[org/gnome/desktop/lockdown]
# Disable command prompt
disable-command-line=true
----
. Create a new file under the `/etc/dconf/db/local.d/locks/` directory and list the keys or subpaths you want to lock down:
+
----
# Lock command prompt
/org/gnome/desktop/lockdown/disable-command-line
----
. Apply the changes to the system databases:
+
----
# dconf update
----
. For this settings to take effect, users needs to log out and log back in.
:leveloffset: 1
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="disabling-repartitioning_{context}"]
= Disabling repartitioning
You can override the default system settings that control disk management.
IMPORTANT: Avoid modifying the `/usr/share/polkit-1/actions/org.freedesktop.udisks2.policy` file directly. Any changes you make will be replaced during the next package update.
.Prerequisites
* Administrative access.
.Procedure
. Copy the `/usr/share/polkit-1/actions/org.freedesktop.udisks2.policy` file under the `/etc/share/polkit-1/actions/` directory:
+
----
# cp /usr/share/polkit-1/actions/org.freedesktop.udisks2.policy /etc/share/polkit-1/actions/org.freedesktop.udisks2.policy
----
. In the `/etc/polkit-1/actions/org.freedesktop.udisks2.policy` file, delete any actions that you do not need and add the following lines:
+
[source,xml]
----
<action id="org.freedesktop.udisks2.modify-device">
<message>Authentication is required to modify the disks settings</message>
<defaults>
<allow_any>no</allow_any>
<allow_inactive>no</allow_inactive>
<allow_active>yes</allow_active>
</defaults>
</action>
----
+
If you want to restrict access only to the root user, replace `<allow_any>no</allow_any>` with `<allow_any>auth_admin</allow_any>`.
:leveloffset: 2
:context: {parent-context-of-restricting-the-desktop-session}
:leveloffset!:
:leveloffset: +1
:_mod-docs-content-type: ASSEMBLY
:parent-context-of-assembly_restricting-the-session-to-a-single-application: {context}
[id="assembly_restricting-the-session-to-a-single-application_{context}"]
= Restricting the session to a single application
:context: assembly_restricting-the-session-to-a-single-application
[role="_abstract"]
You can start the GNOME session in single-application mode, also known as kiosk mode. In this session, GNOME displays only a full-screen window of the application that you have selected.
// == Prerequisites
// * A bulleted list of conditions that must be satisfied before the user starts following this assembly.
// * You can also link to other modules or assemblies the user must follow before starting this assembly.
// * Delete the section title and bullets if the assembly has no prerequisites.
// * X is installed. For information about installing X, see <link>.
// * You can log in to X with administrator privileges.
:leveloffset: +1
:_mod-docs-content-type: CONCEPT
[id="con_single-application-mode_{context}"]
= Single-application mode
[role="_abstract"]
Single-application mode is a modified GNOME session that reconfigures the Mutter window manager into an interactive kiosk. This session locks down certain behavior to make the standard desktop more restrictive. The user can interact only with a single application selected by the administrator.
You can set up single-application mode for several use cases, such as:
* In the communication, entertainment, or education fields
* As a self-serve machine
* As an event manager
* As a registration point
The GNOME Kiosk utility provides the single-application mode configuration and sessions.
The following single-application sessions are available:
Search Appliance Session::
This session always starts the *Mozilla Firefox* web browser at the `www.google.com` website.
Kiosk Script Session::
This session starts an arbitrary application that you specify in a shell script.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="enabling-search-appliance-mode_{context}"]
= Enabling search appliance mode
[role="_abstract"]
This procedure installs and enables the Search Appliance Session, which restricts the GNOME session to the Google search engine in a web browser.
// .Prerequisites
// * A bulleted list of conditions that must be satisfied before the user starts following this module.
// * You can also link to other modules or assemblies the user must follow before starting this module.
// * Delete the section title and bullets if the module has no prerequisites.
.Procedure
. Install the GNOME Kiosk packages:
+
[subs="+attributes"]
----
# {PackageManagerCommand} install gnome-kiosk gnome-kiosk-search-appliance
----
. At the GNOME login screen, select *Search Appliance Session* from the gear button menu and log in as the single-application user.
. The *Mozilla Firefox* browser opens as a full-screen window in its kiosk mode. It shows the Google search page.
// .Verification
// . Start each step with an active verb.
// . Include one command or action per step.
// . Use an unnumbered bullet (*) if the procedure includes only one step.
[role="_additional-resources"]
.Additional resources
* The `/usr/share/doc/gnome-kiosk/README.md` file provided by the [package]`gnome-kiosk` package.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="proc_enabling-single-application-mode_{context}"]
= Enabling single-application mode
[role="_abstract"]
This procedure installs and enables the Kiosk Script Session, which restricts the GNOME session to a selected single application.
// .Prerequisites
// * A bulleted list of conditions that must be satisfied before the user starts following this module.
// * You can also link to other modules or assemblies the user must follow before starting this module.
// * Delete the section title and bullets if the module has no prerequisites.
.Procedure
. Install the GNOME Kiosk packages:
+
[subs="+attributes"]
----
# {PackageManagerCommand} install gnome-kiosk gnome-kiosk-script-session
----
. At the GNOME login screen, select *Kiosk Script Session* from the gear button menu and log in as the single-application user.
. The *gedit* text editor opens as a full-screen window. It shows the shell script that configures which application runs in your single-application session.
+
Edit the shell script and enter the application that you want to start in the single-application session.
+
For example, to start the *Mozilla Firefox* browser, enter the following content:
+
----
#!/usr/bin/sh
firefox --kiosk https://example.org
----
. Save the script file.
. Close the *gedit* window.
+
The session terminates and restarts with your selected application.
. The next time you log into the single-application session, your selected application runs.
// .Verification
// . Start each step with an active verb.
// . Include one command or action per step.
// . Use an unnumbered bullet (*) if the procedure includes only one step.
[role="_additional-resources"]
.Additional resources
* The `/usr/share/doc/gnome-kiosk/README.md` file provided by the [package]`gnome-kiosk` package.
:leveloffset: 2
// [role="_additional-resources"]
// == Additional resources (or Next steps)
// * A bulleted list of links to other closely-related material. These links can include `link:` and `xref:` macros.
// * For more details on writing assemblies, see the link:https://github.com/redhat-documentation/modular-docs#modular-documentation-reference-guide[Modular Documentation Reference Guide].
// * Use a consistent system for file names, IDs, and titles. For tips, see _Anchor Names and File Names_ in link:https://github.com/redhat-documentation/modular-docs#modular-documentation-reference-guide[Modular Documentation Reference Guide].
:!context:
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: ASSEMBLY
:parent-context-of-configuring-sound-in-gnome: {context}
:context: configuring-sound-in-gnome
[id="configuring-sound-in-gnome_{context}"]
= Configuring sound in GNOME
You can configure sound volume and other sound options in GNOME.
// .Prerequisites
//
// * A bulleted list of conditions that must be satisfied before the user starts following this assembly.
// * You can also link to other modules or assemblies the user must follow before starting this assembly.
// * Delete the section title and bullets if the assembly has no prerequisites.
:leveloffset: +1
:_mod-docs-content-type: CONCEPT
[id="sound-configuration-tools-in-gnome_{context}"]
= Sound configuration tools in GNOME
In RHEL 9, the *PipeWire* sound server handles sound output and input. *PipeWire* lets programs output the audio using the `pipewire` daemon.
To configure sound, you can use one of the following graphical applications in GNOME:
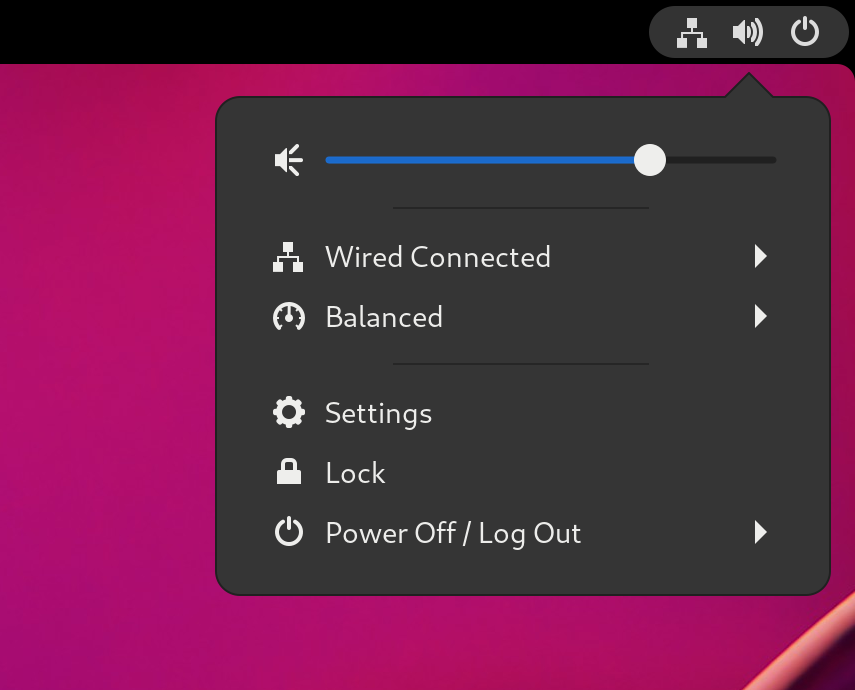
.System menu
The *system menu* is located in the top-right screen corner. It enables you only to set the intensity of the sound output or sound input through the sound bar. The sound bar for input sound is available only if you are running an application that is using an internal microphone (built-in audio), such as some teleconference tools.
image:system-menu.png[System menu]
.Settings
*Settings* provides other general options to configure sound.
.Tweaks
The *Tweaks* application enables you to configure only volume over-amplification.
image:tweaks.png[Tweak application]
[role="_additional-resources"]
.Additional resources
* For more information about *PipeWire*, see the `pipewire` man page on your system.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
:experimental:
[id="accessing-sound-configuration-in-gnome-control-center_{context}"]
= Accessing sound configuration in Settings
This procedure opens the sound configuration screen in the *Settings*.
. Launch *Settings*.
+
You can use one of the approaches described in
link:https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/9/html/getting_started_with_the_gnome_desktop_environment/assembly_launching-applications-in-gnome_getting-started-with-the-gnome-desktop-environment[Launching applications in GNOME].
Alternatively, you can also launch it from the *system menu* by clicking on its icon.
+
image:system-settings.png[]
. In *Settings*, choose *Sound* from the left vertical bar.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: REFERENCE
:experimental:
[id="sound-options-in-gnome-control-center_{context}"]
= Sound options in Settings
Through the *Sound* menu in *Settings*, you can configure the following sound options:
*Volume Levels*::
The *Volume levels* section shows all currently running applications that can process sound, and allows you to amplify or lower the sound of a particular application.
*Output* and *Input*::
The *Output* and *Input* sections show all built-in audio devices and external audio devices that are currently connected.
*Alert sound*::
The *Alert sound* section shows different themes of system audio alerts.
.The Output section on the sound configuration screen
image:sound-options.png[Options in the sound settings]
:leveloffset: 2
// == Additional resources (or Next steps)
//
// * A bulleted list of links to other material closely related to the contents of the assembly, including xref links to other assemblies in your collection.
// * For more details on writing assemblies, see the link:https://github.com/redhat-documentation/modular-docs#modular-documentation-reference-guide[Modular Documentation Reference Guide].
// * Use a consistent system for file names, IDs, and titles. For tips, see _Anchor Names and File Names_ in link:https://github.com/redhat-documentation/modular-docs#modular-documentation-reference-guide[Modular Documentation Reference Guide].
:!context:
:leveloffset: 2
:leveloffset: +1
:parent-context-of-enabling-accessibility-for-visually-impaired-users: {context}
:_mod-docs-content-type: ASSEMBLY
[id="enabling-accessibility-for-visually-impaired-users_{context}"]
= Enabling accessibility for visually impaired users
:context: enabling-accessibility-for-visually-impaired-users
As a system administrator, you can configure the desktop environment to support users with a visual impairment.
To enable accessibility, perform the following procedures.
:leveloffset: +1
:_mod-docs-content-type: CONCEPT
[id="con_components-that-provide-accessibility-features_{context}"]
= Components that provide accessibility features
[role="_abstract"]
On the {ProductShortName}{nbsp}{ProductNumber} desktop, the [application]*Orca* screen reader ensures accessibility for users with a visual impairment. [application]*Orca* is included in the default {ProductShortName} installation.
[application]*Orca* reads information from the screen and communicates it to you using the following components:
Speech Dispatcher::
[application]*Orca* uses [application]*Speech Dispatcher* to communicate with the speech synthesizer. [application]*Speech Dispatcher* supports various speech synthesis backends, ensures that messages from other applications do not to interrupt the messages from Orca, and provides other functionality.
Speech synthesizer::
Provides a speech output. The default speech synthesizer is *eSpeak-NG*.
Braille display::
Provides a tactile output. The *BRLTTY* service enables this functionality.
[role="_additional-resources"]
.Additional resources
* link:https://help.gnome.org/users/orca/stable/[Orca help page]
:leveloffset: 2
// This procedure is different between RHEL 8 and 9.
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
:experimental:
[id="enabling-the-accessibility-menu_{context}"]
= Enabling the Accessibility menu
You can enable the *Accessibility menu* icon in the top panel, which provides a menu with several accessibility options.
.Procedure
. Open the [application]*Settings* application.
. Select *Accessibility*.
. Enable the *Always Show Accessibility Menu* item.
+
.Enabling the Accessibility menu in Settings
image:always-show-accessibility-menu.png[]
.Verification
* Check that the *Accessibility menu* icon is displayed on the top bar even when all options from this menu are switched off.
+
image:accessibility-menu.png[]
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="enabling-the-screen-reader_{context}"]
= Enabling the screen reader
You can enable the *Orca* screen reader in your desktop environment. The screen reader then reads the text displayed on the screen to improve accessibility.
.Procedure
* Enable the screen reader using either of the following ways:
** Press the kbd:[Super+Alt+S] keyboard shortcut.
** If the top panel shows the *Universal Access* menu, select *Screen Reader* in the menu.
.Verification
. Open an application with text content.
. Check that the screen reader reads the text in the application.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: ASSEMBLY
:parent-context-of-enabling-a-braille-display-device: {context}
[id="enabling-a-braille-display-device_{context}"]
= Enabling a Braille display device
:context: enabling-a-braille-display-device
The Braille display is a device that uses the `brltty` service to provide tactile output for visually impaired users.
In order for the Braille display to work correctly, perform the following procedures.
:leveloffset: +1
:_mod-docs-content-type: CONCEPT
[id="supported-braille-device-types_{context}"]
= Supported types of Braille display device
The following types of Braille display devices are supported on {ProductShortName}{nbsp}{ProductNumber}.
.Braille display device types and the corresponding syntax
[options="header"]
|=======
| Braille device type | Syntax of the type | Note
| Serial device | `serial:path` | Relative paths are at [filename]`/dev`.
| USB device | `[serial-number]` | The brackets (`[]`) here indicate optionality.
| Bluetooth device | `bluetooth:address` |
|=======
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="enabling-the-brltty-service_{context}"]
= Enabling the brltty service
To enable the Braille display, enable the `brltty` service to start automatically on boot. By default, `brltty` is disabled.
.Prerequisites
* Ensure that the `brltty` package is installed:
+
[subs="+attributes"]
----
# {PackageManagerCommand} install brltty
----
* Optionally, you can install speech synthesis support for `brltty`:
+
[subs="+attributes"]
----
# {PackageManagerCommand} install brltty-espeak-ng
----
.Procedure
* Enable the `brltty` service to start on boot:
+
----
# systemctl enable --now brltty
----
.Verification
. Reboot the system.
. Check that the `brltty` service is running:
+
----
# systemctl status brltty
● brltty.service - Braille display driver for Linux/Unix
Loaded: loaded (/usr/lib/systemd/system/brltty.service; enabled; vendor pres>
Active: active (running) since Tue 2019-09-10 14:13:02 CEST; 39s ago
Process: 905 ExecStart=/usr/bin/brltty (code=exited, status=0/SUCCESS)
Main PID: 914 (brltty)
Tasks: 3 (limit: 11360)
Memory: 4.6M
CGroup: /system.slice/brltty.service
└─914 /usr/bin/brltty
----
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="authorizing-users-of-braille-display-device_{context}"]
= Authorizing users of a Braille display device
To use a Braille display device, you must set the users who are authorized to use the Braille display device.
.Procedure
. In the [filename]`/etc/brltty.conf` file, ensure that `keyfile` is set to `/etc/brlapi.key`:
+
----
api-parameters Auth=keyfile:/etc/brlapi.key
----
+
This is the default value. Your organization might have overridden it.
. Authorize the selected users by adding them to the `brlapi` group:
+
[subs="+quotes"]
----
# usermod --append -G brlapi __user-name__
----
[role="_additional-resources"]
.Additional resources
* link:https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/{ProductNumberLink}/html/configuring_basic_system_settings/managing-users-and-groups_configuring-basic-system-settings#editing-user-groups-using-the-command-line_managing-users-and-groups[Editing user groups using the command line]
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="setting-the-driver-for-a-braille-display_{context}"]
= Setting the driver for a Braille display device
The `brltty` service automatically chooses a driver for your Braille display device. If the automatic detection fails or takes too long, you can set the driver manually.
.Prerequisites
* The automatic driver detection has failed or takes too long.
.Procedure
. Open the [filename]`/etc/brltty.conf` configuration file.
. Find the `braille-driver` directive, which specifies the driver for your Braille display device.
. Specify the identification code of the required driver in the `braille-driver` directive.
+
Choose the identification code of required driver from the list provided in [filename]`/etc/brltty.conf`. For example, to use the XWindow driver:
+
----
# XWindow
braille-driver xw
----
+
To set multiple drivers, list them separated by commas. Automatic detection then chooses from the listed drivers.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="connecting-a-braille-display-device_{context}"]
= Connecting a Braille display device
The `brltty` service automatically connects to your Braille display device. If the automatic detection fails, you can set the connection method manually.
.Prerequisites
* The Braille display device is physically connected to your system.
* The automatic connection has failed.
.Procedure
. If the device is connected by a serial-to-USB adapter, find the actual device name in the kernel messages on the device plug:
+
----
# journalctl --dmesg | fgrep ttyUSB
----
. Open the [filename]`/etc/brltty.conf` configuration file.
. Find the `braille-device` directive.
. In the `braille-device` directive, specify the connection.
+
You can also set multiple devices, separated by commas, and each of them will be probed in turn.
+
For example:
+
.Settings for the first serial device
====
----
braille-device serial:ttyS0
----
====
+
.Settings for the first USB device matching Braille driver
====
----
braille-device usb:
----
====
+
.Settings for a specific USB device by serial number
====
----
braille-device usb:nnnnn
----
====
+
.Settings for a serial-to-USB adapter
====
Use the device name that you found earlier in the kernel messages:
----
braille-device serial:ttyUSB0
----
NOTE: Setting `braille-device` to `usb:` does not work for a serial-to-USB adapter.
====
+
.Settings for a specific Bluetooth device by address
====
----
braille-device bluetooth:xx:xx:xx:xx:xx:xx
----
====
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="setting-the-text-table_{context}"]
= Setting the text table
The `brltty` service automatically selects a text table based on your system language. If your system language does not match the language of a document that you want to read, you can set the text table manually.
.Procedure
. Edit the [filename]`/etc/brltty.conf` file.
. Identify the code of your selected text table.
+
You can find all available text tables in the `/etc/brltty/Text/` directory. The code is the file name of the text table without its file suffix.
. Specify the code of the selected text table in the `text-table` directive.
+
For example, to use the text table for American English:
+
----
text-table en_US # English (United States)
----
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="setting-the-contraction-table_{context}"]
= Setting the contraction table
You can select which table is used to encode the abbreviations with a Braille display device. Relative paths to particular contraction tables are stored within the [filename]`/etc/brltty/Contraction/` directory.
WARNING: If no table is specified, the `brltty` service does not use a contraction table.
.Procedure
* Choose a contraction table from the list in the [filename]`/etc/brltty.conf` file.
+
For example, to use the contraction table for American English, grade 2:
+
----
contraction-table en-us-g2 # English (US, grade 2)
----
:leveloffset: 2
:context: {parent-context-of-enabling-a-braille-display-device}
:!context:
:leveloffset: 2
:!context:
:leveloffset: 2
:leveloffset: +1
:parent-context-of-special-characters-in-gnome: {context}
:_mod-docs-content-type: ASSEMBLY
[id="special-characters-in-gnome_{context}"]
= Using special characters in GNOME
:context: special-characters-in-gnome
In GNOME, you can use the Compose Key to type special characters from different languages and symbol sets, including those not available on your keyboard. You can enter and view special characters from different languages and symbol sets, making it easy to work with diverse character sets in GNOME.
To input these special characters, you can define one of the existing keys on your keyboard as a Compose Key. Once enabled, the Compose Key allows you to type special characters and symbols by pressing multiple keys in a specific sequence.
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
:experimental:
[id="enabling-the-compose-key-for-an-individual-user_{context}"]
= Enabling the Compose Key for an individual user
You can enable the Compose Key from the Settings menu while logged in as the user.
.Procedure
. Click on the *Activities* button in the upper-left corner of the screen.
. Type *Settings* and click on the *Settings* icon to open the Settings application.
. In the Settings window, click on *Keyboard* in the left sidebar.
. Scroll down and select the *Compose Key* option.
. Toggle the slider to enable the *Compose Key*.
. Select the key you want to use as the Compose Key.
. Once you have selected the Compose Key, close the Settings window.
Now the Compose Key is enabled, and you can use it to input special characters and symbols by pressing the Compose Key, followed by the corresponding sequence of keys.
To see available multi-key sequences for composing special characters, use:
----
$ grep "<Multi_key>" /usr/share/X11/locale/en_US.UTF-8/Compose
----
.Verification
* Press the Compose Key, then type the sequence of keys for the special character you want to input. For example, to type `©`, press the kbd:[Compose Key], then press kbd:[o] and kbd:[c].
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="enabling-the-compose-key-for-another-user_{context}"]
= Enabling the Compose Key for another user
You can enable the Compose Key for another user with the `gsettings` utility.
.Prerequisites
* Administrative access.
.Procedure
. Allow all clients to connect to the X server:
+
----
# xhost +
----
. Run the following command to set the Compose Key:
+
----
# su - <username> -c "gsettings set org.gnome.desktop.input-sources xkb-options \"['compose:<compose_key>']\""
----
+
Replace `<username>` with the username of the user for whom you want to enable the Compose Key. Replace `<compose_key>` with the key you want to use as the Compose Key. You can use the `ralt` option to designate the right kbd:[Alt] key as the Compose Key.
+
To see other Compose Key options that you can use to set up a Compose Key on your keyboard, use:
+
----
$ grep compose /usr/share/X11/xkb/rules/evdev.lst
----
. Resets the access control:
+
----
# xhost -
----
.Verification
* To check the Compose Key settings for another user, use:
+
----
# su - <username> -c "gsettings get org.gnome.desktop.input-sources xkb-options"
----
+
Replace `<username>` with the username of the user for whom you want to check the Compose Key setting.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="enabling-the-compose-key-for-all-users_{context}"]
= Enabling the Compose Key for all users
You can enable the Compose Key for all users by creating a `dconf` configuration file.
.Prerequisites
* Administrative access.
.Procedure
. Create the `/etc/dconf/db/local.d/00-compose-key` configuration file with the following content:
+
[org/gnome/desktop/lockdown]
# Disable command prompt
disable-command-line=true
----
. Create a new file under the `/etc/dconf/db/local.d/locks/` directory and list the keys or subpaths you want to lock down:
+
----
# Lock command prompt
/org/gnome/desktop/lockdown/disable-command-line
----
. Apply the changes to the system databases:
+
----
# dconf update
----
. For this settings to take effect, users needs to log out and log back in.
:leveloffset: 1
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="disabling-repartitioning_{context}"]
= Disabling repartitioning
You can override the default system settings that control disk management.
IMPORTANT: Avoid modifying the `/usr/share/polkit-1/actions/org.freedesktop.udisks2.policy` file directly. Any changes you make will be replaced during the next package update.
.Prerequisites
* Administrative access.
.Procedure
. Copy the `/usr/share/polkit-1/actions/org.freedesktop.udisks2.policy` file under the `/etc/share/polkit-1/actions/` directory:
+
----
# cp /usr/share/polkit-1/actions/org.freedesktop.udisks2.policy /etc/share/polkit-1/actions/org.freedesktop.udisks2.policy
----
. In the `/etc/polkit-1/actions/org.freedesktop.udisks2.policy` file, delete any actions that you do not need and add the following lines:
+
[source,xml]
----
<action id="org.freedesktop.udisks2.modify-device">
<message>Authentication is required to modify the disks settings</message>
<defaults>
<allow_any>no</allow_any>
<allow_inactive>no</allow_inactive>
<allow_active>yes</allow_active>
</defaults>
</action>
----
+
If you want to restrict access only to the root user, replace `<allow_any>no</allow_any>` with `<allow_any>auth_admin</allow_any>`.
:leveloffset: 2
:context: {parent-context-of-restricting-the-desktop-session}
:leveloffset!:
:leveloffset: +1
:_mod-docs-content-type: ASSEMBLY
:parent-context-of-assembly_restricting-the-session-to-a-single-application: {context}
[id="assembly_restricting-the-session-to-a-single-application_{context}"]
= Restricting the session to a single application
:context: assembly_restricting-the-session-to-a-single-application
[role="_abstract"]
You can start the GNOME session in single-application mode, also known as kiosk mode. In this session, GNOME displays only a full-screen window of the application that you have selected.
// == Prerequisites
// * A bulleted list of conditions that must be satisfied before the user starts following this assembly.
// * You can also link to other modules or assemblies the user must follow before starting this assembly.
// * Delete the section title and bullets if the assembly has no prerequisites.
// * X is installed. For information about installing X, see <link>.
// * You can log in to X with administrator privileges.
:leveloffset: +1
:_mod-docs-content-type: CONCEPT
[id="con_single-application-mode_{context}"]
= Single-application mode
[role="_abstract"]
Single-application mode is a modified GNOME session that reconfigures the Mutter window manager into an interactive kiosk. This session locks down certain behavior to make the standard desktop more restrictive. The user can interact only with a single application selected by the administrator.
You can set up single-application mode for several use cases, such as:
* In the communication, entertainment, or education fields
* As a self-serve machine
* As an event manager
* As a registration point
The GNOME Kiosk utility provides the single-application mode configuration and sessions.
The following single-application sessions are available:
Search Appliance Session::
This session always starts the *Mozilla Firefox* web browser at the `www.google.com` website.
Kiosk Script Session::
This session starts an arbitrary application that you specify in a shell script.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="enabling-search-appliance-mode_{context}"]
= Enabling search appliance mode
[role="_abstract"]
This procedure installs and enables the Search Appliance Session, which restricts the GNOME session to the Google search engine in a web browser.
// .Prerequisites
// * A bulleted list of conditions that must be satisfied before the user starts following this module.
// * You can also link to other modules or assemblies the user must follow before starting this module.
// * Delete the section title and bullets if the module has no prerequisites.
.Procedure
. Install the GNOME Kiosk packages:
+
[subs="+attributes"]
----
# {PackageManagerCommand} install gnome-kiosk gnome-kiosk-search-appliance
----
. At the GNOME login screen, select *Search Appliance Session* from the gear button menu and log in as the single-application user.
. The *Mozilla Firefox* browser opens as a full-screen window in its kiosk mode. It shows the Google search page.
// .Verification
// . Start each step with an active verb.
// . Include one command or action per step.
// . Use an unnumbered bullet (*) if the procedure includes only one step.
[role="_additional-resources"]
.Additional resources
* The `/usr/share/doc/gnome-kiosk/README.md` file provided by the [package]`gnome-kiosk` package.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="proc_enabling-single-application-mode_{context}"]
= Enabling single-application mode
[role="_abstract"]
This procedure installs and enables the Kiosk Script Session, which restricts the GNOME session to a selected single application.
// .Prerequisites
// * A bulleted list of conditions that must be satisfied before the user starts following this module.
// * You can also link to other modules or assemblies the user must follow before starting this module.
// * Delete the section title and bullets if the module has no prerequisites.
.Procedure
. Install the GNOME Kiosk packages:
+
[subs="+attributes"]
----
# {PackageManagerCommand} install gnome-kiosk gnome-kiosk-script-session
----
. At the GNOME login screen, select *Kiosk Script Session* from the gear button menu and log in as the single-application user.
. The *gedit* text editor opens as a full-screen window. It shows the shell script that configures which application runs in your single-application session.
+
Edit the shell script and enter the application that you want to start in the single-application session.
+
For example, to start the *Mozilla Firefox* browser, enter the following content:
+
----
#!/usr/bin/sh
firefox --kiosk https://example.org
----
. Save the script file.
. Close the *gedit* window.
+
The session terminates and restarts with your selected application.
. The next time you log into the single-application session, your selected application runs.
// .Verification
// . Start each step with an active verb.
// . Include one command or action per step.
// . Use an unnumbered bullet (*) if the procedure includes only one step.
[role="_additional-resources"]
.Additional resources
* The `/usr/share/doc/gnome-kiosk/README.md` file provided by the [package]`gnome-kiosk` package.
:leveloffset: 2
// [role="_additional-resources"]
// == Additional resources (or Next steps)
// * A bulleted list of links to other closely-related material. These links can include `link:` and `xref:` macros.
// * For more details on writing assemblies, see the link:https://github.com/redhat-documentation/modular-docs#modular-documentation-reference-guide[Modular Documentation Reference Guide].
// * Use a consistent system for file names, IDs, and titles. For tips, see _Anchor Names and File Names_ in link:https://github.com/redhat-documentation/modular-docs#modular-documentation-reference-guide[Modular Documentation Reference Guide].
:!context:
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: ASSEMBLY
:parent-context-of-configuring-sound-in-gnome: {context}
:context: configuring-sound-in-gnome
[id="configuring-sound-in-gnome_{context}"]
= Configuring sound in GNOME
You can configure sound volume and other sound options in GNOME.
// .Prerequisites
//
// * A bulleted list of conditions that must be satisfied before the user starts following this assembly.
// * You can also link to other modules or assemblies the user must follow before starting this assembly.
// * Delete the section title and bullets if the assembly has no prerequisites.
:leveloffset: +1
:_mod-docs-content-type: CONCEPT
[id="sound-configuration-tools-in-gnome_{context}"]
= Sound configuration tools in GNOME
In RHEL 9, the *PipeWire* sound server handles sound output and input. *PipeWire* lets programs output the audio using the `pipewire` daemon.
To configure sound, you can use one of the following graphical applications in GNOME:
.System menu
The *system menu* is located in the top-right screen corner. It enables you only to set the intensity of the sound output or sound input through the sound bar. The sound bar for input sound is available only if you are running an application that is using an internal microphone (built-in audio), such as some teleconference tools.
image:system-menu.png[System menu]
.Settings
*Settings* provides other general options to configure sound.
.Tweaks
The *Tweaks* application enables you to configure only volume over-amplification.
image:tweaks.png[Tweak application]
[role="_additional-resources"]
.Additional resources
* For more information about *PipeWire*, see the `pipewire` man page on your system.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
:experimental:
[id="accessing-sound-configuration-in-gnome-control-center_{context}"]
= Accessing sound configuration in Settings
This procedure opens the sound configuration screen in the *Settings*.
. Launch *Settings*.
+
You can use one of the approaches described in
link:https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/9/html/getting_started_with_the_gnome_desktop_environment/assembly_launching-applications-in-gnome_getting-started-with-the-gnome-desktop-environment[Launching applications in GNOME].
Alternatively, you can also launch it from the *system menu* by clicking on its icon.
+
image:system-settings.png[]
. In *Settings*, choose *Sound* from the left vertical bar.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: REFERENCE
:experimental:
[id="sound-options-in-gnome-control-center_{context}"]
= Sound options in Settings
Through the *Sound* menu in *Settings*, you can configure the following sound options:
*Volume Levels*::
The *Volume levels* section shows all currently running applications that can process sound, and allows you to amplify or lower the sound of a particular application.
*Output* and *Input*::
The *Output* and *Input* sections show all built-in audio devices and external audio devices that are currently connected.
*Alert sound*::
The *Alert sound* section shows different themes of system audio alerts.
.The Output section on the sound configuration screen
image:sound-options.png[Options in the sound settings]
:leveloffset: 2
// == Additional resources (or Next steps)
//
// * A bulleted list of links to other material closely related to the contents of the assembly, including xref links to other assemblies in your collection.
// * For more details on writing assemblies, see the link:https://github.com/redhat-documentation/modular-docs#modular-documentation-reference-guide[Modular Documentation Reference Guide].
// * Use a consistent system for file names, IDs, and titles. For tips, see _Anchor Names and File Names_ in link:https://github.com/redhat-documentation/modular-docs#modular-documentation-reference-guide[Modular Documentation Reference Guide].
:!context:
:leveloffset: 2
:leveloffset: +1
:parent-context-of-enabling-accessibility-for-visually-impaired-users: {context}
:_mod-docs-content-type: ASSEMBLY
[id="enabling-accessibility-for-visually-impaired-users_{context}"]
= Enabling accessibility for visually impaired users
:context: enabling-accessibility-for-visually-impaired-users
As a system administrator, you can configure the desktop environment to support users with a visual impairment.
To enable accessibility, perform the following procedures.
:leveloffset: +1
:_mod-docs-content-type: CONCEPT
[id="con_components-that-provide-accessibility-features_{context}"]
= Components that provide accessibility features
[role="_abstract"]
On the {ProductShortName}{nbsp}{ProductNumber} desktop, the [application]*Orca* screen reader ensures accessibility for users with a visual impairment. [application]*Orca* is included in the default {ProductShortName} installation.
[application]*Orca* reads information from the screen and communicates it to you using the following components:
Speech Dispatcher::
[application]*Orca* uses [application]*Speech Dispatcher* to communicate with the speech synthesizer. [application]*Speech Dispatcher* supports various speech synthesis backends, ensures that messages from other applications do not to interrupt the messages from Orca, and provides other functionality.
Speech synthesizer::
Provides a speech output. The default speech synthesizer is *eSpeak-NG*.
Braille display::
Provides a tactile output. The *BRLTTY* service enables this functionality.
[role="_additional-resources"]
.Additional resources
* link:https://help.gnome.org/users/orca/stable/[Orca help page]
:leveloffset: 2
// This procedure is different between RHEL 8 and 9.
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
:experimental:
[id="enabling-the-accessibility-menu_{context}"]
= Enabling the Accessibility menu
You can enable the *Accessibility menu* icon in the top panel, which provides a menu with several accessibility options.
.Procedure
. Open the [application]*Settings* application.
. Select *Accessibility*.
. Enable the *Always Show Accessibility Menu* item.
+
.Enabling the Accessibility menu in Settings
image:always-show-accessibility-menu.png[]
.Verification
* Check that the *Accessibility menu* icon is displayed on the top bar even when all options from this menu are switched off.
+
image:accessibility-menu.png[]
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="enabling-the-screen-reader_{context}"]
= Enabling the screen reader
You can enable the *Orca* screen reader in your desktop environment. The screen reader then reads the text displayed on the screen to improve accessibility.
.Procedure
* Enable the screen reader using either of the following ways:
** Press the kbd:[Super+Alt+S] keyboard shortcut.
** If the top panel shows the *Universal Access* menu, select *Screen Reader* in the menu.
.Verification
. Open an application with text content.
. Check that the screen reader reads the text in the application.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: ASSEMBLY
:parent-context-of-enabling-a-braille-display-device: {context}
[id="enabling-a-braille-display-device_{context}"]
= Enabling a Braille display device
:context: enabling-a-braille-display-device
The Braille display is a device that uses the `brltty` service to provide tactile output for visually impaired users.
In order for the Braille display to work correctly, perform the following procedures.
:leveloffset: +1
:_mod-docs-content-type: CONCEPT
[id="supported-braille-device-types_{context}"]
= Supported types of Braille display device
The following types of Braille display devices are supported on {ProductShortName}{nbsp}{ProductNumber}.
.Braille display device types and the corresponding syntax
[options="header"]
|=======
| Braille device type | Syntax of the type | Note
| Serial device | `serial:path` | Relative paths are at [filename]`/dev`.
| USB device | `[serial-number]` | The brackets (`[]`) here indicate optionality.
| Bluetooth device | `bluetooth:address` |
|=======
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="enabling-the-brltty-service_{context}"]
= Enabling the brltty service
To enable the Braille display, enable the `brltty` service to start automatically on boot. By default, `brltty` is disabled.
.Prerequisites
* Ensure that the `brltty` package is installed:
+
[subs="+attributes"]
----
# {PackageManagerCommand} install brltty
----
* Optionally, you can install speech synthesis support for `brltty`:
+
[subs="+attributes"]
----
# {PackageManagerCommand} install brltty-espeak-ng
----
.Procedure
* Enable the `brltty` service to start on boot:
+
----
# systemctl enable --now brltty
----
.Verification
. Reboot the system.
. Check that the `brltty` service is running:
+
----
# systemctl status brltty
● brltty.service - Braille display driver for Linux/Unix
Loaded: loaded (/usr/lib/systemd/system/brltty.service; enabled; vendor pres>
Active: active (running) since Tue 2019-09-10 14:13:02 CEST; 39s ago
Process: 905 ExecStart=/usr/bin/brltty (code=exited, status=0/SUCCESS)
Main PID: 914 (brltty)
Tasks: 3 (limit: 11360)
Memory: 4.6M
CGroup: /system.slice/brltty.service
└─914 /usr/bin/brltty
----
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="authorizing-users-of-braille-display-device_{context}"]
= Authorizing users of a Braille display device
To use a Braille display device, you must set the users who are authorized to use the Braille display device.
.Procedure
. In the [filename]`/etc/brltty.conf` file, ensure that `keyfile` is set to `/etc/brlapi.key`:
+
----
api-parameters Auth=keyfile:/etc/brlapi.key
----
+
This is the default value. Your organization might have overridden it.
. Authorize the selected users by adding them to the `brlapi` group:
+
[subs="+quotes"]
----
# usermod --append -G brlapi __user-name__
----
[role="_additional-resources"]
.Additional resources
* link:https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/{ProductNumberLink}/html/configuring_basic_system_settings/managing-users-and-groups_configuring-basic-system-settings#editing-user-groups-using-the-command-line_managing-users-and-groups[Editing user groups using the command line]
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="setting-the-driver-for-a-braille-display_{context}"]
= Setting the driver for a Braille display device
The `brltty` service automatically chooses a driver for your Braille display device. If the automatic detection fails or takes too long, you can set the driver manually.
.Prerequisites
* The automatic driver detection has failed or takes too long.
.Procedure
. Open the [filename]`/etc/brltty.conf` configuration file.
. Find the `braille-driver` directive, which specifies the driver for your Braille display device.
. Specify the identification code of the required driver in the `braille-driver` directive.
+
Choose the identification code of required driver from the list provided in [filename]`/etc/brltty.conf`. For example, to use the XWindow driver:
+
----
# XWindow
braille-driver xw
----
+
To set multiple drivers, list them separated by commas. Automatic detection then chooses from the listed drivers.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="connecting-a-braille-display-device_{context}"]
= Connecting a Braille display device
The `brltty` service automatically connects to your Braille display device. If the automatic detection fails, you can set the connection method manually.
.Prerequisites
* The Braille display device is physically connected to your system.
* The automatic connection has failed.
.Procedure
. If the device is connected by a serial-to-USB adapter, find the actual device name in the kernel messages on the device plug:
+
----
# journalctl --dmesg | fgrep ttyUSB
----
. Open the [filename]`/etc/brltty.conf` configuration file.
. Find the `braille-device` directive.
. In the `braille-device` directive, specify the connection.
+
You can also set multiple devices, separated by commas, and each of them will be probed in turn.
+
For example:
+
.Settings for the first serial device
====
----
braille-device serial:ttyS0
----
====
+
.Settings for the first USB device matching Braille driver
====
----
braille-device usb:
----
====
+
.Settings for a specific USB device by serial number
====
----
braille-device usb:nnnnn
----
====
+
.Settings for a serial-to-USB adapter
====
Use the device name that you found earlier in the kernel messages:
----
braille-device serial:ttyUSB0
----
NOTE: Setting `braille-device` to `usb:` does not work for a serial-to-USB adapter.
====
+
.Settings for a specific Bluetooth device by address
====
----
braille-device bluetooth:xx:xx:xx:xx:xx:xx
----
====
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="setting-the-text-table_{context}"]
= Setting the text table
The `brltty` service automatically selects a text table based on your system language. If your system language does not match the language of a document that you want to read, you can set the text table manually.
.Procedure
. Edit the [filename]`/etc/brltty.conf` file.
. Identify the code of your selected text table.
+
You can find all available text tables in the `/etc/brltty/Text/` directory. The code is the file name of the text table without its file suffix.
. Specify the code of the selected text table in the `text-table` directive.
+
For example, to use the text table for American English:
+
----
text-table en_US # English (United States)
----
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="setting-the-contraction-table_{context}"]
= Setting the contraction table
You can select which table is used to encode the abbreviations with a Braille display device. Relative paths to particular contraction tables are stored within the [filename]`/etc/brltty/Contraction/` directory.
WARNING: If no table is specified, the `brltty` service does not use a contraction table.
.Procedure
* Choose a contraction table from the list in the [filename]`/etc/brltty.conf` file.
+
For example, to use the contraction table for American English, grade 2:
+
----
contraction-table en-us-g2 # English (US, grade 2)
----
:leveloffset: 2
:context: {parent-context-of-enabling-a-braille-display-device}
:!context:
:leveloffset: 2
:!context:
:leveloffset: 2
:leveloffset: +1
:parent-context-of-special-characters-in-gnome: {context}
:_mod-docs-content-type: ASSEMBLY
[id="special-characters-in-gnome_{context}"]
= Using special characters in GNOME
:context: special-characters-in-gnome
In GNOME, you can use the Compose Key to type special characters from different languages and symbol sets, including those not available on your keyboard. You can enter and view special characters from different languages and symbol sets, making it easy to work with diverse character sets in GNOME.
To input these special characters, you can define one of the existing keys on your keyboard as a Compose Key. Once enabled, the Compose Key allows you to type special characters and symbols by pressing multiple keys in a specific sequence.
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
:experimental:
[id="enabling-the-compose-key-for-an-individual-user_{context}"]
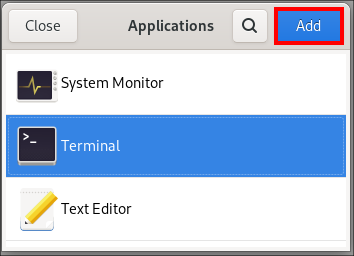
= Enabling the Compose Key for an individual user
You can enable the Compose Key from the Settings menu while logged in as the user.
.Procedure
. Click on the *Activities* button in the upper-left corner of the screen.
. Type *Settings* and click on the *Settings* icon to open the Settings application.
. In the Settings window, click on *Keyboard* in the left sidebar.
. Scroll down and select the *Compose Key* option.
. Toggle the slider to enable the *Compose Key*.
. Select the key you want to use as the Compose Key.
. Once you have selected the Compose Key, close the Settings window.
Now the Compose Key is enabled, and you can use it to input special characters and symbols by pressing the Compose Key, followed by the corresponding sequence of keys.
To see available multi-key sequences for composing special characters, use:
----
$ grep "<Multi_key>" /usr/share/X11/locale/en_US.UTF-8/Compose
----
.Verification
* Press the Compose Key, then type the sequence of keys for the special character you want to input. For example, to type `©`, press the kbd:[Compose Key], then press kbd:[o] and kbd:[c].
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="enabling-the-compose-key-for-another-user_{context}"]
= Enabling the Compose Key for another user
You can enable the Compose Key for another user with the `gsettings` utility.
.Prerequisites
* Administrative access.
.Procedure
. Allow all clients to connect to the X server:
+
----
# xhost +
----
. Run the following command to set the Compose Key:
+
----
# su - <username> -c "gsettings set org.gnome.desktop.input-sources xkb-options \"['compose:<compose_key>']\""
----
+
Replace `<username>` with the username of the user for whom you want to enable the Compose Key. Replace `<compose_key>` with the key you want to use as the Compose Key. You can use the `ralt` option to designate the right kbd:[Alt] key as the Compose Key.
+
To see other Compose Key options that you can use to set up a Compose Key on your keyboard, use:
+
----
$ grep compose /usr/share/X11/xkb/rules/evdev.lst
----
. Resets the access control:
+
----
# xhost -
----
.Verification
* To check the Compose Key settings for another user, use:
+
----
# su - <username> -c "gsettings get org.gnome.desktop.input-sources xkb-options"
----
+
Replace `<username>` with the username of the user for whom you want to check the Compose Key setting.
:leveloffset: 2
:leveloffset: +1
:_mod-docs-content-type: PROCEDURE
[id="enabling-the-compose-key-for-all-users_{context}"]
= Enabling the Compose Key for all users
You can enable the Compose Key for all users by creating a `dconf` configuration file.
.Prerequisites
* Administrative access.
.Procedure
. Create the `/etc/dconf/db/local.d/00-compose-key` configuration file with the following content:
+