Recording sessions
Using the Session Recording solution in Red Hat Enterprise Linux 8
Abstract
Providing feedback on Red Hat documentation
We appreciate your feedback on our documentation. Let us know how we can improve it.
Submitting feedback through Jira (account required)
- Log in to the Jira website.
- Click Create in the top navigation bar.
- Enter a descriptive title in the Summary field.
- Enter your suggestion for improvement in the Description field. Include links to the relevant parts of the documentation.
- Click Create at the bottom of the dialogue.
Chapter 1. Getting started with Session Recording on RHEL
1.1. Session Recording in RHEL
The Session Recording solution in Red Hat Enterprise Linux 8 is based on the tlog package. You can use the tlog package and its associated web console session player to record and play back user terminal sessions. You can configure the recording to take place per user or user group via the SSSD service. All terminal input and output is captured and stored in a text-based format in the system journal.
To not intercept raw passwords and other sensitive information, recording of the terminal input is disabled by default. Be aware that if you turn on recording of the terminal input, all entered passwords are captured in plaintext.
You can use this solution for auditing user sessions on security-sensitive systems or, in the event of a security breach, reviewing recorded sessions as part of forensic analysis. As an administrator, you can configure session recording locally on RHEL 8 systems. You can review the recorded sessions from the web console interface or in a terminal using the tlog-play command.
1.2. Components of Session Recording
There are three main components to the Session Recording solution: the tlog utility, the SSSD service and a web console embedded user interface.
- tlog
-
The
tlogutility is a terminal input/output (I/O) recording and playback program. It inserts thetlog-rec-sessiontool between the user terminal and the user shell, and logs everything that passes through as JSON messages. - SSSD
- The System Security Services Daemon (SSSD) service provides a set of daemons to manage access to remote directories and authentication mechanisms. When configuring session recording, you can use SSSD to specify which users or user groups to record. You can configure these settings from the command line (CLI) or from the RHEL 8 web console interface.
- The RHEL 8 web console embedded interface
- The Session Recording page is part of the RHEL 8 web console interface and you can use it to manage recorded sessions.
You need administrator privileges to access the recorded sessions.
1.3. Limitations of Session Recording
These are the most notable limitations of the Session Recording solution.
- Recordings of root user are not reliable, because the root user can circumvent the recording process.
-
Session recording does not record the terminal in a
GNOME 3graphical session. Recording terminals in graphical sessions is not supported because a graphical session has a single audit session ID for all terminals andtlogis unable to distinguish between the terminals and prevent repeated recordings. If session recording is configured to log to the
journal, the recorded user will see the act of recording the results of viewing the system journal or/var/log/messages. Because viewing generates logs, which then print to the screen, this causes Session Recording to record this action, which generates more records, causing a loop of flooded output.You can use the following command to work around this problem:
journalctl -f | grep -v 'tlog-rec-session'
# journalctl -f | grep -v 'tlog-rec-session'Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can also configure tlog to limit the output. For details, see
tlog-recortlog-rec-sessionmanual pages.To record users executing remote access commands, you must configure session recording for that user on the target host. For example, to record the following remote access command, you need to configure session recording for the
adminuser on theclienthost:ssh admin@client rm -f /some/file
ssh admin@client rm -f /some/fileCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
All recordings are lost on reboot because the
journalis stored in-memory by default on RHEL 8. To export recordings see Exporting recorded sessions to a file.
Chapter 2. Deploying Session Recording on RHEL web console
This section describes how to deploy the Session Recording solution on the Red Hat Enterprise Linux web console.
To be able to deploy the Session Recording solution you need to have the following packages installed:
-
tlog - SSSD
-
cockpit-session-recording
2.1. Installing tlog
Install the tlog packages.
Procedure
Use the following command:
yum install tlog
# yum install tlogCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.2. Installing cockpit-session-recording
The basic web console packages are a part of Red Hat Enterprise Linux 8 by default. To be able to use the Session Recording solution, you have to install the cockpit-session-recording packages and start or enable the web console on your system:
Procedure
Install
cockpit-session-recording.yum install cockpit-session-recording
# yum install cockpit-session-recordingCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start or enable the web console on your system:
systemctl start cockpit.socket systemctl enable cockpit.socket
# systemctl start cockpit.socket # systemctl enable cockpit.socketCopy to Clipboard Copied! Toggle word wrap Toggle overflow or
systemctl enable cockpit.socket --now
# systemctl enable cockpit.socket --nowCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.3. Enabling session recording for users and groups with SSSD from the CLI
If you use SSSD for authentication, you can configure session recording for users and groups from the command line.
Procedure
Open the
sssd-session-recording.confconfiguration file:vi /etc/sssd/conf.d/sssd-session-recording.conf
# vi /etc/sssd/conf.d/sssd-session-recording.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe
sssd-session-recording.conffile is created automatically once you have opened the configuration page in the web console interface.To specify the scope of session recording, enter one of the following values for the scope option:
-
noneto record no sessions. -
someto record only specified sessions. -
allto record all sessions.
-
-
Optional: If you set the scope as
someadd the names of users and groups in comma-separated lists. To enable the SSSD profile, run the following command:
authselect select sssd with-files-domain
# authselect select sssd with-files-domainCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Example 2.1. SSSD configuration
In the following example users example1 and example2, and group examples have session recording enabled.
[session_recording] scope = some users = example1, example2 groups = examples
[session_recording]
scope = some
users = example1, example2
groups = examples2.4. Enabling session recording for users and groups with SSSD from the web UI
If you use SSSD for authentication, you can configure session recording for users and groups in the RHEL 8 web console.
Procedure
-
Connect to the RHEL 8 web console locally by entering
localhost:9090or by entering your IP address<IP_ADDRESS>:9090into your browser. Log in to the RHEL 8 web console.
ImportantYour user has to have administrator privileges to be able to view recorded sessions.
- Go to the Session Recording page in the menu on the left.
Click on the gear button in the right top corner.

Set your parameters in the SSSD Configuration table. Separate the lists of users and groups with commas.
Example 2.2. Configuration of recorded users with SSSD

2.5. Enabling session recording for users without SSSD
Red Hat recommends configuring your recorded users using SSSD, either from the command line or directly from the RHEL 8 web console.
Without SSSD, there is no centralized management for policies. Administrators must set the shell for each user on every system individually, which makes it difficult to scale across multiple systems. Group-based configurations or exclusions such as exclude_users and exclude_groups are also not available. Additionally, tools like Cockpit Session Recording are designed to work with SSSD and might not function as expected without it.
To enable session recording without SSSD, change the shell of the user you want to record to
/usr/bin/tlog-rec-session.sudo usermod -s /usr/bin/tlog-rec-session <user_name>
# sudo usermod -s /usr/bin/tlog-rec-session <user_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The system uses the configuration in the
tlog-rec-session.conffile to determine the user’s working shell.
2.6. Exporting recorded sessions to a file
You can export your recorded sessions and their logs and copy them.
The following procedure shows how to export recorded sessions on a local system.
Prerequisites
Install the
systemd-journal-remotepackage.yum install systemd-journal-remote
# yum install systemd-journal-remoteCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure
Create a directory to store exported recording sessions, such as `/tmp/dir:
mkdir /tmp/dir
# mkdir /tmp/dirCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the
journalctl -o exportcommand to export system journal entries related to tlog recordings:journalctl _COMM=tlog-rec _COMM=tlog-rec-sessio -o export | /usr/lib/systemd/systemd-journal-remote -o /tmp/dir/example.journal -
# journalctl _COMM=tlog-rec _COMM=tlog-rec-sessio -o export | /usr/lib/systemd/systemd-journal-remote -o /tmp/dir/example.journal -Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe
COMM=tlog-rec-sessioCOMM name is shortened due to a 15 character limit.
Chapter 3. Playing back recorded sessions
There are two methods for replaying recorded sessions:
-
the
tlog-playtool - the RHEL 8 web console, also referred to as Cockpit.
3.1. Playback with tlog-play
You can use the tlog-play tool to play back session recordings in a terminal. The tlog-play tool is a playback program for terminal input and output recorded with the tlog-rec tool. It reproduces the recording of the terminal it is under, but cannot change its size. For this reason the playback terminal needs to match the recorded terminal size for proper playback. The tlog-play tool loads its parameters from the /etc/tlog/tlog-play.conf configuration file. You can override those parameters with command line options described in the tlog-play manual pages.
3.2. Playback with the web console
The RHEL 8 web console has a whole interface for managing recorded sessions. You can choose the session you want to review directly from the Session Recording page, where the list of your recorded session is.
Example 3.1. Example list of recorded sessions
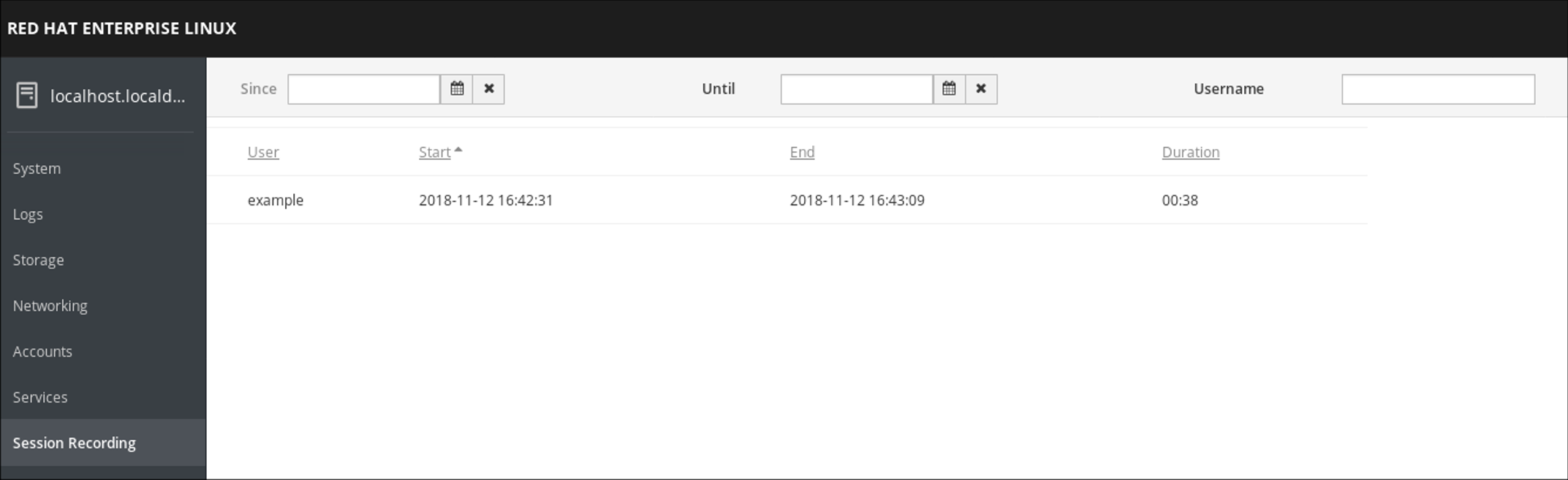
The web console player supports window resizing.
3.3. Playing back recorded sessions with tlog-play
You can play back session recordings from exported log files or from the Systemd Journal.
Playing back from a file
You can play a session back from a file both during and after recording:
tlog-play --reader=file --file-path=tlog.log
# tlog-play --reader=file --file-path=tlog.logPlaying back from the Journal
Generally, you can select Journal log entries for playback using Journal matches and timestamp limits, with the -M or --journal-match, -S or --journal-since, and -U or --journal-until options.
In practice however, playback from Journal is usually done with a single match against the TLOG_REC Journal field. The TLOG_REC field contains a copy of the rec field from the logged JSON data, which is a host-unique ID of the recording.
You can take the ID either from the TLOG_REC field value directly, or from the MESSAGE field from the JSON rec field. Both fields are part of log messages coming from the tlog-rec-session tool.
Procedure
- You can play back the whole recording as follows:
tlog-play -r journal -M TLOG_REC=<your-unique-host-id>
# tlog-play -r journal -M TLOG_REC=<your-unique-host-id>
You can find further instructions and documentation in the tlog-play manual pages.
Chapter 4. Configuring a system for session recording by using RHEL system roles
Use the tlog RHEL system role to record and monitor terminal session activities on your managed nodes in an automatic fashion. You can configure the recording to take place per user or user group by means of the SSSD service.
The session recording solution in the tlog RHEL system role consists of the following components:
-
The
tlogutility - System Security Services Daemon (SSSD)
- Optional: The web console interface
4.1. Configuring session recording for individual users by using the tlog RHEL system role
Prepare and apply an Ansible playbook to configure a RHEL system to log session recording data to the systemd journal. With that, you can enable recording the terminal output and input of a specific user during their sessions, when the user logs in on the console, or by SSH.
The playbook installs tlog-rec-session, a terminal session I/O logging program, that acts as the login shell for a user. The role creates an SSSD configuration drop file, and this file defines for which users and groups the login shell should be used. Additionally, if the cockpit package is installed on the system, the playbook also installs the cockpit-session-recording package, which is a Cockpit module that allows you to view and play recordings in the web console interface.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow tlog_scope_sssd: <value>-
The
somevalue specifies you want to record only certain users and groups, notallornone. tlog_users_sssd: <list_of_users>- A YAML list of users you want to record a session from. Note that the role does not add users if they do not exist.
Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Check the SSSD drop-in file’s content:
cd /etc/sssd/conf.d/sssd-session-recording.conf
# cd /etc/sssd/conf.d/sssd-session-recording.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can see that the file contains the parameters you set in the playbook.
- Log in as a user whose session will be recorded, perform some actions, and log out.
As the
rootuser:Display the list of recorded sessions:
journalctl _COMM=tlog-rec-sessio Nov 12 09:17:30 managed-node-01.example.com -tlog-rec-session[1546]: {"ver":"2.3","host":"managed-node-01.example.com","rec":"07418f2b0f334c1696c10cbe6f6f31a6-60a-e4a2","user":"demo-user",... ...# journalctl _COMM=tlog-rec-sessio Nov 12 09:17:30 managed-node-01.example.com -tlog-rec-session[1546]: {"ver":"2.3","host":"managed-node-01.example.com","rec":"07418f2b0f334c1696c10cbe6f6f31a6-60a-e4a2","user":"demo-user",... ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the value of the
rec(recording ID) field in the next step.Note that the value of the
_COMMfield is shortened due to a 15 character limit.Play back a session:
tlog-play -r journal -M TLOG_REC=<recording_id>
# tlog-play -r journal -M TLOG_REC=<recording_id>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.2. Excluding certain users and groups from session recording by using the tlog RHEL system role
You can use the tlog_exclude_users_sssd and tlog_exclude_groups_sssd role variables from the tlog RHEL system role to exclude users or groups from having their sessions recorded and logged in the systemd journal.
The playbook installs tlog-rec-session, a terminal session I/O logging program, that acts as the login shell for a user. The role creates an SSSD configuration drop file, and this file defines for which users and groups the login shell should be used. Additionally, if the cockpit package is installed on the system, the playbook also installs the cockpit-session-recording package, which is a Cockpit module that allows you to view and play recordings in the web console interface.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow tlog_scope_sssd: <value>-
The value
allspecifies that you want to record all users and groups. tlog_exclude_users_sssd: <user_list>- A YAML list of user names you want to exclude from the session recording.
tlog_exclude_groups_sssd: <group_list>- A YAML list of groups you want to exclude from the session recording.
Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Check the SSSD drop-in file’s content:
cat /etc/sssd/conf.d/sssd-session-recording.conf
# cat /etc/sssd/conf.d/sssd-session-recording.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can see that the file contains the parameters you set in the playbook.
- Log in as a user whose session will be recorded, perform some actions, and log out.
As the
rootuser:Display the list of recorded sessions:
journalctl _COMM=tlog-rec-sessio Nov 12 09:17:30 managed-node-01.example.com -tlog-rec-session[1546]: {"ver":"2.3","host":"managed-node-01.example.com","rec":"07418f2b0f334c1696c10cbe6f6f31a6-60a-e4a2","user":"demo-user",... ...# journalctl _COMM=tlog-rec-sessio Nov 12 09:17:30 managed-node-01.example.com -tlog-rec-session[1546]: {"ver":"2.3","host":"managed-node-01.example.com","rec":"07418f2b0f334c1696c10cbe6f6f31a6-60a-e4a2","user":"demo-user",... ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the value of the
rec(recording ID) field in the next step.Note that the value of the
_COMMfield is shortened due to a 15 character limit.Play back a session:
tlog-play -r journal -M TLOG_REC=<recording_id>
# tlog-play -r journal -M TLOG_REC=<recording_id>Copy to Clipboard Copied! Toggle word wrap Toggle overflow