此内容没有您所选择的语言版本。
2.8.9. IPTables
Included with Red Hat Enterprise Linux are advanced tools for network packet filtering — the process of controlling network packets as they enter, move through, and exit the network stack within the kernel. Kernel versions prior to 2.4 relied on
ipchains for packet filtering and used lists of rules applied to packets at each step of the filtering process. The 2.4 kernel introduced iptables (also called netfilter), which is similar to ipchains but greatly expands the scope and control available for filtering network packets.
This chapter focuses on packet filtering basics, explains various options available with
iptables commands, and explains how filtering rules can be preserved between system reboots.
Important
The default firewall mechanism in the 2.4 and later kernels is
iptables, but iptables cannot be used if ipchains is already running. If ipchains is present at boot time, the kernel issues an error and fails to start iptables.
The functionality of
ipchains is not affected by these errors.
2.8.9.1. Packet Filtering
The Linux kernel uses the Netfilter facility to filter packets, allowing some of them to be received by or pass through the system while stopping others. This facility is built in to the Linux kernel, and has five built-in tables or rules lists, as follows:
filter— The default table for handling network packets.nat— Used to alter packets that create a new connection and used for Network Address Translation (NAT).mangle— Used for specific types of packet alteration.raw— Used mainly for configuring exemptions from connection tracking in combination with the NOTRACK target.security— Used for Mandatory Access Control (MAC) networking rules, such as those enabled by the SECMARK and CONNSECMARK targets.
Each table has a group of built-in chains, which correspond to the actions performed on the packet by
netfilter.
The built-in chains for the
filter table are as follows:
- INPUT — Applies to network packets that are targeted for the host.
- OUTPUT — Applies to locally-generated network packets.
- FORWARD — Applies to network packets routed through the host.
The built-in chains for the
nat table are as follows:
- PREROUTING — Applies to network packets when they arrive.
- OUTPUT — Applies to locally-generated network packets before they are sent out.
- POSTROUTING — Applies to network packets before they are sent out.
The built-in chains for the
mangle table are as follows:
- INPUT — Applies to network packets targeted for the host.
- OUTPUT — Applies to locally-generated network packets before they are sent out.
- FORWARD — Applies to network packets routed through the host.
- PREROUTING — Applies to incoming network packets before they are routed.
- POSTROUTING — Applies to network packets before they are sent out.
The built-in chains for the
raw table are as follows:
- OUTPUT — Applies to locally-generated network packets before they are sent out.
- PREROUTING — Applies to incoming network packets before they are routed.
The built-in chains for the
security table are as follows:
- INPUT — Applies to network packets targeted for the host.
- OUTPUT — Applies to locally-generated network packets before they are sent out.
- FORWARD — Applies to network packets routed through the host.
Every network packet received by or sent from a Linux system is subject to at least one table. However, a packet may be subjected to multiple rules within each table before emerging at the end of the chain. The structure and purpose of these rules may vary, but they usually seek to identify a packet coming from or going to a particular IP address, or set of addresses, when using a particular protocol and network service. The following image outlines how the flow of packets is examined by the
iptables subsystem:
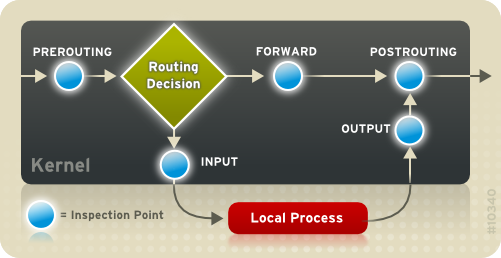
Figure 2.6. Packet filtering in IPTables
Important
By default, firewall rules are saved in the
/etc/sysconfig/iptables or /etc/sysconfig/ip6tables files.
The
iptables service starts before any DNS-related services when a Linux system is booted. This means that firewall rules can only reference numeric IP addresses (for example, 192.168.0.1). Domain names (for example, host.example.com) in such rules produce errors.
Regardless of their destination, when packets match a particular rule in one of the tables, a target or action is applied to them. If the rule specifies an
ACCEPT target for a matching packet, the packet skips the rest of the rule checks and is allowed to continue to its destination. If a rule specifies a DROP target, that packet is refused access to the system and nothing is sent back to the host that sent the packet. If a rule specifies a QUEUE target, the packet is passed to user-space. If a rule specifies the optional REJECT target, the packet is dropped, but an error packet is sent to the packet's originator.
Every chain has a default policy to
ACCEPT, DROP, REJECT, or QUEUE. If none of the rules in the chain apply to the packet, then the packet is dealt with in accordance with the default policy.
The
iptables command configures these tables, as well as sets up new tables if necessary.
Note
The netfilter modules are not loaded by default. Therefore a user will not see all of them by looking in the
/proc/ directory as it only shows what is being used or has been loaded already. This means that there is no way to see what features of netfilter are available before you attempt to use it.