Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
4.13. Multi-Level Security (MLS)
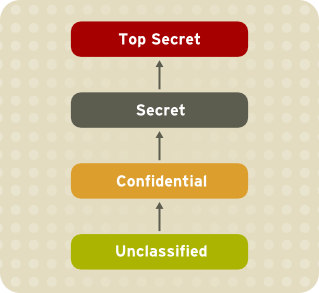
Figure 4.1. Levels of clearance
Figure 4.2. Allowed data flows using MLS
4.13.1. MLS and System Privileges
4.13.2. Enabling MLS in SELinux
Note
Procedure 4.19. Enabling SELinux MLS Policy
- Install the selinux-policy-mls package:
yum install selinux-policy-mls
~]# yum install selinux-policy-mlsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Before the MLS policy is enabled, each file on the file system must be relabeled with an MLS label. When the file system is relabeled, confined domains may be denied access, which may prevent your system from booting correctly. To prevent this from happening, configure
SELINUX=permissivein the/etc/selinux/configfile. Also, enable the MLS policy by configuringSELINUXTYPE=mls. Your configuration file should look like this:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Make sure SELinux is running in permissive mode:
setenforce 0
~]# setenforce 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow getenforce
~]$ getenforce PermissiveCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
fixfilesscript to create the/.autorelabelfile containing the-Foption to ensure that files are relabeled upon next reboot:fixfiles -F onboot
~]# fixfiles -F onbootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot your system. During the next boot, all file systems will be relabeled according to the MLS policy. The label process labels all files with an appropriate SELinux context:
*** Warning -- SELinux mls policy relabel is required. *** Relabeling could take a very long time, depending on file *** system size and speed of hard drives. ***********
*** Warning -- SELinux mls policy relabel is required. *** Relabeling could take a very long time, depending on file *** system size and speed of hard drives. ***********Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each*(asterisk) character on the bottom line represents 1000 files that have been labeled. In the above example, eleven*characters represent 11000 files which have been labeled. The time it takes to label all files depends upon the number of files on the system, and the speed of the hard disk drives. On modern systems, this process can take as little as 10 minutes. Once the labeling process finishes, the system will automatically reboot. - In permissive mode, SELinux policy is not enforced, but denials are still logged for actions that would have been denied if running in enforcing mode. Before changing to enforcing mode, as root, enter the following command to confirm that SELinux did not deny actions during the last boot. If SELinux did not deny actions during the last boot, this command does not return any output. See Chapter 11, Troubleshooting for troubleshooting information if SELinux denied access during boot.
grep "SELinux is preventing" /var/log/messages
~]# grep "SELinux is preventing" /var/log/messagesCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If there were no denial messages in the
/var/log/messagesfile, or you have resolved all existing denials, configureSELINUX=enforcingin the/etc/selinux/configfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot your system and make sure SELinux is running in enforcing mode:
getenforce
~]$ getenforce EnforcingCopy to Clipboard Copied! Toggle word wrap Toggle overflow and the MLS policy is enabled:sestatus |grep mls
~]# sestatus |grep mls Policy from config file: mlsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.13.3. Creating a User With a Specific MLS Range
Procedure 4.20. Creating a User With a Specific MLS Range
- Add a new Linux user using the
useraddcommand and map the new Linux user to an existing SELinux user (in this case,staff_u):useradd -Z staff_u john
~]# useradd -Z staff_u johnCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Assign the newly-created Linux user a password:
prompt~]# passwd john
prompt~]# passwd johnCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter the following command as root to view the mapping between SELinux and Linux users. The output should be as follows:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Define a specific range for user
john:semanage login --modify --range s2:c100 john
~]# semanage login --modify --range s2:c100 johnCopy to Clipboard Copied! Toggle word wrap Toggle overflow - View the mapping between SELinux and Linux users again. Note that the user
johnnow has a specific MLS range defined:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To correct the label on john's home directory if needed, enter the following command:
chcon -R -l s2:c100 /home/john
~]# chcon -R -l s2:c100 /home/johnCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.13.4. Setting Up Polyinstantiated Directories
/tmp and /var/tmp/ directories are normally used for temporary storage by all programs, services, and users. Such setup, however, makes these directories vulnerable to race condition attacks, or an information leak based on file names. SELinux offers a solution in the form of polyinstantiated directories. This effectively means that both /tmp and /var/tmp/ are instantiated, making them appear private for each user. When instantiation of directories is enabled, each user's /tmp and /var/tmp/ directory is automatically mounted under /tmp-inst and /var/tmp/tmp-inst.
Procedure 4.21. Enabling Polyinstantiation Directories
- Uncomment the last three lines in the
/etc/security/namespace.conffile to enable instantiation of the/tmp,/var/tmp/, and users' home directories:tail -n 3 /etc/security/namespace.conf
~]$ tail -n 3 /etc/security/namespace.conf /tmp /tmp-inst/ level root,adm /var/tmp /var/tmp/tmp-inst/ level root,adm $HOME $HOME/$USER.inst/ levelCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Ensure that in the
/etc/pam.d/loginfile, thepam_namespace.somodule is configured for session:grep namespace /etc/pam.d/login
~]$ grep namespace /etc/pam.d/login session required pam_namespace.soCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot your system.