このコンテンツは選択した言語では利用できません。
Developer Guide
For use with Red Hat JBoss Data Grid 6.2.1
Edition 3
Abstract
Part I. Programmable APIs
- Cache
- Batching
- Grouping
- Persistence (formerly CacheStore)
- ConfigurationBuilder
- Externalizable
- Notification (also known as the Listener API because it deals with Notifications and Listeners)
Chapter 1. The Cache API
ConcurrentMap interface. How entries are stored depends on the cache mode in use. For example, an entry may be replicated to a remote node or an entry may be looked up in a cache store.
Note
1.1. Using the ConfigurationBuilder API to Configure the Cache API
ConfigurationBuilder helper object.
An explanation of each line of the provided configuration is as follows:
Configuration c = new ConfigurationBuilder().clustering().cacheMode(CacheMode.REPL_SYNC).build();
Configuration c = new ConfigurationBuilder().clustering().cacheMode(CacheMode.REPL_SYNC).build();Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the first line of the configuration, a new cache configuration object (namedc) is created using theConfigurationBuilder. Configurationcis assigned the default values for all cache configuration options except the cache mode, which is overridden and set to synchronous replication (REPL_SYNC).String newCacheName = "repl";
String newCacheName = "repl";Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the second line of the configuration, a new variable (of typeString) is created and assigned the valuerepl.manager.defineConfiguration(newCacheName, c);
manager.defineConfiguration(newCacheName, c);Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the third line of the configuration, the cache manager is used to define a named cache configuration for itself. This named cache configuration is calledrepland its configuration is based on the configuration provided for cache configurationcin the first line.Cache<String, String> cache = manager.getCache(newCacheName);
Cache<String, String> cache = manager.getCache(newCacheName);Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the fourth line of the configuration, the cache manager is used to obtain a reference to the unique instance of thereplthat is held by the cache manager. This cache instance is now ready to be used to perform operations to store and retrieve data.
Note
org.infinispan.jmx.JmxDomainConflictException: Domain already registered org.infinispan.
1.2. Per-Invocation Flags
1.2.1. Per-Invocation Flag Functions
putForExternalRead() method in Red Hat JBoss Data Grid's Cache API uses flags internally. This method can load a JBoss Data Grid cache with data loaded from an external resource. To improve the efficiency of this call, JBoss Data Grid calls a normal put operation passing the following flags:
- The
ZERO_LOCK_ACQUISITION_TIMEOUTflag: JBoss Data Grid uses an almost zero lock acquisition time when loading data from an external source into a cache. - The
FAIL_SILENTLYflag: If the locks cannot be acquired, JBoss Data Grid fails silently without throwing any lock acquisition exceptions. - The
FORCE_ASYNCHRONOUSflag: If clustered, the cache replicates asynchronously, irrespective of the cache mode set. As a result, a response from other nodes is not required.
putForExternalRead calls of this type are used because the client can retrieve the required data from a persistent store if the data cannot be found in memory. If the client encounters a cache miss, it retries the operation.
1.2.2. Configure Per-Invocation Flags
withFlags() method call. For example:
Cache cache = ...
cache.getAdvancedCache()
.withFlags(Flag.SKIP_CACHE_STORE, Flag.CACHE_MODE_LOCAL)
.put("local", "only");
Cache cache = ...
cache.getAdvancedCache()
.withFlags(Flag.SKIP_CACHE_STORE, Flag.CACHE_MODE_LOCAL)
.put("local", "only");
Note
withFlags() method for each invocation. If the cache operation must be replicated onto another node, the flags are also carried over to the remote nodes.
1.2.3. Per-Invocation Flags Example
put(), must not return the previous value, the IGNORE_RETURN_VALUES flag is used. This flag prevents a remote lookup (to get the previous value) in a distributed environment, which in turn prevents the retrieval of the undesired, potential, previous value. Additionally, if the cache is configured with a cache loader, this flag prevents the previous value from being loaded from its cache store.
IGNORE_RETURN_VALUES flag is:
Cache cache = ...
cache.getAdvancedCache()
.withFlags(Flag.IGNORE_RETURN_VALUES)
.put("local", "only")
Cache cache = ...
cache.getAdvancedCache()
.withFlags(Flag.IGNORE_RETURN_VALUES)
.put("local", "only")
1.3. The AdvancedCache Interface
AdvancedCache interface, geared towards extending JBoss Data Grid, in addition to its simple Cache Interface. The AdvancedCache Interface can:
- Inject custom interceptors
- Access certain internal components
- Apply flags to alter the behavior of certain cache methods
AdvancedCache:
AdvancedCache advancedCache = cache.getAdvancedCache();
AdvancedCache advancedCache = cache.getAdvancedCache();
1.3.1. Flag Usage with the AdvancedCache Interface
AdvancedCache.withFlags() to apply any number of flags to a cache invocation, for example:
advancedCache.withFlags(Flag.CACHE_MODE_LOCAL, Flag.SKIP_LOCKING)
.withFlags(Flag.FORCE_SYNCHRONOUS)
.put("hello", "world");
advancedCache.withFlags(Flag.CACHE_MODE_LOCAL, Flag.SKIP_LOCKING)
.withFlags(Flag.FORCE_SYNCHRONOUS)
.put("hello", "world");
1.3.2. Custom Interceptors and the AdvancedCache Interface
AdvancedCache Interface provides a mechanism that allows advanced developers to attach custom interceptors. Custom interceptors can alter the behavior of the Cache API methods and the AdvacedCache Interface can be used to attach such interceptors programmatically at run time.
1.3.3. Custom Interceptors
1.3.3.1. Custom Interceptor Design
- A custom interceptor must extend the
CommandInterceptor. - A custom interceptor must declare a public, empty constructor to allow for instantiation.
- A custom interceptor must have JavaBean style setters defined for any property that is defined through the
propertyelement.
1.3.3.2. Adding Custom Interceptors Declaratively
Procedure 1.1. Adding Custom Interceptors
Define Custom Interceptors
All custom interceptors must extend org.jboss.cache.interceptors.base.CommandInterceptor. Use the customInterceptors method to add custom interceptors to the cache:<namedCache name="cacheWithCustomInterceptors"> <customInterceptors>
<namedCache name="cacheWithCustomInterceptors"> <customInterceptors>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Define the Position of the New Custom Interceptor
Interceptors must have a defined position. Valid options are:FIRST- Specifies that the new interceptor is placed first in the chain.LAST- Specifies that the new interceptor is placed last in the chain.OTHER_THAN_FIRST_OR_LAST- Specifies that the new interceptor can be placed anywhere except first or last in the chain.
<namedCache name="cacheWithCustomInterceptors"> <customInterceptors> <interceptor position="FIRST" class="com.mycompany.CustomInterceptor1"><namedCache name="cacheWithCustomInterceptors"> <customInterceptors> <interceptor position="FIRST" class="com.mycompany.CustomInterceptor1">Copy to Clipboard Copied! Toggle word wrap Toggle overflow Define Interceptor Properties
Define specific interceptor properties.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Apply Other Custom Interceptors
In this example, the next custom interceptor is called CustomInterceptor2.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Define the
index,before, andafterAttributes.- The
indexidentifies the position of this interceptor in the chain, with 0 being the first position. This attribute is mutually exclusive withposition,before, andafter. - The
aftermethod places the new interceptor directly after the instance of the named interceptor specified via its fully qualified class name. This attribute is mutually exclusive withposition,before, andindex. - The
beforemethod places the new interceptor directly before the instance of the named interceptor specified via its fully qualified class name. This attribute is mutually exclusive withposition,after, andindex.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Note
1.3.3.3. Adding Custom Interceptors Programmatically
AdvancedCache.
CacheManager cm = getCacheManager();
Cache aCache = cm.getCache("aName");
AdvancedCache advCache = aCache.getAdvancedCache();
CacheManager cm = getCacheManager();
Cache aCache = cm.getCache("aName");
AdvancedCache advCache = aCache.getAdvancedCache();
addInterceptor() method to add the interceptor.
advCache.addInterceptor(new MyInterceptor(), 0);
advCache.addInterceptor(new MyInterceptor(), 0);
Chapter 2. The Batching API
Note
2.1. About Java Transaction API Transactions
- First, it retrieves the transactions currently associated with the thread.
- If not already done, it registers an
XAResourcewith the transaction manager to receive notifications when a transaction is committed or rolled back.
2.2. Batching and the Java Transaction API (JTA)
- Locks acquired during an invocation are retained until the transaction commits or rolls back.
- All changes are replicated in a batch on all nodes in the cluster as part of the transaction commit process. Ensuring that multiple changes occur within the single transaction, the replication traffic remains lower and improves performance.
- When using synchronous replication or invalidation, a replication or invalidation failure causes the transaction to roll back.
- If a
CacheLoaderthat is compatible with a JTA resource, for example a JTADataSource, is used for a transaction, the JTA resource can also participate in the transaction. - All configurations related to a transaction apply for batching as well.
<transaction syncRollbackPhase="false" syncCommitPhase="false" useEagerLocking="true" eagerLockSingleNode="true" />
<transaction syncRollbackPhase="false"
syncCommitPhase="false"
useEagerLocking="true"
eagerLockSingleNode="true" />
Note
2.3. Using the Batching API
2.3.1. Enable the Batching API
<distributed-cache name="default" batching="true" statistics="true"> ... </distributed-cache>
<distributed-cache name="default" batching="true" statistics="true">
...
</distributed-cache>
2.3.2. Configure the Batching API
To configure the Batching API in the XML file:
<invocationBatching enabled="true" />
<invocationBatching enabled="true" />
To configure the Batching API programmatically use:
Configuration c = new ConfigurationBuilder().invocationBatching().enable().build();
Configuration c = new ConfigurationBuilder().invocationBatching().enable().build();
Note
2.3.3. Use the Batching API
startBatch() and endBatch() on the cache as follows to use batching:
Cache cache = cacheManager.getCache();
Cache cache = cacheManager.getCache();
Example 2.1. Without Using Batch
cache.put("key", "value");
cache.put("key", "value");
cache.put(key, value); line executes, the values are replaced immediately.
Example 2.2. Using Batch
cache.endBatch(true); executes, all modifications made since the batch started are replicated.
cache.endBatch(false); executes, changes made in the batch are discarded.
2.3.4. Batching API Usage Example
Example 2.3. Batching API Usage Example
Chapter 3. The Grouping API
3.1. Grouping API Operations
- Every node can determine which node owns a particular key without expensive metadata updates across nodes.
- Redundancy is improved because ownership information does not need to be replicated if a node fails.
- Intrinsic to the entry, which means it was generated by the key class.
- Extrinsic to the entry, which means it was generated by an external function.
3.2. Grouping API Use Case
Example 3.1. Grouping API Example
DistributedExecutor only checks node AB and quickly and easily retrieves the required employee records.
3.3. Configure the Grouping API
- Enable groups using either the declarative or programmatic method.
- Specify either an intrinsic or extrinsic group. For more information about these group types, see Section 3.1, “Grouping API Operations”
- Register all specified groupers.
3.3.1. Enable Groups
Use the following configuration to enable groups using XML:
Use the following to enable groups programmatically:
Configuration c = new ConfigurationBuilder().clustering().hash().groups().enabled().build();
Configuration c = new ConfigurationBuilder().clustering().hash().groups().enabled().build();3.3.2. Specify an Intrinsic Group
- the key class definition can be altered, that is if it is not part of an unmodifiable library.
- if the key class is not concerned with the determination of a key/value pair group.
@Group annotation in the relevant method to specify an intrinsic group. The group must always be a String, as illustrated in the example:
Example 3.2. Specifying an Intrinsic Group Example
3.3.3. Specify an Extrinsic Group
- the key class definition cannot be altered, that is if it is part of an unmodifiable library.
- if the key class is concerned with the determination of a key/value pair group.
Grouper interface. This interface uses the computeGroup method to return the group.
Grouper interface acts as an interceptor by passing the computed value to computeGroup. If the @Group annotation is used, the group using it is passed to the first Grouper. As a result, using an intrinsic group provides even greater control.
Example 3.3. Specifying an Extrinsic Group Example
Grouper that uses the key class to extract the group from a key using a pattern. Any group information specified on the key class is ignored in such a situation.
3.3.4. Register Groupers
Use the following code to register a grouping using XML:
Use the following code to register a grouper programmatically:
Configuration c = new ConfigurationBuilder().clustering().hash().groups().addGrouper(new KXGrouper()).enabled().build();
Configuration c = new ConfigurationBuilder().clustering().hash().groups().addGrouper(new KXGrouper()).enabled().build();
Chapter 4. The Persistence SPI
- Memory is volatile and a cache store can increase the life span of the information in the cache, which results in improved durability.
- Using persistent external stores as a caching layer between an application and a custom storage engine provides improved Write-Through functionality.
- Using a combination of eviction and passivation, only the frequently required information is stored in-memory and other data is stored in the external storage.
4.1. Persistence SPI Benefits
- Alignment with JSR-107 (http://jcp.org/en/jsr/detail?id=107). JBoss Data Grid's
CacheWriterandCacheLoaderinterfaces are similar to the JSR-107 writer and reader. As a result, alignment with JSR-107 provides improved portability for stores across JCache-compliant vendors. - Simplified transaction integration. JBoss Data Grid handles locking automatically and so implementations do not have to coordinate concurrent access to the store. Depending on the locking mode, concurrent writes on the same key may not occur. However, implementors expect operations on the store to originate from multiple threads and add the implementation code accordingly.
- Reduced serialization, resulting in reduced CPU usage. The new SPI exposes stored entries in a serialized format. If an entry is fetched from persistent storage to be sent remotely, it does not need to be serialized (when reading from the store) and then serialized again (when writing to the wire). Instead, the entry is written to the wire in the serialized format as fetched from the storage.
4.2. Programmatically Configure the Persistence SPI
Note
Chapter 5. The ConfigurationBuilder API
- Chain coding of configuration options in order to make the coding process more efficient
- Improve the readability of the configuration
5.1. Using the ConfigurationBuilder API
5.1.1. Programmatically Create a CacheManager and Replicated Cache
Procedure 5.1. Steps for Programmatic Configuration in JBoss Data Grid
- Create a CacheManager as a starting point in an XML file. If required, this CacheManager can be programmed in runtime to the specification that meets the requirements of the use case. The following is an example of how to create a CacheManager:
EmbeddedCacheManager manager = new DefaultCacheManager("my-config-file.xml"); Cache defaultCache = manager.getCache();EmbeddedCacheManager manager = new DefaultCacheManager("my-config-file.xml"); Cache defaultCache = manager.getCache();Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Create a new synchronously replicated cache programmatically.
- Create a new configuration object instance using the ConfigurationBuilder helper object:
Configuration c = new ConfigurationBuilder().clustering().cacheMode(CacheMode.REPL_SYNC) .build();
Configuration c = new ConfigurationBuilder().clustering().cacheMode(CacheMode.REPL_SYNC) .build();Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the first line of the configuration, a new cache configuration object (namedc) is created using theConfigurationBuilder. Configurationcis assigned the default values for all cache configuration options except the cache mode, which is overridden and set to synchronous replication (REPL_SYNC). - Set the cache mode to synchronous replication:
String newCacheName = "repl";
String newCacheName = "repl";Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the second line of the configuration, a new variable (of typeString) is created and assigned the valuerepl. - Define or register the configuration with a manager:
manager.defineConfiguration(newCacheName, c);
manager.defineConfiguration(newCacheName, c);Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the third line of the configuration, the cache manager is used to define a named cache configuration for itself. This named cache configuration is calledrepland its configuration is based on the configuration provided for cache configurationcin the first line. Cache<String, String> cache = manager.getCache(newCacheName);
Cache<String, String> cache = manager.getCache(newCacheName);Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the fourth line of the configuration, the cache manager is used to obtain a reference to the unique instance of thereplthat is held by the cache manager. This cache instance is now ready to be used to perform operations to store and retrieve data.
Note
5.1.2. Create a Customized Cache Using the Default Named Cache
infinispan-config-file.xml specifies the configuration for a replicated cache as a default and a distributed cache with a customized lifespan value is required. The required distributed cache must retain all aspects of the default cache specified in the infinispan-config-file.xml file except the mentioned aspects.
Procedure 5.2. Customize the Default Cache
- Read an instance of a default Configuration object to get the default configuration:
EmbeddedCacheManager manager = new DefaultCacheManager("infinispan-config-file.xml"); Configuration dcc = cacheManager.getDefaultCacheConfiguration();EmbeddedCacheManager manager = new DefaultCacheManager("infinispan-config-file.xml"); Configuration dcc = cacheManager.getDefaultCacheConfiguration();Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the ConfigurationBuilder to construct and modify the cache mode and L1 cache lifespan on a new configuration object:
Configuration c = new ConfigurationBuilder().read(dcc).clustering() .cacheMode(CacheMode.DIST_SYNC).l1().lifespan(60000L).enable() .build();
Configuration c = new ConfigurationBuilder().read(dcc).clustering() .cacheMode(CacheMode.DIST_SYNC).l1().lifespan(60000L).enable() .build();Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Register/define your cache configuration with a cache manager, where cacheName is name of cache specified in
infinispan-config-file.xml:manager.defineConfiguration(newCacheName, c);
manager.defineConfiguration(newCacheName, c);Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Get default cache with custom configuration changes:
Cache<String, String> cache = manager.getCache(newCacheName);
Cache<String, String> cache = manager.getCache(newCacheName);Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.1.3. Create a Customized Cache Using a Non-Default Named Cache
replicatedCache as the base instead of the default cache. The following is an example of a customized cache using a non-default named cache:
Procedure 5.3. Create a Customized Cache Using a Non-Default Named Cache
- Read the
replicatedCacheto get the default configuration:EmbeddedCacheManager manager = new DefaultCacheManager("infinispan-config-file.xml"); Configuration rc = cacheManager.getCacheConfiguration("replicatedCache");EmbeddedCacheManager manager = new DefaultCacheManager("infinispan-config-file.xml"); Configuration rc = cacheManager.getCacheConfiguration("replicatedCache");Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the ConfigurationBuilder to construct and modify the desired configuration on a new configuration object:
Configuration c = new ConfigurationBuilder().read(rc).clustering() .cacheMode(CacheMode.DIST_SYNC).l1().lifespan(60000L).enable() .build();
Configuration c = new ConfigurationBuilder().read(rc).clustering() .cacheMode(CacheMode.DIST_SYNC).l1().lifespan(60000L).enable() .build();Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Register/define your cache configuration with a cache manager where newCacheName is the name of cache specified in
infinispan-config-file.xmlmanager.defineConfiguration(newCacheName, c);
manager.defineConfiguration(newCacheName, c);Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Get a default cache with custom configuration changes:
Cache<String, String> cache = manager.getCache(newCacheName);
Cache<String, String> cache = manager.getCache(newCacheName);Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.1.4. Using the Configuration Builder to Create Caches Programmatically
5.1.5. Global Configuration Examples
5.1.5.1. Globally Configure the Transport Layer
GlobalConfiguration globalConfig = new GlobalConfigurationBuilder() .globalJmxStatistics().enable() .build();
GlobalConfiguration globalConfig = new GlobalConfigurationBuilder()
.globalJmxStatistics().enable()
.build();
5.1.5.2. Globally Configure the Cache Manager Name
5.1.5.3. Globally Customize Thread Pool Executors
5.1.6. Cache Level Configuration Examples
5.1.6.1. Cache Level Configuration for the Cluster Mode
5.1.6.2. Cache Level Eviction and Expiration Configuration
5.1.6.3. Cache Level Configuration for JTA Transactions
5.1.6.4. Cache Level Configuration Using Chained Persistent Stores
Configuration config = new ConfigurationBuilder()
.persistence()
.passivation(false)
.addSingleFileStore().shared(false).preload(false).location("/tmp").async().enable().threadPoolSize(20).build();
Configuration config = new ConfigurationBuilder()
.persistence()
.passivation(false)
.addSingleFileStore().shared(false).preload(false).location("/tmp").async().enable().threadPoolSize(20).build();
5.1.6.5. Cache Level Configuration for Advanced Externalizers
Chapter 6. The Externalizable API
Externalizer is a class that can:
- Marshall a given object type to a byte array.
- Unmarshall the contents of a byte array into an instance of the object type.
6.1. Customize Externalizers
- Use an Externalizable Interface. For details, see the Red Hat JBoss Data Grid Developer Guide's The Externalizable API chapter.
- Use an advanced externalizer.
6.2. Annotating Objects for Marshalling Using @SerializeWith
@SerializeWith indicating the Externalizer class to use.
@SerializeWith annotation. JBoss Marshalling will therefore marshall the object using the Externalizer class passed.
- The payload sizes generated using this method are not the most efficient. This is due to some constraints in the model, such as support for different versions of the same class, or the need to marshall the Externalizer class.
- This model requires the marshalled class to be annotated with
@SerializeWith, however an Externalizer may need to be provided for a class for which source code is not available, or for any other constraints, it cannot be modified. - Annotations used in this model may be limiting for framework developers or service providers that attempt to abstract lower level details, such as the marshalling layer, away from the user.
Note
6.3. Using an Advanced Externalizer
- Define and implement the
readObject()andwriteObject()methods. - Link externalizers with marshaller classes.
- Register the advanced externalizer.
6.3.1. Implement the Methods
readObject() and writeObject() methods. The following is a sample definition:
Note
6.3.2. Link Externalizers with Marshaller Classes
getTypeClasses() to discover the classes that this externalizer can marshall and to link the readObject() and writeObject() classes.
ReplicableCommandExternalizer indicates that it can externalize several command types. This sample marshalls all commands that extend the ReplicableCommand interface but the framework only supports class equality comparison so it is not possible to indicate that the classes marshalled are all children of a particular class or interface.
6.3.3. Register the Advanced Externalizer (Declaratively)
Procedure 6.1. Register the Advanced Externalizer
- Add the
globalelement to theinfinispanelement:<infinispan> <global /> </infinispan>
<infinispan> <global /> </infinispan>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the
serializationelement to theglobalelement as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the
advancedExternalizerselement to add information about the new advanced externalizer as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Define the externalizer class using the
externalizerClassattribute as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace the $IdViaAnnotationObj and $AdvancedExternalizer values as required.
6.3.4. Register the Advanced Externalizer (Programmatically)
GlobalConfigurationBuilder builder = ... builder.serialization() .addAdvancedExternalizer(new Person.PersonExternalizer());
GlobalConfigurationBuilder builder = ...
builder.serialization()
.addAdvancedExternalizer(new Person.PersonExternalizer());
6.3.5. Register Multiple Externalizers
GlobalConfiguration.addExternalizer() accepts varargs. Before registering the new externalizers, ensure that their IDs are already defined using the @Marshalls annotation.
builder.serialization()
.addAdvancedExternalizer(new Person.PersonExternalizer(),
new Address.AddressExternalizer());
builder.serialization()
.addAdvancedExternalizer(new Person.PersonExternalizer(),
new Address.AddressExternalizer());
6.4. Custom Externalizer ID Values
| ID Range | Reserved For |
|---|---|
| 1000-1099 | The Infinispan Tree Module |
| 1100-1199 | Red Hat JBoss Data Grid Server modules |
| 1200-1299 | Hibernate Infinispan Second Level Cache |
| 1300-1399 | JBoss Data Grid Lucene Directory |
| 1400-1499 | Hibernate OGM |
| 1500-1599 | Hibernate Search/Infinispan Query |
6.4.1. Customize the Externalizer ID (Declaratively)
Procedure 6.2. Customizing the Externalizer ID (Declaratively)
- Add the
globalelement to theinfinispanelement:<infinispan> <global /> </infinispan>
<infinispan> <global /> </infinispan>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the
serializationelement to theglobalelement as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the
advancedExternalizerelement to add information about the new advanced externalizer as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Define the externalizer ID using the
idattribute as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that the selected ID is not from the range of IDs reserved for other modules. - Define the externalizer class using the
externalizerClassattribute as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace the $IdViaAnnotationObj and $AdvancedExternalizer values as required.
6.4.2. Customize the Externalizer ID (Programmatically)
GlobalConfiguration globalConfiguration = new GlobalConfigurationBuilder()
.serialization()
.addAdvancedExternalizer($ID, new Person.PersonExternalizer())
.build();
GlobalConfiguration globalConfiguration = new GlobalConfigurationBuilder()
.serialization()
.addAdvancedExternalizer($ID, new Person.PersonExternalizer())
.build();
Chapter 7. The Notification/Listener API
7.1. Listener Example
7.2. Cache Entry Modified Listener Configuration
getValue() method's behavior is specific to whether the callback is triggered before or after the actual operation has been performed. For example, if event.isPre() is true, then event.getValue() would return the old value, prior to modification. If event.isPre() is false, then event.getValue() would return new value. If the event is creating and inserting a new entry, the old value would be null. For more information about isPre(), see the Red Hat JBoss Data Grid API Documentation's listing for the org.infinispan.notifications.cachelistener.event package.
7.3. Listener Notifications
@Listener. A Listenable is an interface that denotes that the implementation can have listeners attached to it. Each listener is registered using methods defined in the Listenable.
7.3.1. About Cache-level Notifications
7.3.2. Cache Manager-level Notifications
- Nodes joining or leaving a cluster;
- The starting and stopping of caches
7.3.3. About Synchronous and Asynchronous Notifications
@Listener (sync = false)public class MyAsyncListener { .... }
@Listener (sync = false)public class MyAsyncListener { .... }
<asyncListenerExecutor/> element in the configuration file to tune the thread pool that is used to dispatch asynchronous notifications.
7.4. NotifyingFutures
Futures, but a sub-interface known as a NotifyingFuture. Unlike a JDK Future, a listener can be attached to a NotifyingFuture to notify the user about a completed future.
Note
NotifyingFutures are only available in JBoss Data Grid Library mode.
7.4.1. NotifyingFutures Example
NotifyingFutures in Red Hat JBoss Data Grid:
Part II. Remote Client-Server Mode Interfaces
- The Asynchronous API (can only be used in conjunction with the Hot Rod Client in Remote Client-Server Mode)
- The REST Interface
- The Memcached Interface
- The Hot Rod Interface
- The RemoteCache API
Chapter 8. The Asynchronous API
Async appended to each method name. Asynchronous methods return a Future that contains the result of the operation.
Cache(String, String), Cache.put(String key, String value) returns a String, while Cache.putAsync(String key, String value) returns a Future(String).
8.1. Asynchronous API Benefits
- The guarantee of synchronous communication, with the added ability to handle failures and exceptions.
- Not being required to block a thread's operations until the call completes.
Set<Future<?>> futures = new HashSet<Future<?>>();
futures.add(cache.putAsync("key1", "value1"));
futures.add(cache.putAsync("key2", "value2"));
futures.add(cache.putAsync("key3", "value3"));
Set<Future<?>> futures = new HashSet<Future<?>>();
futures.add(cache.putAsync("key1", "value1"));
futures.add(cache.putAsync("key2", "value2"));
futures.add(cache.putAsync("key3", "value3"));
futures.add(cache.putAsync(key1, value1));futures.add(cache.putAsync(key2, value2));futures.add(cache.putAsync(key3, value3));
8.2. About Asynchronous Processes
- Network calls
- Marshalling
- Writing to a cache store (optional)
- Locking
8.3. Return Values and the Asynchronous API
Future or the NotifyingFuture in order to query the previous value.
Note
NotifyingFutures are only available in JBoss Data Grid Library mode.
Future.get()
Future.get()Chapter 9. The REST Interface
9.1. Ruby Client Code
9.2. Using JSON with Ruby Example
To use JavaScript Object Notation (JSON) with ruby to interact with Red Hat JBoss Data Grid's REST Interface, install the JSON Ruby library (see your platform's package manager or the Ruby documentation) and declare the requirement using the following code:
require 'json'
require 'json'
The following code is an example of how to use JavaScript Object Notation (JSON) in conjunction with Ruby to send specific data, in this case the name and age of an individual, using the PUT function.
data = {:name => "michael", :age => 42 }
http.put('/infinispan/rest/Users/data/0', data.to_json, {"Content-Type" => "application/json"})
data = {:name => "michael", :age => 42 }
http.put('/infinispan/rest/Users/data/0', data.to_json, {"Content-Type" => "application/json"})
9.3. Python Client Code
9.4. Java Client Code
Define imports as follows:
import java.io.BufferedReader;import java.io.IOException; import java.io.InputStreamReader;import java.io.OutputStreamWriter; import java.net.HttpURLConnection;import java.net.URL;
import java.io.BufferedReader;import java.io.IOException;
import java.io.InputStreamReader;import java.io.OutputStreamWriter;
import java.net.HttpURLConnection;import java.net.URL;
The following is an example of using Java to add a string value to a cache:
The following code is an example of a method used that reads a value specified in a URL using Java to interact with the JBoss Data Grid REST Interface.
9.5. Configure the Interface Using Connectors
- The
hotrod-connectorelement, which defines the configuration for a Hot Rod based connector. - The
memcached-connectorelement, which defines the configuration for a memcached based connector. - The
rest-connectorelement, which defines the configuration for a REST interface based connector.
9.5.1. Configure REST Connectors
rest-connector element in Red Hat JBoss Data Grid's Remote Client-Server mode.
Procedure 9.1. Configuring REST Connectors for Remote Client-Server Mode
rest-connector element specifies the configuration information for the REST connector.
The
virtual-serverParameterThevirtual-serverparameter specifies the virtual server used by the REST connector. The default value for this parameter isdefault-host. This is an optional parameter.<subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <rest-connector virtual-server="default-host" /> </subsystem>
<subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <rest-connector virtual-server="default-host" /> </subsystem>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
cache-containerParameterThecache-containerparameter names the cache container used by the REST connector. This is a mandatory parameter.<subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <rest-connector virtual-server="default-host" cache-container="local" /> </subsystem><subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <rest-connector virtual-server="default-host" cache-container="local" /> </subsystem>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
context-pathParameterThecontext-pathparameter specifies the context path for the REST connector. The default value for this parameter is an empty string (""). This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
security-domainParameterThesecurity-domainparameter specifies that the specified domain, declared in the security subsystem, should be used to authenticate access to the REST endpoint. This is an optional parameter. If this parameter is omitted, no authentication is performed.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
auth-methodParameterTheauth-methodparameter specifies the method used to retrieve credentials for the end point. The default value for this parameter isBASIC. Supported alternate values includeDIGEST,CLIENT-CERTandSPNEGO. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
security-modeParameterThesecurity-modeparameter specifies whether authentication is required only for write operations (such as PUT, POST and DELETE) or for read operations (such as GET and HEAD) as well. Valid values for this parameter areWRITEfor authenticating write operations only, orREAD_WRITEto authenticate read and write operations. The default value for this parameter isREAD_WRITE.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.6. Using the REST Interface
- Adding data
- Retrieving data
- Removing data
9.6.1. Adding Data Using REST
- HTTP
PUTmethod - HTTP
POSTmethod
PUT and POST methods are used, the body of the request contains this data, which includes any information added by the user.
PUT and POST methods require a Content-Type header.
9.6.1.1. About PUT /{cacheName}/{cacheKey}
PUT request from the provided URL form places the payload, (from the request body) in the targeted cache using the provided key. The targeted cache must exist on the server for this task to successfully complete.
hr is the cache name and payRoll%2F3 is the key. The value %2F indicates that a / was used in the key.
http://someserver/rest/hr/payRoll%2F3
http://someserver/rest/hr/payRoll%2F3Time-To-Live and Last-Modified values are updated, if an update is required.
Note
%2F to represent a / in the key (as in the provided example) can be successfully run if the server is started using the following argument:
-Dorg.apache.tomcat.util.buf.UDecoder.ALLOW_ENCODED_SLASH=true
-Dorg.apache.tomcat.util.buf.UDecoder.ALLOW_ENCODED_SLASH=true9.6.1.2. About POST /{cacheName}/{cacheKey}
POST method from the provided URL form places the payload (from the request body) in the targeted cache using the provided key. However, in a POST method, if a value in a cache/key exists, a HTTP CONFLICT status is returned and the content is not updated.
9.6.2. Retrieving Data Using REST
- HTTP
GETmethod. - HTTP
HEADmethod.
9.6.2.1. About GET /{cacheName}/{cacheKey}
GET method returns the data located in the supplied cacheName, matched to the relevant key, as the body of the response. The Content-Type header provides the type of the data. A browser can directly access the cache.
9.6.2.2. About HEAD /{cacheName}/{cacheKey}
HEAD method operates in a manner similar to the GET method, however returns no content (header fields are returned).
9.6.3. Removing Data Using REST
DELETE method to retrieve data from the cache. The DELETE method can:
- Remove a cache entry/value. (
DELETE /{cacheName}/{cacheKey}) - Remove all entries from a cache. (
DELETE /{cacheName})
9.6.3.1. About DELETE /{cacheName}/{cacheKey}
DELETE /{cacheName}/{cacheKey}), the DELETE method removes the key/value from the cache for the provided key.
9.6.3.2. About DELETE /{cacheName}
DELETE /{cacheName}), the DELETE method removes all entries in the named cache. After a successful DELETE operation, the HTTP status code 200 is returned.
9.6.3.3. Background Delete Operations
performAsync header to true to ensure an immediate return while the removal operation continues in the background.
9.6.4. REST Interface Operation Headers
| Headers | Mandatory/Optional | Values | Default Value | Details |
|---|---|---|---|---|
| Content-Type | Mandatory | - | - | If the Content-Type is set to application/x-java-serialized-object, it is stored as a Java object. |
| performAsync | Optional | True/False | - | If set to true, an immediate return occurs, followed by a replication of data to the cluster on its own. This feature is useful when dealing with bulk data inserts and large clusters. |
| timeToLiveSeconds | Optional | Numeric (positive and negative numbers) | -1 (This value prevents expiration as a direct result of timeToLiveSeconds. Expiration values set elsewhere override this default value.) | Reflects the number of seconds before the entry in question is automatically deleted. Setting a negative value for timeToLiveSeconds provides the same result as the default value. |
| maxIdleTimeSeconds | Optional | Numeric (positive and negative numbers) | -1 (This value prevents expiration as a direct result of maxIdleTimeSeconds. Expiration values set elsewhere override this default value.) | Contains the number of seconds after the last usage when the entry will be automatically deleted. Passing a negative value provides the same result as the default value. |
timeToLiveSeconds and maxIdleTimeSeconds headers:
- If both the
timeToLiveSecondsandmaxIdleTimeSecondsheaders are assigned the value0, the cache uses the defaulttimeToLiveSecondsandmaxIdleTimeSecondsvalues configured either using XML or programatically. - If only the
maxIdleTimeSecondsheader value is set to0, thetimeToLiveSecondsvalue should be passed as the parameter (or the default-1, if the parameter is not present). Additionally, themaxIdleTimeSecondsparameter value defaults to the values configured either using XML or programatically. - If only the
timeToLiveSecondsheader value is set to0, expiration occurs immediately and themaxIdleTimeSecondsvalue is set to the value passed as a parameter (or the default-1if no parameter was supplied).
ETags (Entity Tags) are returned for each REST Interface entry, along with a Last-Modified header that indicates the state of the data at the supplied URL. ETags are used in HTTP operations to request data exclusively in cases where the data has changed to save bandwidth. The following headers support ETags (Entity Tags) based optimistic locking:
| Header | Algorithm | Example | Details |
|---|---|---|---|
| If-Match | If-Match = "If-Match" ":" ( "*" | 1#entity-tag ) | - | Used in conjunction with a list of associated entity tags to verify that a specified entity (that was previously obtained from a resource) remains current. |
| If-None-Match | - | Used in conjunction with a list of associated entity tags to verify that none of the specified entities (that was previously obtained from a resource) are current. This feature facilitates efficient updates of cached information when required and with minimal transaction overhead. | |
| If-Modified-Since | If-Modified-Since = "If-Modified-Since" ":" HTTP-date | If-Modified-Since: Sat, 29 Oct 1994 19:43:31 GMT | Compares the requested variant's last modification time and date with a supplied time and date value. If the requested variant has not been modified since the specified time and date, a 304 (not modified) response is returned without a message-body instead of an entity. |
| If-Unmodified-Since | If-Unmodified-Since = "If-Unmodified-Since" ":" HTTP-date | If-Unmodified-Since: Sat, 29 Oct 1994 19:43:31 GMT | Compares the requested variant's last modification time and date with a supplied time and date value. If the requested resources has not been modified since the supplied date and time, the specified operation is performed. If the requested resource has been modified since the supplied date and time, the operation is not performed and a 412 (Precondition Failed) response is returned. |
9.7. REST Interface Security
9.7.1. Publish REST Endpoints as a Public Interface
interface parameter in the socket-binding element from management to public as follows:
<socket-binding name="http" interface="public" port="8080"/>
<socket-binding name="http" interface="public" port="8080"/>
9.7.2. Enable Security for the REST Endpoint
Note
Procedure 9.2. Enable Security for the REST Endpoint
standalone.xml:
Specify Security Parameters
Ensure that the rest endpoint specifies a valid value for thesecurity-domainandauth-methodparameters. Recommended settings for these parameters are as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check Security Domain Declaration
Ensure that the security subsystem contains the corresponding security-domain declaration. For details about setting up security-domain declarations, see the WildFly 7 or JBoss Enterprise Application Platform 6 documentation.Add an Application User
Run the relevant script and enter the configuration settings to add an application user.- Run the
adduser.shscript (located in$JDG_HOME/bin).- On a Windows system, run the
adduser.batfile (located in$JDG_HOME/bin) instead.
- When prompted about the type of user to add, select
Application User (application-users.properties)by enteringb. - Accept the default value for realm (
ApplicationRealm) by pressing the return key. - Specify a username and password.
- When prompted for a role for the created user, enter
REST. - Ensure the username and application realm information is correct when prompted and enter "yes" to continue.
Verify the Created Application User
Ensure that the created application user is correctly configured.- Check the configuration listed in the
application-users.propertiesfile (located in$JDG_HOME/standalone/configuration/). The following is an example of what the correct configuration looks like in this file:user1=2dc3eacfed8cf95a4a31159167b936fc
user1=2dc3eacfed8cf95a4a31159167b936fcCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Check the configuration listed in the
application-roles.propertiesfile (located in$JDG_HOME/standalone/configuration/). The following is an example of what the correct configuration looks like in this file:user1=REST
user1=RESTCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Test the Server
Start the server and enter the following link in a browser window to access the REST endpoint:http://localhost:8080/rest/namedCache
http://localhost:8080/rest/namedCacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
If testing using a GET request, a405response code is expected and indicates that the server was successfully authenticated.
Chapter 10. The Memcached Interface
10.1. About Memcached Servers
- Standalone, where each server acts independently without communication with any other memcached servers.
- Clustered, where servers replicate and distribute data to other memcached servers.
10.2. Memcached Statistics
| Statistic | Data Type | Details |
|---|---|---|
| uptime | 32-bit unsigned integer. | Contains the time (in seconds) that the memcached instance has been available and running. |
| time | 32-bit unsigned integer. | Contains the current time. |
| version | String | Contains the current version. |
| curr_items | 32-bit unsigned integer. | Contains the number of items currently stored by the instance. |
| total_items | 32-bit unsigned integer. | Contains the total number of items stored by the instance during its lifetime. |
| cmd_get | 64-bit unsigned integer | Contains the total number of get operation requests (requests to retrieve data). |
| cmd_set | 64-bit unsigned integer | Contains the total number of set operation requests (requests to store data). |
| get_hits | 64-bit unsigned integer | Contains the number of keys that are present from the keys requested. |
| get_misses | 64-bit unsigned integer | Contains the number of keys that were not found from the keys requested. |
| delete_hits | 64-bit unsigned integer | Contains the number of keys to be deleted that were located and successfully deleted. |
| delete_misses | 64-bit unsigned integer | Contains the number of keys to be deleted that were not located and therefore could not be deleted. |
| incr_hits | 64-bit unsigned integer | Contains the number of keys to be incremented that were located and successfully incremented |
| incr_misses | 64-bit unsigned integer | Contains the number of keys to be incremented that were not located and therefore could not be incremented. |
| decr_hits | 64-bit unsigned integer | Contains the number of keys to be decremented that were located and successfully decremented. |
| decr_misses | 64-bit unsigned integer | Contains the number of keys to be decremented that were not located and therefore could not be decremented. |
| cas_hits | 64-bit unsigned integer | Contains the number of keys to be compared and swapped that were found and successfully compared and swapped. |
| cas_misses | 64-bit unsigned integer | Contains the number of keys to be compared and swapped that were not found and therefore not compared and swapped. |
| cas_badval | 64-bit unsigned integer | Contains the number of keys where a compare and swap occurred but the original value did not match the supplied value. |
| evictions | 64-bit unsigned integer | Contains the number of eviction calls performed. |
| bytes_read | 64-bit unsigned integer | Contains the total number of bytes read by the server from the network. |
| bytes_written | 64-bit unsigned integer | Contains the total number of bytes written by the server to the network. |
10.3. Configure the Interface Using Connectors
- The
hotrod-connectorelement, which defines the configuration for a Hot Rod based connector. - The
memcached-connectorelement, which defines the configuration for a memcached based connector. - The
rest-connectorelement, which defines the configuration for a REST interface based connector.
10.3.1. Configure Memcached Connectors
connectors element in Red Hat JBoss Data Grid's Remote Client-Server Mode.
Procedure 10.1. Configuring the Memcached Connector in Remote Client-Server Mode
memcached-connector element defines the configuration elements for use with memcached.
The
socket-bindingParameterThesocket-bindingparameter specifies the socket binding port used by the memcached connector. This is a mandatory parameter.<subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <memcached-connector socket-binding="memcached" />
<subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <memcached-connector socket-binding="memcached" />Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
cache-containerParameterThecache-containerparameter names the cache container used by the memcached connector. This is a mandatory parameter.<subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <memcached-connector socket-binding="memcached" cache-container="local" /><subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <memcached-connector socket-binding="memcached" cache-container="local" />Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
worker-threadsParameterTheworker-threadsparameter specifies the number of worker threads available for the memcached connector. The default value for this parameter is 160. This is an optional parameter.<subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <memcached-connector socket-binding="memcached" cache-container="local" worker-threads="${VALUE}" /><subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <memcached-connector socket-binding="memcached" cache-container="local" worker-threads="${VALUE}" />Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
idle-timeoutParameterTheidle-timeoutparameter specifies the time (in milliseconds) the connector can remain idle before the connection times out. The default value for this parameter is-1, which means that no timeout period is set. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
tcp-nodelayParameterThetcp-nodelayparameter specifies whether TCP packets will be delayed and sent out in batches. Valid values for this parameter aretrueandfalse. The default value for this parameter istrue. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
send-buffer-sizeParameterThesend-buffer-sizeparameter indicates the size of the send buffer for the memcached connector. The default value for this parameter is the size of the TCP stack buffer. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
receive-buffer-sizeParameterThereceive-buffer-sizeparameter indicates the size of the receive buffer for the memcached connector. The default value for this parameter is the size of the TCP stack buffer. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.4. Memcached Interface Security
10.4.1. Publish Memcached Endpoints as a Public Interface
interface parameter in the socket-binding element from management to public as follows:
<socket-binding name="memcached" interface="public" port="11211" />
<socket-binding name="memcached" interface="public" port="11211" />
Chapter 11. The Hot Rod Interface
11.1. About Hot Rod
11.2. The Benefits of Using Hot Rod over Memcached
- Memcached
- The memcached protocol causes the server endpoint to use the memcached text wire protocol. The memcached wire protocol has the benefit of being commonly used, and is available for almost any platform. All of JBoss Data Grid's functions, including clustering, state sharing for scalability, and high availability, are available when using memcached.However the memcached protocol lacks dynamicity, resulting in the need to manually update the list of server nodes on your clients in the event one of the nodes in a cluster fails. Also, memcached clients are not aware of the location of the data in the cluster. This means that they will request data from a non-owner node, incurring the penalty of an additional request from that node to the actual owner, before being able to return the data to the client. This is where the Hot Rod protocol is able to provide greater performance than memcached.
- Hot Rod
- JBoss Data Grid's Hot Rod protocol is a binary wire protocol that offers all the capabilities of memcached, while also providing better scaling, durability, and elasticity.The Hot Rod protocol does not need the hostnames and ports of each node in the remote cache, whereas memcached requires these parameters to be specified. Hot Rod clients automatically detect changes in the topology of clustered Hot Rod servers; when new nodes join or leave the cluster, clients update their Hot Rod server topology view. Consequently, Hot Rod provides ease of configuration and maintenance, with the advantage of dynamic load balancing and failover.Additionally, the Hot Rod wire protocol uses smart routing when connecting to a distributed cache. This involves sharing a consistent hash algorithm between the server nodes and clients, resulting in faster read and writing capabilities than memcached.
11.3. Hot Rod Hash Functions
Integer.MAX_INT). This value is returned to the client using the Hot Rod protocol each time a hash-topology change is detected to prevent Hot Rod clients assuming a specific hash space as a default. The hash space can only contain positive numbers ranging from 0 to Integer.MAX_INT.
The following table describes the client intelligence levels:
| Intelligence Level | Description |
|---|---|
| Level 1 | In this level, simple clients connect to the grid using a list of statically provided server addresses. These addresses are used based on round-robin scheduling. |
| Level 2 | In this level, clients are aware of the topology of the grid and are notified when new servers are added or removed from the grid. |
| Level 3 | In this level, clients use the grid topology and the key hashes to directly connect to the node that is the primary owner for a data item. Thus reducing the need for remote calls between the server nodes. |
11.4. Hot Rod Server Nodes
11.4.1. About Consistent Hashing Algorithms
11.5. Hot Rod Headers
11.5.1. Hot Rod Header Data Types
| Data Type | Size | Details |
|---|---|---|
| vInt | Between 1-5 bytes. | Unsigned variable length integer values. |
| vLong | Between 1-9 bytes. | Unsigned variable length long values. |
| string | - | Strings are always represented using UTF-8 encoding. |
11.5.2. Request Header
| Field Name | Data Type/Size | Details |
|---|---|---|
| Magic | 1 byte | Indicates whether the header is a request header or response header. |
| Message ID | vLong | Contains the message ID. Responses use this unique ID when responding to a request. This allows Hot Rod clients to implement the protocol in an asynchronous manner. |
| Version | 1 byte | Contains the Hot Rod server version. |
| Opcode | 1 byte | Contains the relevant operation code. In a request header, opcode can only contain the request operation codes. |
| Cache Name Length | vInt | Stores the length of the cache name. If Cache Name Length is set to 0 and no value is supplied for Cache Name, the operation interacts with the default cache. |
| Cache Name | string | Stores the name of the target cache for the specified operation. This name must match the name of a predefined cache in the cache configuration file. |
| Flags | vInt | Contains a numeric value of variable length that represents flags passed to the system. Each bit represents a flag, except the most significant bit, which is used to determine whether more bytes must be read. Using a bit to represent each flag facilitates the representation of flag combinations in a condensed manner. |
| Client Intelligence | 1 byte | Contains a value that indicates the client capabilities to the server. |
| Topology ID | vInt | Contains the last known view ID in the client. Basic clients supply the value 0 for this field. Clients that support topology or hash information supply the value 0 until the server responds with the current view ID, which is subsequently used until a new view ID is returned by the server to replace the current view ID. |
| Transaction Type | 1 byte | Contains a value that represents one of two known transaction types. Currently, the only supported value is 0. |
| Transaction ID | byte-array | Contains a byte array that uniquely identifies the transaction associated with the call. The transaction type determines the length of this byte array. If the value for Transaction Type was set to 0, no Transaction ID is present. |
11.5.3. Response Header
| Field Name | Data Type | Details |
|---|---|---|
| Magic | 1 byte | Indicates whether the header is a request or response header. |
| Message ID | vLong | Contains the message ID. This unique ID is used to pair the response with the original request. This allows Hot Rod clients to implement the protocol in an asynchronous manner. |
| Opcode | 1 byte | Contains the relevant operation code. In a response header, opcode can only contain the response operation codes. |
| Status | 1 byte | Contains a code that represents the status of the response. |
| Topology Change Marker | 1 byte | Contains a marker byte that indicates whether the response is included in the topology change information. |
11.5.4. Topology Change Headers
topology ID and the topology ID sent by the client and, if the two differ, it returns a new topology ID.
11.5.4.1. Topology Change Marker Values
Topology Change Marker field in a response header:
| Value | Details |
|---|---|
| 0 | No topology change information is added. |
| 1 | Topology change information is added. |
11.5.4.2. Topology Change Headers for Topology-Aware Clients
| Response Header Fields | Data Type/Size | Details |
|---|---|---|
| Response Header with Topology Change Marker | - | - |
| Topology ID | vInt | - |
| Num Servers in Topology | vInt | Contains the number of Hot Rod servers running in the cluster. This value can be a subset of the entire cluster if only some nodes are running Hot Rod servers. |
| mX: Host/IP Length | vInt | Contains the length of the hostname or IP address of an individual cluster member. Variable length allows this element to include hostnames, IPv4 and IPv6 addresses. |
| mX: Host/IP Address | string | Contains the hostname or IP address of an individual cluster member. The Hot Rod client uses this information to access the individual cluster member. |
| mX: Port | Unsigned Short. 2 bytes | Contains the port used by Hot Rod clients to communicate with the cluster member. |
mX, are repeated for each server in the topology. The first server in the topology's information fields will be prefixed with m1 and the numerical value is incremented by one for each additional server till the value of X equals the number of servers specified in the num servers in topology field.
11.5.4.3. Topology Change Headers for Hash Distribution-Aware Clients
| Field | Data Type/Size | Details |
|---|---|---|
| Response Header with Topology Change Marker | - | - |
| Topology ID | vInt | - |
| Number Key Owners | Unsigned short. 2 bytes. | Contains the number of globally configured copies for each distributed key. Contains the value 0 if distribution is not configured on the cache. |
| Hash Function Version | 1 byte | Contains a pointer to the hash function in use. Contains the value 0 if distribution is not configured on the cache. |
| Hash Space Size | vInt | Contains the modulus used by JBoss Data Grid for all module arithmetic related to hash code generation. Clients use this information to apply the correct hash calculations to the keys. Contains the value 0 if distribution is not configured on the cache. |
| Number servers in topology | vInt | Contains the number of Hot Rod servers running in the cluster. This value can be a subset of the entire cluster if only some nodes are running Hot Rod servers. This value also represents the number of host to port pairings included in the header. |
| Number Virtual Nodes Owners | vInt | Contains the number of configured virtual nodes. Contains the value 0 if no virtual nodes are configured or if distribution is not configured on the cache. |
| mX: Host/IP Length | vInt | Contains the length of the hostname or IP address of an individual cluster member. Variable length allows this element to include hostnames, IPv4 and IPv6 addresses. |
| mX: Host/IP Address | string | Contains the hostname or IP address of an individual cluster member. The Hot Rod client uses this information to access the individual cluster member. |
| mX: Port | Unsigned short. 2 bytes. | Contains the port used by Hot Rod clients to communicate with the cluster member. |
| mX: Hashcode | 4 bytes. |
mX, are repeated for each server in the topology. The first server in the topology's information fields will be prefixed with m1 and the numerical value is incremented by one for each additional server till the value of X equals the number of servers specified in the num servers in topology field.
11.6. Hot Rod Operations
11.6.1. Hot Rod Operations
- BulkGetKeys
- BulkGet
- Clear
- ContainsKey
- Get
- GetWithMetadata
- Ping
- PutIfAbsent
- Put
- Query
- RemoveIfUnmodified
- Remove
- ReplaceIfUnmodified
- Replace
- Stats
11.6.2. Hot Rod BulkGetKeys Operation
BulkGetKeys operation uses the following request format:
| Field | Data Type | Details |
|---|---|---|
| Header | variable | Request header. |
| Scope | vInt |
|
| Field | Data Type | Details |
|---|---|---|
| Header | variable | Response header |
| Response status | 1 byte | 0x00 = success, data follows. |
| More | 1 byte | One byte representing whether more keys need to be read from the stream. When set to 1 an entry follows, when set to 0, it is the end of stream and no more entries are left to read. |
| Key 1 Length | vInt | Length of key |
| Key 1 | Byte array | Retrieved key. |
| More | 1 byte | - |
| Key 2 Length | vInt | - |
| Key 2 | byte array | - |
| ...etc |
11.6.3. Hot Rod BulkGet Operation
BulkGet operation uses the following request format:
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| Entry Count | vInt | Contains the maximum number of Red Hat JBoss Data Grid entries to be returned by the server. The entry is the key and value pair. |
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| More | vInt | Represents if more entries must be read from the stream. While More is set to 1, additional entries follow until the value of More is set to 0, which indicates the end of the stream. |
| Key Size | - | Contains the size of the key. |
| Key | - | Contains the key value. |
| Value Size | - | Contains the size of the value. |
| Value | - | Contains the value. |
More, Key Size, Key, Value Size and Value entry is appended to the response.
11.6.4. Hot Rod Clear Operation
clear operation format includes only a header.
| Response Status | Details |
|---|---|
| 0x00 | Red Hat JBoss Data Grid was successfully cleared. |
11.6.5. Hot Rod ContainsKey Operation
ContainsKey operation uses the following request format:
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| Key Length | vInt | Contains the length of the key. The vInt data type is used because of its size (up to 5 bytes), which is larger than the size of Integer.MAX_VALUE. However, Java disallows single array sizes to exceed the size of Integer.MAX_VALUE. As a result, this vInt is also limited to the maximum size of Integer.MAX_VALUE. |
| Key | Byte array | Contains a key, the corresponding value of which is requested. |
| Response Status | Details |
|---|---|
| 0x00 | Successful operation. |
| 0x02 | The key does not exist. |
11.6.6. Hot Rod Get Operation
Get operation uses the following request format:
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| Key Length | vInt | Contains the length of the key. The vInt data type is used because of its size (up to 5 bytes), which is larger than the size of Integer.MAX_VALUE. However, Java disallows single array sizes to exceed the size of Integer.MAX_VALUE. As a result, this vInt is also limited to the maximum size of Integer.MAX_VALUE. |
| Key | Byte array | Contains a key, the corresponding value of which is requested. |
| Response Status | Details |
|---|---|
| 0x00 | Successful operation. |
| 0x02 | The key does not exist. |
get operation's response when the key is found is as follows:
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| Value Length | vInt | Contains the length of the value. |
| Value | Byte array | Contains the requested value. |
11.6.7. Hot Rod GetWithMetadata Operation
GetWithMetadata operation uses the following request format:
| Field | Data Type | Details |
|---|---|---|
| Header | variable | Request header. |
| Key Length | vInt | Length of key. Note that the size of a vInt can be up to five bytes, which theoretically can produce bigger numbers than Integer.MAX_VALUE. However, Java cannot create a single array that is bigger than Integer.MAX_VALUE, hence the protocol limits vInt array lengths to Integer.MAX_VALUE. |
| Key | byte array | Byte array containing the key whose value is being requested. |
| Field | Data Type | Details |
|---|---|---|
| Header | variable | Response header. |
| Response status | 1 byte | 0x00 = success, if key retrieved.
0x02 = if key does not exist.
|
| Flag | 1 byte | A flag indicating whether the response contains expiration information. The value of the flag is obtained as a bitwise OR operation between INFINITE_LIFESPAN (0x01) and INFINITE_MAXIDLE (0x02). |
| Created | Long | (optional) a Long representing the timestamp when the entry was created on the server. This value is returned only if the flag's INFINITE_LIFESPAN bit is not set. |
| Lifespan | vInt | (optional) a vInt representing the lifespan of the entry in seconds. This value is returned only if the flag's INFINITE_LIFESPAN bit is not set. |
| LastUsed | Long | (optional) a Long representing the timestamp when the entry was last accessed on the server. This value is returned only if the flag's INFINITE_MAXIDLE bit is not set. |
| MaxIdle | vInt | (optional) a vInt representing the maxIdle of the entry in seconds. This value is returned only if the flag's INFINITE_MAXIDLE bit is not set. |
| Entry Version | 8 bytes | Unique value of an existing entry modification. The protocol does not mandate that entry_version values are sequential, however they need to be unique per update at the key level. |
| Value Length | vInt | If success, length of value. |
| Value | byte array | If success, the requested value. |
11.6.8. Hot Rod Ping Operation
ping is an application level request to check for server availability.
| Response Status | Details |
|---|---|
| 0x00 | Successful ping without any errors. |
11.6.9. Hot Rod PutIfAbsent Operation
putIfAbsent operation request format includes the following:
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| Key Length | vInt | Contains the length of the key. |
| Key | Byte array | Contains the key value. |
| Lifespan | vInt | Contains the number of seconds before the entry expires. If the number of seconds exceeds thirty days, the value is treated as UNIX time (i.e. the number of seconds since the date 1/1/1970) as the entry lifespan. When set to the value 0, the entry will never expire. |
| Max Idle | vInt | Contains the number of seconds an entry is allowed to remain idle before it is evicted from the cache. If this entry is set to 0, the entry is allowed to remain idle indefinitely without being evicted due to the max idle value. |
| Value Length | vInt | Contains the length of the value. |
| Value | Byte array | Contains the requested value. |
| Response Status | Details |
|---|---|
| 0x00 | The value was successfully stored. |
| 0x01 | The key was present, therefore the value was not stored. The current value of the key is returned. |
ForceReturnPreviousValue is passed, the previous value and key are returned. If the previous key and value do not exist, the value length would contain the value 0.
11.6.10. Hot Rod Put Operation
put operation request format includes the following:
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| Key Length | - | Contains the length of the key. |
| Key | Byte array | Contains the key value. |
| Lifespan | vInt | Contains the number of seconds before the entry expires. If the number of seconds exceeds thirty days, the value is treated as UNIX time (i.e. the number of seconds since the date 1/1/1970) as the entry lifespan. When set to the value 0, the entry will never expire. |
| Max Idle | vInt | Contains the number of seconds an entry is allowed to remain idle before it is evicted from the cache. If this entry is set to 0, the entry is allowed to remain idle indefinitely without being evicted due to the max idle value. |
| Value Length | vInt | Contains the length of the value. |
| Value | Byte array | The requested value. |
| Response Status | Details |
|---|---|
| 0x00 | The value was successfully stored. |
ForceReturnPreviousValue is passed, the previous value and key are returned. If the previous key and value do not exist, the value length would contain the value 0.
11.6.11. Hot Rod Query Operation
Query operation request format includes the following:
| Field | Data Type | Details |
|---|---|---|
| Header | variable | Request header. |
| Query Length | vInt | The length of the Protobuf encoded query object. |
| Query | Byte array | Byte array containing the Protobuf encoded query object, having a length specified by previous field. |
| Response Status | Data | Details |
|---|---|---|
| Header | variable | Response header. |
| Response payload Length | vInt | The length of the Protobuf encoded response object. |
| Response payload | Byte array | Byte array containing the Protobuf encoded response object, having a length specified by previous field. |
11.6.12. Hot Rod RemoveIfUnmodified Operation
RemoveIfUnmodified operation request format includes the following:
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| Key Length | vInt | Contains the length of the key. |
| Key | Byte array | Contains the key value. |
| Entry Version | 8 bytes | Uses the value returned by the GetWithVersion operation. |
| Response Status | Details |
|---|---|
| 0x00 | Returned status if the entry was replaced or removed. |
| 0x01 | Returns status if the entry replace or remove was unsuccessful because the key was modified. |
| 0x02 | Returns status if the key does not exist. |
ForceReturnPreviousValue is passed, the previous value and key are returned. If the previous key and value do not exist, the value length would contain the value 0.
11.6.13. Hot Rod Remove Operation
Hot Rod Remove operation uses the following request format:
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| Key Length | vInt | Contains the length of the key. The vInt data type is used because of its size (up to 5 bytes), which is larger than the size of Integer.MAX_VALUE. However, Java disallows single array sizes to exceed the size of Integer.MAX_VALUE. As a result, this vInt is also limited to the maximum size of Integer.MAX_VALUE. |
| Key | Byte array | Contains a key, the corresponding value of which is requested. |
| Response Status | Details |
|---|---|
| 0x00 | Successful operation. |
| 0x02 | The key does not exist. |
ForceReturnPreviousValue is passed, the response header contains either:
- The value and length of the previous key.
- The value length
0and the response status0x02to indicate that the key does not exist.
ForceReturnPreviousValue is passed. If the key does not exist or the previous value was null, the value length is 0.
11.6.14. Hot Rod ReplaceIfUnmodified Operation
ReplaceIfUnmodified operation request format includes the following:
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| Key Length | vInt | Contains the length of the key. |
| Key | Byte array | Contains the key value. |
| Lifespan | vInt | Contains the number of seconds before the entry expires. If the number of seconds exceeds thirty days, the value is treated as UNIX time (i.e. the number of seconds since the date 1/1/1970) as the entry lifespan. When set to the value 0, the entry will never expire. |
| Max Idle | vInt | Contains the number of seconds an entry is allowed to remain idle before it is evicted from the cache. If this entry is set to 0, the entry is allowed to remain idle indefinitely without being evicted due to the max idle value. |
| Entry Version | 8 bytes | Uses the value returned by the GetWithVersion operation. |
| Value Length | vInt | Contains the length of the value. |
| Value | Byte array | Contains the requested value. |
| Response Status | Details |
|---|---|
| 0x00 | Returned status if the entry was replaced or removed. |
| 0x01 | Returns status if the entry replace or remove was unsuccessful because the key was modified. |
| 0x02 | Returns status if the key does not exist. |
ForceReturnPreviousValue is passed, the previous value and key are returned. If the previous key and value do not exist, the value length would contain the value 0.
11.6.15. Hot Rod Replace Operation
replace operation request format includes the following:
| Field | Data Type | Details |
|---|---|---|
| Header | - | - |
| Key Length | vInt | Contains the length of the key. |
| Key | Byte array | Contains the key value. |
| Lifespan | vInt | Contains the number of seconds before the entry expires. If the number of seconds exceeds thirty days, the value is treated as UNIX time (i.e. the number of seconds since the date 1/1/1970) as the entry lifespan. When set to the value 0, the entry will never expire. |
| Max Idle | vInt | Contains the number of seconds an entry is allowed to remain idle before it is evicted from the cache. If this entry is set to 0, the entry is allowed to remain idle indefinitely without being evicted due to the max idle value. |
| Value Length | vInt | Contains the length of the value. |
| Value | Byte array | Contains the requested value. |
| Response Status | Details |
|---|---|
| 0x00 | The value was successfully stored. |
| 0x01 | The value was not stored because the key does not exist. |
ForceReturnPreviousValue is passed, the previous value and key are returned. If the previous key and value do not exist, the value length would contain the value 0.
11.6.16. Hot Rod Stats Operation
| Name | Details |
|---|---|
| timeSinceStart | Contains the number of seconds since Hot Rod started. |
| currentNumberOfEntries | Contains the number of entries that currently exist in the Hot Rod server. |
| totalNumberOfEntries | Contains the total number of entries stored in the Hot Rod server. |
| stores | Contains the number of put operations attempted. |
| retrievals | Contains the number of get operations attempted. |
| hits | Contains the number of get hits. |
| misses | Contains the number of get misses. |
| removeHits | Contains the number of remove hits. |
| removeMisses | Contains the number of removal misses. |
| Name | Data Type | Details |
|---|---|---|
| Header | - | - |
| Number of Stats | vInt | Contains the number of individual statistics returned. |
| Name Length | vInt | Contains the length of the named statistic. |
| Name | string | Contains the name of the statistic. |
| Value Length | vInt | Contains the length of the value. |
| Value | string | Contains the statistic value. |
Name Length, Name, Value Length and Value recur for each statistic requested.
11.7. Hot Rod Operation Values
opcode values for a request header and their corresponding response header values:
| Operation | Request Operation Code | Response Operation Code |
|---|---|---|
| put | 0x01 | 0x02 |
| get | 0x03 | 0x04 |
| putIfAbsent | 0x05 | 0x06 |
| replace | 0x07 | 0x08 |
| replaceIfUnmodified | 0x09 | 0x0A |
| remove | 0x0B | 0x0C |
| removeIfUnmodified | 0x0D | 0x0E |
| containsKey | 0x0F | 0x10 |
| getWithVersion | 0x11 | 0x12 |
| clear | 0x13 | 0x14 |
| stats | 0x15 | 0x16 |
| ping | 0x17 | 0x18 |
| bulkGet | 0x19 | 0x1A |
| getWithMetadata | 0x1B | 0x1C |
| bulkKeysGet | 0x1D | 0x1E |
| query | 0x1F | 0x20 |
opcode value is 0x50, it indicates an error response.
11.7.1. Magic Values
Magic field in request and response headers:
| Value | Details |
|---|---|
| 0xA0 | Cache request marker. |
| 0xA1 | Cache response marker. |
11.7.2. Status Values
Status field in a response header:
| Value | Details |
|---|---|
| 0x00 | No error. |
| 0x01 | Not put/removed/replaced. |
| 0x02 | Key does not exist. |
| 0x81 | Invalid Magic value or Message ID. |
| 0x82 | Unknown command. |
| 0x83 | Unknown version. |
| 0x84 | Request parsing error. |
| 0x85 | Server error. |
| 0x86 | Command timed out. |
11.7.3. Transaction Type Values
Transaction Type in a request header:
| Value | Details |
|---|---|
| 0 | Indicates a non-transactional call or that the client does not support transactions. If used, the TX_ID field is omitted. |
| 1 | Indicates X/Open XA transaction ID (XID). This value is currently not supported. |
11.7.4. Client Intelligence Values
Client Intelligence in a request header:
| Value | Details |
|---|---|
| 0x01 | Indicates a basic client that does not require any cluster or hash information. |
| 0x02 | Indicates a client that is aware of topology and requires cluster information. |
| 0x03 | Indicates a client that is aware of hash and distribution and requires both the cluster and hash information. |
11.7.5. Flag Values
flag values in the request header:
| Value | Details |
|---|---|
| 0x0001 | ForceReturnPreviousValue |
11.7.6. Hot Rod Error Handling
| Field | Data Type | Details |
|---|---|---|
| Error Opcode | - | Contains the error operation code. |
| Error Status Number | - | Contains a status number that corresponds to the error opcode. |
| Error Message Length | vInt | Contains the length of the error message. |
| Error Message | string | Contains the actual error message. If an 0x84 error code returns, which indicates that there was an error in parsing the request, this field contains the latest version supported by the Hot Rod server. |
11.8. Put Request Example
put request using Hot Rod:
| Byte | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 |
|---|---|---|---|---|---|---|---|---|
| 8 | 0xA0 | 0x09 | 0x41 | 0x01 | 0x07 | 0x4D ('M') | 0x79 ('y') | 0x43 ('C') |
| 16 | 0x61 ('a') | 0x63 ('c') | 0x68 ('h') | 0x65 ('e') | 0x00 | 0x03 | 0x00 | 0x00 |
| 24 | 0x00 | 0x05 | 0x48 ('H') | 0x65 ('e') | 0x6C ('l') | 0x6C ('l') | 0x6F ('o') | 0x00 |
| 32 | 0x00 | 0x05 | 0x57 ('W') | 0x6F ('o') | 0x72 ('r') | 0x6C ('l') | 0x64 ('d') | - |
| Field Name | Byte | Value |
|---|---|---|
| Magic | 0 | 0xA0 |
| Version | 2 | 0x41 |
| Cache Name Length | 4 | 0x07 |
| Flag | 12 | 0x00 |
| Topology ID | 14 | 0x00 |
| Transaction ID | 16 | 0x00 |
| Key | 18-22 | 'Hello' |
| Max Idle | 24 | 0x00 |
| Value | 26-30 | 'World' |
| Message ID | 1 | 0x09 |
| Opcode | 3 | 0x01 |
| Cache Name | 5-11 | 'MyCache' |
| Client Intelligence | 13 | 0x03 |
| Transaction Type | 15 | 0x00 |
| Key Field Length | 17 | 0x05 |
| Lifespan | 23 | 0x00 |
| Value Field Length | 25 | 0x05 |
put request:
| Byte | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 |
|---|---|---|---|---|---|---|---|---|
| 8 | 0xA1 | 0x09 | 0x01 | 0x00 | 0x00 | - | - | - |
| Field Name | Byte | Value |
|---|---|---|
| Magic | 0 | 0xA1 |
| Opcode | 2 | 0x01 |
| Topology Change Marker | 4 | 0x00 |
| Message ID | 1 | 0x09 |
| Status | 3 | 0x00 |
11.9. Hot Rod Java Client
11.9.1. Hot Rod Java Client Download
client/hotrod/java directory in the Red Hat JBoss Data Grid 6.2 and better Server binary distributions on the Red Hat Customer Portal at https://access.redhat.com
11.9.2. Hot Rod Java Client Configuration
Example 11.1. Client Instance Creation
To configure the Hot Rod Java client, edit the hotrod-client.properties file on the classpath.
hotrod-client.properties file.
Example 11.2. Configuration
new RemoteCacheManager(boolean start)new RemoteCacheManager()
11.9.3. Hot Rod Java Client Basic API
localhost:11222.
Example 11.3. Basic API
RemoteCacheManager corresponds to DefaultCacheManager, and both implement CacheContainer.
DefaultCacheManager and RemoteCacheManager, which is simplified by the common CacheContainer interface.
keySet() method. If the remote cache is a distributed cache, the server will start a Map/Reduce job to retrieve all keys from clustered nodes and return all keys to the client.
Set keys = remoteCache.keySet();
Set keys = remoteCache.keySet();
11.9.4. Hot Rod Java Client Versioned API
getVersioned or getWithVersion, clients can retrieve the value associated with the key as well as the current version.
RemoteCacheManager provides instances of the RemoteCache interface that accesses the named or default cache on the remote cluster. This extends the Cache interface to which it adds new methods, including the versioned API.
remoteCache.put("car", "ferrari");
RemoteCache.VersionedValue valueBinary = remoteCache.getVersioned("car");
assert remoteCache.replace("car", "lamborghini", valueBinary.getVersion());
remoteCache.put("car", "ferrari");
RemoteCache.VersionedValue valueBinary = remoteCache.getVersioned("car");
assert remoteCache.replace("car", "lamborghini", valueBinary.getVersion());
11.10. Hot Rod C ++ Client
11.10.1. Hot Rod C ++ Client Formats
- Static library
- Shared/Dynamic library
The static library is statically linked to an application. This increases the size of the final executable. The application is self-contained and it does not need to ship a separate library.
Shared/Dynamic libraries are dynamically linked to an application at runtime. The library is stored in a separate file and can be upgraded separately from the application, without recompiling the application.
Note
11.10.2. Hot Rod C ++ Client Download
jboss-datagrid-<version>-hotrod-cpp-client-<platform>.zip under Red Hat JBoss Data Grid 6.2 binaries on the Red Hat Customer Portal at https://access.redhat.com. Download the appropriate Hot Rod C++ client which applies to your operating system.
11.10.3. Hot Rod C ++ Client Configuration
- The initial set of servers to connect to.
- Connection pooling attributes.
- Connection/Socket timeouts and TCP nodelay.
- Hot Rod protocol version.
The following example shows how to use the ConfigurationBuilder to configure a RemoteCacheManager and how to obtain the default remote cache:
Example 11.4. SimpleMain.cpp
11.10.4. Hot Rod C ++ Client API
Example 11.5. SimpleMain.cpp
11.10.5. Hot Rod C ++ Client Requisites
- C++ 03 compiler with support for shared_ptr TR1 (GCC 4.0+, Visual Studio C++ 2010).
- Red Hat JBoss Data Grid Server 6.1.0 or higher version.
11.11. Interoperability Between C++ and Hot Rod Java Client
Person object structured and serialized using Protobuf, and the Java C++ client can read the same Person object structured as Protobuf.
11.12. Configure the Interface Using Connectors
- The
hotrod-connectorelement, which defines the configuration for a Hot Rod based connector. - The
memcached-connectorelement, which defines the configuration for a memcached based connector. - The
rest-connectorelement, which defines the configuration for a REST interface based connector.
11.12.1. Configure Hot Rod Connectors
hotrod-connector and topology-state-transfer elements must be configured based on the following procedure.
Procedure 11.1. Configuring Hot Rod Connectors for Remote Client-Server Mode
The
hotrod-connectorElementThehotrod-connectorelement defines the configuration elements for use with Hot Rod.The
socket-bindingParameterThesocket-bindingparameter specifies the socket binding port used by the Hot Rod connector. This is a mandatory parameter.<subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <hotrod-connector socket-binding="hotrod" /><subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <hotrod-connector socket-binding="hotrod" />Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
cache-containerParameterThecache-containerparameter names the cache container used by the Hot Rod connector. This is a mandatory parameter.<subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <hotrod-connector socket-binding="hotrod" cache-container="local" /><subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <hotrod-connector socket-binding="hotrod" cache-container="local" />Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
worker-threadsParameterTheworker-threadsparameter specifies the number of worker threads available for the Hot Rod connector. The default value for this parameter is the number of cores available multiplied by two. This is an optional parameter.<subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <hotrod-connector socket-binding="hotrod" cache-container="local" worker-threads="${VALUE}" /><subsystem xmlns="urn:infinispan:server:endpoint:6.0"> <hotrod-connector socket-binding="hotrod" cache-container="local" worker-threads="${VALUE}" />Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
idle-timeoutParameterTheidle-timeoutparameter specifies the time (in milliseconds) the connector can remain idle before the connection times out. The default value for this parameter is-1, which means that no timeout period is set. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
tcp-nodelayParameterThetcp-nodelayparameter specifies whether TCP packets will be delayed and sent out in batches. Valid values for this parameter aretrueandfalse. The default value for this parameter istrue. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
send-buffer-sizeParameterThesend-buffer-sizeparameter indicates the size of the send buffer for the Hot Rod connector. The default value for this parameter is the size of the TCP stack buffer. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
receive-buffer-sizeParameterThereceive-buffer-sizeparameter indicates the size of the receive buffer for the Hot Rod connector. The default value for this parameter is the size of the TCP stack buffer. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The
topology-state-transferElementThetopology-state-transferelement specifies the topology state transfer configurations for the Hot Rod connector. This element can only occur once within ahotrod-connectorelement.The
lock-timeoutParameterThelock-timeoutparameter specifies the time (in milliseconds) after which the operation attempting to obtain a lock times out. The default value for this parameter is10seconds. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
replication-timeoutParameterThereplication-timeoutparameter specifies the time (in milliseconds) after which the replication operation times out. The default value for this parameter is10seconds. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
update-timeoutParameterTheupdate-timeoutparameter specifies the time (in milliseconds) after which the update operation times out. The default value for this parameter is30seconds. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
external-hostParameterTheexternal-hostparameter specifies the hostname sent by the Hot Rod server to clients listed in the topology information. The default value for this parameter is the host address. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
external-portParameterTheexternal-portparameter specifies the port sent by the Hot Rod server to clients listed in the topology information. The default value for this parameter is the configured port. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
lazy-retrievalParameterThelazy-retrievalparameter indicates whether the Hot Rod connector will carry out retrieval operations lazily. The default value for this parameter istrue. This is an optional parameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
11.13. Hot Rod Interface Security
11.13.1. Publish Hot Rod Endpoints as a Public Interface
interface parameter in the socket-binding element from management to public as follows:
<socket-binding name="hotrod" interface="public" port="11222" />
<socket-binding name="hotrod" interface="public" port="11222" />
11.13.2. SSL/TLS Authentication for Hot Rod
Procedure 11.2. Secure Hot Rod Using SSL/TLS
Generate a Keystore
Create a Java Keystore using the keytool application distributed with the JDK and add your certificate to it. The certificate can be either self signed, or obtained from a trusted CA depending on your security policy.Place the Keystore in the Configuration Directory
Put the keystore in the~/JDG_HOME/standalone/configurationdirectory with thestandalone-hotrod-ssl.xmlfile from the~/JDG_HOME/docs/examples/configsdirectory.Declare an SSL Server Identity
Declare an SSL server identity within a security realm in the management section of the configuration file. The SSL server identity must specify the path to a keystore and its secret key.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the Security Element
Add the security element to the Hot Rod connector as follows:<hotrod-connector socket-binding="hotrod" cache-container="local"> <security ssl="true" security-realm="ApplicationRealm" require-ssl-client-auth="false" /> </hotrod-connector><hotrod-connector socket-binding="hotrod" cache-container="local"> <security ssl="true" security-realm="ApplicationRealm" require-ssl-client-auth="false" /> </hotrod-connector>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Server Authentication of Certificate
If you require the server to perform authentication of the client certificate, create a truststore that contains the valid client certificates and set therequire-ssl-client-authattribute totrue.
Start the Server
Start the server using the following:This will start a server with a Hot Rod endpoint on port 11222. This endpoint will only accept SSL connections.bin/standalone.sh -c standalone-hotrod-ssl.xml
bin/standalone.sh -c standalone-hotrod-ssl.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Part III. Advanced Features in Red Hat JBoss Data Grid
- Transactions
- Marshalling
- Listeners and Notifications
- The Infinspan CDI Module
- Rolling Upgrades
- MapReduce
- Distributed Execution
- Interoperability and Compatibility Mode
Chapter 12. Transactions
12.1. About Java Transaction API Transactions
- First, it retrieves the transactions currently associated with the thread.
- If not already done, it registers an
XAResourcewith the transaction manager to receive notifications when a transaction is committed or rolled back.
12.2. Transactions Spanning Multiple Cache Instances
12.3. The Transaction Manager
TransactionManager tm = cache.getAdvancedCache().getTransactionManager();
TransactionManager tm = cache.getAdvancedCache().getTransactionManager();Note
XAResource xar = cache.getAdvancedCache().getXAResource();
XAResource xar = cache.getAdvancedCache().getXAResource();Chapter 13. Marshalling
- transform data for relay to other JBoss Data Grid nodes within the cluster.
- transform data to be stored in underlying cache stores.
13.1. About Marshalling Framework
java.io.ObjectOutput and java.io.ObjectInput implementations compared to the standard java.io.ObjectOutputStream and java.io.ObjectInputStream.
13.2. Support for Non-Serializable Objects
Serializable or Externalizable support into your classes, you could (as an example) use XStream to convert the non-serializable objects into a String that can be stored in JBoss Data Grid.
Note
13.3. Hot Rod and Marshalling
- All data stored by clients on the JBoss Data Grid server are provided either as a byte array, or in a primitive format that is marshalling compatible for JBoss Data Grid.On the server side of JBoss Data Grid, marshalling occurs where the data stored in primitive format are converted into byte array and replicated around the cluster or stored to a cache store. No marshalling configuration is required on the server side of JBoss Data Grid.
- At the client level, marshalling must have a
Marshallerconfiguration element specified in the RemoteCacheManager configuration in order to serialize and deserialize POJOs.Due to Hot Rod's binary nature, it relies on marshalling to transform POJOs, specifically keys or values, into byte array.
13.4. Configuring the Marshaller using the RemoteCacheManager
marshaller configuration element in the RemoteCacheManager, the value of which must be the name of the class implementing the Marshaller interface. The default value for this property is org.infinispan.commons.marshall.jboss.GenericJBossMarshaller.
Procedure 13.1. Define a Marshaller
Create a ConfigurationBuilder
Create a ConfigurationBuilder and configure it with the required settings.ConfigurationBuilder builder = new ConfigurationBuilder(); //... (other configuration)
ConfigurationBuilder builder = new ConfigurationBuilder(); //... (other configuration)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add a Marshaller Class
Add a Marshaller class specification within the Marshaller method.builder.marshaller(GenericJBossMarshaller.class);
builder.marshaller(GenericJBossMarshaller.class);Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Alternatively, specify a custom Marshaller instance.
builder.marshaller(new GenericJBossMarshaller());
builder.marshaller(new GenericJBossMarshaller());Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Start the RemoteCacheManager
Build the configuration containing the Marshaller, and start a new RemoteCacheManager with it.Configuration configuration = builder.build(); RemoteCacheManager manager = new RemoteCacheManager(configuration);
Configuration configuration = builder.build(); RemoteCacheManager manager = new RemoteCacheManager(configuration);Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Note
13.5. Troubleshooting
13.5.1. Marshalling Troubleshooting
java.lang.Object instance within an org.infinispan.commands.write.PutKeyValueCommand instance cannot be serialized because java.lang.Object@b40ec4 is not serializable.
DEBUG or TRACE logging levels are enabled, marshalling exceptions will contain toString() representations of objects in the stack trace. The following is an example that depicts such a scenario:
IOException was thrown when an instance of the inner class org.infinispan.marshall.VersionAwareMarshallerTest$1 is unmarshalled.
DEBUG or TRACE logging levels are enabled, the class type's classloader information is provided. An example of this classloader information is as follows:
13.5.2. Other Marshalling Related Issues
EOFException, displayed as follows, when failing to read the transaction log that was not written by the sender:
Chapter 14. Listeners and Notifications
14.1. The Notification/Listener API
14.2. Listener Notifications
@Listener. A Listenable is an interface that denotes that the implementation can have listeners attached to it. Each listener is registered using methods defined in the Listenable.
14.2.1. About Cache-level Notifications
14.2.2. Cache Manager-level Notifications
- Nodes joining or leaving a cluster;
- The starting and stopping of caches
14.2.3. About Synchronous and Asynchronous Notifications
@Listener (sync = false)public class MyAsyncListener { .... }
@Listener (sync = false)public class MyAsyncListener { .... }
<asyncListenerExecutor/> element in the configuration file to tune the thread pool that is used to dispatch asynchronous notifications.
14.3. Modifying Cache Entries
14.3.1. Cache Entry Modified Listener Configuration
getValue() method's behavior is specific to whether the callback is triggered before or after the actual operation has been performed. For example, if event.isPre() is true, then event.getValue() would return the old value, prior to modification. If event.isPre() is false, then event.getValue() would return new value. If the event is creating and inserting a new entry, the old value would be null. For more information about isPre(), see the Red Hat JBoss Data Grid API Documentation's listing for the org.infinispan.notifications.cachelistener.event package.
14.3.2. Listener Example
14.3.3. Cache Entry Modified Listener Example
14.4. NotifyingFutures
Futures, but a sub-interface known as a NotifyingFuture. Unlike a JDK Future, a listener can be attached to a NotifyingFuture to notify the user about a completed future.
Note
NotifyingFutures are only available in JBoss Data Grid Library mode.
14.4.1. NotifyingFutures Example
NotifyingFutures in Red Hat JBoss Data Grid:
Chapter 15. The Infinspan CDI Module
infinispan-cdi module. The infinispan-cdi module offers:
- Configuration and injection using the Cache API.
- A bridge between the cache listeners and the CDI event system.
- Partial support for the JCACHE caching annotations.
15.1. Using Infinispan CDI
15.1.1. Infinispan CDI Prerequisites
- Ensure that the most recent version of the infinispan-cdi module is used.
- Ensure that the correct dependency information is set.
15.1.2. Set the CDI Maven Dependency
pom.xml file in your maven project:
infinispan-cdi jar file is available at modules/infinispan-cdi in the ZIP distribution.
15.2. Using the Infinispan CDI Module
- To configure and inject Infinispan caches into CDI Beans and Java EE components.
- To configure cache managers.
- To control storage and retrieval using CDI annotations.
15.2.1. Configure and Inject Infinispan Caches
15.2.1.1. Inject an Infinispan Cache
public class MyCDIBean {
@Inject
Cache<String, String> cache;
}
public class MyCDIBean {
@Inject
Cache<String, String> cache;
}
15.2.1.2. Inject a Remote Infinispan Cache
public class MyCDIBean {
@Inject
RemoteCache<String, String> remoteCache;
}
public class MyCDIBean {
@Inject
RemoteCache<String, String> remoteCache;
}
15.2.1.3. Set the Injection's Target Cache
- Create a qualifier annotation.
- Add a producer class.
- Inject the desired class.
15.2.1.3.1. Create a Qualifier Annotation
@SmallCache qualifier to specify how to create specific caches.
15.2.1.3.2. Add a Producer Class
@SmallCache qualifier (created in the previous step) specifies a way to create a cache:
@ConfigureCachespecifies the name of the cache.@SmallCacheis the cache qualifier.
15.2.1.3.3. Inject the Desired Class
@SmallCache qualifier and the new producer class to inject a specific cache into the CDI bean as follows:
public class MyCDIBean {
@Inject @SmallCache
Cache<String, String> mySmallCache;
}
public class MyCDIBean {
@Inject @SmallCache
Cache<String, String> mySmallCache;
}
15.2.2. Configure Cache Managers with CDI
15.2.2.1. Specify the Default Configuration
Note
@Default qualifier if no other qualifiers are provided.
@Produces annotation is placed in a method that returns a Configuration instance, the method is invoked when a Configuration object is required.
15.2.2.2. Override the Creation of the Embedded Cache Manager
After a producer method is annotated, this method will be called when creating an EmbeddedCacheManager, as follows:
@ApplicationScoped annotation specifies that the method is only called once.
The following configuration can be used to create an EmbeddedCacheManager that can create clustered caches.
The method annotated with @Produces in the non clustered method generates Configuration objects. The methods in the clustered cache example annonated with @Produces generate EmbeddedCacheManager objects.
EmbeddedCacheManager and injects it into the code at runtime.
... @Inject EmbeddedCacheManager cacheManager; ...
...
@Inject
EmbeddedCacheManager cacheManager;
...
15.2.2.3. Configure a Remote Cache Manager
RemoteCacheManager is configured in a manner similar to EmbeddedCacheManagers, as follows:
15.2.2.4. Configure Multiple Cache Managers with a Single Class
15.2.3. Storage and Retrieval Using CDI Annotations
15.2.3.1. Configure Cache Annotations
javax.cache package.
15.2.3.2. Enable Cache Annotations
beans.xml file. Adding the following code adds interceptors such as the CacheResultInterceptor, CachePutInterceptor, CacheRemoveEntryInterceptor and the CacheRemoveAllInterceptor:
Note
beans.xml file for Red Hat JBoss Data Grid to use javax.cache annotations.
15.2.3.3. Caching the Result of a Method Invocation
toCelsiusFormatted method again and stores the result in the cache.
@CacheResult annotation from the javax.cache.annotation package instead, as follows:
toCelsiusFormatted() method call.
Note
15.2.3.3.1. Specify the Cache Used
cacheName) to the @CacheResult annotation to specify the cache to check for results of the method call:
@CacheResult(cacheName = "mySpecialCache")
public void doSomething(String parameter) {
...
}
@CacheResult(cacheName = "mySpecialCache")
public void doSomething(String parameter) {
...
}
15.2.3.3.2. Cache Keys for Cached Results
@CacheResult annotation creates a key for the results fetched from a cache. The key consists of a combination of all parameters in the relevant method.
@CacheKey annotation as follows:
p1 and p2 are used to create the cache key. The value of dontCare is not used when determining the cache key.
15.2.3.3.3. Generate a Custom Key
cacheKeyGenerator to the @CacheResult annotation as follows:
@CacheResult(cacheKeyGenerator = MyCacheKeyGenerator.class)
public void doSomething(String p1, String p2) {
...
}
@CacheResult(cacheKeyGenerator = MyCacheKeyGenerator.class)
public void doSomething(String p1, String p2) {
...
}
p1 contains the custom key.
15.2.3.3.4. CacheKey Implementation Code
equals() and hashCode() methods must be correctly implemented for the GeneratedCacheKey to work as expected.
15.2.4. Cache Operations
15.2.4.1. Update a Cache Entry
@CachePut annotation is invoked, a parameter (normally passed to the method annotated with @CacheValue) is stored in the cache.
@CachePut annotated method:
cacheName and cacheKeyGenerator in the @CachePut method. Additionally, some parameters in the invoked method may be annotated with @CacheKey to control key generation.
15.2.4.2. Remove an Entry from the Cache
@CacheRemoveEntry annotated method and is used to remove an entry from the cache:
cacheName and cacheKeyGenerator attributes.
15.2.4.3. Clear the Cache
@CacheRemoveAll method to clear all entries from the cache. An example of a method annotated with @CacheRemoveAll is as follows
cacheName attribute.
Chapter 16. Rolling Upgrades
16.1. Rolling Upgrades Using REST
Procedure 16.1. Perform Rolling Upgrades Using REST
Create a Target Cluster
Start a new cluster (the target cluster) with the new version of JBoss Data Grid. Use either different network settings of a different JGroups cluster name to set it apart from the source cluster.Migrate Caches to the Target Cluster
To migrate multiple caches from the source and target cluster, configure aRestCacheStorewith the following settings:- Ensure that the
hostandportvalues point to the source cluster. - Ensure that the
pathvalue points to the source cluster's REST endpoint.
Restart Each Node
Configure each client to point to the target cluster instead of the source cluster. One by one, restart each node in the cluster to apply the new configuration. Eventually, the target cluster will handle all requests instead of the source cluster. The target cluster then lazily loads data from the source cluster on demand using theRestCacheStore.Dump the Key Set
When all connections have shifted to the target cluster, remove the source cluster key set. This is done either using JMX or the CLI as follows:Using JMX
Invoke therecordKnownGlobalKeysetoperation on theRollingUpgradeManagerMBean on the source cluster for all caches to be migrated.Using the CLI
Run theupgrade --dumpkeyscommand on the source cluster for all caches to be migrated. Optionally, use the--allswitch to dump all the caches in the cluster.
Fetch the Remaining Data
The target cluster must fetch all the remaining data from the source cluster. This is done either using JMX or the CLI as follows:Using JMX
Invoke thesynchronizeDataoperation with therestparameter specified on theRollingUpgradeManagerMBean on the target cluster for all caches to be migrated.Using the CLI
Run theupgrade --synchronize=reston the target cluster for all caches to be migrated. Optionally, use the--allswitch to synchronize all caches in the cluster.
Disable the RestCacheStore
Disable theRestCacheStoreon the target cluster using either JMX or the CLI as follows:Using JMX
Invoke thedisconnectSourceoperation with therestparameter specified on theRollingUpgradeManagerMBean on the target cluster for all caches to be migrated.Using the CLI
Run theupgrade --disconnectsource=restcommand on the target cluster for all caches to be migrated. Optionally, use the--allswitch to disconnect all caches in the cluster.
Migration to the target cluster is complete. The source cluster can now be decommissioned
16.2. Rolling Upgrades Using Hot Rod (Remote Client-Server Mode)
Important
- For JBoss Data Grid 6.1, use Hot Rod protocol version 1.2
- For JBoss Data Grid 6.2, use Hot Rod protocol version 1.3
This procedure assumes that a cluster is already configured and running, and that it is using an older version of JBoss Data Grid. This cluster is referred to below as the Source Cluster and the Target Cluster refers to the new cluster to which data will be migrated.
Begin a New Cluster (Target Cluster)
Start the Target Cluster with the new version of JBoss Data Grid.Use either different network settings or JGroups cluster name to avoid overlap with the Source Cluster.Configure the Target Cluster with a
RemoteCacheStoreThe Target Cluster is configured with aRemoteCacheStorewith the following settings for each cache to be migrated:serversmust point to the Source Cluster.cache namemust coincide with the name of the cache on the Source Cluster.hotrod-wrappingmust be enabled ("true").purgemust be disabled ("false").passivationmust be disabled ("false").
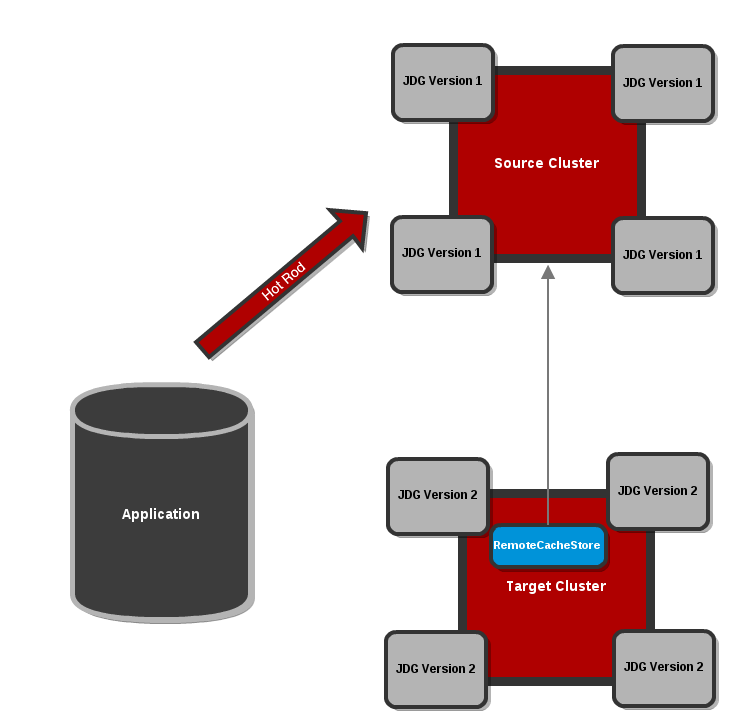
Figure 16.1. Configure the Target Cluster with a RemoteCacheStore
Note
See the$JDG_HOME/server/docs/examples/configs/standalone-hotrod-rolling-upgrade.xmlfile for a full example of the Target Cluster configuration for performing Rolling Upgrades.Target Cluster configuration example assumes the Source Cluster is running withstandalone.xmlconfiguration:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure clients to point to the Target Cluster
Configure clients to point to the Target Cluster instead of the Source Cluster, restarting each client node one by one.Eventually all requests will be handled by the Target Cluster, which will lazily load data from the Source Cluster on demand. The Source Cluster is now theRemoteCacheStorefor the Target Cluster.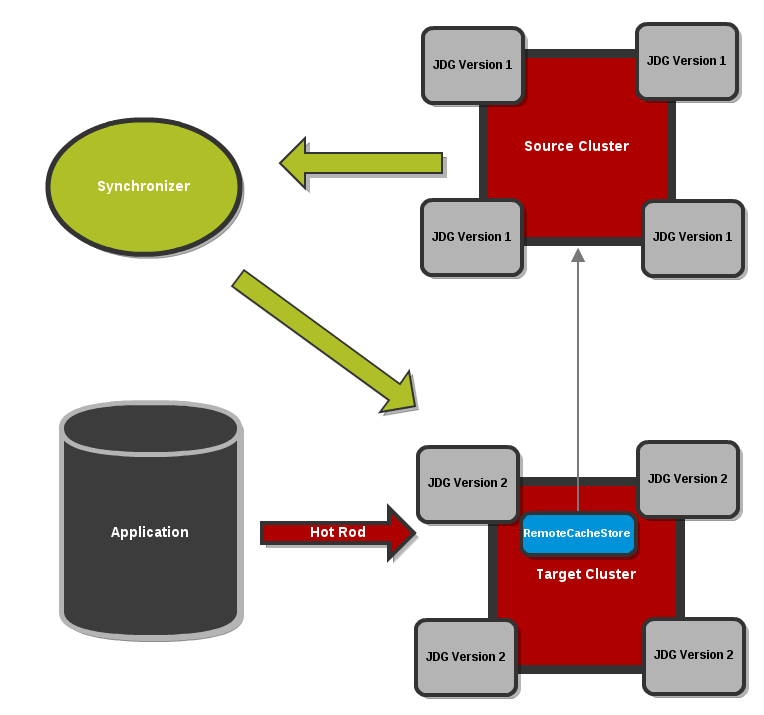
Figure 16.2. Clients point to the Target Cluster with the Source Cluster as
RemoteCacheStorefor the Target Cluster.Dump the Source Cluster keyset
When all connections are using the Target Cluster, the keyset on the Source Cluster must be dumped. This can be done using either JMX or the CLI:JMX
Invoke therecordKnownGlobalKeysetoperation on theRollingUpgradeManagerMBean on the Source Cluster for every cache that must be migrated.CLI
Invoke theupgrade --dumpkeyscommand on the Source Cluster for every cache that must be migrated, or use the--allswitch to dump all caches in the cluster.
Fetch remaining data from the Source Cluster
The Target Cluster fetches all remaining data from the Source Cluster. Again, this can be done using either JMX or CLI:JMX
Invoke thesynchronizeDataoperation and specify thehotrodparameter on theRollingUpgradeManagerMBean on the Target Cluster for every cache that must be migrated.CLI
Invoke theupgrade --synchronize=hotrodcommand on the Target Cluster for every cache that must be migrated, or use the--allswitch to synchronize all caches in the cluster.
Disabling the
RemoteCacheStoreOnce the Target Cluster has obtained all data from the Source Cluster, theRemoteCacheStoreon the Target Cluster must be disabled. This can be done as follows:JMX
Invoke thedisconnectSourceoperation specifying thehotrodparameter on theRollingUpgradeManagerMBean on the Target Cluster.CLI
Invoke theupgrade --disconnectsource=hotrodcommand on the Target Cluster.
- Decommission the Source Cluster.
16.3. RollingUpgradeManager Operations
RollingUpgradeManager Mbean handles the operations that allow data to be migrated from one version of Red Hat JBoss Data Grid to another when performing rolling upgrades. The RollingUpgradeManager operations are:
recordKnownGlobalKeysetretrieves the entire keyset from the cluster running on the old version of JBoss Data Grid.synchronizeDataperforms the migration of data from the Source Cluster to the Target Cluster, which is running the new version of JBoss Data Grid.disconnectSourcedisables the Source Cluster, the older version of JBoss Data Grid, once data migration to the Target Cluster is complete.
16.4. RemoteCacheStore Parameters for Rolling Upgrades
16.4.1. rawValues and RemoteCacheStore
rawValues parameter causes the raw values to be stored instead for interoperability with direct access by RemoteCacheManagers.
rawValues must be enabled in order to interact with a Hot Rod cache via both RemoteCacheStore and RemoteCacheManager.
16.4.2. hotRodWrapping
hotRodWrapping parameter is a shortcut that enables rawValues and sets an appropriate marshaller and entry wrapper for performing Rolling Upgrades.
Chapter 17. MapReduce
- The user initiates a task on a cache instance, which runs on a cluster node (the master node).
- The master node receives the task input, divides the task, and sends tasks for map phase execution on the grid.
- Each node executes a
Mapperfunction on its input, and returns intermediate results back to the master node.- If the
distributedReducePhaseparameter is set to"true", the map results are inserted in an intermediary cache, rather than being returned to the master node. - If a
Combinerhas been specified withtask.combinedWith(combiner), theCombineris called on theMapperresults and the combiner's results are returned to the master node or inserted in the intermediary cache.
- The master node collects all intermediate results from the map phase and merges all intermediate values associated with the same intermediate key.
- If the
distributedReducePhaseparameter is set totrue, the merging of the intermediate values is done on each node, as theMapperorCombinerresults are inserted in the intermediary cache.The master node only receives the intermediate keys.
- The master node sends intermediate key/value pairs for reduction on the grid.
- If the
distributedReducePhaseparameter is set to"false", the reduction phase is executed only on the master node.
- The final results of the reduction phase are returned.
- If the
distributedReducePhaseparameter is set to"true", the master node running the task receives all results from the reduction phase and returns the final result to the MapReduce task initiator. - If a
Collatorhas been specified withtask.execute(Collator), theCollatoris executed on the reduction phase results, and theCollatorresult is returned to the task initiator.
17.1. The MapReduce API
MapperReducerCollatorMapReduceTask
Mapper class implementation is a component of MapReduceTask, which is invoked once per input cache entry key/value pair. Map is a process of applying a given function to each element of a list, returning a list of results.
Mapper on a given cache entry key/value input pair. It then transforms this cache entry key/value pair into an intermediate key/value pair, which is emitted into the provided Collator instance.
Reducer. JBoss Data Grid's distributed execution environment creates one instance of Reducer per execution node.
Reducer interface is used for Combiners. A Combiner is similar to a Reducer, except that it must be able to work on partial results. The Combiner is executed on the results of the Mapper, on the same node, without considering the other nodes that might have generated values for the same intermediate key.
Combiners only see a part of the intermediate values, they cannot be used in all scenarios, however when used they can reduce network traffic and memory consumption in the intermediate cache significantly.
Collator coordinates results from Reducers that have been executed on JBoss Data Grid, and assembles a final result that is delivered to the initiator of the MapReduceTask. The Collator is applied to the final map key/value result of MapReduceTask.
17.1.1. MapReduceTask
MapReduceTask is a distributed task, which unifies the Mapper, Combiner, Reducer, and Collator components into a cohesive computation, which can be parallelized and executed across a large-scale cluster.
new MapReduceTask(cache)
.mappedWith(new MyMapper())
.combinedWith(new MyCombiner())
.reducedWith(new MyReducer())
.execute(new MyCollator());
new MapReduceTask(cache)
.mappedWith(new MyMapper())
.combinedWith(new MyCombiner())
.reducedWith(new MyReducer())
.execute(new MyCollator());MapReduceTask requires a cache containing data that will be used as input for the task. The JBoss Data Grid execution environment will instantiate and migrate instances of provided Mappers and Reducers seamlessly across the nodes.
onKeys method as an input key filter.
MapReduceTask constructor parameters that determine how the intermediate values are processed:
distributedReducePhase- When set to"false", the default setting, the reducers are only executed on the master node. If set to"true", the reducers are executed on every node in the cluster.useIntermediateSharedCache- Only important ifdistributedReducePhaseis set to"true". If"true", which is the default setting, this task will share intermediate value cache with other executing MapReduceTasks on the grid. If set to"false", this task will use its own dedicated cache for intermediate values.
17.1.2. Mapper and CDI
Mapper is invoked with appropriate input key/value pairs on an executing node, however Red Hat JBoss Data Grid also provides a CDI injection for an input cache. The CDI injection can be used where additional data from the input cache is required in order to complete map transformation.
Mapper is executed on a JBoss Data Grid executing node, the JBoss Data Grid CDI module provides an appropriate cache reference, which is injected to the executing Mapper. To use the JBoss Data Grid CDI module with Mapper:
- Declare a cache field in
Mapper. - Annotate the cache field
Mapperwith@org.infinispan.cdi.Input. - Annotate with mandatory
@Inject annotation.
17.2. MapReduceTask Distributed Execution
- Mapping phase.
- Outgoing Key and Outgoing Value Migration.
- Reduce phase.
Procedure 17.1. Mapping Phase
- The input keys are grouped according to their owner nodes.
- On each node the
Mapperfunction processes all key/value pairs local to that node. - The results of the mapping process are collected using a
Collector. - If a
Reduceris specified, it is applied to all intermediate values collected for each outgoing key (KOut,VOut).
Procedure 17.2. Outgoing Key and Outgoing Value Migration Phase
- Intermediate keys exposed by the
Mapperare grouped by the intermediate outgoing key (KOutvalues. This grouping preserves the keys, as the mapping phase, when applied to other nodes in the cluster, may generate identical intermediate keys. - Once the Reduce phase has been invoked, (as described in Step 4 of the Mapping Phase above), an underlying hashing mechanism, a temporary distributed cache, and a DeltaAware cache insertion mechanism are used to:
- hash the intermediate key
KOutusing its owner node. - migrate the hashed
KOutkey and its correspondingVOutvalue to the same owner node.
- The list of
KOutkeys are returned to the master node.VOutvalues are not returned as they are not required by the master node.
Procedure 17.3. Reduce Phase
KOutkeys are grouped according to owner node.- The reduce operation applies to each node and its input (grouped
KOutkeys) as follows:- The reduce operation locates the temporary distributed cache created during the migration phase on the target node.
- For each
KOutkey, a list ofVOutvalues is taken from the temporary cache. - The
KOutandVOutvalues are wrapped in anIteratorand the reduce operation is applied to the result.
- The reduce operation generates a map where each key is
KOutand each value isVOut.Each node has its own map. - The maps from each node in the cluster are combined into a single map (
M). - The MapReduce task returns map (
M) to the node that initiated theMapReducetask.
17.3. Map Reduce Example
sentence stored on JBoss Data Grid nodes.
- Key is a String.
- Each sentence is a String.
Collator is defined, which will transform the result of MapReduceTask Map<KOut,VOut> into a String that is returned to a task invoker. The Collator is a transformation function applied to a final result of MapReduceTask.
Chapter 18. Distributed Execution
ExecutorService interface. Tasks submitted for execution are executed on an entire cluster of JBoss Data Grid nodes, rather than being executed in a local JVM.
- Each
DistributedExecutorServiceis bound to a single cache. Tasks submitted have access to key/value pairs from that particular cache if the task submitted is an instance ofDistributedCallable. - Every
Callable,Runnable, and/orDistributedCallablesubmitted must be eitherSerializableorExternalizable, in order to prevent task migration to other nodes each time one of these tasks is performed. The value returned from aCallablemust also beSerializableorExternalizable.
18.1. DistributedCallable API
DistributedCallable interface is a subtype of the existing Callable from java.util.concurrent.package, and can be executed in a remote JVM and receive input from Red Hat JBoss Data Grid. The DistributedCallable interface is used to facilitate tasks that require access to JBoss Data Grid cache data.
DistributedCallable API to execute a task, the task's main algorithm remains unchanged, however the input source is changed.
Callable interface to describe task units must extend DistributedCallable and use keys from JBoss Data Grid execution environment as input for the task. For example:
18.2. Callable and CDI
DistributedCallable cannot be implemented or is not appropriate, and a reference to input cache used in DistributedExecutorService is still required, there is an option to inject the input cache by CDI mechanism.
Callable task arrives at a Red Hat JBoss Data Grid executing node, JBoss Data Grid's CDI mechanism provides an appropriate cache reference, and injects it to the executing Callable.
Callable:
- Declare a
Cachefield inCallableand annotated withorg.infinispan.cdi.Input - Include the mandatory
@Injectannotation.
18.3. Distributed Task Failover
- Failover due to a node failure where a task is executing.
- Failover due to a task failure; for example, if a
Callabletask throws an exception.
Runnable, Callable, and DistributedCallable tasks fail without invoking any failover mechanism.
Distributed task on another random node if one is available.
DistributedTaskFailoverPolicy interface can also be implemented to provide failover management. For example:
18.4. Distributed Task Execution Policy
DistributedTaskExecutionPolicy allows tasks to specify a custom execution policy across the Red Hat JBoss Data Grid cluster, by scoping execution of tasks to a subset of nodes.
DistributedTaskExecutionPolicy can be used to manage task execution in the following cases:
- where a task is to be exclusively executed on a local network site instead of a backup remote network center.
- where only a dedicated subset of a certain JBoss Data Grid rack nodes are required for specific task execution.
18.5. Distributed Execution Example
- As shown below, the area of a square is:Area of a Square (S) = 4r 2
- The following is an equation for the area of a circle:Area of a Circle (C) = π x r 2
- Isolate r 2 from the first equation:r 2 = S/4
- Inject this value of r 2 into the second equation to find a value for Pi:C = Sπ/4
- Isolating π in the equation results in:C = Sπ/44C = Sπ4C/S = π

Figure 18.1. Distributed Execution Example
Chapter 19. Data Interoperability
19.1. Interoperability Between Library and Remote Client-Server Endpoints
- store and retrieve data in a local (embedded) way
- store and retrieve data remotely using various endpoints
19.2. Using Compatibility Mode
- all endpoints configurations specify the same cache manager
- all endpoints can interact with the same target cache
19.3. Protocol Interoperability
The compatibility element's enabled parameter is set to true or false to determine whether compatibility mode is in use.
Use a configurationBuilder with the compatibility mode enabled as follows:
ConfigurationBuilder builder = ... builder.compatibility().enable();
ConfigurationBuilder builder = ...
builder.compatibility().enable();
The compatibility element's enabled parameter is set to true or false to determine whether compatibility mode is in use.
<namedCache name="compatcache"> <compatibility enabled="true"/> </namedCache>
<namedCache name="compatcache">
<compatibility enabled="true"/>
</namedCache>
19.3.1. Use Cases and Requirements
| Use Case | Client A (Reader or Writer) | Client B (Write/Read Counterpart of Client A) |
|---|---|---|
| 1 | Memcached | Hot Rod Java |
| 2 | REST | Hot Rod Java |
| 3 | Memcached | REST |
| 4 | Hot Rod Java | Hot Rod C++ |
| 5 | Embedded | Hot Rod Java |
| 6 | REST | Hot Rod C++ |
| 7 | Memcached | Hot Rod C++ |
Person instance, it would use a String as a key.
Client A Side
- A uses a third-party marshaller, such as Protobuf or Avro, to serialize the
Personvalue into a byte[]. A UTF-8 encoded string must be used as the key (according to Memcached protocol requirements). - A writes a key-value pair to the server (key as UTF-8 string, the value as byte arrays).
Client B Side
- B must read a
Personfor a specific key (String). - B serializes the same UTF-8 key into the corresponding byte[].
- B invokes
get(byte[]) - B obtains a byte[] representing the serialized object.
- B uses the same marshaller as A to unmarshall the byte[] into the corresponding
Personobject.
Note
- In Use Case 4, the Protostream Marshaller, which is included with the Hot Rod Java client, is recommended. For the Hot Rod C++ client, the Protobuf Marshaller from Google (https://developers.google.com/protocol-buffers/docs/overview) is recommended.
- In Use Case 5, the default Hot Rod marshaller can be used.
19.3.2. Protocol Interoperability Over REST
application/x-java-serialized-object, application/xml, or application/json. Any other byte arrays are treated as application/octet-stream.
Appendix A. Revision History
| Revision History | ||||
|---|---|---|---|---|
| Revision 6.2.1-3 | Tue Mar 18 2014 | |||
| ||||
| Revision 6.2.1-2 | Wed Mar 12 2014 | |||
| ||||
| Revision 6.2.1-1 | Fri Mar 07 2014 | |||
| ||||
| Revision 6.2.1-0 | Thu Feb 27 2014 | |||
| ||||