Security-Enhanced Linux
User Guide
Abstract
Chapter 1. Trademark Information
Chapter 2. Introduction
ls -l command to view file permissions:
ls -l file1 -rwxrw-r-- 1 user1 group1 0 2009-08-30 11:03 file1
~]$ ls -l file1
-rwxrw-r-- 1 user1 group1 0 2009-08-30 11:03 file1
rwx, control the access the Linux user1 user (in this case, the owner) has to file1. The next three permission bits, rw-, control the access the Linux group1 group has to file1. The last three permission bits, r--, control the access everyone else has to file1, which includes all users and processes.
ls -Z command:
ls -Z file1 -rwxrw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
~]$ ls -Z file1
-rwxrw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
unconfined_u), a role (object_r), a type (user_home_t), and a level (s0). This information is used to make access control decisions. With DAC, access is controlled based only on Linux user and group IDs. It is important to remember that SELinux policy rules are checked after DAC rules. SELinux policy rules are not used if DAC rules deny access first.
Note
2.1. Benefits of running SELinux
- All processes and files are labeled with a type. A type defines a domain for processes, and a type for files. Processes are separated from each other by running in their own domains, and SELinux policy rules define how processes interact with files, as well as how processes interact with each other. Access is only allowed if an SELinux policy rule exists that specifically allows it.
- Fine-grained access control. Stepping beyond traditional UNIX permissions that are controlled at user discretion and based on Linux user and group IDs, SELinux access decisions are based on all available information, such as an SELinux user, role, type, and, optionally, a level.
- SELinux policy is administratively-defined, enforced system-wide, and is not set at user discretion.
- Reduced vulnerability to privilege escalation attacks. One example: since processes run in domains, and are therefore separated from each other, and because SELinux policy rules define how processes access files and other processes, if a process is compromised, the attacker only has access to the normal functions of that process, and to files the process has been configured to have access to. For example, if the Apache HTTP Server is compromised, an attacker cannot use that process to read files in user home directories, unless a specific SELinux policy rule was added or configured to allow such access.
- SELinux can be used to enforce data confidentiality and integrity, as well as protecting processes from untrusted inputs.
- antivirus software,
- a replacement for passwords, firewalls, or other security systems,
- an all-in-one security solution.
2.2. Examples
- The default action is deny. If an SELinux policy rule does not exist to allow access, such as for a process opening a file, access is denied.
- SELinux can confine Linux users. A number of confined SELinux users exist in SELinux policy. Linux users can be mapped to confined SELinux users to take advantage of the security rules and mechanisms applied to them. For example, mapping a Linux user to the SELinux
user_uuser, results in a Linux user that is not able to run (unless configured otherwise) set user ID (setuid) applications, such assudoandsu, as well as preventing them from executing files and applications in their home directory. If configured, this prevents users from executing malicious files from their home directories. - Process separation is used. Processes run in their own domains, preventing processes from accessing files used by other processes, as well as preventing processes from accessing other processes. For example, when running SELinux, unless otherwise configured, an attacker cannot compromise a Samba server, and then use that Samba server as an attack vector to read and write to files used by other processes, such as databases used by MySQL.
- SELinux helps limit the damage made by configuration mistakes. Domain Name System (DNS) servers often replicate information between each other in what is known as a zone transfer. Attackers can use zone transfers to update DNS servers with false information. When running the Berkeley Internet Name Domain (BIND) as a DNS server in Red Hat Enterprise Linux, even if an administrator forgets to limit which servers can perform a zone transfer, the default SELinux policy prevents zone files [3] from being updated via zone transfers, by the BIND
nameddaemon itself, and by other processes. - Refer to the Red Hat Magazine article, Risk report: Three years of Red Hat Enterprise Linux 4[4], for exploits that were restricted due to the default SELinux targeted policy in Red Hat Enterprise Linux 4.
- Refer to the NetworkWorld.com article, A seatbelt for server software: SELinux blocks real-world exploits[5], for background information about SELinux, and information about various exploits that SELinux has prevented.
- Refer to James Morris's SELinux mitigates remote root vulnerability in OpenPegasus blog post for information about an exploit in OpenPegasus that was mitigated by SELinux as shipped with Red Hat Enterprise Linux 4 and 5.
2.3. SELinux Architecture
2.4. SELinux States and Modes
- Enforcing: SELinux policy is enforced. SELinux denies access based on SELinux policy rules.
- Permissive: SELinux policy is not enforced. SELinux does not deny access, but denials are logged for actions that would have been denied if running in enforcing mode.
setenforce utility to change between enforcing and permissive mode. Changes made with setenforce do not persist across reboots. To change to enforcing mode, as the Linux root user, run the setenforce 1 command. To change to permissive mode, run the setenforce 0 command. Use the getenforce utility to view the current SELinux mode:
getenforce Enforcing
~]# getenforce
Enforcingsetenforce 0 getenforce Permissive
~]# setenforce 0
~]# getenforce
Permissivesetenforce 1 getenforce Enforcing
~]# setenforce 1
~]# getenforce
EnforcingChapter 3. SELinux Contexts
ls -Z command to view the SELinux context of files and directories:
ls -Z file1 -rwxrw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
~]$ ls -Z file1
-rwxrw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
- SELinux user
- The SELinux user identity is an identity known to the policy that is authorized for a specific set of roles, and for a specific MLS/MCS range. Each Linux user is mapped to an SELinux user via SELinux policy. This allows Linux users to inherit the restrictions placed on SELinux users. The mapped SELinux user identity is used in the SELinux context for processes in that session, in order to define what roles and levels they can enter. Run the
semanage login -lcommand as the Linux root user to view a list of mappings between SELinux and Linux user accounts (you need to have the policycoreutils-python package installed):Copy to Clipboard Copied! Toggle word wrap Toggle overflow Output may differ slightly from system to system. TheLogin Namecolumn lists Linux users, and theSELinux Usercolumn lists which SELinux user the Linux user is mapped to. For processes, the SELinux user limits which roles and levels are accessible. The last column,MLS/MCS Range, is the level used by Multi-Level Security (MLS) and Multi-Category Security (MCS). - role
- Part of SELinux is the Role-Based Access Control (RBAC) security model. The role is an attribute of RBAC. SELinux users are authorized for roles, and roles are authorized for domains. The role serves as an intermediary between domains and SELinux users. The roles that can be entered determine which domains can be entered; ultimately, this controls which object types can be accessed. This helps reduce vulnerability to privilege escalation attacks.
- type
- The type is an attribute of Type Enforcement. The type defines a domain for processes, and a type for files. SELinux policy rules define how types can access each other, whether it be a domain accessing a type, or a domain accessing another domain. Access is only allowed if a specific SELinux policy rule exists that allows it.
- level
- The level is an attribute of MLS and MCS. An MLS range is a pair of levels, written as lowlevel-highlevel if the levels differ, or lowlevel if the levels are identical (
s0-s0is the same ass0). Each level is a sensitivity-category pair, with categories being optional. If there are categories, the level is written as sensitivity:category-set. If there are no categories, it is written as sensitivity.If the category set is a contiguous series, it can be abbreviated. For example,c0.c3is the same asc0,c1,c2,c3. The/etc/selinux/targeted/setrans.conffile maps levels (s0:c0) to human-readable form (that isCompanyConfidential). Do not editsetrans.confwith a text editor: use thesemanagecommand to make changes. Refer to the semanage(8) manual page for further information. In Red Hat Enterprise Linux, targeted policy enforces MCS, and in MCS, there is just one sensitivity,s0. MCS in Red Hat Enterprise Linux supports 1024 different categories:c0through toc1023.s0-s0:c0.c1023is sensitivitys0and authorized for all categories.MLS enforces the Bell-La Padula Mandatory Access Model, and is used in Labeled Security Protection Profile (LSPP) environments. To use MLS restrictions, install the selinux-policy-mls package, and configure MLS to be the default SELinux policy. The MLS policy shipped with Red Hat Enterprise Linux omits many program domains that were not part of the evaluated configuration, and therefore, MLS on a desktop workstation is unusable (no support for the X Window System); however, an MLS policy from the upstream SELinux Reference Policy can be built that includes all program domains. For more information on MLS configuration, refer to Section 5.11, “Multi-Level Security (MLS)”.
3.1. Domain Transitions
entrypoint type for the new domain. The entrypoint permission is used in SELinux policy, and controls which applications can be used to enter a domain. The following example demonstrates a domain transition:
- A user wants to change their password. To do this, they run the
passwdapplication. The/usr/bin/passwdexecutable is labeled with thepasswd_exec_ttype:ls -Z /usr/bin/passwd -rwsr-xr-x root root system_u:object_r:passwd_exec_t:s0 /usr/bin/passwd
~]$ ls -Z /usr/bin/passwd -rwsr-xr-x root root system_u:object_r:passwd_exec_t:s0 /usr/bin/passwdCopy to Clipboard Copied! Toggle word wrap Toggle overflow Thepasswdapplication accesses/etc/shadow, which is labeled with theshadow_ttype:ls -Z /etc/shadow -r--------. root root system_u:object_r:shadow_t:s0 /etc/shadow
~]$ ls -Z /etc/shadow -r--------. root root system_u:object_r:shadow_t:s0 /etc/shadowCopy to Clipboard Copied! Toggle word wrap Toggle overflow - An SELinux policy rule states that processes running in the
passwd_tdomain are allowed to read and write to files labeled with theshadow_ttype. Theshadow_ttype is only applied to files that are required for a password change. This includes/etc/gshadow,/etc/shadow, and their backup files. - An SELinux policy rule states that the
passwd_tdomain hasentrypointpermission to thepasswd_exec_ttype. - When a user runs the
passwdapplication, the user's shell process transitions to thepasswd_tdomain. With SELinux, since the default action is to deny, and a rule exists that allows (among other things) applications running in thepasswd_tdomain to access files labeled with theshadow_ttype, thepasswdapplication is allowed to access/etc/shadow, and update the user's password.
passwd_t domain to access objects labeled with the shadow_t file type, other SELinux policy rules must be met before the subject can transition to a new domain. In this example, Type Enforcement ensures:
- The
passwd_tdomain can only be entered by executing an application labeled with thepasswd_exec_ttype; can only execute from authorized shared libraries, such as thelib_ttype; and cannot execute any other applications. - Only authorized domains, such as
passwd_t, can write to files labeled with theshadow_ttype. Even if other processes are running with superuser privileges, those processes cannot write to files labeled with theshadow_ttype, as they are not running in thepasswd_tdomain. - Only authorized domains can transition to the
passwd_tdomain. For example, thesendmailprocess running in thesendmail_tdomain does not have a legitimate reason to executepasswd; therefore, it can never transition to thepasswd_tdomain. - Processes running in the
passwd_tdomain can only read and write to authorized types, such as files labeled with theetc_torshadow_ttypes. This prevents thepasswdapplication from being tricked into reading or writing arbitrary files.
3.2. SELinux Contexts for Processes
ps -eZ command to view the SELinux context for processes. For example:
- Open a terminal, such as → → .
- Run the
passwdcommand. Do not enter a new password. - Open a new tab, or another terminal, and run the
ps -eZ | grep passwdcommand. The output is similar to the following:unconfined_u:unconfined_r:passwd_t:s0-s0:c0.c1023 13212 pts/1 00:00:00 passwd
unconfined_u:unconfined_r:passwd_t:s0-s0:c0.c1023 13212 pts/1 00:00:00 passwdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - In the first tab/terminal, press
Ctrl+Cto cancel thepasswdapplication.
passwd application (labeled with the passwd_exec_t type) is executed, the user's shell process transitions to the passwd_t domain. Remember that the type defines a domain for processes, and a type for files.
ps -eZ command to view the SELinux contexts for running processes. The following is a truncated example of the output, and may differ on your system:
system_r role is used for system processes, such as daemons. Type Enforcement then separates each domain.
3.3. SELinux Contexts for Users
id -Z command to view the SELinux context associated with your Linux user:
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
unconfined_u user, running as the unconfined_r role, and is running in the unconfined_t domain. s0-s0 is an MLS range, which in this case, is the same as just s0. The categories the user has access to is defined by c0.c1023, which is all categories (c0 through to c1023).
Chapter 4. Targeted Policy
unconfined_t domain, and system processes started by init run in the initrc_t domain; both of these domains are unconfined.
4.1. Confined Processes
sshd or httpd, is confined in Red Hat Enterprise Linux. Also, most processes that run as the Linux root user and perform tasks for users, such as the passwd application, are confined. When a process is confined, it runs in its own domain, such as the httpd process running in the httpd_t domain. If a confined process is compromised by an attacker, depending on SELinux policy configuration, an attacker's access to resources and the possible damage they can do is limited.
Procedure 4.1. How to Verify SELinux Status
- Run the
sestatuscommand to confirm that SELinux is enabled, is running in enforcing mode, and that targeted policy is being used. The correct output should look similar to the output bellow.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Refer to the section Section 5.4, “Permanent Changes in SELinux States and Modes” for detailed information about enabling and disabling SELinux. - As the Linux root user, run the
touch /var/www/html/testfilecommand to create a file. - Run the
ls -Z /var/www/html/testfilecommand to view the SELinux context:-rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 /var/www/html/testfile
-rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 /var/www/html/testfileCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, Linux users run unconfined in Red Hat Enterprise Linux, which is why thetestfilefile is labeled with the SELinuxunconfined_uuser. RBAC is used for processes, not files. Roles do not have a meaning for files; theobject_rrole is a generic role used for files (on persistent storage and network file systems). Under the/proc/directory, files related to processes may use thesystem_rrole. Thehttpd_sys_content_ttype allows thehttpdprocess to access this file.
httpd) from reading files that are not correctly labeled, such as files intended for use by Samba. This is an example, and should not be used in production. It assumes that the httpd and wget packages are installed, the SELinux targeted policy is used, and that SELinux is running in enforcing mode.
Procedure 4.2. An Example of Confined Process
- As the Linux root user, run the
service httpd startcommand to start thehttpdprocess. The output is as follows ifhttpdstarts successfully:service httpd start Starting httpd: [ OK ]
~]# service httpd start Starting httpd: [ OK ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Change into a directory where your Linux user has write access to, and run the
wget http://localhost/testfilecommand. Unless there are changes to the default configuration, this command succeeds:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The
chconcommand relabels files; however, such label changes do not survive when the file system is relabeled. For permanent changes that survive a file system relabel, use thesemanagecommand, which is discussed later. As the Linux root user, run the following command to change the type to a type used by Samba:chcon -t samba_share_t /var/www/html/testfile
~]# chcon -t samba_share_t /var/www/html/testfileCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run thels -Z /var/www/html/testfilecommand to view the changes:-rw-r--r-- root root unconfined_u:object_r:samba_share_t:s0 /var/www/html/testfile
-rw-r--r-- root root unconfined_u:object_r:samba_share_t:s0 /var/www/html/testfileCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Note: the current DAC permissions allow the
httpdprocess access totestfile. Change into a directory where your Linux user has write access to, and run thewget http://localhost/testfilecommand. Unless there are changes to the default configuration, this command fails:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
rm -i /var/www/html/testfilecommand to removetestfile. - If you do not require
httpdto be running, as the Linux root user, run theservice httpd stopcommand to stophttpd:service httpd stop Stopping httpd: [ OK ]
~]# service httpd stop Stopping httpd: [ OK ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow
httpd process access to testfile in step 2, because the file was labeled with a type that the httpd process does not have access to, SELinux denied access.
auditd daemon is running, an error similar to the following is logged to /var/log/audit/audit.log:
type=AVC msg=audit(1220706212.937:70): avc: denied { getattr } for pid=1904 comm="httpd" path="/var/www/html/testfile" dev=sda5 ino=247576 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=unconfined_u:object_r:samba_share_t:s0 tclass=file
type=SYSCALL msg=audit(1220706212.937:70): arch=40000003 syscall=196 success=no exit=-13 a0=b9e21da0 a1=bf9581dc a2=555ff4 a3=2008171 items=0 ppid=1902 pid=1904 auid=500 uid=48 gid=48 euid=48 suid=48 fsuid=48 egid=48 sgid=48 fsgid=48 tty=(none) ses=1 comm="httpd" exe="/usr/sbin/httpd" subj=unconfined_u:system_r:httpd_t:s0 key=(null)
type=AVC msg=audit(1220706212.937:70): avc: denied { getattr } for pid=1904 comm="httpd" path="/var/www/html/testfile" dev=sda5 ino=247576 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=unconfined_u:object_r:samba_share_t:s0 tclass=file
type=SYSCALL msg=audit(1220706212.937:70): arch=40000003 syscall=196 success=no exit=-13 a0=b9e21da0 a1=bf9581dc a2=555ff4 a3=2008171 items=0 ppid=1902 pid=1904 auid=500 uid=48 gid=48 euid=48 suid=48 fsuid=48 egid=48 sgid=48 fsgid=48 tty=(none) ses=1 comm="httpd" exe="/usr/sbin/httpd" subj=unconfined_u:system_r:httpd_t:s0 key=(null)
/var/log/httpd/error_log:
[Wed May 06 23:00:54 2009] [error] [client 127.0.0.1] (13)Permission denied: access to /testfile denied
[Wed May 06 23:00:54 2009] [error] [client 127.0.0.1] (13)Permission denied: access to /testfile denied
4.2. Unconfined Processes
initrc_t domain, unconfined kernel processes run in the kernel_t domain, and unconfined Linux users run in the unconfined_t domain. For unconfined processes, SELinux policy rules are applied, but policy rules exist that allow processes running in unconfined domains almost all access. Processes running in unconfined domains fall back to using DAC rules exclusively. If an unconfined process is compromised, SELinux does not prevent an attacker from gaining access to system resources and data, but of course, DAC rules are still used. SELinux is a security enhancement on top of DAC rules – it does not replace them.
httpd) can access data intended for use by Samba, when running unconfined. Note that in Red Hat Enterprise Linux, the httpd process runs in the confined httpd_t domain by default. This is an example, and should not be used in production. It assumes that the httpd, wget, dbus and audit packages are installed, that the SELinux targeted policy is used, and that SELinux is running in enforcing mode.
Procedure 4.3. An Example of Unconfined Process
- The
chconcommand relabels files; however, such label changes do not survive when the file system is relabeled. For permanent changes that survive a file system relabel, use thesemanagecommand, which is discussed later. As the Linux root user, run the following command to change the type to a type used by Samba:chcon -t samba_share_t /var/www/html/testfile
~]# chcon -t samba_share_t /var/www/html/testfileCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run thels -Z /var/www/html/testfilecommand to view the changes:ls -Z /var/www/html/testfile -rw-r--r-- root root unconfined_u:object_r:samba_share_t:s0 /var/www/html/testfile
~]$ ls -Z /var/www/html/testfile -rw-r--r-- root root unconfined_u:object_r:samba_share_t:s0 /var/www/html/testfileCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the
service httpd statuscommand to confirm that thehttpdprocess is not running:service httpd status httpd is stopped
~]$ service httpd status httpd is stoppedCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the output differs, run theservice httpd stopcommand as the Linux root user to stop thehttpdprocess:service httpd stop Stopping httpd: [ OK ]
~]# service httpd stop Stopping httpd: [ OK ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To make the
httpdprocess run unconfined, run the following command as the Linux root user to change the type of/usr/sbin/httpd, to a type that does not transition to a confined domain:chcon -t unconfined_exec_t /usr/sbin/httpd
~]# chcon -t unconfined_exec_t /usr/sbin/httpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the
ls -Z /usr/sbin/httpdcommand to confirm that/usr/sbin/httpdis labeled with theunconfined_exec_ttype:ls -Z /usr/sbin/httpd -rwxr-xr-x root root system_u:object_r:unconfined_exec_t:s0 /usr/sbin/httpd
~]$ ls -Z /usr/sbin/httpd -rwxr-xr-x root root system_u:object_r:unconfined_exec_t:s0 /usr/sbin/httpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
service httpd startcommand to start thehttpdprocess. The output is as follows ifhttpdstarts successfully:service httpd start Starting httpd: [ OK ]
~]# service httpd start Starting httpd: [ OK ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the
ps -eZ | grep httpdcommand to view thehttpdrunning in theunconfined_tdomain:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Change into a directory where your Linux user has write access to, and run the
wget http://localhost/testfilecommand. Unless there are changes to the default configuration, this command succeeds:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Although thehttpdprocess does not have access to files labeled with thesamba_share_ttype,httpdis running in the unconfinedunconfined_tdomain, and falls back to using DAC rules, and as such, thewgetcommand succeeds. Hadhttpdbeen running in the confinedhttpd_tdomain, thewgetcommand would have failed. - The
restoreconcommand restores the default SELinux context for files. As the Linux root user, run therestorecon -v /usr/sbin/httpdcommand to restore the default SELinux context for/usr/sbin/httpd:restorecon -v /usr/sbin/httpd restorecon reset /usr/sbin/httpd context system_u:object_r:unconfined_exec_t:s0->system_u:object_r:httpd_exec_t:s0
~]# restorecon -v /usr/sbin/httpd restorecon reset /usr/sbin/httpd context system_u:object_r:unconfined_exec_t:s0->system_u:object_r:httpd_exec_t:s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run thels -Z /usr/sbin/httpdcommand to confirm that/usr/sbin/httpdis labeled with thehttpd_exec_ttype:ls -Z /usr/sbin/httpd -rwxr-xr-x root root system_u:object_r:httpd_exec_t:s0 /usr/sbin/httpd
~]$ ls -Z /usr/sbin/httpd -rwxr-xr-x root root system_u:object_r:httpd_exec_t:s0 /usr/sbin/httpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
service httpd restartcommand to restarthttpd. After restarting, run theps -eZ | grep httpdcommand to confirm thathttpdis running in the confinedhttpd_tdomain:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
rm -i /var/www/html/testfilecommand to removetestfile:rm -i /var/www/html/testfile rm: remove regular empty file `/var/www/html/testfile'? y
~]# rm -i /var/www/html/testfile rm: remove regular empty file `/var/www/html/testfile'? yCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If you do not require
httpdto be running, as the Linux root user, run theservice httpd stopcommand to stophttpd:service httpd stop Stopping httpd: [ OK ]
~]# service httpd stop Stopping httpd: [ OK ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.3. Confined and Unconfined Users
semanage login -l command as the Linux root user:
__default__ login by default, which is mapped to the SELinux unconfined_u user. The following line defines the default mapping:
__default__ unconfined_u s0-s0:c0.c1023
__default__ unconfined_u s0-s0:c0.c1023
unconfined_u user. It assumes that the Linux root user is running unconfined, as it does by default in Red Hat Enterprise Linux 6:
- As the Linux root user, run the
useradd newusercommand to create a new Linux user namednewuser. - As the Linux root user, run the
passwd newusercommand to assign a password to the Linuxnewuseruser:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Log out of your current session, and log in as the Linux
newuseruser. When you log in, the pam_selinux PAM module automatically maps the Linux user to an SELinux user (in this case,unconfined_u), and sets up the resulting SELinux context. The Linux user's shell is then launched with this context. Run theid -Zcommand to view the context of a Linux user:id -Z unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[newuser@localhost ~]$ id -Z unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
If you no longer need thenewuseruser on your system, log out of the Linuxnewuser's session, log in with your account, and run theuserdel -r newusercommand as the Linux root user. It will removenewuseralong with their home directory.
unconfined_t domain to its own confined domain, the unconfined Linux user is still subject to the restrictions of that confined domain. The security benefit of this is that, even though a Linux user is running unconfined, the application remains confined. Therefore, the exploitation of a flaw in the application can be limited by the policy.
unconfined_t domain. The SELinux policy can also define a transition from a confined user domain to its own target confined domain. In such a case, confined Linux users are subject to the restrictions of that target confined domain. The main point is that special privileges are associated with the confined users according to their role. In the table below, you can see examples of basic confined domains for Linux users in Red Hat Enterprise Linux 6:
| User | Role | Domain | X Window System | su or sudo | Execute in home directory and /tmp/ (default) | Networking |
|---|---|---|---|---|---|---|
| sysadm_u | sysadm_r | sysadm_t | yes | su and sudo | yes | yes |
| staff_u | staff_r | staff_t | yes | only sudo | yes | yes |
| user_u | user_r | user_t | yes | no | yes | yes |
| guest_u | guest_r | guest_t | no | no | no | no |
| xguest_u | xguest_r | xguest_t | yes | no | no | Firefox only |
- Linux users in the
user_t,guest_t, andxguest_tdomains can only run set user ID (setuid) applications if SELinux policy permits it (for example,passwd). These users cannot run thesuandsudosetuid applications, and therefore cannot use these applications to become the Linux root user. - Linux users in the
sysadm_t,staff_t,user_t, andxguest_tdomains can log in via the X Window System and a terminal. - By default, Linux users in the
guest_tandxguest_tdomains cannot execute applications in their home directories or/tmp/, preventing them from executing applications, which inherit users' permissions, in directories they have write access to. This helps prevent flawed or malicious applications from modifying users' files. - By default, Linux users in the
staff_tanduser_tdomains can execute applications in their home directories and/tmp/. Refer to Section 6.6, “Booleans for Users Executing Applications” for information about allowing and preventing users from executing applications in their home directories and/tmp/. - The only network access Linux users in the
xguest_tdomain have is Firefox connecting to web pages.
webadm_rcan only administrate SELinux types related to the Apache HTTP Server. See chapter Apache HTTP Server in the Managing Confined Services guide for further information.dbadm_rcan only administrate SELinux types related to the MariaDB database and the PostgreSQL database management system. See chapters MySQL and PostgreSQL in the Managing Confined Services guide for further information.logadm_rcan only administrate SELinux types related to thesyslogandauditlogprocesses.secadm_rcan only administrate SELinux.auditadm_rcan only administrate processes related to theauditsubsystem.
seinfo -r
~]$ seinfo -rseinfo command is provided by the setools-console package, which is not installed by default.
Chapter 5. Working with SELinux
mount command; mounting NFS volumes; and how to preserve SELinux contexts when copying and archiving files and directories.
5.1. SELinux Packages
- policycoreutils provides utilities such as
restorecon,secon,setfiles,semodule,load_policy, andsetsebool, for operating and managing SELinux. - selinux-policy provides the SELinux Reference Policy. The SELinux Reference Policy is a complete SELinux policy, and is used as a basis for other policies, such as the SELinux targeted policy; refer to the Tresys Technology SELinux Reference Policy page for further information. This package also provides the
/usr/share/selinux/devel/policygentooldevelopment utility, as well as example policy files. - selinux-policy-targeted provides the SELinux targeted policy.
- libselinux – provides an API for SELinux applications.
- libselinux-utils provides the
avcstat,getenforce,getsebool,matchpathcon,selinuxconlist,selinuxdefcon,selinuxenabled,setenforce, andtoggleseboolutilities. - libselinux-python provides Python bindings for developing SELinux applications.
yum install <package-name> command:
- selinux-policy-mls provides the MLS SELinux policy.
- setroubleshoot-server translates denial messages, produced when access is denied by SELinux, into detailed descriptions that are viewed with the
sealertutility, also provided by this package. - setools-console – this package provides the Tresys Technology SETools distribution, a number of tools and libraries for analyzing and querying policy, audit log monitoring and reporting, and file context management[6]. The setools package is a meta-package for SETools. The setools-gui package provides the
apol,seaudit, andsediffxtools. The setools-console package provides theseaudit-report,sechecker,sediff,seinfo,sesearch,findcon,replcon, andindexconcommand-line tools. Refer to the Tresys Technology SETools page for information about these tools. - mcstrans translates levels, such as
s0-s0:c0.c1023, to an easier to read form, such asSystemLow-SystemHigh. This package is not installed by default. - policycoreutils-python provides utilities such as
semanage,audit2allow,audit2why, andchcat, for operating and managing SELinux. - policycoreutils-gui provides
system-config-selinux, a graphical tool for managing SELinux.
5.2. Which Log File is Used
yum install setroubleshoot command).
auditd daemon is running, SELinux denial messages, such as the following, are written to /var/log/audit/audit.log by default:
type=AVC msg=audit(1223024155.684:49): avc: denied { getattr } for pid=2000 comm="httpd" path="/var/www/html/file1" dev=dm-0 ino=399185 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=system_u:object_r:samba_share_t:s0 tclass=file
type=AVC msg=audit(1223024155.684:49): avc: denied { getattr } for pid=2000 comm="httpd" path="/var/www/html/file1" dev=dm-0 ino=399185 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=system_u:object_r:samba_share_t:s0 tclass=file
May 7 18:55:56 localhost setroubleshoot: SELinux is preventing httpd (httpd_t) "getattr" to /var/www/html/file1 (samba_share_t). For complete SELinux messages. run sealert -l de7e30d6-5488-466d-a606-92c9f40d316d
May 7 18:55:56 localhost setroubleshoot: SELinux is preventing httpd (httpd_t) "getattr" to /var/www/html/file1 (samba_share_t). For complete SELinux messages. run sealert -l de7e30d6-5488-466d-a606-92c9f40d316d
setroubleshootd no longer constantly runs as a service. However, it is still used to analyze the AVC messages. Two new programs act as a method to start setroubleshoot when needed: sedispatch and seapplet. The sedispatch utility runs as part of the audit subsystem, and via dbus, sends a message when an AVC denial message is returned. These messages go straight to setroubleshootd if it is already running. If setroubleshootd is not running, sedispatch starts it automatically. The seapplet utility runs in the system toolbar, waiting for dbus messages in setroubleshootd. It launches the notification bubble, allowing the user to review AVC messages.
Procedure 5.1. Starting Daemons Automatically
auditd and rsyslogd daemons to automatically start at boot, run the following commands as the Linux root user:
chkconfig --levels 2345 auditd on chkconfig --levels 2345 rsyslog on
~]# chkconfig --levels 2345 auditd on ~]# chkconfig --levels 2345 rsyslog onCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
service service-name statuscommand to check if these services are running, for example:service auditd status auditd (pid 1318) is running...
~]# service auditd status auditd (pid 1318) is running...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If the above services are not running (
service-name is stopped), use theservice service-name startcommand as the Linux root user to start them. For example:service auditd start Starting auditd: [ OK ]
~]# service auditd start Starting auditd: [ OK ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.3. Main Configuration File
/etc/selinux/config file is the main SELinux configuration file. It controls whether SELinux is enabled or disabled and which SELinux mode and SELinux policy is used:
SELINUX=- The
SELINUXoption sets whether SELinux is disabled or enabled and in which mode - enforcing or permissive - it is running:- When using
SELINUX=enforcing, SELinux policy is enforced, and SELinux denies access based on SELinux policy rules. Denial messages are logged. - When using
SELINUX=permissive, SELinux policy is not enforced. SELinux does not deny access, but denials are logged for actions that would have been denied if running SELinux in enforcing mode. - When using
SELINUX=disabled, SELinux is disabled (the SELinux module is not registered with the Linux kernel), and only DAC rules are used.
SELINUXTYPE=- The
SELINUXTYPEoption sets the SELinux policy to use. Targeted policy is the default policy. Only change this option if you want to use the MLS policy. For information on how to enable the MLS policy, refer to Section 5.11.2, “Enabling MLS in SELinux”.
5.4. Permanent Changes in SELinux States and Modes
getenforce or sestatus commands to check the status of SELinux. The getenforce command returns Enforcing, Permissive, or Disabled.
sestatus command returns the SELinux status and the SELinux policy being used:
Note
.autorelabel file in the root directory:
touch /.autorelabel; reboot
~]# touch /.autorelabel; reboot5.4.1. Enabling SELinux
5.4.1.1. Enforcing Mode
Procedure 5.2. Changing to Enforcing Mode
rpm -q package_name
rpm -q package_nameImportant
dracut utility has to be run to put SELinux awareness into the initramfs file system. Failing to do so causes SELinux to not start during system startup.
- Before SELinux is enabled, each file on the file system must be labeled with an SELinux context. Before this happens, confined domains may be denied access, preventing your system from booting correctly. To prevent this, configure
SELINUX=permissivein/etc/selinux/config:Copy to Clipboard Copied! Toggle word wrap Toggle overflow For more information about the permissive mode, see Section 5.4.1.2, “Permissive Mode”. - As the Linux root user, reboot the system. During the next boot, file systems are labeled. The label process labels each file with an SELinux context:
*** Warning -- SELinux targeted policy relabel is required. *** Relabeling could take a very long time, depending on file *** system size and speed of hard drives. ****
*** Warning -- SELinux targeted policy relabel is required. *** Relabeling could take a very long time, depending on file *** system size and speed of hard drives. ****Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each*(asterisk) character on the bottom line represents 1000 files that have been labeled. In the above example, four*characters represent 4000 files have been labeled. The time it takes to label all files depends on the number of files on the system and the speed of hard drives. On modern systems, this process can take as short as 10 minutes. - In permissive mode, the SELinux policy is not enforced, but denial messages are still logged for actions that would have been denied in enforcing mode. Before changing to enforcing mode, as the Linux root user, run the following command to confirm that SELinux did not deny actions during the last boot:
grep "SELinux is preventing" /var/log/messages
~]# grep "SELinux is preventing" /var/log/messagesCopy to Clipboard Copied! Toggle word wrap Toggle overflow If SELinux did not deny any actions during the last boot, this command returns no output. See Chapter 8, Troubleshooting for troubleshooting information if SELinux denied access during boot. - If there were no denial messages in
/var/log/messages, configureSELINUX=enforcingin/etc/selinux/config:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot your system. After reboot, confirm that
getenforcereturnsEnforcing:getenforce Enforcing
~]$ getenforce EnforcingCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.4.1.2. Permissive Mode
Procedure 5.3. Changing to Permissive Mode
- Edit the
/etc/selinux/configfile as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot the system:
reboot
~]# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.4.2. Disabling SELinux
Important
Procedure 5.4. Disabling SELinux
- Configure
SELINUX=disabledin the/etc/selinux/configfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot your system. After reboot, confirm that the
getenforcecommand returnsDisabled:~]~ getenforce Disabled
~]~ getenforce DisabledCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.5. Booleans
5.5.1. Listing Booleans
semanage boolean -l command as the Linux root user. The following example does not list all Booleans:
SELinux boolean column lists Boolean names. The Description column lists whether the Booleans are on or off, and what they do.
ftp_home_dir Boolean is off, preventing the FTP daemon (vsftpd) from reading and writing to files in user home directories:
ftp_home_dir -> off Allow ftp to read and write files in the user home directories
ftp_home_dir -> off Allow ftp to read and write files in the user home directories
getsebool -a command lists Booleans, whether they are on or off, but does not give a description of each one. The following example does not list all Booleans:
getsebool -a allow_console_login --> off allow_cvs_read_shadow --> off allow_daemons_dump_core --> on
~]$ getsebool -a
allow_console_login --> off
allow_cvs_read_shadow --> off
allow_daemons_dump_core --> on
getsebool boolean-name command to only list the status of the boolean-name Boolean:
getsebool allow_console_login allow_console_login --> off
~]$ getsebool allow_console_login
allow_console_login --> off
getsebool allow_console_login allow_cvs_read_shadow allow_daemons_dump_core allow_console_login --> off allow_cvs_read_shadow --> off allow_daemons_dump_core --> on
~]$ getsebool allow_console_login allow_cvs_read_shadow allow_daemons_dump_core
allow_console_login --> off
allow_cvs_read_shadow --> off
allow_daemons_dump_core --> on
5.5.2. Configuring Booleans
setsebool utility in the setsebool boolean_name on/off form to enable or disable Booleans.
httpd_can_network_connect_db Boolean:
- By default, the
httpd_can_network_connect_dbBoolean is off, preventing Apache HTTP Server scripts and modules from connecting to database servers:getsebool httpd_can_network_connect_db httpd_can_network_connect_db --> off
~]$ getsebool httpd_can_network_connect_db httpd_can_network_connect_db --> offCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To temporarily enable Apache HTTP Server scripts and modules to connect to database servers, run the
setsebool httpd_can_network_connect_db oncommand as the Linux root user. - Use the
getsebool httpd_can_network_connect_dbcommand to verify the Boolean is enabled:getsebool httpd_can_network_connect_db httpd_can_network_connect_db --> on
~]$ getsebool httpd_can_network_connect_db httpd_can_network_connect_db --> onCopy to Clipboard Copied! Toggle word wrap Toggle overflow This allows Apache HTTP Server scripts and modules to connect to database servers. - This change is not persistent across reboots. To make changes persistent across reboots, run the
setsebool -P boolean-name oncommand as the Linux root user:[7]setsebool -P httpd_can_network_connect_db on
~]# setsebool -P httpd_can_network_connect_db onCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.6. SELinux Contexts – Labeling Files
ls -Z command:
ls -Z file1 -rw-rw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
~]$ ls -Z file1
-rw-rw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
unconfined_u), a role (object_r), a type (user_home_t), and a level (s0). This information is used to make access control decisions. On DAC systems, access is controlled based on Linux user and group IDs. SELinux policy rules are checked after DAC rules. SELinux policy rules are not used if DAC rules deny access first.
Note
/etc/ directory that is labeled with the etc_t type, the new file inherits the same type:
ls -dZ - /etc/ drwxr-xr-x. root root system_u:object_r:etc_t:s0 /etc
~]$ ls -dZ - /etc/
drwxr-xr-x. root root system_u:object_r:etc_t:s0 /etc
touch /etc/file1
~]# touch /etc/file1ls -lZ /etc/file1 -rw-r--r--. root root unconfined_u:object_r:etc_t:s0 /etc/file1
~]# ls -lZ /etc/file1
-rw-r--r--. root root unconfined_u:object_r:etc_t:s0 /etc/file1
chcon, semanage fcontext, and restorecon.
5.6.1. Temporary Changes: chcon
chcon command changes the SELinux context for files. However, changes made with the chcon command do not survive a file system relabel, or the execution of the restorecon command. SELinux policy controls whether users are able to modify the SELinux context for any given file. When using chcon, users provide all or part of the SELinux context to change. An incorrect file type is a common cause of SELinux denying access.
Quick Reference
- Run the
chcon -t type file-namecommand to change the file type, where type is a type, such ashttpd_sys_content_t, and file-name is a file or directory name. - Run the
chcon -R -t type directory-namecommand to change the type of the directory and its contents, where type is a type, such ashttpd_sys_content_t, and directory-name is a directory name.
Procedure 5.5. Changing a File's or Directory's Type
file1 was a directory.
- Run the
cdcommand without arguments to change into your home directory. - Run the
touch file1command to create a new file. Use thels -Z file1command to view the SELinux context forfile1:ls -Z file1 -rw-rw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
~]$ ls -Z file1 -rw-rw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, the SELinux context forfile1includes the SELinuxunconfined_uuser,object_rrole,user_home_ttype, and thes0level. For a description of each part of the SELinux context, refer to Chapter 3, SELinux Contexts. - Run the
chcon -t samba_share_t file1command to change the type tosamba_share_t. The-toption only changes the type. View the change withls -Z file1:ls -Z file1 -rw-rw-r-- user1 group1 unconfined_u:object_r:samba_share_t:s0 file1
~]$ ls -Z file1 -rw-rw-r-- user1 group1 unconfined_u:object_r:samba_share_t:s0 file1Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
restorecon -v file1command to restore the SELinux context for thefile1file. Use the-voption to view what changes:restorecon -v file1 restorecon reset file1 context unconfined_u:object_r:samba_share_t:s0->system_u:object_r:user_home_t:s0
~]$ restorecon -v file1 restorecon reset file1 context unconfined_u:object_r:samba_share_t:s0->system_u:object_r:user_home_t:s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, the previous type,samba_share_t, is restored to the correct,user_home_ttype. When using targeted policy (the default SELinux policy in Red Hat Enterprise Linux 6), therestoreconcommand reads the files in the/etc/selinux/targeted/contexts/files/directory, to see which SELinux context files should have.
Procedure 5.6. Changing a Directory and its Contents Types
/var/www/html/):
- As the Linux root user, run the
mkdir /webcommand to create a new directory, and then thetouch /web/file{1,2,3}command to create 3 empty files (file1,file2, andfile3). The/web/directory and files in it are labeled with thedefault_ttype:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
chcon -R -t httpd_sys_content_t /web/command to change the type of the/web/directory (and its contents) tohttpd_sys_content_t:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
restorecon -R -v /web/command to restore the default SELinux contexts:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
chcon.
Note
5.6.2. Persistent Changes: semanage fcontext
semanage fcontext command is used to change the SELinux context of files. When using targeted policy, changes are written to files located in the /etc/selinux/targeted/contexts/files/ directory:
- The
file_contextsfile specifies default contexts for many files, as well as contexts updated viasemanage fcontext. - The
file_contexts.localfile stores contexts to newly created files and directories not found infile_contexts.
setfiles utility is used when a file system is relabeled and the restorecon utility restores the default SELinux contexts. This means that changes made by semanage fcontext are persistent, even if the file system is relabeled. SELinux policy controls whether users are able to modify the SELinux context for any given file.
Quick Reference
- Run the
semanage fcontext -a options file-name|directory-namecommand, remembering to use the full path to the file or directory. - Run the
restorecon -v file-name|directory-namecommand to apply the context changes.
Procedure 5.7. Changing a File's or Directory 's Type
file1 was a directory.
- As the Linux root user, run the
touch /etc/file1command to create a new file. By default, newly-created files in the/etc/directory are labeled with theetc_ttype:ls -Z /etc/file1 -rw-r--r-- root root unconfined_u:object_r:etc_t:s0 /etc/file1
~]# ls -Z /etc/file1 -rw-r--r-- root root unconfined_u:object_r:etc_t:s0 /etc/file1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use thels -dZ directory_namecommand to list information about a directory. - As the Linux root user, run the
semanage fcontext -a -t samba_share_t /etc/file1command to change thefile1type tosamba_share_t. The-aoption adds a new record, and the-toption defines a type (samba_share_t). Note that running this command does not directly change the type;file1is still labeled with theetc_ttype:semanage fcontext -a -t samba_share_t /etc/file1 ls -Z /etc/file1 -rw-r--r-- root root unconfined_u:object_r:etc_t:s0 /etc/file1
~]# semanage fcontext -a -t samba_share_t /etc/file1 ~]# ls -Z /etc/file1 -rw-r--r-- root root unconfined_u:object_r:etc_t:s0 /etc/file1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Thesemanage fcontext -a -t samba_share_t /etc/file1command adds the following entry to/etc/selinux/targeted/contexts/files/file_contexts.local:/etc/file1 unconfined_u:object_r:samba_share_t:s0
/etc/file1 unconfined_u:object_r:samba_share_t:s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
restorecon -v /etc/file1command to change the type. Because thesemanagecommand added an entry tofile_contexts.localfor/etc/file1, therestoreconcommand changes the type tosamba_share_t:restorecon -v /etc/file1 restorecon reset /etc/file1 context unconfined_u:object_r:etc_t:s0->system_u:object_r:samba_share_t:s0
~]# restorecon -v /etc/file1 restorecon reset /etc/file1 context unconfined_u:object_r:etc_t:s0->system_u:object_r:samba_share_t:s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 5.8. Changing a Directory and its Contents Types
/var/www/html/):
- As the Linux root user, run the
mkdir /webcommand to create a new directory, and then thetouch /web/file{1,2,3}command to create 3 empty files (file1,file2, andfile3). The/web/directory and files in it are labeled with thedefault_ttype:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
semanage fcontext -a -t httpd_sys_content_t "/web(/.*)?"command to change the type of the/web/directory and the files in it, tohttpd_sys_content_t. The-aoption adds a new record, and the-toption defines a type (httpd_sys_content_t). The"/web(/.*)?"regular expression causes thesemanagecommand to apply changes to the/web/directory, as well as the files in it. Note that running this command does not directly change the type;/web/and files in it are still labeled with thedefault_ttype:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Thesemanage fcontext -a -t httpd_sys_content_t "/web(/.*)?"command adds the following entry to/etc/selinux/targeted/contexts/files/file_contexts.local:/web(/.*)? system_u:object_r:httpd_sys_content_t:s0
/web(/.*)? system_u:object_r:httpd_sys_content_t:s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
restorecon -R -v /webcommand to change the type of the/web/directory, as well as all files in it. The-Ris for recursive, which means all files and directories under the/web/directory are labeled with thehttpd_sys_content_ttype. Since thesemanagecommand added an entry tofile.contexts.localfor/web(/.*)?, therestoreconcommand changes the types tohttpd_sys_content_t:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that by default, newly-created files and directories inherit the SELinux type of their parent directories.
Procedure 5.9. Deleting an added Context
/web(/.*)?, use quotation marks around the regular expression:
semanage fcontext -d "/web(/.*)?"
~]# semanage fcontext -d "/web(/.*)?"- To remove the context, as the Linux root user, run the
semanage fcontext -d file-name|directory-namecommand, where file-name|directory-name is the first part infile_contexts.local. The following is an example of a context infile_contexts.local:/test system_u:object_r:httpd_sys_content_t:s0
/test system_u:object_r:httpd_sys_content_t:s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow With the first part being/test. To prevent the/test/directory from being labeled with thehttpd_sys_content_tafter runningrestorecon, or after a file system relabel, run the following command as the Linux root user to delete the context fromfile_contexts.local:semanage fcontext -d /test
~]# semanage fcontext -d /testCopy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, use the
restoreconutility to restore the default SELinux context.
semanage.
Important
semanage fcontext -a, use the full path to the file or directory to avoid files being mislabeled after a file system relabel, or after the restorecon command is run.
5.7. The file_t and default_t Types
file_t type is the default type for files that have not been assigned an EA value. This type is only used for this purpose and does not exist on correctly labeled file systems, because all files on a system running SELinux should have a proper SELinux context, and the file_t type is never used in file-context configuration[8].
default_t type is used on files that do not match any pattern in file-context configuration, so that such files can be distinguished from files that do not have a context on disk, and generally are kept inaccessible to confined domains. For example, if you create a new top-level directory, such as /mydirectory/, this directory may be labeled with the default_t type. If services need access to this directory, you need to update the file-context configuration for this location. See Section 5.6.2, “Persistent Changes: semanage fcontext” for details on adding a context to the file-context configuration.
5.8. Mounting File Systems
mount -o context command to override existing extended attributes, or to specify a different, default context for file systems that do not support extended attributes. This is useful if you do not trust a file system to supply the correct attributes, for example, removable media used in multiple systems. The mount -o context command can also be used to support labeling for file systems that do not support extended attributes, such as File Allocation Table (FAT) or NFS volumes. The context specified with the context is not written to disk: the original contexts are preserved, and are seen when mounting without a context option (if the file system had extended attributes in the first place).
5.8.1. Context Mounts
mount -o context=SELinux_user:role:type:level command when mounting the desired file system. Context changes are not written to disk. By default, NFS mounts on the client side are labeled with a default context defined by policy for NFS volumes. In common policies, this default context uses the nfs_t type. Without additional mount options, this may prevent sharing NFS volumes via other services, such as the Apache HTTP Server. The following example mounts an NFS volume so that it can be shared via the Apache HTTP Server:
mount server:/export /local/mount/point -o \ context="system_u:object_r:httpd_sys_content_t:s0"
~]# mount server:/export /local/mount/point -o \ context="system_u:object_r:httpd_sys_content_t:s0"-o context. However, since these changes are not written to disk, the context specified with this option does not persist between mounts. Therefore, this option must be used with the same context specified during every mount to retain the desired context. For information about making context mount persistent, refer to the Section 5.8.5, “Making Context Mounts Persistent”.
-o context, use the SELinux system_u user and object_r role, and concentrate on the type. If you are not using the MLS policy or multi-category security, use the s0 level.
Note
context option, context changes (by users and processes) are prohibited. For example, running the chcon command on a file system mounted with a context option results in a Operation not supported error.
5.8.2. Changing the Default Context
file_t and default_t Types”, on file systems that support extended attributes, when a file that lacks an SELinux context on disk is accessed, it is treated as if it had a default context as defined by SELinux policy. In common policies, this default context uses the file_t type. If it is desirable to use a different default context, mount the file system with the defcontext option.
/dev/sda2) to the newly-created /test/ directory. It assumes that there are no rules in /etc/selinux/targeted/contexts/files/ that define a context for the /test/ directory:
mount /dev/sda2 /test/ -o defcontext="system_u:object_r:samba_share_t:s0"
~]# mount /dev/sda2 /test/ -o defcontext="system_u:object_r:samba_share_t:s0"- the
defcontextoption defines thatsystem_u:object_r:samba_share_t:s0is "the default security context for unlabeled files"[9]. - when mounted, the root directory (
/test/) of the file system is treated as if it is labeled with the context specified bydefcontext(this label is not stored on disk). This affects the labeling for files created under/test/: new files inherit thesamba_share_ttype, and these labels are stored on disk. - files created under
/test/while the file system was mounted with adefcontextoption retain their labels.
5.8.3. Mounting an NFS Volume
nfs_t type. Depending on policy configuration, services, such as Apache HTTP Server and MySQL, may not be able to read files labeled with the nfs_t type. This may prevent file systems labeled with this type from being mounted and then read or exported by other services.
context option when mounting to override the nfs_t type. Use the following context option to mount NFS volumes so that they can be shared via the Apache HTTP Server:
mount server:/export /local/mount/point -o context="system_u:object_r:httpd_sys_content_t:s0"
~]# mount server:/export /local/mount/point -o context="system_u:object_r:httpd_sys_content_t:s0"context options, Booleans can be enabled to allow services access to file systems labeled with the nfs_t type. Refer to Managing Confined Services for instructions on configuring Booleans to allow services access to the nfs_t type.
5.8.4. Multiple NFS Mounts
/export, which has two subdirectories, web/ and database/. The following commands attempt two mounts from a single NFS export, and try to override the context for each one:
mount server:/export/web /local/web -o context="system_u:object_r:httpd_sys_content_t:s0" mount server:/export/database /local/database -o context="system_u:object_r:mysqld_db_t:s0"
~]# mount server:/export/web /local/web -o context="system_u:object_r:httpd_sys_content_t:s0"
~]# mount server:/export/database /local/database -o context="system_u:object_r:mysqld_db_t:s0"/var/log/messages:
kernel: SELinux: mount invalid. Same superblock, different security settings for (dev 0:15, type nfs)
kernel: SELinux: mount invalid. Same superblock, different security settings for (dev 0:15, type nfs)
-o nosharecache,context options. The following example mounts multiple mounts from a single NFS export, with a different context for each mount (allowing a single service access to each one):
mount server:/export/web /local/web -o nosharecache,context="system_u:object_r:httpd_sys_content_t:s0" mount server:/export/database /local/database -o \ nosharecache,context="system_u:object_r:mysqld_db_t:s0"
~]# mount server:/export/web /local/web -o nosharecache,context="system_u:object_r:httpd_sys_content_t:s0"
~]# mount server:/export/database /local/database -o \ nosharecache,context="system_u:object_r:mysqld_db_t:s0"server:/export/web is mounted locally to /local/web/, with all files being labeled with the httpd_sys_content_t type, allowing Apache HTTP Server access. server:/export/database is mounted locally to /local/database, with all files being labeled with the mysqld_db_t type, allowing MySQL access. These type changes are not written to disk.
Important
nosharecache options allows you to mount the same subdirectory of an export multiple times with different contexts (for example, mounting /export/web multiple times). Do not mount the same subdirectory from an export multiple times with different contexts, as this creates an overlapping mount, where files are accessible under two different contexts.
5.8.5. Making Context Mounts Persistent
/etc/fstab or an automounter map, and use the desired context as a mount option. The following example adds an entry to /etc/fstab for an NFS context mount:
server:/export /local/mount/ nfs context="system_u:object_r:httpd_sys_content_t:s0" 0 0
server:/export /local/mount/ nfs context="system_u:object_r:httpd_sys_content_t:s0" 0 0
5.9. Maintaining SELinux Labels
5.9.1. Copying Files and Directories
user_home_t type:
touch file1 ls -Z file1 -rw-rw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
~]$ touch file1
~]$ ls -Z file1
-rw-rw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
/etc/, the new file is created in accordance to default-labeling rules for the /etc/ directory. Copying a file (without additional options) may not preserve the original context:
file1 is copied to /etc/, if /etc/file1 does not exist, /etc/file1 is created as a new file. As shown in the example above, /etc/file1 is labeled with the etc_t type, in accordance to default-labeling rules.
cp options to preserve the context of the original file, such as --preserve=context. SELinux policy may prevent contexts from being preserved during copies.
Copying Without Preserving SELinux Contexts
cp command, if no options are given, the type is inherited from the targeted, parent directory:
file1 is created in a user's home directory, and is labeled with the user_home_t type. The /var/www/html/ directory is labeled with the httpd_sys_content_t type, as shown with the ls -dZ /var/www/html/ command. When file1 is copied to /var/www/html/, it inherits the httpd_sys_content_t type, as shown with the ls -Z /var/www/html/file1 command.
Preserving SELinux Contexts When Copying
cp --preserve=context command to preserve contexts when copying:
file1 is created in a user's home directory, and is labeled with the user_home_t type. The /var/www/html/ directory is labeled with the httpd_sys_content_t type, as shown with the ls -dZ /var/www/html/ command. Using the --preserve=context option preserves SELinux contexts during copy operations. As shown with the ls -Z /var/www/html/file1 command, the file1 user_home_t type was preserved when the file was copied to /var/www/html/.
Copying and Changing the Context
cp -Z command to change the destination copy's context. The following example was performed in the user's home directory:
-Z option. Without the -Z option, file2 would be labeled with the unconfined_u:object_r:user_home_t context.
Copying a File Over an Existing File
/etc/file1, labeled with the etc_t type, and /tmp/file2, labeled with the user_tmp_t type. The cp /tmp/file2 /etc/file1 command overwrites file1 with file2. After copying, the ls -Z /etc/file1 command shows file1 labeled with the etc_t type, not the user_tmp_t type from /tmp/file2 that replaced /etc/file1.
Important
5.9.2. Moving Files and Directories
/var/www/html/, which is used by the Apache HTTP Server. Since the file is moved, it does not inherit the correct SELinux context:
- Run the
cdcommand without any arguments to change into your home directory. Once in your home directory, run thetouch file1command to create a file. This file is labeled with theuser_home_ttype:ls -Z file1 -rw-rw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
~]$ ls -Z file1 -rw-rw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the
ls -dZ /var/www/html/command to view the SELinux context of the/var/www/html/directory:ls -dZ /var/www/html/ drwxr-xr-x root root system_u:object_r:httpd_sys_content_t:s0 /var/www/html/
~]$ ls -dZ /var/www/html/ drwxr-xr-x root root system_u:object_r:httpd_sys_content_t:s0 /var/www/html/Copy to Clipboard Copied! Toggle word wrap Toggle overflow By default, the/var/www/html/directory is labeled with thehttpd_sys_content_ttype. Files and directories created under the/var/www/html/directory inherit this type, and as such, they are labeled with this type. - As the Linux root user, run the
mv file1 /var/www/html/command to movefile1to the/var/www/html/directory. Since this file is moved, it keeps its currentuser_home_ttype:mv file1 /var/www/html/ ls -Z /var/www/html/file1 -rw-rw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 /var/www/html/file1
~]# mv file1 /var/www/html/ ~]# ls -Z /var/www/html/file1 -rw-rw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 /var/www/html/file1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
user_home_t type. If all files comprising a web page are labeled with the user_home_t type, or another type that the Apache HTTP Server cannot read, permission is denied when attempting to access them via web browsers, such as Firefox.
Important
mv command may result in the incorrect SELinux context, preventing processes, such as the Apache HTTP Server and Samba, from accessing such files and directories.
5.9.3. Checking the Default SELinux Context
matchpathcon command to check if files and directories have the correct SELinux context. From the matchpathcon(8) manual page: "matchpathcon queries the system policy and outputs the default security context associated with the file path."[10]. The following example demonstrates using the matchpathcon command to verify that files in /var/www/html/ directory are labeled correctly:
- As the Linux root user, run the
touch /var/www/html/file{1,2,3}command to create three files (file1,file2, andfile3). These files inherit thehttpd_sys_content_ttype from the/var/www/html/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
chcon -t samba_share_t /var/www/html/file1command to change thefile1type tosamba_share_t. Note that the Apache HTTP Server cannot read files or directories labeled with thesamba_share_ttype. - The
matchpathcon-Voption compares the current SELinux context to the correct, default context in SELinux policy. Run thematchpathcon -V /var/www/html/*command to check all files in the/var/www/html/directory:matchpathcon -V /var/www/html/* /var/www/html/file1 has context unconfined_u:object_r:samba_share_t:s0, should be system_u:object_r:httpd_sys_content_t:s0 /var/www/html/file2 verified. /var/www/html/file3 verified.
~]$ matchpathcon -V /var/www/html/* /var/www/html/file1 has context unconfined_u:object_r:samba_share_t:s0, should be system_u:object_r:httpd_sys_content_t:s0 /var/www/html/file2 verified. /var/www/html/file3 verified.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
matchpathcon command explains that file1 is labeled with the samba_share_t type, but should be labeled with the httpd_sys_content_t type:
/var/www/html/file1 has context unconfined_u:object_r:samba_share_t:s0, should be system_u:object_r:httpd_sys_content_t:s0
/var/www/html/file1 has context unconfined_u:object_r:samba_share_t:s0, should be system_u:object_r:httpd_sys_content_t:s0
file1, as the Linux root user, run the restorecon -v /var/www/html/file1 command:
restorecon -v /var/www/html/file1 restorecon reset /var/www/html/file1 context unconfined_u:object_r:samba_share_t:s0->system_u:object_r:httpd_sys_content_t:s0
~]# restorecon -v /var/www/html/file1
restorecon reset /var/www/html/file1 context unconfined_u:object_r:samba_share_t:s0->system_u:object_r:httpd_sys_content_t:s0
5.9.4. Archiving Files with tar
tar utility does not retain extended attributes by default. Since SELinux contexts are stored in extended attributes, contexts can be lost when archiving files. Use the tar --selinux command to create archives that retain contexts and to restore files from the archives. If a tar archive contains files without extended attributes, or if you want the extended attributes to match the system defaults, use the restorecon utility:
tar -xvf archive.tar | restorecon -f -
~]$ tar -xvf archive.tar | restorecon -f -restorecon.
tar archive that retains SELinux contexts:
Procedure 5.10. Creating a tar Archive
- Change to the
/var/www/html/directory and view its SELinux context:cd /var/www/html/
~]$ cd /var/www/html/Copy to Clipboard Copied! Toggle word wrap Toggle overflow html]$ ls -dZ /var/www/html/ drwxr-xr-x. root root system_u:object_r:httpd_sys_content_t:s0 .
html]$ ls -dZ /var/www/html/ drwxr-xr-x. root root system_u:object_r:httpd_sys_content_t:s0 .Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As root, create three files (
file1,file2, andfile3) in/var/www/html/. These files inherit thehttpd_sys_content_ttype from/var/www/html/:html]# touch file{1,2,3}html]# touch file{1,2,3}Copy to Clipboard Copied! Toggle word wrap Toggle overflow html]$ ls -Z /var/www/html/ -rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 file1 -rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 file2 -rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 file3
html]$ ls -Z /var/www/html/ -rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 file1 -rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 file2 -rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 file3Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As root, run the following command to create a
tararchive namedtest.tar. Use the--selinuxto retain the SELinux context:html]# tar --selinux -cf test.tar file{1,2,3}html]# tar --selinux -cf test.tar file{1,2,3}Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As root, create a new directory named
/test/, and then allow all users full access to it:mkdir /test
~]# mkdir /testCopy to Clipboard Copied! Toggle word wrap Toggle overflow chmod 777 /test/
~]# chmod 777 /test/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the
test.tarfile into/test/:cp /var/www/html/test.tar /test/
~]$ cp /var/www/html/test.tar /test/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Change into
/test/directory. Once in this directory, run the following command to extract thetararchive. Specify the--selinuxoption again otherwise the SELinux context will be changed todefault_t:cd /test/
~]$ cd /test/Copy to Clipboard Copied! Toggle word wrap Toggle overflow test]$ tar --selinux -xvf test.tar
test]$ tar --selinux -xvf test.tarCopy to Clipboard Copied! Toggle word wrap Toggle overflow - View the SELinux contexts. The
httpd_sys_content_ttype has been retained, rather than being changed todefault_t, which would have happened had the--selinuxnot been used:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If the
/test/directory is no longer required, as root, run the following command to remove it, as well as all files in it:rm -ri /test/
~]# rm -ri /test/Copy to Clipboard Copied! Toggle word wrap Toggle overflow
tar, such as the --xattrs option that retains all extended attributes.
5.9.5. Archiving Files with star
star utility does not retain extended attributes by default. Since SELinux contexts are stored in extended attributes, contexts can be lost when archiving files. Use the star -xattr -H=exustar command to create archives that retain contexts. The star package is not installed by default. To install star, run the yum install star command as the Linux root user.
- As the Linux root user, run the
touch /var/www/html/file{1,2,3}command to create three files (file1,file2, andfile3). These files inherit thehttpd_sys_content_ttype from the/var/www/html/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the
cd /var/www/html/command to change into the/var/www/html/directory. Once in this directory, as the Linux root user, run thestar -xattr -H=exustar -c -f=test.star file{1,2,3}command to create a Star archive namedtest.star:star -xattr -H=exustar -c -f=test.star file{1,2,3} star: 1 blocks + 0 bytes (total of 10240 bytes = 10.00k).~]# star -xattr -H=exustar -c -f=test.star file{1,2,3} star: 1 blocks + 0 bytes (total of 10240 bytes = 10.00k).Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
mkdir /testcommand to create a new directory, and then, run thechmod 777 /test/command to allow all users full-access to the/test/directory. - Run the
cp /var/www/html/test.star /test/command to copy thetest.starfile in to the/test/directory. - Run the
cd /test/command to change into the/test/directory. Once in this directory, run thestar -x -f=test.starcommand to extract the Star archive:star -x -f=test.star star: 1 blocks + 0 bytes (total of 10240 bytes = 10.00k).
~]$ star -x -f=test.star star: 1 blocks + 0 bytes (total of 10240 bytes = 10.00k).Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the
ls -lZ /test/command to view the SELinux contexts. Thehttpd_sys_content_ttype has been retained, rather than being changed todefault_t, which would have happened had the-xattr -H=exustaroption not been used:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If the
/test/directory is no longer required, as the Linux root user, run therm -ri /test/command to remove it, as well as all files in it. - If
staris no longer required, as the Linux root user, run theyum remove starcommand to remove the package.
star.
5.10. Information Gathering Tools
avcstat
/selinux/avc/cache_stats, and you can specify a different cache file with the -f /path/to/file option.
avcstat lookups hits misses allocs reclaims frees 47517410 47504630 12780 12780 12176 12275
~]# avcstat
lookups hits misses allocs reclaims frees
47517410 47504630 12780 12780 12176 12275
seinfo
seinfo is a command-line utility that uses a policy.conf file (a single text file containing policy source for versions 12 through 21), a binary policy file, a modular list of policy packages, or a policy list file as input. You must have the setools-console package installed to use the seinfo utility.
seinfo will vary between binary and source files. For example, the policy source file uses the { } brackets to group multiple rule elements onto a single line. A similar effect happens with attributes, where a single attribute expands into one or many types. Because these are expanded and no longer relevant in the binary policy file, they have a return value of zero in the search results. However, the number of rules greatly increases as each formerly one line rule using brackets is now a number of individual lines.
seinfo command can also list the number of types with the domain attribute, giving an estimate of the number of different confined processes:
seinfo -adomain -x | wc -l 550
~]# seinfo -adomain -x | wc -l
550seinfo -aunconfined_domain_type -x | wc -l 52
~]# seinfo -aunconfined_domain_type -x | wc -l
52
--permissive option.
seinfo --permissive -x | wc -l 31
~]# seinfo --permissive -x | wc -l
31
| wc -l option in the above commands to see the full lists.
sesearch
sesearch command to search for a particular type in the policy. You can search either policy source files or the binary file. For example:
sesearch command can provide the number of allow rules:
sesearch --allow | wc -l 262798
~]# sesearch --allow | wc -l
262798
sesearch --dontaudit | wc -l 156712
~]# sesearch --dontaudit | wc -l
156712
5.11. Multi-Level Security (MLS)
Figure 5.1. Levels of clearance
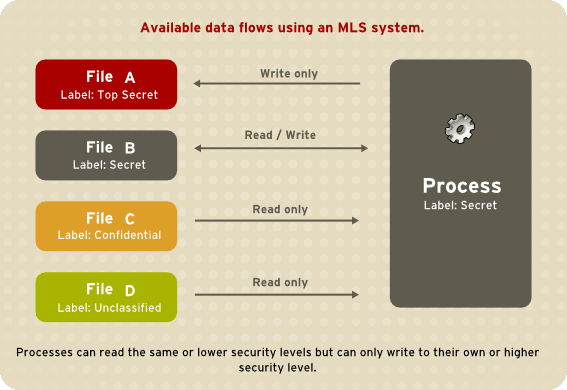
Figure 5.2. Allowed data flows using MLS
5.11.1. MLS and System Privileges
5.11.2. Enabling MLS in SELinux
Note
- Install the selinux-policy-mls package:
yum install selinux-policy-mls
~]# yum install selinux-policy-mlsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Before the MLS policy is enabled, each file on the file system must be relabeled with an MLS label. When the file system is relabeled, confined domains may be denied access, which may prevent your system from booting correctly. To prevent this from happening, configure
SELINUX=permissivein the/etc/selinux/configfile. Also, enable the MLS policy by configuringSELINUXTYPE=mls. Your configuration file should look like this:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Make sure SELinux is running in the permissive mode:
setenforce 0 getenforce Permissive
~]# setenforce 0 ~]# getenforce PermissiveCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Create the
.autorelabelfile in root's home directory to ensure that files are relabeled upon next reboot:touch /.autorelabel
~]# touch /.autorelabelCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot your system. During the next boot, all file systems will be relabeled according to the MLS policy. The label process labels all files with an appropriate SELinux context:
*** Warning -- SELinux mls policy relabel is required. *** Relabeling could take a very long time, depending on file *** system size and speed of hard drives. ***********
*** Warning -- SELinux mls policy relabel is required. *** Relabeling could take a very long time, depending on file *** system size and speed of hard drives. ***********Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each * (asterisk) character on the bottom line represents 1000 files that have been labeled. In the above example, eleven * characters represent 11000 files which have been labeled. The time it takes to label all files depends upon the number of files on the system, and the speed of the hard disk drives. On modern systems, this process can take as little as 10 minutes. Once the labeling process finishes, the system will automatically reboot. - In permissive mode, SELinux policy is not enforced, but denials are still logged for actions that would have been denied if running in enforcing mode. Before changing to enforcing mode, as the Linux root user, run the
grep "SELinux is preventing" /var/log/messagescommand to confirm that SELinux did not deny actions during the last boot. If SELinux did not deny actions during the last boot, this command does not return any output. Refer to Chapter 8, Troubleshooting for troubleshooting information if SELinux denied access during boot. - If there were no denial messages in
/var/log/messages, or you have resolved all existing denials, configureSELINUX=enforcingin the/etc/selinux/configfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot your system and make sure SELinux is running in enforcing mode:
getenforce Enforcing
~]$ getenforce EnforcingCopy to Clipboard Copied! Toggle word wrap Toggle overflow and the MLS policy is enabled:sestatus |grep mls Policy from config file: mls
~]# sestatus |grep mls Policy from config file: mlsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.11.3. Creating a User With a Specific MLS Range
- Add a new Linux user via the
useraddcommand and map the new Linux user to an existing SELinux user (in this case,user_u):useradd -Z user_u john
~]# useradd -Z user_u johnCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Assign the newly-created Linux user a password:
passwd john
~]# passwd johnCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the
semanage login -lcommand to view the mapping between SELinux and Linux users. The output should be as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Define a specific range for user
john:semanage login --modify --seuser user_u --range s2:c100 john
~]# semanage login --modify --seuser user_u --range s2:c100 johnCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the
semanage login -lcommand to view the mapping between SELinux and Linux users. Note that the userjohnnow has a specific MLS range defined:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To correct the label on john's home directory (if needed), run the following command:
chcon -R -l s2:c100 /home/john
~]# chcon -R -l s2:c100 /home/johnCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.11.4. Setting Up Polyinstantiated Directories
/tmp/ and /var/tmp/ directories are normally used for temporary storage by all programs, services, and users. Such setup, however, makes these directories vulnerable to race condition attacks, or an information leak based on file names. SELinux offers a solution in the form of polyinstantiated directories. This effectively means that both /tmp/ and /var/tmp/ are instantiated, making them appear private for each user. When instantiation of directories is enabled, each user's /tmp/ and /var/tmp/ directory is automatically mounted under /tmp-inst and /var/tmp/tmp-inst.
- Uncomment the last three lines in the
/etc/security/namespace.conffile to enable instantiation of the/tmp/,/var/tmp/, and users' home directories:tail -n 3 /etc/security/namespace.conf /tmp /tmp-inst/ level root,adm /var/tmp /var/tmp/tmp-inst/ level root,adm $HOME $HOME/$USER.inst/ level
~]$ tail -n 3 /etc/security/namespace.conf /tmp /tmp-inst/ level root,adm /var/tmp /var/tmp/tmp-inst/ level root,adm $HOME $HOME/$USER.inst/ levelCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Ensure that in the
/etc/pam.d/loginfile, thepam_namespace.somodule is configured for session:grep namespace /etc/pam.d/login session required pam_namespace.so
~]$ grep namespace /etc/pam.d/login session required pam_namespace.soCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot your system.
setsebool httpd_can_network_connect_db off command. For changes that persist across reboots, run the setsebool -P httpd_can_network_connect_db off command.
/etc/selinux/targeted/contexts/files/ directory define contexts for files and directories. Files in this directory are read by the restorecon and setfiles utilities to restore files and directories to their default contexts.
Chapter 6. Confining Users
su and sudo commands. This helps protect the system from the user. Refer to Section 4.3, “Confined and Unconfined Users” for further information about confined users.
6.1. Linux and SELinux User Mappings
semanage login -l command to view the mapping between Linux users and SELinux users:
__default__ login by default (which is in turn mapped to the SELinux unconfined_u user). When a Linux user is created with the useradd command, if no options are specified, they are mapped to the SELinux unconfined_u user. The following defines the default-mapping:
__default__ unconfined_u s0-s0:c0.c1023
__default__ unconfined_u s0-s0:c0.c1023
6.2. Confining New Linux Users: useradd
unconfined_u user run in the unconfined_t domain. This is seen by running the id -Z command while logged-in as a Linux user mapped to unconfined_u:
id -Z unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
~]$ id -Z
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
unconfined_t domain, SELinux policy rules are applied, but policy rules exist that allow Linux users running in the unconfined_t domain almost all access. If unconfined Linux users execute an application that SELinux policy defines can transition from the unconfined_t domain to its own confined domain, unconfined Linux users are still subject to the restrictions of that confined domain. The security benefit of this is that, even though a Linux user is running unconfined, the application remains confined, and therefore, the exploitation of a flaw in the application can be limited by policy.
Note
useradd command, use the -Z option to specify which SELinux user they are mapped to. The following example creates a new Linux user, useruuser, and maps that user to the SELinux user_u user. Linux users mapped to the SELinux user_u user run in the user_t domain. In this domain, Linux users are unable to run setuid applications unless SELinux policy permits it (such as passwd), and cannot run the su or sudo command, preventing them from becoming the Linux root user with these commands.
- As the Linux root user, run the
useradd -Z user_u useruusercommand to create a new Linux user (useruuser) that is mapped to the SELinuxuser_uuser. - As the Linux root user, run the
semanage login -lcommand to view the mapping between the Linuxuseruuseruser anduser_u:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
passwd useruusercommand to assign a password to the Linuxuseruuseruser:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Log out of your current session, and log in as the Linux
useruuseruser. When you log in, pam_selinux maps the Linux user to an SELinux user (in this case,user_u), and sets up the resulting SELinux context. The Linux user's shell is then launched with this context. Run theid -Zcommand to view the context of a Linux user:id -Z user_u:user_r:user_t:s0
~]$ id -Z user_u:user_r:user_t:s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Log out of the Linux
useruuser's session, and log back in with your account. If you do not want the Linuxuseruuseruser, run theuserdel -r useruusercommand as the Linux root user to remove it, along with its home directory.
6.3. Confining Existing Linux Users: semanage login
unconfined_u user (the default behavior), and you would like to change which SELinux user they are mapped to, use the semanage login command. The following example creates a new Linux user named newuser, then maps that Linux user to the SELinux user_u user:
- As the Linux root user, run the
useradd newusercommand to create a new Linux user (newuser). Since this user uses the default mapping, it does not appear in thesemanage login -loutput:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To map the Linux
newuseruser to the SELinuxuser_uuser, run the following command as the Linux root user:semanage login -a -s user_u newuser
~]# semanage login -a -s user_u newuserCopy to Clipboard Copied! Toggle word wrap Toggle overflow The-aoption adds a new record, and the-soption specifies the SELinux user to map a Linux user to. The last argument,newuser, is the Linux user you want mapped to the specified SELinux user. - To view the mapping between the Linux
newuseruser anduser_u, run thesemanage login -lcommand as the Linux root user:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As the Linux root user, run the
passwd newusercommand to assign a password to the Linuxnewuseruser:passwd newuser Changing password for user newuser. New password: Enter a password Retype new password: Enter the same password again passwd: all authentication tokens updated successfully.
~]# passwd newuser Changing password for user newuser. New password: Enter a password Retype new password: Enter the same password again passwd: all authentication tokens updated successfully.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Log out of your current session, and log in as the Linux
newuseruser. Run theid -Zcommand to view thenewuser's SELinux context:id -Z user_u:user_r:user_t:s0
~]$ id -Z user_u:user_r:user_t:s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Log out of the Linux
newuser's session, and log back in with your account. If you do not want the Linuxnewuseruser, run theuserdel -r newusercommand as the Linux root user to remove it, along with its home directory. Run thesemanage login -d newusercommand to remove the mapping between the Linuxnewuseruser anduser_u:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.4. Changing the Default Mapping
__default__ login by default (which is in turn mapped to the SELinux unconfined_u user). If you would like new Linux users, and Linux users not specifically mapped to an SELinux user to be confined by default, change the default mapping with the semanage login command.
unconfined_u to user_u:
semanage login -m -S targeted -s "user_u" -r s0 __default__
~]# semanage login -m -S targeted -s "user_u" -r s0 __default__semanage login -l command as the Linux root user to verify the __default__ login is mapped to user_u:
semanage login -l output, they are mapped to user_u, as per the __default__ login.
__default__ login to the SELinux unconfined_u user:
semanage login -m -S targeted -s "unconfined_u" -r s0-s0:c0.c1023 __default__
~]# semanage login -m -S targeted -s "unconfined_u" -r s0-s0:c0.c1023 __default__6.5. xguest: Kiosk Mode
- As the Linux root user, run the
yum install xguestcommand to install the xguest package. Install dependencies as required. - In order to allow the kiosk account to be used by a variety of people, the account is not password-protected, and as such, the account can only be protected if SELinux is running in enforcing mode. Before logging in with this account, use the
getenforcecommand to confirm that SELinux is running in enforcing mode:getenforce Enforcing
~]$ getenforce EnforcingCopy to Clipboard Copied! Toggle word wrap Toggle overflow If this is not the case, refer to Section 2.4, “SELinux States and Modes” for information about changing to enforcing mode. It is not possible to log in with this account if SELinux is in permissive mode or disabled. - You can only log in to this account via the GNOME Display Manager (GDM). Once the xguest package is installed, a
Guestaccount is added to the GDM login screen.
6.6. Booleans for Users Executing Applications
/tmp/, which they have write access to, helps prevent flawed or malicious applications from modifying files that users own. In Red Hat Enterprise Linux 6, by default, Linux users in the guest_t and xguest_t domains cannot execute applications in their home directories or /tmp/; however, by default, Linux users in the user_t and staff_t domains can.
setsebool command. The setsebool command must be run as the Linux root user. The setsebool -P command makes persistent changes. Do not use the -P option if you do not want changes to persist across reboots:
guest_t
guest_t domain to execute applications in their home directories and /tmp/:
setsebool -P allow_guest_exec_content on
~]# setsebool -P allow_guest_exec_content onxguest_t
xguest_t domain to execute applications in their home directories and /tmp/:
setsebool -P allow_xguest_exec_content on
~]# setsebool -P allow_xguest_exec_content onuser_t
user_t domain from executing applications in their home directories and /tmp/:
setsebool -P allow_user_exec_content off
~]# setsebool -P allow_user_exec_content offstaff_t
staff_t domain from executing applications in their home directories and /tmp/:
setsebool -P allow_staff_exec_content off
~]# setsebool -P allow_staff_exec_content offChapter 7. sVirt
Non-Virtualized Environment
Virtualized Environment
7.1. Security and Virtualization
7.2. sVirt Labeling
ps -eZ | grep qemu system_u:system_r:svirt_t:s0:c87,c520 27950 ? 00:00:17 qemu-kvm system_u:system_r:svirt_t:s0:c639,c757 27989 ? 00:00:06 qemu-system-x86
~]# ps -eZ | grep qemu
system_u:system_r:svirt_t:s0:c87,c520 27950 ? 00:00:17 qemu-kvm
system_u:system_r:svirt_t:s0:c639,c757 27989 ? 00:00:06 qemu-system-x86
ls -lZ /var/lib/libvirt/images/* system_u:object_r:svirt_image_t:s0:c87,c520 image1
~]# ls -lZ /var/lib/libvirt/images/*
system_u:object_r:svirt_image_t:s0:c87,c520 image1
| Type | SELinux Context | Description |
|---|---|---|
| Virtual Machine Processes | system_u:system_r:svirt_t:MCS1 | MCS1 is a randomly selected MCS field. Currently approximately 500,000 labels are supported. |
| Virtual Machine Image | system_u:object_r:svirt_image_t:MCS1 | Only processes labeled svirt_t with the same MCS fields are able to read/write these image files and devices. |
| Virtual Machine Shared Read/Write Content | system_u:object_r:svirt_image_t:s0 | All processes labeled svirt_t are allowed to write to the svirt_image_t:s0 files and devices. |
| Virtual Machine Image | system_u:object_r:virt_content_t:s0 | System default label used when an image exits. No svirt_t virtual processes are allowed to read files/devices with this label. |
Chapter 8. Troubleshooting
audit2allow.
8.1. What Happens when Access is Denied
| Daemon | Log Location |
|---|---|
| auditd on | /var/log/audit/audit.log |
| auditd off; rsyslogd on | /var/log/messages |
| setroubleshootd, rsyslogd, and auditd on | /var/log/audit/audit.log. Easier-to-read denial messages also sent to /var/log/messages |
setroubleshootd and auditd daemons are running, a warning is displayed when access is denied by SELinux:
Forbidden You don't have permission to access file name on this server
Forbidden
You don't have permission to access file name on this server
/var/log/messages and /var/log/audit/audit.log for "SELinux is preventing" and "denied" errors respectively. This can be done by running the following commands as the Linux root user:
grep "SELinux is preventing" /var/log/messages
~]# grep "SELinux is preventing" /var/log/messagesgrep "denied" /var/log/audit/audit.log
~]# grep "denied" /var/log/audit/audit.log8.2. Top Three Causes of Problems
8.2.1. Labeling Problems
/var/www/html/ for a website, an administrator wants to use /srv/myweb/. On Red Hat Enterprise Linux 6, the /srv/ directory is labeled with the var_t type. Files and directories created and /srv/ inherit this type. Also, newly-created top-level directories (such as /myserver/) may be labeled with the default_t type. SELinux prevents the Apache HTTP Server (httpd) from accessing both of these types. To allow access, SELinux must know that the files in /srv/myweb/ are to be accessible to httpd:
semanage fcontext -a -t httpd_sys_content_t "/srv/myweb(/.*)?"
~]# semanage fcontext -a -t httpd_sys_content_t "/srv/myweb(/.*)?"semanage command adds the context for the /srv/myweb/ directory (and all files and directories under it) to the SELinux file-context configuration[11]. The semanage command does not change the context. As the Linux root user, run the restorecon command to apply the changes:
restorecon -R -v /srv/myweb
~]# restorecon -R -v /srv/myweb8.2.1.1. What is the Correct Context?
matchpathcon command checks the context of a file path and compares it to the default label for that path. The following example demonstrates using matchpathcon on a directory that contains incorrectly labeled files:
matchpathcon -V /var/www/html/* /var/www/html/index.html has context unconfined_u:object_r:user_home_t:s0, should be system_u:object_r:httpd_sys_content_t:s0 /var/www/html/page1.html has context unconfined_u:object_r:user_home_t:s0, should be system_u:object_r:httpd_sys_content_t:s0
~]$ matchpathcon -V /var/www/html/*
/var/www/html/index.html has context unconfined_u:object_r:user_home_t:s0, should be system_u:object_r:httpd_sys_content_t:s0
/var/www/html/page1.html has context unconfined_u:object_r:user_home_t:s0, should be system_u:object_r:httpd_sys_content_t:s0
index.html and page1.html files are labeled with the user_home_t type. This type is used for files in user home directories. Using the mv command to move files from your home directory may result in files being labeled with the user_home_t type. This type should not exist outside of home directories. Use the restorecon command to restore such files to their correct type:
restorecon -v /var/www/html/index.html restorecon reset /var/www/html/index.html context unconfined_u:object_r:user_home_t:s0->system_u:object_r:httpd_sys_content_t:s0
~]# restorecon -v /var/www/html/index.html
restorecon reset /var/www/html/index.html context unconfined_u:object_r:user_home_t:s0->system_u:object_r:httpd_sys_content_t:s0
-R option:
restorecon -R -v /var/www/html/ restorecon reset /var/www/html/page1.html context unconfined_u:object_r:samba_share_t:s0->system_u:object_r:httpd_sys_content_t:s0 restorecon reset /var/www/html/index.html context unconfined_u:object_r:samba_share_t:s0->system_u:object_r:httpd_sys_content_t:s0
~]# restorecon -R -v /var/www/html/
restorecon reset /var/www/html/page1.html context unconfined_u:object_r:samba_share_t:s0->system_u:object_r:httpd_sys_content_t:s0
restorecon reset /var/www/html/index.html context unconfined_u:object_r:samba_share_t:s0->system_u:object_r:httpd_sys_content_t:s0
matchpathcon.
8.2.2. How are Confined Services Running?
semanage command.
httpd_can_network_connect_db Boolean:
setsebool -P httpd_can_network_connect_db on
~]# setsebool -P httpd_can_network_connect_db ongetsebool and grep commands to see if any Booleans are available to allow access. For example, use the getsebool -a | grep ftp command to search for FTP related Booleans:
getsebool -a command. For a list of Booleans, an explanation of what each one is, and whether they are on or off, run the semanage boolean -l command as the Linux root user. Refer to Section 5.5, “Booleans” for information about listing and configuring Booleans.
Port Numbers
semanage port -l | grep http command as the Linux root user to list http related ports:
http_port_t port type defines the ports Apache HTTP Server can listen on, which in this case, are TCP ports 80, 443, 488, 8008, 8009, and 8443. If an administrator configures httpd.conf so that httpd listens on port 9876 (Listen 9876), but policy is not updated to reflect this, the service httpd start command fails:
/var/log/audit/audit.log:
type=AVC msg=audit(1225948455.061:294): avc: denied { name_bind } for pid=4997 comm="httpd" src=9876 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=system_u:object_r:port_t:s0 tclass=tcp_socket
type=AVC msg=audit(1225948455.061:294): avc: denied { name_bind } for pid=4997 comm="httpd" src=9876 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=system_u:object_r:port_t:s0 tclass=tcp_socket
httpd to listen on a port that is not listed for the http_port_t port type, run the semanage port command to add a port to policy configuration[12]:
semanage port -a -t http_port_t -p tcp 9876
~]# semanage port -a -t http_port_t -p tcp 9876-a option adds a new record; the -t option defines a type; and the -p option defines a protocol. The last argument is the port number to add.
8.2.3. Evolving Rules and Broken Applications
audit2allow to create a custom policy module to allow access. Refer to Section 8.3.8, “Allowing Access: audit2allow” for information about using audit2allow.
8.3. Fixing Problems
audit2allow.
8.3.1. Linux Permissions
ls -l command to view the standard Linux permissions:
ls -l /var/www/html/index.html -rw-r----- 1 root root 0 2009-05-07 11:06 index.html
~]$ ls -l /var/www/html/index.html
-rw-r----- 1 root root 0 2009-05-07 11:06 index.html
index.html is owned by the root user and group. The root user has read and write permissions (-rw), and members of the root group have read permissions (-r-). Everyone else has no access (---). By default, such permissions do not allow httpd to read this file. To resolve this issue, use the chown command to change the owner and group. This command must be run as the Linux root user:
chown apache:apache /var/www/html/index.html
~]# chown apache:apache /var/www/html/index.htmlhttpd runs as the Linux apache user. If you run httpd with a different user, replace apache:apache with that user.
8.3.2. Possible Causes of Silent Denials
dontaudit rules. These rules are common in standard policy. The downside of dontaudit is that, although SELinux denies access, denial messages are not logged, making troubleshooting more difficult.
dontaudit rules, allowing all denials to be logged, run the following command as the Linux root user:
semodule -DB
~]# semodule -DB-D option disables dontaudit rules; the -B option rebuilds policy. After running semodule -DB, try exercising the application that was encountering permission problems, and see if SELinux denials — relevant to the application — are now being logged. Take care in deciding which denials should be allowed, as some should be ignored and handled via dontaudit rules. If in doubt, or in search of guidance, contact other SELinux users and developers on an SELinux list, such as fedora-selinux-list.
dontaudit rules, run the following command as the Linux root user:
semodule -B
~]# semodule -Bdontaudit rules, run the sesearch --dontaudit command. Narrow down searches using the -s domain option and the grep command. For example:
sesearch --dontaudit -s smbd_t | grep squid dontaudit smbd_t squid_port_t : tcp_socket name_bind ; dontaudit smbd_t squid_port_t : udp_socket name_bind ;
~]$ sesearch --dontaudit -s smbd_t | grep squid
dontaudit smbd_t squid_port_t : tcp_socket name_bind ;
dontaudit smbd_t squid_port_t : udp_socket name_bind ;
8.3.3. Manual Pages for Services
httpd accessing NFS volumes). This information may be in the standard manual page, or a manual page with selinux prepended or appended.
- Samba: the samba_selinux(8) manual page describes that files and directories to be exported via Samba must be labeled with the
samba_share_ttype, as well as Booleans to allow files labeled with types other thansamba_share_tto be exported via Samba. - Berkeley Internet Name Domain (BIND): the named(8) manual page describes what file type to use for a given situation (see the
Red Hat SELinux BIND Security Profilesection). The named_selinux(8) manual page describes that, by default,namedcannot write to master zone files, and to allow such access, thenamed_write_master_zonesBoolean must be enabled.
8.3.4. Permissive Domains
- They can be used for making a single process (domain) run permissive to troubleshoot an issue without putting the entire system at risk by making it permissive.
- They allow an administrator to create policies for new applications. Previously, it was recommended that a minimal policy be created, and then the entire machine put into permissive mode, so that the application could run, but SELinux denials still logged.
audit2allowcould then be used to help write the policy. This put the whole system at risk. With permissive domains, only the domain in the new policy can be marked permissive, without putting the whole system at risk.
8.3.4.1. Making a Domain Permissive
semanage permissive -a domain command, where domain is the domain you want to make permissive. For example, run the following command as the Linux root user to make the httpd_t domain (the domain the Apache HTTP Server runs in) permissive:
semanage permissive -a httpd_t
~]# semanage permissive -a httpd_tsemodule -l | grep permissive command as the Linux root user. For example:
semodule -l | grep permissive permissive_httpd_t 1.0 permissivedomains 1.0.0
~]# semodule -l | grep permissive
permissive_httpd_t 1.0
permissivedomains 1.0.0
semanage permissive -d domain command as the Linux root user. For example:
semanage permissive -d httpd_t
~]# semanage permissive -d httpd_t8.3.4.2. Denials for Permissive Domains
SYSCALL message is different for permissive domains. The following is an example AVC denial (and the associated system call) from the Apache HTTP Server:
type=AVC msg=audit(1226882736.442:86): avc: denied { getattr } for pid=2427 comm="httpd" path="/var/www/html/file1" dev=dm-0 ino=284133 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=unconfined_u:object_r:samba_share_t:s0 tclass=file
type=SYSCALL msg=audit(1226882736.442:86): arch=40000003 syscall=196 success=no exit=-13 a0=b9a1e198 a1=bfc2921c a2=54dff4 a3=2008171 items=0 ppid=2425 pid=2427 auid=502 uid=48 gid=48 euid=48 suid=48 fsuid=48 egid=48 sgid=48 fsgid=48 tty=(none) ses=4 comm="httpd" exe="/usr/sbin/httpd" subj=unconfined_u:system_r:httpd_t:s0 key=(null)
type=AVC msg=audit(1226882736.442:86): avc: denied { getattr } for pid=2427 comm="httpd" path="/var/www/html/file1" dev=dm-0 ino=284133 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=unconfined_u:object_r:samba_share_t:s0 tclass=file
type=SYSCALL msg=audit(1226882736.442:86): arch=40000003 syscall=196 success=no exit=-13 a0=b9a1e198 a1=bfc2921c a2=54dff4 a3=2008171 items=0 ppid=2425 pid=2427 auid=502 uid=48 gid=48 euid=48 suid=48 fsuid=48 egid=48 sgid=48 fsgid=48 tty=(none) ses=4 comm="httpd" exe="/usr/sbin/httpd" subj=unconfined_u:system_r:httpd_t:s0 key=(null)
httpd_t domain is not permissive, and as such, the action is denied, and the SYSCALL message contains success=no. The following is an example AVC denial for the same situation, except the semanage permissive -a httpd_t command has been run to make the httpd_t domain permissive:
type=AVC msg=audit(1226882925.714:136): avc: denied { read } for pid=2512 comm="httpd" name="file1" dev=dm-0 ino=284133 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=unconfined_u:object_r:samba_share_t:s0 tclass=file
type=SYSCALL msg=audit(1226882925.714:136): arch=40000003 syscall=5 success=yes exit=11 a0=b962a1e8 a1=8000 a2=0 a3=8000 items=0 ppid=2511 pid=2512 auid=502 uid=48 gid=48 euid=48 suid=48 fsuid=48 egid=48 sgid=48 fsgid=48 tty=(none) ses=4 comm="httpd" exe="/usr/sbin/httpd" subj=unconfined_u:system_r:httpd_t:s0 key=(null)
type=AVC msg=audit(1226882925.714:136): avc: denied { read } for pid=2512 comm="httpd" name="file1" dev=dm-0 ino=284133 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=unconfined_u:object_r:samba_share_t:s0 tclass=file
type=SYSCALL msg=audit(1226882925.714:136): arch=40000003 syscall=5 success=yes exit=11 a0=b962a1e8 a1=8000 a2=0 a3=8000 items=0 ppid=2511 pid=2512 auid=502 uid=48 gid=48 euid=48 suid=48 fsuid=48 egid=48 sgid=48 fsgid=48 tty=(none) ses=4 comm="httpd" exe="/usr/sbin/httpd" subj=unconfined_u:system_r:httpd_t:s0 key=(null)
success=yes in the SYSCALL message.
8.3.5. Searching For and Viewing Denials
auditd, rsyslogd, and setroubleshootd daemons are running. Refer to Section 5.2, “Which Log File is Used” for information about starting these daemons. A number of tools are available for searching for and viewing SELinux denials, such as ausearch, aureport, and sealert.
ausearch
ausearch utility. From the ausearch(8) manual page: "ausearch is a tool that can query the audit daemon logs for events based on different search criteria"[13]. The ausearch utility accesses /var/log/audit/audit.log, and as such, must be run as the Linux root user:
| Searching For | Command |
|---|---|
| all denials | ausearch -m avc |
| denials for that today | ausearch -m avc -ts today |
| denials from the last 10 minutes | ausearch -m avc -ts recent |
-c comm-name option, where comm-name "is the executable’s name"[14], for example, httpd for the Apache HTTP Server, and smbd for Samba:
ausearch -m avc -c httpd
~]# ausearch -m avc -c httpdausearch -m avc -c smbd
~]# ausearch -m avc -c smbdausearch command, it is advised to use either the --interpret (-i) option for easier readability, or the --raw (-r) option for script processing. Refer to the ausearch(8) manual page for further ausearch options.
aureport
aureport utility. From the aureport(8) manual page: "aureport is a tool that produces summary reports of the audit system logs"[15]. The aureport utility accesses /var/log/audit/audit.log, and as such, must be run as the Linux root user. To view a list of SELinux denials and how often each one occurred, run the aureport -a command. The following is example output that includes two denials:
aureport options.
sealert
sealert utility, which reads denial messages translated by setroubleshoot-server. Denials are assigned IDs, as seen in /var/log/messages. The following is an example denial from messages:
setroubleshoot: SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket. For complete SELinux messages. run sealert -l 8c123656-5dda-4e5d-8791-9e3bd03786b7
setroubleshoot: SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket. For complete SELinux messages. run sealert -l 8c123656-5dda-4e5d-8791-9e3bd03786b7
8c123656-5dda-4e5d-8791-9e3bd03786b7. The -l option takes an ID as an argument. Running the sealert -l 8c123656-5dda-4e5d-8791-9e3bd03786b7 command presents a detailed analysis of why SELinux denied access, and a possible solution for allowing access.
setroubleshootd, dbus and auditd daemons are running, a warning is displayed when access is denied by SELinux:
Show launches the sealert GUI, which allows you to troubleshoot the problem:
sealert -b command to launch the sealert GUI. To view a detailed analysis of all denial messages, run the sealert -l \* command.
sealert options.
8.3.6. Raw Audit Messages
/var/log/audit/audit.log. The following is an example AVC denial (and the associated system call) that occurred when the Apache HTTP Server (running in the httpd_t domain) attempted to access the /var/www/html/file1 file (labeled with the samba_share_t type):
type=AVC msg=audit(1226874073.147:96): avc: denied { getattr } for pid=2465 comm="httpd" path="/var/www/html/file1" dev=dm-0 ino=284133 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=unconfined_u:object_r:samba_share_t:s0 tclass=file
type=SYSCALL msg=audit(1226874073.147:96): arch=40000003 syscall=196 success=no exit=-13 a0=b98df198 a1=bfec85dc a2=54dff4 a3=2008171 items=0 ppid=2463 pid=2465 auid=502 uid=48 gid=48 euid=48 suid=48 fsuid=48 egid=48 sgid=48 fsgid=48 tty=(none) ses=6 comm="httpd" exe="/usr/sbin/httpd" subj=unconfined_u:system_r:httpd_t:s0 key=(null)
type=AVC msg=audit(1226874073.147:96): avc: denied { getattr } for pid=2465 comm="httpd" path="/var/www/html/file1" dev=dm-0 ino=284133 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=unconfined_u:object_r:samba_share_t:s0 tclass=file
type=SYSCALL msg=audit(1226874073.147:96): arch=40000003 syscall=196 success=no exit=-13 a0=b98df198 a1=bfec85dc a2=54dff4 a3=2008171 items=0 ppid=2463 pid=2465 auid=502 uid=48 gid=48 euid=48 suid=48 fsuid=48 egid=48 sgid=48 fsgid=48 tty=(none) ses=6 comm="httpd" exe="/usr/sbin/httpd" subj=unconfined_u:system_r:httpd_t:s0 key=(null)
- { getattr }
- The item in the curly brackets indicates the permission that was denied. The
getattrentry indicates the source process was trying to read the target file's status information. This occurs before reading files. This action is denied due to the file being accessed having a wrong label. Commonly seen permissions includegetattr,read, andwrite. - comm="httpd"
- The executable that launched the process. The full path of the executable is found in the
exe=section of the system call (SYSCALL) message, which in this case, isexe="/usr/sbin/httpd". - path="/var/www/html/file1"
- The path to the object (target) the process attempted to access.
- scontext="unconfined_u:system_r:httpd_t:s0"
- The SELinux context of the process that attempted the denied action. In this case, it is the SELinux context of the Apache HTTP Server, which is running in the
httpd_tdomain. - tcontext="unconfined_u:object_r:samba_share_t:s0"
- The SELinux context of the object (target) the process attempted to access. In this case, it is the SELinux context of
file1. Note that thesamba_share_ttype is not accessible to processes running in thehttpd_tdomain.In certain situations, thetcontextmay match thescontext, for example, when a process attempts to execute a system service that will change characteristics of that running process, such as the user ID. Also, thetcontextmay match thescontextwhen a process tries to use more resources (such as memory) than normal limits allow, resulting in a security check to see if that process is allowed to break those limits.
SYSCALL) message, two items are of interest:
success=no: indicates whether the denial (AVC) was enforced or not.success=noindicates the system call was not successful (SELinux denied access).success=yesindicates the system call was successful. This can be seen for permissive domains or unconfined domains, such asinitrc_tandkernel_t.exe="/usr/sbin/httpd": the full path to the executable that launched the process, which in this case, isexe="/usr/sbin/httpd".
scontext) with the target context (tcontext). Should the process (scontext) be accessing such an object (tcontext)? For example, the Apache HTTP Server (httpd_t) should only be accessing types specified in the httpd_selinux(8) manual page, such as httpd_sys_content_t, public_content_t, and so on, unless configured otherwise.
8.3.7. sealert Messages
/var/log/messages. The following is an example AVC denial (logged to messages) that occurred when the Apache HTTP Server (running in the httpd_t domain) attempted to access the /var/www/html/file1 file (labeled with the samba_share_t type):
hostname setroubleshoot: SELinux is preventing httpd (httpd_t) "getattr" to /var/www/html/file1 (samba_share_t). For complete SELinux messages. run sealert -l 84e0b04d-d0ad-4347-8317-22e74f6cd020
hostname setroubleshoot: SELinux is preventing httpd (httpd_t) "getattr" to /var/www/html/file1 (samba_share_t). For complete SELinux messages. run sealert -l 84e0b04d-d0ad-4347-8317-22e74f6cd020
sealert -l 84e0b04d-d0ad-4347-8317-22e74f6cd020 command to view the complete message. This command only works on the local machine, and presents the same information as the sealert GUI:
- Summary
- A brief summary of the denied action. This is the same as the denial in
/var/log/messages. In this example, thehttpdprocess was denied access to a file (file1), which is labeled with thesamba_share_ttype. - Detailed Description
- A more verbose description. In this example,
file1is labeled with thesamba_share_ttype. This type is used for files and directories that you want to export via Samba. The description suggests changing the type to a type that can be accessed by the Apache HTTP Server and Samba, if such access is desired. - Allowing Access
- A suggestion for how to allow access. This may be relabeling files, enabling a Boolean, or making a local policy module. In this case, the suggestion is to label the file with a type accessible to both the Apache HTTP Server and Samba.
- Fix Command
- A suggested command to allow access and resolve the denial. In this example, it gives the command to change the
file1type topublic_content_t, which is accessible to the Apache HTTP Server and Samba. - Additional Information
- Information that is useful in bug reports, such as the policy package name and version (
selinux-policy-3.5.13-11.fc12), but may not help towards solving why the denial occurred. - Raw Audit Messages
- The raw audit messages from
/var/log/audit/audit.logthat are associated with the denial. Refer to Section 8.3.6, “Raw Audit Messages” for information about each item in the AVC denial.
8.3.8. Allowing Access: audit2allow
audit2allow utility.
audit2allow – generate SELinux policy allow rules from logs of denied operations"[16]. After analyzing denials as per Section 8.3.7, “sealert Messages”, and if no label changes or Booleans allowed access, use audit2allow to create a local policy module. After access is denied by SELinux, running the audit2allow command presents Type Enforcement rules that allow the previously denied access.
audit2allow to create a policy module:
- A denial and the associated system call are logged to
/var/log/audit/audit.log:type=AVC msg=audit(1226270358.848:238): avc: denied { write } for pid=13349 comm="certwatch" name="cache" dev=dm-0 ino=218171 scontext=system_u:system_r:certwatch_t:s0 tcontext=system_u:object_r:var_t:s0 tclass=dir type=SYSCALL msg=audit(1226270358.848:238): arch=40000003 syscall=39 success=no exit=-13 a0=39a2bf a1=3ff a2=3a0354 a3=94703c8 items=0 ppid=13344 pid=13349 auid=4294967295 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=(none) ses=4294967295 comm="certwatch" exe="/usr/bin/certwatch" subj=system_u:system_r:certwatch_t:s0 key=(null)type=AVC msg=audit(1226270358.848:238): avc: denied { write } for pid=13349 comm="certwatch" name="cache" dev=dm-0 ino=218171 scontext=system_u:system_r:certwatch_t:s0 tcontext=system_u:object_r:var_t:s0 tclass=dir type=SYSCALL msg=audit(1226270358.848:238): arch=40000003 syscall=39 success=no exit=-13 a0=39a2bf a1=3ff a2=3a0354 a3=94703c8 items=0 ppid=13344 pid=13349 auid=4294967295 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=(none) ses=4294967295 comm="certwatch" exe="/usr/bin/certwatch" subj=system_u:system_r:certwatch_t:s0 key=(null)Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, certwatch (comm="certwatch") was denied write access ({ write }) to a directory labeled with thevar_ttype (tcontext=system_u:object_r:var_t:s0). Analyze the denial as per Section 8.3.7, “sealert Messages”. If no label changes or Booleans allowed access, useaudit2allowto create a local policy module. - With a denial logged, such as the
certwatchdenial in step 1, run theaudit2allow -w -acommand to produce a human-readable description of why access was denied. The-aoption causes all audit logs to be read. The-woption produces the human-readable description. Theaudit2allowutility accesses/var/log/audit/audit.log, and as such, must be run as the Linux root user:Copy to Clipboard Copied! Toggle word wrap Toggle overflow As shown, access was denied due to a missing Type Enforcement rule. - Run the
audit2allow -acommand to view the Type Enforcement rule that allows the denied access:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Important
Missing Type Enforcement rules are usually caused by bugs in SELinux policy, and should be reported in Red Hat Bugzilla. For Red Hat Enterprise Linux, create bugs against theRed Hat Enterprise Linuxproduct, and select theselinux-policycomponent. Include the output of theaudit2allow -w -aandaudit2allow -acommands in such bug reports. - To use the rule displayed by
audit2allow -a, run theaudit2allow -a -M mycertwatchcommand as the Linux root user to create custom module. The-Moption creates a Type Enforcement file (.te) with the name specified with-M, in your current working directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Also,audit2allowcompiles the Type Enforcement rule into a policy package (.pp). To install the module, run thesemodule -i mycertwatch.ppcommand as the Linux root user.Important
Modules created withaudit2allowmay allow more access than required. It is recommended that policy created withaudit2allowbe posted to an SELinux list, such as fedora-selinux-list, for review. If you believe their is a bug in policy, create a bug in Red Hat Bugzilla.
grep command to narrow down the input for audit2allow. The following example demonstrates using grep to only send denials related to certwatch through audit2allow:
grep certwatch /var/log/audit/audit.log | audit2allow -M mycertwatch2 ******************** IMPORTANT *********************** To make this policy package active, execute: semodule -i mycertwatch2.pp
~]# grep certwatch /var/log/audit/audit.log | audit2allow -M mycertwatch2
******************** IMPORTANT ***********************
To make this policy package active, execute:
~]# semodule -i mycertwatch2.ppaudit2allow to build policy modules.
/etc/selinux/targeted/contexts/files/ define contexts for files and directories. Files in this directory are read by the restorecon and setfiles commands to restore files and directories to their default contexts.
semanage port -a command adds an entry to the /etc/selinux/targeted/modules/active/ports.local file. Note that by default, this file can only be viewed by the Linux root user.
Chapter 9. Further Information
9.1. Contributors
- Domingo Becker – Translation – Spanish
- Dominick Grift – Technical Editor
- Daniel Cabrera – Translation – Spanish
- Murray McAllister – Red Hat Customer Content Services
- James Morris – Technical Editor
- Eric Paris – Technical Editor
- Scott Radvan – Red Hat Customer Content Services
- Daniel Walsh – Red Hat Security Engineering
- Geert Warrink – Translation – Dutch
9.2. Other Resources
The National Security Agency (NSA)
- Main SELinux website: http://www.nsa.gov/research/selinux/index.shtml.
- SELinux documentation: http://www.nsa.gov/research/selinux/docs.shtml.
- SELinux background: http://www.nsa.gov/research/selinux/background.shtml.
Tresys Technology
SELinux Project Wiki
- Main page: http://selinuxproject.org/page/Main_Page.
- User resources, including links to documentation, mailing lists, websites, and tools: http://selinuxproject.org/page/User_Resources.
Fedora
- Main page: http://fedoraproject.org/wiki/SELinux.
- Troubleshooting: http://fedoraproject.org/wiki/SELinux/Troubleshooting.
- Fedora SELinux FAQ: http://docs.fedoraproject.org/.
- SELinux Managing Confined Services Guide: http://docs.fedoraproject.org/
The UnOfficial SELinux FAQ
IRC
- #selinux
- #fedora-selinux
- #security
Appendix A. Revision History
| Revision History | |||
|---|---|---|---|
| Revision 9-2 | Wed Mar 15 2017 | ||
| |||
| Revision 9-1 | Tue Jan 3 2017 | ||
| |||
| Revision 7-4 | Wed May 3 2016 | ||
| |||
| Revision 7-1 | Thu Jul 9 2015 | ||
| |||
| Revision 6-0 | Fri Oct 10 2014 | ||
| |||
| Revision 5-0 | Fri Sep 12 2014 | ||
| |||
| Revision 4-0 | Feb Fri 22 2013 | ||
| |||
| Revision 3-0 | Wed Jun 20 2012 | ||
| |||
| Revision 2-0 | Tue Dec 6 2011 | ||
| |||
| Revision 1.9-0 | Wed Mar 3 2010 | ||
| |||