Configuring Capsules with a load balancer
Distribute load among Capsules
Abstract
Providing feedback on Red Hat documentation
We appreciate your feedback on our documentation. Let us know how we can improve it.
Use the Create Issue form in Red Hat Jira to provide your feedback. The Jira issue is created in the Red Hat Satellite Jira project, where you can track its progress.
Prerequisites
- Ensure you have registered a Red Hat account.
Procedure
- Click the following link: Create Issue. If Jira displays a login error, log in and proceed after you are redirected to the form.
- Complete the Summary and Description fields. In the Description field, include the documentation URL, chapter or section number, and a detailed description of the issue. Do not modify any other fields in the form.
- Click Create.
Chapter 1. Overview of load balancing in Satellite
You can configure your Satellite environment to use a load balancer to distribute host requests and network load across multiple Capsule Servers. This results in an improved performance on Capsule Servers and improved performance and stability for host connections to Satellite. In a load-balanced setup, Capsule functionality supported for load balancing continues to work as expected when one Capsule Server is down for planned or unplanned maintenance.
1.1. Components of a load-balanced setup
When you configure your Satellite environment for load balancing, several components interact to provide the required functionality.
A load-balanced setup in a Satellite environment consists of the following components:
- Satellite Server
- Two or more Capsule Servers
- A load balancer
- Multiple hosts
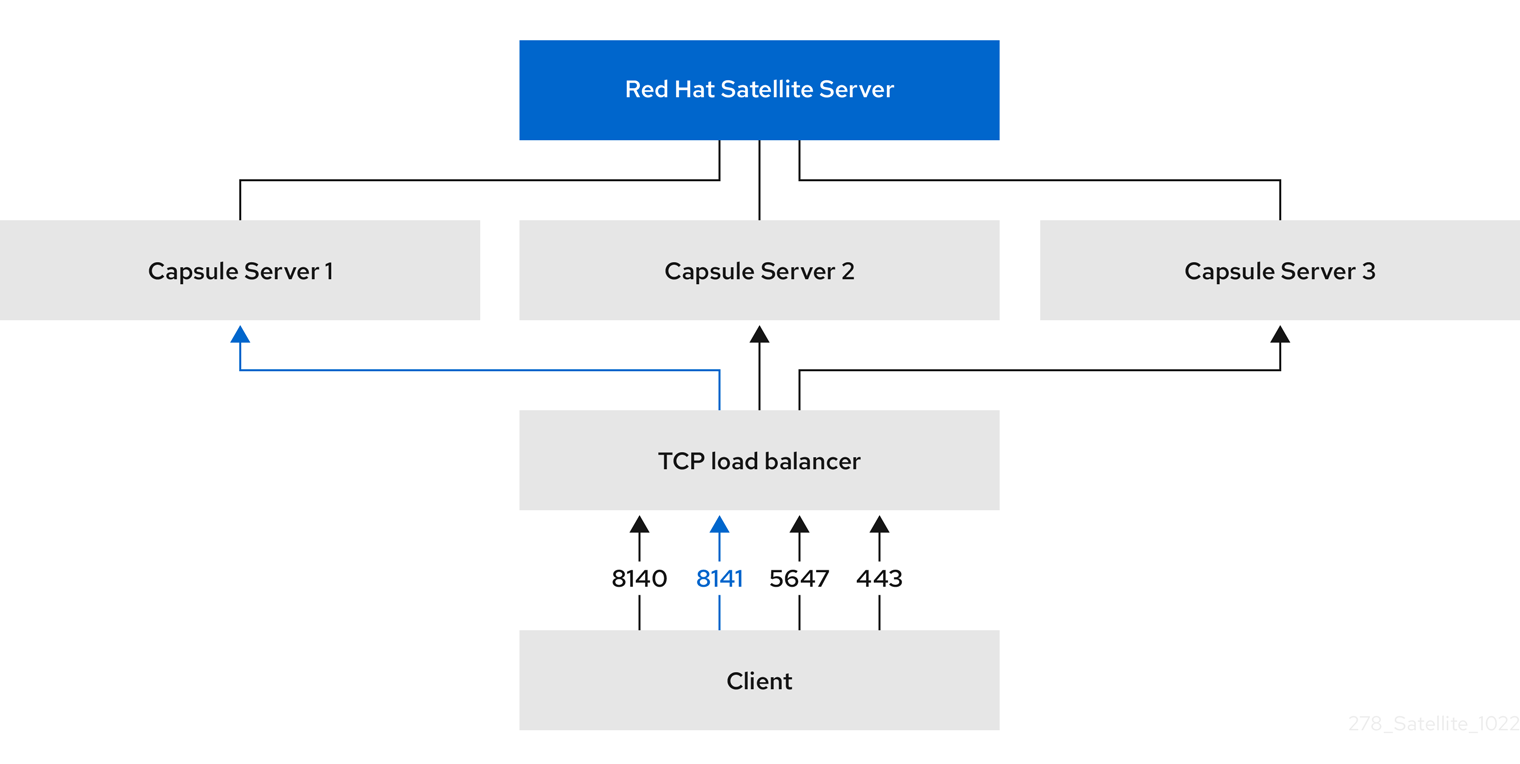
A host sends a request to the TCP load balancer. The load balancer receives the request and determines which Capsule Server will handle the request to ensure optimal performance and availability.
Figure 1.1. Components of a load-balanced setup
1.2. Services and features supported in a load-balanced setup
A load balancer in Satellite distributes load only for selected services and features.
The following services and features are supported for load balancing:
- Registering hosts
- Providing content to hosts
- Configuring hosts by using Puppet
Other Satellite services, such as provisioning, virt-who, or remote execution, go directly through the individual Capsules on which these services are running.
1.3. Additional maintenance required for load balancing
Configuring Capsules to use a load balancer results in a more complex environment and requires additional maintenance.
The following additional steps are required for load balancing:
- You must ensure that all Capsules have the same content. If you publish a content view version on Satellite, synchronize it to all Capsule Servers.
- You must upgrade each Capsule in sequence.
Chapter 2. Preparing Capsule Servers for load balancing
Satellite does not support configuring existing Capsule Servers for load balancing. You must create a new Capsule Server for this purpose.
2.1. Registering to Satellite Server
Register the base operating system on which you want to install Capsule Server to Satellite Server. This enables you to download the installation packages from your synchronized repositories.
Prerequisites
Prerequisites for Red Hat subscription manifest:
- On Satellite Server, a manifest must be installed and it must contain the appropriate repositories for the organization you want Capsule to belong to.
- The manifest must contain repositories for the base operating system on which you want to install Capsule, as well as any clients that you want to connect to Capsule.
The repositories must be synchronized.
For more information on manifests and repositories, see Managing Red Hat Subscriptions in Managing content.
Prerequisites for HTTP proxy and network:
- The Satellite Server base operating system must be able to resolve the host name of the Capsule base operating system and vice versa.
- Ensure HTTPS connection using client certificate authentication is possible between Capsule Server and Satellite Server. HTTP proxies between Capsule Server and Satellite Server are not supported.
- You must configure the host and network-based firewalls accordingly. For more information, see Opening required ports in Installing Capsule Server.
You can register hosts with Satellite using the host registration feature in the Satellite web UI, Hammer CLI, or the Satellite API. For more information, see Registering hosts and setting up host integration in Managing hosts.
Procedure
- In the Satellite web UI, navigate to Hosts > Register Host.
- From the Activation Keys list, select the activation keys to assign to your host.
- Click Generate to create the registration command.
- Click on the files icon to copy the command to your clipboard.
- Connect to your host using SSH and run the registration command.
-
Check the
/etc/yum.repos.d/redhat.repofile and ensure that the appropriate repositories have been enabled.
CLI procedure
Generate the host registration command using the Hammer CLI:
hammer host-registration generate-command \ --activation-keys "My_Activation_Key"
$ hammer host-registration generate-command \ --activation-keys "My_Activation_Key"Copy to Clipboard Copied! Toggle word wrap Toggle overflow If your hosts do not trust the SSL certificate of Satellite Server, you can disable SSL validation by adding the
--insecureflag to the registration command.hammer host-registration generate-command \ --activation-keys "My_Activation_Key" \ --insecure true
$ hammer host-registration generate-command \ --activation-keys "My_Activation_Key" \ --insecure trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Connect to your host using SSH and run the registration command.
-
Check the
/etc/yum.repos.d/redhat.repofile and ensure that the appropriate repositories have been enabled.
API procedure
Generate the host registration command using the Satellite API:
curl -X POST https://satellite.example.com/api/registration_commands \ --user "My_User_Name" \ -H 'Content-Type: application/json' \ -d '{ "registration_command": { "activation_keys": ["My_Activation_Key_1, My_Activation_Key_2"] }}'# curl -X POST https://satellite.example.com/api/registration_commands \ --user "My_User_Name" \ -H 'Content-Type: application/json' \ -d '{ "registration_command": { "activation_keys": ["My_Activation_Key_1, My_Activation_Key_2"] }}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow If your hosts do not trust the SSL certificate of Satellite Server, you can disable SSL validation by adding the
--insecureflag to the registration command.curl -X POST https://satellite.example.com/api/registration_commands \ --user "My_User_Name" \ -H 'Content-Type: application/json' \ -d '{ "registration_command": { "activation_keys": ["My_Activation_Key_1, My_Activation_Key_2"], "insecure": true }}'# curl -X POST https://satellite.example.com/api/registration_commands \ --user "My_User_Name" \ -H 'Content-Type: application/json' \ -d '{ "registration_command": { "activation_keys": ["My_Activation_Key_1, My_Activation_Key_2"], "insecure": true }}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use an activation key to simplify specifying the environments. For more information, see Managing Activation Keys in Managing content.
To enter a password as a command line argument, use
username:passwordsyntax. Keep in mind this can save the password in the shell history. Alternatively, you can use a temporary personal access token instead of a password. To generate a token in the Satellite web UI, navigate to My Account > Personal Access Tokens.- Connect to your host using SSH and run the registration command.
-
Check the
/etc/yum.repos.d/redhat.repofile and ensure that the appropriate repositories have been enabled.
2.2. Configuring repositories
Configure repositories to install your Capsule Server.
Procedure
Disable all repositories:
subscription-manager repos --disable "*"
# subscription-manager repos --disable "*"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the following repositories:
subscription-manager repos \ --enable=rhel-9-for-x86_64-baseos-rpms \ --enable=rhel-9-for-x86_64-appstream-rpms \ --enable=satellite-capsule-6.18-for-rhel-9-x86_64-rpms \ --enable=satellite-maintenance-6.18-for-rhel-9-x86_64-rpms
# subscription-manager repos \ --enable=rhel-9-for-x86_64-baseos-rpms \ --enable=rhel-9-for-x86_64-appstream-rpms \ --enable=satellite-capsule-6.18-for-rhel-9-x86_64-rpms \ --enable=satellite-maintenance-6.18-for-rhel-9-x86_64-rpmsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the required repositories are enabled:
dnf repolist enabled
# dnf repolist enabledCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.3. Installing Capsule Server packages
Before installing Capsule Server packages, you must upgrade all packages that are installed on the base operating system.
Procedure
Upgrade all packages:
dnf upgrade
# dnf upgradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install the packages:
dnf install satellite-capsule
# dnf install satellite-capsuleCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 3. Configuring Capsule Servers with default SSL certificates for load balancing
You can configure one or more Capsule Servers that use default SSL certificates for load balancing.
If you use Puppet in your Satellite deployment, the configuration steps are different. See Chapter 5, Configuring Capsule Servers with default SSL certificates for load balancing (with Puppet).
3.1. Configuring Capsule Server with default SSL certificates for load balancing without Puppet
On each Capsule Server that you want to configure for load balancing, install Katello certificates.
Prerequisites
- Prepare a new Capsule Server to use for load balancing. See Chapter 2, Preparing Capsule Servers for load balancing.
- Review Section 1.2, “Services and features supported in a load-balanced setup”.
Procedure
On Satellite Server, generate Katello certificates for Capsule Server:
capsule-certs-generate \ --certs-tar "/root/capsule.example.com-certs.tar" \ --foreman-proxy-cname loadbalancer.example.com \ --foreman-proxy-fqdn capsule.example.com
# capsule-certs-generate \ --certs-tar "/root/capsule.example.com-certs.tar" \ --foreman-proxy-cname loadbalancer.example.com \ --foreman-proxy-fqdn capsule.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Retain a copy of the example
satellite-installercommand that is output by thecapsule-certs-generatecommand for installing Capsule Server certificate.Copy the certificate archive file from Satellite Server to Capsule Server.
scp /root/capsule.example.com-certs.tar root@capsule.example.com:/root/capsule.example.com-certs.tar
# scp /root/capsule.example.com-certs.tar root@capsule.example.com:/root/capsule.example.com-certs.tarCopy to Clipboard Copied! Toggle word wrap Toggle overflow Append the following options to the
satellite-installercommand that you obtain from the output of thecapsule-certs-generatecommand:--certs-cname "loadbalancer.example.com" \ --enable-foreman-proxy-plugin-remote-execution-script
--certs-cname "loadbalancer.example.com" \ --enable-foreman-proxy-plugin-remote-execution-scriptCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, enter the
satellite-installercommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 4. Configuring Capsule Servers with custom SSL certificates for load balancing
You can configure one or more Capsule Servers that use custom SSL certificates for load balancing. To do this, configure and install certificates on each Capsule Server you want to use for load balancing.
If you use Puppet in your Satellite deployment, the configuration steps are different. See Chapter 6, Configuring Capsule Servers with custom SSL certificates for load balancing (with Puppet).
4.1. Creating a custom SSL certificate for Capsule Server
On each Capsule Server you want to configure for load balancing, create a configuration file for the Certificate Signing Request and include the load balancer and Capsule Server as Subject Alternative Names (SAN).
Procedure
To store all the source certificate files, create a directory that is accessible only to the
rootuser:mkdir /root/capsule_cert
# mkdir /root/capsule_certCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a private key with which to sign the certificate signing request (CSR).
Note that the private key must be unencrypted. If you use a password-protected private key, remove the private key password.
If you already have a private key for this Capsule Server, skip this step.
openssl genrsa -out /root/capsule_cert/capsule_cert_key.pem 4096
# openssl genrsa -out /root/capsule_cert/capsule_cert_key.pem 4096Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
/root/capsule_cert/openssl.cnfconfiguration file for the CSR and include the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The options used in the configuration file include the following:
commonName-
The certificate common name. It must match the FQDN of Capsule Server. Ensure to change this when running the command on each Capsule Server that you configure for load balancing. You can also set a wildcard value
*. [alt_names]The alternative names for the load balancer and Capsule Server. Include the FQDN of the load balancer as
DNS.1and the FQDN of Capsule Server asDNS.2.For more information about the
[ v3_req ]parameters and their purpose, see RFC 5280: Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile.
Optional: If you want to add Distinguished Name (DN) details to the CSR, add the following information to the
[ req_distinguished_name ]section:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The options used in the configuration file include the following:
countryName- The country represented by a two-letter code
stateOrProvinceName- Full name of the state or province
localityName- Full name of the locality (example: New York)
organizationalUnitName- Division responsible for the certificate (example: IT department)
Generate CSR:
openssl req -new \ -key /root/capsule_cert/capsule_cert_key.pem \ -config /root/capsule_cert/openssl.cnf \ -out /root/capsule_cert/capsule_cert_csr.pem
# openssl req -new \ -key /root/capsule_cert/capsule_cert_key.pem \ -config /root/capsule_cert/openssl.cnf \ -out /root/capsule_cert/capsule_cert_csr.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow The options used in the configuration file include the following:
-key- Path to the private key
-config- Path to the configuration file
-out- Path to the CSR to generate
Send the certificate signing request to the certificate authority (CA). The same CA must sign certificates for Satellite Server and Capsule Server.
When you submit the request, specify the lifespan of the certificate. The method for sending the certificate request varies, so consult the CA for the preferred method. In response to the request, you can expect to receive a CA bundle and a signed certificate, in separate files.
- Copy the Certificate Authority bundle and Capsule Server certificate file that you receive from the Certificate Authority, and Capsule Server private key to your Satellite Server.
4.2. Configuring Capsule Server with custom SSL certificates for load balancing without Puppet
On each Capsule Server you want to configure for load balancing, install Katello certificates.
Prerequisites
- Prepare a new Capsule Server to use for load balancing. See Chapter 2, Preparing Capsule Servers for load balancing.
- Review Section 1.2, “Services and features supported in a load-balanced setup”.
Procedure
On Satellite Server, enter the
capsule-certs-generatecommand to generate Capsule certificates:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Retain a copy of the example
satellite-installercommand from the output for installing Capsule Server certificates.Copy the certificate archive file from Satellite Server to Capsule Server:
scp /root/capsule.example.com-certs.tar root@capsule.example.com:capsule.example.com-certs.tar
# scp /root/capsule.example.com-certs.tar root@capsule.example.com:capsule.example.com-certs.tarCopy to Clipboard Copied! Toggle word wrap Toggle overflow Append the following options to the
satellite-installercommand that you obtain from the output of thecapsule-certs-generatecommand:--certs-cname "loadbalancer.example.com" \ --enable-foreman-proxy-plugin-remote-execution-script
--certs-cname "loadbalancer.example.com" \ --enable-foreman-proxy-plugin-remote-execution-scriptCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, enter the
satellite-installercommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 5. Configuring Capsule Servers with default SSL certificates for load balancing (with Puppet)
If you use Puppet in your Satellite setup, you can configure one or more Capsule Servers that use default SSL certificates for load balancing.
To do this, you configure Puppet certificate signing on one of your Capsule Servers. Then, you configure each remaining Puppet Capsule used for load balancing to use the certificates. The first Capsule Server will generate and sign Puppet certificates for the remaining Capsules configured for load balancing.
5.1. Configuring Capsule Server with default SSL certificates to generate and sign Puppet certificates
On the Capsule Server that will generate Puppet certificates for all other load-balancing Capsule Servers, configure Puppet certificate generation and signing.
Prerequisites
- Prepare a new Capsule Server to use for load balancing. See Chapter 2, Preparing Capsule Servers for load balancing.
- Review Section 1.2, “Services and features supported in a load-balanced setup”.
Procedure
On Satellite Server, generate Katello certificates for the system where you configure Capsule Server to generate and sign Puppet certificates:
capsule-certs-generate \ --certs-tar "/root/capsule-ca.example.com-certs.tar" \ --foreman-proxy-cname loadbalancer.example.com \ --foreman-proxy-fqdn capsule-ca.example.com
# capsule-certs-generate \ --certs-tar "/root/capsule-ca.example.com-certs.tar" \ --foreman-proxy-cname loadbalancer.example.com \ --foreman-proxy-fqdn capsule-ca.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Retain a copy of the example
satellite-installercommand that is output by thecapsule-certs-generatecommand for installing Capsule Server certificate.Copy the certificate archive file from Satellite Server to Capsule Server:
scp /root/capsule-ca.example.com-certs.tar root@capsule-ca.example.com:capsule-ca.example.com-certs.tar
# scp /root/capsule-ca.example.com-certs.tar root@capsule-ca.example.com:capsule-ca.example.com-certs.tarCopy to Clipboard Copied! Toggle word wrap Toggle overflow Append the following options to the
satellite-installercommand that you obtain from the output of thecapsule-certs-generatecommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, enter the
satellite-installercommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server that is the Puppetserver Certificate Authority, stop the Puppet server:
systemctl stop puppetserver
# systemctl stop puppetserverCopy to Clipboard Copied! Toggle word wrap Toggle overflow Generate Puppet certificates for all other Capsule Servers that you configure for load balancing, except the system where you first configured Puppet certificate signing:
puppetserver ca generate \ --ca-client \ --certname capsule.example.com \ --subject-alt-names loadbalancer.example.com
# puppetserver ca generate \ --ca-client \ --certname capsule.example.com \ --subject-alt-names loadbalancer.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates the following files:
-
/etc/puppetlabs/puppet/ssl/certs/capsule.example.com.pem -
/etc/puppetlabs/puppet/ssl/private_keys/capsule.example.com.pem -
/etc/puppetlabs/puppet/ssl/public_keys/capsule.example.com.pem -
/etc/puppetlabs/puppetserver/ca/signed/capsule.example.com.pem
-
Start the Puppet server:
systemctl start puppetserver
# systemctl start puppetserverCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.2. Configuring remaining Capsule Servers with default SSL certificates for load balancing
On each load-balancing Capsule Server, excluding the Capsule Server configured to sign Puppet certificates, configure the system to use Puppet certificates.
Procedure
On Satellite Server, generate Katello certificates for Capsule Server:
capsule-certs-generate \ --certs-tar "/root/capsule.example.com-certs.tar" \ --foreman-proxy-cname loadbalancer.example.com \ --foreman-proxy-fqdn capsule.example.com
# capsule-certs-generate \ --certs-tar "/root/capsule.example.com-certs.tar" \ --foreman-proxy-cname loadbalancer.example.com \ --foreman-proxy-fqdn capsule.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Retain a copy of the example
satellite-installercommand that is output by thecapsule-certs-generatecommand for installing Capsule Server certificate.Copy the certificate archive file from Satellite Server to Capsule Server:
scp /root/capsule.example.com-certs.tar root@capsule.example.com:/root/capsule.example.com-certs.tar
# scp /root/capsule.example.com-certs.tar root@capsule.example.com:/root/capsule.example.com-certs.tarCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, install the
puppetserverpackage:satellite-maintain packages install puppetserver
# satellite-maintain packages install puppetserverCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, create directories for puppet certificates:
mkdir -p /etc/puppetlabs/puppet/ssl/certs/ \ /etc/puppetlabs/puppet/ssl/private_keys/ \ /etc/puppetlabs/puppet/ssl/public_keys/
# mkdir -p /etc/puppetlabs/puppet/ssl/certs/ \ /etc/puppetlabs/puppet/ssl/private_keys/ \ /etc/puppetlabs/puppet/ssl/public_keys/Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, copy the Puppet certificates for this Capsule Server from the system where you configure Capsule Server to sign Puppet certificates:
scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/certs/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/certs/capsule.example.com.pem scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/certs/ca.pem /etc/puppetlabs/puppet/ssl/certs/ca.pem scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/private_keys/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/private_keys/capsule.example.com.pem scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/public_keys/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/public_keys/capsule.example.com.pem
# scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/certs/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/certs/capsule.example.com.pem # scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/certs/ca.pem /etc/puppetlabs/puppet/ssl/certs/ca.pem # scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/private_keys/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/private_keys/capsule.example.com.pem # scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/public_keys/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/public_keys/capsule.example.com.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, change the
/etc/puppetlabs/puppet/ssl/directory ownership to userpuppetand grouppuppet:chown -R puppet:puppet /etc/puppetlabs/puppet/ssl/
# chown -R puppet:puppet /etc/puppetlabs/puppet/ssl/Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, set the SELinux context for the
/etc/puppetlabs/puppet/ssl/directory:restorecon -Rv /etc/puppetlabs/puppet/ssl/
# restorecon -Rv /etc/puppetlabs/puppet/ssl/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Append the following options to the
satellite-installercommand that you obtain from the output of thecapsule-certs-generatecommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, enter the
satellite-installercommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.3. Managing Puppet limitations with load balancing in Satellite
If you use Puppet, Puppet certificate signing is assigned to the first Capsule that you configure. If the first Capsule is down, hosts cannot obtain Puppet content.
Puppet Certificate Authority (CA) management does not support certificate signing in a load-balanced setup. Puppet CA stores certificate information, such as the serial number counter and CRL, on the file system. Multiple writer processes that attempt to use the same data can corrupt it.
To manage this Puppet limitation, complete the following steps:
- Configure Puppet certificate signing on one Capsule Server, typically the first system where you configure Capsule Server for load balancing.
- Configure the clients to send CA requests to port 8141 on a load balancer.
- Configure a load balancer to redirect CA requests from port 8141 to port 8140 on the system where you configure Capsule Server to sign Puppet certificates.
To troubleshoot issues, reproduce the issue on each Capsule, bypassing the load balancer. This solution does not use Pacemaker or other similar HA tools to maintain one state across all Capsules.
Chapter 6. Configuring Capsule Servers with custom SSL certificates for load balancing (with Puppet)
You can configure one or more Capsule Servers that use custom SSL certificates for load balancing.
6.1. Creating a custom SSL certificate for Capsule Server
On each Capsule Server you want to configure for load balancing, create a configuration file for the Certificate Signing Request and include the load balancer and Capsule Server as Subject Alternative Names (SAN).
Procedure
To store all the source certificate files, create a directory that is accessible only to the
rootuser:mkdir /root/capsule_cert
# mkdir /root/capsule_certCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a private key with which to sign the certificate signing request (CSR).
Note that the private key must be unencrypted. If you use a password-protected private key, remove the private key password.
If you already have a private key for this Capsule Server, skip this step.
openssl genrsa -out /root/capsule_cert/capsule_cert_key.pem 4096
# openssl genrsa -out /root/capsule_cert/capsule_cert_key.pem 4096Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
/root/capsule_cert/openssl.cnfconfiguration file for the CSR and include the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The options used in the configuration file include the following:
commonName-
The certificate common name. It must match the FQDN of Capsule Server. Ensure to change this when running the command on each Capsule Server that you configure for load balancing. You can also set a wildcard value
*. [alt_names]The alternative names for the load balancer and Capsule Server. Include the FQDN of the load balancer as
DNS.1and the FQDN of Capsule Server asDNS.2.For more information about the
[ v3_req ]parameters and their purpose, see RFC 5280: Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile.
Optional: If you want to add Distinguished Name (DN) details to the CSR, add the following information to the
[ req_distinguished_name ]section:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The options used in the configuration file include the following:
countryName- The country represented by a two-letter code
stateOrProvinceName- Full name of the state or province
localityName- Full name of the locality (example: New York)
organizationalUnitName- Division responsible for the certificate (example: IT department)
Generate CSR:
openssl req -new \ -key /root/capsule_cert/capsule_cert_key.pem \ -config /root/capsule_cert/openssl.cnf \ -out /root/capsule_cert/capsule_cert_csr.pem
# openssl req -new \ -key /root/capsule_cert/capsule_cert_key.pem \ -config /root/capsule_cert/openssl.cnf \ -out /root/capsule_cert/capsule_cert_csr.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow The options used in the configuration file include the following:
-key- Path to the private key
-config- Path to the configuration file
-out- Path to the CSR to generate
Send the certificate signing request to the certificate authority (CA). The same CA must sign certificates for Satellite Server and Capsule Server.
When you submit the request, specify the lifespan of the certificate. The method for sending the certificate request varies, so consult the CA for the preferred method. In response to the request, you can expect to receive a CA bundle and a signed certificate, in separate files.
- Copy the Certificate Authority bundle and Capsule Server certificate file that you receive from the Certificate Authority, and Capsule Server private key to your Satellite Server.
6.2. Configuring Capsule Server with custom SSL certificates to generate and sign Puppet certificates
On the Capsule Server that will generate Puppet certificates for all other load-balancing Capsule Servers, configure Puppet certificate generation and signing.
Prerequisites
- Prepare a new Capsule Server to use for load balancing. See Chapter 2, Preparing Capsule Servers for load balancing.
- Review Section 1.2, “Services and features supported in a load-balanced setup”.
Procedure
On Satellite Server, enter the
capsule-certs-generatecommand to generate Capsule certificates:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Retain a copy of the example
satellite-installercommand from the output for installing Capsule Server certificates.- Copy the certificate archive file from Satellite Server to Capsule Server.
Append the following options to the
satellite-installercommand that you obtain from the output of thecapsule-certs-generatecommand:--enable-foreman-proxy-plugin-remote-execution-script \ --foreman-proxy-puppetca "true" \ --puppet-ca-server "capsule-ca.example.com" \ --puppet-dns-alt-names "loadbalancer.example.com" \ --puppet-server-ca "true"
--enable-foreman-proxy-plugin-remote-execution-script \ --foreman-proxy-puppetca "true" \ --puppet-ca-server "capsule-ca.example.com" \ --puppet-dns-alt-names "loadbalancer.example.com" \ --puppet-server-ca "true"Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, enter the
satellite-installercommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server that is the Puppetserver Certificate Authority, stop the Puppet server:
systemctl stop puppetserver
# systemctl stop puppetserverCopy to Clipboard Copied! Toggle word wrap Toggle overflow Generate Puppet certificates for all other Capsule Servers that you configure for load balancing, except the system where you first configured Puppet certificate signing:
puppetserver ca generate \ --ca-client \ --certname capsule.example.com \ --subject-alt-names loadbalancer.example.com
# puppetserver ca generate \ --ca-client \ --certname capsule.example.com \ --subject-alt-names loadbalancer.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates the following files:
-
/etc/puppetlabs/puppet/ssl/certs/capsule.example.com.pem -
/etc/puppetlabs/puppet/ssl/private_keys/capsule.example.com.pem -
/etc/puppetlabs/puppet/ssl/public_keys/capsule.example.com.pem -
/etc/puppetlabs/puppetserver/ca/signed/capsule.example.com.pem
-
Start the Puppet server:
systemctl start puppetserver
# systemctl start puppetserverCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3. Configuring remaining Capsule Servers with custom SSL certificates for load balancing
On each load-balancing Capsule Server, excluding the Capsule Server configured to sign Puppet certificates, configure the system to use Puppet certificates.
Procedure
On Satellite Server, enter the
capsule-certs-generatecommand to generate Capsule certificates:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Retain a copy of the example
satellite-installercommand from the output for installing Capsule Server certificates.Copy the certificate archive file from Satellite Server to Capsule Server.
scp /root/capsule.example.com-certs.tar root@capsule.example.com:capsule.example.com-certs.tar
# scp /root/capsule.example.com-certs.tar root@capsule.example.com:capsule.example.com-certs.tarCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, install the
puppetserverpackage:satellite-maintain packages install puppetserver
# satellite-maintain packages install puppetserverCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, create directories for puppet certificates:
mkdir -p /etc/puppetlabs/puppet/ssl/certs/ \ /etc/puppetlabs/puppet/ssl/private_keys/ \ /etc/puppetlabs/puppet/ssl/public_keys/
# mkdir -p /etc/puppetlabs/puppet/ssl/certs/ \ /etc/puppetlabs/puppet/ssl/private_keys/ \ /etc/puppetlabs/puppet/ssl/public_keys/Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, copy the Puppet certificates for this Capsule Server from the system where you configure Capsule Server to sign Puppet certificates:
scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/certs/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/certs/capsule.example.com.pem scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/certs/ca.pem /etc/puppetlabs/puppet/ssl/certs/ca.pem scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/private_keys/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/private_keys/capsule.example.com.pem scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/public_keys/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/public_keys/capsule.example.com.pem
# scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/certs/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/certs/capsule.example.com.pem # scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/certs/ca.pem /etc/puppetlabs/puppet/ssl/certs/ca.pem # scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/private_keys/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/private_keys/capsule.example.com.pem # scp root@capsule-ca.example.com:/etc/puppetlabs/puppet/ssl/public_keys/capsule.example.com.pem /etc/puppetlabs/puppet/ssl/public_keys/capsule.example.com.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, change the
/etc/puppetlabs/puppet/ssl/directory ownership to userpuppetand grouppuppet:chown -R puppet:puppet /etc/puppetlabs/puppet/ssl/
# chown -R puppet:puppet /etc/puppetlabs/puppet/ssl/Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, set the SELinux context for the
/etc/puppetlabs/puppet/ssl/directory:restorecon -Rv /etc/puppetlabs/puppet/ssl/
# restorecon -Rv /etc/puppetlabs/puppet/ssl/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Append the following options to the
satellite-installercommand that you obtain from the output of thecapsule-certs-generatecommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow On Capsule Server, enter the
satellite-installercommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.4. Managing Puppet limitations with load balancing in Satellite
If you use Puppet, Puppet certificate signing is assigned to the first Capsule that you configure. If the first Capsule is down, hosts cannot obtain Puppet content.
Puppet Certificate Authority (CA) management does not support certificate signing in a load-balanced setup. Puppet CA stores certificate information, such as the serial number counter and CRL, on the file system. Multiple writer processes that attempt to use the same data can corrupt it.
To manage this Puppet limitation, complete the following steps:
- Configure Puppet certificate signing on one Capsule Server, typically the first system where you configure Capsule Server for load balancing.
- Configure the clients to send CA requests to port 8141 on a load balancer.
- Configure a load balancer to redirect CA requests from port 8141 to port 8140 on the system where you configure Capsule Server to sign Puppet certificates.
To troubleshoot issues, reproduce the issue on each Capsule, bypassing the load balancer. This solution does not use Pacemaker or other similar HA tools to maintain one state across all Capsules.
Chapter 7. Installing and configuring the load balancer
Red Hat provides general guidance for configuring an HAProxy load balancer using Red Hat Enterprise Linux 9. However, you can install any suitable load balancing software solution that supports TCP forwarding.
7.1. Installing the load balancer
The following example provides general guidance for configuring an HAProxy load balancer using Red Hat Enterprise Linux 9. However, you can install any suitable load balancing software solution that supports TCP forwarding.
Procedure
Install HAProxy:
dnf install haproxy
# dnf install haproxyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install the following package that includes the
semanagetool:dnf install policycoreutils-python-utils
# dnf install policycoreutils-python-utilsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure SELinux to allow HAProxy to bind any port:
semanage boolean --modify --on haproxy_connect_any
# semanage boolean --modify --on haproxy_connect_anyCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the load balancer to balance the network load for the ports as described in Section 7.2, “Ports configuration for the load balancer”.
- Configure the load balancer to disable SSL offloading and allow client-side SSL certificates to pass through to back end servers. This is required because communication from clients to Capsule Servers depends on client-side SSL certificates.
Start and enable the HAProxy service:
systemctl enable --now haproxy
# systemctl enable --now haproxyCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.2. Ports configuration for the load balancer
The load balancer must be configured to balance the network load for the ports. For example, to configure ports for HAProxy, edit the /etc/haproxy/haproxy.cfg file to correspond with the table.
| Service | Port | Mode | Balance Mode | Destination |
|---|---|---|---|---|
| HTTP | 80 | TCP | roundrobin | port 80 on all Capsule Servers |
| HTTPS and RHSM | 443 | TCP | source | port 443 on all Capsule Servers |
| Anaconda for template retrieval | 8000 | TCP | roundrobin | port 8000 on all Capsule Servers |
| Puppet (Optional) | 8140 | TCP | roundrobin | port 8140 on all Capsule Servers |
| PuppetCA (Optional) | 8141 | TCP | roundrobin | port 8140 only on the system where you configure Capsule Server to sign Puppet certificates |
| Capsule HTTPS for Host Registration and optionally OpenSCAP | 9090 | TCP | roundrobin | port 9090 on all Capsule Servers |
Chapter 8. Verifying the load balancing configuration
Use this procedure to verify the load balancing configuration for each Capsule Server.
Procedure
- Shut down the base operating system for your Capsule Server.
-
Verify that content or subscription management features are available on clients registered to this Capsule. For example, enter the
subscription-manager refreshcommand on a client. - Restart the base operating system for your Capsule Server.
Chapter 9. Registering clients to the load balancer
To balance the load of network traffic from clients, you must register the clients to the load balancer.
To consume container content from a load balancer regardless of client registration, use the load balancer hostname with the container client of choice. For example, use podman login loadbalancer.example.com to log in.
9.1. Setting the load balancer for host registration
You can configure Satellite to register clients through a load balancer when using the host registration feature.
You will be able to register hosts to the load balancer instead of Capsule. The load balancer will decide through which Capsule to register the host at the time of request. Upon registration, the subscription manager on the host will be configured to manage content through the load balancer.
Prerequisites
You configured SSL certificates on all Capsule Servers. For more information, see the following sections:
- Chapter 3, Configuring Capsule Servers with default SSL certificates for load balancing.
- Chapter 4, Configuring Capsule Servers with custom SSL certificates for load balancing.
- Chapter 5, Configuring Capsule Servers with default SSL certificates for load balancing (with Puppet).
- Chapter 6, Configuring Capsule Servers with custom SSL certificates for load balancing (with Puppet).
You enabled Registration and Templates plugins on all Capsule Servers:
satellite-installer \ --foreman-proxy-registration true \ --foreman-proxy-templates true
# satellite-installer \ --foreman-proxy-registration true \ --foreman-proxy-templates trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure
On all Capsule Servers, set the registration and template URLs using
satellite-installer:satellite-installer \ --foreman-proxy-registration-url "https://loadbalancer.example.com:9090" \ --foreman-proxy-template-url "http://loadbalancer.example.com:8000"
# satellite-installer \ --foreman-proxy-registration-url "https://loadbalancer.example.com:9090" \ --foreman-proxy-template-url "http://loadbalancer.example.com:8000"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - In the Satellite web UI, navigate to Infrastructure > Capsules.
- For each Capsule, click the dropdown menu in the Actions column and select Refresh.
9.2. Registering a host to the load balancer using Satellite web UI
After setting the load balancer for host registration, you can register a host to the load balancer.
Procedure
- In the Satellite web UI, navigate to Hosts > Register Host.
- From the Capsule dropdown list, select your Capsule Server configured for load balancing.
- Select Force to register a host that has been previously registered to a Capsule Server.
- From the Activation Keys list, select the activation keys to assign to your host.
- Click Generate to create the registration command.
- Click on the files icon to copy the command to your clipboard.
- Connect to your host using SSH and run the registration command.
-
Check the
/etc/yum.repos.d/redhat.repofile and ensure that the appropriate repositories have been enabled.
9.3. Registering a host to the load balancer using CLI
After setting the load balancer for host registration, you can register a host to the load balancer.
Procedure
Generate the host registration command using the Hammer CLI:
hammer host-registration generate-command \ --activation-keys "My_Activation_Key"
$ hammer host-registration generate-command \ --activation-keys "My_Activation_Key"Copy to Clipboard Copied! Toggle word wrap Toggle overflow If your hosts do not trust the SSL certificate of Satellite Server, you can disable SSL validation by adding the
--insecureflag to the registration command.hammer host-registration generate-command \ --activation-keys "My_Activation_Key" \ --insecure true
$ hammer host-registration generate-command \ --activation-keys "My_Activation_Key" \ --insecure trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Include the
--smart-proxy-id My_Capsule_IDoption. You can use the ID of any Capsule Server that you configured for host registration load balancing. Satellite will apply the load balancer to the registration command automatically.Include the
--forceoption to register a host that has been previously registered to a Capsule Server.- Connect to your host using SSH and run the registration command.
-
Check the
/etc/yum.repos.d/redhat.repofile and ensure that the appropriate repositories have been enabled.
9.4. Registering a host to the load balancer using API
After setting the load balancer for host registration, you can register a host to a load-balanced Capsule.
Procedure
Generate the host registration command using the Satellite API:
curl -X POST https://satellite.example.com/api/registration_commands \ --user "My_User_Name" \ -H 'Content-Type: application/json' \ -d '{ "registration_command": { "activation_keys": ["My_Activation_Key_1, My_Activation_Key_2"] }}'# curl -X POST https://satellite.example.com/api/registration_commands \ --user "My_User_Name" \ -H 'Content-Type: application/json' \ -d '{ "registration_command": { "activation_keys": ["My_Activation_Key_1, My_Activation_Key_2"] }}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow If your hosts do not trust the SSL certificate of Satellite Server, you can disable SSL validation by adding the
--insecureflag to the registration command.curl -X POST https://satellite.example.com/api/registration_commands \ --user "My_User_Name" \ -H 'Content-Type: application/json' \ -d '{ "registration_command": { "activation_keys": ["My_Activation_Key_1, My_Activation_Key_2"], "insecure": true }}'# curl -X POST https://satellite.example.com/api/registration_commands \ --user "My_User_Name" \ -H 'Content-Type: application/json' \ -d '{ "registration_command": { "activation_keys": ["My_Activation_Key_1, My_Activation_Key_2"], "insecure": true }}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use an activation key to simplify specifying the environments. For more information, see Managing Activation Keys in Managing content.
Include
{ "smart_proxy_id": My_Capsule_ID }. You can use the ID of any Capsule Server that you configured for host registration load balancing. Satellite will apply the load balancer to the registration command automatically.Include
{ "force": true }to register a host that has been previously registered to a Capsule Server.To enter a password as a command line argument, use
username:passwordsyntax. Keep in mind this can save the password in the shell history. Alternatively, you can use a temporary personal access token instead of a password. To generate a token in the Satellite web UI, navigate to My Account > Personal Access Tokens.- Connect to your host using SSH and run the registration command.
-
Check the
/etc/yum.repos.d/redhat.repofile and ensure that the appropriate repositories have been enabled.
9.5. (Deprecated) Registering clients using the bootstrap script
To register clients, enter the following command on the client. You must complete the registration procedure for each client.
Prerequisites
- Ensure that you install the bootstrap script on the client and change file permissions of the script to executable. For more information, see Registering Hosts to Red Hat Satellite Using The Bootstrap Script in Managing hosts.
Procedure
On Red Hat Enterprise Linux 8, enter the following command:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The options used in the command include the following:
enablerepos-
Replace
<arch>with the client architecture, for examplex86. --force-
Include the
--forceoption to register the client that has been previously registered to a standalone Capsule. --puppet-ca-port-
Include the
--puppet-ca-port 8141option if you use Puppet.
On Red Hat Enterprise Linux 7, enter the following command:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The options used in the command include the following:
--force-
Include the
--forceoption to register the client that has been previously registered to a standalone Capsule. --puppet-ca-portInclude the
--puppet-ca-port 8141option if you use Puppet.The script prompts for the password corresponding to the Satellite user name you entered with the
--loginoption.
Chapter 10. Propagating SCAP content through the load balancer
If you use OpenSCAP to manage security compliance on your clients, you must configure the SCAP client to send ARF reports to the load balancer instead of Capsule. The configuration procedure depends on the method you have selected to deploy compliance policies.
10.1. Propagating SCAP content using Ansible deployment
Using this procedure, you can promote Security Content Automation Protocol (SCAP) content through the load balancer in the scope of the Ansible deployment method.
Prerequisites
- Ensure that you have configured Satellite for Ansible deployment of compliance policies. For more information, see Configuring Compliance Policy Deployment Methods in Managing security compliance.
Procedure
- In the Satellite web UI, navigate to Configure > Ansible > Variables.
-
Search for the
foreman_scap_client_portvariable and click its name. - In the Default Behavior area, ensure that the Override checkbox is selected.
-
In the Parameter Type list, ensure that
integeris selected. -
In the Default Value field, enter
9090. - In the Specify Matchers area, remove all matchers that override the default value.
- Click Submit.
-
Search for the
foreman_scap_client_servervariable and click its name. - In the Default Behavior area, ensure that the Override checkbox is selected.
-
In the Parameter Type list, ensure that
stringis selected. -
In the Default Value field, enter the FQDN of your load balancer, such as
loadbalancer.example.com. - In the Specify Matchers area, remove all matchers that override the default value.
- Click Submit.
Continue with deploying a compliance policy using Ansible. For more information, see:
- Deploying a Policy in a Host Group Using Ansible in Managing security compliance
- Deploying a Policy on a Host Using Ansible in Managing security compliance
Verification
On the client, verify that the
/etc/foreman_scap_client/config.yamlfile contains the following lines:# Foreman proxy to which reports should be uploaded :server: 'loadbalancer.example.com' :port: 9090
# Foreman proxy to which reports should be uploaded :server: 'loadbalancer.example.com' :port: 9090Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.2. Propagating SCAP content using Puppet deployment
Using this procedure, you can promote Security Content Automation Protocol (SCAP) content through the load balancer in the scope of the Puppet deployment method.
Prerequisites
- Ensure that you have configured Satellite for Puppet deployment of compliance policies. For more information, see Configuring Compliance Policy Deployment Methods in Managing security compliance.
Procedure
- In the Satellite web UI, navigate to Configure > Puppet ENC > Classes.
-
Click
foreman_scap_client. - Click the Smart Class Parameter tab.
-
In the pane to the left of the Smart Class Parameter window, click
port. - In the Default Behavior area, select the Override checkbox.
-
From the Key Type list, select
integer. -
In the Default Value field, enter
9090. -
In the pane to the left of the Smart Class Parameter window, click
server. - In the Default Behavior area, select the Override checkbox.
-
From the Key Type list, select
string. -
In the Default Value field, enter the FQDN of your load balancer, such as
loadbalancer.example.com. - In the lower left of the Smart Class Parameter window, click Submit.
Continue with deploying a compliance policy using Puppet. For more information, see:
- Deploying a Policy in a Host Group Using Puppet in Managing security compliance
- Deploying a Policy on a Host Using Puppet in Managing security compliance
Verification
On the client, verify that the
/etc/foreman_scap_client/config.yamlfile contains the following lines:# Foreman proxy to which reports should be uploaded :server: 'loadbalancer.example.com' :port: 9090
# Foreman proxy to which reports should be uploaded :server: 'loadbalancer.example.com' :port: 9090Copy to Clipboard Copied! Toggle word wrap Toggle overflow