Telex Number Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | telex-syntax |
| DN of Configuration Entry | cn=Telex Number Syntax,cn=plugins,cn=config |
| Description | Supports syntaxes and related matching rules for the telex number, country code, and answerback code of a telex terminal; from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.59. URI Syntax plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | none |
| DN of Configuration Entry | cn=URI Syntax,cn=plugins,cn=config |
| Description | Supports syntaxes and related matching rules for unique resource identifiers (URIs), including unique resource locators (URLs); from RFC 4517. |
| Type | syntax |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | None |
| Dependencies | None |
| Performance-Related Information | Do not modify the configuration of this plug-in. If enabled, Red Hat recommends leaving this plug-in running at all times. |
| Further Information |
6.3.60. USN plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | USN |
| DN of Configuration Entry | cn=USN,cn=plugins,cn=config |
| Description | Sets an update sequence number (USN) on an entry, for every entry in the directory, whenever there is a modification, including adding and deleting entries and modifying attribute values. |
| Type | object |
| Configurable Options | on | off |
| Default Setting | off |
| Configurable Arguments | None |
| Dependencies | Database |
| Performance-Related Information |
For replication, it is recommended that the |
6.3.61. Views plug-in
| Plug-in Parameter | Description |
|---|---|
| Plug-in ID | views |
| DN of Configuration Entry | cn=Views,cn=plugins,cn=config |
| Description | Enables the use of views in Directory Server databases. |
| Type | object |
| Configurable Options | on | off |
| Default Setting | on |
| Configurable Arguments | None |
| Dependencies | * Type: Database * Named: State Change Plug-in |
| Performance-Related Information | Do not modify the configuration of this plug-in. Red Hat recommends leaving this plug-in running at all times. |
6.4. Database plug-in attributes
The database plug-in is also organized in an information tree. All plug-in technology used by the database instances is stored in the cn=ldbm database plug-in node. This section presents the additional attribute information for each of the nodes in bold in the cn=ldbm database,cn=plugins,cn=config information tree.
6.4.1. Database attributes under cn=config,cn=ldbm database,cn=plugins,cn=config
This section covers global configuration attributes common to all instances are stored in the cn=config,cn=ldbm database,cn=plugins,cn=config tree node.
6.4.1.1. nsslapd-backend-implement
The nsslapd-backend-implement parameter defines the database back end that Directory Server uses.
Directory Server supports the following database types:
- Berkeley Database (BDB)
- Lightning Memory-Mapped Database Manager (LMDB)
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | bdb or mdb |
| Default Value | bdb |
| Syntax | Directory String |
| Example | nsslapd-backend-implement: mdb |
6.4.1.2. nsslapd-backend-opt-level
This parameter can trigger experimental code to improve write performance.
Possible values:
-
0: Disables the parameter. -
1: The replication update vector is not written to the database during the transaction -
2: Changes the order of taking the back end lock and starts the transaction -
4: Moves code out of the transaction.
All parameters can be combined. For example 7 enables all optimisation features.
This parameter is experimental. Never change its value unless you are specifically told to do so by the Red Hat support.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | 0 | 1 | 2 | 4 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-backend-opt-level: 0 |
6.4.1.3. nsslapd-db-deadlock-policy
The nsslapd-db-deadlock-policy parameter sets the libdb library-internal deadlock policy.
Only change this parameter if instructed by Red Hat Support.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | 0-9 |
| Default Value | 0 |
| Syntax | DirectoryString |
| Example | nsslapd-db-deadlock-policy: 9 |
6.4.1.4. nsslapd-db-private-import-mem
The nsslapd-db-private-import-mem parameter manages whether or not Directory Server uses private memory for allocation of regions and mutexes for a database import.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-db-private-import-mem: on |
6.4.1.5. nsslapd-db-transaction-wait
If you enable the nsslapd-db-transaction-wait parameter, Directory Server does not start the transaction and waits until lock resources are available.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-db-transaction-wait: off |
6.4.1.6. nsslapd-directory
This attribute specifies absolute path to database instance. If the database instance is manually created then this attribute must be included. Once the database instance is created, do not modify this path as any changes risk preventing the server from accessing data.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any valid absolute path to the database instance |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-directory: /var/lib/dirsrv/slapd-instance/db |
6.4.1.7. nsslapd-exclude-from-export
This attribute contains a space-separated list of names of attributes to exclude from an entry when a database is exported. This mainly is used for some configuration and operational attributes which are specific to a server instance.
Do not remove any of the default values for this attribute, since that may affect server performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any valid attribute |
| Default Value | entrydn entryid dncomp parentid numSubordinates entryusn |
| Syntax | DirectoryString |
| Example | nsslapd-exclude-from-export: entrydn entryid dncomp parentid numSubordinates entryusn |
6.4.1.8. nsslapd-idlistscanlimit
The nsslapd-idlistscanlimit attribute is deprecated because the impact of the attribute on search performance is more harmful than helpful. Further description is provided for historical purposes only.
This performance-related attribute, present by default, specifies the number of entry IDs that are searched during a search operation. Attempting to set a value that is not a number or is too big for a 32-bit signed integer returns an LDAP_UNWILLING_TO_PERFORM error message, with additional error information explaining the problem. It is advisable to keep the default value to improve search performance.
This parameter can be changed while the server is running, and the new value will affect subsequent searches.
The corresponding user-level attribute is nsIDListScanLimit.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 100 to the maximum 32-bit integer value (2147483647) entry IDs |
| Default Value | 2147483646 |
| Syntax | Integer |
| Example | nsslapd-idlistscanlimit: 50000 |
6.4.1.9. nsslapd-idl-switch
The nsslapd-idl-switch parameter sets the IDL format Directory Server uses. Note that Red Hat no longer supports the old IDL format.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | new | old |
| Default Value | new |
| Syntax | Directory String |
| Example | nsslapd-idl-switch: new |
6.4.1.10. nsslapd-lookthroughlimit
This performance-related attribute specifies the maximum number of entries that Directory Server will check when examining candidate entries in response to a search request. The Directory Manager DN, however, is, by default, unlimited and overrides any other settings specified here. It is worth noting that binder-based resource limits work for this limit, which means that if a value for the operational attribute nsLookThroughLimit is present in the entry as which a user binds, the default limit will be overridden. Attempting to set a value that is not a number or is too big for a 32-bit signed integer returns an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | -1 to maximum 32-bit integer in entries (where -1 is unlimited) |
| Default Value | 5000 |
| Syntax | Integer |
| Example | nsslapd-lookthroughlimit: 5000 |
6.4.1.11. nsslapd-mode
This attribute specifies the permissions used for newly created index files.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values |
Any four-digit octal number. However, mode |
| Default Value | 600 |
| Syntax | Integer |
| Example | nsslapd-mode: 0600 |
6.4.1.12. nsslapd-pagedidlistscanlimit
This performance-related attribute specifies the number of entry IDs that are searched, specifically, for a search operation using the simple paged results control.
This attribute works the same as the nsslapd-idlistscanlimit attribute, except that it only applies to searches with the simple paged results control.
If this attribute is not present or is set to zero, then the nsslapd-idlistscanlimit is used to paged searches as well as non-paged searches.
The corresponding user-level attribute is nsPagedIDListScanLimit.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | -1 to maximum 32-bit integer in entries (where -1 is unlimited) |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-pagedidlistscanlimit: 5000 |
6.4.1.13. nsslapd-pagedlookthroughlimit
This performance-related attribute specifies the maximum number of entries that the Directory Server will check when examining candidate entries for a search which uses the simple paged results control.
This attribute works the same as the nsslapd-lookthroughlimit attribute, except that it only applies to searches with the simple paged results control.
If this attribute is not present or is set to zero, then the nsslapd-lookthroughlimit is used to paged searches as well as non-paged searches.
The corresponding user-level attribute is nsPagedLookThroughLimit.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | -1 to maximum 32-bit integer in entries (where -1 is unlimited) |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-pagedlookthroughlimit: 25000 |
6.4.1.14. nsslapd-rangelookthroughlimit
This performance-related attribute specifies the maximum number of entries that Directory Server will check when examining candidate entries in response to a range search request.
Range searches use operators to set a bracket to search for and return an entire subset of entries within the directory. For example, this searches for every entry modified at or after midnight on January 1:
(modifyTimestamp>=20200101010101Z)
(modifyTimestamp>=20200101010101Z)The nature of a range search is that it must evaluate every single entry within the directory to see if it is within the range given. Essentially, a range search is always an all IDs search.
For most users, the look-through limit kicks in and prevents range searches from turning into an all IDs search. This improves overall performance and speeds up range search results. However, some clients or administrative users like Directory Manager may not have a look-through limit set. In that case, a range search can take several minutes to complete or even continue indefinitely.
The nsslapd-rangelookthroughlimit attribute sets a separate range look-through limit that applies to all users, including Directory Manager.
This allows clients and administrative users to have high look-through limits while still allowing a reasonable limit to be set on potentially performance-impaired range searches.
Unlike other resource limits, this applies to searches by any user, including Directory Manager, regular users, and other LDAP clients.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | -1 to maximum 32-bit integer in entries (where -1 is unlimited) |
| Default Value | 5000 |
| Syntax | Integer |
| Example | nsslapd-rangelookthroughlimit: 5000 |
6.4.1.15. nsslapd-search-bypass-filter-test
If you enable the nsslapd-search-bypass-filter-test parameter, Directory Server bypasses filter checks when it builds candidate lists during a search. If you set the parameter to verify, Directory Server evaluates the filter against the search candidate entries.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off | verify |
| Default Value | on |
| Syntax | Directory String |
| Example | nsslapd-search-bypass-filter-test: on |
6.4.1.16. nsslapd-search-use-vlv-index
The nsslapd-search-use-vlv-index enables and disables virtual list view (VLV) searches.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | Directory String |
| Example | nsslapd-search-use-vlv-index: on |
6.4.2. Database attributes under cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config
This section covers global configuration attributes common to all instances are stored in the cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config tree node.
6.4.2.1. nsslapd-cache-autosize
This performance tuning-related attribute sets the percentage of free memory that is used in total for the database and entry cache. For example, if the value is set to 10, 10% of the system’s free RAM is used for both caches. If this value is set to a value greater than 0, auto-sizing is enabled for the database and entry cache.
For optimized performance, Red Hat recommends not to disable auto-sizing. However, in certain situations in can be necessary to disable auto-sizing. In this case, set the nsslapd-cache-autosize attribute to 0 and manually set:
-
the database cache in the
nsslapd-dbcachesizeattribute. -
the entry cache in the
nsslapd-cachememsizeattribute.
If the nsslapd-cache-autosize and nsslapd-cache-autosize-split attribute are both set to high values, such as 100, Directory Server fails to start. To fix the problem, set both parameters to more reasonable values. For example:
nsslapd-cache-autosize: 10 nsslapd-cache-autosize-split: 40
nsslapd-cache-autosize: 10
nsslapd-cache-autosize-split: 40| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 to 100. If 0 is set, the default value is used instead. |
| Default Value | 10 |
| Syntax | Integer |
| Example | nsslapd-cache-autosize: 10 |
6.4.2.2. nsslapd-cache-autosize-split
This performance tuning-related attribute sets the percentage of RAM that is used for the database cache. The remaining percentage is used for the entry cache. For example, if the value is set to 40, the database cache uses 40%, and the entry cache the remaining 60% of the free RAM reserved in the nsslapd-cache-autosize attribute.
If the nsslapd-cache-autosize and nsslapd-cache-autosize-split attribute are both set to high values, such as 100, Directory Server fails to start. To fix the problem, set both parameters to more reasonable values. For example:
nsslapd-cache-autosize: 10 nsslapd-cache-autosize-split: 40
nsslapd-cache-autosize: 10
nsslapd-cache-autosize-split: 40| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 to 99. If 0 is set, the default value is used instead. |
| Default Value | 40 |
| Syntax | Integer |
| Example | nsslapd-cache-autosize-split: 40 |
6.4.2.3. nsslapd-dbcachesize
This performance tuning-related attribute specifies the database index cache size, in bytes. This is one of the most important values for controlling how much physical RAM the directory server uses.
This is not the entry cache. This is the amount of memory the Berkeley database back end will use to cache the indexes (the .db files) and other files. This value is passed to the Berkeley DB API function set_cachesize. If automatic cache resizing is activated, this attribute is overridden when the server replaces these values with its own guessed values at a later stage of the server startup.
For more technical information on this attribute, see the cache size section of the Berkeley DB reference guide at link:https://docs.oracle.com/cd/E17076_04/html/programmer_reference/general_am_conf.html#am_conf_cachesize.
Attempting to set a value that is not a number or is too big for a 32-bit signed integer returns an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
Do not set the database cache size manually. Red Hat recommends to use the database cache auto-sizing feature for optimized performance.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 500 kilobytes to 4 gigabytes for 32-bit platforms and 500 kilobytes to 2^64-1 for 64-bit platforms |
| Default Value | |
| Syntax | Integer |
| Example | nsslapd-dbcachesize: 10000000 |
6.4.2.4. nsslapd-db-checkpoint-interval
This sets the amount of time in seconds after which Directory Server sends a checkpoint entry to the database transaction log. The database transaction log contains a sequential listing of all recent database operations and is used for database recovery only. A checkpoint entry indicates which database operations have been physically written to the directory database. The checkpoint entries are used to determine where in the database transaction log to begin recovery after a system failure. The nsslapd-db-checkpoint-interval attribute is absent from dse.ldif. To change the checkpoint interval, add the attribute to dse.ldif. This attribute can be dynamically modified using ldapmodify.
This attribute is provided only for system modification/diagnostics and should be changed only with the guidance of Red Hat Technical Support or Red Hat Consulting. Inconsistent settings of this attribute and other configuration attributes may cause Directory Server to be unstable.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 10 to 300 seconds |
| Default Value | 60 |
| Syntax | Integer |
| Example | nsslapd-db-checkpoint-interval: 120 |
6.4.2.5. nsslapd-db-circular-logging
This attribute specifies circular logging for the transaction log files. If this attribute is switched off, old transaction log files are not removed and are kept renamed as old log transaction files. Turning circular logging off can severely degrade server performance and, as such, should only be modified with the guidance of Red Hat Technical Support or Red Hat Consulting.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-db-circular-logging: on |
6.4.2.6. nsslapd-db-debug
This attribute specifies whether additional error information is to be reported to Directory Server. To report error information, set the parameter to on. This parameter is meant for troubleshooting; enabling the parameter may slow down Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-db-debug: off |
6.4.2.7. nsslapd-db-durable-transactions
This attribute sets whether database transaction log entries are immediately written to the disk. The database transaction log contains a sequential listing of all recent database operations and is used for database recovery only. With durable transactions enabled, every directory change will always be physically recorded in the log file and, therefore, able to be recovered in the event of a system failure. However, the durable transactions feature may also slow the performance of Directory Server. When durable transactions is disabled, all transactions are logically written to the database transaction log but may not be physically written to disk immediately. If there were a system failure before a directory change was physically written to disk, that change would not be recoverable. The nsslapd-db-durable-transactions attribute is absent from dse.ldif. To disable durable transactions, add the attribute to dse.ldif.
This attribute is provided only for system modification/diagnostics and should be changed only with the guidance of Red Hat Technical Support or Red Hat Consulting. Inconsistent settings of this attribute and other configuration attributes may cause Directory Server to be unstable.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-db-durable-transactions: on |
6.4.2.8. nsslapd-db-compactdb-interval
The nsslapd-db-compactdb-interval attribute defines the interval in seconds when Directory Server compacts the databases and replication changelogs. The compact operation returns the unused pages to the file system and the database file size shrinks.
Note that compacting the database is resource-intensive and should not be done too often.
The attribute change does not require the server restart. However, Directory Server starts to count the new interval value from the time you changed the value. For example, the compaction is planned for today at 10:40. Then at 10:35, 5 minutes before the planned compaction, you set the new interval (nsslapd-db-compactdb-interval) to 259200 seconds (3 days) and the new compaction time (nsslapd-db-compactdb-time) to 20:30. Now Directory Server discards the compaction planned for today at 10:40 and performs the next compaction in 3 days at 20:30.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | 0 (no compaction) to 2147483647 second |
| Default Value | 2592000 (30 days) |
| Syntax | Integer |
| Example | nsslapd-db-compactdb-interval: 2592000 |
6.4.2.9. nsslapd-db-compactdb-time
The nsslapd-db-compactdb-time attribute sets the time of the day when Directory Server compacts all databases and their replication changelogs. The compaction task runs after the compaction interval (nsslapd-db-compactdb-interval) has been exceeded.
The attribute change does not require the server restart. However, Directory Server applies the new time value when the compaction interval set in nsslapd-db-compactdb-interval expires. For example, the compaction is planned today at 10:40. Then at 10:35, 5 minutes before the planned compaction, you set the new interval (nsslapd-db-compactdb-interval) to 259200 seconds (3 days) and the new compaction time (nsslapd-db-compactdb-time) to 20:30. Now Directory Server discards the compaction planned for today at 10:40 and performs the next compaction in 3 days at 20:30.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | HH:MM. Time is set in 24-hour format |
| Default Value | 23:59 |
| Syntax | DirectoryString |
| Example | nsslapd-db-compactdb-time: 23:59 |
6.4.2.10. nsslapd-db-home-directory
This parameter specifies the location of memory-mapped files of Directory Server databases. For performance reasons, the default value of this parameter refers to the /dev/shm/ directory, which uses a tmpfs file system..
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any valid directory |
| Default Value | /dev/shm/ |
| Syntax | DirectoryString |
| Example | nsslapd-db-home-directory: /dev/shm/ |
6.4.2.11. nsslapd-db-idl-divisor
This attribute specifies the index block size in terms of the number of blocks per database page. The block size is calculated by dividing the database page size by the value of this attribute. A value of 1 makes the block size exactly equal to the page size. The default value of 0 sets the block size to the page size minus an estimated allowance for internal database overhead. For the majority of installations, the default value should not be changed unless there are specific tuning needs.
Before modifying the value of this attribute, export all databases using the db2ldif script. Once the modification has been made, reload the databases using the ldif2db script.
This parameter should only be used by very advanced users.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 to 8 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-db-idl-divisor: 2 |
6.4.2.12. nsslapd-db-locks
Lock mechanisms in Directory Server control how many copies of Directory Server processes can run at the same time. The nsslapd-db-locks parameter sets the maximum number of locks.
Only set this parameter to a higher value if Directory Server runs out of locks and logs libdb: Lock table is out of available locks error messages. If you set a higher value without a need, this increases the size of the /var/lib/dirsrv/slapd-instance_name/db__db.* files without any benefit.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 - 2147483647 |
| Default Value | 10000 |
| Syntax | Integer |
| Example | nsslapd-db-locks: 10000 |
6.4.2.13. nsslapd-db-locks-monitoring-enabled
Running out of database locks can lead to data corruption. With the nsslapd-db-locks-monitoring-enabled parameter, you can enable or disable database lock monitoring. If the parameter is enabled, which is the default, Directory Server terminates all searches if the number of active database locks is higher than the percentage threshold configured in nsslapd-db-locks-monitoring-threshold. If an issue occurs, the administrator can increase the number of database locks in the nsslapd-db-locks parameter.
Restart the service for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-db-locks-monitoring-enabled: on |
6.4.2.14. nsslapd-db-locks-monitoring-pause
If monitoring of database locks is enabled in the nsslapd-db-locks-monitoring-enable parameter, nsslapd-db-locks-monitoring-pause defines the interval in milliseconds that the monitoring thread sleeps between the checks.
If you set this parameter to a too high value, the server can run out of database locks before the monitoring check happens. However, setting a too low value can slow down the server.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | 0 - 2147483647 (value in milliseconds) |
| Default Value | 500 |
| Syntax | DirectoryString |
| Example | nsslapd-db-locks-monitoring-pause: 500 |
6.4.2.15. nsslapd-db-locks-monitoring-threshold
If monitoring of database locks is enabled in the nsslapd-db-locks-monitoring-enable parameter, nsslapd-db-locks-monitoring-threshold sets the maximum percentage of used database locks before Directory Server terminates searches to avoid further lock exhaustion.
Restart the service for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | 70 - 95 |
| Default Value | 90 |
| Syntax | DirectoryString |
| Example | nsslapd-db-locks-monitoring-threshold: 90 |
6.4.2.16. nsslapd-db-logbuf-size
This attribute specifies the log information buffer size. Log information is stored in memory until the buffer fills up or the transaction commit forces the buffer to be written to disk. Larger buffer sizes can significantly increase throughput in the presence of long running transactions, highly concurrent applications, or transactions producing large amounts of data. The log information buffer size is the transaction log size divided by four.
The nsslapd-db-logbuf-size attribute is only valid if the nsslapd-db-durable-transactions attribute is set to on.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 32K to maximum 32-bit integer (limited to the amount of memory available on the machine) |
| Default Value | 32K |
| Syntax | Integer |
| Example | nsslapd-db-logbuf-size: 32K |
6.4.2.17. nsslapd-db-logdirectory
This attribute specifies the path to the directory that contains the database transaction log. The database transaction log contains a sequential listing of all recent database operations. Directory Server uses this information to recover the database after an instance shut down unexpectedly.
By default, the database transaction log is stored in the same directory as the directory database. To update this parameter, you must manually update the /etc/dirsrv/slapd-instance_name/dse.ldif file.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any valid path |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-db-logdirectory: /var/lib/dirsrv/slapd-instance_name/db/ |
6.4.2.18. nsslapd-db-logfile-size
This attribute specifies the maximum size of a single file in the log in bytes. By default, or if the value is set to 0, a maximum size of 10 megabytes is used. The maximum size is an unsigned 4-byte value.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 to unsigned 4-byte integer |
| Default Value | 10MB |
| Syntax | Integer |
| Example | nsslapd-db-logfile-size: 10 MB |
6.4.2.19. nsslapd-dbncache
This attribute can split the LDBM cache into equally sized separate pieces of memory. It is possible to specify caches that are large enough so that they cannot be allocated contiguously on some architectures; for example, some systems limit the amount of memory that may be allocated contiguously by a process. If nsslapd-dbncache is 0 or 1, the cache will be allocated contiguously in memory. If it is greater than 1, the cache will be broken up into ncache, equally sized separate pieces of memory.
To configure a dbcache size larger than 4 gigabytes, add the nsslapd-dbncache attribute to cn=config,cn=ldbm database,cn=plugins,cn=config between the nsslapd-dbcachesize and nsslapd-db-logdirectory attribute lines.
Set this value to an integer that is one-quarter (1/4) the amount of memory in gigabytes. For example, for a 12 gigabyte system, set the nsslapd-dbncache value to 3; for an 8 gigabyte system, set it to 2.
This attribute is provided only for system modification/diagnostics and should be changed only with the guidance of Red Hat technical support or Red Hat professional services. Inconsistent settings of this attribute and other configuration attributes may cause Directory Server to be unstable.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | 1 to 4 |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-dbncache: 1 |
6.4.2.20. nsslapd-db-page-size
This attribute specifies the size of the pages used to hold items in the database in bytes. The minimum size is 512 bytes, and the maximum size is 64 kilobytes. If the page size is not explicitly set, Directory Server defaults to a page size of 8 kilobytes. Changing this default value can have a significant performance impact. If the page size is too small, it results in extensive page splitting and copying, whereas if the page size is too large it can waste disk space.
Before modifying the value of this attribute, export all databases using the db2ldif script. Once the modification has been made, reload the databases using the ldif2db script.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 512 bytes to 64 kilobytes |
| Default Value | 8KB |
| Syntax | Integer |
| Example | nsslapd-db-page-size: 8KB |
6.4.2.21. nsslapd-db-spin-count
This attribute specifies the number of times that test-and-set mutexes should spin without blocking.
Never touch this value unless you are very familiar with the inner workings of Berkeley DB or are specifically told to do so by Red Hat support.
The default value of 0 causes BDB to calculate the actual value by multiplying the number of available CPU cores (as reported by the nproc utility or the sysconf(_SC_NPROCESSORS_ONLN) call) by 50. For example, with a processor with 8 logical cores, leaving this attribute set to 0 is equivalent to setting it to 400. It is not possible to turn spinning off entirely - if you want to minimize the amount of times test-and-set mutexes will spin without blocking, set this attribute to 1.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 to 2147483647 (2^31-1) |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-db-spin-count: 0 |
6.4.2.22. nsslapd-db-transaction-batch-max-wait
If nsslapd-db-transaction-batch-val is set, the flushing of transactions is done by a separate thread when the set batch value is reached. However if there are only a few updates, this process might take too long. This parameter controls when transactions should be flushed latest, independently of the batch count. The values is defined in milliseconds.
This parameter is experimental. Never change its value unless you are specifically told to do so by the Red Hat support.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 - 2147483647 (value in milliseconds) |
| Default Value | 50 |
| Syntax | Integer |
| Example | nsslapd-db-transaction-batch-max-wait: 50 |
6.4.2.23. nsslapd-db-transaction-batch-min-wait
If nsslapd-db-transaction-batch-val is set, the flushing of transactions is done by a separate thread when the set batch value is reached. However if there are only a few updates, this process might take too long. This parameter controls when transactions should be flushed earliest, independently of the batch count. The values is defined in milliseconds.
This parameter is experimental. Never change its value unless you are specifically told to do so by the Red Hat support.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 - 2147483647 (value in milliseconds) |
| Default Value | 50 |
| Syntax | Integer |
| Example | nsslapd-db-transaction-batch-min-wait: 50 |
6.4.2.24. nsslapd-db-transaction-batch-val
This attribute specifies how many transactions will be batched before being committed. This attribute can improve update performance when full transaction durability is not required. This attribute can be dynamically modified using ldapmodify.
Setting this value will reduce data consistency and may lead to loss of data. This is because if there is a power outage before the server can flush the batched transactions, those transactions in the batch will be lost.
Do not set this value unless specifically requested to do so by Red Hat support.
If this attribute is not defined or is set to a value of 0, transaction batching will be turned off, and it will be impossible to make remote modifications to this attribute using LDAP. However, setting this attribute to a value greater than 0 causes the server to delay committing transactions until the number of queued transactions is equal to the attribute value. A value greater than 0 also allows modifications to this attribute remotely using LDAP. A value of 1 for this attribute allows modifications to the attribute setting remotely using LDAP, but results in no batching behavior. A value of 1 at server startup is therefore useful for maintaining normal durability while also allowing transaction batching to be turned on and off remotely when required. Remember that the value for this attribute may require modifying the nsslapd-db-logbuf-size attribute to ensure sufficient log buffer size for accommodating the batched transactions.
The nsslapd-db-transaction-batch-val attribute is only valid if the nsslapd-db-durable-transaction attribute is set to on.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 to 30 |
| Default Value | 0 (or turned off) |
| Syntax | Integer |
| Example | nsslapd-db-transaction-batch-val: 5 |
6.4.2.25. nsslapd-db-trickle-percentage
This attribute sets that at least the specified percentage of pages in the shared-memory pool are clean by writing dirty pages to their backing files. This is to ensure that a page is always available for reading in new information without having to wait for a write.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 to 100 |
| Default Value | 40 |
| Syntax | Integer |
| Example | nsslapd-db-trickle-percentage: 40 |
6.4.2.26. nsslapd-db-verbose
This attribute specifies whether to record additional informational and debugging messages when searching the log for checkpoints, doing deadlock detection, and performing recovery. This parameter is meant for troubleshooting, and enabling the parameter may slow down Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-db-verbose: off |
6.4.2.27. nsslapd-import-cache-autosize
This performance tuning-related attribute automatically sets the size of the import cache (importCache) to be used during the command-line-based import process of LDIF files to the database (the ldif2db operation).
In Directory Server, the import operation can be run as a server task or exclusively on the command-line. In the task mode, the import operation runs as a general Directory Server operation. The nsslapd-import-cache-autosize attribute enables the import cache to be set automatically to a predetermined size when the import operation is run on the command-line. The attribute can also be used by Directory Server during the task mode import for allocating a specified percentage of free memory for import cache.
By default, the nsslapd-import-cache-autosize attribute is enabled and is set to a value of -1. This value autosizes the import cache for the ldif2db operation only, automatically allocating fifty percent (50%) of the free physical memory for the import cache. The percentage value (50%) is hard-coded and cannot be changed.
Setting the attribute value to 50 (nsslapd-import-cache-autosize: 50) has the same effect on performance during an ldif2db operation. However, such a setting will have the same effect on performance when the import operation is run as a Directory Server task. The -1 value autosizes the import cache just for the ldif2db operation and not for any, including import, general Directory Server tasks.
The purpose of a -1 setting is to enable the ldif2db operation to benefit from free physical memory but, at the same time, not compete for valuable memory with the entry cache, which is used for general operations of Directory Server.
Setting the nsslapd-import-cache-autosize attribute value to 0 turns off the import cache autosizing feature - that is, no autosizing occurs during either mode of the import operation. Instead, Directory Server uses the nsslapd-import-cachesize attribute for import cache size, with a default value of 20000000.
There are three caches in the context of Directory Server: database cache, entry cache, and import cache. The import cache is only used during the import operation. The nsslapd-cache-autosize attribute, which is used for autosizing the entry cache and database cache, is used during the Directory Server operations only and not during the ldif2db command-line operation; the attribute value is the percentage of free physical memory to be allocated for the entry cache and database cache.
If both the autosizing attributes, nsslapd-cache-autosize and nsslapd-import-cache-autosize, are enabled, ensure that their sum is less than 100.
| Parameter | Description |
|---|---|
| Entry DN | cn=bdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | -1, 0 (turns import cache autosizing off) to 100 |
| Default Value | -1 (turns import cache autosizing on for ldif2db only and allocates 50% of the free physical memory to import cache) |
| Syntax | Integer |
| Example | nsslapd-import-cache-autosize: -1 |
6.4.2.28. nsslapd-search-bypass-filter-test
If you enable the nsslapd-search-bypass-filter-test parameter, Directory Server bypasses filter checks when it builds candidate lists during a search. If you set the parameter to verify, Directory Server evaluates the filter against the search candidate entries.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off | verify |
| Default Value | on |
| Syntax | Directory String |
| Example | nsslapd-search-bypass-filter-test: on |
6.4.3. Database attributes under cn=mdb,cn=config,cn=ldbm database,cn=plugins,cn=config
The section covers global Lightning Memory-Mapped Database Manager (LMDB) configuration attributes that are stored in the cn=mdb,cn=config,cn=ldbm database,cn=plugins,cn=config tree node and are common to all instances.
6.4.3.1. nsslapd-mdb-max-dbs
The nsslapd-mdb-max-dbs attribute sets the maximum number of named database instances that can be included within the memory mapped database file. If the attribute value is set to zero (0), Directory Server computes this attribute value. Each suffix and default indexes consume 35 named databases. Each additional index consumes one named database. With the default value of 512, you can create up to 14 suffixes.
To apply changes to the attribute value, you must restart the server.
| Parameter | Description |
|---|---|
| Entry DN | cn=mdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | 0-2147483647 |
| Default Value | 512 |
| Syntax | Integer |
| Example | nsslapd-mdb-max-dbs: 512 |
6.4.3.2. nsslapd-mdb-max-readers
The nsslapd-mdb-max-readers attribute sets the maximun number of read operations that can be opened simultaneously. If the attribute value is set to zero (0), Directory Server computes this attribute value.
To apply changes to the attribute value, you must restart the server.
| Parameter | Description |
|---|---|
| Entry DN | cn=mdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | 0-2147483647 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-mdb-max-readers:0 |
6.4.3.3. nsslapd-mdb-max-size
The nsslapd-mdb-max-size attribute sets the database maximum size in bytes. The maximum size of the Lightning Memory-Mapped Database Manager (LMDB) database is limited by the system addressable memory.
Make sure that the value of nsslapd-mdb-max-size is high enough to store all intended data. However, the value must not be too high to impact the performance because the database file is memory-mapped. You can use the database size in the Directory Server Hardware requirements for a reference.
To apply changes to the attribute value, you must restart the server.
| Parameter | Description |
|---|---|
| Entry DN | cn=mdb,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | 512 to maximum 32-bit integer (limited to the amount of memory available on the machine) |
| Default Value | 21474836480 |
| Syntax | Integer |
| Example | nsslapd-mdb-max-size:21474836480 |
6.4.4. Database attributes under cn=monitor,cn=ldbm database,cn=plugins,cn=config
Global read-only attributes containing database statistics for monitoring activity on the databases are stored in the cn=monitor,cn=ldbm database,cn=plugins,cn=config tree node.
6.4.4.1. currentNormalizedDNcachecount
Number of normalized cached DNs.
6.4.4.2. currentNormalizedDNcachesize
Current size of the normalized DN cache in bytes.
6.4.4.3. dbcachehitratio
This attribute shows the percentage of requested pages found in the database cache (hits/tries).
6.4.4.4. dbcachehits
This attribute shows the requested pages found in the database.
6.4.4.5. dbcachepagein
This attribute shows the pages read into the database cache.
6.4.4.6. dbcachepageout
This attribute shows the pages written from the database cache to the backing file.
6.4.4.7. dbcacheroevict
This attribute shows the clean pages forced from the cache.
6.4.4.8. dbcacherwevict
This attribute shows the dirty pages forced from the cache.
6.4.4.9. dbcachetries
This attribute shows the total cache lookups.
6.4.4.10. maxNormalizedDNcachesize
Current value of the nsslapd-ndn-cache-max-size parameter. For details how to update this setting, see Section 2.1.136, “nsslapd-ndn-cache-max-size”.
6.4.4.11. normalizedDNcachehitratio
Percentage of the normalized DNs found in the cache.
6.4.4.12. normalizedDNcachehits
Normalized DNs found within the cache.
6.4.4.13. normalizedDNcachemisses
Normalized DNs not found within the cache.
6.4.4.14. normalizedDNcachetries
Total number of cache lookups since the instance was started.
6.4.5. Database attributes under cn=database_name,cn=ldbm database,cn=plugins,cn=config
The cn=database_name subtree contains all the configuration data for the user-defined database.
The cn=userRoot subtree is called userRoot by default. However, this is not hard-coded and, given the fact that there are going to be multiple database instances, this name is changed and defined by the user as and when new databases are added. The cn=userRoot database referenced can be any user database.
The following attributes are common to databases, such as cn=userRoot.
6.4.5.1. nsslapd-cachememsize
This performance tuning-related attribute specifies the size, in bytes, for the available memory space for the entry cache. The simplest method is limiting cache size in terms of memory occupied. Activating automatic cache resizing overrides this attribute, replacing these values with its own guessed values at a later stage of the server startup.
Attempting to set a value that is not a number or is too big for a 32-bit signed integer (on 32-bit systems) returns an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
The performance counter for this setting goes to the highest 64-bit integer, even on 32-bit systems, but the setting itself is limited on 32-bit systems to the highest 32-bit integer because of how the system addresses memory.
Do not set the database cache size manually. Red Hat recommends to use the entry cache auto-sizing feature for optimized performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 500 kilobytes to 264-1 on 64-bit systems |
| Default Value | 209715200 (200 MiB) |
| Syntax | Integer |
| Example | nsslapd-cachememsize: 209715200 |
6.4.5.2. nsslapd-cachesize
This attribute has been deprecated. To resize the entry cache, use nsslapd-cachememsize.
This performance tuning-related attribute specifies the cache size in terms of the number of entries it can hold. However, this attribute is deprecated in favor of the nsslapd-cachememsize attribute, which sets an absolute allocation of RAM for the entry cache size, as described in Section 6.4.5.1, “nsslapd-cachememsize”
Attempting to set a value that is not a number or is too big for a 32-bit signed integer (on 32-bit systems) returns an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
The server has to be restarted for changes to this attribute to go into effect.
The performance counter for this setting goes to the highest 64-bit integer, even on 32-bit systems, but the setting itself is limited on 32-bit systems to the highest 32-bit integer because of how the system addresses memory.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 1 to 232-1 on 32-bit systems or 263-1 on 64-bit systems or -1, which means limitless |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-cachesize: -1 |
6.4.5.3. nsslapd-directory
This attribute specifies the path to the database instance. If it is a relative path, it starts from the path specified by nsslapd-directory in the global database entry cn=config,cn=ldbm database,cn=plugins,cn=config. The database instance directory is named after the instance name and located in the global database directory, by default. After the database instance has been created, do not modify this path, because any changes risk preventing the server from accessing data.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any valid path to the database instance |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-directory: /var/lib/dirsrv/slapd-instance/db/userRoot |
6.4.5.4. nsslapd-dncachememsize
This performance tuning-related attribute specifies the size, in bytes, for the available memory space for the DN cache. The DN cache is similar to the entry cache for a database, only its table stores only the entry ID and the entry DN. This allows faster lookups for rename and moddn operations.
The simplest method is limiting cache size in terms of memory occupied.
Attempting to set a value that is not a number or is too big for a 32-bit signed integer (on 32-bit systems) returns an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
The performance counter for this setting goes to the highest 64-bit integer, even on 32-bit systems, but the setting itself is limited on 32-bit systems to the highest 32-bit integer because of how the system addresses memory.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 500 kilobytes to 232-1 on 32-bit systems and to 264-1 on 64-bit systems |
| Default Value | 10,485,760 (10 megabytes) |
| Syntax | Integer |
| Example | nsslapd-dncachememsize: 10485760 |
6.4.5.5. nsslapd-readonly
This attribute specifies read-only mode for a single back-end instance. If this attribute has a value of off, then users have all read, write, and execute permissions allowed by their access permissions.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-readonly: off |
6.4.5.6. nsslapd-require-index
When switched to on, this attribute allows one to refuse unindexed searches. This performance-related attribute avoids saturating the server with erroneous searches.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-require-index: off |
6.4.5.7. nsslapd-require-internalop-index
When a plug-in modifies data, it has a write lock on the database. On large databases, if a plug-in then executes an unindexed search, the plug-in can use all database locks and corrupt the database or the server becomes unresponsive. To avoid this problem, you can reject internal unindexed searches by enabling the nsslapd-require-internalop-index parameter.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-require-internalop-index: off |
6.4.5.8. nsslapd-suffix
This attribute specifies the suffix of the database link. This is a single-valued attribute because each database instance can have only one suffix. Previously, it was possible to have more than one suffix on a single database instance, but this is no longer the case. As a result, this attribute is single-valued to enforce the fact that each database instance can only have one suffix entry. Any changes made to this attribute after the entry has been created take effect only after the server containing the database link is restarted.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-suffix: o=Example |
6.4.5.9. vlvBase
This attribute sets the base DN for which the browsing or virtual list view (VLV) index is created.
| Parameter | Description |
|---|---|
| Entry DN | cn=index_name,cn=userRoot,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | vlvBase: ou=People,dc=example,dc=com |
6.4.5.10. vlvEnabled
The vlvEnabled attribute provides status information about a specific VLV index, and Directory Server sets this attribute at run time. Although vlvEnabled is shown in the configuration, you cannot modify this attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=index_name,cn=userRoot,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | 0 (disabled) | 1 (enabled) |
| Default Value | 1 |
| Syntax | DirectoryString |
| Example | vlvEnbled: 0 |
6.4.5.11. vlvFilter
The browsing or virtual list view (VLV) index is created by running a search according to a filter and including entries which match that filter in the index. The filter is specified in the vlvFilter attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=index_name,cn=userRoot,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any valid LDAP filter |
| Default Value | |
| Syntax | DirectoryString |
| Example | vlvFilter: (|(objectclass=*)(objectclass=ldapsubentry)) |
6.4.5.12. vlvIndex
A browsing index or virtual list view (VLV) index dynamically generates an abbreviated index of entry headers that makes it much faster to visually browse large indexes. A VLV index definition has two parts: one which defines the index and one which defines the search used to identify entries to add to the index. The vlvIndex object class defines the index entry.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.42
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| cn | Gives the common name of the entry. |
| vlvSort | Identifies the attribute list that the browsing index (virtual list view index) is sorted on. |
| Attribute | Definition |
|---|---|
| vlvEnabled | Stores the availability of the browsing index. |
| vlvUses | Contains the count the browsing index is used. |
6.4.5.13. vlvScope
This attribute sets the scope of the search to run for entries in the browsing or virtual list view (VLV) index.
| Parameter | Description |
|---|---|
| Entry DN | cn=index_name,cn=userRoot,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | * 1 (one-level or children search) * 2 (subtree search) |
| Default Value | |
| Syntax | Integer |
| Example | vlvScope: 2 |
6.4.5.14. vlvSearch
A browsing index or virtual list view (VLV) index dynamically generates an abbreviated index of entry headers that makes it much faster to visually browse large indexes. A VLV index definition has two parts: one which defines the index and one which defines the search used to identify entries to add to the index. The vlvSearch object class defines the search filter entry.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.38
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| vlvBase | Identifies base DN the browsing index is created. |
| vlvScope | Identifies the scope to define the browsing index. |
| vlvFilter | Identifies the filter string to define the browsing index. |
| Attribute | Definition |
|---|---|
| multiLineDescription | Gives a text description of the entry. |
6.4.5.15. vlvSort
This attribute sets the sort order for returned entries in the browsing or virtual list view (VLV) index.
The entry for this attribute is a vlvIndex entry beneath the vlvSearch entry.
| Parameter | Description |
|---|---|
| Entry DN | cn=index_name,cn=index_name,cn=userRoot,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any Directory Server attributes, in a space-separated list |
| Default Value | |
| Syntax | DirectoryString |
| Example | vlvSort: cn givenName o ou sn |
6.4.5.16. vlvUses
The vlvUses attribute contains the count the browsing index uses, and Directory Server sets this attribute at run time. Although vlvUses is shown in the configuration, you cannot modify this attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=index_name,cn=userRoot,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | N/A |
| Default Value | |
| Syntax | DirectoryString |
| Example | vlvUses: 800 |
6.4.6. Database attributes under cn=database,cn=monitor,cn=ldbm database,cn=plugins,cn=config
The attributes in this tree node entry are all read-only, database performance counters. All of the values for these attributes are 32-bit integers, except for entrycachehits and entrycachetries.
If the nsslapd-counters attribute in cn=config is set to on, then some of the counters kept by the Directory Server instance increment using 64-bit integers, even on 32-bit machines or with a 32-bit version of Directory Server. For the database monitoring, the entrycachehits and entrycachetries counters use 64-bit integers.
The nsslapd-counters attribute enables 64-bit support for these specific database and server counters. The counters which use 64-bit integers are not configurable; the 64-bit integers are either enabled for all the allowed counters or disabled for all allowed counters.
6.4.6.1. currentdncachecount
This attribute shows the number of DNs currently present in the DN cache.
6.4.6.2. currentdncachesize
This attribute shows the total size, in bytes, of DNs currently present in the DN cache.
6.4.6.3. maxdncachesize
This attribute shows the maximum size, in bytes, of DNs that can be maintained in the database DN cache.
6.4.6.4. nsslapd-db-abort-rate
This attribute shows the number of transactions that have been aborted.
6.4.6.5. nsslapd-db-active-txns
This attribute shows the number of transactions that are currently active.
6.4.6.6. nsslapd-db-cache-hit
This attribute shows the requested pages found in the cache.
6.4.6.7. nsslapd-db-cache-region-wait-rate
This attribute shows the number of times that a thread of control was forced to wait before obtaining the region lock.
6.4.6.8. nsslapd-db-cache-size-bytes
This attribute shows the total cache size in bytes.
6.4.6.9. nsslapd-db-cache-try
This attribute shows the total cache lookups.
6.4.6.10. nsslapd-db-clean-pages
This attribute shows the clean pages currently in the cache.
6.4.6.11. nsslapd-db-commit-rate
This attribute shows the number of transactions that have been committed.
6.4.6.12. nsslapd-db-deadlock-rate
This attribute shows the number of deadlocks detected.
6.4.6.13. nsslapd-db-dirty-pages
This attribute shows the dirty pages currently in the cache.
6.4.6.14. nsslapd-db-hash-buckets
This attribute shows the number of hash buckets in buffer hash table.
6.4.6.15. nsslapd-db-hash-elements-examine-rate
This attribute shows the total number of hash elements traversed during hash table lookups.
6.4.6.16. nsslapd-db-hash-search-rate
This attribute shows the total number of buffer hash table lookups.
6.4.6.17. nsslapd-db-lock-conflicts
This attribute shows the total number of locks not immediately available due to conflicts.
6.4.6.18. nsslapd-db-lockers
This attribute shows the number of current lockers.
6.4.6.19. nsslapd-db-lock-region-wait-rate
This attribute shows the number of times that a thread of control was forced to wait before obtaining the region lock.
6.4.6.20. nsslapd-db-lock-request-rate
This attribute shows the total number of locks requested.
6.4.6.21. nsslapd-db-log-bytes-since-checkpoint
This attribute shows the number of bytes written to this log since the last checkpoint.
6.4.6.22. nsslapd-db-log-region-wait-rate
This attribute shows the number of times that a thread of control was forced to wait before obtaining the region lock.
6.4.6.23. nsslapd-db-log-write-rate
This attribute shows the number of megabytes and bytes written to this log.
6.4.6.24. nsslapd-db-longest-chain-length
This attribute shows the longest chain ever encountered in buffer hash table lookups.
6.4.6.25. nsslapd-db-page-create-rate
This attribute shows the pages created in the cache.
6.4.6.26. nsslapd-db-page-read-rate
This attribute shows the pages read into the cache.
6.4.6.27. nsslapd-db-page-ro-evict-rate
This attribute shows the clean pages forced from the cache.
6.4.6.28. nsslapd-db-page-rw-evict-rate
This attribute shows the dirty pages forced from the cache.
6.4.6.29. nsslapd-db-pages-in-use
This attribute shows all pages, clean or dirty, currently in use.
6.4.6.30. nsslapd-db-page-trickle-rate
This attribute shows the dirty pages written using the memp_trickle interface.
6.4.6.31. nsslapd-db-page-write-rate
This attribute shows the pages read into the cache.
6.4.6.32. nsslapd-db-txn-region-wait-rate
This attribute shows the number of times that a thread of control was force to wait before obtaining the region lock.
6.4.7. Database attributes under cn=changelog,cn=database_name,cn=ldbm database,cn=plugins,cn=config
In the multi-supplier replication, Directory Server stores changelog configuration entries under the cn=changelog,cn=database_name,cn=ldbm database,cn=plugins,cn=config entry that has top and extensibleObject object classes.
The term changelog may refer to:
- Changelog
- The actual changelog in the multi-supplier replication that uses attributes described in this chapter.
- Retro Changelog
- The plug-in that Directory Server uses for compatibility with certain legacy applications. Fore more information, see Section 6.3.49, “Retro Changelog plug-in”.
6.4.7.1. cn
The cn attribute sets the relative distinguished name (RDN) of a changelog entry. This attribute is mandatory.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any string |
| Default Value | changelog |
| Syntax | DirectoryString |
| Example | cn=changelog,cn=userRoot,cn=ldbm database,cn=plugins |
6.4.7.2. nsslapd-changelogmaxage
When synchronizing with a consumer, Directory Server stores each update in the changelog with a time stamp. The nsslapd-changelogmaxage attribute sets the maximum age of a record stored in the changelog. Directory Server automatically removes older records that were successfully transferred to all consumers. By default, Directory Server removes records that are older than seven days. However, if you disable the nsslapd-changelogmaxage and nsslapd-changelogmaxentries attributes, Directory Server will keep all records in the changelog, and it can lead to the excessive growth of the changelog file.
Retro changelog has its own nsslapd-changelogmaxage attribute. For more information, see Retro changelog nsslapd-changelogmaxage
The attribute change does not require the server restart, however the change takes effect after the trim operation that is scheduled according to the nsslapd-changelogtrim-interval attribute setting.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 (entries are not removed according to their age) to maximum 32-bit integer (2147483647) |
| Default Value | 7d |
| Syntax | DirectoryString IntegerAgeID, where AgeID is:
If you set only the integer value without the AgeID then Directory Server takes it as seconds. |
| Example | nsslapd-changelogmaxage: 30d |
6.4.7.3. nsslapd-changelogmaxentries
The nsslapd-changelogmaxentries attribute sets the maximum number of records stored in the changelog. If the number of the oldest records that were successfully transferred to all consumers exceeds the nsslapd-changelogmaxentries value, Directory Server automatically removes these records from the changelog. If you set the nsslapd-changelogmaxentries and nsslapd-changelogmaxage attribute to 0, Directory Server keeps all records in the changelog, which can lead to the excessive growth of the changelog file.
Directory Server does not automatically reduce the file size of the replication changelog if you set a lower value in the nsslapd-changelogmaxentries attribute.
The attribute change does not require the server restart, however the change takes effect after the trim operation that is scheduled according to the nsslapd-changelogtrim-interval attribute setting.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 (the only maximum limit is the disk size) to maximum 32-bit integer (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-changelogmaxentries: 5000 |
6.4.7.4. nsslapd-changelogtrim-interval
Directory Server repeatedly runs a trimming process on the changelog. To change the time between two runs, update the nsslapd-changelogtrim-interval attribute and set the interval in seconds.
The attribute change does not require the server restart, however the change takes effect after the trim operation.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | 300 (5 minutes) |
| Syntax | DirectoryString |
| Example | nsslapd-changelogtrim-interval: 300 |
6.4.7.5. nsslapd-encryptionalgorithm
The nsslapd-encryptionalgorithm attribute specifies the encryption algorithm Directory Server uses for the changelog encryption. To enable the changelog encryption, you must install the server certificate on the directory server.
You must restart the server to apply the attribute value changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | AES or 3DES |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-encryptionalgorithm: AES |
6.4.7.6. nsSymmetricKey
The nsSymmetricKey attribute stores the internally-generated symmetric key.
You must restart the server to apply the attribute value changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Range | Base 64-encoded key |
| Default Value | None |
| Syntax | DirectoryString |
| Example | None |
6.4.8. Database attributes under cn=monitor,cn=database_name,cn=ldbm database,cn=plugins,cn=config
The attributes in this tree node entry are all read-only, database performance counters.
If the nsslapd-counters attribute in cn=config is set to on, then some of the counters kept by the Directory Server instance increment using 64-bit integers, even on 32-bit machines or with a 32-bit version of Directory Server. For database monitoring, the entrycachehits and entrycachetries counters use 64-bit integers.
The nsslapd-counters attribute enables 64-bit support for these specific database and server counters. The counters which use 64-bit integers are not configurable; the 64-bit integers are either enabled for all the allowed counters or disabled for all allowed counters.
6.4.8.1. currentDNcachecount
Number of cached DNs.
6.4.8.2. currentDNcachesize
Current size of the DN cache in bytes.
6.4.8.3. dbfilecachehit-number
This attribute gives the number of times that a search requiring data from this file was performed and that the data were successfully obtained from the cache. The number in this attributes name corresponds to the one in dbfilename.
6.4.8.4. dbfilecachemiss-number
This attribute gives the number of times that a search requiring data from this file was performed and that the data could not be obtained from the cache. The number in this attributes name corresponds to the one in dbfilename.
6.4.8.5. dbfilename-number
This attribute gives the name of the file and provides a sequential integer identifier (starting at 0) for the file. All associated statistics for the file are given this same numerical identifier.
6.4.8.6. dbfilepagein-number
This attribute gives the number of pages brought to the cache from this file. The number in this attributes name corresponds to the one in dbfilename.
6.4.8.7. dbfilepageout-number
This attribute gives the number of pages for this file written from cache to disk. The number in this attributes name corresponds to the one in dbfilename.
6.4.8.8. DNcachehitratio
Percentage of the DNs found in the cache.
6.4.8.9. DNcachehits
DNs found within the cache.
6.4.8.10. DNcachemisses
DNs not found within the cache.
6.4.8.11. DNcachetries
Total number of cache lookups since the instance was started.
6.4.8.12. maxDNcachesize
Current value of the nsslapd-ndn-cache-max-size parameter. For details how to update this setting, see Section 2.1.136, “nsslapd-ndn-cache-max-size”.
6.4.9. Database attributes under cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config
The set of default indexes is stored here. Default indexes are configured per back end in order to optimize Directory Server functionality for the majority of setup scenarios. All indexes, except system-essential ones, can be removed, but care should be taken so as not to cause unnecessary disruptions.
6.4.9.1. cn
This attribute provides the name of the attribute to index.
| Parameter | Description |
|---|---|
| Entry DN | cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any valid index cn |
| Default Value | None |
| Syntax | DirectoryString |
| Example | cn: aci |
6.4.9.2. nsIndex
This object class defines an index in the back end database. This object is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.44
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| cn | Gives the common name of the entry. |
| nsSystemIndex | Identify whether or not the index is a system defined index. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| nsIndexType | Identifies the index type. |
| nsMatchingRule | Identifies the matching rule. |
6.4.9.3. nsIndexType
This optional, multi-valued attribute specifies the type of index for Directory Server operations and takes the values of the attributes to be indexed. Each required index type has to be entered on a separate line.
| Parameter | Description |
|---|---|
| Entry DN | cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | * pres = presence index * eq = equality index * approx = approximate index * sub = substring index * matching rule = international index * index browse = browsing index |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsIndexType: eq |
6.4.9.4. nsMatchingRule
This optional, multi-valued attribute specifies the ordering matching rule name or OID used to match values and to generate index keys for the attribute. This is most commonly used to ensure that equality and range searches work correctly for languages other than English (7-bit ASCII).
This is also used to allow range searches to work correctly for integer syntax attributes that do not specify an ordering matching rule in their schema definition. uidNumber and gidNumber are two commonly used attributes that fall into this category.
For example, for a uidNumber that uses integer syntax, the rule attribute could be nsMatchingRule: integerOrderingMatch.
Any change to this attribute will not take effect until the change is saved and the index is rebuilt using db2index command.
| Parameter | Description |
|---|---|
| Entry DN | cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any valid collation order object identifier (OID) |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsMatchingRule: 2.16.840.1.113730.3.3.2.3.1 (For Bulgarian) |
6.4.9.5. nsSystemIndex
This mandatory attribute specifies whether the index is a system index, an index which is vital for Directory Server operations. If this attribute has a value of true, then it is system-essential. System indexes should not be removed, as this will seriously disrupt server functionality.
| Parameter | Description |
|---|---|
| Entry DN | cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | true | false |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssystemindex: true |
6.4.10. Database attributes under cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config
In addition to the set of default indexes that are stored under cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config, custom indexes can be created for user-defined back end instances; these are stored under cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config.
For example, the index file for the aci attribute under o=UserRoot appears in Directory Server as follows:
These entries share all of the indexing attributes listed for the default indexes in Section 6.4.9, “Database attributes under cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config”.
6.4.10.1. nsIndexIDListScanLimit
This multi-valued parameter defines a search limit for certain indices or to use no ID list.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_name,cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsIndexIDListScanLimit: limit=0 type=eq values=inetorgperson |
6.4.10.2. nsSubStrBegin
By default, for a search to be indexed, the search string must be at least three characters long, without counting any wildcard characters. For example, the string abc would be an indexed search while ab* would not be. Indexed searches are significantly faster than unindexed searches, so changing the minimum length of the search key is helpful to increase the number of indexed searches.
This substring length can be edited based on the position of any wildcard characters. The nsSubStrBegin attribute sets the required number of characters for an indexed search for the beginning of a search string, before the wildcard. For example:
abc*
abc*
If the value of this attribute is changed, then the index must be regenerated using db2index.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_name,cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any integer |
| Default Value | 3 |
| Syntax | Integer |
| Example | nsSubStrBegin: 2 |
6.4.10.3. nsSubStrEnd
By default, for a search to be indexed, the search string must be at least three characters long, without counting any wildcard characters. For example, the string abc would be an indexed search while ab* would not be. Indexed searches are significantly faster than unindexed searches, so changing the minimum length of the search key is helpful to increase the number of indexed searches.
This substring length can be edited based on the position of any wildcard characters. The nsSubStrEnd attribute sets the required number of characters for an indexed search for the end of a search string, after the wildcard. For example:
*xyz
*xyz
If the value of this attribute is changed, then the index must be regenerated using db2index.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_name,cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any integer |
| Default Value | 3 |
| Syntax | Integer |
| Example | nsSubStrEnd: 2 |
6.4.10.4. nsSubStrMiddle
By default, for a search to be indexed, the search string must be at least three characters long, without counting any wildcard characters. For example, the string abc would be an indexed search while ab* would not be. Indexed searches are significantly faster than unindexed searches, so changing the minimum length of the search key is helpful to increase the number of indexed searches.
This substring length can be edited based on the position of any wildcard characters. The nsSubStrMiddle attribute sets the required number of characters for an indexed search where a wildcard is used in the middle of a search string. For example:
ab*z
ab*z
If the value of this attribute is changed, then the index must be regenerated using db2index.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_name,cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any integer |
| Default Value | 3 |
| Syntax | Integer |
| Example | nsSubStrMiddle: 3 |
6.4.11. Database attributes under cn=attribute_name,cn=encrypted attributes,cn=database_name,cn=ldbm database,cn=plugins,cn=config
In addition to the set of default indexes that are stored under cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config, custom indexes can be created for user-defined back end instances; these are stored under cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config.
For example, the index file for the aci attribute under o=UserRoot appears in Directory Server as follows:
These entries share all of the indexing attributes listed for the default indexes in Section 6.4.9, “Database attributes under cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config”.
6.4.11.1. nsIndexIDListScanLimit
This multi-valued parameter defines a search limit for certain indices or to use no ID list.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_name,cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsIndexIDListScanLimit: limit=0 type=eq values=inetorgperson |
6.4.11.2. nsSubStrBegin
By default, for a search to be indexed, the search string must be at least three characters long, without counting any wildcard characters. For example, the string abc would be an indexed search while ab* would not be. Indexed searches are significantly faster than unindexed searches, so changing the minimum length of the search key is helpful to increase the number of indexed searches.
This substring length can be edited based on the position of any wildcard characters. The nsSubStrBegin attribute sets the required number of characters for an indexed search for the beginning of a search string, before the wildcard. For example:
abc*
abc*
If the value of this attribute is changed, then the index must be regenerated using db2index.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_name,cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any integer |
| Default Value | 3 |
| Syntax | Integer |
| Example | nsSubStrBegin: 2 |
6.4.11.3. nsSubStrEnd
By default, for a search to be indexed, the search string must be at least three characters long, without counting any wildcard characters. For example, the string abc would be an indexed search while ab* would not be. Indexed searches are significantly faster than unindexed searches, so changing the minimum length of the search key is helpful to increase the number of indexed searches.
This substring length can be edited based on the position of any wildcard characters. The nsSubStrEnd attribute sets the required number of characters for an indexed search for the end of a search string, after the wildcard. For example:
*xyz
*xyz
If the value of this attribute is changed, then the index must be regenerated using db2index.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_name,cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any integer |
| Default Value | 3 |
| Syntax | Integer |
| Example | nsSubStrEnd: 2 |
6.4.11.4. nsSubStrMiddle
By default, for a search to be indexed, the search string must be at least three characters long, without counting any wildcard characters. For example, the string abc would be an indexed search while ab* would not be. Indexed searches are significantly faster than unindexed searches, so changing the minimum length of the search key is helpful to increase the number of indexed searches.
This substring length can be edited based on the position of any wildcard characters. The nsSubStrMiddle attribute sets the required number of characters for an indexed search where a wildcard is used in the middle of a search string. For example:
ab*z
ab*z
If the value of this attribute is changed, then the index must be regenerated using db2index.
| Parameter | Description |
|---|---|
| Entry DN | cn=attribute_name,cn=index,cn=database_name,cn=ldbm database,cn=plugins,cn=config |
| Valid Values | Any integer |
| Default Value | 3 |
| Syntax | Integer |
| Example | nsSubStrMiddle: 3 |
6.5. Database link plug-in attributes
The database link plug-in attributes are also organized in an information tree. All plug-in technology used by the database link instances is stored in the cn=chaining database plug-in node. This section presents the additional attribute information for the three nodes marked in bold in the cn=chaining database,cn=plugins,cn=config information tree in diagram.
6.5.1. Database link attributes under cn=config,cn=chaining database,cn=plugins,cn=config
This section covers global configuration attributes common to all instances are stored in the cn=config,cn=chaining database,cn=plugins,cn=config tree node.
6.5.1.1. nsActiveChainingComponents
This attribute lists the components using chaining. A component is any functional unit in the server. The value of this attribute overrides the value in the global configuration attribute. To disable chaining on a particular database instance, use the value None. This attribute also allows the components used to chain to be altered. By default, no components are allowed to chain, which explains why this attribute will probably not appear in a list of cn=config,cn=chaining database,cn=config attributes, as LDAP considers empty attributes to be non-existent.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=chaining database,cn=plugins,cn=config |
| Valid Values | Any valid component entry |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsActiveChainingComponents: cn=uid uniqueness,cn=plugins,cn=config |
6.5.1.2. nsMaxResponseDelay
This error detection, performance-related attribute specifies the maximum amount of time it can take a remote server to respond to an LDAP operation request made by a database link before an error is suspected. Once this delay period has been met, the database link tests the connection with the remote server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=chaining database,cn=plugins,cn=config |
| Valid Values | Any valid delay period in seconds |
| Default Value | 60 seconds |
| Syntax | Integer |
| Example | nsMaxResponseDelay: 60 |
6.5.1.3. nsMaxTestResponseDelay
This error detection, performance-related attribute specifies the duration of the test issued by the database link to check whether the remote server is responding. If a response from the remote server is not returned before this period has passed, the database link assumes the remote server is down, and the connection is not used for subsequent operations.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=chaining database,cn=plugins,cn=config |
| Valid Values | Any valid delay period in seconds |
| Default Value | 15 seconds |
| Syntax | Integer |
| Example | nsMaxTestResponseDelay: 15 |
6.5.1.4. nsTransmittedControls
This attribute, which can be both a global (and thus dynamic) configuration or an instance (that is, cn=database link instance,cn=chaining database,cn=plugins,cn=config) configuration attribute, allows the controls the database link forwards to be altered. The following controls are forwarded by default by the database link:
- Managed DSA (OID: 2.16.840.1.113730.3.4.2)
- Virtual list view (VLV) (OID: 2.16.840.1.113730.3.4.9)
- Server side sorting (OID: 1.2.840.113556.1.4.473)
- Loop detection (OID: 1.3.6.1.4.1.1466.29539.12)
Other controls, such as dereferencing and simple paged results for searches, can be added to the list of controls to forward.
| Parameter | Description |
|---|---|
| Entry DN | cn=config,cn=chaining database,cn=plugins,cn=config |
| Valid Values | Any valid OID or the above listed controls forwarded by the database link |
| Default Value | None |
| Syntax | Integer |
| Example | nsTransmittedControls: 1.2.840.113556.1.4.473 |
6.5.2. Database link attributes under cn=default instance config,cn=chaining database,cn=plugins,cn=config
Default instance configuration attributes for instances are housed in the cn=default instance config,cn=chaining database,cn=plugins,cn=config tree node.
6.5.2.1. nsAbandonedSearchCheckInterval
This attribute shows the number of seconds that pass before the server checks for abandoned operations.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) seconds |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsAbandonedSearchCheckInterval: 10 |
6.5.2.2. nsBindConnectionsLimit
This attribute shows the maximum number of TCP connections the database link establishes with the remote server.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Range | 1 to 50 connections |
| Default Value | 3 |
| Syntax | Integer |
| Example | nsBindConnectionsLimit: 3 |
6.5.2.3. nsBindRetryLimit
Contrary to what the name suggests, this attribute does not specify the number of times a database link retries to bind with the remote server but the number of times it tries to bind with the remote server. A value of 1 here indicates that the database link only attempts to bind once.
Retries only occur for connection failures and not for other types of errors, such as invalid bind DNs or bad passwords.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Range | 0 to 5 |
| Default Value | 3 |
| Syntax | Integer |
| Example | nsBindRetryLimit: 3 |
6.5.2.4. nsBindTimeout
This attribute shows the amount of time before the bind attempt times out. There is no real valid range for this attribute, except reasonable patience limits.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Range | 0 to 60 seconds |
| Default Value | 15 |
| Syntax | Integer |
| Example | nsBindTimeout: 15 |
6.5.2.5. nsCheckLocalACI
Reserved for advanced use only. This attribute controls whether ACIs are evaluated on the database link as well as the remote data server. Changes to this attribute only take effect once the server has been restarted.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsCheckLocalACI: on |
6.5.2.6. nsConcurrentBindLimit
This attribute shows the maximum number of concurrent bind operations per TCP connection.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Range | 1 to 25 binds |
| Default Value | 10 |
| Syntax | Integer |
| Example | nsConcurrentBindLimit: 10 |
6.5.2.7. nsConcurrentOperationsLimit
This attribute specifies the maximum number of concurrent operations allowed.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Range | 1 to 50 operations |
| Default Value | 2 |
| Syntax | Integer |
| Example | nsConcurrentOperationsLimit: 5 |
6.5.2.8. nsConnectionLife
This attribute specifies connection lifetime. Connections between the database link and the remote server can be kept open for an unspecified time or closed after a specific period of time. It is faster to keep the connections open, but it uses more resources. When the value is 0 and a list of failover servers is provided in the nsFarmServerURL attribute, the main server is never contacted after failover to the alternate server.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Range | 0 to limitless seconds (where 0 means forever) |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsConnectionLife: 0 |
6.5.2.9. nsOperationConnectionsLimit
This attribute shows the maximum number of LDAP connections the database link establishes with the remote server.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Range | 1 to n connections |
| Default Value | 20 |
| Syntax | Integer |
| Example | nsOperationConnectionsLimit: 10 |
6.5.2.10. nsProxiedAuthorization
Reserved for advanced use only. If you disable proxied authorization, binds for chained operations are executed as the user set in the nsMultiplexorBindDn attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsProxiedAuthorization: on |
6.5.2.11. nsReferralOnScopedSearch
This attribute controls whether referrals are returned by scoped searches. This attribute can be used to optimize the directory because returning referrals in response to scoped searches is more efficient. A referral is returned to all the configured farm servers.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsReferralOnScopedSearch: off |
6.5.2.12. nsSizeLimit
This attribute shows the default size limit for the database link in bytes.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Range | -1 (no limit) to maximum 32-bit integer (2147483647) entries |
| Default Value | 2000 |
| Syntax | Integer |
| Example | nsSizeLimit: 2000 |
6.5.2.13. nsTimeLimit
This attribute shows the default search time limit for the database link.
| Parameter | Description |
|---|---|
| Entry DN | cn=default instance config,cn=chaining database,cn=plugins,cn=config |
| Valid Range | -1 to maximum 32-bit integer (2147483647) seconds |
| Default Value | 3600 |
| Syntax | Integer |
| Example | nsTimeLimit: 3600 |
6.5.3. Database link attributes under cn=database_link_name,cn=chaining database,cn=plugins,cn=config
This information node stores the attributes concerning the server containing the data. A farm server is a server which contains data on databases. This attribute can contain optional servers for failover, separated by spaces. For cascading chaining, this URL can point to another database link.
6.5.3.1. nsBindMechanism
This attribute sets a bind mechanism for the farm server to connect to the remote server. A farm server is a server containing data in one or more databases. This attribute configures the connection type, either standard, TLS, or SASL.
-
empty. This performs simple authentication and requires the
nsMultiplexorBindDnandnsMultiplexorCredentialsattributes to give the bind information. EXTERNAL. This uses an TLS certificate to authenticate the farm server to the remote server. Either the farm server URL must be set to the secure URL (
ldaps) or thensUseStartTLSattribute must be set toon.Additionally, the remote server must be configured to map the farm server’s certificate to its bind identity.
-
DIGEST-MD5. This uses SASL with DIGEST-MD5 encryption. As with simple authentication, this requires the
nsMultiplexorBindDnandnsMultiplexorCredentialsattributes to give the bind information. GSSAPI. This uses Kerberos-based authentication over SASL. The farm server must be connected over the standard port, meaning the URL has
ldap, because Directory Server does not support SASL/GS-API over TLS.The farm server must be configured with a Kerberos keytab, and the remote server must have a defined SASL mapping for the farm server’s bind identity.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_link_name,cn=chaining database,cn=plugins,cn=config |
| Valid Values | * empty * EXTERNAL * DIGEST-MD5 * GSSAPI |
| Default Value | empty |
| Syntax | DirectoryString |
| Example | nsBindMechanism: GSSAPI |
6.5.3.2. nsFarmServerURL
This attribute gives the LDAP URL of the remote server. A farm server is a server containing data in one or more databases. This attribute can contain optional servers for failover, separated by spaces. If using cascading changing, this URL can point to another database link.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_link_name,cn=chaining database,cn=plugins,cn=config |
| Valid Values | Any valid remote server LDAP URL |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsFarmServerURL: ldap://farm1.example.com farm2.example.com:389 farm3.example.com:1389/ |
6.5.3.3. nshoplimit
This attribute specifies the maximum number of times a database is allowed to chain; that is, the number of times a request can be forwarded from one database link to another.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_link_name,cn=chaining database,cn=plugins,cn=config |
| Valid Range | 1 to an appropriate upper limit for the deployment |
| Default Value | 10 |
| Syntax | Integer |
| Example | nsHopLimit: 3 |
6.5.3.4. nsMultiplexorBindDN
This attribute gives the DN of the administrative entry used to communicate with the remote server. The multiplexor is the server that contains the database link and communicates with the farm server. This bind DN cannot be the Directory Manager, and, if this attribute is not specified, the database link binds as anonymous.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_link_name,cn=chaining database,cn=plugins,cn=config |
| Valid Values | |
| Default Value | DN of the multiplexor |
| Syntax | DirectoryString |
| Example | nsMultiplexerBindDN: cn=proxy manager |
6.5.3.5. nsMultiplexorCredentials
Password for the administrative user, given in plain text. If no password is provided, it means that users can bind as anonymous. The password is encrypted in the configuration file. The example below is what is shown, not what is typed.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_link_name,cn=chaining database,cn=plugins,cn=config |
| Valid Values | Any valid password, which will then be encrypted using the DES reversible password encryption schema |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsMultiplexerCredentials: {DES} 9Eko69APCJfF |
6.5.3.6. nsUseStartTLS
This attribute sets whether to use Start TLS to initiate a secure, encrypted connection over an insecure port. This attribute can be used if the nsBindMechanism attribute is set to EXTERNAL but the farm server URL set to the standard URL (ldap) or if the nsBindMechanism attribute is left empty.
| Parameter | Description |
|---|---|
| Entry DN | cn=database_link_name,cn=chaining database,cn=plugins,cn=config |
| Valid Values | off | on |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsUseStartTLS: on |
6.5.4. Database link attributes under cn=monitoring,cn=database_link_name,cn=chaining database,cn=plugins,cn=config
Attributes used for monitoring activity on the instances are stored in the cn=monitor,cn=database instance name,cn=chaining database,cn=plugins,cn=config information tree.
6.5.4.1. nsAbandonCount
This attribute gives the number of abandon operations received.
6.5.4.2. nsAddCount
This attribute gives the number of add operations received.
6.5.4.3. nsBindCount
This attribute gives the number of bind requests received.
6.5.4.4. nsCompareCount
This attribute gives the number of compare operations received.
6.5.4.5. nsDeleteCount
This attribute gives the number of delete operations received.
6.5.4.6. nsModifyCount
This attribute gives the number of modify operations received.
6.5.4.7. nsOpenBindConnectionCount
This attribute gives the number of open connections for bind operations.
6.5.4.8. nsOperationConnectionCount
This attribute gives the number of open connections for normal operations.
6.5.4.9. nsRenameCount
This attribute gives the number of rename operations received.
6.5.4.10. nsSearchBaseCount
This attribute gives the number of base level searches received.
6.5.4.11. nsSearchOneLevelCount
This attribute gives the number of one-level searches received.
6.5.4.12. nsSearchSubtreeCount
This attribute gives the number of subtree searches received.
6.5.4.13. nsUnbindCount
This attribute gives the number of unbinds received.
6.6. Referential integrity plug-in attributes
Referential Integrity ensures that when you perform update or remove operations to an entry in the the directory, the server also updates information for entries that reference removed/updated one. For example, if a user’s entry is removed from the directory and Referential Integrity is enabled, the server also removes the user from any groups where the user is a member.
6.6.1. nsslapd-pluginAllowReplUpdates
With nsslapd-pluginAllowReplUpdates set to on, the Referential Integrity plugin processes common and replicated updates.
Referential Integrity can be a very resource demanding procedure. So if you configured multi-supplier replication, the Referential Integrity plugin will ignore replicated updates by default. However, sometimes it is not possible to enable the Referential Integrity plugin, or the plugin is not available.
For example, one of your suppliers in the replication topology is an Active Directory server that does not support Referential Integrity. In such cases you can allow the Referential Integrity plugin on another supplier to process replicated updates by using nsslapd-pluginAllowReplUpdates attribute. For more details about Active Directory integration, see Windows Synchronization.
Only one supplier must have the nsslapd-pluginAllowReplUpdates attribute value set to on in multi-supplier replication topology. Otherwise, it can lead to replication errors, and requires a full initialization to fix the problem. On the other hand, the Referential Integrity plugin must be enabled on all supplies where possible,to maintain data integrity.
| Parameter | Description |
|---|---|
| Entry DN | cn=referential integrity postoperation,cn=plugins,cn=config |
| Valid Range | on/off |
| Default Value | off |
| Syntax | Boolean |
| Example | nsslapd-pluginAllowReplUpdates: off |
Chapter 7. Schema definitions
The directory schema is a set of rules that defines how data can be stored in the directory. Directory information is stored discrete entries, and each entry is comprised of a set of attributes and their values. The kind of identity being described in the entry is defined in the entry’s object classes. An object class specifies the kind of object the entry describes through the defined set of attributes for the object class.
Basically, the schema files are lists of the kinds of entries that can be create (the object classes) and the ways that those entries can be described (the attributes). The schema defines what the object classes and attributes are. The schema also defines the format that the attribute values contain (the attribute’s syntax) and whether there can only be a single instance of that attribute.
Additional schema files can be added to the Directory Server configuration and loaded in the server, so the schema is customizable and can be extended as required.
The Directory Server fails to start if the schema definitions contain too few or too many characters. Use exactly one space in those places where the LDAP standards allow the use of zero or many spaces; for example, the place between the NAME keyword and the name of an attribute type.
7.1. Object classes
In LDAP, an object class defines the set of attributes that can be used to define an entry. The LDAP standard provides object classes for many common types of entries, such as people (person and inetOrgPerson), groups (groupOfUniqueNames), locations (locality), organizations and divisions (organization and organizationalUnit), and equipment (device).
In a schema file, an object class is identified by the objectclasses line, then followed by its OID, name, a description, its direct superior object class (an object class which is required to be used in conjunction with the object class and which shares its attributes with this object class), and the list of required (MUST) and allowed (MAY) attributes. This is shown in the following example:
Example 7.1. person Object Class Schema Entry
objectClasses: ( 2.5.6.6 NAME 'person' DESC 'Standard LDAP objectclass' SUP top MUST ( sn $ cn ) MAY ( description $ seeAlso $ telephoneNumber $ userPassword ) X-ORIGIN 'RFC 2256' )
objectClasses: ( 2.5.6.6 NAME 'person' DESC 'Standard LDAP objectclass' SUP top MUST ( sn $ cn ) MAY ( description $ seeAlso $ telephoneNumber $ userPassword ) X-ORIGIN 'RFC 2256' )7.1.1. Required and allowed attributes
Every object class defines a number of required attributes and of allowed attributes. Required attributes must be present in entries using the specified object class, while allowed attributes are permissible and available for the entry to use, but are not required for the entry to be valid.
As in Example 7.1, “person Object Class Schema Entry”, the person object class requires the cn, sn, and objectClass attributes and allows the description, seeAlso, telephoneNumber, and userPassword attributes.
All entries require the objectClass attribute, which lists the object classes assigned to the entry.
7.1.2. Object class inheritance
An entry can have more than one object class. For example, the entry for a person is defined by the person object class, but the same person may also be described by attributes in the inetOrgPerson and organizationalPerson object classes.
Additionally, object classes can be hierarchical. An object class can inherit attributes from another class, in addition to its own required and allowed attributes. The second object class is the superior object class of the first.
The server’s object class structure determines the list of required and allowed attributes for a particular entry. For example, a user’s entry has to have the inetOrgPerson object class. In that case, the entry must also include the superior object class for inetOrgPerson, organizationalPerson, and the superior object class for organizationalPerson, which is person:
objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetOrgPerson
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
When the inetOrgPerson object class is assigned to an entry, the entry automatically inherits the required and allowed attributes from the superior object classes.
7.2. Attributes
Directory entries are composed of attributes and their values. These pairs are called attribute-value assertions or AVAs. Any piece of information in the directory is associated with a descriptive attribute. For instance, the cn attribute is used to store a person’s full name, such as cn: John Smith.
Additional attributes can supply additional information about John Smith:
givenname: John surname: Smith mail: jsmith@example.com
givenname: John
surname: Smith
mail: jsmith@example.com
In a schema file, an attribute is identified by the attributetypes line, then followed by its OID, name, a description, syntax (allowed format for its value), optionally whether the attribute is single- or multi-valued, and where the attribute is defined.
This is shown in the following example:
Example 7.2. description Attribute Schema Entry
attributetypes: ( 2.5.4.13 NAME 'description' DESC 'Standard LDAP attribute type' SYNTAX 1.3.6.1.4.1.1466.115.121.1.15 X-ORIGIN 'RFC 2256' )
attributetypes: ( 2.5.4.13 NAME 'description' DESC 'Standard LDAP attribute type' SYNTAX 1.3.6.1.4.1.1466.115.121.1.15 X-ORIGIN 'RFC 2256' )Some attributes can be abbreviated. These abbreviations are listed as part of the attribute definition:
attributetypes: ( 2.5.4.3 NAME ( 'cn' 'commonName' ) ...
attributetypes: ( 2.5.4.3 NAME ( 'cn' 'commonName' ) ...7.2.1. Directory Server attribute syntaxes
The attribute’s syntax defines the format of the values which the attribute allows; as with other schema elements, the syntax is defined for an attribute using the syntax’s OID in the schema file entry.
The Directory Server uses the attribute’s syntax to perform sorting and pattern matching on entries.
For more information about LDAP attribute syntaxes, see RFC 4517.
| Name | OID | Definition |
|---|---|---|
| Binary | 1.3.6.1.4.1.1466.115.121.1.5 | Deprecated. Use Octet string instead. |
| Bit String | 1.3.6.1.4.1.1466.115.121.1.6 |
For values which are bitstings, such as |
| Boolean | 1.3.6.1.4.1.1466.115.121.1.7 | For attributes with only two allowed values, TRUE or FALSE. |
| Country String | 1.3.6.1.4.1.1466.115.121.1.11 | For values which are limited to exactly two printable string characters; for example, US for the United States. |
| DN | 1.3.6.1.4.1.1466.115.121.1.12 | For values which are distinguished names (DNs). |
| Delivery Method | 1.3.6.1.4.1.1466.115.121.1.14 | For values which are contained a preferred method of delivering information or contacting an entity. The different values are separated by a dollar sign ($). For example: [literal,subs="+quotes",options="nowrap",role=white-space-pre] …. telephone $ physical …. |
| Directory String | 1.3.6.1.4.1.1466.115.121.1.15 | For values which are valid UTF-8 strings. These values are not necessarily case-insensitive. Both case-sensitive and case-insensitive matching rules are available for Directory String and related syntaxes. |
| Enhanced Guide | 1.3.6.1.4.1.1466.115.121.1.21 | For values which contain complex search parameters based on attributes and filters. |
| Facsimile | 1.3.6.1.4.1.1466.115.121.1.22 | For values which contain fax numbers. |
| Fax | 1.3.6.1.4.1.1466.115.121.1.23 | For values which contain the images of transmitted faxes. |
| Generalized Time | 1.3.6.1.4.1.1466.115.121.1.24 | For values which are encoded as printable strings. The time zone must be specified. It is strongly recommended to use GMT time. |
| Guide | 1.3.6.1.4.1.1466.115.121.1.25 | Obsolete. For values which contain complex search parameters based on attributes and filters. |
| IA5 String | 1.3.6.1.4.1.1466.115.121.1.26 | For values which are valid strings. These values are not necessarily case-insensitive. Both case-sensitive and case-insensitive matching rules are available for IA5 String and related syntaxes. |
| Integer | 1.3.6.1.4.1.1466.115.121.1.27 | For values which are whole numbers. |
| JPEG | 1.3.6.1.4.1.1466.115.121.1.28 | For values which contain image data. |
| Name and Optional UID | 1.3.6.1.4.1.1466.115.121.1.34 | For values which contain a combination value of a DN and (optional) unique ID. |
| Numeric String | 1.3.6.1.4.1.1466.115.121.1.36 | For values which contain a string of both numerals and spaces. |
| OctetString | 1.3.6.1.4.1.1466.115.121.1.40 | For values which are binary; this replaces the binary syntax. |
| Object Class Description | 1.3.6.1.4.1.1466.115.121.1.37 | For values which contain object class definitions. |
| OID | 1.3.6.1.4.1.1466.115.121.1.38 | For values which contain OID definitions. |
| Postal Address | 1.3.6.1.4.1.1466.115.121.1.41 |
For values which are encoded in the format [literal,subs="+quotes",options="nowrap",role=white-space-pre] …. 1234 Main St.$Raleigh, NC 12345$USA …. Each dstring component is encoded as a DirectoryString value. Backslashes and dollar characters, if they occur, are quoted, so that they will not be mistaken for line delimiters. Many servers limit the postal address to 6 lines of up to thirty characters. |
| Printable String | 1.3.6.1.4.1.1466.115.121.1.44 | For values which contain printable strings. |
| Space-Insensitive String | 2.16.840.1.113730.3.7.1 | For values which contain space-insensitive strings. |
| TelephoneNumber | 1.3.6.1.4.1.1466.115.121.1.50 | For values which are in the form of telephone numbers. It is recommended to use telephone numbers in international form. |
| Teletex Terminal Identifier | 1.3.6.1.4.1.1466.115.121.1.51 | For values which contain an international telephone number. |
| Telex Number | 1.3.6.1.4.1.1466.115.121.1.52 | For values which contain a telex number, country code, and answerback code of a telex terminal. |
| URI |
For values in the form of a URL, introduced by a string such as |
7.2.2. Single- and multi-valued attributes
By default, most attributes are multi-valued. This means that an entry can contain the same attribute multiple times, with different values. For example:
dn: uid=jsmith,ou=marketing,ou=people,dc=example,dc=com ou: marketing ou: people
dn: uid=jsmith,ou=marketing,ou=people,dc=example,dc=com
ou: marketing
ou: people
The cn, tel, and objectclass attributes, for example, all can have more than one value. Attributes that are single-valued — that is, only one instance of the attribute can be specified — are specified in the schema as only allowing a single value. For example, uidNumber can only have one possible value, so its schema entry has the term SINGLE-VALUE. If the attribute is multi-valued, there is no value expression.
DIRSRV-307 :_content-type: REFERENCE
7.3. Default Directory Server schema files
Template schema definitions for Directory Server are stored in the /etc/dirsrv/schema directory. These default schema files are used to generate the schema files for new Directory Server instances. Each server instance has its own instance-specific schema directory in /etc/dirsrv/slapd-instance/schema. The schema files in the instance directory are used only by that instance.
To modify the directory schema, create new attributes and new object classes in the instance-specific schema directory. Because the default schema is used for creating new instances and each individual instance has its own schema files, it is possible to have slightly different schema for each instance, matching the use of each instance.
Any custom attributes added using LDAP commands are stored in the 99user.ldif file; other custom schema files can be added to the /etc/dirsrv/slapd-instance/schema directory for each instance. Do not make any modifications with the standard files that come with Red Hat Directory Server.
| Schema File | Purpose |
|---|---|
| 00core.ldif | Recommended core schema from the X.500 and LDAP standards (RFCs). This schema is used by Directory Server itself for the instance configuration and to start the server instance. |
| 01core389.ldif | Recommended core schema from the X.500 and LDAP standards (RFCs). This schema is used by Directory Server itself for the instance configuration and to start the server instance. |
| 02common.ldif | Standard-related schema from RFC 2256, LDAPv3, and standard schema defined by Directory Server which is used to configure entries. |
| 05rfc2927.ldif | Schema from RFC 2927, "MIME Directory Profile for LDAP Schema." |
| 05rfc4523.ldif | Schema definitions for X.509 certificates. |
| 05rfc4524.ldif | Cosine LDAP/X.500 schema. |
| 06inetorgperson.ldif | inetorgperson schema elements from RFC 2798, RFC 2079, and part of RFC 1274. |
| 10rfc2307.ldif | Schema from RFC 2307, "An Approach for Using LDAP as a Network Information Service." |
| 20subscriber.ldif | Common schema element for Directory Server-Nortel subscriber interoperability. |
| 25java-object.ldif | Schema from RFC 2713, "Schema for Representing Java Objects in an LDAP Directory." |
| 28pilot.ldif | Schema from the pilot RFCs, especially RFC 1274, that are no longer recommended for use in new deployments. |
| 30ns-common.ldif | Common schema. |
| 50ns-admin.ldif | Schemas used by the Administration Server. |
| 50ns-certificate.ldif | Schemas used by Red Hat Certificate System. |
| 50ns-directory.ldif | Schema used by legacy Directory Server 4.x servers. |
| 50ns-mail.ldif | Schema for mail servers. |
| 50ns-value.ldif | Schema for value items in Directory Server. |
| 50ns-web.ldif | Schema for web servers. |
| 60autofs.ldif | Object classes for automount configuration; this is one of several schema files used for NIS servers. |
| 60eduperson.ldif | Schema elements for education-related people and organization entries. |
| 60mozilla.ldif | Schema elements for Mozilla-related user profiles. |
| 60nss-ldap.ldif | Schema elements for GSS-API service names. |
| 60pam-plugin.ldif | Schema elements for integrating directory services with PAM modules. |
| 60pureftpd.ldif | Schema elements for defining FTP user accounts. |
| 60rfc2739.ldif | Schema elements for calendars and vCard properties. |
| 60rfc3712.ldif | Schema elements for configuring printers. |
| 60sabayon.ldif | Schema elements for defining sabayon user entries. |
| 60sudo.ldif | Schema elements for defining sudo users and roles. |
| 60trust.ldif | Schema elements for defining trust relationships for NSS or PAM. |
| 99user.ldif | Custom schema elements |
7.4. Object identifiers
All schema elements have object identifiers (OIDs) assigned to them, including attributes and object classes. An OID is a sequence of integers, usually written as a dot-separated string. All custom attributes and classes must conform to the X.500 and LDAP standards.
If an OID is not specified for a schema element, Directory Server automatically uses ObjectClass_name-oid and attribute_name-oid. However, using text OIDs instead of numeric OIDs can lead to problems with clients, server interoperability, and server behavior, assigning a numeric OID is strongly recommended.
OIDs can be built on. The base OID is a root number which is used for every schema element for an organization, and then schema elements can be incremented from there. For example, a base OID could be 1. The company then uses 1.1 for attributes, so every new attribute has an OID of 1.1.x. It uses 1.2 for object classes, so every new object class has an OID of 1.2.x.
For Directory Server-defined schema elements, the base OIDs are as follows:
-
The Netscape base OID is
2.16.840.1.113730. -
The Directory Server base OID is
2.16.840.1.113730.3. -
All Netscape-defined attributes have the base OID
2.16.840.1.113370.3.1. -
All Netscape-defined object classes have the base OID
2.16.840.1.113730.3.2.
For more information about OIDs or to request a prefix, go to the Internet Assigned Number Authority (IANA) website at http://www.iana.org/.
7.5. Extending the schema
The Directory Server schema includes hundreds of object classes and attributes that can be used to meet most of directory requirements. This schema can be extended with new object classes and attributes that meet evolving requirements for the directory service in the enterprise by creating custom schema files.
When adding new attributes to the schema, a new object class should be created to contain them. Adding a new attribute to an existing object class can compromise Directory Server’s compatibility with existing LDAP clients that rely on the standard LDAP schema and may cause difficulties when upgrading the server.
7.6. Schema checking
Schema checking means that Directory Server checks every entry when it is created, modified, or in a database imported using LDIF to make sure that it complies with the schema definitions in the schema files. Schema checking verifies three things:
- Object classes and attributes used in the entry are defined in the directory schema.
- Attributes required for an object class are contained in the entry.
- Only attributes allowed by the object class are contained in the entry.
You should run Directory Server with schema checking turned on.
7.7. Syntax validation
Syntax validation means that Directory Server checks that the value of an attribute matches the required syntax for that attribute. For example, syntax validation will confirm that a new telephoneNumber attribute actually has a valid telephone number for its value.
With its basic configuration, syntax validation (like schema checking) will check any directory modification to make sure the attribute value matches the required syntax and will reject any modifications that violate the syntax. Optionally, syntax validation can be configured to log warning messages about syntax violations, and either reject the change or allow the modification process to succeed.
All syntaxes are validated against RFC 4514, except for DNs. By default, DNs are validated against RFC 1779 or RFC 2253, which are less strict than RFC 4514. Strict validation for DNs has to be explicitly configured.
This feature checks all attribute syntaxes, with the exception of binary syntaxes (which cannot be verified) and non-standard syntaxes, which do not have a defined required format. The unvalidated syntaxes are as follows:
- Fax (binary)
- OctetString (binary)
- JPEG (binary)
- Binary (non-standard)
- Space Insensitive String (non-standard)
- URI (non-standard)
When syntax validation is enabled, new attribute values are checked whenever an attribute is added or modified to an entry. (This does not include replication changes, since the syntax would have been checked on the supplier server.)
Chapter 8. Entry attribute reference
The attributes listed in this reference are manually assigned or available to directory entries. The attributes are listed in alphabetical order with their definition, syntax, and OID.
8.1. abstract
The abstract attribute contains an abstract for a document entry.
| OID | 0.9.2342.19200300.102.1.9 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.2. accessTo
This attribute defines what specific hosts or servers a user is allowed to access.
| OID | 5.3.6.1.1.1.1.1 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | nss_ldap/pam_ldap |
8.3. accountInactivityLimit
The accountInactivityLimit attribute sets the time period, in seconds, from the last login time of an account before that account is locked for inactivity.
| OID | 1.3.6.1.4.1.11.1.3.2.1.3 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
8.4. acctPolicySubentry
The acctPolicySubentry attribute identifies any entry which belongs to an account policy (specifically, an account lockout policy). The value of this attribute points to the account policy which is applied to the entry.
This can be set on an individual user entry or on a CoS template entry or role entry.
| OID | 1.3.6.1.4.1.11.1.3.2.1.2 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
8.5. administratorContactInfo
This attribute contains the contact information for the LDAP or server administrator.
| OID | 2.16.840.1.113730.3.1.74 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.6. adminRole
This attribute contains the role assigned to the user identified in the entry.
| OID | 2.16.840.1.113730.3.1.601 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape Administration Services |
8.7. adminUrl
This attribute contains the URL of the Administration Server.
| OID | 2.16.840.1.113730.3.1.75 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.8. aliasedObjectName
The aliasedObjectName attribute is used by Directory Server to identify alias entries. This attribute contains the DN (distinguished name) for the entry for which this entry is the alias. For example:
aliasedObjectName: uid=jdoe,ou=people,dc=example,dc=com
aliasedObjectName: uid=jdoe,ou=people,dc=example,dc=com| OID | 2.5.4.1 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.9. associatedDomain
The associatedDomain attribute contains the DNS domain associated with the entry in the directory tree. For example, the entry with the distinguished name c=US,o=Example Corporation has the associated domain of EC.US. These domains should be represented in RFC 822 order.
associatedDomain:US
associatedDomain:US| OID | 0.9.2342.19200300.100.1.37 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.10. associatedName
The associatedName identifies an organizational directory tree entry associated with a DNS domain. For example:
associatedName: c=us
associatedName: c=us| OID | 0.9.2342.19200300.100.1.38 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.11. attributeTypes
This attribute is used in a schema file to identify an attribute defined within the subschema.
| OID | 2.5.21.5 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.12. audio
The audio attribute contains a sound file using a binary format. This attribute uses a u-law encoded sound data. For example:
audio:: AAAAAA==
audio:: AAAAAA==| OID | 0.9.2342.19200300.100.1.55 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.13. authorCn
The authorCn attribute contains the common name of the document’s author. For example:
authorCn: John Smith
authorCn: John Smith| OID | 0.9.2342.19200300.102.1.11 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.14. authorityRevocationList
The authorityRevocationList attribute contains a list of revoked CA certificates. This attribute should be requested and stored in a binary format, like authorityRevocationList;binary. For example:
authorityrevocationlist;binary:: AAAAAA==
authorityrevocationlist;binary:: AAAAAA==| OID | 2.5.4.38 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.15. authorSn
The authorSn attribute contains the last name or family name of the author of a document entry. For example:
authorSn: Smith
authorSn: Smith| OID | 0.9.2342.19200300.102.1.12 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.16. automountInformation
This attribute contains information used by the autofs automounter.
The automountInformation attribute is defined in 60autofs.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 60autofs.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.33 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.17. bootFile
This attribute contains the boot image file name.
The bootFile attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.24 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.18. bootParameter
This attribute contains the value for rpc.bootparamd.
The bootParameter attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.23 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.19. buildingName
The buildingName attribute contains the building name associated with the entry. For example:
buildingName: 14
buildingName: 14| OID | 0.9.2342.19200300.100.1.48 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.20. businessCategory
The businessCategory attribute identifies the type of business in which the entry is engaged. The attribute value should be a broad generalization, such as a corporate division level. For example:
businessCategory: Engineering
businessCategory: Engineering| OID | 2.5.4.15 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.21. cACertificate
The cACertificate attribute contains a CA certificate. The attribute should be requested and stored binary format, such as cACertificate;binary. For example:
cACertificate;binary:: AAAAAA==
cACertificate;binary:: AAAAAA==| OID | 2.5.4.37 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.22. c
The countryName, or c, attribute contains the two-character country code to represent the country names. The country codes are defined by the ISO. For example:
countryName: GB c: US
countryName: GB
c: US| OID | 2.5.4.6 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.23. carLicense
The carLicense attribute contains an entry’s automobile license plate number. For example:
carLicense: 6ABC246
carLicense: 6ABC246| OID | 2.16.840.1.113730.3.1.1 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.24. certificateRevocationList
The certificateRevocationList attribute contains a list of revoked user certificates. The attribute value is to be requested and stored in binary form, as certificateACertificate;binary. For example:
certificateRevocationList;binary:: AAAAAA==
certificateRevocationList;binary:: AAAAAA==| OID | 2.5.4.39 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.25. cn
The commonName attribute contains the name of an entry. For user entries, the cn attribute is typically the person’s full name. For example:
commonName: John Smith cn: Bill Anderson
commonName: John Smith
cn: Bill Anderson
With the LDAPReplica or LDAPServerobject object classes, the cn attribute value has the following format:
cn: replicater.example.com:17430/dc%3Dexample%2Cdc%3com
cn: replicater.example.com:17430/dc%3Dexample%2Cdc%3com| OID | 2.5.4.3 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.26. co
The friendlyCountryName attribute contains a country name; this can be any string. Often, the country is used with the ISO-designated two-letter country code, while the co attribute contains a readable country name. For example:
friendlyCountryName: Ireland co: Ireland
friendlyCountryName: Ireland
co: Ireland| OID | 0.9.2342.19200300.100.1.43 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.27. cosAttribute
The cosAttribute contains the name of the attribute for which to generate a value for the CoS. There can be more than one cosAttribute value specified. This attribute is used by all types of CoS definition entries.
| OID | 2.16.840.1.113730.3.1.550 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.28. cosIndirectSpecifier
The cosIndirectSpecifier specifies the attribute values used by an indirect CoS to identify the template entry.
| OID | 2.16.840.1.113730.3.1.577 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
8.29. cosPriority
The cosPriority attribute specifies which template provides the attribute value when CoS templates compete to provide an attribute value. This attribute represents the global priority of a template. A priority of zero is the highest priority.
| OID | 2.16.840.1.113730.3.1.569 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
8.30. cosSpecifier
The cosSpecifier attribute contains the attribute value used by a classic CoS, which, along with the template entry’s DN, identifies the template entry.
| OID | 2.16.840.1.113730.3.1.551 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
8.31. cosTargetTree
The cosTargetTree attribute defines the subtrees to which the CoS schema applies. The values for this attribute for the schema and for multiple CoS schema may overlap their target trees arbitrarily.
| OID | 2.16.840.1.113730.3.1.552 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
8.32. cosTemplateDn
The cosTemplateDn attribute contains the DN of the template entry which contains a list of the shared attribute values. Changes to the template entry attribute values are automatically applied to all the entries within the scope of the CoS. A single CoS might have more than one template entry associated with it.
| OID | 2.16.840.1.113730.3.1.553 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
8.33. crossCertificatePair
The value for the crossCertificatePair attribute must be requested and stored in binary format, such as certificateCertificateRepair;binary. For example:
crossCertificatePair;binary:: AAAAAA==
crossCertificatePair;binary:: AAAAAA==| OID | 2.5.4.40 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.34. dc
The dc attribute contains one component of a domain name. For example:
dc: example domainComponent: example
dc: example
domainComponent: example| OID | 0.9.2342.19200300.100.1.25 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.35. deltaRevocationList
The deltaRevocationList attribute contains a certificate revocation list (CRL). The attribute value is requested and stored in binary format, such as deltaRevocationList;binary.
| OID | 2.5.4.53 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.36. departmentNumber
The departmentNumber attribute contains an entry’s department number. For example:
departmentNumber: 2604
departmentNumber: 2604| OID | 2.16.840.1.113730.3.1.2 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.37. description
The description attribute provides a human-readable description for an entry. For person or organization object classes, this can be used for the entry’s role or work assignment. For example:
description: Quality control inspector for the ME2873 product line.
description: Quality control inspector for the ME2873 product line.| OID | 2.5.4.13 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.38. destinationIndicator
The destinationIndicator attribute contains the city and country associated with the entry. This attribute was once required to provide public telegram service and is generally used in conjunction with the registeredAddress attribute. For example:
destinationIndicator: Stow, Ohio, USA
destinationIndicator: Stow, Ohio, USA| OID | 2.5.4.27 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.39. displayName
The displayName attributes contains the preferred name of a person to use when displaying that person’s entry. This is especially useful for showing the preferred name for an entry in a one-line summary list. Since other attribute types, such as cn, are multi-valued, they cannot be used to display a preferred name. For example:
displayName: John Smith
displayName: John Smith| OID | 2.16.840.1.113730.3.1.241 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.40. dITRedirect
The dITRedirect attribute indicates that the object described by one entry now has a newer entry in the directory tree. This attribute may be used when an individual’s place of work changes, and the individual acquires a new organizational DN.
dITRedirect: cn=jsmith,dc=example,dc=com
dITRedirect: cn=jsmith,dc=example,dc=com| OID | 0.9.2342.19200300.100.1.54 |
| Syntax | DN |
| Defined in |
8.41. dmdName
The dmdName attribute value specifies a directory management domain (DMD), the administrative authority that operates Directory Server.
| OID | 2.5.4.54 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.42. dn
The dn attribute contains an entry’s distinguished name. For example:
dn: uid=Barbara Jensen,ou=Quality Control,dc=example,dc=com
dn: uid=Barbara Jensen,ou=Quality Control,dc=example,dc=com| OID | 2.5.4.49 |
| Syntax | DN |
| Defined in |
8.43. dNSRecord
The dNSRecord attribute contains DNS resource records, including type A (Address), type MX (Mail Exchange), type NS (Name Server), and type SOA (Start of Authority) resource records. For example:
dNSRecord: IN NS ns.uu.net
dNSRecord: IN NS ns.uu.net| OID | 0.9.2342.19200300.100.1.26 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet Directory Pilot |
8.44. documentAuthor
The documentAuthor attribute contains the DN of the author of a document entry. For example:
documentAuthor: uid=Barbara Jensen,ou=People,dc=example,dc=com
documentAuthor: uid=Barbara Jensen,ou=People,dc=example,dc=com| OID | 0.9.2342.19200300.100.1.14 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.45. documentIdentifier
The documentIdentifier attribute contains a unique identifier for a document. For example:
documentIdentifier: L3204REV1
documentIdentifier: L3204REV1| OID | 0.9.2342.19200300.100.1.11 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.46. documentLocation
The documentLocation attribute contains the location of the original version of a document. For example:
documentLocation: Department Library
documentLocation: Department Library| OID | 0.9.2342.19200300.100.1.15 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.47. documentPublisher
The documentPublisher attribute contains the person or organization who published a document. For example:
documentPublisher: Southeastern Publishing
documentPublisher: Southeastern Publishing| OID | 0.9.2342.19200300.100.1.56 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.48. documentStore
The documentStore attribute contains information on where the document is stored.
| OID | 0.9.2342.19200300.102.1.10 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.49. documentTitle
The documentTitle attribute contains a document’s title. For example:
documentTitle: Installing Red Hat Directory Server
documentTitle: Installing Red Hat Directory Server| OID | 0.9.2342.19200300.100.1.12 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.50. documentVersion
The documentVersion attribute contains the current version number for the document. For example:
documentVersion: 1.1
documentVersion: 1.1| OID | 0.9.2342.19200300.100.1.13 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.51. drink
The favouriteDrink attribute contains a person’s favorite beverage. This can be shortened to drink. For example:
favouriteDrink: iced tea drink: cranberry juice
favouriteDrink: iced tea
drink: cranberry juice| OID | 0.9.2342.19200300.100.1.5 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.52. dSAQuality
The dSAQuality attribute contains the rating of the directory system agents' (DSA) quality. This attribute allows a DSA manager to indicate the expected level of availability of the DSA. For example:
dSAQuality: high
dSAQuality: high| OID | 0.9.2342.19200300.100.1.49 |
| Syntax | Directory-String |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.53. employeeNumber
The employeeNumber attribute contains the employee number for the person. For example:
employeeNumber: 3441
employeeNumber: 3441| OID | 2.16.840.1.113730.3.1.3 |
| Syntax | Directory-String |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.54. employeeType
The employeeType attribute contains the employment type for the person. For example:
employeeType: Full time
employeeType: Full time| OID | 2.16.840.1.113730.3.1.4 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.55. enhancedSearchGuide
The enhancedSearchGuide attribute contains information used by an X.500 client to construct search filters. For example:
enhancedSearchGuide: (uid=bjensen)
enhancedSearchGuide: (uid=bjensen)| OID | 2.5.4.47 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.56. fax
The facsimileTelephoneNumber attribute contains the entry’s facsimile number; this attribute can be abbreviated as fax. For example:
facsimileTelephoneNumber: +1 415 555 1212 fax: +1 415 555 1212
facsimileTelephoneNumber: +1 415 555 1212
fax: +1 415 555 1212| OID | 2.5.4.23 |
| Syntax | TelephoneNumber |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.57. gecos
The gecos attribute is used to determine the GECOS field for the user. This is comparable to the cn attribute, although using a gecos attribute allows additional information to be embedded in the GECOS field aside from the common name. This field is also useful if the common name stored in the directory is not the user’s full name.
gecos: John Smith
gecos: John Smith
The gecos attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.2 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.58. generationQualifier
The generationQualifier attribute contains the generation qualifier for a person’s name, which is usually appended as a suffix to the name. For example:
generationQualifier:III
generationQualifier:III| OID | 2.5.4.44 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.59. gidNumber
The gidNumber attribute contains a unique numeric identifier for a group entry or to identify the group for a user entry. This is analogous to the group number in Unix.
gidNumber: 100
gidNumber: 100
The gidNumber attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.1 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.60. givenName
The givenName attribute contains an entry’s given name, which is usually the first name. For example:
givenName: Rachel
givenName: Rachel| OID | 2.5.4.42 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.61. homeDirectory
The homeDirectory attribute contains the path to the user’s home directory.
homeDirectory: /home/jsmith
homeDirectory: /home/jsmith
The homeDirectory attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.3 |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.62. homePhone
The homePhone attribute contains the entry’s residential phone number. For example:
homePhone: 415-555-1234
homePhone: 415-555-1234
Although RFC 1274 defines both homeTelephoneNumber and homePhone as names for the residential phone number attribute, Directory Server only implements the homePhone name.
| OID | 0.9.2342.19200300.100.1.20 |
| Syntax | TelephoneNumber |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.63. homePostalAddress
The homePostalAddress attribute contains an entry’s home mailing address. Since this attribute generally spans multiple lines, each line break has to be represented by a dollar sign ($). To represent an actual dollar sign ($) or backslash (\) in the attribute value, use the escaped hex values \24 and \5c, respectively. For example:
homePostalAddress: 1234 Ridgeway Drive$Santa Clara, CA$99555
homePostalAddress: 1234 Ridgeway Drive$Santa Clara, CA$99555To represent the following string:
The dollar ($) value can be found in the c:\cost file.
The dollar ($) value can be found
in the c:\cost file.The entry value is:
The dollar (\24) value can be found$in the c:\c5cost file.
The dollar (\24) value can be found$in the c:\c5cost file.| OID | 0.9.2342.19200300.100.1.39 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.64. host
The host contains the host name of a computer. For example:
host: labcontroller01
host: labcontroller01| OID | 0.9.2342.19200300.100.1.9 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.65. houseIdentifier
The houseIdentifier contains an identifier for a specific building at a location. For example:
houseIdentifier: B105
houseIdentifier: B105| OID | 2.5.4.51 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.66. inetDomainBaseDN
This attribute identifies the base DN of user subtree for a DNS domain.
| OID | 2.16.840.1.113730.3.1.690 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Subscriber interoperability |
8.67. inetDomainStatus
This attribute shows the current status of the domain. A domain has a status of active, inactive, or deleted.
| OID | 2.16.840.1.113730.3.1.691 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Subscriber interoperability |
8.68. inetSubscriberAccountId
This attribute contains the a unique attribute used to link the user entry for the subscriber to a billing system.
| OID | 2.16.840.1.113730.3.1.694 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Subscriber interoperability |
8.69. inetSubscriberChallenge
The inetSubscriberChallenge attribute contains some kind of question or prompt, the challenge phrase, which is used to confirm the identity of the user in the subscriberIdentity attribute. This attribute is used in conjunction with the inetSubscriberResponse attribute, which contains the response to the challenge.
| OID | 2.16.840.1.113730.3.1.695 |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in | Subscriber interoperability |
8.70. inetSubscriberResponse
The inetSubscriberResponse attribute contains the answer to the challenge question in the inetSubscriberChallenge attribute to verify the user in the subscriberIdentity attribute.
| OID | 2.16.840.1.113730.3.1.696 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Subscriber interoperability |
8.71. inetUserHttpURL
This attribute contains the web addresses associated with the user.
| OID | 2.16.840.1.113730.3.1.693 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Subscriber interoperability |
8.72. inetUserStatus
This attribute shows the current status of the user (subscriber). A user has a status of active, inactive, or deleted.
| OID | 2.16.840.1.113730.3.1.692 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-Valued |
| Defined in | Subscriber interoperability |
8.73. info
The info attribute contains any general information about an object. Avoid using this attribute for specific information and rely instead on specific, possibly custom, attribute types. For example:
info: not valid
info: not valid| OID | 0.9.2342.19200300.100.1.4 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.74. initials
The initials contains a person’s initials; this does not contain the entry’s surname. For example:
initials: BAJ
initials: BAJ
Directory Server and Active Directory handle the initials attribute differently. The Directory Server allows a practically unlimited number of characters, while Active Directory has a restriction of six characters. If an entry is synced with a Windows peer and the value of the initials attribute is longer than six characters, then the value is automatically truncated to six characters when it is synchronized. There is no information written to the error log to indicate that synchronization changed the attribute value, either.
| OID | 2.5.4.43 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.75. installationTimeStamp
This contains the time that the server instance was installed.
| OID | 2.16.840.1.113730.3.1.73 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-Valued |
| Defined in | Netscape Administration Services |
8.76. internationalISDNNumber
The internationalISDNNumber attribute contains the ISDN number of a document entry. This attribute uses the internationally recognized format for ISDN addresses given in CCITT Rec. E. 164.
| OID | 2.5.4.25 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.77. ipHostNumber
This contains the IP address for a server.
The ipHostNumber attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.19 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-Valued |
| Defined in |
8.78. ipNetmaskNumber
This contains the IP netmask for the server.
The ipHostNumber attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 2.16.840.1.113730.3.1.73 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-Valued |
| Defined in |
8.79. ipNetworkNumber
This identifies the IP network.
The ipNetworkNumber attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.20 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-Valued |
| Defined in |
8.80. ipProtocolNumber
This attribute identifies the IP protocol version number.
The ipProtocolNumber attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.17 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-Valued |
| Defined in |
8.81. ipServicePort
This attribute gives the port used by the IP service.
The ipServicePort attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.15 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-Valued |
| Defined in |
8.82. ipServiceProtocol
This identifies the protocol used by the IP service.
The ipServiceProtocol attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.16 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-Valued |
| Defined in |
8.83. janetMailbox
The janetMailbox contains a JANET email address, usually for users located in the United Kingdom who do not use RFC 822 email address. Entries with this attribute must also contain the rfc822Mailbox attribute.
| OID | 0.9.2342.19200300.100.1.46 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.84. jpegPhoto
The jpegPhoto attribute contains a JPEG photo, a binary value. For example:
jpegPhoto:: AAAAAA==
jpegPhoto:: AAAAAA==| OID | 0.9.2342.19200300.100.1.60 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.85. keyWords
The keyWord attribute contains keywords associated with the entry. For example:
keyWords: directory LDAP X.500
keyWords: directory LDAP X.500| OID | 0.9.2342.19200300.102.1.7 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.86. knowledgeInformation
This attribute is no longer used.
| OID | 2.5.4.2 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.87. labeledURI
The labeledURI contains a Uniform Resource Identifier (URI) which is related, in some way, to the entry. Values placed in the attribute should consist of a URI (currently only URLs are supported), optionally followed by one or more space characters and a label.
labeledURI: http://home.example.com labeledURI: http://home.example.com Example website
labeledURI: http://home.example.com
labeledURI: http://home.example.com Example website| OID | 1.3.6.1.4.1.250.1.57 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.88. l
The localityName, or l, attribute contains the county, city, or other geographical designation associated with the entry. For example:
localityName: Santa Clara l: Santa Clara
localityName: Santa Clara
l: Santa Clara| OID | 2.5.4.7 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.89. loginShell
The loginShell attribute contains the path to a script that is launched automatically when a user logs into the domain.
loginShell: c:\scripts\jsmith.bat
loginShell: c:\scripts\jsmith.bat
The loginShell attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.4 |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.90. macAddress
This attribute gives the MAC address for a server or piece of equipment.
The macAddress attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.22 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.91. mailAccessDomain
This attribute lists the domain which a user can use to access the messaging server.
| OID | 2.16.840.1.113730.3.1.12 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.92. mail
The mail attribute contains a user’s primary email address. This attribute value is retrieved and displayed by whitepage applications. For example:
mail: jsmith@example.com
mail: jsmith@example.com| OID | 0.9.2342.19200300.100.1.3 |
| Syntax | DirectyString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.93. mailAlternateAddress
The mailAlternateAddress attribute contains additional email addresses for a user. This attribute does not reflect the default or primary email address; that email address is set by the mail attribute.
For example:
mailAlternateAddress: jsmith@example.com mailAlternateAddress: smith1701@alt.com
mailAlternateAddress: jsmith@example.com
mailAlternateAddress: smith1701@alt.com| OID | 2.16.840.1.113730.3.1.13 |
| Syntax | DirectyString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.94. mailAutoReplyMode
This attribute sets whether automatic replies are enabled for the messaging server.
| OID | 2.16.840.1.113730.3.1.14 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.95. mailAutoReplyText
This attribute stores the text to used in an auto-reply email.
| OID | 2.16.840.1.113730.3.1.15 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.96. mailDeliveryOption
This attribute defines the mail delivery mechanism to use for the mail user.
| OID | 2.16.840.1.113730.3.1.16 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.97. mailEnhancedUniqueMember
This attribute contains the DN of a unique member of a mail group.
| OID | 2.16.840.1.113730.3.1.31 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.98. mailForwardingAddress
This attribute contains an email address to which to forward a user’s email.
| OID | 2.16.840.1.113730.3.1.17 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.99. mailHost
The mailHost attribute contains the host name of a mail server. For example:
mailHost: mail.example.com
mailHost: mail.example.com| OID | 2.16.840.1.113730.3.1.18 |
| Syntax | DirectyString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.100. mailMessageStore
This identifies the location of a user’s email box.
| OID | 2.16.840.1.113730.3.1.19 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.101. mailPreferenceOption
The mailPreferenceOption defines whether a user should be included on a mailing list, both electronic and physical. There are three options.
| 0 | Does not appear in mailing lists. |
| 1 | Add to any mailing lists. |
| 2 | Added only to mailing lists which the provider views as relevant to the user interest. |
If the attribute is absent, then the default is to assume that the user is not included on any mailing list. This attribute should be interpreted by anyone using the directory to derive mailing lists and its value respected. For example:
mailPreferenceOption: 0
mailPreferenceOption: 0| OID | 0.9.2342.19200300.100.1.47 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.102. mailProgramDeliveryInfo
This attribute contains any commands to use for programmed mail delivery.
| OID | 2.16.840.1.113730.3.1.20 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.103. mailQuota
This attribute sets the amount of disk space allowed for a user’s mail box.
| OID | 2.16.840.1.113730.3.1.21 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.104. mailRoutingAddress
This attribute contains the routing address to use when forwarding the emails received by the user to another messaging server.
| OID | 2.16.840.1.113730.3.1.24 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.105. manager
The manager contains the distinguished name (DN) of the manager for the person. For example:
manager: cn=Bill Andersen,ou=Quality Control,dc=example,dc=com
manager: cn=Bill Andersen,ou=Quality Control,dc=example,dc=com| OID | 0.9.2342.19200300.100.1.10 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.106. member
The member attribute contains the distinguished names (DNs) of each member of a group. For example:
member: cn=John Smith,dc=example,dc=com
member: cn=John Smith,dc=example,dc=com| OID | 2.5.4.31 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.107. memberCertificateDescription
This attribute is a multi-valued attribute where each value is a description, a pattern, or a filter matching the subject DN of a certificate, usually a certificate used for TLS client authentication.
memberCertificateDescription matches any certificate that contains a subject DN with the same attribute-value assertions (AVAs) as the description. The description may contain multiple ou AVAs. A matching DN must contain those same ou AVAs, in the same order, although it may be interspersed with other AVAs, including other ou AVAs. For any other attribute type (not ou), there should be at most one AVA of that type in the description. If there are several, all but the last are ignored.
A matching DN must contain that same AVA but no other AVA of the same type nearer the root (later, syntactically).
AVAs are considered the same if they contain the same attribute description (case-insensitive comparison) and the same attribute value (case-insensitive comparison, leading and trailing whitespace ignored, and consecutive whitespace characters treated as a single space).
To be considered a member of a group with the following memberCertificateDescription value, a certificate needs to include ou=x, ou=A, and dc=example, but not dc=company.
memberCertificateDescription: {ou=x,ou=A,dc=company,dc=example}
memberCertificateDescription: {ou=x,ou=A,dc=company,dc=example}
To match the group’s requirements, a certificate’s subject DNs must contain the same ou attribute types in the same order as defined in the memberCertificateDescription attribute.
| OID | 2.16.840.1.113730.3.1.199 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.108. memberNisNetgroup
This attribute merges the attribute values of another netgroup into the current one by listing the name of the merging netgroup.
The memberNisNetgroup attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.13 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.109. memberOf
This attribute contains the name of a group to which the user is a member.
memberOf is the default attribute generated by the MemberOf Plug-in on the user entry of a group member. This attribute is automatically synchronized to the listed member attributes in a group entry, so that displaying group membership for entries is managed by Directory Server.
This attribute is only synchronized between group entries and the corresponding members' user entries if the MemberOf Plug-in is enabled and is configured to use this attribute.
| OID | 1.2.840.113556.1.2.102 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Delegated Administrator |
8.110. memberUid
The memberUid attribute contains the login name of the member of a group; this can be different than the DN identified in the member attribute.
memberUID: jsmith
memberUID: jsmith
The memberUID attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.12 |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.111. memberURL
This attribute identifies a URL associated with each member of a group. Any type of labeled URL can be used.
memberURL: ldap://cn=jsmith,ou=people,dc=example,dc=com
memberURL: ldap://cn=jsmith,ou=people,dc=example,dc=com| OID | 2.16.840.1.113730.3.1.198 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.112. mepManagedBy
This attribute contains a pointer in an automatically-generated entry that points back to the DN of the originating entry. This attribute is set by the Managed Entries Plug-in and cannot be modified manually.
| OID | 2.16.840.1.113730.3.1.2086 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
8.113. mepManagedEntry
This attribute contains a pointer to an automatically-generated entry which corresponds to the current entry. This attribute is set by the Managed Entries Plug-in and cannot be modified manually.
| OID | 2.16.840.1.113730.3.1.2087 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
8.114. mepMappedAttr
This attribute sets an attribute in the Managed Entries template entry which must exist in the generated entry. The mapping means that some value of the originating entry is used to supply the given attribute. The values of these attributes will be tokens in the form attribute: $attr. For example:
mepMappedAttr: gidNumber: $gidNumber
mepMappedAttr: gidNumber: $gidNumberAs long as the syntax of the expanded token of the attribute does not violate the required attribute syntax, then other terms and strings can be used in the attribute. For example:
mepMappedAttr: cn: Managed Group for $cn
mepMappedAttr: cn: Managed Group for $cn| OID | 2.16.840.1.113730.3.1.2089 |
| Syntax | OctetString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.115. mepRDNAttr
This attribute sets which attribute to use as the naming attribute in the automatically-generated entry created by the Managed Entries Plug-in. Whatever attribute type is given in the naming attribute should be present in the managed entries template entry as a mepMappedAttr.
| OID | 2.16.840.1.113730.3.1.2090 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
8.116. mepStaticAttr
This attribute sets an attribute with a defined value that must be added to the automatically-generated entry managed by the Managed Entries Plug-in. This value will be used for every entry generated by that instance of the Managed Entries Plug-in.
mepStaticAttr: posixGroup
mepStaticAttr: posixGroup| OID | 2.16.840.1.113730.3.1.2088 |
| Syntax | OctetString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.117. mgrpAddHeader
This attribute contains information about the header in the messages.
| OID | 2.16.840.1.113730.3.1.781 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.118. mgrpAllowedBroadcaster
This attribute sets whether to allow the user to send broadcast messages.
| OID | 2.16.840.1.113730.3.1.22 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.119. mgrpAllowedDomain
This attribute sets the domains for the mail group.
| OID | 2.16.840.1.113730.3.1.23 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.120. mgrpApprovePassword
This attribute sets whether a user must approve a password used to access their email.
| OID | mgrpApprovePassword-oid |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape Messaging Server |
8.121. mgrpBroadcasterPolicy
This attribute defines the policy for broadcasting emails.
| OID | 2.16.840.1.113730.3.1.788 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.122. mgrpDeliverTo
This attribute contains information about the delivery destination for email.
| OID | 2.16.840.1.113730.3.1.25 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.123. mgrpErrorsTo
This attribute contains information about where to deliver error messages for the messaging server.
| OID | 2.16.840.1.113730.3.1.26 |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape Messaging Server |
8.124. mgrpModerator
This attribute contains the contact name for the mailing list moderator.
| OID | 2.16.840.1.113730.3.1.33 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.125. mgrpMsgMaxSize
This attribute sets the maximum size allowed for email messages.
| OID | 2.16.840.1.113730.3.1.32 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape Messaging Server |
8.126. mgrpMsgRejectAction
This attribute defines what actions the messaging server should take for rejected messages.
| OID | 2.16.840.1.113730.3.1.28 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.127. mgrpMsgRejectText
This attribute sets the text to use for rejection notifications.
| OID | 2.16.840.1.113730.3.1.29 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.128. mgrpNoDuplicateChecks
This attribute defines whether the messaging server checks for duplicate emails.
| OID | 2.16.840.1.113730.3.1.789 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape Messaging Server |
8.129. mgrpRemoveHeader
This attribute sets whether the header is removed in reply messages.
| OID | 2.16.840.1.113730.3.1.801 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.130. mgrpRFC822MailMember
This attribute identifies the member of a mail group.
| OID | 2.16.840.1.113730.3.1.30 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.131. mobile
The mobile, or mobileTelephoneNumber, contains the entry’s mobile or cellular phone number. For example:
mobileTelephoneNumber: 415-555-4321
mobileTelephoneNumber: 415-555-4321| OID | 0.9.2342.19200300.100.1.41 |
| Syntax | TelephoneNumber |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.132. mozillaCustom1
This attribute is used by Mozilla Thunderbird to manage a shared address book.
| OID | 1.3.6.1.4.1.13769.4.1 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.133. mozillaCustom2
This attribute is used by Mozilla Thunderbird to manage a shared address book.
| OID | 1.3.6.1.4.1.13769.4.2 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.134. mozillaCustom3
This attribute is used by Mozilla Thunderbird to manage a shared address book.
| OID | 1.3.6.1.4.1.13769.4.3 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.135. mozillaCustom4
This attribute is used by Mozilla Thunderbird to manage a shared address book.
| OID | 1.3.6.1.4.1.13769.4.4 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.136. mozillaHomeCountryName
This attribute sets the country used by Mozilla Thunderbird in a shared address book.
| OID | 1.3.6.1.4.1.13769.3.6 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.137. mozillaHomeLocalityName
This attribute sets the city used by Mozilla Thunderbird in a shared address book.
| OID | 1.3.6.1.4.1.13769.3.3 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.138. mozillaHomePostalCode
This attribute sets the postal code used by Mozilla Thunderbird in a shared address book.
| OID | 1.3.6.1.4.1.13769.3.5 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.139. mozillaHomeState
This attribute sets the state or province used by Mozilla Thunderbird in a shared address book.
| OID | 1.3.6.1.4.1.13769.3.4 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.140. mozillaHomeStreet2
This attribute contains the second line of a street address used by Mozilla Thunderbird in a shared address book.
| OID | 1.3.6.1.4.1.13769.3.2 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.141. mozillaHomeStreet
This attribute sets the street address used by Mozilla Thunderbird in a shared address book.
| OID | 1.3.6.1.4.1.13769.3.1 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.142. mozillaHomeUrl
This attribute contains a URL used by Mozilla Thunderbird in a shared address book.
| OID | 1.3.6.1.4.1.13769.3.7 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.143. mozillaNickname
This attribute contains a nickname used by Mozilla Thunderbird for a shared address book.
| OID | 1.3.6.1.4.1.13769.2.1 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Mozilla Address Book |
8.144. mozillaSecondEmail
This attribute contains an alternate or secondary email address for an entry in a shared address book for Mozilla Thunderbird.
| OID | 1.3.6.1.4.1.13769.2.2 |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.145. mozillaUseHtmlMail
This attribute sets an email type preference for an entry in a shared address book in Mozilla Thunderbird.
| OID | 1.3.6.1.4.1.13769.2.3 |
| Syntax | Boolean |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.146. mozillaWorkStreet2
This attribute contains a street address for a workplace or office for an entry in Mozilla Thunderbird’s shared address book.
| OID | 1.3.6.1.4.1.13769.3.8 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.147. mozillaWorkUrl
This attribute contains a URL for a work site in an entry in a shared address book in Mozilla Thunderbird.
| OID | 1.3.6.1.4.1.13769.3.9 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Mozilla Address Book |
8.148. multiLineDescription
This attribute contains a description of an entry which spans multiple lines in the LDIF file.
| OID | 1.3.6.1.4.1.250.1.2 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.149. name
The name attribute identifies the attribute supertype which can be used to form string attribute types for naming.
It is unlikely that values of this type will occur in an entry. LDAP server implementations that do not support attribute subtyping do not need to recognize this attribute in requests. Client implementations should not assume that LDAP servers are capable of performing attribute subtyping.
| OID | 2.5.4.41 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.150. netscapeReversiblePassword
This attribute contains the password for HTTP Digest/MD5 authentication.
| OID | 2.16.840.1.113730.3.1.812 |
| Syntax | OctetString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Web Server |
8.151. NisMapEntry
This attribute contains the information for a NIS map to be used by Network Information Services.
This attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.27 |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.152. nisMapName
This attribute contains the name of a mapping used by a NIS server.
| OID | 1.3.6.1.1.1.1.26 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.153. nisNetgroupTriple
This attribute contains information on a netgroup used by a NIS server.
This attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.14 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.154. nsAccessLog
This entry identifies the access log used by a server.
| OID | nsAccessLog-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.155. nsAdminAccessAddresses
This attribute contains the IP address of the Administration Server used by the instance.
| OID | nsAdminAccessAddresses-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.156. nsAdminAccessHosts
This attribute contains the host name of the Administration Server.
| OID | nsAdminAccessHosts-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.157. nsAdminAccountInfo
This attribute contains other information about the Administration Server account.
| OID | nsAdminAccountInfo-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.158. nsAdminCacheLifetime
This sets the length of time to store the cache used by Directory Server.
| OID | nsAdminCacheLifetime-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.159. nsAdminCgiWaitPid
This attribute defines the wait time for Administration Server CGI process IDs.
| OID | nsAdminCgiWaitPid-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.160. nsAdminDomainName
This attribute contains the name of the administration domain containing the Directory Server instance.
| OID | nsAdminDomainName-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.161. nsAdminEnableEnduser
This attribute sets whether to allow end user access to admin services.
| OID | nsAdminEnableEnduser-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.162. nsAdminEndUserHTMLIndex
This attribute sets whether to allow end users to access the HTML index of admin services.
| OID | nsAdminEndUserHTMLIndex-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.163. nsAdminGroupName
This attribute gives the name of the admin guide.
| OID | nsAdminGroupName-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.164. nsAdminOneACLDir
This attribute gives the directory path to the directory containing access control lists for the Administration Server.
| OID | nsAdminOneACLDir-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.165. nsAdminSIEDN
This attribute contains the DN of the serer instance entry (SIE) for the Administration Server.
| OID | nsAdminSIEDN-oid |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.166. nsAdminUsers
This attribute gives the path and name of the file which contains the information for the Administration Server admin user.
| OID | nsAdminUsers-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.167. nsAIMid
This attribute contains the AOL Instant Messaging user ID for the user.
| OID | 2.16.840.1.113730.3.2.300 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.168. nsBaseDN
This contains the base DN used in Directory Server’s server instance definition entry.
| OID | nsBaseDN-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.169. nsBindDN
This attribute contains the bind DN defined in Directory Server SIE.
| OID | nsBindDN-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.170. nsBindPassword
This attribute contains the password used by the bind DN defined in nsBindDN.
| OID | nsBindPassword-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.171. nsBuildNumber
This defines, in Directory Server SIE, the build number of the server instance.
| OID | nsBuildNumber-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.172. nsBuildSecurity
This defines, in Directory Server SIE, the build security level.
| OID | nsBuildSecurity-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.173. nsCertConfig
This attribute defines the configuration for the Red Hat Certificate System.
| OID | nsCertConfig-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Certificate System |
8.174. nsClassname
| OID | nsClassname-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.175. nsConfigRoot
This attribute contains the root DN of the configuration directory.
| OID | nsConfigRoot-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.176. nscpAIMScreenname
This attribute gives the AIM screen name of a user.
| OID | 1.3.6.1.4.1.13769.2.4 |
| Syntax | TelephoneString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Mozilla Address Book |
8.177. nsDefaultAcceptLanguage
This attribute contains the language codes which are accepted for HTML clients.
| OID | nsDefaultAcceptLanguage-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.178. nsDefaultObjectClass
This attribute stores object class information in a container entry.
| OID | nsDefaultObjectClass-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.179. nsDeleteclassname
| OID | nsDeleteclassname-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.180. nsDirectoryFailoverList
This attribute contains a list of Directory Servers to use for failover.
| OID | nsDirectoryFailoverList-oid |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.181. nsDirectoryInfoRef
This attribute refers to a DN of an entry with information about the server.
| OID | nsDirectoryInfoRef-oid |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.182. nsDirectoryURL
This attribute contains Directory Server URL.
| OID | nsDirectoryURL-oid |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.183. nsDisplayName
This attribute contains a display name.
| OID | nsDisplayName-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.184. nsErrorLog
This attribute identifies the error log used by the server.
| OID | nsErrorLog-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.185. nsExecRef
This attribute contains the path or location of an executable which can be used to perform server tasks.
| OID | nsExecRef-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.186. nsExpirationDate
This attribute contains the expiration date of an application.
| OID | nsExpirationDate-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.187. nsGroupRDNComponent
This attribute defines the attribute to use for the RDN of a group entry.
| OID | nsGroupRDNComponent-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.188. nsHardwarePlatform
This attribute indicates the hardware on which the server is running. The value of this attribute is the same as the output from uname -m. For example:
nsHardwarePlatform:i686
nsHardwarePlatform:i686| OID | nsHardwarePlatform-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.189. nsHelpRef
This attribute contains a reference to an online help file.
| OID | nsHelpRef-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.190. nsHostLocation
This attribute contains information about the server host.
| OID | nsHostLocation-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.191. nsICQid
This attribute contains an ICQ ID for the user.
| OID | 2.16.840.1.113730.3.1.2014 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.192. nsInstalledLocation
This attribute contains the installation directory for Directory Servers which are version 7.1 or older.
| OID | nsInstalledLocation-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.193. nsJarfilename
This attribute gives the jar file name used by the Console.
| OID | nsJarfilename-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.194. nsLdapSchemaVersion
This gives the version number of the LDAP directory schema.
| OID | nsLdapSchemaVersion-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.195. nsLicensedFor
The nsLicensedFor attribute identifies the server the user is licensed to use. Administration Server expects each nsLicenseUser entry to contain zero or more instances of this attribute. Valid keywords for this attribute include the following:
-
slapdfor a licensed Directory Server client. -
mailfor a licensed mail server client. -
newsfor a licensed news server client. -
calfor a licensed calender server client.
For example:
nsLicensedFor: slapd
nsLicensedFor: slapd| OID | 2.16.840.1.113730.3.1.36 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Administration Server |
8.196. nsLicenseEndTime
Reserved for future use.
| OID | 2.16.840.1.113730.3.1.38 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Administration Server |
8.197. nsLicenseStartTime
Reserved for future use.
| OID | 2.16.840.1.113730.3.1.37 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Administration Server |
8.198. nsLogSuppress
This attribute sets whether to suppress server logging.
| OID | nsLogSuppress-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.199. nsmsgDisallowAccess
This attribute defines access to a messaging server.
| OID | nsmsgDisallowAccess-oid |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.200. nsmsgNumMsgQuota
This attribute sets a quota for the number of messages which will be kept by the messaging server.
| OID | nsmsgNumMsgQuota-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.201. nsMSNid
This attribute contains the MSN instant messaging ID for the user.
| OID | 2.16.840.1.113730.3.1.2016 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.202. nsNickName
This attribute gives a nickname for an application.
| OID | nsNickName-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.203. nsNYR
| OID | nsNYR-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Administration Services |
8.204. nsOsVersion
This attribute contains the version number of the operating system for the host on which the server is running.
| OID | nsOsVersion-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.205. nsPidLog
| OID | nsPidLog-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.206. nsPreference
This attribute stores the Console preference settings.
| OID | nsPreference-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.207. nsProductName
This contains the name of the product, such as Red Hat Directory Server or Administration Server.
| OID | nsProductName-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.208. nsProductVersion
This contains the version number of Directory Server.
| OID | nsProductVersion-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.209. nsRevisionNumber
This attribute contains the revision number of Directory Server or Administration Server.
| OID | nsRevisionNumber-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.210. nsSecureServerPort
This attribute contains the TLS port for Directory Server.
This attribute does not configure the TLS port for Directory Server. This is configured in nsslapd-secureport configuration attribute in Directory Server’s dse.ldif file. Configuration attributes are described in the Configuration, Command, and File Reference.
| OID | nsSecureServerPort-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.211. nsSerialNumber
This attribute contains a serial number or tracking number assigned to a specific server application, such as Red Hat Directory Server or Administration Server.
| OID | nsSerialNumber-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.212. nsServerAddress
This attribute contains the IP address of the server host on which Directory Server is running.
| OID | nsServerAddress-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.213. nsServerCreationClassname
This attribute gives the class name to use when creating a server.
| OID | nsServerCreationClassname-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.214. nsServerID
This contains the server’s instance name. For example:
nsServerID: slapd-example
nsServerID: slapd-example| OID | nsServerID-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.215. nsServerMigrationClassname
This attribute contains the name of the class to use when migrating a server.
| OID | nsServerMigrationClassname-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.216. nsServerPort
This attribute contains the standard LDAP port for Directory Server.
This attribute does not configure the standard port for Directory Server. This is configured in nsslapd-port configuration attribute in Directory Server’s dse.ldif file. Configuration attributes are described in the Configuration, Command, and File Reference.
| OID | nsServerPort-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.217. nsServerSecurity
This shows whether Directory Server requires a secure TLS or SSL connection.
| OID | nsServerSecurity-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.218. nsSNMPContact
This attribute contains the contact information provided by the SNMP.
| OID | 2.16.840.1.113730.3.1.235 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.219. nsSNMPDescription
This contains a description of the SNMP service.
| OID | 2.16.840.1.113730.3.1.236 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.220. nsSNMPEnabled
This attribute shows whether SNMP is enabled for the server.
| OID | 2.16.840.1.113730.3.1.232 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.221. nsSNMPLocation
This attribute shows the location provided by the SNMP service.
| OID | 2.16.840.1.113730.3.1.234 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.222. nsSNMPMasterHost
This attribute shows the host name for the SNMP master agent.
| OID | 2.16.840.1.113730.3.1.237 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.223. nsSNMPMasterPort
This attribute shows the port number for the SNMP subagent.
| OID | 2.16.840.1.113730.3.1.238 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.224. nsSNMPOrganization
This attribute contains the organization information provided by SNMP.
| OID | 2.16.840.1.113730.3.1.233 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.225. nsSuiteSpotUser
This attribute has been obsoleted.
This attribute identifies the Unix user who installed the server.
| OID | nsSuiteSpotUser-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.226. nsTaskLabel
| OID | nsTaskLabel-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.227. nsUniqueAttribute
This sets a unique attribute for the server preferences.
| OID | nsUniqueAttribute-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.228. nsUserIDFormat
This attribute sets the format to use to generate the uid attribute from the givenname and sn attributes.
| OID | nsUserIDFormat-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.229. nsUserRDNComponent
This attribute sets the attribute type to set the RDN for user entries.
| OID | nsUserRDNComponent-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.230. nsValueBin
| OID | 2.16.840.1.113730.3.1.247 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.231. nsValueCES
| OID | 2.16.840.1.113730.3.1.244 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.232. nsValueCIS
| OID | 2.16.840.1.113730.3.1.243 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.233. nsValueDefault
| OID | 2.16.840.1.113730.3.1.250 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.234. nsValueDescription
| OID | 2.16.840.1.113730.3.1.252 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.235. nsValueDN
| OID | 2.16.840.1.113730.3.1.248 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.236. nsValueFlags
| OID | 2.16.840.1.113730.3.1.251 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.237. nsValueHelpURL
| OID | 2.16.840.1.113730.3.1.254 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.238. nsValueInt
| OID | 2.16.840.1.113730.3.1.246 |
| Syntax | Integer |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.239. nsValueSyntax
| OID | 2.16.840.1.113730.3.1.253 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.240. nsValueTel
| OID | 2.16.840.1.113730.3.1.245 |
| Syntax | TelephoneString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.241. nsValueType
| OID | 2.16.840.1.113730.3.1.249 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape servers — value item |
8.242. nsVendor
This contains the name of the server vendor.
| OID | nsVendor-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape |
8.243. nsViewConfiguration
This attribute stores the view configuration used by Console.
| OID | nsViewConfiguration-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.244. nsViewFilter
This attribute sets the attribute-value pair which is used to identify entries belonging to the view.
| OID | 2.16.840.1.113730.3.1.3023 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.245. nsWellKnownJarfiles
| OID | nsWellKnownJarfiles-oid |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.246. nswmExtendedUserPrefs
This attribute is used to store user preferences for accounts in a messaging server.
| OID | 2.16.840.1.113730.3.1.520 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.247. nsYIMid
This attribute contains the Yahoo instant messaging user name for the user.
| OID | 2.16.840.1.113730.3.1.2015 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
8.248. ntGroupAttributes
This attribute points to a binary file which contains information about the group. For example:
ntGroupAttributes:: IyEvYmluL2tzaAoKIwojIGRlZmF1bHQgdmFsdWUKIwpIPSJgaG9zdG5hb
ntGroupAttributes:: IyEvYmluL2tzaAoKIwojIGRlZmF1bHQgdmFsdWUKIwpIPSJgaG9zdG5hb| OID | 2.16.840.1.113730.3.1.536 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.249. ntGroupCreateNewGroup
The ntGroupCreateNewGroup attribute is used by Windows Sync to determine whether Directory Server should create new group entry when a new group is created on a Windows server. true creates the new entry; false ignores the Windows entry.
| OID | 2.16.840.1.113730.3.1.45 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.250. ntGroupDeleteGroup
The ntGroupDeleteGroup attribute is used by Windows Sync to determine whether Directory Server should delete a group entry when the group is deleted on a Windows sync peer server. true means the account is deleted; false ignores the deletion.
| OID | 2.16.840.1.113730.3.1.46 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.251. ntGroupDomainId
The ntGroupDomainID attribute contains the domain ID string for a group.
ntGroupDomainId: DS HR Group
ntGroupDomainId: DS HR Group| OID | 2.16.840.1.113730.3.1.44 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.252. ntGroupId
The ntGroupId attribute points to a binary file which identifies the group. For example:
ntGroupId: IOUnHNjjRgghghREgfvItrGHyuTYhjIOhTYtyHJuSDwOopKLhjGbnGFtr
ntGroupId: IOUnHNjjRgghghREgfvItrGHyuTYhjIOhTYtyHJuSDwOopKLhjGbnGFtr| OID | 2.16.840.1.113730.3.1.110 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.253. ntGroupType
In Active Directory, there are two major types of groups: security and distribution. Security groups are most similar to groups in Directory Server, since security groups can have policies configured for access controls, resource restrictions, and other permissions. Distribution groups are for mailing distribution. These are further broken down into global and local groups. The Directory Server ntGroupType supports all four group types:
The ntGroupType attribute identifies the type of Windows group. The valid values are as follows:
-
-21483646for global/security -
-21483644for domain local/security -
2for global/distribution -
4for domain local/distribution
This value is set automatically when the Windows groups are synchronized. To determine the type of group, you must manually configure it when the group gets created. By default, Directory Server groups do not have this attribute and are synchronized as global/security groups.
ntGroupType: -21483646
ntGroupType: -21483646| OID | 2.16.840.1.113730.3.1.47 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.254. ntUniqueId
The ntUniqueId attribute contains a generated number used for internal server identification and operation. For example:
ntUniqueId: 352562404224a44ab040df02e4ef500b
ntUniqueId: 352562404224a44ab040df02e4ef500b| OID | 2.16.840.1.113730.3.1.111 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.255. ntUserAcctExpires
This attribute indicates when the entry’s Windows account will expire. This value is stored as a string in GMT format. For example:
ntUserAcctExpires: 20081015203415
ntUserAcctExpires: 20081015203415| OID | 2.16.840.1.113730.3.1.528 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.256. ntUserAuthFlags
This attribute contains authorization flags set for the Windows account.
| OID | 2.16.840.1.113730.3.1.60 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.257. ntUserBadPwCount
This attribute sets the number of bad password failures are allowed before an account is locked.
| OID | 2.16.840.1.113730.3.1.531 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.258. ntUserCodePage
The ntUserCodePage attribute contains the code page for the user’s language of choice. For example:
ntUserCodePage: AAAAAA==
ntUserCodePage: AAAAAA==| OID | 2.16.840.1.113730.3.1.533 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.259. ntUserComment
This attribute contains a text description or note about the user entry.
| OID | 2.16.840.1.113730.3.1.522 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.260. ntUserCountryCode
This attribute contains the two-character country code for the country where the user is located.
| OID | 2.16.840.1.113730.3.1.532 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.261. ntUserCreateNewAccount
The ntUserCreateNewAccount attribute is used by Windows Sync to determine whether Directory Server should create a new user entry when a new user is created on a Windows server. true creates the new entry; false ignores the Windows entry.
| OID | 2.16.840.1.113730.3.1.42 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.262. ntUserDeleteAccount
The ntUserDeleteAccount attribute IS Used by Windows Sync to determine whether a Directory Server entry will be automatically deleted when the user is deleted from the Windows sync peer server. true means the user entry is deleted; false ignores the deletion.
| OID | 2.16.840.1.113730.3.1.43 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.263. ntUserDomainId
The ntUserDomainId attribute contains the Windows domain login ID. For example:
ntUserDomainId: jsmith
ntUserDomainId: jsmith| OID | 2.16.840.1.113730.3.1.41 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.264. ntUserFlags
This attribute contains additional flags set for the Windows account.
| OID | 2.16.840.1.113730.3.1.523 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.265. ntUserHomeDir
The ntUserHomeDir attribute contains an ASCII string representing the Windows user’s home directory. This attribute can be null. For example:
ntUserHomeDir: c:\jsmith
ntUserHomeDir: c:\jsmith| OID | 2.16.840.1.113730.3.1.521 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.266. ntUserHomeDirDrive
This attribute contains information about the drive on which the user’s home directory is stored.
| OID | 2.16.840.1.113730.3.1.535 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.267. ntUserLastLogoff
The ntUserLastLogoff attribute contains the time of the last logoff. This value is stored as a string in GMT format.
If security logging is turned on, then this attribute is updated on synchronization only if some other aspect of the user’s entry has changed.
ntUserLastLogoff: 20201015203415Z
ntUserLastLogoff: 20201015203415Z| OID | 2.16.840.1.113730.3.1.527 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.268. ntUserLastLogon
The ntUserLastLogon attribute contains the time that the user last logged into the Windows domain. This value is stored as a string in GMT format. If security logging is turned on, then this attribute is updated on synchronization only if some other aspect of the user’s entry has changed.
ntUserLastLogon: 20201015203415Z
ntUserLastLogon: 20201015203415Z| OID | 2.16.840.1.113730.3.1.526 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.269. ntUserLogonHours
The ntUserLogonHours attribute contains the time periods that a user is allowed to log onto the Active Directory domain. This attribute corresponds to the logonHours attribute in Active Directory.
| OID | 2.16.840.1.113730.3.1.530 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.270. ntUserLogonServer
The ntUserLogonServer attribute defines the Active Directory server to which the user’s logon request is forwarded.
| OID | 2.16.840.1.113730.3.1.65 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.271. ntUserMaxStorage
The ntUserMaxStorage attribute contains the maximum amount of disk space available for the user.
ntUserMaxStorage: 4294967295
ntUserMaxStorage: 4294967295| OID | 2.16.840.1.113730.3.1.529 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.272. ntUserNumLogons
This attribute shows the number of successful logons to the Active Directory domain for the user.
| OID | 2.16.840.1.113730.3.1.64 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.273. ntUserParms
The ntUserParms attribute contains a Unicode string reserved for use by applications.
| OID | 2.16.840.1.113730.3.1.62 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.274. ntUserPasswordExpired
This attribute shows whether the password for the Active Directory account has expired.
| OID | 2.16.840.1.113730.3.1.68 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.275. ntUserPrimaryGroupId
The ntUserPrimaryGroupId attribute contains the group ID of the primary group to which the user belongs.
| OID | 2.16.840.1.113730.3.1.534 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.276. ntUserPriv
This attribute shows the type of privileges allowed for the user.
| OID | 2.16.840.1.113730.3.1.59 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.277. ntUserProfile
The ntUserProfile attribute contains the path to a user’s profile. For example:
ntUserProfile: c:\jsmith\profile.txt
ntUserProfile: c:\jsmith\profile.txt| OID | 2.16.840.1.113730.3.1.67 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.278. ntUserScriptPath
The ntUserScriptPath attribute contains the path to an ASCII script used by the user to log into the domain.
ntUserScriptPath: c:\jstorm\lscript.bat
ntUserScriptPath: c:\jstorm\lscript.bat| OID | 2.16.840.1.113730.3.1.524 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.279. ntUserUniqueId
The ntUserUniqueId attribute contains a unique numeric ID for the Windows user.
| OID | 2.16.840.1.113730.3.1.66 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.280. ntUserUnitsPerWeek
The ntUserUnitsPerWeek attribute contains the total amount of time that the user has spent logged into the Active Directory domain.
| OID | 2.16.840.1.113730.3.1.63 |
| Syntax | Binary |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.281. ntUserUsrComment
The ntUserUsrComment attribute contains additional comments about the user.
| OID | 2.16.840.1.113730.3.1.61 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.282. ntUserWorkstations
The ntUserWorkstations attribute contains a list of names, in ASCII strings, of work stations which the user is allowed to log in to. There can be up to eight work stations listed, separated by commas. Specify null to permit users to log on from any workstation. For example:
ntUserWorkstations: firefly
ntUserWorkstations: firefly| OID | 2.16.840.1.113730.3.1.525 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape NT Synchronization |
8.283. o
The organizationName, or o, attribute contains the organization name. For example:
organizationName: Example Corporation o: Example Corporation
organizationName: Example Corporation
o: Example Corporation| OID | 2.5.4.10 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.284. objectClass
The objectClass attribute identifies the object classes used for an entry. For example:
objectClass: person
objectClass: person| OID | 2.5.4.0 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.285. objectClasses
This attribute is used in a schema file to identify an object class allowed by the subschema definition.
| OID | 2.5.21.6 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.286. obsoletedByDocument
The obsoletedByDocument attribute contains the distinguished name of a document which obsoletes the current document entry.
| OID | 0.9.2342.19200300.102.1.4 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.287. obsoletesDocument
The obsoletesDocument attribute contains the distinguished name of a documented which is obsoleted by the current document entry.
| OID | 0.9.2342.19200300.102.1.3 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.288. oncRpcNumber
The oncRpcNumber attribute contains part of the RPC map and stores the RPC number for UNIX RPCs.
The oncRpcNumber attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.18 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.289. organizationalStatus
The organizationalStatus identifies the person’s category within an organization.
organizationalStatus: researcher
organizationalStatus: researcher| OID | 0.9.2342.19200300.100.1.45 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.290. otherMailbox
The otherMailbox attribute contains values for email types other than X.400 and RFC 822.
otherMailbox: internet $ jsmith@example.com
otherMailbox: internet $ jsmith@example.com| OID | 0.9.2342.19200300.100.1.22 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.291. ou
The organizationalUnitName, or ou, contains the name of an organizational division or a subtree within the directory hierarchy.
organizationalUnitName: Marketing ou: Marketing
organizationalUnitName: Marketing
ou: Marketing| OID | 2.5.4.11 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.292. owner
The owner attribute contains the DN of the person responsible for an entry. For example:
owner: cn=John Smith,ou=people,dc=example,dc=com
owner: cn=John Smith,ou=people,dc=example,dc=com| OID | 2.5.4.32 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.293. pager
The pagerTelephoneNumber, or pager, attribute contains a person’s pager phone number.
pagerTelephoneNumber: 415-555-6789 pager: 415-555-6789
pagerTelephoneNumber: 415-555-6789
pager: 415-555-6789| OID | 0.9.2342.19200300.100.1.42 |
| Syntax | TelephoneNumber |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.294. parentOrganization
The parentOrganization attribute identifies the parent organization of an organization or organizational unit.
| OID | 1.3.6.1.4.1.1466.101.120.41 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape |
8.295. personalSignature
The personalSignature attribute contains the entry’s signature file, in binary format.
personalSignature:: AAAAAA==
personalSignature:: AAAAAA==| OID | 0.9.2342.19200300.100.1.53 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.296. personalTitle
The personalTitle attribute contains a person’s honorific, such as Ms., Dr., Prof., and Rev.
personalTitle: Mr.
personalTitle: Mr.| OID | 0.9.2342.19200300.100.1.40 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.297. photo
The photo attribute contains a photo file, in a binary format.
photo:: AAAAAA==
photo:: AAAAAA==| OID | 0.9.2342.19200300.100.1.7 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.298. physicalDeliveryOfficeName
The physicalDeliveryOffice contains the city or town in which a physical postal delivery office is located.
physicalDeliveryOfficeName: Raleigh
physicalDeliveryOfficeName: Raleigh| OID | 2.5.4.19 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.299. postalAddress
The postalAddress attribute identifies the entry’s mailing address. This field is intended to include multiple lines. When represented in LDIF format, each line should be separated by a dollar sign ($).
To represent an actual dollar sign ($) or backslash (\) within the entry text, use the escaped hex values \24 and \5c respectively. For example, to represent the string:
The dollar ($) value can be found in the c:\cost file.
The dollar ($) value can be found
in the c:\cost file.provide the string:
The dollar (\24) value can be found$in the c:\5ccost file.
The dollar (\24) value can be found$in the c:\5ccost file.| OID | 2.5.4.16 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.300. postalCode
The postalCode contains the zip code for an entry located within the United States.
postalCode: 44224
postalCode: 44224| OID | 2.5.4.17 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.301. postOfficeBox
The postOfficeBox attribute contains the postal address number or post office box number for an entry’s physical mailing address.
postOfficeBox: 1234
postOfficeBox: 1234| OID | 2.5.4.18 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.302. preferredDeliveryMethod
The preferredDeliveryMethod contains an entry’s preferred contact or delivery method. For example:
preferredDeliveryMethod: telephone
preferredDeliveryMethod: telephone| OID | 2.5.4.28 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.303. preferredLanguage
The preferredLanguage attribute contains a person’s preferred written or spoken language. The value should conform to the syntax for HTTP Accept-Language header values.
| OID | 2.16.840.1.113730.3.1.39 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.304. preferredLocale
A locale identifies language-specific information about how users of a specific region, culture, or custom expect data to be presented, including how data of a given language is interpreted and how data is to be sorted. Directory Server supports three locales for American English, Japanese, and German.
The preferredLocale attribute sets which locale is preferred by a user.
| OID | 1.3.6.1.4.1.1466.101.120.42 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape |
8.305. preferredTimeZone
The preferredTimeZone attribute sets the time zone to use for the user entry.
| OID | 1.3.6.1.4.1.1466.101.120.43 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Netscape |
8.306. presentationAddress
The presentationAddress attribute contains the OSI presentation address for an entry. This attribute includes the OSI Network Address and up to three selectors, one each for use by the transport, session, and presentation entities. For example:
presentationAddress: TELEX+00726322+RFC-1006+02+130.59.2.1
presentationAddress: TELEX+00726322+RFC-1006+02+130.59.2.1| OID | 2.5.4.29 |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.307. protocolInformation
The protocolInformation attribute, used together with the presentationAddress attribute, provides additional information about the OSO network service.
| OID | 2.5.4.48 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.308. pwdReset
When an administrator changes the password of a user, Directory Server sets the pwdReset operational attribute in the user’s entry to true. Applications can use this attribute to identify if a password of a user has been reset by an administrator.
The pwdReset attribute is an operational attribute and, therefore, users cannot edit it.
| OID | 1.3.6.1.4.1.1466.115.121.1.7 |
| Syntax | Boolean |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.309. ref
The ref attribute is used to support LDAPv3 smart referrals. The value of this attribute is an LDAP URL:
ldap: pass:quotes[host_name]:pass:quotes[port_number]/pass:quotes[subtree_dn]
ldap: pass:quotes[host_name]:pass:quotes[port_number]/pass:quotes[subtree_dn]The port number is optional.
For example:
ref: ldap://server.example.com:389/ou=People,dc=example,dc=com
ref: ldap://server.example.com:389/ou=People,dc=example,dc=com| OID | 2.16.840.1.113730.3.1.34 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | LDAPv3 Referrals Internet Draft |
8.310. registeredAddress
This attribute contains a postal address for receiving telegrams or expedited documents. The recipient’s signature is usually required on delivery.
| OID | 2.5.4.26 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.311. roleOccupant
This attribute contains the distinguished name of the person acting in the role defined in the organizationalRole entry.
roleOccupant: uid=bjensen,dc=example,dc=com
roleOccupant: uid=bjensen,dc=example,dc=com| OID | 2.5.4.33 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.312. roomNumber
This attribute specifies the room number of an object. The cn attribute should be used for naming room objects.
roomNumber: 230
roomNumber: 230| OID | 0.9.2342.19200300.100.1.6 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.313. searchGuide
The searchGuide attribute specifies information for suggested search criteria when using the entry as the base object in the directory tree for a search operation. When constructing search filters, use the enhancedSearchGuide attribute instead.
| OID | 2.5.4.14 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.314. secretary
The secretary attribute identifies an entry’s secretary or administrative assistant.
secretary: cn=John Smith,dc=example,dc=com
secretary: cn=John Smith,dc=example,dc=com| OID | 0.9.2342.19200300.100.1.21 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.315. seeAlso
The seeAlso attribute identifies another Directory Server entry that may contain information related to this entry.
seeAlso: cn=Quality Control Inspectors,ou=manufacturing,dc=example,dc=com
seeAlso: cn=Quality Control Inspectors,ou=manufacturing,dc=example,dc=com| OID | 2.5.4.34 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.316. serialNumber
The serialNumber attribute contains the serial number of a device.
serialNumber: 555-1234-AZ
serialNumber: 555-1234-AZ| OID | 2.5.4.5 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.317. serverHostName
The serverHostName attribute contains the host name of the server on which Directory Server is running.
| OID | 2.16.840.1.113730.3.1.76 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Red Hat Administration Services |
8.318. serverProductName
The serverProductName attribute contains the name of the server product.
| OID | 2.16.840.1.113730.3.1.71 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Red Hat Administration Services |
8.319. serverRoot
This attribute is obsolete.
This attribute shows the installation directory (server root) of Directory Servers version 7.1 or older.
| OID | 2.16.840.1.113730.3.1.70 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Administration Services |
8.320. serverVersionNumber
The serverVersionNumber attribute contains the server version number.
| OID | 2.16.840.1.113730.3.1.72 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Red Hat Administration Services |
8.321. shadowExpire
The shadowExpire attribute contains the date that the shadow account expires. The format of the date is in the number days since EPOCH, in UTC. To calculate this on the system, run a command like the following, using -d for the current date and -u to specify UTC:
echo date -u -d 20100108 +%s /24/60/60 |bc 14617
$ echo date -u -d 20100108 +%s /24/60/60 |bc
14617
The result (14617 in the example) is then the value of shadowExpire.
shadowExpire: 14617
shadowExpire: 14617
The shadowExpire attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.10 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.322. shadowFlag
The shadowFlag attribute identifies what area in the shadow map stores the flag values.
shadowFlag: 150
shadowFlag: 150
The shadowFlag attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.11 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.323. shadowInactive
The shadowInactive attribute sets how long, in days, the shadow account can be inactive.
shadowInactive: 15
shadowInactive: 15
The shadowInactive attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.9 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.324. shadowLastChange
The shadowLastChange attribute contains the number of days between January 1, 1970 and the day when the user password was last set. For example, if an account’s password was last set on Nov 4, 2016, the shadowLastChange attribute is set to 0
The following exceptions are existing:
-
When the
passwordMustChangeparameter is enabled in thecn=configentry, new accounts have0set in theshadowLastChangeattribute. -
When you create an account without password, the
shadowLastChangeattribute is not added.
The shadowLastChange attribute is automatically updated for accounts synchronized from Active Directory.
The shadowLastChange attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.5 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.325. shadowMax
The shadowMax attribute sets the maximum number of days that a shadow password is valid.
shadowMax: 10
shadowMax: 10
The shadowMax attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.7 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.326. shadowMin
The shadowMin attribute sets the minimum number of days that must pass between changing the shadow password.
shadowMin: 3
shadowMin: 3
The shadowMin attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.6 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.327. shadowWarning
The shadowWarning attribute sets how may days in advance of password expiration to send a warning to the user.
shadowWarning: 2
shadowWarning: 2
The shadowWarning attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.8 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.328. singleLevelQuality
The singleLevelQuality specifies the purported data quality at the level immediately below in the directory tree.
| OID | 0.9.2342.19200300.100.1.50 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.329. sn
The surname, or sn, attribute contains an entry’s surname, also called a last name or family name.
surname: Jensen sn: Jensen
surname: Jensen
sn: Jensen| OID | 2.5.4.4 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.330. st
The stateOrProvinceName, or st, attributes contains the entry’s state or province.
stateOrProvinceName: California st: California
stateOrProvinceName: California
st: California| OID | 2.5.4.8 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.331. street
The streetAddress, or street, attribute contains an entry’s street name and residential address.
streetAddress: 1234 Ridgeway Drive street: 1234 Ridgeway Drive
streetAddress: 1234 Ridgeway Drive
street: 1234 Ridgeway Drive| OID | 2.5.4.9 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.332. subject
The subject attribute contains information about the subject matter of the document entry.
subject: employee option grants
subject: employee option grants| OID | 0.9.2342.19200300.102.1.8 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.333. subtreeMaximumQuality
The subtreeMaximumQuality attribute specifies the purported maximum data quality for a directory subtree.
| OID | 0.9.2342.19200300.100.1.52 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.334. subtreeMinimumQuality
The subtreeMinimumQuality specifies the purported minimum data quality for a directory subtree.
| OID | 0.9.2342.19200300.100.1.51 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.335. supportedAlgorithms
The supportedAlgorithms attribute contains algorithms which are requested and stored in a binary form, such as supportedAlgorithms;binary.
supportedAlgorithms:: AAAAAA==
supportedAlgorithms:: AAAAAA==| OID | 2.5.4.52 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.336. supportedApplicationContext
This attribute contains the identifiers of OSI application contexts.
| OID | 2.5.4.30 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.337. telephoneNumber
The telephoneNumber contains an entry’s phone number. For example:
telephoneNumber: 415-555-2233
telephoneNumber: 415-555-2233| OID | 2.5.4.20 |
| Syntax | TelephoneNumber |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.338. teletexTerminalIdentifier
The teletexTerminalIdentifier attribute contains an entry’s teletex terminal identifier. The first printable string in the example is the encoding of the first portion of the teletex terminal identifier to be encoded, and the subsequent 0 or more octet strings are subsequent portions of the teletex terminal identifier:
teletex-id = ttx-term 0*("$" ttx-param)
ttx-term = printablestring
ttx-param = ttx-key ":" ttx-value
ttx-key = "graphic" / "control" / "misc" / "page" / "private"
ttx-value = octetstring
teletex-id = ttx-term 0*("$" ttx-param)
ttx-term = printablestring
ttx-param = ttx-key ":" ttx-value
ttx-key = "graphic" / "control" / "misc" / "page" / "private"
ttx-value = octetstring| OID | 2.5.4.22 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.339. telexNumber
This attribute defines the telex number of the entry. The format of the telex number is as follows:
actual-number "$" country "$" answerback
actual-number "$" country "$" answerback- actual-number is the syntactic representation of the number portion of the telex number being encoded.
- country is the TELEX country code.
- answerback is the answerback code of a TELEX terminal.
| OID | 2.5.4.21 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.340. title
The title attribute contains a person’s title within the organization.
title: Senior QC Inspector
title: Senior QC Inspector| OID | 2.5.4.12 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.341. ttl
The TimeToLive, or ttl, attribute contains the time, in seconds, that cached information about an entry should be considered valid. Once the specified time has elapsed, the information is considered out of date. A value of zero (0) indicates that the entry should not be cached.
TimeToLive: 120 ttl: 120
TimeToLive: 120
ttl: 120| OID | 1.3.6.1.4.250.1.60 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | LDAP Caching Internet Draft |
8.342. uid
The userID, more commonly uid, attribute contains the entry’s unique user name.
userID: jsmith uid: jsmith
userID: jsmith
uid: jsmith| OID | 0.9.2342.19200300.100.1.1 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.343. uidNumber
The uidNumber attribute contains a unique numeric identifier for a user entry. This is analogous to the user number in Unix.
uidNumber: 120
uidNumber: 120
The uidNumber attribute is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
| OID | 1.3.6.1.1.1.1.0 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in |
8.344. uniqueIdentifier
This attribute identifies a specific item used to distinguish between two entries when a distinguished name has been reused. This attribute is intended to detect any instance of a reference to a distinguished name that has been deleted. This attribute is assigned by the server.
uniqueIdentifier:: AAAAAA==
uniqueIdentifier:: AAAAAA==| OID | 0.9.2342.19200300.100.1.44 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.345. uniqueMember
The uniqueMember attribute identifies a group of names associated with an entry where each name was given a uniqueIdentifier to ensure its uniqueness. A value for the uniqueMember attribute is a DN followed by the uniqueIdentifier.
| OID | 2.5.4.50 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.346. updatedByDocument
The updatedByDocument attribute contains the distinguished name of a document that is an updated version of the document entry.
| OID | 0.9.2342.19200300.102.1.6 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.347. updatesDocument
The updatesDocument attribute contains the distinguished name of a document for which this document is an updated version.
| OID | 0.9.2342.19200300.102.1.5 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Internet White Pages Pilot |
8.348. userCertificate
This attribute is stored and requested in the binary form, as userCertificate;binary.
userCertificate;binary:: AAAAAA==
userCertificate;binary:: AAAAAA==| OID | 2.5.4.36 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.349. userClass
This attribute specifies a category of computer user. The semantics of this attribute are arbitrary. The organizationalStatus attribute makes no distinction between computer users and other types of users users and may be more applicable.
userClass: intern
userClass: intern| OID | 0.9.2342.19200300.100.1.8 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.350. userPassword
This attribute identifies the entry’s password and encryption method in the format {encryption method}encrypted password. For example:
userPassword: {sha}FTSLQhxXpA05
userPassword: {sha}FTSLQhxXpA05Transferring cleartext passwords is strongly discouraged where the underlying transport service cannot guarantee confidentiality. Transferring in cleartext may result in disclosure of the password to unauthorized parties.
| OID | 2.5.4.35 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.351. userPKCS12
This attribute provides a format for the exchange of personal identity information. The attribute is stored and requested in binary form, as userPKCS12;binary. The attribute values are PFX PDUs stored as binary data.
| OID | 2.16.840.1.113730.3.1.216 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.352. userSMIMECertificate
The userSMIMECertificate attribute contains certificates which can be used by mail clients for S/MIME. This attribute requests and stores data in a binary format. For example:
userSMIMECertificate;binary:: AAAAAA==
userSMIMECertificate;binary:: AAAAAA==| OID | 2.16.840.1.113730.3.1.40 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.353. vacationEndDate
This attribute shows the ending date of the user’s vacation period.
| OID | 2.16.840.1.113730.3.1.708 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.354. vacationStartDate
This attribute shows the start date of the user’s vacation period.
| OID | 2.16.840.1.113730.3.1.707 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Netscape Messaging Server |
8.355. x121Address
The x121Address attribute contains a user’s X.121 address.
| OID | 2.5.4.24 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
8.356. x500UniqueIdentifier
Reserved for future use. An X.500 identifier is a binary method of identification useful for differentiating objects when a distinguished name has been reused.
x500UniqueIdentifier:: AAAAAA==
x500UniqueIdentifier:: AAAAAA==| OID | 2.5.4.45 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
Chapter 9. Entry object class reference
This reference is an alphabetical list of the object classes accepted by the default schema. It gives a definition of each object class and lists its required and allowed attributes. The object classes listed are available to support entry information.
The required attributes listed for an object class must be present in the entry when that object class is added to the directory’s ldif file. If an object class has a superior object class, both of these object classes with all required attributes must be present in the entry. If required attributes are not listed in the ldif file, than the server will not restart.
The LDAP RFCs and X.500 standards allow for an object class to have more than one superior object class. This behavior is not currently supported by Directory Server.
9.1. account
The account object class defines entries for computer accounts. This object class is defined in RFC 1274.
Superior Class
top
OID
0.9.2342.19200300.100.4.5
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes for the entry. |
| userID | Gives the defined account’s user ID. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| host | Gives the host name for the machine on which the account resides. |
| localityName | Gives the city or geographical location of the entry. |
| organizationName | Gives the organization to which the account belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the account belongs. |
| seeAlso | Contains a URL to another entry or site with related information. |
9.2. accountpolicy
The accountpolicy object class defines entries for account inactivation or expiration policies. This is used for a user directory configuration entry, which works in conjunction with the Account Policy Plug-in configuration.
Superior Class
top
OID
1.3.6.1.4.1.11.1.3.2.2.1
| Attribute | Definition |
|---|---|
| accountInactivityLimit | Sets the period, in seconds, from the last login time of an account before that account is locked for inactivity. |
9.3. alias
The alias object class points to other directory entries. This object class is defined in RFC 2256.
Aliasing entries is not supported in Red Hat Directory Server.
Superior Class
top
OID
2.5.6.1
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| aliasedObjectName | Gives the distinguished name of the entry for which this entry is an alias. |
9.4. bootableDevice
The bootableDevice object class points to a device with boot parameters. This object class is defined in RFC 2307.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.12
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| commonName | Gives the common name of the device. |
| Attribute | Definition |
|---|---|
| bootFile | Gives the boot image file. |
| bootParameter | Gives the parameters used by the boot process for the device. |
| description | Gives a text description of the entry. |
| localityName | Gives the city or geographical location of the entry. |
| organizationName | Gives the organization to which the device belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the device belongs. |
| owner | Gives the DN (distinguished name) of the person responsible for the device. |
| seeAlso | Contains a URL to another entry or site with related information. |
| serialNumber | Contains the serial number of the device. |
9.5. cacheObject
The cacheObject is an object that contains the time to live (ttl) attribute type. This object class is defined in the LDAP Caching Internet Draft.
Superior Class
top
OID
1.3.6.1.4.1.250.3.18
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| Attribute | Definition |
|---|---|
| timeToLive | The time that the object remains (lives) in the cache. |
9.6. cosClassicDefinition
The cosClassicDefinition object class defines a class of service template entry using the entry’s DN (distinguished name), given in the cosTemplateDn attribute, and the value of one of the target attributes, specified in the cosSpecifier attribute.
This object class is defined in RFC 1274.
Superior Class
cosSuperDefinition
OID
2.16.840.1.113730.3.2.100
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| cosAttribute |
Provides the name of the attribute for which the CoS generates a value. There can be more than one |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| cosSpecifier | Specifies the attribute value used by a classic CoS, which, along with the template entry’s DN, identifies the template entry. |
| cosTemplateDn | Provides the DN of the template entry which is associated with the CoS definition. |
| description | Gives a text description of the entry. |
9.7. cosDefinition
The cosDefinition object class defines which class of service is being used; this object class provide compatibility with the DS4.1 CoS Plug-in.
This object class is defined in RFC 1274.
Superior Class
top
OID
2.16.840.1.113730.3.2.84
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| aci | Evaluates what rights are granted or denied when Directory Server receives an LDAP request from a client. |
| commonName | Gives the common name of the entry. |
| cosAttribute |
Provides the name of the attribute for which the CoS generates a value. There can be more than one |
| cosSpecifier | Specifies the attribute value used by a classic CoS, which, along with the template entry’s DN, identifies the template entry. |
| cosTargetTree | Defines the subtrees in the directory to which the CoS schema applies. |
| cosTemplateDn | Provides the DN of the template entry which is associated with the CoS definition. |
| userID | Gives the user ID for the entry. |
9.8. cosIndirectDefinition
The cosIndirectDefinition defines the template entry using the value of one of the target entry’s attributes. The attribute of the target entry is specified in the cosIndirectSpecifier attribute.
This object class is defined by Directory Server.
Superior Class
cosSuperDefinition
OID
2.16.840.1.113730.3.2.102
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| cosAttribute |
Provides the name of the attribute for which the CoS generates a value. There can be more than one |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| cosIndirectSpecifier | Specifies the attribute value used by an indirect CoS to identify the template entry. |
| description | Gives a text description of the entry. |
9.9. cosPointerDefinition
This object class identifies the template entry associated with the CoS definition using the template entry’s DN value. The DN of the template entry is specified in the cosIndirectSpecifier attribute.
This object class is defined by Directory Server.
Superior Class
cosSuperDefinition
OID
2.16.840.1.113730.3.2.101
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| cosAttribute |
Provides the name of the attribute for which the CoS generates a value. There can be more than one |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| cosTemplateDn | Provides the DN of the template entry which is associated with the CoS definition. |
| description | Gives a text description of the entry. |
9.10. cosSuperDefinition
All CoS definition object classes inherit from the cosSuperDefinition object class.
This object class is defined by Directory Server.
Superior Class
LDAPsubentry
OID
2.16.840.1.113730.3.2.99
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| cosAttribute |
Provides the name of the attribute for which the CoS generates a value. There can be more than one |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| description | Gives a text description of the entry. |
9.11. cosTemplate
The cosTemplate object class contains a list of the shared attribute values for the CoS.
This object class is defined by Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.128
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| cosPriority | Specifies which template provides the attribute value when CoS templates compete to provide an attribute value. |
9.12. country
The country object class defines entries which represent countries. This object class is defined in RFC 2256.
Superior Class
top
OID
2.5.6.2
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| countryName | Contains the two-character code representing country names, as defined by ISO, in the directory. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| searchGuide | Specifies information for suggested search criteria when using the entry as the base object in the directory tree for a search. |
9.13. dcObject
The dcObject object class allows domain components to be defined for an entry. This object class is defined as auxiliary because it is commonly used in combination with another object class, such as o (organization), ou (organizationalUnit), or l (locality).
For example:
This object class is defined in RFC 2247.
Superior Class
top
OID
1.3.6.1.4.1.1466.344
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| dc | Contains one component of a domain name. |
9.14. device
The device object class stores information about network devices, such as printers, in the directory. This object class is defined in RFC 2247.
Superior Class
top
OID
2.5.6.14
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the device. |
| commonName | Gives the common name of the device. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| localityName | Gives the city or geographical location of the entry. |
| organizationName | Gives the organization to which the device belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the device belongs. |
| owner | Gives the DN (distinguished name) of the person responsible for the device. |
| seeAlso | Contains a URL to another entry or site with related information. |
| serialNumber | Contains the serial number of the device. |
9.15. document
The document object class defines directory entries that represent documents. RFC 1247.
Superior Class
top
OID
0.9.2342.19200300.100.4.6
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| documentIdentifier | Gives the unique ID for the document. |
| Attribute | Definition |
|---|---|
| abstract | Contains the abstract for the document. |
| audio | Stores a sound file in binary format. |
| authorCn | Gives the author’s common name or given name. |
| authorSn | Gives the author’s surname. |
| commonName | Gives the common name of the entry. |
| description | Gives a text description of the entry. |
| dITRedirect | Contains the DN (distinguished name) of the entry to use as a redirect for the document entry. |
| documentAuthor | Contains the DN (distinguished name) of the author. |
| documentLocation | Gives the location of the original document. |
| documentPublisher | Identifies the person or organization that published the document. |
| documentStore | |
| documentTitle | Contains the title of the document. |
| documentVersion | Gives the version number of the document. |
| info | Contains information about the document. |
| jpegPhoto | Stores a JPG image. |
| keyWords | Contains keywords related to the document. |
| localityName | Gives the city or geographical location of the entry. |
| lastModifiedBy | Gives the DN (distinguished name) of the last user which modified the document entry. |
| lastModifiedTime | Gives the time of the last modification. |
| manager | Gives the DN (distinguished name) of the entry’s manager. |
| organizationName | Gives the organization to which the document belongs. |
| obsoletedByDocument | Gives the DN (distinguished name) of another document entry which obsoletes this document. |
| obsoletesDocument | Gives the DN (distinguished name) of another document entry which is obsoleted by this document. |
| organizationalUnitName | Gives the organizational unit or division to which the document belongs. |
| photo | Stores a photo of the document in binary format. |
| seeAlso | Contains a URL to another entry or site with related information. |
| subject | Describes the subject of the document. |
| uniqueIdentifier | Distinguishes between two entries when a distinguished name has been reused. |
| updatedByDocument | Gives the DN (distinguished name) of another document entry which updates this document. |
| updatesDocument | Gives the DN (distinguished name) of another document entry which is updated by this document. |
9.16. documentSeries
The documentSeries object class defines an entry that represents a series of documents. This object class is defined in RFC 1274.
Superior Class
top
OID
0.9.2342.19200300.100.4.9
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| localityName | Gives the place where the document series is physically located. |
| organizationName | Gives the organization to which the document series belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the series belongs. |
| seeAlso | Contains a URL to another entry or site with related information. |
| telephoneNumber | Gives the telephone number of the person responsible for the document series. |
9.17. domain
The domain object class defines directory entries that represent DNS domains. Use the dc attribute to name entries of this object class.
This object class is also used for Internet domain names, such as example.com.
The domain object class can only be used for a directory entry which does not correspond to an organization, organizational unit, or any other object which has an object class defined for it. object for which an object class has been defined.
This object class is defined in RFC 2252.
Superior Class
top
OID
0.9.2342.19200300.100.4.13
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| dc | Contains one component of a domain name. |
| Attribute | Definition |
|---|---|
| associatedName | Gives the name of an entry within the organizational directory tree which is associated with a DNS domain. |
| businessCategory | Gives the type of business in which this domain is engaged. |
| description | Gives a text description of the entry. |
| destinationIndicator | Gives the country and city associated with the entry; this was once required to provide public telegram service. |
| facsimileTelephoneNumber | Gives the fax number for the domain. |
| internationalISDNNumber | Gives the ISDN number for the domain. |
| localityName | Gives the city or geographical location of the entry. |
| organizationName | Gives the organization to which the entry belongs. |
| physicalDeliveryOfficeName | Gives a location where physical deliveries can be made. |
| postOfficeBox | Gives the post office box number for the domain. |
| postalAddress | Contains the mailing address for the domain. |
| postalCode | Gives the postal code for the domain, such as the zip code in the United States. |
| preferredDeliveryMethod | Shows the person’s preferred method of contact or message delivery. |
| General_Atttribute_registeredAddress | Gives a postal address suitable to receive expedited documents when the recipient must verify delivery. |
| searchGuide | Specifies information for suggested search criteria when using the entry as the base object in the directory tree for a search. |
| seeAlso | Contains a URL to another entry or site with related information. |
| stateOrProvinceName | Gives the state or province where the domain is located. |
| streetaddress | Gives the street name and address number for the domain’s physical location. |
| telephoneNumber | Gives the phone number for the domain. |
| teletexTerminalIdentifier | Gives the ID for a domain’s teletex terminal. |
| telexNumber | Gives the telex number for the domain. |
| userPassword | Stores the password with which the entry can bind to the directory. |
| x121Address | Gives the X.121 address for the domain. |
9.18. domainRelatedObject
The domainRelatedObject object class defines entries that represent DNS or NRS domains which are equivalent to an X.500 domain, such as an organization or organizational unit.
This object class is defined in RFC 1274.
Superior Class
top
OID
0.9.2342.19200300.100.4.17
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| associatedDomain | Specifies a DNS domain associated with an object in the directory tree. |
9.19. dSA
The dSA object class defines entries that represent DSAs.
This object class is defined in RFC 1274.
Superior Class
top
OID
2.5.6.13
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| presentationAddress | Contains the entry’s OSI presentation address. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| knowledgeinformation | |
| localityName | Gives the city or geographical location of the entry. |
| organizationName | Gives the organization to which the entry belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| seeAlso | Contains a URL to another entry or site with related information. |
| supportedApplicationContext | Contains the identifiers of OSI application contexts. |
9.20. extensibleObject
When present in an entry, extensibleObject permits the entry to hold optionally any attribute. The allowed attribute list of this class is implicitly the set of all attributes known to the server.
This object class is defined in RFC 2252.
Superior Class
top
OID
1.3.6.1.4.1.1466.101.120.111
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
Allowed Attributes
All attributes known to the server.
9.21. friendlyCountry
The friendlyCountry object class defines country entries within the directory. This object class allows more friendly names than the country object class.
This object class is defined in RFC 1274.
Superior Class
top
OID
0.9.2342.19200300.100.4.18
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| friendlyCountryName | Stores the human-readable country name. |
| countryName | Contains the two-character code representing country names, as defined by ISO, in the directory. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| searchGuide | Specifies information for suggested search criteria when using the entry as the base object in the directory tree for a search. |
9.22. groupOfCertificates
The groupOfCertificates object class describes a set of X.509 certificates. Any certificate that matches one of the memberCertificateDescription values is considered a member of the group.
Superior Class
top
OID
2.16.840.1.113730.3.2.31
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| businessCategory | Gives the type of business in which the group is engaged. |
| description | Gives a text description of the entry. |
| memberCertificateDescription | Contains the values used to determine if a particular certificate is a member of this group. |
| organizationName | Gives the organization to which the entry belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| owner | Contains the DN (distinguished name) of the person responsible for the group. |
| seeAlso | Contains a URL to another entry or site with related information. |
9.23. groupOfMailEnhancedUniqueNames
The groupOfMailEnhancedUniqueNames object class is used for a mail group which must have unique members. This object class is defined for Netscape Messaging Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.5
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| businessCategory | Gives the type of business in which the group is engaged. |
| description | Gives a text description of the entry. |
| mailEnhancedUniqueMember | Contains a unique DN value to identify a member of the mail group. |
| organizationName | Gives the organization to which the entry belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| owner | Contains the DN (distinguished name) of the person responsible for the group. |
| seeAlso | Contains a URL to another entry or site with related information. |
9.24. groupOfNames
The groupOfNames object class contains entries for a group of names. This object class is defined in RFC 2256.
The definition for this object class in Directory Server differs from the standard definition. In the standard definition, member is a required attribute, while in Directory Server it is an allowed attribute. Directory Server, therefore, allows a group to have no members.
Superior Class
top
OID
2.5.6.9
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| businessCategory | Gives the type of business in which the entry is engaged. |
| description | Gives a text description of the entry. |
| member | Contains the DN (distinguished name) of a group member. |
| organizationName | Gives the organization to which the entry belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| owner | Contains the DN (distinguished name) of the person responsible for the group. |
| seeAlso | Contains a URL to another entry or site with related information. |
9.25. groupOfUniqueNames
The groupOfUniqueNames object class defines a group which contains unique names.
The definition for this object class in Directory Server differs from the standard definition. In the standard definition, uniqueMember is a required attribute, while in Directory Server it is an allowed attribute. Directory Server, therefore, allows a group to have no members.
This object class is defined in RFC 2256.
Superior Class
top
OID
2.5.6.17
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| businessCategory | Gives the type of business in which the entry is engaged. |
| description | Gives a text description of the entry. |
| organizationName | Gives the organization to which the entry belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| owner | Contains the DN (distinguished name) of the person responsible for the group. |
| seeAlso | Contains a URL to another entry or site with related information. |
| uniqueMember | Contains the DN (distinguished name) of a member of the group; this DN must be unique. |
9.26. groupOfURLs
The groupOfURLs object class is an auxiliary object class for the groupOfUniqueNames and groupOfNames object classes. This group consists of a list of labeled URLs.
Superior Class
top
OID
2.16.840.1.113730.3.2.33
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| businessCategory | Gives the type of business in which the group is engaged. |
| description | Gives a text description of the entry. |
| memberURL | Contains a URL associated with each member of the group. |
| organizationName | Gives the organization to which the entry belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| owner | Contains the DN (distinguished name) of the person responsible for the group. |
| seeAlso | Contains a URL to another entry or site with related information. |
9.27. ieee802Device
The ieee802Device object class points to a device with a MAC address. This object class is defined in RFC 2307.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.11
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| commonName | Gives the common name of the device. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| localityName | Gives the city or geographical location of the entry. |
| macAddress | Gives the MAC address of the device. |
| organizationName | Gives the organization to which the device belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the device belongs. |
| owner | Gives the DN (distinguished name) of the person responsible for the device. |
| seeAlso | Contains a URL to another entry or site with related information. |
| serialNumber | Contains the serial number of the device. |
9.28. inetAdmin
The inetAdmin object class is a marker for an administrative group or user. This object class is defined for the Netscape Delegated Administrator.
Superior Class
top
OID
2.16.840.1.113730.3.2.112
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| adminRole | Identifies a role to which the administrative user belongs. |
| memberOf | Contains a group name to which the administrative user belongs. This is dynamically managed by the MemberOf Plug-in. |
9.29. inetDomain
The inetDomain object class is a auxiliary class for virtual domain nodes. This object class is defined for the Netscape Delegated Administrator.
Superior Class
top
OID
2.16.840.1.113730.3.2.129
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| inetDomainBaseDN | Defines the base DN of the user subtree for a DNS domain. |
| inetDomainStatus | Gives the status of the domain. The status can be active, inactive, or deleted. |
9.30. inetOrgPerson
The inetOrgPerson object class defines entries representing people in an organization’s enterprise network. This object class inherits the commonName and surname attributes from the person object class.
This object class is defined in RFC 2798.
Superior Class
person
OID
2.16.840.1.113730.3.2.2
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| surname | Gives the person’s family name or last name. |
| Attribute | Definition |
|---|---|
| audio | Stores a sound file in binary format. |
| businessCategory | Gives the type of business in which the entry is engaged. |
| carLicense | Gives the license plate number of the person’s vehicle. |
| departmentNumber | Gives the department for which the person works. |
| description | Gives a text description of the entry. |
| destinationIndicator | Gives the country and city associated with the entry; this was once required to provide public telegram service. |
| displayName | Shows the preferred name of a person to use when displaying entries. |
| employeeNumber | Contains the person’s employee number. |
| employeeType | Shows the person’s type of employment (for example, full time). |
| facsimileTelephoneNumber | Contains the person’s fax number. |
| givenName | Contains the person’s first name. |
| homeTelephoneNumber | Gives the person’s home phone number. |
| homePostalAddress | Gives the person’s home mailing address. |
| initials | Gives the person’s initials. |
| internationalISDNNumber | Contains the ISDN number for the entry. |
| jpegPhoto | Stores a JPG image. |
| localityName | Gives the city or geographical location of the entry. |
| labeledURI | Contains a URL which is relevant to the entry. |
| | Contains the person’s email address. |
| manager | Contains the DN (distinguished name) of the direct supervisor of the person entry. |
| mobile | Gives the person’s mobile phone number. |
| organizationName | Gives the organization to which the entry belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| pagerTelephoneNumber | Gives the person’s pager number. |
| photo | Stores a photo of a person, in binary format. |
| physicalDeliveryOfficeName | Gives a location where physical deliveries can be made. |
| postOfficeBox | Gives the post office box number for the entry. |
| postalAddress | Contains the mailing address for the entry. |
| postalCode | Gives the postal code for the entry, such as the zip code in the United States. |
| preferredDeliveryMethod | Shows the person’s preferred method of contact or message delivery. |
| preferredLanguage | Gives the person’s preferred written or spoken language. |
| General_Atttribute_registeredAddress | Gives a postal address suitable to receive expedited documents when the recipient must verify delivery. |
| roomNumber | Gives the room number where the person is located. |
| secretary | Contains the DN (distinguished name) of the person’s secretary or administrative assistant. |
| seeAlso | Contains a URL to another entry or site with related information. |
| stateOrProvinceName | Gives the state or province where the entry is located. |
| streetaddress | Gives the street name and number for the person’s physical location. |
| telephoneNumber | Gives the telephone number for the entry. |
| teletexTerminalIdentifier | Gives the identifier for the person’s teletex terminal. |
| telexNumber | Gives the telex number associated with the entry. |
| title | Shows the person’s job title. |
| userID | Contains the person’s user ID (usually his logon ID). |
| userCertificate | Stores a user’s certificate in cleartext (not used). |
| userPassword | Stores the password with which the entry can bind to the directory. |
| userSMIMECertificate | Stores the person’s certificate in binary form so it can be used by S/MIME clients. |
| x121Address | Gives the X.121 address for the person. |
| x500UniqueIdentifier | Reserved for future use. |
9.31. inetSubscriber
The inetSubscriber object class is used for general user account management. This object class is defined for the Netscape subscriber interoperability.
Superior Class
top
OID
2.16.840.1.113730.3.2.134
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| inetSubscriberAccountId | Contains a unique attribute linking the subscriber to a billing system. |
| inetSubscriberChallenge | Contains some kind of question or prompt, the challenge phrase, which is used to confirm the identity of the user. |
| inetSubscriberResponse | Contains the answer to the challenge question. |
9.32. inetUser
The inetUser object class is an auxiliary class which must be present in an entry in order to deliver subscriber services. This object class is defined for the Netscape subscriber interoperability.
Superior Class
top
OID
2.16.840.1.113730.3.2.130
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| inetUserHttpURL | Contains web addresses associated with the user. |
| inetUserStatus | Gives the status of the user. The status can be active, inactive, or deleted. |
| memberOf | Contains a group name to which the user belongs. This is dynamically managed by the MemberOf Plug-in. |
| userID | Contains the person’s user ID (usually his logon ID). |
| userPassword | Stores the password with which the user can use to access the user account. |
9.33. ipHost
The ipHost object class stores IP information about a host. This object class is defined in RFC 2307.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.6
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| commonName | Gives the common name of the device. |
| ipHostNumber | Contains the IP address of the device or host. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| localityName | Gives the city or geographical location of the entry. |
| manager | Contains the DN (distinguished name) of the maintainer or supervisor of the entry. |
| organizationName | Gives the organization to which the device belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the device belongs. |
| owner | Gives the DN (distinguished name) of the person responsible for the device. |
| seeAlso | Contains a URL to another entry or site with related information. |
| serialNumber | Contains the serial number of the device. |
9.34. ipNetwork
The ipNetwork object class stores IP information about a network. This object class is defined in RFC 2307.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.7
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| commonName | Gives the common name of the device. |
| ipNetworkNumber | Contains the IP number for the network. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| localityName | Gives the city or geographical location of the entry. |
| manager | Contains the DN (distinguished name) of the maintainer or supervisor of the entry. |
| ipNetmaskNumber | Contains the IP netmask for the network. |
9.35. ipProtocol
The ipProtocol object class shows the IP protocol version. This object class is defined in RFC 2307.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.4
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| commonName | Gives the common name of the device. |
| ipProtocolNumber | Contains the IP protocol number for the network. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
9.36. ipService
The ipService object class stores information about the IP service. This object class is defined in RFC 2307.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.3
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| commonName | Gives the common name of the device. |
| ipServicePort | Gives the port number used by the IP service. |
| ipServiceProtocol | Contains the IP protocol number for the service. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
9.37. labeledURIObject
This object class can be added to existing directory objects to allow URI values to be included. Using this object class does not preclude including the labeledURI attribute type directly in other object classes as appropriate.
This object class is defined in RFC 2079.
Superior Class
top
OID
1.3.6.1.4.1.250.3.15
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| labeledURI | Gives a URI which is relevant to the entry’s object. |
9.38. locality
The locality object class defines entries that represent localities or geographic areas.
This object class is defined in RFC 2256.
Superior Class
top
OID
2.5.6.3
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| localityName | Gives the city or geographical location of the entry. |
| searchGuide | Specifies information for suggested search criteria when using the entry as the base object in the directory tree for a search. |
| seeAlso | Contains a URL to another entry or site with related information. |
| stateOrProvinceName | Gives the state or province associated with the locality. |
| streetaddress | Gives a street and number associated with the locality. |
9.39. mailGroup
The mailGroup object class defines the mail attributes for a group. This object is defined in the schema for the Netscape Messaging Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.4
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| | Stores email addresses for the group. |
| mailAlternateAddress | Contains secondary email addresses for the group. |
| mailHost | Contains the host name of the mail server. |
| owner | Contains the DN (distinguished name) of the person responsible for the group. |
9.40. mailRecipient
The mailRecipient object class defines a mail account for a user. This object is defined in the schema for the Netscape Messaging Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.3
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| | Stores email addresses for the group. |
| mailAccessDomain | Contains the domain from which the user can access the messaging server. |
| mailAlternateAddress | Contains secondary email addresses for the group. |
| mailAutoReplyMode | Specifies whether autoreply mode for the account is enabled. |
| mailAutoReplyText | Contains the text use for automatic reply emails. |
| mailDeliveryOption | Specifies the mail delivery mechanism to be used for the mail user. |
| mailForwardingAddress | Specifies the mail delivery mechanism to use for the mail user. |
| mailHost | Contains the host name of the mail server. |
| mailMessageStore | Specifies the location of the user’s mail box. |
| mailProgramDeliveryInfo | Specifies the commands used for programmed mail delivery. |
| mailQuota | Specifies the disk space allowed for the user’s mail box. |
| mailRoutingAddress | Contains a routing address to use when forwarding the mail from this entry’s account to another messaging server. |
| multiLineDescription | Contains a text description of the entry which spans more than one line. |
| userID | Gives the defined account’s user ID. |
| userPassword | Stores the password with which the entry can access the account. |
9.41. mepManagedEntry
The mepManagedEntry object class identifies an entry which was been generated by an instance of the Managed Entries Plug-in. This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.319
| Attribute | Definition |
|---|---|
| mepManagedBy | Gives the DN of the originating entry which corresponds to the managed entry. |
9.42. mepOriginEntry
The mepOriginEntry object class identifies an entry which is within a subtree that is monitored by an instance of the Managed Entries Plug-in and which has had a managed entry created by the plug-in, for which this is the originating entry. This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.320
| Attribute | Definition |
|---|---|
| mepManagedEntry | Gives the DN of the managed entry entry which was created by the Managed Entries Plug-in instance and which corresponds to this originating entry. |
9.43. mepTemplateEntry
The mepTemplateEntry object class identifies an entry which is used as a template by an instance of the Managed Entries Plug-in to create the managed entries. This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.321
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| mepMappedAttr | Contains an attribute-token pair that the plug-in uses to create an attribute in the managed entry with a value taken from the originating entry. |
| mepRDNAttr | Specifies which attribute to use as the naming attribute in the managed entry. |
| mepStaticAttr | Contains an attribute-value pair that will be used, with that specified value, in the managed entry. |
9.44. netscapeCertificateServer
The netscapeCertificateServer object class stores information about a Netscape certificate server. This object is defined in the schema for the Netscape Certificate Management System.
Superior Class
top
OID
2.16.840.1.113730.3.2.18
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
9.45. netscapeDirectoryServer
The netscapeDirectoryServer object class stores information about a Directory Server instance. This object is defined in the schema for the Netscape Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.23
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
9.46. NetscapeLinkedOrganization
NetscapeLinkedOrganization is an auxiliary object class. This object is defined in the schema for the Netscape server suite.
Superior Class
top
OID
1.3.6.1.4.1.1466.101.120.141
| Attribute | Definition |
|---|---|
| parentOrganization | Identifies the parent organization for the linked organization defined for the server suite. |
9.47. netscapeMachineData
The netscapeMachineData object class distinguishes between machine data and non-machine data. This object is defined in the schema for the Netscape Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.32
9.48. NetscapePreferences
NetscapePreferences is an auxiliary object class which stores the user preferences. This object is defined by Netscape.
Superior Class
top
OID
1.3.6.1.4.1.1466.101.120.142
| Attribute | Definition |
|---|---|
| preferredLanguage | Gives the person’s preferred written or spoken language. |
| preferredLocale | Gives the person’s preferred locale. A locale setting defines cultural or national settings like date formats and currencies. |
| preferredTimeZone | Gives the person’s preferred time zone. |
9.49. netscapeReversiblePasswordObject
netscapeReversiblePasswordObject is an auxiliary object class to store a password. This object is defined in the schema for the Netscape Web Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.154
| Attribute | Definition |
|---|---|
| netscapeReversiblePassword | Contains a password used for HTTP Digest/MD5 authentication. |
9.50. netscapeServer
The netscapeServer object class contains instance-specific information about a Netscape server and its installation.
Superior Class
top
OID
2.16.840.1.113730.3.2.10
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| administratorContactInfo | Contains the contact information for the server administrator. |
| adminUrl | Contains the URL for the Administration Server used by the instance. |
| description | Gives a text description of the entry. |
| installationTimeStamp | Contains the time that the server instance was installed. |
| serverHostName | Contains the host name of the server on which the Directory Server instance is running. |
| serverProductName | Contains the product name of the server type. |
| serverRoot | Specifies the top directory where the server product is installed. |
| serverVersionNumber | Contains the product version number. |
| userPassword | Stores the password with which the entry can bind to the directory. |
9.51. netscapeWebServer
The netscapeWebServer object class identifies an installed Netscape Web Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.29
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| nsServerID | Contains the server’s name or ID. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| nsServerPort | Contains the server’s port number. |
9.52. newPilotPerson
The newPilotPerson object class is a subclass of the person to allow additional attributes to be assigned to entries of the person object class. This object class inherits the commonName and surname attributes from the person object class.
This object class is defined in Internet White Pages Pilot.
Superior Class
person
OID
0.9.2342.19200300.100.4.4
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| surname | Gives the person’s family name or last name. |
| Attribute | Definition |
|---|---|
| businessCategory | Gives the type of business in which the entry is engaged. |
| description | Gives a text description of the entry. |
| favoriteDrink | Gives the person’s favorite drink. |
| homeTelephoneNumber | Gives the person’s home phone number. |
| homePostalAddress | Gives the person’s home mailing address. |
| janetMailbox | Gives the person’s email address; this is primarily for use in Great Britain or organizations which do no use RFC 822 mail addresses. |
| | Contains the person’s email address. |
| mailPreferenceOption | Indicates the user’s preference for including his name on mailing lists (electronic or physical). |
| mobile | Gives the person’s mobile phone number. |
| organizationalStatus | Gives the common job category for a person’s function. |
| otherMailbox | Contains values for electronic mailbox types other than X.400 and RFC 822. |
| pagerTelephoneNumber | Gives the person’s pager number. |
| Personal_Signature_personalSignature | Contains the person’s signature file. |
| personalTitle | Gives the person’s honorific. |
| preferredDeliveryMethod | Shows the person’s preferred method of contact or message delivery. |
| roomNumber | Gives the room number where the person is located. |
| secretary | Contains the DN (distinguished name) of the person’s secretary or administrative assistant. |
| seeAlso | Contains a URL to another entry or site with related information. |
| telephoneNumber | Gives the telephone number for the entry. |
| userID | Contains the person’s user ID (usually his logon ID). |
| userClass | Describes the type of computer user this entry is. |
| userPassword | Stores the password with which the entry can bind to the directory. |
9.53. nisMap
This object class points to a NIS map.
This object class is defined in RFC 2307, which defines object classes and attributes to use LDAP as a network information service.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.13
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| nisMapName | Contains the NIS map name. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
9.54. nisNetgroup
This object class contains a netgroup used within a NIS domain. Adding this object class allows administrators to use netgroups to control login and service authentication in NIS.
This object class is defined in RFC 2307, which defines object classes and attributes to use LDAP as a network information service.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.8
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| memberNisNetgroup | Merges the attribute values of another netgroup into the current one by listing the name of the merging netgroup. |
| nisNetgroupTriple |
Contains a user name ( |
9.55. nisObject
This object class contains information about an object in a NIS domain.
This object class is defined in RFC 2307, which defines object classes and attributes to use LDAP as a network information service.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.10
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| NisMapEntry | Identifies the NIS map entry. |
| nisMapName | Contains the name of the NIS map. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
9.56. nsAdminConfig
This object class stores the configuration parameters for the Administration Server. This object is defined for the Administration Services.
Superior Class
nsConfig
OID
nsAdminConfig-oid
| Attribute | Definition |
|---|---|
| nsAdminAccessAddresses | Identifies the Administration Server IP addresses. |
| nsAdminAccessHosts | Contains the Administration Server host name or a list of Administration Server host names. |
| nsAdminCacheLifetime | Notes the length of the cache timeout period. |
| nsAdminCgiWaitPid | Contains the PID of the CGI process the server is waiting for. |
| nsAdminEnableEnduser | Sets whether to allow or disallow end user access to the Administration Server web services pages. |
| nsAdminOneACLDir | Contains the path of the local ACL directory for the Administration Server. |
| nsAdminUsers | Points to the file which contains the admin user info. |
9.57. nsAdminConsoleUser
This object class stores the configuration parameters for the Administration Server. This object is defined for the Administration Services.
Superior Class
top
OID
nsAdminConsoleUser-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| nsPreference | Stores preference information for console settings. |
9.58. nsAdminDomain
This object class stores user information to access Admin Console. This object is defined for the Administration Services.
Superior Class
organizationalUnit
OID
nsAdminDomain-oid
| Attribute | Definition |
|---|---|
| nsAdminDomainName | Identifies the administration domain for the servers. |
9.59. nsAdminGlobalParameters
This object class stores the configuration parameters for the Administration Server. This object is defined for the Administration Services.
Superior Class
top
OID
nsAdminGlobalParameters-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| nsAdminEndUserHTMLIndex | Sets whether to allow or disallow end-user access to the HTML index pages. |
| nsNickName | Gives the nickname for the application. |
9.60. nsAdminGroup
This object class stores group information for administrator users in the Administration Server. This object is defined for the Administration Services.
Superior Class
top
OID
nsAdminGroup-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| nsAdminGroupName | Contains the name for the admin group. |
| nsAdminSIEDN | Shows the DN of the server instance entry (SIE) for the Administration Server instance. |
| nsConfigRoot | Gives the full path to the Administration Server instance’s configuration directory. |
9.61. nsAdminObject
This object class contains information about an object used by Administration Server, such as a task. This object is defined for the Administration Services.
Superior Class
top
OID
nsAdminObject-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| nsClassname | Contains the class name associated with the task or resource editor for the Administration Server. |
| nsJarfilename | Gives the name of the JAR file used by the Administration Server Console to access the object. |
9.62. nsAdminResourceEditorExtension
This object class contains an extension used by the Console Resource Editor. This object is defined for the Administration Services.
Superior Class
nsAdminObject
OID
nsAdminResourceEditorExtension-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| nsAdminAccountInfo | Contains information about the Administration Server account. |
| nsDeleteclassname | Contains the name of a class to be deleted. |
9.63. nsAdminServer
This object class defines the Administration Server instance. This object is defined for the Administration Services.
Superior Class
top
OID
nsAdminServer-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| nsServerID |
Contains the Directory Server ID, such as |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
9.64. nsAIMpresence
nsAIMpresence is an auxiliary object class which defines the status of an AOL instance messaging account. This object is defined for Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.300
| Attribute | Definition |
|---|---|
| nsAIMid | Contains the AIM user ID for the entry. |
| nsAIMStatusGraphic | Contains a pointer to the graphic image which indicates the AIM account’s status. |
| nsAIMStatusText | Contains the text to indicate the AIM account’s status. |
9.65. nsApplication
nsApplication defines an application or server entry. This is defined by Netscape.
Superior Class
top
OID
nsApplication-oid
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| installationTimeStamp | Contains the time that the server instance was installed. |
| nsBuildNumber | Contains the build number for the server instance. |
| nsBuildSecurity | Contains the level of security used to make the build. |
| nsExpirationDate | Contains the date that the license for the application expires. |
| nsInstalledLocation | For servers which are version 7.1 or older, shows the installation directory for the server. |
| nsLdapSchemaVersion | Gives the version of the LDAP schema files used by Directory Server. |
| nsNickName | Gives the nickname for the application. |
| nsProductName | Gives the name of the server product. |
| nsProductVersion | Shows the version number of the server product. |
| nsRevisionNumber | Contains the revision number (minor version) for the product. |
| nsSerialNumber | Gives the serial number assigned to the server product. |
| nsServerMigrationClassname | Gives the class to use to migrate a server instance. |
| nsServerCreationClassname | Gives the class to use to create a server instance. |
| nsVendor | Contains the name of the vendor who designed the server. |
9.66. nsCertificateServer
The nsCertificateServer object class stores information about a Red Hat Certificate System instance. This object is defined in the schema for the Certificate System.
Superior Class
top
OID
nsCertificateServer-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| nsServerID | Contains the server’s name or ID. |
| Attribute | Definition |
|---|---|
| nsCertConfig | Contains configuration settings for a Red Hat Certificate System instance. |
| nsServerPort | Contains the server’s port number. |
| serverHostName | Contains the host name of the server on which Directory Server instance is running. |
9.67. nsComplexRoleDefinition
Any role that is not a simple role is, by definition, a complex role.
This object class is defined by Directory Server.
Superior Class
nsRoleDefinition
OID
2.16.840.1.113730.3.2.95
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| description | Gives a text description of the entry. |
9.68. nsContainer
Some entries do not define any specific entity, but they create a defined space within the directory tree as a parent entry for similar or related child entries. These are container entries, and they are identified by the nsContainer object class.
Superior Class
top
OID
2.16.840.1.113730.3.2.104
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| cn | Gives the common name of the entry. |
9.69. nsCustomView
The nsCustomView object class defines information about custom views of Directory Server data.
Superior Class
nsAdminObject
OID
nsCustomView-oid
| Attribute | Definition |
|---|---|
| nsDisplayName | Contains the name of the custom view setting profile. |
9.70. nsDefaultObjectClasses
nsDefaultObjectClasses sets default object classes to use when creating a new object of a certain type within the directory. This is defined for Administration Services.
Superior Class
top
OID
nsDefaultObjectClasses-oid
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| commonName | Gives the common name of the device. |
| Attribute | Definition |
|---|---|
| nsDefaultObjectClass | Contains an object class to assign by default to an object type. |
9.71. nsDirectoryInfo
nsDirectoryInfo contains information about a directory instance. This is defined for Administration Services.
Superior Class
top
OID
nsDirectoryInfo-oid
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| commonName | Gives the common name of the device. |
| Attribute | Definition |
|---|---|
| nsBindDN | Contains the bind DN defined for the server in its server instance entry. |
| nsBindPassword | Contains the password for the bind identity in the SIE. |
| nsDirectoryFailoverList |
Contains a list of URLs of other Directory Server instances to use for failover support if the instance in |
| nsDirectoryInfoRef | Contains a reference to a distinguished name (DN) in the directory. |
| nsDirectoryURL | Contains a URL to access Directory Server instance. |
9.72. nsDirectoryServer
nsDirectoryServer is the defining object class for a Directory Server instance. This is defined for Directory Server.
Superior Class
top
OID
nsDirectoryServer-oid
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| nsServerID | Contains the server’s name or ID. |
| Attribute | Definition |
|---|---|
| nsBaseDN | Contains the base DN for the server instance. |
| nsBindDN | Contains the bind DN defined for the server in its server instance entry. |
| nsBindPassword | Contains the password for the bind identity in the SIE. |
| nsSecureServerPort | Contains the server’s TLS port number. |
| nsServerPort | Contains the server’s port number. |
| serverHostName | Contains the host name of the server on which the Directory Server instance is running. |
9.73. nsFilteredRoleDefinition
The nsFilteredRoleDefinition object class defines how entries are assigned to the role, depending upon the attributes contained by each entry.
This object class is defined in Directory Server.
Superior Class
nsComplexRoleDefinition
OID
2.16.840.1.113730.3.2.97
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| nsRoleFilter | Specifies the filter used to identify entries in the filtered role. |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| description | Gives a text description of the entry. |
9.74. nsGlobalParameters
The nsGlobalParameters object class contains global preference settings.
This object class is defined in Administrative Services.
Superior Class
top
OID
nsGlobalParameters-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| nsGroupRDNComponent | Defines the default attribute type used in the RDN of the group entry. |
| nsUniqueAttribute | Defines a unique attribute in the preferences. |
| nsUserIDFormat |
Sets the format to generate the user ID from the |
| nsUserRDNComponent | Sets the attribute type to use as the naming component in the user DN. |
| nsNYR | Not used. |
| nsWellKnownJarfiles | Not used. |
9.75. nsHost
The nsHost object class stores information about the server host.
This object class is defined in Administrative Services.
Superior Class
top
OID
nsHost-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| localityName | Gives the city or geographical location of the entry. |
| nsHardwarePlatform |
Identifies the hardware platform for the host on which the Directory Server instance is running. This is the same information as running |
| nsHostLocation | Gives the location of the server host. |
| nsOsVersion | Contains the operating system version of the server host. |
| serverHostName | Contains the host name of the server on which the Directory Server instance is running. |
9.76. nsICQpresence
nsICQpresence is an auxiliary object class which defines the status of an ICQ messaging account. This object is defined for Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.301
| Attribute | Definition |
|---|---|
| nsICQid | Contains the ICQ user ID for the entry. |
| nsICQStatusGraphic | Contains a pointer to the graphic image which indicates the ICQ account’s status. |
| nsICQStatusText | Contains the text to indicate the ICQ account’s status. |
9.77. nsLicenseUser
The nsLicenseUser object class tracks tracks licenses for servers that are licensed on a per-client basis. nsLicenseUser is intended to be used with the inetOrgPerson object class. You can manage the contents of this object class through the Users and Groups area of the Administration Server.
This object class is defined in the Administration Server schema.
Superior Class
top
OID
2.16.840.1.113730.3.2.7
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| nsLicensedFor | Identifies the server that the user is licensed to use. |
| nsLicenseEndTime | Reserved for future use. |
| nsLicenseStartTime | Reserved for future use. |
9.78. nsManagedRoleDefinition
The nsManagedRoleDefinition object class specifies the member assignments of a role to an explicit, enumerated list of members.
This object class is defined in Directory Server.
Superior Class
nsComplexRoleDefinition
OID
2.16.840.1.113730.3.2.96
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| description | Gives a text description of the entry. |
9.79. nsMessagingServerUser
nsICQpresence is an auxiliary object class that describes a messaging server user. This object class is defined for Netscape Messaging Server.
Superior Class
top
OID
2.16.840.113730.3.2.37
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes for the entry. |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| mailAccessDomain | Contains the domain from which the user can access the messaging server. |
| mailAlternateAddress | Contains secondary email addresses for the group. |
| mailAutoReplyMode | Specifies whether autoreply mode for the account is enabled. |
| mailAutoReplyText | Contains the text use for automatic reply emails. |
| mailDeliveryOption | Specifies the mail delivery mechanism to be used for the mail user. |
| mailForwardingAddress | Specifies the mail delivery mechanism to use for the mail user. |
| mailMessageStore | Specifies the location of the user’s mail box. |
| mailProgramDeliveryInfo | Specifies the commands used for programmed mail delivery. |
| mailQuota | Specifies the disk space allowed for the user’s mail box. |
| nsmsgDisallowAccess | Sets limits on the mail protocols available to the user. |
| nsmsgNumMsgQuota | Specifies the number of messages allowed for the user’s mail box. |
| nswmExtendedUserPrefs | Stores the extended preferences for the user. |
| vacationEndDate | Contains the end date for a vacation period. |
| vacationStartDate | Contains the start date for a vacation period. |
9.80. nsMSNpresence
nsMSNpresence is an auxiliary object class which defines the status of an MSN instance messaging account. This object is defined for Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.303
| Attribute | Definition |
|---|---|
| nsMSNid | Contains the MSN user ID for the entry. |
9.81. nsNestedRoleDefinition
The nsNestedRoleDefinition object class specifies one or more roles, of any type, are included as members within the role.
This object class is defined in Directory Server.
Superior Class
nsComplexRoleDefinition
OID
2.16.840.1.113730.3.2.98
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| nsRoleDn | Specifies the roles assigned to an entry. |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| description | Gives a text description of the entry. |
9.82. nsResourceRef
The nsNestedRoleDefinition object class configures a resource reference.
This object class is defined in the Administration Services.
Superior Class
top
OID
nsResourceRef-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| seeAlso | Contains a URL to another entry or site with related information. |
9.83. nsRoleDefinition
All role definition object classes inherit from the nsRoleDefinition object class.
This object class is defined by Directory Server.
Superior Class
LDAPsubentry
OID
2.16.840.1.113730.3.2.93
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| description | Gives a text description of the entry. |
9.84. nsSimpleRoleDefinition
Roles containing this object class are called simple roles because they have a deliberately limited flexibility, which makes it easy to:
- Enumerate the members of a role.
- Determine whether a given entry possesses a particular role.
- Enumerate all the roles possessed by a given entry.
- Assign a particular role to a given entry.
- Remove a particular role from a given entry.
This object class is defined by Directory Server.
Superior Class
nsRoleDefinition
OID
2.16.840.1.113730.3.2.94
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| description | Gives a text description of the entry. |
9.85. nsSNMP
This object class defines the configuration for the SNMP plug-in object used by Directory Server.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.41
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| nsSNMPEnabled | Sets whether SNMP is enabled for the Directory Server instance. |
| Attribute | Definition |
|---|---|
| nsSNMPContact | Contains the contact information provided by the SNMP agent. |
| nsSNMPDescription | Contains a text description of the SNMP setup. |
| nsSNMPLocation | Contains the location information or configuration for the SNMP agent. |
| nsSNMPMasterHost | Contains the host name for the server where the SNMP master agent is located. |
| nsSNMPMasterPort | Contains the port to access the SNMP subagent. |
| nsSNMPOrganization | Contains the organization name or information provided by the SNMP service. |
9.86. nsTask
This object class defines the configuration for tasks performed by Directory Server.
This object class is defined for the Administrative Services.
Superior Class
top
OID
nsTask-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| nsExecRef | Contains a reference to the program which will perform the task. |
| nsHelpRef | Contains a reference to an online (HTML) help file associated with the task window. |
| nsLogSuppress | Sets whether to suppress logging for the task. |
| nsTaskLabel | Contains a label associated with the task in the Console. |
9.87. nsTaskGroup
This object class defines the information for a group of tasks in the Console.
This object class is defined for the Administrative Services.
Superior Class
top
OID
nsTaskGroup-oid
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| nsTaskLabel | Contains a label associated with the task in the Console. |
9.88. nsTopologyCustomView
This object class configures the topology views used for the profile in the Console.
This object class is defined for the Administrative Services.
Superior Class
nsCustomView
OID
nsTopologyCustomView-oid
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| nsViewConfiguration | Contains the view configuration to use in the Console. |
9.89. nsTopologyPlugin
This object class configures the topology plug-in used to set views in the Console.
This object class is defined for the Administrative Services.
Superior Class
nsAdminObject
OID
nsTopologyPlugin-oid
9.90. nsValueItem
This object class defines a value item object configuration, which is used to specify information that is dependent on the value type of an entry. A value item relates to the allowed attribute value syntax for an entry attribute, such as binary or case-sensitive string.
This object class is defined in Netscape Servers - Value Item.
Superior Class
top
OID
2.16.840.1.113730.3.2.45
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| nsValueBin | Contains information or operations related to the binary value type. |
| nsValueCES | Contains information or operations related to the case-exact string (CES) value type. |
| nsValueCIS | Contains information or operations related to the case-insensitive (CIS) value type. |
| nsValueDefault | Sets the default value type to use for an attribute or configuration parameter. |
| nsValueDescription | Gives a text description of the value item setting. |
| nsValueDN | Contains information or operations related to the DN value type. |
| nsValueFlags | Sets flags for the value item object. |
| nsValueHelpURL | Contains a reference to an online (HTML) help file associated with the value item object. |
| nsValueInt | Contains information or operations related to the integer value type. |
| nsValueSyntax | Defines the syntax to use for the value item object. |
| nsValueTel | Contains information or operations related to the telephone string value type. |
| nsValueType | Sets which value type to apply. |
9.91. nsView
This object class is used for a view entry in the directory tree.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.304
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| nsViewFilter | Identifies the filter used by the view plug-in. |
9.92. nsYIMpresence
nsYIMpresence is an auxiliary object class which defines the status of a Yahoo instance messaging account. This object is defined for Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.302
| Attribute | Definition |
|---|---|
| nsYIMid | Contains the Yahoo user ID for the entry. |
| nsYIMStatusGraphic | Contains a pointer to the graphic image which indicates the Yahoo account’s status. |
| nsYIMStatusText | Contains the text to indicate the Yahoo account’s status. |
9.93. ntGroup
The ntGroup object class holds data for a group entry stored in a Windows Active Directory server. Several Directory Server attributes correspond directly to or are mapped to match Windows group attributes. When you create a new group in Directory Server that is to be synchronized with a Windows server group, Directory Server attributes are assigned to the Windows entry. These attributes may then be added, modified, or deleted in the entry through either directory service.
This object class is defined in Netscape NT Synchronization.
Superior Class
top
OID
2.16.840.1.113730.3.2.9
| Object Class | Definition |
|---|---|
| mailGroup |
Allows the |
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| ntUserDomainId | Contains the Windows domain login ID for the group account. |
| Attribute | Definition |
|---|---|
| commonName |
Gives the common name of the entry; this corresponds to the Windows |
| description |
Gives a text description of the entry; corresponds to the Windows |
| localityName | Gives the city or geographical location of the entry. |
| member | Specifies the members of the group. |
| ntGroupCreateNewGroup | Specifies whether a Windows account should be created when an entry is created in Directory Server. |
| ntGroupDeleteGroup | Specifies whether a Windows account should be deleted when an entry is deleted in Directory Server. |
| ntGroupDomainId | Gives the domain ID string for the group. |
| ntGroupType | Defines what kind of Windows domain group the entry is. |
| ntUniqueId | Contains a generated ID number used by the server for operations and identification. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| seeAlso | Contains a URL to another entry or site with related information. |
9.94. ntUser
The ntUser entry holds data for a user entry stored in a Windows Active Directory server. Several Directory Server attributes correspond directly to or are mapped to match Windows user account fields. When you create a new person entry in Directory Server that is to be synchronized with a Windows server, Directory Server attributes are assigned to Windows user account fields. These attributes may then be added, modified, or deleted in the entry through either directory service.
This object class is defined in Netscape NT Synchronization.
Superior Class
top
OID
2.16.840.1.113730.3.2.8
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName |
Gives the common name of the entry; this corresponds to the Windows |
| ntUserDomainId | Contains the Windows domain login ID for the user account. |
| Attribute | Definition |
|---|---|
| description |
Gives a text description of the entry; corresponds to the Windows |
| destinationIndicator | Gives the country and city associated with the entry; this was once required to provide public telegram service. |
| facsimileTelephoneNumber | Gives the fax number for the user. |
| givenName | Contains the person’s first name. |
| homeTelephoneNumber | Gives the person’s home phone number. |
| homePostalAddress | Gives the person’s home mailing address. |
| initials | Gives the person’s initials. |
| localityName | Gives the city or geographical location of the entry. |
| | Contains the person’s email address. |
| manager | Contains the DN (distinguished name) of the direct supervisor of the person entry. |
| mobile | Gives the person’s mobile phone number. |
| ntUserAcctExpires | Identifies when the user’s Windows account will expire. |
| ntUserCodePage | Gives the user’s code page. |
| ntUserCreateNewAccount | Specifies whether a Windows account should be created when this entry is created in Directory Server. |
| ntUserDeleteAccount | Specifies whether a Windows account should be deleted when this entry is deleted in Directory Server. |
| ntUserHomeDir | Gives the path to the user’s home directory. |
| ntUserLastLogoff | Gives the time of the user’s last logoff from the Windows server. |
| ntUserLastLogon | Gives the time of the user’s last logon to the Windows server. |
| ntUserMaxStorage | Shows the maximum disk space available to the user in the Windows server. |
| ntUserParms | Contains a Unicode string reserved for use by applications. |
| ntUserProfile | Contains the path to the user’s Windows profile. |
| ntUserScriptPath | Contains the path to the user’s Windows login script. |
| ntUserWorkstations | Contains a list of Windows workstations from which the user is allowed to log into the Windows domain. |
| organizationName | Gives the organization to which the entry belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| pagerTelephoneNumber | Gives the person’s pager number. |
| postalAddress | Contains the mailing address for the entry. |
| postalCode | Gives the postal code for the entry, such as the zip code in the United States. |
| postOfficeBox | Gives the post office box number for the entry. |
| General_Atttribute_registeredAddress | Gives a postal address suitable to receive expedited documents when the recipient must verify delivery. |
| seeAlso | Contains a URL to another entry or site with related information. |
| surname | Gives the person’s family name or last name. |
| stateOrProvinceName | Gives the state or province where the person is located. |
| streetaddress | Gives the street name and address number for the person’s physical location. |
| telephoneNumber | Gives the telephone number for the entry. |
| teletexTerminalIdentifier | Gives the identifier for the person’s teletex terminal. |
| telexNumber | Gives the telex number associated with the entry. |
| title | Shows the person’s job title. |
| userCertificate | Stores a user’s certificate in cleartext (not used). |
| x121Address | Gives the X.121 address for the entry. |
9.95. oncRpc
The oncRpc object class defines an abstraction of an Open Network Computing Remote Procedure Call (ONC RPC). This object class is defined in RFC 2307.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.5
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| commonName | Gives the common name of the entry. |
| oncRpcNumber | Contains part of the RPC map and stores the RPC number for UNIX RPCs. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
9.96. organization
The organization attributes defines entries that represent organizations. An organization is generally assumed to be a large, relatively static grouping within a larger corporation or enterprise.
This object class is defined in RFC 2256.
Superior Class
top
OID
2.5.6.4
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| organizationName | Gives the organization to which the entry belongs. |
| Attribute | Definition |
|---|---|
| businessCategory | Gives the type of business in which the entry is engaged. |
| description | Gives a text description of the entry. |
| destinationIndicator | Gives the country and city associated with the entry; this was once required to provide public telegram service. |
| facsimileTelephoneNumber | Contains the fax number for the entry. |
| internationalISDNNumber | Contains the ISDN number for the entry. |
| localityName | Gives the city or geographical location of the entry. |
| physicalDeliveryOfficeName | Gives a location where physical deliveries can be made. |
| postalAddress | Contains the mailing address for the entry. |
| postalCode | Gives the postal code for the entry, such as the zip code in the United States. |
| postOfficeBox | Gives the post office box number for the entry. |
| preferredDeliveryMethod | Shows the preferred method of contact or message delivery for the entry. |
| General_Atttribute_registeredAddress | Gives a postal address suitable to receive expedited documents when the recipient must verify delivery. |
| searchGuide | Specifies information for suggested search criteria when using the entry as the base object in the directory tree for a search. |
| seeAlso | Contains a URL to another entry or site with related information. |
| stateOrProvinceName | Gives the state or province where the person is located. |
| streetaddress | Gives the street name and number for the person’s physical location. |
| telephoneNumber | Gives the telephone number of the person responsible for the organization. |
| teletexTerminalIdentifier | Gives the ID for an entry’s teletex terminal. |
| telexNumber | Gives the telex number associated with the entry. |
| userPassword | Gives the password with which the entry can bind to the directory. |
| x121Address | Gives the X.121 address for the entry. |
9.97. organizationalPerson
The organizationalPerson object class defines entries for people employed or affiliated with the organization. This object class inherits the commonName and surname attributes from the person object class.
This object class is defined in RFC 2256.
Superior Class
person
OID
2.5.6.7
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| surname | Gives the person’s family name or last name. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| destinationIndicator | Gives the country and city associated with the entry; this was once required to provide public telegram service. |
| facsimileTelephoneNumber | Contains the fax number for the entry. |
| internationalISDNNumber | Contains the ISDN number for the entry. |
| localityName | Gives the city or geographical location of the entry. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| physicalDeliveryOfficeName | Gives a location where physical deliveries can be made. |
| postalAddress | Contains the mailing address for the entry. |
| postalCode | Gives the postal code for the entry, such as the zip code in the United States. |
| postOfficeBox | Gives the post office box number for the entry. |
| preferredDeliveryMethod | Shows the person’s preferred method of contact or message delivery. |
| General_Atttribute_registeredAddress | Gives a postal address suitable to receive expedited documents when the recipient must verify delivery. |
| seeAlso | Contains a URL to another entry or site with related information. |
| stateOrProvinceName | Gives the state or province where the person is located. |
| streetaddress | Gives the street name and number for the person’s physical location. |
| telephoneNumber | Gives the telephone number for the entry. |
| teletexTerminalIdentifier | Gives the ID for an entry’s teletex terminal. |
| telexNumber | Gives the telex number associated with the entry. |
| title | Shows the person’s job title. |
| userPassword | Stores the password with which the entry can bind to the directory. |
| x121Address | Gives the X.121 address for the entry. |
9.98. organizationalRole
The organizationalRole object class is used to define entries for roles held by people within an organization.
This object class is defined in RFC 2256.
Superior Class
top
OID
2.5.6.8
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| destinationIndicator | Gives the country and city associated with the entry; this was once required to provide public telegram service. |
| facsimileTelephoneNumber | Contains the fax number for the entry. |
| internationalISDNNumber | Contains the ISDN number for the entry. |
| localityName | Gives the city or geographical location of the entry. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| physicalDeliveryOfficeName | Gives a location where physical deliveries can be made. |
| postalAddress | Contains the mailing address for the entry. |
| postalCode | Gives the postal code for the entry, such as the zip code in the United States. |
| postOfficeBox | Gives the post office box number for the entry. |
| preferredDeliveryMethod | Shows the role’s preferred method of contact or message delivery. |
| General_Atttribute_registeredAddress | Gives a postal address suitable to receive expedited documents when the recipient must verify delivery. |
| roleOccupant | Contains the DN (distinguished name) of the person in the role. |
| seeAlso | Contains a URL to another entry or site with related information. |
| stateOrProvinceName | Gives the state or province where the entry is located. |
| streetaddress | Gives the street name and number for the role’s physical location. |
| telephoneNumber | Gives the telephone number for the entry. |
| teletexTerminalIdentifier | Gives the ID for an entry’s teletex terminal. |
| telexNumber | Gives the telex number associated with the entry. |
| x121Address | Gives the X.121 address for the entry. |
9.99. organizationalUnit
The organizationalUnit object class defines entries that represent organizational units, generally understood to be a relatively static grouping within a larger organization.
This object class is defined in RFC 2256.
Superior Class
top
OID
2.5.6.5
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| Attribute | Definition |
|---|---|
| businessCategory | Gives the type of business in which the entry is engaged. |
| description | Gives a text description of the entry. |
| destinationIndicator | Gives the country and city associated with the entry; this was once required to provide public telegram service. |
| facsimileTelephoneNumber | Contains the fax number for the entry. |
| internationalISDNNumber | Contains the ISDN number for the entry. |
| localityName | Gives the city or geographical location of the entry. |
| physicalDeliveryOfficeName | Gives a location where physical deliveries can be made. |
| postalAddress | Contains the mailing address for the entry. |
| postalCode | Gives the postal code for the entry, such as the zip code in the United States. |
| postOfficeBox | Gives the post office box number for the entry. |
| preferredDeliveryMethod | Gives the preferred method of being contacted. |
| General_Atttribute_registeredAddress | Gives a postal address suitable to receive expedited documents when the recipient must verify delivery. |
| searchGuide | Specifies information for suggested search criteria when using the entry as the base object in the directory tree for a search. |
| seeAlso | Contains a URL to another entry or site with related information. |
| stateOrProvinceName | Gives the state or province where the person is located. |
| streetaddress | Gives the street name and number for the role’s physical location. |
| telephoneNumber | Gives the telephone number for the entry. |
| teletexTerminalIdentifier | Gives the ID for an entry’s teletex terminal. |
| telexNumber | Gives the telex number associated with the entry. |
| userPassword | Stores the password with which the entry can bind to the directory. |
| x121Address | Gives the X.121 address for the entry. |
9.100. person
The person object class represents entries for generic people. This is the base object class for the organizationalPerson object class.
This object class is defined in RFC 2256.
Superior Class
top
OID
2.5.6.6
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| surname | Gives the person’s family name or last name. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| seeAlso | Contains a URL to another entry or site with related information. |
| telephoneNumber | Gives the telephone number for the entry. |
| userPassword | Stores the password with which the entry can bind to the directory. |
9.101. pilotObject
The pilotObject is a subclass to allow additional attributes to be assigned to entries of all other object classes.
This object class is defined in RFC 1274.
Superior Class
top
OID
0.9.2342.19200300.100.4.3
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| audio | Stores a sound file in a binary format. |
| dITRedirect | Contains the DN (distinguished name) of the entry to use as a redirect for the entry. |
| info | Contains information about the entry. |
| jpegPhoto | Stores a JPG image. |
| lastModifiedBy | Gives the DN (distinguished name) of the last user which modified the document entry. |
| lastModifiedTime | Gives the time the object was most recently modified. |
| manager | Gives the DN (distinguished name) of the entry’s manager. |
| photo | Stores a photo of the document in binary format. |
| uniqueIdentifier | Distinguishes between two entries when a distinguished name has been reused. |
9.102. pilotOrganization
The pilotOrganization object class is a subclass used to add attributes to organization and organizationalUnit object class entries.
This object class is defined in RFC 1274.
Superior Class
top
OID
0.9.2342.19200300.100.4.20
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| organizationName | Gives the organization to which the entry belongs. |
| organizationalUnitName | Gives the organizational unit or division to which the entry belongs. |
| Attribute | Definition |
|---|---|
| buildingName | Gives the name of the building where the entry is located. |
| businessCategory | Gives the type of business in which the entry is engaged. |
| description | Gives a text description of the entry. |
| destinationIndicator | Gives the country and city associated with the entry; this was once required to provide public telegram service. |
| facsimileTelephoneNumber | Contains the fax number for the entry. |
| internationalISDNNumber | Contains the ISDN number for the entry. |
| localityName | Gives the city or geographical location of the entry. |
| physicalDeliveryOfficeName | Gives a location where physical deliveries can be made. |
| postalAddress | Contains the mailing address for the entry. |
| postalCode | Gives the postal code for the entry, such as the zip code in the United States. |
| postOfficeBox | Gives the post office box number for the entry. |
| preferredDeliveryMethod | Gives the preferred method of being contacted. |
| General_Atttribute_registeredAddress | Gives a postal address suitable to receive expedited documents when the recipient must verify delivery. |
| searchGuide | Specifies information for suggested search criteria when using the entry as the base object in the directory tree for a search. |
| seeAlso | Contains a URL to another entry or site with related information. |
| stateOrProvinceName | Gives the state or province where the person is located. |
| streetaddress | Gives the street name and address number for the person’s physical location. |
| telephoneNumber | Gives the telephone number for the entry. |
| teletexTerminalIdentifier | Gives the ID for an entry’s teletex terminal. |
| telexNumber | Gives the telex number associated with the entry. |
| userPassword | Stores the password with which the entry can bind to the directory. |
| x121Address | Gives the X.121 address for the entry. |
9.103. pkiCA
The pkiCA auxiliary object class contains required or available certificates that are configured for a certificate authority. This object class is defined in RFC 4523, which defines object classes and attributes for LDAP to use to manage X.509 certificates and related certificate services.
Superior Class
top
OID
2.5.6.22
| Attribute | Definition |
|---|---|
| authorityRevocationList | Contains a list of revoked CA certificates. |
| cACertificate | Contains a CA certificate. |
| certificateRevocationList | Contains a list of certificates that have been revoked. |
| crossCertificatePair | Contains a pair of certificates that are used to cross-certify a pair of CAs in a FBCA-style bridge CA configuration. |
9.104. pkiUser
The pkiUser auxiliary object class contains required certificates for a user or client that connects to a certificate authority or element in the public key infrastructure. This object class is defined in RFC 4523, which defines object classes and attributes for LDAP to use to manage X.509 certificates and related certificate services.
Superior Class
top
OID
2.5.6.21
| Attribute | Definition |
|---|---|
| userCertificate | Stores a user’s certificate, usually in binary form. |
9.105. posixAccount
The posixAccount object class defines network accounts which use POSIX attributes. This object class is defined in RFC 2307, which defines object classes and attributes to use LDAP as a network information service.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.0
| Attribute | Definition |
|---|---|
| commonName | Gives the common name of the entry. |
| gidNumber | Contains a unique numeric identifier for a group entry or to identify the group for a user entry, analogous to the group number in Unix. |
| homeDirectory | Contains the path to the user’s home directory. |
| objectClass | Gives the object classes assigned to the entry. |
| userID | Gives the defined account’s user ID. |
| uidNumber | Contains a unique numeric identifier for a user entry, analogous to the user number in Unix. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| gecos | Used to determine the GECOS field for the user; this is based on a common name, with additional information embedded. |
| loginShell | Contains the path to a script that is launched automatically when a user logs into the domain. |
| userPassword | Stores the password with which the entry can bind to the directory. |
9.106. posixGroup
The posixGroup object class defines a group of network accounts which use POSIX attributes. This object class is defined in RFC 2307, which defines object classes and attributes to use LDAP as a network information service.
Superior Class
top
OID
1.3.6.1.1.1.2.2
| Attribute | Definition |
|---|---|
| gidNumber | Contains the path to a script that is launched automatically when a user logs into the domain. |
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| memberUID | Gives the login name of the group member; this possibly may not be the same as the member’s DN. |
| userPassword | Contains the login name of the member of a group. |
9.107. referral
The referral object class defines an object which supports LDAPv3 smart referrals. This object class is defined in LDAPv3 referrals Internet Draft.
Superior Class
top
OID
2.16.840.1.113730.3.2.6
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| ref | Contains information for an LDAPv3 smart referral. |
9.108. residentialPerson
The residentialPerson object class manages a person’s residential information.
This object class is defined in RFC 2256.
Superior Class
top
OID
2.5.6.10
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| localityName | Gives the city or geographical location of the entry. |
| surname | Gives the person’s family name or last name. |
| Attribute | Definition |
|---|---|
| businessCategory | Gives the type of business in which the entry is engaged. |
| description | Gives a text description of the entry. |
| destinationIndicator | Gives the country and city associated with the entry; this was once required to provide public telegram service. |
| facsimileTelephoneNumber | Contains the fax number for the entry. |
| internationalISDNNumber | Contains the ISDN number for the entry. |
| physicalDeliveryOfficeName | Gives a location where physical deliveries can be made. |
| postalAddress | Contains the mailing address for the entry. |
| postalCode | Gives the postal code for the entry, such as the zip code in the United States. |
| postOfficeBox | Gives the post office box number for the entry. |
| preferredDeliveryMethod | Shows the person’s preferred method of contact or message delivery. |
| General_Atttribute_registeredAddress | Gives a postal address suitable to receive expedited documents when the recipient must verify delivery. |
| seeAlso | Contains a URL to another entry or site with related information. |
| stateOrProvinceName | Gives the state or province where the person is located. |
| streetaddress | Gives the street name and address number for the person’s physical location. |
| telephoneNumber | Gives the telephone number for the entry. |
| teletexTerminalIdentifier | Gives the ID for an entry’s teletex terminal. |
| telexNumber | Gives the telex number associated with the entry. |
| userPassword | Stores the password with which the entry can bind to the directory. |
| x121Address | Gives the X.121 address for the entry. |
9.109. RFC822LocalPart
The RFC822LocalPart object class defines entries that represent the local part of RFC 822 mail addresses. The directory treats this part of an RFC822 address as a domain.
This object class is defined by the Internet Directory Pilot.
Superior Class
domain
OID
0.9.2342.19200300.100.4.14
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| dc | Contains one component of a domain name. |
| Attribute | Definition |
|---|---|
| associatedName | Gives the name of an entry within the organizational directory tree which is associated with a DNS domain. |
| businessCategory | Gives the type of business in which the entry is engaged. |
| commonName | Gives the common name of the entry. |
| description | Gives a text description of the entry. |
| destinationIndicator | Gives the country and city associated with the entry; this was once required to provide public telegram service. |
| facsimileTelephoneNumber | Contains the fax number for the entry. |
| internationalISDNNumber | Contains the ISDN number for the entry. |
| localityName | Gives the city or geographical location of the entry. |
| organizationName | Gives the organization to which the account belongs. |
| physicalDeliveryOfficeName | Gives a location where physical deliveries can be made. |
| postalAddress | Contains the mailing address for the entry. |
| postalCode | Gives the postal code for the entry, such as the zip code in the United States. |
| postOfficeBox | Gives the post office box number for the entry. |
| preferredDeliveryMethod | Shows the person’s preferred method of contact or message delivery. |
| General_Atttribute_registeredAddress | Gives a postal address suitable to receive expedited documents when the recipient must verify delivery. |
| searchGuide | Specifies information for suggested search criteria when using the entry as the base object in the directory tree for a search. |
| seeAlso | Contains a URL to another entry or site with related information. |
| surname | Gives the person’s family name or last name. |
| stateOrProvinceName | Gives the state or province where the person is located. |
| streetaddress | Gives the street name and address number for the person’s physical location. |
| telephoneNumber | Gives the telephone number for the entry. |
| teletexTerminalIdentifier | Gives the identifier for the person’s teletex terminal. |
| telexNumber | Gives the telex number associated with the entry. |
| userPassword | Stores the password with which the entry can bind to the directory. |
| x121Address | Gives the X.121 address for the entry. |
9.110. room
The room object class stores information in the directory about rooms.
Superior Class
top
OID
0.9.2342.19200300.100.4.7
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| commonName | Gives the common name of the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the room. |
| roomNumber | Contains the room’s number. |
| seeAlso | Contains a URL to another entry or site with related information. |
| telephoneNumber | Gives the telephone number for the entry. |
9.111. shadowAccount
The shadowAccount object class allows the LDAP directory to be used as a shadow password service. Shadow password services relocate the password files on a host to a shadow file with tightly restricted access.
This object class is defined in RFC 2307, which defines object classes and attributes to use LDAP as a network information service.
This object class is defined in 10rfc2307.ldif in the Directory Server. To use the updated RFC 2307 schema, remove the 10rfc2307.ldif file and copy the 10rfc2307bis.ldif file from the /usr/share/dirsrv/data directory to the /etc/dirsrv/slapd-instance/schema directory.
Superior Class
top
OID
1.3.6.1.1.1.2.1
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| userID | Gives the defined account’s user ID. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| shadowExpire | Contains the date that the shadow account expires. |
| shadowFlag | Identifies what area in the shadow map stores the flag values. |
| shadowInactive | Sets how long the shadow account can be inactive. |
| shadowLastChange | Contains the time and date of the last modification to the shadow account. |
| shadowMax | Sets the maximum number of days that a shadow password is valid. |
| shadowMin | Sets the minimum number of days that must pass between changing the shadow password. |
| shadowWarning | Sets how may days in advance of password expiration to send a warning to the user. |
| userPassword | Stores the password with which the entry can bind to the directory. |
9.112. simpleSecurityObject
The simpleSecurityObject object class allow an entry to contain the userPassword attribute when an entry’s principal object classes do not allow a password attribute. Reserved for future use.
This object class is defined in RFC 1274.
Superior Class
top
OID
0.9.2342.19200300.100.4.19
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| userPassword | Stores the password with which the entry can bind to the directory. |
9.113. strongAuthenticationUser
The strongAuthenticationUser object class stores a user’s certificate in the directory.
This object class is defined in RFC 2256.
Superior Class
top
OID
2.5.6.15
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| userCertificate | Stores a user’s certificate, usually in binary form. |
Chapter 10. Operational attributes and object classes
Operational attributes are attributes used to perform directory operations and are available for every entry in the directory, regardless of whether they are defined for the object class of the entry. Operational attributes are only returned in an ldapsearch operation if specifically requested. To return all operational attributes of an object, specify +.
Operational attributes are created and managed by Directory Server on entries, such as the time the entry is created or modified and the creator’s name. These attributes can be set on any entry, regardless of other attributes or object classes on the entry.
10.1. accountUnlockTime
The accountUnlockTime attribute contains the date and time in GMT-format at which the account will become unlocked. A value of 0 means that the account must be unlocked by an administrator.
| OID | 2.16.840.1.113730.3.1.95 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
10.2. aci
This attribute is used by Directory Server to evaluate what rights are granted or denied when it receives an LDAP request from a client.
| OID | 2.16.840.1.113730.3.1.55 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
10.3. altServer
The values of this attribute are URLs of other servers which may be contacted when this server becomes unavailable. If the server does not know of any other servers which could be used, this attribute is absent. This information can be cached in case the preferred LDAP server later becomes unavailable.
| OID | 1.3.6.1.4.1.1466.101.120.6 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
10.4. createTimestamp
This attribute contains the date and time that the entry was initially created.
| OID | 2.5.18.1 |
| Syntax | GeneralizedTime |
| Multi- or Single-Valued | Single-valued |
| Defined in |
10.5. creatorsName
This attribute contains the name of the user which created the entry.
| OID | 2.5.18.3 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in |
10.6. dITContentRules
This attribute defines the DIT content rules which are in force within a subschema. Each value defines one DIT content rule. Each value is tagged by the object identifier of the structural object class to which it pertains.
| OID | 2.5.21.2 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
10.7. dITStructureRules
This attribute defines the DIT structure rules which are in force within a subschema. Each value defines one DIT structure rule.
| OID | 2.5.21.1 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
10.8. entryusn
When the USN Plug-in is enabled, the server automatically assigns an update sequence number to entries every time a write operation (add, modify, modrdn, or delete) is performed. The USN is stored in the entryUSN operational attribute on the entry; the entryUSN, then, shows the number for the most recent change on any entry.
The entryUSN attribute increments only with operations performed by LDAP clients. It does not count internal operations.
By default, the entryUSN is unique per back end database instance, so entries in other databases may have the same USN. The nsslapd-entryusn-global parameter changes the assignment of USNs from local to global, that is, from being counted on a single database to being counted for all databases in the topology. The parameter is turned off by default.
A corresponding entry, lastusn, is kept in the root DSE entry, which shows the most recently- assigned USN. In local mode, lastusn shows the most recently- assigned USN per back end database. In global mode, lastusn shows the most recently assigned USN for the entire topology.
| OID | 2.16.840.1.113730.3.1.606 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.9. glue
The glue object class defines an entry in a special state: resurrected due to a replication conflict.
This object class is defined by Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.30
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
10.10. hasSubordinates
This attribute indicates whether the entry has subordinate entries.
| OID | 1.3.6.1.4.1.1466.115.121.1.7 |
| Syntax | Boolean |
| Multi- or Single-Valued | Single-valued |
| Defined in | numSubordinates Internet Draft |
10.11. internalCreatorsName
For entries which were created by a plug-in or by the server, rather than a Directory Server user, this attribute records what internal user (by plug-in DN) created the entry.
The internalCreatorsname attributes always show a plug-in as the identity. This plug-in could be an additional plug-in, such as the MemberOf Plug-in. If the change is made by the core Directory Server, then the plug-in is the database plug-in, cn=ldbm database,cn=plugins,cn=config.
| OID | 2.16.840.1.113730.3.1.2114 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.12. internalModifiersName
If an entry is edited by a plug-in or by the server, rather than a Directory Server user, this attribute records what internal user (by plug-in DN) modified the entry.
The internalModifiersname attributes always show a plug-in as the identity. This plug-in could be an additional plug-in, such as the MemberOf Plug-in. If the change is made by the core Directory Server, then the plug-in is the database plug-in, cn=ldbm database,cn=plugins,cn=config.
| OID | 2.16.840.1.113730.3.1.2113 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.13. lastLoginTime
The lastLoginTime attribute contains a timestamp of the last time that the given account authenticated to the directory, in the format YYYMMDDHHMMSSZ. For example:
lastLoginTime: 20200527001051Z
lastLoginTime: 20200527001051ZThis is used to evaluate account lockout policies based on account inactivity.
| OID | 2.16.840.1.113719.1.1.4.1.35 |
| Syntax | GeneralizedTime |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.14. lastModifiedBy
The lastModifiedBy attribute contains the distinguished name (DN) of the user who last edited the entry. For example:
lastModifiedBy: cn=Barbara Jensen,ou=Engineering,dc=example,dc=com
lastModifiedBy: cn=Barbara Jensen,ou=Engineering,dc=example,dc=com| OID | 0.9.2342.19200300.100.1.24 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
10.15. lastModifiedTime
The lastModifiedTime attribute contains the time, in UTC format, an entry was last modified. For example:
lastModifiedTime: Thursday, 22-Sep-93 14:15:00 GMT
lastModifiedTime: Thursday, 22-Sep-93 14:15:00 GMT| OID | 0.9.2342.19200300.100.1.23 |
| Syntax | DirectyString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
10.16. ldapSubEntry
These entries hold operational data. This object class is defined in the LDAP Subentry Internet Draft.
Superior Class
top
OID
2.16.840.1.113719.2.142.6.1.1
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| commonName | Specifies the common name of the entry. |
10.17. ldapSyntaxes
This attribute identifies the syntaxes implemented, with each value corresponding to one syntax.
| OID | 1.3.6.1.4.1.1466.101.120.16 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
10.18. matchingRules
This attribute defines the matching rules used within a subschema. Each value defines one matching rule.
| OID | 2.5.21.4 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
10.19. matchingRuleUse
This attribute indicates the attribute types to which a matching rule applies in a subschema.
| OID | 2.5.21.8 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
10.20. modifiersName
This attribute contains the name of the user which last modified the entry.
| OID | 2.5.18.4 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in |
10.21. modifyTimestamp
This attribute contains the date and time that the entry was most recently modified.
| OID | 2.5.18.2 |
| Syntax | GeneralizedTime |
| Multi- or Single-Valued | Single-valued |
| Defined in |
10.22. nameForms
This attribute defines the name forms used in a subschema. Each value defines one name form.
| OID | 2.5.21.7 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
10.23. nsAccountLock
This attribute shows whether the account is active or inactive.
| OID | 2.16.840.1.113730.3.1.610 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
10.24. nsAIMStatusGraphic
This attribute contains a path pointing to the graphic which illustrates the AIM user status.
| OID | 2.16.840.1.113730.3.1.2018 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.25. nsAIMStatusText
This attribute contains the text which indicates the current AIM user status.
| OID | 2.16.840.1.113730.3.1.2017 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.26. nsBackendSuffix
This contains the suffix used by the back end.
| OID | 2.16.840.1.113730.3.1.803 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
10.27. nscpEntryDN
This attribute contains the (former) entry DN for a tombstone entry.
| OID | 2.16.840.1.113730.3.1.545 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.28. nsDS5ReplConflict
This attribute is included on entries that have a change conflict that cannot be resolved automatically by the synchronization or replication process. The value of the nsDS5ReplConflict contains information about which entries are in conflict, usually by referring to them by their nsUniqueID for both current entries and tombstone entries.
| OID | 2.16.840.1.113730.3.1.973 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
10.29. nsICQStatusGraphic
This attribute contains a path pointing to the graphic which illustrates the ICQ user status.
| OID | 2.16.840.1.113730.3.1.2022 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.30. nsICQStatusText
This attribute contains the text for the current ICQ user status.
| OID | 2.16.840.1.113730.3.1.2021 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.31. nsIdleTimeout
This attribute identifies the user-based connection idle timeout period, in seconds.
| OID | 2.16.840.1.113730.3.1.573 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.32. nsIDListScanLimit
This attribute specifies the number of entry IDs that are searched during a search operation. Keep the default value to improve search performance.
| OID | 2.16.840.1.113730.3.1.2106 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.33. nsLookThroughLimit
This attribute sets the maximum number of entries for that user through which the server is allowed to look during a search operation. This attribute is configured in the server itself and applied to a user when he initiates a search.
| OID | 2.16.840.1.113730.3.1.570 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.34. nsPagedIDListScanLimit
This attribute specifies the number of entry IDs that are searched, specifically, for a search operation using the simple paged results control. This attribute works the same as the nsIDListScanLimit attribute, except that it only applies to searches with the simple paged results control.
If this attribute is not present or is set to zero, then the nsIDListScanLimit is used to paged searches as well as non-paged searches.
| OID | 2.16.840.1.113730.3.1.2109 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.35. nsPagedLookThroughLimit
This attribute specifies the maximum number of entries that Directory Server will check when examining candidate entries for a search which uses the simple paged results control. This attribute works the same as the nsLookThroughLimit attribute, except that it only applies to searches with the simple paged results control.
If this attribute is not present or is set to zero, then the nsLookThroughLimit is used to paged searches as well as non-paged searches.
| OID | 2.16.840.1.113730.3.1.2108 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.36. nsPagedSizeLimit
This attribute sets the maximum number of entries to return from a search operation specifically which uses the simple paged results control. This overrides the nsSizeLimit attribute for paged searches.
If this value is set to zero, then the nsSizeLimit attribute is used for paged searches as well as non-paged searches for the user, or the global configuration settings are used.
| OID | 2.16.840.1.113730.3.1.2107 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.37. nsParentUniqueId
For tombstone (deleted) entries stored in replication, the nsParentUniqueId attribute contains the DN or entry ID for the parent of the original entry.
| OID | 2.16.840.1.113730.3.1.544 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.38. nsRole
This attribute is a computed attribute that is not stored with the entry itself. It identifies to which roles an entry belongs.
| OID | 2.16.840.1.113730.3.1.574 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
10.39. nsRoleDn
This attribute contains the distinguished name of all roles that apply to an entry. Membership of a managed role is granted upon an entry by adding the role’s DN to the entry’s nsRoleDN attribute. For example:
A nested role specifies containment of one or more roles of any type. In that case, nsRoleDN defines the DN of the contained roles. For example:
| OID | 2.16.840.1.113730.3.1.575 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
10.40. nsRoleFilter
This attribute sets the filter identifies entries which belong to the role.
| OID | 2.16.840.1.113730.3.1.576 |
| Syntax | IA5String |
| Multi- or Single-Valued | Single-valued |
| Defined in |
10.41. nsSchemaCSN
This attribute is one of the subschema DSE attribute types.
| OID | 2.5.21.82.16.840.1.113730.3.1.804 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.42. nsSizeLimit
This attribute shows the default size limit for a database or database link in bytes.
| OID | 2.16.840.1.113730.3.1.571 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.43. nsTimeLimit
This attribute shows the default search time limit for a database or database link.
| OID | 2.16.840.1.113730.3.1.572 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.44. nsTombstone (object class)
Tombstone entries are entries which have been deleted from Directory Server. For replication and restore operations, these deleted entries are saved so that they can be resurrected and replaced if necessary. Each tombstone entry has the nsTombstone object class, automatically.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.113
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| nsParentUniqueId | Identifies the unique ID of the parent entry of the original entry. |
| nscpEntryDN | Identifies the orignal entry DN in a tombstone entry. |
10.45. nsUniqueId
This attribute identifies or assigns a unique ID to a server entry.
| OID | 2.16.840.1.113730.3.1.542 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.46. nsYIMStatusGraphic
This attribute contains a path pointing to the graphic which illustrates the Yahoo IM user status.
| OID | 2.16.840.1.113730.3.1.2020 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.47. nsYIMStatusText
This attribute contains the text for the current Yahoo IM user status.
| OID | 2.16.840.1.113730.3.1.2019 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.48. numSubordinates
This attribute indicates now many immediate subordinates an entry has. For example, numSubordinates=0 in a leaf entry.
| OID | 1.3.1.1.4.1.453.16.2.103 |
| Syntax | Integer |
| Multi- or Single-Valued | Single-valued |
| Defined in | numSubordinates Internet Draft |
10.49. passwordGraceUserTime
The passwordGraceUserTime attribute counts the number of login attempts the user made with the expired password.
| OID | 2.16.840.1.113730.3.1.998 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.50. passwordObject (object class)
This object class is used for entries which store password information for a user in the directory.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.12
| objectClass | Defines the object classes for the entry. |
| Refers to the amount of time that must pass after an account lockout before the user can bind to the directory again. | |
| Specifies the length of time that must pass before users are allowed to change their passwords. | |
| Specifies the length of time that passes before the user’s password expires. | |
| Indicates that a password expiration warning has been sent to the user. | |
| Counts the number of login attempts the user made with the expired password. | |
| Contains the history of the user’s previous passwords. | |
| Counts the number of consecutive failed attempts at entering the correct password. | |
| Points to the entry DN of the new password policy. | |
|
Specifies the length of time that passes before the |
10.51. passwordRetryCount
This attribute counts the number of consecutive failed attempts at entering the correct password.
| OID | 2.16.840.1.113730.3.1.93 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.52. pwdpolicysubentry
This attribute value points to the entry DN of the new password policy.
| OID | 2.16.840.1.113730.3.1.997 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.53. pwdUpdateTime
This attribute value stores the time of the most recent password change for the account.
| OID | 2.16.840.1.113730.3.1.2133 |
| Syntax | GeneralizedTime |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
10.54. subschema (object class)
This identifies an auxiliary object class subentry which administers the subschema for the subschema administrative area. It holds the operational attributes representing the policy parameters which express the subschema.
This object class is defined in RFC 2252.
Superior Class
top
OID
2.5.20.1
| objectClass | Defines the object classes for the entry. |
| attributeTypes | Attribute types used within a subschema. |
| dITContentRules | Defines the DIT content rules which are in force within a subschema. |
| dITStructureRules | Defines the DIT structure rules which are in force within a subschema. |
| matchingRuleUse | Indicates the attribute types to which a matching rule applies in a subschema. |
| matchingRules | Defines the matching rules used within a subschema. |
| nameForms | Defines the name forms used in a subschema. |
| objectClasses | Defines the object classes used in a subschema. |
10.55. subschemaSubentry
This attribute contains the DN of an entry that contains schema information. For example:
subschemaSubentry: cn=schema
subschemaSubentry: cn=schema| OID | 2.5.18.10 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in |
Chapter 11. Log files reference
Directory Server records events to log files that are essential for solving existing problems and predicting potential problems, which might result in failure or poor performance.
With log files you can achieve the following goals:
- Troubleshoot problems.
- Monitor the server activity.
- Analyze the directory activity.
To monitor the directory effectively, you must understand the structure and content of the log files.
You do not find an exhaustive list of log messages in the chapter. Presented information serves as a good starting point to solve common problems and understand the records in the access, error, audit, audit fail, and secure logs.
Directory Server instances store logs in the /var/log/dirsrv/slapd-instance_name directory.
11.1. Access log reference
The Directory Server access log contains detailed information about client connections to the directory. A connection is a sequence of requests from the same client with the following structure:
- A connection record which provides the connection index and the IP address of the client
- A bind record
- A bind result record
- A sequence of operation request and operation result pairs of records, or individual records in the case of connection, closed, and abandon records
- An unbind record
- A closed record
Access log record example:
[time_stamp] conn=1 op=73 SRCH base="dc=example,dc=com" scope=2 filter="(&(objectClass=top)(objectClass=ldapsubentry)(objectClass=passwordpolicy))" attrs="distinguishedName" [time_stamp] conn=1 op=73 RESULT err=0 tag=101 nentries=24 wtime=0.000078414 optime=0.001614101 etime=0.001690742
[time_stamp] conn=1 op=73 SRCH base="dc=example,dc=com" scope=2 filter="(&(objectClass=top)(objectClass=ldapsubentry)(objectClass=passwordpolicy))" attrs="distinguishedName"
[time_stamp] conn=1 op=73 RESULT err=0 tag=101 nentries=24 wtime=0.000078414 optime=0.001614101 etime=0.001690742
Almost all records appear in pairs: a service request record, SRCH in the example, followed by a RESULT record. Connection, closed, and abandon records appear individually.
The access logs have several levels of logging that you can configure using the nsslapd-accesslog-level attribute.
11.1.1. Access logging levels
Different levels of access logging record different kinds of operations that Directory Server performs.
The access log has the following log levels:
- No access logging (0).
- Logging for internal access operations (4).
- Logging for connections, operations, and results (256). The default level.
- Logging for access to an entry and referrals (512).
Use the nsslapd-accesslog-level attribute to configure the access log level. The attribute values are additive: if you set a log level value of 260, it includes levels 256 and 4.
11.1.2. Default access log content
By default, Directory Server has the 256 logging level that records access to an entry and contains information presented further.
Connection number (conn)
Directory Server lists every external LDAP request with an incremental connection number, conn=13 in the example. Connection numbers start at conn=0 immediately after the server startup.
[time_stamp] conn=13 fd=608 slot=608 connection from 172.17.0.2 to 172.17.0.2
[time_stamp] conn=13 fd=608 slot=608 connection from 172.17.0.2 to 172.17.0.2
Directory Server does not record internal LDAP requests by default. To enable logging of internal access operations, use the nsslapd-accesslog-level configuration attribute.
File descriptor (fd)
Every connection from an external LDAP client to Directory Server requires a file descriptor or socket descriptor from the operating system, in this case fd=608. The fd=608 value indicates that an external LDAP client used the file descriptor number 608 out of the total pool of available file descriptors.
[time_stamp] conn=11 fd=608 slot=608 connection from 172.17.0.2 to 172.17.0.2
[time_stamp] conn=11 fd=608 slot=608 connection from 172.17.0.2 to 172.17.0.2Slot number (slot)
The slot number, slot=608 in the example, is a legacy part of the access log that has the same meaning as file descriptor. Ignore this part of the access log.
[time_stamp] conn=11 fd=608 slot=608 connection from 172.17.0.2 to 172.17.0.2.
[time_stamp] conn=11 fd=608 slot=608 connection from 172.17.0.2 to 172.17.0.2.Operation number (opt)
To process an LDAP request, Directory Server performs a series of operations. For a connection, all operation request and operation result pairs have incremental operation numbers beginning with op=0 to identify different operations.
In the example:
-
op=0for the bind operation request and the result -
op=1for the LDAP search request and the result -
op=2for the abandon operation -
op=3for the unbind operation the LDAP client sends and the result
Method type (method)
The method number, method=128 in the example, indicates which LDAPv3 bind method the client used.
[time_stamp] conn=11 op=0 BIND dn="cn=Directory Manager" method=128 version=3
[time_stamp] conn=11 op=0 BIND dn="cn=Directory Manager" method=128 version=3The method type can have one of the three possible values:
-
0for authentication -
128for a simple bind with a user password -
saslfor a SASL bind that uses an external authentication mechanism
Version number (version)
The version number indicates the LDAP version number that the LDAP client used to communicate with the LDAP server. The LDAP version number can be either LDAPv2 or LDAPv3. In the example, it uses version=3.
[time_stamp] conn=11 op=0 BIND dn="cn=Directory Manager" method=128 version=3
[time_stamp] conn=11 op=0 BIND dn="cn=Directory Manager" method=128 version=3Error number (err)
The error number provides the LDAP result code that returns performed LDAP operation. The LDAP error number 0 means that the operation was successful. The example has op=0.
[time_stamp] conn=2 op=0 RESULT err=0 tag=97 nentries=0 wtime=0.000076581 optime=0.000082736 etime=0.000158680
[time_stamp] conn=2 op=0 RESULT err=0 tag=97 nentries=0 wtime=0.000076581 optime=0.000082736 etime=0.000158680Tag number (tag)
The tag number indicates the type of a returned result for an operation. Directory Server uses a BER tags from the LDAP protocol. The example has tag=97.
[time_stamp] conn=11 op=0 RESULT err=0 tag=97 nentries=0 wtime=0.000076581 optime=0.000082736 etime=0.000158680
[time_stamp] conn=11 op=0 RESULT err=0 tag=97 nentries=0 wtime=0.000076581 optime=0.000082736 etime=0.000158680The following table provides commonly used tags:
| Tag | Description |
|---|---|
| tag=97 | The result from a client bind operation. |
| tag=100 | The actual entry that Directory Server searched for. It is not a result tag, and the access log does not contain such a tag. |
| tag=101 | The result from a search operation. |
| tag=103 | The result from a modify operation. |
| tag=105 | The result from an add operation. |
| tag=107 | The result from a delete operation. |
| tag=109 | The result from a moddn (renaming) operation. |
| tag=111 | The result from a compare operation. |
| tag=115 | Search reference when the entry that the operation searches for holds a referral to the required entry. It is not a result tag, and the access log does not contain such a tag. |
| tag=120 | The result from an extended operation. |
| tag=121 | The result from an intermediate operation. |
Number of entries (nentries)
The nentries record shows the number of entries that a search operation found matching the LDAP client request.
[time_stamp] conn=11 op=0 RESULT err=0 tag=97 nentries=0 wtime=0.000076581 optime=0.000082736 etime=0.000158680
[time_stamp] conn=11 op=0 RESULT err=0 tag=97 nentries=0 wtime=0.000076581 optime=0.000082736 etime=0.000158680
In the example, nentries=0, Directory Server did not find any matching entries.
Elapsed time (etime)
The etime record shows the elapsed time or the amount of time (in seconds) that Directory Server spent to perform the LDAP operation.
[time_stamp] conn=11 op=1 RESULT err=0 tag=101 nentries=1 wtime=0.000076581 optime=0.000082736 etime=0.000158680 notes=U
[time_stamp] conn=11 op=1 RESULT err=0 tag=101 nentries=1 wtime=0.000076581 optime=0.000082736 etime=0.000158680 notes=UIn the example, Directory Server spent 0.000158680 seconds to perform the operation.
An etime value of 0 means that the operation actually took 0 nanoseconds to perform.
LDAP request type
The LDAP request type indicates what type of an LDAP request LDAP client issued. Possible values are:
-
SRCHfor a search operation -
MODfor a modify operation -
DELfor a delete operation -
ADDfor an add operation -
MODDNfor a moddn (renaming) operation -
EXTfor an extended operation -
ABANDONfor an abandon operation -
SORT serialnoif the LDAP request results in sorting the entries
[time_stamp] conn=114 op=68 SORT serialno (1)
[time_stamp] conn=114 op=68 SORT serialno (1)In the example, the number enclosed in parentheses specifies that the LDAP request sorted one candidate entry.
LDAP response type
Directory Server can issue three LDAP response types:
-
RESULTmeans a result to the client LDAP request. -
ENTRYmeans an entry Directory Server returns in response to a search operation. -
REFERRALmeans that the Directory Server sends the LDAP request to another server.
The RESULT message contains the following performance-related records:
wtime- The amount of time the operation was waiting in the work queue before a worker thread picked up the operation
optime- The amount of time it took for the actual operation to perform the task
etime- The time between when Directory Server receives the request and when the server sends the result back to the client.
The wtime and optime values provide useful information about how the server handles the load and processes operations. Because Directory Server requires some time to gathers these statistics, the sum of the wtime and optime values are slightly greater than the etime value.
Search indicators (note)
Directory Server provides additional information on searches in the note message of log entries. For example:
[time_stamp] conn=11 op=1 RESULT err=0 tag=101 nentries=1 wtime=0.000076581 optime=0.000082736 etime=0.000158680 notes=U
[time_stamp] conn=11 op=1 RESULT err=0 tag=101 nentries=1 wtime=0.000076581 optime=0.000082736 etime=0.000158680 notes=UDirectory Server supports the following search indicators:
| Search indicator | Description |
|---|---|
|
|
Paged search indicator. LDAP clients with limited resources can control the rate at which an LDAP server returns the results of a search operation. When the performed search used the LDAP control extension for simple paging of search results, Directory Server logs the |
|
|
Unindexed search indicator. Directory Server logs |
|
|
Unindexed search indicator. Directory Server logs
|
|
|
Unknown attribute indicator. Directory Server logs |
|
|
MFA plug-in binds indicator. Directory Server logs |
The note records can have combinations of values: notes=P,A and notes=U,P.
When attributes are not indexed, Directory Server must search them directly in the database. This procedure is more resource-intensive than searching the index file.
Unindexed searches occur in the following scenarios:
-
The search operation exceeds the number of searched entries set in the
nsslapd-idlistscanlimitattribute even when using the index file. For details about thensslapd-idlistscanlimitattribute, see nsslapd-idlistscanlimit description - No index file exists.
- The index file was not configured in the way required by the search.
To optimize future searches, add frequently searched unindexed attributes to the index.
An unindexed search indicator is often accompanied by a large etime value, because unindexed searches are generally more time consuming.
MFA plug-in binds
When you configure the two-factor authentication for user accounts by using a pre-bind authentication plug-in, such as the MFA plug-in, the access log records the notes=M note message to the file:
[time_stamp] conn=1 op=0 BIND dn="uid=jdoe,ou=people,dc=example,dc=com" method=128 version=3 [time_stamp] conn=1 op=0 RESULT err=0 tag=97 nentries=0 wtime=0.000111632 optime=0.006612223 etime=0.006722325 notes=M details="Multi-factor Authentication" dn="uid=jdoe,ou=people,dc=example,dc=com"
[time_stamp] conn=1 op=0 BIND dn="uid=jdoe,ou=people,dc=example,dc=com" method=128 version=3
[time_stamp] conn=1 op=0 RESULT err=0 tag=97 nentries=0 wtime=0.000111632 optime=0.006612223 etime=0.006722325 notes=M details="Multi-factor Authentication" dn="uid=jdoe,ou=people,dc=example,dc=com"
For the access log to record the notes=M note messages, the pre-bind authentication plug-in must set the flag by using the SLAPI API if a bind was part of this plug-in.
VLV-related entries (VLV)
When a search involves virtual list views (VLVs), Directory Server logs appropriate entries to the access log file. Similar to the other entries, VLV-specific records show the request and response information together:
[time_stamp] conn=67 op=8530 VLV 0:5:0210 10:5397 (0)
[time_stamp] conn=67 op=8530 VLV 0:5:0210 10:5397 (0)
In the example, the request information is 0:5:0210 and has the format beforeCount:afterCount:index:contentCount. The response information is 10:5397 (0) and has the format targetPosition:contentCount (resultCode).
If the client uses a position-by-value VLV request, the request information format is beforeCount: afterCount: value.
Search scope (scope)
The scope entry defines the scope for a performed search operation and can have one of the following values:
-
0for a base search -
1for a one-level search -
2for a subtree search
Extended operation OID (oid)
The oid record provides the object identifier (OID) of the performed extended operation. Below is an example of access log records with the extended operation OIDs:
[time_stamp] conn=13 op=1 EXT oid="2.16.840.1.113730.3.5.3" ... [time_stamp] conn=15 op=3 EXT oid="2.16.840.1.113730.3.5.5"
[time_stamp] conn=13 op=1 EXT oid="2.16.840.1.113730.3.5.3"
...
[time_stamp] conn=15 op=3 EXT oid="2.16.840.1.113730.3.5.5"Directory Server supports the following list of LDAPv3 extended operations and their OIDs:
| Extended operation name | Description | OID |
|---|---|---|
| Directory Server Start Replication Request | A replication initiator requests a replication session. | 2.16.840.1.113730.3.5.3 |
| Directory Server Replication Response | A replication responder answers in the response to a Start Replication Request extended operation or an End Replication Request extended operation. | 2.16.840.1.113730.3.5.4 |
| Directory Server End Replication Request | A replication initiator terminates the replication session. | 2.16.840.1.113730.3.5.5 |
| Directory Server Replication Entry Request |
Carries an entry with the state information ( | 2.16.840.1.113730.3.5.6 |
| Directory Server Bulk Import Start | A client requests a bulk import together with the imported suffix using the Bulk Import Start operation, and Directory Server indicates that the bulk import may begin. | 2.16.840.1.113730.3.5.7 |
| Directory Server Bulk Import Finished | A client ends a bulk import using the Bulk Import Finished operation, and Directory Server acknowledges the bulk import ending. | 2.16.840.1.113730.3.5.8 |
Change sequence number (csn)
The csn message, such as csn=3b4c8cfb000000030000, indicates that Directory Server received an update identified by its 'csn' and processed it.
Abandon message (ABANDON)
The abandon message indicates that a client or Directory Server terminates an operation.
Below is an example of log records that contain an abandon message:
[time_stamp] conn=12 op=1 SRCH base="dc=example,dc=com" scope=2 filter="(uid=bjensen)" [time_stamp] conn=12 op=2 ABANDON targetop=2 msgid=3 nentries=0 etime=0.0000113980
[time_stamp] conn=12 op=1 SRCH base="dc=example,dc=com" scope=2 filter="(uid=bjensen)"
[time_stamp] conn=12 op=2 ABANDON targetop=2 msgid=3 nentries=0 etime=0.0000113980
The nentries=0 value indicates the number of entries Directory Server sent before the operation was terminated, etime=0.0000113980 value indicates how much time (in seconds) had elapsed, and targetop=2 corresponds to the operation number that Directory Server initiated earlier (opt=2).
If Directory Server does not find what operation to abandon, a log record contains a targetop=NOTFOUND message:
[time_stamp] conn=12 op=2 ABANDON targetop=NOTFOUND msgid=2
[time_stamp] conn=12 op=2 ABANDON targetop=NOTFOUND msgid=2The example message means that Directory Server has completed the operation earlier or it is an unknown operation.
Message ID (msgid)
An LDAP SDK client generates the message ID, such as msgid=2, which is also an LDAP operation identifier. The msgid value may differ from the opt value; however, it identifies the same operation. Directory Server records the msgid with an ABANDON operation and tells the user which client operation was abandoned:
[time_stamp] conn=12 op=2 ABANDON targetop=NOTFOUND msgid=2
[time_stamp] conn=12 op=2 ABANDON targetop=NOTFOUND msgid=2
The Directory Server operation number opt starts counting at 0 for a connection. In the majority of LDAP SDK/client implementations, the message ID number msgid starts counting at 1. This explains why the msgid is frequently equal to the Directory Server opt plus 1.
SASL multi-stage bind logging
Directory Server logs each stage of the bind process. The error codes for SASL connections are really return codes:
[time_stamp] conn=16 op=0 BIND dn="" method=sasl version=3 mech=DIGEST-MD5 [time_stamp] conn=16 op=0 RESULT err=14 tag=97 nentries=0 wtime=0.000076581 optime=0.000082736 etime=0.000158680, SASL bind in progress
[time_stamp] conn=16 op=0 BIND dn="" method=sasl version=3 mech=DIGEST-MD5
[time_stamp] conn=16 op=0 RESULT err=14 tag=97 nentries=0 wtime=0.000076581 optime=0.000082736 etime=0.000158680, SASL bind in progress
The example record indicates that the SASL bind is currently in progress (SASL bind in progress) and has the return code of err=14. This means that the connection is still open. Directory Server logs SASL bind information together with the LDAP version number (version=3) and used SASL mechanism (mech=DIGEST-MD5).
Because SASL authentication requires multiple steps, Directory Server logs the authenticated DN (the DN used for access control decisions) in the bind RESULT line when Directory Server completes the binding process. This shows what entry was mapped to the SASL bind request:
[time_stamp] conn=14 op=1 RESULT err=0 tag=97 nentries=0 wtime=0.000076581 optime=0.000082736 etime=0.000158680 dn="uid=jdoe,dc=example,dc=com"
[time_stamp] conn=14 op=1 RESULT err=0 tag=97 nentries=0 wtime=0.000076581 optime=0.000082736 etime=0.000158680 dn="uid=jdoe,dc=example,dc=com"11.1.3. Non-default access log content
When you set non-default log levels or apply specific log configurations, Directory Server starts to record additional information to the access log file.
Internal operation records
When you enable logging for internal operations (4), Directory Server starts to log internal operations initiated by Directory Server or a client.
Server-initiated internal operations
If a client deletes an entry, the server runs several internal operations, such as locating the entry and updating groups in which the user was a member.
The following example shows the server-initiated internal operation logs format:
[time_stamp] conn=Internal(0) op=0(0)(0) MOD dn="cn=uniqueid generator,cn=config" [time_stamp] conn=Internal(0) op=0(0)(0) RESULT err=0 tag=48 nentries=0 wtime=0.0003979676 optime=0.0003989250 etime=0.0007968796
[time_stamp] conn=Internal(0) op=0(0)(0) MOD dn="cn=uniqueid generator,cn=config"
[time_stamp] conn=Internal(0) op=0(0)(0) RESULT err=0 tag=48 nentries=0 wtime=0.0003979676 optime=0.0003989250 etime=0.0007968796
The example record has conn=Internal that is followed by (0) and op=0(0)(nesting_level). Operation ID and internal operation ID are always 0. For the non-nested log records the nesting level is 0.
Client-initiated internal operation
Client-initiated internal operation logs have a search base, scope, filter, and requested search attributes in addition to the details of the performed search. The following example shows the format of the log records:
[time_stamp] conn=5 (Internal) op=15(1)(0) SRCH base="cn=config,cn=userroot,cn=ldbm database,cn=plugins,cn=config" scope=1 filter="objectclass=vlvsearch" attrs=ALL [time_stamp] conn=5 (Internal) op=15(1)(0) RESULT err=0 tag=48 nentries=0 wtime=0.0000143989 optime=0.0000151450 etime=0.0000295419 [time_stamp] conn=5 (Internal) op=15(2)(0) SRCH base="cn=config,cn=example,cn=ldbm database,cn=plugins,cn=config" scope=1 filter="objectclass=vlvsearch" attrs=ALL [time_stamp] conn=5 (Internal) op=15(2)(0) RESULT err=0
[time_stamp] conn=5 (Internal) op=15(1)(0) SRCH base="cn=config,cn=userroot,cn=ldbm database,cn=plugins,cn=config" scope=1 filter="objectclass=vlvsearch" attrs=ALL
[time_stamp] conn=5 (Internal) op=15(1)(0) RESULT err=0 tag=48 nentries=0 wtime=0.0000143989 optime=0.0000151450 etime=0.0000295419
[time_stamp] conn=5 (Internal) op=15(2)(0) SRCH base="cn=config,cn=example,cn=ldbm database,cn=plugins,cn=config" scope=1 filter="objectclass=vlvsearch" attrs=ALL
[time_stamp] conn=5 (Internal) op=15(2)(0) RESULT err=0
The example record has the conn record that is set to the client connection ID and followed by the string (Internal). The op record contains the operation ID, followed by (internal_operation_ID)(nesting_level). The internal operation ID can vary. For the non-nested log entries the nesting level is 0.
Internal operations with plug-in logging enabled
If the nsslapd-plugin-logging parameter is set to on and you enabled internal operations logging (4), Directory Server additionally logs internal operations of plug-ins.
For example, if you delete the uid=user,dc=example,dc=com entry, and the Referential Integrity plug-in automatically deletes this entry from the example group, the server logs the following:
Access to an entry and referrals
When you enable logging for the access to an entry and referrals (512), Directory Server has the following records in the access log file:
The example has the logging level 768 (512 + 256) and shows six entries and one referral that a search request returns in response.
Options description
The options=persistent message indicates that Directory Server performs a persistent search. You can use persistent searches for monitoring purposes and configure returning changes to given configurations when changes occur.
The following example shows the 512 and 4 log levels that contain options description.
[time_stamps] conn=1 (Internal) op=2(1)(0) SRCH base="cn=\22dc=example,dc=com\22,cn=mapping tree,cn=config"scope=0 filter="objectclass=nsMappingTree"attrs="nsslapd-referral" options=persistent
[time_stamps] conn=1 (Internal) op=2(1)(0) SRCH base="cn=\22dc=example,dc=com\22,cn=mapping tree,cn=config"scope=0 filter="objectclass=nsMappingTree"attrs="nsslapd-referral" options=persistentStatistics per a search operation
When you set the nsslapd-statlog-level attribute to 1, the access log starts to collect metrics, such as number of index lookups and overall duration of an index lookup, for each search operation.
The example of the log records shows that during the search with filter (cn=user_*), Directory Server performed the following number of database lookups:
- 0 for referrals
-
24 for
er_key -
25 for the
serkey -
25 for the
usekey -
24 for the
^uskey
11.1.4. Common connection codes
Directory Server adds a connection code to the closed log message with additional information related to the connection closure.
| Connection Code | Description |
|---|---|
| A1 | The client aborts the connection. |
| B1 | A corrupt BER tag is encountered. Directory Server logs B1 connection code to the access log when it receives corrupted BER tags that were sent over the wire. A BER tags can be corrupted due to physical layer network problems or bad LDAP client operations, such as an LDAP client cancels the operation before receives all request results. |
| B2 |
The BER tag is longer than the |
| B3 | A corrupt BER tag is encountered. |
| B4 | The server failed to send response back to the client. |
| P2 | A closed or corrupt connection is detected. |
| T1 |
The client does not receive a result after the idle period that you can set in the |
| T2 |
The server closed connection to a stalled LDAP client after a period of time you set in the |
| T3 | The server closed the connection because the specified time limit for a paged result search has been exceeded. |
| U1 | The server closes the connection after the client sends an unbind request. The server always closes a connection when it receives an unbind request. |
11.2. Error log reference
The Directory Server error log records messages of Directory Server transactions and operations. The error log contains not only error messages for failed operations, but also general information about the Directory Server processes and LDAP tasks, such as server startup messages, logins and searches of the directory, and connection information.
11.2.1. Error logging levels
The error log can record different details of the Directory Server operations, including different types of information depending on the enabled logging level.
You can set the logging level by using the nsslapd-errorlog-level configuration attribute of the cn=config entry.
The default logging level is 16384. This level includes critical error messages and standard logged messages, such as LDAP results codes and startup messages. Error logging levels are additive. To enable both replication logging (8192) and plug-in logging (65536), set the nsslapd-errorlog-level attribute to 73728 (8192 + 65536).
Enabling high levels of debug logging can significantly decrease the server performance. Therefore, enable high debug logging levels, such as replication (8192), only for troubleshooting.
| Setting | Console name | Description |
|---|---|---|
| 1 | Trace function calls | Logs a message when the server enters and exits a function. |
| 2 | Packeting handlings | Logs debug information for packets the server processes. |
| 4 | Heavy trace output | Logs when the server enters and exits a function, with additional debugging messages. |
| 8 | Connection management | Logs the current connection status, including the connection methods used for a SASL bind. |
| 16 | Packets sent and received | Prints the numbers of packets the server sends and receives. |
| 32 | Search filter processing | Logs all functions a search operation calls. |
| 64 | Config file processing |
Prints every |
| 128 | Access control list processing | Provides detailed access control list processing information. |
| 2048 | Log entry parsing | Logs schema parsing debugging information. |
| 4096 | Housekeeping | Logs debug information for housekeeping threads. |
| 8192 | Replication | Logs detailed information about every replication-related operation, including updates and errors, which is important for debugging replication problems. |
| 16384 | Default | Logs critical errors and other messages that Directory Server always writes to the error log, such as server startup messages. The error log contains these messages regardless of the log level setting. |
| 32768 | Entry cache | Logs debug information for the database entry cache. |
| 65536 | Plug-in |
Writes an entry to the log file when a server plug-in calls the |
| 262144 | Access control summary |
Summarizes information about access to the server, contains less details than the |
| 524288 | Backend database | Logs debug information for handling databases associated with suffixes. |
| 1048576 | Password policy | Logs debug information about password policy decisions. |
11.2.2. Default error log content
Either a server or a plug-in can write entries to the error log:
When a server writes logs, it uses the following format:
[time_stamp] - <severity_level> - <function_name> - <message>
[time_stamp] - <severity_level> - <function_name> - <message>Copy to Clipboard Copied! Toggle word wrap Toggle overflow An example of the error log a server generates:
[time_stamp] - NOTICE - bdb_start_autotune - found 7110616k physical memory
[time_stamp] - NOTICE - bdb_start_autotune - found 7110616k physical memoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow When a plug-in writes logs, it uses the following format:
[time_stamp] - <severity_level> - <plug-in_name> - <function_name> - <message>
[time_stamp] - <severity_level> - <plug-in_name> - <function_name> - <message>Copy to Clipboard Copied! Toggle word wrap Toggle overflow An example of the error log a plug-in generates:
[time_stamp] - ERR - NSMMReplicationPlugin - multimaster_extop_StartNSDS50ReplicationRequest - conn=19 op=3 repl="o=example.com": Excessive clock skew from supplier RUV
[time_stamp] - ERR - NSMMReplicationPlugin - multimaster_extop_StartNSDS50ReplicationRequest - conn=19 op=3 repl="o=example.com": Excessive clock skew from supplier RUVCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Error log entries contain the following information:
| Log message | Description |
|---|---|
| Time stamp | The time stamp format can differ depending on your local settings. By default, the high-resolution time stamps are enabled and measured in nanoseconds. |
| Severity level | The severity level can have the following values:
|
| Plug-in name | The plug-in name appears only if a plug-in writes the message to the error log. |
| Function name | Functions that the operation or the plug-in call. |
| Message | The output that the operation or plug-in returns. The message contains additional information, such as LDAP error codes and connection information. |
You can use the severity levels to filter your log entries. For example, to display only log entries with the ERR severity, run:
grep ERR /var/log/dirsrv/slapd-instance_name/errors [time_stamp] - ERR - no_diskspace - No enough space left on device (/var/lib/dirsrv/slapd-instance_name/db) (40009728 bytes); at least 145819238 bytes space is needed for db region files [time_stamp] - ERR - ldbm_back_start - Failed to init database, err=28 No space left on device [time_stamp] - ERR - plugin_dependency_startall - Failed to start database plugin ldbm database ...
# grep ERR /var/log/dirsrv/slapd-instance_name/errors
[time_stamp] - ERR - no_diskspace - No enough space left on device (/var/lib/dirsrv/slapd-instance_name/db) (40009728 bytes); at least 145819238 bytes space is needed for db region files
[time_stamp] - ERR - ldbm_back_start - Failed to init database, err=28 No space left on device
[time_stamp] - ERR - plugin_dependency_startall - Failed to start database plugin ldbm database
...11.2.3. Non-default error log content
Different logging levels return different details, including types of server operations. The following are the most frequently used error logging levels that are not enabled by default. Remember that you can combine logging levels.
Replication (8192)
The replication logging is one of the most important diagnostic levels to implement. The replication (8192) level records all operations related to replication and Windows synchronization, including processing modifications on a supplier and writing them to the changelog, sending updates, and changing replication agreements.
When Directory Server prepares or sends a replication update, the error log identifies if it is a replication or synchronization agreement. The log also identifies the consumer host and port and the current replication task.
The replication level log has the following format:
[time_stamp] NSMMReplicationPlugin - agmt="name" (consumer_host:consumer_port): current_task
[time_stamp] NSMMReplicationPlugin - agmt="name" (consumer_host:consumer_port): current_task
The following is the example of the replication (8192) level log, where {replicageneration} means that Directory Server sends the new information and 4949df6e000000010000 is the change sequence number (CSN) of the replicated entry:
[time_stamp] NSMMReplicationPlugin - agmt="cn=example2_agreement" (alt:13864): {replicageneration} 4949df6e000000010000
[time_stamp] NSMMReplicationPlugin - agmt="cn=example2_agreement" (alt:13864): {replicageneration} 4949df6e000000010000The following is the example of the complete process of sending a single entry to a consumer, from adding the entry to the changelog to releasing the consumer after replication is complete.
Plug-in (65536)
The plug-in (65536) level records the name of a plug-in and all functions the plug-in calls.
The plug-in level log has the following format:
[time_stamp] plug-in_name - message [time_stamp] - function - message
[time_stamp] plug-in_name - message
[time_stamp] - function - messageThe returned information can contain hundreds of lines because Directory Server processes every step. The precise recorded information depends on the plug-in itself. In the following example, the ACL Plug-in includes a connection and operation number:
[time_stamp] - DEBUG - NSACLPlugin - acl_access_allowed - conn=15 op=1 (main): Allow search on entry(cn=replication,cn=config): root user
[time_stamp] - DEBUG - NSACLPlugin - acl_access_allowed - conn=15 op=1 (main): Allow search on entry(cn=replication,cn=config): root userConfig file processing (64)
The configuration file processing log level goes through each .conf file the server uses and prints every line when the server starts up. You can use the 64 log level to debug any problems with files outside of the server normal configuration. By default, only the slapd-collations.conf file, which contains configurations for international language sets, is available.
Example of the config file processing (64) level:
[time_stamp] - DEBUG - collation_read_config - Reading config file /etc/dirsrv/slapd-supplier_1/slapd-collations.conf [time_stamp] - DEBUG - collation-plugin - collation_read_config - line 16: collation "" "" "" 1 3 2.16.840.1.113730.3.3.2.0.1 default [time_stamp] - DEBUG - collation-plugin - collation_read_config - line 17: collation ar "" "" 1 3 2.16.840.1.113730.3.3.2.1.1 ar [time_stamp] - DEBUG - collation-plugin - collation_read_config - line 18: collation be "" "" 1 3 2.16.840.1.113730.3.3.2.2.1 be be-BY ...
[time_stamp] - DEBUG - collation_read_config - Reading config file /etc/dirsrv/slapd-supplier_1/slapd-collations.conf
[time_stamp] - DEBUG - collation-plugin - collation_read_config - line 16: collation "" "" "" 1 3 2.16.840.1.113730.3.3.2.0.1 default
[time_stamp] - DEBUG - collation-plugin - collation_read_config - line 17: collation ar "" "" 1 3 2.16.840.1.113730.3.3.2.1.1 ar
[time_stamp] - DEBUG - collation-plugin - collation_read_config - line 18: collation be "" "" 1 3 2.16.840.1.113730.3.3.2.2.1 be be-BY
...Access control list processing (128) and Access control summary (262144)
Both of the ACI logging levels record information that other log levels do not include and contain a connection number (conn) and an operation number (op). The access control list processing (128) shows the series of functions called in the course of the bind and any other operations. The access control summary (262144) records the name of the plug-in, the bind DN of the user, the performed or attempted operation, and the applied ACI.
Example of the access control summary (262144) level:
Other logging levels
Many other logging levels have the output format that is similar to the plug-in logging level. The only difference is in recorded internal operations.
Logging levels, such as Heavy trace output (4), access control list processing (128), schema parsing (2048), and housekeeping (4096) levels, record the called functions when Directory Server performs different operations. In addition, the error log writes why Directory Server calls these functions for specified operations.
11.3. Audit log reference
The audit log records changes made to each database and to the server configuration. This log type is not enabled by default. If you enable audit logging, Directory Server records only successful operations to the audit log file. However, you can record failing operations to a separate file if you enable audit fail logging.
Unlike the error and access log, the audit log does not record access to the server instance, so searches against the database are not logged.
The format of the the audit log differs from the access and error logs format. Directory Server records operations in the audit log in the LDIF statements:
For more details about the LDIF files and formats see LDAP Data Interchange Format
The audit log example:
Additional resources
11.4. Audit fail log reference
If you enable fail audit logging, Directory Server starts to record only failing changes made to the server instance to the audit fail log file.
The audit fail log has the same format as the audit log and looks like LDIF statements and is not enabled by default.
Additional resources
11.5. Security log reference
The security log records a variety of security events, including the following:
- Authentication events
- Authorization issues
- DoS and TCP attacks
Directory Server stores the security log in the /var/log/dirsrv/slapd-instance_name/ directory along with other log files. The security log does not rotate quickly and consumes less disk resources in comparison to the access log that has all the information, but requires expensive parsing to get the security data.
The security log is in JSON format and enables other tooling to do the complex parsing of the log. You cannot change the log format or set a log level for the security log.
The security log example:
{ "date": "[time_stamp] ", "utc_time": "1684155510.154562500", "event": "BIND_SUCCESS", "dn": "cn=directory manager", "bind_method": "LDAPI", "root_dn": true, "client_ip": "local", "server_ip": "\/run\/slapd-instance_name.socket", "ldap_version": 3, "conn_id": 1, "op_id": 0, "msg": "" }
{ "date": "[time_stamp] ", "utc_time": "1684155510.163790695", "event": "BIND_SUCCESS", "dn": "cn=directory manager", "bind_method": "LDAPI", "root_dn": true, "client_ip": "local", "server_ip": "\/run\/slapd-instance_name.socket", "ldap_version": 3, "conn_id": 2, "op_id": 0, "msg": "" }
{'date': '[time_stamp]', 'utc_time': '168485945', 'event': 'BIND_FAILED', 'dn': 'uid=mark,ou=people,dc=example,dc=com', 'bind_method': 'SIMPLE', 'root_dn': 'false', 'client_ip': '127.0.0.1', 'server_ip': '127.0.0.1', 'conn_id': '2', 'op_id': '1', 'msg': 'INVALID_PASSWORD'}
{'date': '[time_stamp]', 'utc_time': '168499999', 'event': 'BIND_FAILED', 'dn': 'uid=mike,ou=people,dc=example,dc=com', 'bind_method': 'SIMPLE', 'root_dn': 'false', 'client_ip': '127.0.0.1', 'server_ip': '127.0.0.1', 'conn_id': '7', 'op_id': '1', 'msg': 'NO_SUCH_ENTRY'}
{"date": "[time_stamp]", "utc_time": 1657907429, "event": "TCP_ERROR", "client_ip": "::1", "server_ip": "::1", "ldap_version": 3, "conn_id": 1, "msg": "Bad Ber Tag or uncleanly closed connection - B1"}
{ "date": "[time_stamp] ", "utc_time": "1684155510.154562500", "event": "BIND_SUCCESS", "dn": "cn=directory manager", "bind_method": "LDAPI", "root_dn": true, "client_ip": "local", "server_ip": "\/run\/slapd-instance_name.socket", "ldap_version": 3, "conn_id": 1, "op_id": 0, "msg": "" }
{ "date": "[time_stamp] ", "utc_time": "1684155510.163790695", "event": "BIND_SUCCESS", "dn": "cn=directory manager", "bind_method": "LDAPI", "root_dn": true, "client_ip": "local", "server_ip": "\/run\/slapd-instance_name.socket", "ldap_version": 3, "conn_id": 2, "op_id": 0, "msg": "" }
{'date': '[time_stamp]', 'utc_time': '168485945', 'event': 'BIND_FAILED', 'dn': 'uid=mark,ou=people,dc=example,dc=com', 'bind_method': 'SIMPLE', 'root_dn': 'false', 'client_ip': '127.0.0.1', 'server_ip': '127.0.0.1', 'conn_id': '2', 'op_id': '1', 'msg': 'INVALID_PASSWORD'}
{'date': '[time_stamp]', 'utc_time': '168499999', 'event': 'BIND_FAILED', 'dn': 'uid=mike,ou=people,dc=example,dc=com', 'bind_method': 'SIMPLE', 'root_dn': 'false', 'client_ip': '127.0.0.1', 'server_ip': '127.0.0.1', 'conn_id': '7', 'op_id': '1', 'msg': 'NO_SUCH_ENTRY'}
{"date": "[time_stamp]", "utc_time": 1657907429, "event": "TCP_ERROR", "client_ip": "::1", "server_ip": "::1", "ldap_version": 3, "conn_id": 1, "msg": "Bad Ber Tag or uncleanly closed connection - B1"}The log example shows that two binds to the server were successful, two binds failed, and one event is a TCP error.
In addition, when you configure the two-factor authentication for user accounts by using a pre-bind authentication plug-in, the security log records the bind method, for example:
{ "date": "[time_stamp] ", "utc_time": "1709327649.232748932", "event": "BIND_SUCCESS", "dn": "uid=djoe,ou=people,dc=example,dc=com", "bind_method": "SIMPLE\/MFA", "root_dn": false, "client_ip": "::1", "server_ip": "::1", "ldap_version": 3, "conn_id": 1, "op_id": 0, "msg": "" }
{ "date": "[time_stamp] ", "utc_time": "1709327649.232748932", "event": "BIND_SUCCESS", "dn": "uid=djoe,ou=people,dc=example,dc=com", "bind_method": "SIMPLE\/MFA", "root_dn": false, "client_ip": "::1", "server_ip": "::1", "ldap_version": 3, "conn_id": 1, "op_id": 0, "msg": "" }Note that for the secutiry log to record such messages, the pre-bind authentication plug-in must set the flag if a bind was part of this plug-in by using the SLAPI API.
Additional resources
11.6. LDAP result codes
Directory Server uses the following LDAP result codes the log files:
| Decimal values | Hex values | Constants |
|---|---|---|
| 0 | 0x00 | LDAP_SUCCESS |
| 1 | 0x01 | LDAP_OPERATIONS_ERROR |
| 2 | 0x02 | LDAP_PROTOCOL_ERROR |
| 3 | 0x03 | LDAP_TIMELIMIT_EXCEEDED |
| 4 | 0x04 | LDAP_SIZELIMIT_EXCEEDED |
| 5 | 0x05 | LDAP_COMPARE_FALSE |
| 6 | 0x06 | LDAP_COMPARE_TRUE |
| 7 | 0x07 | LDAP_AUTH_METHOD_NOT_SUPPORTED LDAP_STRONG_AUTH_NOT_SUPPORTED |
| 8 | 0x08 | LDAP_STRONGER_AUTH_REQUIRED LDAP_STRONG_AUTH_REQUIRED |
| 9 | 0x09 | LDAP_PARTIAL_RESULTS |
| 10 | 0x0a | LDAP_REFERRAL (LDAPv3) |
| 11 | 0x0b | LDAP_ADMINLIMIT_EXCEEDED |
| 12 | 0x0c | LDAP_UNAVAILABLE_CRITICAL_EXTENSION |
| 13 | 0x0d | LDAP_CONFIDENTIALITY_REQUIRED |
| 14 | 0x0e | LDAP_SASL_BIND_IN_PROGRESS |
| 16 | 0x10 | LDAP_NO_SUCH_ATTRIBUTE |
| 17 | 0x11 | LDAP_UNDEFINED_TYPE |
| 18 | 0x12 | LDAP_INAPPROPRIATE_MATCHING |
| 19 | 0x13 | LDAP_CONSTRAINT_VIOLATION |
| 20 | 0x14 | LDAP_TYPE_OR_VALUE_EXISTS |
| 21 | 0x15 | LDAP_INVALID_SYNTAX |
| 32 | 0x20 | LDAP_NO_SUCH_OBJECT |
| 33 | 0x21 | LDAP_ALIAS_PROBLEM |
| 34 | 0x22 | LDAP_INVALID_DN_SYNTAX |
| 35 | 0x23 | LDAP_IS_LEAF (not used in LDAPv3) |
| 36 | 0x24 | LDAP_ALIAS_DEREF_PROBLEM |
| 48 | 0x30 | LDAP_INAPPROPRIATE_AUTH |
| 49 | 0x31 | LDAP_INVALID_CREDENTIALS |
| 50 | 0x32 | LDAP_INSUFFICIENT_ACCESS |
| 51 | 0x33 | LDAP_BUSY |
| 52 | 0x34 | LDAP_UNAVAILABLE |
| 53 | 0x35 | LDAP_UNWILLING_TO_PERFORM |
| 54 | 0x36 | LDAP_LOOP_DETECT |
| 60 | 0x3c | LDAP_SORT_CONTROL_MISSING |
| 61 | 0x3d | LDAP_INDEX_RANGE_ERROR |
| 64 | 0x40 | LDAP_NAMING_VIOLATION |
| 65 | 0x41 | LDAP_OBJECT_CLASS_VIOLATION |
| 66 | 0x42 | LDAP_NOT_ALLOWED_ON_NONLEAF |
| 67 | 0x43 | LDAP_NOT_ALLOWED_ON_RDN |
| 68 | 0x44 | LDAP_ALREADY_EXISTS |
| 69 | 0x45 | LDAP_NO_OBJECT_CLASS_MODS |
| 70 | 0x46 | LDAP_RESULTS_TOO_LARGE (reserved for CLDAP) |
| 71 | 0x47 | LDAP_AFFECTS_MULTIPLE_DSAS |
| 76 | 0x4C | LDAP_VIRTUAL_LIST_VIEW_ERROR |
| 80 | 0x50 | LDAP_OTHER |
| 81 | 0x51 | LDAP_SERVER_DOWN |
| 82 | 0x52 | LDAP_LOCAL_ERROR |
| 83 | 0x53 | LDAP_ENCODING_ERROR |
| 84 | 0x54 | LDAP_DECODING_ERROR |
| 85 | 0x55 | LDAP_TIMEOUT |
| 86 | 0x56 | LDAP_AUTH_UNKNOWN |
| 87 | 0x57 | LDAP_FILTER_ERROR |
| 88 | 0x58 | LDAP_USER_CANCELLED |
| 89 | 0x59 | LDAP_PARAM_ERROR |
| 90 | 0x5A | LDAP_NO_MEMORY |
| 91 | 0x5B | LDAP_CONNECT_ERROR |
| 92 | 0x5C | LDAP_NOT_SUPPORTED |
| 93 | 0x5D | LDAP_CONTROL_NOT_FOUND |
| 94 | 0x5E | LDAP_MORE_RESULTS_TO_RETURN |
| 95 | 0x5F | LDAP_MORE_RESULTS_TO_RETURN |
| 96 | 0x60 | LDAP_CLIENT_LOOP |
| 97 | 0x61 | LDAP_REFERRAL_LIMIT_EXCEEDED |
| 118 | 0x76 | LDAP_CANCELLED |