Configuring and managing networking
Managing network interfaces and advanced networking features
Abstract
- You can configure bonds, VLANs, bridges, tunnels and other network types to connect the host to the network.
- IPSec and WireGuard provide secure VPNs between hosts and networks.
- RHEL also supports advanced networking features, such as policy-based routing and Multipath TCP (MPTCP).
Providing feedback on Red Hat documentation
We are committed to providing high-quality documentation and value your feedback. To help us improve, you can submit suggestions or report errors through the Red Hat Jira tracking system.
Procedure
Log in to the Jira website.
If you do not have an account, select the option to create one.
- Click Create in the top navigation bar.
- Enter a descriptive title in the Summary field.
- Enter your suggestion for improvement in the Description field. Include links to the relevant parts of the documentation.
- Click Create at the bottom of the dialogue.
Chapter 1. Implementing consistent network interface naming
The udev device manager implements consistent device naming in Red Hat Enterprise Linux. The device manager supports different naming schemes and, by default, assigns fixed names based on firmware, topology, and location information.
Without consistent device naming, the Linux kernel assigns names to network interfaces by combining a fixed prefix and an index. The index increases as the kernel initializes the network devices. For example, eth0 represents the first Ethernet device being probed on start-up. If you add another network interface controller to the system, the assignment of the kernel device names is no longer fixed because, after a reboot, the devices can initialize in a different order. In that case, the kernel can name the devices differently.
To solve this problem, udev assigns consistent device names. This has the following advantages:
- Device names are stable across reboots.
- Device names stay fixed even if you add or remove hardware.
- Defective hardware can be seamlessly replaced.
- The network naming is stateless and does not require explicit configuration files.
Generally, Red Hat does not support systems where consistent device naming is disabled. For exceptions, see the Red Hat Knowledgebase solution Is it safe to set net.ifnames=0.
1.1. How the udev device manager renames network interfaces
The udev device manager processes a set of rules to implement a consistent naming scheme for network interfaces.
Order of rule files:
Optional:
/usr/lib/udev/rules.d/60-net.rulesThis file exists only if you install the
initscripts-rename-devicepackage. The/usr/lib/udev/rules.d/60-net.rulesfile defines that the deprecated/usr/lib/udev/rename_devicehelper utility searches for theHWADDRparameter in/etc/sysconfig/network-scripts/ifcfg-*files. If the value set in the variable matches the MAC address of an interface, the helper utility renames the interface to the name set in theDEVICEparameter of theifcfgfile.If the system uses only NetworkManager connection profiles in keyfile format,
udevskips this step.Only on Dell systems:
/usr/lib/udev/rules.d/71-biosdevname.rulesThis file exists only if the
biosdevnamepackage is installed, and the rules file defines that thebiosdevnameutility renames the interface according to its naming policy, if it was not renamed in the previous step.NoteInstall and use
biosdevnameonly on Dell systems./usr/lib/udev/rules.d/75-net-description.rulesThis file defines how
udevexamines the network interface and sets the properties inudev-internal variables. These variables are then processed in the next step by the/usr/lib/udev/rules.d/80-net-setup-link.rulesfile. Some of the properties can be undefined./usr/lib/udev/rules.d/80-net-setup-link.rulesThis file calls the
net_setup_linkbuiltin of theudevservice, andudevrenames the interface based on the order of the policies in theNamePolicyparameter in the/usr/lib/systemd/network/99-default.linkfile. For further details, see Network interface naming policies.If none of the policies applies,
udevdoes not rename the interface.
1.2. Network interface naming policies
By default, the udev device manager uses the /usr/lib/systemd/network/99-default.link file to determine how it renames interfaces. The NamePolicy parameter in this file defines which naming policies udev applies and in what order.
Default order:
NamePolicy=keep kernel database onboard slot path
NamePolicy=keep kernel database onboard slot path
The following table describes the different actions of udev based on which policy matches first as specified by the NamePolicy parameter:
| Policy | Description | Example name |
|---|---|---|
| keep |
If the device already has a name that was assigned in the user space, | |
| kernel |
If the kernel indicates that a device name is predictable, |
|
| database |
This policy assigns names based on mappings in the |
|
| onboard | Device names incorporate firmware or BIOS-provided index numbers for onboard devices. |
|
| slot | Device names incorporate firmware or BIOS-provided PCI Express (PCIe) hot-plug slot-index numbers. |
|
| path | Device names incorporate the physical location of the connector of the hardware. |
|
| mac | Device names incorporate the MAC address. By default, Red Hat Enterprise Linux does not use this policy, but administrators can enable it. |
|
1.3. Network interface naming schemes
The udev device manager uses certain stable interface attributes that device drivers provide to generate consistent device names.
If a new udev version changes how the service creates names for certain interfaces, Red Hat adds a new scheme version and documents the details in the systemd.net-naming-scheme(7) man page on your system. By default, Red Hat Enterprise Linux (RHEL) 9 uses the rhel-9.0 naming scheme, even if you install or update to a later minor version of RHEL.
To prevent new drivers from providing more or other attributes for a network interface, the rhel-net-naming-sysattrs package provides the /usr/lib/udev/hwdb.d/50-net-naming-sysattr-allowlist.hwdb database. This database defines which sysfs values the udev service can use to create network interface names. The entries in the database are also versioned and influenced by the scheme version.
On RHEL 9.4 and later, you can also use all rhel-8.* naming schemes.
If you want to use a scheme other than the default, you can switch the network interface naming scheme.
For further details about the naming schemes for different device types and platforms, see the systemd.net-naming-scheme(7) man page on your system.
1.4. Switching to a different network interface naming scheme
By default, (RHEL) uses the rhel-9.0 naming scheme, even if you install or update to a later minor version of RHEL. While the default naming scheme fits in most scenarios, there might be reasons to switch to a different scheme version.
Examples when you must change the naming scheme:
- A new scheme can help to better identify a device if it adds additional attributes, such as a slot number, to an interface name.
-
An new scheme can prevent
udevfrom falling back to the kernel-assigned device names (eth*). This happens if the driver does not provide enough unique attributes for two or more interfaces to generate unique names for them.
Prerequisites
- You have access to the console of the server.
Procedure
List the network interfaces:
ip link show 2: eno1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...# ip link show 2: eno1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Record the MAC addresses of the interfaces.
Optional: Display the
ID_NET_NAMING_SCHEMEproperty of a network interface to identify the naming scheme that RHEL currently uses:udevadm info --query=property --property=ID_NET_NAMING_SCHEME /sys/class/net/eno1 ID_NET_NAMING_SCHEME=rhel-9.0
# udevadm info --query=property --property=ID_NET_NAMING_SCHEME /sys/class/net/eno1 ID_NET_NAMING_SCHEME=rhel-9.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the property is not available on the
loloopback device.Append the
net.naming-scheme=<scheme>option to the command line of all installed kernels, for example:grubby --update-kernel=ALL --args=net.naming-scheme=rhel-9.4
# grubby --update-kernel=ALL --args=net.naming-scheme=rhel-9.4Copy to Clipboard Copied! Toggle word wrap Toggle overflow Reboot the system.
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow Based on the MAC addresses you recorded, identify the new names of network interfaces that have changed due to the different naming scheme:
ip link show 2: eno1np0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...# ip link show 2: eno1np0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow After switching the scheme,
udevnames the device with the specified MAC addresseno1np0, whereas it was namedeno1before.Identify which NetworkManager connection profile uses an interface with the previous name:
nmcli -f device,name connection show DEVICE NAME eno1 example_profile ...
# nmcli -f device,name connection show DEVICE NAME eno1 example_profile ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
connection.interface-nameproperty in the connection profile to the new interface name:nmcli connection modify example_profile connection.interface-name "eno1np0"
# nmcli connection modify example_profile connection.interface-name "eno1np0"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Reactivate the connection profile:
nmcli connection up example_profile
# nmcli connection up example_profileCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Identify the naming scheme that RHEL now uses by displaying the
ID_NET_NAMING_SCHEMEproperty of a network interface:udevadm info --query=property --property=ID_NET_NAMING_SCHEME /sys/class/net/eno1np0 ID_NET_NAMING_SCHEME=_rhel-9.4
# udevadm info --query=property --property=ID_NET_NAMING_SCHEME /sys/class/net/eno1np0 ID_NET_NAMING_SCHEME=_rhel-9.4Copy to Clipboard Copied! Toggle word wrap Toggle overflow
1.5. Customizing the prefix for Ethernet interfaces during installation
If you do not want to use the default device-naming policy for Ethernet interfaces, you can set a custom device prefix during the Red Hat Enterprise Linux (RHEL) installation.
Red Hat supports systems with customized Ethernet prefixes only if you set the prefix during the RHEL installation. Using the prefixdevname utility on already deployed systems is not supported.
If you set a device prefix during the installation, the udev service uses the <prefix><index> format for Ethernet interfaces after the installation. For example, if you set the prefix net, the service assigns the names net0, net1, and so on to the Ethernet interfaces.
The udev service appends the index to the custom prefix, and preserves the index values of known Ethernet interfaces. If you add an interface, udev assigns an index value that is one greater than the previously-assigned index value to the new interface.
Prerequisites
- The prefix consists of ASCII characters.
- The prefix is an alphanumeric string.
- The prefix is shorter than 16 characters.
-
The prefix does not conflict with any other well-known network interface prefix, such as
eth,eno,ens, andem.
Procedure
- Boot the Red Hat Enterprise Linux installation media.
In the boot manager, follow these steps:
-
Select the
Install Red Hat Enterprise Linux <version>entry. - Press Tab to edit the entry.
-
Append
net.ifnames.prefix=<prefix>to the kernel options. - Press Enter to start the installation program.
-
Select the
- Install Red Hat Enterprise Linux.
Verification
To verify the interface names, display the network interfaces:
ip link show ... 2: net0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...# ip link show ... 2: net0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
1.6. Configuring user-defined network interface names by using udev rules
You can use udev rules to implement custom network interface names that reflect your organization’s requirements.
Procedure
Identify the network interface that you want to rename:
ip link show ... enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...# ip link show ... enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Record the MAC address of the interface.
Display the device type ID of the interface:
cat /sys/class/net/enp1s0/type 1
# cat /sys/class/net/enp1s0/type 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
/etc/udev/rules.d/70-persistent-net.rulesfile, and add a rule for each interface that you want to rename:SUBSYSTEM=="net",ACTION=="add",ATTR{address}=="<MAC_address>",ATTR{type}=="<device_type_id>",NAME="<new_interface_name>"SUBSYSTEM=="net",ACTION=="add",ATTR{address}=="<MAC_address>",ATTR{type}=="<device_type_id>",NAME="<new_interface_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantUse only
70-persistent-net.rulesas a file name if you require consistent device names during the boot process. Thedracututility adds a file with this name to theinitrdimage if you regenerate the RAM disk image.For example, use the following rule to rename the interface with MAC address
00:00:5e:00:53:1atoprovider0:SUBSYSTEM=="net",ACTION=="add",ATTR{address}=="00:00:5e:00:53:1a",ATTR{type}=="1",NAME="provider0"SUBSYSTEM=="net",ACTION=="add",ATTR{address}=="00:00:5e:00:53:1a",ATTR{type}=="1",NAME="provider0"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Regenerate the
initrdRAM disk image:dracut -f
# dracut -fCopy to Clipboard Copied! Toggle word wrap Toggle overflow You require this step only if you need networking capabilities in the RAM disk. For example, this is the case if the root file system is stored on a network device, such as iSCSI.
Identify which NetworkManager connection profile uses the interface that you want to rename:
nmcli -f device,name connection show DEVICE NAME enp1s0 example_profile ...
# nmcli -f device,name connection show DEVICE NAME enp1s0 example_profile ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Unset the
connection.interface-nameproperty in the connection profile:nmcli connection modify example_profile connection.interface-name ""
# nmcli connection modify example_profile connection.interface-name ""Copy to Clipboard Copied! Toggle word wrap Toggle overflow Temporarily, configure the connection profile to match both the new and the previous interface name:
nmcli connection modify example_profile match.interface-name "provider0 enp1s0"
# nmcli connection modify example_profile match.interface-name "provider0 enp1s0"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Reboot the system:
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the device with the MAC address that you specified in the link file has been renamed to
provider0:ip link show provider0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...# ip link show provider0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the connection profile to match only the new interface name:
nmcli connection modify example_profile match.interface-name "provider0"
# nmcli connection modify example_profile match.interface-name "provider0"Copy to Clipboard Copied! Toggle word wrap Toggle overflow You have now removed the old interface name from the connection profile.
Reactivate the connection profile:
nmcli connection up example_profile
# nmcli connection up example_profileCopy to Clipboard Copied! Toggle word wrap Toggle overflow
1.7. Configuring user-defined network interface names by using systemd link files
You can use systemd link files to implement custom network interface names that reflect your organization’s requirements.
Prerequisites
- You must meet one of these conditions: NetworkManager does not manage this interface, or the corresponding connection profile uses the keyfile format.
Procedure
Identify the network interface that you want to rename:
ip link show ... enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...# ip link show ... enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Record the MAC address of the interface.
If it does not already exist, create the
/etc/systemd/network/directory:mkdir -p /etc/systemd/network/
# mkdir -p /etc/systemd/network/Copy to Clipboard Copied! Toggle word wrap Toggle overflow For each interface that you want to rename, create a
70-*.linkfile in the/etc/systemd/network/directory with the following content:[Match] MACAddress=<MAC_address> [Link] Name=<new_interface_name>
[Match] MACAddress=<MAC_address> [Link] Name=<new_interface_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantUse a file name with a
70-prefix to keep the file names consistent with theudevrules-based solution.For example, create the
/etc/systemd/network/70-provider0.linkfile with the following content to rename the interface with MAC address00:00:5e:00:53:1atoprovider0:[Match] MACAddress=00:00:5e:00:53:1a [Link] Name=provider0
[Match] MACAddress=00:00:5e:00:53:1a [Link] Name=provider0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Regenerate the
initrdRAM disk image:dracut -f
# dracut -fCopy to Clipboard Copied! Toggle word wrap Toggle overflow You require this step only if you need networking capabilities in the RAM disk. For example, this is the case if the root file system is stored on a network device, such as iSCSI.
Identify which NetworkManager connection profile uses the interface that you want to rename:
nmcli -f device,name connection show DEVICE NAME enp1s0 example_profile ...
# nmcli -f device,name connection show DEVICE NAME enp1s0 example_profile ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Unset the
connection.interface-nameproperty in the connection profile:nmcli connection modify example_profile connection.interface-name ""
# nmcli connection modify example_profile connection.interface-name ""Copy to Clipboard Copied! Toggle word wrap Toggle overflow Temporarily, configure the connection profile to match both the new and the previous interface name:
nmcli connection modify example_profile match.interface-name "provider0 enp1s0"
# nmcli connection modify example_profile match.interface-name "provider0 enp1s0"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Reboot the system:
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the device with the MAC address that you specified in the link file has been renamed to
provider0:ip link show provider0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...# ip link show provider0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the connection profile to match only the new interface name:
nmcli connection modify example_profile match.interface-name "provider0"
# nmcli connection modify example_profile match.interface-name "provider0"Copy to Clipboard Copied! Toggle word wrap Toggle overflow You have now removed the old interface name from the connection profile.
Reactivate the connection profile.
nmcli connection up example_profile
# nmcli connection up example_profileCopy to Clipboard Copied! Toggle word wrap Toggle overflow
1.8. Assigning alternative names to a network interface by using systemd link files
With alternative interface naming, the kernel can assign additional names to network interfaces. You can use these alternative names in the same way as the normal interface names in commands that require a network interface name.
Prerequisites
- You must use ASCII characters for the alternative name.
- The alternative name must be shorter than 128 characters.
Procedure
Display the network interface names and their MAC addresses:
ip link show ... enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...# ip link show ... enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Record the MAC address of the interface to which you want to assign an alternative name.
If it does not already exist, create the
/etc/systemd/network/directory:mkdir -p /etc/systemd/network/
# mkdir -p /etc/systemd/network/Copy to Clipboard Copied! Toggle word wrap Toggle overflow For each interface that must have an alternative name, create a copy of the
/usr/lib/systemd/network/99-default.linkfile with a unique name and.linksuffix in the/etc/systemd/network/directory, for example:cp /usr/lib/systemd/network/99-default.link /etc/systemd/network/98-lan.link
# cp /usr/lib/systemd/network/99-default.link /etc/systemd/network/98-lan.linkCopy to Clipboard Copied! Toggle word wrap Toggle overflow Modify the file you created in the previous step. Rewrite the
[Match]section as follows, and append theAlternativeNameentries to the[Link]section:Copy to Clipboard Copied! Toggle word wrap Toggle overflow For example, create the
/etc/systemd/network/70-altname.linkfile with the following content to assignprovideras an alternative name to the interface with MAC address00:00:5e:00:53:1a:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Regenerate the
initrdRAM disk image:dracut -f
# dracut -fCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reboot the system:
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Use the alternative interface name. For example, display the IP address settings of the device with the alternative name
provider:ip address show provider 2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff altname provider ...# ip address show provider 2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether 00:00:5e:00:53:1a brd ff:ff:ff:ff:ff:ff altname provider ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 2. Configuring an Ethernet connection
NetworkManager creates a connection profile for each Ethernet adapter that is installed in a host. By default, this profile uses DHCP for both IPv4 and IPv6 connections.
Modify this automatically-created profile or add a new one in the following cases:
- The network requires custom settings, such as a static IP address configuration.
- You require multiple profiles because the host roams among different networks.
Red Hat Enterprise Linux provides administrators different options to configure Ethernet connections. For example:
-
Use
nmclito configure connections on the command line. -
Use
nmtuito configure connections in a text-based user interface. -
Use the GNOME Settings menu or
nm-connection-editorapplication to configure connections in a graphical interface. -
Use
nmstatectlto configure connections through thenmstateAPI. - Use RHEL system roles to automate the configuration of connections on one or multiple hosts.
If you want to manually configure Ethernet connections on hosts running in the Microsoft Azure cloud, disable the cloud-init service or configure it to ignore the network settings retrieved from the cloud environment. Otherwise, cloud-init will override on the next reboot the network settings that you have manually configured.
2.1. Configuring an Ethernet connection by using nmcli
If you connect a host to the network over Ethernet, you can manage the connection’s settings on the command line by using the nmcli utility.
Prerequisites
- A physical or virtual Ethernet Network Interface Controller (NIC) exists in the server’s configuration.
Procedure
List the NetworkManager connection profiles:
nmcli connection show NAME UUID TYPE DEVICE Wired connection 1 a5eb6490-cc20-3668-81f8-0314a27f3f75 ethernet enp1s0
# nmcli connection show NAME UUID TYPE DEVICE Wired connection 1 a5eb6490-cc20-3668-81f8-0314a27f3f75 ethernet enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow By default, NetworkManager creates a profile for each NIC in the host. If you plan to connect this NIC only to a specific network, adapt the automatically-created profile. If you plan to connect this NIC to networks with different settings, create individual profiles for each network.
If you want to create an additional connection profile, enter:
nmcli connection add con-name <connection-name> ifname <device-name> type ethernet
# nmcli connection add con-name <connection-name> ifname <device-name> type ethernetCopy to Clipboard Copied! Toggle word wrap Toggle overflow Skip this step to modify an existing profile.
Optional: Rename the connection profile:
nmcli connection modify "Wired connection 1" connection.id "Internal-LAN"
# nmcli connection modify "Wired connection 1" connection.id "Internal-LAN"Copy to Clipboard Copied! Toggle word wrap Toggle overflow On hosts with multiple profiles, a meaningful name makes it easier to identify the purpose of a profile.
Display the current settings of the connection profile:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the IPv4 settings:
To use DHCP, enter:
nmcli connection modify Internal-LAN ipv4.method auto
# nmcli connection modify Internal-LAN ipv4.method autoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Skip this step if
ipv4.methodis already set toauto(default).To set a static IPv4 address, network mask, default gateway, DNS servers, and search domain, enter:
nmcli connection modify Internal-LAN ipv4.method manual ipv4.addresses 192.0.2.1/24 ipv4.gateway 192.0.2.254 ipv4.dns 192.0.2.200 ipv4.dns-search example.com
# nmcli connection modify Internal-LAN ipv4.method manual ipv4.addresses 192.0.2.1/24 ipv4.gateway 192.0.2.254 ipv4.dns 192.0.2.200 ipv4.dns-search example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Configure the IPv6 settings:
To use stateless address autoconfiguration (SLAAC), enter:
nmcli connection modify Internal-LAN ipv6.method auto
# nmcli connection modify Internal-LAN ipv6.method autoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Skip this step if
ipv6.methodis already set toauto(default).To set a static IPv6 address, network mask, default gateway, DNS servers, and search domain, enter:
nmcli connection modify Internal-LAN ipv6.method manual ipv6.addresses 2001:db8:1::fffe/64 ipv6.gateway 2001:db8:1::fffe ipv6.dns 2001:db8:1::ffbb ipv6.dns-search example.com
# nmcli connection modify Internal-LAN ipv6.method manual ipv6.addresses 2001:db8:1::fffe/64 ipv6.gateway 2001:db8:1::fffe ipv6.dns 2001:db8:1::ffbb ipv6.dns-search example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
To customize other settings in the profile, use the following command:
nmcli connection modify <connection-name> <setting> <value>
# nmcli connection modify <connection-name> <setting> <value>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enclose values with spaces or semicolons in quotes.
Activate the profile:
nmcli connection up Internal-LAN
# nmcli connection up Internal-LANCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IP settings of the NIC:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv4 default gateway:
ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102
# ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 default gateway:
ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref medium
# ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the DNS settings:
cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbb
# cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbbCopy to Clipboard Copied! Toggle word wrap Toggle overflow If multiple connection profiles are active at the same time, the order of
nameserverentries depend on the DNS priority values in these profiles and the connection types.Use the
pingutility to verify that this host can send packets to other hosts:ping <host-name-or-IP-address>
# ping <host-name-or-IP-address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Troubleshooting
- Verify that the network cable is plugged-in to the host and a switch.
- Check whether the link failure exists only on this host or also on other hosts connected to the same switch.
- Verify that the network cable and the network interface are working as expected. Perform hardware diagnosis steps and replace defective cables and network interface cards.
- If the configuration on the disk does not match the configuration on the device, starting or restarting NetworkManager creates an in-memory connection that reflects the configuration of the device. For further details and how to avoid this problem, see the Red Hat Knowledgebase solution NetworkManager duplicates a connection after restart of NetworkManager service.
2.2. Configuring an Ethernet connection by using the nmcli interactive editor
If you connect a host to the network over Ethernet, you can manage the connection’s settings on the command line by using the nmcli utility.
Prerequisites
- A physical or virtual Ethernet Network Interface Controller (NIC) exists in the server’s configuration.
Procedure
List the NetworkManager connection profiles:
nmcli connection show NAME UUID TYPE DEVICE Wired connection 1 a5eb6490-cc20-3668-81f8-0314a27f3f75 ethernet enp1s0
# nmcli connection show NAME UUID TYPE DEVICE Wired connection 1 a5eb6490-cc20-3668-81f8-0314a27f3f75 ethernet enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow By default, NetworkManager creates a profile for each NIC in the host. If you plan to connect this NIC only to a specific network, adapt the automatically-created profile. If you plan to connect this NIC to networks with different settings, create individual profiles for each network.
Start
nmcliin interactive mode:To create an additional connection profile, enter:
nmcli connection edit type ethernet con-name "<connection-name>"
# nmcli connection edit type ethernet con-name "<connection-name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To modify an existing connection profile, enter:
nmcli connection edit con-name "<connection-name>"
# nmcli connection edit con-name "<connection-name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Optional: Rename the connection profile:
nmcli> set connection.id Internal-LAN
nmcli> set connection.id Internal-LANCopy to Clipboard Copied! Toggle word wrap Toggle overflow On hosts with multiple profiles, a meaningful name makes it easier to identify the purpose of a profile.
Do not use quotes to set an ID that contains spaces to avoid
nmclimaking the quotes part of the name. For example, to setExample Connectionas ID, enterset connection.id Example Connection.Display the current settings of the connection profile:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you create a new connection profile, set the network interface:
nmcli> set connection.interface-name enp1s0
nmcli> set connection.interface-name enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the IPv4 settings:
To use DHCP, enter:
nmcli> set ipv4.method auto
nmcli> set ipv4.method autoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Skip this step if
ipv4.methodis already set toauto(default).To set a static IPv4 address, network mask, default gateway, DNS servers, and search domain, enter:
nmcli> ipv4.addresses 192.0.2.1/24 Do you also want to set 'ipv4.method' to 'manual'? [yes]: yes nmcli> ipv4.gateway 192.0.2.254 nmcli> ipv4.dns 192.0.2.200 nmcli> ipv4.dns-search example.com
nmcli> ipv4.addresses 192.0.2.1/24 Do you also want to set 'ipv4.method' to 'manual'? [yes]: yes nmcli> ipv4.gateway 192.0.2.254 nmcli> ipv4.dns 192.0.2.200 nmcli> ipv4.dns-search example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Configure the IPv6 settings:
To use stateless address autoconfiguration (SLAAC), enter:
nmcli> set ipv6.method auto
nmcli> set ipv6.method autoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Skip this step if
ipv6.methodis already set toauto(default).To set a static IPv6 address, network mask, default gateway, DNS servers, and search domain, enter:
nmcli> ipv6.addresses 2001:db8:1::fffe/64 Do you also want to set 'ipv6.method' to 'manual'? [yes]: yes nmcli> ipv6.gateway 2001:db8:1::fffe nmcli> ipv6.dns 2001:db8:1::ffbb nmcli> ipv6.dns-search example.com
nmcli> ipv6.addresses 2001:db8:1::fffe/64 Do you also want to set 'ipv6.method' to 'manual'? [yes]: yes nmcli> ipv6.gateway 2001:db8:1::fffe nmcli> ipv6.dns 2001:db8:1::ffbb nmcli> ipv6.dns-search example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Save and activate the connection:
nmcli> save persistent
nmcli> save persistentCopy to Clipboard Copied! Toggle word wrap Toggle overflow Leave the interactive mode:
nmcli> quit
nmcli> quitCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IP settings of the NIC:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv4 default gateway:
ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102
# ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 default gateway:
ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref medium
# ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the DNS settings:
cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbb
# cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbbCopy to Clipboard Copied! Toggle word wrap Toggle overflow If multiple connection profiles are active at the same time, the order of
nameserverentries depend on the DNS priority values in these profiles and the connection types.Use the
pingutility to verify that this host can send packets to other hosts:ping <host-name-or-IP-address>
# ping <host-name-or-IP-address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Troubleshooting
- Verify that the network cable is plugged-in to the host and a switch.
- Check whether the link failure exists only on this host or also on other hosts connected to the same switch.
- Verify that the network cable and the network interface are working as expected. Perform hardware diagnosis steps and replace defective cables and network interface cards.
- If the configuration on the disk does not match the configuration on the device, starting or restarting NetworkManager creates an in-memory connection that reflects the configuration of the device. For further details and how to avoid this problem, see the Red Hat Knowledgebase solution NetworkManager duplicates a connection after restart of NetworkManager service.
2.3. Configuring an Ethernet connection by using nmtui
If you connect a host to an Ethernet network, you can manage the connection’s settings in a text-based user interface. Use the nmtui application to create new profiles and to update existing ones on a host without a graphical interface.
In nmtui:
- Navigate by using the cursor keys.
- Press a button by selecting it and hitting Enter.
- Select and clear checkboxes by using Space.
- To return to the previous screen, use ESC.
Prerequisites
- A physical or virtual Ethernet Network Interface Controller (NIC) exists in the server’s configuration.
Procedure
If you do not know the network device name you want to use in the connection, display the available devices:
nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet unavailable -- ...
# nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet unavailable -- ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Start
nmtui:nmtui
# nmtuiCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Select Edit a connection, and press Enter.
Choose whether to add a new connection profile or to modify an existing one:
To create a new profile:
- Press Add.
- Select Ethernet from the list of network types, and press Enter.
- To modify an existing profile, select the profile from the list, and press Enter.
Optional: Update the name of the connection profile.
On hosts with multiple profiles, a meaningful name makes it easier to identify the purpose of a profile.
- If you create a new connection profile, enter the network device name into the Device field.
Depending on your environment, configure the IP address settings in the
IPv4 configurationandIPv6 configurationareas accordingly. For this, press the button next to these areas, and select:- Disabled, if this connection does not require an IP address.
- Automatic, if a DHCP server dynamically assigns an IP address to this NIC.
Manual, if the network requires static IP address settings. In this case, you must fill further fields:
- Press Show next to the protocol you want to configure to display additional fields.
Press Add next to Addresses, and enter the IP address and the subnet mask in Classless Inter-Domain Routing (CIDR) format.
If you do not specify a subnet mask, NetworkManager sets a
/32subnet mask for IPv4 addresses and/64for IPv6 addresses.- Enter the address of the default gateway.
- Press Add next to DNS servers, and enter the DNS server address.
- Press Add next to Search domains, and enter the DNS search domain.
Figure 2.1. Example of an Ethernet connection with static IP address settings
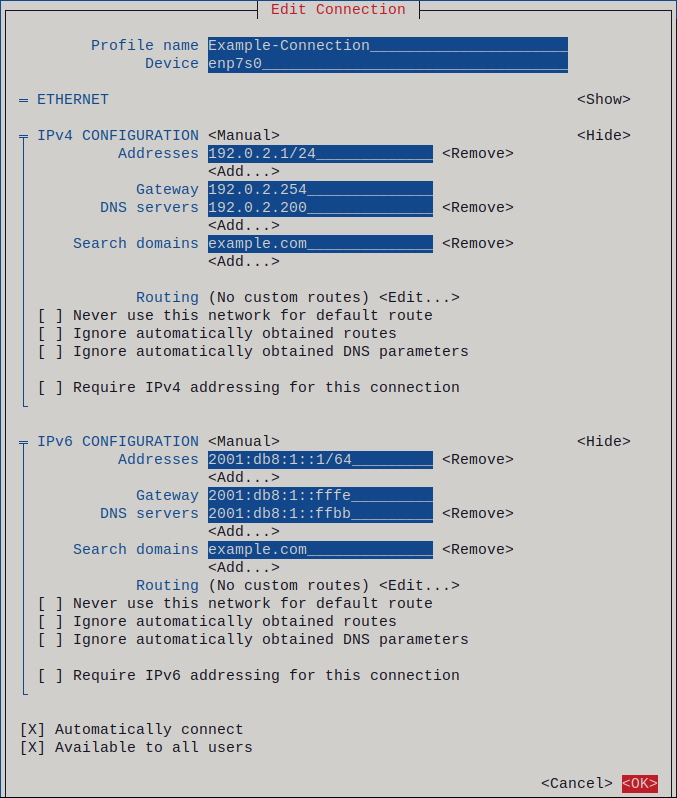
- Press OK to create and automatically activate the new connection.
- Press Back to return to the main menu.
-
Select Quit, and press Enter to close the
nmtuiapplication.
Verification
Display the IP settings of the NIC:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv4 default gateway:
ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102
# ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 default gateway:
ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref medium
# ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the DNS settings:
cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbb
# cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbbCopy to Clipboard Copied! Toggle word wrap Toggle overflow If multiple connection profiles are active at the same time, the order of
nameserverentries depend on the DNS priority values in these profiles and the connection types.Use the
pingutility to verify that this host can send packets to other hosts:ping <host-name-or-IP-address>
# ping <host-name-or-IP-address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Troubleshooting
- Verify that the network cable is plugged-in to the host and a switch.
- Check whether the link failure exists only on this host or also on other hosts connected to the same switch.
- Verify that the network cable and the network interface are working as expected. Perform hardware diagnosis steps and replace defective cables and network interface cards.
- If the configuration on the disk does not match the configuration on the device, starting or restarting NetworkManager creates an in-memory connection that reflects the configuration of the device. For further details and how to avoid this problem, see the Red Hat Knowledgebase solution NetworkManager duplicates a connection after restart of NetworkManager service.
2.4. Configuring an Ethernet connection by using control-center
If you connect a host to the network over Ethernet, you can manage the connection’s settings with a graphical interface by using the GNOME Settings menu.
Note that control-center does not support as many configuration options as the nm-connection-editor application or the nmcli utility.
Prerequisites
- A physical or virtual Ethernet Network Interface Controller (NIC) exists in the server’s configuration.
- GNOME is installed.
Procedure
-
Press the Super key, enter
Settings, and press Enter. - Select Network in the navigation on the left.
Choose whether to add a new connection profile or to modify an existing one:
- To create a new profile, click the button next to the Ethernet entry.
- To modify an existing profile, click the gear icon next to the profile entry.
Optional: On the Identity tab, update the name of the connection profile.
On hosts with multiple profiles, a meaningful name makes it easier to identify the purpose of a profile.
Depending on your environment, configure the IP address settings on the IPv4 and IPv6 tabs accordingly:
-
To use DHCP or IPv6 stateless address autoconfiguration (SLAAC), select
Automatic (DHCP)as method (default). To set a static IP address, network mask, default gateway, DNS servers, and search domain, select
Manualas method, and fill the fields on the tabs: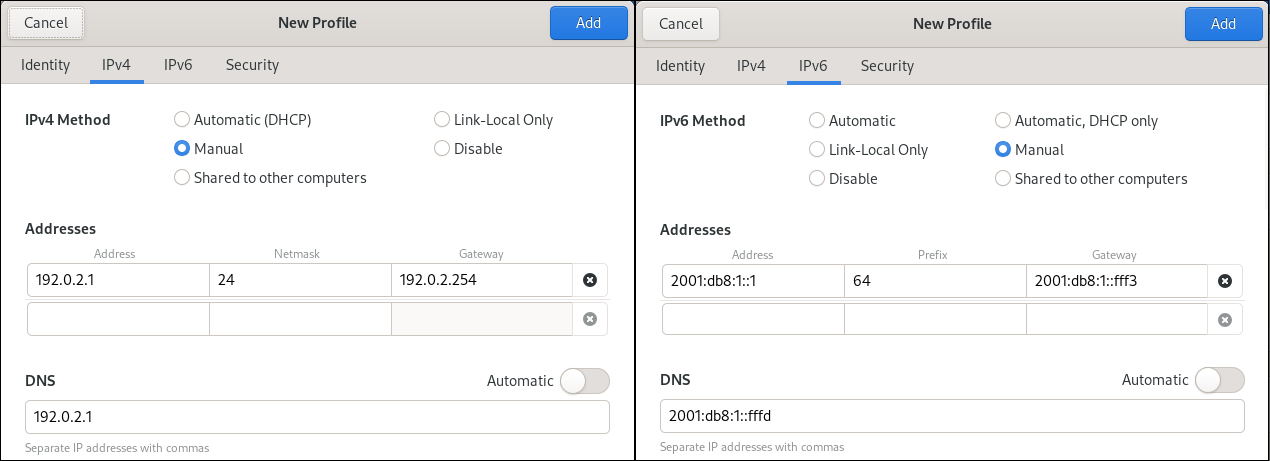
-
To use DHCP or IPv6 stateless address autoconfiguration (SLAAC), select
Depending on whether you add or modify a connection profile, click the or button to save the connection.
The GNOME
control-centerautomatically activates the connection.
Verification
Display the IP settings of the NIC:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv4 default gateway:
ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102
# ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 default gateway:
ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref medium
# ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the DNS settings:
cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbb
# cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbbCopy to Clipboard Copied! Toggle word wrap Toggle overflow If multiple connection profiles are active at the same time, the order of
nameserverentries depend on the DNS priority values in these profiles and the connection types.Use the
pingutility to verify that this host can send packets to other hosts:ping <host-name-or-IP-address>
# ping <host-name-or-IP-address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Troubleshooting steps
- Verify that the network cable is plugged-in to the host and a switch.
- Check whether the link failure exists only on this host or also on other hosts connected to the same switch.
- Verify that the network cable and the network interface are working as expected. Perform hardware diagnosis steps and replace defective cables and network interface cards.
- If the configuration on the disk does not match the configuration on the device, starting or restarting NetworkManager creates an in-memory connection that reflects the configuration of the device. For further details and how to avoid this problem, see the Red Hat Knowledgebase solution NetworkManager duplicates a connection after restart of NetworkManager service.
2.5. Configuring an Ethernet connection by using nm-connection-editor
If you connect a host to the network over Ethernet, you can manage the connection’s settings with a graphical interface by using the nm-connection-editor application.
Prerequisites
- A physical or virtual Ethernet Network Interface Controller (NIC) exists in the server’s configuration.
- GNOME is installed.
Procedure
Open a terminal, and enter:
nm-connection-editor
$ nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow Choose whether to add a new connection profile or to modify an existing one:
To create a new profile:
- Click the button
- Select Ethernet as connection type, and click .
- To modify an existing profile, double-click the profile entry.
Optional: Update the name of the profile in the Connection Name field.
On hosts with multiple profiles, a meaningful name makes it easier to identify the purpose of a profile.
-
If you create a new profile, select the device on the
Ethernettab. Depending on your environment, configure the IP address settings on the IPv4 Settings and IPv6 Settings tabs accordingly:
-
To use DHCP or IPv6 stateless address autoconfiguration (SLAAC), select
Automatic (DHCP)as method (default). To set a static IP address, network mask, default gateway, DNS servers, and search domain, select
Manualas method, and fill the fields on the tabs: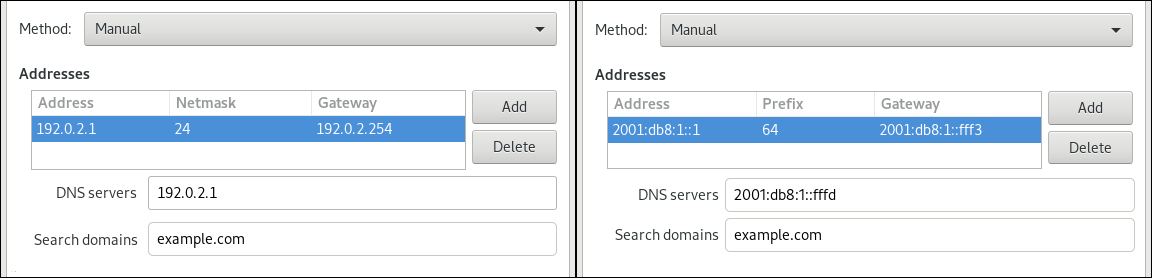
-
To use DHCP or IPv6 stateless address autoconfiguration (SLAAC), select
- Click .
- Close nm-connection-editor.
Verification
Display the IP settings of the NIC:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv4 default gateway:
ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102
# ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 default gateway:
ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref medium
# ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the DNS settings:
cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbb
# cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbbCopy to Clipboard Copied! Toggle word wrap Toggle overflow If multiple connection profiles are active at the same time, the order of
nameserverentries depend on the DNS priority values in these profiles and the connection types.Use the
pingutility to verify that this host can send packets to other hosts:ping <host-name-or-IP-address>
# ping <host-name-or-IP-address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Troubleshooting steps
- Verify that the network cable is plugged-in to the host and a switch.
- Check whether the link failure exists only on this host or also on other hosts connected to the same switch.
- Verify that the network cable and the network interface are working as expected. Perform hardware diagnosis steps and replace defective cables and network interface cards.
- If the configuration on the disk does not match the configuration on the device, starting or restarting NetworkManager creates an in-memory connection that reflects the configuration of the device. For further details and how to avoid this problem, see the Red Hat Knowledgebase solution NetworkManager duplicates a connection after restart of NetworkManager service.
2.6. Configuring an Ethernet connection with a static IP address by using nmstatectl with an interface name
You can use the declarative Nmstate API to configure an Ethernet connection with static IP addresses, gateways, and DNS settings, and assign them to a specified interface name. Nmstate ensures that the result matches the configuration file or rolls back the changes.
Prerequisites
- A physical or virtual Ethernet Network Interface Controller (NIC) exists in the server’s configuration.
-
The
nmstatepackage is installed.
Procedure
Create a YAML file, for example
~/create-ethernet-profile.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow These settings define an Ethernet connection profile for the
enp1s0device with the following settings:-
A static IPv4 address -
192.0.2.1with the/24subnet mask -
A static IPv6 address -
2001:db8:1::1with the/64subnet mask -
An IPv4 default gateway -
192.0.2.254 -
An IPv6 default gateway -
2001:db8:1::fffe -
An IPv4 DNS server -
192.0.2.200 -
An IPv6 DNS server -
2001:db8:1::ffbb -
A DNS search domain -
example.com
-
A static IPv4 address -
Optional: You can define the
identifier: mac-addressandmac-address: <mac_address>properties in theinterfacesproperty to identify the network interface card by its MAC address instead of its name, for example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the settings to the system:
nmstatectl apply ~/create-ethernet-profile.yml
# nmstatectl apply ~/create-ethernet-profile.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the current state in YAML format:
nmstatectl show enp1s0
# nmstatectl show enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IP settings of the NIC:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv4 default gateway:
ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102
# ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 default gateway:
ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref medium
# ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the DNS settings:
cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbb
# cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbbCopy to Clipboard Copied! Toggle word wrap Toggle overflow If multiple connection profiles are active at the same time, the order of
nameserverentries depend on the DNS priority values in these profiles and the connection types.Use the
pingutility to verify that this host can send packets to other hosts:ping <host-name-or-IP-address>
# ping <host-name-or-IP-address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.7. Configuring an Ethernet connection with a static IP address by using nmstatectl with a PCI address
You can use the declarative Nmstate API to configure an Ethernet connection with static IP addresses, gateways, and DNS settings, and assign them to a device based on its PCI address. Nmstate ensures that the result matches the configuration file or rolls back the changes.
Prerequisites
- A physical Ethernet Network Interface Controller (NIC) exists in the server’s configuration.
-
You know the PCI address of the device. You can display the PCI address by using the
ethtool -i <interface_name> | grep bus-infocommand. -
The
nmstatepackage is installed.
Procedure
Create a YAML file, for example
~/create-ethernet-profile.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow These settings define an Ethernet connection profile for the device with the ID
0000:00:14.3with the following settings:-
A static IPv4 address -
192.0.2.1with the/24subnet mask -
A static IPv6 address -
2001:db8:1::1with the/64subnet mask -
An IPv4 default gateway -
192.0.2.254 -
An IPv6 default gateway -
2001:db8:1::fffe -
An IPv4 DNS server -
192.0.2.200 -
An IPv6 DNS server -
2001:db8:1::ffbb -
A DNS search domain -
example.com
-
A static IPv4 address -
Apply the settings to the system:
nmstatectl apply ~/create-ethernet-profile.yml
# nmstatectl apply ~/create-ethernet-profile.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the current state in YAML format:
nmstatectl show <interface_name>
# nmstatectl show <interface_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IP settings of the NIC:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv4 default gateway:
ip route show default default via 192.0.2.254 dev <interface_name> proto static metric 102
# ip route show default default via 192.0.2.254 dev <interface_name> proto static metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 default gateway:
ip -6 route show default default via 2001:db8:1::fffe dev <interface_name> proto static metric 102 pref medium
# ip -6 route show default default via 2001:db8:1::fffe dev <interface_name> proto static metric 102 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the DNS settings:
cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbb
# cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbbCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
pingutility to verify that this host can send packets to other hosts:ping <host-name-or-IP-address>
# ping <host-name-or-IP-address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.8. Configuring an Ethernet connection with a static IP address by using the network RHEL system role with an interface name
You can use the network RHEL system role to configure an Ethernet connection with static IP addresses, gateways, and DNS settings, and assign them to a specified interface name.
To connect a Red Hat Enterprise Linux host to an Ethernet network, create a NetworkManager connection profile for the network device. By using Ansible and the network RHEL system role, you can automate this process and remotely configure connection profiles on the hosts defined in a playbook.
Typically, administrators want to reuse a playbook and not maintain individual playbooks for each host to which Ansible should assign static IP addresses. In this case, you can use variables in the playbook and maintain the settings in the inventory. As a result, you need only one playbook to dynamically assign individual settings to multiple hosts.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. - A physical or virtual Ethernet device exists in the server configuration.
- The managed nodes use NetworkManager to configure the network.
Procedure
Edit the
~/inventoryfile, and append the host-specific settings to the host entries:managed-node-01.example.com interface=enp1s0 ip_v4=192.0.2.1/24 ip_v6=2001:db8:1::1/64 gateway_v4=192.0.2.254 gateway_v6=2001:db8:1::fffe managed-node-02.example.com interface=enp1s0 ip_v4=192.0.2.2/24 ip_v6=2001:db8:1::2/64 gateway_v4=192.0.2.254 gateway_v6=2001:db8:1::fffe
managed-node-01.example.com interface=enp1s0 ip_v4=192.0.2.1/24 ip_v6=2001:db8:1::1/64 gateway_v4=192.0.2.254 gateway_v6=2001:db8:1::fffe managed-node-02.example.com interface=enp1s0 ip_v4=192.0.2.2/24 ip_v6=2001:db8:1::2/64 gateway_v4=192.0.2.254 gateway_v6=2001:db8:1::fffeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow This playbook reads certain values dynamically for each host from the inventory file and uses static values in the playbook for settings which are the same for all hosts.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Query the Ansible facts of the managed node and verify the active network settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.9. Configuring an Ethernet connection with a static IP address by using the network RHEL system role with a device path
You can use the network RHEL system role to configure an Ethernet connection with static IP addresses, gateways, and DNS settings, and assign them to a device based on its path instead of its name.
To connect a Red Hat Enterprise Linux host to an Ethernet network, create a NetworkManager connection profile for the network device. By using Ansible and the network RHEL system role, you can automate this process and remotely configure connection profiles on the hosts defined in a playbook.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. - A physical or virtual Ethernet device exists in the server’s configuration.
- The managed nodes use NetworkManager to configure the network.
-
You know the path of the device. You can display the device path by using the
udevadm info /sys/class/net/<device_name> | grep ID_PATH=command.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
match-
Defines that a condition must be met in order to apply the settings. You can only use this variable with the
pathoption. path-
Defines the persistent path of a device. You can set it as a fixed path or an expression. Its value can contain modifiers and wildcards. The example applies the settings to devices that match PCI ID
0000:00:0[1-3].0, but not0000:00:02.0.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Query the Ansible facts of the managed node and verify the active network settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.10. Configuring an Ethernet connection with a dynamic IP address by using nmstatectl with an interface name
You can use the declarative Nmstate API to configure an Ethernet connection with static IP addresses, gateways, and DNS settings, and assign the configuration to a device based on its PCI address. Nmstate ensures that the result matches the configuration file or rolls back the changes.
Prerequisites
- A physical or virtual Ethernet Network Interface Controller (NIC) exists in the server’s configuration.
- A DHCP server is available in the network.
-
The
nmstatepackage is installed.
Procedure
Create a YAML file, for example
~/create-ethernet-profile.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow These settings define an Ethernet connection profile for the
enp1s0device. The connection retrieves IPv4 addresses, IPv6 addresses, default gateway, routes, DNS servers, and search domains from a DHCP server and IPv6 stateless address autoconfiguration (SLAAC).Optional: You can define the
identifier: mac-addressandmac-address: <mac_address>properties in theinterfacesproperty to identify the network interface card by its MAC address instead of its name, for example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the settings to the system:
nmstatectl apply ~/create-ethernet-profile.yml
# nmstatectl apply ~/create-ethernet-profile.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the current state in YAML format:
nmstatectl show enp1s0
# nmstatectl show enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IP settings of the NIC:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv4 default gateway:
ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102
# ip route show default default via 192.0.2.254 dev enp1s0 proto static metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 default gateway:
ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref medium
# ip -6 route show default default via 2001:db8:1::fffe dev enp1s0 proto static metric 102 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the DNS settings:
cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbb
# cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbbCopy to Clipboard Copied! Toggle word wrap Toggle overflow If multiple connection profiles are active at the same time, the order of
nameserverentries depend on the DNS priority values in these profiles and the connection types.Use the
pingutility to verify that this host can send packets to other hosts:ping <host-name-or-IP-address>
# ping <host-name-or-IP-address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.11. Configuring an Ethernet connection with a dynamic IP address by using nmstatectl with a PCI address
You can use the declarative Nmstate API to configure an Ethernet connection with DHCP and IPv6 stateless address autoconfiguration (SLAAC) and assign the configuration to a device based on its PCI address. Nmstate ensures that the result matches the configuration file or rolls back the changes.
Prerequisites
- A physical Ethernet device exists in the server’s configuration.
- A DHCP server and SLAAC are available in the network.
- The managed hosts use NetworkManager to configure the network.
-
You know the PCI address of the device. You can display the PCI address by using the
ethtool -i <interface_name> | grep bus-infocommand. -
The
nmstatepackage is installed.
Procedure
Create a YAML file, for example
~/create-ethernet-profile.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow These settings define an Ethernet connection profile for the device with the ID
0000:00:14.3. The connection retrieves IPv4 addresses, IPv6 addresses, default gateway, routes, DNS servers, and search domains from a DHCP server and IPv6 stateless address autoconfiguration (SLAAC).Apply the settings to the system:
nmstatectl apply ~/create-ethernet-profile.yml
# nmstatectl apply ~/create-ethernet-profile.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the current state in YAML format:
nmstatectl show <interface_name>
# nmstatectl show <interface_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IP settings of the NIC:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv4 default gateway:
ip route show default default via 192.0.2.254 dev <interface_name> proto static metric 102
# ip route show default default via 192.0.2.254 dev <interface_name> proto static metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 default gateway:
ip -6 route show default default via 2001:db8:1::fffe dev <interface_name> proto static metric 102 pref medium
# ip -6 route show default default via 2001:db8:1::fffe dev <interface_name> proto static metric 102 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the DNS settings:
cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbb
# cat /etc/resolv.conf search example.com nameserver 192.0.2.200 nameserver 2001:db8:1::ffbbCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
pingutility to verify that this host can send packets to other hosts:ping <host-name-or-IP-address>
# ping <host-name-or-IP-address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.12. Configuring an Ethernet connection with a dynamic IP address by using the network RHEL system role with an interface name
You can use the network RHEL system role to configure an Ethernet connection that retrieves its IP addresses, gateways, and DNS settings from a DHCP server and IPv6 stateless address autoconfiguration (SLAAC). With this role you can assign the connection profile to the specified interface name.
To connect a Red Hat Enterprise Linux host to an Ethernet network, create a NetworkManager connection profile for the network device. By using Ansible and the network RHEL system role, you can automate this process and remotely configure connection profiles on the hosts defined in a playbook.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. - A physical or virtual Ethernet device exists in the servers' configuration.
- A DHCP server and SLAAC are available in the network.
- The managed nodes use the NetworkManager service to configure the network.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
dhcp4: yes- Enables automatic IPv4 address assignment from DHCP, PPP, or similar services.
auto6: yes-
Enables IPv6 auto-configuration. By default, NetworkManager uses Router Advertisements. If the router announces the
managedflag, NetworkManager requests an IPv6 address and prefix from a DHCPv6 server.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Query the Ansible facts of the managed node and verify that the interface received IP addresses and DNS settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.13. Configuring an Ethernet connection with a dynamic IP address by using the network RHEL system role with a device path
By using the network RHEL system role, you can configure an Ethernet connection to retrieve its IP addresses, gateways, and DNS settings from a DHCP server and IPv6 stateless address autoconfiguration (SLAAC). The role can assign the profile by the device’s path.
To connect a Red Hat Enterprise Linux host to an Ethernet network, create a NetworkManager connection profile for the network device. By using Ansible and the network RHEL system role, you can automate this process and remotely configure connection profiles on the hosts defined in a playbook.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. - A physical or virtual Ethernet device exists in the server’s configuration.
- A DHCP server and SLAAC are available in the network.
- The managed hosts use NetworkManager to configure the network.
-
You know the path of the device. You can display the device path by using the
udevadm info /sys/class/net/<device_name> | grep ID_PATH=command.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
match: path-
Defines that a condition must be met in order to apply the settings. You can only use this variable with the
pathoption. path: <path_and_expressions>-
Defines the persistent path of a device. You can set it as a fixed path or an expression. Its value can contain modifiers and wildcards. The example applies the settings to devices that match PCI ID
0000:00:0[1-3].0, but not0000:00:02.0. dhcp4: yes- Enables automatic IPv4 address assignment from DHCP, PPP, or similar services.
auto6: yes-
Enables IPv6 auto-configuration. By default, NetworkManager uses Router Advertisements. If the router announces the
managedflag, NetworkManager requests an IPv6 address and prefix from a DHCPv6 server.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Query the Ansible facts of the managed node and verify that the interface received IP addresses and DNS settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.14. Configuring multiple Ethernet interfaces by using a single connection profile by interface name
NetworkManager supports using wildcards for interface names in connection profiles. This lets you create a single profile for multiple Ethernet interfaces, which is useful when a host roams between Ethernet networks with dynamic IP address assignment.
Prerequisites
- Multiple physical or virtual Ethernet devices exist in the server’s configuration.
- A DHCP server is available in the network.
- No connection profile exists on the host.
Procedure
Add a connection profile that applies to all interface names starting with
enp:nmcli connection add con-name "Wired connection 1" connection.multi-connect multiple match.interface-name enp* type ethernet
# nmcli connection add con-name "Wired connection 1" connection.multi-connect multiple match.interface-name enp* type ethernetCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display all settings of the single connection profile:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 3indicates that the interface can be active multiple times at a particular moment. The connection profile uses all devices that match the pattern in thematch.interface-nameparameter and, therefore, the connection profiles have the same Universally Unique Identifier (UUID).Display the status of the connections:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 4. Configuring a NIC team
Network interface controller (NIC) teaming is a method to combine or aggregate physical and virtual network interfaces to provide a logical interface with higher throughput or redundancy. NIC teaming uses a small kernel module to implement fast handling of packet flows and a user-space service for other tasks. This way, NIC teaming is an easily extensible and scalable solution for load-balancing and redundancy requirements.
Red Hat Enterprise Linux provides administrators different options to configure team devices. For example:
-
Use
nmclito configure teams connections using the command line. - Use the RHEL web console to configure team connections using a web browser.
-
Use the
nm-connection-editorapplication to configure team connections in a graphical interface.
NIC teaming is deprecated in Red Hat Enterprise Linux 9. Consider using the network bonding driver as an alternative. For details, see Configuring a network bond.
4.1. Migrating a NIC team configuration to network bond
Network interface controller (NIC) teaming is deprecated in Red Hat Enterprise Linux 9. If you already have a working NIC team configured, for example because you upgraded from an earlier RHEL version, you can migrate the configuration to a network bond that is managed by NetworkManager.
The team2bond utility only converts the team configuration to a bond. Afterwards, you must manually configure further settings of the bond, such as IP addresses and DNS configuration.
Prerequisites
-
The
team-team0NetworkManager connection profile is configured and manages theteam0device. -
The
teamdpackage is installed.
Procedure
Optional: Display the IP configuration of the
team-team0NetworkManager connection:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the configuration of the
team0device to a JSON file:teamdctl team0 config dump actual > /tmp/team0.json
# teamdctl team0 config dump actual > /tmp/team0.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the NIC team. For example, if you configured the team in NetworkManager, remove the
team-team0connection profile and the profiles of associated ports:nmcli connection delete team-team0 nmcli connection delete team-team0-port1 nmcli connection delete team-team0-port2
# nmcli connection delete team-team0 # nmcli connection delete team-team0-port1 # nmcli connection delete team-team0-port2Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the
team2bondutility in dry-run mode to displaynmclicommands that set up a network bond with similar settings as the team device:team2bond --config=/tmp/team0.json --rename=bond0 nmcli con add type bond ifname bond0 bond.options "mode=active-backup,num_grat_arp=1,num_unsol_na=1,resend_igmp=1,miimon=100,miimon=100" nmcli con add type ethernet ifname enp7s0 controller bond0 nmcli con add type ethernet ifname enp8s0 controller bond0
# team2bond --config=/tmp/team0.json --rename=bond0 nmcli con add type bond ifname bond0 bond.options "mode=active-backup,num_grat_arp=1,num_unsol_na=1,resend_igmp=1,miimon=100,miimon=100" nmcli con add type ethernet ifname enp7s0 controller bond0 nmcli con add type ethernet ifname enp8s0 controller bond0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The first command contains two
miimonoptions because the team configuration file contained twolink_watchentries. Note that this does not affect the creation of the bond.If you bound services to the device name of the team and want to avoid updating or breaking these services, omit the
--rename=bond0option. In this case,team2bonduses the same interface name for the bond as for the team.-
Verify that the options for the bond the
team2bondutility suggested are correct. Create the bond. You can execute the suggested
nmclicommands or re-run theteam2bondcommand with the--exec-cmdoption:team2bond --config=/tmp/team0.json --rename=bond0 --exec-cmd Connection 'bond-bond0' (0241a531-0c72-4202-80df-73eadfc126b5) successfully added. Connection 'bond-port-enp7s0' (38489729-b624-4606-a784-1ccf01e2f6d6) successfully added. Connection 'bond-port-enp8s0' (de97ec06-7daa-4298-9a71-9d4c7909daa1) successfully added.
# team2bond --config=/tmp/team0.json --rename=bond0 --exec-cmd Connection 'bond-bond0' (0241a531-0c72-4202-80df-73eadfc126b5) successfully added. Connection 'bond-port-enp7s0' (38489729-b624-4606-a784-1ccf01e2f6d6) successfully added. Connection 'bond-port-enp8s0' (de97ec06-7daa-4298-9a71-9d4c7909daa1) successfully added.Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the name of the bond connection profile (
bond-bond0) in the next steps.Set the IPv4 settings that were previously configured on
team-team0to thebond-bond0connection:nmcli connection modify bond-bond0 ipv4.addresses '192.0.2.1/24' nmcli connection modify bond-bond0 ipv4.gateway '192.0.2.254' nmcli connection modify bond-bond0 ipv4.dns '192.0.2.253' nmcli connection modify bond-bond0 ipv4.dns-search 'example.com' nmcli connection modify bond-bond0 ipv4.method manual
# nmcli connection modify bond-bond0 ipv4.addresses '192.0.2.1/24' # nmcli connection modify bond-bond0 ipv4.gateway '192.0.2.254' # nmcli connection modify bond-bond0 ipv4.dns '192.0.2.253' # nmcli connection modify bond-bond0 ipv4.dns-search 'example.com' # nmcli connection modify bond-bond0 ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the IPv6 settings that were previously configured on
team-team0to thebond-bond0connection:nmcli connection modify bond-bond0 ipv6.addresses '2001:db8:1::1/64' nmcli connection modify bond-bond0 ipv6.gateway '2001:db8:1::fffe' nmcli connection modify bond-bond0 ipv6.dns '2001:db8:1::fffd' nmcli connection modify bond-bond0 ipv6.dns-search 'example.com' nmcli connection modify bond-bond0 ipv6.method manual
# nmcli connection modify bond-bond0 ipv6.addresses '2001:db8:1::1/64' # nmcli connection modify bond-bond0 ipv6.gateway '2001:db8:1::fffe' # nmcli connection modify bond-bond0 ipv6.dns '2001:db8:1::fffd' # nmcli connection modify bond-bond0 ipv6.dns-search 'example.com' # nmcli connection modify bond-bond0 ipv6.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow Activate the connection:
nmcli connection up bond-bond0
# nmcli connection up bond-bond0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IP configuration of the
bond-bond0NetworkManager connection:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the status of the bond:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, both ports are up.
To verify that bonding failover works:
- Temporarily remove the network cable from the host. Note that there is no method to properly test link failure events using the command line.
Display the status of the bond:
cat /proc/net/bonding/bond0
# cat /proc/net/bonding/bond0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.2. Understanding the default behavior of controller and port interfaces
Understanding the default behavior of NetworkManager when managing bond port interfaces helps you to troubleshoot problems more effectively.
Default behavior:
- Starting the controller interface does not automatically start the port interfaces.
- Starting a port interface always starts the controller interface.
- Stopping the controller interface also stops the port interface.
- A controller without ports can start static IP connections.
- A controller without ports waits for ports when starting DHCP connections.
- A controller with a DHCP connection waiting for ports completes when you add a port with a carrier.
- A controller with a DHCP connection waiting for ports continues waiting when you add a port without a carrier.
4.3. Understanding the teamd service, runners, and link-watchers
The team service, teamd, controls one instance of the team driver. This instance of the driver adds instances of a hardware device driver to form a team of network interfaces. The team driver presents a network interface, for example team0, to the kernel.
The teamd service implements the common logic to all methods of teaming. Those functions are unique to the different load sharing and backup methods, such as round-robin, and implemented by separate units of code referred to as runners. Administrators specify runners in JavaScript Object Notation (JSON) format, and the JSON code is compiled into an instance of teamd when the instance is created. Alternatively, when using NetworkManager, you can set the runner in the team.runner parameter, and NetworkManager auto-creates the corresponding JSON code.
The following runners are available:
-
broadcast: Transmits data over all ports. -
roundrobin: Transmits data over all ports in turn. -
activebackup: Transmits data over one port while the others are kept as a backup. -
loadbalance: Transmits data over all ports with active Tx load balancing and Berkeley Packet Filter (BPF)-based Tx port selectors. -
random: Transmits data on a randomly selected port. -
lacp: Implements the 802.3ad Link Aggregation Control Protocol (LACP).
The teamd services use a link watcher to monitor the state of subordinate devices. The following link-watchers are available:
-
ethtool: Thelibteamlibrary uses theethtoolutility to watch for link state changes. This is the default link-watcher. -
arp_ping: Thelibteamlibrary uses thearp_pingutility to monitor the presence of a far-end hardware address using Address Resolution Protocol (ARP). -
nsna_ping: On IPv6 connections, thelibteamlibrary uses the Neighbor Advertisement and Neighbor Solicitation features from the IPv6 Neighbor Discovery protocol to monitor the presence of a neighbor’s interface.
Each runner can use any link watcher, with the exception of lacp. This runner can only use the ethtool link watcher.
4.4. Configuring a NIC team by using nmcli
To configure a network interface controller (NIC) team on the command line, use the nmcli utility.
NIC teaming is deprecated in Red Hat Enterprise Linux 9. Consider using the network bonding driver as an alternative. For details, see Configuring a network bond.
Prerequisites
-
The
teamdandNetworkManager-teampackages are installed. - Two or more physical or virtual network devices are installed on the server.
- To use Ethernet devices as ports of the team, the physical or virtual Ethernet devices must be installed on the server and connected to a switch.
To use bond, bridge, or Virtual Local Area Network (VLAN) devices as ports of the team, you can either create these devices while you create the team or you can create them in advance as described in:
Procedure
Create a team interface:
nmcli connection add type team con-name team0 ifname team0 team.runner activebackup
# nmcli connection add type team con-name team0 ifname team0 team.runner activebackupCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates a NIC team named
team0that uses theactivebackuprunner.Optional: Set a link watcher. For example, to set the
ethtoollink watcher in theteam0connection profile:nmcli connection modify team0 team.link-watchers "name=ethtool"
# nmcli connection modify team0 team.link-watchers "name=ethtool"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Link watchers support different parameters. To set parameters for a link watcher, specify them space-separated in the
nameproperty. Note that the name property must be surrounded by quotation marks. For example, to use theethtoollink watcher and set itsdelay-upparameter to2500milliseconds (2.5 seconds):nmcli connection modify team0 team.link-watchers "name=ethtool delay-up=2500"
# nmcli connection modify team0 team.link-watchers "name=ethtool delay-up=2500"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To set multiple link watchers and each of them with specific parameters, the link watchers must be separated by a comma. The following example sets the
ethtoollink watcher with thedelay-upparameter and thearp_pinglink watcher with thesource-hostandtarget-hostparameter:nmcli connection modify team0 team.link-watchers "name=ethtool delay-up=2, name=arp_ping source-host=192.0.2.1 target-host=192.0.2.2"
# nmcli connection modify team0 team.link-watchers "name=ethtool delay-up=2, name=arp_ping source-host=192.0.2.1 target-host=192.0.2.2"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the network interfaces, and note the names of the interfaces you want to add to the team:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example:
-
enp7s0andenp8s0are not configured. To use these devices as ports, add connection profiles in the next step. Note that you can only use Ethernet interfaces in a team that are not assigned to any connection. -
bond0andbond1have existing connection profiles. To use these devices as ports, modify their profiles in the next step.
-
Assign the port interfaces to the team:
If the interfaces you want to assign to the team are not configured, create new connection profiles for them:
nmcli connection add type ethernet port-type team con-name team0-port1 ifname enp7s0 controller team0 nmcli connection add type ethernet port--type team con-name team0-port2 ifname enp8s0 controller team0
# nmcli connection add type ethernet port-type team con-name team0-port1 ifname enp7s0 controller team0 # nmcli connection add type ethernet port--type team con-name team0-port2 ifname enp8s0 controller team0Copy to Clipboard Copied! Toggle word wrap Toggle overflow These commands create profiles for
enp7s0andenp8s0, and add them to theteam0connection.To assign an existing connection profile to the team:
Set the
controllerparameter of these connections toteam0:nmcli connection modify bond0 controller team0 nmcli connection modify bond1 controller team0
# nmcli connection modify bond0 controller team0 # nmcli connection modify bond1 controller team0Copy to Clipboard Copied! Toggle word wrap Toggle overflow These commands assign the existing connection profiles named
bond0andbond1to theteam0connection.Reactivate the connections:
nmcli connection up bond0 nmcli connection up bond1
# nmcli connection up bond0 # nmcli connection up bond1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Configure the IPv4 settings:
To set a static IPv4 address, network mask, default gateway, and DNS server to the
team0connection, enter:nmcli connection modify team0 ipv4.addresses '192.0.2.1/24' ipv4.gateway '192.0.2.254' ipv4.dns '192.0.2.253' ipv4.dns-search 'example.com' ipv4.method manual
# nmcli connection modify team0 ipv4.addresses '192.0.2.1/24' ipv4.gateway '192.0.2.254' ipv4.dns '192.0.2.253' ipv4.dns-search 'example.com' ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To use DHCP, no action is required.
- If you plan to use this team device as a port of other devices, no action is required.
Configure the IPv6 settings:
To set a static IPv6 address, network mask, default gateway, and DNS server to the
team0connection, enter:nmcli connection modify team0 ipv6.addresses '2001:db8:1::1/64' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd' ipv6.dns-search 'example.com' ipv6.method manual
# nmcli connection modify team0 ipv6.addresses '2001:db8:1::1/64' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd' ipv6.dns-search 'example.com' ipv6.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If you plan to use this team device as a port of other devices, no action is required.
- To use stateless address autoconfiguration (SLAAC), no action is required.
Activate the connection:
nmcli connection up team0
# nmcli connection up team0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the status of the team:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, both ports are up.
4.5. Configuring a NIC team by using the RHEL web console
Use the RHEL web console to configure a network interface controller (NIC) team if you prefer to manage network settings using a web browser-based interface.
NIC teaming is deprecated in Red Hat Enterprise Linux 9. Consider using the network bonding driver as an alternative. For details, see Configuring a network bond.
Prerequisites
-
The
teamdandNetworkManager-teampackages are installed. - Two or more physical or virtual network devices are installed on the server.
- To use Ethernet devices as ports of the team, the physical or virtual Ethernet devices must be installed on the server and connected to a switch.
To use bond, bridge, or Virtual Local Area Network (VLAN) devices as ports of the team, create them in advance as described in:
- You have installed the RHEL 9 web console.
- You have enabled the cockpit service.
Your user account is allowed to log in to the web console.
For instructions, see Installing and enabling the web console.
Procedure
Log in to the RHEL 9 web console.
For details, see Logging in to the web console.
-
Select the
Networkingtab in the navigation on the left side of the screen. -
Click in the
Interfacessection. - Enter the name of the team device you want to create.
- Select the interfaces that should be ports of the team.
Select the runner of the team.
If you select
Load balancingor802.3ad LACP, the web console shows the additional fieldBalancer.Set the link watcher:
-
If you select
Ethtool, additionally, set a link up and link down delay. -
If you set
ARP pingorNSNA ping, additionally, set a ping interval and ping target.
-
If you select
- Click .
By default, the team uses a dynamic IP address. If you want to set a static IP address:
-
Click the name of the team in the
Interfacessection. -
Click
Editnext to the protocol you want to configure. -
Select
Manualnext toAddresses, and enter the IP address, prefix, and default gateway. -
In the
DNSsection, click the button, and enter the IP address of the DNS server. Repeat this step to set multiple DNS servers. -
In the
DNS search domainssection, click the button, and enter the search domain. -
If the interface requires static routes, configure them in the
Routessection. - Click
-
Click the name of the team in the
Verification
-
Select the
Networkingtab in the navigation on the left side of the screen, and check if there is incoming and outgoing traffic on the interface. Display the status of the team:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, both ports are up.
4.6. Configuring a NIC team by using nm-connection-editor
If you use Red Hat Enterprise Linux with a graphical interface, you can configure network interface controller (NIC) teams using the nm-connection-editor application.
Note that nm-connection-editor can add only new ports to a team. To use an existing connection profile as a port, create the team using the nmcli utility as described in Configuring a NIC team by using nmcli.
NIC teaming is deprecated in Red Hat Enterprise Linux 9. Consider using the network bonding driver as an alternative. For details, see Configuring a network bond.
Prerequisites
-
The
teamdandNetworkManager-teampackages are installed. - Two or more physical or virtual network devices are installed on the server.
- To use Ethernet devices as ports of the team, the physical or virtual Ethernet devices must be installed on the server.
- To use team, bond, or Virtual Local Area Network (VLAN) devices as ports of the team, ensure that these devices are not already configured.
Procedure
Open a terminal, and enter
nm-connection-editor:nm-connection-editor
$ nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Click the button to add a new connection.
- Select the Team connection type, and click .
On the Team tab:
- Optional: Set the name of the team interface in the Interface name field.
Click the button to add a new connection profile for a network interface and add the profile as a port to the team.
- Select the connection type of the interface. For example, select Ethernet for a wired connection.
- Optional: Set a connection name for the port.
- If you create a connection profile for an Ethernet device, open the Ethernet tab, and select in the Device field the network interface you want to add as a port to the team. If you selected a different device type, configure it accordingly. Note that you can only use Ethernet interfaces in a team that are not assigned to any connection.
- Click .
- Repeat the previous step for each interface you want to add to the team.
Click the button to set advanced options to the team connection.
- On the Runner tab, select the runner.
- On the Link Watcher tab, set the link watcher and its optional settings.
- Click .
Configure the IP address settings on both the IPv4 Settings and IPv6 Settings tabs:
- If you plan to use this bridge device as a port of other devices, set the Method field to Disabled.
- To use DHCP, leave the Method field at its default, Automatic (DHCP).
To use static IP settings, set the Method field to Manual and fill the fields accordingly:

- Click .
-
Close
nm-connection-editor.
Verification
Display the status of the team:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 5. Configuring VLAN tagging
A Virtual Local Area Network (VLAN) is a logical network within a physical network. The VLAN interface tags packets with the VLAN ID as they pass through the interface, and removes tags of returning packets.
You create VLAN interfaces on top of another interface, such as Ethernet, bond, or bridge devices. These interfaces are called the parent interface.
Red Hat Enterprise Linux provides administrators different options to configure VLAN devices. For example:
-
Use
nmclito configure VLAN tagging using the command line. - Use the RHEL web console to configure VLAN tagging using a web browser.
-
Use
nmtuito configure VLAN tagging in a text-based user interface. -
Use the
nm-connection-editorapplication to configure connections in a graphical interface. -
Use
nmstatectlto configure connections through the Nmstate API. - Use RHEL system roles to automate the VLAN configuration on one or multiple hosts.
5.1. Configuring VLAN tagging by using nmcli
You can configure Virtual Local Area Network (VLAN) tagging on the command line using the nmcli utility.
Prerequisites
- The interface you plan to use as a parent to the virtual VLAN interface supports VLAN tags.
If you configure the VLAN on top of a bond interface:
- The ports of the bond are up.
-
The bond is not configured with the
fail_over_mac=followoption. A VLAN virtual device cannot change its MAC address to match the parent’s new MAC address. In such a case, the traffic would still be sent with the incorrect source MAC address. -
The bond is usually not expected to get IP addresses from a DHCP server or IPv6 auto-configuration. Ensure it by setting the
ipv4.method=disableandipv6.method=ignoreoptions while creating the bond. Otherwise, if DHCP or IPv6 auto-configuration fails after some time, the interface might be brought down.
- The switch, the host is connected to, is configured to support VLAN tags. For details, see the documentation of your switch.
Procedure
Display the network interfaces:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the VLAN interface. For example, to create a VLAN interface named
vlan10that usesenp1s0as its parent interface and that tags packets with VLAN ID10, enter:nmcli connection add type vlan con-name vlan10 ifname vlan10 vlan.parent enp1s0 vlan.id 10
# nmcli connection add type vlan con-name vlan10 ifname vlan10 vlan.parent enp1s0 vlan.id 10Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the VLAN must be within the range from
0to4094.By default, the VLAN connection inherits the maximum transmission unit (MTU) from the parent interface. If you require a different MTU value, enter:
nmcli connection modify vlan10 ethernet.mtu 2000
# nmcli connection modify vlan10 ethernet.mtu 2000Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the IPv4 settings:
To set a static IPv4 address, network mask, default gateway, and DNS server to the
vlan10connection, enter:nmcli connection modify vlan10 ipv4.addresses '192.0.2.1/24' ipv4.gateway '192.0.2.254' ipv4.dns '192.0.2.253' ipv4.method manual
# nmcli connection modify vlan10 ipv4.addresses '192.0.2.1/24' ipv4.gateway '192.0.2.254' ipv4.dns '192.0.2.253' ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To use DHCP, no action is required.
- If you plan to use this VLAN device as a port of other devices, no action is required.
Configure the IPv6 settings:
To set a static IPv6 address, network mask, default gateway, and DNS server to the
vlan10connection, enter:nmcli connection modify vlan10 ipv6.addresses '2001:db8:1::1/32' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd' ipv6.method manual
# nmcli connection modify vlan10 ipv6.addresses '2001:db8:1::1/32' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd' ipv6.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To use stateless address autoconfiguration (SLAAC), no action is required.
- If you plan to use this VLAN device as a port of other devices, no action is required.
Activate the connection:
nmcli connection up vlan10
# nmcli connection up vlan10Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify the settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.2. Configuring nested VLANs by using nmcli
802.1ad is a protocol used for Virtual Local Area Network (VLAN) tagging. It is also known as Q-in-Q tagging. You can use this technology to create multiple VLAN tags within a single Ethernet frame.
Benefits of multiple VLAN tags within a single Ethernet frame:
- Increased network scalability by creating multiple isolated network segments within a VLAN. This enables you to segment and organize large networks into smaller, manageable units.
- Improved traffic management by isolating and controlling different types of network traffic. This can improve the network performance and reduce network congestion.
- Efficient resource utilization by enabling the creation of smaller, more targeted network segments.
- Enhanced security by isolating network traffic and reducing the risk of unauthorized access to sensitive data.
Prerequisites
- The interface you plan to use as a parent to the virtual VLAN interface supports VLAN tags.
If you configure the VLAN on top of a bond interface:
- The ports of the bond are up.
-
The bond is not configured with the
fail_over_mac=followoption. A VLAN virtual device cannot change its MAC address to match the parent’s new MAC address. In such a case, the traffic would still be sent with the incorrect source MAC address. -
The bond is usually not expected to get IP addresses from a DHCP server or IPv6 auto-configuration. Ensure it by setting the
ipv4.method=disableandipv6.method=ignoreoptions while creating the bond. Otherwise, if DHCP or IPv6 auto-configuration fails after some time, the interface might be brought down.
- The switch, the host is connected to, is configured to support VLAN tags. For details, see the documentation of your switch.
Procedure
Display the physical network devices:
nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet connected enp1s0 ...
# nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet connected enp1s0 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the base VLAN interface. For example, to create a base VLAN interface named
vlan10that usesenp1s0as its parent interface and that tags packets with VLAN ID10, enter:nmcli connection add type vlan con-name vlan10 dev enp1s0 vlan.id 10
# nmcli connection add type vlan con-name vlan10 dev enp1s0 vlan.id 10Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the VLAN must be within the range from
0to4094.By default, the VLAN connection inherits the maximum transmission unit (MTU) from the parent interface. If you require a different MTU value, enter:
nmcli connection modify vlan10 ethernet.mtu 2000
# nmcli connection modify vlan10 ethernet.mtu 2000Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the nested VLAN interface on top of the base VLAN interface:
nmcli connection add type vlan con-name vlan10.20 dev enp1s0.10 id 20 vlan.protocol 802.1ad
# nmcli connection add type vlan con-name vlan10.20 dev enp1s0.10 id 20 vlan.protocol 802.1adCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates a new VLAN connection with a name of
vlan10.20and a VLAN ID of20on the parent VLAN connectionvlan10. Thedevoption specifies the parent network device. In this case it isenp1s0.10. Thevlan.protocoloption specifies the VLAN encapsulation protocol. In this case it is802.1ad(Q-in-Q).Configure the IPv4 settings of the nested VLAN interface:
- To use DHCP, no action is required.
To set a static IPv4 address, network mask, default gateway, and DNS server to the
vlan10.20connection, enter:nmcli connection modify vlan10.20 ipv4.method manual ipv4.addresses 192.0.2.1/24 ipv4.gateway 192.0.2.254 ipv4.dns 192.0.2.200
# nmcli connection modify vlan10.20 ipv4.method manual ipv4.addresses 192.0.2.1/24 ipv4.gateway 192.0.2.254 ipv4.dns 192.0.2.200Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Configure the IPv6 settings of the nested VLAN interface:
- To use stateless address autoconfiguration (SLAAC), no action is required.
To set a static IPv6 address, network mask, default gateway, and DNS server to the vlan10 connection, enter:
nmcli connection modify bridge0 ipv6.addresses '2001:db8:1::1/64' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd' ipv6.dns-search 'example.com' ipv6.method manual
# nmcli connection modify bridge0 ipv6.addresses '2001:db8:1::1/64' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd' ipv6.dns-search 'example.com' ipv6.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Activate the profile:
nmcli connection up vlan10.20
# nmcli connection up vlan10.20Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify the configuration of the nested VLAN interface:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.3. Configuring VLAN tagging by using the RHEL web console
You can configure VLAN tagging if you prefer to manage network settings using a web browser-based interface in the RHEL web console.
Prerequisites
- The interface you plan to use as a parent to the virtual VLAN interface supports VLAN tags.
If you configure the VLAN on top of a bond interface:
- The ports of the bond are up.
-
The bond is not configured with the
fail_over_mac=followoption. A VLAN virtual device cannot change its MAC address to match the parent’s new MAC address. In such a case, the traffic would still be sent with the incorrect source MAC address. - The bond is usually not expected to get IP addresses from a DHCP server or IPv6 auto-configuration. Ensure it by disabling the IPv4 and IPv6 protocol creating the bond. Otherwise, if DHCP or IPv6 auto-configuration fails after some time, the interface might be brought down.
- The switch, the host is connected to, is configured to support VLAN tags. For details, see the documentation of your switch.
- You have installed the RHEL 9 web console.
- You have enabled the cockpit service.
Your user account is allowed to log in to the web console.
For instructions, see Installing and enabling the web console.
Procedure
Log in to the RHEL 9 web console.
For details, see Logging in to the web console.
-
Select the
Networkingtab in the navigation on the left side of the screen. -
Click in the
Interfacessection. - Select the parent device.
- Enter the VLAN ID.
- Enter the name of the VLAN device or keep the automatically-generated name.
- Click .
By default, the VLAN device uses a dynamic IP address. If you want to set a static IP address:
-
Click the name of the VLAN device in the
Interfacessection. -
Click
Editnext to the protocol you want to configure. -
Select
Manualnext toAddresses, and enter the IP address, prefix, and default gateway. -
In the
DNSsection, click the button, and enter the IP address of the DNS server. Repeat this step to set multiple DNS servers. -
In the
DNS search domainssection, click the button, and enter the search domain. -
If the interface requires static routes, configure them in the
Routessection. - Click
-
Click the name of the VLAN device in the
Verification
-
Select the
Networkingtab in the navigation on the left side of the screen, and check if there is incoming and outgoing traffic on the interface.
5.4. Configuring VLAN tagging by using nmtui
The nmtui application provides a text-based user interface for NetworkManager. You can use nmtui to configure VLAN tagging on a host without a graphical interface.
In nmtui:
- Navigate by using the cursor keys.
- Press a button by selecting it and hitting Enter.
- Select and clear checkboxes by using Space.
- To return to the previous screen, use ESC.
Prerequisites
- The interface you plan to use as a parent to the virtual VLAN interface supports VLAN tags.
If you configure the VLAN on top of a bond interface:
- The ports of the bond are up.
-
The bond is not configured with the
fail_over_mac=followoption. A VLAN virtual device cannot change its MAC address to match the parent’s new MAC address. In such a case, the traffic would still be sent with the then incorrect source MAC address. -
The bond is usually not expected to get IP addresses from a DHCP server or IPv6 auto-configuration. Ensure it by setting the
ipv4.method=disableandipv6.method=ignoreoptions while creating the bond. Otherwise, if DHCP or IPv6 auto-configuration fails after some time, the interface might be brought down.
- The switch the host is connected to is configured to support VLAN tags. For details, see the documentation of your switch.
Procedure
If you do not know the network device name on which you want configure VLAN tagging, display the available devices:
nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet unavailable -- ...
# nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet unavailable -- ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Start
nmtui:nmtui
# nmtuiCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Select Edit a connection, and press Enter.
- Press Add.
- Select VLAN from the list of network types, and press Enter.
Optional: Enter a name for the NetworkManager profile to be created.
On hosts with multiple profiles, a meaningful name makes it easier to identify the purpose of a profile.
- Enter the VLAN device name to be created into the Device field.
- Enter the name of the device on which you want to configure VLAN tagging into the Parent field.
-
Enter the VLAN ID. The ID must be within the range from
0to4094. Depending on your environment, configure the IP address settings in the IPv4 configuration and IPv6 configuration areas accordingly. For this, press the button next to these areas, and select:
-
Disabled, if this VLAN device does not require an IP address or you want to use it as a port of other devices. -
Automatic, if a DHCP server or stateless address autoconfiguration (SLAAC) dynamically assigns an IP address to the VLAN device. Manual, if the network requires static IP address settings. In this case, you must fill further fields:- Press Show next to the protocol you want to configure to display additional fields.
Press Add next to Addresses, and enter the IP address and the subnet mask in Classless Inter-Domain Routing (CIDR) format.
If you do not specify a subnet mask, NetworkManager sets a
/32subnet mask for IPv4 addresses and/64for IPv6 addresses.- Enter the address of the default gateway.
- Press Add next to DNS servers, and enter the DNS server address.
- Press Add next to Search domains, and enter the DNS search domain.
-
- Press OK to create and automatically activate the new connection.
- Press Back to return to the main menu.
-
Select Quit, and press Enter to close the
nmtuiapplication.
Verification
Verify the settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.5. Configuring VLAN tagging by using nm-connection-editor
You can configure Virtual Local Area Network (VLAN) tagging in a graphical interface using the nm-connection-editor application.
Prerequisites
- The interface you plan to use as a parent to the virtual VLAN interface supports VLAN tags.
If you configure the VLAN on top of a bond interface:
- The ports of the bond are up.
-
The bond is not configured with the
fail_over_mac=followoption. A VLAN virtual device cannot change its MAC address to match the parent’s new MAC address. In such a case, the traffic would still be sent with the incorrect source MAC address.
- The switch, the host is connected to, is configured to support VLAN tags. For details, see the documentation of your switch.
Procedure
Open a terminal, and enter
nm-connection-editor:nm-connection-editor
$ nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Click the button to add a new connection.
- Select the VLAN connection type, and click .
On the VLAN tab:
- Select the parent interface.
- Select the VLAN id. Note that the VLAN must be within the range from 0 to 4094.
- By default, the VLAN connection inherits the maximum transmission unit (MTU) from the parent interface. If you require a different MTU value, enter:
- Optional: Set the name of the VLAN interface and further VLAN-specific options.
Configure the IP address settings on both the IPv4 Settings and IPv6 Settings tabs:
- If you plan to use this bridge device as a port of other devices, set the Method field to Disabled.
- To use DHCP, leave the Method field at its default, Automatic (DHCP).
To use static IP settings, set the Method field to Manual and fill the fields accordingly:
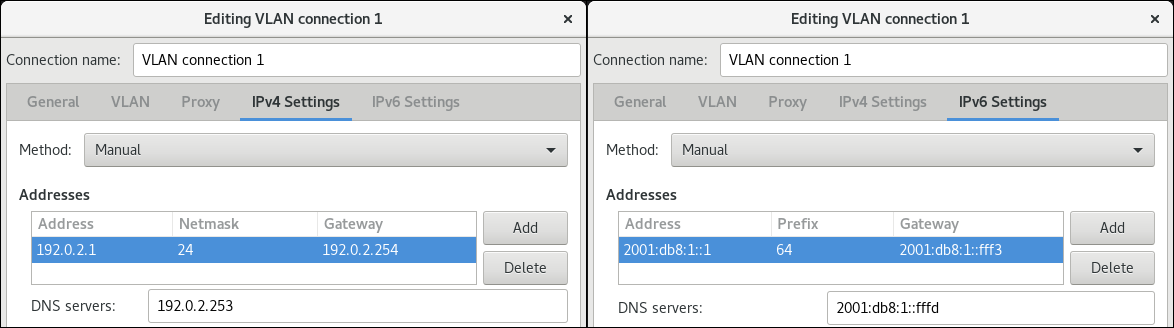
- Click .
-
Close
nm-connection-editor.
Verification
Verify the settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.6. Configuring VLAN tagging by using nmstatectl
You can use the declarative Nmstate API to configure a Virtual Local Area Network VLAN. Nmstate ensures that the result matches the configuration file or rolls back the changes.
Depending on your environment, adjust the YAML file accordingly. For example, to use different devices than Ethernet adapters in the VLAN, adapt the base-iface attribute and type attributes of the ports you use in the VLAN.
Prerequisites
- To use Ethernet devices as ports in the VLAN, the physical or virtual Ethernet devices must be installed on the server.
-
The
nmstatepackage is installed.
Procedure
Create a YAML file, for example
~/create-vlan.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow These settings define a VLAN with ID 10 that uses the
enp1s0device. As the child device, the VLAN connection has the following settings:-
A static IPv4 address -
192.0.2.1with the/24subnet mask -
A static IPv6 address -
2001:db8:1::1with the/64subnet mask -
An IPv4 default gateway -
192.0.2.254 -
An IPv6 default gateway -
2001:db8:1::fffe -
An IPv4 DNS server -
192.0.2.200 -
An IPv6 DNS server -
2001:db8:1::ffbb -
A DNS search domain -
example.com
-
A static IPv4 address -
Apply the settings to the system:
nmstatectl apply ~/create-vlan.yml
# nmstatectl apply ~/create-vlan.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the status of the devices and connections:
nmcli device status DEVICE TYPE STATE CONNECTION vlan10 vlan connected vlan10
# nmcli device status DEVICE TYPE STATE CONNECTION vlan10 vlan connected vlan10Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display all settings of the connection profile:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the connection settings in YAML format:
nmstatectl show vlan10
# nmstatectl show vlan10Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.7. Configuring VLAN tagging by using the network RHEL system role
You can use the network RHEL system role to configure VLAN tagging and, if a connection profile for the VLAN’s parent device does not exist, the role can create it as well.
If your network uses Virtual Local Area Networks (VLANs) to separate network traffic into logical networks, create a NetworkManager connection profile to configure VLAN tagging. By using Ansible and the network RHEL system role, you can automate this process and remotely configure connection profiles on the hosts defined in a playbook.
If the VLAN device requires an IP address, default gateway, and DNS settings, configure them on the VLAN device and not on the parent device.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
type: <profile_type>- Sets the type of the profile to create. The example playbook creates two connection profiles: One for the parent Ethernet device and one for the VLAN device.
dhcp4: <value>-
If set to
yes, automatic IPv4 address assignment from DHCP, PPP, or similar services is enabled. Disable the IP address configuration on the parent device. auto6: <value>-
If set to
yes, IPv6 auto-configuration is enabled. In this case, by default, NetworkManager uses Router Advertisements and, if the router announces themanagedflag, NetworkManager requests an IPv6 address and prefix from a DHCPv6 server. Disable the IP address configuration on the parent device. parent: <parent_device>- Sets the parent device of the VLAN connection profile. In the example, the parent is the Ethernet interface.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify the VLAN settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 6. Configuring a network bridge
A network bridge is a link-layer device that forwards traffic between networks by using a MAC address table. For example, you can use a software bridge to connect virtual machines to the same network as the host.
A bridge requires a network device in each network the bridge should connect. When you configure a bridge, the bridge is called controller and the devices it uses ports.
You can create bridges on different types of devices, such as:
- Physical and virtual Ethernet devices
- Network bonds
- Network teams
- Virtual Local Area Network (VLAN) devices
Due to the IEEE 802.11 standard which specifies the use of 3-address frames in Wi-Fi for the efficient use of airtime, you cannot configure a bridge over Wi-Fi networks operating in Ad-Hoc or Infrastructure modes.
6.1. Configuring a network bridge by using nmcli
To configure a network bridge on the command line, use the nmcli utility.
Prerequisites
- Two or more physical or virtual network devices are installed on the server.
-
The host runs on Red Hat Enterprise Linux 9.4 or later. This version introduced the
port-type,controller,connection.autoconnect-portsoptions used in this procedure. Previous RHEL versions instead useslave-type,master, andconnection.autoconnect-slaves. - To use Ethernet devices as ports of the bridge, the physical or virtual Ethernet devices must be installed on the server.
To use team, bond, or Virtual Local Area Network (VLAN) devices as ports of the bridge, you can either create these devices while you create the bridge or you can create them in advance as described in:
Procedure
Create a bridge interface:
nmcli connection add type bridge con-name bridge0 ifname bridge0
# nmcli connection add type bridge con-name bridge0 ifname bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates a bridge named
bridge0.Display the network interfaces, and note the names of the interfaces you want to add to the bridge:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example:
-
enp7s0andenp8s0are not configured. To use these devices as ports, add connection profiles in the next step. -
bond0andbond1have existing connection profiles. To use these devices as ports, modify their profiles in the next step.
-
Assign the interfaces to the bridge.
If the interfaces you want to assign to the bridge are not configured, create new connection profiles for them:
nmcli connection add type ethernet port-type bridge con-name bridge0-port1 ifname enp7s0 controller bridge0 nmcli connection add type ethernet port-type bridge con-name bridge0-port2 ifname enp8s0 controller bridge0
# nmcli connection add type ethernet port-type bridge con-name bridge0-port1 ifname enp7s0 controller bridge0 # nmcli connection add type ethernet port-type bridge con-name bridge0-port2 ifname enp8s0 controller bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow These commands create profiles for
enp7s0andenp8s0, and add them to thebridge0connection.If you want to assign an existing connection profile to the bridge:
Set the
controllerparameter of these connections tobridge0:nmcli connection modify bond0 controller bridge0 nmcli connection modify bond1 controller bridge0
# nmcli connection modify bond0 controller bridge0 # nmcli connection modify bond1 controller bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow These commands assign the existing connection profiles named
bond0andbond1to thebridge0connection.Reactivate the connections:
nmcli connection up bond0 nmcli connection up bond1
# nmcli connection up bond0 # nmcli connection up bond1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Configure the IPv4 settings:
To set a static IPv4 address, network mask, default gateway, and DNS server to the
bridge0connection, enter:nmcli connection modify bridge0 ipv4.addresses '192.0.2.1/24' ipv4.gateway '192.0.2.254' ipv4.dns '192.0.2.253' ipv4.dns-search 'example.com' ipv4.method manual
# nmcli connection modify bridge0 ipv4.addresses '192.0.2.1/24' ipv4.gateway '192.0.2.254' ipv4.dns '192.0.2.253' ipv4.dns-search 'example.com' ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To use DHCP, no action is required.
- If you plan to use this bridge device as a port of other devices, no action is required.
Configure the IPv6 settings:
To set a static IPv6 address, network mask, default gateway, and DNS server to the
bridge0connection, enter:nmcli connection modify bridge0 ipv6.addresses '2001:db8:1::1/64' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd' ipv6.dns-search 'example.com' ipv6.method manual
# nmcli connection modify bridge0 ipv6.addresses '2001:db8:1::1/64' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd' ipv6.dns-search 'example.com' ipv6.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To use stateless address autoconfiguration (SLAAC), no action is required.
- If you plan to use this bridge device as a port of other devices, no action is required.
Optional: Configure further properties of the bridge. For example, to set the Spanning Tree Protocol (STP) priority of
bridge0to16384, enter:nmcli connection modify bridge0 bridge.priority '16384'
# nmcli connection modify bridge0 bridge.priority '16384'Copy to Clipboard Copied! Toggle word wrap Toggle overflow By default, STP is enabled.
Activate the connection:
nmcli connection up bridge0
# nmcli connection up bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the ports are connected, and the
CONNECTIONcolumn displays the port’s connection name:nmcli device DEVICE TYPE STATE CONNECTION ... enp7s0 ethernet connected bridge0-port1 enp8s0 ethernet connected bridge0-port2
# nmcli device DEVICE TYPE STATE CONNECTION ... enp7s0 ethernet connected bridge0-port1 enp8s0 ethernet connected bridge0-port2Copy to Clipboard Copied! Toggle word wrap Toggle overflow When you activate any port of the connection, NetworkManager also activates the bridge, but not the other ports of it. You can configure that Red Hat Enterprise Linux enables all ports automatically when the bridge is enabled:
Enable the
connection.autoconnect-portsparameter of the bridge connection:nmcli connection modify bridge0 connection.autoconnect-ports 1
# nmcli connection modify bridge0 connection.autoconnect-ports 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Reactivate the bridge:
nmcli connection up bridge0
# nmcli connection up bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Use the
iputility to display the link status of Ethernet devices that are ports of a specific bridge:ip link show master bridge0 3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:62:61:0e brd ff:ff:ff:ff:ff:ff 4: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:9e:f1:ce brd ff:ff:ff:ff:ff:ff# ip link show master bridge0 3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:62:61:0e brd ff:ff:ff:ff:ff:ff 4: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:9e:f1:ce brd ff:ff:ff:ff:ff:ffCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
bridgeutility to display the status of Ethernet devices that are ports of any bridge device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the status for a specific Ethernet device, use the
bridge link show dev <ethernet_device_name>command.
6.2. Configuring a network bridge by using the RHEL web console
Use the RHEL web console to configure a network bridge if you prefer to manage network settings using a web browser-based interface.
Prerequisites
- Two or more physical or virtual network devices are installed on the server.
- To use Ethernet devices as ports of the bridge, the physical or virtual Ethernet devices must be installed on the server.
To use team, bond, or Virtual Local Area Network (VLAN) devices as ports of the bridge, you can either create these devices while you create the bridge or you can create them in advance as described in:
- You have installed the RHEL 9 web console.
- You have enabled the cockpit service.
Your user account is allowed to log in to the web console.
For instructions, see Installing and enabling the web console.
Procedure
Log in to the RHEL 9 web console.
For details, see Logging in to the web console.
- Select the Networking tab in the navigation on the left side of the screen.
- Click in the Interfaces section.
- Enter the name of the bridge device you want to create.
- Select the interfaces that should be ports of the bridge.
- Optional: Enable the Spanning tree protocol (STP) feature to avoid bridge loops and broadcast radiation.
- Click .
By default, the bridge uses a dynamic IP address. If you want to set a static IP address:
- Click the name of the bridge in the Interfaces section.
- Click Edit next to the protocol you want to configure.
- Select Manual next to Addresses, and enter the IP address, prefix, and default gateway.
- In the DNS section, click the button, and enter the IP address of the DNS server. Repeat this step to set multiple DNS servers.
- In the DNS search domains section, click the button, and enter the search domain.
- If the interface requires static routes, configure them in the Routes section.
- Click
Verification
- Select the Networking tab in the navigation on the left side of the screen, and check if there is incoming and outgoing traffic on the interface.
6.3. Configuring a network bridge by using nmtui
The nmtui application provides a text-based user interface for NetworkManager. You can use nmtui to configure a network bridge on a host without a graphical interface.
In nmtui:
- Navigate by using the cursor keys.
- Press a button by selecting it and hitting Enter.
- Select and clear checkboxes by using Space.
- To return to the previous screen, use ESC.
Prerequisites
- Two or more physical or virtual network devices are installed on the server.
- To use Ethernet devices as ports of the bridge, the physical or virtual Ethernet devices must be installed on the server.
Procedure
If you do not know the network device names on which you want configure a network bridge, display the available devices:
nmcli device status DEVICE TYPE STATE CONNECTION enp7s0 ethernet unavailable -- enp8s0 ethernet unavailable -- ...
# nmcli device status DEVICE TYPE STATE CONNECTION enp7s0 ethernet unavailable -- enp8s0 ethernet unavailable -- ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Start
nmtui:nmtui
# nmtuiCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Select
Edit a connection, and press Enter. -
Press
Add. -
Select
Bridgefrom the list of network types, and press Enter. Optional: Enter a name for the NetworkManager profile to be created.
On hosts with multiple profiles, a meaningful name makes it easier to identify the purpose of a profile.
-
Enter the bridge device name to be created into the
Devicefield. Add ports to the bridge to be created:
-
Press
Addnext to thePortslist. -
Select the type of the interface you want to add as a port to the bridge, for example,
Ethernet. - Optional: Enter a name for the NetworkManager profile to be created for this bridge port.
-
Enter the port’s device name into the
Devicefield. -
Press
OKto return to the window with the bridge settings. - Repeat these steps to add more ports to the bridge.
-
Press
Depending on your environment, configure the IP address settings in the
IPv4 configurationandIPv6 configurationareas accordingly. For this, press the button next to these areas, and select:-
Disabled, if the bridge does not require an IP address. -
Automatic, if a DHCP server or stateless address autoconfiguration (SLAAC) dynamically assigns an IP address to the bridge. Manual, if the network requires static IP address settings. In this case, you must fill further fields:-
Press
Shownext to the protocol you want to configure to display additional fields. Press
Addnext toAddresses, and enter the IP address and the subnet mask in Classless Inter-Domain Routing (CIDR) format.If you do not specify a subnet mask, NetworkManager sets a
/32subnet mask for IPv4 addresses and/64for IPv6 addresses.- Enter the address of the default gateway.
-
Press
Addnext toDNS servers, and enter the DNS server address. -
Press
Addnext toSearch domains, and enter the DNS search domain.
-
Press
-
-
Press
OKto create and automatically activate the new connection. -
Press
Backto return to the main menu. -
Select
Quit, and press Enter to close thenmtuiapplication.
Verification
Use the
iputility to display the link status of Ethernet devices that are ports of a specific bridge:ip link show master bridge0 3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:62:61:0e brd ff:ff:ff:ff:ff:ff 4: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:9e:f1:ce brd ff:ff:ff:ff:ff:ff# ip link show master bridge0 3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:62:61:0e brd ff:ff:ff:ff:ff:ff 4: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:9e:f1:ce brd ff:ff:ff:ff:ff:ffCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
bridgeutility to display the status of Ethernet devices that are ports of any bridge device:bridge link show 3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master bridge0 state forwarding priority 32 cost 100 4: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master bridge0 state listening priority 32 cost 100 ...
# bridge link show 3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master bridge0 state forwarding priority 32 cost 100 4: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master bridge0 state listening priority 32 cost 100 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the status for a specific Ethernet device, use the
bridge link show dev <ethernet_device_name>command.
6.4. Configuring a network bridge by using nm-connection-editor
If you use Red Hat Enterprise Linux with a graphical interface, you can configure network bridges using the nm-connection-editor application.
Note that nm-connection-editor can add only new ports to a bridge. To use an existing connection profile as a port, create the bridge using the nmcli utility as described in Configuring a network bridge by using nmcli.
Prerequisites
- Two or more physical or virtual network devices are installed on the server.
- To use Ethernet devices as ports of the bridge, the physical or virtual Ethernet devices must be installed on the server.
- To use team, bond, or Virtual Local Area Network (VLAN) devices as ports of the bridge, ensure that these devices are not already configured.
Procedure
Open a terminal, and enter
nm-connection-editor:nm-connection-editor
$ nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Click the button to add a new connection.
- Select the Bridge connection type, and click .
On the Bridge tab:
- Optional: Set the name of the bridge interface in the Interface name field.
Click the button to create a new connection profile for a network interface and add the profile as a port to the bridge.
- Select the connection type of the interface. For example, select Ethernet for a wired connection.
- Optional: Set a connection name for the port device.
- If you create a connection profile for an Ethernet device, open the Ethernet tab, and select in the Device field the network interface you want to add as a port to the bridge. If you selected a different device type, configure it accordingly.
- Click .
- Repeat the previous step for each interface you want to add to the bridge.
- Optional: Configure further bridge settings, such as Spanning Tree Protocol (STP) options.
Configure the IP address settings on both the IPv4 Settings and IPv6 Settings tabs:
- If you plan to use this bridge device as a port of other devices, set the Method field to Disabled.
- To use DHCP, leave the Method field at its default, Automatic (DHCP).
To use static IP settings, set the Method field to Manual and fill the fields accordingly:
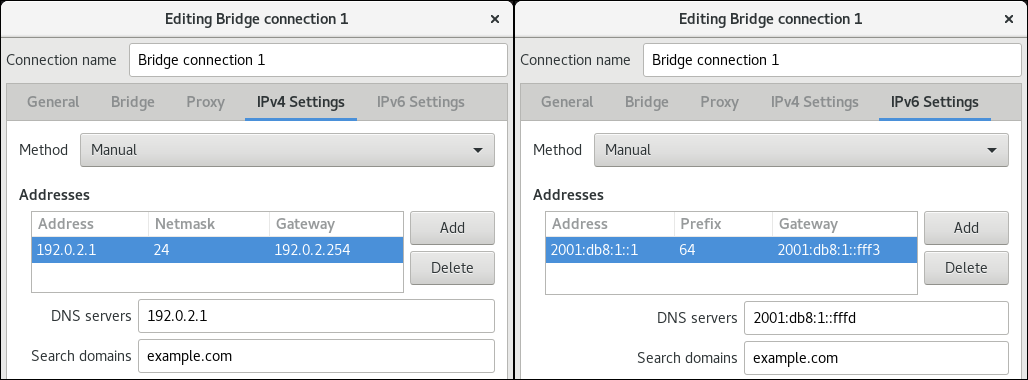
- Click .
-
Close
nm-connection-editor.
Verification
Use the
iputility to display the link status of Ethernet devices that are ports of a specific bridge.ip link show master bridge0 3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:62:61:0e brd ff:ff:ff:ff:ff:ff 4: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:9e:f1:ce brd ff:ff:ff:ff:ff:ff# ip link show master bridge0 3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:62:61:0e brd ff:ff:ff:ff:ff:ff 4: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master bridge0 state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:9e:f1:ce brd ff:ff:ff:ff:ff:ffCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
bridgeutility to display the status of Ethernet devices that are ports in any bridge device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the status for a specific Ethernet device, use the
bridge link show dev ethernet_device_namecommand.
6.5. Configuring a network bridge by using nmstatectl
You can use the declarative Nmstate API to configure a network bridge. Nmstate ensures that the result matches the configuration file or rolls back the changes.
Depending on your environment, adjust the YAML file accordingly. For example, to use different devices than Ethernet adapters in the bridge, adapt the base-iface attribute and type attributes of the ports you use in the bridge.
Prerequisites
- Two or more physical or virtual network devices are installed on the server.
- To use Ethernet devices as ports in the bridge, the physical or virtual Ethernet devices must be installed on the server.
-
To use team, bond, or Virtual Local Area Network (VLAN) devices as ports in the bridge, set the interface name in the
portlist, and define the corresponding interfaces. -
The
nmstatepackage is installed.
Procedure
Create a YAML file, for example
~/create-bridge.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow These settings define a network bridge with the following settings:
-
Network interfaces in the bridge:
enp1s0andenp7s0 - Spanning Tree Protocol (STP): Enabled
-
Static IPv4 address:
192.0.2.1with the/24subnet mask -
Static IPv6 address:
2001:db8:1::1with the/64subnet mask -
IPv4 default gateway:
192.0.2.254 -
IPv6 default gateway:
2001:db8:1::fffe -
IPv4 DNS server:
192.0.2.200 -
IPv6 DNS server:
2001:db8:1::ffbb -
DNS search domain:
example.com
-
Network interfaces in the bridge:
Apply the settings to the system:
nmstatectl apply ~/create-bridge.yml
# nmstatectl apply ~/create-bridge.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the status of the devices and connections:
nmcli device status DEVICE TYPE STATE CONNECTION bridge0 bridge connected bridge0
# nmcli device status DEVICE TYPE STATE CONNECTION bridge0 bridge connected bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display all settings of the connection profile:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the connection settings in YAML format:
nmstatectl show bridge0
# nmstatectl show bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.6. Configuring a network bridge by using the network RHEL system role
You can use the network RHEL system role to configure a bridge and, if a connection profile for the bridge’s parent device does not exist, the role can create it as well.
You can connect multiple networks on layer 2 of the Open Systems Interconnection (OSI) model by creating a network bridge. To configure a bridge, create a connection profile in NetworkManager. By using Ansible and the network RHEL system role, you can automate this process and remotely configure connection profiles on the hosts defined in a playbook.
If you want to assign IP addresses, gateways, and DNS settings to a bridge, configure them on the bridge and not on its ports.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. - Two or more physical or virtual network devices are installed on the server.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
type: <profile_type>- Sets the type of the profile to create. The example playbook creates three connection profiles: One for the bridge and two for the Ethernet devices.
dhcp4: yes- Enables automatic IPv4 address assignment from DHCP, PPP, or similar services.
auto6: yes-
Enables IPv6 auto-configuration. By default, NetworkManager uses Router Advertisements. If the router announces the
managedflag, NetworkManager requests an IPv6 address and prefix from a DHCPv6 server.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the link status of Ethernet devices that are ports of a specific bridge:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the status of Ethernet devices that are ports of any bridge device:
ansible managed-node-01.example.com -m command -a 'bridge link show' managed-node-01.example.com | CHANGED | rc=0 >> 3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master bridge0 state forwarding priority 32 cost 100 4: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master bridge0 state listening priority 32 cost 100
# ansible managed-node-01.example.com -m command -a 'bridge link show' managed-node-01.example.com | CHANGED | rc=0 >> 3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master bridge0 state forwarding priority 32 cost 100 4: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master bridge0 state listening priority 32 cost 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 7. Setting up an IPsec VPN
Configure and manage a secure Virtual Private Network (VPN) by using the Libreswan implementation of the IPsec protocol suite to create encrypted tunnels for secure data transmission over the internet.
IPsec tunnels ensure the confidentiality and integrity of data in transit. Common use cases include connecting branch offices to headquarters or providing remote users with secure access to a corporate network.
RHEL provides different options to configure Libreswan:
- Manually edit the Libreswan configuration files for granular control over advanced options.
-
Use the
vpnRHEL system role to automate the process of creating Libreswan VPN configurations. - Use Nmstate to configure a Libreswan connection through a declarative API.
Libreswan does not use terms such as "client" and "server". Instead, IPsec refers to endpoints as "left" and "right". This design often enables you to use the same configuration on both hosts because Libreswan dynamically determines which role to adopt. As a convention, administrators typically use "left" for the local host and "right" for the remote host.
Libreswan is the only supported VPN technology in RHEL.
IPsec relies on standardized protocols, such as Internet Key Exchange (IKE), to ensure that different systems can communicate effectively. However, in practice, minor differences in how vendors implement these standards can lead to compatibility problems. If you encounter such interoperability issues when connecting Libreswan to a third-party IPsec peer, contact Red Hat Support.
7.1. Components in an IPsec VPN
Before setting up an IPsec VPN, it is important to understand its main components: Internet Key Exchange (IKE) for authentication and negotiation, and IPsec for data encryption and transport.
IKE is the protocol two endpoints use to authenticate each other and negotiate connection rules, including encryption algorithms. Libreswan implements IKE in a daemon called pluto.
IPsec is the part of the protocol that actually encrypts and transports data according to the policy agreed upon during the IKE negotiation. The Linux kernel implements the IPsec protocol suite.
7.2. Libreswan authentication methods
Select the appropriate authentication method to establish a secure VPN connection based on your security needs and network environment.
Libreswan supports the following authentication methods:
- Pre-Shared key
- The Pre-Shared Key (PSK) method involves both endpoints by using the same secret to authenticate each other. PSKs offer simplicity and broad compatibility, making them suitable for small-scale deployments. However, managing PSKs is risky if the key is reused or not rotated frequently. For security, PSKs should consist of more than 64 random characters and must meet FIPS strength requirements if your host operates in FIPS mode.
- Raw RSA key
- This method uses an RSA public and private key pair on each peer for mutual identification. Raw RSA keys provide stronger security than PSKs and are ideal for environments where a full certificate infrastructure is not required.
- X.509 certificates
- This method uses X.509 certificates issued by a trusted Certificate Authority (CA). Each peer proves its identity by using its certificate and private key, which the other peer verifies against the trusted CA. While providing the highest level of security and scalability for large enterprises, this method is more complex as it requires deploying and maintaining a public key infrastructure (PKI).
- NULL authentication
- This method provides only encryption with no authentication between peers. Because it does not verify the identity of the remote endpoint, NULL authentication is insecure and offers no protection against man-in-the-middle attacks.
- Protection against quantum computers
- While not a standalone authentication method, Libreswan offers Post-quantum Pre-shared Keys (PPKs) to protect modern IKEv2 connections from future attacks by quantum computers. This feature is necessary because neither the older IKEv1 protocol nor standard IKEv2 is inherently quantum-resistant on its own. A PPK adds another layer of security on top of the primary authentication method, and its security relies on using a cryptographically strong key that has been distributed securely through an external communication channel.
7.3. Manually configuring an IPsec host-to-host VPN with raw RSA key authentication
A host-to-host VPN establishes a direct, secure, and encrypted connection between two devices, allowing applications to communicate safely over an insecure network, such as the internet.
For authentication, RSA keys are more secure than pre-shared keys (PSKs) because their asymmetric encryption eliminates the risk of a shared secret. Using RSA keys also simplifies deployment by avoiding the need for a certificate authority (CA), while still providing strong peer-to-peer authentication.
Perform the steps on both hosts.
Procedure
If Libreswan is not yet installed, perform the following steps:
Install the
libreswanpackage:dnf install libreswan
# dnf install libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Enable and start the
ipsecservice:systemctl enable --now ipsec
# systemctl enable --now ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow Open the IPsec ports and protocols in the firewall:
firewall-cmd --permanent --add-service="ipsec" firewall-cmd --reload
# firewall-cmd --permanent --add-service="ipsec" # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an RSA key pair:
ipsec newhostkey
# ipsec newhostkeyCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
ipsecutility stores the key pair in the NSS database.- Designate your peers. In an IPsec tunnel, you must designate one host as left and the other as right. This is an arbitrary choice. A common practice is to call your local host left and the remote host right.
Display the Certificate Key Attribute ID (CKAID) on both the left and right peer:
ipsec showhostkey --list < 1> RSA keyid: <key_id> ckaid: <ckaid>
# ipsec showhostkey --list < 1> RSA keyid: <key_id> ckaid: <ckaid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the CKAIDs of both peers in the next steps.
Display the public keys:
On the left peer, enter:
ipsec showhostkey --left --ckaid <ckaid_of_left_peer> # rsakey AwEAAdKCx leftrsasigkey=0sAwEAAdKCxpc9db48cehzQiQD...
# ipsec showhostkey --left --ckaid <ckaid_of_left_peer> # rsakey AwEAAdKCx leftrsasigkey=0sAwEAAdKCxpc9db48cehzQiQD...Copy to Clipboard Copied! Toggle word wrap Toggle overflow On the right peer, enter:
ipsec showhostkey --right --ckaid <ckaid_of_right_peer> # rsakey AwEAAcNWC rightrsasigkey=0sAwEAAcNWCzZO+PR1j8WbO8X...
# ipsec showhostkey --right --ckaid <ckaid_of_right_peer> # rsakey AwEAAcNWC rightrsasigkey=0sAwEAAcNWCzZO+PR1j8WbO8X...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The commands display the public keys with the corresponding parameters that you must use in the configuration file.
Create a
.conffile for the connection in the/etc/ipsec.d/directory. For example, create the/etc/ipsec.d/host-to-host.conffile with the following settings:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou can use the same configuration file on both hosts, and Libreswan identifies whether it is operating on the left or right host by using internal information. However, it is important that all values in
left*parameters belong to one peer and the values inright*parameters belong to the other.The settings specified in the example include the following:
conn <connection_name>- Defines the connection name. The name is arbitrary, and Libreswan uses it to identify the connection. You must indent parameters in this connection by at least one space or tab.
auto=<type>-
Controls how the connection is initiated. If you set the value to
start, Libreswan activates the connection automatically when the service starts. authby=rsasig- Enables RSA signature authentication for this connection.
left=<ip_address_or_fqdn_of_left_peer>andright=<ip_address_or_fqdn_of_right_peer>- Defines the IP address or DNS name of the peers.
leftid=<id>andrightid=<id>-
Defines how each peer is identified during the Internet Key Exchange (IKE) negotiation process. This can be a fully-qualified domain name (FQDN), an IP address, or a literal string. In the latter case, precede the string with an
@sign. leftrsasigkey=<public_key>andrightrsasigkey=<public_key>-
Specifies the public key of the peers. Use the values displayed by the
ipsec showhostkeycommand in a previous step.
Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you use
auto=startin the configuration file, the connection is automatically activated. With other methods, additional steps are required to activate the connection. For details, see theipsec.conf(5)man page on your system.
Verification
Display the IPsec status:
ipsec status
# ipsec statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the connection is successfully established, the output contains lines as follows:
Phase 1 of an Internet Key Exchange version 2 (IKEv2) negotiation has been successfully completed:
000 #1: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;
000 #1: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow The Security Association (SA) is now ready to negotiate the actual data encryption tunnels, known as child SAs or Phase 2 SAs.
A child SA has been established:
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #1; idle;
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #1; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow This is the actual tunnel that your data traffic flows through.
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
7.4. Manually configuring an IPsec site-to-site VPN with raw RSA key authentication
A site-to-site VPN establishes a secure, encrypted tunnel between two distinct networks, seamlessly linking them across an insecure public network such as the internet.
For example, a site-to-site VPN enables devices in a branch office to access resources at a corporate headquarters just as if they were all part of the same local network.
For authenticating the gateway devices, RSA keys are more secure than pre-shared keys (PSKs) because their asymmetric encryption eliminates the risk of a shared secret. Using RSA keys also simplifies deployment by avoiding the need for a certificate authority (CA), while still providing strong peer-to-peer authentication.
Perform the steps on both gateway devices.
Prerequisites
- Routes in both networks ensure that the traffic to the remote networks is sent through the local VPN gateway devices.
Procedure
If Libreswan is not yet installed, perform the following steps:
Install the
libreswanpackage:dnf install libreswan
# dnf install libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Enable and start the
ipsecservice:systemctl enable --now ipsec
# systemctl enable --now ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow Open the IPsec ports and protocols in the firewall:
firewall-cmd --permanent --add-service="ipsec" firewall-cmd --reload
# firewall-cmd --permanent --add-service="ipsec" # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an RSA key pair:
ipsec newhostkey
# ipsec newhostkeyCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
ipsecutility stores the key pair in the NSS database.- Designate your peers. In an IPsec tunnel, you must designate one host as left and the other as right. This is an arbitrary choice. A common practice is to call your local host left and the remote host right.
Display the Certificate Key Attribute ID (CKAID) on both the left and right peer:
ipsec showhostkey --list < 1> RSA keyid: <key_id> ckaid: <ckaid>
# ipsec showhostkey --list < 1> RSA keyid: <key_id> ckaid: <ckaid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the CKAIDs of both peers in the next steps.
Display the public keys:
On the left peer, enter:
ipsec showhostkey --left --ckaid <ckaid_of_left_peer> # rsakey AwEAAdKCx leftrsasigkey=0sAwEAAdKCxpc9db48cehzQiQD...
# ipsec showhostkey --left --ckaid <ckaid_of_left_peer> # rsakey AwEAAdKCx leftrsasigkey=0sAwEAAdKCxpc9db48cehzQiQD...Copy to Clipboard Copied! Toggle word wrap Toggle overflow On the right peer, enter:
ipsec showhostkey --right --ckaid <ckaid_of_right_peer> # rsakey AwEAAcNWC rightrsasigkey=0sAwEAAcNWCzZO+PR1j8WbO8X...
# ipsec showhostkey --right --ckaid <ckaid_of_right_peer> # rsakey AwEAAcNWC rightrsasigkey=0sAwEAAcNWCzZO+PR1j8WbO8X...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The commands display the public keys with the corresponding parameters that you must use in the configuration file.
Create a
.conffile for the connection in the/etc/ipsec.d/directory. For example, create the/etc/ipsec.d/site-to-site.conffile with the following settings:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou can use the same configuration file on both gateway devices, and Libreswan identifies whether it is operating on the left or right host by using internal information. However, it is important that all values in
left*parameters belong to one peer and the values inright*parameters belong to the other.The settings specified in the example include the following:
conn <connection_name>- Defines the connection name. The name is arbitrary, and Libreswan uses it to identify the connection. You must indent parameters in this connection by at least one space or tab.
auto=<type>-
Controls how the connection is initiated. If you set the value to
start, Libreswan activates the connection automatically when the service starts. authby=rsasig- Enables RSA signature authentication for this connection.
left=<ip_address_or_fqdn_of_left_peer>andright=<ip_address_or_fqdn_of_right_peer>- Defines the IP address or DNS name of the peers.
leftid=<id>andrightid=<id>-
Defines how each peer is identified during the Internet Key Exchange (IKE) negotiation process. This can be a fully-qualified domain name (FQDN), an IP address, or a literal string. In the latter case, precede the string with an
@sign. leftrsasigkey=<public_key>andrightrsasigkey=<public_key>-
Specifies the public key of the peers. Use the values displayed by the
ipsec showhostkeycommand in a previous step. leftsubnet=<subnet>andrightsubnet=<subnet>- Defines subnets in classless inter-domain routing (CIDR) format that are connected through the tunnel. If you want to tunnel multiple subnets on one side, specify them in curly brackets and separate them with a comma.
Enable packet forwarding:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you use
auto=startin the configuration file, the connection is automatically activated. With other methods, additional steps are required to activate the connection. For details, see theipsec.conf(5)man page on your system.
Verification
Display the IPsec status:
ipsec status
# ipsec statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the connection is successfully established, the output contains lines as follows:
Phase 1 of an Internet Key Exchange version 2 (IKEv2) negotiation has been successfully completed:
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow The Security Association (SA) is now ready to negotiate the actual data encryption tunnels, known as child SAs or Phase 2 SAs.
A child SA has been established:
000 #3: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #2; idle;
000 #3: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #2; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow This is the actual tunnel that your data traffic flows through.
- From a client in the local subnet, ping a client in the remote subnet.
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
7.5. Manually configuring an IPsec host-to-site VPN with certificate-based authentication
A host-to-site VPN establishes a secure, encrypted connection between an individual remote computer and a private network, allowing them to be seamlessly linked across an insecure public network, such as the internet.
A host-to-site VPN is ideal for remote employees who need to access resources on their company’s internal network from their computer as if they were physically in the office.
For authentication, using digital certificates managed by a Certificate Authority (CA) offers a highly secure and scalable solution. Each connecting host and the gateway presents a certificate signed by a trusted CA. This method provides strong, verifiable authentication and simplifies user management. Access can be granted or revoked centrally at the CA, and Libreswan enforces this by checking each certificate against a certificate revocation list (CRL), denying access if a certificate appears on the list.
7.5.1. Setting up an IPsec gateway manually
You must configure the Libreswan IPsec gateway properly to enable secure remote access. Libreswan reads the server certificate, private key, and CA certificate from a Network Security Services (NSS) database.
The following example permits authenticated clients to access the internal 192.0.2.0/24 subnet and dynamically assigns an IP address from a virtual IP pool to each client. To maintain security, the gateway verifies that client certificates are issued by the same trusted CA and automatically uses a certificate revocation list (CRL) to ensure access is denied for any revoked certificates.
Prerequisites
The Public Key Cryptography Standards #12 (PKCS #12) file
~/file.p12exists on the gateway with the following contents:- The private key of the server
- The server certificate
- The CA certificate
- If required, intermediate certificates
For details about creating a private key and certificate signing request (CSR), as well as about requesting a certificate from a CA, see your CA’s documentation.
The server certificate contains the following fields:
-
Extended Key Usage (EKU) is set to
TLS Web Server Authentication. - Common Name (CN) or Subject Alternative Name (SAN) is set to the fully-qualified domain name (FQDN) of the gateway.
- X509v3 CRL distribution points contains URLs to Certificate Revocation Lists (CRLs).
-
Extended Key Usage (EKU) is set to
- A return route for VPN client traffic is configured on the internal network, pointing to the VPN gateway.
Procedure
If Libreswan is not yet installed:
Install the
libreswanpackage:dnf install libreswan
# dnf install libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Enable and start the
ipsecservice:systemctl enable --now ipsec
# systemctl enable --now ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow Open the IPsec ports and protocols in the firewall:
firewall-cmd --permanent --add-service="ipsec" firewall-cmd --reload
# firewall-cmd --permanent --add-service="ipsec" # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Import the PKCS #12 file into the NSS database:
ipsec import ~/file.p12 Enter password for PKCS12 file: <password> pk12util: PKCS12 IMPORT SUCCESSFUL correcting trust bits for Example-CA
# ipsec import ~/file.p12 Enter password for PKCS12 file: <password> pk12util: PKCS12 IMPORT SUCCESSFUL correcting trust bits for Example-CACopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the nicknames of the server and CA certificates:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You need this information for the configuration file.
Create a
.conffile for the connection in the/etc/ipsec.d/directory. For example, create the/etc/ipsec.d/host-to-site.conffile with the following settings:Add a
config setupsection to enable CRL checks:config setup crl-strict=yes crlcheckinterval=1hconfig setup crl-strict=yes crlcheckinterval=1hCopy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example include the following:
crl-strict=yes- Enables CRL checks. Authenticating clients are rejected if no CRL is available in the NSS database.
crlcheckinterval=1h- Re-fetches the CRL from the URL specified in the server’s certificate after the specified period.
Add a section for the gateway:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example include the following:
ikev2=insist- Defines the modern IKEv2 protocol as the only allowed protocol without fallback to IKEv1.
left=%defaultroute-
Dynamically sets the IP address of the default route interface when the
ipsecservice starts. Alternatively, you can set theleftparameter to the IP address or the FQDN of the host. leftid=%fromcertandrightid=%fromcert- Configures Libreswan to retrieve the identity from the distinguished name (DN) field of the certificate.
leftcert="<server_certificate_nickname>"- Sets the nickname of the server’s certificate used in the NSS database.
leftrsasigkey=%certandrightrsasigkey=%cert- Configures Libreswan to use the RSA public key embedded in the certificate.
leftsendcert=always- Instructs the gateway to always send the certificate, so that clients can validate it against the CA certificate.
leftsubnet=<subnets>- Specifies the subnets connected to the gateway that clients can access through the tunnel.
mobike=yes- Enables clients to seamlessly roam among networks.
rightaddresspool=<ip_range>- Specifies from which range the gateway can assign IP addresses to the clients.
modecfgclient=yes-
Enables clients to receive the DNS server IP set in the
modecfgdnsparameter and the DNS search domain set inmodecfgdomains.
For details about all parameters used in the example, see the
ipsec.conf(5)man page on your system.Enable packet forwarding:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you use
auto=startin the configuration file, the connection is automatically activated. With other methods, additional steps are required to activate the connection. For details, see theipsec.conf(5)man page on your system.
Verification
- Configure a client and connect to the VPN gateway.
Check if the service loaded the CRL and added the entries to the NSS database:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
7.5.2. Configuring a client to connect to an IPsec VPN gateway by using GNOME Settings
To access resources on a remote private network, users must first configure an IPsec VPN connection. The GNOME Settings application provides a graphical solution to create an IPsec VPN connection profile in NetworkManager and to establish the tunnel.
Prerequisites
- You configured the IPsec VPN gateway.
-
The
NetworkManager-libreswan-gnomepackage is installed. The PKCS #12 file
~/file.p12exists on the client with the following contents:- The private key of the user
- The user certificate
- The CA certificate
- If required, intermediate certificates
For details about creating a private key and certificate signing request (CSR), as well as about requesting a certificate from a CA, see your CA’s documentation.
-
The Extended Key Usage (EKU) in the certificate is set to
TLS Web Client Authentication.
Procedure
Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Import the PKCS #12 file into the NSS database:
ipsec import ~/file.p12 Enter password for PKCS12 file: <password> pk12util: PKCS12 IMPORT SUCCESSFUL correcting trust bits for Example-CA
# ipsec import ~/file.p12 Enter password for PKCS12 file: <password> pk12util: PKCS12 IMPORT SUCCESSFUL correcting trust bits for Example-CACopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the nicknames of the user and CA certificates:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require this information in the configuration file.
- Press the Super key, type Settings, and press Enter to open the GNOME Settings application.
- Click the button next to the VPN entry.
- Select IPsec based VPN from the list.
On the Identity tab, fill the fields as follows:
Expand Table 7.1. Identity tab settings Field name Value Corresponding ipsec.confparameterName
<networkmanager_profile_name>N/A
Gateway
<ip_address_or_fqdn_of_the_gateway>rightType
IKEv2 (certificate)authbyGroup name
%fromcertleftidCertificate name
<user_certificate_nickname>leftcertRemote ID
%fromcertrightid- Click Advanced.
In the Advanced properties window, fill the fields of the Connectivity tab as follows:
Expand Table 7.2. Connectivity tab settings Field name Value Corresponding ipsec.confparameterRemote Network
192.0.2.0/24rightsubnetNarrowing
Selected
narrowingEnable MOBIKE
yesmobikeDelay
30dpddelayTimeout
120dpdtimeoutAction
Cleardpdaction- Click to return to the connection settings.
- Click to save the connection.
- In the Network tab of the Settings application, toggle the switch next to the VPN profile to activate the connection.
Verification
- Establish a connection to a host in the remote network or ping it.
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
7.6. Manually configuring an IPsec mesh VPN with certificate-based authentication
An IPsec mesh creates a fully interconnected network where every server can communicate securely and directly with every other server. This is ideal for distributed database clusters or high-availability environments that span multiple data centers or cloud providers.
Establishing a direct, encrypted tunnel between each pair of servers ensures secure communication without a central bottleneck. For authentication, using digital certificates managed by a Certificate Authority (CA) offers a highly secure and scalable solution. Each host in the mesh presents a certificate signed by a trusted CA. This method provides strong, verifiable authentication and simplifies user management. Access can be granted or revoked centrally at the CA, and Libreswan enforces this by checking each certificate against a certificate revocation list (CRL), denying access if a certificate appears on the list.
Prerequisites
A Public Key Cryptography Standards #12 (PKCS #12) file exists on each peer in the mesh with the following contents:
- The private key of the server
- The server certificate
- The CA certificate
- If required, intermediate certificates
For details about creating a private key and certificate signing request (CSR), as well as about requesting a certificate from a CA, see your CA’s documentation.
The server certificate contains the following fields:
-
Extended Key Usage (EKU) is set to
TLS Web Server Authentication. - Common Name (CN) or Subject Alternative Name (SAN) is set to the fully-qualified domain name (FQDN) of the host.
- X509v3 CRL distribution points contains URLs to Certificate Revocation Lists (CRLs).
-
Extended Key Usage (EKU) is set to
Procedure
If Libreswan is not yet installed, perform the following steps:
Install the
libreswanpackage:dnf install libreswan
# dnf install libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Enable and start the
ipsecservice:systemctl enable --now ipsec
# systemctl enable --now ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow Open the IPsec ports and protocols in the firewall:
firewall-cmd --permanent --add-service="ipsec" firewall-cmd --reload
# firewall-cmd --permanent --add-service="ipsec" # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Import the PKCS #12 file into the NSS database:
ipsec import <file>.p12 Enter password for PKCS12 file: <password> pk12util: PKCS12 IMPORT SUCCESSFUL correcting trust bits for Example-CA
# ipsec import <file>.p12 Enter password for PKCS12 file: <password> pk12util: PKCS12 IMPORT SUCCESSFUL correcting trust bits for Example-CACopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the nicknames of the server and CA certificates:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You need this information for the configuration file.
Create a
.conffile for the connection in the/etc/ipsec.d/directory. For example, create the/etc/ipsec.d/mesh.conffile with the following settings:Add a
config setupsection to enable CRL checks:config setup crl-strict=yes crlcheckinterval=1hconfig setup crl-strict=yes crlcheckinterval=1hCopy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example include the following:
crl-strict=yes- Enables CRL checks. Authenticating peers are rejected if no CRL is available in the NSS database.
crlcheckinterval=1h- Re-fetches the CRL from the URL specified in the server’s certificate after the specified period.
Add a section that enforces traffic among members in the mesh:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example include the following:
left=%defaultroute-
Dynamically sets the IP address of the default route interface when the
ipsecservice starts. Alternatively, you can set theleftparameter to the IP address or the FQDN of the host. leftid=%fromcertandrightid=%fromcert- Configures Libreswan to retrieve the identity from the distinguished name (DN) field of the certificate.
leftcert="<server_certificate_nickname>"- Sets the nickname of the server’s certificate used in the NSS database.
leftrsasigkey=%cert- Configures Libreswan to use the RSA public key embedded in the certificate.
leftsendcert=always- Instructs the peer to always send the certificate, so that peers can validate it against the CA certificate.
failureshunt=drop- Enforces encryption and drops traffic if IPsec negotiation fails. This is critical for a secure mesh.
right=%opportunisticgroup- Specifies that the connection should apply to a dynamic group of remote peers defined in a policy file. This enables Libreswan to instantiate IPsec tunnels opportunistically for each listed IP or subnet in that group.
For details about all parameters used in the example, see the
ipsec.conf(5)man page on your system.Create the
/etc/ipsec.d/policies/server-meshpolicy file that specifies the peers or subnets in classless inter-domain routing (CIDR) format:192.0.2.0/24 198.51.100.0/24
192.0.2.0/24 198.51.100.0/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow With these settings, the
ipsecservice encrypts traffic between hosts in these subnets. If a host is not configured as a member of the IPsec mesh, communication between this host and the mesh members fails.Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Repeat the procedure on every host in the subnets you specified in the policy file.
Verification
Send traffic to a host in the mesh to establish the tunnel. For example, ping the host:
ping -c3 <peer_in_mesh>
# ping -c3 <peer_in_mesh>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPsec status:
ipsec status
# ipsec statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the connection is successfully established, the output contains lines as follows for the peer:
Phase 1 of an Internet Key Exchange version 2 (IKEv2) negotiation has been successfully completed:
#1: "<connection_name>#192.0.2.0/24"[1] ...192.0.2.2:500 ESTABLISHED_IKE_SA (established IKE SA); REKEY in 12822s; REPLACE in 13875s; newest; idle;
#1: "<connection_name>#192.0.2.0/24"[1] ...192.0.2.2:500 ESTABLISHED_IKE_SA (established IKE SA); REKEY in 12822s; REPLACE in 13875s; newest; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow The Security Association (SA) is now ready to negotiate the actual data encryption tunnels, known as child SAs or Phase 2 SAs.
A child SA has been established:
#2: "<connection_name>#192.0.2.0/24"[1] ...192.0.2.2:500 ESTABLISHED_CHILD_SA (established Child SA); REKEY in 13071s; REPLACE in 13875s; newest; eroute owner; IKE SA #1; idle;
#2: "<connection_name>#192.0.2.0/24"[1] ...192.0.2.2:500 ESTABLISHED_CHILD_SA (established Child SA); REKEY in 13071s; REPLACE in 13875s; newest; eroute owner; IKE SA #1; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow This is the actual tunnel that your data traffic flows through.
Check if the service loaded the CRL and added the entries to the NSS database:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
7.7. Protecting the IPsec NSS database with a password
By default, only the root user can access the IPsec Network Security Services (NSS) database in the /var/lib/ipsec/nss/ directory. You can additionally protect the database with a password. This is required if you run RHEL in Federal Information Processing Standard (FIPS) mode.
Prerequisites
-
The
/var/lib/ipsec/nss/directory contains the NSS database.
Procedure
Enable password protection for the Libreswan NSS database:
certutil -W -d /var/lib/ipsec/nss/
# certutil -W -d /var/lib/ipsec/nss/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the current password:
Enter Password or Pin for "NSS Certificate DB": <password>
Enter Password or Pin for "NSS Certificate DB": <password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the database is currently not protected by a password, press Enter.
Enter the new password:
Enter new password: <new_password> Re-enter password: <new_password>
Enter new password: <new_password> Re-enter password: <new_password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow To unlock the database, the
ipsecservice requires the/etc/ipsec.d/nsspasswordfile. Create the file with the following content:If the host does not run in FIPS mode:
NSS Certificate DB:<password>
NSS Certificate DB:<password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the host runs in FIPS mode:
NSS FIPS 140-2 Certificate DB:<password>
NSS FIPS 140-2 Certificate DB:<password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Set secure permissions on the
/etc/ipsec.d/nsspasswordfile:chmod 600 /etc/ipsec.d/nsspassword chown root:root /etc/ipsec.d/nsspassword
# chmod 600 /etc/ipsec.d/nsspassword # chown root:root /etc/ipsec.d/nsspasswordCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the
ipsecservice is running:systemctl is-active ipsec
# systemctl is-active ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the command returns
active, the service successfully uses the password file to unlock the NSS database.Perform an action on the NSS database that requires the password. For example, display the private keys:
certutil -K -d /var/lib/ipsec/nss/ certutil: Checking token "NSS Certificate DB" in slot "NSS User Private Key and Certificate Services" Enter Password or Pin for "NSS Certificate DB":
# certutil -K -d /var/lib/ipsec/nss/ certutil: Checking token "NSS Certificate DB" in slot "NSS User Private Key and Certificate Services" Enter Password or Pin for "NSS Certificate DB":Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the command prompts for the password.
7.8. Using IPsec on a system with FIPS mode enabled
RHEL in Federal Information Processing Standard (FIPS) mode exclusively uses validated cryptographic modules, automatically disabling legacy protocols and ciphers. Enabling FIPS mode is often a requirement for federal compliance and enhances system security.
The Libreswan IPsec implementation provided by RHEL is fully FIPS-compliant. When the system is in FIPS mode, Libreswan automatically uses the certified cryptographic modules without requiring any additional configuration, regardless of whether Libreswan is installed on a new FIPS-enabled system or when FIPS mode is activated on a system with an existing Libreswan VPN.
If FIPS mode is enabled, you can confirm that Libreswan is running in FIPS mode:
ipsec whack --fipsstatus 000 FIPS mode enabled
# ipsec whack --fipsstatus
000 FIPS mode enabledTo list the allowed algorithms and ciphers in Libreswan in FIPS mode, enter:
7.9. Configuring TCP fallback for an IPsec VPN connection
Standard IPsec VPNs can fail on restrictive networks that block the UDP and Encapsulating Security Payload (ESP) protocols. To ensure connectivity in such environments, Libreswan can encapsulate all VPN traffic within a TCP connection.
Encapsulating VPN packets within TCP can reduce throughput and increase latency. For this reason, use TCP encapsulation only as a fallback option or if UDP-based connections are consistently blocked in your environment.
Prerequisites
- The IPsec connection is configured.
Procedure
Edit the
/etc/ipsec.conffile, and make the following changes in theconfig setupsection:Configure Libreswan to listen on a TCP port:
listen-tcp=yes
listen-tcp=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, Libreswan listens on port 4500. If you want to use a different port, enter:
tcp-remoteport=<port_number>
tcp-remoteport=<port_number>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Decide whether TCP should be used as a fallback option if UDP is not available or permanent:
As a fallback option, enter:
enable-tcp=fallback retransmit-timeout=5s
enable-tcp=fallback retransmit-timeout=5sCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, Libreswan waits 60 seconds after a failed attempt to connect by using UDP before retrying the connection over TCP. Lowering the
retransmit-timeoutvalue shortens the delay, enabling the fallback protocol to initiate more quickly.As a permanent replacement for UDP, enter:
enable-tcp=yes
enable-tcp=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you configured a TCP port other than the default 4500, open the port in the firewall:
firewall-cmd --permanent --add-port=<tcp_port>/tcp firewall-cmd --reload
# firewall-cmd --permanent --add-port=<tcp_port>/tcp # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Repeat the procedure on the peers that use this gateway.
7.10. Enabling legacy ciphers and algorithms in Libreswan
Enable legacy ciphers and algorithms in Libreswan for backward compatibility with other IPsec peers. This overrides the RHEL system-wide cryptographic policies which, by default, enforce strong encryption ciphers and algorithms for IPsec and Internet Key Exchange (IKE).
The RHEL system-wide cryptographic policies create a special connection called %default. This connection sets the default values for the keyexchange, esp, and ike parameters.
Prerequisites
- Libreswan is installed.
Procedure
To override the defaults set by the RHEL system-wide cryptographic policies, add the
keyexchange,esp, andikeparameters to your connection configuration and set them to the values you require. For example:conn <connection_name> ikev2=no ike=aes-sha2,aes-sha1;modp2048 esp=aes-sha2,aes-sha1 ...conn <connection_name> ikev2=no ike=aes-sha2,aes-sha1;modp2048 esp=aes-sha2,aes-sha1 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.11. Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel
To protect your VPN connection from traffic redirection attacks, assign it to a dedicated routing table. This prevents malicious network servers from bypassing the secure tunnel and compromising data integrity.
Both a DHCP server and Stateless Address Autoconfiguration (SLAAC) can add routes to a client’s routing table. For example, a malicious DHCP server can use this feature to force a host with VPN connection to redirect traffic through a physical interface instead of the VPN tunnel. This vulnerability is also known as TunnelVision and described in the CVE-2024-3661 vulnerability article.
To mitigate this vulnerability, you can assign the VPN connection to a dedicated routing table. This prevents the DHCP configuration or SLAAC from manipulating routing decisions for network packets intended for the VPN tunnel.
Follow the steps if at least one of the conditions applies to your environment:
- At least one network interface uses DHCP or SLAAC.
- Your network does not use mechanisms, such as DHCP snooping, that prevent a rogue DHCP server.
Routing the entire traffic through the VPN prevents the host from accessing local network resources.
Prerequisites
- You use NetworkManager 1.48.10-5 or later.
Procedure
- Decide which routing table you want to use. The following steps use table 75. By default, RHEL does not use the tables 1-254, and you can use any of them.
Configure the VPN connection profile to place the VPN routes in a dedicated routing table:
nmcli connection modify <vpn_connection_profile> ipv4.route-table 75 ipv6.route-table 75
# nmcli connection modify <vpn_connection_profile> ipv4.route-table 75 ipv6.route-table 75Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set a low priority value for the table you used in the previous command:
nmcli connection modify <vpn_connection_profile> ipv4.routing-rules "priority 32345 from all table 75" ipv6.routing-rules "priority 32345 from all table 75"
# nmcli connection modify <vpn_connection_profile> ipv4.routing-rules "priority 32345 from all table 75" ipv6.routing-rules "priority 32345 from all table 75"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The priority value can be any value between 1 and 32766. The lower the value, the higher the priority.
Reconnect the VPN connection:
nmcli connection down <vpn_connection_profile> nmcli connection up <vpn_connection_profile>
# nmcli connection down <vpn_connection_profile> # nmcli connection up <vpn_connection_profile>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 routes in table 75:
ip route show table 75 ... 192.0.2.0/24 via 192.0.2.254 dev vpn_device proto static metric 50 default dev vpn_device proto static scope link metric 50
# ip route show table 75 ... 192.0.2.0/24 via 192.0.2.254 dev vpn_device proto static metric 50 default dev vpn_device proto static scope link metric 50Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that both the route to the remote network and the default gateway are assigned to routing table 75 and, therefore, all traffic is routed through the tunnel. If you set
ipv4.never-default truein the VPN connection profile, a default route is not created and, therefore, not visible in this output.Display the IPv6 routes in table 75:
ip -6 route show table 75 ... 2001:db8:1::/64 dev vpn_device proto kernel metric 50 pref medium default dev vpn_device proto static metric 50 pref medium
# ip -6 route show table 75 ... 2001:db8:1::/64 dev vpn_device proto kernel metric 50 pref medium default dev vpn_device proto static metric 50 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that both the route to the remote network and the default gateway are assigned to routing table 75 and, therefore, all traffic is routed through the tunnel. If you set
ipv6.never-default truein the VPN connection profile, a default route is not created and, therefore, not visible in this output.
7.12. Configuring IPsec VPN connections by using RHEL system roles
Configure IPsec VPN connections to establish encrypted tunnels over untrusted networks and ensure the integrity of data in transit. By using the RHEL system roles, you can automate the setup for use cases, such as connecting branch offices to headquarters.
The vpn RHEL system role can only create VPN configurations that use pre-shared keys (PSKs) or certificates to authenticate peers to each other.
7.12.1. Configuring an IPsec host-to-host VPN with PSK authentication by using the vpn RHEL system role
A host-to-host VPN establishes an encrypted connection between two devices, allowing applications to communicate safely over an insecure network. By using the vpn RHEL system role, you can automate the process of creating IPsec host-to-host connections.
For authentication, a pre-shared key (PSK) is a straightforward method that uses a single, shared secret known only to the two peers. This approach is simple to configure and ideal for basic setups where ease of deployment is a priority. However, you must keep the key strictly confidential. An attacker with access to the key can compromise the connection.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
hosts: <list>Defines a YAML dictionary with the peers between which you want to configure a VPN. If an entry is not an Ansible managed node, you must specify its fully-qualified domain name (FQDN) or IP address in the
hostnameparameter, for example:... - hosts: ... external-host.example.com: hostname: 192.0.2.1... - hosts: ... external-host.example.com: hostname: 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow The role configures the VPN connection on each managed node. The connections are named
<peer_A>-to-<peer_B>, for example,managed-node-01.example.com-to-managed-node-02.example.com. Note that the role cannot configure Libreswan on external (unmanaged) nodes. You must manually create the configuration on these peers.auth_method: psk-
Enables PSK authentication between the peers. The role uses
opensslon the control node to create the PSK. auto: <startup_method>-
Specifies the startup method of the connection. Valid values are
add,ondemand,start, andignore. For details, see theipsec.conf(5)man page on a system with Libreswan installed. The default value of this variable is null, which means no automatic startup operation. vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm that the connections are successfully started, for example:
ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"' ... 006 #3: "managed-node-01.example.com-to-managed-node-02.example.com", type=ESP, add_time=1741857153, inBytes=38622, outBytes=324626, maxBytes=2^63B, id='@managed-node-02.example.com'
# ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"' ... 006 #3: "managed-node-01.example.com-to-managed-node-02.example.com", type=ESP, add_time=1741857153, inBytes=38622, outBytes=324626, maxBytes=2^63B, id='@managed-node-02.example.com'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only succeeds if the VPN connection is active. If you set the
autovariable in the playbook to a value other thanstart, you might need to manually activate the connection on the managed nodes first.
Use the vpn RHEL system role to automate the process of creating an IPsec host-to-host VPN. To enhance security by minimizing the risk of control messages being intercepted or disrupted, configure separate connections for both the data traffic and the control traffic.
A host-to-host VPN establishes a direct, secure, and encrypted connection between two devices, allowing applications to communicate safely over an insecure network, such as the internet.
For authentication, a pre-shared key (PSK) is a straightforward method that uses a single, shared secret known only to the two peers. This approach is simple to configure and ideal for basic setups where ease of deployment is a priority. However, you must keep the key strictly confidential. An attacker with access to the key can compromise the connection.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
hosts: <list>Defines a YAML dictionary with the hosts between which you want to configure a VPN. The connections are named
<name>-<IP_address_A>-to-<IP_address_B>, for examplecontrol_plane_vpn-203.0.113.1-to-198.51.100.2.The role configures the VPN connection on each managed node. Note that the role cannot configure Libreswan on external (unmanaged) nodes. You must manually create the configuration on these hosts.
auth_method: psk-
Enables PSK authentication between the hosts. The role uses
opensslon the control node to create the pre-shared key. auto: <startup_method>-
Specifies the startup method of the connection. Valid values are
add,ondemand,start, andignore. For details, see theipsec.conf(5)man page on a system with Libreswan installed. The default value of this variable is null, which means no automatic startup operation. vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm that the connections are successfully started, for example:
ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "control_plane_vpn-203.0.113.1-to-198.51.100.2"' ... 006 #3: "control_plane_vpn-203.0.113.1-to-198.51.100.2", type=ESP, add_time=1741860073, inBytes=0, outBytes=0, maxBytes=2^63B, id='198.51.100.2'
# ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "control_plane_vpn-203.0.113.1-to-198.51.100.2"' ... 006 #3: "control_plane_vpn-203.0.113.1-to-198.51.100.2", type=ESP, add_time=1741860073, inBytes=0, outBytes=0, maxBytes=2^63B, id='198.51.100.2'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only succeeds if the VPN connection is active. If you set the
autovariable in the playbook to a value other thanstart, you might need to manually activate the connection on the managed nodes first.
7.12.3. Configuring an IPsec site-to-site VPN with PSK authentication by using the vpn RHEL system role
A site-to-site VPN establishes an encrypted tunnel between two distinct networks, seamlessly linking them across an insecure public network. By using the vpn RHEL system role, you can automate the process of creating IPsec site-to-site VPN connections.
A site-to-site VPN enables devices in a branch office to access resources at a corporate headquarters just as if they were all part of the same local network.
For authentication, a pre-shared key (PSK) is a straightforward method that uses a single, shared secret known only to the two peers. This approach is simple to configure and ideal for basic setups where ease of deployment is a priority. However, you must keep the key strictly confidential. An attacker with access to the key can compromise the connection.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
hosts: <list>Defines a YAML dictionary with the gateways between which you want to configure a VPN. If an entry is not an Ansible-managed node, you must specify its fully-qualified domain name (FQDN) or IP address in the
hostnameparameter, for example:... - hosts: ... external-host.example.com: hostname: 192.0.2.1... - hosts: ... external-host.example.com: hostname: 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow The role configures the VPN connection on each managed node. The connections are named
<gateway_A>-to-<gateway_B>, for example,managed-node-01.example.com-to-managed-node-02.example.com. Note that the role cannot configure Libreswan on external (unmanaged) nodes. You must manually create the configuration on these peers.subnets: <yaml_list_of_subnets>- Defines subnets in classless inter-domain routing (CIDR) format that are connected through the tunnel.
auth_method: psk-
Enables PSK authentication between the peers. The role uses
opensslon the control node to create the PSK. auto: <startup_method>-
Specifies the startup method of the connection. Valid values are
add,ondemand,start, andignore. For details, see theipsec.conf(5)man page on a system with Libreswan installed. The default value of this variable is null, which means no automatic startup operation. vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm that the connections are successfully started, for example:
ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"' ... 006 #3: "managed-node-01.example.com-to-managed-node-02.example.com", type=ESP, add_time=1741857153, inBytes=38622, outBytes=324626, maxBytes=2^63B, id='@managed-node-02.example.com'
# ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"' ... 006 #3: "managed-node-01.example.com-to-managed-node-02.example.com", type=ESP, add_time=1741857153, inBytes=38622, outBytes=324626, maxBytes=2^63B, id='@managed-node-02.example.com'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only succeeds if the VPN connection is active. If you set the
autovariable in the playbook to a value other thanstart, you might need to manually activate the connection on the managed nodes first.
7.12.4. Configuring an IPsec mesh VPN with certificate-based authentication by using the vpn RHEL system role
An IPsec mesh creates a fully interconnected network where every server can communicate securely and directly with every other server. By using the vpn RHEL system role, you can automate configuring a VPN mesh with certificate-based authentication among managed nodes.
An IPsec mesh is ideal for distributed database clusters or high-availability environments that span multiple data centers or cloud providers. Establishing a direct, encrypted tunnel between each pair of servers ensures secure communication without a central bottleneck.
For authentication, using digital certificates managed by a Certificate Authority (CA) offers a highly secure and scalable solution. Each host in the mesh presents a certificate signed by a trusted CA. This method provides strong, verifiable authentication and simplifies user management. Access can be granted or revoked centrally at the CA, and Libreswan enforces this by checking each certificate against a certificate revocation list (CRL), denying access if a certificate appears on the list.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. You prepared a PKCS #12 file for each managed node:
Each file contains:
- The private key of the server
- The server certificate
- The CA certificate
- If required, intermediate certificates
-
The files are named
<managed_node_name_as_in_the_inventory>.p12. - The files are stored in the same directory as the playbook.
The server certificate contains the following fields:
-
Extended Key Usage (EKU) is set to
TLS Web Server Authentication. - Common Name (CN) or Subject Alternative Name (SAN) is set to the fully-qualified domain name (FQDN) of the host.
- X509v3 CRL distribution points contain URLs to Certificate Revocation Lists (CRLs).
-
Extended Key Usage (EKU) is set to
Procedure
Edit the
~/inventoryfile, and append thecert_namevariable:managed-node-01.example.com cert_name=managed-node-01.example.com managed-node-02.example.com cert_name=managed-node-02.example.com managed-node-03.example.com cert_name=managed-node-03.example.com
managed-node-01.example.com cert_name=managed-node-01.example.com managed-node-02.example.com cert_name=managed-node-02.example.com managed-node-03.example.com cert_name=managed-node-03.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
cert_namevariable to the value of the common name (CN) field used in the certificate for each host. Typically, the CN field is set to the fully-qualified domain name (FQDN).Store your sensitive variables in an encrypted file:
Create the vault:
ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>
$ ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
ansible-vault createcommand opens an editor, enter the sensitive data in the<key>: <value>format:pkcs12_pwd: <password>
pkcs12_pwd: <password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the changes, and close the editor. Ansible encrypts the data in the vault.
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
opportunistic: true-
Enables an opportunistic mesh among multiple hosts. The
policiesvariable defines for which subnets and hosts traffic must or can be encrypted and which of them should continue using plain text connections. auth_method: cert- Enables certificate-based authentication. This requires that you specify the nickname of each managed node’s certificate in the inventory.
policies: <list_of_policies>Defines the Libreswan policies in YAML list format.
The default policy is
private-or-clear. To change it toprivate, the above playbook contains an according policy for the defaultcidrentry.To prevent a loss of the SSH connection during the execution of the playbook if the Ansible control node is in the same IP subnet as the managed nodes, add a
clearpolicy for the control node’s IP address. For example, if the mesh should be configured for the192.0.2.0/24subnet and the control node uses the IP address192.0.2.1, you require aclearpolicy for192.0.2.1/32as shown in the playbook.For details about policies, see the
ipsec.conf(5)man page on a system with Libreswan installed.vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --ask-vault-pass --syntax-check ~/playbook.yml
$ ansible-playbook --ask-vault-pass --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook --ask-vault-pass ~/playbook.yml
$ ansible-playbook --ask-vault-pass ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
On a node in the mesh, ping another node to activate the connection:
ping managed-node-02.example.com
[root@managed-node-01]# ping managed-node-02.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the connection is active:
ipsec trafficstatus 006 #2: "private#192.0.2.0/24"[1] ...192.0.2.2, type=ESP, add_time=1741938929, inBytes=372408, outBytes=545728, maxBytes=2^63B, id='CN=managed-node-02.example.com'
[root@managed-node-01]# ipsec trafficstatus 006 #2: "private#192.0.2.0/24"[1] ...192.0.2.2, type=ESP, add_time=1741938929, inBytes=372408, outBytes=545728, maxBytes=2^63B, id='CN=managed-node-02.example.com'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.13. Configuring an IPsec based VPN connection by using nmstatectl
Configure IPsec VPN connections to establish encrypted tunnels over untrusted networks and ensure the integrity of data in transit. By using Nmstate, you can create IPsec VPN connections by using a declarative API.
You can use the nmstatectl utility to configure Libreswan IPsec VPN connections through the Nmstate API. The nmstatectl utility is a command-line tool to manage host networking through the declarative Nmstate API. Instead of running multiple imperative commands to configure an interface, you define the expected state in a YAML file. Nmstate then takes this definition and applies it to the system. A key advantage of this approach is an atomic result. Nmstate ensures that the resulting configuration precisely matches your YAML definition. If any part of the configuration fails to apply, it automatically rolls back all changes and prevents the system from entering an incorrect or broken network state.
Due to the design of the NetworkManager-libreswan plugin, you can use nmstatectl only on one peer and must manually configure Libreswan on the other peer.
7.13.1. Configuring an IPsec host-to-host VPN with raw RSA key authentication by using nmstatectl
You can use the declarative Nmstate API to configure a host-to-host VPN between two devices to communicate safely over an insecure network. Nmstate ensures that the result matches the configuration file or rolls back the changes.
For authentication, RSA keys are more secure than pre-shared keys (PSKs) because their asymmetric encryption eliminates the risk of a shared secret. Using RSA keys also simplifies deployment by avoiding the need for a certificate authority (CA), while still providing strong peer-to-peer authentication.
In general, the choice of which host is named left and right is arbitrary. However, NetworkManager always uses the term left for the local host and right for the remote host.
Prerequisites
The remote peer runs Libreswan IPsec and is prepared for a host-to-host connection.
Due to the design of the
NetworkManager-libreswanplugin, Nmstate cannot communicate with other peers that also use this plugin for the same connection.
Procedure
If Libreswan is not yet installed, perform the following steps:
Install the required packages:
dnf install nmstate libreswan NetworkManager-libreswan
# dnf install nmstate libreswan NetworkManager-libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the NetworkManager service:
systemctl restart NetworkManager
# systemctl restart NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Open the IPsec ports and protocols in the firewall:
firewall-cmd --permanent --add-service="ipsec" firewall-cmd --reload
# firewall-cmd --permanent --add-service="ipsec" # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an RSA key pair:
ipsec newhostkey
# ipsec newhostkeyCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
ipsecutility stores the key pair in the NSS database.Display the Certificate Key Attribute ID (CKAID) on both the left and right peers:
ipsec showhostkey --list < 1> RSA keyid: <key_id> ckaid: <ckaid>
# ipsec showhostkey --list < 1> RSA keyid: <key_id> ckaid: <ckaid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the CKAIDs of both peers in the next steps.
Display the public keys:
On the left peer, enter:
ipsec showhostkey --left --ckaid <ckaid_of_left_peer> # rsakey AwEAAdKCx leftrsasigkey=0sAwEAAdKCxpc9db48cehzQiQD...# ipsec showhostkey --left --ckaid <ckaid_of_left_peer> # rsakey AwEAAdKCx leftrsasigkey=0sAwEAAdKCxpc9db48cehzQiQD...Copy to Clipboard Copied! Toggle word wrap Toggle overflow On the right peer, enter:
ipsec showhostkey --right --ckaid <ckaid_of_right_peer> # rsakey AwEAAcNWC rightrsasigkey=0sAwEAAcNWCzZO+PR1j8WbO8X...# ipsec showhostkey --right --ckaid <ckaid_of_right_peer> # rsakey AwEAAcNWC rightrsasigkey=0sAwEAAcNWCzZO+PR1j8WbO8X...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The commands display the public keys with the corresponding parameters that you must use in the configuration file.
Create a YAML file, for example
~/ipsec-host-to-host-rsa-auth.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example include the following:
ikev2: insist- Defines the modern IKEv2 protocol as the only allowed protocol without fallback to IKEv1. This setting is mandatory in a host-to-host configuration with Nmstate.
left=<ip_address_or_fqdn_of_left_peer>andright=<ip_address_or_fqdn_of_right_peer>- Defines the IP address or DNS name of the peers.
leftid=<id>andrightid=<id>-
Defines how each peer is identified during the Internet Key Exchange (IKE) negotiation process. This can be an IP address or a literal string. Note that NetworkManager interprets all values other than IP addresses as a literal string and internally adds a leading
@sign. This requires that the Libreswan peer also uses literal strings as IDs or authentication fails. leftrsasigkey=<public_key>andrightrsasigkey=<public_key>-
Specifies the public key of the peers. Use the values displayed by the
ipsec showhostkeycommand in a previous step. leftmodecfgclient: false- Disables dynamic configuration on this host. This setting is mandatory in a host-to-host configuration with Nmstate.
rightsubnet: <ip_address_of_right_peer>/32- Defines that the host can only access this peer. This setting is mandatory in a host-to-host configuration with Nmstate.
Apply the settings to the system:
nmstatectl apply ~/ipsec-host-to-host-rsa-auth.yml
# nmstatectl apply ~/ipsec-host-to-host-rsa-auth.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPsec status:
ipsec status
# ipsec statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the connection is successfully established, the output contains lines as follows:
Phase 1 of an Internet Key Exchange version 2 (IKEv2) negotiation has been successfully completed:
000 #1: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;
000 #1: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow The Security Association (SA) is now ready to negotiate the actual data encryption tunnels, known as child SAs or Phase 2 SAs.
A child SA has been established:
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #1; idle;
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #1; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow This is the actual tunnel that your data traffic flows through.
Troubleshooting
To display the actual configuration NetworkManager passes to Libreswan, enter:
nmcli connection export <connection_name>
# nmcli connection export <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output can help to identify deviating settings, such as IDs and keys, when you compare them with the Libreswan configuration on the remote host.
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
7.13.2. Configuring an IPsec site-to-site VPN with raw RSA key authentication by using nmstatectl
You can use the declarative Nmstate API to configure a site-to-site VPN between two distinct networks, seamlessly linking them across an insecure network. Nmstate ensures that the result matches the configuration file or rolls back the changes.
For authenticating the gateway devices, RSA keys are more secure than pre-shared keys (PSKs) because their asymmetric encryption eliminates the risk of a shared secret. Using RSA keys also simplifies deployment by avoiding the need for a certificate authority (CA), while still providing strong peer-to-peer authentication.
In general, the choice which host is named left and right is arbitrary. However, NetworkManager always uses the term left for the local host and right for the remote host.
Prerequisites
The remote gateway runs Libreswan IPsec and is prepared for a site-to-site connection.
Due to the design of the
NetworkManager-libreswanplugin, Nmstate cannot communicate with other peers that also use this plugin for the same connection.
Procedure
If Libreswan is not yet installed, perform the following steps:
Install the required packages:
dnf install nmstate libreswan NetworkManager-libreswan
# dnf install nmstate libreswan NetworkManager-libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the NetworkManager service:
systemctl restart NetworkManager
# systemctl restart NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Open the IPsec ports and protocols in the firewall:
firewall-cmd --permanent --add-service="ipsec" firewall-cmd --reload
# firewall-cmd --permanent --add-service="ipsec" # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an RSA key pair:
ipsec newhostkey
# ipsec newhostkeyCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
ipsecutility stores the key pair in the NSS database.Display the Certificate Key Attribute ID (CKAID) on both the left and right peer:
ipsec showhostkey --list < 1> RSA keyid: <key_id> ckaid: <ckaid>
# ipsec showhostkey --list < 1> RSA keyid: <key_id> ckaid: <ckaid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the CKAIDs of both peers in the following steps.
Display the public keys:
On the left peer, enter:
ipsec showhostkey --left --ckaid <ckaid_of_left_peer> # rsakey AwEAAdKCx leftrsasigkey=0sAwEAAdKCxpc9db48cehzQiQD...# ipsec showhostkey --left --ckaid <ckaid_of_left_peer> # rsakey AwEAAdKCx leftrsasigkey=0sAwEAAdKCxpc9db48cehzQiQD...Copy to Clipboard Copied! Toggle word wrap Toggle overflow On the right peer, enter:
ipsec showhostkey --right --ckaid <ckaid_of_right_peer> # rsakey AwEAAcNWC rightrsasigkey=0sAwEAAcNWCzZO+PR1j8WbO8X...# ipsec showhostkey --right --ckaid <ckaid_of_right_peer> # rsakey AwEAAcNWC rightrsasigkey=0sAwEAAcNWCzZO+PR1j8WbO8X...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The commands display the public keys with the corresponding parameters that you must use in the configuration file.
Create a YAML file, for example
~/ipsec-site-to-site-rsa-auth.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example include the following:
ikev2: insist- Defines the modern IKEv2 protocol as the only allowed protocol without fallback to IKEv1. This setting is mandatory in a site-to-site configuration with Nmstate.
left=<ip_address_or_fqdn_of_left_peer>andright=<ip_address_or_fqdn_of_right_peer>- Defines the IP address or DNS name of the peers.
leftid=<id>andrightid=<id>-
Defines how each peer is identified during the Internet Key Exchange (IKE) negotiation process. This can be an IP address or a literal string. Note that NetworkManager interprets all values other than IP addresses as a literal string and internally adds a leading
@sign. This requires that the Libreswan peer also uses literal strings as IDs or authentication fails. leftrsasigkey=<public_key>andrightrsasigkey=<public_key>-
Specifies the public key of the peers. Use the values displayed by the
ipsec showhostkeycommand in a previous step. leftmodecfgclient: false- Disables dynamic configuration on this host. This setting is mandatory in a site-to-site configuration with Nmstate.
leftsubnet=<subnet>andrightsubnet=<subnet>- Defines subnets in classless inter-domain routing (CIDR) format that are connected through the tunnel.
Enable packet forwarding:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the settings to the system:
nmstatectl apply ~/ipsec-site-to-site-rsa-auth.yml
# nmstatectl apply ~/ipsec-site-to-site-rsa-auth.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPsec status:
ipsec status
# ipsec statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the connection is successfully established, the output contains lines as follows:
Phase 1 of an Internet Key Exchange version 2 (IKEv2) negotiation has been successfully completed:
000 #1: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;
000 #1: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow The Security Association (SA) is now ready to negotiate the actual data encryption tunnels, known as child SAs or Phase 2 SAs.
A child SA has been established:
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #1; idle;
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #1; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow This is the actual tunnel that your data traffic flows through.
- From a client in the local subnet, ping a client in the remote subnet.
Troubleshooting
To display the actual configuration NetworkManager passes to Libreswan, enter:
nmcli connection export <connection_name>
# nmcli connection export <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output can help to identify deviating settings, such as IDs and keys, when you compare them with the Libreswan configuration on the remote host.
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
7.13.3. Configuring a client to connect to an IPsec VPN gateway by using nmstatectl
To access resources on a remote private network, users must first configure an IPsec VPN connection. By using Nmstate, you can create the connection with an existing Libreswan IPsec gateway by using a declarative API.
In general, the choice of which host is named left and right is arbitrary. However, NetworkManager always uses the term left for the local host and right for the remote host.
Prerequisites
The remote gateway runs Libreswan IPsec and is prepared for a host-to-site connection with certificate-based authentication.
Due to the design of the
NetworkManager-libreswanplugin, Nmstate cannot communicate with other peers that also use this plugin for the same connection.The PKCS#12 file
~/file.p12exists on the client with the following contents:- The private key of the user
- The user certificate
- The CA certificate
- If required, intermediate certificates
For details about creating a private key and certificate signing request (CSR), as well as about requesting a certificate from a CA, see your CA’s documentation.
-
The Extended Key Usage (EKU) in the certificate is set to
TLS Web Client Authentication.
Procedure
If Libreswan is not yet installed:
Install the required packages:
dnf install nmstate libreswan NetworkManager-libreswan
# dnf install nmstate libreswan NetworkManager-libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the NetworkManager service:
systemctl restart NetworkManager
# systemctl restart NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Open the IPsec ports and protocols in the firewall:
firewall-cmd --permanent --add-service="ipsec" firewall-cmd --reload
# firewall-cmd --permanent --add-service="ipsec" # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Import the PKCS #12 file into the NSS database:
ipsec import ~/file.p12 Enter password for PKCS12 file: <password> pk12util: PKCS12 IMPORT SUCCESSFUL correcting trust bits for Example-CA
# ipsec import ~/file.p12 Enter password for PKCS12 file: <password> pk12util: PKCS12 IMPORT SUCCESSFUL correcting trust bits for Example-CACopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the nicknames of the user and CA certificates:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require this information in the Nmstate YAML file.
Create a YAML file, for example,
~/ipsec-host-to-site-cert-auth.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example include the following:
ikev2: insist- Defines the modern IKEv2 protocol as the only allowed protocol without fallback to IKEv1. This setting is mandatory in a host-to-site configuration with Nmstate.
left=<ip_address_or_fqdn_of_left_peer>andright=<ip_address_or_fqdn_of_right_peer>- Defines the IP address or DNS name of the peers.
leftid=%fromcertandrightid=%fromcert- Configures Libreswan to retrieve the identity from the distinguished name (DN) field of the certificate.
leftcert="<server_certificate_nickname>"- Sets the nickname of the server’s certificate used in the NSS database.
rightsubnet: <subnet>- Defines the subnet in classless inter-domain routing (CIDR) format that is connected to the gateway.
Apply the settings to the system:
nmstatectl apply ~/ipsec-host-to-site-cert-auth.yml
# nmstatectl apply ~/ipsec-host-to-site-cert-auth.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
- Establish a connection to a host in the remote network or ping it.
Troubleshooting
To display the actual configuration NetworkManager passes to Libreswan, enter:
nmcli connection export <connection_name>
# nmcli connection export <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output can help to identify deviating settings, such as IDs and keys, when you compare them with the Libreswan configuration on the remote host.
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
7.14. Troubleshooting IPsec configurations
Diagnosing IPsec configuration failures can be challenging, because issues can be caused by mismatched settings, firewall rules, and kernel-level errors. The following information provides a systematic approach to resolving common problems with IPsec VPN connections.
7.14.1. Basic connection issues
Problems with VPN connections often occur due to mismatched configurations between the endpoints.
To confirm that an IPsec connection is established, enter:
ipsec trafficstatus 006 #8: "vpn.example.com"[1] 192.0.2.1, type=ESP, add_time=1595296930, inBytes=5999, outBytes=3231, id='@vpn.example.com', lease=198.51.100.1/32
# ipsec trafficstatus
006 #8: "vpn.example.com"[1] 192.0.2.1, type=ESP, add_time=1595296930, inBytes=5999, outBytes=3231, id='@vpn.example.com', lease=198.51.100.1/32For a successful connection, the command shows an entry with the connection’s name and details. If the output is empty, the tunnel is not established.
7.14.3. Mismatched Configurations
VPN connections fail if the endpoints are not configured with matching Internet Key Exchange (IKE) versions, algorithms, IP address ranges, or pre-shared keys (PSK). If you identify a mismatch, you must align the settings on both endpoints to resolve the issue.
- Remote Peer Not Running IKE/IPsec
If the connection was refused, an ICMP error is displayed:
ipsec auto --up vpn.example.com ... 000 "vpn.example.com"[1] 192.0.2.2 #16: ERROR: asynchronous network error report on wlp2s0 (192.0.2.2:500), complainant 198.51.100.1: Connection refused [errno 111, origin ICMP type 3 code 3 (not authenticated)]
# ipsec auto --up vpn.example.com ... 000 "vpn.example.com"[1] 192.0.2.2 #16: ERROR: asynchronous network error report on wlp2s0 (192.0.2.2:500), complainant 198.51.100.1: Connection refused [errno 111, origin ICMP type 3 code 3 (not authenticated)]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IKE Algorithms
The connection fails with a
NO_PROPOSAL_CHOSENnotification during the initial setup:ipsec auto --up vpn.example.com ... 003 "vpn.example.com"[1] 193.110.157.148 #3: dropping unexpected IKE_SA_INIT message containing NO_PROPOSAL_CHOSEN notification; message payloads: N; missing payloads: SA,KE,Ni
# ipsec auto --up vpn.example.com ... 003 "vpn.example.com"[1] 193.110.157.148 #3: dropping unexpected IKE_SA_INIT message containing NO_PROPOSAL_CHOSEN notification; message payloads: N; missing payloads: SA,KE,NiCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IPsec Algorithms
The connection fails with a
NO_PROPOSAL_CHOSENerror after the initial exchange:ipsec auto --up vpn.example.com ... 182 "vpn.example.com"[1] 193.110.157.148 #5: STATE_PARENT_I2: sent v2I2, expected v2R2 {auth=IKEv2 cipher=AES_GCM_16_256 integ=n/a prf=HMAC_SHA2_256 group=MODP2048} 002 "vpn.example.com"[1] 193.110.157.148 #6: IKE_AUTH response contained the error notification NO_PROPOSAL_CHOSEN# ipsec auto --up vpn.example.com ... 182 "vpn.example.com"[1] 193.110.157.148 #5: STATE_PARENT_I2: sent v2I2, expected v2R2 {auth=IKEv2 cipher=AES_GCM_16_256 integ=n/a prf=HMAC_SHA2_256 group=MODP2048} 002 "vpn.example.com"[1] 193.110.157.148 #6: IKE_AUTH response contained the error notification NO_PROPOSAL_CHOSENCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IP Address Ranges (IKEv2)
The remote peer responds with a
TS_UNACCEPTABLEerror:ipsec auto --up vpn.example.com ... 1v2 "vpn.example.com" #1: STATE_PARENT_I2: sent v2I2, expected v2R2 {auth=IKEv2 cipher=AES_GCM_16_256 integ=n/a prf=HMAC_SHA2_512 group=MODP2048} 002 "vpn.example.com" #2: IKE_AUTH response contained the error notification TS_UNACCEPTABLE# ipsec auto --up vpn.example.com ... 1v2 "vpn.example.com" #1: STATE_PARENT_I2: sent v2I2, expected v2R2 {auth=IKEv2 cipher=AES_GCM_16_256 integ=n/a prf=HMAC_SHA2_512 group=MODP2048} 002 "vpn.example.com" #2: IKE_AUTH response contained the error notification TS_UNACCEPTABLECopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IP Address Ranges (IKEv1)
The connection times out during quick mode, with a message indicating the peer did not accept the proposal:
ipsec auto --up vpn.example.com ... 031 "vpn.example.com" #2: STATE_QUICK_I1: 60 second timeout exceeded after 0 retransmits. No acceptable response to our first Quick Mode message: perhaps peer likes no proposal
# ipsec auto --up vpn.example.com ... 031 "vpn.example.com" #2: STATE_QUICK_I1: 60 second timeout exceeded after 0 retransmits. No acceptable response to our first Quick Mode message: perhaps peer likes no proposalCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched PSK (IKEv2)
The peer rejects the connection with an
AUTHENTICATION_FAILEDerror:ipsec auto --up vpn.example.com ... 003 "vpn.example.com" #1: received Hash Payload does not match computed value 223 "vpn.example.com" #1: sending notification INVALID_HASH_INFORMATION to 192.0.2.23:500
# ipsec auto --up vpn.example.com ... 003 "vpn.example.com" #1: received Hash Payload does not match computed value 223 "vpn.example.com" #1: sending notification INVALID_HASH_INFORMATION to 192.0.2.23:500Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched PSK (IKEv1)
The hash payload does not match, making the IKE message unreadable and resulting in an
INVALID_HASH_INFORMATIONerror:ipsec auto --up vpn.example.com ... 002 "vpn.example.com" #1: IKE SA authentication request rejected by peer: AUTHENTICATION_FAILED
# ipsec auto --up vpn.example.com ... 002 "vpn.example.com" #1: IKE SA authentication request rejected by peer: AUTHENTICATION_FAILEDCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.14.4. MTU issues
Diagnose intermittent IPsec connection failures caused by Maximum Transmission Unit (MTU) issues. Encryption increases packet size, leading to fragmentation and lost data when packets exceed the network’s MTU, often seen with larger data transfers.
A common symptom is that small packets, for example pings, work correctly, but larger packets, such as an SSH session, freeze after the login. To fix the problem, lower the MTU for the tunnel by adding the mtu=1400 option to the configuration file.
7.14.5. NAT conflicts
Resolve NAT conflicts that occur when an IPsec host also acts as a NAT router. Incorrect NAT application can translate source IP addresses before encryption, causing packets to be sent unencrypted over the network.
For example, if the source IP address of the packet is translated by a masquerade rule before IPsec encryption is applied, the packet’s source no longer matches the IPsec policy, and Libreswan sends it unencrypted over the network.
To solve this problem, add a firewall rule that excludes traffic between the IPsec subnets from NAT. This rule should be inserted at the beginning of the POSTROUTING chain to ensure it is processed before the general NAT rule.
Example 7.1. Solution by using the nftables framework
The following example uses nftables to set up a basic NAT environment that excludes traffic between the 192.0.2.0/24 and 198.51.100.0/24 subnets from address translation:
nft add table ip nat
nft add chain ip nat postrouting { type nat hook postrouting priority 100 \; }
nft add rule ip nat postrouting ip saddr 192.0.2.0/24 ip daddr 198.51.100.0/24 return
# nft add table ip nat
# nft add chain ip nat postrouting { type nat hook postrouting priority 100 \; }
# nft add rule ip nat postrouting ip saddr 192.0.2.0/24 ip daddr 198.51.100.0/24 return7.14.6. Kernel-level IPsec issues
Troubleshoot kernel-level IPsec issues when a VPN tunnel appears established but no traffic flows. In this case, inspect the kernel’s IPsec state to check if the tunnel policies and cryptographic keys were correctly installed.
This process involves checking two components:
- The Security Policy Database (SPD): The rule that instructs the kernel what traffic to encrypt.
- The Security Association Database (SAD): The keys that instruct the kernel how to encrypt that traffic.
First, check if the correct policy exists in the SPD:
ip xfrm policy src 192.0.2.1/32 dst 10.0.0.0/8 dir out priority 666 ptype main tmpl src 198.51.100.13 dst 203.0.113.22 proto esp reqid 16417 mode tunnel
# ip xfrm policy
src 192.0.2.1/32 dst 10.0.0.0/8
dir out priority 666 ptype main
tmpl src 198.51.100.13 dst 203.0.113.22
proto esp reqid 16417 mode tunnel
The output should contain the policies matching your leftsubnet and rightsubnet parameters with both in and out directions. If you do not see a policy for your traffic, Libreswan failed to create the kernel rule, and traffic is not encrypted.
If the policy exists, check if it has a corresponding set of keys in the SAD:
ip xfrm state src 203.0.113.22 dst 198.51.100.13 proto esp spi 0xa78b3fdb reqid 16417 mode tunnel auth-trunc hmac(sha1) 0x3763cd3b... 96 enc cbc(aes) 0xd9dba399...
# ip xfrm state
src 203.0.113.22 dst 198.51.100.13
proto esp spi 0xa78b3fdb reqid 16417 mode tunnel
auth-trunc hmac(sha1) 0x3763cd3b... 96
enc cbc(aes) 0xd9dba399...This command displays private cryptographic keys. Do not share this output, because attackers can use it to decrypt your VPN traffic.
If a policy exists but you see no corresponding state with the same reqid, it typically means the Internet Key Exchange (IKE) negotiation failed. The two VPN endpoints could not agree on a set of keys.
For more detailed diagnostics, use the -s option with either of the commands. This option adds traffic counters, which can help you identify if the kernel processes packets by a specific rule.
7.14.7. Kernel IPsec subsystem bugs
A defect in the kernel’s IPsec subsystem can cause it to lose sync with the IKE daemon. This can lead to discrepancies between negotiated security associations and actual IPsec policy enforcement, disrupting secure network communication.
To check for kernel-level errors, display the transform (XFRM) statistics:
cat /proc/net/xfrm_stat
# cat /proc/net/xfrm_stat
If any of the counters in the output, such as XfrmInError, show a nonzero value, it indicates a problem with the kernel subsystem. In this case, open a support case, and attach the output of the command along with the corresponding IKE logs.
7.14.8. Displaying Libreswan logs
Display Libreswan logs to diagnose and troubleshoot IPsec service events and issues. Access the journal for the ipsec service to gain insights into connection status and potential problems.
To display the journal, enter:
journalctl -xeu ipsec
# journalctl -xeu ipsec
If the default logging level does not provide enough details, enable comprehensive debug logging by adding the following settings to the config setup section in the /etc/ipsec.conf file:
plutodebug=all logfile=/var/log/pluto.log
plutodebug=all
logfile=/var/log/pluto.log
Because debug logging can produce many entries, redirecting the messages to a dedicated log file can prevent the journald and systemd services from rate-limiting the messages.
Chapter 8. Setting up a WireGuard VPN
WireGuard is a high-performance VPN that runs in the Linux kernel. It uses modern cryptography and is easier to configure than other VPN solutions. Its small codebase improves security, and for authentication and encryption, it uses keys similar to SSH.
WireGuard is provided as a Technology Preview only. Technology Preview features are not supported with Red Hat production Service Level Agreements (SLAs), might not be functionally complete, and Red Hat does not recommend using them for production. These previews provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
See Technology Preview Features Support Scope on the Red Hat Customer Portal for information about the support scope for Technology Preview features.
Note that all hosts that participate in a WireGuard VPN are peers. This documentation uses the terms client to describe hosts that establish a connection and server to describe the host with the fixed hostname or IP address that the clients connect to and, optionally, route all traffic through this server.
To set up a WireGuard VPN, you must complete the following steps:
- Configure the server.
- Open the WireGuard port in the local firewall.
- Configure the clients.
WireGuard operates on the network layer (layer 3). Therefore, you cannot use DHCP and must assign static IP addresses or IPv6 global addresses to the tunnel devices on both the server and clients.
You can use WireGuard only if the Federal Information Processing Standard (FIPS) mode in RHEL is disabled.
8.1. Protocols and primitives used by WireGuard
Understanding the protocols and primitives used by WireGuard is important for evaluating its security and trustworthiness. Knowing these components enables a user to verify that the system uses modern and secure cryptographic standards.
WireGuard uses the following protocols and primitives:
- ChaCha20 for symmetric encryption, authenticated with Poly1305, using Authenticated Encryption with Associated Data (AEAD) construction
- Curve25519 for Elliptic-curve Diffie-Hellman (ECDH) key exchange
- BLAKE2s for hashing and keyed hashing
- SipHash24 for hash table keys
- HKDF for key derivation
8.2. How WireGuard uses tunnel IP addresses, public keys, and remote endpoints
WireGuard’s design tightly couples network routing with cryptographic identity, creating a Cryptokey Routing Table. This system enables the protocol to function as both a routing mechanism for outgoing traffic and an access control list for incoming packets, ensuring that only authenticated and authorized traffic is processed.
When WireGuard sends a network packet to a peer:
- WireGuard reads the destination IP from the packet and compares it to the list of allowed IP addresses in the local configuration. If the peer is not found, WireGuard drops the packet.
- If the peer is valid, WireGuard encrypts the packet using the peer’s public key.
- The sending host looks up the most recent Internet IP address of the host and sends the encrypted packet to it.
When WireGuard receives a packet:
- WireGuard decrypts the packet using the private key of the remote host.
- WireGuard reads the internal source address from the packet and looks up whether the IP is configured in the list of allowed IP addresses in the settings for the peer on the local host. If the source IP is on the allowlist, WireGuard accepts the packet. If the IP address is not on the list, WireGuard drops the packet.
8.3. Using a WireGuard client behind NAT and firewalls
WireGuard uses the UDP protocol and transmits data only when a peer sends packets. Stateful firewalls and network address translation (NAT) on routers track connections to enable a peer behind NAT or a firewall to receive packets.
To keep the connection active, WireGuard supports persistent keepalives. This means you can set an interval at which WireGuard sends keepalive packets. By default, the persistent keep-alive feature is disabled to reduce network traffic. Enable this feature on the client if you use the client in a network with NAT or if a firewall closes the connection after some time of inactivity.
Note that you cannot configure keepalive packets in WireGuard connections by using the RHEL web console. To configure this feature, edit the connection profile by using the nmcli utility.
8.4. Creating private and public keys to be used in WireGuard connections
WireGuard uses base64-encoded private and public keys to authenticate hosts to each other. Therefore, you must create the keys on each host that participates in the WireGuard VPN.
For secure connections, create different keys for each host, and ensure that you only share the public key with the remote WireGuard host. Do not use the example keys used in this documentation.
If you plan to use the RHEL web console to create a WireGuard VPN connection, you can, alternatively, generate the public and private key pairs in the web console.
Procedure
Install the
wireguard-toolspackage:dnf install wireguard-tools
# dnf install wireguard-toolsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a private key and a corresponding public key for the host:
wg genkey | tee /etc/wireguard/$HOSTNAME.private.key | wg pubkey > /etc/wireguard/$HOSTNAME.public.key
# wg genkey | tee /etc/wireguard/$HOSTNAME.private.key | wg pubkey > /etc/wireguard/$HOSTNAME.public.keyCopy to Clipboard Copied! Toggle word wrap Toggle overflow You will need the content of the key files, but not the files themselves. However, Red Hat recommends keeping the files in case that you need to remember the keys in future.
Set secure permissions on the key files:
chmod 600 /etc/wireguard/$HOSTNAME.private.key /etc/wireguard/$HOSTNAME.public.key
# chmod 600 /etc/wireguard/$HOSTNAME.private.key /etc/wireguard/$HOSTNAME.public.keyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the private key:
cat /etc/wireguard/$HOSTNAME.private.key YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg=
# cat /etc/wireguard/$HOSTNAME.private.key YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg=Copy to Clipboard Copied! Toggle word wrap Toggle overflow You will need the private key to configure the WireGuard connection on the local host. Do not share the private key.
Display the public key:
cat /etc/wireguard/$HOSTNAME.public.key UtjqCJ57DeAscYKRfp7cFGiQqdONRn69u249Fa4O6BE=
# cat /etc/wireguard/$HOSTNAME.public.key UtjqCJ57DeAscYKRfp7cFGiQqdONRn69u249Fa4O6BE=Copy to Clipboard Copied! Toggle word wrap Toggle overflow You will need the public key to configure the WireGuard connection on the remote host.
8.5. Configuring a WireGuard server by using nmcli
You can configure the WireGuard server by creating a connection profile in NetworkManager. Use this method to let NetworkManager manage the WireGuard connection.
This procedure assumes the following settings:
Server:
-
Private key:
YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg= -
Tunnel IPv4 address:
192.0.2.1/24 -
Tunnel IPv6 address:
2001:db8:1::1/64
-
Private key:
Client:
-
Public key:
bnwfQcC8/g2i4vvEqcRUM2e6Hi3Nskk6G9t4r26nFVM= -
Tunnel IPv4 address:
192.0.2.2/24 -
Tunnel IPv6 address:
2001:db8:1::2/64
-
Public key:
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the server
- The static tunnel IP addresses and subnet masks of the client
- The public key of the client
- The static tunnel IP addresses and subnet masks of the server
Procedure
Add a NetworkManager WireGuard connection profile:
nmcli connection add type wireguard con-name server-wg0 ifname wg0 autoconnect no
# nmcli connection add type wireguard con-name server-wg0 ifname wg0 autoconnect noCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates a profile named
server-wg0and assigns the virtual interfacewg0to it. To prevent the connection from starting automatically after you add it without finalizing the configuration, disable theautoconnectparameter.Set the tunnel IPv4 address and subnet mask of the server:
nmcli connection modify server-wg0 ipv4.method manual ipv4.addresses 192.0.2.1/24
# nmcli connection modify server-wg0 ipv4.method manual ipv4.addresses 192.0.2.1/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the tunnel IPv6 address and subnet mask of the server:
nmcli connection modify server-wg0 ipv6.method manual ipv6.addresses 2001:db8:1::1/64
# nmcli connection modify server-wg0 ipv6.method manual ipv6.addresses 2001:db8:1::1/64Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the server’s private key to the connection profile:
nmcli connection modify server-wg0 wireguard.private-key "YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg="
# nmcli connection modify server-wg0 wireguard.private-key "YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg="Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the port for incoming WireGuard connections:
nmcli connection modify server-wg0 wireguard.listen-port 51820
# nmcli connection modify server-wg0 wireguard.listen-port 51820Copy to Clipboard Copied! Toggle word wrap Toggle overflow Always set a fixed port number on hosts that receive incoming WireGuard connections. If you do not set a port, WireGuard uses a random free port each time you activate the
wg0interface.Add peer connection configurations for each client that you want to allow to communicate with this server:
nmcli connection modify client-wg0 wireguard.peers 'bnwfQcC8/g2i4vvEqcRUM2e6Hi3Nskk6G9t4r26nFVM= allowed-ips=192.0.2.2;2001:db8:1::2'
nmcli connection modify client-wg0 wireguard.peers 'bnwfQcC8/g2i4vvEqcRUM2e6Hi3Nskk6G9t4r26nFVM= allowed-ips=192.0.2.2;2001:db8:1::2'Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
wireguard.peersparameter defines the peer section of the client in the NetworkManager connection profile.Optional: Configure the connection to start automatically, enter:
nmcli connection modify server-wg0 autoconnect yes
# nmcli connection modify server-wg0 autoconnect yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reactivate the
server-wg0connection:nmcli connection up server-wg0
# nmcli connection up server-wg0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.6. Configuring a WireGuard server by using nmtui
You can configure the WireGuard server by creating a connection profile in NetworkManager. Use this method to let NetworkManager manage the WireGuard connection.
This procedure assumes the following settings:
Server:
-
Private key:
YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg= -
Tunnel IPv4 address:
192.0.2.1/24 -
Tunnel IPv6 address:
2001:db8:1::1/64
-
Private key:
Client:
-
Public key:
bnwfQcC8/g2i4vvEqcRUM2e6Hi3Nskk6G9t4r26nFVM= -
Tunnel IPv4 address:
192.0.2.2/24 -
Tunnel IPv6 address:
2001:db8:1::2/64
-
Public key:
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the server
- The static tunnel IP addresses and subnet masks of the client
- The public key of the client
- The static tunnel IP addresses and subnet masks of the server
-
You installed the
NetworkManager-tuipackage.
Procedure
Start the
nmtuiapplication:nmtui
# nmtuiCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Select Edit a connection, and press Enter.
- Select , and press Enter.
- Select the WireGuard connection type in the list, and press Enter.
In the Edit connection window:
-
Enter the name of the connection and the virtual interface, such as
wg0, that NetworkManager should assign to the connection. - Enter the private key of the server.
Set the listen port number, such as
51820, for incoming WireGuard connections.Always set a fixed port number on hosts that receive incoming WireGuard connections. If you do not set a port, WireGuard uses a random free port each time you activate the interface.
Click next to the Peers pane:
- Enter the public key of the client.
- Set the Allowed IPs field to the tunnel IP addresses of the client that are allowed to send data to this server.
Select , and press Enter.

Select next to *IPv4 Configuration, and press Enter.
- Select the IPv4 configuration method Manual.
- Enter the tunnel IPv4 address and the subnet mask. Leave the Gateway field empty.
Select next to IPv6 Configuration, and press Enter.
- Select the IPv6 configuration method Manual.
-
Enter the tunnel IPv6 address and the subnet mask. Leave the
Gatewayfield empty.
Select , and press Enter

-
Enter the name of the connection and the virtual interface, such as
- In the window with the list of connections, select , and press Enter.
- In the NetworkManager TUI main window, select , and press Enter.
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.7. Configuring a WireGuard server by using the RHEL web console
You can configure a WireGuard server by using the browser-based RHEL web console. Use this method to let NetworkManager manage the WireGuard connection.
Prerequisites
- You are logged in to the RHEL web console.
You know the following information:
- The static tunnel IP addresses and subnet masks of both the server and client
- The public key of the client
Procedure
- Select the Networking tab in the navigation on the left side of the screen.
- Click Add VPN in the Interfaces section.
-
If the
wireguard-toolsandsystemd-resolvedpackages are not already installed, the web console displays a corresponding notification. Click Install to install these packages. - Enter the name of the WireGuard device that you want to create.
Configure the key pair of this host:
If you want use the keys that the web console has created:
- Keep the pre-selected Generated option in the Private key area.
- Note the Public key value. You require this information when you configure the client.
If you want to use an existing private key:
- Select Paste existing key in the Private key area.
- Paste the private key into the text field. The web console automatically calculates the corresponding public key.
Set a listen port number, such as
51820, for incoming WireGuard connections.Always set a fixed port number on hosts that receive incoming WireGuard connections. If you do not set a port, WireGuard uses a random free port each time you activate the interface.
Set the tunnel IPv4 address and subnet mask of the server.
To also set an IPv6 address, you must edit the connection after you have created it.
Add peer configurations for each client that you want to allow to communicate with this server:
- Click Add peer.
- Enter the public key of the client.
- Leave the Endpoint field empty.
- Set the Allowed IPs field to the tunnel IP addresses of the clients that are allowed to send data to this server.
- Click Add to create the WireGuard connection.
If you want to also set a tunnel IPv6 address:
- Click on the WireGuard connection’s name in the Interfaces section.
- Click edit next to IPv6.
-
Set the Addresses field to
Manual, and enter the tunnel IPv6 address and prefix of the server. - Click Save.
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.8. Configuring a WireGuard server by using nm-connection-editor
You can configure the WireGuard server by creating a connection profile in NetworkManager. Use this method to let NetworkManager manage the WireGuard connection.
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the server
- The static tunnel IP addresses and subnet masks of the client
- The public key of the client
- The static tunnel IP addresses and subnet masks of the server
Procedure
Open a terminal, and enter:
nm-connection-editor
# nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Add a new connection by clicking the button.
-
Select the
WireGuardconnection type, and click . - Optional: Update the connection name.
-
On the
Generaltab, selectConnect automatically with priority. Optionally, set a priority value. On the
WireGuardtab:-
Enter the name of the virtual interface, such as
wg0, that NetworkManager should assign to the connection. - Enter the private key of the server.
Set the listen port number, such as
51820, for incoming WireGuard connections.Always set a fixed port number on hosts that receive incoming WireGuard connections. If you do not set a port, WireGuard uses a random free port each time you activate the interface.
Click to add peers:
- Enter the public key of the client.
-
Set the
Allowed IPsfield to the tunnel IP addresses of the client that are allowed to send data to this server. - Click .
-
Enter the name of the virtual interface, such as
On the
IPv4 Settingstab:-
Select
Manualin theMethodlist. -
Click to enter the tunnel IPv4 address and the subnet mask. Leave the
Gatewayfield empty.
-
Select
On the
IPv6 Settingstab:-
Select
Manualin theMethodlist. -
Click to enter the tunnel IPv6 address and the subnet mask. Leave the
Gatewayfield empty.
-
Select
- Click to store the connection profile.
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.9. Configuring a WireGuard server by using the wg-quick service
You can configure the WireGuard server by creating a configuration file in the /etc/wireguard/ directory. Use this method to configure the service independently from NetworkManager.
This procedure assumes the following settings:
Server:
-
Private key:
YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg= -
Tunnel IPv4 address:
192.0.2.1/24 -
Tunnel IPv6 address:
2001:db8:1::1/64
-
Private key:
Client:
-
Public key:
bnwfQcC8/g2i4vvEqcRUM2e6Hi3Nskk6G9t4r26nFVM= -
Tunnel IPv4 address:
192.0.2.2/24 -
Tunnel IPv6 address:
2001:db8:1::2/64
-
Public key:
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the server
- The static tunnel IP addresses and subnet masks of the client
- The public key of the client
- The static tunnel IP addresses and subnet masks of the server
Procedure
Install the
wireguard-toolspackage:dnf install wireguard-tools
# dnf install wireguard-toolsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
/etc/wireguard/wg0.conffile with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
[Interface]section describes the WireGuard settings of the interface on the server:-
Address: A comma-separated list of the server’s tunnel IP addresses. -
PrivateKey: The private key of the server. ListenPort: The port on which WireGuard listens for incoming UDP connections.Always set a fixed port number on hosts that receive incoming WireGuard connections. If you do not set a port, WireGuard uses a random free port each time you activate the
wg0interface.
-
Each
[Peer]section describes the settings of one client:-
PublicKey: The public key of the client. -
AllowedIPs: The tunnel IP addresses of the client that are allowed to send data to this server.
-
Enable and start the WireGuard connection:
systemctl enable --now wg-quick@wg0
# systemctl enable --now wg-quick@wg0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The systemd instance name must match the name of the configuration file in the
/etc/wireguard/directory without the.confsuffix. The service also uses this name for the virtual network interface.- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.10. Configuring firewalld on a WireGuard server by using the command line
Configure the firewalld service on the WireGuard server, allowing incoming connections from clients. If clients need to use the server as their default gateway and route all traffic through the tunnel, enable also masquerading.
Procedure
Open the WireGuard port for incoming connections in the
firewalldservice:firewall-cmd --permanent --add-port=51820/udp --zone=public
# firewall-cmd --permanent --add-port=51820/udp --zone=publicCopy to Clipboard Copied! Toggle word wrap Toggle overflow If clients should route all traffic through the tunnel and use the WireGuard server as the default gateway, enable masquerading for the
publiczone:firewall-cmd --permanent --zone=public --add-masquerade
# firewall-cmd --permanent --zone=public --add-masqueradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reload the
firewalldrules.firewall-cmd --reload
# firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the configuration of the
publiczone:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.11. Configuring firewalld on a WireGuard server by using the RHEL web console
Configure the firewalld service on the WireGuard server, allowing incoming connections from clients. If clients need to use the server as their default gateway and route all traffic through the tunnel, enable also masquerading.
Prerequisites
- You are logged in to the RHEL web console.
Procedure
- Select the Networking tab in the navigation on the left side of the screen.
- Click Edit rules and zones in the Firewall section.
- Click Add services.
-
Enter
wireguardinto the Filter services field. Select the
wireguardentry from the list.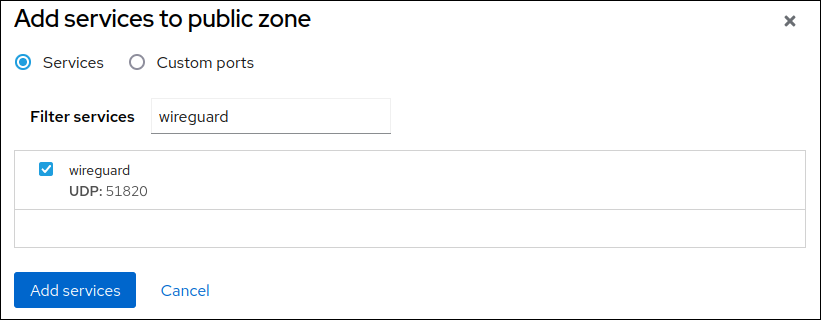
- Click Add services.
If clients should route all traffic through the tunnel and use the WireGuard server as the default gateway, enable masquerading for the
publiczone:firewall-cmd --permanent --zone=public --add-masquerade firewall-cmd --reload
# firewall-cmd --permanent --zone=public --add-masquerade # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that you cannot enable masquerading in
firewalldzones in the web console.
Verification
- Select the Networking tab in the navigation on the left side of the screen.
- Click Edit rules and zones in the Firewall section.
-
The list contains an entry for the
wireguardservice and displays the UDP port that you configured in the WireGuard connection profile. To verify that masquerading is enabled in the
publiczone offirewalld, enter:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.12. Configuring firewalld on a WireGuard server by using the graphical interface
Configure the firewalld service on the WireGuard server, allowing incoming connections from clients. If clients need to use the server as their default gateway and route all traffic through the tunnel, enable also masquerading.
Procedure
-
Press the Super key, enter
firewall, and select the Firewall application from the results. -
Select
Permanentin the Configuration list. -
Select the
publiczone. Allow incoming connections to the WireGuard port:
- On the Ports tab, click .
- Enter the port number you set for incoming WireGuard connections:
-
Select
udpfrom theProtocollist. - Click .
If clients should route all traffic through the tunnel and use the WireGuard server as the default gateway:
- Navigate to the Masquerading tab of the public zone.
-
Select
Masquerade zone.
- Select → .
Verification
Display the configuration of the
publiczone:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.13. Configuring a WireGuard client by using nmcli
You can configure a WireGuard client by creating a connection profile in NetworkManager. Use this method to let NetworkManager manage the WireGuard connection.
This procedure assumes the following settings:
Client:
-
Private key:
aPUcp5vHz8yMLrzk8SsDyYnV33IhE/k20e52iKJFV0A= -
Tunnel IPv4 address:
192.0.2.2/24 -
Tunnel IPv6 address:
2001:db8:1::2/64
-
Private key:
Server:
-
Public key:
UtjqCJ57DeAscYKRfp7cFGiQqdONRn69u249Fa4O6BE= -
Tunnel IPv4 address:
192.0.2.1/24 -
Tunnel IPv6 address:
2001:db8:1::1/64
-
Public key:
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the client
- The static tunnel IP addresses and subnet masks of the client
- The public key of the server
- The static tunnel IP addresses and subnet masks of the server
Procedure
Add a NetworkManager WireGuard connection profile:
nmcli connection add type wireguard con-name client-wg0 ifname wg0
# nmcli connection add type wireguard con-name client-wg0 ifname wg0Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates a profile named
client-wg0and assigns the virtual interfacewg0to it.Optional: Configure NetworkManager so that it does not automatically start the
client-wgconnection:nmcli connection modify client-wg0 autoconnect no
# nmcli connection modify client-wg0 autoconnect noCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the tunnel IPv4 address and subnet mask of the client:
nmcli connection modify client-wg0 ipv4.method manual ipv4.addresses 192.0.2.2/24
# nmcli connection modify client-wg0 ipv4.method manual ipv4.addresses 192.0.2.2/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the tunnel IPv6 address and subnet mask of the client:
nmcli connection modify client-wg0 ipv6.method manual ipv6.addresses 2001:db8:1::2/64
# nmcli connection modify client-wg0 ipv6.method manual ipv6.addresses 2001:db8:1::2/64Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you want to route all traffic through the tunnel, set the tunnel IP addresses of the server as the default gateway:
nmcli connection modify client-wg0 ipv4.gateway 192.0.2.1 ipv6.gateway 2001:db8:1::1
# nmcli connection modify client-wg0 ipv4.gateway 192.0.2.1 ipv6.gateway 2001:db8:1::1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Routing all traffic through the tunnel requires that you set, in a later step, the
allowed-ipson this client to0.0.0.0/0;::/0.Note that routing all traffic through the tunnel can impact the connectivity to other hosts based on the server routing and firewall configuration.
Add the client’s private key to the connection profile:
nmcli connection modify client-wg0 wireguard.private-key "aPUcp5vHz8yMLrzk8SsDyYnV33IhE/k20e52iKJFV0A="
# nmcli connection modify client-wg0 wireguard.private-key "aPUcp5vHz8yMLrzk8SsDyYnV33IhE/k20e52iKJFV0A="Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add peer connection configurations for each server that you want to allow to communicate with this client:
nmcli connection modify client-wg0 wireguard.peers 'kEyMNyYhpmn9zPQ4m7iGmU9G7nooS9eeUBe0Y0wO0gM= endpoint=server.example.com:51820 allowed-ips=0.0.0.0/0 ;::/0'
# nmcli connection modify client-wg0 wireguard.peers 'kEyMNyYhpmn9zPQ4m7iGmU9G7nooS9eeUBe0Y0wO0gM= endpoint=server.example.com:51820 allowed-ips=0.0.0.0/0 ;::/0'Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
wireguard.peersparameter defines the peer section of the client in the NetworkManager connection profile. Use0.0.0.0/0;::/0;inallowed-ipsto allow any remote IPv4 and IPv6 address to communicate with this client. Use this setting to route all traffic through the tunnel and use the WireGuard server as default gateway.Reactivate the
client-wg0connection:nmcli connection up client-wg0
# nmcli connection up client-wg0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Ping the IP addresses of the server:
ping 192.0.2.1 ping6 2001:db8:1::1
# ping 192.0.2.1 # ping6 2001:db8:1::1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Note that the output has only the
latest handshakeandtransferentries if you have already sent traffic through the VPN tunnel.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.14. Configuring a WireGuard client by using nmtui
You can configure a WireGuard client by creating a connection profile in NetworkManager. Use this method to let NetworkManager manage the WireGuard connection.
This procedure assumes the following settings:
Client:
-
Private key:
aPUcp5vHz8yMLrzk8SsDyYnV33IhE/k20e52iKJFV0A= -
Tunnel IPv4 address:
192.0.2.2/24 -
Tunnel IPv6 address:
2001:db8:1::2/64
-
Private key:
Server:
-
Public key:
UtjqCJ57DeAscYKRfp7cFGiQqdONRn69u249Fa4O6BE= -
Tunnel IPv4 address:
192.0.2.1/24 -
Tunnel IPv6 address:
2001:db8:1::1/64
-
Public key:
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the client
- The static tunnel IP addresses and subnet masks of the client
- The public key of the server
- The static tunnel IP addresses and subnet masks of the server
-
You installed the
NetworkManager-tuipackage
Procedure
Start the
nmtuiapplication:nmtui
# nmtuiCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Select Edit a connection, and press Enter.
- Select , and press Enter.
- Select the WireGuard connection type in the list, and press Enter.
In the Edit connection window:
-
Enter the name of the connection and the virtual interface, such as
wg0, that NetworkManager should assign to the connection. Enter the private key of the client.
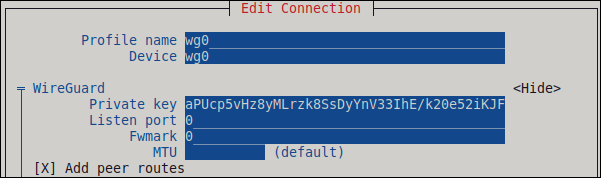
Click next to the Peers pane:
- Enter the public key of the server.
Set the Allowed IPs field. For example, set it to:
- The tunnel IP addresses of the server to allow only the server to communicate with this client.
-
0.0.0.0/0,::/0to allow any remote IPv4 and IPv6 address to communicate with this client. Use this setting to route all traffic through the tunnel and use the WireGuard server as default gateway.
-
Enter the host name or IP address and port of the WireGuard server into the Endpoint field. Use the following format:
<hostname_or_IP>:<port_number> - Optional: If you use the client in a network with network address translation (NAT) or if a firewall closes the UDP connection after some time of inactivity, set a persistent keep alive interval in seconds. In this interval, the client sends a keepalive packet to the server.
Select , and press Enter.
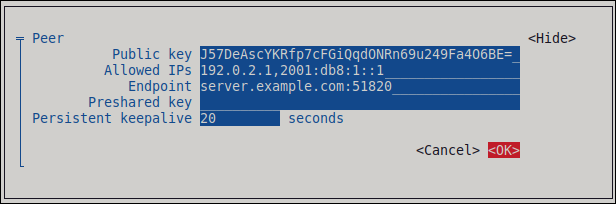
Select next to IPv4 Configuration, and press Enter.
- Select the IPv4 configuration method Manual.
- Enter the tunnel IPv4 address and the subnet mask. Leave the Gateway field empty.
Select next to IPv6 Configuration, and press Enter.
- Select the IPv6 configuration method Manual.
- Enter the tunnel IPv6 address and the subnet mask. Leave the Gateway field empty.
- Optional: Select Automatically connect.
Select , and press Enter

-
Enter the name of the connection and the virtual interface, such as
- In the window with the list of connections, select , and press Enter.
- In the NetworkManager TUI main window, select , and press Enter.
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Ping the IP addresses of the server:
ping 192.0.2.1 ping6 2001:db8:1::1
# ping 192.0.2.1 # ping6 2001:db8:1::1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Note that the output contains only the
latest handshakeandtransferentries if you have already sent traffic through the VPN tunnel.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.15. Configuring a WireGuard client by using the RHEL web console
You can configure a WireGuard client by using the browser-based RHEL web console. Use this method to let NetworkManager manage the WireGuard connection.
Prerequisites
- You are logged in to the RHEL web console.
You know the following information:
- The static tunnel IP addresses and subnet masks of both the server and client
- The public key of the server
Procedure
- Select the Networking tab in the navigation on the left side of the screen.
- Click Add VPN in the Interfaces section.
-
If the
wireguard-toolsandsystemd-resolvedpackages are not already installed, the web console displays a corresponding notification. Click Install to install these packages. - Enter the name of the WireGuard device that you want to create.
Configure the key pair of this host:
If you want use the keys that the web console has created:
- Keep the pre-selected Generated option in the Private key area.
- Note the Public key value. You require this information when you configure the client.
If you want to use an existing private key:
- Select Paste existing key in the Private key area.
- Paste the private key into the text field. The web console automatically calculates the corresponding public key.
-
Preserve the
0value in the Listen port field. Set the tunnel IPv4 address and subnet mask of the client.
To also set an IPv6 address, you must edit the connection after you have created it.
Add a peer configuration for the server that you want to allow to communicate with this client:
- Click Add peer.
- Enter the public key of the server.
-
Set the Endpoint field to the hostname or IP address and the port of the server, for example
server.example.com:51820. The client uses this information to establish the connection. Set the Allowed IPs field to the tunnel IP addresses of the clients that are allowed to send data to this server. For example, set the field to one of the following:
- The tunnel IP addresses of the server to allow only the server to communicate with this client. The value in the screen capture below configures this scenario.
-
0.0.0.0/0to allow any remote IPv4 address to communicate with this client. Use this setting to route all traffic through the tunnel and use the WireGuard server as default gateway.
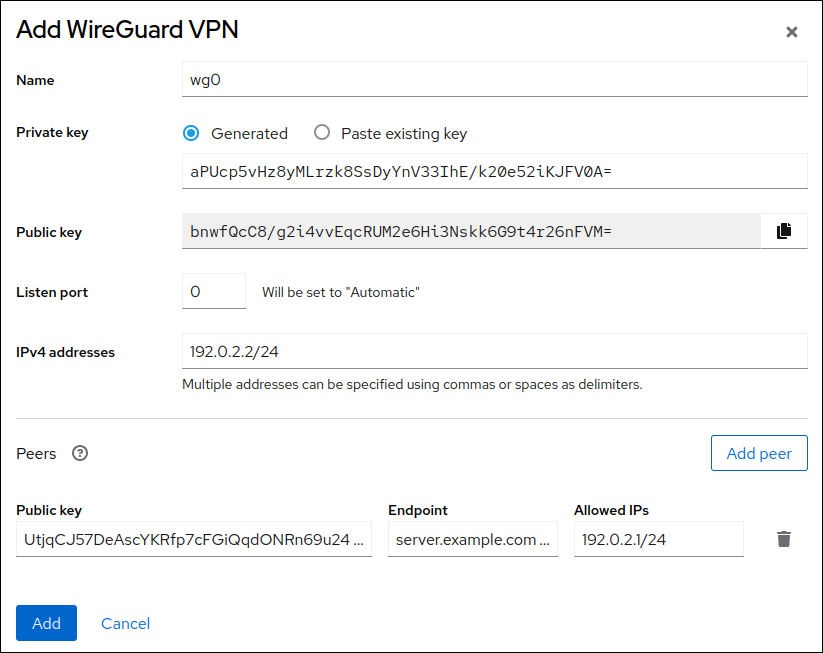
- Click Add to create the WireGuard connection.
If you want to also set a tunnel IPv6 address:
- Click on the WireGuard connection’s name in the Interfaces section.
- Click Edit next to IPv6.
-
Set the Addresses field to
Manual, and enter the tunnel IPv6 address and prefix of the client. - Click Save.
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Ping the IP addresses of the server:
ping 192.0.2.1
# ping 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow WireGuard establishes the connection when you try to send traffic through the tunnel.
Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Note that the output has only the
latest handshakeandtransferentries if you have already sent traffic through the VPN tunnel.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.16. Configuring a WireGuard client by using nm-connection-editor
You can configure a WireGuard client by creating a connection profile in NetworkManager. Use this method to let NetworkManager manage the WireGuard connection.
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the client
- The static tunnel IP addresses and subnet masks of the client
- The public key of the server
- The static tunnel IP addresses and subnet masks of the server
Procedure
Open a terminal, and enter:
nm-connection-editor
# nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Add a new connection by clicking the button.
- Select the WireGuard connection type, and click .
- Optional: Update the connection name.
- Optional: On the General tab, select Connect automatically with priority.
On the WireGuard tab:
-
Enter the name of the virtual interface, such as
wg0, that NetworkManager should assign to the connection. - Enter client’s private key.
Click to add peers:
- Enter the public key of the server.
Set the Allowed IPs field. For example, set it to:
- The tunnel IP addresses of the server to allow only the server to communicate with this client.
0.0.0.0/0;::/0;to allow any remote IPv4 and IPv6 address to communicate with this client. Use this setting to route all traffic through the tunnel and use the WireGuard server as default gateway.Note that routing all traffic through the tunnel can impact the connectivity to other hosts based on the server routing and firewall configuration.
-
Enter the hostname or IP address and port of the WireGuard server into the Endpoint field. Use the following format:
<hostname_or_IP<:<port_number> - Optional: If you use the client in a network with network address translation (NAT) or if a firewall closes the UDP connection after some time of inactivity, set a persistent keep alive interval in seconds. In this interval, the client sends a keep alive packet to the server.
- Click .
-
Enter the name of the virtual interface, such as
On the IPv4 Settings tab:
- Select Manual in the Method list.
- Click to enter the tunnel IPv4 address and the subnet mask.
If you want to route all traffic through the tunnel, set the tunnel IPv4 address of the server in the Gateway field. Otherwise, leave the field empty.
Routing all IPv4 traffic through the tunnel requires that you included
0.0.0.0/0in the Allowed IPs field on this client.
On the IPv6 Settings tab:
- Select Manual in the Method list.
- Click to enter the tunnel IPv6 address and the subnet mask.
If you want to route all traffic through the tunnel, set the tunnel IPv6 address of the server in the Gateway field. Otherwise, leave the field empty.
Routing all IPv4 traffic through the tunnel requires that you included
::/0in the Allowed IPs field on this client.
- Click to store the connection profile.
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Ping the IP addresses of the server:
ping 192.0.2.1 ping6 2001:db8:1::1
# ping 192.0.2.1 # ping6 2001:db8:1::1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Note that the output only has the
latest handshakeandtransferentries if you have already sent traffic through the VPN tunnel.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.17. Configuring a WireGuard client by using the wg-quick service
You can configure a WireGuard client by creating a configuration file in the /etc/wireguard/ directory. Use this method to configure the service independently from NetworkManager.
This procedure assumes the following settings:
Client:
-
Private key:
aPUcp5vHz8yMLrzk8SsDyYnV33IhE/k20e52iKJFV0A= -
Tunnel IPv4 address:
192.0.2.2/24 -
Tunnel IPv6 address:
2001:db8:1::2/64
-
Private key:
Server:
-
Public key:
UtjqCJ57DeAscYKRfp7cFGiQqdONRn69u249Fa4O6BE= -
Tunnel IPv4 address:
192.0.2.1/24 -
Tunnel IPv6 address:
2001:db8:1::1/64
-
Public key:
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the client
- The static tunnel IP addresses and subnet masks of the client
- The public key of the server
- The static tunnel IP addresses and subnet masks of the server
Procedure
Install the
wireguard-toolspackage:dnf install wireguard-tools
# dnf install wireguard-toolsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
/etc/wireguard/wg0.conffile with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
[Interface]section describes the WireGuard settings of the interface on the client:-
Address: A comma-separated list of the client’s tunnel IP addresses. -
PrivateKey: The private key of the client.
-
The
[Peer]section describes the settings of the server:-
PublicKey: The public key of the server. AllowedIPs: The IP addresses that are allowed to send data to this client. For example, set the parameter to:- The tunnel IP addresses of the server to allow only the server to communicate with this client. The value in the example above configures this scenario.
-
0.0.0.0/0, ::/0to allow any remote IPv4 and IPv6 address to communicate with this client. Use this setting to route all traffic through the tunnel and use the WireGuard server as default gateway.
-
Endpoint: Sets the hostname or IP address and the port of the server. The client uses this information to establish the connection. -
The optional
persistent-keepaliveparameter defines an interval in seconds in which WireGuard sends a keepalive packet to the server. Set this parameter if you use the client in a network with network address translation (NAT) or if a firewall closes the UDP connection after some time of inactivity.
-
Enable and start the WireGuard connection:
systemctl enable --now wg-quick@wg0
# systemctl enable --now wg-quick@wg0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The systemd instance name must match the name of the configuration file in the
/etc/wireguard/directory without the.confsuffix. The service also uses this name for the virtual network interface.- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Ping the IP addresses of the server:
ping 192.0.2.1 ping6 2001:db8:1::1
# ping 192.0.2.1 # ping6 2001:db8:1::1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Note that the output contains only the
latest handshakeandtransferentries if you have already sent traffic through the VPN tunnel.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.18. Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel
To protect your VPN connection from traffic redirection attacks, assign it to a dedicated routing table. This prevents malicious network servers from bypassing the secure tunnel and compromising data integrity.
Both a DHCP server and Stateless Address Autoconfiguration (SLAAC) can add routes to a client’s routing table. For example, a malicious DHCP server can use this feature to force a host with VPN connection to redirect traffic through a physical interface instead of the VPN tunnel. This vulnerability is also known as TunnelVision and described in the CVE-2024-3661 vulnerability article.
To mitigate this vulnerability, you can assign the VPN connection to a dedicated routing table. This prevents the DHCP configuration or SLAAC from manipulating routing decisions for network packets intended for the VPN tunnel.
Follow the steps if at least one of the conditions applies to your environment:
- At least one network interface uses DHCP or SLAAC.
- Your network does not use mechanisms, such as DHCP snooping, that prevent a rogue DHCP server.
Routing the entire traffic through the VPN prevents the host from accessing local network resources.
Prerequisites
- You use NetworkManager 1.48.10-5 or later.
Procedure
- Decide which routing table you want to use. The following steps use table 75. By default, RHEL does not use the tables 1-254, and you can use any of them.
Configure the VPN connection profile to place the VPN routes in a dedicated routing table:
nmcli connection modify <vpn_connection_profile> ipv4.route-table 75 ipv6.route-table 75
# nmcli connection modify <vpn_connection_profile> ipv4.route-table 75 ipv6.route-table 75Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set a low priority value for the table you used in the previous command:
nmcli connection modify <vpn_connection_profile> ipv4.routing-rules "priority 32345 from all table 75" ipv6.routing-rules "priority 32345 from all table 75"
# nmcli connection modify <vpn_connection_profile> ipv4.routing-rules "priority 32345 from all table 75" ipv6.routing-rules "priority 32345 from all table 75"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The priority value can be any value between 1 and 32766. The lower the value, the higher the priority.
Reconnect the VPN connection:
nmcli connection down <vpn_connection_profile> nmcli connection up <vpn_connection_profile>
# nmcli connection down <vpn_connection_profile> # nmcli connection up <vpn_connection_profile>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 routes in table 75:
ip route show table 75 ... 192.0.2.0/24 via 192.0.2.254 dev vpn_device proto static metric 50 default dev vpn_device proto static scope link metric 50
# ip route show table 75 ... 192.0.2.0/24 via 192.0.2.254 dev vpn_device proto static metric 50 default dev vpn_device proto static scope link metric 50Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that both the route to the remote network and the default gateway are assigned to routing table 75 and, therefore, all traffic is routed through the tunnel. If you set
ipv4.never-default truein the VPN connection profile, a default route is not created and, therefore, not visible in this output.Display the IPv6 routes in table 75:
ip -6 route show table 75 ... 2001:db8:1::/64 dev vpn_device proto kernel metric 50 pref medium default dev vpn_device proto static metric 50 pref medium
# ip -6 route show table 75 ... 2001:db8:1::/64 dev vpn_device proto kernel metric 50 pref medium default dev vpn_device proto static metric 50 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that both the route to the remote network and the default gateway are assigned to routing table 75 and, therefore, all traffic is routed through the tunnel. If you set
ipv6.never-default truein the VPN connection profile, a default route is not created and, therefore, not visible in this output.
Chapter 9. Configuring IP tunnels
Similar to a VPN, an IP tunnel directly connects two networks over a third network, such as the internet. However, not all tunnel protocols support encryption.
The routers in both networks that establish the tunnel requires at least two interfaces:
- One interface that is connected to the local network
- One interface that is connected to the network through which the tunnel is established.
To establish the tunnel, you create a virtual interface on both routers with an IP address from the remote subnet.
NetworkManager supports the following IP tunnels:
- Generic Routing Encapsulation (GRE)
- Generic Routing Encapsulation over IPv6 (IP6GRE)
- Generic Routing Encapsulation Terminal Access Point (GRETAP)
- Generic Routing Encapsulation Terminal Access Point over IPv6 (IP6GRETAP)
- IPv4 over IPv4 (IPIP)
- IPv4 over IPv6 (IPIP6)
- IPv6 over IPv6 (IP6IP6)
- Simple Internet Transition (SIT)
Depending on the type, these tunnels act either on layer 2 or 3 of the Open Systems Interconnection (OSI) model.
9.1. Configuring an IPIP tunnel to encapsulate IPv4 traffic in IPv4 packets
An IP over IP (IPIP) tunnel operates on OSI layer 3 and encapsulates IPv4 traffic in IPv4 packets.
Data sent through an IPIP tunnel is not encrypted. For security reasons, use the tunnel only for data that is already encrypted, for example, by other protocols, such as HTTPS.
Note that IPIP tunnels support only unicast packets. If you require an IPv4 tunnel that supports multicast, see Configuring a GRE tunnel to encapsulate layer-3 traffic in IPv4 packets.
For example, you can create an IPIP tunnel between two RHEL routers to connect two internal subnets over the internet as shown in the following diagram:
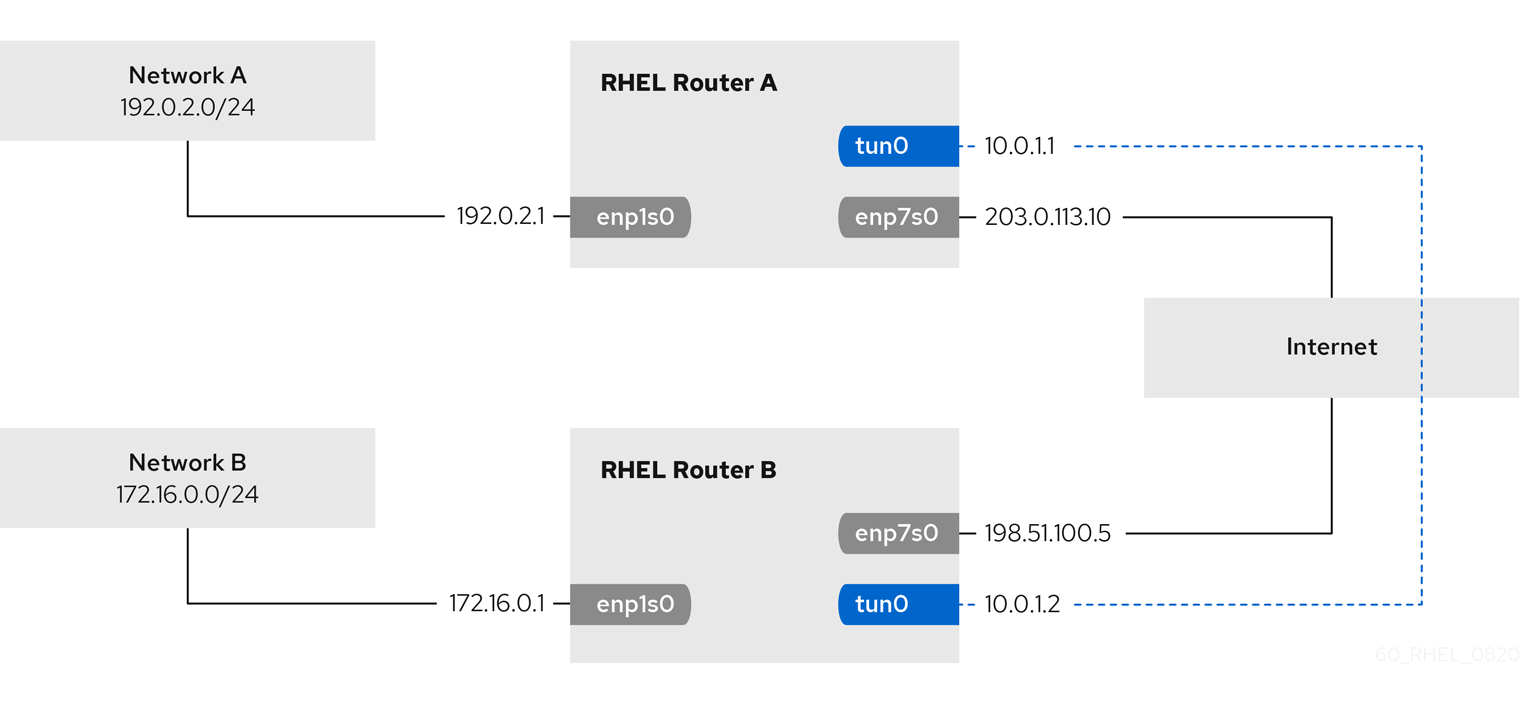
Prerequisites
- Each RHEL router has a network interface that is connected to its local subnet.
- Each RHEL router has a network interface that is connected to the internet.
- The traffic you want to send through the tunnel is IPv4 unicast.
Procedure
On the RHEL router in network A:
Create an IPIP tunnel interface named
tun0:nmcli connection add type ip-tunnel ip-tunnel.mode ipip con-name tun0 ifname tun0 remote 198.51.100.5 local 203.0.113.10
# nmcli connection add type ip-tunnel ip-tunnel.mode ipip con-name tun0 ifname tun0 remote 198.51.100.5 local 203.0.113.10Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
remoteandlocalparameters set the public IP addresses of the remote and the local routers.Set the IPv4 address to the
tun0device:nmcli connection modify tun0 ipv4.addresses '10.0.1.1/30'
# nmcli connection modify tun0 ipv4.addresses '10.0.1.1/30'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that a
/30subnet with two usable IP addresses is sufficient for the tunnel.Configure the
tun0connection to use a manual IPv4 configuration:nmcli connection modify tun0 ipv4.method manual
# nmcli connection modify tun0 ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a static route that routes traffic to the
172.16.0.0/24network to the tunnel IP on router B:nmcli connection modify tun0 +ipv4.routes "172.16.0.0/24 10.0.1.2"
# nmcli connection modify tun0 +ipv4.routes "172.16.0.0/24 10.0.1.2"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
tun0connection.nmcli connection up tun0
# nmcli connection up tun0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable packet forwarding:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow
On the RHEL router in network B:
Create an IPIP tunnel interface named
tun0:nmcli connection add type ip-tunnel ip-tunnel.mode ipip con-name tun0 ifname tun0 remote 203.0.113.10 local 198.51.100.5
# nmcli connection add type ip-tunnel ip-tunnel.mode ipip con-name tun0 ifname tun0 remote 203.0.113.10 local 198.51.100.5Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
remoteandlocalparameters set the public IP addresses of the remote and local routers.Set the IPv4 address to the
tun0device:nmcli connection modify tun0 ipv4.addresses '10.0.1.2/30'
# nmcli connection modify tun0 ipv4.addresses '10.0.1.2/30'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the
tun0connection to use a manual IPv4 configuration:nmcli connection modify tun0 ipv4.method manual
# nmcli connection modify tun0 ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a static route that routes traffic to the
192.0.2.0/24network to the tunnel IP on router A:nmcli connection modify tun0 +ipv4.routes "192.0.2.0/24 10.0.1.1"
# nmcli connection modify tun0 +ipv4.routes "192.0.2.0/24 10.0.1.1"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
tun0connection.nmcli connection up tun0
# nmcli connection up tun0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable packet forwarding:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
From each RHEL router, ping the IP address of the internal interface of the other router:
On Router A, ping
172.16.0.1:ping 172.16.0.1
# ping 172.16.0.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Router B, ping
192.0.2.1:ping 192.0.2.1
# ping 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.2. Configuring a GRE tunnel to encapsulate layer-3 traffic in IPv4 packets
A Generic Routing Encapsulation (GRE) tunnel encapsulates layer-3 traffic in IPv4 packets. A GRE tunnel can encapsulate any layer 3 protocol with a valid Ethernet type.
Data sent through a GRE tunnel is not encrypted. For security reasons, use the tunnel only for data that is already encrypted, for example, by other protocols, such as HTTPS.
For example, you can create a GRE tunnel between two RHEL routers to connect two internal subnets over the internet as shown in the following diagram:
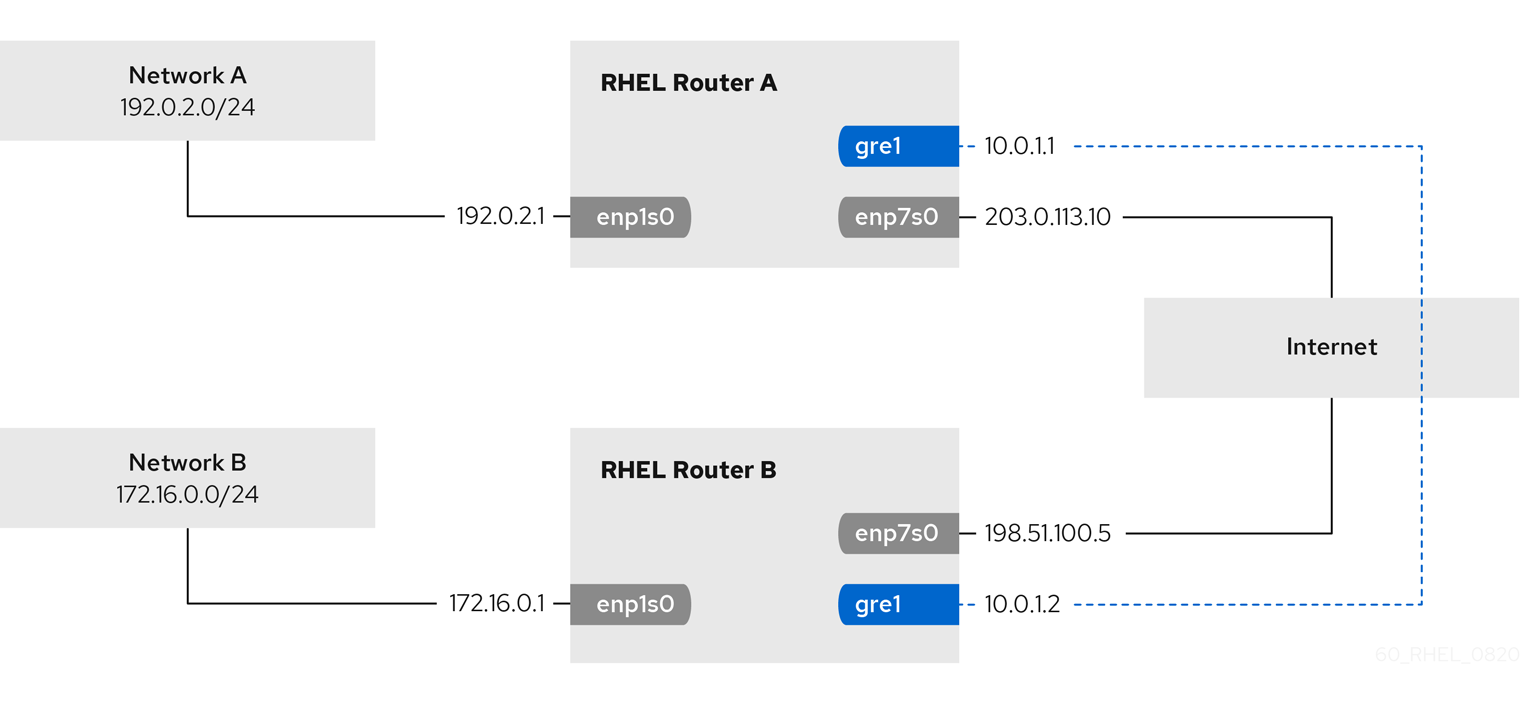
Prerequisites
- Each RHEL router has a network interface that is connected to its local subnet.
- Each RHEL router has a network interface that is connected to the internet.
Procedure
On the RHEL router in network A:
Create a GRE tunnel interface named
gre1:nmcli connection add type ip-tunnel ip-tunnel.mode gre con-name gre1 ifname gre1 remote 198.51.100.5 local 203.0.113.10
# nmcli connection add type ip-tunnel ip-tunnel.mode gre con-name gre1 ifname gre1 remote 198.51.100.5 local 203.0.113.10Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
remoteandlocalparameters set the public IP addresses of the remote and the local routers.ImportantThe
gre0device name is reserved. Usegre1or a different name for the device.Set the IPv4 address to the
gre1device:nmcli connection modify gre1 ipv4.addresses '10.0.1.1/30'
# nmcli connection modify gre1 ipv4.addresses '10.0.1.1/30'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that a
/30subnet with two usable IP addresses is sufficient for the tunnel.Configure the
gre1connection to use a manual IPv4 configuration:nmcli connection modify gre1 ipv4.method manual
# nmcli connection modify gre1 ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a static route that routes traffic to the
172.16.0.0/24network to the tunnel IP on router B:nmcli connection modify gre1 +ipv4.routes "172.16.0.0/24 10.0.1.2"
# nmcli connection modify gre1 +ipv4.routes "172.16.0.0/24 10.0.1.2"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
gre1connection.nmcli connection up gre1
# nmcli connection up gre1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable packet forwarding:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow
On the RHEL router in network B:
Create a GRE tunnel interface named
gre1:nmcli connection add type ip-tunnel ip-tunnel.mode gre con-name gre1 ifname gre1 remote 203.0.113.10 local 198.51.100.5
# nmcli connection add type ip-tunnel ip-tunnel.mode gre con-name gre1 ifname gre1 remote 203.0.113.10 local 198.51.100.5Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
remoteandlocalparameters set the public IP addresses of the remote and the local routers.Set the IPv4 address to the
gre1device:nmcli connection modify gre1 ipv4.addresses '10.0.1.2/30'
# nmcli connection modify gre1 ipv4.addresses '10.0.1.2/30'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the
gre1connection to use a manual IPv4 configuration:nmcli connection modify gre1 ipv4.method manual
# nmcli connection modify gre1 ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a static route that routes traffic to the
192.0.2.0/24network to the tunnel IP on router A:nmcli connection modify gre1 +ipv4.routes "192.0.2.0/24 10.0.1.1"
# nmcli connection modify gre1 +ipv4.routes "192.0.2.0/24 10.0.1.1"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
gre1connection.nmcli connection up gre1
# nmcli connection up gre1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable packet forwarding:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
From each RHEL router, ping the IP address of the internal interface of the other router:
On Router A, ping
172.16.0.1:ping 172.16.0.1
# ping 172.16.0.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Router B, ping
192.0.2.1:ping 192.0.2.1
# ping 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.3. Configuring a GRETAP tunnel to transfer Ethernet frames over IPv4
A Generic Routing Encapsulation Terminal Access Point (GRETAP) tunnel operates on OSI level 2 and encapsulates Ethernet traffic in IPv4 packets.
Data sent through a GRETAP tunnel is not encrypted. For security reasons, establish the tunnel over a VPN or a different encrypted connection.
For example, you can create a GRETAP tunnel between two RHEL routers to connect two networks using a bridge as shown in the following diagram:
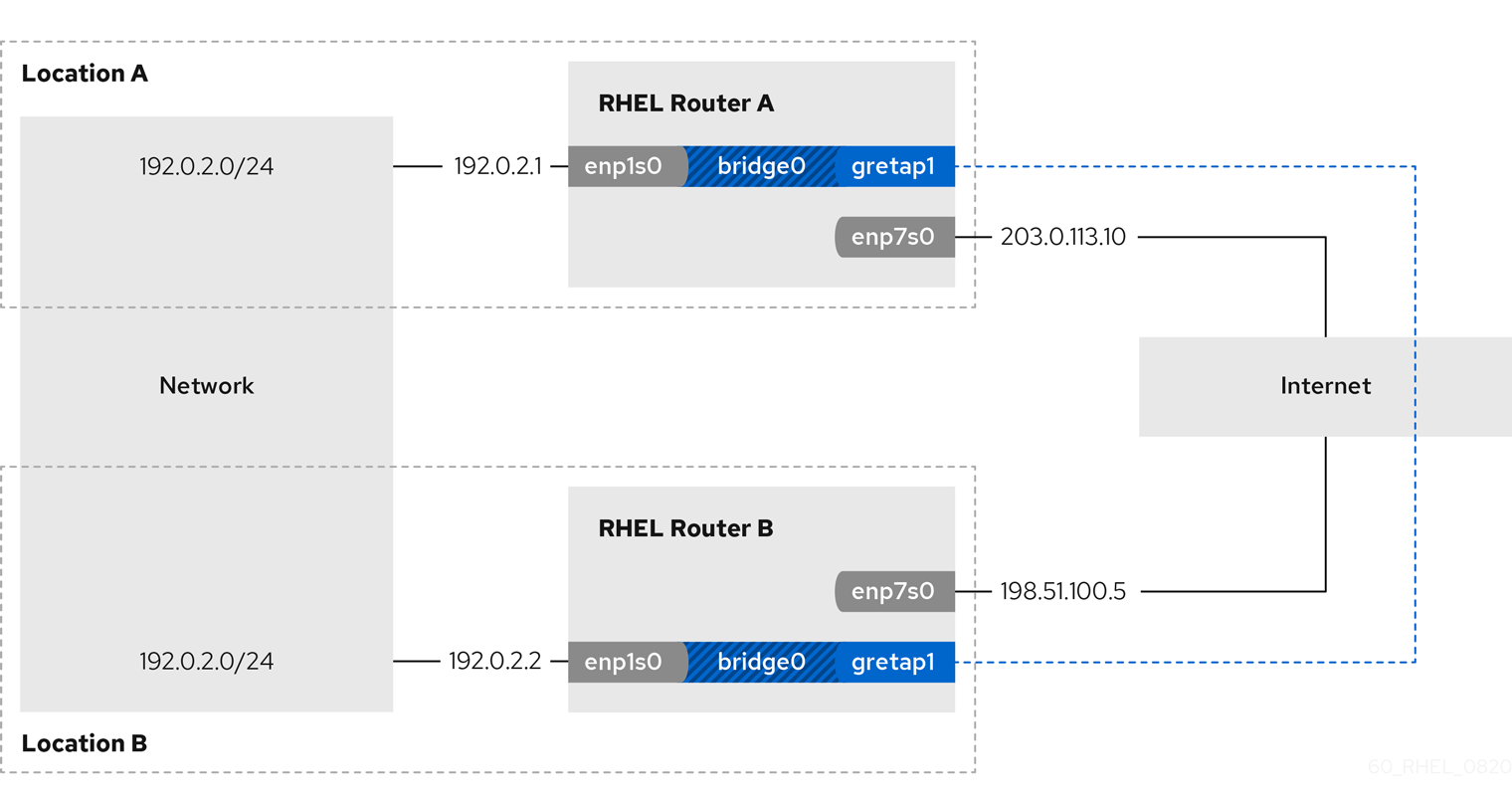
Prerequisites
- Each RHEL router has a network interface that is connected to its local network, and the interface has no IP configuration assigned.
- Each RHEL router has a network interface that is connected to the internet.
Procedure
On the RHEL router in network A:
Create a bridge interface named
bridge0:nmcli connection add type bridge con-name bridge0 ifname bridge0
# nmcli connection add type bridge con-name bridge0 ifname bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the IP settings of the bridge:
nmcli connection modify bridge0 ipv4.addresses '192.0.2.1/24' nmcli connection modify bridge0 ipv4.method manual
# nmcli connection modify bridge0 ipv4.addresses '192.0.2.1/24' # nmcli connection modify bridge0 ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a new connection profile for the interface that is connected to local network to the bridge:
nmcli connection add type ethernet port-type bridge con-name bridge0-port1 ifname enp1s0 controller bridge0
# nmcli connection add type ethernet port-type bridge con-name bridge0-port1 ifname enp1s0 controller bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add a new connection profile for the GRETAP tunnel interface to the bridge:
nmcli connection add type ip-tunnel ip-tunnel.mode gretap port-type bridge con-name bridge0-port2 ifname gretap1 remote 198.51.100.5 local 203.0.113.10 controller bridge0
# nmcli connection add type ip-tunnel ip-tunnel.mode gretap port-type bridge con-name bridge0-port2 ifname gretap1 remote 198.51.100.5 local 203.0.113.10 controller bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
remoteandlocalparameters set the public IP addresses of the remote and the local routers.ImportantThe
gretap0device name is reserved. Usegretap1or a different name for the device.Optional: Disable the Spanning Tree Protocol (STP) if you do not need it:
nmcli connection modify bridge0 bridge.stp no
# nmcli connection modify bridge0 bridge.stp noCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, STP is enabled and causes a delay before you can use the connection.
Configure that activating the
bridge0connection automatically activates the ports of the bridge:nmcli connection modify bridge0 connection.autoconnect-ports 1
# nmcli connection modify bridge0 connection.autoconnect-ports 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Active the
bridge0connection:nmcli connection up bridge0
# nmcli connection up bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
On the RHEL router in network B:
Create a bridge interface named
bridge0:nmcli connection add type bridge con-name bridge0 ifname bridge0
# nmcli connection add type bridge con-name bridge0 ifname bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the IP settings of the bridge:
nmcli connection modify bridge0 ipv4.addresses '192.0.2.2/24' nmcli connection modify bridge0 ipv4.method manual
# nmcli connection modify bridge0 ipv4.addresses '192.0.2.2/24' # nmcli connection modify bridge0 ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a new connection profile for the interface that is connected to local network to the bridge:
nmcli connection add type ethernet port-type bridge con-name bridge0-port1 ifname enp1s0 controller bridge0
# nmcli connection add type ethernet port-type bridge con-name bridge0-port1 ifname enp1s0 controller bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add a new connection profile for the GRETAP tunnel interface to the bridge:
nmcli connection add type ip-tunnel ip-tunnel.mode gretap port-type bridge con-name bridge0-port2 ifname gretap1 remote 203.0.113.10 local 198.51.100.5 controller bridge0
# nmcli connection add type ip-tunnel ip-tunnel.mode gretap port-type bridge con-name bridge0-port2 ifname gretap1 remote 203.0.113.10 local 198.51.100.5 controller bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
remoteandlocalparameters set the public IP addresses of the remote and the local routers.Optional: Disable the Spanning Tree Protocol (STP) if you do not need it:
nmcli connection modify bridge0 bridge.stp no
# nmcli connection modify bridge0 bridge.stp noCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure that activating the
bridge0connection automatically activates the ports of the bridge:nmcli connection modify bridge0 connection.autoconnect-ports 1
# nmcli connection modify bridge0 connection.autoconnect-ports 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Active the
bridge0connection:nmcli connection up bridge0
# nmcli connection up bridge0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
On both routers, verify that the
enp1s0andgretap1connections are connected and that theCONNECTIONcolumn displays the connection name of the port:Copy to Clipboard Copied! Toggle word wrap Toggle overflow From each RHEL router, ping the IP address of the internal interface of the other router:
On Router A, ping
192.0.2.2:ping 192.0.2.2
# ping 192.0.2.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Router B, ping
192.0.2.1:ping 192.0.2.1
# ping 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 10. Using a VXLAN to create a virtual layer-2 domain for VMs
A virtual extensible LAN (VXLAN) is a networking protocol that tunnels layer-2 traffic over an IP network using the UDP protocol. For example, certain virtual machines (VMs) that are running on different hosts can communicate over a VXLAN tunnel. The hosts can be in different subnets or even in different data centers around the world. From the perspective of the VMs, other VMs in the same VXLAN are within the same layer-2 domain:
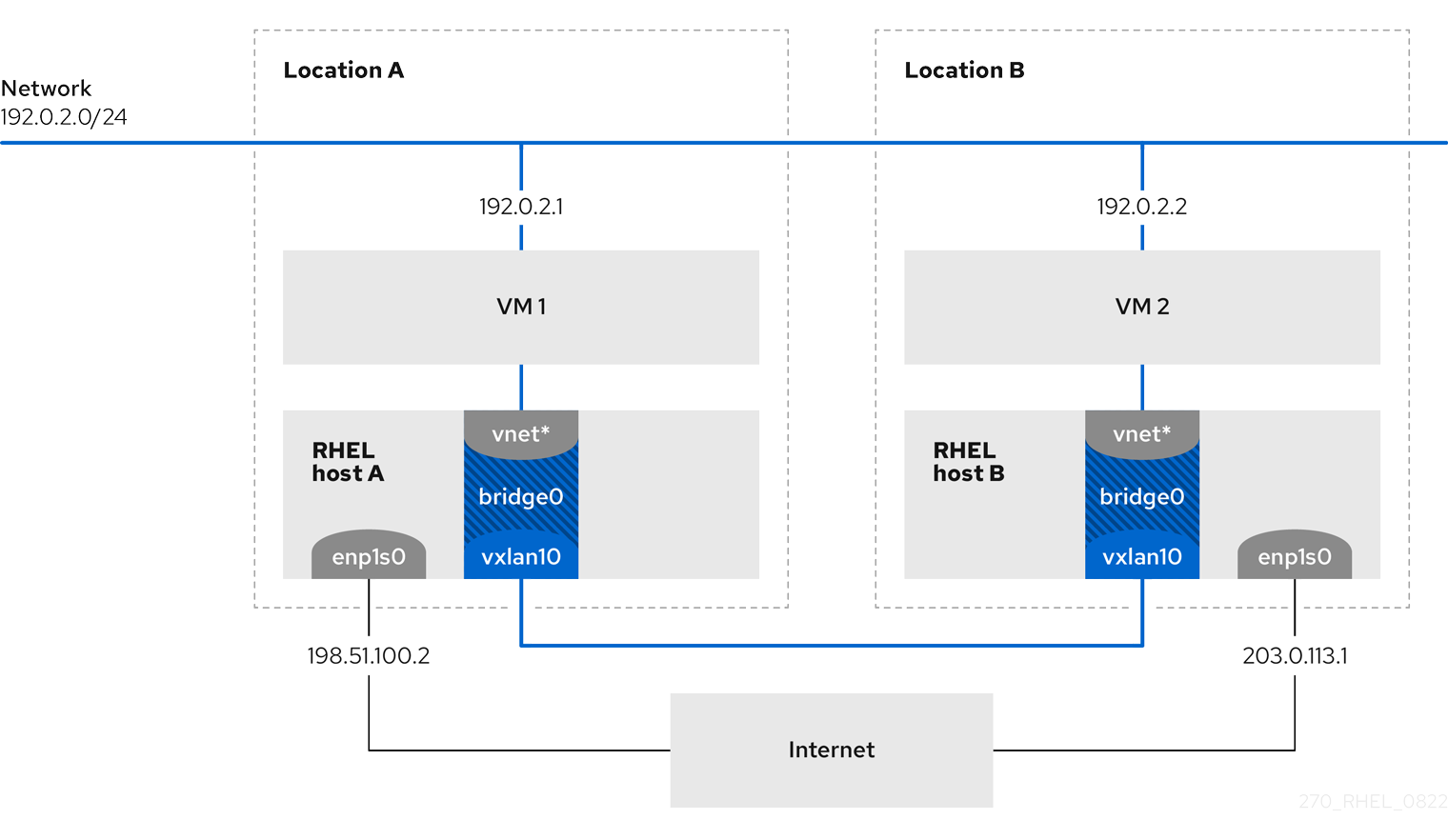
In this example, RHEL-host-A and RHEL-host-B use a bridge, br0, to connect the virtual network of a VM on each host with a VXLAN named vxlan10. Due to this configuration, the VXLAN is invisible to the VMs, and the VMs do not require any special configuration. If you later connect more VMs to the same virtual network, the VMs are automatically members of the same virtual layer-2 domain.
Just as normal layer-2 traffic, data in a VXLAN is not encrypted. For security reasons, use a VXLAN over a VPN or other types of encrypted connections.
10.1. Benefits of VXLANs
A virtual extensible LAN (VXLAN) provides the following major benefits:
- VXLANs use a 24-bit ID. Therefore, you can create up to 16,777,216 isolated networks. For example, a virtual LAN (VLAN), supports only 4,096 isolated networks.
- VXLANs use the IP protocol. This enables you to route the traffic and virtually run systems in different networks and locations within the same layer-2 domain.
- Unlike most tunnel protocols, a VXLAN is not only a point-to-point network. A VXLAN can learn the IP addresses of the other endpoints either dynamically or use statically-configured forwarding entries.
- Certain network cards support UDP tunnel-related offload features.
For further details, see the /usr/share/doc/kernel-doc-<kernel_version>/Documentation/networking/vxlan.rst file provided by the kernel-doc package.
10.2. Configuring the Ethernet interface on the hosts
To connect a RHEL VM host to the Ethernet, create a network connection profile, configure the IP settings, and activate the profile.
Run this procedure on both RHEL hosts, and adjust the IP address configuration accordingly.
Prerequisites
- The host is connected to the Ethernet.
Procedure
Add a new Ethernet connection profile to NetworkManager:
nmcli connection add con-name Example ifname enp1s0 type ethernet
# nmcli connection add con-name Example ifname enp1s0 type ethernetCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the IPv4 settings:
nmcli connection modify Example ipv4.addresses 198.51.100.2/24 ipv4.method manual ipv4.gateway 198.51.100.254 ipv4.dns 198.51.100.200 ipv4.dns-search example.com
# nmcli connection modify Example ipv4.addresses 198.51.100.2/24 ipv4.method manual ipv4.gateway 198.51.100.254 ipv4.dns 198.51.100.200 ipv4.dns-search example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Skip this step if the network uses DHCP.
Activate the
Exampleconnection:nmcli connection up Example
# nmcli connection up ExampleCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the status of the devices and connections:
nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet connected Example
# nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet connected ExampleCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ping a host in a remote network to verify the IP settings:
ping RHEL-host-B.example.com
# ping RHEL-host-B.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that you cannot ping the other VM host before you have configured the network on that host as well.
10.3. Creating a network bridge with a VXLAN attached
To make a virtual extensible LAN (VXLAN) invisible to virtual machines (VMs), create a bridge on a host, and attach the VXLAN to the bridge. Use NetworkManager to create both the bridge and the VXLAN. You do not add any traffic access point (TAP) devices of the VMs, typically named vnet* on the host, to the bridge. The libvirtd service adds them dynamically when the VMs start.
Run this procedure on both RHEL hosts, and adjust the IP addresses accordingly.
Procedure
Create the bridge
br0:nmcli connection add type bridge con-name br0 ifname br0 ipv4.method disabled ipv6.method disabled
# nmcli connection add type bridge con-name br0 ifname br0 ipv4.method disabled ipv6.method disabledCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command sets no IPv4 and IPv6 addresses on the bridge device, because this bridge works on layer 2.
Create the VXLAN interface and attach it to
br0:nmcli connection add type vxlan port-type bridge con-name br0-vxlan10 ifname vxlan10 id 10 local 198.51.100.2 remote 203.0.113.1 controller br0
# nmcli connection add type vxlan port-type bridge con-name br0-vxlan10 ifname vxlan10 id 10 local 198.51.100.2 remote 203.0.113.1 controller br0Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command uses the following settings:
-
id 10: Sets the VXLAN identifier. -
local 198.51.100.2: Sets the source IP address of outgoing packets. -
remote 203.0.113.1: Sets the unicast or multicast IP address to use in outgoing packets when the destination link layer address is not known in the VXLAN device forwarding database. -
controller br0: Sets this VXLAN connection to be created as a port in thebr0connection. -
ipv4.method disabledandipv6.method disabled: Disables IPv4 and IPv6 on the bridge.
By default, NetworkManager uses
8472as the destination port. If the destination port is different, additionally, pass thedestination-port <port_number>option to the command.-
Activate the
br0connection profile:nmcli connection up br0
# nmcli connection up br0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Open port
8472for incoming UDP connections in the local firewall:firewall-cmd --permanent --add-port=8472/udp firewall-cmd --reload
# firewall-cmd --permanent --add-port=8472/udp # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the forwarding table:
bridge fdb show dev vxlan10 2a:53:bd:d5:b3:0a master br0 permanent 00:00:00:00:00:00 dst 203.0.113.1 self permanent ...
# bridge fdb show dev vxlan10 2a:53:bd:d5:b3:0a master br0 permanent 00:00:00:00:00:00 dst 203.0.113.1 self permanent ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.4. Creating a virtual network in libvirt with an existing bridge
To enable virtual machines (VM) to use the br0 bridge with the attached virtual extensible LAN (VXLAN), first add a virtual network to the libvirtd service that uses this bridge.
Prerequisites
-
You installed the
libvirtpackage. -
You started and enabled the
libvirtdservice. -
You configured the
br0device with the VXLAN on RHEL.
Procedure
Create the
~/vxlan10-bridge.xmlfile with the following content:<network> <name>vxlan10-bridge</name> <forward mode="bridge" /> <bridge name="br0" /> </network>
<network> <name>vxlan10-bridge</name> <forward mode="bridge" /> <bridge name="br0" /> </network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
~/vxlan10-bridge.xmlfile to create a new virtual network inlibvirt:virsh net-define ~/vxlan10-bridge.xml
# virsh net-define ~/vxlan10-bridge.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the
~/vxlan10-bridge.xmlfile:rm ~/vxlan10-bridge.xml
# rm ~/vxlan10-bridge.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the
vxlan10-bridgevirtual network:virsh net-start vxlan10-bridge
# virsh net-start vxlan10-bridgeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the
vxlan10-bridgevirtual network to start automatically when thelibvirtdservice starts:virsh net-autostart vxlan10-bridge
# virsh net-autostart vxlan10-bridgeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the list of virtual networks:
virsh net-list Name State Autostart Persistent ---------------------------------------------------- vxlan10-bridge active yes yes ...
# virsh net-list Name State Autostart Persistent ---------------------------------------------------- vxlan10-bridge active yes yes ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.5. Configuring virtual machines to use VXLAN
To configure a VM to use a bridge device with an attached virtual extensible LAN (VXLAN) on the host, create a new VM that uses the vxlan10-bridge virtual network or update the settings of existing VMs to use this network.
Perform this procedure on the RHEL hosts.
Prerequisites
-
You configured the
vxlan10-bridgevirtual network inlibvirtd.
Procedure
To create a new VM and configure it to use the
vxlan10-bridgenetwork, pass the--network network:vxlan10-bridgeoption to thevirt-installcommand when you create the VM:virt-install ... --network network:vxlan10-bridge
# virt-install ... --network network:vxlan10-bridgeCopy to Clipboard Copied! Toggle word wrap Toggle overflow To change the network settings of an existing VM:
Connect the VM’s network interface to the
vxlan10-bridgevirtual network:virt-xml VM_name --edit --network network=vxlan10-bridge
# virt-xml VM_name --edit --network network=vxlan10-bridgeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Shut down the VM, and start it again:
virsh shutdown VM_name virsh start VM_name
# virsh shutdown VM_name # virsh start VM_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the virtual network interfaces of the VM on the host:
virsh domiflist VM_name Interface Type Source Model MAC ------------------------------------------------------------------- vnet1 bridge vxlan10-bridge virtio 52:54:00:c5:98:1c
# virsh domiflist VM_name Interface Type Source Model MAC ------------------------------------------------------------------- vnet1 bridge vxlan10-bridge virtio 52:54:00:c5:98:1cCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the interfaces attached to the
vxlan10-bridgebridge:ip link show master vxlan10-bridge 18: vxlan10: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br0 state UNKNOWN mode DEFAULT group default qlen 1000 link/ether 2a:53:bd:d5:b3:0a brd ff:ff:ff:ff:ff:ff 19: vnet1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br0 state UNKNOWN mode DEFAULT group default qlen 1000 link/ether 52:54:00:c5:98:1c brd ff:ff:ff:ff:ff:ff# ip link show master vxlan10-bridge 18: vxlan10: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br0 state UNKNOWN mode DEFAULT group default qlen 1000 link/ether 2a:53:bd:d5:b3:0a brd ff:ff:ff:ff:ff:ff 19: vnet1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br0 state UNKNOWN mode DEFAULT group default qlen 1000 link/ether 52:54:00:c5:98:1c brd ff:ff:ff:ff:ff:ffCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the
libvirtdservice dynamically updates the bridge’s configuration. When you start a VM which uses thevxlan10-bridgenetwork, the correspondingvnet*device on the host appears as a port of the bridge.Use address resolution protocol (ARP) requests to verify whether VMs are in the same VXLAN:
- Start two or more VMs in the same VXLAN.
Send an ARP request from one VM to the other one:
arping -c 1 192.0.2.2 ARPING 192.0.2.2 from 192.0.2.1 enp1s0 Unicast reply from 192.0.2.2 [52:54:00:c5:98:1c] 1.450ms Sent 1 probe(s) (0 broadcast(s)) Received 1 response(s) (0 request(s), 0 broadcast(s))
# arping -c 1 192.0.2.2 ARPING 192.0.2.2 from 192.0.2.1 enp1s0 Unicast reply from 192.0.2.2 [52:54:00:c5:98:1c] 1.450ms Sent 1 probe(s) (0 broadcast(s)) Received 1 response(s) (0 request(s), 0 broadcast(s))Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the command shows a reply, the VM is in the same layer-2 domain and, in this case in the same VXLAN.
Install the
iputilspackage to use thearpingutility.
Chapter 11. Managing wifi connections
If your host contains a wifi adapter, you can connect it to a wifi network.
-
Use the
nmcliutility to configure connections by using the command line. -
Use the
nmtuiapplication to configure connections in a text-based user interface. - Use the GNOME system menu to quickly connect to wifi networks that do not require any configuration.
-
Use the
GNOME Settingsapplication to configure connections by using the GNOME application. -
Use the
nm-connection-editorapplication to configure connections in a graphical user interface. -
Use the
networkRHEL system role to automate the configuration of connections on one or multiple hosts.
11.1. Supported wifi security types
Depending on the security type a wifi network supports, you can transmit data more or less securely.
Do not connect to wifi networks that do not use encryption or which support only the insecure WEP or WPA standards.
RHEL 9 supports the following wifi security types:
-
None: Encryption is disabled, and data is transferred in plain text over the network. -
Enhanced Open: With opportunistic wireless encryption (OWE), devices negotiate unique pairwise master keys (PMK) to encrypt connections in wireless networks without authentication. -
LEAP: The Lightweight Extensible Authentication Protocol, which was developed by Cisco, is a proprietary version of the extensible authentication protocol (EAP). -
WPA & WPA2 Personal: In personal mode, the Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access 2 (WPA2) authentication methods use a pre-shared key. -
WPA & WPA2 Enterprise: In enterprise mode, WPA and WPA2 use the EAP framework and authenticate users to a remote authentication dial-in user service (RADIUS) server. -
WPA3 Personal: Wi-Fi Protected Access 3 (WPA3) Personal uses simultaneous authentication of equals (SAE) instead of pre-shared keys (PSK) to prevent dictionary attacks. WPA3 uses perfect forward secrecy (PFS).
11.2. Connecting to a wifi network by using nmcli
When you first use the nmcli utility to connect to a wifi network, it automatically creates a NetworkManager connection profile. You can then modify this profile to add specific settings, such as a static IP address.
Prerequisites
- A wifi device is installed on the host.
-
The wifi device is enabled. To verify, use the
nmcli radiocommand.
Procedure
If the wifi radio has been disabled in NetworkManager, enable this feature:
nmcli radio wifi on
# nmcli radio wifi onCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Display the available wifi networks:
nmcli device wifi list IN-USE BSSID SSID MODE CHAN RATE SIGNAL BARS SECURITY 00:53:00:2F:3B:08 Office Infra 44 270 Mbit/s 57 ▂▄▆_ WPA2 WPA3 00:53:00:15:03:BF -- Infra 1 130 Mbit/s 48 ▂▄__ WPA2 WPA3# nmcli device wifi list IN-USE BSSID SSID MODE CHAN RATE SIGNAL BARS SECURITY 00:53:00:2F:3B:08 Office Infra 44 270 Mbit/s 57 ▂▄▆_ WPA2 WPA3 00:53:00:15:03:BF -- Infra 1 130 Mbit/s 48 ▂▄__ WPA2 WPA3Copy to Clipboard Copied! Toggle word wrap Toggle overflow The service set identifier (
SSID) column contains the names of the networks. If the column shows--, the access point of this network does not broadcast an SSID.Connect to the wifi network:
nmcli device wifi connect Office --ask Password: wifi-password
# nmcli device wifi connect Office --ask Password: wifi-passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you prefer to set the password in the command instead of entering it interactively, use the
password <wifi_password>option in the command instead of--ask:nmcli device wifi connect Office password <wifi_password>
# nmcli device wifi connect Office password <wifi_password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that, if the network requires static IP addresses, NetworkManager fails to activate the connection at this point. You can configure the IP addresses in later steps.
If the network requires static IP addresses:
Configure the IPv4 address settings, for example:
nmcli connection modify Office ipv4.method manual ipv4.addresses 192.0.2.1/24 ipv4.gateway 192.0.2.254 ipv4.dns 192.0.2.200 ipv4.dns-search example.com
# nmcli connection modify Office ipv4.method manual ipv4.addresses 192.0.2.1/24 ipv4.gateway 192.0.2.254 ipv4.dns 192.0.2.200 ipv4.dns-search example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the IPv6 address settings, for example:
nmcli connection modify Office ipv6.method manual ipv6.addresses 2001:db8:1::1/64 ipv6.gateway 2001:db8:1::fffe ipv6.dns 2001:db8:1::ffbb ipv6.dns-search example.com
# nmcli connection modify Office ipv6.method manual ipv6.addresses 2001:db8:1::1/64 ipv6.gateway 2001:db8:1::fffe ipv6.dns 2001:db8:1::ffbb ipv6.dns-search example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Re-activate the connection:
nmcli connection up Office
# nmcli connection up OfficeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the active connections:
nmcli connection show --active NAME ID TYPE DEVICE Office 2501eb7e-7b16-4dc6-97ef-7cc460139a58 wifi wlp0s20f3
# nmcli connection show --active NAME ID TYPE DEVICE Office 2501eb7e-7b16-4dc6-97ef-7cc460139a58 wifi wlp0s20f3Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the output lists the wifi connection you have created, the connection is active.
Ping a hostname or IP address:
ping -c 3 example.com
# ping -c 3 example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.4. Connecting to a wifi network by using GNOME Settings
You can use the GNOME Settings application, also named gnome-control-center, to connect to a wifi network and configure the connection. When you connect to the network for the first time, GNOME creates a NetworkManager connection profile for it.
In GNOME Settings, you can configure wifi connections for all wifi network security types that RHEL supports.
Prerequisites
- A wifi device is installed on the host.
-
The wifi device is enabled. To verify, use the
nmcli radiocommand.
Procedure
-
Press the Super key, type
Wi-Fi, and press Enter. - Click on the name of the wifi network you want to connect to.
-
Enter the password for the network, and click
Connect. If the network requires additional settings, such as static IP addresses or a security type other than WPA2 Personal:
- Click the gear icon next to the network’s name.
Optional: Configure the network profile on the
Detailstab to not automatically connect.If you deactivate this feature, you must always manually connect to the network, for example, by using GNOME Settings or the GNOME system menu.
-
Configure IPv4 settings on the
IPv4tab, and IPv6 settings on theIPv6tab. On the
Securitytab, select the authentication of the network, such asWPA3 Personal, and enter the password.Depending on the selected security, the application shows additional fields. Fill them accordingly. For details, ask the administrator of the wifi network.
-
Click
Apply.
Verification
Open the system menu on the right side of the top bar, and verify that the wifi network is connected:
If the network appears in the list, it is connected.
Ping a hostname or IP address:
ping -c 3 example.com
# ping -c 3 example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.5. Configuring a wifi connection by using nmtui
The nmtui application provides a text-based user interface for NetworkManager. You can use nmtui to connect to a wifi network.
In nmtui:
- Navigate by using the cursor keys.
- Press a button by selecting it and hitting Enter.
- Select and clear checkboxes by using Space.
- To return to the previous screen, use ESC.
Procedure
Start
nmtui:nmtui
# nmtuiCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Select
Edit a connection, and press Enter. -
Press the
Addbutton. -
Select
Wi-Fifrom the list of network types, and press Enter. Optional: Enter a name for the NetworkManager profile to be created.
On hosts with multiple profiles, a meaningful name makes it easier to identify the purpose of a profile.
-
Enter the name of the Wi-Fi network, the Service Set Identifier (SSID), into the
SSIDfield. -
Leave the
Modefield set to its default,Client. Select the
Securityfield, press Enter, and set the authentication type of the network from the list.Depending on the authentication type you have selected,
nmtuidisplays different fields.- Fill the authentication type-related fields.
If the Wi-Fi network requires static IP addresses:
-
Press the
Automaticbutton next to the protocol, and selectManualfrom the displayed list. -
Press the
Showbutton next to the protocol you want to configure to display additional fields, and fill them.
-
Press the
-
Press the
OKbutton to create and automatically activate the new connection. -
Press the
Backbutton to return to the main menu. -
Select
Quit, and press Enter to close thenmtuiapplication.
Verification
Display the active connections:
nmcli connection show --active NAME ID TYPE DEVICE Office 2501eb7e-7b16-4dc6-97ef-7cc460139a58 wifi wlp0s20f3
# nmcli connection show --active NAME ID TYPE DEVICE Office 2501eb7e-7b16-4dc6-97ef-7cc460139a58 wifi wlp0s20f3Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the output lists the wifi connection you have created, the connection is active.
Ping a hostname or IP address:
ping -c 3 example.com
# ping -c 3 example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.6. Configuring a wifi connection by using nm-connection-editor
You can use the nm-connection-editor application to create a connection profile for a wireless network. In this application you can configure all wifi network authentication types that RHEL supports.
By default, NetworkManager enables the auto-connect feature for connection profiles and automatically connects to a saved network if it is available.
Prerequisites
- A wifi device is installed on the host.
-
The wifi device is enabled. To verify, use the
nmcli radiocommand.
Procedure
Open a terminal and enter:
nm-connection-editor
# nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Click the button to add a new connection.
-
Select the
Wi-Ficonnection type, and click . - Optional: Set a name for the connection profile.
Optional: Configure the network profile on the
Generaltab to not automatically connect.If you deactivate this feature, you must always manually connect to the network, for example, by using GNOME Settings or the GNOME system menu.
-
On the
Wi-Fitab, enter the service set identifier (SSID) in theSSIDfield. On the
Wi-Fi Securitytab, select the authentication type for the network, such asWPA3 Personal, and enter the password.Depending on the selected security, the application shows additional fields. Fill them accordingly. For details, ask the administrator of the wifi network.
-
Configure IPv4 settings on the
IPv4tab, and IPv6 settings on theIPv6tab. -
Click
Save. -
Close the
Network Connectionswindow.
Verification
Open the system menu on the right side of the top bar, and verify that the wifi network is connected:

If the network appears in the list, it is connected.
Ping a hostname or IP address:
ping -c 3 example.com
# ping -c 3 example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.7. Configuring a wifi connection with 802.1X network authentication in an existing profile by using nmcli
You can use the nmcli utility to configure a client to authenticate itself to a network.
For example, you can configure Protected Extensible Authentication Protocol (PEAP) authentication with Microsoft Challenge-Handshake Authentication Protocol version 2 (MSCHAPv2) in an existing NetworkManager wifi profile.
Prerequisites
- The network must have 802.1X network authentication.
- The wifi connection profile exists in NetworkManager and has a valid IP configuration.
-
If the client is required to verify the certificate of the authenticator, the Certificate Authority (CA) certificate must be stored in the
/etc/pki/ca-trust/source/anchors/directory. -
The
wpa_supplicantpackage is installed.
Procedure
Set the wifi security mode to
wpa-eap, the Extensible Authentication Protocol (EAP) topeap, the inner authentication protocol tomschapv2, and the user name:nmcli connection modify wlp1s0 wireless-security.key-mgmt wpa-eap 802-1x.eap peap 802-1x.phase2-auth mschapv2 802-1x.identity user_name
# nmcli connection modify wlp1s0 wireless-security.key-mgmt wpa-eap 802-1x.eap peap 802-1x.phase2-auth mschapv2 802-1x.identity user_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that you must set the
wireless-security.key-mgmt,802-1x.eap,802-1x.phase2-auth, and802-1x.identityparameters in a single command.Optional: Store the password in the configuration:
nmcli connection modify wlp1s0 802-1x.password password
# nmcli connection modify wlp1s0 802-1x.password passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantBy default, NetworkManager stores the password in plain text in the
/etc/sysconfig/network-scripts/keys-connection_namefile, which is readable only by therootuser. However, plain text passwords in a configuration file can be a security risk.To increase the security, set the
802-1x.password-flagsparameter toagent-owned. With this setting, on servers with the GNOME desktop environment or thenm-appletrunning, NetworkManager retrieves the password from these services, after you unlock the keyring first. In other cases, NetworkManager prompts for the password.If the client needs to verify the certificate of the authenticator, set the
802-1x.ca-certparameter in the connection profile to the path of the CA certificate:nmcli connection modify wlp1s0 802-1x.ca-cert /etc/pki/ca-trust/source/anchors/ca.crt
# nmcli connection modify wlp1s0 802-1x.ca-cert /etc/pki/ca-trust/source/anchors/ca.crtCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteFor security reasons, clients should validate the certificate of the authenticator.
Activate the connection profile:
nmcli connection up wlp1s0
# nmcli connection up wlp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
- Access resources on the network that require network authentication.
11.8. Configuring a wifi connection with 802.1X network authentication by using the network RHEL system role
By using the network RHEL system role, you can automate setting up Network Access Control (NAC) on remote hosts. You can define authentication details for clients in a playbook to ensure only authorized clients can access the network.
You can use an Ansible playbook to copy a private key, a certificate, and the CA certificate to the client, and then use the network RHEL system role to configure a connection profile with 802.1X network authentication.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. - The network supports 802.1X network authentication.
-
You installed the
wpa_supplicantpackage on the managed node. - DHCP is available in the network of the managed node.
The following files required for TLS authentication exist on the control node:
-
The client key is stored in the
/srv/data/client.keyfile. -
The client certificate is stored in the
/srv/data/client.crtfile. -
The CA certificate is stored in the
/srv/data/ca.crtfile.
-
The client key is stored in the
Procedure
Store your sensitive variables in an encrypted file:
Create the vault:
ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>
$ ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
ansible-vault createcommand opens an editor, enter the sensitive data in the<key>: <value>format:pwd: <password>
pwd: <password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the changes, and close the editor. Ansible encrypts the data in the vault.
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
ieee802_1x- This variable contains the 802.1X-related settings.
eap: tls-
Configures the profile to use the certificate-based
TLSauthentication method for the Extensible Authentication Protocol (EAP).
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --ask-vault-pass --syntax-check ~/playbook.yml
$ ansible-playbook --ask-vault-pass --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook --ask-vault-pass ~/playbook.yml
$ ansible-playbook --ask-vault-pass ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 12. Configuring RHEL as a WPA2 or WPA3 Personal access point
On a host with a wifi device, you can use NetworkManager to configure this host as an access point. Wireless clients can use a pre-shared key (PSK) to connect to the access point and use services on the RHEL host and in the network.
When you configure an access point, NetworkManager automatically:
-
Configures the
dnsmasqservice to provide DHCP and DNS services for clients - Enables IP forwarding
-
Adds
nftablesfirewall rules to masquerade traffic from the wifi device and configures IP forwarding
Prerequisites
- The wifi device supports running in access point mode.
- The wifi device is not in use.
- The host has internet access.
Procedure
List the wifi devices to identify the one that should provide the access point:
nmcli device status | grep wifi wlp0s20f3 wifi disconnected --
# nmcli device status | grep wifi wlp0s20f3 wifi disconnected --Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the device supports the access point mode:
nmcli -f WIFI-PROPERTIES.AP device show wlp0s20f3 WIFI-PROPERTIES.AP: yes
# nmcli -f WIFI-PROPERTIES.AP device show wlp0s20f3 WIFI-PROPERTIES.AP: yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow To use a wifi device as an access point, the device must support this feature.
Install the
dnsmasqandNetworkManager-wifipackages:dnf install dnsmasq NetworkManager-wifi
# dnf install dnsmasq NetworkManager-wifiCopy to Clipboard Copied! Toggle word wrap Toggle overflow NetworkManager uses the
dnsmasqservice to provide DHCP and DNS services to clients of the access point.Create the initial access point configuration:
nmcli device wifi hotspot ifname wlp0s20f3 con-name Example-Hotspot ssid Example-Hotspot password "password"
# nmcli device wifi hotspot ifname wlp0s20f3 con-name Example-Hotspot ssid Example-Hotspot password "password"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates a connection profile for an access point on the
wlp0s20f3device that provides WPA2 and WPA3 Personal authentication. The name of the wireless network, the Service Set Identifier (SSID), isExample-Hotspotand uses the pre-shared keypassword.Optional: Configure the access point to support only WPA3:
nmcli connection modify Example-Hotspot 802-11-wireless-security.key-mgmt sae
# nmcli connection modify Example-Hotspot 802-11-wireless-security.key-mgmt saeCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, NetworkManager uses the IP address
10.42.0.1for the wifi device and assigns IP addresses from the remaining10.42.0.0/24subnet to clients. To configure a different subnet and IP address, enter:nmcli connection modify Example-Hotspot ipv4.addresses 192.0.2.254/24
# nmcli connection modify Example-Hotspot ipv4.addresses 192.0.2.254/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow The IP address you set, in this case
192.0.2.254, is the one that NetworkManager assigns to the wifi device. Clients will use this IP address as default gateway and DNS server.Activate the connection profile:
nmcli connection up Example-Hotspot
# nmcli connection up Example-HotspotCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
On the server:
Verify that NetworkManager started the
dnsmasqservice and that the service listens on port 67 (DHCP) and 53 (DNS):ss -tulpn | grep -E ":53|:67" udp UNCONN 0 0 10.42.0.1:53 0.0.0.0:* users:(("dnsmasq",pid=55905,fd=6)) udp UNCONN 0 0 0.0.0.0:67 0.0.0.0:* users:(("dnsmasq",pid=55905,fd=4)) tcp LISTEN 0 32 10.42.0.1:53 0.0.0.0:* users:(("dnsmasq",pid=55905,fd=7))# ss -tulpn | grep -E ":53|:67" udp UNCONN 0 0 10.42.0.1:53 0.0.0.0:* users:(("dnsmasq",pid=55905,fd=6)) udp UNCONN 0 0 0.0.0.0:67 0.0.0.0:* users:(("dnsmasq",pid=55905,fd=4)) tcp LISTEN 0 32 10.42.0.1:53 0.0.0.0:* users:(("dnsmasq",pid=55905,fd=7))Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the
nftablesrule set to ensure that NetworkManager enabled forwarding and masquerading for traffic from the10.42.0.0/24subnet:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
On a client with a wifi adapter:
Display the list of available networks:
nmcli device wifi IN-USE BSSID SSID MODE CHAN RATE SIGNAL BARS SECURITY 00:53:00:88:29:04 Example-Hotspot Infra 11 130 Mbit/s 62 ▂▄▆_ WPA3 ...# nmcli device wifi IN-USE BSSID SSID MODE CHAN RATE SIGNAL BARS SECURITY 00:53:00:88:29:04 Example-Hotspot Infra 11 130 Mbit/s 62 ▂▄▆_ WPA3 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Connect to the
Example-Hotspotwireless network. See Managing Wi-Fi connections. Ping a host on the remote network or the internet to verify that the connection works:
ping -c 3 www.redhat.com
# ping -c 3 www.redhat.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 13. Using MACsec to encrypt layer-2 traffic in the same physical network
MACsec secures point-to-point communication between devices. For example, you can configure MACsec on the two hosts connecting your branch and central offices over a Metro-Ethernet connection to increase security.
13.1. How MACsec increases security
Media Access Control security (MACsec) is a layer-2 protocol that encrypts and authenticates all LAN traffic. It uses a pre-shared key to establish connections. To change this key, you must update the NetworkManager configuration on all hosts that use MACsec.
MACsec secures different traffic types over the Ethernet links, including:
- Dynamic host configuration protocol (DHCP)
- address resolution protocol (ARP)
- IPv4 and IPv6 traffic
- Any traffic over IP such as TCP or UDP
A MACsec connection uses an Ethernet device, such as an Ethernet network card, Virtual Local Area Network (VLAN), or tunnel device, as a parent. You can either set an IP configuration only on the MACsec device to communicate with other hosts only by using the encrypted connection, or you can also set an IP configuration on the parent device. In the latter case, you can use the parent device to communicate with other hosts using an unencrypted connection and the MACsec device for encrypted connections.
MACsec does not require any special hardware. For example, you can use any switch, except if you want to encrypt traffic only between a host and a switch. In this scenario, the switch must also support MACsec.
In other words, you can configure MACsec for two common scenarios:
- Host-to-host
- Host-to-switch and switch-to-other-hosts
You can use MACsec only between hosts being in the same physical or virtual LAN.
Using the MACsec security standard for securing communication at the link layer, also known as layer 2 of the Open Systems Interconnection (OSI) model provides the following notable benefits:
- Encryption at layer 2 eliminates the need for encrypting individual services at layer 7. This reduces the overhead associated with managing a large number of certificates for each endpoint on each host.
- Point-to-point security between directly connected network devices such as routers and switches.
- No changes needed for applications and higher-layer protocols.
13.2. Configuring a MACsec connection by using nmcli
You can use the nmcli utility to configure Ethernet interfaces to use MACsec. For example, you can create a MACsec connection between two hosts that are connected over Ethernet.
Procedure
On the first host on which you configure MACsec:
Create the connectivity association key (CAK) and connectivity-association key name (CKN) for the pre-shared key:
Create a 16-byte hexadecimal CAK:
dd if=/dev/urandom count=16 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' 50b71a8ef0bd5751ea76de6d6c98c03a
# dd if=/dev/urandom count=16 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' 50b71a8ef0bd5751ea76de6d6c98c03aCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a 32-byte hexadecimal CKN:
dd if=/dev/urandom count=32 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' f2b4297d39da7330910a74abc0449feb45b5c0b9fc23df1430e1898fcf1c4550
# dd if=/dev/urandom count=32 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' f2b4297d39da7330910a74abc0449feb45b5c0b9fc23df1430e1898fcf1c4550Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- On both hosts you want to connect over a MACsec connection:
Create the MACsec connection:
nmcli connection add type macsec con-name macsec0 ifname macsec0 connection.autoconnect yes macsec.parent enp1s0 macsec.mode psk macsec.mka-cak 50b71a8ef0bd5751ea76de6d6c98c03a macsec.mka-ckn f2b4297d39da7330910a74abc0449feb45b5c0b9fc23df1430e1898fcf1c4550
# nmcli connection add type macsec con-name macsec0 ifname macsec0 connection.autoconnect yes macsec.parent enp1s0 macsec.mode psk macsec.mka-cak 50b71a8ef0bd5751ea76de6d6c98c03a macsec.mka-ckn f2b4297d39da7330910a74abc0449feb45b5c0b9fc23df1430e1898fcf1c4550Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the CAK and CKN generated in the previous step in the
macsec.mka-cakandmacsec.mka-cknparameters. The values must be the same on every host in the MACsec-protected network.Configure the IP settings on the MACsec connection.
Configure the
IPv4settings. For example, to set a staticIPv4address, network mask, default gateway, and DNS server to themacsec0connection, enter:nmcli connection modify macsec0 ipv4.method manual ipv4.addresses '192.0.2.1/24' ipv4.gateway '192.0.2.254' ipv4.dns '192.0.2.253'
# nmcli connection modify macsec0 ipv4.method manual ipv4.addresses '192.0.2.1/24' ipv4.gateway '192.0.2.254' ipv4.dns '192.0.2.253'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the
IPv6settings. For example, to set a staticIPv6address, network mask, default gateway, and DNS server to themacsec0connection, enter:nmcli connection modify macsec0 ipv6.method manual ipv6.addresses '2001:db8:1::1/32' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd'
# nmcli connection modify macsec0 ipv6.method manual ipv6.addresses '2001:db8:1::1/32' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Activate the connection:
nmcli connection up macsec0
# nmcli connection up macsec0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the traffic is encrypted:
tcpdump -nn -i enp1s0
# tcpdump -nn -i enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Display the unencrypted traffic:
tcpdump -nn -i macsec0
# tcpdump -nn -i macsec0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display MACsec statistics:
ip macsec show
# ip macsec showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display individual counters for each type of protection: integrity-only (encrypt off) and encryption (encrypt on)
ip -s macsec show
# ip -s macsec showCopy to Clipboard Copied! Toggle word wrap Toggle overflow
13.3. Configuring a MACsec connection by using nmstatectl
You can use the declarative Nmstate API to configure Ethernet interfaces to use MACsec. Nmstate ensures that the result matches the configuration file or rolls back the changes.
Prerequisites
- A physical or virtual Ethernet Network Interface Controller (NIC) exists in the server configuration.
-
The
nmstatepackage is installed.
Procedure
On the first host on which you configure MACsec, create the connectivity association key (CAK) and connectivity-association key name (CKN) for the pre-shared key:
Create a 16-byte hexadecimal CAK:
dd if=/dev/urandom count=16 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' 50b71a8ef0bd5751ea76de6d6c98c03a
# dd if=/dev/urandom count=16 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' 50b71a8ef0bd5751ea76de6d6c98c03aCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a 32-byte hexadecimal CKN:
dd if=/dev/urandom count=32 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' f2b4297d39da7330910a74abc0449feb45b5c0b9fc23df1430e1898fcf1c4550
# dd if=/dev/urandom count=32 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' f2b4297d39da7330910a74abc0449feb45b5c0b9fc23df1430e1898fcf1c4550Copy to Clipboard Copied! Toggle word wrap Toggle overflow
On both hosts that you want to connect over a MACsec connection, complete the following steps:
Create a YAML file, for example
create-macsec-connection.yml, with the following settings:Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Use the CAK and CKN generated in the previous step in the
mka-cakandmka-cknparameters. The values must be the same on every host in the MACsec-protected network. Optional: In the same YAML configuration file, you can also configure the following settings:
-
A static IPv4 address -
192.0.2.1with the/32subnet mask -
A static IPv6 address -
2001:db8:1::1with the/64subnet mask -
An IPv4 default gateway -
192.0.2.2 -
An IPv4 DNS server -
192.0.2.200 -
An IPv6 DNS server -
2001:db8:1::ffbb -
A DNS search domain -
example.com
-
A static IPv4 address -
Apply the settings to the system:
nmstatectl apply create-macsec-connection.yml
# nmstatectl apply create-macsec-connection.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the current state in YAML format:
nmstatectl show macsec0
# nmstatectl show macsec0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the traffic is encrypted:
tcpdump -nn -i enp0s1
# tcpdump -nn -i enp0s1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Display the unencrypted traffic:
tcpdump -nn -i macsec0
# tcpdump -nn -i macsec0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display MACsec statistics:
ip macsec show
# ip macsec showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display individual counters for each type of protection: integrity-only (encrypt off) and encryption (encrypt on)
ip -s macsec show
# ip -s macsec showCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 14. Getting started with IPVLAN
IPVLAN is a driver for a virtual network device that can be used in container environment to access the host network.
IPVLAN exposes a single MAC address to the external network regardless of the number of IPVLAN devices created inside the host network. This means that a user can have multiple IPVLAN devices in multiple containers and the corresponding switch reads a single MAC address. The IPVLAN driver is useful when the local switch imposes constraints on the total number of MAC addresses that it can manage.
14.1. IPVLAN modes
The following modes are available for IPVLAN:
L2 mode
In IPVLAN L2 mode, virtual devices receive and respond to address resolution protocol (ARP) requests. The
netfilterframework runs only inside the container that owns the virtual device. Nonetfilterchains are executed in the default namespace on the containerized traffic. Using L2 mode provides good performance, but less control on the network traffic.L3 mode
In L3 mode, virtual devices process only L3 traffic and above. Virtual devices do not respond to ARP requests and users must configure the neighbour entries for the IPVLAN IP addresses on the relevant peers manually. The egress traffic of a relevant container is landed on the
netfilterPOSTROUTING and OUTPUT chains in the default namespace while the ingress traffic is threaded in the same way as L2 mode. Using L3 mode provides good control but decreases the network traffic performance.L3S mode
In L3S mode, virtual devices process the same way as in L3 mode, except that both egress and ingress traffics of a relevant container are landed on the
netfilterchain in the default namespace. L3S mode behaves in a similar way to L3 mode but provides greater control of the network.
The IPVLAN virtual device does not receive broadcast and multicast traffic in case of L3 and L3S modes.
14.2. Comparison of IPVLAN and MACVLAN
The following table shows the major differences between MACVLAN and IPVLAN:
| MACVLAN | IPVLAN |
|---|---|
| Uses MAC address for each MACVLAN device. Note that, if a switch reaches the maximum number of MAC addresses it can store in its MAC table, connectivity can be lost. | Uses a single MAC address which does not limit the number of IPVLAN devices. |
| Netfilter rules for a global namespace cannot affect traffic to or from a MACVLAN device in a child namespace. | It is possible to control traffic to or from an IPVLAN device in L3 mode and L3S mode. |
Both IPVLAN and MACVLAN do not require any level of encapsulation.
14.3. Creating and configuring the IPVLAN device using iproute2
This procedure shows how to set up the IPVLAN device using iproute2.
Procedure
To create an IPVLAN device, enter the following command:
ip link add link <real_nic_device> name <ipvlan_device> type ipvlan mode l2
# ip link add link <real_nic_device> name <ipvlan_device> type ipvlan mode l2Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that network interface controller (NIC) is a hardware component which connects a computer to a network.
To assign an
IPv4orIPv6address to the interface, enter the following command:ip addr add dev <ipvlan_device> <ip_address/subnet_mask_prefix>
# ip addr add dev <ipvlan_device> <ip_address/subnet_mask_prefix>Copy to Clipboard Copied! Toggle word wrap Toggle overflow In case of configuring an IPVLAN device in L3 mode or L3S mode, make the following setups:
Configure the neighbor setup for the remote peer on the remote host:
ip neigh add dev <peer_device> <ipvlan_device_IP_address> lladdr <mac_address>
# ip neigh add dev <peer_device> <ipvlan_device_IP_address> lladdr <mac_address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where MAC_address is the MAC address of the real NIC on which an IPVLAN device is based on.
Configure an IPVLAN device for L3 mode with the following command:
ip route add dev <real_nic_device> <peer_ip_address/32>
# ip route add dev <real_nic_device> <peer_ip_address/32>Copy to Clipboard Copied! Toggle word wrap Toggle overflow For L3S mode:
ip route add dev <real_nic_device> <peer_ip_address>/32
# ip route add dev <real_nic_device> <peer_ip_address>/32Copy to Clipboard Copied! Toggle word wrap Toggle overflow where IP-address represents the address of the remote peer.
To set an IPVLAN device active, enter the following command:
ip link set dev <ipvlan_device> up
# ip link set dev <ipvlan_device> upCopy to Clipboard Copied! Toggle word wrap Toggle overflow To check if the IPVLAN device is active, execute the following command on the remote host:
ping <IP_address>
# ping <IP_address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where the IP_address uses the IP address of the IPVLAN device.
Chapter 15. Configuring an IP address ping target to ensure active network connections
Configure the connection.ip-ping-addresses and connection.ip-ping-timeout settings to verify connectivity to a specific target.
The NetworkManager service starts after the system boots. Certain services, such as network file system (NFS), are dependent on the network connectivity. If the gateway IP or the target IP address does not return a response, NFS fails to mount because it cannot connect to its destination as the network is not completely up and running. Therefore, you can configure the connection.ip-ping-addresses and connection.ip-ping-timeout settings to verify connectivity to a specific target to avoid such problems. The connection.ip-ping-addresses setting supports configuration of IPv4 and IPv6 addresses.
Procedure
Create a connection profile, if it does not already exist. For example, to create a profile for the
enp1s0interface with dynamic IP address assignment, enter:nmcli connection add con-name enp1s0 ifname enp1s0 type ethernet
# nmcli connection add con-name enp1s0 ifname enp1s0 type ethernetCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteConfiguration of
connection.ip-ping-addressescan result in the delay of response from thenetwork-onlinetarget service ofsystemd, because of waiting for either the ping operation completion or timeout period.Configure the connection to ping the specified IP addresses with a defined timeout period:
nmcli connection modify enp1s0 connection.ip-ping-addresses "192.0.2.56, 192.0.2.60" connection.ip-ping-timeout 10 ipv4.may-fail no
# nmcli connection modify enp1s0 connection.ip-ping-addresses "192.0.2.56, 192.0.2.60" connection.ip-ping-timeout 10 ipv4.may-fail noCopy to Clipboard Copied! Toggle word wrap Toggle overflow Setting the
ipv4.may-failattribute tono, ensures that IPv4 configuration must complete successfully.Re-activate the connection:
nmcli connection up enp1s0
# nmcli connection up enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 16. Configuring NetworkManager to ignore certain devices
By default, NetworkManager manages all devices except the ones described in the /usr/lib/udev/rules.d/85-nm-unmanaged.rules file. To ignore certain other devices, you can configure them in NetworkManager as unmanaged.
16.1. Permanently configuring a device as unmanaged in NetworkManager
You can configure devices as unmanaged based on several criteria, such as the interface name or MAC address. If you use a device section in the configuration to set a device as unmanaged, NetworkManager does not manage the device until you start using it in a connection profile.
Procedure
Optional: Display the list of devices to identify the device or MAC address you want to set as
unmanaged:ip link show ... 2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:74:79:56 brd ff:ff:ff:ff:ff:ff ...# ip link show ... 2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000 link/ether 52:54:00:74:79:56 brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Create a
*.conffile in the/etc/NetworkManager/conf.d/directory, for example,/etc/NetworkManager/conf.d/99-unmanaged-devices.conf. For each device you want to configure as unmanaged, add a section with a unique name to the file.
ImportantThe section name must begin with
device-.To configure a specific interface as unmanaged, add:
[device-enp1s0-unmanaged] match-device=interface-name:enp1s0 managed=0
[device-enp1s0-unmanaged] match-device=interface-name:enp1s0 managed=0Copy to Clipboard Copied! Toggle word wrap Toggle overflow To configure a device with a specific MAC address as unmanaged, add:
[device-mac525400747956-unmanaged] match-device=mac:52:54:00:74:79:56 managed=0
[device-mac525400747956-unmanaged] match-device=mac:52:54:00:74:79:56 managed=0Copy to Clipboard Copied! Toggle word wrap Toggle overflow To configure all devices of a specific type as unmanaged, add:
[device-ethernet-unmanaged] match-device=type:ethernet managed=0
[device-ethernet-unmanaged] match-device=type:ethernet managed=0Copy to Clipboard Copied! Toggle word wrap Toggle overflow To set multiple devices as unmanaged, separate the entries in the
unmanaged-devicesparameter with a semicolon, for example:[device-multiple-devices-unmanaged] match-device=interface-name:enp1s0;interface-name:enp7s0 managed=0
[device-multiple-devices-unmanaged] match-device=interface-name:enp1s0;interface-name:enp7s0 managed=0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can add separate sections for each device in this file or create additional
*.conffiles in the/etc/NetworkManager/conf.d/directory.
Restart the host system:
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow The reboot clears the state in the
/run/NetworkManager/devices/directory. This prevents that NetworkManager uses an existing connection from this directory for the device you set as unmanaged.
Verification
Display the list of devices:
nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet unmanaged -- ...
# nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet unmanaged -- ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
unmanagedstate next to theenp1s0device indicates that NetworkManager does not manage this device.
Troubleshooting
If the output of the
nmcli device statuscommand does not list the device asunmanaged, display the NetworkManager configuration:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the output does not match the settings that you configured, ensure that no configuration file with a higher priority overrides your settings. For details on how NetworkManager merges multiple configuration files, see the
NetworkManager.conf(5)man page on your system.
16.2. Temporarily configuring a device as unmanaged in NetworkManager
You can temporarily configure devices as unmanaged, for example, for testing purposes. This change persists a reload and restart of the NetworkManager systemd service, but not a system reboot.
Procedure
Optional: Display the list of devices to identify the device you want to set as
unmanaged:nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet disconnected -- ...
# nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet disconnected -- ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
enp1s0device to theunmanagedstate:nmcli device set enp1s0 managed no
# nmcli device set enp1s0 managed noCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the list of devices:
nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet unmanaged -- ...
# nmcli device status DEVICE TYPE STATE CONNECTION enp1s0 ethernet unmanaged -- ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
unmanagedstate next to theenp1s0device indicates that NetworkManager does not manage this device.
16.3. Identifying the reason why NetworkManager does not manage a certain network device
In addition to the status of each network device, NetworkManager also tracks the reason why the devices are in their current status. You can use this feature to identify why NetworkManager does not manage certain devices.
Procedure
Display the status and its reason of all network devices:
nmcli -f GENERAL.DEVICE,GENERAL.STATE,GENERAL.REASON device show
# nmcli -f GENERAL.DEVICE,GENERAL.STATE,GENERAL.REASON device showCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you pass a device name to the command, you can display the output only of the specified device.
Example output:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteNote that the command returns the status of all devices, regardless whether they are managed or unmanaged.
Chapter 17. Configuring the loopback interface by using nmcli
By default, NetworkManager does not manage the loopback (lo) interface. After creating a connection profile for the lo interface, you can configure this device by using NetworkManager.
Some of the examples when users want to configure the loopback interface are as follows:
-
Assign additional IP addresses to the
lointerface - Define DNS addresses
-
Change the Maximum Transmission Unit (MTU) size of the
lointerface
Procedure
Create a new connection of type
loopback:nmcli connection add con-name example-loopback type loopback
# nmcli connection add con-name example-loopback type loopbackCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure custom connection settings, for example:
To assign an additional IP address to the interface, enter:
nmcli connection modify example-loopback +ipv4.addresses 192.0.2.1/24
# nmcli connection modify example-loopback +ipv4.addresses 192.0.2.1/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteNetworkManager manages the
lointerface by always assigning the IP addresses127.0.0.1and::1that are persistent across the reboots. You cannot override127.0.0.1and::1. However, you can assign additional IP addresses to the interface.To set a custom Maximum Transmission Unit (MTU), enter:
nmcli con mod example-loopback loopback.mtu 16384
# nmcli con mod example-loopback loopback.mtu 16384Copy to Clipboard Copied! Toggle word wrap Toggle overflow To set an IP address to your DNS server, enter:
nmcli connection modify example-loopback ipv4.dns 192.0.2.0
# nmcli connection modify example-loopback ipv4.dns 192.0.2.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you set a DNS server in the loopback connection profile, this entry is always available in the
/etc/resolv.conffile. The DNS server entry remains independent of whether or not the host roams between different networks.
Activate the connection:
nmcli connection up example-loopback
# nmcli connection up example-loopbackCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the settings of the
lointerface:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify the DNS address:
cat /etc/resolv.conf ... nameserver 192.0.2.0 ...
# cat /etc/resolv.conf ... nameserver 192.0.2.0 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 18. Creating a dummy interface
As a Red Hat Enterprise Linux user, you can create and use dummy network interfaces for debugging and testing purposes. A dummy interface provides a device to route packets without actually transmitting them. It enables you to create additional loopback-like devices managed by NetworkManager and makes an inactive SLIP (Serial Line Internet Protocol) address look like a real address for local programs.
18.1. Creating a dummy interface with both an IPv4 and IPv6 address by using nmcli
You can create a dummy interface with various settings, such as IPv4 and IPv6 addresses. After creating the interface, NetworkManager automatically assigns it to the default public firewalld zone.
Procedure
Create a dummy interface named
dummy0with static IPv4 and IPv6 addresses:nmcli connection add type dummy ifname dummy0 ipv4.method manual ipv4.addresses 192.0.2.1/24 ipv6.method manual ipv6.addresses 2001:db8:2::1/64
# nmcli connection add type dummy ifname dummy0 ipv4.method manual ipv4.addresses 192.0.2.1/24 ipv6.method manual ipv6.addresses 2001:db8:2::1/64Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteTo configure a dummy interface without IPv4 and IPv6 addresses, set both the
ipv4.methodandipv6.methodparameters todisabled. Otherwise, IP auto-configuration fails, and NetworkManager deactivates the connection and removes the device.
Verification
List the connection profiles:
nmcli connection show NAME UUID TYPE DEVICE dummy-dummy0 aaf6eb56-73e5-4746-9037-eed42caa8a65 dummy dummy0
# nmcli connection show NAME UUID TYPE DEVICE dummy-dummy0 aaf6eb56-73e5-4746-9037-eed42caa8a65 dummy dummy0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 19. Using NetworkManager to disable IPv6 for a specific connection
On a system that uses NetworkManager to manage network interfaces, you can disable the IPv6 protocol if the network only uses IPv4. If you disable IPv6, NetworkManager automatically sets the corresponding sysctl values in the Kernel.
If disabling IPv6 using kernel tunables or kernel boot parameters, additional consideration must be given to system configuration. For more information, see the Red Hat Knowledgebase solution How do I disable or enable the IPv6 protocol in RHEL.
19.1. Disabling IPv6 on a connection using nmcli
You can use the nmcli utility to disable the IPv6 protocol on the command line.
Prerequisites
- The system uses NetworkManager to manage network interfaces.
Procedure
Optional: Display the list of network connections:
nmcli connection show NAME UUID TYPE DEVICE Example 7a7e0151-9c18-4e6f-89ee-65bb2d64d365 ethernet enp1s0 ...
# nmcli connection show NAME UUID TYPE DEVICE Example 7a7e0151-9c18-4e6f-89ee-65bb2d64d365 ethernet enp1s0 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
ipv6.methodparameter of the connection todisabled:nmcli connection modify Example ipv6.method "disabled"
# nmcli connection modify Example ipv6.method "disabled"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the network connection:
nmcli connection up Example
# nmcli connection up ExampleCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IP settings of the device:
ip address show enp1s0 2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether 52:54:00:6b:74:be brd ff:ff:ff:ff:ff:ff inet 192.0.2.1/24 brd 192.10.2.255 scope global noprefixroute enp1s0 valid_lft forever preferred_lft forever# ip address show enp1s0 2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether 52:54:00:6b:74:be brd ff:ff:ff:ff:ff:ff inet 192.0.2.1/24 brd 192.10.2.255 scope global noprefixroute enp1s0 valid_lft forever preferred_lft foreverCopy to Clipboard Copied! Toggle word wrap Toggle overflow If no
inet6entry is displayed,IPv6is disabled on the device.Verify that the
/proc/sys/net/ipv6/conf/enp1s0/disable_ipv6file now contains the value1:cat /proc/sys/net/ipv6/conf/enp1s0/disable_ipv6 1
# cat /proc/sys/net/ipv6/conf/enp1s0/disable_ipv6 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow The value
1means thatIPv6is disabled for the device.
Chapter 20. Changing a hostname
The hostname of a system is the name on the system itself. You can set the name when you install RHEL, and you can change it afterwards.
20.1. Changing a hostname by using nmcli
You can use the nmcli utility to update the system hostname. Note that other utilities might use a different term, such as static or persistent hostname.
Procedure
Optional: Display the current hostname setting:
nmcli general hostname old-hostname.example.com
# nmcli general hostname old-hostname.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the new hostname:
nmcli general hostname new-hostname.example.com
# nmcli general hostname new-hostname.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow NetworkManager automatically restarts the
systemd-hostnamedto activate the new name. For the changes to take effect, reboot the host:reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, if you know which services use the hostname:
Restart all services that only read the hostname when the service starts:
systemctl restart <service_name>
# systemctl restart <service_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Active shell users must re-login for the changes to take effect.
Verification
Display the hostname:
nmcli general hostname new-hostname.example.com
# nmcli general hostname new-hostname.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
20.2. Changing a hostname by using hostnamectl
You can use the hostnamectl utility to update the hostname.
By default, hostnamectl sets the following hostname types:
-
Static hostname: Stored in the
/etc/hostnamefile. Typically, services use this name as the hostname. -
Pretty hostname: A descriptive name, such as
Proxy server in data center A. - Transient hostname: A fall-back value that is typically received from the network configuration.
Procedure
Optional: Display the current hostname setting:
hostnamectl status --static old-hostname.example.com
# hostnamectl status --static old-hostname.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the new hostname:
hostnamectl set-hostname new-hostname.example.com
# hostnamectl set-hostname new-hostname.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command sets the static and transient hostname to the new value. To set only a specific type, pass the
--static,--pretty, or--transientoption to the command.The
hostnamectlutility automatically restarts thesystemd-hostnamedto activate the new name. For the changes to take effect, reboot the host:reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, if you know which services use the hostname:
Restart all services that only read the hostname when the service starts:
systemctl restart <service_name>
# systemctl restart <service_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Active shell users must re-login for the changes to take effect.
Verification
Display the hostname:
hostnamectl status --static new-hostname.example.com
# hostnamectl status --static new-hostname.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 21. Configuring NetworkManager DHCP settings
NetworkManager provides different configuration options related to DHCP. For example, you can configure NetworkManager to use the built-in DHCP client (default) or an external client, and you can influence DHCP settings of individual profiles.
21.1. Changing the DHCP client of NetworkManager
By default, NetworkManager uses its internal DHCP client. However, if you require a DHCP client with features that the built-in client does not provide, you can alternatively configure NetworkManager to use dhclient.
Note that RHEL does not provide dhcpcd and, therefore, NetworkManager cannot use this client.
Procedure
Create the
/etc/NetworkManager/conf.d/dhcp-client.conffile with the following content:[main] dhcp=dhclient
[main] dhcp=dhclientCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can set the
dhcpparameter tointernal(default) ordhclient.If you set the
dhcpparameter todhclient, install thedhcp-clientpackage:dnf install dhcp-client
# dnf install dhcp-clientCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart NetworkManager:
systemctl restart NetworkManager
# systemctl restart NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the restart temporarily interrupts all network connections.
Verification
Search in the
/var/log/messageslog file for an entry similar to the following:Apr 26 09:54:19 server NetworkManager[27748]: <info> [1650959659.8483] dhcp-init: Using DHCP client 'dhclient'
Apr 26 09:54:19 server NetworkManager[27748]: <info> [1650959659.8483] dhcp-init: Using DHCP client 'dhclient'Copy to Clipboard Copied! Toggle word wrap Toggle overflow This log entry confirms that NetworkManager uses
dhclientas DHCP client.
21.2. Configuring the DHCP timeout behavior of a NetworkManager connection
In a connection profile that uses DHCP, NetworkManager waits, by default, 45 seconds for the DHCP request to complete. You can customize timeout-related settings, to adjust the connection profile to your environment.
Prerequisites
- A connection that uses DHCP is configured on the host.
Procedure
Optional: Set the
ipv4.dhcp-timeoutandipv6.dhcp-timeoutproperties. For example, to set both options to30seconds, enter:nmcli connection modify <connection_name> ipv4.dhcp-timeout 30 ipv6.dhcp-timeout 30
# nmcli connection modify <connection_name> ipv4.dhcp-timeout 30 ipv6.dhcp-timeout 30Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, set the parameters to
infinityto configure that NetworkManager does not stop trying to request and renew an IP address until it is successful.Optional: Configure the behavior if NetworkManager does not receive an IPv4 address before the timeout:
nmcli connection modify <connection_name> ipv4.may-fail <value>
# nmcli connection modify <connection_name> ipv4.may-fail <value>Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you set the
ipv4.may-failoption to:yes, the status of the connection depends on the IPv6 configuration:- If the IPv6 configuration is enabled and successful, NetworkManager activates the IPv6 connection and no longer tries to activate the IPv4 connection.
- If the IPv6 configuration is disabled or not configured, the connection fails.
no, the connection is deactivated. In this case:-
If the
autoconnectproperty of the connection is enabled, NetworkManager retries to activate the connection as many times as set in theautoconnect-retriesproperty. The default is4. - If the connection still cannot acquire a DHCP address, auto-activation fails. Note that after 5 minutes, the auto-connection process starts again to acquire an IP address from the DHCP server.
-
If the
Optional: Configure the behavior if NetworkManager does not receive an IPv6 address before the timeout:
nmcli connection modify <connection_name> ipv6.may-fail <value>
# nmcli connection modify <connection_name> ipv6.may-fail <value>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 22. Running dhclient exit hooks using NetworkManager a dispatcher script
You can use a NetworkManager dispatcher script to execute dhclient exit hooks.
22.1. The concept of NetworkManager dispatcher scripts
The NetworkManager-dispatcher service executes user-provided scripts in alphabetical order when network events happen. These scripts are typically shell scripts, but can be any executable script or application. You can use dispatcher scripts, for example, to adjust network-related settings that you cannot manage with NetworkManager.
You can store dispatcher scripts in the following directories:
-
/etc/NetworkManager/dispatcher.d/: The general location for dispatcher scripts therootuser can edit. -
/usr/lib/NetworkManager/dispatcher.d/: For pre-deployed immutable dispatcher scripts.
For security reasons, the NetworkManager-dispatcher service executes scripts only if the following conditions met:
-
The script is owned by the
rootuser. -
The script is only readable and writable by
root. -
The
setuidbit is not set on the script.
The NetworkManager-dispatcher service runs each script with two arguments:
- The interface name of the device the operation happened on.
-
The action, such as
up, when the interface has been activated.
The Dispatcher scripts section in the NetworkManager(8) man page provides an overview of actions and environment variables you can use in scripts.
The NetworkManager-dispatcher service runs one script at a time, but asynchronously from the main NetworkManager process. Note that, if a script is queued, the service will always run it, even if a later event makes it obsolete. However, the NetworkManager-dispatcher service runs scripts that are symbolic links referring to files in /etc/NetworkManager/dispatcher.d/no-wait.d/ immediately, without waiting for the termination of previous scripts, and in parallel.
22.2. Creating a NetworkManager dispatcher script that runs dhclient exit hooks
When a DHCP server assigns or updates an IPv4 address, NetworkManager can run a dispatcher script stored in the /etc/dhcp/dhclient-exit-hooks.d/ directory. This dispatcher script can then, for example, run dhclient exit hooks.
Prerequisites
-
The
dhclientexit hooks are stored in the/etc/dhcp/dhclient-exit-hooks.d/directory.
Procedure
Create the
/etc/NetworkManager/dispatcher.d/12-dhclient-downfile with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
rootuser as owner of the file:chown root:root /etc/NetworkManager/dispatcher.d/12-dhclient-down
# chown root:root /etc/NetworkManager/dispatcher.d/12-dhclient-downCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the permissions so that only the root user can execute it:
chmod 0700 /etc/NetworkManager/dispatcher.d/12-dhclient-down
# chmod 0700 /etc/NetworkManager/dispatcher.d/12-dhclient-downCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restore the SELinux context:
restorecon /etc/NetworkManager/dispatcher.d/12-dhclient-down
# restorecon /etc/NetworkManager/dispatcher.d/12-dhclient-downCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 23. Manually configuring the /etc/resolv.conf file
By default, NetworkManager dynamically updates the /etc/resolv.conf file with the DNS settings from active NetworkManager connection profiles. However, you can disable this behavior and manually configure DNS settings in /etc/resolv.conf.
Alternatively, if you require a specific order of DNS servers in /etc/resolv.conf, see Configuring the order of DNS servers.
23.1. Disabling DNS processing in the NetworkManager configuration
By default, NetworkManager manages DNS settings in the /etc/resolv.conf file, and you can configure the order of DNS servers. Alternatively, you can disable DNS processing in NetworkManager if you prefer to manually configure DNS settings in /etc/resolv.conf.
Procedure
As the root user, create the
/etc/NetworkManager/conf.d/90-dns-none.conffile with the following content by using a text editor:[main] dns=none
[main] dns=noneCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reload the
NetworkManagerservice:systemctl reload NetworkManager
# systemctl reload NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAfter you reload the service, NetworkManager no longer updates the
/etc/resolv.conffile. However, the last contents of the file are preserved.-
Optional: Remove the
Generated by NetworkManagercomment from/etc/resolv.confto avoid confusion.
Verification
-
Edit the
/etc/resolv.conffile and manually update the configuration. Reload the
NetworkManagerservice:systemctl reload NetworkManager
# systemctl reload NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the
/etc/resolv.conffile:cat /etc/resolv.conf
# cat /etc/resolv.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you successfully disabled DNS processing, NetworkManager did not override the manually configured settings.
Troubleshooting
Display the NetworkManager configuration to ensure that no other configuration file with a higher priority overrode the setting:
# NetworkManager --print-config ... dns=none ...
# NetworkManager --print-config ... dns=none ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
23.2. Replacing /etc/resolv.conf with a symbolic link to manually configure DNS settings
By default, NetworkManager manages DNS settings in the /etc/resolv.conf file, and you can configure the order of DNS servers. Alternatively, you can disable DNS processing in NetworkManager if you prefer to manually configure DNS settings in /etc/resolv.conf. For example, NetworkManager does not automatically update the DNS configuration if /etc/resolv.conf is a symbolic link.
Prerequisites
-
The NetworkManager
rc-managerconfiguration option is not set tofile. To verify, use theNetworkManager --print-configcommand.
Procedure
-
Create a file, such as
/etc/resolv.conf.manually-configured, and add the DNS configuration for your environment to it. Use the same parameters and syntax as in the original/etc/resolv.conf. Remove the
/etc/resolv.conffile:rm /etc/resolv.conf
# rm /etc/resolv.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a symbolic link named
/etc/resolv.confthat refers to/etc/resolv.conf.manually-configured:ln -s /etc/resolv.conf.manually-configured /etc/resolv.conf
# ln -s /etc/resolv.conf.manually-configured /etc/resolv.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 24. Configuring the order of DNS servers
The getaddrinfo() function of the glibc library sends all DNS requests to the first DNS server specified in the /etc/resolv.conf file. If this server does not reply, RHEL tries all other name servers. You can configure NetworkManager to influence the DNS server order in /etc/resolv.conf.
24.1. How NetworkManager orders DNS servers in /etc/resolv.conf
NetworkManager orders DNS servers in the /etc/resolv.conf file by applying a specific set of rules.
The ordering depends on the following conditions:
- If only one connection profile exists, NetworkManager uses the order of IPv4 and IPv6 DNS server specified in that connection.
If multiple connection profiles are activated, NetworkManager orders DNS servers based on a DNS priority value. If you set DNS priorities, the behavior of NetworkManager depends on the value set in the
dnsparameter. You can set this parameter in the[main]section in the/etc/NetworkManager/NetworkManager.conffile:dns=defaultor if thednsparameter is not set:NetworkManager orders the DNS servers from different connections based on the
ipv4.dns-priorityandipv6.dns-priorityparameters in each connection.If you set no value or you set
ipv4.dns-priorityandipv6.dns-priorityto0, NetworkManager uses the global default value.dns=dnsmasqordns=systemd-resolved:When you use one of these settings, NetworkManager sets either
127.0.0.1fordnsmasqor127.0.0.53asnameserverentry in the/etc/resolv.conffile.Both the
dnsmasqandsystemd-resolvedservices forward queries for the search domain set in a NetworkManager connection to the DNS server specified in that connection, and forwards queries to other domains to the connection with the default route. When multiple connections have the same search domain set,dnsmasqandsystemd-resolvedforward queries for this domain to the DNS server set in the connection with the lowest priority value.
NetworkManager uses the following default values for connections:
-
50for VPN connections -
100for other connections
You can set both the global default and connection-specific ipv4.dns-priority and ipv6.dns-priority parameters to a value between -2147483647 and 2147483647.
- A lower value has a higher priority.
- Negative values have the special effect of excluding other configurations with a greater value. For example, if at least one connection with a negative priority value exists, NetworkManager uses only the DNS servers specified in the connection profile with the lowest priority.
If multiple connections have the same DNS priority, NetworkManager prioritizes the DNS in the following order:
- VPN connections
- Connection with an active default route. The active default route is the default route with the lowest metric.
24.2. Setting a NetworkManager-wide default DNS server priority value
You can override NetworkManager’s system-wide DNS server priority default values to set custom defaults for IPv4 and IPv6 DNS servers.
The default values are as follows:
-
50for VPN connections -
100for other connections
Procedure
Edit the
/etc/NetworkManager/NetworkManager.conffile:Add the
[connection]section, if it does not exist:[connection]
[connection]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the custom default values to the
[connection]section. For example, to set the new default for both IPv4 and IPv6 to200, add:ipv4.dns-priority=200 ipv6.dns-priority=200
ipv4.dns-priority=200 ipv6.dns-priority=200Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can set the parameters to a value between
-2147483647and2147483647. Note that setting the parameters to0enables the built-in defaults (50for VPN connections and100for other connections).
Reload the
NetworkManagerservice:systemctl reload NetworkManager
# systemctl reload NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow
24.3. Setting the DNS priority of a NetworkManager connection
If you require a specific order of DNS servers you can set priority values in connection profiles. NetworkManager uses these values to order the servers when the service creates or updates the /etc/resolv.conf file.
Note that setting DNS priorities makes only sense if you have multiple connections with different DNS servers configured. If you have only one connection with multiple DNS servers configured, manually set the DNS servers in the preferred order in the connection profile.
Prerequisites
- The system has multiple NetworkManager connections configured.
-
The system either has no
dnsparameter set in the/etc/NetworkManager/NetworkManager.conffile or the parameter is set todefault.
Procedure
Optional: Display the available connections:
nmcli connection show NAME UUID TYPE DEVICE Example_con_1 d17ee488-4665-4de2-b28a-48befab0cd43 ethernet enp1s0 Example_con_2 916e4f67-7145-3ffa-9f7b-e7cada8f6bf7 ethernet enp7s0 ...
# nmcli connection show NAME UUID TYPE DEVICE Example_con_1 d17ee488-4665-4de2-b28a-48befab0cd43 ethernet enp1s0 Example_con_2 916e4f67-7145-3ffa-9f7b-e7cada8f6bf7 ethernet enp7s0 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
ipv4.dns-priorityandipv6.dns-priorityparameters. For example, to set both parameters to10, enter:nmcli connection modify <connection_name> ipv4.dns-priority 10 ipv6.dns-priority 10
# nmcli connection modify <connection_name> ipv4.dns-priority 10 ipv6.dns-priority 10Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Optional: Repeat the previous step for other connections.
Re-activate the connection you updated:
nmcli connection up <connection_name>
# nmcli connection up <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the contents of the
/etc/resolv.conffile to verify that the DNS server order is correct:cat /etc/resolv.conf
# cat /etc/resolv.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 25. Using different DNS servers for different domains
In environments where one DNS server cannot resolve all domains, you can configure Red Hat Enterprise Linux (RHEL) to send DNS requests for a specific domain to a selected DNS server.
By default, RHEL sends all DNS requests to the first DNS server specified in the /etc/resolv.conf file. If this server does not reply, RHEL tries the next server in this file until it finds a working one.
For example, you connect a server to a Virtual Private Network (VPN), and hosts in the VPN use the example.com domain. In this case, you can configure RHEL to process DNS queries in the following way:
-
Send only DNS requests for
example.comto the DNS server in the VPN network. - Send all other requests to the DNS server that is configured in the connection profile with the default gateway.
25.1. Using dnsmasq in NetworkManager to send DNS requests for a specific domain to a selected DNS server
On hosts with multiple network interfaces and where one DNS server cannot resolve all domains, you can configure RHEL to send DNS requests for a specific domain to a selected DNS server.
You can configure NetworkManager to start an instance of dnsmasq. This DNS caching server then listens on port 53 on the loopback device. Consequently, this service is only reachable from the local system and not from the network.
With this configuration, NetworkManager adds the nameserver 127.0.0.1 entry to the /etc/resolv.conf file, and dnsmasq dynamically routes DNS requests to the corresponding DNS servers specified in the NetworkManager connection profiles.
Prerequisites
- The system has multiple NetworkManager connections configured.
A DNS server and search domain are configured for the connection that is responsible for resolving a specific domain.
For example, to ensure that the DNS server specified in a VPN connection resolves queries for the
example.comdomain, the following settings must be available:-
A DNS server that can resolve
example.com. A DHCP server can provide this information dynamically or you set theipv4.dnsandipv6.dnsparameters in the VPN connection profile. -
A search domain set to
example.com. A DHCP server can provide this information dynamically or you set theipv4.dns-searchandipv6.dns-searchparameters in the VPN connection profile.
-
A DNS server that can resolve
-
The
dnsmasqservice is not running or configured to listen on a different interface thanlocalhost.
Procedure
Install the
dnsmasqpackage:dnf install dnsmasq
# dnf install dnsmasqCopy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the
/etc/NetworkManager/NetworkManager.conffile, and set the following entry in the[main]section:dns=dnsmasq
dns=dnsmasqCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reload the
NetworkManagerservice:systemctl reload NetworkManager
# systemctl reload NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Search in the
systemdjournal of theNetworkManagerunit for which domains the service uses a different DNS server:journalctl -xeu NetworkManager ... Jun 02 13:30:17 <client_hostname>_ dnsmasq[5298]: using nameserver 198.51.100.7#53 for domain example.com ...
# journalctl -xeu NetworkManager ... Jun 02 13:30:17 <client_hostname>_ dnsmasq[5298]: using nameserver 198.51.100.7#53 for domain example.com ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
tcpdumppacket sniffer to verify the correct route of DNS requests:Install the
tcpdumppackage:dnf install tcpdump
# dnf install tcpdumpCopy to Clipboard Copied! Toggle word wrap Toggle overflow On one terminal, start
tcpdumpto capture DNS traffic on all interfaces:tcpdump -i any port 53
# tcpdump -i any port 53Copy to Clipboard Copied! Toggle word wrap Toggle overflow On a different terminal, resolve host names for a domain for which an exception exists and another domain, for example:
host -t A www.example.com host -t A www.redhat.com
# host -t A www.example.com # host -t A www.redhat.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify in the
tcpdumpoutput that Red Hat Enterprise Linux sends only DNS queries for theexample.comdomain to the designated DNS server and through the corresponding interface:... 13:52:42.234533 tun0 Out IP server.43534 > 198.51.100.7.domain: 50121+ A? www.example.com. (33) ... 13:52:57.753235 enp1s0 Out IP server.40864 > 192.0.2.1.domain: 6906+ A? www.redhat.com. (33) ...
... 13:52:42.234533 tun0 Out IP server.43534 > 198.51.100.7.domain: 50121+ A? www.example.com. (33) ... 13:52:57.753235 enp1s0 Out IP server.40864 > 192.0.2.1.domain: 6906+ A? www.redhat.com. (33) ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Red Hat Enterprise Linux sends the DNS query for
www.example.comto the DNS server on198.51.100.7and the query forwww.redhat.comto192.0.2.1.
Troubleshooting
Verify that the
nameserverentry in the/etc/resolv.conffile refers to127.0.0.1:cat /etc/resolv.conf nameserver 127.0.0.1
# cat /etc/resolv.conf nameserver 127.0.0.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the entry is missing, check the
dnsparameter in the/etc/NetworkManager/NetworkManager.conffile.Verify that the
dnsmasqservice listens on port53on theloopbackdevice:ss -tulpn | grep "127.0.0.1:53" udp UNCONN 0 0 127.0.0.1:53 0.0.0.0:* users:(("dnsmasq",pid=7340,fd=18)) tcp LISTEN 0 32 127.0.0.1:53 0.0.0.0:* users:(("dnsmasq",pid=7340,fd=19))# ss -tulpn | grep "127.0.0.1:53" udp UNCONN 0 0 127.0.0.1:53 0.0.0.0:* users:(("dnsmasq",pid=7340,fd=18)) tcp LISTEN 0 32 127.0.0.1:53 0.0.0.0:* users:(("dnsmasq",pid=7340,fd=19))Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the service does not listen on
127.0.0.1:53, check the journal entries of theNetworkManagerunit:journalctl -u NetworkManager
# journalctl -u NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow
25.2. Using systemd-resolved in NetworkManager to send DNS requests for a specific domain to a selected DNS server
On hosts with multiple network interfaces and where one DNS server cannot resolve all domains, you can configure RHEL to send DNS requests for a specific domain to a selected DNS server.
You can configure NetworkManager to start an instance of systemd-resolved. This DNS stub resolver then listens on port 53 on IP address 127.0.0.53. Consequently, this stub resolver is only reachable from the local system and not from the network.
With this configuration, NetworkManager adds the nameserver 127.0.0.53 entry to the /etc/resolv.conf file, and systemd-resolved dynamically routes DNS requests to the corresponding DNS servers specified in the NetworkManager connection profiles.
The systemd-resolved service is provided as a Technology Preview only. Technology Preview features are not supported with Red Hat production Service Level Agreements (SLAs), might not be functionally complete, and Red Hat does not recommend using them for production. These previews provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
See Technology Preview Features Support Scope on the Red Hat Customer Portal for information about the support scope for Technology Preview features.
For a supported solution, see Using dnsmasq in NetworkManager to send DNS requests for a specific domain to a selected DNS server.
Prerequisites
- The system has multiple NetworkManager connections configured.
A DNS server and search domain are configured for the connection that is responsible for resolving a specific domain.
For example, to ensure that the DNS server specified in a VPN connection resolves queries for the
example.comdomain, the following settings must be available:-
A DNS server that can resolve
example.com. A DHCP server can provide this information dynamically or you set theipv4.dnsandipv6.dnsparameters in the VPN connection profile. -
A search domain set to
example.com. A DHCP server can provide this information dynamically or you set theipv4.dns-searchandipv6.dns-searchparameters in the VPN connection profile.
-
A DNS server that can resolve
Procedure
Install the
systemd-resolvedpackage:dnf install systemd-resolved
# dnf install systemd-resolvedCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable and start the
systemd-resolvedservice:systemctl --now enable systemd-resolved
# systemctl --now enable systemd-resolvedCopy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the
/etc/NetworkManager/NetworkManager.conffile, and set the following entry in the[main]section:dns=systemd-resolved
dns=systemd-resolvedCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reload the
NetworkManagerservice:systemctl reload NetworkManager
# systemctl reload NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the DNS servers
systemd-resolveduses and for which domains the service uses a different DNS server:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that
systemd-resolveduses different DNS servers for theexample.comdomain.Use the
tcpdumppacket sniffer to verify the correct route of DNS requests:Install the
tcpdumppackage:dnf install tcpdump
# dnf install tcpdumpCopy to Clipboard Copied! Toggle word wrap Toggle overflow On one terminal, start
tcpdumpto capture DNS traffic on all interfaces:tcpdump -i any port 53
# tcpdump -i any port 53Copy to Clipboard Copied! Toggle word wrap Toggle overflow On a different terminal, resolve host names for a domain for which an exception exists and another domain, for example:
host -t A www.example.com host -t A www.redhat.com
# host -t A www.example.com # host -t A www.redhat.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify in the
tcpdumpoutput that Red Hat Enterprise Linux sends only DNS queries for theexample.comdomain to the designated DNS server and through the corresponding interface:... 13:52:42.234533 tun0 Out IP server.43534 > 198.51.100.7.domain: 50121+ A? www.example.com. (33) ... 13:52:57.753235 enp1s0 Out IP server.40864 > 192.0.2.1.domain: 6906+ A? www.redhat.com. (33) ...
... 13:52:42.234533 tun0 Out IP server.43534 > 198.51.100.7.domain: 50121+ A? www.example.com. (33) ... 13:52:57.753235 enp1s0 Out IP server.40864 > 192.0.2.1.domain: 6906+ A? www.redhat.com. (33) ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Red Hat Enterprise Linux sends the DNS query for
www.example.comto the DNS server on198.51.100.7and the query forwww.redhat.comto192.0.2.1.
Troubleshooting
Verify that the
nameserverentry in the/etc/resolv.conffile refers to127.0.0.53:cat /etc/resolv.conf nameserver 127.0.0.53
# cat /etc/resolv.conf nameserver 127.0.0.53Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the entry is missing, check the
dnsparameter in the/etc/NetworkManager/NetworkManager.conffile.Verify that the
systemd-resolvedservice listens on port53on the local IP address127.0.0.53:ss -tulpn | grep "127.0.0.53" udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:* users:(("systemd-resolve",pid=1050,fd=12)) tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:* users:(("systemd-resolve",pid=1050,fd=13))# ss -tulpn | grep "127.0.0.53" udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:* users:(("systemd-resolve",pid=1050,fd=12)) tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:* users:(("systemd-resolve",pid=1050,fd=13))Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the service does not listen on
127.0.0.53:53, check if thesystemd-resolvedservice is running.
25.3. Routing DNS traffic through a certain interface
If your host has multiple network interfaces and each DNS server is reachable only through a specific interface, configure RHEL to route DNS traffic correctly to prevent misdirected queries and resolution failures.
NetworkManager can configure the systemd-resolved, dnsmasq, and dnsconf DNS backends. To avoid DNS resolution issues on multi-interface systems, NetworkManager can automatically create dedicated routes for DNS servers tied to specific network interfaces.
Each DNS server mentioned in a connection profile is associated with a specific network interface. The DNS backend services systemd-resolved and dnsmasq ensure that each DNS name server remains accessible only through the correct network interface. However, other backend services do not support this feature. In this regard, NetworkManager has a feature that automatically adds a dedicated route so that each name server is reached only through the correct interface. You can set up the ipv4.routed-dns and ipv6.routed-dns properties to use this feature.
Example scenario:
Connection profile 1 <example-connection-1> :
-
Default gateway:
192.0.2.254 -
DNS server:
10.0.0.1 - Search domain: example-domain.com
-
Default gateway:
Connection profile 2 <example-connection-2> :
-
Default gateway:
198.51.100.254(this gateway has no access to the10.0.0.0/24network) -
DNS server:
203.0.113.1
-
Default gateway:
In this example, you have two connection profiles: <example-connection-1> and <example-connection-2> that are connected through enp1s0 and enp7s0 network interfaces. If the <example-connection-2> second profile was connected first, the default gateway 198.51.100.254 of this connection has a lower metric and takes precedence over the first profile. Consequently, RHEL uses the default gateway of the second connection while connecting to the DNS server 10.0.0.1 of the first profile. As a result, the DNS resolution fails. To solve this problem, enable the ipv4.routed-dns setting for both connection profiles so that NetworkManager creates a dedicated route for the 10.0.0.1 DNS server through the correct interface, in this case, enp1s0.
Prerequisites
- The connection profiles already exist.
Procedure
Modify the connection profile to enable the creation of routes to the name server:
For connection profile 1, enter:
nmcli connection modify <example-connection-1> ipv4.routed-dns yes
# nmcli connection modify <example-connection-1> ipv4.routed-dns yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow For connection profile 2, enter:
nmcli connection modify <example-connection-2> ipv4.routed-dns yes
# nmcli connection modify <example-connection-2> ipv4.routed-dns yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Re-activate the connections:
nmcli connection up <example-connection-1> nmcli connection up <example-connection-2>
# nmcli connection up <example-connection-1> # nmcli connection up <example-connection-2>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the route to reach an IP address:
ip route get 203.0.113.1 203.0.113.1 dev enp1s0 table 20053 src 10.0.0.1 uid 0
# ip route get 203.0.113.1 203.0.113.1 dev enp1s0 table 20053 src 10.0.0.1 uid 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command verifies if the name server is reached through the correct interface and uses the policy routing method that places all the routes for DNS servers in the special routing table
20053.
Chapter 26. Managing the default gateway setting
The default gateway is a router that forwards network packets when no other route matches the destination of a packet. In a local network, the default gateway is typically the host that is one hop closer to the internet.
26.1. Setting the default gateway on an existing connection by using nmcli
In most situations, administrators set the default gateway when they create a connection. However, you can also set or update the default gateway setting on a previously created connection by using the nmcli utility.
Prerequisites
- At least one static IP address must be configured on the connection on which the default gateway will be set.
-
If the user is logged in on a physical console, user permissions are sufficient. Otherwise, the user must have
rootpermissions.
Procedure
Set the IP addresses of the default gateway:
To set the IPv4 default gateway, enter:
nmcli connection modify <connection_name> ipv4.gateway "<IPv4_gateway_address>"
# nmcli connection modify <connection_name> ipv4.gateway "<IPv4_gateway_address>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To set the IPv6 default gateway, enter:
nmcli connection modify <connection_name> ipv6.gateway "<IPv6_gateway_address>"
# nmcli connection modify <connection_name> ipv6.gateway "<IPv6_gateway_address>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the network connection for changes to take effect:
nmcli connection up <connection_name>
# nmcli connection up <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningAll connections currently using this network connection are temporarily interrupted during the restart.
Verification
Verify that the route is active:
To display the IPv4 default gateway, enter:
ip -4 route default via 192.0.2.1 dev example proto static metric 100
# ip -4 route default via 192.0.2.1 dev example proto static metric 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the IPv6 default gateway, enter:
ip -6 route default via 2001:db8:1::1 dev example proto static metric 100 pref medium
# ip -6 route default via 2001:db8:1::1 dev example proto static metric 100 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow
26.2. Setting the default gateway on an existing connection by using the nmcli interactive mode
In most situations, administrators set the default gateway when they create a connection. However, you can also set or update the default gateway setting on a previously created connection by using the interactive mode of the nmcli utility.
Prerequisites
- At least one static IP address must be configured on the connection on which the default gateway will be set.
-
If the user is logged in on a physical console, user permissions are sufficient. Otherwise, the user must have
rootpermissions.
Procedure
Open the
nmcliinteractive mode for the required connection:nmcli connection edit <connection_name>
# nmcli connection edit <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the default gateway
To set the IPv4 default gateway, enter:
nmcli> set ipv4.gateway "<IPv4_gateway_address>"
nmcli> set ipv4.gateway "<IPv4_gateway_address>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To set the IPv6 default gateway, enter:
nmcli> set ipv6.gateway "<IPv6_gateway_address>"
nmcli> set ipv6.gateway "<IPv6_gateway_address>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Verify that the default gateway was set correctly:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Save the configuration:
nmcli> save persistent
nmcli> save persistentCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the network connection for changes to take effect:
nmcli> activate <connection_name>
nmcli> activate <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningAll connections currently using this network connection are temporarily interrupted during the restart.
Leave the
nmcliinteractive mode:nmcli> quit
nmcli> quitCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the route is active:
To display the IPv4 default gateway, enter:
ip -4 route default via 192.0.2.1 dev example proto static metric 100
# ip -4 route default via 192.0.2.1 dev example proto static metric 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the IPv6 default gateway, enter:
ip -6 route default via 2001:db8:1::1 dev example proto static metric 100 pref medium
# ip -6 route default via 2001:db8:1::1 dev example proto static metric 100 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow
26.3. Setting the default gateway on an existing connection by using nm-connection-editor
In most situations, administrators set the default gateway when they create a connection. However, you can also set or update the default gateway setting on a previously created connection using the nm-connection-editor application.
Prerequisites
- At least one static IP address must be configured on the connection on which the default gateway will be set.
Procedure
Open a terminal, and enter
nm-connection-editor:nm-connection-editor
# nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Select the connection to modify, and click the gear wheel icon to edit the existing connection.
Set the IPv4 default gateway. For example, to set the IPv4 address of the default gateway on the connection to
192.0.2.1:-
Open the
IPv4 Settingstab. Enter the address in the
gatewayfield next to the IP range the gateway’s address is within:
-
Open the
Set the IPv6 default gateway. For example, to set the IPv6 address of the default gateway on the connection to
2001:db8:1::1:-
Open the
IPv6tab. Enter the address in the
gatewayfield next to the IP range the gateway’s address is within: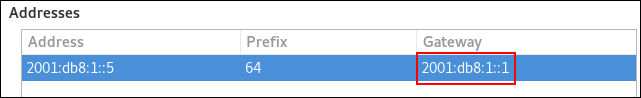
-
Open the
- Click .
- Click .
Restart the network connection for changes to take effect. For example, to restart the
exampleconnection using the command line:nmcli connection up example
# nmcli connection up exampleCopy to Clipboard Copied! Toggle word wrap Toggle overflow WarningAll connections currently using this network connection are temporarily interrupted during the restart.
Verification
Verify that the route is active.
To display the IPv4 default gateway:
ip -4 route default via 192.0.2.1 dev example proto static metric 100
# ip -4 route default via 192.0.2.1 dev example proto static metric 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the IPv6 default gateway:
ip -6 route default via 2001:db8:1::1 dev example proto static metric 100 pref medium
# ip -6 route default via 2001:db8:1::1 dev example proto static metric 100 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow
26.4. Setting the default gateway on an existing connection by using control-center
In most situations, administrators set the default gateway when they create a connection. However, you can also set or update the default gateway setting on a previously created connection using the control-center application.
Prerequisites
- At least one static IP address must be configured on the connection on which the default gateway will be set.
-
The network configuration of the connection is open in the
control-centerapplication.
Procedure
Set the IPv4 default gateway. For example, to set the IPv4 address of the default gateway on the connection to
192.0.2.1:-
Open the
IPv4tab. Enter the address in the
gatewayfield next to the IP range the gateway’s address is within: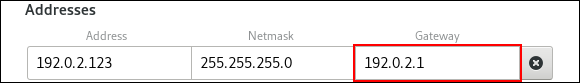
-
Open the
Set the IPv6 default gateway. For example, to set the IPv6 address of the default gateway on the connection to
2001:db8:1::1:-
Open the
IPv6tab. Enter the address in the
gatewayfield next to the IP range the gateway’s address is within:
-
Open the
- Click .
Back in the
Networkwindow, disable and re-enable the connection by switching the button for the connection to and back to for changes to take effect.WarningAll connections currently using this network connection are temporarily interrupted during the restart.
Verification
Verify that the route is active.
To display the IPv4 default gateway:
ip -4 route default via 192.0.2.1 dev example proto static metric 100
$ ip -4 route default via 192.0.2.1 dev example proto static metric 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the IPv6 default gateway:
ip -6 route default via 2001:db8:1::1 dev example proto static metric 100 pref medium
$ ip -6 route default via 2001:db8:1::1 dev example proto static metric 100 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow
26.5. Setting the default gateway on an existing connection by using nmstatectl
You can use the declarative Nmstate API to set or update the default gateway in a connection. Nmstate ensures that the result matches the configuration file or rolls back the changes.
Prerequisites
- At least one static IP address must be configured on the connection on which the default gateway will be set.
-
The
enp1s0interface is configured, and the IP address of the default gateway is within the subnet of the IP configuration of this interface. -
The
nmstatepackage is installed.
Procedure
Create a YAML file, for example
~/set-default-gateway.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow These settings define
192.0.2.1as the default gateway, and the default gateway is reachable through theenp1s0interface.Apply the settings to the system:
nmstatectl apply ~/set-default-gateway.yml
# nmstatectl apply ~/set-default-gateway.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
26.6. Setting the default gateway on an existing connection by using the network RHEL system role
By using the network RHEL system role, you can automate setting the default gateway in a NetworkManager connection profile. With this method, you can remotely configure the default gateway on hosts defined in a playbook.
In most situations, administrators set the default gateway when they create a connection. However, you can also set or update the default gateway setting on a previously-created connection.
You cannot use the network RHEL system role to update only specific values in an existing connection profile. The role ensures that a connection profile exactly matches the settings in a playbook. If a connection profile with the same name already exists, the role applies the settings from the playbook and resets all other settings in the profile to their defaults. To prevent resetting values, always specify the whole configuration of the network connection profile in the playbook, including the settings that you do not want to change.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Query the Ansible facts of the managed node and verify the active network settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
26.7. How NetworkManager manages multiple default gateways
In certain situations, for example for fallback reasons, you set multiple default gateways on a host. However, to avoid asynchronous routing issues, each default gateway of the same protocol requires a separate metric value.
Note that RHEL only uses the connection to the default gateway that has the lowest metric set.
You can set the metric for both the IPv4 and IPv6 gateway of a connection using the following command:
nmcli connection modify <connection_name> ipv4.route-metric <value> ipv6.route-metric <value>
# nmcli connection modify <connection_name> ipv4.route-metric <value> ipv6.route-metric <value>Do not set the same metric value for the same protocol in multiple connection profiles to avoid routing issues.
If you set a default gateway without a metric value, NetworkManager automatically sets the metric value based on the interface type. For that, NetworkManager assigns the default value of this network type to the first connection that is activated, and sets an incremented value to each other connection of the same type in the order they are activated. For example, if two Ethernet connections with a default gateway exist, NetworkManager sets a metric of 100 on the route to the default gateway of the connection that you activate first. For the second connection, NetworkManager sets 101.
The following is an overview of frequently-used network types and their default metrics:
| Connection type | Default metric value |
|---|---|
| VPN | 50 |
| Ethernet | 100 |
| MACsec | 125 |
| InfiniBand | 150 |
| Bond | 300 |
| Team | 350 |
| VLAN | 400 |
| Bridge | 425 |
| TUN | 450 |
| Wi-Fi | 600 |
| IP tunnel | 675 |
26.8. Configuring NetworkManager to avoid using a specific profile to provide a default gateway
In connection profiles that are not connected to the default gateway, you can configure that NetworkManager never uses this profile to provide the default gateway.
Prerequisites
- The NetworkManager connection profile for the connection that is not connected to the default gateway exists.
Procedure
If the connection uses a dynamic IP configuration, configure that NetworkManager does not use this connection as the default connection for the corresponding IP type, meaning that NetworkManager will never assign the default route to it:
nmcli connection modify <connection_name> ipv4.never-default yes ipv6.never-default yes
# nmcli connection modify <connection_name> ipv4.never-default yes ipv6.never-default yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that setting
ipv4.never-defaultandipv6.never-defaulttoyes, automatically removes the default gateway’s IP address for the corresponding protocol from the connection profile.Activate the connection:
nmcli connection up <connection_name>
# nmcli connection up <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
-
Use the
ip -4 routeandip -6 routecommands to verify that RHEL does not use the network interface for the default route for the IPv4 and IPv6 protocol.
26.9. Fixing unexpected routing behavior due to multiple default gateways
For most hosts, you require only a single default gateway to prevent unexpected routing behavior and asynchronous routing issues. Multiple default gateways are typically needed only for specific scenarios, such as when using Multipath TCP.
To route traffic to different internet providers, use policy-based routing instead of multiple default gateways.
Prerequisites
- The host uses NetworkManager to manage network connections, which is the default.
- The host has multiple network interfaces.
- The host has multiple default gateways configured.
Procedure
Display the routing table:
For IPv4, enter:
ip -4 route default via 192.0.2.1 dev enp1s0 proto dhcp metric 101 default via 198.51.100.1 dev enp7s0 proto dhcp metric 102 ...
# ip -4 route default via 192.0.2.1 dev enp1s0 proto dhcp metric 101 default via 198.51.100.1 dev enp7s0 proto dhcp metric 102 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow For IPv6, enter:
ip -6 route default via 2001:db8:1::1 dev enp1s0 proto static ra 101 pref medium default via 2001:db8:2::1 dev enp7s0 proto static ra 102 pref medium ...
# ip -6 route default via 2001:db8:1::1 dev enp1s0 proto static ra 101 pref medium default via 2001:db8:2::1 dev enp7s0 proto static ra 102 pref medium ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Entries starting with
defaultindicate a default route. Note the interface names of these entries displayed next todev.Use the following commands to display the NetworkManager connections that use the interfaces you identified in the previous step:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In these examples, the profiles named
Corporate-LANandInternet-Providerhave the default gateways set. Because, in a local network, the default gateway is typically the host that is one hop closer to the internet, the rest of this procedure assumes that the default gateways in theCorporate-LANare incorrect.Configure that NetworkManager does not use the
Corporate-LANconnection as the default route for IPv4 and IPv6 connections:nmcli connection modify Corporate-LAN ipv4.never-default yes ipv6.never-default yes
# nmcli connection modify Corporate-LAN ipv4.never-default yes ipv6.never-default yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that setting
ipv4.never-defaultandipv6.never-defaulttoyes, automatically removes the default gateway’s IP address for the corresponding protocol from the connection profile.Activate the
Corporate-LANconnection:nmcli connection up Corporate-LAN
# nmcli connection up Corporate-LANCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 and IPv6 routing tables and verify that only one default gateway is available for each protocol:
For IPv4, enter:
ip -4 route default via 198.51.100.1 dev enp7s0 proto dhcp metric 102 ...
# ip -4 route default via 198.51.100.1 dev enp7s0 proto dhcp metric 102 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow For IPv6, enter:
ip -6 route default via 2001:db8:2::1 dev enp7s0 proto ra metric 102 pref medium ...
# ip -6 route default via 2001:db8:2::1 dev enp7s0 proto ra metric 102 pref medium ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 27. Configuring a static route
Routing directs traffic between mutually-connected networks. In larger environments, administrators configure services so that routers dynamically learn about each other. In smaller ones, administrators often configure static routes to ensure traffic can reach its destination.
You need static routes to achieve a functioning communication among multiple networks if all of these conditions apply:
- The traffic has to pass multiple networks.
- The exclusive traffic flow through the default gateways is not sufficient.
The Example of a network that requires static routes section describes scenarios and how the traffic flows between different networks when you do not configure static routes.
27.1. Example of a network that requires static routes
You require static routes in this example because not all IP networks are directly connected through one router. Without the static routes, some networks cannot communicate with each other. Additionally, traffic from some networks flows only in one direction.
The network topology in this example is artificial and only used to explain the concept of static routing. It is not a recommended topology in production environments.
For a functioning communication among all networks in this example, configure a static route to Raleigh (198.51.100.0/24) with next the hop Router 2 (203.0.113.10). The IP address of the next hop is the one of Router 2 in the data center network (203.0.113.0/24).
You can configure the static route as follows:
-
For a simplified configuration, set this static route only on Router 1. However, this increases the traffic on Router 1 because hosts from the data center (
203.0.113.0/24) send traffic to Raleigh (198.51.100.0/24) always through Router 1 to Router 2. -
For a more complex configuration, configure this static route on all hosts in the data center (
203.0.113.0/24). All hosts in this subnet then send traffic directly to Router 2 (203.0.113.10) that is closer to Raleigh (198.51.100.0/24).
For more details between which networks traffic flows or not, see the explanations below the diagram.
In case that the required static routes are not configured, the following are the situations in which the communication works and when it does not:
Hosts in the Berlin network (
192.0.2.0/24):- Can communicate with other hosts in the same subnet because they are directly connected.
-
Can communicate with the internet because Router 1 is in the Berlin network (
192.0.2.0/24) and has a default gateway, which leads to the internet. -
Can communicate with the data center network (
203.0.113.0/24) because Router 1 has interfaces in both the Berlin (192.0.2.0/24) and the data center (203.0.113.0/24) networks. -
Cannot communicate with the Raleigh network (
198.51.100.0/24) because Router 1 has no interface in this network. Therefore, Router 1 sends the traffic to its own default gateway (internet).
Hosts in the data center network (
203.0.113.0/24):- Can communicate with other hosts in the same subnet because they are directly connected.
-
Can communicate with the internet because they have their default gateway set to Router 1, and Router 1 has interfaces in both networks, the data center (
203.0.113.0/24) and to the internet. -
Can communicate with the Berlin network (
192.0.2.0/24) because they have their default gateway set to Router 1, and Router 1 has interfaces in both the data center (203.0.113.0/24) and the Berlin (192.0.2.0/24) networks. -
Cannot communicate with the Raleigh network (
198.51.100.0/24) because the data center network has no interface in this network. Therefore, hosts in the data center (203.0.113.0/24) send traffic to their default gateway (Router 1). Router 1 also has no interface in the Raleigh network (198.51.100.0/24) and, as a result, Router 1 sends this traffic to its own default gateway (internet).
Hosts in the Raleigh network (
198.51.100.0/24):- Can communicate with other hosts in the same subnet because they are directly connected.
-
Cannot communicate with hosts on the internet. Router 2 sends the traffic to Router 1 because of the default gateway settings. The actual behavior of Router 1 depends on the reverse path filter (
rp_filter) system control (sysctl) setting. By default on RHEL, Router 1 drops the outgoing traffic instead of routing it to the internet. However, regardless of the configured behavior, communication is not possible without the static route. -
Cannot communicate with the data center network (
203.0.113.0/24). The outgoing traffic reaches the destination through Router 2 because of the default gateway setting. However, replies to packets do not reach the sender because hosts in the data center network (203.0.113.0/24) send replies to their default gateway (Router 1). Router 1 then sends the traffic to the internet. -
Cannot communicate with the Berlin network (
192.0.2.0/24). Router 2 sends the traffic to Router 1 because of the default gateway settings. The actual behavior of Router 1 depends on thesysctlsettingrp_filter. By default on RHEL, Router 1 drops the outgoing traffic instead of sending it to the Berlin network (192.0.2.0/24). However, regardless of the configured behavior, communication is not possible without the static route.
In addition to configuring the static routes, you must enable IP forwarding on both routers.
27.2. How to use the nmcli utility to configure a static route
You can use the nmcli utility to configure a static route on the command line.
Use following syntax:
nmcli connection modify connection_name ipv4.routes "ip[/prefix] [next_hop] [metric] [attribute=value] [attribute=value] ..."
$ nmcli connection modify connection_name ipv4.routes "ip[/prefix] [next_hop] [metric] [attribute=value] [attribute=value] ..."The command supports the following route attributes:
-
cwnd=n: Sets the congestion window (CWND) size, defined in the number of packets. -
lock-cwnd=true|false: Defines whether or not the kernel can update the CWND value. -
lock-mtu=true|false: Defines whether or not the kernel can update the MTU to path MTU discovery. -
lock-window=true|false: Defines whether or not the kernel can update the maximum window size for TCP packets. -
mtu=<mtu_value>: Sets the maximum transfer unit (MTU) to use along the path to the destination. -
onlink=true|false: Defines whether the next hop is directly attached to this link even if it does not match any interface prefix. -
scope=<scope>: For an IPv4 route, this attribute sets the scope of the destinations covered by the route prefix. Set the value as an integer (0-255). -
src=<source_address>: Sets the source address to prefer when sending traffic to the destinations covered by the route prefix. -
table=<table_id>: Sets the ID of the table the route should be added to. If you omit this parameter, NetworkManager uses themaintable. -
tos=<type_of_service_key>: Sets the type of service (TOS) key. Set the value as an integer (0-255). -
type=<route_type>: Sets the route type. NetworkManager supports theunicast,local,blackhole,unreachable,prohibit, andthrowroute types. The default isunicast. -
window=<window_size>: Sets the maximal window size for TCP to advertise to these destinations, measured in bytes.
If you use the ipv4.routes option without a preceding + sign, nmcli overrides all current settings of this parameter.
To create an additional route, enter:
nmcli connection modify connection_name +ipv4.routes "<route>"
$ nmcli connection modify connection_name +ipv4.routes "<route>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To remove a specific route, enter:
nmcli connection modify connection_name -ipv4.routes "<route>"
$ nmcli connection modify connection_name -ipv4.routes "<route>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
27.3. Configuring a static route by using nmcli
You can add a static route to an existing NetworkManager connection profile using the nmcli connection modify command.
The procedure below configures the following routes:
-
An IPv4 route to the remote
198.51.100.0/24network. The corresponding gateway with the IP address192.0.2.10is reachable through theLANconnection profile. -
An IPv6 route to the remote
2001:db8:2::/64network. The corresponding gateway with the IP address2001:db8:1::10is reachable through theLANconnection profile.
Prerequisites
-
The
LANconnection profile exists and it configures this host to be in the same IP subnet as the gateways.
Procedure
Add the static IPv4 route to the
LANconnection profile:nmcli connection modify LAN +ipv4.routes "198.51.100.0/24 192.0.2.10"
# nmcli connection modify LAN +ipv4.routes "198.51.100.0/24 192.0.2.10"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To set multiple routes in one step, pass the individual routes comma-separated to the command:
nmcli connection modify <connection_profile> +ipv4.routes "<remote_network_1>/<subnet_mask_1> <gateway_1>, <remote_network_n>/<subnet_mask_n> <gateway_n>, ..."
# nmcli connection modify <connection_profile> +ipv4.routes "<remote_network_1>/<subnet_mask_1> <gateway_1>, <remote_network_n>/<subnet_mask_n> <gateway_n>, ..."Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the static IPv6 route to the
LANconnection profile:nmcli connection modify LAN +ipv6.routes "2001:db8:2::/64 2001:db8:1::10"
# nmcli connection modify LAN +ipv6.routes "2001:db8:2::/64 2001:db8:1::10"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Re-activate the connection:
nmcli connection up LAN
# nmcli connection up LANCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 routes:
ip -4 route ... 198.51.100.0/24 via 192.0.2.10 dev enp1s0
# ip -4 route ... 198.51.100.0/24 via 192.0.2.10 dev enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 routes:
ip -6 route ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp1s0 metric 1024 pref medium
# ip -6 route ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp1s0 metric 1024 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.4. Configuring a static route by using nmtui
The nmtui application provides a text-based user interface for NetworkManager. You can use nmtui to configure static routes on a host without a graphical interface.
For example, the procedure below adds a route to the 192.0.2.0/24 network that uses the gateway running on 198.51.100.1, which is reachable through an existing connection profile.
In nmtui:
- Navigate by using the cursor keys.
- Press a button by selecting it and hitting Enter.
- Select and clear checkboxes by using Space.
- To return to the previous screen, use ESC.
Prerequisites
- The network is configured.
- The gateway for the static route must be directly reachable on the interface.
- If the user is logged in on a physical console, user permissions are sufficient. Otherwise, the command requires root permissions.
Procedure
Start
nmtui:nmtui
# nmtuiCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Select Edit a connection, and press Enter.
- Select the connection profile through which you can reach the next hop to the destination network, and press Enter.
- Depending on whether it is an IPv4 or IPv6 route, press the Show button next to the protocol’s configuration area.
Press the Edit button next to Routing. This opens a new window where you configure static routes:
Press the Add button and fill in:
- The destination network, including the prefix in Classless Inter-Domain Routing (CIDR) format
- The IP address of the next hop
- A metric value, if you add multiple routes to the same network and want to prioritize the routes by efficiency
- Repeat the previous step for every route you want to add and that is reachable through this connection profile.
Press the OK button to return to the window with the connection settings.
Figure 27.1. Example of a static route without metric

-
Press the OK button to return to the
nmtuimain menu. - Select Activate a connection and press Enter.
Select the connection profile that you edited, and press Enter twice to deactivate and activate it again.
ImportantSkip this step if you run
nmtuiover a remote connection, such as SSH, that uses the connection profile you want to reactivate. In this case, if you deactivate it innmtui, the connection is terminated and, consequently, you cannot activate it again. To avoid this problem, use thenmcli connection <connection_profile> upcommand to reactivate the connection in the mentioned scenario.- Press the Back button to return to the main menu.
-
Select Quit, and press Enter to close the
nmtuiapplication.
Verification
Verify that the route is active:
ip route ... 192.0.2.0/24 via 198.51.100.1 dev example proto static metric 100
$ ip route ... 192.0.2.0/24 via 198.51.100.1 dev example proto static metric 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow
27.5. Configuring a static route by using control-center
You can use control-center in GNOME to add a static route to the configuration of a network connection.
The procedure below configures the following routes:
-
An IPv4 route to the remote
198.51.100.0/24network. The corresponding gateway has the IP address192.0.2.10. -
An IPv6 route to the remote
2001:db8:2::/64network. The corresponding gateway has the IP address2001:db8:1::10.
Prerequisites
- The network is configured.
- This host is in the same IP subnet as the gateways.
-
The network configuration of the connection is opened in the
control-centerapplication. See Configuring an Ethernet connection by using nm-connection-editor.
Procedure
On the
IPv4tab:-
Optional: Disable automatic routes by clicking the button in the
Routessection of theIPv4tab to use only static routes. If automatic routes are enabled, Red Hat Enterprise Linux uses static routes and routes received from a DHCP server. Enter the address, netmask, gateway, and optionally a metric value of the IPv4 route:
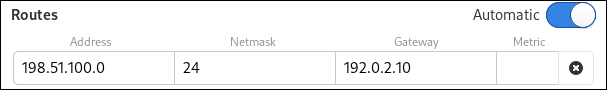
-
Optional: Disable automatic routes by clicking the button in the
On the
IPv6tab:-
Optional: Disable automatic routes by clicking the button in the
Routessection of theIPv4tab to use only static routes. Enter the address, netmask, gateway, and optionally a metric value of the IPv6 route:
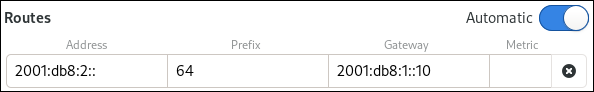
-
Optional: Disable automatic routes by clicking the button in the
- Click .
Back in the
Networkwindow, disable and re-enable the connection by switching the button for the connection to and back to for changes to take effect.WarningRestarting the connection briefly disrupts connectivity on that interface.
Verification
Display the IPv4 routes:
ip -4 route ... 198.51.100.0/24 via 192.0.2.10 dev enp1s0
# ip -4 route ... 198.51.100.0/24 via 192.0.2.10 dev enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 routes:
ip -6 route ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp1s0 metric 1024 pref medium
# ip -6 route ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp1s0 metric 1024 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.6. Configuring a static route by using nm-connection-editor
You can use the nm-connection-editor application to add a static route to the configuration of a network connection.
The procedure below configures the following routes:
-
An IPv4 route to the remote
198.51.100.0/24network. The corresponding gateway with the IP address192.0.2.10is reachable through theexampleconnection. -
An IPv6 route to the remote
2001:db8:2::/64network. The corresponding gateway with the IP address2001:db8:1::10is reachable through theexampleconnection.
Prerequisites
- The network is configured.
- This host is in the same IP subnet as the gateways.
Procedure
Open a terminal, and enter
nm-connection-editor:nm-connection-editor
$ nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Select the
exampleconnection profile, and click the gear wheel icon to edit the existing connection. On the
IPv4 Settingstab:- Click the button.
Click the button and enter the address, netmask, gateway, and optionally a metric value.
- Click .
On the
IPv6 Settingstab:- Click the button.
Click the button and enter the address, netmask, gateway, and optionally a metric value.
- Click .
- Click .
Restart the network connection for changes to take effect. For example, to restart the
exampleconnection using the command line:nmcli connection up example
# nmcli connection up exampleCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 routes:
ip -4 route ... 198.51.100.0/24 via 192.0.2.10 dev enp1s0
# ip -4 route ... 198.51.100.0/24 via 192.0.2.10 dev enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 routes:
ip -6 route ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp1s0 metric 1024 pref medium
# ip -6 route ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp1s0 metric 1024 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.7. Configuring a static route by using the nmcli interactive mode
You can use the interactive mode of the nmcli utility to add a static route to the configuration of a network connection.
The procedure below configures the following routes:
-
An IPv4 route to the remote
198.51.100.0/24network. The corresponding gateway with the IP address192.0.2.10is reachable through theexampleconnection. -
An IPv6 route to the remote
2001:db8:2::/64network. The corresponding gateway with the IP address2001:db8:1::10is reachable through theexampleconnection.
Prerequisites
-
The
exampleconnection profile exists and it configures this host to be in the same IP subnet as the gateways.
Procedure
Open the
nmcliinteractive mode for theexampleconnection:nmcli connection edit example
# nmcli connection edit exampleCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the static IPv4 route:
nmcli> set ipv4.routes 198.51.100.0/24 192.0.2.10
nmcli> set ipv4.routes 198.51.100.0/24 192.0.2.10Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the static IPv6 route:
nmcli> set ipv6.routes 2001:db8:2::/64 2001:db8:1::10
nmcli> set ipv6.routes 2001:db8:2::/64 2001:db8:1::10Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Verify that the routes were added correctly to the configuration:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
ipattribute displays the network to route and thenhattribute the gateway (next hop).Save the configuration:
nmcli> save persistent
nmcli> save persistentCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the network connection:
nmcli> activate example
nmcli> activate exampleCopy to Clipboard Copied! Toggle word wrap Toggle overflow Leave the
nmcliinteractive mode:nmcli> quit
nmcli> quitCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 routes:
ip -4 route ... 198.51.100.0/24 via 192.0.2.10 dev enp1s0
# ip -4 route ... 198.51.100.0/24 via 192.0.2.10 dev enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 routes:
ip -6 route ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp1s0 metric 1024 pref medium
# ip -6 route ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp1s0 metric 1024 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.8. Configuring a static route by using nmstatectl
You can use the declarative Nmstate API to configure a static route. Nmstate ensures that the result matches the configuration file or rolls back the changes.
Prerequisites
-
The
enp1s0network interface is configured and is in the same IP subnet as the gateways. -
The
nmstatepackage is installed.
Procedure
Create a YAML file, for example
~/add-static-route-to-enp1s0.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow These settings define the following static routes:
-
An IPv4 route to the remote
198.51.100.0/24network. The corresponding gateway with the IP address192.0.2.10is reachable through theenp1s0interface. -
An IPv6 route to the remote
2001:db8:2::/64network. The corresponding gateway with the IP address2001:db8:1::10is reachable through theenp1s0interface.
-
An IPv4 route to the remote
Apply the settings to the system:
nmstatectl apply ~/add-static-route-to-enp1s0.yml
# nmstatectl apply ~/add-static-route-to-enp1s0.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 routes:
ip -4 route ... 198.51.100.0/24 via 192.0.2.10 dev enp1s0
# ip -4 route ... 198.51.100.0/24 via 192.0.2.10 dev enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 routes:
ip -6 route ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp1s0 metric 1024 pref medium
# ip -6 route ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp1s0 metric 1024 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.9. Configuring a static route by using the network RHEL system role
You can use the network RHEL system role to configure static routes.
When you run a play that uses the network RHEL system role and if the setting values do not match the values specified in the play, the role overrides the existing connection profile with the same name. To prevent resetting these values to their defaults, always specify the whole configuration of the network connection profile in the play, even if the configuration, for example the IP configuration, already exists.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 routes:
ansible managed-node-01.example.com -m command -a 'ip -4 route' managed-node-01.example.com | CHANGED | rc=0 >> ... 198.51.100.0/24 via 192.0.2.10 dev enp7s0
# ansible managed-node-01.example.com -m command -a 'ip -4 route' managed-node-01.example.com | CHANGED | rc=0 >> ... 198.51.100.0/24 via 192.0.2.10 dev enp7s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the IPv6 routes:
ansible managed-node-01.example.com -m command -a 'ip -6 route' managed-node-01.example.com | CHANGED | rc=0 >> ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp7s0 metric 1024 pref medium
# ansible managed-node-01.example.com -m command -a 'ip -6 route' managed-node-01.example.com | CHANGED | rc=0 >> ... 2001:db8:2::/64 via 2001:db8:1::10 dev enp7s0 metric 1024 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 28. Configuring policy-based routing to define alternative routes
By default, the RHEL kernel forwards network packets based on the destination address by using a routing table. With policy-based routing, you can configure complex scenarios to route packets based on various criteria, such as the source address.
28.1. Routing traffic from a specific subnet to a different default gateway by using nmcli
You can use policy-based routing to configure a different default gateway for traffic from certain subnets.
For example, you can configure RHEL as a router that, by default, routes all traffic to internet provider A using the default route. However, traffic received from the internal workstations subnet is routed to provider B.
The procedure assumes the following network topology:
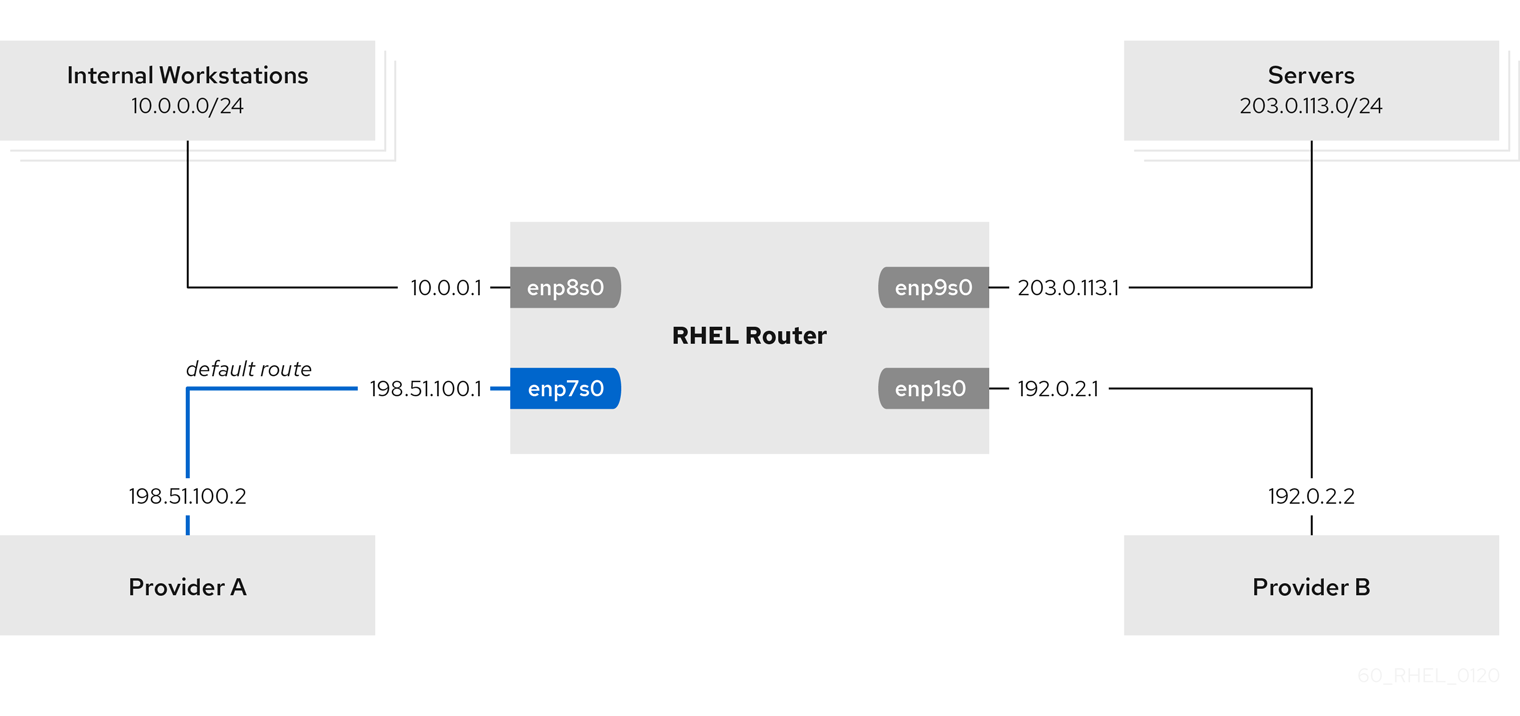
Prerequisites
-
The system uses
NetworkManagerto configure the network, which is the default. The RHEL router you want to set up in the procedure has four network interfaces:
-
The
enp7s0interface is connected to the network of provider A. The gateway IP in the provider’s network is198.51.100.2, and the network uses a/30network mask. -
The
enp1s0interface is connected to the network of provider B. The gateway IP in the provider’s network is192.0.2.2, and the network uses a/30network mask. -
The
enp8s0interface is connected to the10.0.0.0/24subnet with internal workstations. -
The
enp9s0interface is connected to the203.0.113.0/24subnet with the company’s servers.
-
The
-
Hosts in the internal workstations subnet use
10.0.0.1as the default gateway. In the procedure, you assign this IP address to theenp8s0network interface of the router. -
Hosts in the server subnet use
203.0.113.1as the default gateway. In the procedure, you assign this IP address to theenp9s0network interface of the router. -
The
firewalldservice is enabled and active.
Procedure
Configure the network interface to provider A:
nmcli connection add type ethernet con-name Provider-A ifname enp7s0 ipv4.method manual ipv4.addresses 198.51.100.1/30 ipv4.gateway 198.51.100.2 ipv4.dns 198.51.100.200 connection.zone external
# nmcli connection add type ethernet con-name Provider-A ifname enp7s0 ipv4.method manual ipv4.addresses 198.51.100.1/30 ipv4.gateway 198.51.100.2 ipv4.dns 198.51.100.200 connection.zone externalCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
nmcli connection addcommand creates a NetworkManager connection profile. The command uses the following options:-
type ethernet: Defines that the connection type is Ethernet. -
con-name <connection_name>: Sets the name of the profile. Use a meaningful name to avoid confusion. -
ifname <network_device>: Sets the network interface. -
ipv4.method manual: Enables to configure a static IP address. -
ipv4.addresses <IP_address>/<subnet_mask>: Sets the IPv4 addresses and subnet mask. -
ipv4.gateway <IP_address>: Sets the default gateway address. -
ipv4.dns <IP_of_DNS_server>: Sets the IPv4 address of the DNS server. -
connection.zone <firewalld_zone>: Assigns the network interface to the definedfirewalldzone. Note thatfirewalldautomatically enables masquerading for interfaces assigned to theexternalzone.
-
Configure the network interface to provider B:
nmcli connection add type ethernet con-name Provider-B ifname enp1s0 ipv4.method manual ipv4.addresses 192.0.2.1/30 ipv4.routes "0.0.0.0/0 192.0.2.2 table=5000" connection.zone external
# nmcli connection add type ethernet con-name Provider-B ifname enp1s0 ipv4.method manual ipv4.addresses 192.0.2.1/30 ipv4.routes "0.0.0.0/0 192.0.2.2 table=5000" connection.zone externalCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command uses the
ipv4.routesparameter instead ofipv4.gatewayto set the default gateway. This is required to assign the default gateway for this connection to a different routing table (5000) than the default. NetworkManager automatically creates this new routing table when the connection is activated.Configure the network interface to the internal workstations subnet:
nmcli connection add type ethernet con-name Internal-Workstations ifname enp8s0 ipv4.method manual ipv4.addresses 10.0.0.1/24 ipv4.routes "10.0.0.0/24 table=5000" ipv4.routing-rules "priority 5 from 10.0.0.0/24 table 5000" connection.zone trusted
# nmcli connection add type ethernet con-name Internal-Workstations ifname enp8s0 ipv4.method manual ipv4.addresses 10.0.0.1/24 ipv4.routes "10.0.0.0/24 table=5000" ipv4.routing-rules "priority 5 from 10.0.0.0/24 table 5000" connection.zone trustedCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command uses the
ipv4.routesparameter to add a static route to the routing table with ID5000. This static route for the10.0.0.0/24subnet uses the IP of the local network interface to provider B (192.0.2.1) as the next hop.Additionally, the command uses the
ipv4.routing-rulesparameter to add a routing rule with priority5that routes traffic from the10.0.0.0/24subnet to table5000. Low values have a high priority.Note that the syntax in the
ipv4.routing-rulesparameter is the same as in anip rule addcommand, except thatipv4.routing-rulesalways requires specifying a priority.Configure the network interface to the server subnet:
nmcli connection add type ethernet con-name Servers ifname enp9s0 ipv4.method manual ipv4.addresses 203.0.113.1/24 connection.zone trusted
# nmcli connection add type ethernet con-name Servers ifname enp9s0 ipv4.method manual ipv4.addresses 203.0.113.1/24 connection.zone trustedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
On a RHEL host in the internal workstation subnet:
Install the
traceroutepackage:dnf install traceroute
# dnf install tracerouteCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
tracerouteutility to display the route to a host on the internet:traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 10.0.0.1 (10.0.0.1) 0.337 ms 0.260 ms 0.223 ms 2 192.0.2.2 (192.0.2.2) 0.884 ms 1.066 ms 1.248 ms ...
# traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 10.0.0.1 (10.0.0.1) 0.337 ms 0.260 ms 0.223 ms 2 192.0.2.2 (192.0.2.2) 0.884 ms 1.066 ms 1.248 ms ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output of the command displays that the router sends packets over
192.0.2.1, which is the network of provider B.
On a RHEL host in the server subnet:
Install the
traceroutepackage:dnf install traceroute
# dnf install tracerouteCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
tracerouteutility to display the route to a host on the internet:traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 203.0.113.1 (203.0.113.1) 2.179 ms 2.073 ms 1.944 ms 2 198.51.100.2 (198.51.100.2) 1.868 ms 1.798 ms 1.549 ms ...
# traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 203.0.113.1 (203.0.113.1) 2.179 ms 2.073 ms 1.944 ms 2 198.51.100.2 (198.51.100.2) 1.868 ms 1.798 ms 1.549 ms ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output of the command displays that the router sends packets over
198.51.100.2, which is the network of provider A.
Troubleshooting steps
On the RHEL router:
Display the rule list:
ip rule list 0: from all lookup local 5: from 10.0.0.0/24 lookup 5000 32766: from all lookup main 32767: from all lookup default
# ip rule list 0: from all lookup local 5: from 10.0.0.0/24 lookup 5000 32766: from all lookup main 32767: from all lookup defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, RHEL contains rules for the tables
local,main, anddefault.Display the routes in table
5000:ip route list table 5000 0.0.0.0/0 via 192.0.2.2 dev enp1s0 proto static metric 100 10.0.0.0/24 dev enp8s0 proto static scope link src 192.0.2.1 metric 102
# ip route list table 5000 0.0.0.0/0 via 192.0.2.2 dev enp1s0 proto static metric 100 10.0.0.0/24 dev enp8s0 proto static scope link src 192.0.2.1 metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the interfaces and firewall zones:
firewall-cmd --get-active-zones external interfaces: enp1s0 enp7s0 trusted interfaces: enp8s0 enp9s0
# firewall-cmd --get-active-zones external interfaces: enp1s0 enp7s0 trusted interfaces: enp8s0 enp9s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the
externalzone has masquerading enabled:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
28.2. Routing traffic from a specific subnet to a different default gateway by using the network RHEL system role
You can use policy-based routing to configure a different default gateway for traffic from certain subnets. By using the network RHEL system role, you can automate the creation of the connection profiles, including routing tables and rules.
For example, you can configure RHEL as a router that, by default, routes all traffic to internet provider A using the default route. However, traffic received from the internal workstations subnet is routed to provider B. By using Ansible and the network RHEL system role, you can automate this process and remotely configure connection profiles on the hosts defined in a playbook.
This procedure assumes the following network topology:

Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. -
The managed nodes use NetworkManager and the
firewalldservice. The managed nodes you want to configure has four network interfaces:
-
The
enp7s0interface is connected to the network of provider A. The gateway IP in the provider’s network is198.51.100.2, and the network uses a/30network mask. -
The
enp1s0interface is connected to the network of provider B. The gateway IP in the provider’s network is192.0.2.2, and the network uses a/30network mask. -
The
enp8s0interface is connected to the10.0.0.0/24subnet with internal workstations. -
The
enp9s0interface is connected to the203.0.113.0/24subnet with the company’s servers.
-
The
-
Hosts in the internal workstations subnet use
10.0.0.1as the default gateway. In the procedure, you assign this IP address to theenp8s0network interface of the router. -
Hosts in the server subnet use
203.0.113.1as the default gateway. In the procedure, you assign this IP address to theenp9s0network interface of the router.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
table: <value>-
Assigns the route from the same list entry as the
tablevariable to the specified routing table. routing_rule: <list>- Defines the priority of the specified routing rule and from a connection profile to which routing table the rule is assigned.
zone: <zone_name>-
Assigns the network interface from a connection profile to the specified
firewalldzone.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
On a RHEL host in the internal workstation subnet:
Install the
traceroutepackage:dnf install traceroute
# dnf install tracerouteCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
tracerouteutility to display the route to a host on the internet:traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 10.0.0.1 (10.0.0.1) 0.337 ms 0.260 ms 0.223 ms 2 192.0.2.2 (192.0.2.2) 0.884 ms 1.066 ms 1.248 ms ...
# traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 10.0.0.1 (10.0.0.1) 0.337 ms 0.260 ms 0.223 ms 2 192.0.2.2 (192.0.2.2) 0.884 ms 1.066 ms 1.248 ms ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output of the command displays that the router sends packets over
192.0.2.1, which is the network of provider B.
On a RHEL host in the server subnet:
Install the
traceroutepackage:dnf install traceroute
# dnf install tracerouteCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
tracerouteutility to display the route to a host on the internet:traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 203.0.113.1 (203.0.113.1) 2.179 ms 2.073 ms 1.944 ms 2 198.51.100.2 (198.51.100.2) 1.868 ms 1.798 ms 1.549 ms ...
# traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 203.0.113.1 (203.0.113.1) 2.179 ms 2.073 ms 1.944 ms 2 198.51.100.2 (198.51.100.2) 1.868 ms 1.798 ms 1.549 ms ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output of the command displays that the router sends packets over
198.51.100.2, which is the network of provider A.
On the RHEL router that you configured using the RHEL system role:
Display the rule list:
ip rule list 0: from all lookup local 5: from 10.0.0.0/24 lookup 5000 32766: from all lookup main 32767: from all lookup default
# ip rule list 0: from all lookup local 5: from 10.0.0.0/24 lookup 5000 32766: from all lookup main 32767: from all lookup defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, RHEL contains rules for the tables
local,main, anddefault.Display the routes in table
5000:ip route list table 5000 0.0.0.0/0 via 192.0.2.2 dev enp1s0 proto static metric 100 10.0.0.0/24 dev enp8s0 proto static scope link src 192.0.2.1 metric 102
# ip route list table 5000 0.0.0.0/0 via 192.0.2.2 dev enp1s0 proto static metric 100 10.0.0.0/24 dev enp8s0 proto static scope link src 192.0.2.1 metric 102Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the interfaces and firewall zones:
firewall-cmd --get-active-zones external interfaces: enp1s0 enp7s0 trusted interfaces: enp8s0 enp9s0
# firewall-cmd --get-active-zones external interfaces: enp1s0 enp7s0 trusted interfaces: enp8s0 enp9s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the
externalzone has masquerading enabled:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 29. Reusing the same IP address on different interfaces
With Virtual routing and forwarding (VRF), administrators can use multiple routing tables simultaneously on the same host. For that, VRF partitions a network at layer 3. This enables the administrator to isolate traffic using separate and independent route tables per VRF domain. This technique is similar to virtual LANs (VLAN), which partitions a network at layer 2, where the operating system uses different VLAN tags to isolate traffic sharing the same physical medium.
One benefit of VRF over partitioning on layer 2 is that routing scales better considering the number of peers involved.
Red Hat Enterprise Linux uses a virtual vrt device for each VRF domain and adds routes to a VRF domain by adding existing network devices to a VRF device. Addresses and routes previously attached to the original device will be moved inside the VRF domain.
Note that each VRF domain is isolated from each other.
29.1. Permanently reusing the same IP address on different interfaces
You can use the virtual routing and forwarding (VRF) feature to permanently use the same IP address on different interfaces in one server.
To enable remote peers to contact both VRF interfaces while reusing the same IP address, the network interfaces must belong to different broadcasting domains. A broadcast domain in a network is a set of nodes, which receive broadcast traffic sent by any of them. In most configurations, all nodes connected to the same switch belong to the same broadcasting domain.
Prerequisites
-
You are logged in as the
rootuser. - The network interfaces are not configured.
Procedure
Create and configure the first VRF device:
Create a connection for the VRF device and assign it to a routing table. For example, to create a VRF device named
vrf0that is assigned to the1001routing table:nmcli connection add type vrf ifname vrf0 con-name vrf0 table 1001 ipv4.method disabled ipv6.method disabled
# nmcli connection add type vrf ifname vrf0 con-name vrf0 table 1001 ipv4.method disabled ipv6.method disabledCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
vrf0device:nmcli connection up vrf0
# nmcli connection up vrf0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Assign a network device to the VRF just created. For example, to add the
enp1s0Ethernet device to thevrf0VRF device and assign an IP address and the subnet mask toenp1s0, enter:nmcli connection add type ethernet con-name vrf.enp1s0 ifname enp1s0 controller vrf0 ipv4.method manual ipv4.address 192.0.2.1/24
# nmcli connection add type ethernet con-name vrf.enp1s0 ifname enp1s0 controller vrf0 ipv4.method manual ipv4.address 192.0.2.1/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow Activate the
vrf.enp1s0connection:nmcli connection up vrf.enp1s0
# nmcli connection up vrf.enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Create and configure the next VRF device:
Create the VRF device and assign it to a routing table. For example, to create a VRF device named
vrf1that is assigned to the1002routing table, enter:nmcli connection add type vrf ifname vrf1 con-name vrf1 table 1002 ipv4.method disabled ipv6.method disabled
# nmcli connection add type vrf ifname vrf1 con-name vrf1 table 1002 ipv4.method disabled ipv6.method disabledCopy to Clipboard Copied! Toggle word wrap Toggle overflow Activate the
vrf1device:nmcli connection up vrf1
# nmcli connection up vrf1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Assign a network device to the VRF just created. For example, to add the
enp7s0Ethernet device to thevrf1VRF device and assign an IP address and the subnet mask toenp7s0, enter:nmcli connection add type ethernet con-name vrf.enp7s0 ifname enp7s0 controller vrf1 ipv4.method manual ipv4.address 192.0.2.1/24
# nmcli connection add type ethernet con-name vrf.enp7s0 ifname enp7s0 controller vrf1 ipv4.method manual ipv4.address 192.0.2.1/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow Activate the
vrf.enp7s0device:nmcli connection up vrf.enp7s0
# nmcli connection up vrf.enp7s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
29.2. Temporarily reusing the same IP address on different interfaces
You can use the virtual routing and forwarding (VRF) feature to temporarily use the same IP address on different interfaces in one server. Use this procedure only for testing purposes, because the configuration is temporary and lost after you reboot the system.
To enable remote peers to contact both VRF interfaces while reusing the same IP address, the network interfaces must belong to different broadcasting domains. A broadcast domain in a network is a set of nodes which receive broadcast traffic sent by any of them. In most configurations, all nodes connected to the same switch belong to the same broadcasting domain.
Prerequisites
-
You are logged in as the
rootuser. - The network interfaces are not configured.
Procedure
Create and configure the first VRF device:
Create the VRF device and assign it to a routing table. For example, to create a VRF device named
bluethat is assigned to the1001routing table:ip link add dev blue type vrf table 1001
# ip link add dev blue type vrf table 1001Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
bluedevice:ip link set dev blue up
# ip link set dev blue upCopy to Clipboard Copied! Toggle word wrap Toggle overflow Assign a network device to the VRF device. For example, to add the
enp1s0Ethernet device to theblueVRF device:ip link set dev enp1s0 master blue
# ip link set dev enp1s0 master blueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
enp1s0device:ip link set dev enp1s0 up
# ip link set dev enp1s0 upCopy to Clipboard Copied! Toggle word wrap Toggle overflow Assign an IP address and subnet mask to the
enp1s0device. For example, to set it to192.0.2.1/24:ip addr add dev enp1s0 192.0.2.1/24
# ip addr add dev enp1s0 192.0.2.1/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Create and configure the next VRF device:
Create the VRF device and assign it to a routing table. For example, to create a VRF device named
redthat is assigned to the1002routing table:ip link add dev red type vrf table 1002
# ip link add dev red type vrf table 1002Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
reddevice:ip link set dev red up
# ip link set dev red upCopy to Clipboard Copied! Toggle word wrap Toggle overflow Assign a network device to the VRF device. For example, to add the
enp7s0Ethernet device to theredVRF device:ip link set dev enp7s0 master red
# ip link set dev enp7s0 master redCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
enp7s0device:ip link set dev enp7s0 up
# ip link set dev enp7s0 upCopy to Clipboard Copied! Toggle word wrap Toggle overflow Assign the same IP address and subnet mask to the
enp7s0device as you used forenp1s0in theblueVRF domain:ip addr add dev enp7s0 192.0.2.1/24
# ip addr add dev enp7s0 192.0.2.1/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Optional: Create further VRF devices as described above.
Chapter 30. Starting a service within an isolated VRF network
With virtual routing and forwarding (VRF), you can create isolated networks with a routing table that is different to the main routing table of the operating system. You can then start services and applications so that they have only access to the network defined in that routing table.
30.1. Configuring a VRF device
To use virtual routing and forwarding (VRF), you create a VRF device and attach a physical or virtual network interface and routing information to it.
To prevent that you lock yourself out yourself out remotely, perform this procedure on the local console or remotely over a network interface that you do not want to assign to the VRF device.
Prerequisites
- You are logged in locally or using a network interface that is different to the one you want to assign to the VRF device.
Procedure
Create the
vrf0connection with a same-named virtual device, and attach it to routing table1000:nmcli connection add type vrf ifname vrf0 con-name vrf0 table 1000 ipv4.method disabled ipv6.method disabled
# nmcli connection add type vrf ifname vrf0 con-name vrf0 table 1000 ipv4.method disabled ipv6.method disabledCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
enp1s0device to thevrf0connection, and configure the IP settings:nmcli connection add type ethernet con-name enp1s0 ifname enp1s0 controller vrf0 ipv4.method manual ipv4.address 192.0.2.1/24 ipv4.gateway 192.0.2.254
# nmcli connection add type ethernet con-name enp1s0 ifname enp1s0 controller vrf0 ipv4.method manual ipv4.address 192.0.2.1/24 ipv4.gateway 192.0.2.254Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates the
enp1s0connection as a port of thevrf0connection. Due to this configuration, the routing information are automatically assigned to the routing table1000that is associated with thevrf0device.If you require static routes in the isolated network:
Add the static routes:
nmcli connection modify enp1s0 +ipv4.routes "198.51.100.0/24 192.0.2.2"
# nmcli connection modify enp1s0 +ipv4.routes "198.51.100.0/24 192.0.2.2"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This adds a route to the
198.51.100.0/24network that uses192.0.2.2as the router.Activate the connection:
nmcli connection up enp1s0
# nmcli connection up enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IP settings of the device that is associated with
vrf0:ip -br addr show vrf vrf0 enp1s0 UP 192.0.2.1/24
# ip -br addr show vrf vrf0 enp1s0 UP 192.0.2.1/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the VRF devices and their associated routing table:
ip vrf show Name Table ----------------------- vrf0 1000
# ip vrf show Name Table ----------------------- vrf0 1000Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the main routing table:
ip route show default via 203.0.113.0/24 dev enp7s0 proto static metric 100
# ip route show default via 203.0.113.0/24 dev enp7s0 proto static metric 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow The main routing table does not mention any routes associated with the device
enp1s0device or the192.0.2.1/24subnet.Display the routing table
1000:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
defaultentry indicates that services that use this routing table, use192.0.2.254as their default gateway and not the default gateway in the main routing table.Execute the
tracerouteutility in the network associated withvrf0to verify that the utility uses the route from table1000:ip vrf exec vrf0 traceroute 203.0.113.1 traceroute to 203.0.113.1 (203.0.113.1), 30 hops max, 60 byte packets 1 192.0.2.254 (192.0.2.254) 0.516 ms 0.459 ms 0.430 ms ...
# ip vrf exec vrf0 traceroute 203.0.113.1 traceroute to 203.0.113.1 (203.0.113.1), 30 hops max, 60 byte packets 1 192.0.2.254 (192.0.2.254) 0.516 ms 0.459 ms 0.430 ms ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The first hop is the default gateway that is assigned to the routing table
1000and not the default gateway from the system’s main routing table.
30.2. Starting a service within an isolated VRF network
You can configure a service, such as the Apache HTTP Server, to start within an isolated virtual routing and forwarding (VRF) network.
Services can only bind to local IP addresses that are in the same VRF network.
Prerequisites
-
You configured the
vrf0device. -
You configured Apache HTTP Server to listen only on the IP address that is assigned to the interface associated with the
vrf0device.
Procedure
Display the content of the
httpdsystemd service:systemctl cat httpd ... [Service] ExecStart=/usr/sbin/httpd $OPTIONS -DFOREGROUND ...
# systemctl cat httpd ... [Service] ExecStart=/usr/sbin/httpd $OPTIONS -DFOREGROUND ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the content of the
ExecStartparameter in a later step to run the same command within the isolated VRF network.Create the
/etc/systemd/system/httpd.service.d/directory:mkdir /etc/systemd/system/httpd.service.d/
# mkdir /etc/systemd/system/httpd.service.d/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
/etc/systemd/system/httpd.service.d/override.conffile with the following content:[Service] ExecStart= ExecStart=/usr/sbin/ip vrf exec vrf0 /usr/sbin/httpd $OPTIONS -DFOREGROUND ProtectControlGroups=no
[Service] ExecStart= ExecStart=/usr/sbin/ip vrf exec vrf0 /usr/sbin/httpd $OPTIONS -DFOREGROUND ProtectControlGroups=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow To override an existing parameter, such as
ExecStartin the example, you first need to unset this parameter and then set it to the new value as shown.NoteThe
ProtectControlGroups=nosetting ensures that theiputility has access to the/sys/fs/cgroup/directory to set up VRF.Reload systemd.
systemctl daemon-reload
# systemctl daemon-reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
httpdservice.systemctl restart httpd
# systemctl restart httpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the process IDs (PID) of
httpdprocesses:pidof -c httpd 1904 ...
# pidof -c httpd 1904 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the VRF association for the PIDs, for example:
ip vrf identify 1904 vrf0
# ip vrf identify 1904 vrf0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display all PIDs associated with the
vrf0device:ip vrf pids vrf0 1904 httpd ...
# ip vrf pids vrf0 1904 httpd ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 31. Configuring ethtool settings in NetworkManager connection profiles
NetworkManager can configure certain network driver and hardware settings persistently. Compared to using the ethtool utility to manage these settings, this has the benefit of not losing the settings after a reboot.
You can set the following ethtool settings in NetworkManager connection profiles:
- Offload features
- Network interface controllers can use the TCP offload engine (TOE) to offload processing certain operations to the network controller. This improves the network throughput.
- Interrupt coalesce settings
- By using interrupt coalescing, the system collects network packets and generates a single interrupt for multiple packets. This increases the amount of data sent to the kernel with one hardware interrupt, which reduces the interrupt load, and maximizes the throughput.
- Ring buffers
- These buffers store incoming and outgoing network packets. You can increase the ring buffer sizes to reduce a high packet drop rate.
- Channel settings
A network interface manages its associated number of channels along with hardware settings and network drivers. All devices associated with a network interface communicate with each other through interrupt requests (IRQ). Each device queue holds pending IRQ and communicates with each other over a data line known as channel. Types of queues are associated with specific channel types. These channel types include:
-
rxfor receiving queues -
txfor transmit queues -
otherfor link interrupts or single root input/output virtualization (SR-IOV) coordination -
combinedfor hardware capacity-based multipurpose channels
-
31.1. Configuring an ethtool offload feature by using nmcli
You can use NetworkManager to enable and disable ethtool offload features in a connection profile.
Procedure
For example, to enable the RX offload feature and disable TX offload in the
enp1s0connection profile, enter:nmcli con modify enp1s0 ethtool.feature-rx on ethtool.feature-tx off
# nmcli con modify enp1s0 ethtool.feature-rx on ethtool.feature-tx offCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command explicitly enables RX offload and disables TX offload.
To remove the setting of an offload feature that you previously enabled or disabled, set the feature’s parameter to a null value. For example, to remove the configuration for TX offload, enter:
nmcli con modify enp1s0 ethtool.feature-tx ""
# nmcli con modify enp1s0 ethtool.feature-tx ""Copy to Clipboard Copied! Toggle word wrap Toggle overflow Reactivate the network profile:
nmcli connection up enp1s0
# nmcli connection up enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Use the
ethtool -kcommand to display the current offload features of a network device:ethtool -k network_device
# ethtool -k network_deviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow
31.2. Configuring an ethtool offload feature by using the network RHEL system role
You can use the network RHEL system role to automate configuring TCP offload engine (TOE) to offload processing certain operations to the network controller. TOE improves the network throughput.
You cannot use the network RHEL system role to update only specific values in an existing connection profile. The role ensures that a connection profile exactly matches the settings in a playbook. If a connection profile with the same name already exists, the role applies the settings from the playbook and resets all other settings in the profile to their defaults. To prevent resetting values, always specify the whole configuration of the network connection profile in the playbook, including the settings that you do not want to change.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
gro: no- Disables Generic receive offload (GRO).
gso: yes- Enables Generic segmentation offload (GSO).
tx_sctp_segmentation: no- Disables TX stream control transmission protocol (SCTP) segmentation.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Query the Ansible facts of the managed node and verify the offload settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
31.3. Configuring an ethtool coalesce settings by using nmcli
You can use NetworkManager to set ethtool coalesce settings in connection profiles.
Procedure
For example, to set the maximum number of received packets to delay to
128in theenp1s0connection profile, enter:nmcli connection modify enp1s0 ethtool.coalesce-rx-frames 128
# nmcli connection modify enp1s0 ethtool.coalesce-rx-frames 128Copy to Clipboard Copied! Toggle word wrap Toggle overflow To remove a coalesce setting, set it to a null value. For example, to remove the
ethtool.coalesce-rx-framessetting, enter:nmcli connection modify enp1s0 ethtool.coalesce-rx-frames ""
# nmcli connection modify enp1s0 ethtool.coalesce-rx-frames ""Copy to Clipboard Copied! Toggle word wrap Toggle overflow To reactivate the network profile:
nmcli connection up enp1s0
# nmcli connection up enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Use the
ethtool -ccommand to display the current offload features of a network device:ethtool -c network_device
# ethtool -c network_deviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow
31.4. Configuring an ethtool coalesce settings by using the network RHEL system role
Interrupt coalescing collects network packets and generates a single interrupt for multiple packets. This reduces interrupt load and maximizes throughput. You can automate the configuration of these settings in the NetworkManager connection profile by using the network RHEL system role.
You cannot use the network RHEL system role to update only specific values in an existing connection profile. The role ensures that a connection profile exactly matches the settings in a playbook. If a connection profile with the same name already exists, the role applies the settings from the playbook and resets all other settings in the profile to their defaults. To prevent resetting values, always specify the whole configuration of the network connection profile in the playbook, including the settings that you do not want to change.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
rx_frames: <value>- Sets the number of RX frames.
gso: <value>- Sets the number of TX frames.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the current offload features of the network device:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
31.5. Increasing the ring buffer size to reduce a high packet drop rate by using nmcli
Increase the size of an Ethernet device’s ring buffers if the packet drop rate causes applications to report a loss of data, timeouts, or other issues.
Receive ring buffers are shared between the device driver and network interface controller (NIC). The card assigns a transmit (TX) and receive (RX) ring buffer. As the name implies, the ring buffer is a circular buffer where an overflow overwrites existing data. There are two ways to move data from the NIC to the kernel, hardware interrupts and software interrupts, also called SoftIRQs.
The kernel uses the RX ring buffer to store incoming packets until the device driver can process them. The device driver drains the RX ring, typically by using SoftIRQs, which puts the incoming packets into a kernel data structure called an sk_buff or skb to begin its journey through the kernel and up to the application that owns the relevant socket.
The kernel uses the TX ring buffer to hold outgoing packets which should be sent to the network. These ring buffers reside at the bottom of the stack and are a crucial point at which packet drop can occur, which in turn will adversely affect network performance.
Procedure
Display the packet drop statistics of the interface:
ethtool -S enp1s0 ... rx_queue_0_drops: 97326 rx_queue_1_drops: 63783 ...# ethtool -S enp1s0 ... rx_queue_0_drops: 97326 rx_queue_1_drops: 63783 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the output of the command depends on the network card and the driver.
High values in
discardordropcounters indicate that the available buffer fills up faster than the kernel can process the packets. Increasing the ring buffers can help to avoid such loss.Display the maximum ring buffer sizes:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the values in the
Pre-set maximumssection are higher than in theCurrent hardware settingssection, you can change the settings in the next steps.Identify the NetworkManager connection profile that uses the interface:
nmcli connection show NAME UUID TYPE DEVICE Example-Connection a5eb6490-cc20-3668-81f8-0314a27f3f75 ethernet enp1s0
# nmcli connection show NAME UUID TYPE DEVICE Example-Connection a5eb6490-cc20-3668-81f8-0314a27f3f75 ethernet enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the connection profile, and increase the ring buffers:
To increase the RX ring buffer, enter:
nmcli connection modify Example-Connection ethtool.ring-rx 4096
# nmcli connection modify Example-Connection ethtool.ring-rx 4096Copy to Clipboard Copied! Toggle word wrap Toggle overflow To increase the TX ring buffer, enter:
nmcli connection modify Example-Connection ethtool.ring-tx 4096
# nmcli connection modify Example-Connection ethtool.ring-tx 4096Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Reload the NetworkManager connection:
nmcli connection up Example-Connection
# nmcli connection up Example-ConnectionCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantDepending on the driver your NIC uses, changing in the ring buffer can shortly interrupt the network connection.
31.6. Increasing the ring buffer size to reduce a high packet drop rate by using the network RHEL system role
Increase the size of an Ethernet device’s ring buffers if the packet drop rate causes applications to report a loss of data, timeouts, or other issues.
Ring buffers are circular buffers where an overflow overwrites existing data. The network card assigns a transmit (TX) and receive (RX) ring buffer. Receive ring buffers are shared between the device driver and the network interface controller (NIC). Data can move from NIC to the kernel through either hardware interrupts or software interrupts, also called SoftIRQs.
The kernel uses the RX ring buffer to store incoming packets until the device driver can process them. The device driver drains the RX ring, typically by using SoftIRQs, which puts the incoming packets into a kernel data structure called an sk_buff or skb to begin its journey through the kernel and up to the application that owns the relevant socket.
The kernel uses the TX ring buffer to hold outgoing packets which should be sent to the network. These ring buffers reside at the bottom of the stack and are a crucial point at which packet drop can occur, which in turn will adversely affect network performance.
You configure ring buffer settings in the NetworkManager connection profiles. By using Ansible and the network RHEL system role, you can automate this process and remotely configure connection profiles on the hosts defined in a playbook.
You cannot use the network RHEL system role to update only specific values in an existing connection profile. The role ensures that a connection profile exactly matches the settings in a playbook. If a connection profile with the same name already exists, the role applies the settings from the playbook and resets all other settings in the profile to their defaults. To prevent resetting values, always specify the whole configuration of the network connection profile in the playbook, including the settings that you do not want to change.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. - You know the maximum ring buffer sizes that the device supports.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
rx: <value>- Sets the maximum number of received ring buffer entries.
tx: <value>- Sets the maximum number of transmitted ring buffer entries.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the maximum ring buffer sizes:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
31.7. Configuring an ethtool channels settings by using nmcli
The ethtool utility handles IRQ based communication with associated devices to manage related channels settings in connection profiles. Use the nmcli utility to configure ethtool settings in NetworkManager connection profiles.
Procedure
Display the channels associated with a network device:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the channel settings of a network interface:
nmcli connection modify enp1s0 ethtool.channels-rx 4 ethtool.channels-tx 3 ethtools.channels-other 9 ethtool.channels-combined 50
# nmcli connection modify enp1s0 ethtool.channels-rx 4 ethtool.channels-tx 3 ethtools.channels-other 9 ethtool.channels-combined 50Copy to Clipboard Copied! Toggle word wrap Toggle overflow Reactivate the network profile:
nmcli connection up enp1s0
# nmcli connection up enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Check the updated channel settings associated with the network device:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 32. Introduction to NetworkManager Debugging
Increasing the log levels for all or certain domains helps to log more details of the operations that NetworkManager performs. You can use this information to troubleshoot problems.
NetworkManager provides different levels and domains to produce logging information. The /etc/NetworkManager/NetworkManager.conf file is the main configuration file for NetworkManager. The logs are stored in the journal.
32.1. Introduction to NetworkManager reapply() method
NetworkManager uses profiles to manage device connection settings, which can be created, modified, or deleted through the D-Bus API. When a profile is changed, D-Bus clones the settings. To apply these changes, you must reactivate the connection’s settings or use the reapply() method.
The reapply() method has the following features:
- Updating modified connection settings without deactivation or restart of a network interface.
-
Removing pending changes from the modified connection settings. As
NetworkManagerdoes not revert the manual changes, you can reconfigure the device and revert external or manual parameters. - Creating different modified connection settings than that of the existing connection settings.
Also, reapply() method supports the following attributes:
-
bridge.ageing-time -
bridge.forward-delay -
bridge.group-address -
bridge.group-forward-mask -
bridge.hello-time -
bridge.max-age -
bridge.multicast-hash-max -
bridge.multicast-last-member-count -
bridge.multicast-last-member-interval -
bridge.multicast-membership-interval -
bridge.multicast-querier -
bridge.multicast-querier-interval -
bridge.multicast-query-interval -
bridge.multicast-query-response-interval -
bridge.multicast-query-use-ifaddr -
bridge.multicast-router -
bridge.multicast-snooping -
bridge.multicast-startup-query-count -
bridge.multicast-startup-query-interval -
bridge.priority -
bridge.stp -
bridge.VLAN-filtering -
bridge.VLAN-protocol -
bridge.VLANs -
802-3-ethernet.accept-all-mac-addresses -
802-3-ethernet.cloned-mac-address -
IPv4.addresses -
IPv4.dhcp-client-id -
IPv4.dhcp-iaid -
IPv4.dhcp-timeout -
IPv4.DNS -
IPv4.DNS-priority -
IPv4.DNS-search -
IPv4.gateway -
IPv4.ignore-auto-DNS -
IPv4.ignore-auto-routes -
IPv4.may-fail -
IPv4.method -
IPv4.never-default -
IPv4.route-table -
IPv4.routes -
IPv4.routing-rules -
IPv6.addr-gen-mode -
IPv6.addresses -
IPv6.dhcp-duid -
IPv6.dhcp-iaid -
IPv6.dhcp-timeout -
IPv6.DNS -
IPv6.DNS-priority -
IPv6.DNS-search -
IPv6.gateway -
IPv6.ignore-auto-DNS -
IPv6.may-fail -
IPv6.method -
IPv6.never-default -
IPv6.ra-timeout -
IPv6.route-metric -
IPv6.route-table -
IPv6.routes -
IPv6.routing-rules
32.2. Setting the NetworkManager log level
By default, all the log domains are set to record the INFO log level. Disable rate-limiting before collecting debug logs. With rate-limiting, systemd-journald drops messages if there are too many of them in a short time. This can occur when the log level is TRACE.
This procedure disables rate-limiting and enables recording debug logs for the all (ALL) domains.
Procedure
To disable rate-limiting, edit the
/etc/systemd/journald.conffile, uncomment theRateLimitBurstparameter in the[Journal]section, and set its value as0:RateLimitBurst=0
RateLimitBurst=0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
systemd-journaldservice.systemctl restart systemd-journald
# systemctl restart systemd-journaldCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
/etc/NetworkManager/conf.d/95-nm-debug.conffile with the following content:[logging] domains=ALL:TRACE
[logging] domains=ALL:TRACECopy to Clipboard Copied! Toggle word wrap Toggle overflow The
domainsparameter can contain multiple comma-separateddomain:levelpairs.Restart the NetworkManager service.
systemctl restart NetworkManager
# systemctl restart NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Query the
systemdjournal to display the journal entries of theNetworkManagerunit:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
32.3. Temporarily setting log levels at run time using nmcli
You can change the log level at run time using nmcli.
Procedure
Optional: Display the current logging settings:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To modify the logging level and domains, use the following options:
To set the log level for all domains to the same
LEVEL, enter:nmcli general logging level LEVEL domains ALL
# nmcli general logging level LEVEL domains ALLCopy to Clipboard Copied! Toggle word wrap Toggle overflow To change the level for specific domains, enter:
nmcli general logging level LEVEL domains DOMAINS
# nmcli general logging level LEVEL domains DOMAINSCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that updating the logging level using this command disables logging for all the other domains.
To change the level of specific domains and preserve the level of all other domains, enter:
nmcli general logging level KEEP domains DOMAIN:LEVEL,DOMAIN:LEVEL
# nmcli general logging level KEEP domains DOMAIN:LEVEL,DOMAIN:LEVELCopy to Clipboard Copied! Toggle word wrap Toggle overflow
32.4. Viewing NetworkManager logs
You can view the NetworkManager logs for troubleshooting.
Procedure
To view the logs, enter:
journalctl -u NetworkManager -b
# journalctl -u NetworkManager -bCopy to Clipboard Copied! Toggle word wrap Toggle overflow
32.5. Debugging levels and domains
You can use the levels and domains parameters to manage the debugging for NetworkManager. The level defines the verbosity level, whereas the domains define the category of the messages to record the logs with given severity (level).
| Log levels | Description |
|---|---|
|
| Does not log any messages about NetworkManager |
|
| Logs only critical errors |
|
| Logs warnings that can reflect the operation |
|
| Logs various informational messages that are useful for tracking state and operations |
|
| Enables verbose logging for debugging purposes |
|
|
Enables more verbose logging than the |
Note that subsequent levels log all messages from earlier levels. For example, setting the log level to INFO also logs messages contained in the ERR and WARN log level.
Chapter 33. Using LLDP to debug network configuration problems
You can use the Link Layer Discovery Protocol (LLDP) to debug network configuration problems in the topology. This means that, LLDP can report configuration inconsistencies with other hosts or routers and switches.
33.1. Debugging an incorrect VLAN configuration using LLDP information
If you configured a switch port to use a certain VLAN and a host does not receive these VLAN packets, you can use the Link Layer Discovery Protocol (LLDP) to debug the problem.
Prerequisites
-
The
nmstatepackage is installed. - The switch supports LLDP.
- LLDP is enabled on neighbor devices.
Procedure
Create the
~/enable-LLDP-enp1s0.ymlfile with the following content:interfaces: - name: enp1s0 type: ethernet lldp: enabled: trueinterfaces: - name: enp1s0 type: ethernet lldp: enabled: trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
~/enable-LLDP-enp1s0.ymlfile to enable LLDP on interfaceenp1s0:nmstatectl apply ~/enable-LLDP-enp1s0.yml
# nmstatectl apply ~/enable-LLDP-enp1s0.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the LLDP information:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify the output to ensure that the settings match your expected configuration. For example, the LLDP information of the interface connected to the switch shows that the switch port this host is connected to uses VLAN ID
448:- type: 127 ieee-802-1-vlans: - name: v2-0488-03-0505 vid: 488- type: 127 ieee-802-1-vlans: - name: v2-0488-03-0505 vid: 488Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the network configuration of the
enp1s0interface uses a different VLAN ID, change it accordingly.
Chapter 34. Linux traffic control
Linux Traffic Control (TC) helps in policing, classifying, shaping, and scheduling network traffic. It uses queuing disciplines (qdisc) and filters to manage and manipulate packet transmission, including mangling packet content.
The scheduling mechanism arranges or rearranges the packets before they enter or exit different queues. The most common scheduler is the First-In-First-Out (FIFO) scheduler. You can do the qdiscs operations temporarily using the tc utility or permanently using NetworkManager.
In Red Hat Enterprise Linux, you can configure default queueing disciplines in various ways to manage the traffic on a network interface.
34.1. Overview of queuing disciplines
Queuing disciplines (qdiscs) help with queuing up and, later, scheduling of traffic transmission by a network interface.
A qdisc has two operations;
- enqueue requests so that a packet can be queued up for later transmission and
- dequeue requests so that one of the queued-up packets can be chosen for immediate transmission.
Every qdisc has a 16-bit hexadecimal identification number called a handle, with an attached colon, such as 1: or abcd:. This number is called the qdisc major number. If a qdisc has classes, then the identifiers are formed as a pair of two numbers with the major number before the minor, <major>:<minor>, for example abcd:1. The numbering scheme for the minor numbers depends on the qdisc type. Sometimes the numbering is systematic, where the first-class has the ID <major>:1, the second one <major>:2, and so on. Some qdiscs allow the user to set class minor numbers arbitrarily when creating the class.
- Classful
qdiscs Different types of
qdiscsexist and help in the transfer of packets to and from a networking interface. You can configureqdiscswith root, parent, or child classes. The point where children can be attached are called classes. Classes inqdiscare flexible and can always contain either multiple children classes or a single child,qdisc. There is no prohibition against a class containing a classfulqdiscitself, this facilitates complex traffic control scenarios.Classful
qdiscsdo not store any packets themselves. Instead, they enqueue and dequeue requests down to one of their children according to criteria specific to theqdisc. Eventually, this recursive packet passing ends up where the packets are stored (or picked up from in the case of dequeuing).- Classless
qdiscs -
Some
qdiscscontain no child classes and they are called classlessqdiscs. Classlessqdiscsrequire less customization compared to classfulqdiscs. It is usually enough to attach them to an interface.
34.2. Introduction to connection tracking
Connection tracking is a Linux kernel networking feature for logical networks that tracks connections and identifies packet flow in those connections.
At a firewall, the Netfilter framework filters packets from an external network. After a packet arrives, Netfilter assigns a connection tracking entry. Connection tracking filters and analyzes every packet, sets up the connection tracking table to store connection status, and updates the connection status based on identified packets. For example, in the case of FTP connection, Netfilter assigns a connection tracking entry to ensure all packets of FTP connection work in the same manner. The connection tracking entry stores a Netfilter mark and tracks the connection state information in the memory table in which a new packet tuple maps with an existing entry. If the packet tuple does not map with an existing entry, the packet adds a new connection tracking entry that groups packets of the same connection.
You can control and analyze traffic on the network interface. The tc traffic controller utility uses the qdisc discipline to configure the packet scheduler in the network. The qdisc kernel-configured queuing discipline enqueues packets to the interface. By using qdisc, Kernel catches all the traffic before a network interface transmits it. Also, to limit the bandwidth rate of packets belonging to the same connection, use the tc qdisc command.
To retrieve data from connection tracking marks into various fields, use the tc utility with the ctinfo module and the connmark functionality. For storing packet mark information, the ctinfo module copies the Netfilter mark and the connection state information into a socket buffer (skb) mark metadata field.
Transmitting a packet over a physical medium removes all the metadata of a packet. Before the packet loses its metadata, the ctinfo module maps and copies the Netfilter mark value to a specific value of the Diffserv code point (DSCP) in the packet’s IP field.
34.3. Inspecting qdiscs of a network interface using the tc utility
By default, Red Hat Enterprise Linux systems use fq_codel qdisc. You can inspect the qdisc counters using the tc utility.
Procedure
Optional: View your current
qdisc:tc qdisc show dev enp0s1
# tc qdisc show dev enp0s1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Inspect the current
qdisccounters:tc -s qdisc show dev enp0s1 qdisc fq_codel 0: root refcnt 2 limit 10240p flows 1024 quantum 1514 target 5.0ms interval 100.0ms memory_limit 32Mb ecn Sent 1008193 bytes 5559 pkt (dropped 233, overlimits 55 requeues 77) backlog 0b 0p requeues 0
# tc -s qdisc show dev enp0s1 qdisc fq_codel 0: root refcnt 2 limit 10240p flows 1024 quantum 1514 target 5.0ms interval 100.0ms memory_limit 32Mb ecn Sent 1008193 bytes 5559 pkt (dropped 233, overlimits 55 requeues 77) backlog 0b 0p requeues 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
dropped- the number of times a packet is dropped because all queues are full -
overlimits- the number of times the configured link capacity is filled -
sent- the number of dequeues
-
34.4. Updating the default qdisc
If you observe networking packet losses with the current qdisc, you can change the qdisc based on your network-requirements.
Procedure
View the current default
qdisc:sysctl -a | grep qdisc net.core.default_qdisc = fq_codel
# sysctl -a | grep qdisc net.core.default_qdisc = fq_codelCopy to Clipboard Copied! Toggle word wrap Toggle overflow View the
qdiscof current Ethernet connection:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the existing
qdisc:sysctl -w net.core.default_qdisc=pfifo_fast
# sysctl -w net.core.default_qdisc=pfifo_fastCopy to Clipboard Copied! Toggle word wrap Toggle overflow To apply the changes, reload the network driver:
modprobe -r NETWORKDRIVERNAME modprobe NETWORKDRIVERNAME
# modprobe -r NETWORKDRIVERNAME # modprobe NETWORKDRIVERNAMECopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the network interface:
ip link set enp0s1 up
# ip link set enp0s1 upCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
View the
qdiscof the Ethernet connection:tc -s qdisc show dev enp0s1 qdisc pfifo_fast 0: root refcnt 2 bands 3 priomap 1 2 2 2 1 2 0 0 1 1 1 1 1 1 1 1 Sent 373186 bytes 5333 pkt (dropped 0, overlimits 0 requeues 0) backlog 0b 0p requeues 0 ....
# tc -s qdisc show dev enp0s1 qdisc pfifo_fast 0: root refcnt 2 bands 3 priomap 1 2 2 2 1 2 0 0 1 1 1 1 1 1 1 1 Sent 373186 bytes 5333 pkt (dropped 0, overlimits 0 requeues 0) backlog 0b 0p requeues 0 ....Copy to Clipboard Copied! Toggle word wrap Toggle overflow
34.5. Temporarily setting the current qdisc of a network interface using the tc utility
Changing the current qdisc can optimize how the kernel handles packets as they pass through a network interface. For testing and benchmarking purposes, you can change the qdisc temporarily.
Procedure
Optional: View the current
qdisc:tc -s qdisc show dev enp0s1
# tc -s qdisc show dev enp0s1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the current
qdisc:tc qdisc replace dev enp0s1 root htb
# tc qdisc replace dev enp0s1 root htbCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
View the updated current
qdisc:tc -s qdisc show dev enp0s1 qdisc htb 8001: root refcnt 2 r2q 10 default 0 direct_packets_stat 0 direct_qlen 1000 Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0) backlog 0b 0p requeues 0
# tc -s qdisc show dev enp0s1 qdisc htb 8001: root refcnt 2 r2q 10 default 0 direct_packets_stat 0 direct_qlen 1000 Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0) backlog 0b 0p requeues 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
34.6. Permanently setting the current qdisc of a network interface using NetworkManager
Changing the current qdisc can optimize how the kernel handles packets as they pass through a network interface. If you identified the optimal qdisc for your scenario, set it permanently in the NetworkManager connection profile.
Procedure
Optional: View the current
qdisc:tc qdisc show dev enp0s1 qdisc fq_codel 0: root refcnt 2
# tc qdisc show dev enp0s1 qdisc fq_codel 0: root refcnt 2Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the current
qdisc:nmcli connection modify enp0s1 tc.qdiscs 'root pfifo_fast'
# nmcli connection modify enp0s1 tc.qdiscs 'root pfifo_fast'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: To add another
qdiscover the existingqdisc, use the+tc.qdiscoption:nmcli connection modify enp0s1 +tc.qdisc 'ingress handle ffff:'
# nmcli connection modify enp0s1 +tc.qdisc 'ingress handle ffff:'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Activate the changes:
nmcli connection up enp0s1
# nmcli connection up enp0s1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
View current
qdiscthe network interface:tc qdisc show dev enp0s1 qdisc pfifo_fast 8001: root refcnt 2 bands 3 priomap 1 2 2 2 1 2 0 0 1 1 1 1 1 1 1 1 qdisc ingress ffff: parent ffff:fff1 ----------------
# tc qdisc show dev enp0s1 qdisc pfifo_fast 8001: root refcnt 2 bands 3 priomap 1 2 2 2 1 2 0 0 1 1 1 1 1 1 1 1 qdisc ingress ffff: parent ffff:fff1 ----------------Copy to Clipboard Copied! Toggle word wrap Toggle overflow
34.7. Configuring the rate limiting of packets by using the tc-ctinfo utility
With rate limiting, you can limit network traffic, prevent the exhaustion of resources in the network, and reduce the load on servers by limiting repetitive packet requests in a specific time frame.
The connection tracking entry stores the Netfilter mark and connection information. When a router forwards a packet from the firewall, the router either removes or modifies the connection tracking entry from the packet. The connection tracking information (ctinfo) module retrieves data from connection tracking marks into various fields. This kernel module preserves the Netfilter mark by copying it into a socket buffer (skb) mark metadata field.
Prerequisites
-
The
iperf3utility is installed on a server and a client.
Procedure
Perform the following steps on the server:
Add a virtual link to the network interface:
ip link add name ifb4eth0 numtxqueues 48 numrxqueues 48 type ifb
# ip link add name ifb4eth0 numtxqueues 48 numrxqueues 48 type ifbCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command has the following parameters:
name ifb4eth0- Sets a new virtual device interface.
numtxqueues 48- Sets the number of transmit queues.
numrxqueues 48- Sets the number of receive queues.
type ifb- Sets the type of the new device.
Change the state of the interface:
ip link set dev ifb4eth0 up
# ip link set dev ifb4eth0 upCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
qdiscattribute on the physical network interface and apply it to the incoming traffic:tc qdisc add dev enp1s0 handle ffff: ingress
# tc qdisc add dev enp1s0 handle ffff: ingressCopy to Clipboard Copied! Toggle word wrap Toggle overflow In the
handle ffff:option, thehandleparameter assigns the major numberffff:as a default value to a classfulqdiscon theenp1s0physical network interface, whereqdiscis a queueing discipline parameter to analyze traffic control.Add a filter on the physical interface of the
ipprotocol to classify packets:tc filter add dev enp1s0 parent ffff: protocol ip u32 match u32 0 0 action ctinfo cpmark 100 action mirred egress redirect dev ifb4eth0
# tc filter add dev enp1s0 parent ffff: protocol ip u32 match u32 0 0 action ctinfo cpmark 100 action mirred egress redirect dev ifb4eth0Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command has the following attributes:
parent ffff:-
Sets major number
ffff:for the parentqdisc. u32 match u32 0 0-
Sets the
u32filter tomatchthe IP headers the ofu32pattern. The first0represents the second byte of IP header while the other0is for the mask match telling the filter which bits to match. action ctinfo- Sets action to retrieve data from the connection tracking mark into various fields.
cpmark 100-
Copies the connection tracking mark (connmark)
100into the packet IP header field. action mirred egress redirect dev ifb4eth0-
Sets the
actiontomirredto redirect the received packets to theifb4eth0destination interface.
Add a classful
qdiscto the interface:tc qdisc add dev ifb4eth0 root handle 1: htb default 1000
# tc qdisc add dev ifb4eth0 root handle 1: htb default 1000Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command sets the major number
1to rootqdiscand uses thehtbhierarchy token bucket with classfulqdiscof minor-id1000.Limit the traffic on the interface to 1 Mbit/s with an upper limit of 2 Mbit/s:
tc class add dev ifb4eth0 parent 1:1 classid 1:100 htb ceil 2mbit rate 1mbit prio 100
# tc class add dev ifb4eth0 parent 1:1 classid 1:100 htb ceil 2mbit rate 1mbit prio 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command has the following parameters:
parent 1:1-
Sets
parentwithclassidas1androotas1. classid 1:100-
Sets
classidas1:100where1is the number of parentqdiscand100is the number of classes of the parentqdisc. htb ceil 2mbit-
The
htbclassfulqdiscallows upper limit bandwidth of2 Mbit/sas theceilrate limit.
Apply the Stochastic Fairness Queuing (
sfq) of classlessqdiscto interface with a time interval of60seconds to reduce queue algorithm perturbation:tc qdisc add dev ifb4eth0 parent 1:100 sfq perturb 60
# tc qdisc add dev ifb4eth0 parent 1:100 sfq perturb 60Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the firewall mark (
fw) filter to the interface:tc filter add dev ifb4eth0 parent 1:0 protocol ip prio 100 handle 100 fw classid 1:100
# tc filter add dev ifb4eth0 parent 1:0 protocol ip prio 100 handle 100 fw classid 1:100Copy to Clipboard Copied! Toggle word wrap Toggle overflow Restore the packet meta mark from the connection mark (
CONNMARK):nft add rule ip mangle PREROUTING counter meta mark set ct mark
# nft add rule ip mangle PREROUTING counter meta mark set ct markCopy to Clipboard Copied! Toggle word wrap Toggle overflow In this command, the
nftutility has amangletable with thePREROUTINGchain rule specification that alters incoming packets before routing to replace the packet mark withCONNMARK.If no
nfttable and chain exist, create a table and add a chain rule:nft add table ip mangle nft add chain ip mangle PREROUTING {type filter hook prerouting priority mangle \;}# nft add table ip mangle # nft add chain ip mangle PREROUTING {type filter hook prerouting priority mangle \;}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the meta mark on
tcppackets that are received on the specified destination address192.0.2.3:nft add rule ip mangle PREROUTING ip daddr 192.0.2.3 counter meta mark set 0x64
# nft add rule ip mangle PREROUTING ip daddr 192.0.2.3 counter meta mark set 0x64Copy to Clipboard Copied! Toggle word wrap Toggle overflow Save the packet mark into the connection mark:
nft add rule ip mangle PREROUTING counter ct mark set mark
# nft add rule ip mangle PREROUTING counter ct mark set markCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the
iperf3utility as the server on a system by using the-sparameter and the server then waits for the response of the client connection:iperf3 -s
# iperf3 -sCopy to Clipboard Copied! Toggle word wrap Toggle overflow
On the client, run
iperf3as a client and connect to the server that listens on IP address192.0.2.3for periodic HTTP request-response timestamp:iperf3 -c 192.0.2.3 -t TCP_STREAM | tee rate
# iperf3 -c 192.0.2.3 -t TCP_STREAM | tee rateCopy to Clipboard Copied! Toggle word wrap Toggle overflow 192.0.2.3is the IP address of the server while192.0.2.4is the IP address of the client.Terminate the
iperf3utility on the server by pressing Ctrl+C:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Terminate the
iperf3utility on the client by pressing Ctrl+C:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the statistics about packet counts of the
htbandsfqclasses on the interface:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the statistics of packet counts for the
mirredandctinfoactions:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the statistics of the
htbrate-limiter and its configuration:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
34.8. Available qdiscs in RHEL
Each qdisc addresses unique networking-related issues. You can use any of them to shape network traffic based on your networking requirements.
These qdiscs are available in RHEL:
qdisc name | Included in | Offload support |
|---|---|---|
| Credit-Based Shaper |
| Yes |
| CHOose and Keep for responsive flows, CHOose and Kill for unresponsive flows (CHOKE) |
| |
| Controlled Delay (CoDel) |
| |
| Enhanced Transmission Selection (ETS) |
| Yes |
| Fair Queue (FQ) |
| |
| Fair Queuing Controlled Delay (FQ_CODel) |
| |
| Generalized Random Early Detection (GRED) |
| |
| Hierarchical Fair Service Curve (HSFC) |
| |
| Heavy-Hitter Filter (HHF) |
| |
| Hierarchy Token Bucket (HTB) |
| Yes |
| INGRESS |
| Yes |
| Multi Queue Priority (MQPRIO) |
| Yes |
| Multiqueue (MULTIQ) |
| Yes |
| Network Emulator (NETEM) |
| |
| Proportional Integral-controller Enhanced (PIE) |
| |
| PLUG |
| |
| Quick Fair Queueing (QFQ) |
| |
| Random Early Detection (RED) |
| Yes |
| Stochastic Fair Blue (SFB) |
| |
| Stochastic Fairness Queueing (SFQ) |
| |
| Token Bucket Filter (TBF) |
| Yes |
| Trivial Link Equalizer (TEQL) |
|
The qdisc offload requires hardware and driver support on NIC.
Chapter 35. Authenticating a RHEL client to the network by using the 802.1X standard with a certificate stored on the file system
Port-based Network Access Control (NAC), based on the IEEE 802.1X standard, protects a network from unauthorized clients. If the network uses Extensible Authentication Protocol Transport Layer Security (EAP-TLS), you require a certificate to authenticate the client.
35.1. Configuring 802.1X network authentication on an existing Ethernet connection by using nmcli
You can use the nmcli utility to configure an Ethernet connection with 802.1X network authentication on the command line.
Prerequisites
- The network supports 802.1X network authentication.
- The Ethernet connection profile exists in NetworkManager and has a valid IP configuration.
The following files required for TLS authentication exist on the client:
-
The client key stored is in the
/etc/pki/tls/private/client.keyfile, and the file is owned and only readable by therootuser. -
The client certificate is stored in the
/etc/pki/tls/certs/client.crtfile. -
The Certificate Authority (CA) certificate is stored in the
/etc/pki/tls/certs/ca.crtfile.
-
The client key stored is in the
-
The
wpa_supplicantpackage is installed.
Procedure
Set the Extensible Authentication Protocol (EAP) to
tlsand the paths to the client certificate and key file:nmcli connection modify enp1s0 802-1x.eap tls 802-1x.client-cert /etc/pki/tls/certs/client.crt 802-1x.private-key /etc/pki/tls/private/client.key
# nmcli connection modify enp1s0 802-1x.eap tls 802-1x.client-cert /etc/pki/tls/certs/client.crt 802-1x.private-key /etc/pki/tls/private/client.keyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that you must set the
802-1x.eap,802-1x.client-cert, and802-1x.private-keyparameters in a single command.Set the path to the CA certificate:
nmcli connection modify enp1s0 802-1x.ca-cert /etc/pki/tls/certs/ca.crt
# nmcli connection modify enp1s0 802-1x.ca-cert /etc/pki/tls/certs/ca.crtCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the identity of the user used in the certificate:
nmcli connection modify enp1s0 802-1x.identity user@example.com
# nmcli connection modify enp1s0 802-1x.identity user@example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Store the password in the configuration:
nmcli connection modify enp1s0 802-1x.private-key-password password
# nmcli connection modify enp1s0 802-1x.private-key-password passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantBy default, NetworkManager stores the password in clear text in the connection profile on the disk, but the file is readable only by the
rootuser. However, clear text passwords in a configuration file can be a security risk.To increase the security, set the
802-1x.password-flagsparameter toagent-owned. With this setting, on servers with the GNOME desktop environment or thenm-appletrunning, NetworkManager retrieves the password from these services, after you unlock the keyring. In other cases, NetworkManager prompts for the password.Activate the connection profile:
nmcli connection up enp1s0
# nmcli connection up enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
- Access resources on the network that require network authentication.
35.2. Configuring a static Ethernet connection with 802.1X network authentication by using nmstatectl
You can use the declarative Nmstate API to configure an Ethernet connection with 802.1X network authentication. Nmstate ensures that the result matches the configuration file or rolls back the changes.
The nmstate library only supports the TLS Extensible Authentication Protocol (EAP) method.
Prerequisites
- The network supports 802.1X network authentication.
- The managed node uses NetworkManager.
The following files required for TLS authentication exist on the client:
-
The client key stored is in the
/etc/pki/tls/private/client.keyfile, and the file is owned and only readable by therootuser. -
The client certificate is stored in the
/etc/pki/tls/certs/client.crtfile. -
The Certificate Authority (CA) certificate is stored in the
/etc/pki/tls/certs/ca.crtfile.
-
The client key stored is in the
Procedure
Create a YAML file, for example
~/create-ethernet-profile.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow These settings define an Ethernet connection profile for the
enp1s0device with the following settings:-
A static IPv4 address -
192.0.2.1with a/24subnet mask -
A static IPv6 address -
2001:db8:1::1with a/64subnet mask -
An IPv4 default gateway -
192.0.2.254 -
An IPv6 default gateway -
2001:db8:1::fffe -
An IPv4 DNS server -
192.0.2.200 -
An IPv6 DNS server -
2001:db8:1::ffbb -
A DNS search domain -
example.com -
802.1X network authentication using the
TLSEAP protocol
-
A static IPv4 address -
Apply the settings to the system:
nmstatectl apply ~/create-ethernet-profile.yml
# nmstatectl apply ~/create-ethernet-profile.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
- Access resources on the network that require network authentication.
35.3. Configuring a static Ethernet connection with 802.1X network authentication by using the network RHEL system role
By using the network RHEL system role, you can automate setting up Network Access Control (NAC) on remote hosts. You can define authentication details for clients in a playbook to ensure only authorized clients can access the network.
You can use an Ansible playbook to copy a private key, a certificate, and the CA certificate to the client, and then use the network RHEL system role to configure a connection profile with 802.1X network authentication.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. - The network supports 802.1X network authentication.
- The managed nodes use NetworkManager.
The following files required for the TLS authentication exist on the control node:
-
The client key is stored in the
/srv/data/client.keyfile. -
The client certificate is stored in the
/srv/data/client.crtfile. -
The Certificate Authority (CA) certificate is stored in the
/srv/data/ca.crtfile.
-
The client key is stored in the
Procedure
Store your sensitive variables in an encrypted file:
Create the vault:
ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>
$ ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
ansible-vault createcommand opens an editor, enter the sensitive data in the<key>: <value>format:pwd: <password>
pwd: <password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the changes, and close the editor. Ansible encrypts the data in the vault.
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
ieee802_1x- This variable contains the 802.1X-related settings.
eap: tls-
Configures the profile to use the certificate-based
TLSauthentication method for the Extensible Authentication Protocol (EAP).
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --ask-vault-pass --syntax-check ~/playbook.yml
$ ansible-playbook --ask-vault-pass --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook --ask-vault-pass ~/playbook.yml
$ ansible-playbook --ask-vault-pass ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
- Access resources on the network that require network authentication.
35.4. Configuring a wifi connection with 802.1X network authentication by using the network RHEL system role
By using the network RHEL system role, you can automate setting up Network Access Control (NAC) on remote hosts. You can define authentication details for clients in a playbook to ensure only authorized clients can access the network.
You can use an Ansible playbook to copy a private key, a certificate, and the CA certificate to the client, and then use the network RHEL system role to configure a connection profile with 802.1X network authentication.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. - The network supports 802.1X network authentication.
-
You installed the
wpa_supplicantpackage on the managed node. - DHCP is available in the network of the managed node.
The following files required for TLS authentication exist on the control node:
-
The client key is stored in the
/srv/data/client.keyfile. -
The client certificate is stored in the
/srv/data/client.crtfile. -
The CA certificate is stored in the
/srv/data/ca.crtfile.
-
The client key is stored in the
Procedure
Store your sensitive variables in an encrypted file:
Create the vault:
ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>
$ ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
ansible-vault createcommand opens an editor, enter the sensitive data in the<key>: <value>format:pwd: <password>
pwd: <password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the changes, and close the editor. Ansible encrypts the data in the vault.
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
ieee802_1x- This variable contains the 802.1X-related settings.
eap: tls-
Configures the profile to use the certificate-based
TLSauthentication method for the Extensible Authentication Protocol (EAP).
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.network/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --ask-vault-pass --syntax-check ~/playbook.yml
$ ansible-playbook --ask-vault-pass --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook --ask-vault-pass ~/playbook.yml
$ ansible-playbook --ask-vault-pass ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 37. Getting started with Multipath TCP
Multipath TCP (MPTCP) is an extension to the original TCP protocol (single-path). MPTCP enables a transport connection to operate across multiple paths simultaneously, and brings network connection redundancy to user endpoint devices.
37.1. Understanding MPTCP
The Multipath TCP (MPTCP) protocol provides simultaneous usage of multiple paths between connection endpoints. The protocol design improves connection stability and also brings other benefits compared to the single-path TCP.
In MPTCP terminology, links are considered as paths.
The following are some of the advantages of using MPTCP:
- It allows a connection to simultaneously use multiple network interfaces.
- In case a connection is bound to a link speed, the usage of multiple links can increase the connection throughput. Note, that in case of the connection is bound to a CPU, the usage of multiple links causes the connection slowdown.
- It increases the resilience to link failures.
37.2. Preparing RHEL to enable MPTCP support
By default the MPTCP support is disabled in RHEL. Enable MPTCP so that applications that support this feature can use it. Additionally, you have to configure user space applications to force use MPTCP sockets if those applications have TCP sockets by default.
Prerequisites
The following packages are installed:
-
iperf3 -
mptcpd -
systemtap
Procedure
Enable MPTCP sockets in the kernel:
echo "net.mptcp.enabled=1" > /etc/sysctl.d/90-enable-MPTCP.conf sysctl -p /etc/sysctl.d/90-enable-MPTCP.conf
# echo "net.mptcp.enabled=1" > /etc/sysctl.d/90-enable-MPTCP.conf # sysctl -p /etc/sysctl.d/90-enable-MPTCP.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the
iperf3server, and force it to create MPTCP sockets instead of TCP sockets:mptcpize run iperf3 -s Server listening on 5201
# mptcpize run iperf3 -s Server listening on 5201Copy to Clipboard Copied! Toggle word wrap Toggle overflow Connect the client to the server, and force it to create MPTCP sockets instead of TCP sockets:
mptcpize iperf3 -c 127.0.0.1 -t 3
# mptcpize iperf3 -c 127.0.0.1 -t 3Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the connection is established, verify the
ssoutput to see the subflow-specific status:ss -nti '( dport :5201 )' State Recv-Q Send-Q Local Address:Port Peer Address:Port Process ESTAB 0 0 127.0.0.1:41842 127.0.0.1:5201 cubic wscale:7,7 rto:205 rtt:4.455/8.878 ato:40 mss:21888 pmtu:65535 rcvmss:536 advmss:65483 cwnd:10 bytes_sent:141 bytes_acked:142 bytes_received:4 segs_out:8 segs_in:7 data_segs_out:3 data_segs_in:3 send 393050505bps lastsnd:2813 lastrcv:2772 lastack:2772 pacing_rate 785946640bps delivery_rate 10944000000bps delivered:4 busy:41ms rcv_space:43690 rcv_ssthresh:43690 minrtt:0.008 tcp-ulp-mptcp flags:Mmec token:0000(id:0)/2ff053ec(id:0) seq:3e2cbea12d7673d4 sfseq:3 ssnoff:ad3d00f4 maplen:2
# ss -nti '( dport :5201 )' State Recv-Q Send-Q Local Address:Port Peer Address:Port Process ESTAB 0 0 127.0.0.1:41842 127.0.0.1:5201 cubic wscale:7,7 rto:205 rtt:4.455/8.878 ato:40 mss:21888 pmtu:65535 rcvmss:536 advmss:65483 cwnd:10 bytes_sent:141 bytes_acked:142 bytes_received:4 segs_out:8 segs_in:7 data_segs_out:3 data_segs_in:3 send 393050505bps lastsnd:2813 lastrcv:2772 lastack:2772 pacing_rate 785946640bps delivery_rate 10944000000bps delivered:4 busy:41ms rcv_space:43690 rcv_ssthresh:43690 minrtt:0.008 tcp-ulp-mptcp flags:Mmec token:0000(id:0)/2ff053ec(id:0) seq:3e2cbea12d7673d4 sfseq:3 ssnoff:ad3d00f4 maplen:2Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify MPTCP counters:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
37.3. Using iproute2 to temporarily configure and enable multiple paths for MPTCP applications
Each MPTCP connection uses a single subflow similar to plain TCP. To get the MPTCP benefits, specify a higher limit for maximum number of subflows for each MPTCP connection. Then configure additional endpoints to create those subflows.
The configuration in this procedure will not persist after rebooting your machine.
Note that MPTCP does not yet support mixed IPv6 and IPv4 endpoints for the same socket. Use endpoints belonging to the same address family.
Prerequisites
-
The
mptcpdpackage is installed -
The
iperf3package is installed Server network interface settings:
-
enp4s0:
192.0.2.1/24 -
enp1s0:
198.51.100.1/24
-
enp4s0:
Client network interface settings:
-
enp4s0f0:
192.0.2.2/24 -
enp4s0f1:
198.51.100.2/24
-
enp4s0f0:
Procedure
Configure the client to accept up to 1 additional remote address, as provided by the server:
ip mptcp limits set add_addr_accepted 1
# ip mptcp limits set add_addr_accepted 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add IP address
198.51.100.1as a new MPTCP endpoint on the server:ip mptcp endpoint add 198.51.100.1 dev enp1s0 signal
# ip mptcp endpoint add 198.51.100.1 dev enp1s0 signalCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
signaloption ensures that theADD_ADDRpacket is sent after the three-way-handshake.Start the
iperf3server, and force it to create MPTCP sockets instead of TCP sockets:mptcpize run iperf3 -s Server listening on 5201
# mptcpize run iperf3 -s Server listening on 5201Copy to Clipboard Copied! Toggle word wrap Toggle overflow Connect the client to the server, and force it to create MPTCP sockets instead of TCP sockets:
mptcpize iperf3 -c 192.0.2.1 -t 3
# mptcpize iperf3 -c 192.0.2.1 -t 3Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify the connection is established:
ss -nti '( sport :5201 )'
# ss -nti '( sport :5201 )'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify the connection and IP address limit:
ip mptcp limit show
# ip mptcp limit showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify the newly added endpoint:
ip mptcp endpoint show
# ip mptcp endpoint showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify MPTCP counters by using the
nstat MPTcp*command on a server:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
37.4. Permanently configuring multiple paths for MPTCP applications
You can configure MultiPath TCP (MPTCP) by using the nmcli command to permanently establish multiple subflows between a source and destination system.
The subflows can use different resources, different routes to the destination, and even different networks. Such as Ethernet, cellular, wifi, and so on. As a result, you achieve combined connections, which increase network resilience and throughput.
The server uses the following network interfaces in our example:
-
enp4s0:
192.0.2.1/24 -
enp1s0:
198.51.100.1/24 -
enp7s0:
192.0.2.3/24
The client uses the following network interfaces in our example:
-
enp4s0f0:
192.0.2.2/24 -
enp4s0f1:
198.51.100.2/24 -
enp6s0:
192.0.2.5/24
Prerequisites
- You configured the default gateway on the relevant interfaces.
Procedure
Enable MPTCP sockets in the kernel:
echo "net.mptcp.enabled=1" > /etc/sysctl.d/90-enable-MPTCP.conf sysctl -p /etc/sysctl.d/90-enable-MPTCP.conf
# echo "net.mptcp.enabled=1" > /etc/sysctl.d/90-enable-MPTCP.conf # sysctl -p /etc/sysctl.d/90-enable-MPTCP.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: The RHEL kernel default for subflow limit is 2. If you require more:
Create the
/etc/systemd/system/set_mptcp_limit.servicefile with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The oneshot unit executes the
ip mptcp limits set subflows 3command after your network (network.target) is operational during every boot process.The
ip mptcp limits set subflows 3command sets the maximum number of additional subflows for each connection, so 4 in total. It is possible to add maximally 3 additional subflows.Enable the
set_mptcp_limitservice:systemctl enable --now set_mptcp_limit
# systemctl enable --now set_mptcp_limitCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Enable MPTCP on all connection profiles that you want to use for connection aggregation:
nmcli connection modify <profile_name> connection.mptcp-flags signal,subflow,also-without-default-route
# nmcli connection modify <profile_name> connection.mptcp-flags signal,subflow,also-without-default-routeCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
connection.mptcp-flagsparameter configures MPTCP endpoints and the IP address flags. If MPTCP is enabled in a NetworkManager connection profile, the setting will configure the IP addresses of the relevant network interface as MPTCP endpoints.By default, NetworkManager does not add MPTCP flags to IP addresses if there is no default gateway. If you want to bypass that check, you need to use the
also-without-default-routeflag.
Verification
Verify that you enabled the MPTCP kernel parameter:
sysctl net.mptcp.enabled net.mptcp.enabled = 1
# sysctl net.mptcp.enabled net.mptcp.enabled = 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that you set the subflow limit correctly, in case the default was not enough:
ip mptcp limit show add_addr_accepted 2 subflows 3
# ip mptcp limit show add_addr_accepted 2 subflows 3Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that you configured the per-address MPTCP setting correctly:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
37.5. Monitoring MPTCP sub-flows
Monitoring MPTCP (Multipath TCP) subflows is crucial for optimizing performance, ensuring reliability, and maintaining control over multi-path network communication.
The life cycle of a multipath TCP (MPTCP) socket can be complex: The main MPTCP socket is created, the MPTCP path is validated, one or more sub-flows are created and eventually removed. Finally, the MPTCP socket is terminated.
The MPTCP protocol allows monitoring MPTCP-specific events related to socket and sub-flow creation and deletion, using the ip utility provided by the iproute package. This utility uses the netlink interface to monitor MPTCP events.
This procedure demonstrates how to monitor MPTCP events. For that, it simulates a MPTCP server application, and a client connects to this service. The involved clients in this example use the following interfaces and IP addresses:
-
Server:
192.0.2.1 -
Client (Ethernet connection):
192.0.2.2 -
Client (WiFi connection):
192.0.2.3
To simplify this example, all interfaces are within the same subnet. This is not a requirement. However, it is important that routing has been configured correctly, and the client can reach the server via both interfaces.
Prerequisites
- A RHEL client with two network interfaces, such as a laptop with Ethernet and WiFi
- The client can connect to the server via both interfaces
- A RHEL server
- Both the client and the server run RHEL 9.0 or later
-
You installed the
mptcpdpackage on both the client and the server
Procedure
Set the per connection additional subflow limits to
1on both client and server:ip mptcp limits set add_addr_accepted 0 subflows 1
# ip mptcp limits set add_addr_accepted 0 subflows 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow On the server, to simulate a MPTCP server application, start
netcat(nc) in listen mode with enforced MPTCP sockets instead of TCP sockets:mptcpize run nc -l -k -p 12345
# mptcpize run nc -l -k -p 12345Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
-koption causes thatncdoes not close the listener after the first accepted connection. This is required to demonstrate the monitoring of sub-flows.On the client:
Identify the interface with the lowest metric:
ip -4 route 192.0.2.0/24 dev enp1s0 proto kernel scope link src 192.0.2.2 metric 100 192.0.2.0/24 dev wlp1s0 proto kernel scope link src 192.0.2.3 metric 600
# ip -4 route 192.0.2.0/24 dev enp1s0 proto kernel scope link src 192.0.2.2 metric 100 192.0.2.0/24 dev wlp1s0 proto kernel scope link src 192.0.2.3 metric 600Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
enp1s0interface has a lower metric thanwlp1s0. Therefore, RHEL usesenp1s0by default.On the first terminal, start the monitoring:
ip mptcp monitor
# ip mptcp monitorCopy to Clipboard Copied! Toggle word wrap Toggle overflow On the second terminal, start a MPTCP connection to the server:
mptcpize run nc 192.0.2.1 12345
# mptcpize run nc 192.0.2.1 12345Copy to Clipboard Copied! Toggle word wrap Toggle overflow RHEL uses the
enp1s0interface and its associated IP address as a source for this connection.On the monitoring terminal, the
ip mptcp monitorcommand now logs:[ CREATED] token=63c070d2 remid=0 locid=0 saddr4=192.0.2.2 daddr4=192.0.2.1 sport=36444 dport=12345
[ CREATED] token=63c070d2 remid=0 locid=0 saddr4=192.0.2.2 daddr4=192.0.2.1 sport=36444 dport=12345Copy to Clipboard Copied! Toggle word wrap Toggle overflow The token identifies the MPTCP socket as an unique ID, and later it enables you to correlate MPTCP events on the same socket.
On the terminal with the running
ncconnection to the server, press Enter. This first data packet fully establishes the connection. Note that, as long as no data has been sent, the connection is not established.On the monitoring terminal,
ip mptcp monitornow logs:[ ESTABLISHED] token=63c070d2 remid=0 locid=0 saddr4=192.0.2.2 daddr4=192.0.2.1 sport=36444 dport=12345
[ ESTABLISHED] token=63c070d2 remid=0 locid=0 saddr4=192.0.2.2 daddr4=192.0.2.1 sport=36444 dport=12345Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Display the connections to port
12345on the server:ss -taunp | grep ":12345" tcp ESTAB 0 0 192.0.2.2:36444 192.0.2.1:12345
# ss -taunp | grep ":12345" tcp ESTAB 0 0 192.0.2.2:36444 192.0.2.1:12345Copy to Clipboard Copied! Toggle word wrap Toggle overflow At this point, only one connection to the server has been established.
On a third terminal, create another endpoint:
ip mptcp endpoint add dev wlp1s0 192.0.2.3 subflow
# ip mptcp endpoint add dev wlp1s0 192.0.2.3 subflowCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command sets the name and IP address of the WiFi interface of the client in this command.
On the monitoring terminal,
ip mptcp monitornow logs:[SF_ESTABLISHED] token=63c070d2 remid=0 locid=2 saddr4=192.0.2.3 daddr4=192.0.2.1 sport=53345 dport=12345 backup=0 ifindex=3
[SF_ESTABLISHED] token=63c070d2 remid=0 locid=2 saddr4=192.0.2.3 daddr4=192.0.2.1 sport=53345 dport=12345 backup=0 ifindex=3Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
locidfield displays the local address ID of the new sub-flow and identifies this sub-flow even if the connection uses network address translation (NAT). Thesaddr4field matches the endpoint’s IP address from theip mptcp endpoint addcommand.Optional: Display the connections to port
12345on the server:ss -taunp | grep ":12345" tcp ESTAB 0 0 192.0.2.2:36444 192.0.2.1:12345 tcp ESTAB 0 0 192.0.2.3%wlp1s0:53345 192.0.2.1:12345
# ss -taunp | grep ":12345" tcp ESTAB 0 0 192.0.2.2:36444 192.0.2.1:12345 tcp ESTAB 0 0 192.0.2.3%wlp1s0:53345 192.0.2.1:12345Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command now displays two connections:
-
The connection with source address
192.0.2.2corresponds to the first MPTCP sub-flow that you established previously. -
The connection from the sub-flow over the
wlp1s0interface with source address192.0.2.3.
-
The connection with source address
On the third terminal, delete the endpoint:
ip mptcp endpoint delete id 2
# ip mptcp endpoint delete id 2Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the ID from the
locidfield from theip mptcp monitoroutput, or retrieve the endpoint ID using theip mptcp endpoint showcommand.On the monitoring terminal,
ip mptcp monitornow logs:[ SF_CLOSED] token=63c070d2 remid=0 locid=2 saddr4=192.0.2.3 daddr4=192.0.2.1 sport=53345 dport=12345 backup=0 ifindex=3
[ SF_CLOSED] token=63c070d2 remid=0 locid=2 saddr4=192.0.2.3 daddr4=192.0.2.1 sport=53345 dport=12345 backup=0 ifindex=3Copy to Clipboard Copied! Toggle word wrap Toggle overflow On the first terminal with the
ncclient, press Ctrl+C to terminate the session.On the monitoring terminal,
ip mptcp monitornow logs:[ CLOSED] token=63c070d2
[ CLOSED] token=63c070d2Copy to Clipboard Copied! Toggle word wrap Toggle overflow
37.6. Disabling Multipath TCP in the kernel
If you do not require MPTCP, you can explicitly disable the MPTCP option in the kernel.
Procedure
Disable the
mptcp.enabledoption.echo "net.mptcp.enabled=0" > /etc/sysctl.d/90-enable-MPTCP.conf sysctl -p /etc/sysctl.d/90-enable-MPTCP.conf
# echo "net.mptcp.enabled=0" > /etc/sysctl.d/90-enable-MPTCP.conf # sysctl -p /etc/sysctl.d/90-enable-MPTCP.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify whether the
mptcp.enabledis disabled in the kernel.sysctl -a | grep mptcp.enabled net.mptcp.enabled = 0
# sysctl -a | grep mptcp.enabled net.mptcp.enabled = 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 38. Managing the mptcpd service
This section describes the basic management of the mptcpd service. The mptcpd package provides the mptcpize tool, which switches on the mptcp protocol in the TCP environment.
38.1. Configuring mptcpd
The mptcpd service is a component of the mptcp protocol which provides an instrument to configure mptcp endpoints. The mptcpd service creates a subflow endpoint for each address by default. The endpoint list is updated dynamically according to IP addresses modification on the running host. The mptcpd service creates the list of endpoints automatically. It enables multiple paths as an alternative to using the ip utility.
Prerequisites
-
The
mptcpdpackage installed
Procedure
Enable
mptcp.enabledoption in the kernel with the following command:echo "net.mptcp.enabled=1" > /etc/sysctl.d/90-enable-MPTCP.conf sysctl -p /etc/sysctl.d/90-enable-MPTCP.conf
# echo "net.mptcp.enabled=1" > /etc/sysctl.d/90-enable-MPTCP.conf # sysctl -p /etc/sysctl.d/90-enable-MPTCP.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the
mptcpdservice:systemctl start mptcp.service
# systemctl start mptcp.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify endpoint creation:
ip mptcp endpoint
# ip mptcp endpointCopy to Clipboard Copied! Toggle word wrap Toggle overflow To stop the
mptcpdservice, use the following command:systemctl stop mptcp.service
# systemctl stop mptcp.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow To configure
mptcpdservice manually, modify the/etc/mptcpd/mptcpd.confconfiguration file.Note, that the endpoint, which mptcpd service creates, lasts till the host shutdown.
38.2. Managing applications with mptcpize tool
Using the mptcpize tool manage applications and services.
The instruction below shows how to use the mptcpize tool to manage applications in the TCP environment.
Assuming, you need to run the iperf3 utility with the enabled MPTCP socket. You can achieve this goal by following the procedure below.
Prerequisites
-
The
mptcpdpackage is installed -
The
iperf3package is installed
Procedure
Start
iperf3utility withMPTCPsockets enabled:mptcpize run iperf3 -s &
# mptcpize run iperf3 -s &Copy to Clipboard Copied! Toggle word wrap Toggle overflow
38.3. Enabling MPTCP sockets for a service by using the mptcpize utility
The following set of commands instruct you how to manage services using the mptcpize tool. You can enable or disable the mptcp socket for a service.
Assuming, you need to manage mptcp socket for the nginx service. You can achieve this goal by following the procedure below.
Prerequisites
-
The
mptcpdpackage is installed -
The
nginxpackage is installed
Procedure
Enable
MPTCPsockets for a service:mptcpize enable nginx
# mptcpize enable nginxCopy to Clipboard Copied! Toggle word wrap Toggle overflow Disable the
MPTCPsockets for a service:mptcpize disable nginx
# mptcpize disable nginxCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the service to make the changes to take effect:
systemctl restart nginx
# systemctl restart nginxCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 39. NetworkManager connection profiles in keyfile format
By default, NetworkManager in Red Hat Enterprise Linux 9 and later stores connection profiles in keyfile format. Unlike the deprecated ifcfg format, the keyfile format supports all connection settings that NetworkManager provides.
39.1. The keyfile format of NetworkManager profiles
The keyfile format is an INI-like configuration for network connections.
For example, the following is an Ethernet connection profile in keyfile format:
Typos or incorrect placements of parameters can lead to unexpected behavior. Therefore, do not manually edit or create NetworkManager profiles.
Use the nmcli utility, the network RHEL system role, or the nmstate API to manage NetworkManager connections. For example, you can use the nmcli utility in offline mode to create connection profiles.
Each section corresponds to a NetworkManager setting name as described in the nm-settings(5) man page. Each key-value-pair in a section is one of the properties listed in the settings specification of the man page.
Most variables in NetworkManager keyfiles have a one-to-one mapping. This means that a NetworkManager property is stored in the keyfile as a variable of the same name and in the same format. However, there are exceptions, mainly to make the keyfile syntax easier to read. For a list of these exceptions, see the nm-settings-keyfile(5) man page on your system.
For security reasons, because connection profiles can contain sensitive information, such as private keys and passphrases, NetworkManager uses only configuration files owned by the root user and that are only readable and writable by root.
Save the connection profile with a .nmconnection suffix in the /etc/NetworkManager/system-connections/ directory. This directory contains persistent profiles. If you modify a persistent profile by using the NetworkManager API, NetworkManager writes and overwrites files in this directory.
NetworkManager does not automatically reload profiles from disk. When you create or update a connection profile in keyfile format, use the nmcli connection reload command to inform NetworkManager about the changes.
39.2. Using nmcli to create keyfile connection profiles in offline mode
You can use the nmcli utility in offline mode to create and manage NetworkManager connection profiles. In this mode, nmcli operates without the NetworkManager service to produce keyfile connection profiles through standard output.
This feature can be useful in the following scenarios:
- You want to create your connection profiles that need to be pre-deployed somewhere. For example in a container image, or as an RPM package.
-
You want to create your connection profiles in an environment where the
NetworkManagerservice is not available, for example, when you want to use thechrootutility. Alternatively, when you want to create or modify the network configuration of the RHEL system to be installed through the Kickstart%postscript.
Procedure
Create a new connection profile in the keyfile format. For example, for a connection profile of an Ethernet device that does not use DHCP, run a similar
nmclicommand:nmcli --offline connection add type ethernet con-name Example-Connection ipv4.addresses 192.0.2.1/24 ipv4.dns 192.0.2.200 ipv4.method manual > /etc/NetworkManager/system-connections/example.nmconnection
# nmcli --offline connection add type ethernet con-name Example-Connection ipv4.addresses 192.0.2.1/24 ipv4.dns 192.0.2.200 ipv4.method manual > /etc/NetworkManager/system-connections/example.nmconnectionCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe connection name you specified with the
con-namekey is saved into theidvariable of the generated profile. When you use thenmclicommand to manage this connection later, specify the connection as follows:-
When the
idvariable is not omitted, use the connection name, for exampleExample-Connection. -
When the
idvariable is omitted, use the file name without the.nmconnectionsuffix, for exampleoutput.
-
When the
Set permissions to the configuration file so that only the
rootuser can read and update it:chmod 600 /etc/NetworkManager/system-connections/example.nmconnection chown root:root /etc/NetworkManager/system-connections/example.nmconnection
# chmod 600 /etc/NetworkManager/system-connections/example.nmconnection # chown root:root /etc/NetworkManager/system-connections/example.nmconnectionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the
NetworkManagerservice:systemctl start NetworkManager.service
# systemctl start NetworkManager.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you set the
autoconnectvariable in the profile tofalse, activate the connection:nmcli connection up Example-Connection
# nmcli connection up Example-ConnectionCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the
NetworkManagerservice is running:systemctl status NetworkManager.service ● NetworkManager.service - Network Manager Loaded: loaded (/usr/lib/systemd/system/NetworkManager.service; enabled; vendor preset: enabled) Active: active (running) since Wed 2022-08-03 13:08:32 CEST; 1min 40s ago ...
# systemctl status NetworkManager.service ● NetworkManager.service - Network Manager Loaded: loaded (/usr/lib/systemd/system/NetworkManager.service; enabled; vendor preset: enabled) Active: active (running) since Wed 2022-08-03 13:08:32 CEST; 1min 40s ago ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that NetworkManager can read the profile from the configuration file:
nmcli -f TYPE,FILENAME,NAME connection TYPE FILENAME NAME ethernet /etc/NetworkManager/system-connections/examaple.nmconnection Example-Connection ethernet /etc/sysconfig/network-scripts/ifcfg-enp1s0 enp1s0 ...
# nmcli -f TYPE,FILENAME,NAME connection TYPE FILENAME NAME ethernet /etc/NetworkManager/system-connections/examaple.nmconnection Example-Connection ethernet /etc/sysconfig/network-scripts/ifcfg-enp1s0 enp1s0 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the output does not show the newly created connection, verify that the keyfile permissions and the syntax you used are correct.
Display the connection profile:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
39.3. Manually creating a NetworkManager profile in keyfile format
You can manually create a NetworkManager connection profile in keyfile format. For example, this can be required if an external application generates the profiles.
Manually creating or updating the configuration files can result in an unexpected or non-functional network configuration. As an alternative, you can use nmcli in offline mode. See Using nmcli to create keyfile connection profiles in offline mode
Procedure
Create a connection profile. For example, for a connection profile for the
enp1s0Ethernet device that uses DHCP, create the/etc/NetworkManager/system-connections/example.nmconnectionfile with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou can use any file name with a
.nmconnectionsuffix. However, when you later usenmclicommands to manage the connection, you must use the connection name set in theidvariable when you refer to this connection. When you omit theidvariable, use the file name without the.nmconnectionto refer to this connection.Set permissions on the configuration file so that only the
rootuser can read and update it:chown root:root /etc/NetworkManager/system-connections/example.nmconnection chmod 600 /etc/NetworkManager/system-connections/example.nmconnection
# chown root:root /etc/NetworkManager/system-connections/example.nmconnection # chmod 600 /etc/NetworkManager/system-connections/example.nmconnectionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reload the connection profiles:
nmcli connection reload
# nmcli connection reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that NetworkManager read the profile from the configuration file:
nmcli -f NAME,UUID,FILENAME connection NAME UUID FILENAME Example-Connection 86da2486-068d-4d05-9ac7-957ec118afba /etc/NetworkManager/system-connections/example.nmconnection ...
# nmcli -f NAME,UUID,FILENAME connection NAME UUID FILENAME Example-Connection 86da2486-068d-4d05-9ac7-957ec118afba /etc/NetworkManager/system-connections/example.nmconnection ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the command does not show the newly added connection, verify that the file permissions and the syntax you used in the file are correct.
If you set the
autoconnectvariable in the profile tofalse, activate the connection:nmcli connection up example_connection
# nmcli connection up example_connectionCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the connection profile:
nmcli connection show example_connection
# nmcli connection show example_connectionCopy to Clipboard Copied! Toggle word wrap Toggle overflow
39.4. The differences in interface renaming with profiles in ifcfg and keyfile format
You can define custom network interface names, such as lan to make interface names more descriptive. In this case, the udev service renames the interfaces. The renaming process works differently depending on whether you use connection profiles in ifcfg or keyfile format.
- The interface renaming process when using a profile in
ifcfgformat -
The
udevrule file/usr/lib/udev/rules.d/60-net.rulescalls the/lib/udev/rename_devicehelper utility. -
The helper utility searches for the
HWADDRparameter in/etc/sysconfig/network-scripts/ifcfg-*files. -
If the value set in the variable matches the MAC address of an interface, the helper utility renames the interface to the name set in the
DEVICEparameter of the file.
-
The
- The interface renaming process when using a profile in keyfile format
- Create a systemd link file or a udev rule to rename an interface.
-
Use the custom interface name in the
interface-nameproperty of a NetworkManager connection profile.
39.5. Migrating NetworkManager profiles from ifcfg to keyfile format
If you still use connection profiles in the deprecated ifcfg format, you can convert them to the keyfile format.
If an ifcfg file contains the NM_CONTROLLED=no setting, NetworkManager does not control this profile and, consequently, the migration process ignores it.
Prerequisites
-
You have connection profiles in
ifcfgformat in the/etc/sysconfig/network-scripts/directory. -
If the connection profiles contain a
DEVICEvariable that is set to a custom device name, such asproviderorlan, you created a systemd link file or a udev rule for each of the custom device names.
Procedure
Migrate the connection profiles:
nmcli connection migrate Connection 'enp1s0' (43ed18ab-f0c4-4934-af3d-2b3333948e45) successfully migrated. Connection 'enp2s0' (883333e8-1b87-4947-8ceb-1f8812a80a9b) successfully migrated. ...
# nmcli connection migrate Connection 'enp1s0' (43ed18ab-f0c4-4934-af3d-2b3333948e45) successfully migrated. Connection 'enp2s0' (883333e8-1b87-4947-8ceb-1f8812a80a9b) successfully migrated. ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Optional: You can verify that you successfully migrated all your connection profiles:
nmcli -f TYPE,FILENAME,NAME connection TYPE FILENAME NAME ethernet /etc/NetworkManager/system-connections/enp1s0.nmconnection enp1s0 ethernet /etc/NetworkManager/system-connections/enp2s0.nmconnection enp2s0 ...
# nmcli -f TYPE,FILENAME,NAME connection TYPE FILENAME NAME ethernet /etc/NetworkManager/system-connections/enp1s0.nmconnection enp1s0 ethernet /etc/NetworkManager/system-connections/enp2s0.nmconnection enp2s0 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 40. Systemd network targets and services
RHEL uses the network and network-online targets and the NetworkManager-wait-online service while applying network settings. Configure systemd services to start after the network is fully available if those services cannot react dynamically to a change in the network state.
40.1. Differences between the network and network-online systemd target
The network target indicates that the network management stack has been started, and the network-online target is to actively wait until the network is up and a usable network connection is available.
Systemd maintains the network and network-online target units. The special units such as NetworkManager-wait-online.service, have WantedBy=network-online.target and Before=network-online.target parameters. If enabled, these units get started with network-online.target and delay the target to be reached until some form of network connectivity is established. They delay the network-online target until the network is connected.
The network-online target starts a service, which adds substantial delays to further execution. Systemd automatically adds dependencies with Wants and After parameters for this target unit to all the System V (SysV) init script service units with a Linux Standard Base (LSB) header referring to the $network facility. The LSB header is metadata for init scripts. You can use it to specify dependencies. This is similar to the systemd target.
The network target does not significantly delay the execution of the boot process. Reaching the network target means that the service that is responsible for setting up the network has started. However, it does not mean that a network device was configured. This target is important during the shutdown of the system. For example, if you have a service that was ordered after the network target during bootup, then this dependency is reversed during the shutdown. The network does not get disconnected until your service has been stopped. All mount units for remote network file systems automatically start the network-online target unit and order themselves after it.
The network-online target unit is only useful during the system startup. After the system has completed booting up, this target does not track the online state of the network. Therefore, you cannot use network-online to monitor the network connection. This target provides a one-time system startup concept.
40.2. Overview of NetworkManager-wait-online
The NetworkManager-wait-online service delays reaching the network-online target until NetworkManager reports that the startup is complete.
During boot, NetworkManager activates all profiles with the connection.autoconnect parameter set to yes. However, the activation of profiles is not complete as long as NetworkManager profiles are in an activating state. If activation fails, NetworkManager retries the activation depending on the value of the connection.autoconnect-retries.
When a device reaches the activated state depends on its configuration. For example, if a profile contains both IPv4 and IPv6 configuration, by default, NetworkManager considers the device as fully activated when only one of the Address families is ready. The ipv4.may-fail and ipv6.may-fail parameters in a connection profile control this behavior.
For Ethernet devices, NetworkManager waits for the carrier with a timeout. Consequently, if the Ethernet cable is not connected, this can further delay NetworkManager-wait-online.service.
When the startup completes, either all profiles are in a disconnected state or are successfully activated. You can configure profiles to auto-connect. The following are a few examples of parameters that set timeouts or define when the connection is considered active:
-
connection.wait-device-timeout: Sets the timeout for the driver to detect the device. -
ipv4.may-failandipv6.may-fail: Sets activation with one IP address family ready, or whether a particular address family must have completed configuration. -
ipv4.gateway-ping-timeout: Delays network activation until NetworkManager receives a ping response from the IPv4 gateway. The system waits up to the specified number of seconds before proceeding. -
ip-ping-timeoutandip-ping-addresses: Delays network activation until NetworkManager receives a ping response from the hosts defined inip-ping-addresses. The system waits up to the specified number of seconds before proceeding.
For further details, see the nm-settings(5), systemd.special(7), NetworkManager-wait-online.service(8) man pages on your system.
40.3. Configuring a systemd service to start after the network has been started
RHEL installs systemd service files in the /usr/lib/systemd/system/ directory. You can create a drop-in snippet in /etc/systemd/system/<service_name>.service.d/ to start a service after the network is online.
This snippet’s settings override any conflicting settings in the original service file.
Procedure
Open a service file in the editor:
systemctl edit <service_name>
# systemctl edit <service_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following, and save the changes:
[Unit] After=network-online.target
[Unit] After=network-online.targetCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reload the
systemdservice.systemctl daemon-reload
# systemctl daemon-reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 41. Introduction to Nmstate
Nmstate is a declarative network manager API. When you use Nmstate, you describe the expected networking state by using YAML or JSON-formatted instructions.
Nmstate has many benefits. For example, it:
- Provides a stable and extensible interface to manage RHEL network capabilities
- Supports atomic and transactional operations at the host and cluster level
- Supports partial editing of most properties and preserves existing settings that are not specified in the instructions
Nmstate consists of the following packages:
| Packages | Contents |
|---|---|
|
|
The |
|
|
The |
|
| The Nmstate C library |
|
| The Nmstate C library headers |
41.1. Using the libnmstate library in a Python application
The libnmstate Python library enables developers to use Nmstate in their own application.
To use the library, import it in your source code:
import libnmstate
import libnmstate
Note that you must install the nmstate and python3-libnmstate packages to use this library.
Example 41.1. Querying the network state by using the libnmstate library
The following Python code imports the libnmstate library and displays the available network interfaces and their state:
41.2. Updating the current network configuration by using nmstatectl
You can use the nmstatectl utility to store the current network configuration of one or all interfaces in a file.
You can then use this file to:
- Modify the configuration and apply it to the same system.
- Copy the file to a different host and configure the host with the same or modified settings.
For example, you can export the settings of the enp1s0 interface to a file, modify the configuration, and apply the settings to the host.
Prerequisites
-
The
nmstatepackage is installed.
Procedure
Export the settings of the
enp1s0interface to the~/network-config.ymlfile:nmstatectl show enp1s0 > ~/network-config.yml
# nmstatectl show enp1s0 > ~/network-config.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command stores the configuration of
enp1s0in YAML format. To store the output in JSON format, pass the--jsonoption to the command.If you do not specify an interface name,
nmstatectlexports the configuration of all interfaces.-
Modify the
~/network-config.ymlfile using a text editor to update the configuration. Apply the settings from the
~/network-config.ymlfile:nmstatectl apply ~/network-config.yml
# nmstatectl apply ~/network-config.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you exported the settings in JSON format, pass the
--jsonoption to the command.
41.3. The nmstate systemd service
With the nmstate package installed, you can automatically apply new network settings when the system boots by configuring the nmstate systemd service.
The nmstate service is a oneshot systemd service. Consequently, systemd executes it only when the system boots and when you manually restart the service.
By default, the nmstate service is disabled. Use the systemctl enable nmstate command to enable it. Afterwards, systemd executes this service each time when the system starts.
To use this service, store *.yml files with Nmstate instructions in the /etc/nmstate/ directory. The nmstate service then automatically applies the files on the next reboot or when you manually restart the service. By default, after Nmstate successfully applies a file, it renames the file’s .yml suffix to .applied to prevent the service from processing the same file again.
You can configure the nmstate service in the /etc/nmstate/nmstate.conf file. For example, to preserve the original *.yml file after it was applied and to create only a copy with the .applied suffix, add the following lines to /etc/nmstate/nmstate.conf:
[service] keep_state_file_after_apply = false
[service]
keep_state_file_after_apply = false
For further details and other configuration options, see the nmstate.service(8) man page on your system.
41.4. Network states for the network RHEL system role
The network RHEL system role supports state configurations in playbooks to configure the devices. For this, use the network_state variable followed by the state configurations.
Benefits of using the network_state variable in a playbook:
- Using the declarative method with the state configurations, you can configure interfaces, and the NetworkManager creates a profile for these interfaces in the background.
-
With the
network_statevariable, you can specify the options that you require to change, and all the other options will remain the same as they are. However, with thenetwork_connectionsvariable, you must specify all settings to change the network connection profile.
You can set only Nmstate YAML instructions in network_state. These instructions differ from the variables you can set in network_connections.
For example, to create an Ethernet connection with dynamic IP address settings, use the following vars block in your playbook:
| Playbook with state configurations | Regular playbook |
|
|
|
For example, to only change the connection status of dynamic IP address settings that you created as above, use the following vars block in your playbook:
| Playbook with state configurations | Regular playbook |
|
|
|
Chapter 42. Capturing network packets
To debug network issues and communications, you can capture network packets. The following sections provide instructions and additional information about capturing network packets.
42.1. Using xdpdump to capture network packets including packets dropped by XDP programs
The xdpdump utility captures network packets, including those dropped or modified by XDP programs. Unlike tcpdump, xdpdump uses an eBPF program, allowing it to capture packets that traditional user-space utilities cannot.
You can use xdpdump to debug XDP programs that are already attached to an interface. Therefore, the utility can capture packets before an XDP program is started and after it has finished. In the latter case, xdpdump also captures the XDP action. By default, xdpdump captures incoming packets at the entry of the XDP program.
On other architectures than AMD and Intel 64-bit, the xdpdump utility is provided as a Technology Preview only. Technology Preview features are not supported with Red Hat production Service Level Agreements (SLAs), might not be functionally complete, and Red Hat does not recommend using them for production. These previews provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
See Technology Preview Features Support Scope on the Red Hat Customer Portal for information about the support scope for Technology Preview features.
Note that xdpdump has no packet filter or decode capabilities. However, you can use it in combination with tcpdump for packet decoding.
If you are a developer and you are interested in the source code of xdpdump, download and install the corresponding source RPM (SRPM) from the Red Hat Customer Portal.
Prerequisites
- A network driver that supports XDP programs.
-
An XDP program is loaded to the
enp1s0interface. If no program is loaded,xdpdumpcaptures packets in a similar waytcpdumpdoes, for backward compatibility.
Procedure
To capture packets on the
enp1s0interface and write them to the/root/capture.pcapfile, enter:xdpdump -i enp1s0 -w /root/capture.pcap
# xdpdump -i enp1s0 -w /root/capture.pcapCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To stop capturing packets, press Ctrl+C.
Chapter 43. Understanding the eBPF networking features in RHEL 9
The extended Berkeley Packet Filter (eBPF) is an in-kernel virtual machine that allows code execution in the kernel space. This code runs in a restricted sandbox environment with access only to a limited set of functions.
In networking, you can use eBPF to complement or replace kernel packet processing. Depending on the hook you use, eBPF programs have, for example:
- Read and write access to packet data and metadata
- Can look up sockets and routes
- Can set socket options
- Can redirect packets
43.1. Overview of networking eBPF features in RHEL 9
The Extended Berkeley Packet Filter (eBPF) lets developers run sandboxed programs in the Linux kernel. For networking, eBPF programs attach to hooks to inspect, modify, and filter traffic.
You can attach extended Berkeley Packet Filter (eBPF) networking programs to the following hooks in RHEL:
- eXpress Data Path (XDP): Provides early access to received packets before the kernel networking stack processes them.
-
tceBPF classifier with a direct-action flag: Provides powerful packet processing on ingress and egress. Programs can be attached as an eBPF classifier with a direct-action flag in theqdischierarchy, or using the link-basedtcxAPI. - Control Groups version 2 (cgroup v2): Enables filtering and overriding socket-based operations performed by programs in a control group.
- Socket filtering: Enables filtering of packets received from sockets. This feature was also available in the classic Berkeley Packet Filter (cBPF), but has been extended to support eBPF programs.
- Stream parser: Enables splitting up streams to individual messages, filtering, and redirecting them to sockets.
-
SO_REUSEPORTsocket selection: Provides a programmable selection of a receiving socket from areuseportsocket group. - Flow dissector: Enables overriding the way the kernel parses packet headers in certain situations.
- TCP congestion control callbacks: Enables implementing a custom TCP congestion control algorithm.
Routes with encapsulation: Enables creating custom tunnel encapsulation.
- XDP
You can attach programs of the
BPF_PROG_TYPE_XDPtype to a network interface. The kernel then executes the program on received packets before the kernel network stack starts processing them. This allows fast packet forwarding in certain situations, such as fast packet dropping to prevent distributed denial of service (DDoS) attacks and fast packet redirects for load balancing scenarios.You can also use XDP for different forms of packet monitoring and sampling. The kernel allows XDP programs to modify packets and to pass them for further processing to the kernel network stack.
The following XDP modes are available:
- Native (driver) XDP: The kernel executes the program from the earliest possible point during packet reception. At this moment, the kernel did not parse the packet and, therefore, no metadata provided by the kernel is available. This mode requires that the network interface driver supports XDP but not all drivers support this native mode.
- Generic XDP: The kernel network stack executes the XDP program early in the processing. At that time, kernel data structures have been allocated, and the packet has been pre-processed. If a packet should be dropped or redirected, it requires a significant overhead compared to the native mode. However, the generic mode does not require network interface driver support and works with all network interfaces.
- Offloaded XDP: The kernel executes the XDP program on the network interface instead of on the host CPU. Note that this requires specific hardware, and only certain eBPF features are available in this mode.
On RHEL, load all XDP programs using the
libxdplibrary. This library enables system-controlled usage of XDP.NoteCurrently, there are some system configuration limitations for XDP programs. For example, you must disable certain hardware offload features on the receiving interface. Additionally, not all features are available with all drivers that support the native mode.
In RHEL 9, Red Hat supports the XDP features only if you use the
libxdplibrary to load the program into the kernel.- AF_XDP
-
Using an XDP program that filters and redirects packets to a given
AF_XDPsocket, you can use one or more sockets from theAF_XDPprotocol family to quickly copy packets from the kernel to the user space. - Traffic Control
The Traffic Control (
tc) subsystem offers the following types of eBPF programs:-
BPF_PROG_TYPE_SCHED_CLS -
BPF_PROG_TYPE_SCHED_ACT
These types enable you to write custom
tcclassifiers andtcactions in eBPF. Together with the parts of thetcecosystem, this provides the ability for powerful packet processing and is the core part of several container networking orchestration solutions.In most cases, only the classifier is used, as with the direct-action flag, the eBPF classifier can execute actions directly from the same eBPF program. The
clsactQueueing Discipline (qdisc) has been designed to enable this on the ingress side.Note that using a flow dissector eBPF program can influence operation of some other
qdiscsandtcclassifiers, such asflower.The link-based
tcxAPI is provided along with theqdiscAPI. It enables your applications to maintain ownership over a BPF program to prevent accidental removal of the BPF program. Also, thetcxAPI has multiprogram support that allows multiple applications to attach BPF programs in thetclayer in parallel.-
- Socket filter
Several utilities use or have used the classic Berkeley Packet Filter (cBPF) for filtering packets received on a socket. For example, the
tcpdumputility enables the user to specify expressions, whichtcpdumpthen translates into cBPF code.As an alternative to cBPF, the kernel allows eBPF programs of the
BPF_PROG_TYPE_SOCKET_FILTERtype for the same purpose.- Control Groups
In RHEL, you can use multiple types of eBPF programs that you can attach to a cgroup. The kernel executes these programs when a program in the given cgroup performs an operation. Note that you can use only cgroups version 2.
The following networking-related cgroup eBPF programs are available in RHEL:
-
BPF_PROG_TYPE_SOCK_OPS: The kernel calls this program on various TCP events. The program can adjust the behavior of the kernel TCP stack, including custom TCP header options, and so on. -
BPF_PROG_TYPE_CGROUP_SOCK_ADDR: The kernel calls this program duringconnect,bind,sendto,recvmsg,getpeername, andgetsocknameoperations. This program allows changing IP addresses and ports. This is useful when you implement socket-based network address translation (NAT) in eBPF. -
BPF_PROG_TYPE_CGROUP_SOCKOPT: The kernel calls this program duringsetsockoptandgetsockoptoperations and allows changing the options. -
BPF_PROG_TYPE_CGROUP_SOCK: The kernel calls this program during socket creation, socket releasing, and binding to addresses. You can use these programs to allow or deny the operation, or only to inspect socket creation for statistics. -
BPF_PROG_TYPE_CGROUP_SKB: This program filters individual packets on ingress and egress, and can accept or reject packets.
-
- Stream Parser
A stream parser operates on a group of sockets that are added to a special eBPF map. The eBPF program then processes packets that the kernel receives or sends on those sockets.
The following stream parser eBPF programs are available in RHEL:
-
BPF_PROG_TYPE_SK_SKB: An eBPF program parses packets received on the socket into individual messages, and instructs the kernel to drop those messages, accept them, or send them to another socket. -
BPF_PROG_TYPE_SK_MSG: This program filters egress messages. An eBPF program parses the packets and either approves or rejects them.
-
- SO_REUSEPORT socket selection
-
Using this socket option, you can bind multiple sockets to the same IP address and port. Without eBPF, the kernel selects the receiving socket based on a connection hash. With the
BPF_PROG_TYPE_SK_REUSEPORTprogram, the selection of the receiving socket is fully programmable. - Flow dissector
-
When the kernel needs to process packet headers without going through the full protocol decode, they are
dissected. For example, this happens in thetcsubsystem, in multipath routing, in bonding, or when calculating a packet hash. In this situation the kernel parses the packet headers and fills internal structures with the information from the packet headers. You can replace this internal parsing using theBPF_PROG_TYPE_FLOW_DISSECTORprogram. Note that you can only dissect TCP and UDP over IPv4 and IPv6 in eBPF in RHEL. - TCP Congestion Control
-
You can write a custom TCP congestion control algorithm using a group of
BPF_PROG_TYPE_STRUCT_OPSprograms that implementstruct tcp_congestion_oopscallbacks. An algorithm that is implemented this way is available to the system alongside the built-in kernel algorithms. - Routes with encapsulation
You can attach one of the following eBPF program types to routes in the routing table as a tunnel encapsulation attribute:
-
BPF_PROG_TYPE_LWT_IN -
BPF_PROG_TYPE_LWT_OUT -
BPF_PROG_TYPE_LWT_XMIT
The functionality of such an eBPF program is limited to specific tunnel configurations and does not allow creating a generic encapsulation or decapsulation solution.
-
- Socket lookup
-
To bypass limitations of the
bindsystem call, use an eBPF program of theBPF_PROG_TYPE_SK_LOOKUPtype. Such programs can select a listening socket for new incoming TCP connections or an unconnected socket for UDP packets.
43.2. Overview of XDP features in RHEL 9 by network cards
The XDP features available in RHEL depend on the network card and their drivers.
The following is an overview of XDP-enabled network cards and the XDP features you can use with them:
| Network card | Driver | Basic | Redirect | Target | HW offload | Zero-copy | Large MTU |
|---|---|---|---|---|---|---|---|
| Amazon Elastic Network Adapter |
| yes | yes | yes [a] | no | no | no |
| aQuantia AQtion Ethernet card |
| yes | yes | no | no | no | no |
| Broadcom NetXtreme-C/E 10/25/40/50 gigabit Ethernet |
| yes | yes | yes [a] | no | no | yes |
| Cavium Thunder Virtual function |
| yes | no | no | no | no | no |
| Google Virtual NIC (gVNIC) support |
| yes | yes | yes | no | yes | no |
| Intel® 10GbE PCI Express Virtual Function Ethernet |
| yes | no | no | no | no | no |
| Intel® 10GbE PCI Express adapters |
| yes | yes | yes [a] | no | yes | yes [b] |
| Intel® Ethernet Connection E800 Series |
| yes | yes | yes [a] | no | yes | yes |
| Intel® Ethernet Controller I225-LM/I225-V family |
| yes | yes | yes | no | yes | yes [b] |
| Intel® PCI Express Gigabit adapters |
| yes | yes | yes [a] | no | no | yes [b] |
| Intel® Ethernet Controller XL710 Family |
| yes | yes | no | yes | no | |
| Marvell OcteonTX2 |
| yes | yes | no | no | no | |
| Mellanox 5th generation network adapters (ConnectX series) |
| yes | yes | yes [c] | no | yes | yes |
| Mellanox Technologies 1/10/40Gbit Ethernet |
| yes | yes | no | no | no | no |
| Microsoft Azure Network Adapter |
| yes | yes | yes | no | no | no |
| Microsoft Hyper-V virtual network |
| yes | yes | yes | no | no | no |
| Netronome® NFP4000/NFP6000 NIC [d] |
| yes | no | no | yes | yes | no |
| QEMU Virtio network |
| yes | yes | yes [a] | no | no | yes |
| QLogic QED 25/40/100Gb Ethernet NIC |
| yes | yes | yes | no | no | no |
| STMicroelectronics Multi-Gigabit Ethernet |
| yes | yes | yes | no | yes | no |
| Solarflare SFC9000/SFC9100/EF100-family |
| yes | yes | yes [c] | no | no | no |
| Universal TUN/TAP device |
| yes | yes | yes | no | no | no |
| Virtual Ethernet pair device |
| yes | yes | yes | no | no | yes |
| VMware VMXNET3 ethernet driver |
| yes | yes | no | no | no | |
| Xen paravirtual network device |
| yes | yes | yes | no | no | no |
[a]
Only if an XDP program is loaded on the interface.
[b]
Transmitting side only. Cannot receive large packets through XDP.
[c]
Requires several XDP TX queues allocated that are larger or equal to the largest CPU index.
[d]
Some of the listed features are not available for the Netronome® NFP3800 NIC.
| |||||||
Legend:
-
Basic: Supports basic return codes:
DROP,PASS,ABORTED, andTX. -
Redirect: Supports the
XDP_REDIRECTreturn code. -
Target: Can be a target of a
XDP_REDIRECTreturn code. - HW offload: Supports XDP hardware offload.
-
Zero-copy: Supports the zero-copy mode for the
AF_XDPprotocol family. - Large MTU: Supports packets larger than page size.
Chapter 44. Network tracing using the BPF compiler collection
BPF Compiler Collection (BCC) is a library, which facilitates the creation of the extended Berkeley Packet Filter (eBPF) programs. The main utility of eBPF programs is analyzing the operating system performance and network performance without experiencing overhead or security issues.
BCC removes the need for users to know deep technical details of eBPF, and provides many out-of-the-box starting points, such as the bcc-tools package with pre-created eBPF programs.
The eBPF programs are triggered on events, such as disk I/O, TCP connections, and process creations. It is unlikely that the programs should cause the kernel to crash, loop or become unresponsive because they run in a safe virtual machine in the kernel.
44.1. Installing the bcc-tools package
Install the bcc-tools package, which also installs the BPF Compiler Collection (BCC) library as a dependency.
Procedure
Install
bcc-tools.dnf install bcc-tools
# dnf install bcc-toolsCopy to Clipboard Copied! Toggle word wrap Toggle overflow The BCC tools are installed in the
/usr/share/bcc/tools/directory.
Verification
Inspect the installed tools:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
docdirectory in the listing provides documentation for each tool.
44.2. Displaying TCP connections added to the Kernel’s accept queue
By using the tcpaccept utility, you can monitor newly accepted connections by tracing the kernel’s accept() function.
After the kernel receives the ACK packet in a TCP 3-way handshake, the kernel moves the connection from the SYN queue to the accept queue after the connection’s state changes to ESTABLISHED. Therefore, only successful TCP connections are visible in this queue.
The tcpaccept utility uses eBPF features to display all connections the kernel adds to the accept queue. The utility is lightweight because it traces the accept() function of the kernel instead of capturing packets and filtering them. For example, use tcpaccept for general troubleshooting to display new connections the server has accepted.
Procedure
Enter the following command to start the tracing the kernel
acceptqueue:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each time the kernel accepts a connection,
tcpacceptdisplays the details of the connections.- Press Ctrl+C to stop the tracing process.
44.3. Tracing outgoing TCP connection attempts
The tcpconnect utility uses eBPF features to trace outgoing TCP connection attempts. The output of the utility also includes connections that failed.
The tcpconnect utility is lightweight because it traces, for example, the connect() function of the kernel instead of capturing packets and filtering them.
Procedure
Enter the following command to start the tracing process that displays all outgoing connections:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each time the kernel processes an outgoing connection,
tcpconnectdisplays the details of the connections.- Press Ctrl+C to stop the tracing process.
44.4. Measuring the latency of outgoing TCP connections
The tcpconnlat utility uses eBPF features to measure the time between a sent SYN packet and the received response packet.
The TCP connection latency is the time taken to establish a connection. This typically involves the kernel TCP/IP processing and network round trip time, and not the application runtime.
Procedure
Start measuring the latency of outgoing connections:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each time the kernel processes an outgoing connection,
tcpconnlatdisplays the details of the connection after the kernel receives the response packet.- Press Ctrl+C to stop the tracing process.
44.5. Displaying details about TCP packets and segments that were dropped by the kernel
The tcpdrop utility enables administrators to display details about TCP packets and segments that were dropped by the kernel. Use this utility to debug high rates of dropped packets that can cause the remote system to send timer-based retransmits.
High rates of dropped packets and segments can impact the performance of a server. Instead of capturing and filtering packets, which is resource-intensive, the tcpdrop utility uses eBPF features to retrieve the information directly from the kernel.
Procedure
Enter the following command to start displaying details about dropped TCP packets and segments:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each time the kernel drops TCP packets and segments,
tcpdropdisplays the details of the connection, including the kernel stack trace that led to the dropped package.- Press Ctrl+C to stop the tracing process.
44.6. Tracing TCP sessions
The tcplife utility uses eBPF to trace TCP sessions that open and close, and prints a line of output to summarize each one. Administrators can use tcplife to identify connections and the amount of transferred traffic.
For example, you can display connections to port 22 (SSH) to retrieve the following information:
- The local process ID (PID)
- The local process name
- The local IP address and port number
- The remote IP address and port number
- The amount of received and transmitted traffic in KB.
- The time in milliseconds the connection was active
Procedure
Enter the following command to start the tracing of connections to the local port
22:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each time a connection is closed,
tcplifedisplays the details of the connections.- Press Ctrl+C to stop the tracing process.
44.7. Tracing TCP retransmissions
The tcpretrans utility displays details about TCP retransmissions, such as the local and remote IP address and port number, as well as the TCP state at the time of the retransmissions.
The utility uses eBPF features and, therefore, has a very low overhead.
Procedure
Use the following command to start displaying TCP retransmission details:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each time the kernel calls the TCP retransmit function,
tcpretransdisplays the details of the connection.- Press Ctrl+C to stop the tracing process.
44.8. Displaying TCP state change information
During a TCP session, the TCP state changes. The tcpstates utility uses eBPF functions to trace these state changes, and prints details including the duration in each state. For example, use tcpstates to identify if connections spend too much time in the initialization state.
Procedure
Use the following command to start tracing TCP state changes:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each time a connection changes its state,
tcpstatesdisplays a new line with updated connection details.If multiple connections change their state at the same time, use the socket address in the first column (
SKADDR) to determine which entries belong to the same connection.- Press Ctrl+C to stop the tracing process.
44.9. Summarizing and aggregating TCP traffic sent to specific subnets
The tcpsubnet utility summarizes and aggregates IPv4 TCP traffic that the local host sends to subnets and displays the output on a fixed interval. The utility uses eBPF features to collect and summarize the data to reduce the overhead.
By default, tcpsubnet summarizes traffic for the following subnets:
-
127.0.0.1/32 -
10.0.0.0/8 -
172.16.0.0/12 -
192.0.2.0/24/16 -
0.0.0.0/0
Note that the last subnet (0.0.0.0/0) is a catch-all option. The tcpsubnet utility counts all traffic for subnets different from the first four in this catch-all entry.
Follow the procedure to count the traffic for the 192.0.2.0/24 and 198.51.100.0/24 subnets. Traffic to other subnets will be tracked in the 0.0.0.0/0 catch-all subnet entry.
Procedure
Start monitoring the amount of traffic sent to the
192.0.2.0/24,198.51.100.0/24, and other subnets:Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command displays the traffic in bytes for the specified subnets once per second.
- Press Ctrl+C to stop the tracing process.
44.10. Displaying the network throughput by IP address and port
The tcptop utility displays TCP traffic the host sends and receives in kilobytes. The report automatically refreshes and contains only active TCP connections. The utility uses eBPF features and, therefore, has only a very low overhead.
Procedure
To monitor the sent and received traffic, enter:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output of the command includes only active TCP connections. If the local or remote system closes a connection, the connection is no longer visible in the output.
- Press Ctrl+C to stop the tracing process.
44.11. Tracing established TCP connections
The tcptracer utility traces the kernel functions that connect, accept, and close TCP connections. The utility uses eBPF features and, therefore, has a very low overhead.
Procedure
Use the following command to start the tracing process:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each time the kernel connects, accepts, or closes a connection,
tcptracerdisplays the details of the connections.- Press Ctrl+C to stop the tracing process.
44.12. Tracing IPv4 and IPv6 listen attempts
The solisten utility traces all IPv4 and IPv6 listen attempts. It traces the attempts including which ultimately fail or the listening program that does not accept the connection. The utility traces functions that the kernel calls when a program wants to listen for TCP connections.
Procedure
Enter the following command to start the tracing process that displays all listen TCP attempts:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Press Ctrl+C to stop the tracing process.
44.13. Summarizing the service time of soft interrupts
The softirqs utility summarizes the time spent servicing soft interrupts (soft IRQs) and shows this time as either totals or histogram distributions. This utility uses the irq:softirq_enter and irq:softirq_exit kernel tracepoints, which is a stable tracing mechanism.
Procedure
Enter the following command to start the tracing
soft irqevent time:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Press Ctrl+C to stop the tracing process.
44.14. Summarizing packets size and count on a network interface
The netqtop utility displays statistics about the attributes of received (RX) and transmitted (TX) packets on each network queue of a particular network interface.
The statistics include:
- Bytes per second (BPS)
- Packets per second (PPS)
- The average packet size
- Total number of packets
To generate these statistics, netqtop traces the kernel functions that perform events of transmitted packets net_dev_start_xmit and received packets netif_receive_skb.
Procedure
Display the number of packets within the range of bytes size of the time interval of
2seconds:Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Press Ctrl+C to stop
netqtop.
Chapter 45. Configuring network devices to accept traffic from all MAC addresses
Network devices usually intercept and read packets that their controller is programmed to receive. You can configure the network devices to accept traffic from all MAC addresses in a virtual switch or at the port group level.
You can use this network mode to:
- Diagnose network connectivity issues
- Monitor network activity for security reasons
- Intercept private data-in-transit or intrusion in the network
You can enable this mode for any kind of network device, except InfiniBand.
45.1. Temporarily configuring a device to accept all traffic
You can use the ip utility to temporarily configure a network device to accept all traffic regardless of the MAC addresses.
Procedure
Optional: Display the network interfaces to identify the one for which you want to receive all traffic:
ip address show 1: enp1s0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc fq_codel state DOWN group default qlen 1000 link/ether 98:fa:9b:a4:34:09 brd ff:ff:ff:ff:ff:ff ...# ip address show 1: enp1s0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc fq_codel state DOWN group default qlen 1000 link/ether 98:fa:9b:a4:34:09 brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Modify the device to enable or disable this property:
To enable the
accept-all-mac-addressesmode forenp1s0:ip link set enp1s0 promisc on
# ip link set enp1s0 promisc onCopy to Clipboard Copied! Toggle word wrap Toggle overflow To disable the
accept-all-mac-addressesmode forenp1s0:ip link set enp1s0 promisc off
# ip link set enp1s0 promisc offCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the
accept-all-mac-addressesmode is enabled:ip link show enp1s0 1: enp1s0: <NO-CARRIER,BROADCAST,MULTICAST,PROMISC,UP> mtu 1500 qdisc fq_codel state DOWN mode DEFAULT group default qlen 1000 link/ether 98:fa:9b:a4:34:09 brd ff:ff:ff:ff:ff:ff# ip link show enp1s0 1: enp1s0: <NO-CARRIER,BROADCAST,MULTICAST,PROMISC,UP> mtu 1500 qdisc fq_codel state DOWN mode DEFAULT group default qlen 1000 link/ether 98:fa:9b:a4:34:09 brd ff:ff:ff:ff:ff:ffCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
PROMISCflag in the device description indicates that the mode is enabled.
45.2. Permanently configuring a network device to accept all traffic using nmcli
You can use the nmcli utility to permanently configure a network device to accept all traffic regardless of the MAC addresses.
Procedure
Optional: Display the network interfaces to identify the one for which you want to receive all traffic:
ip address show 1: enp1s0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc fq_codel state DOWN group default qlen 1000 link/ether 98:fa:9b:a4:34:09 brd ff:ff:ff:ff:ff:ff ...# ip address show 1: enp1s0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc fq_codel state DOWN group default qlen 1000 link/ether 98:fa:9b:a4:34:09 brd ff:ff:ff:ff:ff:ff ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can create a new connection, if you do not have any.
Modify the network device to enable or disable this property.
To enable the
ethernet.accept-all-mac-addressesmode forenp1s0:nmcli connection modify enp1s0 ethernet.accept-all-mac-addresses yes
# nmcli connection modify enp1s0 ethernet.accept-all-mac-addresses yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow To disable the
accept-all-mac-addressesmode forenp1s0:nmcli connection modify enp1s0 ethernet.accept-all-mac-addresses no
# nmcli connection modify enp1s0 ethernet.accept-all-mac-addresses noCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Apply the changes, reactivate the connection:
nmcli connection up enp1s0
# nmcli connection up enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the
ethernet.accept-all-mac-addressesmode is enabled:nmcli connection show enp1s0 ... 802-3-ethernet.accept-all-mac-addresses:1 (true)
# nmcli connection show enp1s0 ... 802-3-ethernet.accept-all-mac-addresses:1 (true)Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
802-3-ethernet.accept-all-mac-addresses: trueindicates that the mode is enabled.
45.3. Permanently configuring a network device to accept all traffic using nmstatectl
Use the nmstatectl utility to configure a device to accept all traffic regardless of the MAC addresses through the Nmstate API. The Nmstate API ensures that, after setting the configuration, the result matches the configuration file. If anything fails, nmstatectl automatically rolls back the changes to avoid leaving the system in an incorrect state.
Prerequisites
-
The
nmstatepackage is installed. -
The
enp1s0.ymlfile that you used to configure the device is available.
Procedure
Edit the existing
enp1s0.ymlfile for theenp1s0connection and add the following content to it:Copy to Clipboard Copied! Toggle word wrap Toggle overflow These settings configure the
enp1s0device to accept all traffic.Apply the network settings:
nmstatectl apply ~/enp1s0.yml
# nmstatectl apply ~/enp1s0.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the
802-3-ethernet.accept-all-mac-addressesmode is enabled:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
802-3-ethernet.accept-all-mac-addresses: trueindicates that the mode is enabled.
Chapter 46. Mirroring a network interface by using nmcli
Network administrators can use port mirroring to replicate inbound and outbound network traffic being communicated from one network device to another. Mirroring traffic of an interface can be helpful in the following situations:
- To debug networking issues and tune the network flow
- To inspect and analyze the network traffic
- To detect an intrusion
Prerequisites
- A network interface to mirror the network traffic to.
Procedure
Add a network connection profile that you want to mirror the network traffic from:
nmcli connection add type ethernet ifname enp1s0 con-name enp1s0 autoconnect no
# nmcli connection add type ethernet ifname enp1s0 con-name enp1s0 autoconnect noCopy to Clipboard Copied! Toggle word wrap Toggle overflow Attach a
qdiscof typepriotoenp1s0for the egress (outgoing) traffic with the10:handle:nmcli connection modify enp1s0 +tc.qdisc "root prio handle 10:"
# nmcli connection modify enp1s0 +tc.qdisc "root prio handle 10:"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
qdiscset toprioattached without children allows attaching filters.Add a
qdiscfor the ingress traffic, with theffff:handle:nmcli connection modify enp1s0 +tc.qdisc "ingress handle ffff:"
# nmcli connection modify enp1s0 +tc.qdisc "ingress handle ffff:"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the following filters to match packets on the ingress and egress
qdiscs, and to mirror them toenp7s0:nmcli connection modify enp1s0 +tc.tfilter "parent ffff: matchall action mirred egress mirror dev enp7s0" nmcli connection modify enp1s0 +tc.tfilter "parent 10: matchall action mirred egress mirror dev enp7s0"
# nmcli connection modify enp1s0 +tc.tfilter "parent ffff: matchall action mirred egress mirror dev enp7s0" # nmcli connection modify enp1s0 +tc.tfilter "parent 10: matchall action mirred egress mirror dev enp7s0"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
matchallfilter matches all packets, and themirredaction redirects packets to destination.Activate the connection:
nmcli connection up enp1s0
# nmcli connection up enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Install the
tcpdumputility:dnf install tcpdump
# dnf install tcpdumpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the traffic mirrored on the target device (
enp7s0):tcpdump -i enp7s0
# tcpdump -i enp7s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 47. Using nmstate-autoconf to automatically configure the network state using LLDP
Network devices can use the Link Layer Discovery Protocol (LLDP) to advertise their identity, capabilities, and neighbors in a LAN. The nmstate-autoconf utility can use this information to automatically configure local network interfaces.
The nmstate-autoconf utility is provided as a Technology Preview only. Technology Preview features are not supported with Red Hat production Service Level Agreements (SLAs), might not be functionally complete, and Red Hat does not recommend using them for production. These previews provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
See Technology Preview Features Support Scope on the Red Hat Customer Portal for information about the support scope for Technology Preview features.
47.1. Using nmstate-autoconf to automatically configure network interfaces
The nmstate-autoconf utility uses LLDP to identify the Virtual Local Area Network (VLAN) settings of interfaces connected to a switch to configure local devices.
This procedure assumes the following scenario and that the switch broadcasts the VLAN settings using LLDP:
-
The
enp1s0andenp2s0interfaces of the RHEL server are connected to switch ports that are configured with VLAN ID100and VLAN nameprod-net. -
The
enp3s0interface of the RHEL server is connected to a switch port that is configured with VLAN ID200and VLAN namemgmt-net.
The nmstate-autoconf utility then uses this information to create the following interfaces on the server:
-
bond100- A bond interface withenp1s0andenp2s0as ports. -
prod-net- A VLAN interface on top ofbond100with VLAN ID100. -
mgmt-net- A VLAN interface on top ofenp3s0with VLAN ID200
If you connect multiple network interfaces to different switch ports for which LLDP broadcasts the same VLAN ID, nmstate-autoconf creates a bond with these interfaces and, additionally, configures the common VLAN ID on top of it.
Prerequisites
-
The
nmstatepackage is installed. - LLDP is enabled on the network switch.
- The Ethernet interfaces are up.
Procedure
Enable LLDP on the Ethernet interfaces:
Create a YAML file, for example
~/enable-lldp.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the settings to the system:
nmstatectl apply ~/enable-lldp.yml
# nmstatectl apply ~/enable-lldp.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Configure the network interfaces using LLDP:
Optional, start a dry-run to display and verify the YAML configuration that
nmstate-autoconfgenerates:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use
nmstate-autoconfto generate the configuration based on information received from LLDP, and apply the settings to the system:nmstate-autoconf enp1s0,enp2s0,enp3s0
# nmstate-autoconf enp1s0,enp2s0,enp3s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the settings of the individual interfaces:
nmstatectl show <interface_name>
# nmstatectl show <interface_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
If there is no DHCP server in your network that provides the IP settings to the interfaces, configure them manually. For details, see:
Chapter 48. Configuring 802.3 link settings
By using the auto-negotiation protocol, you have optimal performance of data transfer over the Ethernet.
Auto-negotiation is a feature of the IEEE 802.3u Fast Ethernet protocol. It targets the device ports to provide an optimal performance of speed, duplex mode, and flow control for information exchange over a link.
To utilize maximum performance of auto-negotiation, use the same configuration on both sides of a link.
48.1. Configuring 802.3 link settings using the nmcli utility
To configure the 802.3 link settings of an Ethernet connection, modify the following configuration parameters:
-
802-3-ethernet.auto-negotiate -
802-3-ethernet.speed -
802-3-ethernet.duplex
Procedure
Display the current settings of the connection:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can use these values if you need to reset the parameters in case of any problems.
Set the speed and duplex link settings:
nmcli connection modify Example-connection 802-3-ethernet.auto-negotiate yes 802-3-ethernet.speed 10000 802-3-ethernet.duplex full
# nmcli connection modify Example-connection 802-3-ethernet.auto-negotiate yes 802-3-ethernet.speed 10000 802-3-ethernet.duplex fullCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command enables auto-negotiation and sets the speed of the connection to
10000Mbit full duplex.Reactivate the connection:
nmcli connection up Example-connection
# nmcli connection up Example-connectionCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Use the
ethtoolutility to verify the values of Ethernet interfaceenp1s0:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 49. Getting started with DPDK
The data plane development kit (DPDK) provides libraries and network drivers to accelerate packet processing in user space.
Administrators use DPDK, for example, in virtual machines to use Single Root I/O Virtualization (SR-IOV) to reduce latencies and increase I/O throughput.
Red Hat does not support experimental DPDK APIs.
49.1. Installing the dpdk package
To use DPDK, install the dpdk package.
Procedure
Use the
dnfutility to install thedpdkpackage:dnf install dpdk
# dnf install dpdkCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 50. Getting started with TIPC
Transparent Inter-process Communication (TIPC), which is also known as Cluster Domain Sockets, is an Inter-process Communication (IPC) service for cluster-wide operation.
Applications that are running in a high-available and dynamic cluster environment have special needs. The number of nodes in a cluster can vary, routers can fail, and, due to load balancing considerations, functionality can be moved to different nodes in the cluster. TIPC minimizes the effort by application developers to deal with such situations, and maximizes the chance that they are handled in a correct and optimal way. Additionally, TIPC provides a more efficient and fault-tolerant communication than general protocols, such as TCP.
Use other bearer level protocols to encrypt the communication between nodes based on the transport media. For example:
+ * MACSec: See Using MACsec to encrypt layer 2 traffic * IPsec: See Configuring a VPN with IPsec
50.1. The architecture of TIPC
TIPC is a layer between applications using TIPC and a packet transport service (bearer), and spans the level of transport, network, and signaling link layers. However, TIPC can use a different transport protocol as bearer, so that, for example, a TCP connection can serve as a bearer for a TIPC signaling link.
TIPC supports the following bearers:
- Ethernet
- InfiniBand
- UDP protocol
TIPC provides a reliable transfer of messages between TIPC ports, that are the endpoints of all TIPC communication.
The following is a diagram of the TIPC architecture:
50.2. Loading the tipc module when the system boots
Before you can use the TIPC protocol, you must load the tipc kernel module. You can configure Red Hat Enterprise Linux to automatically load this kernel module automatically when the system boots.
Procedure
Create the
/etc/modules-load.d/tipc.conffile with the following content:tipc
tipcCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
systemd-modules-loadservice to load the module without rebooting the system:systemctl start systemd-modules-load
# systemctl start systemd-modules-loadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Use the following command to verify that RHEL loaded the
tipcmodule:lsmod | grep tipc tipc 311296 0
# lsmod | grep tipc tipc 311296 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the command shows no entry for the
tipcmodule, RHEL failed to load it.
50.3. Creating a TIPC network
To create a TIPC network, perform this procedure on each host that should join the TIPC network.
The commands configure the TIPC network only temporarily. To permanently configure TIPC on a node, use the commands of this procedure in a script, and configure RHEL to execute that script when the system boots.
Prerequisites
-
The
tipcmodule has been loaded. For details, see Loading the tipc module when the system boots
Procedure
Optional: Set a unique node identity, such as a UUID or the node’s host name:
tipc node set identity host_name
# tipc node set identity host_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow The identity can be any unique string consisting of a maximum 16 letters and numbers.
You cannot set or change an identity after this step.
Add a bearer. For example, to use Ethernet as media and
enp0s1device as physical bearer device, enter:tipc bearer enable media eth device enp1s0
# tipc bearer enable media eth device enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Optional: For redundancy and better performance, attach further bearers using the command from the previous step. You can configure up to three bearers, but not more than two on the same media.
- Repeat all previous steps on each node that should join the TIPC network.
Verification
Display the link status for cluster members:
tipc link list broadcast-link: up 5254006b74be:enp1s0-525400df55d1:enp1s0: up
# tipc link list broadcast-link: up 5254006b74be:enp1s0-525400df55d1:enp1s0: upCopy to Clipboard Copied! Toggle word wrap Toggle overflow This output indicates that the link between bearer
enp1s0on node5254006b74beand bearerenp1s0on node525400df55d1isup.Display the TIPC publishing table:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
The two entries with service type
0indicate that two nodes are members of this cluster. -
The entry with service type
1represents the built-in topology service tracking service. -
The entry with service type
2displays the link as seen from the issuing node. The range limit3741353223represents the peer endpoint’s address (a unique 32-bit hash value based on the node identity) in decimal format.
-
The two entries with service type
Chapter 51. Automatically configuring network interfaces in public clouds using nm-cloud-setup
Usually, a virtual machine (VM) has only one interface that is configurable by DHCP. However, DHCP cannot configure VMs with multiple network entities, such as interfaces, IP subnets, and IP addresses. Additionally, you cannot apply settings when the VM instance is running. To solve this runtime configuration issue, the nm-cloud-setup utility automatically retrieves configuration information from the metadata server of the cloud service provider and updates the network configuration of the host. The utility automatically picks up multiple network interfaces, multiple IP addresses, or IP subnets on one interface and helps to reconfigure the network of the running VM instance.
51.1. Configuring and pre-deploying nm-cloud-setup
To enable and configure network interfaces in public clouds, run nm-cloud-setup as a timer and service.
On Red Hat Enterprise Linux On Demand and AWS golden images, nm-cloud-setup is already enabled and no action is required.
Prerequisites
- A network connection exists.
The connection uses DHCP.
By default, NetworkManager creates a connection profile which uses DHCP. If no profile was created because you set the
no-auto-defaultparameter in/etc/NetworkManager/NetworkManager.conf, create this initial connection manually.
Procedure
Install the
nm-cloud-setuppackage:dnf install NetworkManager-cloud-setup
# dnf install NetworkManager-cloud-setupCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create and run the snap-in file for the
nm-cloud-setupservice:Use the following command to start editing the snap-in file:
systemctl edit nm-cloud-setup.service
# systemctl edit nm-cloud-setup.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow It is important to either start the service explicitly or reboot the system to make configuration settings effective.
Use the
systemdsnap-in file to configure the cloud provider innm-cloud-setup. For example, to use Amazon EC2, enter:[Service] Environment=NM_CLOUD_SETUP_EC2=yes
[Service] Environment=NM_CLOUD_SETUP_EC2=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can set the following environment variables to enable the cloud provide you use:
-
NM_CLOUD_SETUP_ALIYUNfor Alibaba Cloud (Aliyun) -
NM_CLOUD_SETUP_AZUREfor Microsoft Azure -
NM_CLOUD_SETUP_EC2for Amazon EC2 (AWS) -
NM_CLOUD_SETUP_GCPfor Google Cloud -
NM_CLOUD_SETUP_OCIfor Oracle Cloud Infrastructure (OCI)
-
- Save the file and quit the editor.
Reload the
systemdconfiguration:systemctl daemon-reload
# systemctl daemon-reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable and start the
nm-cloud-setupservice:systemctl enable --now nm-cloud-setup.service
# systemctl enable --now nm-cloud-setup.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable and start the
nm-cloud-setuptimer:systemctl enable --now nm-cloud-setup.timer
# systemctl enable --now nm-cloud-setup.timerCopy to Clipboard Copied! Toggle word wrap Toggle overflow
51.2. Understanding the role of IMDSv2 and nm-cloud-setup in the RHEL EC2 instance
The instance metadata service (IMDS) in Amazon EC2 allows you to manage permissions to access instance metadata of a running Red Hat Enterprise Linux (RHEL) EC2 instance. The RHEL EC2 instance uses IMDS version 2 (IMDSv2), a session-oriented method. By using the nm-cloud-setup utility, administrators can reconfigure the network and automatically update the configuration of running RHEL EC2 instances. The nm-cloud-setup utility handles IMDSv2 API calls by using IMDSv2 tokens without any user intervention.
-
IMDS runs on a link-local address
169.254.169.254for providing access to native applications on a RHEL EC2 instance. - After you have specified and configured IMDSv2 for each RHEL EC2 instance for applications and users, you can no longer access IMDSv1.
- By using IMDSv2, the RHEL EC2 instance maintains metadata without using the IAM role while remaining accessible through the IAM role.
-
When the RHEL EC2 instance boots, the
nm-cloud-setuputility automatically runs to fetch the EC2 instance API access token for using the RHEL EC2 instance API.
Use the IMDSv2 token as an HTTP header to check the details of the EC2 environment.