Installing and Operating Fuse Online on OpenShift Container Platform
Install, configure, and upgrade Fuse Online, and export/import integrations for CI/CD pipelines
Abstract
Preface
You can install and operate Fuse Online on-site on OpenShift Container Platform (OCP). When Fuse Online is running on-site, additional features are available beyond the features that are provided when Fuse Online is running on OpenShift Dedicated.
The term on-site means a customer-managed environment; Red Hat is not managing the OpenShift environment. A customer-managed environment can be on-premise, in the cloud, or in a hybrid cloud.
See the following topics for details:
- Chapter 1, Installing Fuse Online on OCP 4.x
- Chapter 2, Installing Fuse Online on OCP 3.11
- Chapter 3, Changing the configuration of a Fuse Online environment
- Chapter 4, Managing Fuse Online on OCP
- Chapter 5, How to invoke Fuse Online public REST API endpoints
- Chapter 6, Using external tools to export/import Fuse Online integrations for CI/CD
- Chapter 7, Fuse Online public REST API endpoints reference
- Chapter 8, Rebranding the Fuse Online user interface
Making open source more inclusive
Red Hat is committed to replacing problematic language in our code, documentation, and web properties. We are beginning with these four terms: master, slave, blacklist, and whitelist. Because of the enormity of this endeavor, these changes will be implemented gradually over several upcoming releases. For more details, see our CTO Chris Wright’s message.
Chapter 1. Installing Fuse Online on OCP 4.x
Fuse Online is a flexible and customizable, open source platform that provides core integration capabilities as a service.
Each installation of Fuse Online is referred to as a Fuse Online instance (or environment). In a given OpenShift project, there can be exactly one Fuse Online instance. Each Fuse Online instance has its own URL. In a single OpenShift cluster, there can be multiple Fuse Online instances.
You can install Fuse Online as an OpenShift developer user if you have the proper permissions to install operators from OperatorHub. You can install a default Fuse Online instance or a customized Fuse Online instance. For a customized Fuse Online instance, you must edit the default custom resource.
The Fuse Online installation process requires access to registry.redhat.io, which is the Red Hat Ecosystem Catalog for container images.
The following topics provide details for installing Fuse Online:
- Section 1.1, “Overview of the steps required to install Fuse Online on OCP 4.x”
- Section 1.1.1, “Considerations for installing Fuse Online in a restricted environment (OCP 4.6 and later)”
- Section 1.2, “When editing the default custom resource is required before installing Fuse Online”
- Section 1.3, “Descriptions of custom resource attributes that configure Fuse Online”
- Section 1.4, “About configuring Fuse Online for Jaeger monitoring”
- Section 1.6.1, “Authenticating with registry.redhat.io for container images”
- Section 1.6, “Installing Fuse Online”
1.1. Overview of the steps required to install Fuse Online on OCP 4.x
To install Fuse Online on OCP 4.x, here are the main steps:
- Generate an OpenShift secret that configures authentication to Red Hat container images.
- Install the Fuse Online Operator from the OperatorHub to a project (namespace) on the cluster.
- Optionally, if you want to include an external database for persisting connection and integration definitions, create an OpenShift secret.
Add a Fuse Online instance to an OpenShift 4.x project.
Optionally, edit the custom resource to enable one or more add-on features and/or implement one or more custom configuration settings.
- Optionally, grant permission to other developer users so that they can access the Fuse Online web console.
1.1.1. Considerations for installing Fuse Online in a restricted environment (OCP 4.6 and later)
Before you install Fuse Online in a restricted environment, you must complete the following tasks.
Prerequisite
- You have cluster admin access on the restricted environment’s OpenShift cluster.
Procedure
- Mirror all of the Fuse Online images to a location available on your private network. For more information about installing images for OpenShift operators in a restricted environment, see the Using Operator Lifecycle Manager on restricted networks section in the OpenShift documentation.
- Set up a custom Maven repository with the Fuse repository contents. For detailed information, see the Red Hat Solution: How to create an offline Maven repository for Fuse 7.
Before you install Fuse Online, edit the Fuse Online custom resource. Use the
maven:mirrorsetting to instruct Fuse Online to only look at the single specified Maven repository to access Maven artifacts when it builds integrations.In the following example, replace
https://customRepowith your offline repository’s URL:components: server: features: maven: mirror: https://customRepoSet the
HTTPS_PROXY,HTTP_PROXY, andNO_PROXYenvironment variables tosyndesis-oauthproxy. You can set these environment values when you install Fuse Online or afterwards.To set the environment values on
syndesis/appafter you install Fuse Online:Retrieve the values from proxy/cluster by using the following commands:
myhttpProxy=$(oc get proxy/cluster -ojsonpath='{.status.httpProxy}') myhttpsProxy=$(oc get proxy/cluster -ojsonpath='{.status.httpsProxy}') mynoProxy=$(oc get proxy/cluster -ojsonpath='{.status.noProxy}')Set the values by using the following oc patch command:
oc patch syndesis/app --type=merge -p "{\"spec\": {\"components\": {\"oauth\": {\"environment\": {\"HTTPS_PROXY\": \""${myhttpsProxy}"\", \"HTTP_PROXY\": \"${myhttpProxy}\", \"NO_PROXY\": \"${mynoProxy}\"}}}}}"This command returns the following confirmation:
syndesis.syndesis.io/app patched
Because you changed the
syndesis-oauthproxydeployment, OpenShift recreates thesyndesis-oauthproxy-1-deploypod.
-
By default, the
todosample application is disabled (in the Fuse Online custom resource, theaddon:todo:enabledvalue is set tofalse). Optionally, after you install Fuse Online in a restricted environment, you can download thetodosample application from https://github.com/syndesisio/todo-example and follow the steps in the Readme file, changing the repository URL to the location available on your private network.
1.2. When editing the default custom resource is required before installing Fuse Online
The Fuse Online installation includes a default custom resource, which specifies the default settings for configurable Fuse Online environment add-on features and parameter settings.
You need to edit the default custom resource before you install Fuse Online if you want the installed Fuse Online environment to:
- Use a URL that you specify for the OpenShift route by which the Fuse Online console can be reached. The default is that the installation process calculates this route.
- Use an external database to store connection and integration definitions. The default is that the environment uses an internal database.
-
Increase the amount of internal storage that is available for persisting connection and integration definitions. The default, which is
1Gi, is sufficient for most Fuse Online environments.
To configure a Fuse Online environment for any one of these behaviors, you MUST edit the custom resource when you install Fuse Online. In other words, you cannot change the configuration of an installed Fuse Online environment to implement any of these behaviors. Also, after you install a Fuse Online environment that is configured for any of these behaviors, you cannot change that behavior in the installed environment.
1.3. Descriptions of custom resource attributes that configure Fuse Online
In addition to the custom resource attributes that you can specify only before installation, there are a number of custom resource attributes that you can change before or after installation.
Table 1 provides a brief description of configurable custom resource settings and indicates when you can change them: before and/or after installation. To achieve the Fuse Online configuration that you want, use the information in this table to determine how you need to change the custom resource before installation or how you want to change it after installation. Then follow the appropriate procedure:
For OCP 4.x:
For OCP 3.11:
| Feature/Setting | When you can set this | Specification |
|---|---|---|
|
Enhanced activity tracking | Set only before installation |
Enhanced activity tracking is enabled, by default. If you want to customize the Jaeger configuration, you can set |
|
External database | Set only before installation |
|
|
Internal storage capacity for connections and integrations. | Set only before installation |
|
| OpenShift route for accessing Fuse Online console | Set only before installation |
|
|
Memory and CPU Each component defines its own memory requirement, which means that each pod has a limit on the amount of memory it is assigned. For information about limit and request settings, see the section on Configuring cluster memory to meet container memory and risk requirements in the OpenShift documentation.
You can also specify CPU resources for the
The
The
The | Set only before installation |
|
|
3scale discovery | Set before or after installation |
|
|
Backups | Set before or after installation |
|
|
Node affinity and tolerations Determines the placement of Fuse Online infrastructure component and integration pods onto nodes within the cluster. Node affinity allows you to specify an affinity for Fuse Online pods towards a group of nodes to be placed on. Tolerations allows you to control which nodes the Fuse Online pods run on and to prevent other workloads from using those nodes. See also: Configuring Fuse Online pods. | Set before or after installation |
Note: Use
|
|
Integration limit | Set before or after installation |
|
| Database connection pool You can adjust the server connection pool configuration to manage the connections to the database. Additional information about the database pool configuration follows this table. | Set before or after installation |
|
| Java Options
You can specify Java options for the
Depending on the Java option, you can specify different values for the components. For example, you can set a JVM-related parameter for | Set before or after installation |
Replace
Replace
For example, to configure the HTTP proxy: components:+ server: |
|
Maven Arguments | Set before or after installation |
|
|
Maven Mirror | Set before or after installation |
|
|
Maven Repositories | Set before or after installation |
|
|
Monitoring | Set before or after installation |
|
|
Public REST API | Set before or after installation |
|
|
ToDo addon | Set before or after installation |
See also Adding sample data to a Fuse Online environment running on OCP. |
| Auditing For viewing basic changes made to connectors, connections, and integrations. See also Auditing Fuse Fuse Online components. Note: This is a Technology Preview feature. | Set before or after installation |
|
About add-on features and configuration settings
Enhanced activity tracking
Activity tracking, using Jaeger, is enabled by default when you install Fuse Online. The Fuse Online installation (from the OperatorHub or the command-line script) detects the existence of the OperatorHub and installs Jaeger by using the OperatorHub’s subscription functionality. For the limited circumstances in which the OperatorHub is not available, Fuse Online uses its own installation functions to install Jaeger. Optionally, you can customize the Jaeger configuration before you install Fuse Online as described in the About configuring Fuse Online for Jaeger monitoring section.
External database for persisting connections and integrations
A default installation of Fuse Online provides an internal PostgreSQL database that Fuse Online uses to persist connection and integration definitions. You can choose to use an external PostgreSQL database instead, such as one of the PostgreSQL templates that OpenShift provides by default.
Internal storage capacity
The default setting of
1Giis sufficient for most Fuse Online environments. It is expected that you would increase this setting for a new Fuse Online installation only upon the recommendation of Red Hat technical support. That is, you have been running another Fuse Online environment in which you encountered Fuse Online server errors and Red Hat technical support determined that you need to install a new Fuse Online environment with a database volume capacity that is larger than the default.To increase Fuse Online internal storage capacity in an OpenShift project that is already running Fuse Online, you must first uninstall Fuse Online. See Uninstalling Fuse Online from an OCP project.
Database connection pool configuration
You can configure the following
syndesis-serverdatabase connection pool properties:-
connectionTimeout- The maximum number of milliseconds that thesyndesis-serverwaits for a connection from the pool. The lowest acceptable connection timeout is 250 ms. The default is 30000 (30 seconds). -
idleTimeout- The maximum amount of time (in milliseconds) that a connection is allowed to sit idle in the pool before the connection is removed. A value of 0 means that idle connections are never removed from the pool. The minimum allowed value is 10000 (10 seconds). The default is 600000 (10 minutes), -
leakDetectionThreshold- The amount of time (in milliseconds) that a connection can be out of the pool before a message is logged indicating a possible connection leak. A value of 0 means leak detection is disabled. The lowest acceptable value for enabling leak detection is 2000 (2 seconds). The default is 0. -
maxLifetime- The maximum lifetime (in milliseconds) of a connection in the pool. The minimum allowed value is 30000 (30 seconds). The default is 1800000 (30 minutes). -
maximumPoolSize- The maximum size that the pool is allowed to reach, including both idle and in-use connections. The default is 10. -
minimumIdle- The minimum number of idle connections maintained in the pool. The default is the value ofmaximumPoolSize.
-
1.4. About configuring Fuse Online for Jaeger monitoring
Jaeger is open source software for tracing transactions between distributed services. It is especially useful for monitoring and troubleshooting complex microservices environments.
When you install Fuse Online, either from the OperatorHub or by using the command-line script, the Fuse Online installation detects the existence of the OperatorHub and installs Jaeger by using the OperatorHub’s subscription functionality. For the limited circumstances in which the OperatorHub is not available, Fuse Online uses its own installation functions to install Jaeger.
A default Fuse Online environment configures all needed Jaeger components. Optionally, you can edit the Fuse Online custom resource to specify a client-only/independent server configuration or a hybrid Jaeger client and Jaeger Operator configuration.
Default Jaeger configuration
The basic, out-of-the-box, configuration includes all Jaeger components. You can start learning about how Jaeger works by experimenting with its monitoring capabilities. The default configuration provides a memory-only, limited, backend storage capability.
Installing Fuse Online with the default Jaeger configuration has the following results:
- Fuse Online components have Jaeger communication URLs.
- Jaeger Operator is installed.
- Jaeger custom resource is configured with a default configuration for activity monitoring.
A Fuse Online installation with the default Jaeger configuration, has the following syndesis custom resource specification:
apiVersion: syndesis.io/v1beta2
kind: Syndesis
metadata:
name: app
spec:
addons:
jaeger:
enabled: true
When the clientOnly and operatorOnly are unspecified (set to false, by default) Fuse Online uses the provided Jaeger backend as well as the default, memory-only storage provided by the Jaeger server configuration.
Client-only/independent server configuration
With a client-only/independent server configuration, only client URL connections are configured for communication between Fuse Online and an externally configured Jaeger backend. All aspects of the Jaeger backend are external and independent of the Fuse Online environment and syndesis-operator. This includes the Jaeger Operator and the Jaeger custom resource.
To install a client-only Jaeger configuration, edit the custom resource before you install Fuse Online as follows:
-
Set
clientOnlytotrueto add Jaeger agent capabilities. -
Set
queryUrito the URI of the query component of the independently installed Jaeger backend. -
Set
collectorUrito the URI of the collector component of the independently installed Jaeger backend.
For example:
apiVersion: syndesis.io/v1beta2
kind: Syndesis
metadata:
name: app
spec:
addons:
jaeger:
enabled: true
clientOnly: true
queryUri: https://jaeger-query-hostname:443/api
collectorUri: https://jaeger-collector-hostname:14268/api/tracesHybrid Jaeger client and operator configuration
With a hybrid Jaeger client and Jaeger Operator configuration, Fuse Online installs the Jaeger Operator as well as the Jaeger client capabilities. A Jaeger custom resource is not installed. You must install your own Jaeger custom resource, which defines your Jaeger server configuration. This lets you take advantage of the Fuse Online-provided capability and also tailor Jaeger configuration for your own environment, for example, you can use Elasticsearch or Cassandra for data storage.
To install a hybrid Jaeger client and Jaeger Operator configuration:
Edit the custom resource before you install Fuse Online as shown in the following example:
apiVersion: syndesis.io/v1beta2 kind: Syndesis metadata: name: app spec: addons: jaeger: enabled: true operatorOnly: trueName the Jaeger custom resource
syndesis-jaegeras shown in the following example:apiVersion: jaegertracing.io/v1 kind: Jaeger metadata: name: syndesis-jaeger ... spec: ....
Note: Alternately, if you want to use a different name for the Jaeger custom resource, set the
queryUriandcollectorUriin the Syndesis custom resource as described in the Client-only/independent server configuration section.
When the Jaeger custom resource with syndesis-jaeger name is created, the Jaeger instance collects data from the Fuse Online integrations. By default, you can view this data in the Fuse Online activity log.
1.5. Installing Fuse Online with an external database
If you want to install a Fuse Online environment that uses an external database to persist connection and integration definitions:
- Create a postgreSQL database with a hostname that the OpenShift cluster can locate.
-
Before you install Fuse Online, create an OpenShift secret named
syndesis-global-configfor the external database. - Install Fuse Online.
- Before you deploy Fuse Online, edit the custom resource to configure the connection to the external database.
Prerequisites
-
For OCP 3.11 only, you edited the
default-cr.ymlfile to specify the use of an external database to persist connection and integration definitions. - Fuse Online is not yet installed.
-
The
occlient tool is installed and it is connected to the OCP cluster in which you plan to install Fuse Online. - A user with cluster administration permissions gave you permission to install Fuse Online in any project that you have permission to access in the cluster.
Procedure
Log in to OpenShift with an account that has permission to install Fuse Online. For example:
oc login -u developer -p developer
Create a postgreSQL database that is available to the OpenShift cluster on which you install Fuse Online and that defines values for the following configuration options:
- Connection username
- Database name
Database password
The following example uses one of the PostgreSQL templates that OpenShift provides by default.
Note: Only use the PostgreSQL ephemeral (
postgresql-ephemeral) template for development or testing purposes. For a production environment, use the PostgreSQL (postgresql) template.oc new-app postgresql-ephemeral -p POSTGRESQL_USER=syndesis -p POSTGRESQL_PASSWORD=exdb-pwd -p POSTGRESQL_DATABASE=syndesisdb
This command returns information about the database that you need when you configure Fuse Online, such as the URL.
For information about creating a database see the PostgreSQL topic in the OpenShift documentation.
Create and save a resource file (for example,
my-fuse-online-secret-cr.yml) that contains the following content:apiVersion: v1 kind: Secret metadata: name: syndesis-global-config namespace: my-fuse-online-project type: Opaque stringData: POSTGRESQL_PASSWORD: exdb-pw
Replace
my-fuse-online-projectwith the name of the OpenShift project in which you plan to install the Fuse Online environment for which you are specifying an external database.Replace
exdb-pwwith the password from Step 2. Fuse Online will use it as the password for accessing the external database. Note thatstringDataconverts the password value to a base64-encoded value (so that you do not have to do the conversion).For information about OpenShift secrets, see Secrets.
Add the secret to the cluster, for example:
oc apply -f my-fuse-online-secret-cr.yml
On the OpenShift cluster, the
syndesis-global-configsecret is available to a Fuse Online environment that is installed with a custom resource that specifies an external database.Install Fuse Online in the
my-fuse-online-projectproject that you specified in theYAMLfile for the secret (in Step 4).- For OCP 3.11, follow the instructions in Editing the default custom resource file before installing Fuse Online.
For OCP 4.6 and later, follow the instructions in Installing the Fuse Online Operator from the OperatorHub. In Adding a Fuse Online instance to an OpenShift 4.x project, before you deploy Fuse Online, edit the custom resource to specify the use of an external database, for example:
apiVersion: syndesis.io/v1alpha1 kind: Syndesis metadata: name: app spec: components: database: externalDbURL: "postgresql://syndesis-external-db:5432" user: db-user-name name: db-name-
Replace
syndesis-external-db:5432with the host name and port for the external PostgreSQL database. -
Replace
db-user-namewith the Connection username. -
Replace
db-namewith the name of the database.
Result
The Fuse Online installation process uses the settings in the custom resource to determine the configuration of the installed Fuse Online environment.
When correctly installed and deployed, Fuse Online brings up all of the required pods except for syndesis-db. Instead of syndesis-db, the syndesis-server connects to the database with the service name of the external database. If the external database configuration is incorrect then the syndesis-server fails to initialize and the Fuse Online deployment ends with an error.
1.6. Installing Fuse Online
Fuse Online is a flexible and customizable, open source platform that provides core integration capabilities as a service. You can install Fuse Online as an OpenShift developer user if you have the proper permissions to install operators from OperatorHub.
Here are the general steps for installing Fuse Online by using the operator:
-
Create a secret in the OpenShift project (namespace) to configure authentication with
registry.redhat.ioso that the Fuse Online Operator can access the necessary installation templates. - Install the Fuse Online Operator to an OpenShift project (namespace). When the operator is installed, the operator is running in the selected namespace.
- Create an instance of Fuse Online from the installed operator. You can create an instance with default settings or you can customize the instance by editing the instance’s custom resource. You can then access Fuse Online from the provided URL.
The following topics provide details for installing Fuse Online on OCP 4.x by using the operator:
1.6.1. Authenticating with registry.redhat.io for container images
Configure authentication with registry.redhat.io before you can deploy Fuse container images on OpenShift.
Prerequisites
- Cluster administrator access to an OpenShift Container Platform cluster.
-
OpenShift
occlient tool is installed. For more details, see the OpenShift CLI documentation.
Procedure
Log into your OpenShift cluster as administrator:
oc login --user system:admin --token=my-token --server=https://my-cluster.example.com:6443
Open the project in which you want to deploy Fuse:
oc project myproject
Create a
docker-registrysecret using your Red Hat Customer Portal account, replacingPULL_SECRET_NAMEwith the secret to create:oc create secret docker-registry PULL_SECRET_NAME \ --docker-server=registry.redhat.io \ --docker-username=CUSTOMER_PORTAL_USERNAME \ --docker-password=CUSTOMER_PORTAL_PASSWORD \ --docker-email=EMAIL_ADDRESS
You should see the following output:
secret/PULL_SECRET_NAME created
ImportantYou must create this
docker-registrysecret in every OpenShift project namespace that will authenticate toregistry.redhat.io.Link the secret to your service account to use the secret for pulling images. The following example uses the
defaultservice account:oc secrets link default PULL_SECRET_NAME --for=pull
The service account name must match the name that the OpenShift pod uses.
Link the secret to the
builderservice account to use the secret for pushing and pulling build images:oc secrets link builder PULL_SECRET_NAME --for=pull,mount
NoteIf you do not want to use your Red Hat username and password to create the pull secret, you can create an authentication token using a registry service account.
Additional resources
For more details on authenticating with Red Hat for container images:
1.6.2. Installing the Fuse Online Operator from the OperatorHub
You can install the Fuse Online Operator from OperatorHub by using the OpenShift Container Platform web console. Follow these steps for each OpenShift project (namespace) in which you want to install Fuse Online.
Prerequisites
- You have administrator or developer access to the OpenShift cluster. For a developer user, you have proper permissions to install operators from OperatorHub.
-
You have configured authentication with
registry.redhat.ioas described in Authenticating withregistry.redhat.iofor container images. -
You installed the
occlient tool and it is connected to the OCP cluster on which you plan to install Fuse Online.
Procedure
- In a web browser, navigate to the OpenShift console in your browser and then log in to the console with your administrator or developer credentials.
-
If you are logged in as an administrator, click Operators and then click OperatorHub.
If you are logged in as a developer, click Add and then click the From Catalog card. - In the Filter by keyword field, type Fuse Online.
- Click the Red Hat Integration - Fuse Online card. The Fuse Online Operator install page opens.
Click Install. The Install Operator page opens.
- The Update Channel defines a stream of updates for the operator and is used to roll out updates for subscribers. Accept the default channel, 7.n where n is the current Fuse Online release number.
-
For Installation mode, select a namespace (project) from the list of namespaces on the cluster. Select the same namespace that you used when you created a docker registry secret in Authenticating with
registry.redhat.iofor container images. For the Update Approval, select Automatic or Manual to configure how OpenShift handles updates to the Fuse Online Operator.
- If you select Automatic updates, when a new version of the Fuse Online Operator is available, the OpenShift Operator Lifecycle Manager (OLM) automatically upgrades the running instance of the Fuse Online without human intervention.
- If you select Manual updates, when a newer version of an operator is available, the OLM creates an update request. A cluster administrator must then manually approve that update request to have the Fuse Online Operator updated to the new version.
- Click Install to make the Fuse Online Operator available in the specified namespace (project).
- To verify that Fuse Online is installed in the project, click Operators and then click Installed Operators to see Red Hat Integration - Fuse Online in the list.
In a Terminal window, type the following command to link the secret (that you created in Authenticating with
registry.redhat.iofor container images) to the Fuse Online Operator service account:oc secrets link syndesis-operator PULL_SECRET_NAME --for=pull
Next Steps
After the Fuse Online Operator is installed, you add an instance of Fuse Online to the OpenShift project.
1.6.3. Adding a Fuse Online instance to an OpenShift 4.x project
After the Fuse Online Operator is installed in an OpenShift 4.x project, you add an instance of Fuse Online to the OpenShift project. The Fuse Online instance provides the URL that a developer uses to access Fuse Online.
Prerequisites
- The Fuse Online Operator is installed into the current OpenShift project.
On your OCP environment, at least three persistent volumes are available for use by Fuse Online. All of the persistent volumes must have the following configuration requirements:
-
capacity.storage:
1Gi -
accessMode:
ReadWriteOnce
-
capacity.storage:
- Decide if you want to install a default Fuse Online instance or customized instance. For more information about the custom resource settings that you can specify, see When editing the default custom resource is required before installation.
Procedure
Follow these steps to access the Create Syndesis page depending on your user role:
If you are logged in as an administrator:
- Click Operators and then click Installed Operators.
- In the Name column, click Red Hat Integration - Fuse Online. The Operator Details page opens.
- Under Provided APIs, click Create Instance.
If you are logged in as a developer:
- Click Add and then click the Operator Backed card.
- Click the Syndesis CRD card. The Syndesis CRD page opens.
-
Click Create.
The Create Syndesis page opens.
- Enter a name or leave app as the default.
- Select the YAML view option to view the default custom resource.
Optional. Edit the custom resource.
For details on the custom resource settings that you can specify see When editing the default custom resource is required before installation and Descriptions of custom resource attributes that configure Fuse Online.
The Fuse Online installation process uses the settings that you specify in the custom resource to determine the configuration of the installed Fuse Online environment.
- Click Create to create the Fuse Online instance. OpenShift starts the pods, services, and other components for Fuse Online.
To obtain the URL for Fuse Online:
- Click Networking > Routes.
- Make sure that the correct project is selected.
- In the syndesis row, in the Location column, click the URL for Fuse Online.
- Use your OpenShift login credentials to login to the Fuse Online environment.
To allow other developer users access to the Fuse Online web console, an administrator must grant each developer user the
viewrole for the project in which Fuse Online is installed by using the following command:oc adm policy add-role-to-user view <username> -n <project-name>For example, to grant
viewpermission for themyfuseonlineproject to userjdoe:oc adm policy add-role-to-user view jdoe -n myfuseonline
Chapter 2. Installing Fuse Online on OCP 3.11
Installation of Fuse Online on OCP 3.11 requires a cluster administrator to register the Fuse Online custom resource definition and grant installation permission to the appropriate user(s). The user who installs Fuse Online must determine whether to install a default Fuse Online environment or a customized Fuse Online environment. For a customized Fuse Online environment, editing of the default custom resource file is required.
Each installation of Fuse Online is referred to as a Fuse Online environment. In a given OpenShift project, there can be exactly one Fuse Online environment. Each Fuse Online environment has its own URL. In a single OpenShift cluster, there can be multiple Fuse Online environments.
The Fuse Online installation process requires access to registry.redhat.io, which is the Red Hat Ecosystem Catalog for container images. Fuse Online does not support or test the use of external container registries, custom registries, or registries in disconnected environments.
The following topics provide details for installing Fuse Online:
- Section 2.1, “Overview of the steps required to install Fuse Online on OCP 3.11”
- Section 2.2, “Registering a custom resource definition for deploying Fuse Online resources”
- Section 2.3, “When editing the default custom resource is required before installing Fuse Online”
- Section 2.4, “Descriptions of custom resource attributes that configure Fuse Online”
- Section 2.5, “Editing the default custom resource file before installing Fuse Online”
- Section 2.6, “About configuring Fuse Online for Jaeger monitoring”
- Section 2.7, “Installing Fuse Online with an external database”
- Section 2.8, “Running the script that installs Fuse Online on OCP 3.11”
2.1. Overview of the steps required to install Fuse Online on OCP 3.11
To install Fuse Online on OCP on-site, a cluster administrator must perform some tasks and then a user who has permission to install Fuse Online in a particular OpenShift project performs some tasks and runs the installation script. The following diagram shows the workflow:
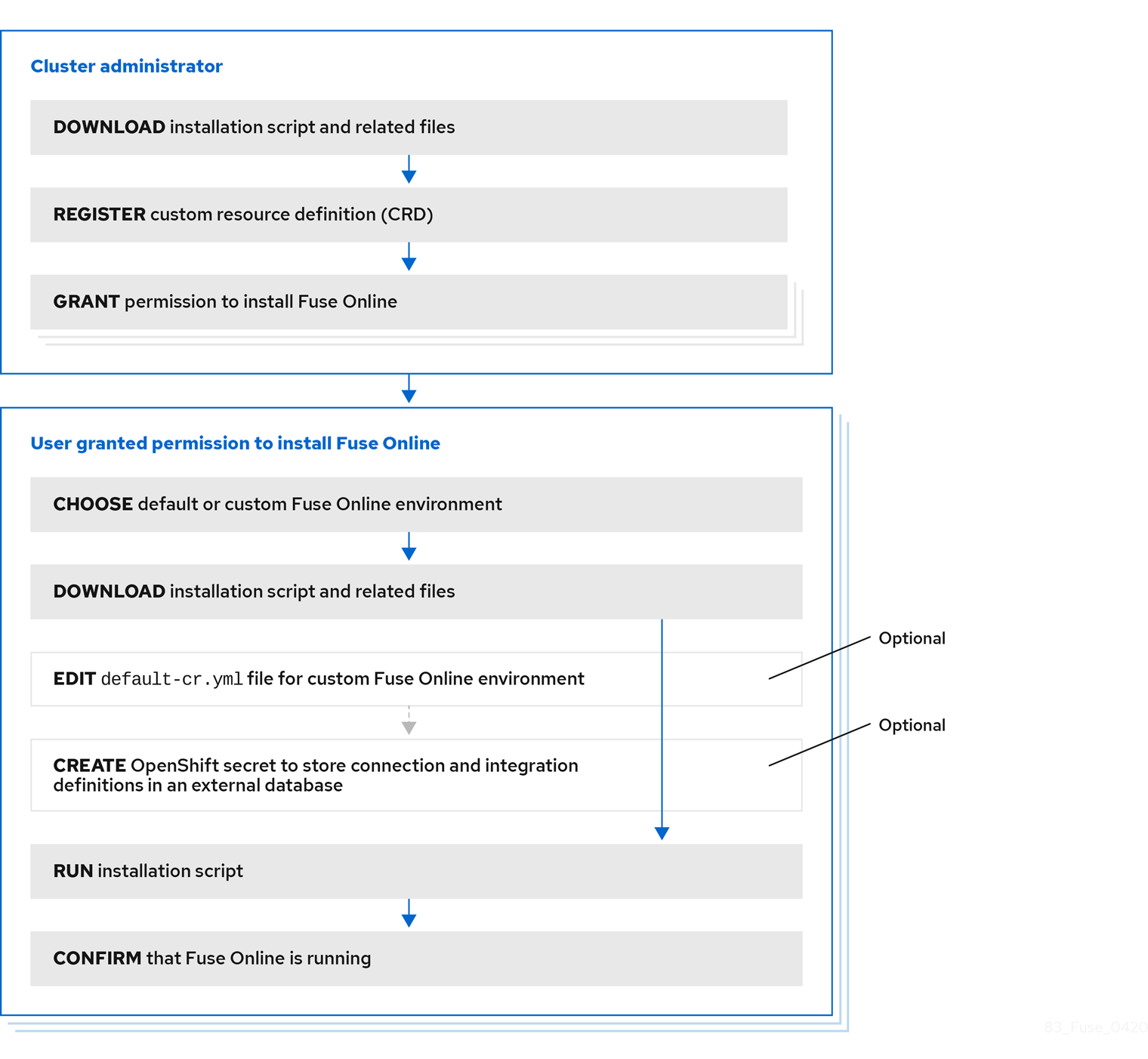
Outline for installing Fuse Online on OCP 3.11 workflow image
To install Fuse Online on OCP, the main steps are:
A user with cluster administration permissions:
- Downloads the installation script and related files.
-
Registers a custom resource definition (CRD) at the cluster level, by using OpenShift
occlient tool commands. -
Grants permission for one or more users to install Fuse Online in their projects, by using OpenShift
occlient tool commands.
For each OpenShift project in which you want to install Fuse Online, a user who is granted permission to install Fuse Online:
- Decides whether to install a default Fuse Online environment or a customized Fuse Online environment. A customized Fuse Online environment enables one or more add-on features and/or implements one or more custom configuration settings.
- Downloads the installation script and related files.
- Optional. Edits the default-cr.yml file (provided in the Fuse Online download package) if a customized Fuse Online environment is wanted.
- Optional. Creates an OpenShift secret if an external database for persisting connection and integration definitions is wanted.
- Invokes the installation script.
- Confirms that Fuse Online is running.
For each OpenShift project in which Fuse Online is to be installed, the cluster administrator must grant permission to a user to install Fuse Online in that particular project.
To install a default Fuse Online environment, the user with permission to install Fuse Online downloads and runs the installation script. No other steps are required.
Additional resource
2.2. Registering a custom resource definition for deploying Fuse Online resources
To enable installation of Fuse Online, a cluster administrator registers a custom resource definition. The administrator needs to do this only once for the OpenShift cluster. Then, for each project in which the administrator wants Fuse Online to be installed, the administrator grants an appropriate user permission to install Fuse Online in that project.
Prerequisites
- You must have cluster administration permissions.
-
You installed the
occlient tool and it is connected to the OCP cluster into which Fuse Online will be installed. On your OCP environment, at least three persistent volumes are available for use by Fuse Online. All of the persistent volumes must have the following configuration requirements:
-
capacity.storage:
1Gi -
accessMode:
ReadWriteOnce
-
capacity.storage:
Procedure
Download the package that contains the Fuse Online installation script from the following location:
https://github.com/syndesisio/fuse-online-install/releases/tag/1.13
-
Unpack the downloaded archive at a convenient location on your file system. The
fuse-online-install-1.13directory contains the script and supporting files for installing Fuse Online. Log in to OpenShift with an account that has cluster admin permissions. For example:
oc login -u admin -p adminpwdConfirm that you are properly connected by running the following command, which lists any custom resource definitions that are already registered in this cluster.
oc get crdYou are properly connected if there is no error message.
Register the custom resource definition at the cluster level by switching to the
fuse-online-install-1.13directory and invoking the following command:bash install_ocp.sh --setupConfirm that registration was successful by running the following command again:
oc get crdThe output list of registered custom resource definitions should include
syndesis.In each project in which you want Fuse Online to be installed, grant installation permission to a user. For each project:
Change to the project in which you want a user to be able to install Fuse Online. For example:
oc project fuse-online-projectGrant a user permission to install Fuse Online in that project. For example, the following command grants permission to install Fuse Online to
developeruser. After running this command, thedeveloperuser can install Fuse Online in the current project, which isfuse-online-projectin this example:bash install_ocp.sh --grant developerRepeat these two commands for each OpenShift project in which you want to grant permission for Fuse Online installation. A single user can install Fuse Online in more than one project in the cluster. To enable this, change to another project and specify the same user, for example:
oc project another-fuse-online-projectbash install_ocp.sh --grant developer
Result
The syndesis custom resource definition is registered in the cluster.
Next steps
Users with permission to install Fuse Online must decide whether to install a default Fuse Online environment or a customized Fuse Online environment.
2.3. When editing the default custom resource is required before installing Fuse Online
The Fuse Online installation includes a default custom resource, which specifies the default settings for configurable Fuse Online environment add-on features and parameter settings.
You need to edit the default custom resource before you install Fuse Online if you want the installed Fuse Online environment to:
- Use a URL that you specify for the OpenShift route by which the Fuse Online console can be reached. The default is that the installation process calculates this route.
- Use an external database to store connection and integration definitions. The default is that the environment uses an internal database.
-
Increase the amount of internal storage that is available for persisting connection and integration definitions. The default, which is
1Gi, is sufficient for most Fuse Online environments.
To configure a Fuse Online environment for any one of these behaviors, you MUST edit the custom resource when you install Fuse Online. In other words, you cannot change the configuration of an installed Fuse Online environment to implement any of these behaviors. Also, after you install a Fuse Online environment that is configured for any of these behaviors, you cannot change that behavior in the installed environment.
2.4. Descriptions of custom resource attributes that configure Fuse Online
In addition to the custom resource attributes that you can specify only before installation, there are a number of custom resource attributes that you can change before or after installation.
Table 1 provides a brief description of configurable custom resource settings and indicates when you can change them: before and/or after installation. To achieve the Fuse Online configuration that you want, use the information in this table to determine how you need to change the custom resource before installation or how you want to change it after installation. Then follow the appropriate procedure:
For OCP 4.x:
For OCP 3.11:
| Feature/Setting | When you can set this | Specification |
|---|---|---|
|
Enhanced activity tracking | Set only before installation |
Enhanced activity tracking is enabled, by default. If you want to customize the Jaeger configuration, you can set |
|
External database | Set only before installation |
|
|
Internal storage capacity for connections and integrations. | Set only before installation |
|
| OpenShift route for accessing Fuse Online console | Set only before installation |
|
|
Memory and CPU Each component defines its own memory requirement, which means that each pod has a limit on the amount of memory it is assigned. For information about limit and request settings, see the section on Configuring cluster memory to meet container memory and risk requirements in the OpenShift documentation.
You can also specify CPU resources for the
The
The
The | Set only before installation |
|
|
3scale discovery | Set before or after installation |
|
|
Backups | Set before or after installation |
|
|
Node affinity and tolerations Determines the placement of Fuse Online infrastructure component and integration pods onto nodes within the cluster. Node affinity allows you to specify an affinity for Fuse Online pods towards a group of nodes to be placed on. Tolerations allows you to control which nodes the Fuse Online pods run on and to prevent other workloads from using those nodes. See also: Configuring Fuse Online pods. | Set before or after installation |
Note: Use
|
|
Integration limit | Set before or after installation |
|
| Database connection pool You can adjust the server connection pool configuration to manage the connections to the database. Additional information about the database pool configuration follows this table. | Set before or after installation |
|
| Java Options
You can specify Java options for the
Depending on the Java option, you can specify different values for the components. For example, you can set a JVM-related parameter for | Set before or after installation |
Replace
Replace
For example, to configure the HTTP proxy: components:+ server: |
|
Maven Arguments | Set before or after installation |
|
|
Maven Mirror | Set before or after installation |
|
|
Maven Repositories | Set before or after installation |
|
|
Monitoring | Set before or after installation |
|
|
Public REST API | Set before or after installation |
|
|
ToDo addon | Set before or after installation |
See also Adding sample data to a Fuse Online environment running on OCP. |
| Auditing For viewing basic changes made to connectors, connections, and integrations. See also Auditing Fuse Fuse Online components. Note: This is a Technology Preview feature. | Set before or after installation |
|
About add-on features and configuration settings
Enhanced activity tracking
Activity tracking, using Jaeger, is enabled by default when you install Fuse Online. The Fuse Online installation (from the OperatorHub or the command-line script) detects the existence of the OperatorHub and installs Jaeger by using the OperatorHub’s subscription functionality. For the limited circumstances in which the OperatorHub is not available, Fuse Online uses its own installation functions to install Jaeger. Optionally, you can customize the Jaeger configuration before you install Fuse Online as described in the About configuring Fuse Online for Jaeger monitoring section.
External database for persisting connections and integrations
A default installation of Fuse Online provides an internal PostgreSQL database that Fuse Online uses to persist connection and integration definitions. You can choose to use an external PostgreSQL database instead, such as one of the PostgreSQL templates that OpenShift provides by default.
Internal storage capacity
The default setting of
1Giis sufficient for most Fuse Online environments. It is expected that you would increase this setting for a new Fuse Online installation only upon the recommendation of Red Hat technical support. That is, you have been running another Fuse Online environment in which you encountered Fuse Online server errors and Red Hat technical support determined that you need to install a new Fuse Online environment with a database volume capacity that is larger than the default.To increase Fuse Online internal storage capacity in an OpenShift project that is already running Fuse Online, you must first uninstall Fuse Online. See Uninstalling Fuse Online from an OCP project.
Database connection pool configuration
You can configure the following
syndesis-serverdatabase connection pool properties:-
connectionTimeout- The maximum number of milliseconds that thesyndesis-serverwaits for a connection from the pool. The lowest acceptable connection timeout is 250 ms. The default is 30000 (30 seconds). -
idleTimeout- The maximum amount of time (in milliseconds) that a connection is allowed to sit idle in the pool before the connection is removed. A value of 0 means that idle connections are never removed from the pool. The minimum allowed value is 10000 (10 seconds). The default is 600000 (10 minutes), -
leakDetectionThreshold- The amount of time (in milliseconds) that a connection can be out of the pool before a message is logged indicating a possible connection leak. A value of 0 means leak detection is disabled. The lowest acceptable value for enabling leak detection is 2000 (2 seconds). The default is 0. -
maxLifetime- The maximum lifetime (in milliseconds) of a connection in the pool. The minimum allowed value is 30000 (30 seconds). The default is 1800000 (30 minutes). -
maximumPoolSize- The maximum size that the pool is allowed to reach, including both idle and in-use connections. The default is 10. -
minimumIdle- The minimum number of idle connections maintained in the pool. The default is the value ofmaximumPoolSize.
-
2.5. Editing the default custom resource file before installing Fuse Online
To install a default Fuse Online environment, you do not need to edit the default custom resource file. See Installing Fuse Online on OCP 4.x or Installing Fuse Online on OCP 3.11.
To install a customized Fuse Online environment, you must edit the default-cr.yml file before you install Fuse Online. This file is in the Fuse Online download package. There are some custom resource settings that you can specify only before Fuse Online installation. See When editing the default custom resource is required before installation.
There are other custom resource settings that you can specify before or after Fuse Online installation. See Descriptions of custom resource attributes that configure Fuse Online.
The Fuse Online installation process uses the settings that you specify in the default-cr.yml file to create the syndesis custom resource. The syndesis custom resource settings determine the configuration of the installed Fuse Online environment.
Prerequisites
- You plan to install and run Fuse Online on OCP on-site.
-
The
occlient tool is installed and it is connected to the OCP cluster in which you plan to install Fuse Online - A user with cluster administration permissions gave you permission to install Fuse Online in any project that you have permission to access in the cluster.
Procedure
If you did not already download the package that contains the Fuse Online installation scripts:
Download it now from the following location:
https://github.com/syndesisio/fuse-online-install/releases/tag/1.13
-
Unpack the downloaded archive at a convenient location on your file system. The
fuse-online-install-1.13directory contains the scripts and supporting files for installing Fuse Online.
Log in to OpenShift with an account that has permission to install Fuse Online. For example:
oc login -u developer -p developer-
Open the
fuse-online-install-1.13/default-cr.ymlfile in an editor. -
Edit the
default-cr.ymlfile so that it enables the features and sets the parameters that you want. To determine what you need to specify, see Descriptions of custom resource attributes that configure Fuse Online. -
Save the
default-cr.ymlfile.
Result
The default-cr.yml file contains the configuration specifications for a new Fuse Online installation.
Next steps
If you edited the default-cr.yml file to specify an external database then follow the instructions in Installing Fuse Online with an external database before you install Fuse Online. Otherwise, you are ready to follow the instructions in Installing Fuse Online on OCP 3.11.
2.6. About configuring Fuse Online for Jaeger monitoring
Jaeger is open source software for tracing transactions between distributed services. It is especially useful for monitoring and troubleshooting complex microservices environments.
When you install Fuse Online, either from the OperatorHub or by using the command-line script, the Fuse Online installation detects the existence of the OperatorHub and installs Jaeger by using the OperatorHub’s subscription functionality. For the limited circumstances in which the OperatorHub is not available, Fuse Online uses its own installation functions to install Jaeger.
A default Fuse Online environment configures all needed Jaeger components. Optionally, you can edit the Fuse Online custom resource to specify a client-only/independent server configuration or a hybrid Jaeger client and Jaeger Operator configuration.
Default Jaeger configuration
The basic, out-of-the-box, configuration includes all Jaeger components. You can start learning about how Jaeger works by experimenting with its monitoring capabilities. The default configuration provides a memory-only, limited, backend storage capability.
Installing Fuse Online with the default Jaeger configuration has the following results:
- Fuse Online components have Jaeger communication URLs.
- Jaeger Operator is installed.
- Jaeger custom resource is configured with a default configuration for activity monitoring.
A Fuse Online installation with the default Jaeger configuration, has the following syndesis custom resource specification:
apiVersion: syndesis.io/v1beta2
kind: Syndesis
metadata:
name: app
spec:
addons:
jaeger:
enabled: true
When the clientOnly and operatorOnly are unspecified (set to false, by default) Fuse Online uses the provided Jaeger backend as well as the default, memory-only storage provided by the Jaeger server configuration.
Client-only/independent server configuration
With a client-only/independent server configuration, only client URL connections are configured for communication between Fuse Online and an externally configured Jaeger backend. All aspects of the Jaeger backend are external and independent of the Fuse Online environment and syndesis-operator. This includes the Jaeger Operator and the Jaeger custom resource.
To install a client-only Jaeger configuration, edit the custom resource before you install Fuse Online as follows:
-
Set
clientOnlytotrueto add Jaeger agent capabilities. -
Set
queryUrito the URI of the query component of the independently installed Jaeger backend. -
Set
collectorUrito the URI of the collector component of the independently installed Jaeger backend.
For example:
apiVersion: syndesis.io/v1beta2
kind: Syndesis
metadata:
name: app
spec:
addons:
jaeger:
enabled: true
clientOnly: true
queryUri: https://jaeger-query-hostname:443/api
collectorUri: https://jaeger-collector-hostname:14268/api/tracesHybrid Jaeger client and operator configuration
With a hybrid Jaeger client and Jaeger Operator configuration, Fuse Online installs the Jaeger Operator as well as the Jaeger client capabilities. A Jaeger custom resource is not installed. You must install your own Jaeger custom resource, which defines your Jaeger server configuration. This lets you take advantage of the Fuse Online-provided capability and also tailor Jaeger configuration for your own environment, for example, you can use Elasticsearch or Cassandra for data storage.
To install a hybrid Jaeger client and Jaeger Operator configuration:
Edit the custom resource before you install Fuse Online as shown in the following example:
apiVersion: syndesis.io/v1beta2 kind: Syndesis metadata: name: app spec: addons: jaeger: enabled: true operatorOnly: trueName the Jaeger custom resource
syndesis-jaegeras shown in the following example:apiVersion: jaegertracing.io/v1 kind: Jaeger metadata: name: syndesis-jaeger ... spec: ....
Note: Alternately, if you want to use a different name for the Jaeger custom resource, set the
queryUriandcollectorUriin the Syndesis custom resource as described in the Client-only/independent server configuration section.
When the Jaeger custom resource with syndesis-jaeger name is created, the Jaeger instance collects data from the Fuse Online integrations. By default, you can view this data in the Fuse Online activity log.
2.7. Installing Fuse Online with an external database
If you want to install a Fuse Online environment that uses an external database to persist connection and integration definitions:
- Create a postgreSQL database with a hostname that the OpenShift cluster can locate.
-
Before you install Fuse Online, create an OpenShift secret named
syndesis-global-configfor the external database. - Install Fuse Online.
- Before you deploy Fuse Online, edit the custom resource to configure the connection to the external database.
Prerequisites
-
For OCP 3.11 only, you edited the
default-cr.ymlfile to specify the use of an external database to persist connection and integration definitions. - Fuse Online is not yet installed.
-
The
occlient tool is installed and it is connected to the OCP cluster in which you plan to install Fuse Online. - A user with cluster administration permissions gave you permission to install Fuse Online in any project that you have permission to access in the cluster.
Procedure
Log in to OpenShift with an account that has permission to install Fuse Online. For example:
oc login -u developer -p developer
Create a postgreSQL database that is available to the OpenShift cluster on which you install Fuse Online and that defines values for the following configuration options:
- Connection username
- Database name
Database password
The following example uses one of the PostgreSQL templates that OpenShift provides by default.
Note: Only use the PostgreSQL ephemeral (
postgresql-ephemeral) template for development or testing purposes. For a production environment, use the PostgreSQL (postgresql) template.oc new-app postgresql-ephemeral -p POSTGRESQL_USER=syndesis -p POSTGRESQL_PASSWORD=exdb-pwd -p POSTGRESQL_DATABASE=syndesisdb
This command returns information about the database that you need when you configure Fuse Online, such as the URL.
For information about creating a database see the PostgreSQL topic in the OpenShift documentation.
Create and save a resource file (for example,
my-fuse-online-secret-cr.yml) that contains the following content:apiVersion: v1 kind: Secret metadata: name: syndesis-global-config namespace: my-fuse-online-project type: Opaque stringData: POSTGRESQL_PASSWORD: exdb-pw
Replace
my-fuse-online-projectwith the name of the OpenShift project in which you plan to install the Fuse Online environment for which you are specifying an external database.Replace
exdb-pwwith the password from Step 2. Fuse Online will use it as the password for accessing the external database. Note thatstringDataconverts the password value to a base64-encoded value (so that you do not have to do the conversion).For information about OpenShift secrets, see Secrets.
Add the secret to the cluster, for example:
oc apply -f my-fuse-online-secret-cr.yml
On the OpenShift cluster, the
syndesis-global-configsecret is available to a Fuse Online environment that is installed with a custom resource that specifies an external database.Install Fuse Online in the
my-fuse-online-projectproject that you specified in theYAMLfile for the secret (in Step 4).- For OCP 3.11, follow the instructions in Editing the default custom resource file before installing Fuse Online.
For OCP 4.6 and later, follow the instructions in Installing the Fuse Online Operator from the OperatorHub. In Adding a Fuse Online instance to an OpenShift 4.x project, before you deploy Fuse Online, edit the custom resource to specify the use of an external database, for example:
apiVersion: syndesis.io/v1alpha1 kind: Syndesis metadata: name: app spec: components: database: externalDbURL: "postgresql://syndesis-external-db:5432" user: db-user-name name: db-name-
Replace
syndesis-external-db:5432with the host name and port for the external PostgreSQL database. -
Replace
db-user-namewith the Connection username. -
Replace
db-namewith the name of the database.
Result
The Fuse Online installation process uses the settings in the custom resource to determine the configuration of the installed Fuse Online environment.
When correctly installed and deployed, Fuse Online brings up all of the required pods except for syndesis-db. Instead of syndesis-db, the syndesis-server connects to the database with the service name of the external database. If the external database configuration is incorrect then the syndesis-server fails to initialize and the Fuse Online deployment ends with an error.
2.8. Running the script that installs Fuse Online on OCP 3.11
The Fuse Online installation script installs a Fuse Online environment according to the specifications in the default-cr.yml file, which is in the Fuse Online download package. To install a default environment, no editing of that file is required. To install a customized environment, you must edit the default-cr.yml file before you run the installation script.
Prerequisites
- OCP is running on-site.
-
The
occlient tool is installed and connected to the OCP cluster in which you want to install Fuse Online. - A user with cluster administration permissions gave you permission to install Fuse Online in the project in which you plan to install Fuse Online.
-
If you determined that you needed to edit the
default-cr.ymlfile before installation, you completed those edits. (When editing the default custom resource file is required before installing Fuse Online) -
If the edited
default-cr.ymfile specifies an external database for persisting connection and integration definitions, you created an Openshift secret for accessing the external database. (Installing Fuse Online with an external database) -
You have a Red Hat developer account for which you know your user name and password. The installation script prompts you for these credentials so it can authenticate you against
https://developers.redhat.com. For details about creating an account, see Accessing and Configuring the Red Hat Registry.
Procedure
If you did not already download the package that contains the Fuse Online installation scripts:
Download it from the following location:
https://github.com/syndesisio/fuse-online-install/releases/tag/1.13
-
Unpack the downloaded archive at a convenient location on your file system. The
fuse-online-install-1.13directory contains the scripts and supporting files for installing Fuse Online.
Log in to OpenShift with an account that has permission to install Fuse Online. For example:
oc login -u developer -p developerSwitch to the OpenShift project into which you want to install Fuse Online, for example:
oc project my-fuse-online-projectAlternatively, when you run the installation script, you can specify, for example,
--project my-fuse-online-project.In the directory in which you downloaded the installation script, invoke the installation script:
bash install_ocp.shTo learn about the installation script options, invoke the
bash install_ocp.sh --helpcommand.Confirm that the
syndesiscustom resource thatsyndesis-operatorused to install Fuse Online contains exactly the content that you want:Invoke the following command to display the
syndesiscustom resource content:oc describe syndesis/appCheck the content of the custom resource.
If it does not contain all of your updates, then there was probably a syntax error in the custom resource. You must uninstall Fuse Online and try again to define a valid custom resource. See Uninstalling Fuse Online from an OCP project.
Confirm that installation was successful:
Display the OpenShift OAuth proxy log-in page at
https://openshift-route.If you chose to let the installation script calculate the OpenShift route, then the script displays the calculated route near the end of its execution. Replace
openshift-routewith the value that the script provided.If you edited the
default-cr.ymlfile to specify therouteHostnamefor Fuse Online, replaceopenshift-routewith the route that you specified.- If you are not already logged in to the OpenShift console, its log-in page appears. Enter your OpenShift user name and password to log in.
The Fuse Online home page appears either immediately or after you log in to the OpenShift console.
Additional resource
Chapter 3. Changing the configuration of a Fuse Online environment
After you install Fuse Online on OpenShift Container Platform (OCP) on-site, you can change the configuration of the Fuse Online environment.
See the following topics for details:
- Section 3.1, “Fuse Online configuration changes allowed after installation”
- Section 3.2, “General procedure for changing Fuse Online configuration”.
Configuring (prodname} and 3scale discovery of APIs:
- Section 3.5, “Configuring the HTTP proxy”
- Section 3.6, “Adding sample data to a Fuse Online environment running on OCP”
3.1. Fuse Online configuration changes allowed after installation
After you install Fuse Online on OpenShift Container Platform (OCP) on-site, you can change its configuration to enable/disable some features or change some configuration settings. The following table lists the features and settings that you can change, the effect of the change, and where to find instructions for making the change.
When changes to the syndesis custom resource cause redeployment of syndesis-server, OpenShift creates a new server pod. It takes a maximum of one to two minutes until the new server is ready. During this time, the Fuse Online console is not usable. Integrations that are running continue to run while a new server is being deployed. When the new deployment is ready, the new server loads the state of the integrations. You can use the Fuse Online console again when the syndesis-server pod status is Running and refreshing the Fuse Online console displays values for integrations, connections, messages, and uptime.
| Feature/Setting | Effect of changing | Information |
|---|---|---|
| 3scale discovery |
Redploys | |
| Backups |
Adds a backup job to | |
| Auditing Note: This is a Technology Preview feature. |
Updates the configuration of the running | |
| Monitoring | Installs new OpenShift resources | |
| Public Fuse Online REST API endpoints |
Creates | Exposing Fuse Online public REST APIs for use by external tools |
| Sample Todo app and sample PostresSQL database and connector |
The
Note that changing the | Adding sample data to a Fuse Online environment running on OCP Descriptions of custom resource attributes that configure Fuse Online |
| Java options |
Redeploys | Descriptions of custom resource attributes that configure Fuse Online |
| Maven configuration |
You must delete the | |
| Assigning Fuse Online pods to OpenShift cluster nodes | Redeploys Fuse Online infrastructure component and integration pods | Descriptions of custom resource attributes that configure Fuse Online |
| Memory available to Fuse Online components | Redeploys component with changed memory | Descriptions of custom resource attributes that configure Fuse Online |
| Number of running integrations allowed |
You must delete the | |
| Database connection pool |
Redploys |
3.2. General procedure for changing Fuse Online configuration
For a Fuse Online environment that is installed on OCP, you can change its configuration by updating its syndesis custom resource. After you save your changes, OpenShift updates syndesis-operator with your updates if they are syntactically correct. A syntax error prevents the update.
While editing the syndesis custom resource, ensure that you do not specify an invalid setting that is syntactically correct. The syndesis-operator will use the updated syndesis custom resource even if a syntactically correct setting is invalid. If you do specify an invalid setting, you learn about it only after OpenShift completes the update. During the update, OpenShift deletes invalid settings.
Prerequisites
- Fuse Online is installed on OCP on-site.
-
The
occlient tool is installed and it is connected to the OCP cluster in which Fuse Online is installed. - You have permission to install Fuse Online in the project for which you want to change Fuse Online configuration.
-
You consulted Descriptions of custom resource attributes that configure Fuse Online to learn which configuration changes are allowed after installation and how to update the
syndesiscustom resource for the configuration changes you want to make.
Procedure
Log in to OpenShift with an account that has permission to install Fuse Online. For example:
oc login -u developer -p developerSwitch to the OpenShift project that is running the Fuse Online environment whose configuration you want to change. For example:
oc project my-fuse-online-projectOptional. Create a backup copy of the current settings in the
syndesiscustom resource, just in case you update and save incorrect content. For example, invoking the following command saves a backup in thesyndesis_app_backup.ymlfile:oc get syndesis app -o yaml > syndesis_app_backup.ymlInvoke the following command to open the syndesis custom resource in an editor:
oc edit syndesis/appNote: This procedure describes how to set configurations by opening the custom resource file in an editor. Alternatively, you can use
oc patchcommands to edit the custom resource.-
Edit the
syndesiscustom resource as needed. Save the resource.
Depending on the type of object that your edits apply to, your update triggers the
syndesis-operatorto redeploy some Fuse Online components when you save the resource.Wait two or three minutes, and then confirm that the
syndesiscustom resource was updated correctly:Invoke the following command to display the content of the
syndesiscustom resource:oc describe syndesis/appCheck the content.
If the
syndesiscustom resource does not contain the settings that you need, edit it again to specify valid settings.
Results
Most changes to the syndesis custom resource trigger syndesis-operator to redeploy the Fuse Online syndesis-server component. This means that OpenShift creates a new server pod.
It takes a maximum of one to two minutes until the new server is ready. During this time, the Fuse Online console is not usable. Integrations that are running continue to run while a new server is being deployed. When the new deployment is ready, the new server loads the state of the integrations. You can use the Fuse Online console again when:
-
The
syndesis-serverpod status isRunning. - Refreshing the Fuse Online console displays values for integrations, connections, messages, and uptime.
Some changes to the syndesis custom resource update the Fuse Online configuration but do not require redeployment of syndesis-server. For example:
-
When you update the
syndesiscustom resource to specify backups, it is a few seconds before the backup job is in place.
The effect of each configuration change is described in Fuse Online configuration changes allowed after installation.
3.3. Configuring Fuse Online and 3scale discovery of APIs
If you create an API provider integration, you might want to enable discovery of the API for that integration in Red Hat 3scale. The default behavior is that APIs are not exposed for automatic discovery in 3scale.
If you enable 3scale discovery, you can later optionally disable it.
3.3.1. Configuring Fuse Online to enable 3scale discovery of APIs
If you create an API provider integration, you might want to enable discovery of the API for that integration in Red Hat 3scale. The default behavior is that APIs are not exposed for automatic discovery in 3scale. When you enable discovery, you must provide a URL for a 3scale user interface.
To configure Fuse Online to enable 3scale discovery of APIs before you install Fuse Online, see Descriptions of custom resource attributes that configure Fuse Online.
After installation, you can enable discovery by updating the syndesis custom resource. Instructions for doing this are in this topic. When you enable discovery, it applies to only the OpenShift project that you are connected to when you update the resource.
Turning on 3scale service discovery means that:
The default behavior is that 3scale publishes API provider integrations. When 3scale publishes an API provider integration:
- Fuse Online does not provide an external URL for an API provider integration that is running.
- The API is accessible only through 3scale. Configuration in 3scale is required to expose the endpoint. For details, see Red Hat 3scale API Management, Service Discovery.
- The creator of an API provider integration can disable 3scale discovery for that integration. In other words, each API provider integration creator can choose whether that integration’s API is discoverable.
Prerequisites
- Fuse Online is installed on OCP on-site.
-
The
occlient tool is installed and it is connected to the OCP cluster in which Fuse Online is installed. - You have permission to install Fuse Online in the project for which you want to enable discovery of APIs.
- You know the name of the 3scale project on the OpenShift cluster.
Procedure
Log in to OpenShift with an account that has permission to install Fuse Online. For example:
oc login -u developer -p developerSwitch to an OpenShift project in which Fuse Online is running. You are enabling discovery for only this project. For example:
oc project my-fuse-online-projectAdd permissions that allow the 3scale project to view Fuse Online integrations:
oc adm policy add-cluster-role-to-user view system:serviceaccount:<3scale-project>:ampFor example, if the 3scale project on OpenShift is named
my3scale:oc adm policy add-cluster-role-to-user view system:serviceaccount:my3scale:ampEdit the
syndesiscustom resource:Invoke the following command, which typically opens the resource in an editor:
oc edit syndesisEdit the resource by setting
managementUrlFor3scaleto the URL for your 3scale user interface. The result looks like this:spec: components: server: features: managementUrlFor3scale: https://3scale-admin.apps.mycluster.com- Save the resource.
Optional. To confirm that discovery is turned on for the project that you switched to, invoke the following command:
oc describe dc/syndesis-serverWhen discovery is turned on, the output from this command shows that the
OPENSHIFT_MANAGEMENT_URL_FOR3SCALEenvironment variable is set to the URL that you specified in the custom resource.
Results
This change to the syndesis custom resource triggers syndesis-operator, which is responsible for installing Fuse Online, to redeploy syndesis-server. In the OpenShift project that you switched to, the new default behavior is that APIs are exposed for discovery in 3scale.
Do not edit the syndesis-server DeploymentConfig object to set the OPENSHIFT_MANAGEMENT_URL_FOR3SCALE environment variable. This does not work because syndesis-operator reverts your change. The syndesis-operator ensures that Fuse Online is deployed only and always according to the syndesis custom resource.
3.3.2. Configuring Fuse Online to disable 3scale discovery of APIs
If you followed the procedure described in Configuring Fuse Online to enable 3scale discovery of APIs, each API provider integration creator can choose whether that integration’s API is discoverable. At some point, you might want to reconfigure the default behavior, which is that integration APIs are not discoverable in 3scale, For example, you might want to edit and test an API provider integration in Fuse Online. To do this, update the Fuse Online syndesis custom resource so that the line that specifies the managementUrlFor3scale key and value is commented out. This disables discovery by 3scale. Then republish any API provider integrations that were published with discoverable APIs.
Prerequisites
- Fuse Online is installed on OCP on-site.
- You have permission to install Fuse Online in the project in which you want to disable discovery.
-
The
occlient tool is installed and it is connected to the OCP cluster in which Fuse Online is installed. - 3scale discovery was enabled in an OpenShift project as described in Configuring Fuse Online to enable 3scale discovery of APIs.
Procedure
Log in to OpenShift with an account that has permission to install Fuse Online. For example:
oc login -u developer -p developerSwitch to an OpenShift project in which 3scale discovery was enabled. For example:
oc project my-fuse-online-projectEdit the
syndesiscustom resource:Invoke the following command, which typically opens the resource in an editor:
oc edit syndesisEdit the resource by inserting a hash sign (
#) at the beginning of the line that specifies themanagementUrlFor3scalekey and value. This makes the line a comment, which disables discovery. The result should look like this:spec: components: server: features: # managementUrlFor3scale: https://3scale-admin.apps.mycluster.comSave the resource.
This updates the
syndesiscustom resource. The update removes theOPENSHIFT_MANAGEMENT_URL_FOR3SCALEenvironment variable. This change to thesyndesiscustom resource triggerssyndesis-operator, which is responsible for installing Fuse Online, to redeploysyndesis-server. The new default behavior is that APIs are no longer exposed for discovery in 3scale.
Do not edit the
syndesis-server DeploymentConfigobject to remove the setting of theOPENSHIFT_MANAGEMENT_URL_FOR3SCALEenvironment variable. This does not work becausesyndesis-operatorreverts your change. Thesyndesis-operatorensures that Fuse Online is deployed only and always according to thesyndesiscustom resource.Republish any API provider integration that had discovery enabled and that was created in the project in which you just disabled discovery.
In other words, you do not need to republish an API provider integration if you disabled discovery of that integration’s API while discovery was enabled for the project in which the API provider integration was created.
Results
APIs for API provider integrations that were created in the relevant OpenShift project are no longer discoverable in 3scale.
When Fuse Online publishes (or republishes) an API provider integration that is in the relevant project, Fuse Online provides an external URL for invoking the API provider integration operations.
3.4. Configuring Fuse Online pods
You can configure the placement of Fuse Online infrastructure component and integration pods onto nodes within an OpenShift cluster by setting node affinity and tolerations options in the Fuse Online custom resource. The nodeAffinity option allows you to specify an affinity for Fuse Online pods towards a group of nodes to be placed on. The tolerations option allows you to control which nodes the Fuse Online pods run on and to prevent other workloads from using those nodes.
You set these options by editing the Fuse Online custom resource before or after installing Fuse Online.
You specify configure node affinity or tolerations settings for infrastructure component deployments separately from integration deployments:
infraScheduling- Specify theinfraSchedulingoption to configure node affinity and tolerations settings for these Fuse Online infrastructure deployments:-
syndesis-db -
syndesis-meta -
syndesis-prometheus syndesis-uiNote: The
syndesis-operatordeployment is not affected by a change in node affinity or tolerations because it is the Fuse Online management component.
-
integrationScheduling- Specify theintegrationSchedulingoption to configure node affinity and tolerations settings for all Fuse Online integration deployments.Note: If you want to know whether a Fuse Online deployment is an integration deployment, check the deployment name. You can use the
oc get podscommand to view a list of running deployments. If a deployment name includes a-iprefix, it is an integration deployment, for example,i-my-integration.
The following procedure describes how to edit the custom resource with the oc patch command. Alternatively, you can edit the custom resource as described in these topics:
- If you have already installed Fuse Online, open the custom resource by following the steps in “General procedure for changing Fuse Online configuration.
If you have not yet installed Fuse Online, open the custom resource by following the steps in these topics, depending on your OCP version:
Prerequisites
- Fuse Online is installed on OCP on-site.
-
The
occlient tool is installed and it is connected to the OCP cluster in which Fuse Online is installed.
Procedure
Use the
oc patchcommand with the following syntax to configure tolerations settings. SpecifyinfraSchedulingfor Fuse Online infrastructure component deployments orintegrationSchedulingfor Fuse Online integration deployments:oc patch syndesis/app --type=merge -p '{"spec":{"infraScheduling"|"infraScheduling":{"tolerations":[{"key":"_value1_","operator":"_value2_","effect":"_value3_"},{"key":"_value4_","operator":"_value5_","effect":"_value6_"}]}}}'For example, the following command adds tolerations for Fuse Online infrastructure components:
oc patch syndesis/app --type=merge -p '{"spec":{"infraScheduling":{"tolerations":[{"key":"tol_1","operator":"Equal","effect":"NoSchedule"},{"key":"tol_2","operator":"Equal","value":"value2","effect":"NoSchedule"}]}}}'Use the
oc patchcommand with the following syntax to configure node affinity settings. SpecifyinfraSchedulingfor Fuse Online infrastructure component deployments orintegrationSchedulingfor Fuse Online integration deployments:oc patch syndesis/app --type=merge -p '{"spec":{"infraScheduling"|"infraScheduling":{"affinity":{"nodeAffinity":{"preferredDuringSchedulingIgnoredDuringExecution":[{"weight":_value1_,"preference":{"matchExpressions":[{"key":"_value1_","operator":"_value2_","values":["_value3_","_value4_"]}]}}]}}}'For example, the following command sets nodeAffinity to both Fuse Online infrastructure components and integrations:
oc patch syndesis/app --type=merge -p '{"spec":{"infraScheduling":{"affinity":{"nodeAffinity":{"preferredDuringSchedulingIgnoredDuringExecution":[{"weight":11,"preference":{"matchExpressions":[{"key":"_affinity","operator":"In","values":["foo","bar"]}]}}]}}},"integrationScheduling":{"affinity":{"nodeAffinity":{"preferredDuringSchedulingIgnoredDuringExecution":[{"weight":22,"preference":{"matchExpressions":[{"key":"my_affinity2","operator":"In","values":["foo","bar"]}]}}]}}}}}'To remove a configuration setting, use the
removeoption in theoc patchcommand, as demonstrated in the following example commands:The following example command removes the
preferredDuringSchedulingIgnoredDuringExecutionsetting from a nodeAffinity for Fuse Online integrations:oc patch syndesis/app --type=json -p '[{"op": "remove", "path": "/spec/integrationScheduling/affinity/nodeAffinity/preferredDuringSchedulingIgnoredDuringExecution" }]'The following example removes the tolerations from Fuse Online infrastructure components:
oc patch syndesis/app --type=json -p '[{"op": "remove", "path": "/spec/infraScheduling/tolerations" }]'
Additional resources
For information about tolerations and node affinity, see the Understanding node affinity and the Controlling pod placement using node taints sections of the OpenShift documentation.
3.5. Configuring the HTTP proxy
Many services use a HTTP proxy to filter and secure communications with other services or components. To configure the HTTP proxy on Fuse Online components and integrations, edit the Fuse Online custom resource before or after installing Fuse Online.
Prerequisite
- You know the host and port values for the HTTP proxy.
Procedure
Open the custom resource in an editor:
If you have already installed Fuse Online, open the custom resource by following the steps in “General procedure for changing Fuse Online configuration.
If you have not yet installed Fuse Online, open the custom resource by following the steps in these topics, depending on your OCP version:
For the
syndesis-serverandsyndesis-metacomponents, set the Java Options (javaOptions) parameter and specify values for the HTTP proxy host and port. Use the same HTTP proxy values for bothsyndesis-serverandsyndesis-meta.For example:
spec: components: server: javaOptions: -Dhttp.proxyHost=10.0.0.100 -Dhttp.proxyPort=8800 meta: javaOptions: -Dhttp.proxyHost=10.0.0.100 -Dhttp.proxyPort=8800For Fuse Online integrations, set the Maven Arguments (additionalArguments) parameter. For example:
spec: components: server: features: maven: additionalArguments: "-Dhttp.proxy=10.0.0.100 -Dhttp.proxyPort=8800"Save the custom resource.
If Fuse Online is already installed, the
syndesis-serverpod is redeployed in response to the javaOptions update in Step 2.Republish any running integrations that use the HTTP proxy.
- In Fuse Online, select the integration that you want to update.
- Select Edit.
- Select Publish.
Fuse Online uses the HTTP proxy settings when it rebuilds the integration.
3.6. Adding sample data to a Fuse Online environment running on OCP
To help new users learn how to create integrations with Fuse Online, you can add sample data to your Fuse Online environment.
- The ToDo app
- The sample PostgresDB database and PostgresDB connection
The Salesforce to Database, AMQ to REST API, and API Provider quickstart sample integrations require this sample data.
By default, the sample PostgresDB database and connection and the ToDo app are disabled (not installed).
To configure Fuse Online to include the sample data before you install Fuse Online, see Descriptions of custom resource attributes that configure Fuse Online.
Prerequisites
- Fuse Online is installed and running on OCP on-site.
-
The
occlient tool is installed and it is connected to the OCP cluster in which Fuse Online is installed. - You have permission to edit the Fuse Online custom resource.
Procedure
Log in to OpenShift with an account that has permission to edit the Fuse Online custom resource. For example:
oc login -u developer -p developerSwitch to the project in which Fuse Online is running. For example:
oc project my-fuse-online-projectEdit the
syndesiscustom resource:Invoke the following command, which typically opens the resource in an editor:
oc edit syndesisEdit the custom resource by changing the
addons:todo:enabledfield to true:spec: addons: todo: enabled: trueSave the resource.
Saving this change to the
syndesiscustom resource triggers thesyndesis-operatorto create a newtodopod and triggers the redeployment of thesyndesis-serverandsyndesis-dbpods.
Chapter 4. Managing Fuse Online on OCP
After you install Fuse Online on OpenShift Container Platform (OCP) on-site, you can use Prometheus to monitor integration activity, and you can set up periodic Fuse Online backups, which you can use to restore Fuse Online environments. As needed, you can upgrade Fuse Online, uninstall Fuse Online, or delete an OCP project that contains Fuse Online.
See the following topics for details:
- Section 4.1, “Auditing Fuse Online components”
- Section 4.2, “Monitoring Fuse Online integrations and infrastructure components with Prometheus”
- Section 4.3, “Fuse Online Metering labels”
- Section 4.4, “Backing up a Fuse Online environment”
- Section 4.5, “Restoring a Fuse Online environment”
- Section 4.6, “Upgrading Fuse Online”
- Section 4.7, “Uninstalling Fuse Online from an OCP project”
- Section 4.8, “Deleting an OCP project that contains Fuse Online”
4.1. Auditing Fuse Online components
Fuse Online auditing is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production.These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.For more information about the support scope of Red Hat Technology Preview features, see https://access.redhat.com/support/offerings/techpreview/
Fuse Online supports basic auditing for changes made by any user to the following Fuse Online components: * Connections - The Name and any other fields shown on the connector’s Details page in the Fuse Online web console. * Connectors - The Name field. * Integrations - The Name field.
When a developer makes an update to one of these component fields (for example, changes the name of an integration), Fuse Online sends an AUDIT message to standard output that includes information such as ID, user, timestamp, component (connection, connector, or integration), and the type of change (create, modify, or delete). Note that the field values in an audit message are truncated to 30 characters.
By default, Fuse Online auditing is disabled. You can enable it by editing the Fuse Online custom resource. To enable auditing before you install Fuse Online, see Descriptions of custom resource attributes that configure Fuse Online.
Prerequisites
-
The
occlient tool is installed and it is connected to the OCP cluster in which Fuse Online is installed. - You have permission to edit the Fuse Online custom resource.
Procedure
Log in to OpenShift with an account that gives you permission to edit the Fuse Online custom resource. For example:
oc login -u admin -p admin-passwordSwitch to the project that is running the Fuse Online environment. For example:
oc project my-fuse-online-projectEdit the syndesis custom resource:
Invoke the following command, which typically opens the resource in an editor:
oc edit syndesisEnsure that the following lines are in the resource. Edit as needed:
components: server: features: auditing: true
Save the resource.
When you enable the auditing feature in the syndesis custom resource, the running
syndesis-serverconfiguration reloads and Fuse Online starts logging relevant changes to Fuse Online components.- To view the Fuse Online audit log messages, type the following command:
oc logs -l syndesis.io/component=syndesis-server
4.2. Monitoring Fuse Online integrations and infrastructure components with Prometheus
You can use Prometheus to monitor Fuse Online infrastructure components and Fuse Online integrations. You can also use Grafana dashboards to visualize the metrics gathered by Prometheus.
Red Hat support for Prometheus is limited to the setup and configuration recommendations provided in Red Hat product documentation.
Grafana is a community-supported feature. Deploying Grafana to monitor Red Hat Fuse products is not supported with Red Hat production service level agreements (SLAs).
In addition to monitoring Fuse Online integrations, you can use Prometheus to monitor the metrics exposed by the following Fuse Online infrastructure components:
- Syndesis Server
-
The
syndesis-servercomponent has been instrumented with Micrometer and exposes all of the JVM Micrometer metrics automatically by default. Additionally,syndesis-serverexposes metrics about the REST API endpoints, such as request rate, error rate, and latency. - Syndesis Meta
-
The
syndesis-metacomponent has been instrumented with Micrometer and exposes all of the JVM Micrometer metrics automatically by default. It also exposes metrics about its REST API endpoints. - Syndesis DB
- Metrics for the Fuse Online Postgres database are exported using a third-party Prometheus exporter.
- Integrations
-
The
integrationmetrics are visible after an integration has been created and are exported by using the official JMX exporter, which exposes several JVM metrics by default. Additionally, integration metrics expose metrics that are specific to Apache Camel, such as message rate and error rate.
Prerequisites
- Fuse Online is installed and running on OCP 4.9 (or later) on-site.
-
The
occlient tool is installed and it is connected to the OCP cluster in which Fuse Online is installed. -
You have
adminaccess to the OCP cluster. Your Fuse Online installation is configured with the
ops addonenabled. If required, you can enable it with this command:oc patch syndesis/app --type=merge -p '{"spec": {"addons": {"ops": {"enabled": true}}}}'
Procedure
If there is an existing
openshift-monitoringconfiguration, skip to Step 2.Otherwise, create an
openshift-monitoringconfiguration, that sets the user workload monitoring option totrueand then skip to Step 3:oc apply -f - <<EOF apiVersion: v1 kind: ConfigMap metadata: name: cluster-monitoring-config namespace: openshift-monitoring data: config.yaml: | enableUserWorkload: true EOF
If there is an existing
openshift-monitoringconfiguration:Check the existing
openshift-monitoringconfiguration to determine whether the user workload monitoring option is set to true:oc get -n openshift-monitoring cm/cluster-monitoring-config -ojsonpath='{.data.config\.yaml}'If the result is
enableUserWorkload: true, the user workload monitoring option is set to true. Skip to Step 3.If the result shows any other configurations, continue to the next step to enable the monitoring of user workloads by editing the ConfigMap.
Open the ConfigMap file in an editor, for example:
oc -n openshift-monitoring edit cm/cluster-monitoring-config
Set enableUserWorkload to true. For example:
apiVersion: v1 kind: ConfigMap metadata: name: cluster-monitoring-config namespace: openshift-monitoring data: config.yaml: | enableUserWorkload: true
- Save the ConfigMap file.
Use the following command to watch the status of the pods in the
openshift-user-workload-monitoringnamespace:oc -n openshift-user-workload-monitoring get pods -w
Wait until the status of the pods is Running, for example:
prometheus-operator-5d989f48fd-2qbzd 2/2 Running prometheus-user-workload-0 5/5 Running prometheus-user-workload-1 5/5 Running thanos-ruler-user-workload-0 3/3 Running thanos-ruler-user-workload-1 3/3 Running
Verify that the Fuse Online alert rules are enabled in Prometheus:
Access the internal prometheus instance
oc port-forward -n openshift-user-workload-monitoring pod/prometheus-user-workload-0 9090
-
Open your browser to
localhost:9090 -
Select Status> Targets. You should see three
syndesisendpoints. -
Press CTRL-C to terminate the
port-forwardprocess.
-
From the OperatorHub, install the Grafana Operator to a namespace of your choosing, for example, to the
grafana-middlewarenamespace. Add a cluster role and a cluster role binding to allow the
grafana-operatorto list nodes and namespaces:Download the cluster role YAML file from the
grafana-operatorwebsite:curl https://raw.githubusercontent.com/grafana-operator/grafana-operator/master/deploy/cluster_roles/cluster_role_grafana_operator.yaml > tmp_role.yaml
Add cluster permission for the
grafana-operatorto read other namespaces and nodes:cat <<EOF >> tmp_role.yaml - apiGroups: - "" resources: - namespaces - nodes verbs: - get - list - watch EOFoc apply -f tmp_role.yaml
oc apply -f - <<EOF apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: grafana-operator roleRef: name: grafana-operator kind: ClusterRole apiGroup: "" subjects: - kind: ServiceAccount name: grafana-operator-controller-manager namespace: grafana-middleware EOF
Enable the
grafana-operatorto read Grafana dashboards from other namespaces by using theDASHBOARD_NAMESPACES_ALLenvironment variable to limit the namespaces:oc -n grafana-middleware patch subs/grafana-operator --type=merge -p '{"spec":{"config":{"env":[{"name":"DASHBOARD_NAMESPACES_ALL","value":"true"}]}}}'Check that the
grafanapods are recreated:oc -n grafana-middleware get pods -w
Optionally, view the
grafana-operatorlogs:oc -n grafana-middleware logs -f `oc -n grafana-middleware get pods -oname|grep grafana-operator-controller-manager` -c manager
Add a Grafana custom resource to start a Grafana server pod, for example:
oc apply -f - <<EOF apiVersion: integreatly.org/v1alpha1 kind: Grafana metadata: name: grafana-middleware namespace: grafana-middleware spec: config: auth: disable_signout_menu: true auth.anonymous: enabled: true log: level: warn mode: console security: admin_password: secret admin_user: root dashboardLabelSelector: - matchExpressions: - key: app operator: In values: - grafana - syndesis ingress: enabled: true EOFAllow the
grafana-operatorto read monitoring information:oc -n grafana-middleware adm policy add-cluster-role-to-user cluster-monitoring-view -z grafana-serviceaccount
Add a
GrafanaDatasourceto querythanos-querier:oc apply -f - <<EOF apiVersion: integreatly.org/v1alpha1 kind: GrafanaDataSource metadata: name: prometheus-grafanadatasource namespace: grafana-middleware spec: datasources: - access: proxy editable: true isDefault: true jsonData: httpHeaderName1: 'Authorization' timeInterval: 5s tlsSkipVerify: true name: Prometheus secureJsonData: httpHeaderValue1: "Bearer $(oc -n grafana-middleware serviceaccounts get-token grafana-serviceaccount)" type: prometheus url: "https://$(oc get route thanos-querier -n openshift-monitoring -ojsonpath='{.spec.host}')" name: prometheus-grafanadatasource.yaml EOFView the grafana server log:
oc logs -f `oc get pods -l app=grafana -oname`
To access the grafana URL and view the Fuse Online dashboards:
echo "https://"$(oc -n grafana-middleware get route/grafana-route -ojsonpath='{.spec.host}')In the left panel of the Grafana console, click the search button. A folder (OCP namespace name) containing the dashboards for each Syndesis instance is displayed.
- For Fuse Online integrations, select Integration - Camel. This dashboard displays the standard metrics exposed by Apache Camel integration applications.
For Fuse Online infrastructure components, select one of the following infrastructure dashboards:
- Infrastructure - DB
- Displays metrics related to the Fuse Online Postgres instance.
- Infrastructure - JVM
-
Displays metrics about the running JVM for the
syndesis-metaorsyndesis-serverapplications. Chose the application that you want to monitor from the Application drop down list at the top of the dashboard. - Infrastructure - REST APIs
-
Displays metrics relating to the Fuse Online infrastructure API endpoints, such as
request throughputandlatency. Choose the application that you want to monitor from the Application drop down list at the top of the dashboard.
Additional resources
For information about getting started with Prometheus, go to: https://prometheus.io/docs/prometheus/latest/getting_started/
4.3. Fuse Online Metering labels
You can use the OpenShift Metering operator to analyze your installed Fuse Online operator and components to determine whether you are in compliance with your Red Hat subscription. For more information on Metering, see the OpenShift documentation.
The following table lists the metering labels for Fuse Online infrastructure components and integrations.
| Label | Possible values |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Examples
Infrastructure example (where the infrastructure component is syndesis-db)
com.company: Red_Hat rht.prod_name: Red_Hat_Integration rht.prod_ver: 7.8 rht.comp: Fuse rht.comp_ver: 7.8 rht.subcomp: syndesis-db rht.subcomp_t: infrastructure
Application example (where the integration deployment name is mytestapp)
com.company: Red_Hat rht.prod_name: Red_Hat_Integration rht.prod_ver: 7.8 rht.comp: Fuse rht.comp_ver: 7.8 rht.subcomp: i-mytestapp rht.subcomp_t: application
4.4. Backing up a Fuse Online environment
You can configure Fuse Online to periodically back up:
- The internal PostgreSQL database in which Fuse Online stores connections and integrations.
-
OpenShift resources that
syndesis-operatorcreates and that are needed to run Fuse Online. This includes, but is not limited to, configuration maps, deployment configurations, and service accounts.
You can configure backups for a Fuse Online environment before you install Fuse Online or you can change the configuration of a Fuse Online environment to enable backups.
When Fuse Online is configured to perform backups, Fuse Online zips data into one file and uploads that file to an Amazon S3 bucket that you specify. You can apply a backup to a new Fuse Online environment (no connections or integrations defined) to restore the Fuse Online environment that was backed up.
Prerequisites
- OCP is running on-site.
-
The
occlient tool is installed and connected to the OCP cluster in which Fuse Online is or will be running. - A user with cluster administration permissions gave you permission to install Fuse Online in any project that you have permission to access in the cluster.
- You have an AWS access key and an AWS secret key. For details about obtaining these credentials, see the AWS documentation for Managing Access Keys for IAM Users.
- You know the AWS region where the S3 bucket that you want to upload to resides.
- You know the name of the S3 bucket that you want to upload backups to.
Procedure
Log in to OpenShift with an account that has permission to install Fuse Online. For example:
oc login -u developer -p developerSwitch to the OpenShift project that is or will be running the Fuse Online environment for which you want to configure backups. For example:
oc project my-fuse-online-projectCreate an OpenShift secret. In the command line:
-
Specify
syndesis-backup-s3as shown in the following command format. Replace the AWS variables with your AWS access key, AWS secret key, AWS region in which the bucket resides, and the name of the bucket.
Use the following command format to create the secret:
oc create secret generic syndesis-backup-s3 \ --from-literal=secret-key-id="my-aws-access-key" \ --from-literal=secret-access-key="my-aws-secret-key" \ --from-literal=region="aws-region" \ --from-literal=bucket-name="aws-bucket-name"
This secret must be present when the backup job is running.
-
Specify
If Fuse Online is not yet installed, you must edit the
default-cr.ymlfile to enable backups. See Editing thesyndesiscustom resource before installing Fuse Online. After Fuse Online is installed, there will be backup jobs according to the schedule that you specified in the custom resource.If Fuse Online is running, you must edit the
syndesiscustom resource:Invoke the following command, which opens the
syndesiscustom resource in an editor:oc edit syndesisAdd the following under
spec::backup: schedule: my-backup-interval
Replace
my-backup-intervalwith the desired duration between backups. To determine how to specify the interval between backups, consult the following resources:- cron pre-defined schedules
Do not specify the
@sign in front of the interval. For example, to configure daily backups, the custom resource would contain something like this:apiVersion: syndesis.io/v1beta1 kind: Syndesis metadata: name: app spec: backup: schedule: daily
Save the file.
This adds a backup job to
syndesis-operator.
Result
If Fuse Online was already running, there is now a Fuse Online backup job according to the schedule that you defined.
Next steps
If Fuse Online needs to be installed, edit the default-cr.yml file to enable any other desired features or set any other parameters. When the default-cr.yml file has all the settings that you want, install Fuse Online in the project that you specified when you created the OpenShift secret.
4.5. Restoring a Fuse Online environment
In a new Fuse Online environment, in which you have not yet created any connections or integrations, you can restore a backup of a Fuse Online environment. After you restore a Fuse Online environment, you must edit the restored connections to update their passwords. You should then be able to publish the restored integrations.
Prerequisites
- OCP is running on-site.
-
The
occlient tool is installed and connected to the OCP cluster in which you want to restore a Fuse Online environment. - A user with cluster administration permissions gave you permission to install Fuse Online in any project that you have permission to access in the cluster.
- There is a Fuse Online environment that was configured to periodically back up data and upload the data to Amazon S3.
- The Fuse Online release number, for example, 7.6, is the same for the Fuse Online environment that was backed up and the Fuse Online environment in which you want to restore the backup.
- You have permission to access the AWS bucket that contains the Fuse Online backups.
- The Fuse Online environment in which you want to restore a backup is a new Fuse Online installation. In other words, there are no connections or integrations that you defined. If you want to restore Fuse Online in a project that has a Fuse Online environment with connections and integrations, then you must uninstall that Fuse Online environment and install a new Fuse Online environment.
Procedure
- Download the desired backup file from Amazon S3. Details for doing this are in the AWS documentation for How Do I Download an Object from an S3 Bucket?
Extract the content of the zip file. For example, the following command line unzips the
7.6-2020-03-15-23:30:00.zipfile and copies the content into the/tmp/fuse-online-backupfolder:unzip 7.6-2020-03-15-23:30:00.zip -d /tmp/fuse-online-backupDecode the Fuse Online database, for example:
base64 -d /tmp/fuse-online-backup/syndesis-db.dump > /tmp/fuse-online-backup/syndesis-db
Switch to the OpenShift project that is running the new Fuse Online environment. For example, if the new Fuse Online environment is in the
my-fuse-online-project, then you would invoke the following command:oc project my-fuse-online-projectThe remainder of this procedure assumes that you have switched to the project that contains the new Fuse Online environment.
Obtain the name of the database pod.
If the restored Fuse Online environment uses the provided, internal, PostgreSQL database, invoke the following command to obtain the name of the database pod:
oc get pods -l deploymentconfig=syndesis-db -o jsonpath='{.items[*].metadata.name}'If the restored Fuse Online environment uses an external database, it is assumed that you know how to obtain the name of the pod for that database.
In the remaining commands, where you see
DATABASE_POD_NAME, insert the name of the database pod for the restored Fuse Online environment.Scale down the components that are accessing the database in any way.
Scale down
syndesis-operatorso that other components can be scaled down:oc scale deployment syndesis-operator --replicas 0Scale down the
syndesis-serverandsyndesis-metacomponents:oc scale dc syndesis-server --replicas 0oc scale dc syndesis-meta --replicas 0
Send the database backup file to the Fuse Online database pod:
oc cp /tmp/fuse-online-backup/syndesis-db DATABASE_POD_NAME:/tmp/syndesis-db
Open a remote shell session in the Fuse Online database pod:
oc rsh DATABASE_POD_NAMEInvoke the following commands to restore the Fuse Online database.
If a
psqlcommand prompts for the database password, and the restored Fuse Online environment uses the provided, internal PostgreSQL database, you can find the password in thePOSTGRESQL_PASSWORDenvironment variable in thesyndesis-dbdeployment configuration. If the restored Fuse Online environment uses an external database, then it is assumed that you know the password.cd /tmp psql -c 'DROP database if exists syndesis_restore' psql -c 'CREATE database syndesis_restore' pg_restore -v -d syndesis_restore /tmp/syndesis-db psql -c "SELECT pg_terminate_backend(pid) FROM pg_stat_activity WHERE datname = 'syndesis'" psql -c 'DROP database if exists syndesis' psql -c 'ALTER database syndesis_restore rename to syndesis'
Fuse Online should now be restored. You can end the RSH session:
exitScale up the Fuse Online components:
oc scale deployment syndesis-operator --replicas 1Scaling
syndesis-operatorto1should bring up the other pods that were scaled down. However, if that does not happen, you can scale them up manually:oc scale dc syndesis-server --replicas 1oc scale dc syndesis-meta --replicas 1The server tries to start each restored integration but you need to update connections first. Consequently, ensure that the restored integrations are not running:
Obtain the Fuse Online console route:
echo "https://$(oc get route/syndesis -o jsonpath='{.spec.host}' )"- Log in into the Fuse Online console with an OpenShift user account that has permission to install Fuse Online.
- Display the list of integrations and ensure that all integrations are stopped. If an integration is running, stop it.
For each connection that has a password, you need to update the connection to have the correct password for this Fuse Online environment. The following steps show how to do this for the provided PostgresDB connection.
-
In the OpenShift console for the project in which this restored Fuse Online environment is running, retrieve the password for the PostgresDB connection. In the
syndesis-dbdeployment, the password is available in the environment variables. - In the Fuse Online console, display the connections.
- Edit the PostgresDB connection.
- In the connection details for the PostgresDB connection, paste the retrieved password in the Password field.
-
In the OpenShift console for the project in which this restored Fuse Online environment is running, retrieve the password for the PostgresDB connection. In the
For each integration, confirm that there are no Configuration Required indicators. If there are, edit the integration to resolve the issues. When all steps in the integration are correct, publish the integration.
If Fuse Online keeps rolling an integration back to a Stopped state right after the Build step, delete the deployment, ensure that no configuration is required, and try publishing the integration again.
You can safely ignore the following message if you see it in the log:
Error performing GET request to https://syndesis-my-fuse-online-project.my-cluster-url/api/v1/metrics/integrations
4.6. Upgrading Fuse Online
From time to time, fresh application images, which incorporate patches and security fixes, are released for Fuse Online. You are notified of these updates through Red Hat’s errata update channel. You can then upgrade your Fuse Online images.
For OCP 4.x, upgrade from Fuse Online 7.9 to 7.10 by following the steps in Upgrading Fuse Online by using the OperatorHub.
For OCP 3.11, use the install script to upgrade from Fuse Online 7.9 to 7.10 as described in Upgrading Fuse Online by using the install script.
You should determine whether upgrading to Fuse Online 7.10 requires you to make changes to your existing integrations. Even if no changes are required, you must republish any running integrations when you upgrade Fuse Online.
4.6.1. Upgrading Fuse Online by using the OperatorHub (OCP 4.x)
Use the OpenShift OperatorHub to upgrade from Fuse Online 7.9 to 7.10.
- If you want to upgrade from Fuse Online 7.9.x to Fuse Online 7.10.1, you must first manually upgrade to Fuse Online 7.10.0 as described in the Upgrading from Fuse Online 7.9.x to 7.10.1 requires manual upgrade steps release note.
- Fuse Online 7.10 requires OpenShift Container Platform (OCP) 4.6 or later. If you are using OCP 4.5 or earlier, you must upgrade to OCP 4.6 or later, if you want to upgrade to Fuse Online 7.10 .
On OCP 4.9, When you upgrade to 7.10, the following warning is displayed during the Fuse Online Operator upgrade process:
W1219 18:38:58.064578 1 warnings.go:70] extensions/v1beta1 Ingress is deprecated in v1.14+, unavailable in v1.22+; use networking.k8s.io/v1 IngressThis warning appears because clients (that Fuse Online uses for the Kubernetes/OpenShift API initialization code) access a deprecated Ingress version. This warning is not an indicator of complete use of deprecated APIs and there is no issue with upgrading to Fuse Online 7.10.
The upgrade process from a Fuse Online 7.9 or an earlier 7.10 version to a newer Fuse Online 7.10 version depends on the Approval Strategy that you selected when you installed Fuse Online:
- For Automatic updates, when a new version of the Fuse Online operator is available, the OpenShift Operator Lifecycle Manager (OLM) automatically upgrades the running instance of the Fuse Online without human intervention.
- For Manual updates, when a newer version of an Operator is available, the OLM creates an update request. As a cluster administrator, you must then manually approve that update request to have the Fuse Online operator updated to the new version as described in the Manually approving a pending Operator upgrade section of the OpenShift documentation.
During and after an infrastructure upgrade, existing integrations continue to run with the older versions of Fuse Online libraries and dependencies.
To have existing integrations run with the updated Fuse Online version, you must republish the integrations.
4.6.2. Upgrading Fuse Online by using the install script (OCP 3.11)
For OCP 3.11, the install script procedure for the following upgrades is the same:
- From Fuse Online 7.9 to Fuse Online 7.10
- From a Fuse Online 7.10 version to a newer Fuse Online 7.10 version
Prerequisites
You installed and are running version 7.9 of Fuse Online on OCP 3.11 on-site OR you installed and are running a version of 7.10 of Fuse Online on OCP 3.11 and you want to upgrade to fresh application images.
For earlier versions:
- If you are running version 7.8 of Fuse Online on OCP, then you must upgrade to 7.9 and then you can upgrade to 7.10.
- If you are running version 7.7 of Fuse Online on OCP, then you must upgrade to 7.8 and then you can upgrade to 7.9.
- If you are running version 7.6 of Fuse Online on OCP, then you must upgrade to 7.7 and then you can upgrade to 7.8.
- If you are running version 7.5 of Fuse Online on OCP, then you must upgrade to 7.6 and then you can upgrade to 7.7.
- If you are running version 7.4 of Fuse Online on OCP, then you must upgrade to 7.5 and then you can upgrade to 7.6.
- If you are running version 7.3 of Fuse Online on OCP, then you must upgrade to 7.4 and then you can upgrade to 7.5.
- If you are running version 7.2 of Fuse Online on OCP, then you must upgrade to 7.3.
- If you are running version 7.1 of Fuse Online on OCP, then you must upgrade to 7.2.
-
You installed the
occlient tool and it is connected to the OCP cluster in which Fuse Online is installed. - You have cluster administration permissions, which are required for the first two steps in this procedure.
Procedure
- To avoid encountering a possible Docker limit error, a cluster administrator sets up access to Docker images as described in Access Docker images before an upgrade.
A cluster administrator downloads the Fuse Online package and grants permission for a user to upgrade Fuse Online in a particular project:
Download the package containing the Fuse Online installation scripts from the following location:
https://github.com/syndesisio/fuse-online-install/releases/tag/1.13
Unpack the downloaded archive at a convenient location on your file system. The
fuse-online-install-1.13directory contains the scripts and supporting files for upgrading Fuse Online.Change to the directory that contains the extracted archive. For example:
cd fuse-online-install-1.13Log in to OpenShift with a cluster administration account, for example:
oc login -u admin -p adminChange to the OpenShift project in which Fuse Online needs to be upgraded, for example:
oc project fuse-online-projectUpdate the Fuse Online custom resource definition:
bash install_ocp.sh --setupGrant permission for upgrading Fuse Online in just this project. For example, the following command grants permission for upgrading Fuse Online to the
developeruser. After the cluster administrator runs this command, thedeveloperuser can upgrade Fuse Online in only this project, which isfuse-online-project, in this example:bash install_ocp.sh --grant developer
The user who was granted permission to upgrade Fuse Online performs the upgrade:
Log in to OpenShift, for example:
oc login -u developerSwitch to the project in which you want to upgrade Fuse Online, for example:
oc project fuse-online-projectTo check which version you are about to upgrade to, run the update script with the
--versionoption, as follows:bash update_ocp.sh --versionInvoke the update script as follows:
bash update_ocp.shTo learn more about the script, invoke
bash update_ocp.sh --help.During and after an infrastructure upgrade, existing integrations continue to run with the older versions of Fuse Online libraries and dependencies.
Upgrade Fuse Online integrations that are running as follows:
- In Fuse Online, select the integration that you want to upgrade.
- Select Edit.
- Select Publish to republish the integration.
Republishing the integration forces a rebuild that uses the latest Fuse Online dependencies.
4.6.3. Upgrading Fuse Online integrations
When you upgrade to Fuse Online 7.10, you should determine whether you need to make changes to your existing integrations.
Review the Apache Camel updates described in Camel Migration Considerations.
Even if your integrations do not require changes, you must republish any running integrations because during and after an infrastructure upgrade, existing integrations continue to run with the older versions of Fuse Online libraries and dependencies. To have them run with the updated versions, you must republish them.
Procedure
To republish your integrations, in your Fuse Online environment:
- In the Fuse Online left navigation panel, click Integrations.
For each integration:
-
To the right of the integration entry, click
 and select Edit.
and select Edit.
- When Fuse Online displays the integration for editing, in the upper right, click Publish.
-
To the right of the integration entry, click
Publishing forces a rebuild that uses the latest Fuse Online dependencies.
The Fuse Online user interface shows a warning if any element of an integration has a newer dependency that you need to update.
4.7. Uninstalling Fuse Online from an OCP project
You can uninstall Fuse Online from an OCP project without deleting the project nor anything else in that project. After uninstalling Fuse Online, integrations that are running continue to run but you can no longer edit or republish them.
Prerequisite
- You have an OCP project in which Fuse Online is installed.
- You exported any integrations that you might want to use in some other OpenShift project in which Fuse Online is installed. If necessary, see Export integrations.
Procedure
Log in to OpenShift with an account that has permission to install Fuse Online. For example:
oc login -u developer -p developerSwitch to the OpenShift project that is running the Fuse Online environment that you want to uninstall. For example:
oc project my-fuse-online-projectDelete Fuse Online infrastructure:
oc delete syndesis appDelete
syndesis-operator DeploymentConfigandImageStreamresources:oc delete deployment/syndesis-operatoroc delete is/syndesis-operator
4.8. Deleting an OCP project that contains Fuse Online
Deleting an OpenShift project in which Fuse Online is installed deletes everything in the project. This includes all integrations that have been defined as well as all integrations that are running.
Prerequisites
- You have an OCP project in which Fuse Online is installed.
- You exported any integrations that you might want to use in some other OpenShift project in which Fuse Online is installed. If necessary, see Exporting integrations.
Procedure
Invoke the oc delete project command. For example, to delete an OpenShift project whose name is fuse-online-project, enter the following command:
oc delete project fuse-online-project
Chapter 5. How to invoke Fuse Online public REST API endpoints
When you are running Fuse Online on OCP, each Fuse Online environment can expose public REST API endpoints. External Continuous Integration/Continuous Delivery (CI/CD) tools can invoke these endpoints to operate on the resources that are in that Fuse Online environment.
In each Fuse Online environment, an OpenShift administrator must expose Fuse Online public REST API endpoints before external tools can invoke those endpoints. The command that invokes an API endpoint specifies the URL for the Fuse Online environment on which the endpoint operates, a secret token, and an authorization token.
See the following topics for details:
- Section 5.1, “Exposing Fuse Online public REST APIs for use by external tools”
- Section 5.2, “Description of base URL for Fuse Online public REST API endpoints”
- Section 5.3, “Obtaining a secret token for calling a public REST API endpoint”
- Section 5.4, “How to find integration IDs”
-
Section 5.5, “Format for specifying
curlcommands to invoke Fuse Online public endpoints”
5.1. Exposing Fuse Online public REST APIs for use by external tools
When you are running Fuse Online on OCP on-site, you might want to use an external tool to copy Fuse Online integrations from one Fuse Online environment to another Fuse Online environment. An external CI/CD tool might be a Jenkins job, an Ansible playbook, a cron-based shell script, or something else. For example, an Ansible playbook can export an integration from a Fuse Online development environment and import it into a Fuse Online testing environment.
To enable this, you must expose Fuse Online public REST API endpoints for each Fuse Online environment. In other words, you must repeat the procedure here in each OpenShift project in which Fuse Online is installed.
Prerequisites
- You have an OCP project in which Fuse Online is installed.
-
The
occlient tool is installed and it is connected to the OCP cluster in which Fuse Online is installed. - You use an external CI/CD tool and you want it to copy marked integrations from one Fuse Online environment to another.
-
Cluster administration privileges are required to execute the
syndesis-operator grantcommand. A user who has administrative privileges for the OpenShift project, but not cluster administration privileges, can execute the other commands.
Procedure
Log in to OpenShift with an account that has cluster administration privileges. For example:
oc login -u admin -p adminWhile cluster administration privileges are required for only the
syndesis-operator grantcommand, this procedure assumes that a cluster administrator is performing all steps.Switch to an OpenShift project in which Fuse Online is running. You are exposing the public API in only this project. For example:
oc project fuse-online-northGrant roles to the
syndesis-public-oauthproxyservice account. Your OpenShift project uses this service account to run an OAuth proxy service. Specify a user account that has cluster administration privileges. For example:syndesis-operator grant --user developerThis command creates and assigns a cluster role and cluster role binding to the
syndesis-public-oauthproxyservice account. The ClusterRoleBinding specifies the name of the OpenShift project in which you are exposing the API, which isfuse-online-northin this example:-
ClusterRole:
syndesis-auth-delegator -
ClusterRoleBinding:
syndesis-fuse-online-north-auth-delegator
-
ClusterRole:
Create a client service account and grant it permission to access the Fuse Online public API:
Create an OpenShift service account with a name that you choose. For example, the following command creates the
cicd-clientservice account:oc create serviceaccount cicd-clientCommands that invoke public API endpoints use this account to access the public API. Also, you will need this service account to obtain a secret token, which must be specified in calls to API endpoints. This is described in Obtaining a secret token for calling a REST API endpoint.
Grant the client service account permission to access the Fuse Online public API. If
fuse-online-northis the name of the OpenShift project in which Fuse Online is installed, and ifcicd-clientis the name of the service account that you created for accessing the API service, then you would invoke the following command:oc policy add-role-to-user edit system:serviceaccount:fuse-online-north:cicd-client`
Edit the
syndesiscustom resource:Invoke the following command, which typically opens the resource in an editor:
oc edit syndesisEdit the resource so that it enables the public API and specifies the Fuse Online environment’s public address for invoking endpoints as the setting of
routeHostname. (If edits to thedefault-cr.ymlfile, which was used to install Fuse Online, enabled the public API and specified the route hostname for endpoints, you will not need to edit the resource.)Your cluster setup determines the public address that you need to specify. For details, see the OpenShift documentation for routes. In the following example, the route host name is valid for a minishift cluster.
spec: addons: publicApi: enabled: true routeHostname: public-syndesis.192.168.64.63.nip.ioSave (or close) the resource.
Saving the
syndesiscustom resource triggerssyndesis-operator, which is responsible for installing Fuse Online, to deploy the public API OAuth proxy service.If you did not need to edit the
syndesiscustom resource, then the public API OAuth proxy service has already been deployed. This is probably becausepublicApiwas enabled and its route specified in thedefault-cr.ymlfile that was used to install Fuse Online.
Result
In OpenShift, you can now see:
-
A pod for the
syndesis-public-oauthproxydeployment configuration. -
A
syndesis-public-oauthproxyservice. -
A
syndesis-public-apiroute.
In the OpenShift project in which you performed this procedure, external CI/CD tools can use Fuse Online public REST API endpoints to export or import Fuse Online integrations.
Next steps
- Mark integrations for export to other Fuse Online environments. You can mark an integration in the Fuse Online console or invoke the Fuse Online public REST API endpoint that marks an integration.
-
To confirm that public API endpoints are available, invoke a
curlcommand that returns environment names. See Endpoint for obtaining a list of environment labels. - Configure external tools to call the Fuse Online public REST API endpoints.
5.2. Description of base URL for Fuse Online public REST API endpoints
The base URL for Fuse Online public REST API endpoints is something like this:
https://public-syndesis.192.168.64.42.nip.io/api/v1/public
The first part of the base URL is different for each Fuse Online environment. When you create the OpenShift application that runs the Fuse Online public OAuth proxy that enables access to public REST API endpoints, you specify the public address of your Fuse Online environment. This address is the first part of the base URL for calling endpoints that operate in that Fuse Online environment. For example:
https://public-syndesis.192.168.64.42.nip.io
The second part of the base URL is the same for all Fuse Online environments:
/api/v1/public
The Fuse Online public REST API provides endpoints that operate on three resources:
-
/integrationsare the integrations that are in the Fuse Online environment that is identified in the base URL. -
/connectionsare the connections that are in the Fuse Online environment that is identified in the base URL. -
/environmentsis the set of environment labels that are in the Fuse Online environment that is identified in the base URL.
5.3. Obtaining a secret token for calling a public REST API endpoint
A command that calls a Fuse Online public REST API endpoint must specify a secret token. This token is for the service account that you created when you exposed the Fuse Online public REST API in a given Fuse Online environment.
Prerequisites
- You are running Fuse Online on OCP on-site.
- You exposed the public REST API that is provided by a Fuse Online environment in which you want to invoke endpoints.
Procedure
Obtain the names of the secret tokens for the service account that you created when you exposed the public REST API for this Fuse Online environment. For example, if
cicd-clientis the name of the service account, you would invoke the following command:oc describe serviceaccount cicd-clientThis displays a list of information about the
cicd-clientservice account including the names of its two tokens, which looks something like this:Tokens: cicd-client-token-gxb25 cicd-client-token-gxdnvDisplay the content of either one of the tokens. For example:
oc describe secret cicd-client-token-gxb25This displays a list of information, including a
Datasection that displaystoken:followed by a long series of random characters. This is one of the service account’s two secret tokens.- Copy the secret token, paste it into a file, and save it.
Result
In a curl command, specification of the secret token looks like this:
-H 'Authorization: Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJzeW5kZXNpcyIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJzeW5kZXNpcy1jZC1jbGllbnQtdG9rZW4tMnZjNmwiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoic3luZGVzaXMtY2QtY2xpZW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNjUxMjYxNGMtMmYwMS0xMWU5LTk3OWEtNDI1YWNlMzY3MTcyIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OnN5bmRlc2lzOnN5bmRlc2lzLWNkLWNsaWVudCJ9.uKsri0JSKJDbgHoQwAhBJSNuWKwJgjegf2QlrCkhxVssSK1zIMZQaF9P5a4R7ZcWRnrZ_345UTqxYVeRlfHWVH0PqBkD-n7PAS9dcKJIFdS1jUHOmL1FTGgc3YW-bz1SlWT93tvK1EhorZ4_-EBfXhSAP4Uumi5qAg3_QUTMDstq233NSwBKYtFOw3Pp1ys3p3y0hcaiLMimeCH60vR4iWvptqqzc5QDigHiPySZNWxs_5awZlwdoIDvR-nSj690aC-49UKFgyEEdzdFU4bI2W4hOyDyhN9fVaIAZQKeJUrJBU-lnFTHI_NAd2OwzOEBpWZuj31Za5w9fU4kf4UDGA'
Next step
Copy the token from your saved file into a command that calls a public REST API endpoint in the given Fuse Online environment.
5.4. How to find integration IDs
In a command that invokes a Fuse Online public REST API endpoint that operates on only a particular integration, you must specify the ID of the integration that you want the endpoint to operate on. Specify one of the following:
The integration’s name
You must specify it exactly as it appears in the Fuse Online console, for example,
timer-to-log. If the integration name has any spaces or special characters, then you must specify HTML escape characters.The internal integration ID
This ID is in the Fuse Online console URL when you view an integration’s summary. To view an integration’s summary, in the left navigation panel, click Integrations. In the list of integrations, click the entry for the integration whose ID you need.
With the integration summary visible in the browser, you would see something like this at the end of the URL:
/integrations/i-Lauq5ShznJ4LcuWwiwcz. This integration’s ID isi-Lauq5ShznJ4LcuWwiwcz.
5.5. Format for specifying curl commands to invoke Fuse Online public endpoints
A curl command that calls a Fuse Online public REST API endpoint has the following format:
curl [options] \
-H "Content-Type: <media-type>" \
-H "SYNDESIS-XSRF-TOKEN: awesome" \
-H `Authorization: Bearer <token>` \
<base-url><endpoint> \
[--request <HTTP-method>] \
[-d <data>] \
[-o <filename>]| Option | Description |
|---|---|
|
|
Specify |
|
|
For the export and import endpoints, specify |
|
| Specify a secret token for the OpenShift service account that you created when you exposed the public REST API. |
|
| Specify the base URL for the Fuse Online environment that has the integration, connection, or environment label, that you want the endpoint to operate on. |
|
| Specify the endpoint that you want to call. |
|
|
Optionally, specify the HTTP method, for example, |
|
|
Optionally, depending on the endpoint that is being called, specify arguments that the endpoint requires. For example, to change an integration’s environment label to |
|
|
Optionally, if you need to specify the name of a file that contains output, specify the |
The following curl command invokes the Fuse Online public API endpoint that marks an integration for one or more environments that you specify:
curl -v -k -L -H "Content-Type: application/json" -H "SYNDESIS-XSRF-TOKEN: awesome" -H 'Authorization: Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJzeW5kZXNpcyIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJzeW5kZXNpcy1jZC1jbGllbnQtdG9rZW4tMnZjNmwiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoic3luZGVzaXMtY2QtY2xpZW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNjUxMjYxNGMtMmYwMS0xMWU5LTk3OWEtNDI1YWNlMzY3MTcyIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OnN5bmRlc2lzOnN5bmRlc2lzLWNkLWNsaWVudCJ9.uKsri0JSKJDbgHoQwAhBJSNuWKwJgjegf2QlrCkhxVssSK1zIMZQaF9P5a4R7ZcWRnrZ_345UTqxYVeRlfHWVH0PqBkD-n7PAS9dcKJIFdS1jUHOmL1FTGgc3YW-bz1SlWT93tvK1EhorZ4_-EBfXhSAP4Uumi5qAg3_QUTMDstq233NSwBKYtFOw3Pp1ys3p3y0hcaiLMimeCH60vR4iWvptqqzc5QDigHiPySZNWxs_5awZlwdoIDvR-nSj690aC-49UKFgyEEdzdFU4bI2W4hOyDyhN9fVaIAZQKeJUrJBU-lnFTHI_NAd2OwzOEBpWZuj31Za5w9fU4kf4UDGA' https://public-syndesis.192.168.64.42.nip.io/api/v1/public/integrations/timer-to-log/tags -d '["test","staging"]' --request PUT
In the sample curl command:
- The URL at the end of the command identifies the Fuse Online environment whose endpoint you are invoking.
-
timer-to-logindicates that you are marking thetimer-to-logintegration for the specified environments. -
Specification of
testandstagingmarks thetimer-to-logintegration for those environments.
Chapter 6. Using external tools to export/import Fuse Online integrations for CI/CD
When you are running Fuse Online on OCP on-site, you might have Continuous Integration/Continuous Deployment (CI/CD) pipelines that you want to act on certain integrations. Implementing this requires the completion of these tasks:
- In the Fuse Online console, mark integrations for CI/CD pipelines.
- In OpenShift, expose the Fuse Online public API.
- Use external tools to invoke Fuse Online public API endpoints that export and import integrations.
See the following topics for details:
6.1. About marking integrations for CI/CD
When you are running Fuse Online on OCP on-site, to identify an integration for pipelines, mark the integration for a CI/CD environment that you specify. This applies a time-stamped label to the integration. Backend CI/CD Fuse Online public APIs use the label and its timestamp to filter integrations to find an integration that a pipeline needs to act on.
For example, suppose that in Fuse Online you mark an integration for the test1 environment. You can then invoke the Fuse Online public API export endpoint to export integrations that have the test1 environment label. The endpoint packages test1 integrations into an export file and returns that file. To copy test1 integrations to a Fuse Online test environment, you would invoke the public API import endpoint and provide the file that contains the exported test1 integrations.
Now suppose that you iteratively update and publish an integration that you previously marked for the test1 environment. You now have a new version of the integration and you want to export the updated version to the test1 environment. You must mark the integration again, even though it is already marked for the test1 environment. Marking the integration again updates the timestamp on the test1 environment label. This indicates to external tools that the integration has been updated and it is ready to be exported.
To mark an integration again, that is, to refresh the timestamp on an environment label that is already assigned to an integration, start the procedure for Marking integrations for CI/CD. In the CI/CD dialog, click Save since the checkbox for the desired environment should already be selected.
6.2. Marking an integration for CI/CD
When you are running Fuse Online on OCP on-site, to identify an integration for pipelines, mark the integration for a CI/CD environment that you specify. This applies a label to the integration.
Prerequisite
You have an OCP project in which Fuse Online is installed.
Procedure
- In the Fuse Online navigation panel on the left, click Integrations.
-
In the list of integrations, at the right of the entry for the integration that you want to mark, click
 to display a popup menu and click Manage CI/CD.
to display a popup menu and click Manage CI/CD.
In the dialog that appears, do one or more of the following:
- If the environment for which you want to mark this integration already appears, select the checkbox to the left of that environment.
- If the environment for which you want to mark this integration is already selected, leave it selected.
- If you need to create a label for an environment, then click Manage CI/CD, which displays a dialog for creating new environment labels. Create the label that you need, and then return to this procedure to mark the integration.
Fuse Online applies selected environment label(s) to the integration. You can apply any number of environment labels to an integration.
- Click Save.
Result
Fuse Online labels the integration for release in the selected environment. Backend APIs can filter integrations to find the integrations that have, for example, the test1 label.
Next step
You must expose the Fuse Online public API endpoints before pipelines can act on integrations that are marked for a particular environment. See Exposing Fuse Online public REST APIs for use by external tools.
6.3. Managing environment labels for CI/CD
In the Fuse Online console, you can create, change, or remove CI/CD environment labels. CI/CD environment labels are tags that you can apply to integrations to identify them for CI/CD pipelines.
Prerequisites
- Fuse Online is running on OCP on-site.
- External tools use Fuse Online environment labels to identify integrations for CI/CD pipelines.
Procedure
- In Fuse Online, in the left navigation panel, click Integrations.
- In the upper right, click Manage CI/CD.
On the Manage CI/CD page:
To create a CI/CD environment label:
- Click Add New.
- In the Add Tag Name dialog, in the Tag Name input field, enter a name for a new environment label, for example, test1.
- Click Save. On the Manage CI/CD page, there is a new entry for the environment label that you just added.
To change a CI/CD environment label:
- In the list of CI/CD environment labels, in the entry for the label that you want to change, click Edit.
- In the Edit Tag dialog, change the name as needed.
- Click Save to see the updated name in the list of environment labels. Fuse Online applies the updated name to every integration that is already marked with the environment label that you changed.
To delete a CI/CD environment label:
- In the list of CI/CD environment labels, in the entry for the label that you want to delete, click Remove.
- In the confirmation dialog, click Yes. Fuse Online deletes the environment label and also removes the deleted environment label from any integrations that have been marked with it.
Next step
Mark integrations with new environment labels. See Marking an integration for CI/CD.
6.4. Invoking the Fuse Online public API export endpoint
Before you can use external tools to copy Fuse Online integrations from one Fuse Online environment to another, the following tasks must be completed:
In Fuse Online, an integration that you want to export for a CI/CD pipeline must be marked for a particular environment. See Marking an integration for CI/CD.
There is an exception to this requirement. When you want to export all integrations from a Fuse Online environment in one export operation, it does not matter whether or not an integration has already been marked for a particular environment.
- You exposed the Fuse Online public API. See Exposing Fuse Online public API endpoints for external tools.
Endpoint for exporting integrations for a particular environment
To export integrations that have been marked for a particular environment, Fuse Online provides the following GET method endpoint:
/public/integrations/{env}/export.zip
Replace {env} with a CI/CD environment label that you already created. When an integration is marked for a particular environment, Fuse Online maintains a timestamp that indicates when it was marked. The default behavior is that the endpoint exports an integration only if it has not already been exported since it was marked. For example, to export integrations that have been marked for the test1 environment, the endpoint is:
/public/integrations/test1/export.zip
This endpoint exports each integration that has the test1 environment label and that meets one of the following conditions:
-
The integration was marked for the
test1environment since the last time that it was exported. -
The integration was marked for the
test1environment and it has never been exported.
The endpoint packages the integrations in the export.zip file and returns that file.
If no integration that is marked for the specified environment has been marked since the last time that the integration was exported, then the endpoint returns an HTTP 204 response to indicate that there is nothing to return.
Endpoint for exporting all integrations tagged for the specified environment
You can invoke the export endpoint so that it exports all integrations in a Fuse Online environment that are tagged with an environment label that you specify. The endpoint exports the integration whether or not it was marked for the specified environment since the last time the integration was exported. This makes it easy to duplicate all integrations that have a particular tag in another Fuse Online environment. To do this:
- You must have already created the environment label. See Marking an integration for CI/CD.
-
Add the
ignoreTimestamp=trueoption to the invocation of the export endpoint.
For example:
/public/integrations/test1/export.zip?ignoreTimestamp=true -o export.zip
Endpoint for exporting all integrations
You can invoke the export endpoint so that it exports all integrations in one Fuse Online environment. This makes it easy to duplicate all integrations in another Fuse Online environment. To do this:
- You must have already created the environment label. See Marking an integration for CI/CD.
-
Add the
all=trueoption to the invocation of the export endpoint.
For example:
/public/integrations/{env}/export.zip?all=true
Replace {env} with a CI/CD environment label. The endpoint assigns the specified environment label to each integration that is not already marked for that environment.
When you add the all=true option, you must also explicitly specify that you want the exported integrations to be packaged in the export.zip file. For example:
/public/integrations/test1/export.zip?all=true -o export.zip
This invocation of the endpoint:
-
Marks each integration for the
test1environment. Returns all integrations in the
export.zipfile.If you do not specify the
-o export.zipoption, then the endpoint returns a file whose name isexport.zip?all=true.
Custom headers required by export endpoint
A command that invokes the export endpoint must specify these custom headers exactly as follows:
-
-H "Content-Type: multipart/form-data" -H "SYNDESIS-XSRF-TOKEN: awesome"The Fuse Online public API requires this header to authenticate the request.
-H 'Authorization: Bearer <token>'Replace
<token>with the secret token that you copied into a file when you created the OpenShift service account that is used to expose the Fuse Online public API.
Sample curl command that exports integrations
Following is an example of a curl command that invokes a Fuse Online API endpoint that exports integrations:
curl -v -k -L -H "Content-Type: multipart/form-data" -H "SYNDESIS-XSRF-TOKEN: awesome" -H 'Authorization: Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJzeW5kZXNpcyIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJzeW5kZXNpcy1jZC1jbGllbnQtdG9rZW4tMnZjNmwiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoic3luZGVzaXMtY2QtY2xpZW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNjUxMjYxNGMtMmYwMS0xMWU5LTk3OWEtNDI1YWNlMzY3MTcyIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OnN5bmRlc2lzOnN5bmRlc2lzLWNkLWNsaWVudCJ9.uKsri0JSKJDbgHoQwAhBJSNuWKwJgjegf2QlrCkhxVssSK1zIMZQaF9P5a4R7ZcWRnrZ_345UTqxYVeRlfHWVH0PqBkD-n7PAS9dcKJIFdS1jUHOmL1FTGgc3YW-bz1SlWT93tvK1EhorZ4_-EBfXhSAP4Uumi5qAg3_QUTMDstq233NSwBKYtFOw3Pp1ys3p3y0hcaiLMimeCH60vR4iWvptqqzc5QDigHiPySZNWxs_5awZlwdoIDvR-nSj690aC-49UKFgyEEdzdFU4bI2W4hOyDyhN9fVaIAZQKeJUrJBU-lnFTHI_NAd2OwzOEBpWZuj31Za5w9fU4kf4UDGA' https://public-syndesis.192.168.64.42.nip.io/api/v1/public/integrations/dev1/export.zip
In the command:
- The URL at the end of the command identifies the Fuse Online environment from which to export integrations.
-
Specification of the
dev1environment label indicates that you want to export integrations that have been marked for thedev1environment and that have not already been exported since they were marked.
6.5. Invoking the Fuse Online public API import endpoint
You can obtain one or more integrations by invoking a Fuse Online public API export endpoint. To copy exported integrations to another Fuse Online environment, invoke the Fuse Online public API import endpoint.
Endpoint for importing an integration
To import integrations, Fuse Online provides the following POST method endpoint:
/public/integrations
In the following example, the endpoint imports the integrations that are in the export.zip file and tags them for the testing environment:
/public/integrations -F data=@export.zip -F environment=testing --request POST
An import endpoint always imports the supplied integrations. That is, even if an integration has not changed since the last time it was imported, the endpoint still imports it.
Custom headers required by import endpoint
A command that invokes the import endpoint must specify these custom headers exactly as follows:
-
-H "Content-Type: multipart/form-data" -H "SYNDESIS-XSRF-TOKEN: awesome"The Fuse Online public API requires this header to authenticate the request.
-H 'Authorization: Bearer <token>'Replace
<token>with the secret token that you copied into a file when you created the OpenShift service account that is used to expose the Fuse Online public API.
Sample curl command that imports integrations
Following is an example of a curl command that invokes a Fuse Online API endpoint that imports integrations:
curl -v -k -L -H "Content-Type: multipart/form-data" -H "SYNDESIS-XSRF-TOKEN: awesome" -H 'Authorization: Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJzeW5kZXNpcyIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJzeW5kZXNpcy1jZC1jbGllbnQtdG9rZW4tMnZjNmwiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoic3luZGVzaXMtY2QtY2xpZW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNjUxMjYxNGMtMmYwMS0xMWU5LTk3OWEtNDI1YWNlMzY3MTcyIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OnN5bmRlc2lzOnN5bmRlc2lzLWNkLWNsaWVudCJ9.uKsri0JSKJDbgHoQwAhBJSNuWKwJgjegf2QlrCkhxVssSK1zIMZQaF9P5a4R7ZcWRnrZ_345UTqxYVeRlfHWVH0PqBkD-n7PAS9dcKJIFdS1jUHOmL1FTGgc3YW-bz1SlWT93tvK1EhorZ4_-EBfXhSAP4Uumi5qAg3_QUTMDstq233NSwBKYtFOw3Pp1ys3p3y0hcaiLMimeCH60vR4iWvptqqzc5QDigHiPySZNWxs_5awZlwdoIDvR-nSj690aC-49UKFgyEEdzdFU4bI2W4hOyDyhN9fVaIAZQKeJUrJBU-lnFTHI_NAd2OwzOEBpWZuj31Za5w9fU4kf4UDGA' https://public-syndesis.192.168.64.45.nip.io/api/v1/public/integrations -F data=@export.zip -F environment=testing --request POST
In this command:
- The URL at the end of the command identifies the Fuse Online environment to import integrations into.
-
The
export.zipfile contains the integrations to be imported. -
Specification of
environment=testingcauses the endpoint to mark each imported integration for thetestingenvironment. -
This command produces
multipart/form-data.
Chapter 7. Fuse Online public REST API endpoints reference
This section provides reference information for each Fuse Online public REST API endpoint. For additional information, see How to invoke Fuse Online public REST API endpoints.
The OpenAPI document that defines the public REST API endpoints is available in your Fuse Online environment at https://<fuse-online-host>/api/v1/openapi.json. However, this document defines the tags object as having three tags: public-api, extensions, and integration-support. Only the public-api tag is accessible when using the OpenShift public OAuth proxy process for Fuse Online. You should ignore the other two tags.
- Section 7.1, “Endpoint for obtaining the state of an integration”
- Section 7.2, “Endpoint for obtaining a list of an integration’s environment labels”
- Section 7.3, “Endpoint for marking an integration and keeping unspecified tags”
- Section 7.4, “Endpoint for marking an integration and removing unspecified tags”
- Section 7.5, “Endpoint for publishing an integration”
- Section 7.6, “Endpoint for stopping an integration”
- Section 7.7, “Endpoint for exporting integrations”
- Section 7.8, “Endpoint for importing integrations”
- Section 7.9, “Endpoint for removing an environment label from a particular integration”
- Section 7.10, “Endpoint for creating an environment label”
- Section 7.11, “Endpoint for obtaining a list of environment labels”
- Section 7.12, “Endpoint for changing an environment label”
- Section 7.13, “Endpoint for removing an environment label from all integrations”
- Section 7.14, “Endpoint for changing a connection’s properties”
7.1. Endpoint for obtaining the state of an integration
This endpoint returns the state of the specified integration. The state is Running, Stopped, Pending, or Error.
Method and endpoint
GET
/public/integrations/{id}/state
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| string | Required path parameter. Name or internal ID of the integration whose state you want to obtain. See How to find integration IDs. |
Request example
In the following example, the endpoint returns the state of the timer-to-log integration:
/public/integrations/timer-to-log/state
Produces
application/json
Response example
{"currentState":"Unpublished","stateDetails":{"id":"i-Lc0JLrsUFtBJfR_ylfEz:5","integrationId":"i-Lc0JLrsUFtBJfR_ylfEz","deploymentVersion":5,"detailedState":{"value":"BUILDING","currentStep":2,"totalSteps":4},"namespace":"syndesis","podName":"i-timer-to-log-5-build","linkType":"LOGS"}}`
7.2. Endpoint for obtaining a list of an integration’s environment labels
This endpoint returns the environment labels (tags) that have been applied to the specified integration.
Method and endpoint
GET
/public/integrations/{id}/tags
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| string | Required path parameter. Name or internal ID of the integration whose environment labels you want to obtain. How to find integration IDs. |
Request example
In the following example, the endpoint returns the environment labels for the timer-to-log integration:
/public/integrations/timer-to-log/tags
Produces
application/json
Response example
{"test":{"name":"test","releaseTag":"i-Lc5WI16UFtBJfR_ylggz","lastTaggedAt":1554887553159,"lastExportedAt":1554887330152,"lastImportedAt":1554888047271},"staging":{"name":"staging","releaseTag":"i-Lc5WI16UFtBJfR_ylgfz","lastTaggedAt":1554887553159}}
7.3. Endpoint for marking an integration and keeping unspecified tags
This endpoint uses the PATCH method to mark the specified integration for the specified environment(s). If the integration is already marked for a specified environment, the endpoint updates the timestamp for that environment label. If the integration was previously marked for an environment that is not specified in a new request, the endpoint leaves that tag in place and does not update its timestamp.
This PATCH endpoint is a convenience method for CI/CD tools because it adds tags without the need to remove any other existing tags. This is in contrast to the PUT endpoint, which marks the integration for specified environments and removes any tags for environments that are not specified in the request.
Method and endpoint
PATCH
/public/integrations/{id}/tags
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| string | Required. Name or internal ID of the integration that you want to mark for the specified environment(s). See How to find integration IDs. |
| Additional Parameters | ||
|
|
|
Specify the |
|
| string | Required. Specify one or more, comma-separated, environment labels, that you want to add to the specified integration. You must have already created the environment label; the endpoint cannot create a label. See Marking integrations for CI/CD. |
Request example
In the following example, the endpoint marks the timer-to-log integration for the test2 and test3 environments:
public/integrations/timer-to-log/tags --request PATCH -d '["test2","test3"]'
Produces
application/json
Response example
{"test2":{"name":"test2","releaseTag":"i-LcXydouUFtBJfR_ylgrz","lastTaggedAt":1555365010746},"test3":{"name":"test3","releaseTag":"i-LcXydouUFtBJfR_ylgsz","lastTaggedAt":1555365010746},"test":{"name":"test","releaseTag":"i-Lc5WI16UFtBJfR_ylggz","lastTaggedAt":1554887553159,"lastExportedAt":1554887330152,"lastImportedAt":1554888047271},"staging":{"name":"staging","releaseTag":"i-Lc5WI16UFtBJfR_ylgfz","lastTaggedAt":1554887553159}}
7.4. Endpoint for marking an integration and removing unspecified tags
This endpoint uses the PUT method to mark the specified integration for the specified environment(s). If the integration was previously marked for an environment that is not specified in the new request, the endpoint removes that environment label from the integration.
To mark an integration without removing unspecified environment labels, call the PATCH method endpoint instead.
Method and endpoint
PUT
/public/integrations/{id}/tags
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| string | Required. Name or internal ID of the integration that you want to mark. See How to find integration IDs. |
| Additional Parameters | ||
|
|
|
Specify the |
|
| string | Required. Specify one or more, comma-separated, environment labels. The endpoint marks the specified integration for these environments. You must have already created the environment label; the endpoint cannot create a label. See Marking integrations for CI/CD. |
Request example
In the following example, the endpoint marks the timer-to-log integration for the test2 and test3 environments. If the integration was previously marked for any other environments, the endpoint removes those tags from the integration.
public/integrations/timer-to-log/tags --request PUT -d '["test2","test3"]'
Produces
application/json
Response example
{"test2":{"name":"test2","releaseTag":"i-LcXyw7GUFtBJfR_ylgtz","lastTaggedAt":1555365085713},"test3":{"name":"test3","releaseTag":"i-LcXyw7GUFtBJfR_ylguz","lastTaggedAt":1555365085713}}
7.5. Endpoint for publishing an integration
This endpoint publishes the specified integration. If the integration is already running, then the endpoint stops the integration and re-publishes it.
Method and endpoint
POST
/public/integrations/{id}/deployments
| Name | Type | Description |
|---|---|---|
| Required Header Parameter | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameters | ||
|
| string | Required. Name or internal ID of the integration that you want to publish. See How to find integration IDs. |
Request example
In the following example, the endpoint publishes the timer-to-log integration.
/public/integrations/timer-to-log/deployments
Produces
application/json
Response example
In this example, the ellipsis indicates the omission of some of the response.
{"id":"i-Lc0JLrsUFtBJfR_ylfEz:8","version":8,"createdAt":1555365135324,"updatedAt":1555365135324,"userId":"system:serviceaccount:syndesis:syndesis-cd-client","currentState":"Pending","targetState":"Published","integrationId":"i-Lc0JLrsUFtBJfR_ylfEz", . .2c+PC9zdmc+","description":"Trigger events based on an interval or a cron expression","isDerived":false},"stepKind":"endpoint"},{"id":"-Lc0I7wqEVfKCDDHC8Jv","configuredProperties":{"bodyLoggingEnabled":"true","contextLoggingEnabled":"true"},"metadata":{"configured":"true"},"stepKind":"log","name":"Log"}]}],"continuousDeliveryState":{"test2":{"name":"test2","releaseTag":"i-LcXyw7GUFtBJfR_ylgtz","lastTaggedAt":1555365085713},"test3":{"name":"test3","releaseTag":"i-LcXyw7GUFtBJfR_ylguz","lastTaggedAt":1555365085713}}}}
7.6. Endpoint for stopping an integration
This endpoint stops the specified integration.
Method and endpoint
PUT
/public/integrations/{id}/deployments/stop
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| string | Required. Name or internal ID of the integration that you want to stop. See How to find integration IDs. |
Request example
In the following example, the endpoint stops the timer-to-log integration.
/public/integrations/timer-to-log/deployments stop
Produces
application/json
Response example
No content with a 204 status code
7.7. Endpoint for exporting integrations
This endpoint exports integrations. The default behavior is that the endpoint exports integrations that are marked for the specified environment and that have never been exported or that have not been exported since the last time that they were marked for that environment. You can specify options when you want to do either of the following:
- Export all integrations in a Fuse Online environment and tag them with the specified environment label.
- Export all integrations that are tagged with the specified environment label regardless of whether or not an integration was updated and tagged since the last time it was exported.
See also: Invoking the Fuse Online public API export endpoint.
Method and endpoint
GET
/public/integrations/{env}/export.zip
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| string | Required. Environment label that you created in the Fuse Online console. The endpoint exports the integrations that are marked for this environment. |
| Query Parameters | ||
|
| string | Optional. Specify this option to export all integrations that are in the Fuse Online environment. The endpoint exports the current version of each integration. If an integration is not already marked for the specified environment, then the endpoint adds the specified environment label to the integration. You must have already created the environment label; the endpoint cannot create a label. |
|
| string | Export all integrations tagged with the specified environment label. Do this regardless of whether or not an integration was edited and tagged since the last time the integration was exported. |
| Additional Parameter | ||
|
| string |
Required if you specify the query parameter. Without this option, the exported integrations are in a file named |
Request examples
In the first example, the endpoint exports integrations that have been marked for the test1 environment and that have never been exported or that have not been exported since the last time that they were marked for that environment.
/public/integrations/test1/export.zip
In the next example, the endpoint exports all integrations that have been marked for the test1 environment. It does not matter whether or not the integration was updated since the last time it was exported.
/public/integrations/test1/export.zip?ignoreTimestamp=true -o export.zip
In the last example, the endpoint ensures that each integration is marked for the test1 environment and returns all integrations in the export.zip file.
/public/integrations/test1/export.zip?all=true -o export.zip
Produces
application/octet-stream
Response
The export.zip file that contains the exported integration(s). The endpoint returns an HTTP status of 204 if there are no integrations to export.
7.8. Endpoint for importing integrations
This endpoint imports the integrations that are in the provided file. See also: Invoking the Fuse Online public REST API import endpoint.
Method and endpoint
POST
/public/integrations
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Additional Parameters | ||
|
| string | Required. This is the file that contains the integrations that you want to import. You must have previously invoked the export endpoint to obtain this file. |
|
| string | Required. Environment label that you want to add to each imported integration. You must have already created the environment label; the endpoint cannot create a label. |
Request example
In the following example, the endpoint imports the integrations that are in the export.zip file and marks them for the testing environment.
/public/integrations -F data=@export.zip -F environment=testing --request POST
Produces
multipart/form-data
Response example
The response is a list of the imported resources, which includes integrations and connections. In the following example, an ellipsis indicates that part of the response is omitted here.
{"lastImportedAt":1554888047271,"results":[{"id":"i-Lc0JLrsUFtBJfR_ylfEz","version":5,"createdAt":1554800274935,"updatedAt":0,"tags":["timer"],"name":"timer-to-log","flows":[{"id":"-Lc0I5AZEVfKCDDHC8Jv","steps":[{"id":"-Lc0I5jnEVfKCDDHC8Jv","configuredProperties":{"period":"900000"},"metadata":…"description":"Trigger events based on an interval or a cron expression","isDerived":false},"stepKind":"endpoint"},{"id":"-Lc0I7wqEVfKCDDHC8Jv","configuredProperties":{"bodyLoggingEnabled":"true","contextLoggingEnabled":"true"},"metadata":{"configured":"true"},"stepKind":"log","name":"Log"}]}],"continuousDeliveryState":{"staging":{"name":"staging","releaseTag":"i-Lc5WI16UFtBJfR_ylgfz","lastTaggedAt":1554887553159},"test":{"name":"test","releaseTag":"i-Lc5WI16UFtBJfR_ylggz","lastTaggedAt":1554887553159,"lastExportedAt":1554887330152,"lastImportedAt":1554887859824}}}]}
7.9. Endpoint for removing an environment label from a particular integration
This endpoint removes the specified environment label from the specified integration. The environment label itself continues to exist but it no longer marks the specified integration.
Method and endpoint
DELETE
/public/integrations/{id}/tags/{env}
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameters | ||
|
| string | Required path parameter. Name or internal ID of the integration that you want to unmark. See How to find integration IDs. |
|
| string | Required path parameter. Environment label that you want to remove from the specified integration. |
| Additional Parameter | ||
|
|
|
Specify the |
Request example
In the following example, the endpoint removes the dev1 environment label from the timer-to-log integration.
/public/integrations/timer-to-log/tags/dev1 --request DELETE
Response example
No content with a 204 status code
7.10. Endpoint for creating an environment label
This endpoint creates an environment label. No integrations are marked with this label until you explicitly mark them in the Fuse Online console or by invoking a public API endpoint.
Method and endpoint
POST
/public/environments/{env}
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| string | Required. Environment label that you want to create. |
Produces
Does not produce anything but responds as follows:
| Response | Description |
|---|---|
|
| Success. |
|
| The environment name you specified already exists. |
|
| The server is unable to fulfill the request. |
Request example
In the following example, the endpoint creates the dev1 environment label:
/public/environments/dev1 --request POST
The dev1 environment label now exists in the Fuse Online environment in which you invoked this endpoint. There are not yet any integrations that are marked with this label.
Response example
No content with response status code 204
7.11. Endpoint for obtaining a list of environment labels
This endpoint returns a list of environment labels that exist in the Fuse Online environment. You create environment labels in the Fuse Online console. See Managing environment labels for CI/CD.
Method and endpoint
GET
/public/environments[?withUses=true]
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| Boolean |
Optional. If the command specifies |
Produces
application/json
Request examples
/public/environmentsResponse example:
["env-label-1", "env-label-2"]/public/environments/?withUses=trueResponse example
[{"name":"env-label-1","uses":1},
{"name":"env-label-2","uses":0}]
7.12. Endpoint for changing an environment label
This endpoint changes an environment label. Integrations that were marked for the original environment label are now marked for the new environment label.
Method and endpoint
PUT
/public/environments/{env}
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| string | Required. Environment label that you want to change. |
| Additional Parameters | ||
|
| string | Required. Specify the new label for the environment. You must have already created the environment label; the endpoint cannot create a label. |
|
|
|
Specify the |
Request example
In the following example, the endpoint changes the dev1 environment label to dev2:
/public/environments/dev1 -d ‘dev2’ --request PUT
Integrations that were marked for the dev1 environment no longer have that tag. Those integrations are now marked for the dev2 environment.
Response example
No content with response status code 204
7.13. Endpoint for removing an environment label from all integrations
This endpoint removes the specified environment label from each integration to which it has been applied.
Method and endpoint
DELETE
/public/environments/{env}
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| string | Required. Environment label that you want to remove from integrations that have it. |
| Additional Parameter | ||
|
|
|
Specify the |
Request example
In the following example, the endpoint removes the dev1 tag from any integrations that have it:
/public/environments/dev1 --request DELETE
Response example
No content with response status code 204
7.14. Endpoint for changing a connection’s properties
This endpoint changes the properties of the specified connection. This is often useful after you import an integration that has connections that require configuration. For example, you might need to change the credentials that a connection uses.
Method and endpoint
POST
/public/connections/{id}/properties
| Name | Type | Description |
|---|---|---|
| Required Header Parameters | ||
|
|
| Media type that the endpoint requires. |
|
| Custom | Required for authentication. |
|
| Custom | Secret token for the OpenShift service account that exposes the Fuse Online public REST API. See Obtaining a secret token. |
| Path Parameter | ||
|
| string |
Required. Replace
|
Request example
The following example changes the properties of the PostgresDB connection. The new value of the user property is myuser, and the new value of the password property is mypassword:
/public/connections/PostgresDB/properties --request POST -d '{ "user": "myuser", "password": "mypassword" }'
Produces
application/json
Sample response
In this example, there is an ellipsis that indicates the omission of a large part of the response.
{"uses":0,"id":"i-LaOziUGpQE45nua4pfCz","name":"TODO app","configuredProperties":{"password":"»ENC:c2cb731046372a275b76beabc92aefa061f79b43fb791fb599d9e85ec0235a7e","basePath":"/api","host":"http://todo-syndesis.my-minishift.syndesis.io/","specification":…"userId":"admin","lastUpdated":1555365796629,"createdDate":1553066813379,"board":{"id":"i-Lbj4-vqUFtBJfR_ylfCz","metadata":{"connector-id":"i-LaOzcPZpQE45nua4pfBz","connector-version-latest":"1","connector-version-connection":"1"},"messages":[{"level":"WARN","code":"SYNDESIS007"}],"createdAt":1554494263030,"updatedAt":1554494263727,"targetResourceId":"i-LaOziUGpQE45nua4pfCz","notices":0,"warnings":1,"errors":0},"isDerived":false}
Chapter 8. Rebranding the Fuse Online user interface
You can rebrand Fuse Online by replacing the Fuse Online application name, logo, icons, and other user interface details. You do this by mounting customized resources as ConfigMap objects in the syndesis-ui deployment file.
Prerequisites
- Fuse Online is installed and running on OpenShift Container Platform on-site in a customer-managed environment.
-
The
occlient tool is connected to the OCP cluster in which Fuse Online is installed. - You have permission to install Fuse Online.
Procedure
Obtain the name of the
syndesis-uipod in which Fuse Online is installed by invoking the following command:oc get podsFetch customizable logos, icons, fonts, and backgrounds by invoking the following command and replacing SYNDESIS_UI_POD_NAME with the actual name of the pod that is running
syndesis-ui:oc rsync SYNDESIS_UI_POD_NAME:/opt/app-root/src/static/media ~/This puts user interface resources in the the
~/media/folder.-
Edit and save the file that contains the header logo, which is
~/media/syndesis_logo_full_darkbkg.9c467d96.svg. Upload the modified file to the cluster by creating a
ConfigMapobject that contains the updated logo file:cd ~/ oc create configmap syndesis-ui-custom-logo --from-file=media/syndesis_logo_full_darkbkg.9c467d96.svg
Modify the
syndesis-uideployment file to mount thesyndesis-ui-custom-logoConfigMapobject. Do this by invokingoc edit dc/syndesis-uior by using the OpenShift web console, selecting Applications > Deployments > syndesis-ui > Actions > Edit YAML.Under
spec.template.containers.volumeMounts, add the following:-name: syndesis-ui-custom-logo-volume mountPath: /opt/app-root/src/static/media/syndesis_logo_full_darkbkg.9c467d96.svg subPath: syndesis_logo_full_darkbkg.9c467d96.svg
Under
spec.template.volumes, add the following:-name: syndesis-ui-custom-logo-volume configMap: name: syndesis-ui-custom-logo
-
Save the
syndesis-uideployment file.
-
Repeat steps 3 through 5 for each file that is in the
`~/mediafolder and that you want to customize. Edit and save the file that contains the application title:
Create a directory in which to update the file:
mkdir ~/syndesis-custom/srcFetch the application title file by invoking the following command and replacing SYNDESIS_UI_POD_NAME with the actual name of the pod that is running
syndesis-ui:oc rsync SYNDESIS_UI_POD_NAME:/opt/app-root/src/index.html ~/syndesis-custom/src
Replace the application title. For example:
sed -i 's/<title>.*<\/title>/<title>NEW_TITLE<\/title>/g' ~/syndesis-custom/src/index.html
Upload the modified application title file to the cluster by creating a
ConfigMapobject that contains the updated file:cd ~/syndesis-custom/src oc create configmap syndesis-ui-custom-index --from-file=index.html
Modify the
syndesis-uideployment by mounting thesyndesis-ui-custom-indexConfigMapobject:Under
spec.template.containers.volumeMounts, add the following:-name: syndesis-ui-custom-vindex-olume mountPath: /opt/app-root/src/index.html subPath: index.html
Under
spec.template.volumes, add the following:-name: syndesis-ui-custom-index-volume configMap: name: syndesis-ui-custom-index
-
Save the
syndesis-uideployment file.
Results
Saving the syndesis-ui deployment file automatically redeploys Fuse Online with a user interface that reflects your changes. Subsequent re-deployments of Fuse Online also reflect your changes.