Questo contenuto non è disponibile nella lingua selezionata.
2.8.2. Basic Firewall Configuration
Just as a firewall in a building attempts to prevent a fire from spreading, a computer firewall attempts to prevent malicious software from spreading to your computer. It also helps to prevent unauthorized users from accessing your computer.
In a default Red Hat Enterprise Linux installation, a firewall exists between your computer or network and any untrusted networks, for example the Internet. It determines which services on your computer remote users can access. A properly configured firewall can greatly increase the security of your system. It is recommended that you configure a firewall for any Red Hat Enterprise Linux system with an Internet connection.
2.8.2.1. Firewall Configuration Tool
Copia collegamentoCollegamento copiato negli appunti!
During the Firewall Configuration screen of the Red Hat Enterprise Linux installation, you were given the option to enable a basic firewall as well as to allow specific devices, incoming services, and ports.
After installation, you can change this preference by using the Firewall Configuration Tool.
To start this application, either select
system-config-firewall at a shell prompt.
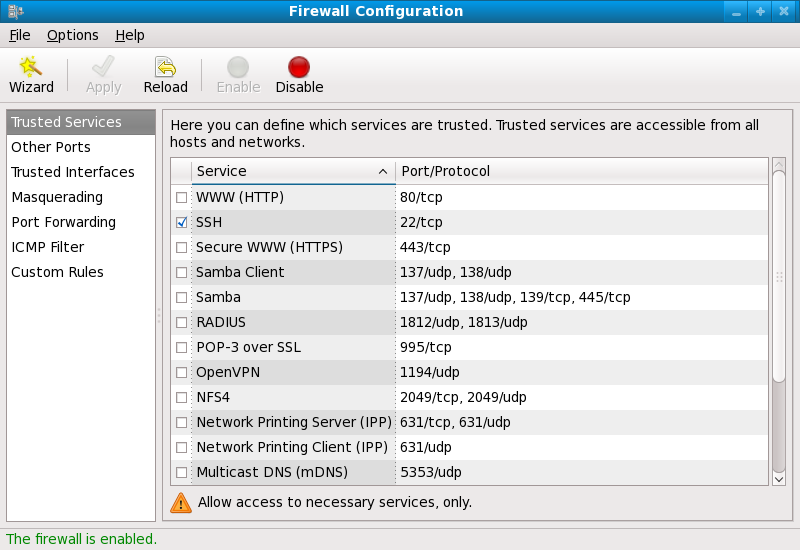
Figure 2.5. Firewall Configuration Tool
Note
The Firewall Configuration Tool only configures a basic firewall. If the system needs more complex rules, see Section 2.8.9, “IPTables” for details on configuring specific
iptables rules.
As of Red Hat Enterprise Linux 6.5, the
iptables and ip6tables services now provide the ability to assign a fallback firewall configuration if the default configuration cannot be applied. If application of the firewall rules from /etc/sysconfig/iptables fails, the fallback file is applied if it exists. The fallback file is named /etc/sysconfig/iptables.fallback and uses the same file format as /etc/sysconfig/iptables. If application of the fallback file also fails, there is no further fallback. To create a fallback file, use the standard firewall configuration tool and rename or copy the file to the fallback file.
For the
ip6tables service, replace all occurrences of iptables with ip6tables in the above examples.
Warning
If you have previously set up some custom packet-filtering rules by directly using the
iptables utility (as described in Section 2.8.9, “IPTables”), running the system-config-firewall utility will erase these custom rules immediately.