Configuring Identity Management
Managing Identity and Authorization Policies for Linux-Based Infrastructures
Edition 2.1.4
Abstract
Preface
1. Audience and Purpose
2. Examples and Formatting
2.1. Brackets
[]) are used to indicate an alternative element in a name. For example, if a tool is available in /usr/lib on 32-bit systems and in /usr/lib64 on 64-bit systems, then the tool location may be represented as /usr/lib[64].
2.2. Client Tool Information
/usr/bin and the /usr/sbin directories.
ldapmodify and ldapsearch, are from OpenLDAP. OpenLDAP tools use SASL connections by default. To perform a simple bind using a username and password, use the -x argument to disable SASL.
2.3. Text Formatting and Styles
| Formatting Style | Purpose |
|---|---|
Monospace with a background | This type of formatting is used for anything entered or returned in a command prompt. |
| Italicized text | Any text which is italicized is a variable, such as instance_name or hostname. Occasionally, this is also used to emphasize a new term or other phrase. |
| Bolded text | Most phrases which are in bold are application names, such as Cygwin, or are fields or options in a user interface, such as a User Name Here: field or button. This can also indicate a file, package, or directory name, such as /usr/sbin. |
Note
Important
Warning
3. Document Change History
| Revision History | |||
|---|---|---|---|
| Revision 2.1.4-15.400 | 2013-10-31 | ||
| |||
| Revision 2.1.4-15 | 2012-07-18 | ||
| |||
| Revision 5.8-0 | December 15, 2011 | ||
| |||
Chapter 1. Introduction to Identity Management
1.1. A Working Definition for Identity Management
- Create a Linux-based and Linux-controlled domain. Both IPA servers and IPA clients are Linux or Unix machines. While IPA can synchronize data with an Active Directory domain to allow integration with Windows servers, it is not an administrative tools for Windows machines and it does not support Windows clients. Identity Management is a management tool for Linux domains.
- Centralize identity management and identity policies.
- Build on existing, native Linux applications and protocols. While IPA has its own processes and configuration, its underlying technologies are familiar and trusted by Linux administrators and are well established on Linux systems.
1.2. Relationships Between Servers and Clients
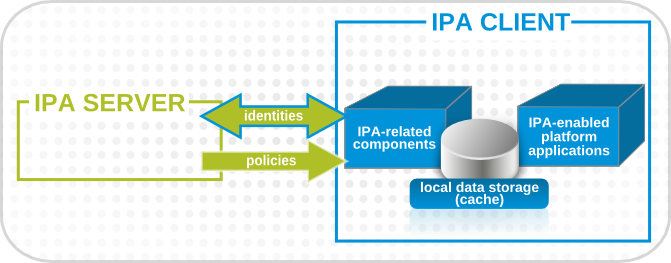
Figure 1.1. Server and Client Interactions
- Store IPA information when the machine is offline.
- Keep information active beyond its normal timeout period if the client cannot access the central server. The cache is persistent even after rebooting the machine.
- Reduce the round-trip time of requests by checking information locally before looking at the server.
- Identity information (about users, machines, and groups) is stored in the LDB database, which uses the same syntax as an LDAP directory. This identity information is originally stored in the IPA server's 389 Directory Server instance. Because this information changes frequently and is referenced frequently, it is important to be able to call the more current information quickly, which is possible using an LDB database on the client and the Directory Server on the server.
- Policy information is more static than identity information, and it can include configuration for SELinux or sudo. These policies are set globally on the server and then are propagated to the clients. On the client, the policy information is stored in the filesystem in XML files which can be downloaded and converted into a native file for whatever service is being managed.
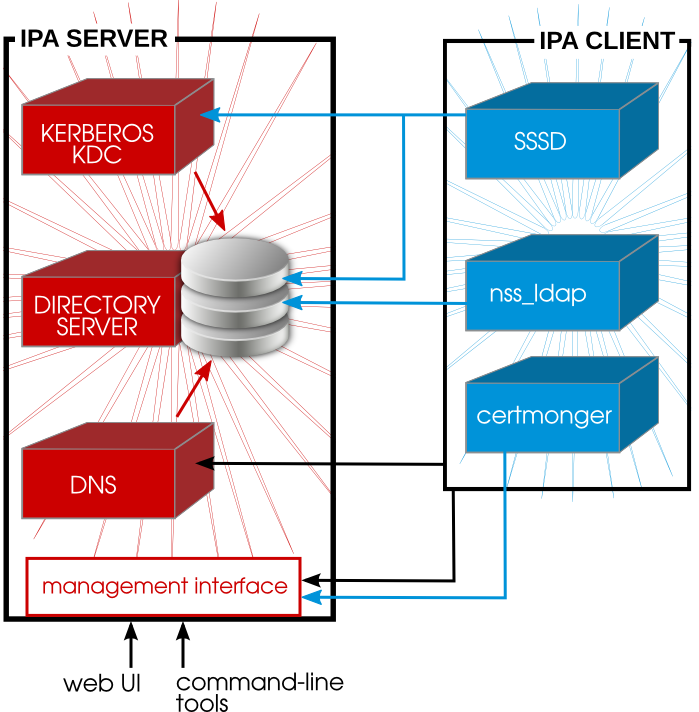
Figure 1.2. Interactions Between IPA Services
- SSSD provides the user authentication for the machine and enforces host-based access control rules.
certmongermonitors and renews the certificates on the client. It can request new certificates for the services on the system, including virtual machines.
certmonger are configured to connect to the IPA server and the required Kerberos keytab and host certificates are created. (The host certificate is not used directly by IPA; it may be used by other services, such as a web server.)
Chapter 2. Setting up Systems as IPA Clients
Note
Note
2.1. What Happens in Client Setup
- Retrieve the CA certificate for the IPA CA.
- Create a separate Kerberos configuration to test the provided credentials. This enables a Kerberos connection to the IPA XML-RPC server, necessary to join the IPA client to the IPA domain. This Kerberos configuration is ultimately discarded.Setting up the Kerberos configuration includes specifying the realm and domain details, and default ticket attributes. Forwardable tickets are configured by default, which facilitates connection to the administration interface from any operating system, and also provides for auditing of administration operations. For example, this is the Kerberos configuration for Red Hat Enterprise Linux systems:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the
ipa-joincommand to perform the actual join - Obtain a service principal for the host service and installs it into
/etc/krb5.keytab. For example,host/ipa.example.com@EXAMPLE.COM. - Enable certmonger, retrieve an SSL server certificate, and install the certificate in
/etc/pki/nssdb. - Disable the nscd daemon.
- Configures SSSD or LDAP/KRB5, including NSS and PAM configuration files.
- Configure NTP.
2.2. Configuring a Red Hat Enterprise Linux System as an IPA Client
- There must be a way to connect the client machine to the Kerberos domain, either by having an available Kerberos identity (such as the admin user) or by manually adding the client machine to the KDC on the server with a one-time password before beginning the enrollment process for the client machine.
- If there is an Active Directory server on the same network that serves DNS records, the Active Directory DNS records could prevent the client from automatically detecting the IPA server address. The
ipa-client-installscript retrieves the Active Directory DNS records instead of any records that were added for IPA.In this case, it is necessary to pass the IPA server address directly to theipa-client-installscript.
- Install the client packages. These packages provide a simple way to configure the system as a client; they also install and configure SSSD.
yum install ipa-client
# yum install ipa-clientCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If the IPA server is configured as the DNS server and is in the same domain as the client, add the server's IP address as the first entry in the client's
/etc/resolv.conffile.Note
If every machine in the domain will be an IPA client, then add the IPA server address to the DHCP configuration. - Run the client setup command.
ipa-client-install --enable-dns-updates
# ipa-client-install --enable-dns-updatesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The--enable-dns-updatesoption updates DNS with the client machine's IP address. This option should only be used if the IPA server was installed with integrated DNS or if the DNS server on the network accepts DNS entry updates with the GSS-TSIG protocol.When using the--serveroption to specify the IPA server to register with, the server name must be a fully-qualified domain name.Important
This must be a valid DNS name, which means only numbers, alphabetic characters, and hyphens (-) are allowed. Other characters, like underscores, in the hostname will cause DNS failures.Note
There is an--on-masteroption that is used as part of configuring an IPA server (which also is an IPA client, since it is within the domain). This option should never be used when configuring a regular IPA client, because it results in slightly different client configuration which may not work on a non-IPA server machine. - If prompted, enter the domain name for the IPA's DNS domain.
DNS discovery failed to determine your DNS domain Please provide the domain name of your IPA server (ex: example.com): example.com
DNS discovery failed to determine your DNS domain Please provide the domain name of your IPA server (ex: example.com): example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If prompted, enter the fully-qualified domain name of the IPA server. Alternatively, use the
--serveroption with the client installation script to supply the fully-qualified domain name of the IPA server.DNS discovery failed to find the IPA Server Please provide your IPA server name (ex: ipa.example.com): ipaserver.example.com
DNS discovery failed to find the IPA Server Please provide your IPA server name (ex: ipa.example.com): ipaserver.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Important
This must be a valid DNS name, which means only numbers, alphabetic characters, and hyphens (-) are allowed. Other characters, like underscores, in the hostname will cause DNS failures. - The client script then prompts for a Kerberos identity to use to contact and then join the Kerberos realm. When these credentials are supplied, then the client is able to join the IPA Kerberos domain and then complete the configuration:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Test that the client can connect successfully to the IPA domain and can perform basic tasks. For example, check that the IPA tools can be used to get user and group information:
id getent passwd userID getent group ipausers
$ id $ getent passwd userID $ getent group ipausersCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Set up NFS to work with Kerberos.
Note
To help troubleshoot potential NFS setup errors, enable debug information in the/etc/sysconfig/nfsfile.RPCGSSDARGS="-vvv" RPCSVCGSSDARGS="-vvv"
RPCGSSDARGS="-vvv" RPCSVCGSSDARGS="-vvv"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - On an IPA server, add an NFS service principal for the NFS client.
ipa service-add nfs/ipaclient.example.com@EXAMPLE
# ipa service-add nfs/ipaclient.example.com@EXAMPLECopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
This must be run from a machine with the ipa-admintools package installed so that theipacommand is available. - On the IPA server, obtain a keytab for the NFS service principal.
ipa-getkeytab -s ipaserver.example.com -p nfs/ipaclient.example.com@EXAMPLE -k /tmp/krb5.keytab
# ipa-getkeytab -s ipaserver.example.com -p nfs/ipaclient.example.com@EXAMPLE -k /tmp/krb5.keytabCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Some versions of the Linux NFS implementation have limited encryption type support. If the NFS server is hosted on a version older than Red Hat Enterprise Linux 5, use the-e des-cbc-crcoption to theipa-getkeytabcommand for any nfs/<FQDN> service keytabs to set up, both on the server and on all clients. This instructs the KDC to generate only DES keys.When using DES keys, all clients and servers that rely on this encryption type need to have theallow_weak_cryptooption enabled in the[libdefaults]section of the/etc/krb5.conffile. Without these configuration changes, NFS clients and servers are unable to authenticate to each other, and attempts to mount NFS filesystems may fail. The client'srpc.gssdand the server'srpc.svcgssddaemons may log errors indicating that DES encryption types are not permitted. - Copy the keytab from the IPA server to the NFS server. For example, if the IPA and NFS servers are on different machines:
scp /tmp/krb5.keytab root@nfs.example.com:/etc/krb5.keytab
# scp /tmp/krb5.keytab root@nfs.example.com:/etc/krb5.keytabCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the keytab from the IPA server to the IPA client. For example:
scp /tmp/krb5.keytab root@client.example.com:/etc/krb5.keytab
# scp /tmp/krb5.keytab root@client.example.com:/etc/krb5.keytabCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the
/etc/exportsfile on the NFS server./ipashare gss/krb5p(rw,no_root_squash,subtree_check,fsid=0)
/ipashare gss/krb5p(rw,no_root_squash,subtree_check,fsid=0)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - On the client, mount the NFS share. Use the same
-o secsetting as is used in the/etc/exportsfile for the NFS server.mount -v -t nfs4 -o sec=krb5p nfs.example.com:/ /mnt/ipashare
[root@client ~]# mount -v -t nfs4 -o sec=krb5p nfs.example.com:/ /mnt/ipashareCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.3. Manually Configuring a Linux Client
ipa-client-install command automatically configures services like Kerberos, SSSD, PAM, and NSS. However, if the ipa-client-install command cannot be used on a system for some reason, then the IPA client entries and the services can be configured manually.
- Install SSSD 1.5.x or later, if it is not already installed.
- On an IPA server. Create a host entry for the client.
ipa host-add --force --ip-address=192.168.166.31 client1.example.com
$ ipa host-add --force --ip-address=192.168.166.31 client1.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - On an IPA server. Create keytabs for the client.
- Log in as IPA; administrator.
kinit admin
$ kinit adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Set the client host to be managed by the server.
ipa host-add-managedby --hosts=ipaserver.example.com client1.example.com
$ ipa host-add-managedby --hosts=ipaserver.example.com client1.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Generate the keytab for the client.
ipa-getkeytab -s ipaserver.example.com -p host/client1.example.com -k /tmp/client1.keytab
# ipa-getkeytab -s ipaserver.example.com -p host/client1.example.com -k /tmp/client1.keytabCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Copy the keytab to the client machine and rename it
/etc/krb5.ketab.Note
If there is an existing/etc/krb5.ketabthat should be preserved, the two files can be combined usingktutil. - Set the correct user permissions and, if necessary, SELinux contexts for the
/etc/krb5.ketabfile.chown root:root 0600 system_u:object_r:krb5_keytab_t:s0
chown root:root 0600 system_u:object_r:krb5_keytab_t:s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure SSSD by editing the
/etc/sssd/sssd.conffile to point to the IPA domain.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure NSS to use SSSD for passwords, groups, users, and netgroups.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the
/etc/krb5.conffile to point to the IPA KDC.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Update the
/etc/pam.dconfiguration to use thepam_sss.somodules.- For
/etc/pam.d/fingerprint-auth:... account [default=bad success=ok user_unknown=ignore] pam_sss.so ... session optional pam_sss.so
... account [default=bad success=ok user_unknown=ignore] pam_sss.so ... session optional pam_sss.soCopy to Clipboard Copied! Toggle word wrap Toggle overflow - For
/etc/pam.d/system-auth:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - For
/etc/pam.d/password-auth:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - For
/etc/pam.d/smartcard-auth:... account [default=bad success=ok user_unknown=ignore] pam_sss.so ... session optional pam_sss.so
... account [default=bad success=ok user_unknown=ignore] pam_sss.so ... session optional pam_sss.soCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Set up NFS to work with Kerberos.
Note
To help troubleshoot potential NFS setup errors, enable debug information in the/etc/sysconfig/nfsfile.RPCGSSDARGS="-vvv" RPCSVCGSSDARGS="-vvv"
RPCGSSDARGS="-vvv" RPCSVCGSSDARGS="-vvv"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - On an IPA server, add an NFS service principal for the NFS client.
ipa service-add nfs/ipaclient.example.com@EXAMPLE
# ipa service-add nfs/ipaclient.example.com@EXAMPLECopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
This must be run from a machine with the ipa-admintools package installed so that theipacommand is available. - On the IPA server, obtain a keytab for the NFS service principal.
ipa-getkeytab -s ipaserver.example.com -p nfs/ipaclient.example.com@EXAMPLE -k /tmp/krb5.keytab
# ipa-getkeytab -s ipaserver.example.com -p nfs/ipaclient.example.com@EXAMPLE -k /tmp/krb5.keytabCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Some versions of the Linux NFS implementation have limited encryption type support. If the NFS server is hosted on a version older than Red Hat Enterprise Linux 5, use the-e des-cbc-crcoption to theipa-getkeytabcommand for any nfs/<FQDN> service keytabs to set up, both on the server and on all clients. This instructs the KDC to generate only DES keys.When using DES keys, all clients and servers that rely on this encryption type need to have theallow_weak_cryptooption enabled in the[libdefaults]section of the/etc/krb5.conffile. Without these configuration changes, NFS clients and servers are unable to authenticate to each other, and attempts to mount NFS filesystems may fail. The client'srpc.gssdand the server'srpc.svcgssddaemons may log errors indicating that DES encryption types are not permitted. - Copy the keytab from the IPA server to the NFS server. For example, if the IPA and NFS servers are on different machines:
scp /tmp/krb5.keytab root@nfs.example.com:/etc/krb5.keytab
# scp /tmp/krb5.keytab root@nfs.example.com:/etc/krb5.keytabCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the keytab from the IPA server to the IPA client. For example:
scp /tmp/krb5.keytab root@client.example.com:/etc/krb5.keytab
# scp /tmp/krb5.keytab root@client.example.com:/etc/krb5.keytabCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the
/etc/exportsfile on the NFS server./ipashare gss/krb5p(rw,no_root_squash,subtree_check,fsid=0)
/ipashare gss/krb5p(rw,no_root_squash,subtree_check,fsid=0)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - On the client, mount the NFS share.
- Always specify the share as nfs_server:/ /mountpoint.
- Use the same
-o secsetting as is used in the/etc/exportsfile for the NFS server.
mount -v -t nfs4 -o sec=krb5p nfs.example.com:/ /mnt/ipashare
[root@client ~]# mount -v -t nfs4 -o sec=krb5p nfs.example.com:/ /mnt/ipashareCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.4. Performing a Split Enrollment
ipa-client-install command. It is also possible to perform those steps separately; this allows for administrators to prepare machines and IPA in advance of actually configuring the clients. This allows more flexible setup scenarios, including bulk deployments.
Note
ipa-client-install command and allowing it to create the host. However, that administrator may have the right to run the command after a host entry exists. In that case, one administrator can create the host entry manually, then the second administrator can complete the enrollment by running the ipa-client-install command.
- An administrator creates the host entry on the IPA server.
- The second administrator installs the IPA client packages on the machine, as in Section 2.2, “Configuring a Red Hat Enterprise Linux System as an IPA Client”.
- When the second administrator runs the setup script, he must pass his Kerberos password and username (principal) with the
ipa-client-installcommand. For example:ipa-client-install -w secret -p admin2
$ ipa-client-install -w secret -p admin2Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The keytab is generated on the server and provisioned to the client machine, so that the client machine is not able to connect to the IPA domain. The keytab is saved with
root:rootownership and 0600 permissions.
Chapter 3. Basic Usage
3.1. Looking at the IPA UI
- It shows instant, visual relationships between entries (such as a user and all the groups, sudo rules, netgroups, and policies which are associated with that user).
- All entries are listed immediately without having to run a search. This makes it possible to browse entries. The UI also has a simple search box which quickly filters the list of entries.
- The interface is intuitive to use, without having to learn the command-line tools.
- The web UI can be accessed from machines outside the IPA domain, so the domain can be managed from anywhere.Using the web UI requires a valid Kerberos ticket for the IPA domain (by default), meaning that it can only be accessed from a machine within the IPA domain. Alternatively, the web UI can be configured to allow password authentication along with Kerberos authentication (Section 3.3.5, “Enabling Username/Password Authentication in Your Browser”), or a machine outside the IPA can be configured to work with Kerberos (Section 3.3.4, “Using a Browser on Another System”).
3.1.1. The UI Layout
| Main Menu Tab | Configuration Areas |
|---|---|
| Identity |
|
| Policy |
|
| Access controls within Identity Management |
|
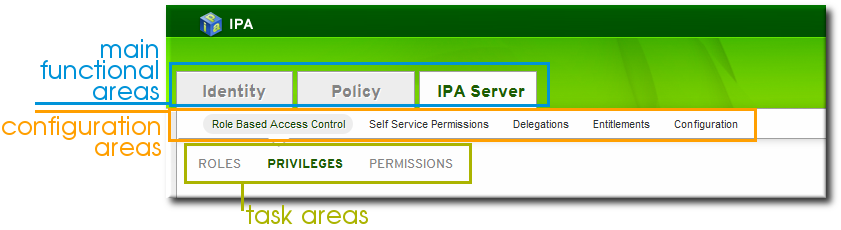
Figure 3.1. The Main Menu
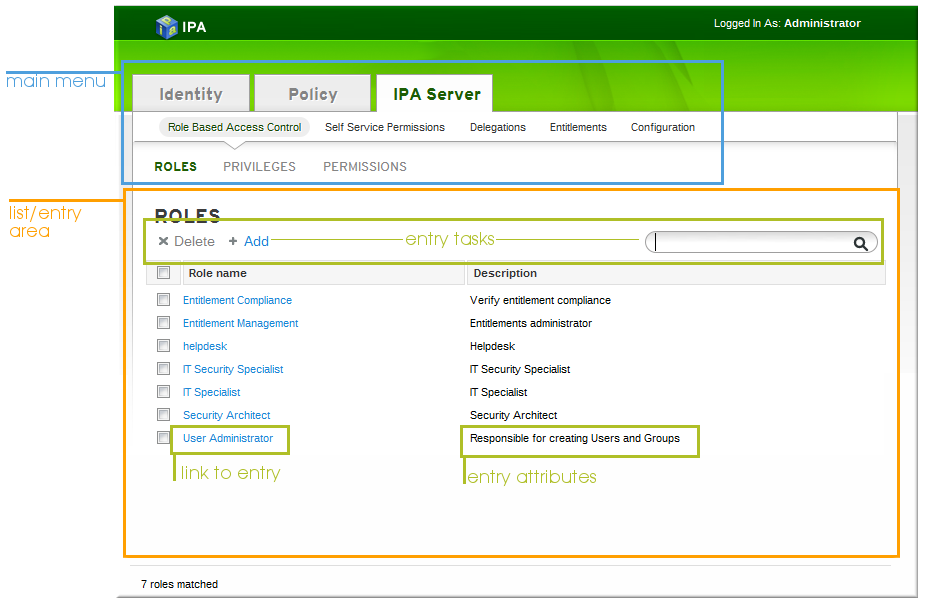
Figure 3.2. List View
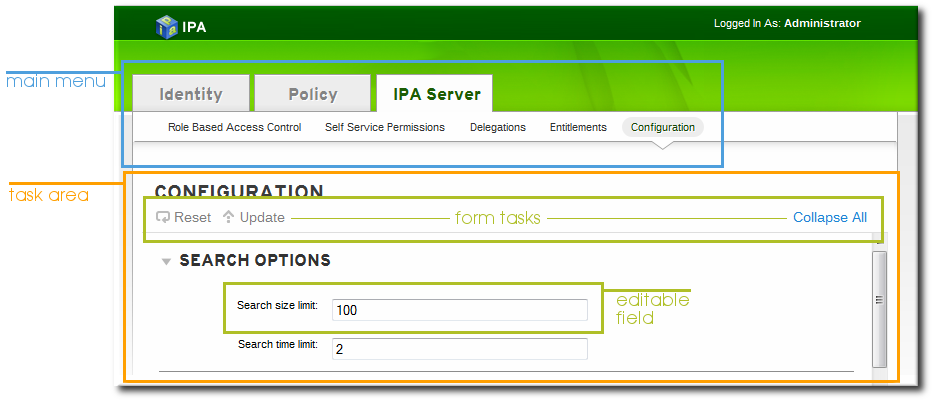
Figure 3.3. Form/Entry View
3.1.2. Page Elements
Figure 3.4. Active Task Link
Figure 3.5. Entry Breadcrumbs
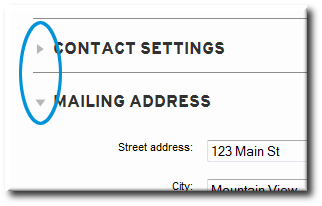
Figure 3.6. Collapsing and Expanding Form Elements
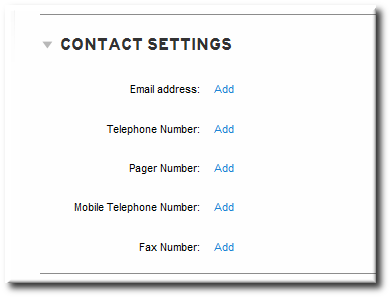
Figure 3.7. Add an Attribute
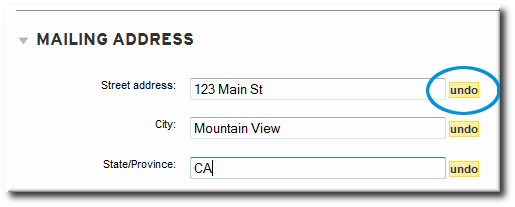
Figure 3.8. Undo Edits
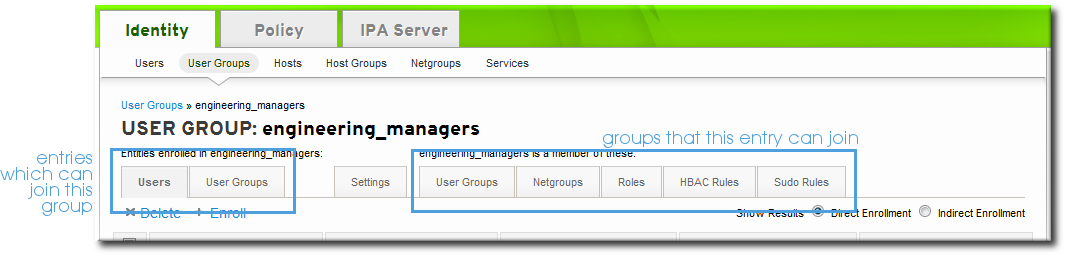
3.1.3. Showing and Changing Group Members
3.1.4. Looking at Search Results
3.2. Logging into IPA
kinit.
kinit issues the user a Kerberos ticket. This ticket is checked by any IPA or Kerberos-aware service, so that a user only needs to log in once to access all domain services. Domain services include the IPA web UI, mounted file shares, wikis, or any other application which uses IPA as its identity/authentication store.
3.2.1. Logging into IPA
kinit on a client within the IPA domain.
kinit
$ kinitkinit command must be run from a machine which has been configured as a client within the IPA domain, so that the client retrieves authenticates with the IPA KDC.
kinit logs into IPA as the currently logged-in user account. This user account must also be an IPA user for them to authenticate to the IPA Kerberos domain successfully. For example, if you are logged into the machine as jsmith:
kinit Password for jsmith@EXAMPLE.COM:
$ kinit
Password for jsmith@EXAMPLE.COM:Note
pam_krb5 is configured on the IPA client machine, then when a user logs into the machine, a ticket is created which can be used for machine services which require authentication, such as sudo.
3.2.2. Logging in When an IPA User Is Different Than the System User
kinit command, specifying the new user. For example:
kinit userName Password for userName@EXAMPLE.COM:
$ kinit userName
Password for userName@EXAMPLE.COM:admin, is created to perform normal administrative activities. To authenticate as the admin user, use the name admin when running kinit:
kinit admin
$ kinit adminNote
3.2.3. Checking the Current Logged in User
klist command to verify the identity and the ticket granting ticket (TGT) from the server:
kinit have some limitation, one of them being that the current ticket is overwritten with any new invocation of kinit. Authenticating as User A and then authenticating as User B overwrites User A's ticket.
KRB5CCNAME environment variable. This variable keeps credential caches separate in different shells.
3.2.4. Caching User Kerberos Tickets
admin, added a new user, set the password, and then tried to authenticate as that user, the administrator's ticket is lost.
KRB5CCNAME, can be used.
3.3. Using the IPA Web UI
3.3.1. Supported Web Browsers
3.3.2. Opening the IPA Web UI
- Get a valid Kerberos ticket using
kinit, as in Section 3.2, “Logging into IPA”. - Open the IPA URL. The full URL is
https://IPAserver-FQDN/ipa/ui, but this service is also accessed simply by openinghttps://IPAserver-FQDN. For example:https://server.example.com https://server.example.com/ipa/ui
https://server.example.com https://server.example.com/ipa/uiCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.3.3. Configuring the Browser
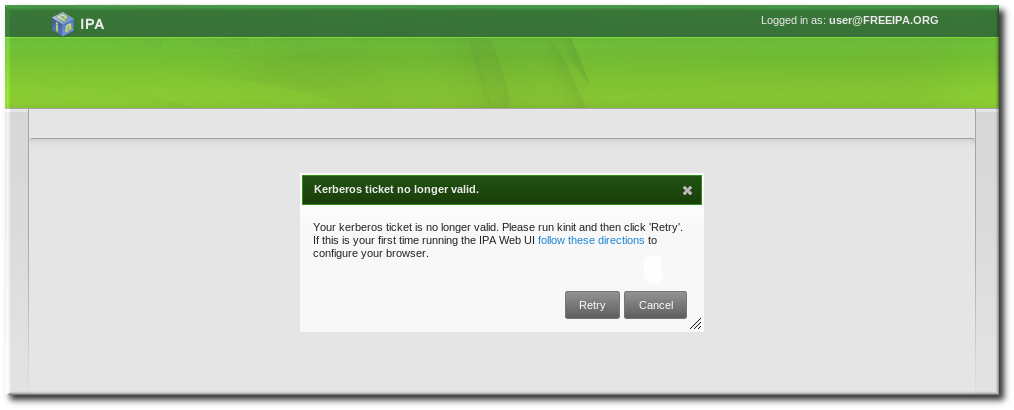
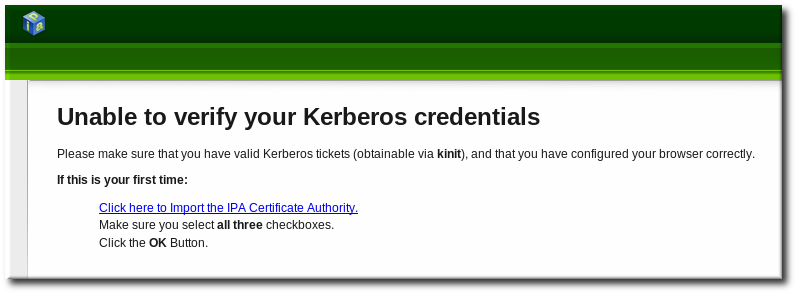
Figure 3.10. Kerberos Authentication Error
- Click the follow these directions link.
- Click the link to import the CA certificate for the IPA server.
- Set the web site and software developer (first and last) trust bits for the CA certificate.

- Click the Configure Firefox button. This automatically fills out all the
negotiatesettings in the Firefox configuration to use the IPA domain settings.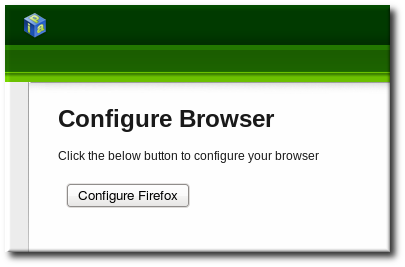 When the process is complete, a success box pops up saying that Firefox has been configured for single sign-on. For there, you are redirected to the IPA web UI.
When the process is complete, a success box pops up saying that Firefox has been configured for single sign-on. For there, you are redirected to the IPA web UI.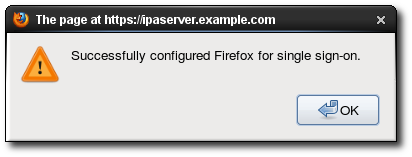
- Open Firefox.
- Type
about:configin the address bar. - In the Search field, type
negotiateto filter out the Kerberos-related parameters. - On Red Hat Enterprise Linux, enter the domain name for the URI parameters, including the preceding period (.) and set the
gsslibparameter to true:network.negotiate-auth.trusted-uris .example.com network.negotiate-auth.delegation-uris .example.com network.negotiate-auth.using-native-gsslib true
network.negotiate-auth.trusted-uris .example.com network.negotiate-auth.delegation-uris .example.com network.negotiate-auth.using-native-gsslib trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Open the web UI by going to the fully-qualified domain name of the IPA server such as
http://ipaserver.example.com. Make sure that you can open the web UI and that there are no Kerberos authentication errors. - Next, download the IPA server's CA certificate from
http://ipa.example.com/ipa/config/ca.crt. - Select the first (Trust this CA to identify web sites) and third (Trust this CA to identify software developers) check boxes.
3.3.4. Using a Browser on Another System
kinit, and then the user can authenticate against the IPA server domain.
- Copy the
/etc/krb5.conffile from the IPA server.scp /etc/krb5.conf root@externalmachine.example.com:/etc/krb5_ipa.conf
# scp /etc/krb5.conf root@externalmachine.example.com:/etc/krb5_ipa.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Warning
Do not overwrite the existingkrb5.conffile. - On the external machine, set the terminal session to use the copied IPA Kerberos configuration file:
export KRB5_CONFIG=/etc/krb5_ipa.conf
$ export KRB5_CONFIG=/etc/krb5_ipa.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure Firefox on the external machine as in Section 3.3.3, “Configuring the Browser”.
3.3.5. Enabling Username/Password Authentication in Your Browser
- Open the
ipa.conffile used by the Apache web service.vim /etc/httpd/conf.d/ipa.conf
vim /etc/httpd/conf.d/ipa.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - In the
<Location "/ipa">location definition, change theKrbMethodK5Passwdattribute from off to on.KrbMethodK5Passwd on
KrbMethodK5Passwd onCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the
httpdservice:service httpd restart
# service httpd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
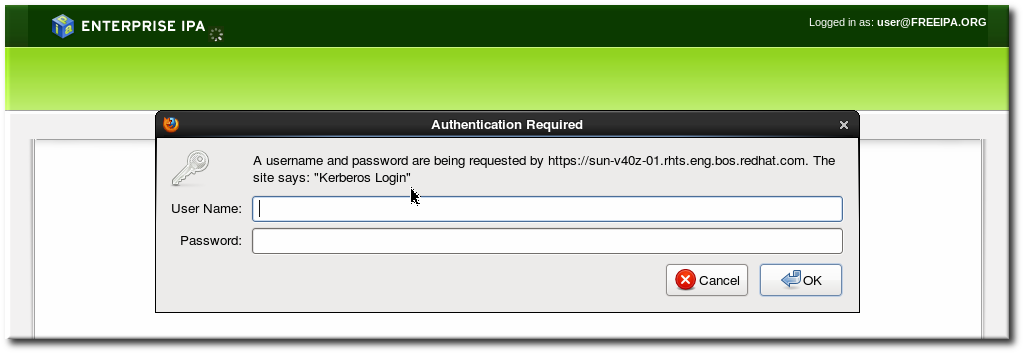
Figure 3.11. IPA Password Prompt
Note
3.3.6. Using the UI with Proxy Servers
3.3.7. Troubleshooting UI Connection Problems
- Close all browser windows.
- In a terminal, set the new log levels for Firefox:
export NSPR_LOG_MODULES=negotiateauth:5 export NSPR_LOG_FILE=/tmp/moz.log
export NSPR_LOG_MODULES=negotiateauth:5 export NSPR_LOG_FILE=/tmp/moz.logCopy to Clipboard Copied! Toggle word wrap Toggle overflow This enables verbose logging and logs all information to/tmp/moz.log. - Restart the browser from the same terminal window and attempt t .
| Error Log Message | Description and Fix |
|---|---|
-1208550944[90039d0]: entering nsNegotiateAuth::GetNextToken() -1208550944[90039d0]: gss_init_sec_context() failed: Miscellaneous failure No credentials cache found | There are no Kerberos tickets. Run kinit. |
-1208994096[8d683d8]: entering nsAuthGSSAPI::GetNextToken() -1208994096[8d683d8]: gss_init_sec_context() failed: Miscellaneous failure Server not found in Kerberos database | This can occur when you have successfully obtained Kerberos tickets but are still unable to authenticate to the UI. This indicates that there is a problem with the Kerberos configuration. The first place to check is the [domain_realm] section in the /etc/krb5.conf file. Make sure that the IPA Kerberos domain entry is correct and matches the configuration in the Firefox negotiation parameters. For example:
.example.com = EXAMPLE.COM example.com = EXAMPLE.COM |
| Nothing is in the log file. | It is possible that you are behind a proxy which is removing the HTTP headers required for negotiate authentication. Try to connect to the server using HTTPS instead, which allows the request to pass through unmodified. Then check the log file again. |
Chapter 4. Configuring Red Hat Enterprise Linux 5 Servers for IPA Domain Services
4.1. Client Configuration for sudo Rules
- Configure
sudoto look to LDAP for thesudoersfile.vim /etc/nsswitch.conf sudoers: files ldap
vim /etc/nsswitch.conf sudoers: files ldapCopy to Clipboard Copied! Toggle word wrap Toggle overflow Leaving thefilesoption in place allowssudoto check its local configuration before checking the LDAP-based IPA configuration. - Enable debug logging for
sudooperations in the/etc/ldap.conffile. If this file does not exist, it can be created.vim /etc/ldap.conf sudoers_debug: 1
vim /etc/ldap.conf sudoers_debug: 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Adding thesudoers_debugparameter helps with troubleshooting. Valid values for this parameter are 0,http://jboss-on-docs.etherpad.corp.redhat.com/10 1, and 2. Thesudodocumentation at http://www.gratisoft.us/sudo/readme_ldap.html has more information on debugging the process. - Optionally, enable debugging in SSSD to show what LDAP settings it is using.
vim /etc/sssd/sssd.conf [domain/IPADOMAIN] debug_level = 6 ....
vim /etc/sssd/sssd.conf [domain/IPADOMAIN] debug_level = 6 ....Copy to Clipboard Copied! Toggle word wrap Toggle overflow The LDAP search base used by SSSD for operations is recorded in thesssd_DOMAINNAME.loglog. - Edit the NSS/LDAP configuration file and add the following
sudo-related lines to the/etc/nss_ldap.conffile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Multiple LDAP servers can be configured in a space-separated list, and other options (like SSL and non-standard ports) can be used with the LDAP URL. ThesudoLDAP configuration is covered in thesudomanpages, http://www.sudo.ws/sudo/man/1.8.2/sudoers.ldap.man.html.Important
Theuridirective must give the fully-qualified domain name of the LDAP server, not an IP address. Otherwise,sudofails to connect to the LDAP server. - Create a symlink between the
nss_ldapmodule configuration file and the system LDAP configuration file:ln -s /etc/nss_ldap.conf /etc/ldap.conf
# ln -s /etc/nss_ldap.conf /etc/ldap.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Set a name for the NIS domain in the
sudoconfiguration.sudouses NIS netgroups, so the NIS domain name must be set in the system configuration forsudoto be able to find the host groups used in the IPAsudoconfiguration.- Open the
/etc/rc.d/rc.localfile. Setting the NIS domain name in this file allows the value to persist between reboots.vim /etc/rc.d/rc.local
# vim /etc/rc.d/rc.localCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the command to set the NIS domain name.
nisdomainname example.com
nisdomainname example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Important
Even thoughsudouses NIS-style netgroups, it is not necessary to have a NIS server installed. Netgroups require that a NIS domain be named in their configuration, sosudorequires that a NIS domain be named for netgroups. However, that NIS domain does not actually need to exist.
4.2. Configuring autofs
- Edit the
/etc/sysconfig/autofsfile to specify the schema attributes that autofs searches for:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Specify the LDAP configuration. There are two ways to do this. The simplest is to let the automount service discover the LDAP server and locations on its own:
LDAP_URI="ldap:///dc=example,dc=com"
LDAP_URI="ldap:///dc=example,dc=com"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, explicitly set which LDAP server to use and the base DN for LDAP searches:LDAP_URI="ldap://ipa.example.com" SEARCH_BASE="cn=location,cn=automount,dc=example,dc=com"
LDAP_URI="ldap://ipa.example.com" SEARCH_BASE="cn=location,cn=automount,dc=example,dc=com"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
The default value for location isdefault. If additional locations are added, then the client can be pointed to use those locations, instead. - Edit the
/etc/autofs_ldap_auth.conffile so that autofs allows client authentication with the IPA LDAP server. Changeauthrequiredto yes and set the principal to the Kerberos host principal:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If necessary, runklist -kto get the exact host principal information. - Check the
/etc/nssswitch.conffile, so that LDAP is listed as a source for automount configuration:automount: files ldap
automount: files ldapCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart autofs:
service autofs restart
# service autofs restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Test the configuration by listing a user's
/homedirectory:ls /home/userName
# ls /home/userNameCopy to Clipboard Copied! Toggle word wrap Toggle overflow If this does not mount the remote file system, check the/var/log/messagesfile for errors. If necessary, increase the debug level in the/etc/sysconfig/autofsfile by setting theLOGGINGparameter todebug.
Note
automount -f -d
automount -f -d4.3. Setting up NFS
4.3.1. Setting up a Kerberized NFS Server
- If the NFS host machine has not been added as a client to the IPA domain, then create the host entry.
- Create the NFS service entry in the IPA domain.
- Generate an NFS service keytab for the NFS server. If this command is run on the NFS server, then save the keys directly to the host keytab. For example:
ipa-getkeytab -s server.example.com -p nfs/nfs-server.example.com -k /etc/krb5.keytab -e des-cbc-crc
# ipa-getkeytab -s server.example.com -p nfs/nfs-server.example.com -k /etc/krb5.keytab -e des-cbc-crcCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Only DES keys are supported on Red Hat Enterprise Linux 5.If this command is run on a different machine:- Save the keytab to a temporary file. For example:
... -k /tmp/nfs.keytab
... -k /tmp/nfs.keytabCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the keytabs over to the NFS machine.
- Set the file permissions to 0700.
- On the NFS host machine, add the service key to the keytab file.
( echo rkt /tmp/nfs.keytab; echo wkt /etc/krb5.keytab) |ktutil
# ( echo rkt /tmp/nfs.keytab; echo wkt /etc/krb5.keytab) |ktutilCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Install the NFS packages. For example:
yum install nfs-utils
# yum install nfs-utilsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the
krb5.conffile to allow weak crypto. This is required for every NFS client if any client in the domain will use older encryption options like DES.vim /etc/krb5.conf allow_weak_crypto = true
# vim /etc/krb5.conf allow_weak_crypto = trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the NFS server configuration to use NFSv4 security by uncommenting the
SECURE_NFSline.vim /etc/sysconfig/nfs SECURE_NFS="yes"
# vim /etc/sysconfig/nfs SECURE_NFS="yes"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If the NFS server and client are in different DNS domains, then configure the NFS domain.
vim /etc/idmapd.conf Domain = example.com
# vim /etc/idmapd.conf Domain = example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the
/etc/exportsfile and add the Kerberos information:/export *(rw,sec=sys:krb5:krb5i:krb5p)
/export *(rw,sec=sys:krb5:krb5i:krb5p)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the NFS server.
service nfs restart
# service nfs restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the NFS server as an NFS client, following the directions in Section 4.3.2, “Setting up a Kerberized NFS Client”.
4.3.2. Setting up a Kerberized NFS Client
- If the NFS client is not enrolled as a client in the IPA domain, then set up the required host entries.
- Create the host entry.
- Generate host keytab for the NFS client. If this command is run on the NFS clien, then save the keys directly to the host keytab. For example:
ipa-getkeytab -p host/nfs-client-server.example.com@EXAMPLE.COM -k /etc/krb5.keytab -e des-cbc-crc
# ipa-getkeytab -p host/nfs-client-server.example.com@EXAMPLE.COM -k /etc/krb5.keytab -e des-cbc-crcCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Only DES keys are supported on Red Hat Enterprise Linux 5.If this command is run on a different machine:- Save the keytab to a temporary file. For example:
... -k /tmp/nfs.keytab
... -k /tmp/nfs.keytabCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the keytabs over to the NFS machine.
- Set the file permissions to 0700.
- On the NFS host machine, add the service key to the keytab file.
( echo rkt /root/nfs-client.keytab; echo wkt /etc/krb5.keytab) |ktutil
# ( echo rkt /root/nfs-client.keytab; echo wkt /etc/krb5.keytab) |ktutilCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Edit the
krb5.conffile to allow weak crypto. This is required for every client if any client in the domain will use older encryption options like DES.vim /etc/krb5.conf allow_weak_crypto = true
# vim /etc/krb5.conf allow_weak_crypto = trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the NFS common configuration to enable client-side secure NFS, by uncommenting the
SECURE_NFSline.vim /etc/sysconfig/nfs SECURE_NFS="yes"
# vim /etc/sysconfig/nfs SECURE_NFS="yes"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If the NFS server and client are in different DNS domains, then configure the NFS domain. The
idmapd.confmust be the same on the NFS client as it is on the NFS server.vim /etc/idmapd.conf Domain = example.com
# vim /etc/idmapd.conf Domain = example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Start the GSS daemon.
service rpc.gssd start
# service rpc.gssd startCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mount the directory.
echo "$NFSSERVER:/this /mnt/this nfs4 sec=krb5i,rw,proto=tcp,port=2049" >>/etc/fstab mount -av
# echo "$NFSSERVER:/this /mnt/this nfs4 sec=krb5i,rw,proto=tcp,port=2049" >>/etc/fstab # mount -avCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Index
K
- Kerberos
- separate credentials cache, Caching User Kerberos Tickets
L
- logging in
- separate credentials cache, Caching User Kerberos Tickets
P
- port forwarding
- for the UI, Using the UI with Proxy Servers
- proxy servers
- for the UI, Using the UI with Proxy Servers
U
- users
- separate credentials cache, Caching User Kerberos Tickets
W
- web UI
- port forwarding, Using the UI with Proxy Servers
- proxy servers, Using the UI with Proxy Servers