Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 7. Setting up a WireGuard VPN
WireGuard is a high-performance VPN that runs in the Linux kernel. It uses modern cryptography and is easier to configure than many other VPN solutions. Its small codebase improves security and, for authentication and encryption, it uses keys similar to SSH.
WireGuard is provided as a Technology Preview only. Technology Preview features are not supported with Red Hat production Service Level Agreements (SLAs), might not be functionally complete, and Red Hat does not recommend using them for production. These previews provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
See Technology Preview Features Support Scope on the Red Hat Customer Portal for information about the support scope for Technology Preview features.
Note that all hosts that participate in a WireGuard VPN are peers. This documentation uses the terms client to describe hosts that establish a connection and server to describe the host with the fixed hostname or IP address that the clients connect to and, optionally, route all traffic through this server.
To set up a WireGuard VPN, you must complete the following steps:
- Configure the server.
- Open the WireGuard port in the local firewall.
- Configure the clients.
WireGuard operates on the network layer (layer 3). Therefore, you cannot use DHCP and must assign static IP addresses or IPv6 global addresses to the tunnel devices on both the server and clients.
You can use WireGuard only if the Federal Information Processing Standard (FIPS) mode in RHEL is disabled.
7.1. Protocols and primitives used by WireGuard
Understanding the protocols and primitives used by WireGuard is important for evaluating its security and trustworthiness. Knowing these components enables a user to verify that the system uses modern and secure cryptographic standards.
WireGuard uses the following protocols and primitives:
- ChaCha20 for symmetric encryption, authenticated with Poly1305, using Authenticated Encryption with Associated Data (AEAD) construction
- Curve25519 for Elliptic-curve Diffie-Hellman (ECDH) key exchange
- BLAKE2s for hashing and keyed hashing
- SipHash24 for hash table keys
- HKDF for key derivation
7.2. How WireGuard uses tunnel IP addresses, public keys, and remote endpoints
WireGuard’s design tightly couples network routing with cryptographic identity. With this design, the protocol functions as both a routing mechanism for outgoing traffic and an access control list for incoming packets, ensuring that only authenticated and authorized traffic is processed.
When WireGuard sends a network packet to a peer:
- WireGuard reads the destination IP from the packet and compares it to the list of allowed IP addresses in the local configuration. If the peer is not found, WireGuard drops the packet.
- If the peer is valid, WireGuard encrypts the packet using the peer’s public key.
- The sending host looks up the most recent Internet IP address of the host and sends the encrypted packet to it.
When WireGuard receives a packet:
- WireGuard decrypts the packet using the private key of the remote host.
- WireGuard reads the internal source address from the packet and looks up whether the IP is configured in the list of allowed IP addresses in the settings for the peer on the local host. If the source IP is on the allowlist, WireGuard accepts the packet. If the IP address is not on the list, WireGuard drops the packet.
7.3. Using a WireGuard client behind NAT and firewalls
WireGuard uses the UDP protocol and transmits data only when a peer sends packets. Stateful firewalls and network address translation (NAT) on routers track connections to enable a peer behind NAT or a firewall to receive packets.
To keep the connection active, WireGuard supports persistent keepalives. This means you can set an interval at which WireGuard sends keepalive packets. By default, the persistent keep-alive feature is disabled to reduce network traffic. Enable this feature on the client if you use the client in a network with NAT or if a firewall closes the connection after some time of inactivity.
Note that you cannot configure keepalive packets in WireGuard connections by using the RHEL web console. To configure this feature, edit the connection profile by using the nmcli utility.
7.4. Creating private and public keys to be used in WireGuard connections
WireGuard uses base64-encoded private and public keys to authenticate hosts to each other. Therefore, you must create the keys on each host that participates in the WireGuard VPN.
For secure connections, create different keys for each host, and ensure that you only share the public key with the remote WireGuard host. Do not use the example keys used in this documentation.
If you plan to use the RHEL web console to create a WireGuard VPN connection, you can, alternatively, generate the public and private key pairs in the web console.
Procedure
Install the
wireguard-toolspackage:dnf install wireguard-tools
# dnf install wireguard-toolsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a private key and a corresponding public key for the host:
wg genkey | tee /etc/wireguard/$HOSTNAME.private.key | wg pubkey > /etc/wireguard/$HOSTNAME.public.key
# wg genkey | tee /etc/wireguard/$HOSTNAME.private.key | wg pubkey > /etc/wireguard/$HOSTNAME.public.keyCopy to Clipboard Copied! Toggle word wrap Toggle overflow You will need the content of the key files, but not the files themselves. However, Red Hat recommends keeping the files in case that you need to remember the keys in future.
Set secure permissions on the key files:
chmod 600 /etc/wireguard/$HOSTNAME.private.key /etc/wireguard/$HOSTNAME.public.key
# chmod 600 /etc/wireguard/$HOSTNAME.private.key /etc/wireguard/$HOSTNAME.public.keyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the private key:
cat /etc/wireguard/$HOSTNAME.private.key YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg=
# cat /etc/wireguard/$HOSTNAME.private.key YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg=Copy to Clipboard Copied! Toggle word wrap Toggle overflow You will need the private key to configure the WireGuard connection on the local host. Do not share the private key.
Display the public key:
cat /etc/wireguard/$HOSTNAME.public.key UtjqCJ57DeAscYKRfp7cFGiQqdONRn69u249Fa4O6BE=
# cat /etc/wireguard/$HOSTNAME.public.key UtjqCJ57DeAscYKRfp7cFGiQqdONRn69u249Fa4O6BE=Copy to Clipboard Copied! Toggle word wrap Toggle overflow You will need the public key to configure the WireGuard connection on the remote host.
7.5. Configuring a WireGuard server by using nmcli
You can configure the WireGuard server by creating a connection profile in NetworkManager. Use this method to let NetworkManager manage the WireGuard connection.
This procedure assumes the following settings:
Server:
-
Private key:
YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg= -
Tunnel IPv4 address:
192.0.2.1/24 -
Tunnel IPv6 address:
2001:db8:1::1/64
-
Private key:
Client:
-
Public key:
bnwfQcC8/g2i4vvEqcRUM2e6Hi3Nskk6G9t4r26nFVM= -
Tunnel IPv4 address:
192.0.2.2/24 -
Tunnel IPv6 address:
2001:db8:1::2/64
-
Public key:
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the server
- The static tunnel IP addresses and subnet masks of the client
- The public key of the client
- The static tunnel IP addresses and subnet masks of the server
Procedure
Add a NetworkManager WireGuard connection profile:
nmcli connection add type wireguard con-name server-wg0 ifname wg0 autoconnect no
# nmcli connection add type wireguard con-name server-wg0 ifname wg0 autoconnect noCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates a profile named
server-wg0and assigns the virtual interfacewg0to it. To prevent the connection from starting automatically after you add it without finalizing the configuration, disable theautoconnectparameter.Set the tunnel IPv4 address and subnet mask of the server:
nmcli connection modify server-wg0 ipv4.method manual ipv4.addresses 192.0.2.1/24
# nmcli connection modify server-wg0 ipv4.method manual ipv4.addresses 192.0.2.1/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the tunnel IPv6 address and subnet mask of the server:
nmcli connection modify server-wg0 ipv6.method manual ipv6.addresses 2001:db8:1::1/64
# nmcli connection modify server-wg0 ipv6.method manual ipv6.addresses 2001:db8:1::1/64Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the server’s private key to the connection profile:
nmcli connection modify server-wg0 wireguard.private-key "YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg="
# nmcli connection modify server-wg0 wireguard.private-key "YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg="Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the port for incoming WireGuard connections:
nmcli connection modify server-wg0 wireguard.listen-port 51820
# nmcli connection modify server-wg0 wireguard.listen-port 51820Copy to Clipboard Copied! Toggle word wrap Toggle overflow Always set a fixed port number on hosts that receive incoming WireGuard connections. If you do not set a port, WireGuard uses a random free port each time you activate the
wg0interface.Add peer connection configurations for each client that you want to allow to communicate with this server:
nmcli connection modify client-wg0 wireguard.peers 'bnwfQcC8/g2i4vvEqcRUM2e6Hi3Nskk6G9t4r26nFVM= allowed-ips=192.0.2.2;2001:db8:1::2'
nmcli connection modify client-wg0 wireguard.peers 'bnwfQcC8/g2i4vvEqcRUM2e6Hi3Nskk6G9t4r26nFVM= allowed-ips=192.0.2.2;2001:db8:1::2'Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
wireguard.peersparameter defines the peer section of the client in the NetworkManager connection profile.Optional: Configure the connection to start automatically, enter:
nmcli connection modify server-wg0 autoconnect yes
# nmcli connection modify server-wg0 autoconnect yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reactivate the
server-wg0connection:nmcli connection up server-wg0
# nmcli connection up server-wg0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.6. Configuring a WireGuard server by using nmtui
You can configure the WireGuard server by creating a connection profile in NetworkManager. Use this method to let NetworkManager manage the WireGuard connection.
This procedure assumes the following settings:
Server:
-
Private key:
YFAnE0psgIdiAF7XR4abxiwVRnlMfeltxu10s/c4JXg= -
Tunnel IPv4 address:
192.0.2.1/24 -
Tunnel IPv6 address:
2001:db8:1::1/64
-
Private key:
Client:
-
Public key:
bnwfQcC8/g2i4vvEqcRUM2e6Hi3Nskk6G9t4r26nFVM= -
Tunnel IPv4 address:
192.0.2.2/24 -
Tunnel IPv6 address:
2001:db8:1::2/64
-
Public key:
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the server
- The static tunnel IP addresses and subnet masks of the client
- The public key of the client
- The static tunnel IP addresses and subnet masks of the server
-
You installed the
NetworkManager-tuipackage.
Procedure
Start the
nmtuiapplication:nmtui
# nmtuiCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Select Edit a connection, and press Enter.
- Select , and press Enter.
- Select the WireGuard connection type in the list, and press Enter.
In the Edit connection window:
-
Enter the name of the connection and the virtual interface, such as
wg0, that NetworkManager should assign to the connection. - Enter the private key of the server.
Set the listen port number, such as
51820, for incoming WireGuard connections.Always set a fixed port number on hosts that receive incoming WireGuard connections. If you do not set a port, WireGuard uses a random free port each time you activate the interface.
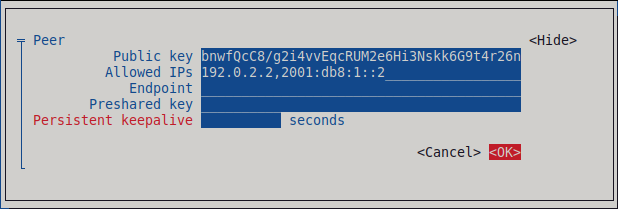
Click next to the Peers pane:
- Enter the public key of the client.
- Set the Allowed IPs field to the tunnel IP addresses of the client that are allowed to send data to this server.
Select , and press Enter.
Select next to *IPv4 Configuration, and press Enter.
- Select the IPv4 configuration method Manual.
- Enter the tunnel IPv4 address and the subnet mask. Leave the Gateway field empty.
Select next to IPv6 Configuration, and press Enter.
- Select the IPv6 configuration method Manual.
-
Enter the tunnel IPv6 address and the subnet mask. Leave the
Gatewayfield empty.
Select , and press Enter
-
Enter the name of the connection and the virtual interface, such as
- In the window with the list of connections, select , and press Enter.
- In the NetworkManager TUI main window, select , and press Enter.
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.7. Configuring a WireGuard server by using the RHEL web console
You can configure a WireGuard server by using the browser-based RHEL web console. Use this method to let NetworkManager manage the WireGuard connection.
Prerequisites
- You are logged in to the RHEL web console.
You know the following information:
- The static tunnel IP addresses and subnet masks of both the server and client
- The public key of the client
Procedure
- Select the Networking tab in the navigation on the left side of the screen.
- Click Add VPN in the Interfaces section.
-
If the
wireguard-toolsandsystemd-resolvedpackages are not already installed, the web console displays a corresponding notification. Click Install to install these packages. - Enter the name of the WireGuard device that you want to create.
Configure the key pair of this host:
If you want use the keys that the web console has created:
- Keep the pre-selected Generated option in the Private key area.
- Note the Public key value. You require this information when you configure the client.
If you want to use an existing private key:
- Select Paste existing key in the Private key area.
- Paste the private key into the text field. The web console automatically calculates the corresponding public key.
Set a listen port number, such as
51820, for incoming WireGuard connections.Always set a fixed port number on hosts that receive incoming WireGuard connections. If you do not set a port, WireGuard uses a random free port each time you activate the interface.
Set the tunnel IPv4 address and subnet mask of the server.
To also set an IPv6 address, you must edit the connection after you have created it.
Add peer configurations for each client that you want to allow to communicate with this server:
- Click Add peer.
- Enter the public key of the client.
- Leave the Endpoint field empty.
- Set the Allowed IPs field to the tunnel IP addresses of the clients that are allowed to send data to this server.
- Click Add to create the WireGuard connection.
If you want to also set a tunnel IPv6 address:
- Click on the WireGuard connection’s name in the Interfaces section.
- Click edit next to IPv6.
-
Set the Addresses field to
Manual, and enter the tunnel IPv6 address and prefix of the server. - Click Save.
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.8. Configuring firewalld on a WireGuard server by using the command line
Configure the firewalld service on the WireGuard server, allowing incoming connections from clients. If clients need to use the server as their default gateway and route all traffic through the tunnel, enable also masquerading.
Procedure
Open the WireGuard port for incoming connections in the
firewalldservice:firewall-cmd --permanent --add-port=51820/udp --zone=public
# firewall-cmd --permanent --add-port=51820/udp --zone=publicCopy to Clipboard Copied! Toggle word wrap Toggle overflow If clients should route all traffic through the tunnel and use the WireGuard server as the default gateway, enable masquerading for the
publiczone:firewall-cmd --permanent --zone=public --add-masquerade
# firewall-cmd --permanent --zone=public --add-masqueradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reload the
firewalldrules.firewall-cmd --reload
# firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the configuration of the
publiczone:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.9. Configuring firewalld on a WireGuard server by using the RHEL web console
Configure the firewalld service on the WireGuard server, allowing incoming connections from clients. If clients need to use the server as their default gateway and route all traffic through the tunnel, enable also masquerading.
Prerequisites
- You are logged in to the RHEL web console.
Procedure
- Select the Networking tab in the navigation on the left side of the screen.
- Click Edit rules and zones in the Firewall section.
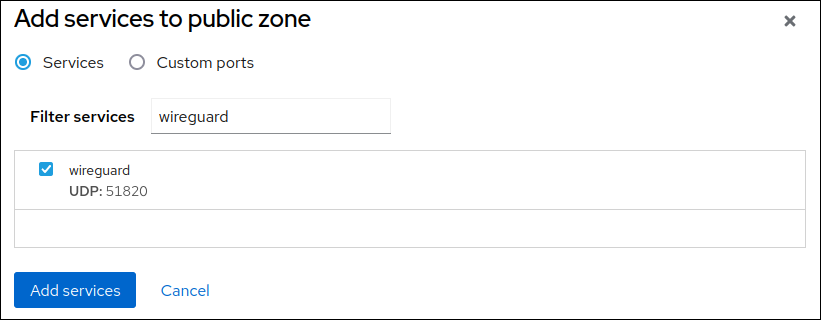
- Click Add services.
-
Enter
wireguardinto the Filter services field. Select the
wireguardentry from the list.- Click Add services.
If clients should route all traffic through the tunnel and use the WireGuard server as the default gateway, enable masquerading for the
publiczone:firewall-cmd --permanent --zone=public --add-masquerade firewall-cmd --reload
# firewall-cmd --permanent --zone=public --add-masquerade # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that you cannot enable masquerading in
firewalldzones in the web console.
Verification
- Select the Networking tab in the navigation on the left side of the screen.
- Click Edit rules and zones in the Firewall section.
-
The list contains an entry for the
wireguardservice and displays the UDP port that you configured in the WireGuard connection profile. To verify that masquerading is enabled in the
publiczone offirewalld, enter:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.10. Configuring a WireGuard client by using nmcli
You can configure a WireGuard client by creating a connection profile in NetworkManager. Use this method to let NetworkManager manage the WireGuard connection.
This procedure assumes the following settings:
Client:
-
Private key:
aPUcp5vHz8yMLrzk8SsDyYnV33IhE/k20e52iKJFV0A= -
Tunnel IPv4 address:
192.0.2.2/24 -
Tunnel IPv6 address:
2001:db8:1::2/64
-
Private key:
Server:
-
Public key:
UtjqCJ57DeAscYKRfp7cFGiQqdONRn69u249Fa4O6BE= -
Tunnel IPv4 address:
192.0.2.1/24 -
Tunnel IPv6 address:
2001:db8:1::1/64
-
Public key:
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the client
- The static tunnel IP addresses and subnet masks of the client
- The public key of the server
- The static tunnel IP addresses and subnet masks of the server
Procedure
Add a NetworkManager WireGuard connection profile:
nmcli connection add type wireguard con-name client-wg0 ifname wg0
# nmcli connection add type wireguard con-name client-wg0 ifname wg0Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command creates a profile named
client-wg0and assigns the virtual interfacewg0to it.Optional: Configure NetworkManager so that it does not automatically start the
client-wgconnection:nmcli connection modify client-wg0 autoconnect no
# nmcli connection modify client-wg0 autoconnect noCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the tunnel IPv4 address and subnet mask of the client:
nmcli connection modify client-wg0 ipv4.method manual ipv4.addresses 192.0.2.2/24
# nmcli connection modify client-wg0 ipv4.method manual ipv4.addresses 192.0.2.2/24Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the tunnel IPv6 address and subnet mask of the client:
nmcli connection modify client-wg0 ipv6.method manual ipv6.addresses 2001:db8:1::2/64
# nmcli connection modify client-wg0 ipv6.method manual ipv6.addresses 2001:db8:1::2/64Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you want to route all traffic through the tunnel, set the tunnel IP addresses of the server as the default gateway:
nmcli connection modify client-wg0 ipv4.gateway 192.0.2.1 ipv6.gateway 2001:db8:1::1
# nmcli connection modify client-wg0 ipv4.gateway 192.0.2.1 ipv6.gateway 2001:db8:1::1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Routing all traffic through the tunnel requires that you set, in a later step, the
allowed-ipson this client to0.0.0.0/0;::/0.Note that routing all traffic through the tunnel can impact the connectivity to other hosts based on the server routing and firewall configuration.
Add the client’s private key to the connection profile:
nmcli connection modify client-wg0 wireguard.private-key "aPUcp5vHz8yMLrzk8SsDyYnV33IhE/k20e52iKJFV0A="
# nmcli connection modify client-wg0 wireguard.private-key "aPUcp5vHz8yMLrzk8SsDyYnV33IhE/k20e52iKJFV0A="Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add peer connection configurations for each server that you want to allow to communicate with this client:
nmcli connection modify client-wg0 wireguard.peers 'kEyMNyYhpmn9zPQ4m7iGmU9G7nooS9eeUBe0Y0wO0gM= endpoint=server.example.com:51820 allowed-ips=0.0.0.0/0 ;::/0'
# nmcli connection modify client-wg0 wireguard.peers 'kEyMNyYhpmn9zPQ4m7iGmU9G7nooS9eeUBe0Y0wO0gM= endpoint=server.example.com:51820 allowed-ips=0.0.0.0/0 ;::/0'Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
wireguard.peersparameter defines the peer section of the client in the NetworkManager connection profile. Use0.0.0.0/0;::/0;inallowed-ipsto allow any remote IPv4 and IPv6 address to communicate with this client. Use this setting to route all traffic through the tunnel and use the WireGuard server as default gateway.Reactivate the
client-wg0connection:nmcli connection up client-wg0
# nmcli connection up client-wg0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Ping the IP addresses of the server:
ping 192.0.2.1 ping6 2001:db8:1::1
# ping 192.0.2.1 # ping6 2001:db8:1::1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Note that the output has only the
latest handshakeandtransferentries if you have already sent traffic through the VPN tunnel.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.11. Configuring a WireGuard client by using nmtui
You can configure a WireGuard client by creating a connection profile in NetworkManager. Use this method to let NetworkManager manage the WireGuard connection.
This procedure assumes the following settings:
Client:
-
Private key:
aPUcp5vHz8yMLrzk8SsDyYnV33IhE/k20e52iKJFV0A= -
Tunnel IPv4 address:
192.0.2.2/24 -
Tunnel IPv6 address:
2001:db8:1::2/64
-
Private key:
Server:
-
Public key:
UtjqCJ57DeAscYKRfp7cFGiQqdONRn69u249Fa4O6BE= -
Tunnel IPv4 address:
192.0.2.1/24 -
Tunnel IPv6 address:
2001:db8:1::1/64
-
Public key:
Prerequisites
- You have generated the public and private key for both the server and client.
You know the following information:
- The private key of the client
- The static tunnel IP addresses and subnet masks of the client
- The public key of the server
- The static tunnel IP addresses and subnet masks of the server
-
You installed the
NetworkManager-tuipackage
Procedure
Start the
nmtuiapplication:nmtui
# nmtuiCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Select Edit a connection, and press Enter.
- Select , and press Enter.
- Select the WireGuard connection type in the list, and press Enter.
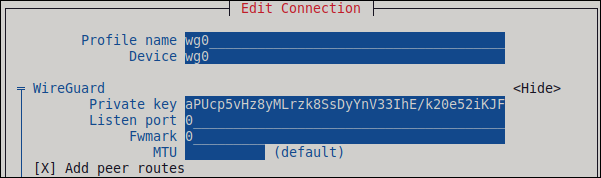
In the Edit connection window:
-
Enter the name of the connection and the virtual interface, such as
wg0, that NetworkManager should assign to the connection. Enter the private key of the client.
Click next to the Peers pane:
- Enter the public key of the server.
Set the Allowed IPs field. For example, set it to:
- The tunnel IP addresses of the server to allow only the server to communicate with this client.
-
0.0.0.0/0,::/0to allow any remote IPv4 and IPv6 address to communicate with this client. Use this setting to route all traffic through the tunnel and use the WireGuard server as default gateway.
-
Enter the host name or IP address and port of the WireGuard server into the Endpoint field. Use the following format:
<hostname_or_IP>:<port_number> - Optional: If you use the client in a network with network address translation (NAT) or if a firewall closes the UDP connection after some time of inactivity, set a persistent keepalive interval in seconds. In this interval, the client sends a keepalive packet to the server.
Select , and press Enter.
Select next to IPv4 Configuration, and press Enter.
- Select the IPv4 configuration method Manual.
- Enter the tunnel IPv4 address and the subnet mask. Leave the Gateway field empty.
Select next to IPv6 Configuration, and press Enter.
- Select the IPv6 configuration method Manual.
- Enter the tunnel IPv6 address and the subnet mask. Leave the Gateway field empty.
- Optional: Select Automatically connect.
Select , and press Enter
-
Enter the name of the connection and the virtual interface, such as
- In the window with the list of connections, select , and press Enter.
- In the NetworkManager TUI main window, select , and press Enter.
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Ping the IP addresses of the server:
ping 192.0.2.1 ping6 2001:db8:1::1
# ping 192.0.2.1 # ping6 2001:db8:1::1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Note that the output contains only the
latest handshakeandtransferentries if you have already sent traffic through the VPN tunnel.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.12. Configuring a WireGuard client by using the RHEL web console
You can configure a WireGuard client by using the browser-based RHEL web console. Use this method to let NetworkManager manage the WireGuard connection.
Prerequisites
- You are logged in to the RHEL web console.
You know the following information:
- The static tunnel IP addresses and subnet masks of both the server and client
- The public key of the server
Procedure
- Select the Networking tab in the navigation on the left side of the screen.
- Click Add VPN in the Interfaces section.
-
If the
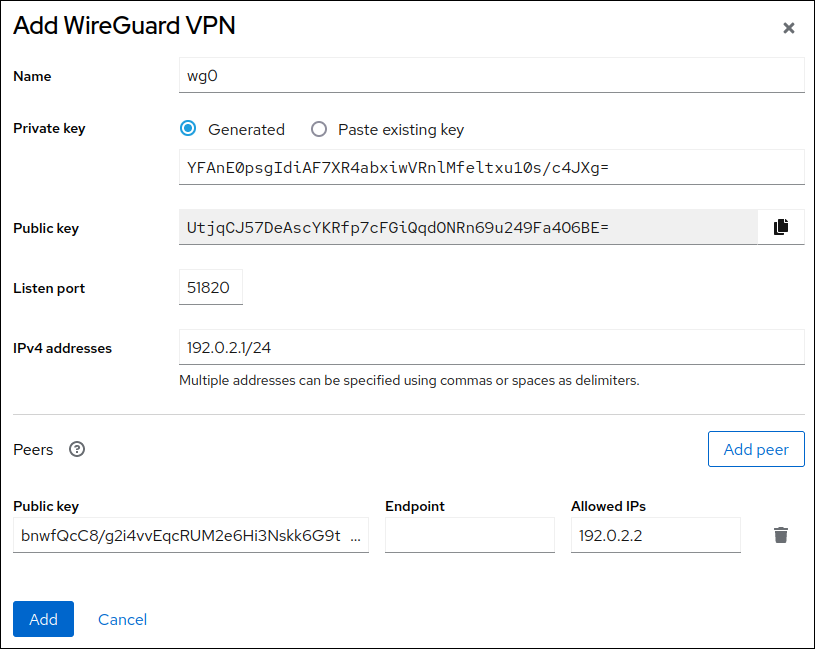
wireguard-toolsandsystemd-resolvedpackages are not already installed, the web console displays a corresponding notification. Click Install to install these packages. - Enter the name of the WireGuard device that you want to create.
Configure the key pair of this host:
If you want use the keys that the web console has created:
- Keep the pre-selected Generated option in the Private key area.
- Note the Public key value. You require this information when you configure the client.
If you want to use an existing private key:
- Select Paste existing key in the Private key area.
- Paste the private key into the text field. The web console automatically calculates the corresponding public key.
-
Preserve the
0value in the Listen port field. Set the tunnel IPv4 address and subnet mask of the client.
To also set an IPv6 address, you must edit the connection after you have created it.
Add a peer configuration for the server that you want to allow to communicate with this client:
- Click Add peer.
- Enter the public key of the server.
-
Set the Endpoint field to the hostname or IP address and the port of the server, for example
server.example.com:51820. The client uses this information to establish the connection. Set the Allowed IPs field to the tunnel IP addresses of the clients that are allowed to send data to this server. For example, set the field to one of the following:
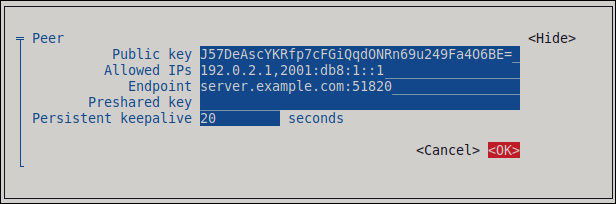
- The tunnel IP addresses of the server to allow only the server to communicate with this client. The value in the screen capture below configures this scenario.
-
0.0.0.0/0to allow any remote IPv4 address to communicate with this client. Use this setting to route all traffic through the tunnel and use the WireGuard server as default gateway.
- Click Add to create the WireGuard connection.
If you want to also set a tunnel IPv6 address:
- Click on the WireGuard connection’s name in the Interfaces section.
- Click Edit next to IPv6.
-
Set the Addresses field to
Manual, and enter the tunnel IPv6 address and prefix of the client. - Click Save.
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Ping the IP addresses of the server:
ping 192.0.2.1
# ping 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow WireGuard establishes the connection when you try to send traffic through the tunnel.
Display the interface configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To display the private key in the output, use the
WG_HIDE_KEYS=never wg show wg0command.Note that the output has only the
latest handshakeandtransferentries if you have already sent traffic through the VPN tunnel.Display the IP configuration of the
wg0device:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.13. Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel
To protect your VPN connection from traffic redirection attacks, assign it to a dedicated routing table. This prevents malicious network servers from bypassing the secure tunnel and compromising data integrity.
Both a DHCP server and Stateless Address Autoconfiguration (SLAAC) can add routes to a client’s routing table. For example, a malicious DHCP server can use this feature to force a host with VPN connection to redirect traffic through a physical interface instead of the VPN tunnel. This vulnerability is also known as TunnelVision and described in the CVE-2024-3661 vulnerability article.
To mitigate this vulnerability, you can assign the VPN connection to a dedicated routing table. This prevents the DHCP configuration or SLAAC from manipulating routing decisions for network packets intended for the VPN tunnel.
Follow the steps if at least one of the conditions applies to your environment:
- At least one network interface uses DHCP or SLAAC.
- Your network does not use mechanisms, such as DHCP snooping, that prevent a rogue DHCP server.
Routing the entire traffic through the VPN prevents the host from accessing local network resources.
Procedure
- Decide which routing table you want to use. The following steps use table 75. By default, RHEL does not use the tables 1-254, and you can use any of them.
Configure the VPN connection profile to place the VPN routes in a dedicated routing table:
nmcli connection modify <vpn_connection_profile> ipv4.route-table 75 ipv6.route-table 75
# nmcli connection modify <vpn_connection_profile> ipv4.route-table 75 ipv6.route-table 75Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set a low priority value for the table you used in the previous command:
nmcli connection modify <vpn_connection_profile> ipv4.routing-rules "priority 32345 from all table 75" ipv6.routing-rules "priority 32345 from all table 75"
# nmcli connection modify <vpn_connection_profile> ipv4.routing-rules "priority 32345 from all table 75" ipv6.routing-rules "priority 32345 from all table 75"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The priority value can be any value between 1 and 32766. The lower the value, the higher the priority.
Reconnect the VPN connection:
nmcli connection down <vpn_connection_profile> nmcli connection up <vpn_connection_profile>
# nmcli connection down <vpn_connection_profile> # nmcli connection up <vpn_connection_profile>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 routes in table 75:
ip route show table 75 ... 192.0.2.0/24 via 192.0.2.254 dev vpn_device proto static metric 50 default dev vpn_device proto static scope link metric 50
# ip route show table 75 ... 192.0.2.0/24 via 192.0.2.254 dev vpn_device proto static metric 50 default dev vpn_device proto static scope link metric 50Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that both the route to the remote network and the default gateway are assigned to routing table 75 and, therefore, all traffic is routed through the tunnel. If you set
ipv4.never-default truein the VPN connection profile, a default route is not created and, therefore, not visible in this output.Display the IPv6 routes in table 75:
ip -6 route show table 75 ... 2001:db8:1::/64 dev vpn_device proto kernel metric 50 pref medium default dev vpn_device proto static metric 50 pref medium
# ip -6 route show table 75 ... 2001:db8:1::/64 dev vpn_device proto kernel metric 50 pref medium default dev vpn_device proto static metric 50 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that both the route to the remote network and the default gateway are assigned to routing table 75 and, therefore, all traffic is routed through the tunnel. If you set
ipv6.never-default truein the VPN connection profile, a default route is not created and, therefore, not visible in this output.