Red Hat Insights Remediations Guide
Fixing issues on RHEL systems by using remediation plans
Abstract
Chapter 1. Remediations overview
After identifying the highest remediation priorities in your Red Hat Enterprise Linux (RHEL) infrastructure, you can create and execute remediation plans to fix those issues.
Remediations enables you to address the following on your connected RHEL systems:
- Advisor recommendations
- Content advisories
- Vulnerability CVEs
- Failed compliance rules found by Red Hat Insights
You can remediate a single issue or a related group of issues by using a pathway in Insights. Pathways group multiple advisor recommendations under common actions for better efficiency. For more information, see Remediating pathways in Assessing RHEL Configuration Issues Using the Red Hat Insights Advisor Service.
For some issues, Red Hat Insights provides several different remediation paths.
When you create a remediation plan, Insights generates an Ansible Playbook to implement the required remediation actions and apply any required patches on affected systems in your RHEL infrastructure.
Some issues require a manual fix and cannot be resolved by executing a remediation plan in Insights. You can determine whether it’s possible to remediate a problem within Insights by checking the Resolution type value of the issue or recommendation.
Resolution types
In Insights, an issue or recommendation for remediation can be one of two types:
- Manual: Red Hat Insights provides the manual remediation steps needed to fix or address all issues and recommendations, including whether the system requires a reboot for the remediation to take effect.
Playbook: For many issues, Insights also provides a pre-built remediation playbook automating the required resolution steps, which you can either:
- Run on your systems from within Insights
- Download and run externally in your Ansible Playbooks environment
Insights remediations workflow
Choose an issue or recommendation
- The first step to creating a remediation plan is to choose an issue or recommendation that Red Hat Insights has detected on one or more of your RHEL systems.
Review the recommended resolution path
- Determine which versions of RHEL are affected and whether or not a playbook is available. You can only create a remediation plan in Red Hat Insights if a pre-built playbook exists.
Decide which RHEL systems to remediate
When you have reviewed the recommended resolution steps and determined whether a playbook is available to remediate the issue, choose which systems to include in the plan.
ImportantTo create a remediation plan for a group of systems, you must ensure that all systems in the group are running the same RHEL major and minor versions to ensure that the resolution applied by the Red Hat Insights-generated playbook is compatible.
Create a remediation plan
- The Insights UI provides a wizard to help you create a remediation plan, which is accessible from the advisor, compliance, vulnerability, and patch service pages. You can start the wizard for creating a remediation plan by clicking Plan remediation after you have selected at least one system and an issue or recommendation for remediation. You can also create a remediation plan from the details page of a system, provided Insights has detected issues that impact the system.
Decide how you want to execute your remediation plan
- You can execute a remediation plan from within Insights on directly connected Red Hat Enterprise Linux systems without additional subscriptions or tools. You can also download and run the associated playbook on your organization’s Ansible Automation Platform (AAP) workflow.
Subscription requirements
- Red Hat Insights for Red Hat Enterprise Linux is included with every RHEL subscription. No additional subscriptions are required to use Insights remediation features.
User requirements
- By default, all Insights users automatically have access to read, create, and manage remediation plans.
To remediate your Red Hat Enterprise Linux systems from Insights, you also need:
- Access to Insights for Red Hat Enterprise Linux on the Red Hat Hybrid Cloud Console (Hybrid Cloud Console).
- If using Red Hat Satellite, access to Satellite-managed systems on the console or in the Satellite application UI.
- The required Hybrid Cloud Console User Access roles for managing and executing remediation plans.
While all Insights users automatically have access to read, create, and manage remediation plans, to execute a remediation plan in Insights, you need the Remediations administrator predefined User Access role. User Access roles can be granted by your Organization Administrator in Identity & Access Management settings on the Hybrid Cloud Console.
Remote host connectivity
To execute remediations, you must set up and enable the remote host configuration (rhc) within Insights.
You will also need to permit Insights users to execute remediation playbooks on rhc-connected systems, which can be done by enabling the Remote Host Configuration Manager (rhc) setting in Insights, provided you have the required administrative permissions.
1.1. Getting started with remediations by using an interactive quick start
To help you get started with remediations, an interactive quick start is available in Insights on the Hybrid Cloud Console. The Creating and executing remediation plans quick start guides you through the process in under 10 minutes and provides links to additional resources.
Prerequisites
- You must have a Red Hat Hybrid Cloud Console account and be subscribed to the Insights for Red Hat Enterprise Linux services.
Procedure
- Log on to Red Hat Hybrid Cloud Console and then navigate to the Insights services.
To access the quick start, use one of the following steps:
- From within the Insights application: Go to Automation Toolkit > Remediation Plans, and then click Launch Quick Start in the upper right corner.
- From the Quick starts library: Go to RHEL Learning Resources.
1.2. User Access settings in the Red Hat Hybrid Cloud Console
User Access is the Red Hat implementation of role-based access control (RBAC). Your Organization Administrator uses User Access to configure what users can see and do on the Red Hat Hybrid Cloud Console (the console):
- Control user access by organizing roles instead of assigning permissions individually to users.
- Create groups that include roles and their corresponding permissions.
- Assign users to these groups, allowing them to inherit the permissions associated with their group’s roles.
1.2.1. Predefined User Access groups and roles
To make groups and roles easier to manage, Red Hat provides two predefined groups and a set of predefined roles:
Predefined groups
The Default access group contains all users in your organization. Many predefined roles are assigned to this group. It is automatically updated by Red Hat.
NoteIf the Organization Administrator makes changes to the Default access group its name changes to Custom default access group and it is no longer updated by Red Hat.
The Default admin access group contains only users who have Organization Administrator permissions. This group is automatically maintained and users and roles in this group cannot be changed.
On the Hybrid Cloud Console navigate to Red Hat Hybrid Cloud Console > the Settings icon (⚙) > Identity & Access Management > User Access > Groups to see the current groups in your account. This view is limited to the Organization Administrator.
Predefined roles assigned to groups
The Default access group contains many of the predefined roles. Because all users in your organization are members of the Default access group, they inherit all permissions assigned to that group.
The Default admin access group includes many (but not all) predefined roles that provide update and delete permissions. The roles in this group usually include administrator in their name.
On the Hybrid Cloud Console navigate to Red Hat Hybrid Cloud Console > the Settings icon (⚙) > Identity & Access Management > User Access > Roles to see the current roles in your account. You can see how many groups each role is assigned to. This view is limited to the Organization Administrator.
1.2.2. Access permissions
The Prerequisites for each procedure list which predefined role provides the permissions you must have. As a user, you can navigate to Red Hat Hybrid Cloud Console > the Settings icon (⚙) > My User Access to view the roles and application permissions currently inherited by you.
If you try to access Insights for Red Hat Enterprise Linux features and see a message that you do not have permission to perform this action, you must obtain additional permissions. The Organization Administrator or the User Access administrator for your organization configures those permissions.
Use the Red Hat Hybrid Cloud Console Virtual Assistant to ask "Contact my Organization Administrator". The assistant sends an email to the Organization Administrator on your behalf.
Additional resources
For more information about user access and permissions, see User Access Configuration Guide for Role-based Access Control (RBAC).
1.3. User Access roles for creating and executing remediation plans
To fix issues on your systems by using the Red Hat Insights remediation features, become familiar with the roles that provide the required access permissions for creating, managing, and executing remediation plans.
The following user access roles provide standard or enhanced access to remediation features in Insights:
Remediations user: The Remediations user role is included in the default access group. With this role, a user has permissions to:
- View existing remediation plans
- Create a remediation plan
- Delete a remediation plan
Remediations administrator: With this role, a user has permissions to:
- Do everything that a Remediations user can do
- Execute remediation plans on connected remote host systems from within Insights
For more information about user access and permissions, see User Access Configuration Guide for Role-based Access Control (RBAC).
Chapter 2. Enabling host communication with Insights
Before you can execute the playbooks in your remediation plans on remote systems from Red Hat Insights for Red Hat Enterprise Linux, your systems have to be able to communicate with Red Hat Insights.
- For Red Hat Enterprise Linux systems that are not managed by Red Hat Satellite, you should follow the procedure below to enable the rhc client on those systems.
- For systems that are managed by Satellite, you will configure Cloud Connector on the host servers for those systems.
2.1. Enabling the rhc client on systems directly managed by Insights
To be able to execute Ansible Playbooks from Insights for Red Hat Enterprise Linux, the rhc client must be enabled on the systems in your infrastructure. The rhc connect command does this by registering (RHEL8.6 and later, and 9.0 and later) systems with Red Hat Subscription Manager and Red Hat Insights, and enabling remote host configuration (rhc) features in Insights for Red Hat Enterprise Linux.
Prerequisites
- Sudo access on the Red Hat Enterprise Linux host system
Connect rhc on RHEL 8.5 systems
Remote host configuration on RHEL 8.5 has dependencies on ansible and rhc-worker-playbook. To install the dependencies, you must first register with Subscription Manager.
Use the following commands to enable rhc on RHEL 8.5 systems.
subscription-manager repos --enable ansible-2.9-for-rhel-8-x86_64-rpms dnf -y install ansible rhc-worker-playbook-0.1.5-3.el8_4 rhc connect
[root]# subscription-manager repos --enable ansible-2.9-for-rhel-8-x86_64-rpms [root]# dnf -y install ansible rhc-worker-playbook-0.1.5-3.el8_4 [root]# rhc connectCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Connect rhc on RHEL8.6 and later systems
Use the following commands to enable rhc on RHEL8.6 and later systems.
dnf -y update rhc dnf -y install rhc-worker-playbook rhc connect
[root]# dnf -y update rhc [root]# dnf -y install rhc-worker-playbook [root]# rhc connectCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Connect rhc on RHEL9.0 and later systems
Use the following commands to enable rhc on RHEL9.0 and later systems.
dnf -y install rhc rhc-worker-playbook rhc connect
[root]# dnf -y install rhc rhc-worker-playbook [root]# rhc connectCopy to Clipboard Copied! Toggle word wrap Toggle overflow
More information
- After enabling rhc, you can manage the configuration at Red Hat Hybrid Cloud Console > Red Hat Insights > Inventory > System Configuration > Remote Host Configuration (RHC).
- For complete rhc documentation, see Remote Host Configuration and Management.
2.2. Enabling Remote Host Configuration Manager in the Insights UI
To allow users to execute a remediation plan on a remote system from Red Hat Insights, you must configure the Remote Host Configuration Manager settings in the Insights UI.
Prerequisites
- You have the RHC Administrator and Inventory Hosts Administrator roles. If not, contact your Organization Administrator to obtain these permissions.
Procedure
- Navigate to Remote Host Configuration Manager.
- Under Permission, set the option Allow permitted Insights users to execute remediation playbooks on rhc-connected systems to Enabled.
- Click Save changes.
Results
A confirmation box with the message Changes saved displays at the top right corner of the UI.
2.3. Checking the connection status of host systems in the Insights UI
After setting up the Remote Host Configuration client (rhc connect) and enabling host communication, from the Red Hat Insights UI, verify that the host system is connected.
Prerequisites
- You are logged in to the Red Hat Hybrid Cloud Console.
You have the RHC Administrator and Inventory Hosts Administrator roles. If not, contact your Organization Administrator to obtain these permissions.
NoteTo execute a remediation plan on remote hosts from Insights, you also need the Remediations administrator role.
Procedure
- Navigate to Automation Toolkit > Remediation Plans.
- On the Remediation Plans page, choose a remediation plan that includes the system you are interested in checking. The General tab opens.
- Open the Systems tab, and locate the system in the table.
- Check the Connection Status value for the system.
If the Connection Status value is Unknown, this means you do not have the correct User Access permissions to view the status, as outlined in the prerequisites.
2.4. Enabling Cloud Connector for content hosts managed by Satellite
You can remediate issues on Satellite-managed content hosts remotely from the Insights for Red Hat Enterprise Linux UI in the Red Hat Hybrid Cloud Console. Remote remediation from Insights requires that you first configure the Cloud Connector plugin on the Satellite Server.
If you want to manage and execute host remediations entirely from the Satellite web console, you do not need to enable the Cloud Connector plugin.
The following prerequisites are comprehensive for Satellite Server configuration:
Prerequisites
- Satellite must be version 6.9 or later.
- You have root access to the Satellite server.
- The content hosts that are managed by the satellite should have the Insights client installed and turned on. See the reference section of this documentation for Insights client installation and enablement procedures.
- Import a Subscription Manifest into Satellite. For more information, see Importing a Subscription Manifest into Satellite Server in the Red Hat Satellite Content Management Guide.
- Register your hosts to Satellite using an activation key to attach Red Hat subscriptions. For more information, see Registering Hosts in the Red Hat Satellite Managing Hosts guide.
2.4.1. Configuring Cloud Connector and uploading your Satellite Server content host inventory to Insights
Before you can run the playbooks in your remediation plans remotely from within Red Hat Insights, you must install and configure the Cloud Connector plugin on the Satellite Server.
Complete the following tasks to install, configure, and verify the configuration of Cloud Connector.
Prerequisites
- You are logged in to the Red Hat Hybrid Cloud Console.
You have the RHC Administrator and Inventory Hosts Administrator roles. If not, contact your Organization Administrator to obtain these permissions.
NoteTo execute a remediation plan on remote hosts from Insights, you also need the Remediations administrator role.
Procedure
On Satellite Server, enable the
remote-executionplugin by entering one of the following commands, based on your version of Satellite Server.On Satellite Server 6.12 and later.
satellite-installer --foreman-proxy-plugin-remote-execution-script-install-key true
[root]# satellite-installer --foreman-proxy-plugin-remote-execution-script-install-key trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow *On Satellite Server 6.9 - 6.11
satellite-installer --foreman-proxy-plugin-remote-execution-ssh-install-key true
[root]# satellite-installer --foreman-proxy-plugin-remote-execution-ssh-install-key trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteConfiguring Cloud Connector requires that the satellite perform a remote execution on itself. This is why the first step is to enable the
remote-executionscript or plugin.
- In the Satellite Server web UI, navigate to Configure > Red Hat Cloud > Inventory Upload. Verify that the Automatic Inventory Upload switch is turned ON, which is the default setting.
Optionally: Toggle the Obfuscate host names switch to the ON position to hide hostnames that Satellite Server reports to the Hybrid Cloud Console.
NoteThe Obfuscate host names setting only affects
rh_cloudreports. If you want to obfuscate hostnames, IP addresses, or Media Access Control (MAC) addresses, configure obfuscation in the Insights client configuration. Satellite Server observes the Insights obfuscation configuration settings. For more information, see the following resources:- Obfuscating hostnames
- Obfuscating IP addresses.
- Obfuscating MAC addresses.
Automatic inventory upload and Obfuscate host names are global settings. They affect content hosts that belong to all organizations.
- Click Configure Cloud Connector. A Notice dialog box warns you that this action also enables auto reports upload.
- Click Confirm, and then wait for the task to finish. This should take about one minute.
Go to Monitor > Jobs > Configure Cloud Connector to see the job.
- Eventually, you will see the satellite in Red Hat Hybrid Cloud Console > the Settings icon (⚙) > Integrations, on the Red Hat tab. Allow up to one hour after the job is visible in the Satellite web console.
- The bottom of the Inventory Uploads page shows the name of your organization; hovering over it will turn the area gray.
- Click Restart to generate a data payload from each of the content hosts that have Insights client running, and upload your host inventory to Insights for Red Hat Enterprise Linux.
- Repeat the previous step for each organization for which you want to upload a content host inventory.
- Under Configure > Red Hat Cloud (after Sat 6.11) > Insights, set Auto sync for the organization by using the toggle in the upper right corner of the screen.
Verification steps
To verify that the upload was successful, log in to Red Hat Hybrid Cloud Console > Red Hat Enterprise Linux > Red Hat Insights > Inventory and search for the satellite_id tag for your content hosts.
Optional: Push the Sync inventory status button and wait for the task to finish. It will show you the number of content hosts recognized by Insights inventory.
Chapter 3. Creating a remediation plan in Insights
You can create a remediation plan to fix one or more issues identified by Red Hat Insights for a system or group of RHEL systems in your organization.
To create a remediation plan in Insights, you need to do the following:
- Find an issue to resolve
- Review the recommended remediation steps
- Select the systems to remediate
You can create a remediation plan to address recommendations and issues found by the following services of Insights:
- advisor
- compliance
- vulnerability
- patch
You can start the wizard for creating a remediation plan by clicking the Plan remediation button after you have selected at least one system and an issue or recommendation for remediation. You can also start the Plan remediation wizard from the Insights Inventory details page for a system, provided Insights services have detected any issues that impact the system.
The workflow to create a remediation plan is similar for all services in Insights for Red Hat Enterprise Linux that support remediations. For more information, see Insights remediations workflow in the Remediations overview section.
Some of the recommended paths to remediate an issue require manual actions and do not have an associated Ansible Playbook. In the Insights UI, you will see that those issues or recommendations have a Remediation type value of Manual.
You can create a remediation plan for any Insights recommendations or remedial actions that have a Remediation type value of Playbook.
When you create a remediation plan, Insights generates an Ansible Playbook from the built-in play for that issue to implement the required remediation actions and the reboot instructions on the selected host systems.
3.1. Creating a remediation plan to remediate an advisor service recommendation
Advisor recommendations
The advisor service assesses and monitors the health of your Red Hat Insights for Red Hat Enterprise Linux infrastructure and provides recommendations to address availability, stability, performance, and security issues. Red Hat Insights detects the systems in your infrastructure that are impacted and provides a set of recommended actions that can help you prioritize and plan how to remediate your systems.
For more information about the Red Hat Insights advisor service, see Assessing RHEL Configuration Issues Using the Red Hat Insights Advisor Service.
To create a remediation plan that addresses a recommendation generated by the Insights advisor service, complete the following procedure.
Prerequisites
You are logged into the Red Hat Hybrid Cloud Console.
NoteBy default, all Insights users have permissions to create remediation plans. However, you will need the Remediations administrator role to execute a remediation plan on remote hosts from Insights. For more information, see the Required permissions for remediation plan execution.
Procedure
Choose an Insights advisor service recommendation to remediate:
- Navigate to Operations > Advisor > Recommendations.
- Review the Recommendations table to see which recommendations are applicable for your systems and whether they have a playbook already created.
Use the search and filtering function in the table to sort the items by Resolution type.
ImportantLook for recommendations that have a Resolution type of Playbook. You cannot create a remediation plan if the Resolution type is set to Manual.
- Click the recommendation name. The full details of the recommendation are displayed, and a list of impacted systems is displayed on the lower part of the page.
Select which systems to include in the remediation plan:
- Scroll to view all of the registered RHEL systems that are impacted by the recommendation.
Find the systems to include. If needed, use the search and filter functions in the table. For example, you can use the filtering options to list the affected systems by version.
ImportantTo create a remediation plan for a group of systems, all systems in the group must be running the same RHEL major and minor versions to ensure that the resolution applied by the Red Hat Insights-generated playbook is compatible.
- Select at least one system to include in a remediation plan by clicking the checkbox to the left of the system ID.
Create and save the plan:
- Click Plan remediation to start the wizard.
Select Create new playbook, and enter a name for the playbook.
NoteYou can also add this recommendation or the selected systems to an existing remediation plan by choosing Add to existing playbook, and then selecting the plan name from the list presented.
- Under Review systems, review the systems included in the plan, and if applicable, clear the checkbox next to any systems that you do not want to include.
- Click Next.
Under Review and edit actions, review the resolution steps for the action. Some actions will present different steps that you can choose from in the wizard. Complete one of the following steps:
If the action has a choice of methods to remediate:
- Select Review and/or change the resolution steps for this 1 action, and click Next.
- Choose one of the step choices, and click Next.
- If there are no choices to be made and you are satisfied with the actions for this plan, select Accept all recommended resolution steps for all actions, and then click Next.
On the Remediation review pane, review the summary of your remediation plan and use the back button to make changes if needed.
NoteIf a reboot is required to fix the issue or risk, all systems in the remediation plan will be automatically rebooted. If you prefer to reboot manually after the plan has been executed, toggle the Auto-reboot button accordingly.
- Click Submit.
Verification steps
- Navigate to Automation Toolkit > Remediation Plans.
- Search for your remediation plan in the table. Click the remediation plan to open the plan.
3.2. Creating a remediation plan to remediate a CVE vulnerability on RHEL systems
Create a remediation plan in the Red Hat Insights vulnerability service. The workflow to create a remediation plan is similar for other services in Insights for Red Hat Enterprise Linux. When you create a remediation plan, Insights uses Ansible Playbooks to remediate or mitigate CVE vulnerabilities on your systems and apply any required patches.
The Red Hat Insights advisor service analyzes and detects which systems in your organization are affected by known problems.
Prerequisites
You are logged into the Red Hat Hybrid Cloud Console.
NoteBy default, all Insights users have permissions to create remediation plans. However, you need the Remediations administrator role to execute a remediation plan on remote hosts from Insights. For more information, see Required permissions for remediation plan execution.
Procedure
- Navigate to the Security > Vulnerability > CVEs page.
- Set the filters as needed and select a CVE.
- Scroll down to view all of the affected systems. Use the filtering options to list the affected systems by version.
Select systems to include in a remediation plan by clicking the box to the left of the system ID.
ImportantTo create a remediation plan for a group of systems, all systems in the group must be running the same RHEL major and minor versions to ensure that the resolution applied by the Red Hat Insights-generated playbook is compatible.
- Click Plan remediation.
Choose whether to add the remediations to an existing or new remediation plan, and then do one of the following actions, and then click Next:
- Click Add to existing playbook, and then select a remediation plan from the list presented.
- Click Create new playbook, and enter a name for the playbook.
Review the systems to include in the remediation plan, then click Next.
NoteOnly affected systems can be selected and included in a remediation plan.
Review the information under the remediation review summary.
- If a reboot is required to fix the issue or risk, all systems in the remediation plan will be automatically rebooted. If you prefer to reboot manually after the plan has been executed, toggle the Auto-reboot button accordingly.
- Click Submit.
Verification steps
- Navigate to Automation Toolkit > Remediation Plans.
- Search for your remediation plan. You should see the plan that you just created showing in the list.
3.2.1. Remediating CVEs with security rules when recommended and alternate resolution options exist
Most CVEs in Red Hat Insights for RHEL will have one remediation option for you to use to resolve an issue. Remediating a CVE with security rules might include more than one resolution from which to choose. For example, you might have a recommended action to take, and one or more alternate resolutions. The workflow to create remediation plans for CVEs that have one or more resolution options is similar to the remediation steps in the advisor service.
For more information about security rules, see Security rules and Filtering lists of systems exposed to security rules in Assessing and Monitoring Security Vulnerabilities on RHEL Systems .
Prerequisites
You are logged into the Red Hat Hybrid Cloud Console.
NoteBy default, all Insights users have permissions to create remediation plans. However, you will need the Remediations administrator role to execute a remediation plan on remote hosts from Insights. For more information, see the Required permissions for remediation plan execution.
Procedure
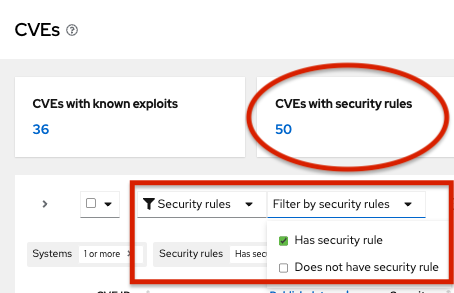
- Navigate to Security > Vulnerability > CVEs.
Set filters if needed (for example, filter to see CVEs with security rules to focus on issues that have elevated risk associated with them). Or, click the CVEs with security rules tile on the dashbar.
- Click a CVE in the list.
Scroll to view affected systems, and select the systems you want to include in a remediation plan by clicking the box to the left of the system ID on the Review systems page. When you select at least one system, the Plan remediation button gets activated.
NoteRecommended: Include systems of the same RHEL major or minor version by filtering the list of affected systems.
- Click Plan remediation.
Decide whether to add the selected remediations to an existing or new remediation plan by taking one of the following actions:
- Click Add to existing playbook and select the required playbook from the dropdown list.
- Click Create new playbook, and add a playbook name.
Click Next. The systems impacted by the CVE are listed.
NoteOnly impacted systems can be selected and included in a remediation plan.
- Review the systems to include in the playbook and clear the checkbox beside any systems that you do not want to include.
Click Next to see the Review and edit actions page, which shows you options to remediate the CVE. The number of items to remediate can vary. You will also see additional information (that you can expand and collapse) about the CVE, such as:
- Action: Shows the CVE ID.
- Resolution: Displays the recommended resolution for the CVE and also confirms whether you have alternate resolution options.
- Reboot required: Confirms whether you must reboot your systems.
- Systems: Confirms the number of systems you are remediating.
On the Review and edit actions page, choose one of two options to finish creating your remediation plan and to generate the Ansible Playbook:
Option 1: To review all of the recommended and alternative remediation options available (and choose one of those options):
- Select Review and/or change the resolution steps for this 1 action or similar based on your actual options.
- Click Next.
- On the Choose action: <CVE information> page, click a tile to select your preferred remediation option. The bottom edge of the tile highlights when selected. The recommended solution is highlighted by default.
- Click Next.
Option 2: To accept all recommended remediations:
- Choose Accept all recommended resolution steps for all actions.
- Click Next.
On the final Remediation review pane, review the summary of your remediation plan and use the back button to make changes to the actions or resolution options if required.
NoteIf a reboot is required to fix the issue or risk, all systems in the remediation plan will be automatically rebooted. If you prefer to reboot manually after the plan has been executed, toggle the Auto-reboot button accordingly.
- Click Submit.
Results
A notification confirming the total number of remediation actions and other information about your remediation plan is displayed.
Next steps
To view your remediation plan:
- Navigate to Automation Toolkit > Remediation Plans.
- Search for your remediation plan.
- To execute your remediation plan and run the generated Ansible Playbook on the affected systems, see Executing remediation playbooks from the Insights UI.
Chapter 4. Viewing and managing your remediation plans
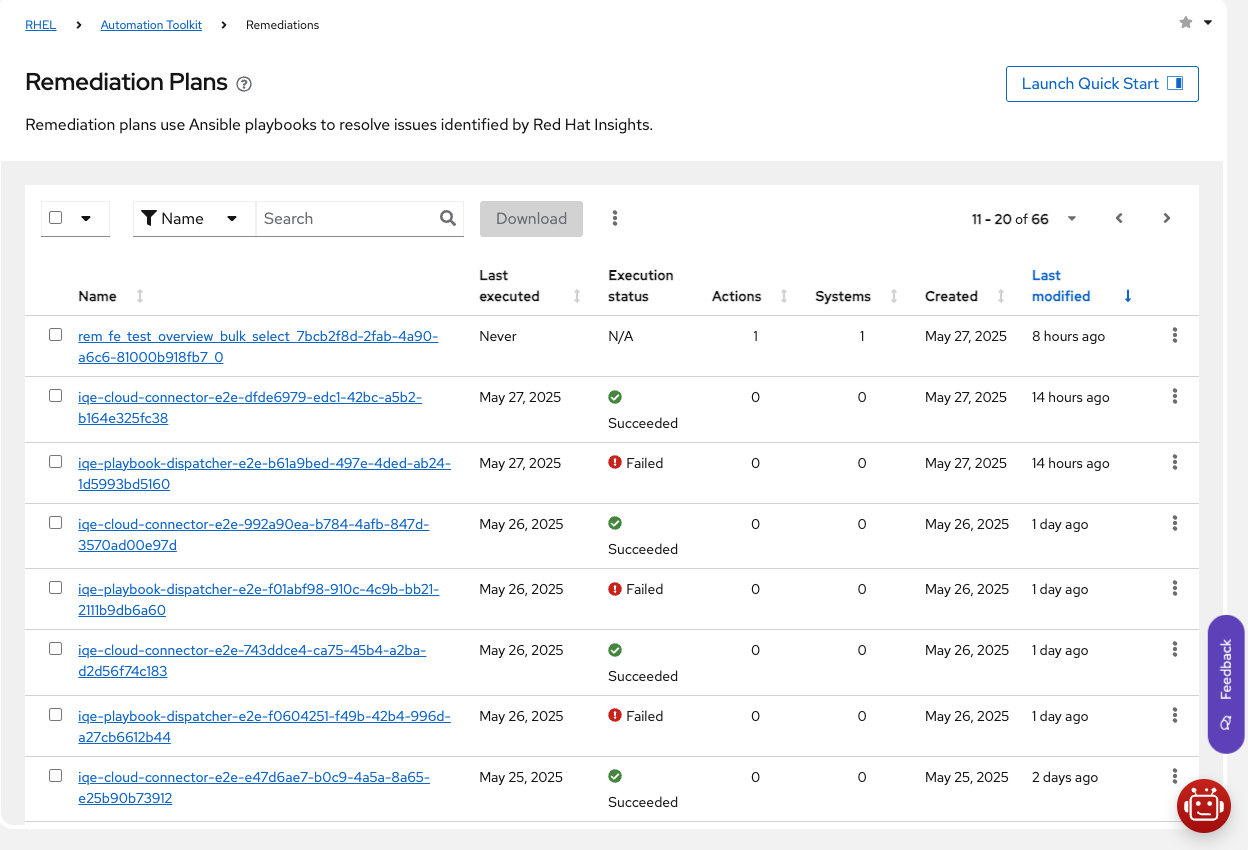
Red Hat Insights provides a central location under Automation Toolkit > Remediation Plans to help you find, view the full details of, and manage the remediation plans that have been created for your organization. You can also download, delete, or modify your remediation plans from the main Remediation Plans page.
You cannot create a remediation plan from Automation Toolkit > Remediation Plans. To create a new remediation plan, you must use the Red Hat Insights service that generated the recommendation and the underlying Ansible Playbook, such as the advisor, compliance, or vulnerability service.
For more information, see Creating a remediation plan in Insights.
4.1. Viewing remediation plans
The Remediation Plan view provides a comprehensive overview of all remediation plans created for your organization in Insights.
- You can access this view by navigating to the Automation Toolkit page and selecting Remediation Plans.
The table view in Remediation Plans provides a quick overview of all remediation plans, including their status and last execution date.
From here, you can search, sort, and filter the list of all of the remediation plans for your organization. For example, you can also filter the table to show only specific remediation plans based on criteria such as status.
By default, the columns in the table contain the following information:
- Name: The name of the remediation plan.
- Last Executed: The date and time when the remediation plan was last executed.
- Execution Status: The latest execution status of the remediation plan, for example, successful or failed. N/A indicates that the remediation plan has not been executed yet.
- Actions: The number of actions to be run when the remediation plan is executed.
- Systems: The number of systems that the remediation plan is selected to run on.
- Created: The date and time when the remediation plan was created.
- Last Modified: The date and time when the remediation plan was last modified.
4.1.1. Customizing the Remediation Plan table
Table view of all remediation plans
You can customize the Remediation Plan table to suit your needs. You can add or remove columns and sort the table by any column.
- Click Modify Columns to select which columns to display in the table.
- You can also restore the default view by clicking Reset to Default.
4.1.2. Viewing the details and execution history of a remediation plan
When you select and click a remediation plan in the table view, all of the available details about the plan are displayed on the following tabs:
- General: Displays the remediation plan status, summary details, and execution readiness checklist results. The summary details include name, date created, last modified date, latest execution status, total number of actions and systems included, and auto-reboot configuration.
- Actions: Displays a table listing the actions included in the plan.
- Systems: Displays a table listing the systems included in the plan.
- Execution History: A timeline of all executions of the remediation plan, including the dates, status, history, and links to the logs of a plan execution for each included system. From here, you can see any errors that occurred during execution.
You can also download and view the associated playbook by clicking on the Download button.
4.2. Downloading remediation plans
You can download the generated playbooks for each remediation plan in your organization. When you download a remediation plan, the YAML file for the underlying Ansible Playbook is saved to the preferred download directory on your local browser client.
You might need to download a remediation plan for the following reasons:
- To execute a remediation plan on your host systems by using the external Ansible Automation Platform (AAP) workflow for your organization instead of from within the Red Hat Insights application.
- To view the specific plays of a remediation plan.
- To troubleshoot issues with executing a remediation plan.
Procedure
- Navigate to Automation Toolkit > Remediation Plans.
- Select the checkbox next to the name of the remediation plan you want to download.
Complete one of the following steps:
-
To download a single remediation plan, go to the end of the row, click More options
 > Download.
> Download.
- To download multiple remediation plans in bulk, click the Download button at the top of the table.
-
To download a single remediation plan, go to the end of the row, click More options
Results
A message is displayed to confirm that the download was a success, and a YAML file for each of the selected remediation plans is downloaded to your local drive.
4.3. Deleting remediation plans
You can permanently delete remediation plans that are no longer needed.
You cannot recover a deleted remediation plan. Also, you cannot archive and restore a remediation plan from the Insights UI.
Procedure
- Navigate to Automation Toolkit > Remediation Plans.
- In the table, find the plan you want to delete.
-
At the end of the row, click the More options
 icon, and then click Delete.
icon, and then click Delete.
- When prompted, click Delete to confirm the permanent removal of the plan.
Results
A message is displayed to confirm the successful deletion of the selected remediation plan.
4.4. Renaming a remediation plan
Use the following procedure to rename an existing remediation plan in your organization.
Procedure
- Navigate to Automation Toolkit > Remediation Plans.
- In the table, find the plan you want to rename.
-
At the end of the row, click the More options
 icon, and then click Rename.
icon, and then click Rename.
- When prompted, enter a unique title for the plan name and click Rename.
Verification steps
A message is displayed to confirm the successful renaming of the selected remediation plan.
4.5. Modifying the actions in a remediation plan
After you create a remediation plan, you might later want to remove an action or system from the plan, especially if the plan contains many items.
4.5.1. Adding a new recommendation action to an existing remediation plan
If the Red Hat advisor or other service recommends a new remedial action for one or more systems in your organization, you can add that recommendation to an existing remediation plan.
Complete the following steps to add a new recommendation to an existing remediation plan.
- Navigate to Operations > Advisor > Recommendations to view the status of a remediation plan.
In the table, use the search and filtering options to find the recommendation you want to add.
ImportantThe recommendation must have a Resolution type of Playbook. You cannot create a remediation plan if the Resolution type is Manual.
- Click the recommendation name.
- Select at least one impacted system to remediate, and click Plan remediation.
- Select the option to Add to existing playbook, and then select the remediation plan name from the list presented. Click Next.
- Review the systems in the plan, and if applicable, clear the checkbox next to any systems that you do not want to include.
- Click Next.
- Review the remedial actions of your plan and adjust if necessary. When you are satisfied, click Next.
On the final Remediation review pane, review the summary of your remediation plan, and click Back to make changes, if needed.
NoteThe Auto-reboot button is enabled if any of the recommended actions to remediate require a system reboot to take effect. If you prefer to reboot manually after the plan has been executed, toggle the Auto-reboot button accordingly.
- Click Submit.
Verification steps
- Navigate to Automation Toolkit > Remediation Plans.
- Search for the remediation plan you just created, and click the name to open the details.
- Click Actions to view the remedial actions included in the plan. The recommendations that you just added are listed.
4.5.2. Removing a remedial action from a remediation plan
Complete the following steps to remove an action from a remediation plan.
Procedure
- Navigate to Automation Toolkit > Remediation Plans. The remediation plans for your organization are displayed.
- Find the remediation plan that you want to change.
- Click the name of the remediation plan to display the details of the plan.
- Navigate to the Actions tab.
In the table, do one of the following:
- Select the checkbox next to the actions that you want to remove, and click the Remove button at the top of the table.
-
Find a single action to remove, go to the end of the corresponding row, and click the More options icon
 and click Remove.
and click Remove.
- When prompted, click Remove.
Results
A message is displayed to confirm that the action was successfully removed from the remediation plan.
4.5.3. Adding more systems to an existing remediation plan
After creating a remediation plan, you might decide to include more systems.
You must ensure that all systems in the remediation plan are running the same RHEL major and minor versions to ensure that the resolution applied by the Red Hat Insights-generated playbook is compatible.
Complete the following steps to add more systems to an existing remediation plan.
- Navigate to Operations > Advisor > Recommendations.
- Use the search and filtering options to find the recommendation in the existing plan.
- Click the recommendation name.
- Select the systems you want to add to the plan, and then click Plan remediation.
- Select the option to Add to existing playbook, and then select the existing remediation plan name from the list presented. Click Next.
- Review the systems in the plan, and if applicable, clear the checkbox next to any systems that you do not want to include. Click Next.
- Review the remedial actions of your plan and adjust if necessary, as outlined in the section titled Creating a remediation plan to remediate an advisor service recommendation. Click Next.
On the final Remediation review pane, review the summary of your remediation plan and use the back button to make changes if required.
NoteThe Auto-reboot button is enabled if any of the recommended actions to remediate require a system reboot to take effect. If you prefer to reboot manually after the plan has been executed, toggle the Auto-reboot button accordingly.
- Click Submit.
Verification steps
- Navigate to Automation Toolkit > Remediation Plans.
- Search for your remediation plan in the table, and click the name to open the remediation plan.
- Click Systems to view a list of the systems included in the plan. The systems you added should be listed.
4.5.4. Removing a system from a remediation plan
Complete the following steps to remove a system from a remediation plan.
- Navigate to Automation Toolkit > Remediation Plans.
- Find the remediation plan that you want to remove a system from.
- Click the name to open the details of the remediation plan.
- Navigate to the Systems tab.
In the table, complete one of the following steps:
- Select the checkbox next to the systems that you want to remove, and click the Remove button above the table.
-
Find a single system to remove, go to the end of the corresponding row, and click More options
 > Remove.
> Remove.
- When prompted, click Remove.
Results
A message is displayed to confirm that the system was successfully removed from the remediation plan.
4.6. Monitoring remediation status
You can view the latest execution status and activity for each remediation plan that you execute from the Red Hat Insights application. You can also view the execution logs for the remediation plan and see the results of the Ansible Playbook execution.
Prerequisites
- You are logged into the Insights UI with Remediations user permissions.
Procedure
- Navigate to Automation Toolkit > Remediation Plans.
- In the table, find the plan that you want to monitor.
Click the name of the remediation plan to open the Plan details and status card on the General tab. The latest execution status of the remediation plan is displayed.
NoteA status of N/A indicates that the remediation plan has not yet been executed from within Insights.
- Optional: Go to the Execution History tab to view the progress or status status of the execution on each individual system included in the plan including links to more detailed execution activity logs.
Next steps
To monitor the status of a playbook in the Satellite web UI, see Monitoring Remote Jobs in the Red Hat Satellite Managing Hosts guide.
Chapter 5. Executing remediation plans
After you create a remediation plan, you can download and run the generated playbook by using your organization’s Ansible Automation Platform (AAP) workflow, or you can execute the playbook on remote systems from the Insights for Red Hat Enterprise Linux application.
5.1. Executing remediation plans from the Insights UI
You can execute the playbooks generated by your remediation plans from the Insights UI on the Red Hat Hybrid Cloud Console, if you have the required permissions and pass the readiness check.
Execution readiness check
When you open a remediation plan in the Insights UI, a readiness check is automatically activated. The readiness check ensures that you have completed the prerequisites necessary to execute the playbook on the systems that are included in the plan.
The results of the readiness check display in the Execution readiness section of the remediation plan details, along with some hints to help you understand which prerequisites were not met.
If the readiness check fails, the Execute button is disabled. This does not necessarily mean that there is an issue with your plan. It could mean that there is an issue connecting to the remote host or that you do not have the required permissions to connect and trigger the execution readiness checks.
Required permissions for remediation plan execution
You need the Remediations administrator role to execute a remediation plan on remote hosts from Insights.
The Remediations administrator role is a predefined role created and granted by your Organization Administrator in the Identity and Access Management (IAM) settings on the Red Hat Hybrid Cloud Console.
- The Remediations user role does not have the required permissions to execute remediation plans on remote systems. The Remediations administrator role permits access to all remediations capabilities and also allows you to discover whether your systems are connected.
- If you do not have the required permissions, the connection status for your system will be set to Unknown, even though you can connect to that system for other use cases in the console.
- The Remediations administrator role is not a default role. You must create the group and add yourself to the group. For more information about User Access permissions, see Managing group access with roles and members.
Prerequisites
To pass the remediations execution readiness check, ensure the following prerequisites are met:
- You can log on to the Red Hat Hybrid Cloud Console.
- Your user account is a member of a User Access group with the Remediations administrator role, as outlined earlier in this section.
- You have completed the steps in Enabling host communication with Insights
- The option Allow permitted Insights users to execute remediation playbooks on rhc-connected systems is enabled on the Remote Host Configuration Manager page in the Insights UI.
To execute a remediation plan on one or more directly connected RHEL systems, complete the following steps from the Insights UI.
Procedure
- Navigate to Automation Toolkit > Remediation Plans.
- Scroll through the list and find a remediation plan.
- Click the name to open the Remediation plan details view.
Click Execute.
ImportantIf the Execute button is disabled, this means that the execution readiness check failed because one of the requirements was not met. To help you troubleshoot and complete the execution readiness check successfully, see Execution readiness check.
- When prompted, click Execute playbook on systems. The playbook runs on the systems included in the remediation plan.
A remediation plan with a large number of actions to execute on many systems might take a while to complete.
Next steps
- To monitor the progress, go to the Execution History tab for the plan you just executed. The Execution History tab displays the status, history and links to the logs of a plan execution for each included system.
- When the remediation plan is successfully executed, find and open the recommendation or issue that your remediation plan addressed, and verify that the impacted systems you remediated are no longer in the list.
5.2. Executing remediations from the Satellite UI
You can also remediate using the Satellite UI.
Prerequisites
- You are a Cloud Administrator.
- You are a Remediations Administrator.
- You have completed Host registration by using the Insights client.
For specific instructions, see Creating an Insights Remediation Plan for Hosts in the Satellite Managing Hosts documentation.
When you introduce a new host into your Satellite inventory, by means of provisioning or registration, two automatic background tasks will initiate. It will take 24 hours for these tasks to complete. This is a typical time frame for the automatic synchronization.
If you identify security issues or another scenario that warrants not waiting 24 hours for the automatic sync, you can manually synchronize by clicking the sync button in the UI. This manual sync will complete in a few minutes.
To see the procedures for enabling automatic and manual synchronization, see the Configuring Synchronization of Insights Recommendations for Hosts in the Satellite documentation.
Chapter 6. Reference
The following information is provided to help you create, configure, and manage remediation plans in Red Hat Insights, including their associated playbooks.
6.1. Installing the Insights client on Satellite Server content hosts
The Insights client comes preinstalled on most versions of Red Hat Enterprise Linux; however, if you have to install it, use this procedure to install the Insights client on each system.
Prerequisites
Register your hosts to Satellite
- If you already have Red Hat Enterprise Linux hosts, you can use the Global Registration Template to register them to Satellite. For more information, see Registering Hosts in the Satellite documentation.
Procedure
Install the Insights for Red Hat Enterprise Linux client:
yum install insights-client
# yum install insights-clientCopy to Clipboard Copied! Toggle word wrap Toggle overflow Register the host to Insights for Red Hat Enterprise Linux:
insights-client --register
# insights-client --registerCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Repeat these steps on each host.
Alternatively, you can use the RedHatInsights.insights-client` Ansible role to install the Insights client and register the hosts. For more information, see Monitoring hosts by using Red Hat Insights in the Red Hat Satellite Managing Hosts guide.
6.2. Configuring Cloud Connector after upgrading Satellite Server 6.10 to 6.11
After you upgrade your Satellite Server, configure Cloud Connector to complete the upgrade process.
The following information applies to upgrades from Satellite Server version 6.10 to 6.11.
For more information, see Upgrading and Updating Red Hat Satellite.
Procedure
To configure Cloud Connector after upgrading the Satellite Server, click Configure Cloud Connector from Configure > RH Cloud - Inventory Upload to enable it on the new version of Satellite Server. Simultaneously, you must remove the previous source from the cloud manually on the Red Hat Hybrid Cloud Console after upgrading your Satellite Server.
Results
Once the Cloud Connector is configured, it will remove the receptor bits and install the RHC bits. At the same time, the Cloud Connector announces all the organizations in the Satellite to the source and is ready to receive the connections.
6.3. Disabling direct remediations on a Satellite Server content host
The enable_cloud_remediations setting in Satellite controls whether your hosts can be directly remediated through the Red Hat Insights console. When the value of enable_cloud_remediations is set to False, direct remediation from Insights is disabled for that specific host. The parameter is not set for your systems, which means that by default, direct remediation is enabled with Cloud Connector.
All hosts in the organization inherit the value that is set for enable_cloud_remediations.
For information about how to enable automatic and manual synchronization, see the Configuring Synchronization of Insights Recommendations for Hosts in the Satellite documentation.
When Satellite receives the request to run the remediation plan’s playbook from Cloud Connector, the request includes a list of hosts on which to execute the playbook.
Complete the following steps to ensure the playbook run does not get invoked from the cloud on a single host.
Procedure
- Go to Hosts menu > All Hosts in the Satellite web UI.
- Locate the host, and click Edit > Parameters.
-
Set the
enable_cloud_remediationsparameter to False.
6.4. Disabling direct remediation on a Satellite Server content host group
The enable_cloud_remediations setting in Satellite controls whether your host group can be directly remediated through the Red Hat Insights console. When the value of enable_cloud_remediations is set to False, direct remediation from Insights is disabled for the host group. The parameter is not set for your systems, which means that by default, direct remediation is enabled with Cloud Connector.
All hosts in your organization inherit the same parameters.
Prerequisites
If you are an Organization Administrator, you can disable remediations for the entire organization or host group by changing the Global Parameters in the Red Hat Satellite UI, as follows:
Procedure
- Navigate to the Satellite Dashboard.
- Click Configure > Global Parameters > Create Parameter.
-
In the Name field, enter
enable_cloud_remediations. -
In the Value field, enter
false. - Click Submit.
Verification steps
- Check to see whether your new parameter is listed in the Global Parameters table. For more information about configuring global parameters, see the Parameters section of the Red Hat Satellite documentation.
Providing feedback on Red Hat documentation
We appreciate and prioritize your feedback regarding our documentation. Provide as much detail as possible, so that your request can be quickly addressed.
Prerequisites
- You are logged in to the Red Hat Customer Portal.
Procedure
To provide feedback, perform the following steps:
- Click the following link: Create Issue
- Describe the issue or enhancement in the Summary text box.
- Provide details about the issue or requested enhancement in the Description text box.
- Type your name in the Reporter text box.
- Click the Create button.
This action creates a documentation ticket and routes it to the appropriate documentation team. Thank you for taking the time to provide feedback.