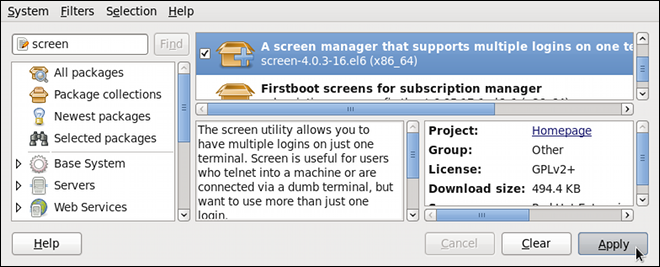
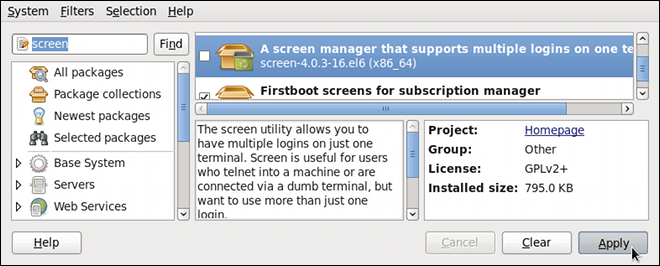
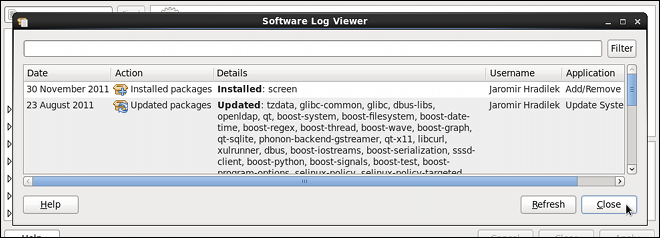
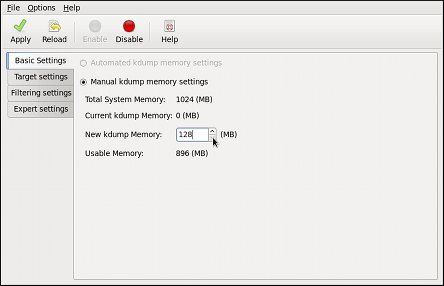
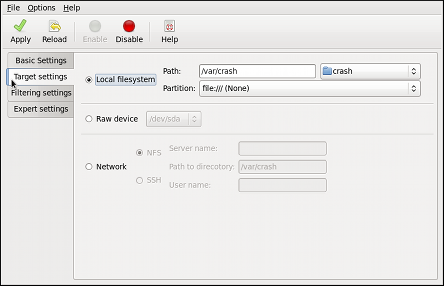
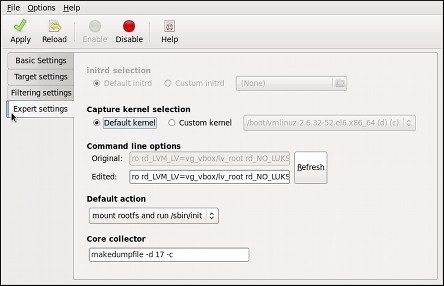
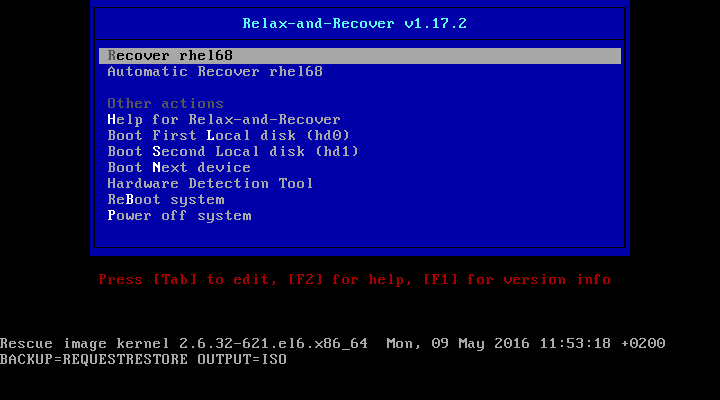
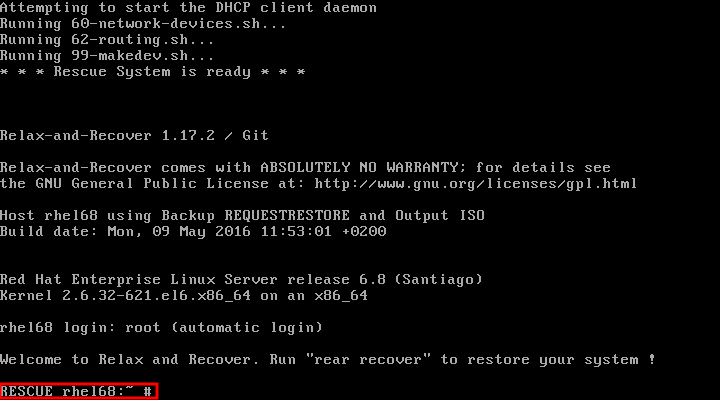
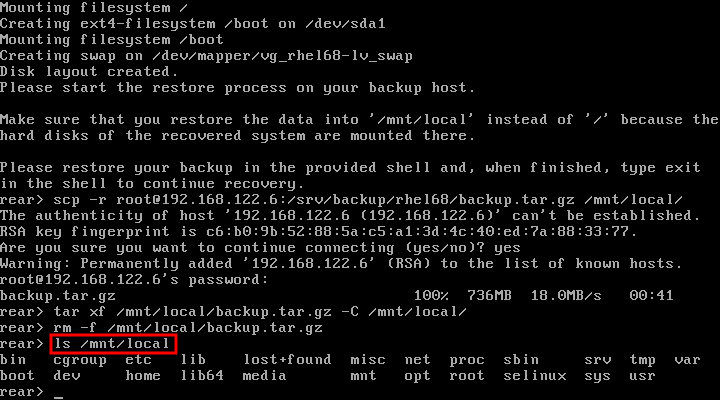
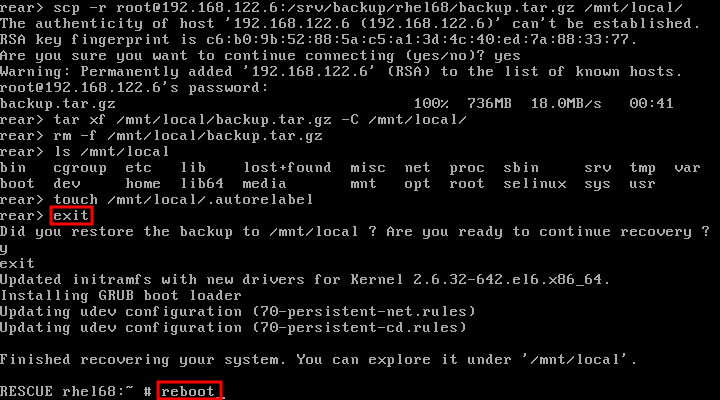
Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Deployment Guide
Deployment, Configuration and Administration of Red Hat Enterprise Linux 6
Abstract
Part I. Basic System Configuration
Chapter 1. Keyboard Configuration
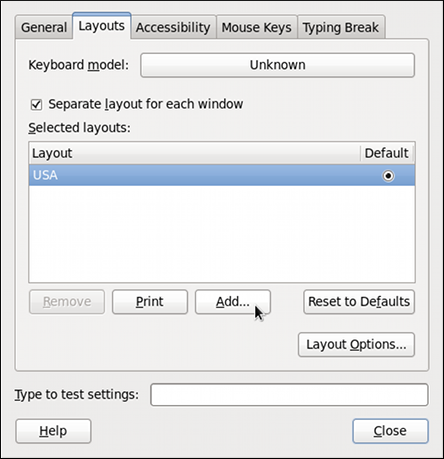
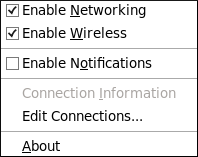
1.1. Changing the Keyboard Layout
Figure 1.1. Keyboard Layout Preferences
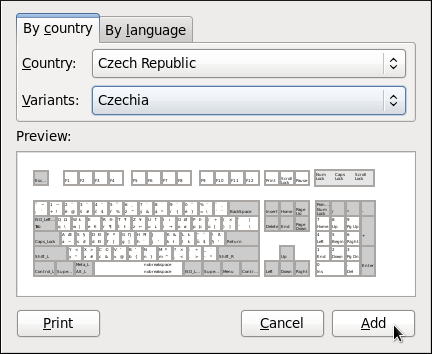
Figure 1.2. Choosing a layout
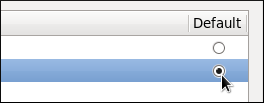
Figure 1.3. Selecting the default layout
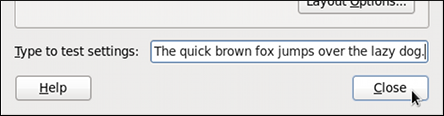
Figure 1.4. Testing the layout
Note
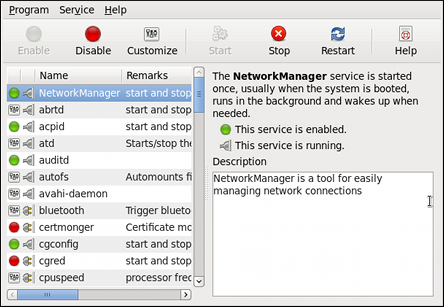
1.2. Adding the Keyboard Layout Indicator
Figure 1.5. Adding a new applet
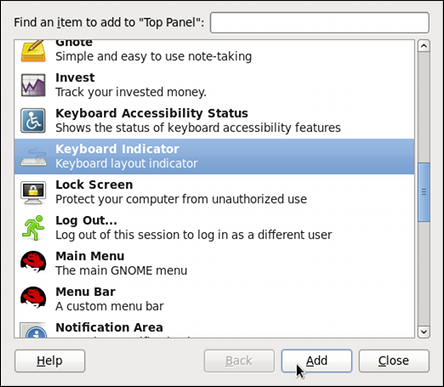
Figure 1.6. Selecting the Keyboard Indicator
Figure 1.7. The Keyboard Indicator applet
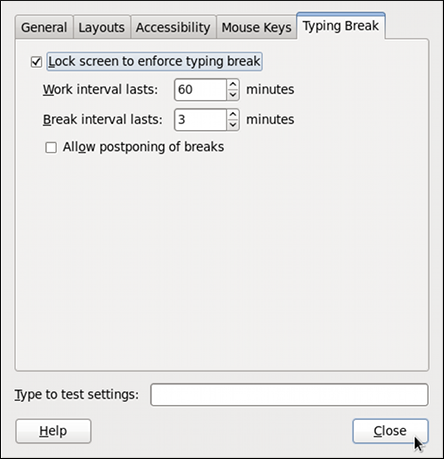
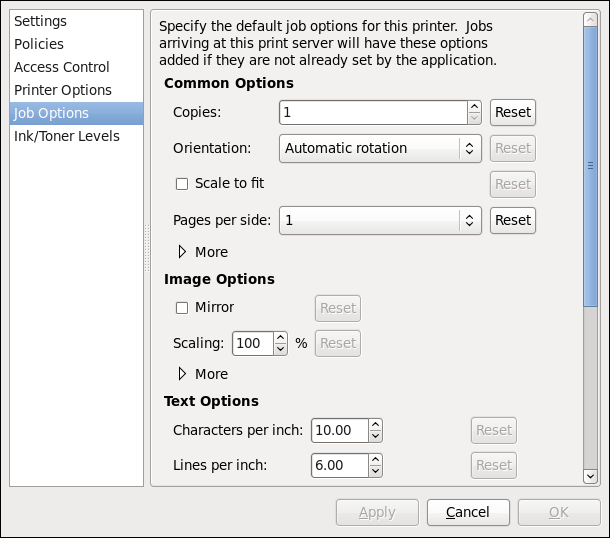
1.3. Setting Up a Typing Break
Figure 1.8. Typing Break Properties
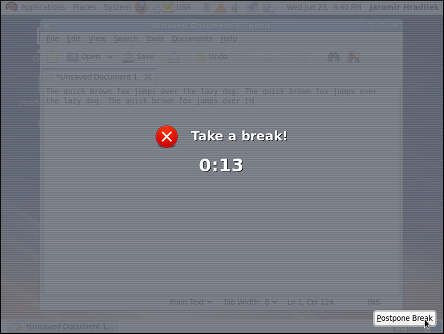
Figure 1.9. Taking a break
Chapter 2. Date and Time Configuration
2.1. Date/Time Properties Tool
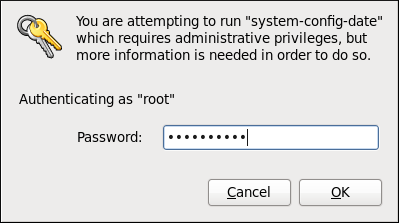
system-config-date command at a shell prompt (e.g., xterm or GNOME Terminal). Unless you are already authenticated, you will be prompted to enter the superuser password.
Figure 2.1. Authentication Query
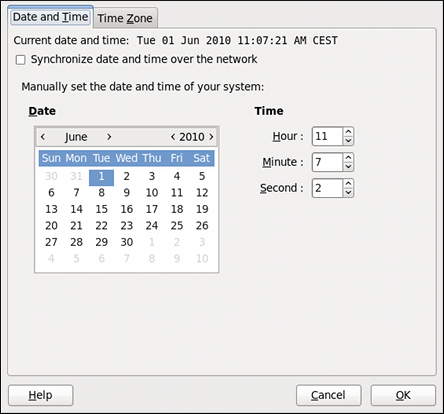
2.1.1. Date and Time Properties
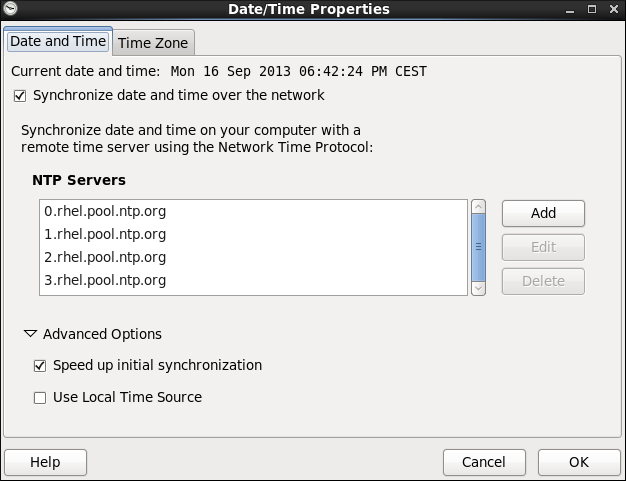
Figure 2.2. Date and Time Properties
- Change the current date. Use the arrows to the left and right of the month and year to change the month and year respectively. Then click inside the calendar to select the day of the month.
- Change the current time. Use the up and down arrow buttons beside the Hour, Minute, and Second, or replace the values directly.
2.1.2. Network Time Protocol Properties
Figure 2.3. Network Time Protocol Properties
Note
2.1.3. Time Zone Properties
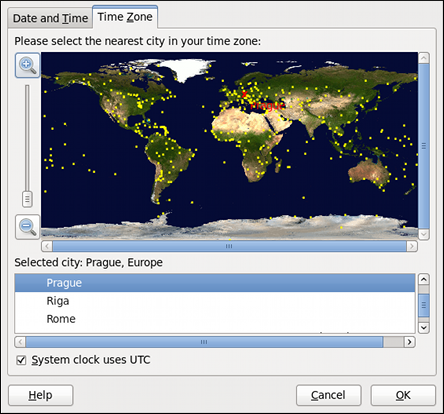
Figure 2.4. Time Zone Properties
- Using the interactive map. Click “zoom in” and “zoom out” buttons next to the map, or click on the map itself to zoom into the selected region. Then choose the city specific to your time zone. A red X appears and the time zone selection changes in the list below the map.
- Use the list below the map. To make the selection easier, cities and countries are grouped within their specific continents. Note that non-geographic time zones have also been added to address needs in the scientific community.
2.2. Command Line Configuration
su - Password:
~]$ su -
Password:2.2.1. Date and Time Setup
date command allows the superuser to set the system date and time manually:
- Change the current date. Type the command in the following form at a shell prompt, replacing the YYYY with a four-digit year, MM with a two-digit month, and DD with a two-digit day of the month:
date +%D -s YYYY-MM-DD
~]# date +%D -s YYYY-MM-DDCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example, to set the date to 2 June 2010, type:date +%D -s 2010-06-02
~]# date +%D -s 2010-06-02Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Change the current time. Use the following command, where HH stands for an hour, MM is a minute, and SS is a second, all typed in a two-digit form:
date +%T -s HH:MM:SS
~]# date +%T -s HH:MM:SSCopy to Clipboard Copied! Toggle word wrap Toggle overflow If your system clock is set to use UTC (Coordinated Universal Time), add the following option:date +%T -s HH:MM:SS -u
~]# date +%T -s HH:MM:SS -uCopy to Clipboard Copied! Toggle word wrap Toggle overflow For instance, to set the system clock to 11:26 PM using the UTC, type:date +%T -s 23:26:00 -u
~]# date +%T -s 23:26:00 -uCopy to Clipboard Copied! Toggle word wrap Toggle overflow
date without any additional argument:
Example 2.1. Displaying the current date and time
date Wed Jun 2 11:58:48 CEST 2010
~]$ date
Wed Jun 2 11:58:48 CEST 20102.2.2. Network Time Protocol Setup
- Firstly, check whether the selected NTP server is accessible:
ntpdate -q server_address
~]# ntpdate -q server_addressCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:ntpdate -q 0.rhel.pool.ntp.org
~]# ntpdate -q 0.rhel.pool.ntp.orgCopy to Clipboard Copied! Toggle word wrap Toggle overflow - When you find a satisfactory server, run the ntpdate command followed by one or more server addresses:
ntpdate server_address...
~]# ntpdate server_address...Copy to Clipboard Copied! Toggle word wrap Toggle overflow For instance:ntpdate 0.rhel.pool.ntp.org 1.rhel.pool.ntp.org
~]# ntpdate 0.rhel.pool.ntp.org 1.rhel.pool.ntp.orgCopy to Clipboard Copied! Toggle word wrap Toggle overflow Unless an error message is displayed, the system time should now be set. You can check the current by setting typingdatewithout any additional arguments as shown in Section 2.2.1, “Date and Time Setup”. - In most cases, these steps are sufficient. Only if you really need one or more system services to always use the correct time, enable running the ntpdate at boot time:
chkconfig ntpdate on
~]# chkconfig ntpdate onCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information about system services and their setup, see Chapter 12, Services and Daemons.Note
If the synchronization with the time server at boot time keeps failing, i.e., you find a relevant error message in the/var/log/boot.logsystem log, try to add the following line to/etc/sysconfig/network:NETWORKWAIT=1
NETWORKWAIT=1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Open the NTP configuration file
/etc/ntp.confin a text editor such as vi or nano, or create a new one if it does not already exist:nano /etc/ntp.conf
~]# nano /etc/ntp.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Now add or edit the list of public NTP servers. If you are using Red Hat Enterprise Linux 6, the file should already contain the following lines, but feel free to change or expand these according to your needs:
server 0.rhel.pool.ntp.org iburst server 1.rhel.pool.ntp.org iburst server 2.rhel.pool.ntp.org iburst server 3.rhel.pool.ntp.org iburst
server 0.rhel.pool.ntp.org iburst server 1.rhel.pool.ntp.org iburst server 2.rhel.pool.ntp.org iburst server 3.rhel.pool.ntp.org iburstCopy to Clipboard Copied! Toggle word wrap Toggle overflow Theiburstdirective at the end of each line is to speed up the initial synchronization. As of Red Hat Enterprise Linux 6.5 it is added by default. If upgrading from a previous minor release, and your/etc/ntp.conffile has been modified, then the upgrade to Red Hat Enterprise Linux 6.5 will create a new file/etc/ntp.conf.rpmnewand will not alter the existing/etc/ntp.conffile. - Once you have the list of servers complete, in the same file, set the proper permissions, giving the unrestricted access to localhost only:
restrict default kod nomodify notrap nopeer noquery restrict -6 default kod nomodify notrap nopeer noquery restrict 127.0.0.1 restrict -6 ::1
restrict default kod nomodify notrap nopeer noquery restrict -6 default kod nomodify notrap nopeer noquery restrict 127.0.0.1 restrict -6 ::1Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save all changes, exit the editor, and restart the NTP daemon:
service ntpd restart
~]# service ntpd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Make sure that
ntpdis started at boot time:chkconfig ntpd on
~]# chkconfig ntpd onCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 3. Managing Users and Groups
3.1. What Users and Groups Are
Note
cat /usr/share/doc/setup-2.8.14/uidgid
cat /usr/share/doc/setup-2.8.14/uidgidUID_MIN and GID_MIN directives in the /etc/login.defs file:
[file contents truncated] UID_MIN 5000 [file contents truncated] GID_MIN 5000 [file contents truncated]
[file contents truncated]
UID_MIN 5000
[file contents truncated]
GID_MIN 5000
[file contents truncated]newgrp command, after which all newly created files are owned by the new group. A supplementary group serves to grant a certain set of users, its members, access to a certain set of files, those owned by this group.
root, and access permissions can be changed by both the root user and file owner.
umask and can be configured in the /etc/bashrc file for all users, or in ~/.bashrc for each user individually . The configuration in ~/.bashrc overrides the configuration in /etc/bashrc. Additionally, the umask command overrides the default permissions for the duration of the shell session.
/etc/shadow file, which is only readable by the root user. The file also stores information about password aging and policies for specific accounts. The default values for a newly created account are stored in the /etc/login.defs and /etc/default/useradd files. The Red Hat Enterprise Linux 6 Security Guide provides more security-related information about users and groups.
3.2. Managing Users via the User Manager Application
To start the User Manager application:
- From the toolbar, select → → .
- Or, type
system-config-usersat the shell prompt.
Note
root.
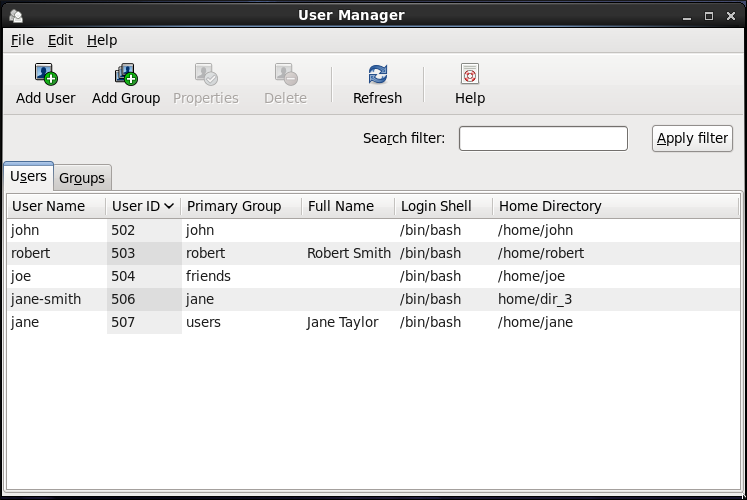
3.2.1. Viewing Users
Figure 3.1. Viewing Users
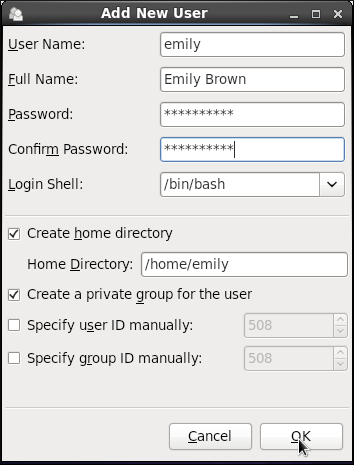
3.2.2. Adding a New User
- Click the button.
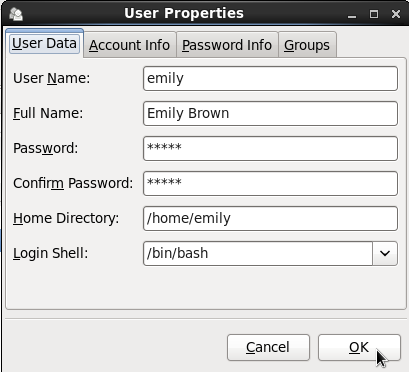
- Enter the user name and full name in the appropriate fields
- Type the user's password in the Password and Confirm Password fields. The password must be at least six characters long.
Note
For safety reasons, choose a long password not based on a dictionary term; use a combination of letters, numbers, and special characters. - Select a login shell for the user from the Login Shell drop-down list or accept the default value of .
- Clear the Create home directory check box if you choose not to create the home directory for a new user in
/home/username/.You can also change this home directory by editing the content of the Home Directory text box. Note that when the home directory is created, default configuration files are copied into it from the/etc/skel/directory. - Clear the Create a private group for the user check box if you do not want a unique group with the same name as the user to be created. User private group (UPG) is a group assigned to a user account to which that user exclusively belongs, which is used for managing file permissions for individual users.
- Specify a user ID for the user by selecting Specify user ID manually. If the option is not selected, the next available user ID above 500 is assigned to the new user.
- Click the button to complete the process.
3.2.3. Modifying User Properties
- Select the user from the user list by clicking once on the user name.
- Click from the toolbar or choose → from the drop-down menu.
Figure 3.2. User Properties
- There are four tabs you can update to your preferences. When you have finished, click the button to save your changes.
3.3. Managing Groups via the User Manager Application
3.3.1. Viewing Groups
Figure 3.3. Viewing Groups
3.3.2. Adding a New Group
- Select from the User Manager toolbar:
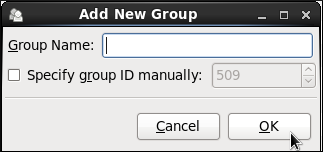
Figure 3.4. New Group
- Type the name of the new group.
- Specify the group ID (GID) for the new group by checking the Specify group ID manually check box.
- Select the GID. Note that Red Hat Enterprise Linux also reserves group IDs lower than 500 for system groups.
- Click to create the group. The new group appears in the group list.
3.3.3. Modifying Group Properties
- Select the group from the group list by clicking on its name.
- Click from the toolbar or choose → from the drop-down menu.
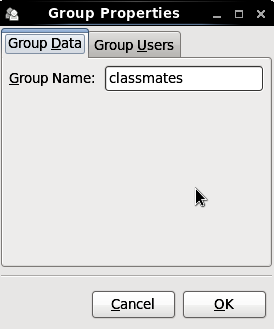
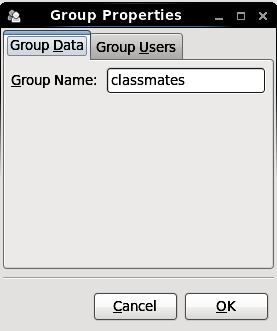
Figure 3.5. Group Properties
- The Group Users tab displays the list of group members. Use this tab to add or remove users from the group. Click to save your changes.
3.4. Managing Users via Command-Line Tools
useradd, usermod, userdel, or passwd. The files affected include /etc/passwd which stores user accounts information and /etc/shadow, which stores secure user account information.
3.4.1. Creating Users
useradd utility creates new users and adds them to the system. Following the short procedure below, you will create a default user account with its UID, automatically create a home directory where default user settings will be stored, /home/username/, and set the default shell to /bin/bash.
- Run the following command at a shell prompt as
rootsubstituting username with the name of your choice:useradd username
useradd usernameCopy to Clipboard Copied! Toggle word wrap Toggle overflow - By setting a password unlock the account to make it accessible. Type the password twice when the program prompts you to.
passwd
passwdCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Example 3.1. Creating a User with Default Settings
useradd robert command creates an account named robert. If you run cat /etc/passwd to view the content of the /etc/passwd file, you can learn more about the new user from the line displayed to you:
robert:x:502:502::/home/robert:/bin/bash
robert:x:502:502::/home/robert:/bin/bashrobert has been assigned a UID of 502, which reflects the rule that the default UID values from 0 to 499 are typically reserved for system accounts. GID, group ID of User Private Group, equals to UID. The home directory is set to /home/robert and login shell to /bin/bash. The letter x signals that shadow passwords are used and that the hashed password is stored in /etc/shadow.
useradd (see the useradd(8) man page for the whole list of options). As you can see from the basic syntax of the command, you can add one or more options:
useradd [option(s)] username
useradd [option(s)] username-c option to specify, for example, the full name of the user when creating them. Use -c followed by a string, which adds a comment to the user:
useradd -c "string" username
useradd -c "string" usernameExample 3.2. Specifying a User's Full Name when Creating a User
useradd -c "Robert Smith" robert cat /etc/passwd robert:x:502:502:Robert Smith:/home/robert:/bin/bash
~]# useradd -c "Robert Smith" robert
~]# cat /etc/passwd
robert:x:502:502:Robert Smith:/home/robert:/bin/bash
robert, sometimes called the login name, and full name Robert Smith.
/home/username/ directory for the user account, set a different one instead of it. Execute the command below:
useradd -d home_directory
useradd -d home_directoryExample 3.3. Adding a User with non-default Home Directory
useradd -d /home/dir_1 robert
~]# useradd -d /home/dir_1 robert
robert's home directory is now not the default /home/robert but /home/dir_1/.
useradd with the -M option. However, when such a user logs into a system that has just booted and their home directory does not exist, their login directory will be the root directory. If such a user logs into a system using the su command, their login directory will be the current directory of the previous user.
useradd -M username
useradd -M username/home directory while creating a new user, make use of the -m and -k options together followed by the path.
Example 3.4. Creating a User while Copying Contents to the Home Directory
/dir_1 to /home/jane, which is the default home directory of a new user jane:
useradd -m -k /dir_1 jane
~]# useradd -m -k /dir_1 jane
useradd command, this means creating an account for a certain amount of time only and disabling it at a certain date. This is a particularly useful setting as there is no security risk resulting from forgetting to delete a certain account. For this, the -e option is used with the specified expire_date in the YYYY-MM-DD format.
Note
useradd -e YYYY-MM-DD username
useradd -e YYYY-MM-DD usernameExample 3.5. Setting the Account Expiration Date
useradd -e 2015-11-05 emily
~]# useradd -e 2015-11-05 emily
emily will be created now and automatically disabled on 5 November, 2015.
/bin/bash, but can be changed by the -s option to any other shell different from bash, ksh, csh, tsh, for example.
useradd -s login_shell username
useradd -s login_shell usernameExample 3.6. Adding a User with Non-default Shell
useradd -s /bin/ksh robert
~]# useradd -s /bin/ksh robert
robert which has the /bin/ksh shell.
-r option creates a system account, which is an account for administrative use that has some, but not all, root privileges. Such accounts have a UID lower than the value of UID_MIN defined in /etc/login.defs, typically 500 and above for ordinary users.
useradd -r username
useradd -r username
3.4.2. Attaching New Users to Groups
useradd command creates a User Private Group (UPG, a group assigned to a user account to which that user exclusively belongs) whenever a new user is added to the system and names the group after the user. For example, when the account robert is created, an UPG named robert is created at the same time, the only member of which is the user robert.
User Private Group for a user for whatever reason, execute the useradd command with the following option:
useradd -N username
useradd -N username-g and -G options. While the -g option specifies the primary group membership, -G refers to supplementary groups into which the user is also included. The group names you specify must already exist on the system.
Example 3.7. Adding a User to a Group
useradd -g "friends" -G "family,schoolmates" emily
~]# useradd -g "friends" -G "family,schoolmates" emily
useradd -g "friends" -G "family,schoolmates" emily command creates the user emily but emily's primary group is set to friends as specified by the -g option. emily is also a group member of the supplementary groups family and schoolmates.
usermod command with the -G option and a list of groups divided by commas, no spaces:
usermod -G group_1,group_2,group_3
usermod -G group_1,group_2,group_33.4.3. Updating Users' Authentication
useradd username command, the password is automatically set to never expire (see the /etc/shadow file).
passwd, the standard utility for administering the /etc/passwd file. The syntax of the passwd command look as follows:
passwd option(s) username
passwd option(s) username!). If you later find a reason to unlock the account, passwd has a reverse operation for locking. Only root can carry out these two operations.
passwd -l username passwd -u username
passwd -l username
passwd -u usernameExample 3.8. Unlocking a User Password
-l option locks robert's account password successfully. However, running the passwd -u command does not unlock the password because by default passwd refuses to create a passwordless account.
passwd with the -e option. The user will be forced to change the password during the next login attempt:
passwd -e username
passwd -e username-n option) and the maximum (the -x option) lifetimes. To inform the user about their password expiration, use the -w option. All these options must be accompanied with the number of days and can be run as root only.
Example 3.9. Adjusting Aging Data for User Passwords
passwd -n 10 -x 60 -w 3 jane
~]# passwd -n 10 -x 60 -w 3 jane
jane will begin receiving warnings in advance that her password will expire to 3 day.
-S option which outputs a short information for you to know the status of the password for a given account:
passwd -S jane jane LK 2014-07-22 10 60 3 -1 (Password locked.)
~]# passwd -S jane
jane LK 2014-07-22 10 60 3 -1 (Password locked.)
useradd command, which disables the account permanently. A value of 0 disables the account as soon as the password has expired, and a value of -1 disables the feature, that is, the user will have to change his password when the password expires. The -f option is used to specify the number of days after a password expires until the account is disabled (but may be unblocked by system administrator):
useradd -f number-of-days username
useradd -f number-of-days usernamepasswd command see the passwd(1) man page.
3.4.4. Modifying User Settings
usermod command. The logic of using usermod is identical to useradd as well as its syntax:
usermod option(s) username
usermod option(s) username-l option with the new user name (or login).
Example 3.10. Changing User's Login
usermod -l "emily-smith" emily
~]# usermod -l "emily-smith" emily
-l option changes the name of the user from the login emily to the new login, emily-smith. Nothing else is changed. In particular, emily's home directory name (/home/emily) remains the same unless it is changed manually to reflect the new user name.
Note
Example 3.11. Changing User's UID and Home Directory
usermod -a -u 699 -d /home/dir_2 robert
~]# usermod -a -u 699 -d /home/dir_2 robert
-a -u and -d options changes the settings of user robert. Now, his ID is 699 instead of 501, and his home directory is no longer /home/robert but /home/dir_2.
usermod command you can also move the content of the user's home directory to a new location, or lock the account by locking its password.
Example 3.12. Changing User's
usermod -m -d /home/jane -L jane
~]# usermod -m -d /home/jane -L jane
-m and -d options used together move the content of jane's home directory to the /home/dir_3 directory. The -L option locks the access to jane's account by locking its password.
usermod command, see the usermod(8) man page or run usermod --help on the command line.
3.4.5. Deleting Users
userdel command on the command line as root.
userdel username
userdel usernameuserdel with the -r option removes files in the user's home directory along with the home directory itself and the user's mail spool. Files located in other file systems have to be searched for and deleted manually.
userdel -r username
userdel -r usernameNote
-r option is relatively safer, and thus recommended, compared to -f which forces the removal of the user account even if the user is still logged in.
3.4.6. Displaying Comprehensive User Information
lslogins [OPTIONS]
lslogins [OPTIONS]lslogins(1) manual page or the output of the lslogins --help command for the complete list of available options and their usage.
lslogins command without any options shows default information about all system and user accounts on the system. Specifically, their UID, user name, and GECOS information, as well as information about the user's last login to the system, and whether their password is locked or login by password disabled.
Example 3.13. Displaying basic information about all accounts on the system
lslogins LOGIN command, where LOGIN is either a UID or a user name. The following example displays detailed information about John Doe's account and his activity on the system:
Example 3.14. Displaying detailed information about a single account
--logins=LOGIN option, you can display information about a group of accounts that are specified as a list of UIDs or user names. Specifying the --output=COLUMNS option, where COLUMNS is a list of available output parameters, you can customize the output of the lslogins command. For example, the following command shows login activity of the users root, jsmith, jdoe, and esmith:
Example 3.15. Displaying specific information about a group of users
--system-accs option. To address user accounts, use the --user-accs. For example, the following command displays information about supplementary groups and password expirations for all user accounts:
Example 3.16. Displaying information about supplementary groups and password expiration for all user accounts
lslogins commands according to the user's needs makes lslogins an ideal tool to use in scripts and for automatic processing. For example, the following command returns a single string that represents the time and date of the last login. This string can be passed as input to another utility for further processing.
Example 3.17. Displaying a single piece of information without the heading
lslogins --logins=jsmith --output=LAST-LOGIN --time-format=iso | tail -1 2014-08-06T10:56:12+0200
~]# lslogins --logins=jsmith --output=LAST-LOGIN --time-format=iso | tail -1
2014-08-06T10:56:12+02003.5. Managing Groups via Command-Line Tools
groupadd, groupmod, groupdel, or gpasswd. The files affected include /etc/group which stores group account information and /etc/gshadow, which stores secure group account information.
3.5.1. Creating Groups
groupadd command is run at the shell prompt as root.
groupadd group_name
groupadd group_nameExample 3.18. Creating a Group with Default Settings
groupadd friends
~]# groupadd friends
groupadd command creates a new group called friends. You can read more information about the group from the newly-created line in the /etc/group file:
classmates:x:30005:
classmates:x:30005:friends is attached with a unique GID (group ID) of 30005 and is not attached with any users. Optionally, you can set a password for a group by running gpasswd groupname.
groupadd option(s) groupname
groupadd option(s) groupnamegroupadd command with the -g option. Remember that this value must be unique (unless the -o option is used) and the value must be non-negative.
groupadd -g GID
groupadd -g GIDExample 3.19. Creating a Group with Specified GID
schoolmates and sets GID of 60002 for it:
groupadd -g 60002 schoolmates
~]# groupadd -g 60002 schoolmates
-g and GID already exists, groupadd refuses to create another group with existing GID. As a workaround, use the -f option, with which groupadd creates a group, but with a different GID.
groupadd -f GID
groupadd -f GID-r option to the groupadd command. System groups are used for system purposes, which practically means that GID is allocated from 1 to 499 within the reserved range of 999.
groupadd -r group_name
groupadd -r group_namegroupadd, see the groupadd(8) man pages.
3.5.2. Attaching Users to Groups
gpasswd command.
gpasswd -a username which_group_to_edit
gpasswd -a username which_group_to_editgpasswd -d username which_group_to_edit
gpasswd -d username which_group_to_edit--members option dividing them with commas and no spaces:
gpasswd --members username_1,username_2 which_group_to_edit
gpasswd --members username_1,username_2 which_group_to_edit3.5.3. Updating Group Authentication
gpasswd command administers /etc/group and /etc/gshadow files. Note that this command works only if run by a group administrator.
root user can add group administrators with the gpasswd -A users groupname where users is a comma-separated list of existing users you want to be group administrators (without any spaces between commas).
gpasswd command with the relevant group name. You will be prompted to type the new password of the group.
gpasswd groupname
gpasswd groupnameExample 3.20. Changing a Group Password
gpasswd crowd Changing password for group crowd New password: Re-enter new password:
~]# gpasswd crowd
Changing password for group crowd
New password:
Re-enter new password:
crowd has been changed.
-r option.
gpasswd -r schoolmates
gpasswd -r schoolmates3.5.4. Modifying Group Settings
groupmod command. The logic of using groupmod is identical to groupadd as well as its syntax:
groupmod option(s) groupname
groupmod option(s) groupnamegroupmod command in the following way:
groupmod -g GID_NEW which_group_to_edit
groupmod -g GID_NEW which_group_to_editNote
groupmod -n new_groupname groupname
groupmod -n new_groupname groupnameExample 3.21. Changing a Group's Name
schoolmates to crowd:
groupmod -n crowd schoolmates
~]# groupmod -n crowd schoolmates
3.5.5. Deleting Groups
groupdel command modifies the system account files, deleting all entries that see the group. The named group must exist when you execute this command.
groupdel groupname
groupdel groupname3.6. Additional Resources
3.6.1. Installed Documentation
- chage(1) — A command to modify password aging policies and account expiration.
- gpasswd(1) — A command to administer the
/etc/groupfile. - groupadd(8) — A command to add groups.
- grpck(8) — A command to verify the
/etc/groupfile. - groupdel(8) — A command to remove groups.
- groupmod(8) — A command to modify group membership.
- pwck(8) — A command to verify the
/etc/passwdand/etc/shadowfiles. - pwconv(8) — A tool to convert standard passwords to shadow passwords.
- pwunconv(8) — A tool to convert shadow passwords to standard passwords.
- useradd(8) — A command to add users.
- userdel(8) — A command to remove users.
- usermod(8) — A command to modify users.
- group(5) — The file containing group information for the system.
- passwd(5) — The file containing user information for the system.
- shadow(5) — The file containing passwords and account expiration information for the system.
- login.defs(5) - The file containing shadow password suite configuration.
- useradd(8) - For
/etc/default/useradd, section “Changing the default values” in manual page.
Chapter 4. Gaining Privileges
root is potentially dangerous and can lead to widespread damage to the system and data. This chapter covers ways to gain administrative privileges using the su and sudo programs. These programs allow specific users to perform tasks which would normally be available only to the root user while maintaining a higher level of control and system security.
4.1. The su Command
su command, they are prompted for the root password and, after authentication, are given a root shell prompt.
su command, the user is the root user and has absolute administrative access to the system[1]. In addition, once a user has become root, it is possible for them to use the su command to change to any other user on the system without being prompted for a password.
usermod -a -G wheel username
~]# usermod -a -G wheel usernamewheel group.
- Click the menu on the Panel, point to and then click to display the User Manager. Alternatively, type the command
system-config-usersat a shell prompt. - Click the Users tab, and select the required user in the list of users.
- Click on the toolbar to display the User Properties dialog box (or choose on the menu).
- Click the Groups tab, select the check box for the wheel group, and then click .
wheel group, it is advisable to only allow these specific users to use the su command. To do this, you will need to edit the PAM configuration file for su: /etc/pam.d/su. Open this file in a text editor and remove the comment (#) from the following line:
#auth required pam_wheel.so use_uid
#auth required pam_wheel.so use_uidwheel can switch to another user using the su command.
Note
root user is part of the wheel group by default.
4.2. The sudo Command
sudo command offers another approach to giving users administrative access. When trusted users precede an administrative command with sudo, they are prompted for their own password. Then, when they have been authenticated and assuming that the command is permitted, the administrative command is executed as if they were the root user.
sudo command is as follows:
sudo <command>
sudo <command>mount.
sudo command allows for a high degree of flexibility. For instance, only users listed in the /etc/sudoers configuration file are allowed to use the sudo command and the command is executed in the user's shell, not a root shell. This means the root shell can be completely disabled as shown in the Red Hat Enterprise Linux 6 Security Guide.
sudo is logged to the file /var/log/messages and the command issued along with the issuer's user name is logged to the file /var/log/secure. Should you require additional logging, use the pam_tty_audit module to enable TTY auditing for specified users by adding the following line to your /etc/pam.d/system-auth file:
session required pam_tty_audit.so disable=<pattern> enable=<pattern>
session required pam_tty_audit.so disable=<pattern> enable=<pattern>session required pam_tty_audit.so disable=* enable=root
session required pam_tty_audit.so disable=* enable=rootsudo command is that an administrator can allow different users access to specific commands based on their needs.
sudo configuration file, /etc/sudoers, should use the visudo command.
visudo and add a line similar to the following in the user privilege specification section:
juan ALL=(ALL) ALL
juan ALL=(ALL) ALLjuan, can use sudo from any host and execute any command.
sudo:
%users localhost=/sbin/shutdown -h now
%users localhost=/sbin/shutdown -h now/sbin/shutdown -h now as long as it is issued from the console.
sudoers has a detailed listing of options for this file.
Important
sudo command. You can avoid them by editing the /etc/sudoers configuration file using visudo as described above. Leaving the /etc/sudoers file in its default state gives every user in the wheel group unlimited root access.
- By default,
sudostores the sudoer's password for a five minute timeout period. Any subsequent uses of the command during this period will not prompt the user for a password. This could be exploited by an attacker if the user leaves his workstation unattended and unlocked while still being logged in. This behavior can be changed by adding the following line to the/etc/sudoersfile:Defaults timestamp_timeout=<value>
Defaults timestamp_timeout=<value>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where <value> is the desired timeout length in minutes. Setting the <value> to 0 causessudoto require a password every time. - If a sudoer's account is compromised, an attacker can use
sudoto open a new shell with administrative privileges:sudo /bin/bash
sudo /bin/bashCopy to Clipboard Copied! Toggle word wrap Toggle overflow Opening a new shell as root in this or similar fashion gives the attacker administrative access for a theoretically unlimited amount of time, bypassing the timeout period specified in the/etc/sudoersfile and never requiring the attacker to input a password forsudoagain until the newly opened session is closed.
4.3. Additional Resources
Installed Documentation
- su(1) - the manual page for
suprovides information regarding the options available with this command. - sudo(8) - the manual page for
sudoincludes a detailed description of this command as well as a list of options available for customizingsudo's behavior. - pam(8) - the manual page describing the use of Pluggable Authentication Modules for Linux.
Online Documentation
- Red Hat Enterprise Linux 6 Security Guide - The Security Guide describes in detail security risks and mitigating techniques related to programs for gaining privileges.
- Red Hat Enterprise Linux 6 Managing Single Sign-On and Smart Cards - This guide provides, among other things, a detailed description of Pluggable Authentication Modules (PAM), their configuration and usage.
Chapter 5. Console Access
- They can run certain programs that they otherwise cannot run.
- They can access certain files that they otherwise cannot access. These files normally include special device files used to access diskettes, CD-ROMs, and so on.
halt, poweroff, and reboot.
5.1. Disabling Console Program Access for Non-root Users
/etc/security/console.apps/ directory. To list these programs, run the following command:
/etc/security/console.apps/ resides in the /etc/pam.d/ directory and is named the same as the program. Using this file, you can configure PAM to deny access to the program if the user is not root. To do that, insert line auth requisite pam_deny.so directly after the first uncommented line auth sufficient pam_rootok.so.
Example 5.1. Disabling Access to the Reboot Program
/etc/security/console.apps/reboot, insert line auth requisite pam_deny.so into the /etc/pam.d/reboot PAM configuration file:
reboot utility is disabled.
/etc/security/console.apps/ partially derive their PAM configuration from the /etc/pam.d/config-util configuration file. This allows to change configuration for all these programs at once by editing /etc/pam.d/config-util. To find all these programs, search for PAM configuration files that refer to the config-util file:
halt, poweroff, reboot, and other programs, which by default are accessible from the console.
5.2. Disabling Rebooting Using Ctrl+Alt+Del
/etc/init/control-alt-delete.conf file. By default, the shutdown utility with the -r option is used to shutdown and reboot the system.
exec true command, which does nothing. To do that, run the following command as root:
echo "exec true" >> /etc/init/control-alt-delete.override
~]# echo "exec true" >> /etc/init/control-alt-delete.overridePart II. Subscription and Support
Chapter 6. Registering the System and Managing Subscriptions
Note
6.1. Registering the System and Attaching Subscriptions
subscription-manager commands are supposed to be run as root.
- Run the following command to register your system. You will be prompted to enter your user name and password. Note that the user name and password are the same as your login credentials for Red Hat Customer Portal.
subscription-manager register
subscription-manager registerCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Determine the pool ID of a subscription that you require. To do so, type the following at a shell prompt to display a list of all subscriptions that are available for your system:
subscription-manager list --available
subscription-manager list --availableCopy to Clipboard Copied! Toggle word wrap Toggle overflow For each available subscription, this command displays its name, unique identifier, expiration date, and other details related to your subscription. To list subscriptions for all architectures, add the--alloption. The pool ID is listed on a line beginning withPool ID. - Attach the appropriate subscription to your system by entering a command as follows:
subscription-manager attach --pool=pool_id
subscription-manager attach --pool=pool_idCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace pool_id with the pool ID you determined in the previous step.To verify the list of subscriptions your system has currently attached, at any time, run:subscription-manager list --consumed
subscription-manager list --consumedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Note
yum and subscription-manager to work correctly. Refer to the "Setting Firewall Access for Content Delivery" section of the Red Hat Enterprise Linux 6 Subscription Management guide if you use a firewall and to the "Using an HTTP Proxy" section if you use a proxy.
6.2. Managing Software Repositories
/etc/yum.repos.d/ directory. To verify that, use yum to list all enabled repositories:
yum repolist
yum repolistsubscription-manager repos --list
subscription-manager repos --listrhel-variant-rhscl-version-rpms rhel-variant-rhscl-version-debug-rpms rhel-variant-rhscl-version-source-rpms
rhel-variant-rhscl-version-rpms
rhel-variant-rhscl-version-debug-rpms
rhel-variant-rhscl-version-source-rpms
server or workstation), and version is the Red Hat Enterprise Linux system version (6 or 7), for example:
rhel-server-rhscl-6-eus-rpms rhel-server-rhscl-6-eus-source-rpms rhel-server-rhscl-6-eus-debug-rpms
rhel-server-rhscl-6-eus-rpms
rhel-server-rhscl-6-eus-source-rpms
rhel-server-rhscl-6-eus-debug-rpmssubscription-manager repos --enable repository
subscription-manager repos --enable repositorysubscription-manager repos --disable repository
subscription-manager repos --disable repository6.3. Removing Subscriptions
- Determine the serial number of the subscription you want to remove by listing information about already attached subscriptions:
subscription-manager list --consumed
subscription-manager list --consumedCopy to Clipboard Copied! Toggle word wrap Toggle overflow The serial number is the number listed asserial. For instance,744993814251016831in the example below:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter a command as follows to remove the selected subscription:
subscription-manager remove --serial=serial_number
subscription-manager remove --serial=serial_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace serial_number with the serial number you determined in the previous step.
subscription-manager remove --all
subscription-manager remove --all6.4. Additional Resources
Installed Documentation
subscription-manager(8) — the manual page for Red Hat Subscription Management provides a complete list of supported options and commands.
Related Books
- Red Hat Subscription Management collection of guides — These guides contain detailed information how to use Red Hat Subscription Management.
- Installation Guide — see the Firstboot chapter for detailed information on how to register during the firstboot process.
Online Resources
- Red Hat Access Labs — The Red Hat Access Labs includes a “Registration Assistant”.
See Also
- Chapter 4, Gaining Privileges documents how to gain administrative privileges by using the
suandsudocommands. - Chapter 8, Yum provides information about using the yum packages manager to install and update software.
- Chapter 9, PackageKit provides information about using the PackageKit package manager to install and update software.
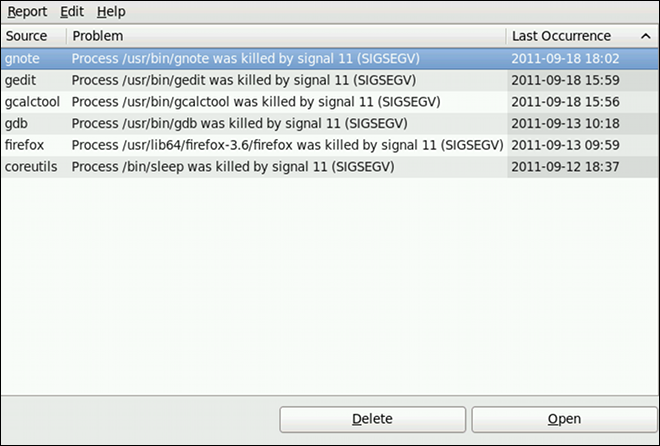
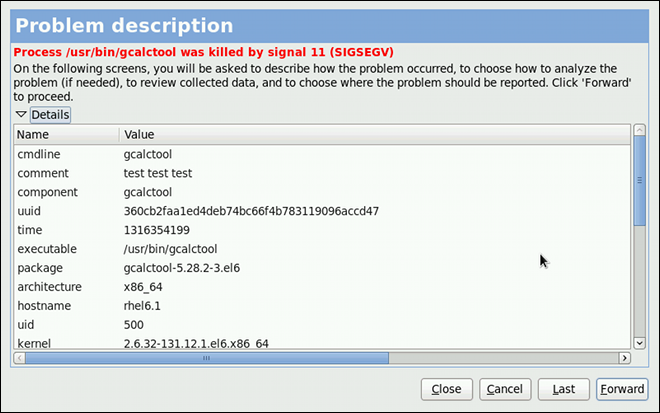
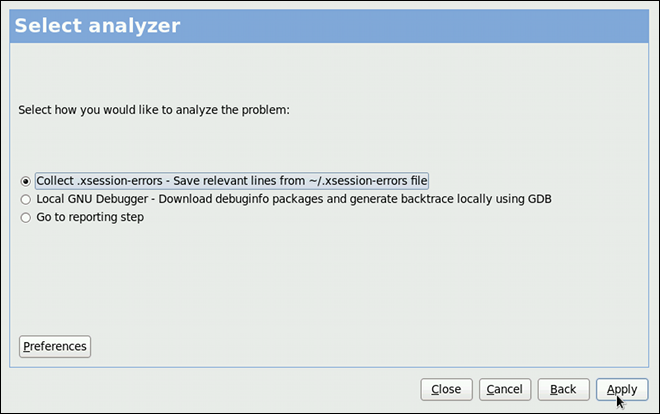
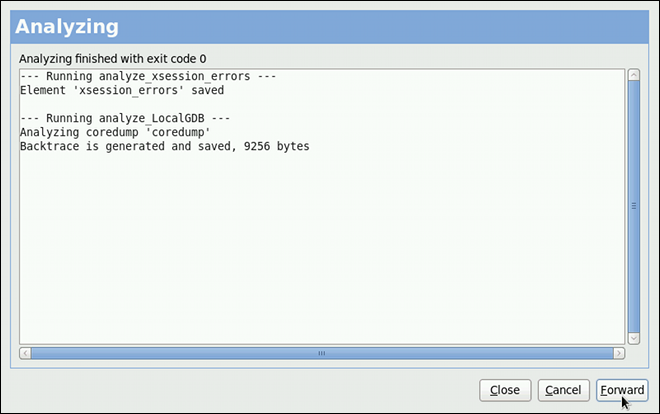
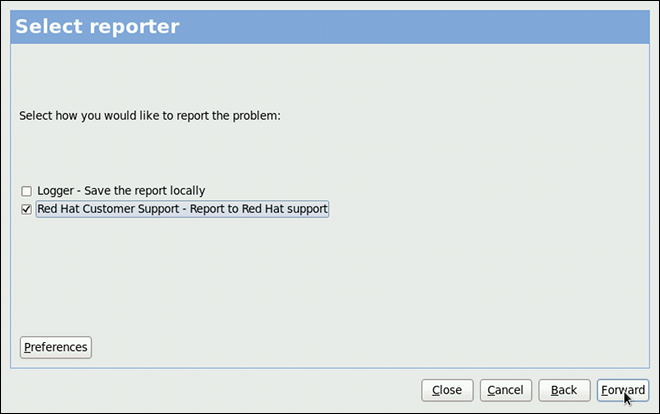
Chapter 7. Accessing Support Using the Red Hat Support Tool
SSH or from any terminal. It enables, for example, searching the Red Hat Knowledgebase from the command line, copying solutions directly on the command line, opening and updating support cases, and sending files to Red Hat for analysis.
7.1. Installing the Red Hat Support Tool
root:
yum install redhat-support-tool
~]# yum install redhat-support-tool7.2. Registering the Red Hat Support Tool Using the Command Line
- Where username is the user name of the Red Hat Customer Portal account.
redhat-support-tool config user username
~]# redhat-support-tool config user usernameCopy to Clipboard Copied! Toggle word wrap Toggle overflow redhat-support-tool config password Please enter the password for username:
~]# redhat-support-tool config password Please enter the password for username:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.3. Using the Red Hat Support Tool in Interactive Shell Mode
redhat-support-tool Welcome to the Red Hat Support Tool. Command (? for help):
~]$ redhat-support-tool
Welcome to the Red Hat Support Tool.
Command (? for help):root.
? character. The program or menu selection can be exited by entering the q or e character. You will be prompted for your Red Hat Customer Portal user name and password when you first search the Knowledgebase or support cases. Alternately, set the user name and password for your Red Hat Customer Portal account using interactive mode, and optionally save it to the configuration file.
7.4. Configuring the Red Hat Support Tool
config --help:
Procedure 7.1. Registering the Red Hat Support Tool Using Interactive Mode
- Start the tool by entering the following command:
redhat-support-tool
~]# redhat-support-toolCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter your Red Hat Customer Portal user name:To save your user name to the global configuration file, add the
Command (? for help): config user username
Command (? for help): config user usernameCopy to Clipboard Copied! Toggle word wrap Toggle overflow -goption. - Enter your Red Hat Customer Portal password:
Command (? for help): config password Please enter the password for username:
Command (? for help): config password Please enter the password for username:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.4.1. Saving Settings to the Configuration Files
~/.redhat-support-tool/redhat-support-tool.conf configuration file. If required, it is recommended to save passwords to this file because it is only readable by that particular user. When the tool starts, it will read values from the global configuration file /etc/redhat-support-tool.conf and from the local configuration file. Locally stored values and options take precedence over globally stored settings.
Warning
/etc/redhat-support-tool.conf configuration file because the password is just base64 encoded and can easily be decoded. In addition, the file is world readable.
-g, --global option as follows:
Command (? for help): config setting -g value
Command (? for help): config setting -g valueNote
-g, --global option, the Red Hat Support Tool must be run as root because normal users do not have the permissions required to write to /etc/redhat-support-tool.conf.
-u, --unset option as follows:
Command (? for help): config setting -u value
Command (? for help): config setting -u valueNote
-u, --unset option, but they can be cleared, unset, from the current running instance of the tool by using the -g, --global option simultaneously with the -u, --unset option. If running as root, values and options can be removed from the global configuration file using -g, --global simultaneously with the -u, --unset option.
7.5. Opening and Updating Support Cases Using Interactive Mode
Procedure 7.2. Opening a New Support Case Using Interactive Mode
- Start the tool by entering the following command:
redhat-support-tool
~]# redhat-support-toolCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter the
opencasecommand:Command (? for help): opencase
Command (? for help): opencaseCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Follow the on screen prompts to select a product and then a version.
- Enter a summary of the case.
- Enter a description of the case and press Ctrl+D on an empty line when complete.
- Select a severity of the case.
- Optionally chose to see if there is a solution to this problem before opening a support case.
- Confirm you would still like to open the support case.
Support case 0123456789 has successfully been opened
Support case 0123456789 has successfully been openedCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally chose to attach an SOS report.
- Optionally chose to attach a file.
Procedure 7.3. Viewing and Updating an Existing Support Case Using Interactive Mode
- Start the tool by entering the following command:
redhat-support-tool
~]# redhat-support-toolCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter the
getcasecommand:Where case-number is the number of the case you want to view and update.Command (? for help): getcase case-number
Command (? for help): getcase case-numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Follow the on screen prompts to view the case, modify or add comments, and get or add attachments.
Procedure 7.4. Modifying an Existing Support Case Using Interactive Mode
- Start the tool by entering the following command:
redhat-support-tool
~]# redhat-support-toolCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter the
modifycasecommand:Where case-number is the number of the case you want to view and update.Command (? for help): modifycase case-number
Command (? for help): modifycase case-numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow - The modify selection list appears:Follow the on screen prompts to modify one or more of the options.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - For example, to modify the status, enter
3:Selection: 3 1 Waiting on Customer 2 Waiting on Red Hat 3 Closed Please select a status (or 'q' to exit):
Selection: 3 1 Waiting on Customer 2 Waiting on Red Hat 3 Closed Please select a status (or 'q' to exit):Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.6. Viewing Support Cases on the Command Line
redhat-support-tool getcase case-number
~]# redhat-support-tool getcase case-number7.7. Additional Resources
Part III. Installing and Managing Software
Chapter 8. Yum
Important
Note
yum to install, update or remove packages on your system. All examples in this chapter assume that you have already obtained superuser privileges by using either the su or sudo command.
8.1. Checking For and Updating Packages
8.1.1. Checking For Updates
yum check-update
yum check-updatePackageKit— the name of the packagex86_64— the CPU architecture the package was built for0.5.8— the version of the updated package to be installedrhel— the repository in which the updated package is located
yum.
8.1.2. Updating Packages
Updating a Single Package
root:
yum update package_name
yum update package_nameLoaded plugins: product-id, refresh-packagekit, subscription-manager—yumalways informs you which Yum plug-ins are installed and enabled. See Section 8.5, “Yum Plug-ins” for general information on Yum plug-ins, or to Section 8.5.3, “Plug-in Descriptions” for descriptions of specific plug-ins.udev.x86_64— you can download and install new udev package.yumpresents the update information and then prompts you as to whether you want it to perform the update;yumruns interactively by default. If you already know which transactions theyumcommand plans to perform, you can use the-yoption to automatically answeryesto any questions thatyumasks (in which case it runs non-interactively). However, you should always examine which changesyumplans to make to the system so that you can easily troubleshoot any problems that might arise.If a transaction does go awry, you can view Yum's transaction history by using theyum historycommand as described in Section 8.3, “Working with Transaction History”.
Important
yum always installs a new kernel in the same sense that RPM installs a new kernel when you use the command rpm -i kernel. Therefore, you do not need to worry about the distinction between installing and upgrading a kernel package when you use yum: it will do the right thing, regardless of whether you are using the yum update or yum install command.
rpm -i kernel command (which installs a new kernel) instead of rpm -u kernel (which replaces the current kernel). See Section B.2.2, “Installing and Upgrading” for more information on installing/upgrading kernels with RPM.
Updating All Packages and Their Dependencies
yum update (without any arguments):
yum update
yum updateUpdating Security-Related Packages
yum command with a set of highly-useful security-centric commands, subcommands and options. See Section 8.5.3, “Plug-in Descriptions” for specific information.
Updating Packages Automatically
cron daemon and downloads metadata from your package repositories. With the yum-cron service enabled, the user can schedule an automated daily Yum update as a cron job.
Note
yum install yum-cron
~]# yum install yum-cronchkconfig yum-cron on
~]# chkconfig yum-cron onservice yum-cron start
~]# service yum-cron startservice yum-cron status
~]# service yum-cron status/etc/sysconfig/yum-cron file.
yum-cron can be found in the comments within /etc/sysconfig/yum-cron and at the yum-cron(8) manual page.
8.1.3. Preserving Configuration File Changes
8.1.4. Upgrading the System Off-line with ISO and Yum
yum update command with the Red Hat Enterprise Linux installation ISO image is an easy and quick way to upgrade systems to the latest minor version. The following steps illustrate the upgrading process:
- Create a target directory to mount your ISO image. This directory is not automatically created when mounting, so create it before proceeding to the next step. As
root, type:mkdir mount_dir
mkdir mount_dirCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace mount_dir with a path to the mount directory. Typically, users create it as a subdirectory in the/mediadirectory. - Mount the Red Hat Enterprise Linux 6 installation ISO image to the previously created target directory. As
root, type:mount -o loop iso_name mount_dir
mount -o loop iso_name mount_dirCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace iso_name with a path to your ISO image and mount_dir with a path to the target directory. Here, the-oloopoption is required to mount the file as a block device. - Copy the
media.repofile from the mount directory to the/etc/yum.repos.d/directory. Note that configuration files in this directory must have the .repo extension to function properly.cp mount_dir/media.repo /etc/yum.repos.d/new.repo
cp mount_dir/media.repo /etc/yum.repos.d/new.repoCopy to Clipboard Copied! Toggle word wrap Toggle overflow This creates a configuration file for the yum repository. Replace new.repo with the filename, for example rhel6.repo. - Edit the new configuration file so that it points to the Red Hat Enterprise Linux installation ISO. Add the following line into the
/etc/yum.repos.d/new.repofile:baseurl=file:///mount_dir
baseurl=file:///mount_dirCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace mount_dir with a path to the mount point. - Update all yum repositories including
/etc/yum.repos.d/new.repocreated in previous steps. Asroot, type:yum update
yum updateCopy to Clipboard Copied! Toggle word wrap Toggle overflow This upgrades your system to the version provided by the mounted ISO image. - After successful upgrade, you can unmount the ISO image. As
root, type:umount mount_dir
umount mount_dirCopy to Clipboard Copied! Toggle word wrap Toggle overflow where mount_dir is a path to your mount directory. Also, you can remove the mount directory created in the first step. Asroot, type:rmdir mount_dir
rmdir mount_dirCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If you will not use the previously created configuration file for another installation or update, you can remove it. As
root, type:rm /etc/yum.repos.d/new.repo
rm /etc/yum.repos.d/new.repoCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Example 8.1. Upgrading from Red Hat Enterprise Linux 6.3 to 6.4
RHEL6.4-Server-20130130.0-x86_64-DVD1.iso. A target directory created for mounting is /media/rhel6/. As root, change into the directory with your ISO image and type:
mount -o loop RHEL6.4-Server-20130130.0-x86_64-DVD1.iso /media/rhel6/
~]# mount -o loop RHEL6.4-Server-20130130.0-x86_64-DVD1.iso /media/rhel6/media.repo file from the mount directory:
cp /media/rhel6/media.repo /etc/yum.repos.d/rhel6.repo
~]# cp /media/rhel6/media.repo /etc/yum.repos.d/rhel6.repo/etc/yum.repos.d/rhel6.repo copied in the previous step:
baseurl=file:///media/rhel6/
baseurl=file:///media/rhel6/RHEL6.4-Server-20130130.0-x86_64-DVD1.iso. As root, execute:
yum update
~]# yum updateumount /media/rhel6/
~]# umount /media/rhel6/rmdir /media/rhel6/
~]# rmdir /media/rhel6/rm /etc/yum.repos.d/rhel6.repo
~]# rm /etc/yum.repos.d/rhel6.repo8.2. Packages and Package Groups
8.2.1. Searching Packages
yum search term…
yum search term…Example 8.2. Searching for packages matching a specific string
yum search command is useful for searching for packages you do not know the name of, but for which you know a related term. Note that by default, yum search returns matches in package name and summary, which makes the search faster. Use the yum search all command for a more exhaustive but slower search.
8.2.2. Listing Packages
yum list and related commands provide information about packages, package groups, and repositories.
* (which expands to match any character multiple times) and ? (which expands to match any one character).
Note
yum command, otherwise the Bash shell will interpret these expressions as pathname expansions, and potentially pass all files in the current directory that match the globs to yum. To make sure the glob expressions are passed to yum as intended, either:
- escape the wildcard characters by preceding them with a backslash character
- double-quote or single-quote the entire glob expression.
-
yum list glob_expression - Lists information on installed and available packages matching all glob expressions.
Example 8.3. Listing all ABRT add-ons and plug-ins using glob expressions
Packages with various ABRT add-ons and plug-ins either begin with “abrt-addon-”, or “abrt-plugin-”. To list these packages, type the following at a shell prompt:Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
yum list all - Lists all installed and available packages.
-
yum list installed - Lists all packages installed on your system. The rightmost column in the output lists the repository from which the package was retrieved.
Example 8.4. Listing installed packages using a double-quoted glob expression
To list all installed packages that begin with “krb” followed by exactly one character and a hyphen, type:Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
yum list available - Lists all available packages in all enabled repositories.
Example 8.5. Listing available packages using a single glob expression with escaped wildcard characters
To list all available packages with names that contain “gstreamer” and then “plugin”, run the following command:Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
yum grouplist - Lists all package groups.
-
yum repolist - Lists the repository ID, name, and number of packages it provides for each enabled repository.
8.2.3. Displaying Package Information
yum info package_name
yum info package_nameyum info package_name command is similar to the rpm -q --info package_name command, but provides as additional information the ID of the Yum repository the RPM package is found in (look for the From repo: line in the output).
yumdb info package_name
yumdb info package_nameuser indicates it was installed by the user, and dep means it was brought in as a dependency). For example, to display additional information about the yum package, type:
yumdb command, see the yumdb(8) manual page.
Listing Files Contained in a Package
repoquery --list package_name
repoquery --list package_namerepoquery command, see the repoquery manual page.
yum provides command, described in Finding which package owns a file
8.2.4. Installing Packages
Installing Individual Packages
yum install package_name
yum install package_nameyum install package_name package_name
yum install package_name package_namei686, type:
yum install sqlite.i686
~]# yum install sqlite.i686yum install perl-Crypt-\*
~]# yum install perl-Crypt-\*yum install. If you know the name of the binary you want to install, but not its package name, you can give yum install the path name:
yum install /usr/sbin/named
~]# yum install /usr/sbin/namedyum then searches through its package lists, finds the package which provides /usr/sbin/named, if any, and prompts you as to whether you want to install it.
Note
named binary, but you do not know in which bin or sbin directory is the file installed, use the yum provides command with a glob expression:
yum provides "*/file_name" is a common and useful trick to find the package(s) that contain file_name.
Installing a Package Group
yum grouplist -v command lists the names of all package groups, and, next to each of them, their groupid in parentheses. The groupid is always the term in the last pair of parentheses, such as kde-desktop in the following example:
groupinstall:
yum groupinstall group_name
yum groupinstall group_nameyum groupinstall groupid
yum groupinstall groupidinstall command if you prepend it with an @-symbol (which tells yum that you want to perform a groupinstall):
yum install @group
yum install @groupKDE Desktop group:
yum groupinstall "KDE Desktop" yum groupinstall kde-desktop yum install @kde-desktop
~]# yum groupinstall "KDE Desktop"
~]# yum groupinstall kde-desktop
~]# yum install @kde-desktop8.2.5. Removing Packages
Removing Individual Packages
root:
yum remove package_name
yum remove package_nameyum remove totem rhythmbox sound-juicer
~]# yum remove totem rhythmbox sound-juicerinstall, remove can take these arguments:
- package names
- glob expressions
- file lists
- package provides
Warning
Removing a Package Group
install syntax:
yum groupremove group
yum groupremove groupyum remove @group
yum remove @groupKDE Desktop group:
yum groupremove "KDE Desktop" yum groupremove kde-desktop yum remove @kde-desktop
~]# yum groupremove "KDE Desktop"
~]# yum groupremove kde-desktop
~]# yum remove @kde-desktopImportant
yum to remove only those packages which are not required by any other packages or groups by adding the groupremove_leaf_only=1 directive to the [main] section of the /etc/yum.conf configuration file. For more information on this directive, see Section 8.4.1, “Setting [main] Options”.
8.3. Working with Transaction History
yum history command allows users to review information about a timeline of Yum transactions, the dates and times they occurred, the number of packages affected, whether transactions succeeded or were aborted, and if the RPM database was changed between transactions. Additionally, this command can be used to undo or redo certain transactions.
8.3.1. Listing Transactions
root, either run yum history with no additional arguments, or type the following at a shell prompt:
yum history list
yum history listall keyword:
yum history list all
yum history list allyum history list start_id..end_id
yum history list start_id..end_idyum history list glob_expression
yum history list glob_expressionyum history list command produce tabular output with each row consisting of the following columns:
ID— an integer value that identifies a particular transaction.Login user— the name of the user whose login session was used to initiate a transaction. This information is typically presented in theFull Name <username>form. For transactions that were not issued by a user (such as an automatic system update),System <unset>is used instead.Date and time— the date and time when a transaction was issued.Action(s)— a list of actions that were performed during a transaction as described in Table 8.1, “Possible values of the Action(s) field”.Altered— the number of packages that were affected by a transaction, possibly followed by additional information as described in Table 8.2, “Possible values of the Altered field”.
| Action | Abbreviation | Description |
|---|---|---|
Downgrade | D | At least one package has been downgraded to an older version. |
Erase | E | At least one package has been removed. |
Install | I | At least one new package has been installed. |
Obsoleting | O | At least one package has been marked as obsolete. |
Reinstall | R | At least one package has been reinstalled. |
Update | U | At least one package has been updated to a newer version. |
| Symbol | Description |
|---|---|
< | Before the transaction finished, the rpmdb database was changed outside Yum. |
> | After the transaction finished, the rpmdb database was changed outside Yum. |
* | The transaction failed to finish. |
# | The transaction finished successfully, but yum returned a non-zero exit code. |
E | The transaction finished successfully, but an error or a warning was displayed. |
P | The transaction finished successfully, but problems already existed in the rpmdb database. |
s | The transaction finished successfully, but the --skip-broken command-line option was used and certain packages were skipped. |
root:
yum history summary
yum history summaryyum history summary start_id..end_id
yum history summary start_id..end_idyum history list command, you can also display a summary of transactions regarding a certain package or packages by supplying a package name or a glob expression:
yum history summary glob_expression
yum history summary glob_expressionyum history summary command produce simplified tabular output similar to the output of yum history list.
yum history list and yum history summary are oriented towards transactions, and although they allow you to display only transactions related to a given package or packages, they lack important details, such as package versions. To list transactions from the perspective of a package, run the following command as root:
yum history package-list glob_expression
yum history package-list glob_expression8.3.2. Examining Transactions
root, use the yum history summary command in the following form:
yum history summary id
yum history summary idroot:
yum history info id
yum history info idyum automatically uses the last transaction. Note that when specifying more than one transaction, you can also use a range:
yum history info start_id..end_id
yum history info start_id..end_idroot:
yum history addon-info id
yum history addon-info idyum history info, when no id is provided, yum automatically uses the latest transaction. Another way to see the latest transaction is to use the last keyword:
yum history addon-info last
yum history addon-info lastyum history addon-info command would provide the following output:
config-main— global Yum options that were in use during the transaction. See Section 8.4.1, “Setting [main] Options” for information on how to change global options.config-repos— options for individual Yum repositories. See Section 8.4.2, “Setting [repository] Options” for information on how to change options for individual repositories.saved_tx— the data that can be used by theyum load-transactioncommand in order to repeat the transaction on another machine (see below).
root:
yum history addon-info id information
yum history addon-info id information8.3.3. Reverting and Repeating Transactions
yum history command provides means to revert or repeat a selected transaction. To revert a transaction, type the following at a shell prompt as root:
yum history undo id
yum history undo idroot, run the following command:
yum history redo id
yum history redo idlast keyword to undo or repeat the latest transaction.
yum history undo and yum history redo commands only revert or repeat the steps that were performed during a transaction. If the transaction installed a new package, the yum history undo command will uninstall it, and if the transaction uninstalled a package the command will again install it. This command also attempts to downgrade all updated packages to their previous version, if these older packages are still available.
root:
yum -q history addon-info id saved_tx > file_name
yum -q history addon-info id saved_tx > file_nameroot:
yum load-transaction file_name
yum load-transaction file_namerpmdb version stored in the file must be identical to the version on the target system. You can verify the rpmdb version by using the yum version nogroups command.
8.3.4. Completing Transactions
root:
yum-complete-transaction
yum-complete-transaction/var/lib/yum/transaction-all and /var/lib/yum/transaction-done files. If there are more unfinished transactions, yum-complete-transaction attempts to complete the most recent one first.
--cleanup-only option:
yum-complete-transaction --cleanup-only
yum-complete-transaction --cleanup-only8.3.5. Starting New Transaction History
root:
yum history new
yum history new/var/lib/yum/history/ directory. The old transaction history will be kept, but will not be accessible as long as a newer database file is present in the directory.
8.4. Configuring Yum and Yum Repositories
yum and related utilities is located at /etc/yum.conf. This file contains one mandatory [main] section, which allows you to set Yum options that have global effect, and can also contain one or more [repository] sections, which allow you to set repository-specific options. However, it is recommended to define individual repositories in new or existing .repo files in the /etc/yum.repos.d/ directory. The values you define in individual [repository] sections of the /etc/yum.conf file override values set in the [main] section.
- set global Yum options by editing the
[main]section of the/etc/yum.confconfiguration file; - set options for individual repositories by editing the
[repository]sections in/etc/yum.confand.repofiles in the/etc/yum.repos.d/directory; - use Yum variables in
/etc/yum.confand files in the/etc/yum.repos.d/directory so that dynamic version and architecture values are handled correctly; - add, enable, and disable Yum repositories on the command line; and,
- set up your own custom Yum repository.
8.4.1. Setting [main] Options
/etc/yum.conf configuration file contains exactly one [main] section, and while some of the key-value pairs in this section affect how yum operates, others affect how Yum treats repositories. You can add many additional options under the [main] section heading in /etc/yum.conf.
/etc/yum.conf configuration file can look like this:
[main] section:
assumeyes=value- where value is one of:
0—yumshould prompt for confirmation of critical actions it performs. This is the default.1— Do not prompt for confirmation of criticalyumactions. Ifassumeyes=1is set,yumbehaves in the same way that the command-line option-ydoes. cachedir=directory- where directory is an absolute path to the directory where Yum should store its cache and database files. By default, Yum's cache directory is
/var/cache/yum/$basearch/$releasever.See Section 8.4.3, “Using Yum Variables” for descriptions of the$basearchand$releaseverYum variables. debuglevel=value- where value is an integer between
1and10. Setting a higherdebuglevelvalue causesyumto display more detailed debugging output.debuglevel=0disables debugging output, whiledebuglevel=2is the default. exactarch=value- where value is one of:
0— Do not take into account the exact architecture when updating packages.1— Consider the exact architecture when updating packages. With this setting,yumwill not install an i686 package to update an i386 package already installed on the system. This is the default. exclude=package_name [more_package_names]- This option allows you to exclude packages by keyword during installation/updates. Listing multiple packages for exclusion can be accomplished by quoting a space-delimited list of packages. Shell globs using wildcards (for example,
*and?) are allowed. gpgcheck=value- where value is one of:
0— Disable GPG signature-checking on packages in all repositories, including local package installation.1— Enable GPG signature-checking on all packages in all repositories, including local package installation.gpgcheck=1is the default, and thus all packages' signatures are checked.If this option is set in the[main]section of the/etc/yum.conffile, it sets the GPG-checking rule for all repositories. However, you can also setgpgcheck=valuefor individual repositories instead; that is, you can enable GPG-checking on one repository while disabling it on another. Settinggpgcheck=valuefor an individual repository in its corresponding.repofile overrides the default if it is present in/etc/yum.conf.For more information on GPG signature-checking, see Section B.3, “Checking a Package's Signature”. groupremove_leaf_only=value- where value is one of:
0—yumshould not check the dependencies of each package when removing a package group. With this setting,yumremoves all packages in a package group, regardless of whether those packages are required by other packages or groups.groupremove_leaf_only=0is the default.1—yumshould check the dependencies of each package when removing a package group, and remove only those packages which are not required by any other package or group.For more information on removing packages, see Intelligent package group removal. installonlypkgs=space separated list of packages- Here you can provide a space-separated list of packages which
yumcan install, but will never update. See the yum.conf(5) manual page for the list of packages which are install-only by default.If you add theinstallonlypkgsdirective to/etc/yum.conf, you should ensure that you list all of the packages that should be install-only, including any of those listed under theinstallonlypkgssection of yum.conf(5). In particular, kernel packages should always be listed ininstallonlypkgs(as they are by default), andinstallonly_limitshould always be set to a value greater than2so that a backup kernel is always available in case the default one fails to boot. installonly_limit=value- where value is an integer representing the maximum number of versions that can be installed simultaneously for any single package listed in the
installonlypkgsdirective.The defaults for theinstallonlypkgsdirective include several different kernel packages, so be aware that changing the value ofinstallonly_limitwill also affect the maximum number of installed versions of any single kernel package. The default value listed in/etc/yum.confisinstallonly_limit=3, and it is not recommended to decrease this value, particularly below2. keepcache=value- where value is one of:
0— Do not retain the cache of headers and packages after a successful installation. This is the default.1— Retain the cache after a successful installation. logfile=file_name- where file_name is an absolute path to the file in which
yumshould write its logging output. By default,yumlogs to/var/log/yum.log. multilib_policy=value- where value is one of:
best— install the best-choice architecture for this system. For example, settingmultilib_policy=beston an AMD64 system causesyumto install 64-bit versions of all packages.all— always install every possible architecture for every package. For example, withmultilib_policyset toallon an AMD64 system,yumwould install both the i686 and AMD64 versions of a package, if both were available. obsoletes=value- where value is one of:
0— Disableyum's obsoletes processing logic when performing updates.1— Enableyum's obsoletes processing logic when performing updates. When one package declares in its spec file that it obsoletes another package, the latter package will be replaced by the former package when the former package is installed. Obsoletes are declared, for example, when a package is renamed.obsoletes=1the default. plugins=value- where value is one of:
0— Disable all Yum plug-ins globally.Important
Disabling all plug-ins is not advised because certain plug-ins provide importantYumservices. In particular, rhnplugin provides support forRHN Classic, and product-id and subscription-manager plug-ins provide support for the certificate-basedContent Delivery Network(CDN). Disabling plug-ins globally is provided as a convenience option, and is generally only recommended when diagnosing a potential problem withYum.1— Enable all Yum plug-ins globally. Withplugins=1, you can still disable a specific Yum plug-in by settingenabled=0in that plug-in's configuration file.For more information about various Yum plug-ins, see Section 8.5, “Yum Plug-ins”. For further information on controlling plug-ins, see Section 8.5.1, “Enabling, Configuring, and Disabling Yum Plug-ins”. reposdir=directory- where directory is an absolute path to the directory where
.repofiles are located. All.repofiles contain repository information (similar to the[repository]sections of/etc/yum.conf).yumcollects all repository information from.repofiles and the[repository]section of the/etc/yum.conffile to create a master list of repositories to use for transactions. Ifreposdiris not set,yumuses the default directory/etc/yum.repos.d/. retries=value- where value is an integer
0or greater. This value sets the number of timesyumshould attempt to retrieve a file before returning an error. Setting this to0makesyumretry forever. The default value is10.
[main] options, see the [main] OPTIONS section of the yum.conf(5) manual page.
8.4.2. Setting [repository] Options
[repository] sections, where repository is a unique repository ID such as my_personal_repo (spaces are not permitted), allow you to define individual Yum repositories. To avoid conflicts, custom repositories should not use names used by Red Hat repositories.
[repository] section takes:
[repository] name=repository_name baseurl=repository_url
[repository]
name=repository_name
baseurl=repository_url[repository] section must contain the following directives:
name=repository_name- where repository_name is a human-readable string describing the repository.
baseurl=repository_url- where repository_url is a URL to the directory where the
repodatadirectory of a repository is located:- If the repository is available over HTTP, use:
http://path/to/repo - If the repository is available over FTP, use:
ftp://path/to/repo - If the repository is local to the machine, use:
file:///path/to/local/repo - If a specific online repository requires basic HTTP authentication, you can specify your user name and password by prepending it to the URL as
username:password@link. For example, if a repository on http://www.example.com/repo/ requires a user name of “user” and a password of “password”, then thebaseurllink could be specified ashttp://.user:password@www.example.com/repo/
Usually this URL is an HTTP link, such as:baseurl=http://path/to/repo/releases/$releasever/server/$basearch/os/
baseurl=http://path/to/repo/releases/$releasever/server/$basearch/os/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that Yum always expands the$releasever,$arch, and$basearchvariables in URLs. For more information about Yum variables, see Section 8.4.3, “Using Yum Variables”.
[repository] directive is the following:
enabled=value- where value is one of:
0— Do not include this repository as a package source when performing updates and installs. This is an easy way of quickly turning repositories on and off, which is useful when you desire a single package from a repository that you do not want to enable for updates or installs.1— Include this repository as a package source.Turning repositories on and off can also be performed by passing either the--enablerepo=repo_nameor--disablerepo=repo_nameoption toyum, or through the Add/Remove Software window of the PackageKit utility.
[repository] options exist. For a complete list, see the [repository] OPTIONS section of the yum.conf(5) manual page.
Example 8.6. A sample /etc/yum.repos.d/redhat.repo file
/etc/yum.repos.d/redhat.repo file:
8.4.3. Using Yum Variables
yum commands and in all Yum configuration files (that is, /etc/yum.conf and all .repo files in the /etc/yum.repos.d/ directory):
$releasever- You can use this variable to reference the release version of Red Hat Enterprise Linux. Yum obtains the value of
$releaseverfrom thedistroverpkg=valueline in the/etc/yum.confconfiguration file. If there is no such line in/etc/yum.conf, thenyuminfers the correct value by deriving the version number from the redhat-release-server package. The value of$releasevertypically consists of the major release number and the variant of Red Hat Enterprise Linux, for example6Client, or6Server. $arch- You can use this variable to refer to the system's CPU architecture as returned when calling Python's
os.uname()function. Valid values for$archincludei686andx86_64. $basearch- You can use
$basearchto reference the base architecture of the system. For example, i686 machines have a base architecture ofi386, and AMD64 and Intel 64 machines have a base architecture ofx86_64. $YUM0-9- These ten variables are each replaced with the value of any shell environment variables with the same name. If one of these variables is referenced (in
/etc/yum.conffor example) and a shell environment variable with the same name does not exist, then the configuration file variable is not replaced.
$” sign) in the /etc/yum/vars/ directory, and add the desired value on its first line.
$osname, create a new file with “Red Hat Enterprise Linux” on the first line and save it as /etc/yum/vars/osname:
echo "Red Hat Enterprise Linux" > /etc/yum/vars/osname
~]# echo "Red Hat Enterprise Linux" > /etc/yum/vars/osname.repo files:
name=$osname $releasever
name=$osname $releasever8.4.4. Viewing the Current Configuration
[main] section of the /etc/yum.conf file), run the yum-config-manager with no command-line options:
yum-config-manager
yum-config-manageryum-config-manager section
yum-config-manager sectionyum-config-manager glob_expression
yum-config-manager glob_expression8.4.5. Adding, Enabling, and Disabling a Yum Repository
yum-config-manager command.
Important
Red Hat Network, the Red Hat Subscription Manager tools are used to manage repositories in the /etc/yum.repos.d/redhat.repo file. See Chapter 6, Registering the System and Managing Subscriptions for more information how to register a system with Red Hat Network and use the Red Hat Subscription Manager tools to manage subscriptions.
Adding a Yum Repository
[repository] section to the /etc/yum.conf file, or to a .repo file in the /etc/yum.repos.d/ directory. All files with the .repo file extension in this directory are read by yum, and it is recommended to define your repositories here instead of in /etc/yum.conf.
Warning
.repo file. To add such a repository to your system and enable it, run the following command as root:
yum-config-manager --add-repo repository_url
yum-config-manager --add-repo repository_url.repo file. For example, to add a repository located at http://www.example.com/example.repo, type the following at a shell prompt:
Enabling a Yum Repository
root:
yum-config-manager --enable repository
yum-config-manager --enable repositoryyum repolist all to list available repository IDs). Alternatively, you can use a glob expression to enable all matching repositories:
yum-config-manager --enable glob_expression
yum-config-manager --enable glob_expression[example], [example-debuginfo], and [example-source]sections, type:
yum-config-manager --enable command displays the current repository configuration.
Disabling a Yum Repository
root:
yum-config-manager --disable repository
yum-config-manager --disable repositoryyum repolist all to list available repository IDs). Similarly to yum-config-manager --enable, you can use a glob expression to disable all matching repositories at the same time:
yum-config-manager --disable glob_expression
yum-config-manager --disable glob_expressionyum-config-manager --disable command displays the current configuration.
8.4.6. Creating a Yum Repository
- Install the createrepo package. To do so, type the following at a shell prompt as
root:yum install createrepo
yum install createrepoCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy all packages that you want to have in your repository into one directory, such as
/mnt/local_repo/. - Change to this directory and run the following command:
createrepo --database /mnt/local_repo
createrepo --database /mnt/local_repoCopy to Clipboard Copied! Toggle word wrap Toggle overflow This creates the necessary metadata for your Yum repository, as well as the sqlite database for speeding upyumoperations.Important
Compared to Red Hat Enterprise Linux 5, RPM packages for Red Hat Enterprise Linux 6 are compressed with the XZ lossless data compression format and can be signed with newer hash algorithms like SHA-256. Consequently, it is not recommended to use thecreaterepocommand on Red Hat Enterprise Linux 5 to create the package metadata for Red Hat Enterprise Linux 6.
8.4.7. Working with Yum Cache
/var/cache/yum/$basearch/$releasever/ directory, where $basearch and $releasever are Yum variables referring to base architecture of the system and the release version of Red Hat Enterprise Linux. Each configured repository has one subdirectory. For example, the directory /var/cache/yum/$basearch/$releasever/development/packages/ holds packages downloaded from the development repository. You can find the values for the $basearch and $releasever variables in the output of the yum version command.
cachedir option in the [main] section of the /etc/yum.conf configuration file. See Section 8.4, “Configuring Yum and Yum Repositories” for more information on configuring yum.
Enabling the Caches
[main] section of /etc/yum.conf.
keepcache = 1
keepcache = 1yum makecache
yum makecachemetadata-expire setting in /etc/yum.conf.
Using yum in Cache-only Mode
-C or --cacheonly command-line option. With this option, yum proceeds without checking any network repositories, and uses only cached files. In this mode, yum may only install packages that have been downloaded and cached by a previous operation.
yum -C list gstreamer*
yum -C list gstreamer*Clearing the yum Caches
/var/cache/yum/ directory. If you remove a package from the cache, you do not affect the copy of the software installed on your system. To remove all entries for currently enabled repositories from the cache, type the following as a root:
yum clean all
yum clean allyum in clean mode depending on the type of cached data you want to remove. See Table 8.3, “Available yum clean options” for a complete list of available configuration options.
| Option | Description |
|---|---|
| expire-cache | eliminates time records of the metadata and mirrorlists download for each repository. This forces yum to revalidate the cache for each repository the next time it is used. |
| packages | eliminates any cached packages from the system |
| headers | eliminates all header files that previous versions of yum used for dependency resolution |
| metadata | eliminates all files that yum uses to determine the remote availability of packages. These metadata are downloaded again the next time yum is run. |
| dbcache | eliminates the sqlite cache used for faster access to metadata. Using this option will force yum to download the sqlite metadata the next time it is run. This does not apply for repositories that contain only .xml data, in that case, sqlite data are deleted but without subsequent download |
| rpmdb | eliminates any cached data from the local rpmdb |
| plugins | enabled plugins are forced to eliminate their cached data |
| all | removes all of the above |
expire-cache option is most preferred from the above list. In many cases, it is a sufficient and much faster replacement for clean all.
8.4.8. Adding the Optional and Supplementary Repositories
8.5. Yum Plug-ins
yum command. For example:
yum info yum Loaded plugins: product-id, refresh-packagekit, subscription-manager [output truncated]
~]# yum info yum
Loaded plugins: product-id, refresh-packagekit, subscription-manager
[output truncated]Loaded plugins are the names you can provide to the --disableplugins=plugin_name option.
8.5.1. Enabling, Configuring, and Disabling Yum Plug-ins
plugins= is present in the [main] section of /etc/yum.conf, and that its value is 1:
plugins=1
plugins=1plugins=0.
Important
Yum services. In particular, rhnplugin provides support for RHN Classic, and product-id and subscription-manager plug-ins provide support for the certificate-based Content Delivery Network (CDN). Disabling plug-ins globally is provided as a convenience option, and is generally only recommended when diagnosing a potential problem with Yum.
/etc/yum/pluginconf.d/ directory. You can set plug-in specific options in these files. For example, here is the refresh-packagekit plug-in's refresh-packagekit.conf configuration file:
[main] enabled=1
[main]
enabled=1[main] section (similar to Yum's /etc/yum.conf file) in which there is (or you can place if it is missing) an enabled= option that controls whether the plug-in is enabled when you run yum commands.
enabled=0 in /etc/yum.conf, then all plug-ins are disabled regardless of whether they are enabled in their individual configuration files.
yum command, use the --noplugins option.
yum command, add the --disableplugin=plugin_name option to the command. For example, to disable the presto plug-in while updating a system, type:
yum update --disableplugin=presto
~]# yum update --disableplugin=presto--disableplugin= option are the same names listed after the Loaded plugins line in the output of any yum command. You can disable multiple plug-ins by separating their names with commas. In addition, you can match multiple plug-in names or shorten long ones by using glob expressions:
yum update --disableplugin=presto,refresh-pack*
~]# yum update --disableplugin=presto,refresh-pack*8.5.2. Installing Additional Yum Plug-ins
yum-plugin-plugin_name package-naming convention, but not always: the package which provides the presto plug-in is named yum-presto, for example. You can install a Yum plug-in in the same way you install other packages. For instance, to install the security plug-in, type the following at a shell prompt:
yum install yum-plugin-security
~]# yum install yum-plugin-security8.5.3. Plug-in Descriptions
- search-disabled-repos (subscription-manager)
- The search-disabled-repos plug-in allows you to temporarily or permanently enable disabled repositories to help resolve dependencies. With this plug-in enabled, when Yum fails to install a package due to failed dependency resolution, it offers to temporarily enable disabled repositories and try again. If the installation succeeds, Yum also offers to enable the used repositories permanently. Note that the plug-in works only with the repositories that are managed by subscription-manager and not with custom repositories.
Important
Ifyumis executed with the--assumeyesor-yoption, or if theassumeyesdirective is enabled in/etc/yum.conf, the plug-in enables disabled repositories, both temporarily and permanently, without prompting for confirmation. This may lead to problems, for example, enabling repositories that you do not want enabled.To configure the search-disabled-repos plug-in, edit the configuration file located in/etc/yum/pluginconf.d/search-disabled-repos.conf. For the list of directives you can use in the[main]section, see the table below.Expand Table 8.4. Supported search-disabled-repos.conf directives Directive Description enabled=valueAllows you to enable or disable the plug-in. The value must be either 1(enabled), or0(disabled). The plug-in is enabled by default.notify_only=valueAllows you to restrict the behavior of the plug-in to notifications only. The value must be either 1(notify only without modifying the behavior of Yum), or0(modify the behavior of Yum). By default the plug-in only notifies the user.ignored_repos=repositoriesAllows you to specify the repositories that will not be enabled by the plug-in. - kabi (kabi-yum-plugins)
- The kabi plug-in checks whether a driver update package conforms with official Red Hat kernel Application Binary Interface (kABI). With this plug-in enabled, when a user attempts to install a package that uses kernel symbols which are not on a whitelist, a warning message is written to the system log. Additionally, configuring the plug-in to run in enforcing mode prevents such packages from being installed at all.To configure the kabi plug-in, edit the configuration file located in
/etc/yum/pluginconf.d/kabi.conf. See Table 8.5, “Supportedkabi.confdirectives” for a list of directives that can be used in the[main]section.Expand Table 8.5. Supported kabi.conf directives Directive Description enabled=valueAllows you to enable or disable the plug-in. The value must be either 1(enabled), or0(disabled). When installed, the plug-in is enabled by default.whitelists=directoryAllows you to specify the directory in which the files with supported kernel symbols are located. By default, the kabi plug-in uses files provided by the kernel-abi-whitelists package (that is, the /lib/modules/kabi/directory).enforce=valueAllows you to enable or disable enforcing mode. The value must be either 1(enabled), or0(disabled). By default, this option is commented out and the kabi plug-in only displays a warning message. - presto (yum-presto)
- The presto plug-in adds support to Yum for downloading delta RPM packages, during updates, from repositories which have presto metadata enabled. Delta RPMs contain only the differences between the version of the package installed on the client requesting the RPM package and the updated version in the repository.Downloading a delta RPM is much quicker than downloading the entire updated package, and can speed up updates considerably. Once the delta RPMs are downloaded, they must be rebuilt to apply the difference to the currently-installed package and thus create the full, updated package. This process takes CPU time on the installing machine. Using delta RPMs is therefore a compromise between time-to-download, which depends on the network connection, and time-to-rebuild, which is CPU-bound. Using the presto plug-in is recommended for fast machines and systems with slower network connections, while slower machines on very fast connections benefit more from downloading normal RPM packages, that is, by disabling presto.
- product-id (subscription-manager)
- The product-id plug-in manages product identity certificates for products installed from the Content Delivery Network. The product-id plug-in is installed by default.
- refresh-packagekit (PackageKit-yum-plugin)
- The refresh-packagekit plug-in updates metadata for PackageKit whenever
yumis run. The refresh-packagekit plug-in is installed by default. - rhnplugin (yum-rhn-plugin)
- The rhnplugin provides support for connecting to
RHN Classic. This allows systems registered withRHN Classicto update and install packages from this system. Note thatRHN Classicis only provided for older Red Hat Enterprise Linux systems (that is, Red Hat Enterprise Linux 4.x, Red Hat Enterprise Linux 5.x, and Satellite 5.x) in order to migrate them over to Red Hat Enterprise Linux 6. The rhnplugin is installed by default.See the rhnplugin(8) manual page for more information about the plug-in. - security (yum-plugin-security)
- Discovering information about and applying security updates easily and often is important to all system administrators. For this reason Yum provides the security plug-in, which extends
yumwith a set of highly-useful security-related commands, subcommands and options.You can check for security-related updates as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can then use eitheryum update --securityoryum update-minimal --securityto update those packages which are affected by security advisories. Both of these commands update all packages on the system for which a security advisory has been issued.yum update-minimal --securityupdates them to the latest packages which were released as part of a security advisory, whileyum update --securitywill update all packages affected by a security advisory to the latest version of that package available.In other words, if:- the kernel-2.6.30.8-16 package is installed on your system;
- the kernel-2.6.30.8-32 package was released as a security update;
- then kernel-2.6.30.8-64 was released as a bug fix update,
...thenyum update-minimal --securitywill update you to kernel-2.6.30.8-32, andyum update --securitywill update you to kernel-2.6.30.8-64. Conservative system administrators probably want to useupdate-minimalto reduce the risk incurred by updating packages as much as possible.See the yum-security(8) manual page for usage details and further explanation of the enhancements the security plug-in adds toyum. - subscription-manager (subscription-manager)
- The subscription-manager plug-in provides support for connecting to
Red Hat Network. This allows systems registered withRed Hat Networkto update and install packages from the certificate-based Content Delivery Network. The subscription-manager plug-in is installed by default.See Chapter 6, Registering the System and Managing Subscriptions for more information how to manage product subscriptions and entitlements. - yum-downloadonly (yum-plugin-downloadonly)
- The yum-downloadonly plug-in provides the
--downloadonlycommand-line option which can be used to download packages from Red Hat Network or a configured Yum repository without installing the packages.To install the package, follow the instructions in Section 8.5.2, “Installing Additional Yum Plug-ins”. After the installation, see the contents of the/etc/yum/pluginconf.d/downloadonly.conffile to ensure that the plug-in is enabled:~]$ cat /etc/yum/pluginconf.d/downloadonly.conf [main] enabled=1
~]$ cat /etc/yum/pluginconf.d/downloadonly.conf [main] enabled=1Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the following example, theyum install --downloadonlycommand is run to download the latest version of the httpd package, without installing it:Copy to Clipboard Copied! Toggle word wrap Toggle overflow By default, packages downloaded using the--downloadonlyoption are saved in one of the subdirectories of the/var/cache/yumdirectory, depending on the Red Hat Enterprise Linux variant and architecture.If you want to specify an alternate directory to save the packages, pass the--downloaddiroption along with--downloadonly:yum install --downloadonly --downloaddir=/path/to/directory httpd
~]# yum install --downloadonly --downloaddir=/path/to/directory httpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
As an alternative to the yum-downloadonly plugin — to download packages without installing them — you can use the yumdownloader utility that is provided by the yum-utils package.
8.6. Additional Resources
Installed Documentation
yum(8) — The manual page for theyumcommand-line utility provides a complete list of supported options and commands.yumdb(8) — The manual page for theyumdbcommand-line utility documents how to use this tool to query and, if necessary, alter the yum database.yum.conf(5) — The manual page namedyum.confdocuments available yum configuration options.yum-utils(1) — The manual page namedyum-utilslists and briefly describes additional utilities for managing yum configuration, manipulating repositories, and working with yum database.
Online Resources
- Yum Guides — The Yum Guides page on the project home page provides links to further documentation.
- Red Hat Access Labs — The Red Hat Access Labs includes a “Yum Repository Configuration Helper”.
See Also
- Chapter 4, Gaining Privileges documents how to gain administrative privileges by using the
suandsudocommands. - Appendix B, RPM describes the RPM Package Manager (RPM), the packaging system used by Red Hat Enterprise Linux.
Chapter 9. PackageKit
9.1. Updating Packages with Software Update
Figure 9.1. PackageKit's icon in the Notification Area
gpk-update-viewer command at the shell prompt. In the Software Updates window, all available updates are listed along with the names of the packages being updated (minus the .rpm suffix, but including the CPU architecture), a short summary of the package, and, usually, short descriptions of the changes the update provides. Any updates you do not want to install can be de-selected here by unchecking the check box corresponding to the update.
Figure 9.2. Installing updates with Software Update
Setting the Update-Checking Interval
Figure 9.3. Setting PackageKit's update-checking interval
9.2. Using Add/Remove Software
gpk-application command at the shell prompt.
Figure 9.4. PackageKit's Add/Remove Software window
9.2.1. Refreshing Software Sources (Yum Repositories)
name=<My Repository Name> field of all [repository] sections in the /etc/yum.conf configuration file, and in all repository.repo files in the /etc/yum.repos.d/ directory.
enabled=<1 or 0> field in [repository] sections. When you click the check box, PackageKit inserts the enabled=<1 or 0> line into the correct [repository] section if it does not exist, or changes the value if it does. This means that enabling or disabling a repository through the Software Sources window causes that change to persist after closing the window or rebooting the system.
Note
9.2.2. Finding Packages with Filters
Figure 9.5. Filtering out already-installed packages
<package_name>-devel packages we are not interested in.
Figure 9.6. Filtering out development packages from the list of Find results
- Narrows the search to either applications which provide a GUI interface () or those that do not. This filter is useful when browsing for GUI applications that perform a specific function.
- Search for packages which are considered to be free software. See the Fedora Licensing List for details on approved licenses.
- Checking the check box filters out generally-uninteresting packages that are typically only dependencies of other packages that we want. For example, checking and searching for
<package>would cause the following related packages to be filtered out of the results (if it exists):<package>-devel<package>-libs<package>-libs-devel<package>-debuginfo
- Checking filters out all older versions of the same package from the list of results, which is generally what we want. Note that this filter is often combined with the filter to search for the latest available versions of new (not installed) packages.
- Only native packages
- Checking the box on a multilib system causes PackageKit to omit listing results for packages compiled for the architecture that runs in compatibility mode. For example, enabling this filter on a 64-bit system with an AMD64 CPU would cause all packages built for the 32-bit x86 CPU architecture not to be shown in the list of results, even though those packages are able to run on an AMD64 machine. Packages which are architecture-agnostic (i.e. noarch packages such as
crontabs-1.10-32.1.el6.noarch.rpm) are never filtered out by checking . This filter has no affect on non-multilib systems, such as x86 machines.
9.2.3. Installing and Removing Packages (and Dependencies)
Figure 9.7. Viewing and installing a package with PackageKit's Add/Remove Software window
screen, a screen manager that allows you to have multiple logins on one terminal, by typing screen at a shell prompt.
Warning
Figure 9.8. Removing a package with PackageKit's Add/Remove Software window
9.2.4. Installing and Removing Package Groups
Figure 9.9. Installing the Czech Support package group
9.2.5. Viewing the Transaction Log
gpk-log command at the shell prompt.
- Date — the date on which the transaction was performed.
- Action — the action that was performed during the transaction, for example Updated packages or Installed packages.
- Details — the transaction type such as Updated, Installed, or Removed, followed by a list of affected packages.
- Username — the name of the user who performed the action.
- Application — the front end application that was used to perform the action, for example Update System.
Figure 9.10. Viewing the log of package management transactions with the Software Log Viewer
9.3. PackageKit Architecture
packagekitd daemon back end, which communicates with a package manager-specific back end that utilizes Yum to perform the actual transactions, such as installing and removing packages, etc.
| Window Title | Function | How to Open | Shell Command |
|---|---|---|---|
| Add/Remove Software | Install, remove or view package info |
From the GNOME panel: → →
| gpk-application |
| Software Update | Perform package updates |
From the GNOME panel: → →
| gpk-update-viewer |
| Software Sources | Enable and disable Yum repositories |
From Add/Remove Software: →
| gpk-repo |
| Software Log Viewer | View the transaction log |
From Add/Remove Software: →
| gpk-log |
| Software Update Preferences | Set PackageKit preferences | gpk-prefs | |
| (Notification Area Alert) | Alerts you when updates are available |
From the GNOME panel: → → , the Startup Programs tab
| gpk-update-icon |
packagekitd daemon runs outside the user session and communicates with the various graphical front ends. The packagekitd daemon[2] communicates via the DBus system message bus with another back end, which utilizes Yum's Python API to perform queries and make changes to the system. On Linux systems other than Red Hat Enterprise Linux and Fedora, packagekitd can communicate with other back ends that are able to utilize the native package manager for that system. This modular architecture provides the abstraction necessary for the graphical interfaces to work with many different package managers to perform essentially the same types of package management tasks. Learning how to use the PackageKit front ends means that you can use the same familiar graphical interface across many different Linux distributions, even when they utilize a native package manager other than Yum.
packagekitd daemon, which runs outside of the user session.
pkcon.
9.4. Additional Resources
Installed Documentation
gpk-application(1)— The manual page containing information about thegpk-applicationcommand.gpk-backend-status(1)— The manual page containing information about thegpk-backend-statuscommand.gpk-install-local-file(1)— The manual page containing information about thegpk-install-local-filecommand.gpk-install-mime-type(1)— The manual page containing information about thegpk-install-mime-typecommand.gpk-install-package-name(1)— The manual page containing information about theqpk-install-package-namecommand.gpk-install-package-name(1)— The manual page containing information about thegpk-install-package-namecommand.gpk-prefs(1)— The manual page containing information about thegpk-prefscommand.gpk-repo(1)— The manual page containing information about thegpk-repocommand.gpk-update-icon(1)— The manual page containing information about thegpk-update-iconcommand.gpk-update-viewer(1)— The manual page containing information about thegpk-update-viewercommand.pkcon(1)andpkmon(1)— The manual pages containing information about the PackageKit console client.pkgenpack(1)— The manual page containing information about the PackageKit Pack Generator.
Online Documentation
- PackageKit home page — The PackageKit home page listing detailed information about the PackageKit software suite.
- PackageKit FAQ — An informative list of Frequently Asked Questions for the PackageKit software suite.
See Also
- Chapter 8, Yum documents Yum, the Red Hat package manager.
service command and can be turned on or off permanently by using the chkconfig on or chkconfig off commands. They can typically be recognized by a “d” appended to their name, such as the packagekitd daemon. See Chapter 12, Services and Daemons for information about system services.
Part IV. Networking
Chapter 10. NetworkManager
DSL and PPPoE (Point-to-Point over Ethernet). In addition, NetworkManager allows for the configuration of network aliases, static routes, DNS information and VPN connections, as well as many connection-specific parameters. Finally, NetworkManager provides a rich API via D-Bus which allows applications to query and control network configuration and state.
system-config-network after its command-line invocation. In Red Hat Enterprise Linux 6, NetworkManager replaces the former Network Administration Tool while providing enhanced functionality, such as user-specific and mobile broadband configuration. It is also possible to configure the network in Red Hat Enterprise Linux 6 by editing interface configuration files; see Chapter 11, Network Interfaces for more information.
root:
yum install NetworkManager
~]# yum install NetworkManager10.1. The NetworkManager Daemon
root privileges and is usually configured to start up at boot time. You can determine whether the NetworkManager daemon is running by entering this command as root:
service NetworkManager status
NetworkManager (pid 1527) is running...
~]# service NetworkManager status
NetworkManager (pid 1527) is running...
service command will report NetworkManager is stopped if the NetworkManager service is not running. To start it for the current session:
service NetworkManager start
~]# service NetworkManager startchkconfig command to ensure that NetworkManager starts up every time the system boots:
chkconfig NetworkManager on
~]# chkconfig NetworkManager on10.2. Interacting with NetworkManager
Figure 10.1. NetworkManager applet states
root):
nm-applet &
~]$ nm-applet &10.2.1. Connecting to a Network
- a list of categorized networks you are currently connected to (such as Wired and Wireless);
- a list of all Available Networks that NetworkManager has detected;
- options for connecting to any configured Virtual Private Networks (VPNs); and,
- options for connecting to hidden or new wireless networks.
Figure 10.2. The NetworkManager applet's left-click menu, showing all available and connected-to networks
10.2.2. Configuring New and Editing Existing Connections
nm-connection-editor &
~]$ nm-connection-editor &Figure 10.4. Configure networks using the Network Connections window
- wired Ethernet connections, proceed to Section 10.3.1, “Establishing a Wired (Ethernet) Connection”;
- wireless connections, proceed to Section 10.3.2, “Establishing a Wireless Connection”; or,
- mobile broadband connections, proceed to Section 10.3.3, “Establishing a Mobile Broadband Connection”; or,
- VPN connections, proceed to Section 10.3.4, “Establishing a VPN Connection”.
10.2.3. Connecting to a Network Automatically
Procedure 10.1. Configuring NetworkManager to Connect to a Network Automatically When Detected
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Click the arrow head if necessary to reveal the list of connections.
- Select the specific connection that you want to configure and click .
- Check Connect automatically to cause NetworkManager to auto-connect to the connection whenever NetworkManager detects that it is available. Uncheck the check box if you do not want NetworkManager to connect automatically. If the box is unchecked, you will have to select that connection manually in the NetworkManager applet's left-click menu to cause it to connect.
10.2.4. User and System Connections
root privileges to create and modify system connections. NetworkManager's default policy enables users to create and modify user connections, but requires them to have root privileges to add, modify or delete system connections.
/etc/sysconfig/network-scripts/ directory (mainly in ifcfg-<network_type> interface configuration files), user connection settings are stored in the GConf configuration database and the GNOME keyring, and are only available during login sessions for the user who created them. Thus, logging out of the desktop session causes user-specific connections to become unavailable.
Note
root users on the system cannot view or access these connections in any way.
/etc/sysconfig/network-scripts/ directory, and to delete the GConf settings from the user's session. Conversely, converting a system to a user-specific connection causes NetworkManager to remove the system-wide configuration files and create the corresponding GConf/GNOME keyring settings.
Figure 10.5. The Available to all users check box controls whether connections are user-specific or system-wide
Procedure 10.2. Changing a Connection to be User-Specific instead of System-Wide, or Vice-Versa
Note
root privileges on the system in order to change whether a connection is user-specific or system-wide.
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- If needed, select the arrow head (on the left hand side) to hide and reveal the types of available network connections.
- Select the specific connection that you want to configure and click .
- Check the Available to all users check box to ask NetworkManager to make the connection a system-wide connection. Depending on system policy, you may then be prompted for the
rootpassword by the PolicyKit application. If so, enter therootpassword to finalize the change.Conversely, uncheck the Available to all users check box to make the connection user-specific.
10.3. Establishing Connections
10.3.1. Establishing a Wired (Ethernet) Connection
nm-connection-editor &
~]$ nm-connection-editor &Figure 10.6. The Network Connections window showing the newly created System eth0 connection
Figure 10.7. Selecting a new connection type from the "Choose a Connection Type" list
Note
Figure 10.8. Editing the newly created Wired connection System eth0
Configuring the Connection Name, Auto-Connect Behavior, and Availability Settings
- Connection name — Enter a descriptive name for your network connection. This name will be used to list this connection in the Wired section of the Network Connections window.
- Connect automatically — Check this box if you want NetworkManager to auto-connect to this connection when it is available. See Section 10.2.3, “Connecting to a Network Automatically” for more information.
- Available to all users — Check this box to create a connection available to all users on the system. Changing this setting may require
rootprivileges. See Section 10.2.4, “User and System Connections” for details.
Configuring the Wired Tab
automatic. These defaults will suffice unless you are associating a wired connection with a second or specific NIC, or performing advanced networking. In such cases, see the following descriptions:
- MAC Address
- Network hardware such as a Network Interface Card (NIC) has a unique MAC address (Media Access Control; also known as a hardware address) that identifies it to the system. Running the
ip addrcommand will show the MAC address associated with each interface. For example, in the followingip addroutput, the MAC address for the eth0 interface (which is52:54:00:26:9e:f1) immediately follows thelink/etherkeyword:Copy to Clipboard Copied! Toggle word wrap Toggle overflow A single system can have one or more NICs installed on it. The MAC address field therefore allows you to associate a specific NIC with a specific connection (or connections). As mentioned, you can determine the MAC address using theip addrcommand, and then copy and paste that value into the MAC address text-entry field.The cloned MAC address field is mostly for use in such situations were a network service has been restricted to a specific MAC address and you need to emulate that MAC address. - MTU
- The MTU (Maximum Transmission Unit) value represents the size in bytes of the largest packet that the connection will use to transmit. This value defaults to
1500when using IPv4, or a variable number1280or higher for IPv6, and does not generally need to be specified or changed.
Saving Your New (or Modified) Connection and Making Further Configurations
- port-based Network Access Control (PNAC), click the 802.1X Security tab and proceed to Section 10.3.9.1, “Configuring 802.1X Security”;
- IPv4 settings for the connection, click the IPv4 Settings tab and proceed to Section 10.3.9.4, “Configuring IPv4 Settings”; or,
- IPv6 settings for the connection, click the IPv6 Settings tab and proceed to Section 10.3.9.5, “Configuring IPv6 Settings”.
10.3.2. Establishing a Wireless Connection
Quickly Connecting to an Available Access Point
Figure 10.9. Authenticating to a wireless access point
Note
Figure 10.10. Applet icon indicating a wireless connection signal strength of 75%
Auto <SSID>, where SSID is the Service Set identifier of the access point.
Figure 10.11. An example of access points that have previously been connected to
Connecting to a Hidden Wireless Network
Editing a Connection, or Creating a Completely New One
Auto refer to the SSID of an access point), and clicking Edit.
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Click the button.
- Select the Wireless entry from the list.
- Click the button.
Figure 10.12. Editing the newly created Wireless connection 1
Configuring the Connection Name, Auto-Connect Behavior, and Availability Settings
- Connection name — Enter a descriptive name for your network connection. This name will be used to list this connection in the Wireless section of the Network Connections window. By default, wireless connections are named the same as the SSID of the wireless access point. You can rename the wireless connection without affecting its ability to connect, but it is recommended to retain the SSID name.
- Connect automatically — Check this box if you want NetworkManager to auto-connect to this connection when it is available. See Section 10.2.3, “Connecting to a Network Automatically” for more information.
- Available to all users — Check this box to create a connection available to all users on the system. Changing this setting may require
rootprivileges. See Section 10.2.4, “User and System Connections” for details.
Configuring the Wireless Tab
- SSID
- All access points have a Service Set identifier to identify them. However, an access point may be configured not to broadcast its SSID, in which case it is hidden, and will not show up in NetworkManager's list of Available networks. You can still connect to a wireless access point that is hiding its SSID as long as you know its SSID (and authentication secrets).For information on connecting to a hidden wireless network, see the section called “Connecting to a Hidden Wireless Network”.
- Mode
- — Set Mode to if you are connecting to a dedicated wireless access point or one built into a network device such as a router or a switch.— Set Mode to if you are creating a peer-to-peer network for two or more mobile devices to communicate directly with each other. If you use mode, referred to as Independent Basic Service Set (IBSS) in the 802.11 standard, you must ensure that the same SSID is set for all participating wireless devices, and that they are all communicating over the same channel.
- BSSID
- The Basic Service Set Identifier (BSSID) is the MAC address of the specific wireless access point you are connecting to when in Infrastructure mode. This field is blank by default, and you are able to connect to a wireless access point by SSID without having to specify its BSSID. If the BSSID is specified, it will force the system to associate to a specific access point only.For ad-hoc networks, the BSSID is generated randomly by the
mac80211subsystem when the ad-hoc network is created. It is not displayed by NetworkManager - MAC address
- Like an Ethernet Network Interface Card (NIC), a wireless adapter has a unique MAC address (Media Access Control; also known as a hardware address) that identifies it to the system. Running the
ip addrcommand will show the MAC address associated with each interface. For example, in the followingip addroutput, the MAC address for thewlan0interface (which is00:1c:bf:02:f8:70) immediately follows thelink/etherkeyword:Copy to Clipboard Copied! Toggle word wrap Toggle overflow A single system could have one or more wireless network adapters connected to it. The MAC address field therefore allows you to associate a specific wireless adapter with a specific connection (or connections). As mentioned, you can determine the MAC address using theip addrcommand, and then copy and paste that value into the MAC address text-entry field. - MTU
- The MTU (Maximum Transmission Unit) value represents the size in bytes of the largest packet that the connection will use to transmit. If set to a non-zero number, only packets of the specified size or smaller will be transmitted. Larger packets are broken up into multiple Ethernet frames. It is recommended to leave this setting on .
Saving Your New (or Modified) Connection and Making Further Configurations
- security authentication for the wireless connection, click the Wireless Security tab and proceed to Section 10.3.9.2, “Configuring Wireless Security”;
- IPv4 settings for the connection, click the IPv4 Settings tab and proceed to Section 10.3.9.4, “Configuring IPv4 Settings”; or,
- IPv6 settings for the connection, click the IPv6 Settings tab and proceed to Section 10.3.9.5, “Configuring IPv6 Settings”.
10.3.3. Establishing a Mobile Broadband Connection
- 2G — GPRS (General Packet Radio Service) or EDGE (Enhanced Data Rates for GSM Evolution)
- 3G — UMTS (Universal Mobile Telecommunications System) or HSPA (High Speed Packet Access)
Procedure 10.3. Adding a New Mobile Broadband Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Click the button to open the selection list. Select Mobile Broadband and then click . The Set up a Mobile Broadband Connection assistant appears.
- Under Create a connection for this mobile broadband device, choose the 2G- or 3G-capable device you want to use with the connection. If the dropdown menu is inactive, this indicates that the system was unable to detect a device capable of mobile broadband. In this case, click Cancel, ensure that you do have a mobile broadband-capable device attached and recognized by the computer and then retry this procedure. Click the Forward button.
- Select the country where your service provider is located from the list and click the Forward button.
- Select your provider from the list or enter it manually. Click the Forward button.
- Select your payment plan from the dropdown menu and confirm the Access Point Name (APN) is correct. Click the Forward button.
- Review and confirm the settings and then click the Apply button.
- Edit the mobile broadband-specific settings by referring to the Configuring the Mobile Broadband Tab description below .
Procedure 10.4. Editing an Existing Mobile Broadband Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Select the connection you want to edit and click the Edit button.
- Select the Mobile Broadband tab.
- Configure the connection name, auto-connect behavior, and availability settings.Three settings in the Editing dialog are common to all connection types:
- Connection name — Enter a descriptive name for your network connection. This name will be used to list this connection in the Mobile Broadband section of the Network Connections window.
- Connect automatically — Check this box if you want NetworkManager to auto-connect to this connection when it is available. See Section 10.2.3, “Connecting to a Network Automatically” for more information.
- Available to all users — Check this box to create a connection available to all users on the system. Changing this setting may require
rootprivileges. See Section 10.2.4, “User and System Connections” for details.
- Edit the mobile broadband-specific settings by referring to the Configuring the Mobile Broadband Tab description below .
Saving Your New (or Modified) Connection and Making Further Configurations
- Point-to-point settings for the connection, click the PPP Settings tab and proceed to Section 10.3.9.3, “Configuring PPP (Point-to-Point) Settings”;
- IPv4 settings for the connection, click the IPv4 Settings tab and proceed to Section 10.3.9.4, “Configuring IPv4 Settings”; or,
- IPv6 settings for the connection, click the IPv6 Settings tab and proceed to Section 10.3.9.5, “Configuring IPv6 Settings”.
Configuring the Mobile Broadband Tab
- Number
- The number that is dialed to establish a PPP connection with the GSM-based mobile broadband network. This field may be automatically populated during the initial installation of the broadband device. You can usually leave this field blank and enter the APN instead.
- Username
- Enter the user name used to authenticate with the network. Some providers do not provide a user name, or accept any user name when connecting to the network.
- Password
- Enter the password used to authenticate with the network. Some providers do not provide a password, or accept any password.
- APN
- Enter the Access Point Name (APN) used to establish a connection with the GSM-based network. Entering the correct APN for a connection is important because it often determines:
- how the user is billed for their network usage; and/or
- whether the user has access to the Internet, an intranet, or a subnetwork.
- Network ID
- Entering a Network ID causes NetworkManager to force the device to register only to a specific network. This can be used to ensure the connection does not roam when it is not possible to control roaming directly.
- Type
- Any — The default value of Any leaves the modem to select the fastest network.3G (UMTS/HSPA) — Force the connection to use only 3G network technologies.2G (GPRS/EDGE) — Force the connection to use only 2G network technologies.Prefer 3G (UMTS/HSPA) — First attempt to connect using a 3G technology such as HSPA or UMTS, and fall back to GPRS or EDGE only upon failure.Prefer 2G (GPRS/EDGE) — First attempt to connect using a 2G technology such as GPRS or EDGE, and fall back to HSPA or UMTS only upon failure.
- Allow roaming if home network is not available
- Uncheck this box if you want NetworkManager to terminate the connection rather than transition from the home network to a roaming one, thereby avoiding possible roaming charges. If the box is checked, NetworkManager will attempt to maintain a good connection by transitioning from the home network to a roaming one, and vice versa.
- PIN
- If your device's SIM (Subscriber Identity Module) is locked with a PIN (Personal Identification Number), enter the PIN so that NetworkManager can unlock the device. NetworkManager must unlock the SIM if a PIN is required in order to use the device for any purpose.
10.3.4. Establishing a VPN Connection
- it adds an Authentication Header for routing and authentication purposes;
- it encrypts the packet data; and,
- it encloses the data with an Encapsulating Security Payload (ESP), which constitutes the decryption and handling instructions.
Procedure 10.5. Adding a New VPN Connection
- You can configure a new VPN connection by opening the Network Connections window, clicking the button and selecting a type of VPN from the VPN section of the new connection list.
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Click the button.
- The Choose a Connection Type list appears.
Note
The appropriate NetworkManager VPN plug-in for the VPN type you want to configure must be installed (see Section 8.2.4, “Installing Packages” for more information on how to install new packages in Red Hat Enterprise Linux 6).The VPN section in the Choose a Connection Type list will not appear if you do not have a suitable plug-in installed.- Select the VPN protocol for the gateway you are connecting to from the Choose a Connection Type list. The VPN protocols available for selection in the list correspond to the NetworkManager VPN plug-ins installed. For example, if NetworkManager-openswan, the NetworkManager VPN plug-in for libreswan, is installed, then the IPsec based VPN will be selectable from the Choose a Connection Type list.
Note
In Red Hat Enterprise Linux 6.8, openswan has been obsoleted by libreswan. NetworkManager-openswan has been modified to support both openswan and libreswan.After selecting the correct one, press the button. - The Editing VPN Connection 1 window then appears. This window presents settings customized for the type of VPN connection you selected in Step 6.
Procedure 10.6. Editing an Existing VPN Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Select the connection you want to edit and click the Edit button.
Figure 10.13. Editing the newly created IPsec VPN connection 1
Configuring the Connection Name, Auto-Connect Behavior, and Availability Settings
- Connection name — Enter a descriptive name for your network connection. This name will be used to list this connection in the VPN section of the Network Connections window.
- Connect automatically — Check this box if you want NetworkManager to auto-connect to this connection when it is available. See Section 10.2.3, “Connecting to a Network Automatically” for more information.
- Available to all users — Check this box to create a connection available to all users on the system. Changing this setting may require
rootprivileges. See Section 10.2.4, “User and System Connections” for details.
Configuring the VPN Tab
- Gateway
- The name or IP address of the remote VPN gateway.
- Group name
- The name of a VPN group configured on the remote gateway.
- User password
- If required, enter the password used to authenticate with the VPN.
- Group password
- If required, enter the password used to authenticate with the VPN.
- User name
- If required, enter the user name used to authenticate with the VPN.
- Phase1 Algorithms
- If required, enter the algorithms to be used to authenticate and set up an encrypted channel.
- Phase2 Algorithms
- If required, enter the algorithms to be used for the IPsec negotiations.
- Domain
- If required, enter the Domain Name.
- NAT traversal
- — IPsec over UDP.— ESP encapsulation and IKE extensions are used to handle NAT Traversal.— No special NAT measures required.Disable Dead Peer Detection — Disable the sending of probes to the remote gateway or endpoint.
Saving Your New (or Modified) Connection and Making Further Configurations
- IPv4 settings for the connection, click the IPv4 Settings tab and proceed to Section 10.3.9.4, “Configuring IPv4 Settings”.
10.3.5. Establishing a DSL Connection
Procedure 10.7. Adding a New DSL Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Click the button.
- The Choose a Connection Type list appears.
- Select DSL and press the button.
- The Editing DSL Connection 1 window appears.
Procedure 10.8. Editing an Existing DSL Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Select the connection you want to edit and click the Edit button.
Configuring the Connection Name, Auto-Connect Behavior, and Availability Settings
- Connection name — Enter a descriptive name for your network connection. This name will be used to list this connection in the DSL section of the Network Connections window.
- Connect automatically — Check this box if you want NetworkManager to auto-connect to this connection when it is available. See Section 10.2.3, “Connecting to a Network Automatically” for more information.
- Available to all users — Check this box to create a connection available to all users on the system. Changing this setting may require
rootprivileges. See Section 10.2.4, “User and System Connections” for details.
Configuring the DSL Tab
- Username
- Enter the user name used to authenticate with the service provider.
- Service
- Leave blank unless otherwise directed.
- Password
- Enter the password supplied by the service provider.
Saving Your New (or Modified) Connection and Making Further Configurations
- The MAC address and MTU settings, click the Wired tab and proceed to the section called “Configuring the Wired Tab”;
- Point-to-point settings for the connection, click the PPP Settings tab and proceed to Section 10.3.9.3, “Configuring PPP (Point-to-Point) Settings”;
- IPv4 settings for the connection, click the IPv4 Settings tab and proceed to Section 10.3.9.4, “Configuring IPv4 Settings”.
10.3.6. Establishing a Bond Connection
Note
NM_BOND_VLAN_ENABLED directive and then NetworkManager must be restarted. See Section 11.2.1, “Ethernet Interfaces” for an explanation of NM_CONTROLLED and the NM_BOND_VLAN_ENABLED directive. See Section 12.3.4, “Restarting a Service” for an explanation of restarting a service such as NetworkManager from the command line. Alternatively, for a graphical tool see Section 12.2.1, “Using the Service Configuration Utility”.
Procedure 10.9. Adding a New Bond Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Click the button to open the selection list. Select Bond and then click . The Editing Bond connection 1 window appears.
- On the Bond tab, click and select the type of interface you want to use with the bond connection. Click the button. Note that the dialog to select the slave type only comes up when you create the first slave; after that, it will automatically use that same type for all further slaves.
- The Editing bond0 slave 1 window appears. Fill in the MAC address of the first interface to be bonded. The first slave's MAC address will be used as the MAC address for the bond interface. If required, enter a clone MAC address to be used as the bond's MAC address. Click the button.
- The Authenticate window appears. Enter the
rootpassword to continue. Click the button. - The name of the bonded slave appears in the Bonded Connections window. Click the button to add further slave connections.
- Review and confirm the settings and then click the Apply button.
- Edit the bond-specific settings by referring to the section called “Configuring the Bond Tab” below.
Figure 10.14. Editing the newly created Bond connection 1
Procedure 10.10. Editing an Existing Bond Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Select the connection you want to edit and click the Edit button.
- Select the Bond tab.
- Configure the connection name, auto-connect behavior, and availability settings.Three settings in the Editing dialog are common to all connection types:
- Connection name — Enter a descriptive name for your network connection. This name will be used to list this connection in the Bond section of the Network Connections window.
- Connect automatically — Select this box if you want NetworkManager to auto-connect to this connection when it is available. See Section 10.2.3, “Connecting to a Network Automatically” for more information.
- Available to all users — Select this box to create a connection available to all users on the system. Changing this setting may require
rootprivileges. See Section 10.2.4, “User and System Connections” for details.
- Edit the bond-specific settings by referring to the section called “Configuring the Bond Tab” below.
Saving Your New (or Modified) Connection and Making Further Configurations
- IPv4 settings for the connection, click the IPv4 Settings tab and proceed to Section 10.3.9.4, “Configuring IPv4 Settings”; or,
- IPv6 settings for the connection, click the IPv6 Settings tab and proceed to Section 10.3.9.5, “Configuring IPv6 Settings”.
Configuring the Bond Tab
- Mode
- The mode that is used to share traffic over the slave connections which make up the bond. The default is Round-robin. Other load sharing modes, such as
802.3ad, can be selected by means of the drop-down list. - Link Monitoring
- The method of monitoring the slaves ability to carry network traffic.
- Round-robin
- Sets a round-robin policy for fault tolerance and load balancing. Transmissions are received and sent out sequentially on each bonded slave interface beginning with the first one available. This mode might not work behind a bridge with virtual machines without additional switch configuration.
- Active backup
- Sets an active-backup policy for fault tolerance. Transmissions are received and sent out via the first available bonded slave interface. Another bonded slave interface is only used if the active bonded slave interface fails. Note that this is the only mode available for bonds of InfiniBand devices.
- XOR
- Sets an XOR (exclusive-or) policy. Transmissions are based on the selected hash policy. The default is to derive a hash by XOR of the source and destination MAC addresses multiplied by the modulo of the number of slave interfaces. In this mode traffic destined for specific peers will always be sent over the same interface. As the destination is determined by the MAC addresses this method works best for traffic to peers on the same link or local network. If traffic has to pass through a single router then this mode of traffic balancing will be suboptimal.
- Broadcast
- Sets a broadcast policy for fault tolerance. All transmissions are sent on all slave interfaces. This mode might not work behind a bridge with virtual machines without additional switch configuration.
- 802.3ad
- Sets an IEEE
802.3addynamic link aggregation policy. Creates aggregation groups that share the same speed and duplex settings. Transmits and receives on all slaves in the active aggregator. Requires a network switch that is802.3adcompliant. - Adaptive transmit load balancing
- Sets an adaptive Transmit Load Balancing (TLB) policy for fault tolerance and load balancing. The outgoing traffic is distributed according to the current load on each slave interface. Incoming traffic is received by the current slave. If the receiving slave fails, another slave takes over the MAC address of the failed slave. This mode is only suitable for local addresses known to the kernel bonding module and therefore cannot be used behind a bridge with virtual machines.
- Adaptive load balancing
- Sets an Adaptive Load Balancing (ALB) policy for fault tolerance and load balancing. Includes transmit and receive load balancing for
IPv4traffic. Receive load balancing is achieved throughARPnegotiation. This mode is only suitable for local addresses known to the kernel bonding module and therefore cannot be used behind a bridge with virtual machines.
- MII (Media Independent Interface)
- The state of the carrier wave of the interface is monitored. This can be done by querying the driver, by querying MII registers directly, or by using ethtool to query the device. Three options are available:
- Monitoring Frequency
- The time interval, in milliseconds, between querying the driver or MII registers.
- Link up delay
- The time in milliseconds to wait before attempting to use a link that has been reported as up. This delay can be used if some gratuitous
ARPrequests are lost in the period immediately following the link being reported as “up”. This can happen during switch initialization for example. - Link down delay
- The time in milliseconds to wait before changing to another link when a previously active link has been reported as “down”. This delay can be used if an attached switch takes a relatively long time to change to backup mode.
- ARP
- The address resolution protocol (
ARP) is used to probe one or more peers to determine how well the link-layer connections are working. It is dependent on the device driver providing the transmit start time and the last receive time.Two options are available:- Monitoring Frequency
- The time interval, in milliseconds, between sending
ARPrequests. - ARP targets
- A comma separated list of
IPaddresses to sendARPrequests to.
10.3.7. Establishing a VLAN Connection
Procedure 10.11. Adding a New VLAN Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Click the button to open the selection list. Select VLAN and then click . The Editing VLAN Connection 1 window appears.
- On the VLAN tab, select the parent interface from the drop-down list you want to use for the VLAN connection.
- Enter the VLAN ID
- Enter a VLAN interface name. This is the name of the VLAN interface that will be created. For example, "eth0.1" or "vlan2". (Normally this is either the parent interface name plus "." and the VLAN ID, or "vlan" plus the VLAN ID.)
- Review and confirm the settings and then click the Apply button.
- Edit the VLAN-specific settings by referring to the Configuring the VLAN Tab description below .
Procedure 10.12. Editing an Existing VLAN Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Select the connection you want to edit and click the Edit button.
- Select the VLAN tab.
- Configure the connection name, auto-connect behavior, and availability settings.Three settings in the Editing dialog are common to all connection types:
- Connection name — Enter a descriptive name for your network connection. This name will be used to list this connection in the VLAN section of the Network Connections window.
- Connect automatically — Check this box if you want NetworkManager to auto-connect to this connection when it is available. See Section 10.2.3, “Connecting to a Network Automatically” for more information.
- Available to all users — Check this box to create a connection available to all users on the system. Changing this setting may require
rootprivileges. See Section 10.2.4, “User and System Connections” for details.
- Edit the VLAN-specific settings by referring to the Configuring the VLAN Tab description below .
Saving Your New (or Modified) Connection and Making Further Configurations
- IPv4 settings for the connection, click the IPv4 Settings tab and proceed to Section 10.3.9.4, “Configuring IPv4 Settings”.
Configuring the VLAN Tab
- Parent Interface
- A previously configured interface can be selected in the drop-down list.
- VLAN ID
- The identification number to be used to tag the VLAN network traffic.
- VLAN interface name
- The name of the VLAN interface that will be created. For example, "eth0.1" or "vlan2".
- Cloned MAC address
- Optionally sets an alternate MAC address to use for identifying the VLAN interface. This can be used to change the source MAC address for packets sent on this VLAN.
- MTU
- Optionally sets a Maximum Transmission Unit (MTU) size to be used for packets to be sent over the VLAN connection.
10.3.8. Establishing an IP-over-InfiniBand (IPoIB) Connection
Procedure 10.13. Adding a New InfiniBand Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Click the button to open the selection list. Select InfiniBand and then click . The Editing InfiniBand Connection 1 window appears.
- On the InfiniBand tab, select the transport mode from the drop-down list you want to use for the InfiniBand connection.
- Enter the InfiniBand MAC address.
- Review and confirm the settings and then click the Apply button.
- Edit the InfiniBand-specific settings by referring to the Configuring the InfiniBand Tab description below .
Figure 10.15. Editing the newly created InfiniBand connection 1
Procedure 10.14. Editing an Existing InfiniBand Connection
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Select the connection you want to edit and click the Edit button.
- Select the InfiniBand tab.
- Configure the connection name, auto-connect behavior, and availability settings.Three settings in the Editing dialog are common to all connection types:
- Connection name — Enter a descriptive name for your network connection. This name will be used to list this connection in the InfiniBand section of the Network Connections window.
- Connect automatically — Check this box if you want NetworkManager to auto-connect to this connection when it is available. See Section 10.2.3, “Connecting to a Network Automatically” for more information.
- Available to all users — Check this box to create a connection available to all users on the system. Changing this setting may require
rootprivileges. See Section 10.2.4, “User and System Connections” for details.
- Edit the InfiniBand-specific settings by referring to the Configuring the InfiniBand Tab description below .
Saving Your New (or Modified) Connection and Making Further Configurations
- IPv4 settings for the connection, click the IPv4 Settings tab and proceed to Section 10.3.9.4, “Configuring IPv4 Settings”; or,
- IPv6 settings for the connection, click the IPv6 Settings tab and proceed to Section 10.3.9.5, “Configuring IPv6 Settings”.
Configuring the InfiniBand Tab
- Transport mode
- Datagram or Connected mode can be selected from the drop-down list. Select the same mode the rest of your IPoIB network is using.
- Device MAC address
- The MAC address of the InfiniBand capable device to be used for the InfiniBand network traffic.This hardware address field will be pre-filled if you have InfiniBand hardware installed.
- MTU
- Optionally sets a Maximum Transmission Unit (MTU) size to be used for packets to be sent over the InfiniBand connection.
10.3.9. Configuring Connection Settings
10.3.9.1. Configuring 802.1X Security
Procedure 10.15. For a wired connection...
- Either click , select a new network connection for which you want to configure 802.1X security and then click , or select an existing connection and click .
- Then select the 802.1X Security tab and check the Use 802.1X security for this connection check box to enable settings configuration.
Procedure 10.16. For a wireless connection...
- Either click on , select a new network connection for which you want to configure 802.1X security and then click , or select an existing connection and click .
- Select the Wireless Security tab.
- Then click the Security dropdown and choose one of the following security methods: , , or .
- See Section 10.3.9.1.1, “Configuring TLS (Transport Layer Security) Settings” for descriptions of which EAP types correspond to your selection in the Security dropdown.
10.3.9.1.1. Configuring TLS (Transport Layer Security) Settings
- Identity
- Identity string for EAP authentication methods, such as a user name or login name.
- User certificate
- Click to browse for, and select, a user's certificate.
- CA certificate
- Click to browse for, and select, a Certificate Authority's certificate.
- Private key
- Click to browse for, and select, a user's private key file. Note that the key must be password protected.
- Private key password
- Enter the user password corresponding to the user's private key.
10.3.9.1.2. Configuring Tunneled TLS Settings
- Anonymous identity
- This value is used as the unencrypted identity.
- CA certificate
- Click to browse for, and select, a Certificate Authority's certificate.
- Inner authentication
- — Password Authentication Protocol.— Challenge Handshake Authentication Protocol.— Microsoft Challenge Handshake Authentication Protocol version 2.— Challenge Handshake Authentication Protocol.
- Username
- Enter the user name to be used in the authentication process.
- Password
- Enter the password to be used in the authentication process.
10.3.9.1.3. Configuring Protected EAP (PEAP) Settings
- Anonymous Identity
- This value is used as the unencrypted identity.
- CA certificate
- Click to browse for, and select, a Certificate Authority's certificate.
- PEAP version
- The version of Protected EAP to use. Automatic, 0 or 1.
- Inner authentication
- — Microsoft Challenge Handshake Authentication Protocol version 2.— Message Digest 5, a cryptographic hash function.— Generic Token Card.
- Username
- Enter the user name to be used in the authentication process.
- Password
- Enter the password to be used in the authentication process.
10.3.9.2. Configuring Wireless Security
- Security
- — Do not encrypt the Wi-Fi connection.— Wired Equivalent Privacy (WEP), from the IEEE 802.11 standard. Uses a single pre-shared key (PSK).— An MD5 hash of the passphrase will be used to derive a WEP key.— Lightweight Extensible Authentication Protocol, from Cisco Systems.— WEP keys are changed dynamically.— Wi-Fi Protected Access (WPA), from the draft IEEE 802.11i standard. A replacement for WEP. Wi-Fi Protected Access II (WPA2), from the 802.11i-2004 standard. Personal mode uses a pre-shared key (WPA-PSK).— WPA for use with a RADIUS authentication server to provide IEEE 802.1X network access control.
- Password
- Enter the password to be used in the authentication process.
Note
Figure 10.16. Editing the Wireless Security tab and selecting the WPA protocol
10.3.9.3. Configuring PPP (Point-to-Point) Settings
- Configure Methods
- Use point-to-point encryption (MPPE)
- Microsoft Point-To-Point Encryption protocol (RFC 3078).
- Allow BSD data compression
- PPP BSD Compression Protocol (RFC 1977).
- Allow Deflate data compression
- PPP Deflate Protocol (RFC 1979).
- Use TCP header compression
- Compressing TCP/IP Headers for Low-Speed Serial Links (RFC 1144).
- Send PPP echo packets
- LCP Echo-Request and Echo-Reply Codes for loopback tests (RFC 1661).
10.3.9.4. Configuring IPv4 Settings
Figure 10.17. Editing the IPv4 Settings Tab
Setting the Method
Available IPv4 Methods by Connection Type
- Method
- — Choose this option if the network you are connecting to uses a DHCP server to assign IP addresses. You do not need to fill in the DHCP client ID field.— Choose this option if the network you are connecting to uses a DHCP server to assign IP addresses but you want to assign DNS servers manually.— Choose this option if the network you are connecting to does not have a DHCP server and you do not want to assign IP addresses manually. Random addresses will be selected as per RFC 3927.— Choose this option if the interface you are configuring is for sharing an Internet or WAN connection.
- Wired, Wireless and DSL Connection Methods
- — Choose this option if the network you are connecting to does not have a DHCP server and you want to assign IP addresses manually.
- Mobile Broadband Connection Methods
- — Choose this option if the network you are connecting to uses a DHCP server to assign IP addresses.— Choose this option if the network you are connecting to uses a DHCP server to assign IP addresses but you want to assign DNS servers manually.
- VPN Connection Methods
- — Choose this option if the network you are connecting to uses a DHCP server to assign IP addresses.— Choose this option if the network you are connecting to uses a DHCP server to assign IP addresses but you want to assign DNS servers manually.
- DSL Connection Methods
- — Choose this option if the network you are connecting to uses a DHCP server to assign IP addresses.— Choose this option if the network you are connecting to uses a DHCP server to assign IP addresses but you want to assign DNS servers manually.
PPPoE Specific Configuration Steps
- Enter the MAC address in nm-connection-editor for that connection. Optionally select Connect automatically and Available to all users to make the connection come up without requiring user login after system start.
- Set the hardware-address in the [802-3-ethernet] section in the appropriate file for that connection in
/etc/NetworkManager/system-connections/as follows:Mere presence of the file in[802-3-ethernet] mac-address=00:11:22:33:44:55
[802-3-ethernet] mac-address=00:11:22:33:44:55Copy to Clipboard Copied! Toggle word wrap Toggle overflow /etc/NetworkManager/system-connections/means that it is “available to all users”. Ensure thatautoconnect=trueappears in the [connection] section for the connection to be brought up without requiring user login after system start.
10.3.9.5. Configuring IPv6 Settings
- Method
- — Choose this option if you want to disable IPv6 settings.— Choose this option if the network you are connecting to uses a DHCP server to assign IP addresses.— Choose this option if the network you are connecting to uses a DHCP server to assign IP addresses but you want to assign DNS servers manually.— Choose this option if the network you are connecting to does not have a DHCP server and you want to assign IP addresses manually.— Choose this option if the network you are connecting to does not have a DHCP server and you do not want to assign IP addresses manually. Random addresses will be selected as per RFC 4862.— Choose this option if the interface you are configuring is for sharing an Internet or WAN connection.
- Addresses
- — Enter a comma separated list of DNS servers.— Enter a comma separated list of domain controllers.
10.3.9.6. Configuring Routes
Figure 10.18. Configuring static network routes
- Addresses
- — The IP address of a network, sub-net or host.— The netmask or prefix length of the IP address just entered.— The IP address of the gateway leading to the network, sub-net or host.— A network cost, that is to say a preference value to give to this route. Lower values will be preferred over higher values.
- Ignore automatically obtained routes
- Select this check box to only use manually entered routes for this connection.
- Use this connection only for resources on its network
- Select this check box to prevent the connection from becoming the default route. Typical examples are where a connection is a VPN or a leased line to a head office and you do not want any Internet bound traffic to pass over the connection. Selecting this option means that only traffic specifically destined for routes learned automatically over the connection or entered here manually will be routed over the connection.
Chapter 11. Network Interfaces
/etc/sysconfig/network-scripts/ directory. The scripts used to activate and deactivate these network interfaces are also located here. Although the number and type of interface files can differ from system to system, there are three categories of files that exist in this directory:
- Interface configuration files
- Interface control scripts
- Network function files
11.1. Network Configuration Files
-
/etc/hosts - The main purpose of this file is to resolve host names that cannot be resolved any other way. It can also be used to resolve host names on small networks with no
DNSserver. Regardless of the type of network the computer is on, this file should contain a line specifying theIPaddress of the loopback device (127.0.0.1) aslocalhost.localdomain. For more information, see thehosts(5)manual page. -
/etc/resolv.conf - This file specifies the
IPaddresses ofDNSservers and the search domain. Unless configured to do otherwise, the network initialization scripts populate this file. For more information about this file, see theresolv.conf(5)manual page. -
/etc/sysconfig/network - This file specifies routing and host information for all network interfaces. It is used to contain directives which are to have global effect and not to be interface specific. For more information about this file and the directives it accepts, see Section D.1.14, “/etc/sysconfig/network”.
-
/etc/sysconfig/network-scripts/ifcfg-interface-name - For each network interface, there is a corresponding interface configuration script. Each of these files provide information specific to a particular network interface. See Section 11.2, “Interface Configuration Files” for more information on this type of file and the directives it accepts.
Important
Warning
/etc/sysconfig/networking/ directory is used by the now deprecated Network Administration Tool (system-config-network). Its contents should not be edited manually. Using only one method for network configuration is strongly encouraged, due to the risk of configuration deletion. For more information about configuring network interfaces using graphical configuration tools, see Chapter 10, NetworkManager.
11.1.1. Setting the Host Name
/etc/sysconfig/network file. For example:
HOSTNAME=penguin.example.com
HOSTNAME=penguin.example.com/etc/sysconfig/network, or by the /etc/hosts file. The default setting of hosts: files dns in /etc/nsswitch.conf causes the configuration files to be checked before a resolver. The default setting of multi on in the /etc/host.conf file means that all valid values in the /etc/hosts file are returned, not just the first.
/etc/hosts file instead of the HOSTNAME directive in /etc/sysconfig/network, for example, when DNS is not running during system bootup.
/etc/hosts file, add lines to it in the following format:
192.168.1.2 penguin.example.com penguin
192.168.1.2 penguin.example.com penguin11.2. Interface Configuration Files
ifcfg-name, where name refers to the name of the device that the configuration file controls.
11.2.1. Ethernet Interfaces
/etc/sysconfig/network-scripts/ifcfg-eth0, which controls the first Ethernet network interface card or NIC in the system. In a system with multiple NICs, there are multiple ifcfg-ethX files (where X is a unique number corresponding to a specific interface). Because each device has its own configuration file, an administrator can control how each interface functions individually.
ifcfg-eth0 file for a system using a fixed IP address:
ifcfg-eth0 file for an interface using DHCP looks different because IP information is provided by the DHCP server:
DEVICE=eth0 BOOTPROTO=dhcp ONBOOT=yes
DEVICE=eth0
BOOTPROTO=dhcp
ONBOOT=yes-
BONDING_OPTS=parameters - sets the configuration parameters for the bonding device, and is used in
/etc/sysconfig/network-scripts/ifcfg-bondN(see Section 11.2.4, “Channel Bonding Interfaces”). These parameters are identical to those used for bonding devices in/sys/class/net/bonding_device/bonding, and the module parameters for the bonding driver as described inbondingModule Directives.This configuration method is used so that multiple bonding devices can have different configurations. In Red Hat Enterprise Linux 6, place all interface-specific bonding options after theBONDING_OPTSdirective inifcfg-namefiles. See Where to specify bonding module parameters for more information. -
BOOTPROTO=protocol - where protocol is one of the following:
none— No boot-time protocol should be used.bootp— TheBOOTPprotocol should be used.dhcp— TheDHCPprotocol should be used.
BROADCAST=address- where address is the broadcast address. This directive is deprecated, as the value is calculated automatically with
ipcalc. -
DEVICE=name - where name is the name of the physical device (except for dynamically-allocated
PPPdevices where it is the logical name). DHCP_HOSTNAME=name- where name is a short host name to be sent to the
DHCPserver. Use this option only if theDHCPserver requires the client to specify a host name before receiving anIPaddress. DHCPV6C=answer- where answer is one of the following:
yes— UseDHCPto obtain anIPv6address for this interface.no— Do not useDHCPto obtain anIPv6address for this interface. This is the default value.
AnIPv6link-local address will still be assigned by default. The link-local address is based on the MAC address of the interface as per RFC 4862. DHCPV6C_OPTIONS=answer- where answer is one of the following:
-P— EnableIPv6prefix delegation.-S— UseDHCPto obtain stateless configuration only, not addresses, for this interface.-N— Restore normal operation after using the-Tor-Poptions.-T— UseDHCPto obtain a temporaryIPv6address for this interface.-D— Override the default when selecting the type of DHCP Unique Identifier (DUID) to use.By default, theDHCPclient (dhclient) creates a DHCP Unique Identifier (DUID) based on the link-layer address (DUID-LL) if it is running in stateless mode (with the-Soption, to not request an address), or it creates an identifier based on the link-layer address plus a timestamp (DUID-LLT) if it is running in stateful mode (without-S, requesting an address). The-Doption overrides this default, with a value of eitherLLorLLT.
DNS{1,2}=address- where address is a name server address to be placed in
/etc/resolv.confprovided that thePEERDNSdirective is not set tono. -
ETHTOOL_OPTS=options - where options are any device-specific options supported by
ethtool. For example, if you wanted to force 100Mb, full duplex:ETHTOOL_OPTS="autoneg off speed 100 duplex full"
ETHTOOL_OPTS="autoneg off speed 100 duplex full"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Instead of a custom initscript, useETHTOOL_OPTSto set the interface speed and duplex settings. Custom initscripts run outside of the network init script lead to unpredictable results during a post-boot network service restart.Important
Changing speed or duplex settings almost always requires disabling auto-negotiation with theautoneg offoption. This option needs to be stated first, as the option entries are order-dependent.See Section 11.8, “Ethtool” for more ethtool options. HOTPLUG=answer- where answer is one of the following:
yes— This device should be activated when it is hot-plugged (this is the default option).no— This device should not be activated when it is hot-plugged.
TheHOTPLUG=nooption can be used to prevent a channel bonding interface from being activated when a bonding kernel module is loaded.See Section 11.2.4, “Channel Bonding Interfaces” for more information about channel bonding interfaces. -
HWADDR=MAC-address - where MAC-address is the hardware address of the Ethernet device in the form AA:BB:CC:DD:EE:FF. This directive must be used in machines containing more than one NIC to ensure that the interfaces are assigned the correct device names regardless of the configured load order for each NIC's module. This directive should not be used in conjunction with
MACADDR.Note
- Persistent device names are now handled by
/etc/udev/rules.d/70-persistent-net.rules. HWADDRmust not be used with System z network devices.- See Section 25.3.3, "Mapping subchannels and network device names", in the Red Hat Enterprise Linux 6 Installation Guide.
-
IPADDRn=address - where address is the
IPv4address and the n is expected to be consecutive positive integers starting from 0 (for example, IPADDR0). It is used for configurations with multiple IP addresses on an interface. It can be omitted if there is only one address being configured. -
IPV6ADDR=address - where address is the first static, or primary,
IPv6address on an interface.The format is Address/Prefix-length. If no prefix length is specified,/64is assumed. Note that this setting depends onIPV6INITbeing enabled. -
IPV6ADDR_SECONDARIES=address - where address is one or more, space separated, additional
IPv6addresses.The format is Address/Prefix-length. If no prefix length is specified,/64is assumed. Note that this setting depends onIPV6INITbeing enabled. -
IPV6INIT=answer - where answer is one of the following:
yes— Initialize this interface forIPv6addressing.no— Do not initialize this interface forIPv6addressing. This is the default value.This setting is required forIPv6static andDHCPassignment ofIPv6addresses. It does not affect IPv6 Stateless Address Autoconfiguration (SLAAC) as per RFC 4862.See Section D.1.14, “/etc/sysconfig/network” for information on disablingIPv6.
-
IPV6_AUTOCONF=answer - where answer is one of the following:
yes— EnableIPv6autoconf configuration for this interface.no— DisableIPv6autoconf configuration for this interface.
If enabled, anIPv6address will be requested using Neighbor Discovery (ND) from a router running theradvddaemon.Note that the default value ofIPV6_AUTOCONFdepends onIPV6FORWARDINGas follows:- If
IPV6FORWARDING=yes, thenIPV6_AUTOCONFwill default tono. - If
IPV6FORWARDING=no, thenIPV6_AUTOCONFwill default toyesandIPV6_ROUTERhas no effect.
-
IPV6_MTU=value - where value is an optional dedicated MTU for this interface.
-
IPV6_PRIVACY=rfc3041 - where rfc3041 optionally sets this interface to support RFC 3041 Privacy Extensions for Stateless Address Autoconfiguration in IPv6. Note that this setting depends on
IPV6INIToption being enabled.The default is for RFC 3041 support to be disabled. Stateless Autoconfiguration will derive addresses based on the MAC address, when available, using the modifiedEUI-64method. The address is appended to a prefix but as the address is normally derived from the MAC address it is globally unique even when the prefix changes. In the case of a link-local address the prefix isfe80::/64as per RFC 2462 IPv6 Stateless Address Autoconfiguration. -
LINKDELAY=time - where time is the number of seconds to wait for link negotiation before configuring the device. The default is 5 secs. Delays in link negotiation, caused by
STPfor example, can be overcome by increasing this value. -
MACADDR=MAC-address - where MAC-address is the hardware address of the Ethernet device in the form AA:BB:CC:DD:EE:FF.This directive is used to assign a MAC address to an interface, overriding the one assigned to the physical NIC. This directive should not be used in conjunction with the
HWADDRdirective. -
MASTER=bond-interface - where bond-interface is the channel bonding interface to which the Ethernet interface is linked.This directive is used in conjunction with the
SLAVEdirective.See Section 11.2.4, “Channel Bonding Interfaces” for more information about channel bonding interfaces. -
NETMASKn=mask - where mask is the netmask value and the n is expected to be consecutive positive integers starting from 0 (for example, NETMASK0). It is used for configurations with multiple IP addresses on an interface. It can be omitted if there is only one address being configured.
-
NETWORK=address - where address is the network address. This directive is deprecated, as the value is calculated automatically with
ipcalc. -
NM_CONTROLLED=answer - where answer is one of the following:
yes— NetworkManager is permitted to configure this device. This is the default behavior and can be omitted.no— NetworkManager is not permitted to configure this device.
Note
TheNM_CONTROLLEDdirective is now, as of Red Hat Enterprise Linux 6.3, dependent on theNM_BOND_VLAN_ENABLEDdirective in/etc/sysconfig/network. If and only if that directive is present and is one ofyes,y, ortrue, will NetworkManager detect and manage bonding and VLAN interfaces. ONBOOT=answer- where answer is one of the following:
yes— This device should be activated at boot-time.no— This device should not be activated at boot-time.
PEERDNS=answer- where answer is one of the following:
yes— Modify/etc/resolv.confif theDNSdirective is set, if usingDHCP, or if using Microsoft's RFC 1877IPCPextensions withPPP. In all casesyesis the default.no— Do not modify/etc/resolv.conf.
SLAVE=answer- where answer is one of the following:
yes— This device is controlled by the channel bonding interface specified in theMASTERdirective.no— This device is not controlled by the channel bonding interface specified in theMASTERdirective.
This directive is used in conjunction with theMASTERdirective.See Section 11.2.4, “Channel Bonding Interfaces” for more about channel bonding interfaces. -
SRCADDR=address - where address is the specified source
IPaddress for outgoing packets. -
USERCTL=answer - where answer is one of the following:
yes— Non-rootusers are allowed to control this device.no— Non-rootusers are not allowed to control this device.
11.2.2. Specific ifcfg Options for Linux on System z
-
SUBCHANNELS=<read_device_bus_id>, <write_device_bus_id>, <data_device_bus_id> - where <read_device_bus_id>, <write_device_bus_id>, and <data_device_bus_id> are the three device bus IDs representing a network device.
-
PORTNAME=myname; - where myname is the Open Systems Adapter (OSA) portname or LAN Channel Station (LCS) portnumber.
CTCPROT=answer- where answer is one of the following:
0— Compatibility mode, TCP/IP for Virtual Machines (used with non-Linux peers other than IBM S/390 and IBM System z operating systems). This is the default mode.1— Extended mode, used for Linux-to-Linux Peers.3— Compatibility mode for S/390 and IBM System z operating systems.
This directive is used in conjunction with the NETTYPE directive. It specifies the CTC protocol for NETTYPE='ctc'. The default is 0. OPTION='answer'- where 'answer' is a quoted string of any valid sysfs attributes and their value. The Red Hat Enterprise Linux installer currently uses this to configure the layer mode, (layer2), and the relative port number, (portno), of QETH devices. For example:
OPTIONS='layer2=1 portno=0'
OPTIONS='layer2=1 portno=0'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
11.2.3. Required ifcfg Options for Linux on System z
NETTYPE=answer- where answer is one of the following:
ctc— Channel-to-Channel communication. For point-to-point TCP/IP or TTY.lcs— LAN Channel Station (LCS).qeth— QETH (QDIO Ethernet). This is the default network interface. It is the preferred installation method for supporting real or virtual OSA cards and HiperSockets devices.
11.2.4. Channel Bonding Interfaces
bonding kernel module and a special network interface called a channel bonding interface. Channel bonding enables two or more network interfaces to act as one, simultaneously increasing the bandwidth and providing redundancy.
Warning
Note
bonding.txt file in the kernel-doc package (see Section 31.9, “Additional Resources”).
11.2.4.1. Check if Bonding Kernel Module is Installed
root:
modprobe --first-time bonding
~]# modprobe --first-time bondingBONDING_OPTS directive, the bonding module will be loaded as required and therefore does not need to be loaded separately.
modinfo bonding
~]$ modinfo bondingmodprobe(8) man page for more command options and see Chapter 31, Working with Kernel Modules for information on loading and unloading modules.
11.2.4.2. Create a Channel Bonding Interface
/etc/sysconfig/network-scripts/ directory called ifcfg-bondN, replacing N with the number for the interface, such as 0.
DEVICE directive is bondN, replacing N with the number for the interface. The NM_CONTROLLED directive can be added to prevent NetworkManager from configuring this device.
Example 11.1. Example ifcfg-bond0 interface configuration file
NM_CONTROLLED=no directive, or set it to yes, and add TYPE=Bond and BONDING_MASTER=yes.
MASTER and SLAVE directives to their configuration files. The configuration files for each of the channel-bonded interfaces can be nearly identical.
Example 11.2. Example ifcfg-ethX bonded interface configuration file
eth0 and eth1 can be as follows:
root, issue the following command:
service network restart
~]# service network restart/proc/ file by issuing a command in the following format: cat /proc/net/bonding/bondN
cat /proc/net/bonding/bondNNM_CONTROLLED and the NM_BOND_VLAN_ENABLED directive.
Important
BONDING_OPTS="bonding parameters" directive in the ifcfg-bondN interface file. Do not specify options specific to a bond in /etc/modprobe.d/bonding.conf, or in the deprecated /etc/modprobe.conf file.
max_bonds parameter is not interface specific and therefore, if required, should be specified in /etc/modprobe.d/bonding.conf as follows:
options bonding max_bonds=1
options bonding max_bonds=1max_bonds parameter should not be set when using ifcfg-bondN files with the BONDING_OPTS directive as this directive will cause the network scripts to create the bond interfaces as required.
/etc/modprobe.d/bonding.conf will not take effect until the module is next loaded. A running module must first be unloaded. See Chapter 31, Working with Kernel Modules for more information on loading and unloading modules.
11.2.4.2.1. Creating Multiple Bonds
BONDING_OPTS directive. This configuration method is used so that multiple bonding devices can have different configurations. To create multiple channel bonding interfaces, proceed as follows:
- Create multiple
ifcfg-bondNfiles with theBONDING_OPTSdirective; this directive will cause the network scripts to create the bond interfaces as required. - Create, or edit existing, interface configuration files to be bonded and include the
SLAVEdirective. - Assign the interfaces to be bonded, the slave interfaces, to the channel bonding interfaces by means of the
MASTERdirective.
Example 11.3. Example multiple ifcfg-bondN interface configuration files
ifcfg-bond0 and ifcfg-bond1.
MASTER=bondN directive. For example, continuing on from the example above, if two interfaces per bond are required, then for two bonds create four interface configuration files and assign the first two using MASTER=bond0 and the next two using MASTER=bond1.
11.2.5. Configuring a VLAN over a Bond
IP addresses.
Warning
Note
bonding.txt file in the kernel-doc package (see Section 31.9, “Additional Resources”).
Procedure 11.1. Configuring the Interfaces on the Server
- Configure a slave interface using
eth0:The use of the NAME directive is optional. It is for display by a GUI interface, such as nm-connection-editor and nm-applet.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure a slave interface using
eth1:The use of the NAME directive is optional. It is for display by a GUI interface, such as nm-connection-editor and nm-applet.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure a channel bonding interface
ifcfg-bond0:The use of the NAME directive is optional. It is for display by a GUI interface, such as nm-connection-editor and nm-applet. In this example MII is used for link monitoring, see the Section 31.8.1.1, “Bonding Module Directives” section for more information on link monitoring.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Check the status of the interfaces on the server:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 11.2. Resolving Conflicts with Interfaces
IP addresses assigned to them apart from the IPv6 link-local addresses (starting fe80). If you have an unexpected IP address, then there may be another configuration file with ONBOOT set to yes.
- If this occurs, issue the following command to list all
ifcfgfiles that may be causing a conflict:The above shows the expected result on a new installation. Any file having both the ONBOOT directive as well as the IPADDR or SLAVE directive will be displayed. For example, if thegrep -r "ONBOOT=yes" /etc/sysconfig/network-scripts/ | cut -f1 -d":" | xargs grep -E "IPADDR|SLAVE" /etc/sysconfig/network-scripts/ifcfg-lo:IPADDR=127.0.0.1
~]$ grep -r "ONBOOT=yes" /etc/sysconfig/network-scripts/ | cut -f1 -d":" | xargs grep -E "IPADDR|SLAVE" /etc/sysconfig/network-scripts/ifcfg-lo:IPADDR=127.0.0.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow ifcfg-eth1file was incorrectly configured, the display might look similar to the following:grep -r "ONBOOT=yes" /etc/sysconfig/network-scripts/ | cut -f1 -d":" | xargs grep -E "IPADDR|SLAVE" /etc/sysconfig/network-scripts/ifcfg-lo:IPADDR=127.0.0.1 /etc/sysconfig/network-scripts/ifcfg-eth1:SLAVE=yes /etc/sysconfig/network-scripts/ifcfg-eth1:IPADDR=192.168.55.55
~]# grep -r "ONBOOT=yes" /etc/sysconfig/network-scripts/ | cut -f1 -d":" | xargs grep -E "IPADDR|SLAVE" /etc/sysconfig/network-scripts/ifcfg-lo:IPADDR=127.0.0.1 /etc/sysconfig/network-scripts/ifcfg-eth1:SLAVE=yes /etc/sysconfig/network-scripts/ifcfg-eth1:IPADDR=192.168.55.55Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Any other configuration files found should be moved to a different directory for backup, or assigned to a different interface by means of the HWADDR directive. After resolving any conflict set the interfaces “down” and “up” again or restart the network service as
root:If you are using NetworkManager, you might need to restart it at this point to make it forget the unwantedCopy to Clipboard Copied! Toggle word wrap Toggle overflow IPaddress. Asroot:service NetworkManager restart
~]# service NetworkManager restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 11.3. Checking the bond on the Server
- Bring up the bond on the server as
root:ifup /etc/sysconfig/network-scripts/ifcfg-bond0 Determining if ip address 192.168.100.100 is already in use for device bond0...
~]# ifup /etc/sysconfig/network-scripts/ifcfg-bond0 Determining if ip address 192.168.100.100 is already in use for device bond0...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Check the status of the interfaces on the server:Notice that
Copy to Clipboard Copied! Toggle word wrap Toggle overflow eth0andeth1havemaster bond0 state UPandbond0has status ofMASTER,UP. - View the bond configuration details:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Check the routes on the server:
ip route 192.168.100.0/24 dev bond0 proto kernel scope link src 192.168.100.100 169.254.0.0/16 dev bond0 scope link metric 1004
~]$ ip route 192.168.100.0/24 dev bond0 proto kernel scope link src 192.168.100.100 169.254.0.0/16 dev bond0 scope link metric 1004Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 11.4. Configuring the VLAN on the Server
Important
yes is important to ensure that the VLAN interface does not attempt to come up before the bond is up. This is because a VLAN virtual device takes the MAC address of its parent, and when a NIC is enslaved, the bond changes its MAC address to that NIC's MAC address.
Note
fail_over_mac=follow option, because the VLAN virtual device cannot change its MAC address to match the parent's new MAC address. In such a case, traffic would still be sent with the now incorrect source MAC address.
- Create a VLAN interface file
bond0.192:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Bring up the VLAN interface as
root:ifup /etc/sysconfig/network-scripts/ifcfg-bond0.192 Determining if ip address 192.168.10.1 is already in use for device bond0.192...
~]# ifup /etc/sysconfig/network-scripts/ifcfg-bond0.192 Determining if ip address 192.168.10.1 is already in use for device bond0.192...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Enabling VLAN tagging on the network switch. Consult the documentation for the switch to see what configuration is required.
- Check the status of the interfaces on the server:Notice there is now
Copy to Clipboard Copied! Toggle word wrap Toggle overflow bond0.192@bond0in the list of interfaces and the status isMASTER,UP. - Check the route on the server:Notice there is now a route for the
ip route 192.168.100.0/24 dev bond0 proto kernel scope link src 192.168.100.100 192.168.10.0/24 dev bond0.192 proto kernel scope link src 192.168.10.1 169.254.0.0/16 dev bond0 scope link metric 1004 169.254.0.0/16 dev bond0.192 scope link metric 1005
~]$ ip route 192.168.100.0/24 dev bond0 proto kernel scope link src 192.168.100.100 192.168.10.0/24 dev bond0.192 proto kernel scope link src 192.168.10.1 169.254.0.0/16 dev bond0 scope link metric 1004 169.254.0.0/16 dev bond0.192 scope link metric 1005Copy to Clipboard Copied! Toggle word wrap Toggle overflow 192.168.10.0/24network pointing to the VLAN interfacebond0.192.
Configuring the Second Server
IP addresses but from the same subnets respectively.
Testing the VLAN
Optional Steps
- If required, perform further tests by removing and replacing network cables one at a time to verify that failover works as expected. Make use of the ethtool utility to verify which interface is connected to which cable. For example:Where integer is the number of times to flash the LED on the network interface.
ethtool --identify ifname integer
ethtool --identify ifname integerCopy to Clipboard Copied! Toggle word wrap Toggle overflow - The bonding module does not support
STP, therefore consider disabling the sending of BPDU packets from the network switch. - If the system is not linked to the network except over the connection just configured, consider enabling the switch port to transition directly to sending and receiving. For example on a Cisco switch, by means of the
portfastcommand.
11.2.6. Network Bridge
/etc/sysconfig/network-scripts/ directory called ifcfg-brN, replacing N with the number for the interface, such as 0.
- The
DEVICEdirective is given an interface name as its argument in the formatbrN, where N is replaced with the number of the interface. - The
TYPEdirective is given an argumentBridge. This directive determines the device type and the argument is case sensitive. - The bridge interface configuration file now has the
IPaddress and the physical interface has only a MAC address. - An extra directive,
DELAY=0, is added to prevent the bridge from waiting while it monitors traffic, learns where hosts are located, and builds a table of MAC addresses on which to base its filtering decisions. The default delay of 15 seconds is not needed if no routing loops are possible. - The
NM_CONTROLLED=noshould be added to the Ethernet interface to prevent NetworkManager from altering the file. It can also be added to the bridge configuration file in case future versions of NetworkManager support bridge configuration.
IP address:
Example 11.4. Sample ifcfg-br0 interface configuration file
/etc/sysconfig/network-scripts/ifcfg-ethX, where X is a unique number corresponding to a specific interface, as follows:
Example 11.5. Sample ifcfg-ethX interface configuration file
Note
DEVICE directive, almost any interface name could be used as it does not determine the device type. Other commonly used names include tap, dummy and bond for example. TYPE=Ethernet is not strictly required. If the TYPE directive is not set, the device is treated as an Ethernet device (unless its name explicitly matches a different interface configuration file.)
Warning
service network restart
service network restart 11.2.6.1. Network Bridge with Bond
Note
ethX as the interface name is common practice but almost any name could be used. Names such as tap, dummy and bond are commonly used.
/etc/sysconfig/network-scripts/ifcfg-bond0, as follows:
DEVICE=bond0 ONBOOT=yes BONDING_OPTS='mode=1 miimon=100' BRIDGE=br0 NM_CONTROLLED=no
DEVICE=bond0
ONBOOT=yes
BONDING_OPTS='mode=1 miimon=100'
BRIDGE=br0
NM_CONTROLLED=no/etc/sysconfig/network-scripts/ifcfg-br0, as follows:
Figure 11.1. A network bridge consisting of two bonded Ethernet interfaces.
MASTER=bond0 directive. These point to the configuration file named /etc/sysconfig/network-scripts/ifcfg-bond0, which contains the DEVICE=bond0 directive. This ifcfg-bond0 in turn points to the /etc/sysconfig/network-scripts/ifcfg-br0 configuration file, which contains the IP address, and acts as an interface to the virtual networks inside the host.
root in the following format: ifup device
ifup deviceservice network restart
~]# service network restart11.2.6.2. Network Bridge with Bonded VLAN
- Ensure the bond and VLAN have been configured as outlined in Section 11.2.5, “Configuring a VLAN over a Bond”.
- Create the bridge's configuration file,
ifcfg-br0:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Adjust the VLAN's configuration file,
ifcfg-bond0.192from the earlier example, to use the newly createdbr0as its master:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To bring up the new or recently configured interfaces, issue a command as
rootin the following format:ifup device
ifup deviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, restart the networking service, in order for the changes to take effect, as follows:service network restart
~]# service network restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.2.7. Setting Up 802.1Q VLAN Tagging
- If required, start the VLAN 8021q module by issuing the following command as
root:No visual output indicates the module was not running and has now been loaded. Note that given a correct configuration file, the VLAN 8021q module will be loaded as required and therefore does not need to be loaded separately.modprobe --first-time 8021q
~]# modprobe --first-time 8021qCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure your physical interface in
/etc/sysconfig/network-scripts/ifcfg-ethX, where X is a unique number corresponding to a specific interface, as follows:DEVICE=ethX TYPE=Ethernet BOOTPROTO=none ONBOOT=yes
DEVICE=ethX TYPE=Ethernet BOOTPROTO=none ONBOOT=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the VLAN interface configuration in
/etc/sysconfig/network-scripts. The configuration filename should be the physical interface plus a.character plus the VLAN ID number. For example, if the VLAN ID is 192, and the physical interface iseth0, then the configuration filename should beifcfg-eth0.192:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If there is a need to configure a second VLAN, with for example, VLAN ID 193, on the same interface,eth0, add a new file with the nameeth0.193with the VLAN configuration details. - Restart the networking service, in order for the changes to take effect. Issue the following command as
root:service network restart
~]# service network restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.2.8. Alias and Clone Files
man ip(8) page. The package name in Red Hat Enterprise Linux 6 is iproute.
Note
ifcfg alias files and assigns the addresses in them to their master interface, using the alias name as the address label. For example, if ifcfg-eth0 and ifcfg-eth0:1 files are present, NetworkManager reads the alias file's DEVICE line and stores this as an address label. The use of secondary addresses rather than alias is still preferred.
IPv4 or IPv6 tab in NetworkManager to assign multiple IP address to the same interface. For more information on using this tool, see Chapter 10, NetworkManager.
ifcfg-if-name:alias-value naming scheme.
ifcfg-eth0:0 file could be configured to specify DEVICE=eth0:0 and a static IP address of 10.0.0.2, serving as an alias of an Ethernet interface already configured to receive its IP information via DHCP in ifcfg-eth0. Under this configuration, eth0 is bound to a dynamic IP address, but the same physical network card can receive requests via the fixed, 10.0.0.2 IP address.
Warning
DHCP.
ifcfg-if-name-clone-name. While an alias file allows multiple addresses for an existing interface, a clone file is used to specify additional options for an interface. For example, a standard DHCP Ethernet interface called eth0, may look similar to this:
DEVICE=eth0 ONBOOT=yes BOOTPROTO=dhcp
DEVICE=eth0
ONBOOT=yes
BOOTPROTO=dhcpUSERCTL directive is no if it is not specified, users cannot bring this interface up and down. To give users the ability to control the interface, create a clone by copying ifcfg-eth0 to ifcfg-eth0-user and add the following line to ifcfg-eth0-user:
USERCTL=yes
USERCTL=yeseth0 interface using the /sbin/ifup eth0-user command because the configuration options from ifcfg-eth0 and ifcfg-eth0-user are combined. While this is a very basic example, this method can be used with a variety of options and interfaces.
IP address to the same interface. For new installations, users should select the Manual method on the IPv4 or IPv6 tab in NetworkManager to assign multiple IP address to the same interface. For more information on using this tool, see Chapter 10, NetworkManager.
11.2.9. Dialup Interfaces
PPP interface files are named using the following format:
ifcfg-pppX- where X is a unique number corresponding to a specific interface.
PPP interface configuration file is created automatically when wvdial, or Kppp is used to create a dialup account. It is also possible to create and edit this file manually.
/etc/sysconfig/network-scripts/ifcfg-ppp0 file:
SLIP files have interface configuration file names such as ifcfg-sl0.
-
DEFROUTE=answer - where answer is one of the following:
yes— Set this interface as the default route.no— Do not set this interface as the default route.
DEMAND=answer- where answer is one of the following:
yes— This interface allowspppdto initiate a connection when someone attempts to use it.no— A connection must be manually established for this interface.
IDLETIMEOUT=value- where value is the number of seconds of idle activity before the interface disconnects itself.
INITSTRING=string- where string is the initialization string passed to the modem device. This option is primarily used in conjunction with
SLIPinterfaces. LINESPEED=value- where value is the baud rate of the device. Possible standard values include
57600,38400,19200, and9600. MODEMPORT=device- where device is the name of the serial device that is used to establish the connection for the interface.
MTU=value- where value is the Maximum Transfer Unit (MTU) setting for the interface. The MTU refers to the largest number of bytes of data a frame can carry, not counting its header information. In some dialup situations, setting this to a value of
576results in fewer packets dropped and a slight improvement to the throughput for a connection. NAME=name- where name is the reference to the title given to a collection of dialup connection configurations.
PAPNAME=name- where name is the user name given during the Password Authentication Protocol (PAP) exchange that occurs to allow connections to a remote system.
PERSIST=answer- where answer is one of the following:
yes— This interface should be kept active at all times, even if deactivated after a modem hang up.no— This interface should not be kept active at all times.
REMIP=address- where address is the
IPaddress of the remote system. This is usually left unspecified. -
WVDIALSECT=name - where name associates this interface with a dialer configuration in
/etc/wvdial.conf. This file contains the phone number to be dialed and other important information for the interface.
11.2.10. Other Interfaces
ifcfg-lo- A local loopback interface is often used in testing, as well as being used in a variety of applications that require an
IPaddress pointing back to the same system. Any data sent to the loopback device is immediately returned to the host's network layer.Warning
The loopback interface script,/etc/sysconfig/network-scripts/ifcfg-lo, should never be edited manually. Doing so can prevent the system from operating correctly. ifcfg-irlan0- An infrared interface allows information between devices, such as a laptop and a printer, to flow over an infrared link. This works in a similar way to an Ethernet device except that it commonly occurs over a peer-to-peer connection.
ifcfg-plip0- A Parallel Line Interface Protocol (PLIP) connection works much the same way as an Ethernet device, except that it utilizes a parallel port.
ifcfg-hsiN- A HiperSockets interface is an interface for high-speed TCP/IP communication within and across z/VM guest virtual machines and logical partitions (LPARs) on an IBM System z mainframe.
11.3. Interface Control Scripts
/etc/sysconfig/network-scripts/ directory: /sbin/ifdown and /sbin/ifup.
ifup and ifdown interface scripts are symbolic links to scripts in the /sbin/ directory. When either of these scripts are called, they require the value of the interface to be specified, such as:
ifup eth0
ifup eth0Warning
ifup and ifdown interface scripts are the only scripts that the user should use to bring up and take down network interfaces.
/etc/rc.d/init.d/functions and /etc/sysconfig/network-scripts/network-functions. See Section 11.7, “Network Function Files” for more information.
/etc/sysconfig/network-scripts/ directory:
ifup-aliases- Configures
IPaliases from interface configuration files when more than oneIPaddress is associated with an interface. ifup-ipppandifdown-ippp- Brings ISDN interfaces up and down.
ifup-ipv6andifdown-ipv6- Brings
IPv6interfaces up and down. ifup-plip- Brings up a
PLIPinterface. ifup-plusb- Brings up a USB interface for network connections.
ifup-postandifdown-post- Contains commands to be executed after an interface is brought up or down.
ifup-pppandifdown-ppp- Brings a
PPPinterface up or down. ifup-routes- Adds static routes for a device as its interface is brought up.
ifdown-sitandifup-sit- Contains function calls related to bringing up and down an
IPv6tunnel within anIPv4connection. ifup-wireless- Brings up a wireless interface.
Warning
/etc/sysconfig/network-scripts/ directory can cause interface connections to act irregularly or fail. Only advanced users should modify scripts related to a network interface.
/sbin/service command on the network service (/etc/rc.d/init.d/network), as illustrated by the following command:
/sbin/service network action
/sbin/service network actionstart, stop, or restart.
/sbin/service network status
/sbin/service network status11.4. Static Routes and the Default Gateway
Configuring Static Routes Using the Command Line
ip route add command and removed using the ip route del command. The more frequently used ip route commands take the following form: ip route [ add | del | change | append | replace ] destination-address
ip route [ add | del | change | append | replace ] destination-addressip-route(8) man page for more details on the options and formats.
ip route command without options to display the IP routing table. For example:
ip route default via 192.168.122.1 dev eth0 proto static metric 1024 192.168.122.0/24 dev ens9 proto kernel scope link src 192.168.122.107 192.168.122.0/24 dev eth0 proto kernel scope link src 192.168.122.126
~]$ ip route
default via 192.168.122.1 dev eth0 proto static metric 1024
192.168.122.0/24 dev ens9 proto kernel scope link src 192.168.122.107
192.168.122.0/24 dev eth0 proto kernel scope link src 192.168.122.126IP address, issue a command as root:
ip route add 192.0.2.1 via 10.0.0.1 [dev ifname]
~]# ip route add 192.0.2.1 via 10.0.0.1 [dev ifname]IP address of the host in dotted decimal notation, 10.0.0.1 is the next hop address and ifname is the exit interface leading to the next hop.
IP address representing a range of IP addresses, issue the following command as root:
ip route add 192.0.2.0/24 via 10.0.0.1 [dev ifname]
~]# ip route add 192.0.2.0/24 via 10.0.0.1 [dev ifname]IP address of the destination network in dotted decimal notation and /24 is the network prefix. The network prefix is the number of enabled bits in the subnet mask. This format of network address slash network prefix length is sometimes referred to as classless inter-domain routing (CIDR) notation.
/etc/sysconfig/network-scripts/route-interface file. For example, static routes for the eth0 interface would be stored in the /etc/sysconfig/network-scripts/route-eth0 file. The route-interface file has two formats: ip command arguments and network/netmask directives. These are described below.
ip-route(8) man page for more information on the ip route command.
Configuring The Default Gateway
/etc/sysconfig/network file first and then the network interface ifcfg files for interfaces that are “up”. The ifcfg files are parsed in numerically ascending order, and the last GATEWAY directive to be read is used to compose a default route in the routing table.
DHCP. In special cases where it is necessary to influence NetworkManager's selection of the exit interface to be used to reach a gateway, make use of the DEFROUTE=no command in the ifcfg files for those interfaces which do not lead to the default gateway.
/etc/sysconfig/network file. This file specifies gateway and host information for all network interfaces. For more information about this file and the directives it accepts, see Section D.1.14, “/etc/sysconfig/network”.
11.5. Configuring Static Routes in ifcfg files
/etc/sysconfig/network-scripts/ directory. The file name should be of the format route-ifname. There are two types of commands to use in the configuration files; ip commands as explained in Section 11.5.1, “Static Routes Using the IP Command Arguments Format” and the Network/Netmask format as explained in Section 11.5.2, “Network/Netmask Directives Format”.
11.5.1. Static Routes Using the IP Command Arguments Format
/etc/sysconfig/network-scripts/route-eth0, define a route to a default gateway on the first line. This is only required if the gateway is not set via DHCP and is not set globally in the /etc/sysconfig/network file:
default via 192.168.1.1 dev interface
default via 192.168.1.1 dev interfaceIP address of the default gateway. The interface is the interface that is connected to, or can reach, the default gateway. The dev option can be omitted, it is optional. Note that this setting takes precedence over a setting in the /etc/sysconfig/network file.
10.10.10.0/24 via 192.168.1.1 [dev interface]
10.10.10.0/24 via 192.168.1.1 [dev interface]IP address leading to the remote network. It is preferably the next hop address but the address of the exit interface will work. The “next hop” means the remote end of a link, for example a gateway or router. The dev option can be used to specify the exit interface interface but it is not required. Add as many static routes as required.
route-interface file using the ip command arguments format. The default gateway is 192.168.0.1, interface eth0 and a leased line or WAN connection is available at 192.168.0.10. The two static routes are for reaching the 10.10.10.0/24 network and the 172.16.1.10/32 host:
default via 192.168.0.1 dev eth0 10.10.10.0/24 via 192.168.0.10 dev eth0 172.16.1.10/32 via 192.168.0.10 dev eth0
default via 192.168.0.1 dev eth0
10.10.10.0/24 via 192.168.0.10 dev eth0
172.16.1.10/32 via 192.168.0.10 dev eth0192.168.0.0/24 network will be directed out the interface attached to that network. Packets going to the 10.10.10.0/24 network and 172.16.1.10/32 host will be directed to 192.168.0.10. Packets to unknown, remote, networks will use the default gateway therefore static routes should only be configured for remote networks or hosts if the default route is not suitable. Remote in this context means any networks or hosts that are not directly attached to the system.
Important
DHCP, the IP command arguments format can cause one of two errors during start-up, or when bringing up an interface from the down state using the ifup command: "RTNETLINK answers: File exists" or 'Error: either "to" is a duplicate, or "X.X.X.X" is a garbage.', where X.X.X.X is the gateway, or a different IP address. These errors can also occur if you have another route to another network using the default gateway. Both of these errors are safe to ignore.
11.5.2. Network/Netmask Directives Format
route-interface files. The following is a template for the network/netmask format, with instructions following afterwards:
ADDRESS0=10.10.10.0 NETMASK0=255.255.255.0 GATEWAY0=192.168.1.1
ADDRESS0=10.10.10.0
NETMASK0=255.255.255.0
GATEWAY0=192.168.1.1ADDRESS0=10.10.10.0is the network address of the remote network or host to be reached.NETMASK0=255.255.255.0is the netmask for the network address defined withADDRESS0=10.10.10.0.GATEWAY0=192.168.1.1is the default gateway, or anIPaddress that can be used to reachADDRESS0=10.10.10.0
route-interface file using the network/netmask directives format. The default gateway is 192.168.0.1 but a leased line or WAN connection is available at 192.168.0.10. The two static routes are for reaching the 10.10.10.0/24 and 172.16.1.0/24 networks:
ADDRESS0, ADDRESS1, ADDRESS2, and so on.
11.6. Configuring IPv6 Tokenized Interface Identifiers
DHCP server which may fail or run out of addresses. The IPv6 protocol introduced Stateless Address Autoconfiguration (SLAAC) which enables clients to assign themselves an address without relying on a DHCPv6 server. SLAAC derives the IPv6 address based on the interface hardware, therefore it should not be used for servers in case the hardware is changed and the associated SLAAC generated address changes with it. In an IPv6 environment, if the network prefix is changed, or the system is moved to a new location, any manually configured static addresses would have to be edited due to the changed prefix.
ip utility. This enables the lower 64 bit interface identifier part of the IPv6 address to be based on a token, supplied by the administrator, leaving the network prefix, the higher 64 bits, to be obtained from router advertisements (RA). This means that if the network interface hardware is changed, the lower 64 bits of the address will not change, and if the system is moved to another network, the network prefix will be obtained from router advertisements automatically, thus no manual editing is required.
IPv6 identifier, issue a command in the following format as root user:
ip token set ::1a:2b:3c:4d/64 dev eth4
~]# ip token set ::1a:2b:3c:4d/64 dev eth4::1a:2b:3c:4d/64 is the token to be used. This setting is not persistent. To make it persistent, add the command to an init script. See Section 11.3, “Interface Control Scripts”.
DNS server, which traditionally uses port 53, a token of ::53/64 could be used.
IPv6 tokens, issue the following command:
IPv6 token for a specific interface, issue the following command:
ip token get dev eth4
token ::1a:2b:3c:4d dev eth4
~]$ ip token get dev eth4
token ::1a:2b:3c:4d dev eth4IP address.
Note
11.7. Network Function Files
/etc/sysconfig/network-scripts/network-functions file contains the most commonly used IPv4 functions, which are useful to many interface control scripts. These functions include contacting running programs that have requested information about changes in the status of an interface, setting host names, finding a gateway device, verifying whether or not a particular device is down, and adding a default route.
IPv6 interfaces are different from IPv4 interfaces, a /etc/sysconfig/network-scripts/network-functions-ipv6 file exists specifically to hold this information. The functions in this file configure and delete static IPv6 routes, create and remove tunnels, add and remove IPv6 addresses to an interface, and test for the existence of an IPv6 address on an interface.
11.8. Ethtool
ethtool -h or see the man page, ethtool(8), for a more comprehensive list and explanation. The first two examples are information queries and show the use of the different formats of the command.
ethtool [option...] devname
ethtool [option...] devnameroot. Here is an example of the output when the command is run as root:
ethtool -i, --driver devname
ethtool -i, --driver devname-short and --long form:
-
--statistics - The
--statisticsor-Squeries the specified network device for NIC and driver statistics. It takes the following form:-S, --statistics devname
-S, --statistics devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where devname is your NIC. -
--identify - The
--identifyor-poption initiates adapter-specific action intended to enable an operator to easily identify the adapter by sight. Typically this involves blinking one or more LEDs on the specified network port. It takes the following form:-p, --identify devname integer
-p, --identify devname integerCopy to Clipboard Copied! Toggle word wrap Toggle overflow where integer is length of time in seconds to perform the action,and devname is your NIC. -
--show-time-stamping - The
--show-time-stampingor-Toption queries the specified network device for time stamping parameters. It takes the following form:-T, --show-time-stamping devname
-T, --show-time-stamping devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where devname is your NIC. -
--show-offload - The
--show-features, or--show-offload, or-koption queries the specified network device for the state of protocol offload and other features. It takes the following form:-k, --show-features, --show-offload devname
-k, --show-features, --show-offload devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where devname is your NIC. -
--test - The
--testor-toption is used to perform tests on a Network Interface Card. It takes the following form:-t, --test devname word
-t, --test devname wordCopy to Clipboard Copied! Toggle word wrap Toggle overflow where word is one of the following:offline— Perform a comprehensive set of tests. Service will be interrupted.online— Perform a reduced set of tests. Service should not be interrupted.external_lb— Perform full set of tests including loopback tests while fitted with a loopback cable.
and devname is your NIC.
-s or --change option. All the following options are only applied if the -s or --change option is also specified. For the sake of clarity we will omit it here.
ETHTOOL_OPTS directive. It can be used in interface configuration files to set the desired options when the network interface is brought up. See Section 11.2.1, “Ethernet Interfaces” for more details on how to use this directive.
-
--offload - The
--features, or--offload, or-Koption changes the offload parameters and other features of the specified network device. It takes the following form:-K, --features, --offload devname feature boolean
-K, --features, --offload devname feature booleanCopy to Clipboard Copied! Toggle word wrap Toggle overflow where feature is a built-in or kernel supplied feature,boolean is one ofONorOFF,and devname is your NIC.Theethtool(8)man page lists most features. As the feature set is dependent on the NIC driver, you should consult the driver documentation for features not listed in the man page. -
--speed - The
--speedoption is used to set the speed in megabits per second (Mb/s). Omitting the speed value will show the supported device speeds. It takes the following form:--speed number devname
--speed number devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where number is the speed in megabits per second (Mb/s),and devname is your NIC. -
--duplex - The
--duplexoption is used to set the transmit and receive mode of operation. It takes the following form:--duplex word devname
--duplex word devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where word is one of the following:half— Sets half-duplex mode. Usually used when connected to a hub.full— Sets full-duplex mode. Usually used when connected to a switch or another host.
and devname is your NIC. -
--port - The
--portoption is used to select the device port . It takes the following form:--port value devname
--port value devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where value is one of the following:tp— An Ethernet interface using Twisted-Pair cable as the medium.aui— Attachment Unit Interface (AUI). Normally used with hubs.bnc— An Ethernet interface using BNC connectors and co-axial cable.mii— An Ethernet interface using a Media Independent Interface (MII).fibre— An Ethernet interface using Optical Fibre as the medium.
and devname is your NIC. -
--autoneg - The
--autonegoption is used to control auto-negotiation of network speed and mode of operation (full-duplex or half-duplex mode). If auto-negotiation is enabled you can initiate re-negotiation of network speeds and mode of operation by using the-r, --negotiateoption. You can display the auto-negotiation state using the--a, --show-pauseoption.It takes the following form:--autoneg value devname
--autoneg value devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where value is one of the following:yes— Allow auto-negotiating of network speed and mode of operation.no— Do not allow auto-negotiating of network speed and mode of operation.
and devname is your NIC. -
--advertise - The
--advertiseoption is used to set what speeds and modes of operation (duplex mode) are advertised for auto-negotiation. The argument is one or more hexadecimal values from Table 11.1, “Ethtool advertise options: speed and mode of operation”.It takes the following form:--advertise option devname
--advertise option devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where option is one or more of the hexadecimal values from the table below and devname is your NIC.Expand Table 11.1. Ethtool advertise options: speed and mode of operation Hex Value Speed Duplex Mode IEEE standard? 0x001 10 HalfYes 0x002 10 FullYes 0x004 100 HalfYes 0x008 100 FullYes 0x010 1000 Half No 0x020 1000 FullYes 0x8000 2500 Full Yes 0x1000 10000 Full Yes 0x20000 20000MLD2 Full No 0x20000 20000MLD2 Full No 0x40000 20000KR2 Full No -
--phyad - The
--phyadoption is used to change the physical address. Often referred to as the MAC or hardware address but in this context referred to as the physical address.It takes the following form:--phyad physical_address devname
--phyad physical_address devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where physical_address is the physical address in hexadecimal format and devname is your NIC. -
--xcvr - The
--xcvroption is used to select the transceiver type. Currently only “internal” and “external” can be specified. In the future other types might be added.It takes the following form:--xcvr word devname
--xcvr word devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where word is one of the following:internal— Use internal transceiver.external— Use external transceiver.
and devname is your NIC. -
--wol - The
--woloption is used to set “Wake-on-LAN” options. Not all devices support this. The argument to this option is a string of characters specifying which options to enable.It takes the following form:--wol value devname
--wol value devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where value is one or more of the following:p— Wake on PHY activity.u— Wake on unicast messages.m— Wake on multicast messages.b— Wake on broadcast messages.g— Wake-on-Lan; wake on receipt of a "magic packet".s— Enable security function using password for Wake-on-Lan.d— Disable Wake-on-Lan and clear all settings.
and devname is your NIC. -
--sopass - The
--sopassoption is used to set the “SecureOn” password. The argument to this option must be 6 bytes in Ethernet MAC hexadecimal format (xx:yy:zz:aa:bb:cc).It takes the following form:--sopass xx:yy:zz:aa:bb:cc devname
--sopass xx:yy:zz:aa:bb:cc devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where xx:yy:zz:aa:bb:cc is the password in the same format as a MAC address and devname is your NIC. -
--msglvl - The
--msglvloption is used to set the driver message-type flags by name or number. The precise meanings of these type flags differ between drivers.It takes the following form:--msglvl message_type devname
--msglvl message_type devnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow where message_type is one of:- message type name in plain text.
- hexadecimal number indicating the message type.
and devname is your NIC.The defined message type names and numbers are shown in the table below:Expand Table 11.2. Driver message type Message Type Hex Value Description drv 0x0001 General driver statusprobe 0x0002 Hardware probinglink 0x0004 Link statetimer 0x0008 Periodic status checkifdown 0x0010 Interface being brought down ifup 0x0020 Interface being brought uprx_err 0x0040 Receive error tx_err 0x0080 Transmit error intr 0x0200 Interrupt handling tx_done 0x0400 Transmit completion rx_status 0x0800 Receive completion pktdata 0x1000 Packet contents hw 0x2000 Hardware status wol 0x4000 Wake-on-LAN status
11.9. Configuring netconsole
netconsole kernel module enables logging of kernel messages over the network to another computer. It allows kernel debugging when disk logging fails or when using the serial console is not possible.
Configuring a Listening Machine
netconsole logging messages, install the rsyslog package:
yum install rsyslog
]# yum install rsyslogrsyslogd to listen on the 514/UDP port and receive messages from the network, uncomment the following lines in the MODULES section of /etc/rsyslog.conf:
$ModLoad imudp $UDPServerRun 514
$ModLoad imudp
$UDPServerRun 514rsyslogd service for the changes to take effect:
service rsyslog restart
]# service rsyslog restartrsyslogd is listening on the 514/udp port, use the following command:
netstat -l | grep syslog udp 0 0 *:syslog *:* udp 0 0 *:syslog *:*
]# netstat -l | grep syslog
udp 0 0 *:syslog *:*
udp 0 0 *:syslog *:*0 *:syslog value in the netstat -l output mean that rsyslogd is listening on default netconsole port, which is defined in the /etc/services file:
]$ cat /etc/services | grep syslog syslog 514/udp syslog-conn 601/tcp # Reliable Syslog Service syslog-conn 601/udp # Reliable Syslog Service syslog-tls 6514/tcp # Syslog over TLS
]$ cat /etc/services | grep syslog
syslog 514/udp
syslog-conn 601/tcp # Reliable Syslog Service
syslog-conn 601/udp # Reliable Syslog Service
syslog-tls 6514/tcp # Syslog over TLSConfiguring a Sending Machine
netconsole is configured using the file /etc/sysconfig/netconsole, which is part of the initscripts package. This package is installed by default and it also provides the netconsole service.
SYSLOGADDR variable in the /etc/sysconfig/netconsole file to match the IP address of the syslogd server, for example:
SYSLOGADDR=192.168.0.1
SYSLOGADDR=192.168.0.1netconsole service so the changes take effect. Then, use the chkconfig command to ensure netconsole service starts automatically after next reboot:
service netconsole restart Initializing netconsole [ OK ] chkconfig netconsole on
]# service netconsole restart
Initializing netconsole [ OK ]
]# chkconfig netconsole onrsyslogd server writes the netconsole messages from the client in /var/log/messages or in the file specified in rsyslog.conf.
Note
rsyslogd and netconsole to use a different port, change the following line in /etc/rsyslog.conf to the desired port number:
$UDPServerRun <PORT>
$UDPServerRun <PORT>/etc/sysconfig/netconsole file:
SYSLOGPORT=514
SYSLOGPORT=514netconsole configuration and troubleshooting tips, see Netconsole Kernel Documentation.
11.10. Additional Resources
Installed Documentation
/usr/share/doc/initscripts-version/sysconfig.txt— A guide to available options for network configuration files, includingIPv6options not covered in this chapter.
Online Resources
- http://linux-ip.net/gl/ip-cref/ — This document contains a wealth of information about the
ipcommand, which can be used to manipulate routing tables, among other things. - Red Hat Access Labs — The Red Hat Access Labs includes a “Network Bonding Helper”.
See Also
- Appendix E, The proc File System — Describes the sysctl utility and the virtual files within the
/proc/directory, which contain networking parameters and statistics among other things.
Part V. Infrastructure Services
Chapter 12. Services and Daemons
httpd if you are running a web server). However, if you do not need to provide a service, you should turn it off to minimize your exposure to possible bug exploits.
Important
12.1. Configuring the Default Runlevel
| Runlevel | Description |
|---|---|
0 | Used to halt the system. This runlevel is reserved and cannot be changed. |
1 | Used to run in a single-user mode. This runlevel is reserved and cannot be changed. |
2 | Not used by default. You are free to define it yourself. |
3 | Used to run in a full multi-user mode with a command-line user interface. |
4 | Not used by default. You are free to define it yourself. |
5 | Used to run in a full multi-user mode with a graphical user interface. |
6 | Used to reboot the system. This runlevel is reserved and cannot be changed. |
runlevel N 5
~]$ runlevel
N 5runlevel command displays previous and current runlevel. In this case it is number 5, which means the system is running in a full multi-user mode with a graphical user interface.
/etc/inittab file, which contains a line near the end of the file similar to the following:
id:5:initdefault:
id:5:initdefault:root and change the number on this line to the desired value. The change will take effect the next time you reboot the system.
12.2. Configuring the Services
Important
irqbalance service is enabled. In most cases, this service is installed and configured to run during the Red Hat Enterprise Linux 6 installation. To verify that irqbalance is running, as root, type the following at a shell prompt:
service irqbalance status irqbalance (pid 1234) is running...
~]# service irqbalance status
irqbalance (pid 1234) is running...12.2.1. Using the Service Configuration Utility
system-config-services at a shell prompt.
Note
system-config-services utility is provided by the system-config-services package, which may not be installed by default on your version of Red Hat Enterprise Linux. To ensure that, first run the following command:
rpm -q system-config-services
~]$ rpm -q system-config-servicesyum install system-config-services
~]# yum install system-config-servicesFigure 12.1. The Service Configuration utility
/etc/rc.d/init.d/ directory, as well as services controlled by xinetd) along with their description and the current status. For a complete list of used icons and an explanation of their meaning, see Table 12.2, “Possible service states”.
| Icon | Description |
|---|---|

| The service is enabled. |

| The service is disabled. |

| The service is enabled for selected runlevels only. |

| The service is running. |

| The service is stopped. |

| There is something wrong with the service. |

| The status of the service is unknown. |
12.2.1.1. Enabling and Disabling a Service
12.2.1.2. Starting, Restarting, and Stopping a Service
12.2.1.3. Selecting Runlevels
12.2.2. Using the ntsysv Utility
ntsysv at a shell prompt as root.
Figure 12.2. The ntsysv utility
/etc/rc.d/init.d/ directory) along with their current status and a description obtainable by pressing F1. For a list of used symbols and an explanation of their meaning, see Table 12.3, “Possible service states”.
| Symbol | Description |
|---|---|
| [*] | The service is enabled. |
| [ ] | The service is disabled. |
12.2.2.1. Enabling and Disabling a Service
service command as described in Section 12.3.2, “Starting a Service”.
12.2.2.2. Selecting Runlevels
root, run the command with the additional --level option followed by numbers from 0 to 6 representing each runlevel you want to configure:
ntsysv --level runlevels
ntsysv --level runlevelsntsysv --level 35
~]# ntsysv --level 3512.2.3. Using the chkconfig Utility
12.2.3.1. Listing the Services
/etc/rc.d/init.d/ directory, as well as the services controlled by xinetd), either type chkconfig --list, or use chkconfig with no additional arguments. You will be presented with an output similar to the following:
chkconfig --list followed by the name of the service:
chkconfig --list service_name
chkconfig --list service_namesshd service, type:
chkconfig --list sshd sshd 0:off 1:off 2:on 3:on 4:on 5:on 6:off
~]# chkconfig --list sshd
sshd 0:off 1:off 2:on 3:on 4:on 5:on 6:offchkconfig --list rsync rsync off
~]# chkconfig --list rsync
rsync off12.2.3.2. Enabling a Service
root:
chkconfig service_name on
chkconfig service_name onhttpd service in these four runlevels, type:
chkconfig httpd on
~]# chkconfig httpd on--level option followed by numbers from 0 to 6 representing each runlevel in which you want the service to run:
chkconfig service_name on --level runlevels
chkconfig service_name on --level runlevelschkconfig abrtd on --level 35
~]# chkconfig abrtd on --level 35service command as described in Section 12.3.2, “Starting a Service”.
--level option when working with a service that is managed by xinetd, as it is not supported. For example, to enable the rsync service, type:
chkconfig rsync on
~]# chkconfig rsync on12.2.3.3. Disabling a Service
root:
chkconfig service_name off
chkconfig service_name offhttpd service in these four runlevels, type:
chkconfig httpd off
~]# chkconfig httpd off--level option followed by numbers from 0 to 6 representing each runlevel in which you do not want the service to run:
chkconfig service_name off --level runlevels
chkconfig service_name off --level runlevelschkconfig abrtd off --level 24
~]# chkconfig abrtd off --level 24service command as described in Section 12.3.3, “Stopping a Service”.
--level option when working with a service that is managed by xinetd, as it is not supported. For example, to disable the rsync service, type:
chkconfig rsync off
~]# chkconfig rsync off12.3. Running Services
/etc/init.d/ directory.
12.3.1. Determining the Service Status
service service_name status
service service_name statushttpd service, type:
service httpd status httpd (pid 7474) is running...
~]# service httpd status
httpd (pid 7474) is running...service command with the --status-all option:
12.3.2. Starting a Service
root:
service service_name start
service service_name starthttpd service, type:
service httpd start Starting httpd: [ OK ]
~]# service httpd start
Starting httpd: [ OK ]12.3.3. Stopping a Service
root:
service service_name stop
service service_name stophttpd service, type:
service httpd stop Stopping httpd: [ OK ]
~]# service httpd stop
Stopping httpd: [ OK ]12.3.4. Restarting a Service
root:
service service_name restart
service service_name restarthttpd service, type:
service httpd restart Stopping httpd: [ OK ] Starting httpd: [ OK ]
~]# service httpd restart
Stopping httpd: [ OK ]
Starting httpd: [ OK ]12.4. Additional Resources
12.4.1. Installed Documentation
- chkconfig(8) — a manual page for the chkconfig utility.
- ntsysv(8) — a manual page for the ntsysv utility.
- service(8) — a manual page for the service utility.
- system-config-services(8) — a manual page for the system-config-services utility.
12.4.2. Related Books
- Red Hat Enterprise Linux 6 Security Guide
- A guide to securing Red Hat Enterprise Linux 6. It contains valuable information on how to set up the firewall, as well as the configuration of SELinux.
Chapter 13. Configuring Authentication
13.1. Configuring System Authentication
Important
13.1.1. Launching the Authentication Configuration Tool UI
- Log into the system as root.
- Open the .
- Select the menu.
- Select the item.
system-config-authentication command.
Important
- Identity & Authentication, which configures the resource used as the identity store (the data repository where the user IDs and corresponding credentials are stored).
- Advanced Options, which allows authentication methods other than passwords or certificates, like smart cards and fingerprint.
13.1.2. Selecting the Identity Store for Authentication
Figure 13.1. Local Authentication
13.1.2.1. Configuring LDAP Authentication
- Open the Authentication Configuration Tool, as in Section 13.1.1, “Launching the Authentication Configuration Tool UI”.
- Select in the User Account Database drop-down menu.
- Set the information that is required to connect to the LDAP server.
- LDAP Search Base DN gives the root suffix or distinguished name (DN) for the user directory. All of the user entries used for identity/authentication will exist below this parent entry. For example, ou=people,dc=example,dc=com.This field is optional. If it is not specified, then the System Security Services Daemon (SSSD) attempts to detect the search base using the
namingContextsanddefaultNamingContextattributes in the LDAP server's configuration entry. - LDAP Server gives the URL of the LDAP server. This usually requires both the host name and port number of the LDAP server, such as ldap://ldap.example.com:389.Entering the secure protocol in the URL,
ldaps://, enables the button. - Use TLS to encrypt connections sets whether to use Start TLS to encrypt the connections to the LDAP server. This enables a secure connection over a standard port.Selecting TLS enables the button, which retrieves the issuing CA certificate for the LDAP server from whatever certificate authority issued it. The CA certificate must be in the privacy enhanced mail (PEM) format.
Important
Do not select Use TLS to encrypt connections if the server URL uses a secure protocol (ldaps). This option uses Start TLS, which initiates a secure connection over a standard port; if a secure port is specified, then a protocol like SSL must be used instead of Start TLS.
- Select the authentication method. LDAP allows simple password authentication or Kerberos authentication.Using Kerberos is described in Section 13.1.2.4, “Using Kerberos with LDAP or NIS Authentication”.The LDAP password option uses PAM applications to use LDAP authentication. This option requires either a secure (
ldaps://) URL or the TLS option to connect to the LDAP server.
13.1.2.2. Configuring NIS Authentication
- Install the ypbind package. This is required for NIS services, but is not installed by default.
yum install ypbind
~]# yum install ypbindCopy to Clipboard Copied! Toggle word wrap Toggle overflow When theypbindservice is installed, theportmapandypbindservices are started and enabled to start at boot time. - Open the Authentication Configuration Tool, as in Section 13.1.1, “Launching the Authentication Configuration Tool UI”.
- Select in the User Account Database drop-down menu.
- Set the information to connect to the NIS server, meaning the NIS domain name and the server host name. If the NIS server is not specified, the
authconfigdaemon scans for the NIS server. - Select the authentication method. NIS allows simple password authentication or Kerberos authentication.Using Kerberos is described in Section 13.1.2.4, “Using Kerberos with LDAP or NIS Authentication”.
13.1.2.3. Configuring Winbind Authentication
- Install the samba-winbind package. This is required for Windows integration features in Samba services, but is not installed by default.
yum install samba-winbind
~]# yum install samba-winbindCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Open the Authentication Configuration Tool, as in Section 13.1.1, “Launching the Authentication Configuration Tool UI”.
- Select in the User Account Database drop-down menu.
- Set the information that is required to connect to the Microsoft Active Directory domain controller.
- Winbind Domain gives the Windows domain to connect to.This should be in the Windows 2000 format, such as
DOMAIN. - Security Model sets the security model to use for Samba clients.
authconfigsupports four types of security models:- ads configures Samba to act as a domain member in an Active Directory Server realm. To operate in this mode, the krb5-server package must be installed and Kerberos must be configured properly. Also, when joining to the Active Directory Server using the command line, the following command must be used:
net ads join
net ads joinCopy to Clipboard Copied! Toggle word wrap Toggle overflow - domain has Samba validate the user name/password by authenticating it through a Windows primary or backup domain controller, much like a Windows server.
- server has a local Samba server validate the user name/password by authenticating it through another server, such as a Windows server. If the server authentication attempt fails, the system then attempts to authenticate using
usermode. - user requires a client to log in with a valid user name and password. This mode does support encrypted passwords.The user name format must be domain\user, such as
EXAMPLE\jsmith.Note
When verifying that a given user exists in the Windows domain, always use Windows 2000-style formats and escape the backslash (\) character. For example:getent passwd domain\\user DOMAIN\user:*:16777216:16777216:Name Surname:/home/DOMAIN/user:/bin/bash
~]# getent passwd domain\\user DOMAIN\user:*:16777216:16777216:Name Surname:/home/DOMAIN/user:/bin/bashCopy to Clipboard Copied! Toggle word wrap Toggle overflow This is the default option.
- Winbind ADS Realm gives the Active Directory realm that the Samba server will join. This is only used with the ads security model.
- Winbind Domain Controllers gives the domain controller to use. For more information about domain controllers, see Section 21.1.6.3, “Domain Controller”.
- Template Shell sets which login shell to use for Windows user account settings.
- Allow offline login allows authentication information to be stored in a local cache. The cache is referenced when a user attempts to authenticate to system resources while the system is offline.
Winbind service, see Section 21.1.2, “Samba Daemons and Related Services”.
Winbind and troubleshooting tips, see the Knowledgebase on the Red Hat Customer Portal.
Winbind Mapper utility that generates a part of the smb.conf file to help you connect a Red Hat Enterprise Linux to an Active Directory.
13.1.2.4. Using Kerberos with LDAP or NIS Authentication
- It uses a security layer for communication while still allowing connections over standard ports.
- It automatically uses credentials caching with SSSD, which allows offline logins.
Figure 13.2. Kerberos Fields
- Realm gives the name for the realm for the Kerberos server. The realm is the network that uses Kerberos, composed of one or more key distribution centers (KDC) and a potentially large number of clients.
- KDCs gives a comma-separated list of servers that issue Kerberos tickets.
- Admin Servers gives a list of administration servers running the
kadmindprocess in the realm. - Optionally, use DNS to resolve server host name and to find additional KDCs within the realm.
13.1.3. Configuring Alternative Authentication Features
Figure 13.3. Advanced Options
13.1.3.1. Using Fingerprint Authentication
13.1.3.2. Setting Local Authentication Parameters
- Enable local access control instructs the
/etc/security/access.conffile to check for local user authorization rules. - Password Hashing Algorithm sets the hashing algorithm to use to encrypt locally-stored passwords.
13.1.3.3. Enabling Smart Card Authentication
- Card Removal Action tells the system how to respond when the card is removed from the card reader during an active session. A system can either ignore the removal and allow the user to access resources as normal, or a system can immediately lock until the smart card is supplied.
- Require smart card login sets whether a smart card is required for logins or allowed for logins. When this option is selected, all other methods of authentication are immediately blocked.
Warning
Do not select this option until you have successfully authenticated to the system using a smart card.
13.1.3.4. Creating User Home Directories
13.1.4. Configuring Authentication from the Command Line
authconfig command-line tool updates all of the configuration files and services required for system authentication, according to the settings passed to the script. Along with allowing all of the identity and authentication configuration options that can be set through the UI, the authconfig tool can also be used to create backup and kickstart files.
authconfig options, check the help output and the man page.
13.1.4.1. Tips for Using authconfig
authconfig:
- With every command, use either the
--updateor--testoption. One of those options is required for the command to run successfully. Using--updatewrites the configuration changes.--testprints the changes to stdout but does not apply the changes to the configuration. - Each enable option has a corresponding disable option.
13.1.4.2. Configuring LDAP User Stores
--enableldap. To use LDAP as the authentication source, use --enableldapauth and then the requisite connection information, like the LDAP server name, base DN for the user suffix, and (optionally) whether to use TLS. The authconfig command also has options to enable or disable RFC 2307bis schema for user entries, which is not possible through the Authentication Configuration UI.
ldap or ldaps) and the port number. Do not use a secure LDAP URL (ldaps) with the --enableldaptls option.
authconfig --enableldap --enableldapauth --ldapserver=ldap://ldap.example.com:389,ldap://ldap2.example.com:389 --ldapbasedn="ou=people,dc=example,dc=com" --enableldaptls --ldaploadcacert=https://ca.server.example.com/caCert.crt --update
authconfig --enableldap --enableldapauth --ldapserver=ldap://ldap.example.com:389,ldap://ldap2.example.com:389 --ldapbasedn="ou=people,dc=example,dc=com" --enableldaptls --ldaploadcacert=https://ca.server.example.com/caCert.crt --update
--ldapauth for LDAP password authentication, it is possible to use Kerberos with the LDAP user store. These options are described in Section 13.1.4.5, “Configuring Kerberos Authentication”.
13.1.4.3. Configuring NIS User Stores
--enablenis. This automatically uses NIS authentication, unless the Kerberos parameters are explicitly set, so it uses Kerberos authentication (Section 13.1.4.5, “Configuring Kerberos Authentication”). The only parameters are to identify the NIS server and NIS domain; if these are not used, then the authconfig service scans the network for NIS servers.
authconfig --enablenis --nisdomain=EXAMPLE --nisserver=nis.example.com --update
authconfig --enablenis --nisdomain=EXAMPLE --nisserver=nis.example.com --update13.1.4.4. Configuring Winbind User Stores
authconfig --enablewinbind --enablewinbindauth --smbsecurity=user|server --enablewinbindoffline --smbservers=ad.example.com --smbworkgroup=EXAMPLE --update
authconfig --enablewinbind --enablewinbindauth --smbsecurity=user|server --enablewinbindoffline --smbservers=ad.example.com --smbworkgroup=EXAMPLE --updateNote
EXAMPLE\jsmith.
getent passwd domain\\user DOMAIN\user:*:16777216:16777216:Name Surname:/home/DOMAIN/user:/bin/bash
~]# getent passwd domain\\user DOMAIN\user:*:16777216:16777216:Name Surname:/home/DOMAIN/user:/bin/bashauthconfig --enablewinbind --enablewinbindauth --smbsecurity ads --enablewinbindoffline --smbservers=ad.example.com --smbworkgroup=EXAMPLE --smbrealm EXAMPLE.COM --winbindtemplateshell=/bin/sh --update
authconfig --enablewinbind --enablewinbindauth --smbsecurity ads --enablewinbindoffline --smbservers=ad.example.com --smbworkgroup=EXAMPLE --smbrealm EXAMPLE.COM --winbindtemplateshell=/bin/sh --updateauthconfig help.
13.1.4.5. Configuring Kerberos Authentication
authconfig NIS or LDAP options --enablekrb5 --krb5realm EXAMPLE --krb5kdc kdc.example.com:88,server.example.com:88 --krb5adminserver server.example.com:749 --enablekrb5kdcdns --enablekrb5realmdns --update
authconfig NIS or LDAP options --enablekrb5 --krb5realm EXAMPLE --krb5kdc kdc.example.com:88,server.example.com:88 --krb5adminserver server.example.com:749 --enablekrb5kdcdns --enablekrb5realmdns --update13.1.4.6. Configuring Local Authentication Settings
authconfig --enablemkhomedir --update
authconfig --enablemkhomedir --updateauthconfig --passalgo=sha512 --update
authconfig --passalgo=sha512 --update13.1.4.7. Configuring Fingerprint Authentication
authconfig settings, like LDAP user stores.
authconfig --enablefingerprint --update
~]# authconfig --enablefingerprint --update13.1.4.8. Configuring Smart Card Authentication
--enablesmartcard option:
authconfig --enablesmartcard --update
~]# authconfig --enablesmartcard --updateauthconfig --enablesmartcard --smartcardaction=0 --update
~]# authconfig --enablesmartcard --smartcardaction=0 --updateauthconfig --enablerequiresmartcard --update
~]# authconfig --enablerequiresmartcard --updateWarning
--enablerequiresmartcard option until you have successfully authenticated to the system using a smart card. Otherwise, users may be unable to log into the system.
13.1.4.9. Managing Kickstart and Configuration Files
--update option updates all of the configuration files with the configuration changes. There are a couple of alternative options with slightly different behavior:
--kickstartwrites the updated configuration to a kickstart file.--testprints the full configuration, with changes, to stdout but does not edit any configuration files.
authconfig can be used to back up and restore previous configurations. All archives are saved to a unique subdirectory in the /var/lib/authconfig/ directory. For example, the --savebackup option gives the backup directory as 2011-07-01:
authconfig --savebackup=2011-07-01
~]# authconfig --savebackup=2011-07-01/var/lib/authconfig/backup-2011-07-01 directory.
--restorebackup option, giving the name of the manually-saved configuration:
authconfig --restorebackup=2011-07-01
~]# authconfig --restorebackup=2011-07-01authconfig automatically makes a backup of the configuration before it applies any changes (with the --update option). The configuration can be restored from the most recent automatic backup, without having to specify the exact backup, using the --restorelastbackup option.
13.1.5. Using Custom Home Directories
/home and the system is configured to create home directories the first time users log in, then these directories are created with the wrong permissions.
- Apply the correct SELinux context and permissions from the
/homedirectory to the home directory that is created on the local system. For example:semanage fcontext -a -e /home /home/locale
~]# semanage fcontext -a -e /home /home/localeCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Install the oddjob-mkhomedir package on the system.This package provides the
pam_oddjob_mkhomedir.solibrary, which the Authentication Configuration Tool uses to create home directories. Thepam_oddjob_mkhomedir.solibrary, unlike the defaultpam_mkhomedir.solibrary, can create SELinux labels.The Authentication Configuration Tool automatically uses thepam_oddjob_mkhomedir.solibrary if it is available. Otherwise, it will default to usingpam_mkhomedir.so. - Make sure the
oddjobdservice is running. - Re-run the Authentication Configuration Tool and enable home directories, as in Section 13.1.3, “Configuring Alternative Authentication Features”.
semanage fcontext -a -e /home /home/locale # restorecon -R -v /home/locale
~]# semanage fcontext -a -e /home /home/locale
# restorecon -R -v /home/locale13.2. Using and Caching Credentials with SSSD
13.2.1. About SSSD
- Reducing the load on identification/authentication servers. Rather than having every client service attempt to contact the identification server directly, all of the local clients can contact SSSD which can connect to the identification server or check its cache.
- Permitting offline authentication. SSSD can optionally keep a cache of user identities and credentials that it retrieves from remote services. This allows users to authenticate to resources successfully, even if the remote identification server is offline or the local machine is offline.
- Using a single user account. Remote users frequently have two (or even more) user accounts, such as one for their local system and one for the organizational system. This is necessary to connect to a virtual private network (VPN). Because SSSD supports caching and offline authentication, remote users can connect to network resources by authenticating to their local machine and then SSSD maintains their network credentials.
While this chapter covers the basics of configuring services and domains in SSSD, this is not a comprehensive resource. Many other configuration options are available for each functional area in SSSD; check out the man page for the specific functional area to get a complete list of options.
sssd(8) man page.
| Functional Area | Man Page | ||
|---|---|---|---|
| General Configuration | sssd.conf(8) | ||
| sudo Services | sssd-sudo | ||
| LDAP Domains | sssd-ldap | ||
| Active Directory Domains |
| ||
| Identity Management (IdM or IPA) Domains |
| ||
| Kerberos Authentication for Domains | sssd-krb5 | ||
| OpenSSH Keys |
| ||
| Cache Maintenance |
|
13.2.2. Setting up the sssd.conf File
.conf file. By default, this is /etc/sssd/sssd.conf — although that file must be created and configured manually, since SSSD is not configured after installation.
13.2.2.1. Creating the sssd.conf File
[sssd], for general SSSD process and operational configuration; this basically lists the configured services, domains, and configuration parameters for each- [service_name], for configuration options for each supported system service, as described in Section 13.2.4, “SSSD and System Services”
- [domain_type/DOMAIN_NAME], for configuration options for each configured identity provider
Important
While services are optional, at least one identity provider domain must be configured before the SSSD service can be started.
Example 13.1. Simple sssd.conf File
[sssd] section has three important parameters:
domainslists all of the domains, configured in thesssd.conf, which SSSD uses as identity providers. If a domain is not listed in thedomainskey, it is not used by SSSD, even if it has a configuration section.serviceslists all of the system services, configured in thesssd.conf, which use SSSD; when SSSD starts, the corresponding SSSD service is started for each configured system service. If a service is not listed in theserviceskey, it is not used by SSSD, even if it has a configuration section.config_file_versionsets the version of the configuration file to set file format expectations. This is version 2, for all recent SSSD versions.
Note
sssd.conf file, SSSD does not interact with that service or domain unless it is listed in the services or domains parameters, respectively, in the [sssd] section.
sssd.conf man page.
13.2.2.2. Using a Custom Configuration File
sssd process assumes that the configuration file is /etc/sssd/sssd.conf.
-c option with the sssd command:
sssd -c /etc/sssd/customfile.conf --daemon
~]# sssd -c /etc/sssd/customfile.conf --daemon13.2.3. Starting and Stopping SSSD
Important
service command or the /etc/init.d/sssd script can start SSSD. For example:
service sssd start
~]# service sssd start- Enabling SSSD through the
authconfigcommand:authconfig --enablesssd --enablesssdauth --update
~]# authconfig --enablesssd --enablesssdauth --updateCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Adding the SSSD process to the start list using the
chkconfigcommand:chkconfig sssd on
~]# chkconfig sssd onCopy to Clipboard Copied! Toggle word wrap Toggle overflow
13.2.4. SSSD and System Services
sssd.conf file. The [sssd] section also lists the services that are active and should be started when sssd starts within the services directive.
- A Name Service Switch (NSS) provider service that answers name service requests from the
sssd_nssmodule. This is configured in the[nss]section of the SSSD configuration.This is described in Section 13.2.5, “Configuring Services: NSS”. - A PAM provider service that manages a PAM conversation through the
sssd_pammodule. This is configured in the[pam]section of the configuration.This is described in Section 13.2.6, “Configuring Services: PAM”. - An SSH provider service that defines how SSSD manages the
known_hostsfile and other key-related configuration. Using SSSD with OpenSSH is described in Section 13.2.9, “Configuring Services: OpenSSH and Cached Keys”. - An
autofsprovider service that connects to an LDAP server to retrieve configured mount locations. This is configured as part of an LDAP identity provider in a[domain/NAME]section in the configuration file.This is described in Section 13.2.7, “Configuring Services: autofs”. - A
sudoprovider service that connects to an LDAP server to retrieve configuredsudopolicies. This is configured as part of an LDAP identity provider in a[domain/NAME]section in the configuration file.This is described in Section 13.2.8, “Configuring Services: sudo”. - A PAC responder service that defines how SSSD works with Kerberos to manage Active Directory users and groups. This is specifically part of managing Active Directory identity providers with domains, as described in Section 13.2.13, “Creating Domains: Active Directory”.
13.2.5. Configuring Services: NSS
sssd_nss, which instructs the system to use SSSD to retrieve user information. The NSS configuration must include a reference to the SSSD module, and then the SSSD configuration sets how SSSD interacts with NSS.
About NSS Service Maps and SSSD
- Passwords (
passwd) - User groups (
shadow) - Groups (
groups) - Netgroups (
netgroups) - Services (
services)
Procedure 13.1. Configuring NSS Services to Use SSSD
nss_sss module has to be included for the desired service type.
- Use the Authentication Configuration tool to enable SSSD. This automatically configured the
nsswitch.conffile to use SSSD as a provider.authconfig --enablesssd --update
~]# authconfig --enablesssd --updateCopy to Clipboard Copied! Toggle word wrap Toggle overflow This automatically configures the password, shadow, group, and netgroups services maps to use the SSSD module:passwd: files sss shadow: files sss group: files sss netgroup: files sss
passwd: files sss shadow: files sss group: files sss netgroup: files sssCopy to Clipboard Copied! Toggle word wrap Toggle overflow - The services map is not enabled by default when SSSD is enabled with
authconfig. To include that map, open thensswitch.conffile and add thesssmodule to theservicesmap:vim /etc/nsswitch.conf ... services: file sss ...
~]# vim /etc/nsswitch.conf ... services: file sss ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 13.2. Configuring SSSD to Work with NSS
[nss] services section.
- Open the
sssd.conffile.vim /etc/sssd/sssd.conf
~]# vim /etc/sssd/sssd.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Make sure that NSS is listed as one of the services that works with SSSD.
[sssd] config_file_version = 2 reconnection_retries = 3 sbus_timeout = 30 services = nss, pam
[sssd] config_file_version = 2 reconnection_retries = 3 sbus_timeout = 30 services = nss, pamCopy to Clipboard Copied! Toggle word wrap Toggle overflow - In the
[nss]section, change any of the NSS parameters. These are listed in Table 13.2, “SSSD [nss] Configuration Parameters”.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart SSSD.
service sssd restart
~]# service sssd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
| Parameter | Value Format | Description |
|---|---|---|
| entry_cache_nowait_percentage | integer | Specifies how long sssd_nss should return cached entries before refreshing the cache. Setting this to zero (0) disables the entry cache refresh.
This configures the entry cache to update entries in the background automatically if they are requested if the time before the next update is a certain percentage of the next interval. For example, if the interval is 300 seconds and the cache percentage is 75, then the entry cache will begin refreshing when a request comes in at 225 seconds — 75% of the interval.
The allowed values for this option are 0 to 99, which sets the percentage based on the
entry_cache_timeout value. The default value is 50%.
|
| entry_negative_timeout | integer | Specifies how long, in seconds, sssd_nss should cache negative cache hits. A negative cache hit is a query for an invalid database entries, including non-existent entries. |
| filter_users, filter_groups | string | Tells SSSD to exclude certain users from being fetched from the NSS database. This is particularly useful for system accounts such as root. |
| filter_users_in_groups | Boolean | Sets whether users listed in the filter_users list appear in group memberships when performing group lookups. If set to FALSE, group lookups return all users that are members of that group. If not specified, this value defaults to true, which filters the group member lists. |
| debug_level | integer, 0 - 9 | Sets a debug logging level. |
NSS Compatibility Mode
/etc/passwd file to ensure that users or members of netgroups have access to the system.
/etc/nsswitch.conf file:
passwd: compat passwd_compat: sss
passwd: compat
passwd_compat: ssspasswd entries are supported:
+user-userInclude (+) or exclude (-) a specified user from the Network Information System (NIS) map.+@netgroup-@netgroupInclude (+) or exclude (-) all users in the given netgroup from the NIS map.+Exclude all users, except previously excluded ones from the NIS map.
nsswitch.conf(5) manual page.
13.2.6. Configuring Services: PAM
Warning
sssd_pam, which instructs the system to use SSSD to retrieve user information. The PAM configuration must include a reference to the SSSD module, and then the SSSD configuration sets how SSSD interacts with PAM.
Procedure 13.3. Configuring PAM
- Use
authconfigto enable SSSD for system authentication.This automatically updates the PAM configuration to reference all of the SSSD modules:authconfig --update --enablesssd --enablesssdauth
# authconfig --update --enablesssd --enablesssdauthCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow These modules can be set toincludestatements, as necessary. - Open the
sssd.conffile.vim /etc/sssd/sssd.conf
# vim /etc/sssd/sssd.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Make sure that PAM is listed as one of the services that works with SSSD.
[sssd] config_file_version = 2 reconnection_retries = 3 sbus_timeout = 30 services = nss, pam
[sssd] config_file_version = 2 reconnection_retries = 3 sbus_timeout = 30 services = nss, pamCopy to Clipboard Copied! Toggle word wrap Toggle overflow - In the
[pam]section, change any of the PAM parameters. These are listed in Table 13.3, “SSSD [pam] Configuration Parameters”.[pam] reconnection_retries = 3 offline_credentials_expiration = 2 offline_failed_login_attempts = 3 offline_failed_login_delay = 5
[pam] reconnection_retries = 3 offline_credentials_expiration = 2 offline_failed_login_attempts = 3 offline_failed_login_delay = 5Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart SSSD.
service sssd restart
~]# service sssd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
| Parameter | Value Format | Description |
|---|---|---|
| offline_credentials_expiration | integer | Sets how long, in days, to allow cached logins if the authentication provider is offline. This value is measured from the last successful online login. If not specified, this defaults to zero (0), which is unlimited. |
| offline_failed_login_attempts | integer | Sets how many failed login attempts are allowed if the authentication provider is offline. If not specified, this defaults to zero (0), which is unlimited. |
| offline_failed_login_delay | integer | Sets how long to prevent login attempts if a user hits the failed login attempt limit. If set to zero (0), the user cannot authenticate while the provider is offline once he hits the failed attempt limit. Only a successful online authentication can re-enable offline authentication. If not specified, this defaults to five (5). |
13.2.7. Configuring Services: autofs
About Automount, LDAP, and SSSD
nfs.example.com which hosts the directory pub, and automount is configured to mount directories in the /shares/ directory. So, the mount location is /shares/pub. All of the mounts are listed in the auto.master file, which identifies the different mount directories and the files which configure them. The auto.shares file then identifies each file server and mount directory which goes into the /shares/ directory. The relationships could be viewed like this:
auto.master and auto.whatever file, and those files have to be available to each local automount process.
autofs uses those schema elements to derive the automount configuration. The /etc/sysconfig/autofs file identifies the LDAP server, directory location, and schema elements used for automount entities:
Procedure 13.4. Configuring autofs Services in SSSD
- Make sure that the autofs and sssd-common packages are installed.
- Open the
sssd.conffile.vim /etc/sssd/sssd.conf
~]# vim /etc/sssd/sssd.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the
autofsservice to the list of services that SSSD manages.[sssd] services = nss,pam,autofs ....
[sssd] services = nss,pam,autofs ....Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Create a new
[autofs]service configuration section. This section can be left blank; there is only one configurable option, for timeouts for negative cache hits.This section is required, however, for SSSD to recognize theautofsservice and supply the default configuration.[autofs]
[autofs]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The automount information is read from a configured LDAP domain in the SSSD configuration, so an LDAP domain must be available. If no additional settings are made, then the configuration defaults to the RFC 2307 schema and the LDAP search base (
ldap_search_base) for the automount information. This can be customized:- The directory type,
autofs_provider; this defaults to theid_providervalue; a value of none explicitly disables autofs for the domain. - The search base,
ldap_autofs_search_base. - The object class to use to recognize map entries,
ldap_autofs_map_object_class - The attribute to use to recognize map names,
ldap_autofs_map_name - The object class to use to recognize mount point entries,
ldap_autofs_entry_object_class - The attribute to use to recognize mount point names,
ldap_autofs_entry_key - The attribute to use for additional configuration information for the mount point,
ldap_autofs_entry_value
For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save and close the
sssd.conffile. - Configure
autofsto look for the automount map information in SSSD by editing thensswitch.conffile and changing the location fromldaptosss:vim /etc/nsswitch.conf automount: files sss
# vim /etc/nsswitch.conf automount: files sssCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart SSSD.
service sssd restart
# service sssd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
13.2.8. Configuring Services: sudo
About sudo, LDAP, and SSSD
sudo rules are defined in the sudoers file, which must be distributed separately to every machine to maintain consistency.
sudo configuration in a central LDAP directory, and just configure each local system to point to that LDAP directory. That means that updates only need to be made in a single location, and any new rules are automatically recognized by local systems.
sudo-LDAP configuration, each sudo rule is stored as an LDAP entry, with each component of the sudo rule defined in an LDAP attribute.
sudoers rule looks like this:
Defaults env_keep+=SSH_AUTH_SOCK ... %wheel ALL=(ALL) ALL
Defaults env_keep+=SSH_AUTH_SOCK
...
%wheel ALL=(ALL) ALLNote
sudo rules which apply to the local system, depending on the value of the sudoHost attribute. This can mean that the sudoHost value is set to ALL, uses a regular expression that matches the host name, matches the systems netgroup, or matches the systems host name, fully qualified domain name, or IP address.
sudo service can be configured to point to an LDAP server and to pull its rule configuration from those LDAP entries. Rather than pointing the sudo configuration to the LDAP directory, it can be configured to point to SSSD. SSSD, then, stores all of the information that sudo needs, and every time a user attempts a sudo-related operation, the latest sudo configuration can be pulled from the LDAP directory (through SSSD). SSSD, however, also caches all of the sudo riles, so that users can perform tasks, using that centralized LDAP configuration, even if the LDAP server goes offline.
Procedure 13.5. Configuring sudo with SSSD
sudo configuration options are listed in the sssd-ldap(5) man page.
- Make sure that the sssd-common package is installed.
rpm -q sssd-common
~]$ rpm -q sssd-commonCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Open the
sssd.conffile.vim /etc/sssd/sssd.conf
~]# vim /etc/sssd/sssd.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the
sudoservice to the list of services that SSSD manages.[sssd] services = nss,pam,sudo ....
[sssd] services = nss,pam,sudo ....Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Create a new
[sudo]service configuration section. This section can be left blank; there is only one configurable option, for evaluating the sudo not before/after period.This section is required, however, for SSSD to recognize thesudoservice and supply the default configuration.[sudo]
[sudo]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The
sudoinformation is read from a configured LDAP domain in the SSSD configuration, so an LDAP domain must be available. For an LDAP provider, these parameters are required:- The directory type,
sudo_provider; this is alwaysldap. - The search base,
ldap_sudo_search_base. - The URI for the LDAP server,
ldap_uri.
For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow For an Identity Management (IdM or IPA) provider, there are additional parameters required to perform Kerberos authentication when connecting to the server.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Thesudo_providertype for an Identity Management provider is stillldap. - Set the intervals to use to refresh the
sudorule cache.The cache for a specific system user is always checked and updated whenever that user performs a task. However, SSSD caches all rules which relate to the local system. That complete cache is updated in two ways:- Incrementally, meaning only changes to rules since the last full update (
ldap_sudo_smart_refresh_interval, the time in seconds); the default is 15 minutes, - Fully, which dumps the entire caches and pulls in all of the current rules on the LDAP server(
ldap_sudo_full_refresh_interval, the time in seconds); the default is six hours.
These two refresh intervals are set separately. For example:[domain/LDAP] ... ldap_sudo_full_refresh_interval=86400 ldap_sudo_smart_refresh_interval=3600
[domain/LDAP] ... ldap_sudo_full_refresh_interval=86400 ldap_sudo_smart_refresh_interval=3600Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
SSSD only cachessudorules which apply to the local system. This can mean that thesudoHostvalue is set to ALL, uses a regular expression that matches the host name, matches the systems netgroup, or matches the systems host name, fully qualified domain name, or IP address. - Optionally, set any values to change the schema used for
sudorules.Schema elements are set in theldap_sudorule_*attributes. By default, all of the schema elements use the schema defined in sudoers.ldap; these defaults will be used in almost all deployments. - Save and close the
sssd.conffile. - Configure
sudoto look for rules configuration in SSSD by editing thensswitch.conffile and adding thessslocation:vim /etc/nsswitch.conf sudoers: files sss
~]# vim /etc/nsswitch.conf sudoers: files sssCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart SSSD.
service sssd restart
~]# service sssd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
13.2.9. Configuring Services: OpenSSH and Cached Keys
known_hosts file or for the remote user in authorized_keys. Whenever that remote machine or user attempts to authenticate again, the local system checks the known_hosts or authorized_keys file first to see if that remote entity is recognized and trusted. If it is, then access is granted.
known_hosts file is a triplet of the machine name, its IP address, and its public key:
server.example.com,255.255.255.255 ssh-rsa AbcdEfg1234ZYX098776/AbcdEfg1234ZYX098776/AbcdEfg1234ZYX098776=
server.example.com,255.255.255.255 ssh-rsa AbcdEfg1234ZYX098776/AbcdEfg1234ZYX098776/AbcdEfg1234ZYX098776=known_hosts file can quickly become outdated for a number of different reasons: systems using DHCP cycle through IP addresses, new keys can be re-issued periodically, or virtual machines or services can be brought online and removed. This changes the host name, IP address, and key triplet.
known_hosts file to maintain security. (Or system users get in the habit of accepting any machine and key presented, which negates the security benefits of key-based security.)
known_hosts file has not been updated uniformly.
Note
known_hosts file.
Configuring OpenSSH to Use SSSD for Host Keys
~/.ssh/config) or a system-wide configuration file (/etc/ssh/ssh_config). The user file has precedence over the system settings and the first obtained value for a parameter is used. The formatting and conventions for this file are covered in Chapter 14, OpenSSH.
sss_ssh_knownhostsproxy, which performs two operations:
- Asks SSSD to retrieve the public host key from the Identity Management server and store it in the
/var/lib/sss/pubconf/known_hostsfile. - Establishes a connection with the host machine, using either a socket (the default) or a proxy command.
sss_ssh_knownhostsproxy [-d sssd_domain] [-p ssh_port] HOST [PROXY_COMMAND]
sss_ssh_knownhostsproxy [-d sssd_domain] [-p ssh_port] HOST [PROXY_COMMAND]| Short Argument | Long Argument | Description |
|---|---|---|
| HOSTNAME | Gives the host name of the host to check and connect to. In the OpenSSH configuration file, this can be a token, %h. | |
| PROXY_COMMAND | Passes a proxy command to use to connect to the SSH client. This is similar to running ssh -o ProxyCommand=value. This option is used when running sss_ssh_knownhostsproxy from the command line or through another script, but is not necessary in the OpenSSH configuration file. | |
| -d sssd_domain | --domain sssd_domain | Only searches for public keys in entries in the specified domain. If not given, SSSD searches for keys in all configured domains. |
| -p port | --port port | Uses this port to connect to the SSH client. By default, this is port 22. |
ssh_config or ~/.ssh/config file:
- Specify the command to use to connect to the SSH client (
ProxyCommand). This is thesss_ssh_knownhostsproxy, with the desired arguments and host name. - Specify the location of the SSSD hosts file (
GlobalKnownHostsFile).
ProxyCommand /usr/bin/sss_ssh_knownhostsproxy -p %p %h GlobalKnownHostsFile /var/lib/sss/pubconf/known_hosts
ProxyCommand /usr/bin/sss_ssh_knownhostsproxy -p %p %h
GlobalKnownHostsFile /var/lib/sss/pubconf/known_hostsConfiguring OpenSSH to Use SSSD for User Keys
sshd, directly from the output of the sss_ssh_authorizedkeys tool and are not stored in a file.
sshd to read a user's public keys from an external program, in this case the sss_ssh_authorizedkeys tool, use the AuthorizedKeysCommand directive in the /etc/ssh/sshd_config file.
sss_ssh_authorizedkeys tool can be used to acquire SSH public keys from the user entries in the Identity Management (IPA) domain and output them in OpenSSH authorized_keys format. The command has the following format:
sss_ssh_authorizedkeys [-d sssd_domain] USER
sss_ssh_authorizedkeys [-d sssd_domain] USER| Short Argument | Long Argument | Description |
|---|---|---|
| USER | The user name or account name for which to obtain the public key. In the OpenSSH configuration file, this can be represented by a token, %u. | |
| -d sssd_domain | --domain sssd_domain | Only search for public keys in entries in the specified domain. If not given, SSSD searches for keys in all configured domains. |
/etc/ssh/sshd_config as follows:
AuthorizedKeysCommand /usr/bin/sss_ssh_authorizedkeys AuthorizedKeysCommandRunAs nobody
AuthorizedKeysCommand /usr/bin/sss_ssh_authorizedkeys
AuthorizedKeysCommandRunAs nobodysshd_config(5) man page. Note that the sshd service must be restarted for any changes to take effect.
13.2.10. SSSD and Identity Providers (Domains)
- LDAP, for general LDAP servers
- Active Directory (an extension of the LDAP provider type)
- Identity Management (an extension of the LDAP provider type)
- Local, for the local SSSD database
- Proxy
- Kerberos (authentication provider only)
| Identification Provider | Authentication Provider |
|---|---|
| Identity Management (LDAP) | Identity Management (LDAP) |
| Active Directory (LDAP) | Active Directory (LDAP) |
| Active Directory (LDAP) | Kerberos |
| LDAP | LDAP |
| LDAP | Kerberos |
| proxy | LDAP |
| proxy | Kerberos |
| proxy | proxy |
| Parameter | Value Format | Description |
|---|---|---|
| id_provider | string | Specifies the data back end to use for this domain. The supported identity back ends are:
|
| auth_provider | string | Sets the authentication provider used for the domain. The default value for this option is the value of id_provider. The supported authentication providers are ldap, ipa, ad, krb5 (Kerberos), proxy, and none. |
| min_id,max_id | integer | Optional. Specifies the UID and GID range for the domain. If a domain contains entries that are outside that range, they are ignored. The default value for min_id is 1; the default value for max_id is 0, which is unlimited.
Important
The default min_id value is the same for all types of identity provider. If LDAP directories are using UID numbers that start at one, it could cause conflicts with users in the local /etc/passwd file. To avoid these conflicts, set min_id to 1000 or higher as possible.
|
| cache_credentials | Boolean | Optional. Specifies whether to store user credentials in the local SSSD domain database cache. The default value for this parameter is false. Set this value to true for domains other than the LOCAL domain to enable offline authentication. |
| entry_cache_timeout | integer | Optional. Specifies how long, in seconds, SSSD should cache positive cache hits. A positive cache hit is a successful query. |
| use_fully_qualified_names | Boolean | Optional. Specifies whether requests to this domain require fully qualified domain names. If set to true, all requests to this domain must use fully qualified domain names. It also means that the output from the request displays the fully-qualified name. Restricting requests to fully qualified user names allows SSSD to differentiate between domains with users with conflicting user names.
If
use_fully_qualified_names is set to false, it is possible to use the fully-qualified name in the requests, but only the simplified version is displayed in the output.
SSSD can only parse names based on the domain name, not the realm name. The same name can be used for both domains and realms, however.
|
13.2.11. Creating Domains: LDAP
- Red Hat Directory Server
- OpenLDAP
- Identity Management (IdM or IPA)
- Microsoft Active Directory 2008 R2
Note
Parameters for Configuring an LDAP Domain
Note
ldap_pwd_policy=shadow option, the policies defined with the shadow LPAD attributes for a user have no effect on whether the password policy is enabled on the OpenLDAP server.
Note
sssd-ldap(5).
| Parameter | Description |
|---|---|
| ldap_uri | Gives a comma-separated list of the URIs of the LDAP servers to which SSSD will connect. The list is given in order of preference, so the first server in the list is tried first. Listing additional servers provides failover protection. This can be detected from the DNS SRV records if it is not given. |
| ldap_search_base |
Gives the base DN to use for performing LDAP user operations.
Important
If used incorrectly, ldap_search_base might cause SSSD lookups to fail.
With an AD provider, setting
ldap_search_base is not required. The AD provider automatically discovers all the necessary information. Red Hat recommends not to set the parameter in this situation and instead rely on what the AD provider discovers.
|
| ldap_tls_reqcert | Specifies how to check for SSL server certificates in a TLS session. There are four options:
|
| ldap_tls_cacert | Gives the full path and file name to the file that contains the CA certificates for all of the CAs that SSSD recognizes. SSSD will accept any certificate issued by these CAs.
This uses the OpenLDAP system defaults if it is not given explicitly.
|
| ldap_referrals | Sets whether SSSD will use LDAP referrals, meaning forwarding queries from one LDAP database to another. SSSD supports database-level and subtree referrals. For referrals within the same LDAP server, SSSD will adjust the DN of the entry being queried. For referrals that go to different LDAP servers, SSSD does an exact match on the DN. Setting this value to true enables referrals; this is the default.
Referrals can negatively impact overall performance because of the time spent attempting to trace referrals. Disabling referral checking can significantly improve performance.
|
| ldap_schema | Sets what version of schema to use when searching for user entries. This can be rfc2307, rfc2307bis, ad, or ipa. The default is rfc2307.
In RFC 2307, group objects use a multi-valued attribute,
memberuid, which lists the names of the users that belong to that group. In RFC 2307bis, group objects use the member attribute, which contains the full distinguished name (DN) of a user or group entry. RFC 2307bis allows nested groups using the member attribute. Because these different schema use different definitions for group membership, using the wrong LDAP schema with SSSD can affect both viewing and managing network resources, even if the appropriate permissions are in place.
For example, with RFC 2307bis, all groups are returned when using nested groups or primary/secondary groups.
id uid=500(myserver) gid=500(myserver) groups=500(myserver),510(myothergroup)
If SSSD is using RFC 2307 schema, only the primary group is returned.
This setting only affects how SSSD determines the group members. It does not change the actual user data.
|
| ldap_search_timeout | Sets the time, in seconds, that LDAP searches are allowed to run before they are canceled and cached results are returned.
When an LDAP search times out, SSSD automatically switches to offline mode.
|
| ldap_network_timeout | Sets the time, in seconds, SSSD attempts to poll an LDAP server after a connection attempt fails. The default is six seconds. |
| ldap_opt_timeout | Sets the time, in seconds, to wait before aborting synchronous LDAP operations if no response is received from the server. This option also controls the timeout when communicating with the KDC in case of a SASL bind. The default is five seconds. |
LDAP Domain Example
Note
sssd.conf file. For example:
domains = LOCAL,LDAP1,AD,PROXYNIS
domains = LOCAL,LDAP1,AD,PROXYNISExample 13.2. A Basic LDAP Domain Configuration
- An LDAP server
- The search base
- A way to establish a secure connection
ldap_uri option:
ldap_id_use_start_tls option to use Start TLS and then ldap_tls_cacert to identify the CA certificate which issued the SSL server certificates.
13.2.12. Creating Domains: Identity Management (IdM)
*_provider parameters for a domain. Additionally, Identity Management has configuration options within its own domain to manage SELinux policies, automount information, and host-based access control. All of those features in IdM domains can be tied to SSSD configuraiton, allowing those security-related policies to be applied and cached for system users.
Example 13.3. Basic IdM Provider
- Use the specific IdM schema rather than the default RFC 2307 schema.
- Set SSSD to update the Identity Management domain's DNS server with the IP address of this client when the client first connects to the IdM domain.
sssd.conf.
Example 13.4. IdM Provider with SELinux
selinux_provider parameter. The provider defaults to the id_provider value, so this is not necessary to set explicitly to support SELinux rules. However, it can be useful to explicitly disable SELinux support for the IdM provider in SSSD.
selinux_provider = ipa
selinux_provider = ipaExample 13.5. IdM Provider with Host-Based Access Control
- SSSD can evaluate what machine (source host) the user is using to connect to the IdM resource; this is disabled by default, so that only the target host part of the rule is evaluated.
- SSSD can refresh the host-based access control rules in its cache at a specified interval.
access_provider = ipa ipa_hbac_refresh = 120 # check for source machine rules; disabled by default ipa_hbac_support_srchost = true
access_provider = ipa
ipa_hbac_refresh = 120
# check for source machine rules; disabled by default
ipa_hbac_support_srchost = trueExample 13.6. Identity Management with Cross-Realm Kerberos Trusts
- A service that adds required data to Kerberos tickets
- A setting to support subdomains
pac service in SSSD:
[sssd] services = nss, pam, pac ...
[sssd]
services = nss, pam, pac
...subdomains_provider parameter to the IdM domain section. This is actually an optional parameter; if a subdomain is discovered, then SSSD defaults to using the ipa provider type. However, this parameter can also be used to disable subdomain fetches by setting a value of none.
[domain/IDM] ... subdomains_provider = ipa get_domains_timeout = 300
[domain/IDM]
...
subdomains_provider = ipa
get_domains_timeout = 30013.2.13. Creating Domains: Active Directory
- Identities using a Windows security ID must be mapped to the corresponding Linux system user ID.
- Searches must account for the range retrieval extension.
- There may be performance issues with LDAP referrals.
Mapping Active Directory Securiy IDs and Linux User IDs
- Using Services for Unix to insert POSIX attributes on Windows user and group entries, and then having those attributes pulled into PAM/NSS
- Using ID mapping on SSSD to create a map between Active Directory security IDs (SIDs) and the generated UIDs on Linux
The Mechanism of ID Mapping
S-1-5-21-3623811015-3361044348-30300820-1013
S-1-5-21-3623811015-3361044348-30300820-1013S-1-5-21-3623811015-3361044348-30300820-1013
S-1-5-21-3623811015-3361044348-30300820-1013S-1-5-21-3623811015-3361044348-30300820-1013
S-1-5-21-3623811015-3361044348-30300820-1013|_____________________________| | | minimum ID max ID
|_____________________________|
| |
minimum ID max ID| slice 1 | slice 2 | ... | |_________|_________|_________| | | | | minimum ID max ID
| slice 1 | slice 2 | ... |
|_________|_________|_________|
| | | |
minimum ID max IDNote
ID Mapping Parameters
ldap_id_mapping = True ldap_schema = ad
ldap_id_mapping = True
ldap_schema = adNote
uidNumber and gidNumber attributes are ignored. This prevents any manually-assigned values. If any values must be manually assigned, then all values must be manually assigned, and ID mapping should be disabled.
Mapping Users
- A system UID is created for the user based on his SID and the ID range for that domain.
- A GID is created for the user, which is identical to the UID.
- A private group is created for the user.
- A home directory is created, based on the home directory format in the
sssd.conffile. - A shell is created, according to the system defaults or the setting in the
sssd.conffile. - If the user belongs to any groups in the Active Directory domain, then, using the SID, SSSD adds the user to those groups on the Linux system.
Active Directory Users and Range Retrieval Searches
MaxValRange, which sets a limit on how many values for a multi-valued attribute will be returned. This is the range retrieval search extension. Essentially, this runs multiuple mini-searches, each returning a subset of the results within a given range, until all matches are returned.
member attribute, each entry could have multiple values, and there can be multiple entries with that attribute. If there are 2000 matching results (or more), then MaxValRange limits how many are displayed at once; this is the value range. The given attribute then has an additional flag set, showing which range in the set the result is in:
attribute:range=low-high:value
attribute:range=low-high:valuemember;range=99-499: cn=John Smith...
member;range=99-499: cn=John Smith...ldap_user_search_base — are not performant with range retrievals. Be cautious when configuring search bases in the Active Directory provider domain and consider what searches may trigger a range retrieval.
Performance and LDAP Referrals
ldap_referrals = false
ldap_referrals = falseActive Directory as Other Provider Types
ad value is a short-cut which automatically pulls in the parameters and values to configure a given provider for Active Directory. For example, using access_provider = ad to configure an Active Directory access provider expands to this configuration using the explicit LDAP provider parameters:
access_provider = ldap ldap_access_order = expire ldap_account_expire_policy = ad
access_provider = ldap
ldap_access_order = expire
ldap_account_expire_policy = adProcedure 13.6. Configuring an Active Directory Identity Provider
*_provider parameters for a domain. Additionally, it is possible to load the native Active Directory schema for user and group entries, rather than using the default RFC 2307.
- Make sure that both the Active Directory and Linux systems have a properly configured environment.
- Name resolution must be properly configured, particularly if service discovery is used with SSSD.
- The clocks on both systems must be in sync for Kerberos to work properly.
- Set up the Linux system as an Active Directory client and enroll it within the Active Directory domain. This is done by configuring the Kerberos and Samba services on the Linux system.
- Set up Kerberos to use the Active Directory Kerberos realm.
- Open the Kerberos client configuration file.
vim /etc/krb5.conf
~]# vim /etc/krb5.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the
[logging]and[libdefaults]sections so that they connect to the Active Directory realm.Copy to Clipboard Copied! Toggle word wrap Toggle overflow If autodiscovery is not used with SSSD, then also configure the[realms]and[domain_realm]sections to explicitly define the Active Directory server.
- Configure the Samba server to connect to the Active directory server.
- Open the Samba configuration file.
vim /etc/samba/smb.conf
~]# vim /etc/samba/smb.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Set the Active Directory domain information in the
[global]section.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Add the Linux machine to the Active Directory domain.
- Obtain Kerberos credentials for a Windows administrative user.
kinit Administrator
~]# kinit AdministratorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the machine to the domain using the
netcommand.net ads join -k Joined 'server' to dns domain 'example.com'
~]# net ads join -k Joined 'server' to dns domain 'example.com'Copy to Clipboard Copied! Toggle word wrap Toggle overflow This creates a new keytab file,/etc/krb5.keytab.List the keys for the system and check that the host principal is there.klist -k
~]# klist -kCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Use
authconfigto enable SSSD for system authentication.authconfig --update --enablesssd --enablesssdauth
# authconfig --update --enablesssd --enablesssdauthCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Set the Active Directory domain as an identity provider in the SSSD configuration, as shown in Example 13.7, “An Active Directory 2008 R2 Domain” and Example 13.8, “An Active Directory 2008 R2 Domain with ID Mapping”.
- Restart the SSH service to load the new PAM configuration.
service sshd restart
~]# service sshd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart SSSD after changing the configuration file.
service sssd restart
~]# service sssd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Example 13.7. An Active Directory 2008 R2 Domain
ldap_schema) and ID mapping must be explicitly enabled (ldap_id_mapping).
Example 13.8. An Active Directory 2008 R2 Domain with ID Mapping
sssd-ldap(5) and sssd-ad(5) man pages.
13.2.14. Configuring Domains: Active Directory as an LDAP Provider (Alternative)
Procedure 13.7. Configuring Active Directory as an LDAP Provider
- It is recommended that SSSD connect to the Active Directory server using SASL, which means that the local host must have a service keytab for the Windows domain on the Linux host.This keytab can be created using Samba.
- Configure the
/etc/krb5.conffile to use the Active Directory realm.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Set the Samba configuration file,
/etc/samba/smb.conf, to point to the Windows Kerberos realm.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To initialize Kerberos, type the following command as
root:kinit Administrator@EXAMPLE.COM
~]# kinit Administrator@EXAMPLE.COMCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Then, run the
net adscommand to log in as an administrator principal. This administrator account must have sufficient rights to add a machine to the Windows domain, but it does not require domain administrator privileges.net ads join -U Administrator
~]# net ads join -U AdministratorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run
net adsagain to add the host machine to the domain. This can be done with the host principal (host/FQDN) or, optionally, with the NFS service (nfs/FQDN).net ads join createupn="host/rhel-server.example.com@AD.EXAMPLE.COM" -U Administrator
~]# net ads join createupn="host/rhel-server.example.com@AD.EXAMPLE.COM" -U AdministratorCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Make sure that the Services for Unix package is installed on the Windows server.
- Set up the Windows domain which will be used with SSSD.
- On the Windows machine, open Server Manager.
- Create the Active Directory Domain Services role.
- Create a new domain, such as
ad.example.com. - Add the Identity Management for UNIX service to the Active Directory Domain Services role. Use the Unix NIS domain as the domain name in the configuration.
- On the Active Directory server, create a group for the Linux users.
- Open Administrative Tools and select Active Directory Users and Computers.
- Select the Active Directory domain,
ad.example.com. - In the Users tab, right-click and select .
- Name the new group
unixusers, and save. - Double-click the
unixusersgroup entry, and open the Users tab. - Open the Unix Attributes tab.
- Set the NIS domain to the NIS domain that was configured for
ad.example.comand, optionally, set a group ID (GID) number.
- Configure a user to be part of the Unix group.
- Open Administrative Tools and select Active Directory Users and Computers.
- Select the Active Directory domain,
ad.example.com. - In the Users tab, right-click and select .
- Name the new user
aduser, and make sure that the User must change password at next logon and Lock account check boxes are not selected.Then save the user. - Double-click the
aduseruser entry, and open the Unix Attributes tab. Make sure that the Unix configuration matches that of the Active Directory domain and theunixgroupgroup:- The NIS domain, as created for the Active Directory domain
- The UID
- The login shell, to
/bin/bash - The home directory, to
/home/aduser - The primary group name, to
unixusers
Note
Password lookups on large directories can take several seconds per request. The initial user lookup is a call to the LDAP server. Unindexed searches are much more resource-intensive, and therefore take longer, than indexed searches because the server checks every entry in the directory for a match. To speed up user lookups, index the attributes that are searched for by SSSD:- uid
- uidNumber
- gidNumber
- gecos
- On the Linux system, configure the SSSD domain.
vim /etc/sssd/sssd.conf
~]# vim /etc/sssd/sssd.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow For a complete list of LDAP provider parameters, see thesssd-ldap(5)man pages.Example 13.9. An Active Directory 2008 R2 Domain with Services for Unix
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart SSSD.
service sssd restart
~]# service sssd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
13.2.15. Domain Options: Setting Username Formats
jsmith in the ldap.example.com domain and jsmith in the ldap.otherexample.com domain.
[sssd] section of the configuration and can then be defined individually in each domain section.
re_expression parameter.
(?P<name>[^@]+)@?(?P<domain>[^@]*$)
(?P<name>[^@]+)@?(?P<domain>[^@]*$)Note
jsmith and if the user belongs to the LOCAL domain (for example), then his user name is interpreted by SSSD as jsmith@LOCAL.
(?P<domain>[^\\]*?)\\?(?P<name>[^\\]+$)
(?P<domain>[^\\]*?)\\?(?P<name>[^\\]+$)- username
- username@domain.name
- DOMAIN\username
(((?P<domain>[^\\]+)\\(?P<name>.+$))|((?P<name>[^@]+)@(?P<domain>.+$))|(^(?P<name>[^@\\]+)$))
(((?P<domain>[^\\]+)\\(?P<name>.+$))|((?P<name>[^@]+)@(?P<domain>.+$))|(^(?P<name>[^@\\]+)$)) Note
jsmith@ldap.example.com, always returns the proper user account. If there are multiple users with the same user name in different domains, specifying only the user name returns the user for whichever domain comes first in the lookup order.
re_expression is the most important method for setting user name formats, there are two other options which are useful for other applications.
The first sets a default domain name to be used with all users, default_domain_suffix. (This is a global setting, available in the [sssd] section only.) There may be a case where multiple domains are configured but only one stores user data and the others are used for host or service identities. Setting a default domain name allows users to log in with only their user name, not specifying the domain name (which would be required for users outside the primary domain).
[sssd] ... default_domain_suffix = USERS.EXAMPLE.COM
[sssd]
...
default_domain_suffix = USERS.EXAMPLE.COM
The other parameter is related to re_expression, only instead of defining how to interpret a user name, it defines how to print an identified name. The full_name_format parameter sets how the user name and domain name (once determined) are displayed.
full_name_format = %1$s@%2$s
full_name_format = %1$s@%2$s13.2.16. Domain Options: Enabling Offline Authentication
[domain/EXAMPLE] cache_credentials = true
[domain/EXAMPLE]
cache_credentials = trueoffline_credentials_expiration sets the number of days after a successful login that a single credentials entry for a user is preserved in cache. Setting this to zero (0) means that entries are kept forever.
account_cache_expirationsets the number of days after a successful login that the entire user account entry is removed from the SSSD cache. This must be equal to or longer than the individual offline credentials cache expiration period.entry_cache_timeoutsets a validity period, in seconds, for all entries stored in the cache before SSSD requests updated information from the identity provider. There are also individual cache timeout parameters for group, service, netgroup, sudo, and autofs entries; these are listed in thesssd.confman page. The default time is 5400 seconds (90 minutes).
13.2.17. Domain Options: Setting Password Expirations
- The
pam_pwd_expiration_warningparameter defines the global default setting for all domains on how far in advance of the password expiration to display a warning. This is set for the PAM service. - The
pwd_expiration_warningparameter defines the per-domain setting on how far in advance of the password expiration to display a warning.When using a domain-level password expiration warning, an authentication provider (auth_provider) must also be configured for the domain.
0, then the SSSD password warning filter is not applied and the server-side password warning is automatically displayed.
Note
Password Expiration Warnings for Non-Password Authentication
- Make sure the
access_providerparameter is set toldapin thesssd.conffile. - Make sure the
ldap_pwd_policyparameter is set insssd.conf. In most situations, the appropriate value isshadow. - Add one of the following
pwd_expire_*values to theldap_access_orderparameter insssd.conf. If the password is about to expire, each one of these values only displays the expiration warning. In addition:pwd_expire_policy_rejectprevents the user from logging in if the password is already expired.pwd_expire_policy_warnallows the user to log in even if the password is already expired.pwd_expire_policy_renewprompts the user to immediately change the password if the user attempts to log in with an expired password.
For example:[domain/EXAMPLE] access_provider = ldap ldap_pwd_policy = shadow ldap_access_order = pwd_expire_policy_warn
[domain/EXAMPLE] access_provider = ldap ldap_pwd_policy = shadow ldap_access_order = pwd_expire_policy_warnCopy to Clipboard Copied! Toggle word wrap Toggle overflow
ldap_access_order and its values, see the sssd-ldap(5) man page.
13.2.18. Domain Options: Using DNS Service Discovery
id_provider = ldap is set without a corresponding ldap_uri parameter — then discovery is automatically used.
_service._protocol.domain
_service._protocol.domainexample.com domain looks like this:
_ldap._tcp.example.com
_ldap._tcp.example.comNote
_service._protocol._domain TTL priority weight port hostname
_service._protocol._domain TTL priority weight port hostnamedns_discovery_domain parameter).
[domain/EXAMPLE] ... chpass_provider = ldap ldap_chpass_dns_service_name = ldap
[domain/EXAMPLE]
...
chpass_provider = ldap
ldap_chpass_dns_service_name = ldapdns_discovery_domain) or by setting a different service type to scan for. For example:
_srv_ as the primary server value, and then list the backup servers. For example:
Note
lookup family order option in the sssd.conf configuration file.
13.2.19. Domain Options: Using IP Addresses in Certificate Subject Names (LDAP Only)
ldap_uri option instead of the server name may cause the TLS/SSL connection to fail. TLS/SSL certificates contain the server name, not the IP address. However, the subject alternative name field in the certificate can be used to include the IP address of the server, which allows a successful secure connection using an IP address.
Procedure 13.8. Using IP Addresses in Certificate Subject Names
- Convert an existing certificate into a certificate request. The signing key (
-signkey) is the key of the issuer of whatever CA originally issued the certificate. If this is done by an external CA, it requires a separate PEM file; if the certificate is self-signed, then this is the certificate itself. For example:openssl x509 -x509toreq -in old_cert.pem -out req.pem -signkey key.pem
openssl x509 -x509toreq -in old_cert.pem -out req.pem -signkey key.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow With a self-signed certificate:openssl x509 -x509toreq -in old_cert.pem -out req.pem -signkey old_cert.pem
openssl x509 -x509toreq -in old_cert.pem -out req.pem -signkey old_cert.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the
/etc/pki/tls/openssl.cnfconfiguration file to include the server's IP address under the[ v3_ca ]section:subjectAltName = IP:10.0.0.10
subjectAltName = IP:10.0.0.10Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the generated certificate request to generate a new self-signed certificate with the specified IP address:
openssl x509 -req -in req.pem -out new_cert.pem -extfile ./openssl.cnf -extensions v3_ca -signkey old_cert.pem
openssl x509 -req -in req.pem -out new_cert.pem -extfile ./openssl.cnf -extensions v3_ca -signkey old_cert.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow The-extensionsoption sets which extensions to use with the certificate. For this, it should be v3_ca to load the appropriate section. - Copy the private key block from the
old_cert.pemfile into thenew_cert.pemfile to keep all relevant information in one file.
13.2.20. Creating Domains: Proxy
| Parameter | Description |
|---|---|
| proxy_pam_target | Specifies the target to which PAM must proxy as an authentication provider. The PAM target is a file containing PAM stack information in the default PAM directory, /etc/pam.d/.
This is used to proxy an authentication provider.
Important
Ensure that the proxy PAM stack does not recursively include pam_sss.so.
|
| proxy_lib_name | Specifies which existing NSS library to proxy identity requests through.
This is used to proxy an identity provider.
|
Example 13.10. Proxy Identity and Kerberos Authentication
proxy_lib_name parameter. This library can be anything as long as it is compatible with the given authentication service. For a Kerberos authentication provider, it must be a Kerberos-compatible library, like NIS.
Example 13.11. LDAP Identity and Proxy Authentication
proxy_pam_target parameter. This library must be a PAM module that is compatible with the given identity provider. For example, this uses a PAM fingerprint module with LDAP:
sssdpamproxy, so create a /etc/pam.d/sssdpamproxy file and load the PAM/LDAP modules:
auth required pam_frprint.so account required pam_frprint.so password required pam_frprint.so session required pam_frprint.so
auth required pam_frprint.so
account required pam_frprint.so
password required pam_frprint.so
session required pam_frprint.soExample 13.12. Proxy Identity and Authentication
proxy_pam_target for the authentication PAM module and proxy_lib_name for the service, like NIS or LDAP.
- Create a
/etc/pam.d/sssdproxyldapfile which requires thepam_ldap.somodule:auth required pam_ldap.so account required pam_ldap.so password required pam_ldap.so session required pam_ldap.so
auth required pam_ldap.so account required pam_ldap.so password required pam_ldap.so session required pam_ldap.soCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Make sure the nss-pam-ldapd package is installed.
yum install nss-pam-ldapd
~]# yum install nss-pam-ldapdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the
/etc/nslcd.conffile, the configuration file for the LDAP name service daemon, to contain the information for the LDAP directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
13.2.21. Creating Domains: Kerberos Authentication
Note
krb5_kpasswd option to specify where the password changing service is running or if it is running on a non-default port. If the krb5_kpasswd option is not defined, SSSD tries to use the Kerberos KDC to change the password.
sssd-krb5(5) man page has more information about Kerberos configuration options.
Example 13.13. Basic Kerberos Authentication
Example 13.14. Setting Kerberos Ticket Renewal Options
krb5_renewable_lifetime and krb5_renew_interval parameters.
krb5_lifetime parameter. This specifies how long a single ticket is valid, and overrides any values in the KDC.
krb5_renewable_lifetime parameter, which sets the maximum lifetime of the ticket, counting all renewals.
krb5_lifetime = 1h krb5_renewable_lifetime = 1d
krb5_lifetime = 1h
krb5_renewable_lifetime = 1dkrb5_renew_interval parameter, which sets how frequently SSSD checks to see if the ticket needs to be renewed. At half of the ticket lifetime (whatever that setting is), the ticket is renewed automatically. (This value is always in seconds.)
krb5_lifetime = 1h krb5_renewable_lifetime = 1d krb5_renew_interval = 60s
krb5_lifetime = 1h
krb5_renewable_lifetime = 1d
krb5_renew_interval = 60sNote
krb5_renewable_lifetime value is not set or the krb5_renew_interval parameter is not set or is set to zero (0), then ticket renewal is disabled. Both krb5_renewable_lifetime and krb5_renew_interval are required for ticket renewal to be enabled.
| Parameter | Description |
|---|---|
| chpass_provider | Specifies which service to use for password change operations. This is assumed to be the same as the authentication provider. To use Kerberos, set this to krb5. |
| krb5_server | Gives the primary Kerberos server, by IP address or host names, to which SSSD will connect. |
| krb5_backup_server | Gives a comma-separated list of IP addresses or host names of Kerberos servers to which SSSD will connect if the primary server is not available. The list is given in order of preference, so the first server in the list is tried first.
After an hour, SSSD will attempt to reconnect to the primary service specified in the
krb5_server parameter.
When using service discovery for KDC or kpasswd servers, SSSD first searches for DNS entries that specify UDP as the connection protocol, and then falls back to TCP.
|
| krb5_realm | Identifies the Kerberos realm served by the KDC. |
| krb5_lifetime | Requests a Kerberos ticket with the specified lifetime in seconds (s), minutes (m), hours (h) or days (d). |
| krb5_renewable_lifetime | Requests a renewable Kerberos ticket with a total lifetime that is specified in seconds (s), minutes (m), hours (h) or days (d). |
| krb5_renew_interval | Sets the time, in seconds, for SSSD to check if tickets should be renewed. Tickets are renewed automatically once they exceed half their lifetime. If this option is missing or set to zero, then automatic ticket renewal is disabled. |
| krb5_store_password_if_offline | Sets whether to store user passwords if the Kerberos authentication provider is offline, and then to use that cache to request tickets when the provider is back online. The default is false, which does not store passwords. |
| krb5_kpasswd | Lists alternate Kerberos kadmin servers to use if the change password service is not running on the KDC. |
| krb5_ccname_template | Gives the directory to use to store the user's credential cache. This can be templatized, and the following tokens are supported:
krb5_ccname_template = FILE:%d/krb5cc_%U_XXXXXX |
| krb5_ccachedir | Specifies the directory to store credential caches. This can be templatized, using the same tokens as krb5_ccname_template, except for %d and %P. If %u, %U, %p, or %h are used, then SSSD creates a private directory for each user; otherwise, it creates a public directory. |
| krb5_auth_timeout | Gives the time, in seconds, before an online authentication or change password request is aborted. If possible, the authentication request is continued offline. The default is 15 seconds. |
13.2.22. Creating Domains: Access Control
Using the Simple Access Provider
simple_allow_users and simple_allow_groups, which grant access explicitly to specific users (either the given users or group members) and deny access to everyone else. It is also possible to create deny lists (which deny access only to explicit people and implicitly allow everyone else access).
- If both the allow and deny lists are empty, access is granted.
- If any list is provided, allow rules are evaluated first, and then deny rules. Practically, this means that deny rules supersede allow rules.
- If an allowed list is provided, then all users are denied access unless they are in the list.
- If only deny lists are provided, then all users are allowed access unless they are in the list.
[domain/example.com] access_provider = simple simple_allow_users = jsmith,bjensen simple_allow_groups = itgroup
[domain/example.com]
access_provider = simple
simple_allow_users = jsmith,bjensen
simple_allow_groups = itgroupNote
simple as an access provider.
sssd-simple man page, but these are rarely used.
Using the Access Filters
ldap_access_filter for LDAP and IdM and ad_access_filter for AD) specify which users are granted access to the specified host. The user filter must be used or all users are denied access. See the examples below:
[domain/example.com] access_provider = ldap ldap_access_filter = memberOf=cn=allowedusers,ou=Groups,dc=example,dc=com
[domain/example.com]
access_provider = ldap
ldap_access_filter = memberOf=cn=allowedusers,ou=Groups,dc=example,dc=com[domain/example.com] access_provider = ad ad_access_filter = memberOf=cn=allowedusers,ou=Groups,dc=example,dc=com
[domain/example.com]
access_provider = ad
ad_access_filter = memberOf=cn=allowedusers,ou=Groups,dc=example,dc=comNote
authorizedService or host attribute in an entry. In fact, all options — LDAP filter, authorizedService, and host — can be evaluated, depending on the user entry and the configuration. The ldap_access_order parameter lists all access control methods to use, in order of how they should be evaluated.
[domain/example.com] access_provider = ldap ldap_access_filter = memberOf=cn=allowedusers,ou=Groups,dc=example,dc=com ldap_access_order = filter, host, authorized_service
[domain/example.com]
access_provider = ldap
ldap_access_filter = memberOf=cn=allowedusers,ou=Groups,dc=example,dc=com
ldap_access_order = filter, host, authorized_servicesssd-ldap(5) man page.
13.2.23. Creating Domains: Primary Server and Backup Servers
Note
| Service Area | Primary Server Attribute | Backup Server Attribute |
|---|---|---|
| LDAP identity provider | ldap_uri | ldap_backup_uri |
| Active Directory identity provider | ad_server | ad_backup_server |
| Identity Management (IdM or IPA) identity provider | ipa_server | ipa_backup_server |
| Kerberos authentication provider | krb5_server | krb5_backup_server |
| Kerberos authentication provider | krb5_server | krb5_backup_server |
| Password change provider | ldap_chpass_uri | ldap_chpass_backup_uri |
_srv_ rather than a host name.) Multiple backup servers can be set, in a comma-separated list. The backup server list is in order of preference, so the first server listed is tried first.
[domain/EXAMPLE] id_provider = ad ad_server = ad.example.com ad_backup_server = ad1.example.com, ad-backup.example.com
[domain/EXAMPLE]
id_provider = ad
ad_server = ad.example.com
ad_backup_server = ad1.example.com, ad-backup.example.com13.2.24. Installing SSSD Utilities
yum install sssd-tools
~]# yum install sssd-toolsNote
13.2.25. SSSD and UID and GID Numbers
useradd or through an application such as Red Hat Identity Management or other client tools — the user is automatically assigned a user ID number and a group ID number.
Important
sss_cache -u jsmith
~]# sss_cache -u jsmith13.2.26. Creating Local System Users
Note
sss_useradd command.
sss_useradd command only requires the new user name.
sss_useradd jsmith
~]# sss_useradd jsmithsss_useradd(8) man page) which can be used to set attributes on the account, like the UID and GID, the home directory, or groups which the user belongs to.
sss_useradd --UID 501 --home /home/jsmith --groups admin,dev-group jsmith
~]# sss_useradd --UID 501 --home /home/jsmith --groups admin,dev-group jsmith13.2.27. Seeding Users into the SSSD Cache During Kickstart
Note
sss_seed utility:
sss_seed --domain EXAMPLE.COM --username testuser --password-file /tmp/sssd-pwd.txt
sss_seed --domain EXAMPLE.COM --username testuser --password-file /tmp/sssd-pwd.txt--domaingives the domain name from the SSSD configuration. This domain must already exist in the SSSD configuration.--usernamefor the short name of the user account.--password-filefor the path and name of a file containing a temporary password for the seed entry. If the user account already exists in the SSSD cache, then the temporary password in this file overwrites the stored password in the SSSD cache.
sss_seed(8) man page.
13.2.28. Managing the SSSD Cache
/var/lib/sss/db/ directory.
Purging the SSSD Cache
sss_cache, invalidates records in the SSSD cache for a user, a domain, or a group. Invalidating the current records forces the cache to retrieve the updated records from the identity provider, so changes can be realized quickly.
Note
sss_cache -E
~]# sss_cache -Esss_cache command can also clear all cached entries for a particular domain:
sss_cache -Ed LDAP1
~]# sss_cache -Ed LDAP1sss_cache can purge the records for that specific account and leave the rest of the cache intact:
sss_cache -u jsmith
~]# sss_cache -u jsmith| Short Argument | Long Argument | Description |
|---|---|---|
| -E | --everything | Invalidates all cached entries with the exception of sudo rules. |
| -d name | --domain name | Invalidates cache entries for users, groups, and other entries only within the specified domain. |
| -G | --groups | Invalidates all group records. If -g is also used, -G takes precedence and -g is ignored. |
| -g name | --group name | Invalidates the cache entry for the specified group. |
| -N | --netgroups | Invalidates cache entries for all netgroup cache records. If -n is also used, -N takes precedence and -n is ignored. |
| -n name | --netgroup name | Invalidates the cache entry for the specified netgroup. |
| -U | --users | Invalidates cache entries for all user records. If the -u option is also used, -U takes precedence and -u is ignored. |
| -u name | --user name | Invalidates the cache entry for the specified user. |
Deleting Domain Cache Files
exampleldap, the cache file is named cache_exampleldap.ldb.
- Deleting the cache file deletes all user data, both identification and cached credentials. Consequently, do not delete a cache file unless the system is online and can authenticate with a user name against the domain's servers. Without a credentials cache, offline authentication will fail.
- If the configuration is changed to reference a different identity provider, SSSD will recognize users from both providers until the cached entries from the original provider time out.It is possible to avoid this by purging the cache, but the better option is to use a different domain name for the new provider. When SSSD is restarted, it creates a new cache file with the new name and the old file is ignored.
13.2.29. Downgrading SSSD
(Wed Nov 28 21:25:50 2012) [sssd] [sysdb_domain_init_internal] (0x0010): Unknown DB version [0.14], expected [0.10] for domain AD!
(Wed Nov 28 21:25:50 2012) [sssd] [sysdb_domain_init_internal] (0x0010): Unknown DB version [0.14], expected [0.10] for domain AD!- Delete the existing cache database files.
rm -rf /var/lib/sss/db/*
~]# rm -rf /var/lib/sss/db/*Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the SSSD process.
service sssd restart Stopping sssd: [FAILED] Starting sssd: [ OK ]
~]# service sssd restart Stopping sssd: [FAILED] Starting sssd: [ OK ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow
13.2.30. Using NSCD with SSSD
resolv.conf file. This file is typically only read once, and so any changes made to this file are not automatically applied. This can cause NFS locking to fail on the machine where the NSCD service is running, unless that service is manually restarted.
/etc/nscd.conf file and rely on the SSSD cache for the passwd, group, and netgroup entries.
/etc/nscd.conf file:
enable-cache hosts yes enable-cache passwd no enable-cache group no enable-cache netgroup no
enable-cache hosts yes
enable-cache passwd no
enable-cache group no
enable-cache netgroup no
13.2.31. Troubleshooting SSSD
Setting Debug Logs for SSSD Domains
debug_level parameter for each section in the sssd.conf file for which to produce extra logs. For example:
[domain/LDAP] cache_credentials = true debug_level = 9
[domain/LDAP]
cache_credentials = true
debug_level = 9| Level | Description |
|---|---|
| 0 | Fatal failures. Anything that would prevent SSSD from starting up or causes it to cease running. |
| 1 | Critical failures. An error that doesn't kill the SSSD, but one that indicates that at least one major feature is not going to work properly. |
| 2 | Serious failures. An error announcing that a particular request or operation has failed. |
| 3 | Minor failures. These are the errors that would percolate down to cause the operation failure of 2. |
| 4 | Configuration settings. |
| 5 | Function data. |
| 6 | Trace messages for operation functions. |
| 7 | Trace messages for internal control functions. |
| 8 | Contents of function-internal variables that may be interesting. |
| 9 | Extremely low-level tracing information. |
Note
[sssd] section. Now, each domain and service must configure its own debug log level.
sssd_update_debug_levels.py script.
python -m SSSDConfig.sssd_update_debug_levels.py
python -m SSSDConfig.sssd_update_debug_levels.pyChecking SSSD Log Files
/var/log/sssd/ directory. SSSD produces a log file for each domain, as well as an sssd_pam.log and an sssd_nss.log file.
/var/log/secure file logs authentication failures and the reason for the failure.
Problems with SSSD Configuration
- Q: SSSD fails to start
- Q: I don't see any groups with 'id' or group members with 'getent group'.
- Q: Authentication fails against LDAP.
- Q: Connecting to LDAP servers on non-standard ports fail.
- Q: NSS fails to return user information
- Q: NSS returns incorrect user information
- Q: Setting the password for the local SSSD user prompts twice for the password
- Q: I am trying to use sudo rules with an Identity Management (IPA) provider, but no sudo rules are being found, even though sudo is properly configured.
- Q: Password lookups on large directories can take several seconds per request. How can this be improved?
- Q: An Active Directory identity provider is properly configured in my sssd.conf file, but SSSD fails to connect to it, with GSS-API errors.
- Q: I configured SSSD for central authentication, but now several of my applications (such as Firefox or Adobe) will not start.
- Q: SSSD is showing an automount location that I removed.
- SSSD requires at least one properly configured domain before the service will start. Without a domain, attempting to start SSSD returns an error that no domains are configured:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the/etc/sssd/sssd.conffile and create at least one domain. - SSSD also requires at least one available service provider before it will start. If the problem is with the service provider configuration, the error message indicates that there are no services configured:
[sssd] [get_monitor_config] (0): No services configured!
[sssd] [get_monitor_config] (0): No services configured!Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the/etc/sssd/sssd.conffile and configure at least one service provider.Important
SSSD requires that service providers be configured as a comma-separated list in a singleservicesentry in the/etc/sssd/sssd.conffile. If services are listed in multiple entries, only the last entry is recognized by SSSD.
ldap_schema setting in the [domain/DOMAINNAME] section of sssd.conf.
memberuid attribute, which contains the name of the users that are members. In an RFC2307bis server, group members are stored as the multi-valued member or uniqueMember attribute which contains the DN of the user or group that is a member of this group. RFC2307bis allows nested groups to be maintained as well.
- Set
ldap_schematorfc2307bis. - Delete
/var/lib/sss/db/cache_DOMAINNAME.ldb. - Restarting SSSD.
sssd.conf:
ldap_group_name = uniqueMember
ldap_group_name = uniqueMembersssd.conf is configured to connect over a standard protocol (ldap://), it attempts to encrypt the communication channel with Start TLS. If sssd.conf is configured to connect over a secure protocol (ldaps://), then SSSD uses SSL.
syslog message is written, indicating that TLS encryption could not be started. The certificate configuration can be tested by checking if the LDAP server is accessible apart from SSSD. For example, this tests an anonymous bind over a TLS connection to test.example.com:
ldapsearch -x -ZZ -h test.example.com -b dc=example,dc=com
$ ldapsearch -x -ZZ -h test.example.com -b dc=example,dc=comldap_start_tls: Connect error (-11) additional info: TLS error -8179:Unknown code ___f 13
ldap_start_tls: Connect error (-11) additional info: TLS error -8179:Unknown code ___f 13- Obtain a copy of the public CA certificate for the certificate authority used to sign the LDAP server certificate and save it to the local system.
- Add a line to the
sssd.conffile that points to the CA certificate on the filesystem.ldap_tls_cacert = /path/to/cacert
ldap_tls_cacert = /path/to/cacertCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If the LDAP server uses a self-signed certificate, remove the
ldap_tls_reqcertline from thesssd.conffile.This parameter directs SSSD to trust any certificate issued by the CA certificate, which is a security risk with a self-signed CA certificate.
semanage port -a -t ldap_port_t -p tcp 1389
# semanage port -a -t ldap_port_t -p tcp 1389- Ensure that NSS is running:
service sssd status
# service sssd statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If NSS is running, make sure that the provider is properly configured in the
[nss]section of the/etc/sssd/sssd.conffile. Especially check thefilter_usersandfilter_groupsattributes. - Make sure that NSS is included in the list of services that SSSD uses.
- Check the configuration in the
/etc/nsswitch.conffile.
use_fully_qualified_domains attribute to true in the /etc/sssd/sssd.conf file. This differentiates between different users in different domains with the same name.
use_authtok option is correctly configured in your /etc/pam.d/system-auth file.
sssd.conf. For example:
- uid
- uidNumber
- gidNumber
- gecos
sssd.conf file, but SSSD fails to connect to it, with GSS-API errors.
(Fri Jul 27 18:27:44 2012) [sssd[be[ADTEST]]] [sasl_bind_send] (0x0020): ldap_sasl_bind failed (-2)[Local error] (Fri Jul 27 18:27:44 2012) [sssd[be[ADTEST]]] [sasl_bind_send] (0x0080): Extended failure message: [SASL(-1): generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Cannot determine realm for numeric host address)]
(Fri Jul 27 18:27:44 2012) [sssd[be[ADTEST]]] [sasl_bind_send] (0x0020): ldap_sasl_bind failed (-2)[Local error]
(Fri Jul 27 18:27:44 2012) [sssd[be[ADTEST]]] [sasl_bind_send] (0x0080): Extended failure message: [SASL(-1): generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Cannot determine realm for numeric host address)]ad_server to the name of the Active Directory host.
Failed to contact configuration server. See http://www.gnome.org/projects/gconf/ for information. (Details - 1: IOR file '/tmp/gconfd-somebody/lock/ior' not opened successfully, no gconfd located: Permission denied 2: IOR file '/tmp/gconfd-somebody/lock/ior' not opened successfully, no gconfd located: Permission denied)
Failed to contact configuration server. See http://www.gnome.org/projects/gconf/
for information. (Details - 1: IOR file '/tmp/gconfd-somebody/lock/ior'
not opened successfully, no gconfd located: Permission denied 2: IOR
file '/tmp/gconfd-somebody/lock/ior' not opened successfully, no gconfd
located: Permission denied)acroread (acroread:12739): GLib-WARNING **: getpwuid_r(): failed due to unknown user id (366)
~]$ acroread
(acroread:12739): GLib-WARNING **: getpwuid_r(): failed due to unknown
user id (366)- Remove the autofs cache, as described in the section called “Purging the SSSD Cache”.
- Restart SSSD, as in Section 13.2.3, “Starting and Stopping SSSD”.
Chapter 14. OpenSSH
SSH (Secure Shell) is a protocol which facilitates secure communications between two systems using a client-server architecture and allows users to log into server host systems remotely. Unlike other remote communication protocols, such as FTP, Telnet, or rlogin, SSH encrypts the login session, rendering the connection difficult for intruders to collect unencrypted passwords.
telnet or rsh. A related program called scp replaces older programs designed to copy files between hosts, such as rcp. Because these older applications do not encrypt passwords transmitted between the client and the server, avoid them whenever possible. Using secure methods to log into remote systems decreases the risks for both the client system and the remote host.
14.1. The SSH Protocol
14.1.1. Why Use SSH?
- Interception of communication between two systems
- The attacker can be somewhere on the network between the communicating parties, copying any information passed between them. He may intercept and keep the information, or alter the information and send it on to the intended recipient.This attack is usually performed using a packet sniffer, a rather common network utility that captures each packet flowing through the network, and analyzes its content.
- Impersonation of a particular host
- Attacker's system is configured to pose as the intended recipient of a transmission. If this strategy works, the user's system remains unaware that it is communicating with the wrong host.This attack can be performed using a technique known as DNS poisoning, or via so-called IP spoofing. In the first case, the intruder uses a cracked DNS server to point client systems to a maliciously duplicated host. In the second case, the intruder sends falsified network packets that appear to be from a trusted host.
14.1.2. Main Features
- No one can pose as the intended server
- After an initial connection, the client can verify that it is connecting to the same server it had connected to previously.
- No one can capture the authentication information
- The client transmits its authentication information to the server using strong, 128-bit encryption.
- No one can intercept the communication
- All data sent and received during a session is transferred using 128-bit encryption, making intercepted transmissions extremely difficult to decrypt and read.
- It provides secure means to use graphical applications over a network
- Using a technique called X11 forwarding, the client can forward X11 (X Window System) applications from the server. Note that if you set the
ForwardX11Trustedoption toyesor you use SSH with the-Yoption, you bypass the X11 SECURITY extension controls, which can result in a security threat. - It provides a way to secure otherwise insecure protocols
- The SSH protocol encrypts everything it sends and receives. Using a technique called port forwarding, an SSH server can become a conduit to securing otherwise insecure protocols, like POP, and increasing overall system and data security.
- It can be used to create a secure channel
- The OpenSSH server and client can be configured to create a tunnel similar to a virtual private network for traffic between server and client machines.
- It supports the Kerberos authentication
- OpenSSH servers and clients can be configured to authenticate using the GSSAPI (Generic Security Services Application Program Interface) implementation of the Kerberos network authentication protocol.
14.1.3. Protocol Versions
Important
14.1.4. Event Sequence of an SSH Connection
- A cryptographic handshake is made so that the client can verify that it is communicating with the correct server.
- The transport layer of the connection between the client and remote host is encrypted using a symmetric cipher.
- The client authenticates itself to the server.
- The client interacts with the remote host over the encrypted connection.
14.1.4.1. Transport Layer
- Keys are exchanged
- The public key encryption algorithm is determined
- The symmetric encryption algorithm is determined
- The message authentication algorithm is determined
- The hash algorithm is determined
Warning
14.1.4.2. Authentication
14.1.4.3. Channels
14.2. Configuring OpenSSH
14.2.1. Configuration Files
ssh, scp, and sftp), and those for the server (the sshd daemon).
/etc/ssh/ directory as described in Table 14.1, “System-wide configuration files”. User-specific SSH configuration information is stored in ~/.ssh/ within the user's home directory as described in Table 14.2, “User-specific configuration files”.
| File | Description |
|---|---|
/etc/ssh/moduli | Contains Diffie-Hellman groups used for the Diffie-Hellman key exchange which is critical for constructing a secure transport layer. When keys are exchanged at the beginning of an SSH session, a shared, secret value is created which cannot be determined by either party alone. This value is then used to provide host authentication. |
/etc/ssh/ssh_config | The default SSH client configuration file. Note that it is overridden by ~/.ssh/config if it exists. |
/etc/ssh/sshd_config | The configuration file for the sshd daemon. |
/etc/ssh/ssh_host_dsa_key | The DSA private key used by the sshd daemon. |
/etc/ssh/ssh_host_dsa_key.pub | The DSA public key used by the sshd daemon. |
/etc/ssh/ssh_host_key | The RSA private key used by the sshd daemon for version 1 of the SSH protocol. |
/etc/ssh/ssh_host_key.pub | The RSA public key used by the sshd daemon for version 1 of the SSH protocol. |
/etc/ssh/ssh_host_rsa_key | The RSA private key used by the sshd daemon for version 2 of the SSH protocol. |
/etc/ssh/ssh_host_rsa_key.pub | The RSA public key used by the sshd daemon for version 2 of the SSH protocol. |
/etc/pam.d/sshd | The PAM configuration file for the sshd daemon. |
/etc/sysconfig/sshd | Configuration file for the sshd service. |
| File | Description |
|---|---|
~/.ssh/authorized_keys | Holds a list of authorized public keys for servers. When the client connects to a server, the server authenticates the client by checking its signed public key stored within this file. |
~/.ssh/id_dsa | Contains the DSA private key of the user. |
~/.ssh/id_dsa.pub | The DSA public key of the user. |
~/.ssh/id_rsa | The RSA private key used by ssh for version 2 of the SSH protocol. |
~/.ssh/id_rsa.pub | The RSA public key used by ssh for version 2 of the SSH protocol. |
~/.ssh/identity | The RSA private key used by ssh for version 1 of the SSH protocol. |
~/.ssh/identity.pub | The RSA public key used by ssh for version 1 of the SSH protocol. |
~/.ssh/known_hosts | Contains DSA host keys of SSH servers accessed by the user. This file is very important for ensuring that the SSH client is connecting the correct SSH server. |
ssh_config(5) and sshd_config(5) manual pages.
14.2.2. Starting an OpenSSH Server
sshd daemon, type the following at a shell prompt:
service sshd start
~]# service sshd startsshd daemon, use the following command:
service sshd stop
~]# service sshd stopchkconfig sshd on
~]# chkconfig sshd on/etc/ssh/ directory (see Table 14.1, “System-wide configuration files” for a complete list), and restore them whenever you reinstall the system.
14.2.3. Requiring SSH for Remote Connections
telnet, rsh, rlogin, and vsftpd.
chkconfig telnet off chkconfig rsh off chkconfig rlogin off chkconfig vsftpd off
~]# chkconfig telnet off
~]# chkconfig rsh off
~]# chkconfig rlogin off
~]# chkconfig vsftpd off14.2.4. Using Key-Based Authentication
/etc/ssh/sshd_config configuration file in a text editor such as vi or nano, and change the PasswordAuthentication option as follows:
PasswordAuthentication no
PasswordAuthentication nossh, scp, or sftp to connect to the server from a client machine, generate an authorization key pair by following the steps below. Note that keys must be generated for each user separately.
Important
root, as only root would be able to use those keys.
Note
~/.ssh/ directory to keep the generated key pair. Copy the backed-up data to the home directory in the new system for any user you require, including root.
14.2.4.1. Generating Key Pairs
- Generate an RSA key pair by typing the following at a shell prompt:
ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/home/john/.ssh/id_rsa):
~]$ ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/home/john/.ssh/id_rsa):Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Press Enter to confirm the default location (that is,
~/.ssh/id_rsa) for the newly created key. - Enter a passphrase, and confirm it by entering it again when prompted to do so. For security reasons, avoid using the same password as you use to log in to your account.After this, you will be presented with a message similar to this:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Change the permissions of the
~/.ssh/directory:chmod 700 ~/.ssh
~]$ chmod 700 ~/.sshCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the content of
~/.ssh/id_rsa.pubinto the~/.ssh/authorized_keyson the machine to which you want to connect, appending it to its end if the file already exists. - Change the permissions of the
~/.ssh/authorized_keysfile using the following command:chmod 600 ~/.ssh/authorized_keys
~]$ chmod 600 ~/.ssh/authorized_keysCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Generate a DSA key pair by typing the following at a shell prompt:
ssh-keygen -t dsa Generating public/private dsa key pair. Enter file in which to save the key (/home/john/.ssh/id_dsa):
~]$ ssh-keygen -t dsa Generating public/private dsa key pair. Enter file in which to save the key (/home/john/.ssh/id_dsa):Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Press Enter to confirm the default location (that is,
~/.ssh/id_dsa) for the newly created key. - Enter a passphrase, and confirm it by entering it again when prompted to do so. For security reasons, avoid using the same password as you use to log in to your account.After this, you will be presented with a message similar to this:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Change the permissions of the
~/.ssh/directory:chmod 700 ~/.ssh
~]$ chmod 700 ~/.sshCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the content of
~/.ssh/id_dsa.pubinto the~/.ssh/authorized_keyson the machine to which you want to connect, appending it to its end if the file already exists. - Change the permissions of the
~/.ssh/authorized_keysfile using the following command:chmod 600 ~/.ssh/authorized_keys
~]$ chmod 600 ~/.ssh/authorized_keysCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Generate an RSA key pair by typing the following at a shell prompt:
ssh-keygen -t rsa1 Generating public/private rsa1 key pair. Enter file in which to save the key (/home/john/.ssh/identity):
~]$ ssh-keygen -t rsa1 Generating public/private rsa1 key pair. Enter file in which to save the key (/home/john/.ssh/identity):Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Press Enter to confirm the default location (that is,
~/.ssh/identity) for the newly created key. - Enter a passphrase, and confirm it by entering it again when prompted to do so. For security reasons, avoid using the same password as you use to log into your account.After this, you will be presented with a message similar to this:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Change the permissions of the
~/.ssh/directory:chmod 700 ~/.ssh
~]$ chmod 700 ~/.sshCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the content of
~/.ssh/identity.pubinto the~/.ssh/authorized_keyson the machine to which you want to connect, appending it to its end if the file already exists. - Change the permissions of the
~/.ssh/authorized_keysfile using the following command:chmod 600 ~/.ssh/authorized_keys
~]$ chmod 600 ~/.ssh/authorized_keysCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Important
14.2.4.2. Configuring ssh-agent
ssh-agent authentication agent. If you are running GNOME, you can configure it to prompt you for your passphrase whenever you log in and remember it during the whole session. Otherwise you can store the passphrase for a certain shell prompt.
- Make sure you have the openssh-askpass package installed. If not, see Section 8.2.4, “Installing Packages” for more information on how to install new packages in Red Hat Enterprise Linux.
- Select → → from the panel. The Startup Applications Preferences will be started, and the tab containing a list of available startup programs will be shown by default.
Figure 14.1. Startup Applications Preferences
- Click the button on the right, and enter
/usr/bin/ssh-addin the Command field.Figure 14.2. Adding new application
- Click and make sure the check box next to the newly added item is selected.
Figure 14.3. Enabling the application
- Log out and then log back in. A dialog box will appear prompting you for your passphrase. From this point on, you should not be prompted for a password by
ssh,scp, orsftp.Figure 14.4. Entering a passphrase
ssh-add Enter passphrase for /home/john/.ssh/id_rsa:
~]$ ssh-add
Enter passphrase for /home/john/.ssh/id_rsa:14.2.4.3. Multiple required methods of authentication for sshd
RequiredAuthentications2 option in the /etc/ssh/sshd_config file as desired, for example by running:
echo "RequiredAuthentications2 publickey,password" >> /etc/ssh/sshd_config
~]# echo "RequiredAuthentications2 publickey,password" >> /etc/ssh/sshd_configsshd_config(5) manual page.
14.3. Using OpenSSH Certificate Authentication
14.3.1. Introduction to SSH Certificates
ssh-keygen utility. The format of the certificate is described in /usr/share/doc/openssh-version/PROTOCOL.certkeys.
ssh-keygen utility supports two types of certificates: user and host. User certificates authenticate users to servers, whereas host certificates authenticate server hosts to users. For certificates to be used for user or host authentication, sshd must be configured to trust the CA public key.
14.3.2. Support for SSH Certificates
root:
yum install openssh Package openssh-5.3p1-104.el6_6.1.i686 already installed and latest version Nothing to do
~]# yum install openssh
Package openssh-5.3p1-104.el6_6.1.i686 already installed and latest version
Nothing to do14.3.3. Creating SSH CA Certificate Signing Keys
ca_user_key and ca_host_key, however it is possible to use just one CA key to sign both certificates. It is also easier to follow the procedures if separate keys are used, so the examples that follow will use separate keys.
ssh-keygen -s ca_user_key -I certificate_ID id_rsa.pub
ssh-keygen -s ca_user_key -I certificate_ID id_rsa.pub-s indicates the private key used to sign the certificate, -I indicates an identity string, the certificate_ID, which can be any alpha numeric value. It is stored as a zero terminated string in the certificate. The certificate_ID is logged whenever the certificate is used for identification and it is also used when revoking a certificate. Having a long value would make logs hard to read, therefore using the host name for host certificates and the user name for user certificates is a safe choice.
-h option: ssh-keygen -s ca_host_key -I certificate_ID -h ssh_host_rsa_key.pub
ssh-keygen -s ca_host_key -I certificate_ID -h ssh_host_rsa_key.pubImportant
root user will be used. In a real production environment using an offline computer with an administrative user account is recommended. For guidance on key lengths see NIST Special Publication 800-131A.
Procedure 14.1. Generating SSH CA Certificate Signing Keys
- On the server designated to be the CA, generate two keys for use in signing certificates. These are the keys that all other hosts need to trust. Choose suitable names, for example
ca_user_keyandca_host_key. To generate the user certificate signing key, enter the following command asroot:Generate a host certificate signing key,Copy to Clipboard Copied! Toggle word wrap Toggle overflow ca_host_key, as follows:If required, confirm the permissions are correct:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Create the CA server's own host certificate by signing the server's host public key together with an identification string such as the host name, the CA server's fully qualified domain name (FQDN) but without the trailing
., and a validity period. The command takes the following form:Thessh-keygen -s ~/.ssh/ca_host_key -I certificate_ID -h -Z host_name.example.com -V -start:+end /etc/ssh/ssh_host_rsa.pub
ssh-keygen -s ~/.ssh/ca_host_key -I certificate_ID -h -Z host_name.example.com -V -start:+end /etc/ssh/ssh_host_rsa.pubCopy to Clipboard Copied! Toggle word wrap Toggle overflow -Zoption restricts this certificate to a specific host within the domain. The-Voption is for adding a validity period; this is highly recommend. Where the validity period is intended to be one year, fifty two weeks, consider the need for time to change the certificates and any holiday periods around the time of certificate expiry.For example:ssh-keygen -s ~/.ssh/ca_host_key -I host_name -h -Z host_name.example.com -V -1w:+54w5d /etc/ssh/ssh_host_rsa.pub Enter passphrase: Signed host key /root/.ssh/ssh_host_rsa-cert.pub: id "host_name" serial 0 for host_name.example.com valid from 2015-05-15T13:52:29 to 2016-06-08T13:52:29
~]# ssh-keygen -s ~/.ssh/ca_host_key -I host_name -h -Z host_name.example.com -V -1w:+54w5d /etc/ssh/ssh_host_rsa.pub Enter passphrase: Signed host key /root/.ssh/ssh_host_rsa-cert.pub: id "host_name" serial 0 for host_name.example.com valid from 2015-05-15T13:52:29 to 2016-06-08T13:52:29Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14.3.4. Distributing and Trusting SSH CA Public Keys
ca_user_key.pub.
ca_user_key.pub key and download it to all hosts that are required to allow remote users to log in. Alternately, copy the CA user public key to all the hosts. In a production environment, consider copying the public key to an administrator account first. The secure copy command can be used to copy the public key to remote hosts. The command has the following format: scp ~/.ssh/ca_user_key.pub root@host_name.example.com:/etc/ssh/
scp ~/.ssh/ca_user_key.pub root@host_name.example.com:/etc/ssh/root:
~/.ssh/authorized_keys file using the cert-authority directive or for global use by means of the TrustedUserCAKeys directive in the /etc/ssh/sshd_config file. For remote host authentication, CA keys can be marked as trusted globally in the /etc/ssh/known_hosts file or per-user in the ~/.ssh/ssh_known_hosts file.
Procedure 14.2. Trusting the User Signing Key
- For user certificates which have one or more principles listed, and where the setting is to have global effect, edit the
/etc/ssh/sshd_configfile as follows:RestartTrustedUserCAKeys /etc/ssh/ca_user_key.pub
TrustedUserCAKeys /etc/ssh/ca_user_key.pubCopy to Clipboard Copied! Toggle word wrap Toggle overflow sshdto make the changes take effect:service sshd restart
~]# service sshd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
ca_host_key.pub.
Procedure 14.3. Trusting the Host Signing Key
- Extract the contents of the public key used to sign the host certificate. For example, on the CA:
cat ~/.ssh/ca_host_key.pub ssh-rsa AAAAB5Wm.== root@ca-server.example.com
cat ~/.ssh/ca_host_key.pub ssh-rsa AAAAB5Wm.== root@ca-server.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To configure client systems to trust servers' signed host certificates, add the contents of the
ca_host_key.pubinto the globalknown_hostsfile. This will automatically check a server's host advertised certificate against the CA public key for all users every time a new machine is connected to in the domain*.example.com. Login asrootand configure the/etc/ssh/ssh_known_hostsfile, as follows:Wherevi /etc/ssh/ssh_known_hosts # A CA key, accepted for any host in *.example.com @cert-authority *.example.com ssh-rsa AAAAB5Wm.
~]# vi /etc/ssh/ssh_known_hosts # A CA key, accepted for any host in *.example.com @cert-authority *.example.com ssh-rsa AAAAB5Wm.Copy to Clipboard Copied! Toggle word wrap Toggle overflow ssh-rsa AAAAB5Wm.is the contents ofca_host_key.pub. The above configures the system to trust the CA servers host public key. This enables global authentication of the certificates presented by hosts to remote users.
14.3.5. Creating SSH Certificates
Important
root user's /etc/ssh/ directory is not recommend. In the examples below an account named admin with a directory named keys/ will be used.
admin, and a directory to receive the user's keys. For example:
mkdir keys
~]$ mkdir keyschmod o+w keys ls -la keys total 8 drwxrwxrwx. 2 admin admin 4096 May 22 16:17 . drwx------. 3 admin admin 4096 May 22 16:17 ..
~]$ chmod o+w keys
ls -la keys
total 8
drwxrwxrwx. 2 admin admin 4096 May 22 16:17 .
drwx------. 3 admin admin 4096 May 22 16:17 ..14.3.5.1. Creating SSH Certificates to Authenticate Hosts
ssh-keygen -s ca_host_key -I host_name -h ssh_host_rsa_key.pub
ssh-keygen -s ca_host_key -I host_name -h ssh_host_rsa_key.pubssh_host_rsa_key-cert.pub.
Procedure 14.4. Generating a Host Certificate
- Host keys are generated automatically on the system. To list them enter the following command:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the chosen public key to the server designated as the CA. For example, from the host:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternately, from the CA:scp root@host_name.example.com:/etc/ssh/ssh_host_rsa_key.pub ~/keys/ssh_host_rsa_key.pub
~]$ scp root@host_name.example.com:/etc/ssh/ssh_host_rsa_key.pub ~/keys/ssh_host_rsa_key.pubCopy to Clipboard Copied! Toggle word wrap Toggle overflow - On the CA server, sign the host's public key. For example, as
root:Where host_name is the host name of the system requiring the certificate.ssh-keygen -s ~/.ssh/ca_host_key -I host_name -h -Z host_name.example.com -V -1d:+54w /home/admin/keys/ssh_host_rsa_key.pub Enter passphrase: Signed host key /home/admin/keys/ssh_host_rsa_key-cert.pub: id "host_name" serial 0 for host_name.example.com valid from 2015-05-26T12:21:54 to 2016-06-08T12:21:54
~]# ssh-keygen -s ~/.ssh/ca_host_key -I host_name -h -Z host_name.example.com -V -1d:+54w /home/admin/keys/ssh_host_rsa_key.pub Enter passphrase: Signed host key /home/admin/keys/ssh_host_rsa_key-cert.pub: id "host_name" serial 0 for host_name.example.com valid from 2015-05-26T12:21:54 to 2016-06-08T12:21:54Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the certificate to the host. For example, from the CA:
scp /home/admin/keys/ssh_host_rsa_key-cert.pub root@host_name.example.com:/etc/ssh/ root@host_name.example.com's password: ssh_host_rsa_key-cert.pub 100% 1384 1.5KB/s 00:00
~]# scp /home/admin/keys/ssh_host_rsa_key-cert.pub root@host_name.example.com:/etc/ssh/ root@host_name.example.com's password: ssh_host_rsa_key-cert.pub 100% 1384 1.5KB/s 00:00Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the host to present the certificate to a user's system when a user initiates the login process. As
root, edit the/etc/ssh/sshd_configfile as follows:HostCertificate /etc/ssh/ssh_host_rsa_key-cert.pub
HostCertificate /etc/ssh/ssh_host_rsa_key-cert.pubCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart
sshdto make the changes take effect:service sshd restart
~]# service sshd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow - On user's systems. remove keys belonging to hosts from the
~/.ssh/known_hostsfile if the user has previously logged into the host configured above. When a user logs into the host they should no longer be presented with the warning about the hosts authenticity.
/etc/ssh/known_hosts file, as described in Procedure 14.3, “Trusting the Host Signing Key”, and that the server's public key is not in the ~/.ssh/known_hosts file. Then attempt to log into the server over SSH as a remote user. You should not see a warning about the authenticity of the host. If required, add the -v option to the SSH command to see logging information.
14.3.5.2. Creating SSH Certificates for Authenticating Users
ssh-keygen -s ca_user_key -I user_name -Z user_name -V -start:+end id_rsa.pub
ssh-keygen -s ca_user_key -I user_name -Z user_name -V -start:+end id_rsa.pubid_rsa-cert.pub.
- Add more user's names to the certificate during the signing process using the
-Zoption:-Z "name1[,name2,...]"
-Z "name1[,name2,...]"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - On the user's system, add the public key of the CA in the
~/.ssh/authorized_keysfile using thecert-authoritydirective and list the principals names as follows:vi ~/.ssh/authorized_keys # A CA key, accepted for any host in *.example.com @cert-authority principals="name1,name2" *.example.com ssh-rsa AAAAB5Wm.
~]# vi ~/.ssh/authorized_keys # A CA key, accepted for any host in *.example.com @cert-authority principals="name1,name2" *.example.com ssh-rsa AAAAB5Wm.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - On the server, create an
AuthorizedPrincipalsFilefile, either per user or globally, and add the principles' names to the file for those users allowed to log in. Then in the/etc/ssh/sshd_configfile, specify the file using theAuthorizedPrincipalsFiledirective.
Procedure 14.5. Generating a User Certificate
- On client systems, login as the user who requires the certificate. Check for available keys as follows:If no suitable public key exists, generate one and set the directory permissions if the directory is not the default directory. For example, enter the following command:
ls -l ~/.ssh/
~]$ ls -l ~/.ssh/Copy to Clipboard Copied! Toggle word wrap Toggle overflow By default the directory permissions for a user's keys areCopy to Clipboard Copied! Toggle word wrap Toggle overflow drwx------., or octal 0700. If required, confirm the permissions are correct:See Section 14.2.4, “Using Key-Based Authentication” for more examples of key generation and for instructions on setting the correct directory permissions.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The chosen public key must be copied to the server designated as the CA, in order to be signed. The secure copy command can be used to do this, the command has the following format:Where protocol is the part of the file name indicating the protocol used to generate the key, for example
scp ~/.ssh/id_protocol.pub admin@ca_server.example.com:~/keys/
scp ~/.ssh/id_protocol.pub admin@ca_server.example.com:~/keys/Copy to Clipboard Copied! Toggle word wrap Toggle overflow rsa, admin is an account on the CA server, and /keys/ is a directory setup to receive the keys to be signed.Copy the chosen public key to the server designated as the CA. For example:If you have configured the client system to trust the host signing key as described in Procedure 14.3, “Trusting the Host Signing Key” then you should not see a warning about the authenticity of the remote host.scp ~/.ssh/id_rsa.pub admin@ca-server.example.com:~/keys/ admin@ca-server.example.com's password: id_rsa.pub 100% 421 0.4KB/s 00:00
~]$ scp ~/.ssh/id_rsa.pub admin@ca-server.example.com:~/keys/ admin@ca-server.example.com's password: id_rsa.pub 100% 421 0.4KB/s 00:00Copy to Clipboard Copied! Toggle word wrap Toggle overflow - On the CA server, sign the user's public key. For example, as
root:ssh-keygen -s ~/.ssh/ca_user_key -I user1 -Z user1 -V -1d:+54w /home/admin/keys/id_rsa.pub Enter passphrase: Signed user key /home/admin/keys/id_rsa-cert.pub: id "user1" serial 0 for host_name.example.com valid from 2015-05-21T16:43:17 to 2016-06-03T16:43:17
~]# ssh-keygen -s ~/.ssh/ca_user_key -I user1 -Z user1 -V -1d:+54w /home/admin/keys/id_rsa.pub Enter passphrase: Signed user key /home/admin/keys/id_rsa-cert.pub: id "user1" serial 0 for host_name.example.com valid from 2015-05-21T16:43:17 to 2016-06-03T16:43:17Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the resulting certificate to the user's
~/.ssh/directory on their system. For example:scp /home/admin/keys/id_rsa-cert.pub user1@host_name.example.com:~/.ssh/ user1@host_name.example.com's password: id_rsa-cert.pub 100% 1498 1.5KB/s 00:00
~]# scp /home/admin/keys/id_rsa-cert.pub user1@host_name.example.com:~/.ssh/ user1@host_name.example.com's password: id_rsa-cert.pub 100% 1498 1.5KB/s 00:00Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If using the standard file names and location then no further configuration is required as the SSH daemon will search for user certificates ending in
-cert.puband use them automatically if it finds them. Note that the default location and file names for for SSH version 2 keys are:~/.ssh/id_dsa,~/.ssh/id_ecdsaand~/.ssh/id_rsaas explained in thessh_config(5)manual page. If you use these locations and naming conventions then there is no need for editing the configuration files to enablesshdto present the certificate. They will be used automatically when logging in to a remote system. In this is the case then skip to step 6.If required to use a non-default directory or file naming convention, then asroot, add the following line to the/etc/ssh/ssh_configor~/.ssh/configfiles:Note that this must be the private key name, do not hadIdentityFile ~/path/key_file
IdentityFile ~/path/key_fileCopy to Clipboard Copied! Toggle word wrap Toggle overflow .pubor-cert.pub. Ensure the file permission are correct. For example:This will enable the user of this system to be authenticated by a user certificate when logging into a remote system configured to trust the CA user certificate signing key.ls -la ~/.ssh/config -rw-rw-r--. 1 user1 user1 36 May 27 21:49 /home/user1/.ssh/config chmod 700 ~/.ssh/config ls -la ~/.ssh/config -rwx------. 1 user1 user1 36 May 27 21:49 /home/user1/.ssh/config
~]$ ls -la ~/.ssh/config -rw-rw-r--. 1 user1 user1 36 May 27 21:49 /home/user1/.ssh/config chmod 700 ~/.ssh/config ~]$ ls -la ~/.ssh/config -rwx------. 1 user1 user1 36 May 27 21:49 /home/user1/.ssh/configCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To test the user certificate, attempt to log into a server over SSH from the user's account. You should do this as the user listed as a principle in the certificate, if any are specified. You should not be prompted for a password. If required, add the
-voption to the SSH command to see logging information.
14.3.6. Signing an SSH Certificate Using a PKCS#11 Token
-D and identifying the CA key by providing its public half as an argument to the -s option: ssh-keygen -s ca_host_key.pub -D libpkcs11.so -I certificate_ID host_key.pub
ssh-keygen -s ca_host_key.pub -D libpkcs11.so -I certificate_ID host_key.pub-Z option as follows:
ssh-keygen -s ca_user_key.pub -D libpkcs11.so -I certificate_ID -Z user1,user2 id_rsa.pub
ssh-keygen -s ca_user_key.pub -D libpkcs11.so -I certificate_ID -Z user1,user2 id_rsa.pubssh-keygen -s ca_host_key.pub -D libpkcs11.so -I certificate_ID -h -Z host.domain ssh_host_rsa_key.pub
ssh-keygen -s ca_host_key.pub -D libpkcs11.so -I certificate_ID -h -Z host.domain ssh_host_rsa_key.pubssh-keygen(1) manual page for the -O option.
-V option allows specifying a certificates start and end times. For example: ssh-keygen -s ca_user_key -I certificate_ID id_rsa.pub -V "-1w:+54w5d"
ssh-keygen -s ca_user_key -I certificate_ID id_rsa.pub -V "-1w:+54w5d"14.3.7. Viewing an SSH CA Certificate
-L to list the contents. For example, for a user's certificate:
14.3.8. Revoking an SSH CA Certificate
revoked_keys file and specifying the file name in the sshd_config file as follows: RevokedKeys /etc/ssh/revoked_keys
RevokedKeys /etc/ssh/revoked_keysssh-keygen -Qf /etc/ssh/revoked_keys ~/.ssh/id_rsa.pub
ssh-keygen -Qf /etc/ssh/revoked_keys ~/.ssh/id_rsa.pubcert-authority directive to revoke in the known_hosts file.
14.4. OpenSSH Clients
14.4.1. Using the ssh Utility
ssh utility allows you to log in to a remote machine and execute commands there. It is a secure replacement for the rlogin, rsh, and telnet programs.
telnet command, log in to a remote machine by using the following command:
ssh hostname
ssh hostnamepenguin.example.com, type the following at a shell prompt:
ssh penguin.example.com
~]$ ssh penguin.example.comssh username@hostname
ssh username@hostnamepenguin.example.com as john, type:
ssh john@penguin.example.com
~]$ ssh john@penguin.example.comThe authenticity of host 'penguin.example.com' can't be established. RSA key fingerprint is 94:68:3a:3a:bc:f3:9a:9b:01:5d:b3:07:38:e2:11:0c. Are you sure you want to continue connecting (yes/no)?
The authenticity of host 'penguin.example.com' can't be established.
RSA key fingerprint is 94:68:3a:3a:bc:f3:9a:9b:01:5d:b3:07:38:e2:11:0c.
Are you sure you want to continue connecting (yes/no)?yes to confirm. You will see a notice that the server has been added to the list of known hosts, and a prompt asking for your password:
Warning: Permanently added 'penguin.example.com' (RSA) to the list of known hosts. john@penguin.example.com's password:
Warning: Permanently added 'penguin.example.com' (RSA) to the list of known hosts.
john@penguin.example.com's password:Important
~/.ssh/known_hosts file. Contact the system administrator of the SSH server to verify the server is not compromised, then remove the line with the name of the remote machine at the beginning.
ssh program can be used to execute a command on the remote machine without logging in to a shell prompt:
ssh [username@]hostname command
ssh [username@]hostname command/etc/redhat-release file provides information about the Red Hat Enterprise Linux version. To view the contents of this file on penguin.example.com, type:
~]$ ssh john@penguin.example.com cat /etc/redhat-release john@penguin.example.com's password: Red Hat Enterprise Linux Server release 6.2 (Santiago)
~]$ ssh john@penguin.example.com cat /etc/redhat-release
john@penguin.example.com's password:
Red Hat Enterprise Linux Server release 6.2 (Santiago)14.4.2. Using the scp Utility
scp can be used to transfer files between machines over a secure, encrypted connection. In its design, it is very similar to rcp.
scp localfile username@hostname:remotefile
scp localfile username@hostname:remotefiletaglist.vim to a remote machine named penguin.example.com, type the following at a shell prompt:
scp taglist.vim john@penguin.example.com:.vim/plugin/taglist.vim john@penguin.example.com's password: taglist.vim 100% 144KB 144.5KB/s 00:00
~]$ scp taglist.vim john@penguin.example.com:.vim/plugin/taglist.vim
john@penguin.example.com's password:
taglist.vim 100% 144KB 144.5KB/s 00:00.vim/plugin/ to the same directory on the remote machine penguin.example.com, type the following command:
scp .vim/plugin/* john@penguin.example.com:.vim/plugin/ john@penguin.example.com's password: closetag.vim 100% 13KB 12.6KB/s 00:00 snippetsEmu.vim 100% 33KB 33.1KB/s 00:00 taglist.vim 100% 144KB 144.5KB/s 00:00
~]$ scp .vim/plugin/* john@penguin.example.com:.vim/plugin/
john@penguin.example.com's password:
closetag.vim 100% 13KB 12.6KB/s 00:00
snippetsEmu.vim 100% 33KB 33.1KB/s 00:00
taglist.vim 100% 144KB 144.5KB/s 00:00scp username@hostname:remotefile localfile
scp username@hostname:remotefile localfile.vimrc configuration file from the remote machine, type:
scp john@penguin.example.com:.vimrc .vimrc john@penguin.example.com's password: .vimrc 100% 2233 2.2KB/s 00:00
~]$ scp john@penguin.example.com:.vimrc .vimrc
john@penguin.example.com's password:
.vimrc 100% 2233 2.2KB/s 00:0014.4.3. Using the sftp Utility
sftp utility can be used to open a secure, interactive FTP session. In its design, it is similar to ftp except that it uses a secure, encrypted connection.
sftp username@hostname
sftp username@hostnamepenguin.example.com with john as a user name, type:
sftp john@penguin.example.com john@penguin.example.com's password: Connected to penguin.example.com. sftp>
~]$ sftp john@penguin.example.com
john@penguin.example.com's password:
Connected to penguin.example.com.
sftp>sftp utility accepts a set of commands similar to those used by ftp (see Table 14.3, “A selection of available sftp commands”).
| Command | Description |
|---|---|
ls [directory] | List the content of a remote directory. If none is supplied, a current working directory is used by default. |
cd directory | Change the remote working directory to directory. |
mkdir directory | Create a remote directory. |
rmdir path | Remove a remote directory. |
put localfile [remotefile] | Transfer localfile to a remote machine. |
get remotefile [localfile] | Transfer remotefile from a remote machine. |
sftp(1) manual page.
14.5. More Than a Secure Shell
14.5.1. X11 Forwarding
ssh -Y username@hostname
ssh -Y username@hostnamepenguin.example.com with john as a user name, type:
ssh -Y john@penguin.example.com john@penguin.example.com's password:
~]$ ssh -Y john@penguin.example.com
john@penguin.example.com's password:system-config-printer &
~]$ system-config-printer &14.5.2. Port Forwarding
TCP/IP protocols via port forwarding. When using this technique, the SSH server becomes an encrypted conduit to the SSH client.
Note
root level access.
localhost, use a command in the following form:
ssh -L local-port:remote-hostname:remote-port username@hostname
ssh -L local-port:remote-hostname:remote-port username@hostnamemail.example.com using POP3 through an encrypted connection, use the following command:
ssh -L 1100:mail.example.com:110 mail.example.com
~]$ ssh -L 1100:mail.example.com:110 mail.example.com1100 on the localhost to check for new email. Any requests sent to port 1100 on the client system will be directed securely to the mail.example.com server.
mail.example.com is not running an SSH server, but another machine on the same network is, SSH can still be used to secure part of the connection. However, a slightly different command is necessary:
ssh -L 1100:mail.example.com:110 other.example.com
~]$ ssh -L 1100:mail.example.com:110 other.example.com1100 on the client machine are forwarded through the SSH connection on port 22 to the SSH server, other.example.com. Then, other.example.com connects to port 110 on mail.example.com to check for new email. Note that when using this technique, only the connection between the client system and other.example.com SSH server is secure.
Important
No parameter for the AllowTcpForwarding line in the /etc/ssh/sshd_config file and restarting the sshd service.
14.6. Additional Resources
14.6.1. Installed Documentation
- sshd(8) — a manual page for the
sshddaemon. - ssh(1) — a manual page for the ssh client.
- scp(1) — a manual page for the scp utility.
- sftp(1) — a manual page for the sftp utility.
- ssh-keygen(1) — a manual page for the ssh-keygen utility.
- ssh_config(5) — a manual page with a full description of available SSH client configuration options.
- sshd_config(5) — a manual page with a full description of available SSH daemon configuration options.
/usr/share/doc/openssh-version/Contains detailed information on the protocols supported by OpenSSH.
14.6.2. Useful Websites
- http://www.openssh.com/
- The OpenSSH home page containing further documentation, frequently asked questions, links to the mailing lists, bug reports, and other useful resources.
- http://www.openssl.org/
- The OpenSSL home page containing further documentation, frequently asked questions, links to the mailing lists, and other useful resources.
Chapter 15. TigerVNC
TigerVNC (Tiger Virtual Network Computing) is a system for graphical desktop sharing which allows you to remotely control other computers.
TigerVNC works on the client-server principle: a server shares its output (vncserver) and a client (vncviewer) connects to the server.
15.1. VNC Server
vncserver is a utility which starts a VNC (Virtual Network Computing) desktop. It runs Xvnc with appropriate options and starts a window manager on the VNC desktop. vncserver allows users to run separate sessions in parallel on a machine which can then be accessed by any number of clients from anywhere.
15.1.1. Installing VNC Server
root:
yum install tigervnc-server
~]# yum install tigervnc-server15.1.2. Configuring VNC Server
Procedure 15.1. Configuring a VNC Display for a Single User
- Specify the user name and the display number by editing
/etc/sysconfig/vncserversand adding a line in the following format:The VNC user names must correspond to users of the system.VNCSERVERS="display_number:user"
VNCSERVERS="display_number:user"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example 15.1. Setting the Display Number for a User
For example, to configure display number3for userjoe, open the configuration file for editing:vi /etc/sysconfig/vncservers
~]# vi /etc/sysconfig/vncserversCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a line as follows:Save and close the file.VNCSERVERS="3:joe"
VNCSERVERS="3:joe"Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the example above, display number 3 and the user joe are set. Do not use 0 as the display number since the main X display of a workstation is usually indicated as 0.
Procedure 15.2. Configuring a VNC Display for Multiple Users
- To set a VNC display for more than one user, specify the user names and display numbers by editing
/etc/sysconfig/vncserversand adding a line in the following format:The VNC user names must correspond to users of the system.VNCSERVERS="display_number:user display_number:user"
VNCSERVERS="display_number:user display_number:user"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example 15.2. Setting the Display Numbers for Two Users
For example, to configure two users, open the configuration file for editing:vi /etc/sysconfig/vncservers
~]# vi /etc/sysconfig/vncserversCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a line as follows:VNCSERVERS="3:joe 4:jill"
VNCSERVERS="3:joe 4:jill"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 15.3. Configuring VNC Display Arguments
- Specify additional settings in the
/etc/sysconfig/vncserversfile by adding arguments using the VNCSERVERARGS directive as follows:VNCSERVERS="display_number:user display_number:user" VNCSERVERARGS[display_number]="arguments"
VNCSERVERS="display_number:user display_number:user" VNCSERVERARGS[display_number]="arguments"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Expand Table 15.1. Frequently Used VNC Server Parameters VNCSERVERARGS Definition -geometry specifies the size of the VNC desktop to be created, default is 1024x768. -nolisten tcp prevents connections to your VNC server through TCP (Transmission Control Protocol) -localhost prevents remote VNC clients from connecting except when doing so through a secure tunnel See theXvnc(1)man page for further options.Example 15.3. Setting vncserver Arguments
Following on from the example above, to add arguments for two users, edit the/etc/sysconfig/vncserversfile as follows:VNCSERVERS="3:joe 4:jill" VNCSERVERARGS[1]="-geometry 800x600 -nolisten tcp -localhost" VNCSERVERARGS[2]="-geometry 1920×1080 -nolisten tcp -localhost"
VNCSERVERS="3:joe 4:jill" VNCSERVERARGS[1]="-geometry 800x600 -nolisten tcp -localhost" VNCSERVERARGS[2]="-geometry 1920×1080 -nolisten tcp -localhost"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 15.4. Configuring VNC User Passwords
- To set the VNC password for all users defined in the
/etc/sysconfig/vncserversfile, enter the following command asroot:To set the VNC password individually for a user:vncpasswd Password: Verify:
~]# vncpasswd Password: Verify:Copy to Clipboard Copied! Toggle word wrap Toggle overflow su - user vncpasswd Password: Verify:
~]# su - user ~]$ vncpasswd Password: Verify:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Important
The stored password is not encrypted; anyone who has access to the password file can find the plain-text password.
15.1.3. Starting VNC Server
vncserver utility is used. It is a Perl script which simplifies the process of starting an Xvnc server. It runs Xvnc with appropriate options and starts a window manager on the VNC desktop. There are three ways to start vncserver:
- You can allow
vncserverto choose the first available display number, start Xvnc with that display number, and start the default window manager in the Xvnc session. All these steps are provided by one command:You will be prompted to enter a VNC password the first time the command is run if no VNC password has been set.vncserver
~]$ vncserverCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Alternately, you can specify a specific display number:
vncserver :display_number
vncserver :display_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow vncserverattempts to start Xvnc with that display number and exits if the display number is not available.For example:vncserver :20
~]$ vncserver :20Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Alternately, to start VNC server with displays for the users configured in the
/etc/sysconfig/vncserversconfiguration file, asrootenter:service vncserver start
~]# service vncserver startCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can enable thevncserverservice automatically at system start. Every time you log in,vncserveris automatically started. Asroot, runchkconfig vncserver on
~]# chkconfig vncserver onCopy to Clipboard Copied! Toggle word wrap Toggle overflow
15.1.4. Terminating a VNC Session
vncserver service, you can disable the automatic start of the service at system start:
chkconfig vncserver off
~]# chkconfig vncserver offroot:
service vncserver stop
~]# service vncserver stopvncserver using the -kill option along with the display number.
Example 15.4. Terminating a Specific Display
vncserver -kill :2
~]# vncserver -kill :2Example 15.5. Terminating an Xvnc process
service vncserver status Xvnc (pid 4290 4189) is running...
~]$ service vncserver status
Xvnc (pid 4290 4189) is running...4290, enter as root:
kill -s 15 4290
~]# kill -s 15 429015.2. Sharing an Existing Desktop
0. A user can share their desktop using the TigerVNC server x0vncserver.
Procedure 15.5. Sharing an X Desktop
x0vncserver, proceed as follows:
- Enter the following command as
rootyum install tigervnc-server
~]# yum install tigervnc-serverCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Set the VNC password for the user:
vncpasswd Password: Verify:
~]$ vncpasswd Password: Verify:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter the following command as that user:
x0vncserver -PasswordFile=.vnc/passwd -AlwaysShared=1
~]$ x0vncserver -PasswordFile=.vnc/passwd -AlwaysShared=1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5900, the remote viewer can now connect to display 0, and view the logged in users desktop. See Section 15.3.2.1, “Configuring the Firewall for VNC” for information on how to configure the firewall.
15.3. Using a VNC Viewer
15.3.1. Installing the VNC Viewer
vncviewer, as root, run the following command: yum install tigervnc
~]# yum install tigervncvncviewer. Alternatively, you can operate vncviewer through the command-line interface (CLI). To view a list of parameters for vncviewer enter vncviewer -h on the command line.
15.3.2. Connecting to a VNC Server
Procedure 15.6. Connecting to a VNC Server Using a GUI
- Enter the
vncviewercommand with no arguments, the VNC Viewer: Connection Details utility appears. It prompts for a VNC server to connect to. - If required, to prevent disconnecting any existing VNC connections to the same display, select the option to allow sharing of the desktop as follows:
- Select the button.
- Select the Misc. tab.
- Select the button.
- Press OK to return to the main menu.
- Enter an address and display number to connect to:
address:display_number
address:display_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Press Connect to connect to the VNC server display.
- You will be prompted to enter the VNC password. This will be the VNC password for the user corresponding to the display number unless a global default VNC password was set.A window appears showing the VNC server desktop. Note that this is not the desktop the normal user sees, it is an Xvnc desktop.
Procedure 15.7. Connecting to a VNC Server Using the CLI
- Enter the
viewercommand with the address and display number as arguments:Where address is anvncviewer address:display_number
vncviewer address:display_numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow IPaddress or host name. - Authenticate yourself by entering the VNC password. This will be the VNC password for the user corresponding to the display number unless a global default VNC password was set.
- A window appears showing the VNC server desktop. Note that this is not the desktop the normal user sees, it is the Xvnc desktop.
15.3.2.1. Configuring the Firewall for VNC
TCP packets. If required, open a port for the TCP protocol as described below. When using the -via option, traffic is redirected over SSH which is enabled by default.
Note
Procedure 15.8. Opening a Port Using lokkit
lokkit command provides a way to quickly enable a port using the command line.
- To enable a specific port, for example port
5902forTCP, issue the following command asroot:Note that this will restart the firewall as long as it has not been disabled with thelokkit --port=5902:tcp --update
~]# lokkit --port=5902:tcp --updateCopy to Clipboard Copied! Toggle word wrap Toggle overflow --disabledoption. Active connections will be terminated and time out on the initiating machine. - Verify whether the chosen port is open. As
root, enter:iptables -L -n | grep 'tcp.*59' ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:5902
~]# iptables -L -n | grep 'tcp.*59' ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:5902Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If you are unsure of the port numbers in use for VNC, as
root, enter:Ports startingCopy to Clipboard Copied! Toggle word wrap Toggle overflow 59XXare for the VNCRFBprotocol. Ports starting60XXare for the X windows protocol.To list the ports and the Xvnc session's associated user, asroot, enter:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 15.9. Configuring the Firewall Using an Editor
/etc/sysconfig/system-config-firewall file thoroughly after editing.
- To check what the firewall is configured to allow, issue the following command as
rootto view the firewall configuration file:In this example taken from a default installation, the firewall is enabled but VNC ports have not been configured to pass through.less /etc/sysconfig/system-config-firewall # Configuration file for system-config-firewall --enabled --service=ssh
~]# less /etc/sysconfig/system-config-firewall # Configuration file for system-config-firewall --enabled --service=sshCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Open
/etc/sysconfig/system-config-firewallfor editing asrootand add lines in the following format to the firewall configuration file:For example, to add port--port=port_number:tcp
--port=port_number:tcpCopy to Clipboard Copied! Toggle word wrap Toggle overflow 5902:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Note that these changes will not take effect even if the firewall is reloaded or the system rebooted. To apply the settings in
/etc/sysconfig/system-config-firewall, issue the following command asroot:lokkit --update
~]# lokkit --updateCopy to Clipboard Copied! Toggle word wrap Toggle overflow
15.3.3. Connecting to VNC Server Using SSH
-via option. This will create an SSH tunnel between the VNC server and the client.
vncviewer -via user@host:display_number
vncviewer -via user@host:display_numberExample 15.6. Using the -via Option
- To connect to a VNC server using
SSH, enter a command as follows:vncviewer -via joe@192.168.2.101 127.0.0.1:3
$ vncviewer -via joe@192.168.2.101 127.0.0.1:3Copy to Clipboard Copied! Toggle word wrap Toggle overflow - When you are prompted to, type the password, and confirm by pressing Enter.
- A window with a remote desktop appears on your screen.
SSH, see Chapter 14, OpenSSH.
15.4. Additional Resources
Installed Documentation
vncserver(1)— The manual page for the VNC server utility.vncviewer(1)— The manual page for the VNC viewer.vncpasswd(1)— The manual page for the VNC password command.Xvnc(1)— The manual page for the Xvnc server configuration options.x0vncserver(1)— The manual page for theTigerVNCserver for sharing existing X servers.
Part VI. Servers
Chapter 16. DHCP Servers
16.1. Why Use DHCP?
16.2. Configuring a DHCPv4 Server
yum install dhcp
~]# yum install dhcp/etc/dhcp/dhcpd.conf, which is merely an empty configuration file:
~]# cat /etc/dhcp/dhcpd.conf # # DHCP Server Configuration file. see /usr/share/doc/dhcp*/dhcpd.conf.sample
~]# cat /etc/dhcp/dhcpd.conf
#
# DHCP Server Configuration file.
# see /usr/share/doc/dhcp*/dhcpd.conf.sample/usr/share/doc/dhcp-<version>/dhcpd.conf.sample. You should use this file to help you configure /etc/dhcp/dhcpd.conf, which is explained in detail below.
/var/lib/dhcpd/dhcpd.leases to store the client lease database. See Section 16.2.2, “Lease Database” for more information.
16.2.1. Configuration File
- Parameters — State how to perform a task, whether to perform a task, or what network configuration options to send to the client.
- Declarations — Describe the topology of the network, describe the clients, provide addresses for the clients, or apply a group of parameters to a group of declarations.
Important
service dhcpd restart.
Note
omshell command provides an interactive way to connect to, query, and change the configuration of a DHCP server. By using omshell, all changes can be made while the server is running. For more information on omshell, see the omshell man page.
routers, subnet-mask, domain-search, domain-name-servers, and time-offset options are used for any host statements declared below it.
subnet which will be served, and for every subnet to which the DHCP server is connected, there must be one subnet declaration, which tells the DHCP daemon how to recognize that an address is on that subnet. A subnet declaration is required for each subnet even if no addresses will be dynamically allocated to that subnet.
range declared. Clients are assigned an IP address within the range.
Example 16.1. Subnet Declaration
range 192.168.1.10 and 192.168.1.100 to client systems.
Example 16.2. Range Parameter
hardware ethernet parameter within a host declaration. As demonstrated in Example 16.3, “Static IP Address Using DHCP”, the host apex declaration specifies that the network interface card with the MAC address 00:A0:78:8E:9E:AA always receives the IP address 192.168.1.4.
host-name to assign a host name to the client.
Example 16.3. Static IP Address Using DHCP
shared-network declaration as shown in Example 16.4, “Shared-network Declaration”. Parameters within the shared-network, but outside the enclosed subnet declarations, are considered to be global parameters. The name of the shared-network must be a descriptive title for the network, such as using the title 'test-lab' to describe all the subnets in a test lab environment.
group declaration is used to apply global parameters to a group of declarations. For example, shared networks, subnets, and hosts can be grouped.
Example 16.5. Group Declaration
Note
root:
cp /usr/share/doc/dhcp-<version_number>/dhcpd.conf.sample /etc/dhcp/dhcpd.conf
~]# cp /usr/share/doc/dhcp-<version_number>/dhcpd.conf.sample /etc/dhcp/dhcpd.confdhcp-options man page.
16.2.2. Lease Database
/var/lib/dhcpd/dhcpd.leases stores the DHCP client lease database. Do not change this file. DHCP lease information for each recently assigned IP address is automatically stored in the lease database. The information includes the length of the lease, to whom the IP address has been assigned, the start and end dates for the lease, and the MAC address of the network interface card that was used to retrieve the lease.
dhcpd.leases file is renamed dhcpd.leases~ and the temporary lease database is written to dhcpd.leases.
dhcpd.leases file does not exist, but it is required to start the service. Do not create a new lease file. If you do, all old leases are lost which causes many problems. The correct solution is to rename the dhcpd.leases~ backup file to dhcpd.leases and then start the daemon.
16.2.3. Starting and Stopping the Server
Important
dhcpd.leases file exists. Use the command touch /var/lib/dhcpd/dhcpd.leases to create the file if it does not exist.
named service automatically checks for a dhcpd.leases file.
/sbin/service dhcpd start. To stop the DHCP server, use the command /sbin/service dhcpd stop.
/etc/sysconfig/dhcpd, add the name of the interface to the list of DHCPDARGS:
# Command line options here DHCPDARGS=eth0
# Command line options here
DHCPDARGS=eth0
/etc/sysconfig/dhcpd include:
-p <portnum>— Specifies the UDP port number on whichdhcpdshould listen. The default is port 67. The DHCP server transmits responses to the DHCP clients at a port number one greater than the UDP port specified. For example, if the default port 67 is used, the server listens on port 67 for requests and responds to the client on port 68. If a port is specified here and the DHCP relay agent is used, the same port on which the DHCP relay agent should listen must be specified. See Section 16.2.4, “DHCP Relay Agent” for details.-f— Runs the daemon as a foreground process. This is mostly used for debugging.-d— Logs the DHCP server daemon to the standard error descriptor. This is mostly used for debugging. If this is not specified, the log is written to/var/log/messages.-cf <filename>— Specifies the location of the configuration file. The default location is/etc/dhcp/dhcpd.conf.-lf <filename>— Specifies the location of the lease database file. If a lease database file already exists, it is very important that the same file be used every time the DHCP server is started. It is strongly recommended that this option only be used for debugging purposes on non-production machines. The default location is/var/lib/dhcpd/dhcpd.leases.-q— Do not print the entire copyright message when starting the daemon.
16.2.4. DHCP Relay Agent
dhcrelay) allows for the relay of DHCP and BOOTP requests from a subnet with no DHCP server on it to one or more DHCP servers on other subnets.
/etc/sysconfig/dhcrelay with the INTERFACES directive.
service dhcrelay start.
16.3. Configuring a DHCPv4 Client
/etc/sysconfig/network file to enable networking and the configuration file for each network device in the /etc/sysconfig/network-scripts directory. In this directory, each device should have a configuration file named ifcfg-eth0, where eth0 is the network device name.
/etc/sysconfig/network-scripts/ifcfg-eth0 file contains the following lines:
DEVICE=eth0 BOOTPROTO=dhcp ONBOOT=yes
DEVICE=eth0
BOOTPROTO=dhcp
ONBOOT=yes
DHCP_HOSTNAME— Only use this option if the DHCP server requires the client to specify a host name before receiving an IP address.PEERDNS=<answer>, where<answer>is one of the following:yes— Modify/etc/resolv.confwith information from the server. This is the default.no— Do not modify/etc/resolv.conf.
Note
dhclient and dhclient.conf man pages.
16.4. Configuring a Multihomed DHCP Server
/etc/sysconfig/dhcpd and /etc/dhcp/dhcpd.conf files.
/etc/sysconfig/dhcpd file to specify which network interfaces the DHCP daemon listens on. The following /etc/sysconfig/dhcpd example specifies that the DHCP daemon listens on the eth0 and eth1 interfaces:
DHCPDARGS="eth0 eth1";
DHCPDARGS="eth0 eth1";
eth0, eth1, and eth2 — and it is only desired that the DHCP daemon listens on the eth0 card, then only specify eth0 in /etc/sysconfig/dhcpd:
DHCPDARGS="eth0";
DHCPDARGS="eth0";
/etc/dhcp/dhcpd.conf file, for a server that has two network interfaces, eth0 in a 10.0.0.0/24 network, and eth1 in a 172.16.0.0/24 network. Multiple subnet declarations allow you to define different settings for multiple networks:
-
subnet 10.0.0.0 netmask 255.255.255.0; - A
subnetdeclaration is required for every network your DHCP server is serving. Multiple subnets require multiplesubnetdeclarations. If the DHCP server does not have a network interface in a range of asubnetdeclaration, the DHCP server does not serve that network.If there is only onesubnetdeclaration, and no network interfaces are in the range of that subnet, the DHCP daemon fails to start, and an error such as the following is logged to/var/log/messages:Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
option subnet-mask 255.255.255.0; - The
option subnet-maskoption defines a subnet mask, and overrides thenetmaskvalue in thesubnetdeclaration. In simple cases, the subnet and netmask values are the same. -
option routers 10.0.0.1; - The
option routersoption defines the default gateway for the subnet. This is required for systems to reach internal networks on a different subnet, as well as external networks. -
range 10.0.0.5 10.0.0.15; - The
rangeoption specifies the pool of available IP addresses. Systems are assigned an address from the range of specified IP addresses.
dhcpd.conf(5) man page.
16.4.1. Host Configuration
/etc/sysconfig/dhcpd and /etc/dhcp/dhcpd.conf files.
The following /etc/dhcp/dhcpd.conf example creates two subnets, and configures an IP address for the same system, depending on which network it connects to:
-
host example0 - The
hostdeclaration defines specific parameters for a single system, such as an IP address. To configure specific parameters for multiple hosts, use multiplehostdeclarations.Most DHCP clients ignore the name inhostdeclarations, and as such, this name can be anything, as long as it is unique to otherhostdeclarations. To configure the same system for multiple networks, use a different name for eachhostdeclaration, otherwise the DHCP daemon fails to start. Systems are identified by thehardware ethernetoption, not the name in thehostdeclaration. -
hardware ethernet 00:1A:6B:6A:2E:0B; - The
hardware ethernetoption identifies the system. To find this address, run theip linkcommand. -
fixed-address 10.0.0.20; - The
fixed-addressoption assigns a valid IP address to the system specified by thehardware ethernetoption. This address must be outside the IP address pool specified with therangeoption.
option statements do not end with a semicolon, the DHCP daemon fails to start, and an error such as the following is logged to /var/log/messages:
The following host declarations configure a single system, which has multiple network interfaces, so that each interface receives the same IP address. This configuration will not work if both network interfaces are connected to the same network at the same time:
interface0 is the first network interface, and interface1 is the second interface. The different hardware ethernet options identify each interface.
host declarations, remembering to:
- assign a valid
fixed-addressfor the network the host is connecting to. - make the name in the
hostdeclaration unique.
host declaration is not unique, the DHCP daemon fails to start, and an error such as the following is logged to /var/log/messages:
dhcpd: /etc/dhcp/dhcpd.conf line 31: host interface0: already exists dhcpd: } dhcpd: ^ dhcpd: Configuration file errors encountered -- exiting
dhcpd: /etc/dhcp/dhcpd.conf line 31: host interface0: already exists
dhcpd: }
dhcpd: ^
dhcpd: Configuration file errors encountered -- exiting
host interface0 declarations defined in /etc/dhcp/dhcpd.conf.
16.5. DHCP for IPv6 (DHCPv6)
16.5.1. Configuring a DHCPv6 Server
/etc/dhcp/dhcpd6.conf.
/usr/share/doc/dhcp-<version>/dhcpd6.conf.sample, in Red Hat Enterprise Linux 6 at /usr/share/doc/dhcp-4.1.1/dhcpd6.conf.sample.
subnet6 2001:db8:0:1::/64 {
range6 2001:db8:0:1::129 2001:db8:0:1::254;
option dhcp6.name-servers fec0:0:0:1::1;
option dhcp6.domain-search "domain.example";
}
subnet6 2001:db8:0:1::/64 {
range6 2001:db8:0:1::129 2001:db8:0:1::254;
option dhcp6.name-servers fec0:0:0:1::1;
option dhcp6.domain-search "domain.example";
}dhcpd.conf(5) man page.
service dhcpd6 start as root. To stop the DHCPv6 server, use the command service dhcpdv6 stop.
dhcpd daemon when the DHCPv6 service starts, use the /etc/sysconfig/dhcpd6 file. This file uses the same structure like the /etc/sysconfig/dhcpd:
cat /etc/sysconfig/dhcpd6 # Command line options here DHCPDARGS=
# cat /etc/sysconfig/dhcpd6
# Command line options here
DHCPDARGS=DHCPDARGS option is passed to the DHCPv6 service, which passes it to the dhcpd daemon. For more information, see the STANDARD DHCPV6 OPTIONS section in the dhcpd-options(5) man page. For additional examples, see the Dynamic IPv6 configuration on the Fedora Project wiki.
16.5.2. Configuring a DHCPv6 Client
/etc/dhcp/dhclient.conf file. See the /usr/share/doc/dhclient-4.1.1/dhclient6.conf.sample for a client configuration file example.
dhclient.conf(5) man page and the STANDARD DHCPV6 OPTIONS section in the dhcpd-options(5) man page.
Important
16.6. Additional Resources
16.6.1. Installed Documentation
dhcpdman page — Describes how the DHCP daemon works.dhcpd.confman page — Explains how to configure the DHCP configuration file; includes some examples.dhcpd.leasesman page — Describes a persistent database of leases.dhcp-optionsman page — Explains the syntax for declaring DHCP options indhcpd.conf; includes some examples.dhcrelayman page — Explains the DHCP Relay Agent and its configuration options./usr/share/doc/dhcp-<version>/— Contains sample files, README files, and release notes for current versions of the DHCP service.
Chapter 17. DNS Servers
DNS (Domain Name System), also known as a nameserver, is a network system that associates host names with their respective IP addresses. For users, this has the advantage that they can refer to machines on the network by names that are usually easier to remember than the numerical network addresses. For system administrators, using the nameserver allows them to change the IP address for a host without ever affecting the name-based queries, or to decide which machines handle these queries.
17.1. Introduction to DNS
17.1.1. Nameserver Zones
Example 17.1. A simple resource record
bob.sales.example.com
bob.sales.example.com.). In Example 17.1, “A simple resource record”, com defines the top-level domain, example its subdomain, and sales the subdomain of example. In this case, bob identifies a resource record that is part of the sales.example.com domain. With the exception of the part furthest to the left (that is, bob), each of these sections is called a zone and defines a specific namespace.
17.1.2. Nameserver Types
- authoritative
- Authoritative nameservers answer to resource records that are part of their zones only. This category includes both primary (master) and secondary (slave) nameservers.
- recursive
- Recursive nameservers offer resolution services, but they are not authoritative for any zone. Answers for all resolutions are cached in a memory for a fixed period of time, which is specified by the retrieved resource record.
17.1.3. BIND as a Nameserver
named, an administration utility called rndc, and a debugging tool called dig. See Chapter 12, Services and Daemons for more information on how to run a service in Red Hat Enterprise Linux.
17.2. BIND
BIND (Berkeley Internet Name Domain), the DNS server included in Red Hat Enterprise Linux. It focuses on the structure of its configuration files, and describes how to administer it both locally and remotely.
17.2.1. Configuring the named Service
named service is started, it reads the configuration from the files as described in Table 17.1, “The named service configuration files”.
| Path | Description |
|---|---|
/etc/named.conf | The main configuration file. |
/etc/named/ | An auxiliary directory for configuration files that are included in the main configuration file. |
named service will not start. A typical /etc/named.conf file is organized as follows:
Note
/var/named/chroot environment. In that case, the initialization script will mount the above configuration files using the mount --bind command, so that you can manage the configuration outside this environment. There is no need to copy anything into the /var/named/chroot directory because it is mounted automatically. This simplifies maintenance since you do not need to take any special care of BIND configuration files if it is run in a chroot environment. You can organize everything as you would with BIND not running in a chroot environment.
/var/named/chroot if they are empty in the /var/named/chroot directory. They must be kept empty if you want them to be mounted into /var/named/chroot:
/var/named/etc/pki/dnssec-keys/etc/named/usr/lib64/bindor/usr/lib/bind(architecture dependent).
/var/named/chroot.
/etc/named.conf/etc/rndc.conf/etc/rndc.key/etc/named.rfc1912.zones/etc/named.dnssec.keys/etc/named.iscdlv.key/etc/named.root.key
17.2.1.1. Common Statement Types
/etc/named.conf:
-
acl - The
acl(Access Control List) statement allows you to define groups of hosts, so that they can be permitted or denied access to the nameserver. It takes the following form:acl acl-name { match-element; ... };acl acl-name { match-element; ... };Copy to Clipboard Copied! Toggle word wrap Toggle overflow The acl-name statement name is the name of the access control list, and the match-element option is usually an individual IP address (such as10.0.1.1) or a CIDR (Classless Inter-Domain Routing) network notation (for example,10.0.1.0/24). For a list of already defined keywords, see Table 17.2, “Predefined access control lists”.Expand Table 17.2. Predefined access control lists Keyword Description anyMatches every IP address. localhostMatches any IP address that is in use by the local system. localnetsMatches any IP address on any network to which the local system is connected. noneDoes not match any IP address. Theaclstatement can be especially useful in conjunction with other statements such asoptions. Example 17.2, “Using acl in conjunction with options” defines two access control lists,black-hatsandred-hats, and addsblack-hatson the blacklist while grantingred-hatsa normal access.Example 17.2. Using acl in conjunction with options
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
include - The
includestatement allows you to include files in the/etc/named.conf, so that potentially sensitive data can be placed in a separate file with restricted permissions. It takes the following form:include "file-name"
include "file-name"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The file-name statement name is an absolute path to a file.Example 17.3. Including a file to /etc/named.conf
include "/etc/named.rfc1912.zones";
include "/etc/named.rfc1912.zones";Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
options - The
optionsstatement allows you to define global server configuration options as well as to set defaults for other statements. It can be used to specify the location of thenamedworking directory, the types of queries allowed, and much more. It takes the following form:options { option; ... };options { option; ... };Copy to Clipboard Copied! Toggle word wrap Toggle overflow For a list of frequently used option directives, see Table 17.3, “Commonly used options” below.Expand Table 17.3. Commonly used options Option Description allow-querySpecifies which hosts are allowed to query the nameserver for authoritative resource records. It accepts an access control list, a collection of IP addresses, or networks in the CIDR notation. All hosts are allowed by default. allow-query-cacheSpecifies which hosts are allowed to query the nameserver for non-authoritative data such as recursive queries. Only localhostandlocalnetsare allowed by default.blackholeSpecifies which hosts are not allowed to query the nameserver. This option should be used when particular host or network floods the server with requests. The default option is none.directorySpecifies a working directory for the namedservice. The default option is/var/named/.dnssec-enableSpecifies whether to return DNSSEC related resource records. The default option is yes.dnssec-validationSpecifies whether to prove that resource records are authentic via DNSSEC. The default option is yes.forwardersSpecifies a list of valid IP addresses for nameservers to which the requests should be forwarded for resolution. forwardSpecifies the behavior of theforwardersdirective. It accepts the following options:first— The server will query the nameservers listed in theforwardersdirective before attempting to resolve the name on its own.only— When unable to query the nameservers listed in theforwardersdirective, the server will not attempt to resolve the name on its own.
listen-onSpecifies the IPv4 network interface on which to listen for queries. On a DNS server that also acts as a gateway, you can use this option to answer queries originating from a single network only. All IPv4 interfaces are used by default. listen-on-v6Specifies the IPv6 network interface on which to listen for queries. On a DNS server that also acts as a gateway, you can use this option to answer queries originating from a single network only. All IPv6 interfaces are used by default. max-cache-sizeSpecifies the maximum amount of memory to be used for server caches. When the limit is reached, the server causes records to expire prematurely so that the limit is not exceeded. In a server with multiple views, the limit applies separately to the cache of each view. The default option is 32M.notifySpecifies whether to notify the secondary nameservers when a zone is updated. It accepts the following options:yes— The server will notify all secondary nameservers.no— The server will not notify any secondary nameserver.master-only— The server will notify primary server for the zone only.explicit— The server will notify only the secondary servers that are specified in thealso-notifylist within a zone statement.
pid-fileSpecifies the location of the process ID file created by the namedservice.recursionSpecifies whether to act as a recursive server. The default option is yes.statistics-fileSpecifies an alternate location for statistics files. The /var/named/named.statsfile is used by default.Important
To prevent distributed denial of service (DDoS) attacks, it is recommended that you use theallow-query-cacheoption to restrict recursive DNS services for a particular subset of clients only.See the BIND 9 Administrator Reference Manual referenced in Section 17.2.7.1, “Installed Documentation”, and thenamed.confmanual page for a complete list of available options.Example 17.4. Using the options statement
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
zone - The
zonestatement allows you to define the characteristics of a zone, such as the location of its configuration file and zone-specific options, and can be used to override the globaloptionsstatements. It takes the following form:zone zone-name [zone-class] { option; ... };zone zone-name [zone-class] { option; ... };Copy to Clipboard Copied! Toggle word wrap Toggle overflow The zone-name attribute is the name of the zone, zone-class is the optional class of the zone, and option is azonestatement option as described in Table 17.4, “Commonly used options”.The zone-name attribute is particularly important, as it is the default value assigned for the$ORIGINdirective used within the corresponding zone file located in the/var/named/directory. Thenameddaemon appends the name of the zone to any non-fully qualified domain name listed in the zone file. For example, if azonestatement defines the namespace forexample.com, useexample.comas the zone-name so that it is placed at the end of host names within theexample.comzone file.For more information about zone files, see Section 17.2.2, “Editing Zone Files”.Expand Table 17.4. Commonly used options Option Description allow-querySpecifies which clients are allowed to request information about this zone. This option overrides global allow-queryoption. All query requests are allowed by default.allow-transferSpecifies which secondary servers are allowed to request a transfer of the zone's information. All transfer requests are allowed by default. allow-updateSpecifies which hosts are allowed to dynamically update information in their zone. The default option is to deny all dynamic update requests.Note that you should be careful when allowing hosts to update information about their zone. Do not set IP addresses in this option unless the server is in the trusted network. Instead, use TSIG key as described in Section 17.2.5.3, “Transaction SIGnatures (TSIG)”.fileSpecifies the name of the file in the namedworking directory that contains the zone's configuration data.mastersSpecifies from which IP addresses to request authoritative zone information. This option is used only if the zone is defined as typeslave.notifySpecifies whether to notify the secondary nameservers when a zone is updated. It accepts the following options:yes— The server will notify all secondary nameservers.no— The server will not notify any secondary nameserver.master-only— The server will notify primary server for the zone only.explicit— The server will notify only the secondary servers that are specified in thealso-notifylist within a zone statement.
typeSpecifies the zone type. It accepts the following options:delegation-only— Enforces the delegation status of infrastructure zones such as COM, NET, or ORG. Any answer that is received without an explicit or implicit delegation is treated asNXDOMAIN. This option is only applicable in TLDs (Top-Level Domain) or root zone files used in recursive or caching implementations.forward— Forwards all requests for information about this zone to other nameservers.hint— A special type of zone used to point to the root nameservers which resolve queries when a zone is not otherwise known. No configuration beyond the default is necessary with ahintzone.master— Designates the nameserver as authoritative for this zone. A zone should be set as themasterif the zone's configuration files reside on the system.slave— Designates the nameserver as a slave server for this zone. Master server is specified inmastersdirective.
Most changes to the/etc/named.conffile of a primary or secondary nameserver involve adding, modifying, or deletingzonestatements, and only a small subset ofzonestatement options is usually needed for a nameserver to work efficiently.In Example 17.5, “A zone statement for a primary nameserver”, the zone is identified asexample.com, the type is set tomaster, and thenamedservice is instructed to read the/var/named/example.com.zonefile. It also allows only a secondary nameserver (192.168.0.2) to transfer the zone.Example 17.5. A zone statement for a primary nameserver
zone "example.com" IN { type master; file "example.com.zone"; allow-transfer { 192.168.0.2; }; };zone "example.com" IN { type master; file "example.com.zone"; allow-transfer { 192.168.0.2; }; };Copy to Clipboard Copied! Toggle word wrap Toggle overflow A secondary server'szonestatement is slightly different. The type is set toslave, and themastersdirective is tellingnamedthe IP address of the master server.In Example 17.6, “A zone statement for a secondary nameserver”, thenamedservice is configured to query the primary server at the192.168.0.1IP address for information about theexample.comzone. The received information is then saved to the/var/named/slaves/example.com.zonefile. Note that you have to put all slave zones to/var/named/slavesdirectory, otherwise the service will fail to transfer the zone.Example 17.6. A zone statement for a secondary nameserver
zone "example.com" { type slave; file "slaves/example.com.zone"; masters { 192.168.0.1; }; };zone "example.com" { type slave; file "slaves/example.com.zone"; masters { 192.168.0.1; }; };Copy to Clipboard Copied! Toggle word wrap Toggle overflow
17.2.1.2. Other Statement Types
/etc/named.conf:
-
controls - The
controlsstatement allows you to configure various security requirements necessary to use therndccommand to administer thenamedservice.See Section 17.2.3, “Using the rndc Utility” for more information on therndcutility and its usage. -
key - The
keystatement allows you to define a particular key by name. Keys are used to authenticate various actions, such as secure updates or the use of therndccommand. Two options are used withkey:algorithm algorithm-name— The type of algorithm to be used (for example,hmac-md5).secret "key-value"— The encrypted key.
See Section 17.2.3, “Using the rndc Utility” for more information on therndcutility and its usage. -
logging - The
loggingstatement allows you to use multiple types of logs, so called channels. By using thechanneloption within the statement, you can construct a customized type of log with its own file name (file), size limit (size), versioning (version), and level of importance (severity). Once a customized channel is defined, acategoryoption is used to categorize the channel and begin logging when thenamedservice is restarted.By default,namedsends standard messages to thersyslogdaemon, which places them in/var/log/messages. Several standard channels are built into BIND with various severity levels, such asdefault_syslog(which handles informational logging messages) anddefault_debug(which specifically handles debugging messages). A default category, calleddefault, uses the built-in channels to do normal logging without any special configuration.Customizing the logging process can be a very detailed process and is beyond the scope of this chapter. For information on creating custom BIND logs, see the BIND 9 Administrator Reference Manual referenced in Section 17.2.7.1, “Installed Documentation”. -
server - The
serverstatement allows you to specify options that affect how thenamedservice should respond to remote nameservers, especially with regard to notifications and zone transfers.Thetransfer-formatoption controls the number of resource records that are sent with each message. It can be eitherone-answer(only one resource record), ormany-answers(multiple resource records). Note that while themany-answersoption is more efficient, it is not supported by older versions of BIND. -
trusted-keys - The
trusted-keysstatement allows you to specify assorted public keys used for secure DNS (DNSSEC). See Section 17.2.5.4, “DNS Security Extensions (DNSSEC)” for more information on this topic. -
view - The
viewstatement allows you to create special views depending upon which network the host querying the nameserver is on. This allows some hosts to receive one answer regarding a zone while other hosts receive totally different information. Alternatively, certain zones may only be made available to particular trusted hosts while non-trusted hosts can only make queries for other zones.Multiple views can be used as long as their names are unique. Thematch-clientsoption allows you to specify the IP addresses that apply to a particular view. If theoptionsstatement is used within a view, it overrides the already configured global options. Finally, mostviewstatements contain multiplezonestatements that apply to thematch-clientslist.Note that the order in which theviewstatements are listed is important, as the first statement that matches a particular client's IP address is used. For more information on this topic, see Section 17.2.5.1, “Multiple Views”.
17.2.1.3. Comment Tags
/etc/named.conf file can also contain comments. Comments are ignored by the named service, but can prove useful when providing additional information to a user. The following are valid comment tags:
-
// - Any text after the
//characters to the end of the line is considered a comment. For example:notify yes; // notify all secondary nameservers
notify yes; // notify all secondary nameserversCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
# - Any text after the
#character to the end of the line is considered a comment. For example:notify yes; # notify all secondary nameservers
notify yes; # notify all secondary nameserversCopy to Clipboard Copied! Toggle word wrap Toggle overflow /*and*/- Any block of text enclosed in
/*and*/is considered a comment. For example:notify yes; /* notify all secondary nameservers */
notify yes; /* notify all secondary nameservers */Copy to Clipboard Copied! Toggle word wrap Toggle overflow
17.2.2. Editing Zone Files
named working directory located in /var/named/ by default, and each zone file is named according to the file option in the zone statement, usually in a way that relates to the domain in question and identifies the file as containing zone data, such as example.com.zone.
| Path | Description |
|---|---|
/var/named/ | The working directory for the named service. The nameserver is not allowed to write to this directory. |
/var/named/slaves/ | The directory for secondary zones. This directory is writable by the named service. |
/var/named/dynamic/ | The directory for other files, such as dynamic DNS (DDNS) zones or managed DNSSEC keys. This directory is writable by the named service. |
/var/named/data/ | The directory for various statistics and debugging files. This directory is writable by the named service. |
17.2.2.1. Common Directives
-
$INCLUDE - The
$INCLUDEdirective allows you to include another file at the place where it appears, so that other zone settings can be stored in a separate zone file.Example 17.7. Using the $INCLUDE directive
$INCLUDE /var/named/penguin.example.com
$INCLUDE /var/named/penguin.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
$ORIGIN - The
$ORIGINdirective allows you to append the domain name to unqualified records, such as those with the host name only. Note that the use of this directive is not necessary if the zone is specified in/etc/named.conf, since the zone name is used by default.In Example 17.8, “Using the $ORIGIN directive”, any names used in resource records that do not end in a trailing period are appended withexample.com.Example 17.8. Using the $ORIGIN directive
$ORIGIN example.com.
$ORIGIN example.com.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
$TTL - The
$TTLdirective allows you to set the default Time to Live (TTL) value for the zone, that is, how long is a zone record valid. Each resource record can contain its own TTL value, which overrides this directive.Increasing this value allows remote nameservers to cache the zone information for a longer period of time, reducing the number of queries for the zone and lengthening the amount of time required to propagate resource record changes.Example 17.9. Using the $TTL directive
$TTL 1D
$TTL 1DCopy to Clipboard Copied! Toggle word wrap Toggle overflow
17.2.2.2. Common Resource Records
-
A - The Address record specifies an IP address to be assigned to a name. It takes the following form:
hostname IN A IP-address
hostname IN A IP-addressCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the hostname value is omitted, the record will point to the last specified hostname.In Example 17.10, “Using the A resource record”, the requests forserver1.example.comare pointed to10.0.1.3or10.0.1.5.Example 17.10. Using the A resource record
server1 IN A 10.0.1.3 IN A 10.0.1.5server1 IN A 10.0.1.3 IN A 10.0.1.5Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
CNAME - The Canonical Name record maps one name to another. Because of this, this type of record is sometimes referred to as an alias record. It takes the following form:
alias-name IN CNAME real-name
alias-name IN CNAME real-nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow CNAMErecords are most commonly used to point to services that use a common naming scheme, such aswwwfor Web servers. However, there are multiple restrictions for their usage:- CNAME records should not point to other CNAME records. This is mainly to avoid possible infinite loops.
- CNAME records should not contain other resource record types (such as A, NS, MX, etc.). The only exception are DNSSEC related records (that is, RRSIG, NSEC, etc.) when the zone is signed.
- Other resource record that point to the fully qualified domain name (FQDN) of a host (that is, NS, MX, PTR) should not point to a CNAME record.
In Example 17.11, “Using the CNAME resource record”, theArecord binds a host name to an IP address, while theCNAMErecord points the commonly usedwwwhost name to it.Example 17.11. Using the CNAME resource record
server1 IN A 10.0.1.5 www IN CNAME server1
server1 IN A 10.0.1.5 www IN CNAME server1Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MX - The Mail Exchange record specifies where the mail sent to a particular namespace controlled by this zone should go. It takes the following form:
IN MX preference-value email-server-name
IN MX preference-value email-server-nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow The email-server-name is a fully qualified domain name (FQDN). The preference-value allows numerical ranking of the email servers for a namespace, giving preference to some email systems over others. TheMXresource record with the lowest preference-value is preferred over the others. However, multiple email servers can possess the same value to distribute email traffic evenly among them.In Example 17.12, “Using the MX resource record”, the firstmail.example.comemail server is preferred to themail2.example.comemail server when receiving email destined for theexample.comdomain.Example 17.12. Using the MX resource record
example.com. IN MX 10 mail.example.com. IN MX 20 mail2.example.com.example.com. IN MX 10 mail.example.com. IN MX 20 mail2.example.com.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
NS - The Nameserver record announces authoritative nameservers for a particular zone. It takes the following form:
IN NS nameserver-name
IN NS nameserver-nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow The nameserver-name should be a fully qualified domain name (FQDN). Note that when two nameservers are listed as authoritative for the domain, it is not important whether these nameservers are secondary nameservers, or if one of them is a primary server. They are both still considered authoritative.Example 17.13. Using the NS resource record
IN NS dns1.example.com. IN NS dns2.example.com.
IN NS dns1.example.com. IN NS dns2.example.com.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
PTR - The Pointer record points to another part of the namespace. It takes the following form:
last-IP-digit IN PTR FQDN-of-system
last-IP-digit IN PTR FQDN-of-systemCopy to Clipboard Copied! Toggle word wrap Toggle overflow The last-IP-digit directive is the last number in an IP address, and the FQDN-of-system is a fully qualified domain name (FQDN).PTRrecords are primarily used for reverse name resolution, as they point IP addresses back to a particular name. See Section 17.2.2.4.2, “A Reverse Name Resolution Zone File” for more examples ofPTRrecords in use. -
SOA - The Start of Authority record announces important authoritative information about a namespace to the nameserver. Located after the directives, it is the first resource record in a zone file. It takes the following form:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The directives are as follows:- The
@symbol places the$ORIGINdirective (or the zone's name if the$ORIGINdirective is not set) as the namespace being defined by thisSOAresource record. - The primary-name-server directive is the host name of the primary nameserver that is authoritative for this domain.
- The hostmaster-email directive is the email of the person to contact about the namespace.
- The serial-number directive is a numerical value incremented every time the zone file is altered to indicate it is time for the
namedservice to reload the zone. - The time-to-refresh directive is the numerical value secondary nameservers use to determine how long to wait before asking the primary nameserver if any changes have been made to the zone.
- The time-to-retry directive is a numerical value used by secondary nameservers to determine the length of time to wait before issuing a refresh request in the event that the primary nameserver is not answering. If the primary server has not replied to a refresh request before the amount of time specified in the time-to-expire directive elapses, the secondary servers stop responding as an authority for requests concerning that namespace.
- In BIND 4 and 8, the minimum-TTL directive is the amount of time other nameservers cache the zone's information. In BIND 9, it defines how long negative answers are cached for. Caching of negative answers can be set to a maximum of 3 hours (that is,
3H).
When configuring BIND, all times are specified in seconds. However, it is possible to use abbreviations when specifying units of time other than seconds, such as minutes (M), hours (H), days (D), and weeks (W). Table 17.6, “Seconds compared to other time units” shows an amount of time in seconds and the equivalent time in another format.Expand Table 17.6. Seconds compared to other time units Seconds Other Time Units 60 1M1800 30M3600 1H10800 3H21600 6H43200 12H86400 1D259200 3D604800 1W31536000 365DExample 17.14. Using the SOA resource record
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
17.2.2.3. Comment Tags
named service, but can prove useful when providing additional information to the user. Any text after the semicolon character to the end of the line is considered a comment. For example:
604800 ; expire after 1 week
604800 ; expire after 1 week17.2.2.4. Example Usage
17.2.2.4.1. A Simple Zone File
SOA values.
Example 17.15. A simple zone file
dns1.example.com and dns2.example.com, and are tied to the 10.0.1.1 and 10.0.1.2 IP addresses respectively using the A record.
MX records point to mail and mail2 via A records. Since these names do not end in a trailing period, the $ORIGIN domain is placed after them, expanding them to mail.example.com and mail2.example.com.
www.example.com (WWW), are pointed at the appropriate servers using the CNAME record.
zone statement in the /etc/named.conf similar to the following:
zone "example.com" IN {
type master;
file "example.com.zone";
allow-update { none; };
};
zone "example.com" IN {
type master;
file "example.com.zone";
allow-update { none; };
};17.2.2.4.2. A Reverse Name Resolution Zone File
PTR resource records are used to link the IP addresses to a fully qualified domain name as shown in Example 17.16, “A reverse name resolution zone file”.
Example 17.16. A reverse name resolution zone file
10.0.1.1 through 10.0.1.6 are pointed to the corresponding fully qualified domain name.
zone statement in the /etc/named.conf file similar to the following:
zone "1.0.10.in-addr.arpa" IN {
type master;
file "example.com.rr.zone";
allow-update { none; };
};
zone "1.0.10.in-addr.arpa" IN {
type master;
file "example.com.rr.zone";
allow-update { none; };
};zone statement, except for the zone name. Note that a reverse name resolution zone requires the first three blocks of the IP address reversed followed by .in-addr.arpa. This allows the single block of IP numbers used in the reverse name resolution zone file to be associated with the zone.
17.2.3. Using the rndc Utility
rndc utility is a command-line tool that allows you to administer the named service, both locally and from a remote machine. Its usage is as follows:
rndc [option...] command [command-option]
rndc [option...] command [command-option]17.2.3.1. Configuring the Utility
named must be configured to listen on the selected port (that is, 953 by default), and an identical key must be used by both the service and the rndc utility.
rndc configuration is located in /etc/rndc.conf. If the file does not exist, the utility will use the key located in /etc/rndc.key, which was generated automatically during the installation process using the rndc-confgen -a command.
named service is configured using the controls statement in the /etc/named.conf configuration file as described in Section 17.2.1.2, “Other Statement Types”. Unless this statement is present, only the connections from the loopback address (that is, 127.0.0.1) will be allowed, and the key located in /etc/rndc.key will be used.
Important
/etc/rndc.key file:
chmod o-rwx /etc/rndc.key
~]# chmod o-rwx /etc/rndc.key17.2.3.2. Checking the Service Status
named service, use the following command:
17.2.3.3. Reloading the Configuration and Zones
rndc reload server reload successful
~]# rndc reload
server reload successfulreload command, for example:
rndc reload localhost zone reload up-to-date
~]# rndc reload localhost
zone reload up-to-daterndc reconfig
~]# rndc reconfigNote
freeze command first:
rndc freeze localhost
~]# rndc freeze localhostthaw command to allow the DDNS again and reload the zone:
rndc thaw localhost The zone reload and thaw was successful.
~]# rndc thaw localhost
The zone reload and thaw was successful.17.2.3.4. Updating Zone Keys
sign command. For example:
rndc sign localhost
~]# rndc sign localhostauto-dnssec option has to be set to maintain in the zone statement. For instance:
17.2.3.5. Enabling the DNSSEC Validation
rndc validation on
~]# rndc validation onrndc validation off
~]# rndc validation offoptions statement described in Section 17.2.1.1, “Common Statement Types” for information on how to configure this option in /etc/named.conf.
17.2.3.6. Enabling the Query Logging
rndc querylog
~]# rndc querylogstatus command as described in Section 17.2.3.2, “Checking the Service Status”.
17.2.4. Using the dig Utility
dig utility is a command-line tool that allows you to perform DNS lookups and debug a nameserver configuration. Its typical usage is as follows:
dig [@server] [option...] name type
dig [@server] [option...] name type17.2.4.1. Looking Up a Nameserver
dig name NS
dig name NSdig utility is used to display nameservers for example.com.
Example 17.17. A sample nameserver lookup
17.2.4.2. Looking Up an IP Address
dig name A
dig name Adig utility is used to display the IP address of example.com.
Example 17.18. A sample IP address lookup
17.2.4.3. Looking Up a Hostname
dig -x address
dig -x addressdig utility is used to display the host name assigned to 192.0.32.10.
Example 17.19. A sample host name lookup
17.2.5. Advanced Features of BIND
named service to provide name resolution services or to act as an authority for a particular domain. However, BIND version 9 has a number of advanced features that allow for a more secure and efficient DNS service.
Important
17.2.5.1. Multiple Views
view statement to the /etc/named.conf configuration file. Use the match-clients option to match IP addresses or entire networks and give them special options and zone data.
17.2.5.2. Incremental Zone Transfers (IXFR)
17.2.5.3. Transaction SIGnatures (TSIG)
Important
17.2.5.4. DNS Security Extensions (DNSSEC)
SERFVAIL response is returned for each resource record that fails the validation.
dig utility as described in Section 17.2.4, “Using the dig Utility”. Useful options are +dnssec (requests DNSSEC-related resource records by setting the DNSSEC OK bit), +cd (tells recursive nameserver not to validate the response), and +bufsize=512 (changes the packet size to 512B to get through some firewalls).
17.2.5.5. Internet Protocol version 6 (IPv6)
AAAA resource records, and the listen-on-v6 directive as described in Table 17.3, “Commonly used options”.
17.2.6. Common Mistakes to Avoid
- Use semicolons and curly brackets correctly
- An omitted semicolon or unmatched curly bracket in the
/etc/named.conffile can prevent thenamedservice from starting. - Use period correctly
- In zone files, a period at the end of a domain name denotes a fully qualified domain name. If omitted, the
namedservice will append the name of the zone or the value of$ORIGINto complete it. - Increment the serial number when editing a zone file
- If the serial number is not incremented, the primary nameserver will have the correct, new information, but the secondary nameservers will never be notified of the change, and will not attempt to refresh their data of that zone.
- Configure the firewall
- If a firewall is blocking connections from the
namedservice to other nameservers, the recommended practice is to change the firewall settings.Warning
According to the recent research in DNS security, using a fixed UDP source port for DNS queries is a potential security vulnerability that could allow an attacker to conduct cache-poisoning attacks more easily. To prevent this, configure your firewall to allow queries from a random UDP source port.
17.2.7. Additional Resources
17.2.7.1. Installed Documentation
-
/usr/share/doc/bind-version/ - The main directory containing the most recent documentation.
-
/usr/share/doc/bind-version/arm/ - The directory containing the BIND 9 Administrator Reference Manual in HTML and SGML formats, which details BIND resource requirements, how to configure different types of nameservers, how to perform load balancing, and other advanced topics. For most new users of BIND, this is the best place to start.
-
/usr/share/doc/bind-version/draft/ - The directory containing assorted technical documents that review issues related to the DNS service, and propose some methods to address them.
-
/usr/share/doc/bind-version/misc/ - The directory designed to address specific advanced issues. Users of BIND version 8 should consult the
migrationdocument for specific changes they must make when moving to BIND 9. Theoptionsfile lists all of the options implemented in BIND 9 that are used in/etc/named.conf. -
/usr/share/doc/bind-version/rfc/ - The directory providing every RFC document related to BIND.
-
man rndc - The manual page for
rndccontaining the full documentation on its usage. -
man named - The manual page for
namedcontaining the documentation on assorted arguments that can be used to control the BIND nameserver daemon. -
man lwresd - The manual page for
lwresdcontaining the full documentation on the lightweight resolver daemon and its usage. -
man named.conf - The manual page with a comprehensive list of options available within the
namedconfiguration file. -
man rndc.conf - The manual page with a comprehensive list of options available within the
rndcconfiguration file.
17.2.7.2. Useful Websites
- http://www.isc.org/software/bind
- The home page of the BIND project containing information about current releases as well as a PDF version of the BIND 9 Administrator Reference Manual.
Chapter 18. Web Servers
HTTP (Hypertext Transfer Protocol) server, or a web server, is a network service that serves content to a client over the web. This typically means web pages, but any other documents can be served as well.
- Apache HTTP Server
- nginx
Important
18.1. The Apache HTTP Server
httpd service, and covers advanced topics such as adding server modules, setting up virtual hosts, or configuring the secure HTTP server.
httpd service configuration accordingly. This section reviews some of the newly added features, outlines important changes, and guides you through the update of older configuration files.
18.1.1. New Features
- Support for large files on 32-bit architectures, allowing the web server to handle files greater than 2GB.
- A new structure for authentication and authorization support, replacing the authentication modules provided in previous versions.
18.1.2. Notable Changes
httpd service configuration:
18.1.3. Updating the Configuration
- Make sure all module names are correct, since they may have changed. Adjust the
LoadModuledirective for each module that has been renamed. - Recompile all third party modules before attempting to load them. This typically means authentication and authorization modules.
- If you use the Apache HTTP Secure Server, see Section 18.1.9, “Enabling the mod_ssl Module” for important information on enabling the Secure Sockets Layer (SSL) protocol.
service httpd configtest Syntax OK
~]# service httpd configtest
Syntax OK18.1.4. Running the httpd Service
httpd service, make sure you have the httpd installed. You can do so by using the following command:
yum install httpd
~]# yum install httpd18.1.4.1. Starting the Service
httpd service, type the following at a shell prompt as root:
service httpd start Starting httpd: [ OK ]
~]# service httpd start
Starting httpd: [ OK ]chkconfig httpd on
~]# chkconfig httpd onNote
18.1.4.2. Stopping the Service
httpd service, type the following at a shell prompt as root:
service httpd stop Stopping httpd: [ OK ]
~]# service httpd stop
Stopping httpd: [ OK ]chkconfig httpd off
~]# chkconfig httpd off18.1.4.3. Restarting the Service
httpd service:
- To restart the service completely, enter the following command as
root:service httpd restart Stopping httpd: [ OK ] Starting httpd: [ OK ]
~]# service httpd restart Stopping httpd: [ OK ] Starting httpd: [ OK ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow This stops the runninghttpdservice and immediately starts it again. Use this command after installing or removing a dynamically loaded module such as PHP. - To only reload the configuration, as
root, type:service httpd reload
~]# service httpd reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow This causes the runninghttpdservice to reload its configuration file. Any requests being currently processed will be interrupted, which may cause a client browser to display an error message or render a partial page. - To reload the configuration without affecting active requests, enter the following command as
root:service httpd graceful
~]# service httpd gracefulCopy to Clipboard Copied! Toggle word wrap Toggle overflow This causes the runninghttpdservice to reload its configuration file. Any requests being currently processed will use the old configuration.
18.1.4.4. Verifying the Service Status
httpd service is running, type the following at a shell prompt:
service httpd status httpd (pid 19014) is running...
~]# service httpd status
httpd (pid 19014) is running...18.1.5. Editing the Configuration Files
httpd service is started, by default, it reads the configuration from locations that are listed in Table 18.1, “The httpd service configuration files”.
httpd service.
service httpd configtest Syntax OK
~]# service httpd configtest
Syntax OK18.1.5.1. Common httpd.conf Directives
/etc/httpd/conf/httpd.conf configuration file:
-
<Directory> - The
<Directory>directive allows you to apply certain directives to a particular directory only. It takes the following form:<Directory directory> directive … </Directory>
<Directory directory> directive … </Directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The directory can be either a full path to an existing directory in the local file system, or a wildcard expression.This directive can be used to configure additionalcgi-bindirectories for server-side scripts located outside the directory that is specified byScriptAlias. In this case, theExecCGIandAddHandlerdirectives must be supplied, and the permissions on the target directory must be set correctly (that is,0755).Example 18.1. Using the <Directory> directive
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
<IfDefine> - The
IfDefinedirective allows you to use certain directives only when a particular parameter is supplied on the command line. It takes the following form:<IfDefine [!]parameter> directive … </IfDefine>
<IfDefine [!]parameter> directive … </IfDefine>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The parameter can be supplied at a shell prompt using the-Dparameter command-line option (for example,httpd -DEnableHome). If the optional exclamation mark (that is,!) is present, the enclosed directives are used only when the parameter is not specified.Example 18.2. Using the <IfDefine> directive
<IfDefine EnableHome> UserDir public_html </IfDefine>
<IfDefine EnableHome> UserDir public_html </IfDefine>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
<IfModule> - The
<IfModule>directive allows you to use certain directive only when a particular module is loaded. It takes the following form:<IfModule [!]module> directive … </IfModule>
<IfModule [!]module> directive … </IfModule>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The module can be identified either by its name, or by the file name. If the optional exclamation mark (that is,!) is present, the enclosed directives are used only when the module is not loaded.Example 18.3. Using the <IfModule> directive
<IfModule mod_disk_cache.c> CacheEnable disk / CacheRoot /var/cache/mod_proxy </IfModule>
<IfModule mod_disk_cache.c> CacheEnable disk / CacheRoot /var/cache/mod_proxy </IfModule>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
<Location> - The
<Location>directive allows you to apply certain directives to a particular URL only. It takes the following form:<Location url> directive … </Location>
<Location url> directive … </Location>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The url can be either a path relative to the directory specified by theDocumentRootdirective (for example,/server-info), or an external URL such ashttp://example.com/server-info.Example 18.4. Using the <Location> directive
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
<Proxy> - The
<Proxy>directive allows you to apply certain directives to the proxy server only. It takes the following form:<Proxy pattern> directive … </Proxy>
<Proxy pattern> directive … </Proxy>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The pattern can be an external URL, or a wildcard expression (for example,http://example.com/*).Example 18.5. Using the <Proxy> directive
<Proxy *> Order deny,allow Deny from all Allow from .example.com </Proxy>
<Proxy *> Order deny,allow Deny from all Allow from .example.com </Proxy>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
<VirtualHost> - The
<VirtualHost>directive allows you apply certain directives to particular virtual hosts only. It takes the following form:<VirtualHost address[:port]…> directive … </VirtualHost>
<VirtualHost address[:port]…> directive … </VirtualHost>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The address can be an IP address, a fully qualified domain name, or a special form as described in Table 18.2, “Available <VirtualHost> options”.Expand Table 18.2. Available <VirtualHost> options Option Description *Represents all IP addresses. _default_Represents unmatched IP addresses. Example 18.6. Using the <VirtualHost> directive
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
AccessFileName - The
AccessFileNamedirective allows you to specify the file to be used to customize access control information for each directory. It takes the following form:AccessFileName filename…
AccessFileName filename…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The filename is a name of the file to look for in the requested directory. By default, the server looks for.htaccess.For security reasons, the directive is typically followed by theFilestag to prevent the files beginning with.htfrom being accessed by web clients. This includes the.htaccessand.htpasswdfiles.Example 18.7. Using the AccessFileName directive
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Action - The
Actiondirective allows you to specify a CGI script to be executed when a certain media type is requested. It takes the following form:Action content-type path
Action content-type pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow The content-type has to be a valid MIME type such astext/html,image/png, orapplication/pdf. The path refers to an existing CGI script, and must be relative to the directory specified by theDocumentRootdirective (for example,/cgi-bin/process-image.cgi).Example 18.8. Using the Action directive
Action image/png /cgi-bin/process-image.cgi
Action image/png /cgi-bin/process-image.cgiCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
AddDescription - The
AddDescriptiondirective allows you to specify a short description to be displayed in server-generated directory listings for a given file. It takes the following form:AddDescription "description" filename…
AddDescription "description" filename…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The description should be a short text enclosed in double quotes (that is,"). The filename can be a full file name, a file extension, or a wildcard expression.Example 18.9. Using the AddDescription directive
AddDescription "GZIP compressed tar archive" .tgz
AddDescription "GZIP compressed tar archive" .tgzCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
AddEncoding - The
AddEncodingdirective allows you to specify an encoding type for a particular file extension. It takes the following form:AddEncoding encoding extension…
AddEncoding encoding extension…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The encoding has to be a valid MIME encoding such asx-compress,x-gzip, etc. The extension is a case sensitive file extension, and is conventionally written with a leading dot (for example,.gz).This directive is typically used to instruct web browsers to decompress certain file types as they are downloaded.Example 18.10. Using the AddEncoding directive
AddEncoding x-gzip .gz .tgz
AddEncoding x-gzip .gz .tgzCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
AddHandler - The
AddHandlerdirective allows you to map certain file extensions to a selected handler. It takes the following form:AddHandler handler extension…
AddHandler handler extension…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The handler has to be a name of a previously defined handler. The extension is a case sensitive file extension, and is conventionally written with a leading dot (for example,.cgi).This directive is typically used to treat files with the.cgiextension as CGI scripts regardless of the directory they are in. Additionally, it is also commonly used to process server-parsed HTML and image-map files.Example 18.11. Using the AddHandler option
AddHandler cgi-script .cgi
AddHandler cgi-script .cgiCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
AddIcon - The
AddIcondirective allows you to specify an icon to be displayed for a particular file in server-generated directory listings. It takes the following form:AddIcon path pattern…
AddIcon path pattern…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The path refers to an existing icon file, and must be relative to the directory specified by theDocumentRootdirective (for example,/icons/folder.png). The pattern can be a file name, a file extension, a wildcard expression, or a special form as described in the following table:Expand Table 18.3. Available AddIcon options Option Description ^^DIRECTORY^^Represents a directory. ^^BLANKICON^^Represents a blank line. Example 18.12. Using the AddIcon directive
AddIcon /icons/text.png .txt README
AddIcon /icons/text.png .txt READMECopy to Clipboard Copied! Toggle word wrap Toggle overflow -
AddIconByEncoding - The
AddIconByEncodingdirective allows you to specify an icon to be displayed for a particular encoding type in server-generated directory listings. It takes the following form:AddIconByEncoding path encoding…
AddIconByEncoding path encoding…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The path refers to an existing icon file, and must be relative to the directory specified by theDocumentRootdirective (for example,/icons/compressed.png). The encoding has to be a valid MIME encoding such asx-compress,x-gzip, etc.Example 18.13. Using the AddIconByEncoding directive
AddIconByEncoding /icons/compressed.png x-compress x-gzip
AddIconByEncoding /icons/compressed.png x-compress x-gzipCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
AddIconByType - The
AddIconByTypedirective allows you to specify an icon to be displayed for a particular media type in server-generated directory listings. It takes the following form:AddIconByType path content-type…
AddIconByType path content-type…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The path refers to an existing icon file, and must be relative to the directory specified by theDocumentRootdirective (for example,/icons/text.png). The content-type has to be either a valid MIME type (for example,text/htmlorimage/png), or a wildcard expression such astext/*,image/*, etc.Example 18.14. Using the AddIconByType directive
AddIconByType /icons/video.png video/*
AddIconByType /icons/video.png video/*Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
AddLanguage - The
AddLanguagedirective allows you to associate a file extension with a specific language. It takes the following form:AddLanguage language extension…
AddLanguage language extension…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The language has to be a valid MIME language such ascs,en, orfr. The extension is a case sensitive file extension, and is conventionally written with a leading dot (for example,.cs).This directive is especially useful for web servers that serve content in multiple languages based on the client's language settings.Example 18.15. Using the AddLanguage directive
AddLanguage cs .cs .cz
AddLanguage cs .cs .czCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
AddType - The
AddTypedirective allows you to define or override the media type for a particular file extension. It takes the following form:AddType content-type extension…
AddType content-type extension…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The content-type has to be a valid MIME type such astext/html,image/png, etc. The extension is a case sensitive file extension, and is conventionally written with a leading dot (for example,.cs).Example 18.16. Using the AddType directive
AddType application/x-gzip .gz .tgz
AddType application/x-gzip .gz .tgzCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Alias - The
Aliasdirective allows you to refer to files and directories outside the default directory specified by theDocumentRootdirective. It takes the following form:Alias url-path real-path
Alias url-path real-pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow The url-path must be relative to the directory specified by theDocumentRootdirective (for example,/images/). The real-path is a full path to a file or directory in the local file system.This directive is typically followed by theDirectorytag with additional permissions to access the target directory. By default, the/icons/alias is created so that the icons from/var/www/icons/are displayed in server-generated directory listings.Example 18.17. Using the Alias directive
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Allow - The
Allowdirective allows you to specify which clients have permission to access a given directory. It takes the following form:Allow from client…
Allow from client…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The client can be a domain name, an IP address (both full and partial), a network/netmask pair, orallfor all clients.Example 18.18. Using the Allow directive
Allow from 192.168.1.0/255.255.255.0
Allow from 192.168.1.0/255.255.255.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
AllowOverride - The
AllowOverridedirective allows you to specify which directives in a.htaccessfile can override the default configuration. It takes the following form:AllowOverride type…
AllowOverride type…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The type has to be one of the available grouping options as described in Table 18.4, “Available AllowOverride options”.Expand Table 18.4. Available AllowOverride options Option Description AllAll directives in .htaccessare allowed to override earlier configuration settings.NoneNo directive in .htaccessis allowed to override earlier configuration settings.AuthConfigAllows the use of authorization directives such as AuthName,AuthType, orRequire.FileInfoAllows the use of file type, metadata, and mod_rewritedirectives such asDefaultType,RequestHeader, orRewriteEngine, as well as theActiondirective.IndexesAllows the use of directory indexing directives such as AddDescription,AddIcon, orFancyIndexing.LimitAllows the use of host access directives, that is, Allow,Deny, andOrder.Options[=option,…]Allows the use of the Optionsdirective. Additionally, you can provide a comma-separated list of options to customize which options can be set using this directive.Example 18.19. Using the AllowOverride directive
AllowOverride FileInfo AuthConfig Limit
AllowOverride FileInfo AuthConfig LimitCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
BrowserMatch - The
BrowserMatchdirective allows you to modify the server behavior based on the client's web browser type. It takes the following form:BrowserMatch pattern variable…
BrowserMatch pattern variable…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The pattern is a regular expression to match the User-Agent HTTP header field. The variable is an environment variable that is set when the header field matches the pattern.By default, this directive is used to deny connections to specific browsers with known issues, and to disable keepalives and HTTP header flushes for browsers that are known to have problems with these actions.Example 18.20. Using the BrowserMatch directive
BrowserMatch "Mozilla/2" nokeepalive
BrowserMatch "Mozilla/2" nokeepaliveCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
CacheDefaultExpire - The
CacheDefaultExpireoption allows you to set how long to cache a document that does not have any expiration date or the date of its last modification specified. It takes the following form:CacheDefaultExpire time
CacheDefaultExpire timeCopy to Clipboard Copied! Toggle word wrap Toggle overflow The time is specified in seconds. The default option is3600(that is, one hour).Example 18.21. Using the CacheDefaultExpire directive
CacheDefaultExpire 3600
CacheDefaultExpire 3600Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
CacheDisable - The
CacheDisabledirective allows you to disable caching of certain URLs. It takes the following form:CacheDisable path
CacheDisable pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow The path must be relative to the directory specified by theDocumentRootdirective (for example,/files/).Example 18.22. Using the CacheDisable directive
CacheDisable /temporary
CacheDisable /temporaryCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
CacheEnable - The
CacheEnabledirective allows you to specify a cache type to be used for certain URLs. It takes the following form:CacheEnable type url
CacheEnable type urlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The type has to be a valid cache type as described in Table 18.5, “Available cache types”. The url can be a path relative to the directory specified by theDocumentRootdirective (for example,/images/), a protocol (for example,ftp://), or an external URL such ashttp://example.com/.Expand Table 18.5. Available cache types Type Description memThe memory-based storage manager. diskThe disk-based storage manager. fdThe file descriptor cache. Example 18.23. Using the CacheEnable directive
CacheEnable disk /
CacheEnable disk /Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
CacheLastModifiedFactor - The
CacheLastModifiedFactordirective allows you to customize how long to cache a document that does not have any expiration date specified, but that provides information about the date of its last modification. It takes the following form:CacheLastModifiedFactor number
CacheLastModifiedFactor numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow The number is a coefficient to be used to multiply the time that passed since the last modification of the document. The default option is0.1(that is, one tenth).Example 18.24. Using the CacheLastModifiedFactor directive
CacheLastModifiedFactor 0.1
CacheLastModifiedFactor 0.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
CacheMaxExpire - The
CacheMaxExpiredirective allows you to specify the maximum amount of time to cache a document. It takes the following form:CacheMaxExpire time
CacheMaxExpire timeCopy to Clipboard Copied! Toggle word wrap Toggle overflow The time is specified in seconds. The default option is86400(that is, one day).Example 18.25. Using the CacheMaxExpire directive
CacheMaxExpire 86400
CacheMaxExpire 86400Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
CacheNegotiatedDocs - The
CacheNegotiatedDocsdirective allows you to enable caching of the documents that were negotiated on the basis of content. It takes the following form:CacheNegotiatedDocs option
CacheNegotiatedDocs optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.6, “Available CacheNegotiatedDocs options”. Since the content-negotiated documents may change over time or because of the input from the requester, the default option isOff.Expand Table 18.6. Available CacheNegotiatedDocs options Option Description OnEnables caching the content-negotiated documents. OffDisables caching the content-negotiated documents. Example 18.26. Using the CacheNegotiatedDocs directive
CacheNegotiatedDocs On
CacheNegotiatedDocs OnCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
CacheRoot - The
CacheRootdirective allows you to specify the directory to store cache files in. It takes the following form:CacheRoot directory
CacheRoot directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow The directory must be a full path to an existing directory in the local file system. The default option is/var/cache/mod_proxy/.Example 18.27. Using the CacheRoot directive
CacheRoot /var/cache/mod_proxy
CacheRoot /var/cache/mod_proxyCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
CustomLog - The
CustomLogdirective allows you to specify the log file name and the log file format. It takes the following form:CustomLog path format
CustomLog path formatCopy to Clipboard Copied! Toggle word wrap Toggle overflow The path refers to a log file, and must be relative to the directory that is specified by theServerRootdirective (that is,/etc/httpd/by default). The format has to be either an explicit format string, or a format name that was previously defined using theLogFormatdirective.Example 18.28. Using the CustomLog directive
CustomLog logs/access_log combined
CustomLog logs/access_log combinedCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
DefaultIcon - The
DefaultIcondirective allows you to specify an icon to be displayed for a file in server-generated directory listings when no other icon is associated with it. It takes the following form:DefaultIcon path
DefaultIcon pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow The path refers to an existing icon file, and must be relative to the directory specified by theDocumentRootdirective (for example,/icons/unknown.png).Example 18.29. Using the DefaultIcon directive
DefaultIcon /icons/unknown.png
DefaultIcon /icons/unknown.pngCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
DefaultType - The
DefaultTypedirective allows you to specify a media type to be used in case the proper MIME type cannot be determined by the server. It takes the following form:DefaultType content-type
DefaultType content-typeCopy to Clipboard Copied! Toggle word wrap Toggle overflow The content-type has to be a valid MIME type such astext/html,image/png,application/pdf, etc.Example 18.30. Using the DefaultType directive
DefaultType text/plain
DefaultType text/plainCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Deny - The
Denydirective allows you to specify which clients are denied access to a given directory. It takes the following form:Deny from client…
Deny from client…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The client can be a domain name, an IP address (both full and partial), a network/netmask pair, orallfor all clients.Example 18.31. Using the Deny directive
Deny from 192.168.1.1
Deny from 192.168.1.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
DirectoryIndex - The
DirectoryIndexdirective allows you to specify a document to be served to a client when a directory is requested (that is, when the URL ends with the/character). It takes the following form:DirectoryIndex filename…
DirectoryIndex filename…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The filename is a name of the file to look for in the requested directory. By default, the server looks forindex.html, andindex.html.var.Example 18.32. Using the DirectoryIndex directive
DirectoryIndex index.html index.html.var
DirectoryIndex index.html index.html.varCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
DocumentRoot - The
DocumentRootdirective allows you to specify the main directory from which the content is served. It takes the following form:DocumentRoot directory
DocumentRoot directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow The directory must be a full path to an existing directory in the local file system. The default option is/var/www/html/.Example 18.33. Using the DocumentRoot directive
DocumentRoot /var/www/html
DocumentRoot /var/www/htmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ErrorDocument - The
ErrorDocumentdirective allows you to specify a document or a message to be displayed as a response to a particular error. It takes the following form:ErrorDocument error-code action
ErrorDocument error-code actionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The error-code has to be a valid code such as403(Forbidden),404(Not Found), or500(Internal Server Error). The action can be either a URL (both local and external), or a message string enclosed in double quotes (that is,").Example 18.34. Using the ErrorDocument directive
ErrorDocument 403 "Access Denied" ErrorDocument 404 /404-not_found.html
ErrorDocument 403 "Access Denied" ErrorDocument 404 /404-not_found.htmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ErrorLog - The
ErrorLogdirective allows you to specify a file to which the server errors are logged. It takes the following form:ErrorLog path
ErrorLog pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow The path refers to a log file, and can be either absolute, or relative to the directory that is specified by theServerRootdirective (that is,/etc/httpd/by default). The default option islogs/error_logExample 18.35. Using the ErrorLog directive
ErrorLog logs/error_log
ErrorLog logs/error_logCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ExtendedStatus - The
ExtendedStatusdirective allows you to enable detailed server status information. It takes the following form:ExtendedStatus option
ExtendedStatus optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.7, “Available ExtendedStatus options”. The default option isOff.Expand Table 18.7. Available ExtendedStatus options Option Description OnEnables generating the detailed server status. OffDisables generating the detailed server status. Example 18.36. Using the ExtendedStatus directive
ExtendedStatus On
ExtendedStatus OnCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Group - The
Groupdirective allows you to specify the group under which thehttpdservice will run. It takes the following form:Group group
Group groupCopy to Clipboard Copied! Toggle word wrap Toggle overflow The group has to be an existing UNIX group. The default option isapache.Note thatGroupis no longer supported inside<VirtualHost>, and has been replaced by theSuexecUserGroupdirective.Example 18.37. Using the Group directive
Group apache
Group apacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
HeaderName - The
HeaderNamedirective allows you to specify a file to be prepended to the beginning of the server-generated directory listing. It takes the following form:HeaderName filename
HeaderName filenameCopy to Clipboard Copied! Toggle word wrap Toggle overflow The filename is a name of the file to look for in the requested directory. By default, the server looks forHEADER.html.Example 18.38. Using the HeaderName directive
HeaderName HEADER.html
HeaderName HEADER.htmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
HostnameLookups - The
HostnameLookupsdirective allows you to enable automatic resolving of IP addresses. It takes the following form:HostnameLookups option
HostnameLookups optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.8, “Available HostnameLookups options”. To conserve resources on the server, the default option isOff.Expand Table 18.8. Available HostnameLookups options Option Description OnEnables resolving the IP address for each connection so that the host name can be logged. However, this also adds a significant processing overhead. DoubleEnables performing the double-reverse DNS lookup. In comparison to the above option, this adds even more processing overhead. OffDisables resolving the IP address for each connection. Note that when the presence of host names is required in server log files, it is often possible to use one of the many log analyzer tools that perform the DNS lookups more efficiently.Example 18.39. Using the HostnameLookups directive
HostnameLookups Off
HostnameLookups OffCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Include - The
Includedirective allows you to include other configuration files. It takes the following form:Include filename
Include filenameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Thefilenamecan be an absolute path, a path relative to the directory specified by theServerRootdirective, or a wildcard expression. All configuration files from the/etc/httpd/conf.d/directory are loaded by default.Example 18.40. Using the Include directive
Include conf.d/*.conf
Include conf.d/*.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
IndexIgnore - The
IndexIgnoredirective allows you to specify a list of file names to be omitted from the server-generated directory listings. It takes the following form:IndexIgnore filename…
IndexIgnore filename…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The filename option can be either a full file name, or a wildcard expression.Example 18.41. Using the IndexIgnore directive
IndexIgnore .??* *~ *# HEADER* README* RCS CVS *,v *,t
IndexIgnore .??* *~ *# HEADER* README* RCS CVS *,v *,tCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
IndexOptions - The
IndexOptionsdirective allows you to customize the behavior of server-generated directory listings. It takes the following form:IndexOptions option…
IndexOptions option…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.9, “Available directory listing options”. The default options areCharset=UTF-8,FancyIndexing,HTMLTable,NameWidth=*, andVersionSort.Expand Table 18.9. Available directory listing options Option Description Charset=encodingSpecifies the character set of a generated web page. The encoding has to be a valid character set such as UTF-8orISO-8859-2.Type=content-typeSpecifies the media type of a generated web page. The content-type has to be a valid MIME type such as text/htmlortext/plain.DescriptionWidth=valueSpecifies the width of the description column. The value can be either a number of characters, or an asterisk (that is, *) to adjust the width automatically.FancyIndexingEnables advanced features such as different icons for certain files or possibility to re-sort a directory listing by clicking on a column header. FolderFirstEnables listing directories first, always placing them above files. HTMLTableEnables the use of HTML tables for directory listings. IconsAreLinksEnables using the icons as links. IconHeight=valueSpecifies an icon height. The value is a number of pixels. IconWidth=valueSpecifies an icon width. The value is a number of pixels. IgnoreCaseEnables sorting files and directories in a case-sensitive manner. IgnoreClientDisables accepting query variables from a client. NameWidth=valueSpecifies the width of the file name column. The value can be either a number of characters, or an asterisk (that is, *) to adjust the width automatically.ScanHTMLTitlesEnables parsing the file for a description (that is, the titleelement) in case it is not provided by theAddDescriptiondirective.ShowForbiddenEnables listing the files with otherwise restricted access. SuppressColumnSortingDisables re-sorting a directory listing by clicking on a column header. SuppressDescriptionDisables reserving a space for file descriptions. SuppressHTMLPreambleDisables the use of standard HTML preamble when a file specified by the HeaderNamedirective is present.SuppressIconDisables the use of icons in directory listings. SuppressLastModifiedDisables displaying the date of the last modification field in directory listings. SuppressRulesDisables the use of horizontal lines in directory listings. SuppressSizeDisables displaying the file size field in directory listings. TrackModifiedEnables returning the Last-ModifiedandETagvalues in the HTTP header.VersionSortEnables sorting files that contain a version number in the expected manner. XHTMLEnables the use of XHTML 1.0 instead of the default HTML 3.2. Example 18.42. Using the IndexOptions directive
IndexOptions FancyIndexing VersionSort NameWidth=* HTMLTable Charset=UTF-8
IndexOptions FancyIndexing VersionSort NameWidth=* HTMLTable Charset=UTF-8Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
KeepAlive - The
KeepAlivedirective allows you to enable persistent connections. It takes the following form:KeepAlive option
KeepAlive optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.10, “Available KeepAlive options”. The default option isOff.Expand Table 18.10. Available KeepAlive options Option Description OnEnables the persistent connections. In this case, the server will accept more than one request per connection. OffDisables the keep-alive connections. Note that when the persistent connections are enabled, on a busy server, the number of child processes can increase rapidly and eventually reach the maximum limit, slowing down the server significantly. To reduce the risk, it is recommended that you setKeepAliveTimeoutto a low number, and monitor the/var/log/httpd/logs/error_loglog file carefully.Example 18.43. Using the KeepAlive directive
KeepAlive Off
KeepAlive OffCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
KeepAliveTimeout - The
KeepAliveTimeoutdirective allows you to specify the amount of time to wait for another request before closing the connection. It takes the following form:KeepAliveTimeout time
KeepAliveTimeout timeCopy to Clipboard Copied! Toggle word wrap Toggle overflow The time is specified in seconds. The default option is15.Example 18.44. Using the KeepAliveTimeout directive
KeepAliveTimeout 15
KeepAliveTimeout 15Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
LanguagePriority - The
LanguagePrioritydirective allows you to customize the precedence of languages. It takes the following form:LanguagePriority language…
LanguagePriority language…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The language has to be a valid MIME language such ascs,en, orfr.This directive is especially useful for web servers that serve content in multiple languages based on the client's language settings.Example 18.45. Using the LanguagePriority directive
LanguagePriority sk cs en
LanguagePriority sk cs enCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Listen - The Listen directive allows you to specify IP addresses or ports to listen to. It takes the following form:
Listen [ip-address:]port [protocol]
Listen [ip-address:]port [protocol]Copy to Clipboard Copied! Toggle word wrap Toggle overflow The ip-address is optional and unless supplied, the server will accept incoming requests on a given port from all IP addresses. Since the protocol is determined automatically from the port number, it can be usually omitted. The default option is to listen to port80.Note that if the server is configured to listen to a port under 1024, only superuser will be able to start thehttpdservice.Example 18.46. Using the Listen directive
Listen 80
Listen 80Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
LoadModule - The
LoadModuledirective allows you to load a Dynamic Shared Object (DSO) module. It takes the following form:LoadModule name path
LoadModule name pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow The name has to be a valid identifier of the required module. The path refers to an existing module file, and must be relative to the directory in which the libraries are placed (that is,/usr/lib/httpd/on 32-bit and/usr/lib64/httpd/on 64-bit systems by default).See Section 18.1.6, “Working with Modules” for more information on the Apache HTTP Server's DSO support.Example 18.47. Using the LoadModule directive
LoadModule php5_module modules/libphp5.so
LoadModule php5_module modules/libphp5.soCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
LogFormat - The LogFormat directive allows you to specify a log file format. It takes the following form:
LogFormat format name
LogFormat format nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow The format is a string consisting of options as described in Table 18.11, “Common LogFormat options”. The name can be used instead of the format string in theCustomLogdirective.Expand Table 18.11. Common LogFormat options Option Description %bRepresents the size of the response in bytes. %hRepresents the IP address or host name of a remote client. %lRepresents the remote log name if supplied. If not, a hyphen (that is, -) is used instead.%rRepresents the first line of the request string as it came from the browser or client. %sRepresents the status code. %tRepresents the date and time of the request. %uIf the authentication is required, it represents the remote user. If not, a hyphen (that is, -) is used instead.%{field}Represents the content of the HTTP header field. The common options include %{Referer}(the URL of the web page that referred the client to the server) and%{User-Agent}(the type of the web browser making the request).Example 18.48. Using the LogFormat directive
LogFormat "%h %l %u %t \"%r\" %>s %b" common
LogFormat "%h %l %u %t \"%r\" %>s %b" commonCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
LogLevel - The
LogLeveldirective allows you to customize the verbosity level of the error log. It takes the following form:LogLevel option
LogLevel optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.12, “Available LogLevel options”. The default option iswarn.Expand Table 18.12. Available LogLevel options Option Description emergOnly the emergency situations when the server cannot perform its work are logged. alertAll situations when an immediate action is required are logged. critAll critical conditions are logged. errorAll error messages are logged. warnAll warning messages are logged. noticeEven normal, but still significant situations are logged. infoVarious informational messages are logged. debugVarious debugging messages are logged. Example 18.49. Using the LogLevel directive
LogLevel warn
LogLevel warnCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
MaxKeepAliveRequests - The
MaxKeepAliveRequestsdirective allows you to specify the maximum number of requests for a persistent connection. It takes the following form:MaxKeepAliveRequests number
MaxKeepAliveRequests numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow A high number can improve the performance of the server. Note that using0allows unlimited number of requests. The default option is100.Example 18.50. Using the MaxKeepAliveRequests option
MaxKeepAliveRequests 100
MaxKeepAliveRequests 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
NameVirtualHost - The
NameVirtualHostdirective allows you to specify the IP address and port number for a name-based virtual host. It takes the following form:NameVirtualHost ip-address[:port]
NameVirtualHost ip-address[:port]Copy to Clipboard Copied! Toggle word wrap Toggle overflow The ip-address can be either a full IP address, or an asterisk (that is,*) representing all interfaces. Note that IPv6 addresses have to be enclosed in square brackets (that is,[and]). The port is optional.Name-based virtual hosting allows one Apache HTTP Server to serve different domains without using multiple IP addresses.Important
Name-based virtual hosts only work with non-secure HTTP connections. If using virtual hosts with a secure server, use IP address-based virtual hosts instead.Example 18.51. Using the NameVirtualHost directive
NameVirtualHost *:80
NameVirtualHost *:80Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Options - The
Optionsdirective allows you to specify which server features are available in a particular directory. It takes the following form:Options option…
Options option…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.13, “Available server features”.Expand Table 18.13. Available server features Option Description ExecCGIEnables the execution of CGI scripts. FollowSymLinksEnables following symbolic links in the directory. IncludesEnables server-side includes. IncludesNOEXECEnables server-side includes, but does not allow the execution of commands. IndexesEnables server-generated directory listings. MultiViewsEnables content-negotiated “MultiViews”. SymLinksIfOwnerMatchEnables following symbolic links in the directory when both the link and the target file have the same owner. AllEnables all of the features above with the exception of MultiViews.NoneDisables all of the features above. Important
TheSymLinksIfOwnerMatchoption is not a security feature as it can be bypassed by an attacker.Example 18.52. Using the Options directive
Options Indexes FollowSymLinks
Options Indexes FollowSymLinksCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Order - The
Orderdirective allows you to specify the order in which theAllowandDenydirectives are evaluated. It takes the following form:Order option
Order optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.14, “Available Order options”. The default option isallow,deny.Expand Table 18.14. Available Order options Option Description allow,denyAllowdirectives are evaluated first.deny,allowDenydirectives are evaluated first.Example 18.53. Using the Order directive
Order allow,deny
Order allow,denyCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
PidFile - The
PidFiledirective allows you to specify a file to which the process ID (PID) of the server is stored. It takes the following form:PidFile path
PidFile pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow The path refers to a pid file, and can be either absolute, or relative to the directory that is specified by theServerRootdirective (that is,/etc/httpd/by default). The default option isrun/httpd.pid.Example 18.54. Using the PidFile directive
PidFile run/httpd.pid
PidFile run/httpd.pidCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ProxyRequests - The
ProxyRequestsdirective allows you to enable forward proxy requests. It takes the following form:ProxyRequests option
ProxyRequests optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.15, “Available ProxyRequests options”. The default option isOff.Expand Table 18.15. Available ProxyRequests options Option Description OnEnables forward proxy requests. OffDisables forward proxy requests. Example 18.55. Using the ProxyRequests directive
ProxyRequests On
ProxyRequests OnCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ReadmeName - The
ReadmeNamedirective allows you to specify a file to be appended to the end of the server-generated directory listing. It takes the following form:ReadmeName filename
ReadmeName filenameCopy to Clipboard Copied! Toggle word wrap Toggle overflow The filename is a name of the file to look for in the requested directory. By default, the server looks forREADME.html.Example 18.56. Using the ReadmeName directive
ReadmeName README.html
ReadmeName README.htmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Redirect - The
Redirectdirective allows you to redirect a client to another URL. It takes the following form:Redirect [status] path url
Redirect [status] path urlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The status is optional, and if provided, it has to be a valid keyword as described in Table 18.16, “Available status options”. The path refers to the old location, and must be relative to the directory specified by theDocumentRootdirective (for example,/docs). The url refers to the current location of the content (for example,http://docs.example.com).Expand Table 18.16. Available status options Status Description permanentIndicates that the requested resource has been moved permanently. The 301(Moved Permanently) status code is returned to a client.tempIndicates that the requested resource has been moved only temporarily. The 302(Found) status code is returned to a client.seeotherIndicates that the requested resource has been replaced. The 303(See Other) status code is returned to a client.goneIndicates that the requested resource has been removed permanently. The 410(Gone) status is returned to a client.Note that for more advanced redirection techniques, you can use themod_rewritemodule that is part of the Apache HTTP Server installation.Example 18.57. Using the Redirect directive
Redirect permanent /docs http://docs.example.com
Redirect permanent /docs http://docs.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ScriptAlias - The
ScriptAliasdirective allows you to specify the location of CGI scripts. It takes the following form:ScriptAlias url-path real-path
ScriptAlias url-path real-pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow The url-path must be relative to the directory specified by theDocumentRootdirective (for example,/cgi-bin/). The real-path is a full path to a file or directory in the local file system.This directive is typically followed by theDirectorytag with additional permissions to access the target directory. By default, the/cgi-bin/alias is created so that the scripts located in the/var/www/cgi-bin/are accessible.TheScriptAliasdirective is used for security reasons to prevent CGI scripts from being viewed as ordinary text documents.Example 18.58. Using the ScriptAlias directive
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
ServerAdmin - The
ServerAdmindirective allows you to specify the email address of the server administrator to be displayed in server-generated web pages. It takes the following form:ServerAdmin email
ServerAdmin emailCopy to Clipboard Copied! Toggle word wrap Toggle overflow The default option isroot@localhost.This directive is commonly set towebmaster@hostname, where hostname is the address of the server. Once set, aliaswebmasterto the person responsible for the web server in/etc/aliases, and as superuser, run thenewaliasescommand.Example 18.59. Using the ServerAdmin directive
ServerAdmin webmaster@penguin.example.com
ServerAdmin webmaster@penguin.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ServerName - The
ServerNamedirective allows you to specify the host name and the port number of a web server. It takes the following form:ServerName hostname[:port]
ServerName hostname[:port]Copy to Clipboard Copied! Toggle word wrap Toggle overflow The hostname has to be a fully qualified domain name (FQDN) of the server. The port is optional, but when supplied, it has to match the number specified by theListendirective.When using this directive, make sure that the IP address and server name pair are included in the/etc/hostsfile.Example 18.60. Using the ServerName directive
ServerName penguin.example.com:80
ServerName penguin.example.com:80Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
ServerRoot - The
ServerRootdirective allows you to specify the directory in which the server operates. It takes the following form:ServerRoot directory
ServerRoot directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow The directory must be a full path to an existing directory in the local file system. The default option is/etc/httpd/.Example 18.61. Using the ServerRoot directive
ServerRoot /etc/httpd
ServerRoot /etc/httpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ServerSignature - The
ServerSignaturedirective allows you to enable displaying information about the server on server-generated documents. It takes the following form:ServerSignature option
ServerSignature optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.17, “Available ServerSignature options”. The default option isOn.Expand Table 18.17. Available ServerSignature options Option Description OnEnables appending the server name and version to server-generated pages. OffDisables appending the server name and version to server-generated pages. EMailEnables appending the server name, version, and the email address of the system administrator as specified by the ServerAdmindirective to server-generated pages.Example 18.62. Using the ServerSignature directive
ServerSignature On
ServerSignature OnCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ServerTokens - The
ServerTokensdirective allows you to customize what information is included in the Server response header. It takes the following form:ServerTokens option
ServerTokens optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.18, “Available ServerTokens options”. The default option isOS.Expand Table 18.18. Available ServerTokens options Option Description ProdIncludes the product name only (that is, Apache).MajorIncludes the product name and the major version of the server (for example, 2).MinorIncludes the product name and the minor version of the server (for example, 2.2).MinIncludes the product name and the minimal version of the server (for example, 2.2.15).OSIncludes the product name, the minimal version of the server, and the type of the operating system it is running on (for example, Red Hat).FullIncludes all the information above along with the list of loaded modules. Note that for security reasons, it is recommended to reveal as little information about the server as possible.Example 18.63. Using the ServerTokens directive
ServerTokens Prod
ServerTokens ProdCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
SuexecUserGroup - The
SuexecUserGroupdirective allows you to specify the user and group under which the CGI scripts will be run. It takes the following form:SuexecUserGroup user group
SuexecUserGroup user groupCopy to Clipboard Copied! Toggle word wrap Toggle overflow The user has to be an existing user, and the group must be a valid UNIX group.For security reasons, the CGI scripts should not be run with root privileges. Note that in<VirtualHost>,SuexecUserGroupreplaces theUserandGroupdirectives.Example 18.64. Using the SuexecUserGroup directive
SuexecUserGroup apache apache
SuexecUserGroup apache apacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Timeout - The
Timeoutdirective allows you to specify the amount of time to wait for an event before closing a connection. It takes the following form:Timeout time
Timeout timeCopy to Clipboard Copied! Toggle word wrap Toggle overflow The time is specified in seconds. The default option is60.Example 18.65. Using the Timeout directive
Timeout 60
Timeout 60Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
TypesConfig - The
TypesConfigallows you to specify the location of the MIME types configuration file. It takes the following form:TypesConfig path
TypesConfig pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow The path refers to an existing MIME types configuration file, and can be either absolute, or relative to the directory that is specified by theServerRootdirective (that is,/etc/httpd/by default). The default option is/etc/mime.types.Note that instead of editing/etc/mime.types, the recommended way to add MIME type mapping to the Apache HTTP Server is to use theAddTypedirective.Example 18.66. Using the TypesConfig directive
TypesConfig /etc/mime.types
TypesConfig /etc/mime.typesCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
UseCanonicalName - The
UseCanonicalNameallows you to specify the way the server refers to itself. It takes the following form:UseCanonicalName option
UseCanonicalName optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option has to be a valid keyword as described in Table 18.19, “Available UseCanonicalName options”. The default option isOff.Expand Table 18.19. Available UseCanonicalName options Option Description OnEnables the use of the name that is specified by the ServerNamedirective.OffDisables the use of the name that is specified by the ServerNamedirective. The host name and port number provided by the requesting client are used instead.DNSDisables the use of the name that is specified by the ServerNamedirective. The host name determined by a reverse DNS lookup is used instead.Example 18.67. Using the UseCanonicalName directive
UseCanonicalName Off
UseCanonicalName OffCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
User - The
Userdirective allows you to specify the user under which thehttpdservice will run. It takes the following form:User user
User userCopy to Clipboard Copied! Toggle word wrap Toggle overflow The user has to be an existing UNIX user. The default option isapache.For security reasons, thehttpdservice should not be run with root privileges. Note thatUseris no longer supported inside<VirtualHost>, and has been replaced by theSuexecUserGroupdirective.Example 18.68. Using the User directive
User apache
User apacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
UserDir - The
UserDirdirective allows you to enable serving content from users' home directories. It takes the following form:UserDir option
UserDir optionCopy to Clipboard Copied! Toggle word wrap Toggle overflow The option can be either a name of the directory to look for in user's home directory (typicallypublic_html), or a valid keyword as described in Table 18.20, “Available UserDir options”. The default option isdisabled.Expand Table 18.20. Available UserDir options Option Description enableduser…Enables serving content from home directories of given users. disabled[user…]Disables serving content from home directories, either for all users, or, if a space separated list of users is supplied, for given users only. Note
In order for the web server to access the content, the permissions on relevant directories and files must be set correctly. Make sure that all users are able to access the home directories, and that they can access and read the content of the directory specified by theUserDirdirective. For example:chmod a+x /home/username/ chmod a+rx /home/username/public_html/
~]# chmod a+x /home/username/ ~]# chmod a+rx /home/username/public_html/Copy to Clipboard Copied! Toggle word wrap Toggle overflow All files in this directory must be set accordingly.Example 18.69. Using the UserDir directive
UserDir public_html
UserDir public_htmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
18.1.5.2. Common ssl.conf Directives
/etc/httpd/conf.d/ssl.conf:
-
SetEnvIf - The
SetEnvIfdirective allows you to set environment variables based on the headers of incoming connections. It takes the following form:SetEnvIf option pattern [!]variable[=value]…
SetEnvIf option pattern [!]variable[=value]…Copy to Clipboard Copied! Toggle word wrap Toggle overflow The option can be either a HTTP header field, a previously defined environment variable name, or a valid keyword as described in Table 18.21, “Available SetEnvIf options”. The pattern is a regular expression. The variable is an environment variable that is set when the option matches the pattern. If the optional exclamation mark (that is,!) is present, the variable is removed instead of being set.Expand Table 18.21. Available SetEnvIf options Option Description Remote_HostRefers to the client's host name. Remote_AddrRefers to the client's IP address. Server_AddrRefers to the server's IP address. Request_MethodRefers to the request method (for example, GET).Request_ProtocolRefers to the protocol name and version (for example, HTTP/1.1).Request_URIRefers to the requested resource. TheSetEnvIfdirective is used to disable HTTP keepalives, and to allow SSL to close the connection without a closing notification from the client browser. This is necessary for certain web browsers that do not reliably shut down the SSL connection.Example 18.70. Using the SetEnvIf directive
SetEnvIf User-Agent ".*MSIE.*" \ nokeepalive ssl-unclean-shutdown \ downgrade-1.0 force-response-1.0SetEnvIf User-Agent ".*MSIE.*" \ nokeepalive ssl-unclean-shutdown \ downgrade-1.0 force-response-1.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
/etc/httpd/conf.d/ssl.conf file to be present, the mod_ssl needs to be installed. See Section 18.1.8, “Setting Up an SSL Server” for more information on how to install and configure an SSL server.
18.1.5.3. Common Multi-Processing Module Directives
IfModule. By default, the server-pool is defined for both the prefork and worker MPMs.
/etc/httpd/conf/httpd.conf:
-
MaxClients - The
MaxClientsdirective allows you to specify the maximum number of simultaneously connected clients to process at one time. It takes the following form:MaxClients number
MaxClients numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow A high number can improve the performance of the server, although it is not recommended to exceed256when using thepreforkMPM.Example 18.71. Using the MaxClients directive
MaxClients 256
MaxClients 256Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MaxRequestsPerChild - The
MaxRequestsPerChilddirective allows you to specify the maximum number of request a child process can serve before it dies. It takes the following form:MaxRequestsPerChild number
MaxRequestsPerChild numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow Setting the number to0allows unlimited number of requests.TheMaxRequestsPerChilddirective is used to prevent long-lived processes from causing memory leaks.Example 18.72. Using the MaxRequestsPerChild directive
MaxRequestsPerChild 4000
MaxRequestsPerChild 4000Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MaxSpareServers - The
MaxSpareServersdirective allows you to specify the maximum number of spare child processes. It takes the following form:MaxSpareServers number
MaxSpareServers numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow This directive is used by thepreforkMPM only.Example 18.73. Using the MaxSpareServers directive
MaxSpareServers 20
MaxSpareServers 20Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MaxSpareThreads - The
MaxSpareThreadsdirective allows you to specify the maximum number of spare server threads. It takes the following form:MaxSpareThreads number
MaxSpareThreads numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow The number must be greater than or equal to the sum ofMinSpareThreadsandThreadsPerChild. This directive is used by theworkerMPM only.Example 18.74. Using the MaxSpareThreads directive
MaxSpareThreads 75
MaxSpareThreads 75Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MinSpareServers - The
MinSpareServersdirective allows you to specify the minimum number of spare child processes. It takes the following form:MinSpareServers number
MinSpareServers numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that a high number can create a heavy processing load on the server. This directive is used by thepreforkMPM only.Example 18.75. Using the MinSpareServers directive
MinSpareServers 5
MinSpareServers 5Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MinSpareThreads - The
MinSpareThreadsdirective allows you to specify the minimum number of spare server threads. It takes the following form:MinSpareThreads number
MinSpareThreads numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow This directive is used by theworkerMPM only.Example 18.76. Using the MinSpareThreads directive
MinSpareThreads 75
MinSpareThreads 75Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
StartServers - The
StartServersdirective allows you to specify the number of child processes to create when the service is started. It takes the following form:StartServers number
StartServers numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow Since the child processes are dynamically created and terminated according to the current traffic load, it is usually not necessary to change this value.Example 18.77. Using the StartServers directive
StartServers 8
StartServers 8Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
ThreadsPerChild - The
ThreadsPerChilddirective allows you to specify the number of threads a child process can create. It takes the following form:ThreadsPerChild number
ThreadsPerChild numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow This directive is used by theworkerMPM only.Example 18.78. Using the ThreadsPerChild directive
ThreadsPerChild 25
ThreadsPerChild 25Copy to Clipboard Copied! Toggle word wrap Toggle overflow
18.1.6. Working with Modules
httpd service is distributed along with a number of Dynamic Shared Objects (DSOs), which can be dynamically loaded or unloaded at runtime as necessary. By default, these modules are located in /usr/lib/httpd/modules/ on 32-bit and in /usr/lib64/httpd/modules/ on 64-bit systems.
18.1.6.1. Loading a Module
LoadModule directive as described in Section 18.1.5.1, “Common httpd.conf Directives”. Note that modules provided by a separate package often have their own configuration file in the /etc/httpd/conf.d/ directory.
Example 18.79. Loading the mod_ssl DSO
LoadModule ssl_module modules/mod_ssl.so
LoadModule ssl_module modules/mod_ssl.sohttpd service.
18.1.6.2. Writing a Module
root:
yum install httpd-devel
~]# yum install httpd-develapxs) utility required to compile a module.
apxs -i -a -c module_name.c
~]# apxs -i -a -c module_name.c18.1.7. Setting Up Virtual Hosts
/etc/httpd/conf/httpd.conf as an example, remove the hash sign (that is, #) from the beginning of each line, and customize the options according to your requirements as shown in Example 18.80, “Example virtual host configuration”.
Example 18.80. Example virtual host configuration
ServerName must be a valid DNS name assigned to the machine. The <VirtualHost> container is highly customizable, and accepts most of the directives available within the main server configuration. Directives that are not supported within this container include User and Group, which were replaced by SuexecUserGroup.
Note
Listen directive in the global settings section of the /etc/httpd/conf/httpd.conf file accordingly.
httpd service.
18.1.8. Setting Up an SSL Server
mod_ssl, a module that uses the OpenSSL toolkit to provide the SSL/TLS support, is commonly referred to as the SSL server. Red Hat Enterprise Linux also supports the use of Mozilla NSS as the TLS implementation. Support for Mozilla NSS is provided by the mod_nss module.
18.1.8.1. An Overview of Certificates and Security
| Web Browser | Link |
|---|---|
| Mozilla Firefox | Mozilla root CA list. |
| Opera | Information on root certificates used by Opera. |
| Internet Explorer | Information on root certificates used by Microsoft Windows. |
| Chromium | Information on root certificates used by the Chromium project. |
18.1.9. Enabling the mod_ssl Module
mod_ssl, you cannot have another application or module, such as mod_nss configured to use the same port. Port 443 is the default port for HTTPS.
mod_ssl module and the OpenSSL toolkit, install the mod_ssl and openssl packages. Enter the following command as root:
yum install mod_ssl openssl
~]# yum install mod_ssl opensslmod_ssl configuration file at /etc/httpd/conf.d/ssl.conf, which is included in the main Apache HTTP Server configuration file by default. For the module to be loaded, restart the httpd service as described in Section 18.1.4.3, “Restarting the Service”.
Important
SSL, if it is enabled, and using only TLSv1.1 or TLSv1.2. Backwards compatibility can be achieved using TLSv1.0. Many products Red Hat supports have the ability to use SSLv2 or SSLv3 protocols. However, the use of SSLv2 or SSLv3 is now strongly recommended against.
18.1.9.1. Enabling and Disabling SSL and TLS in mod_ssl
SSLProtocol directive in the “## SSL Global Context” section of the configuration file and removing it everywhere else, or edit the default entry under “# SSL Protocol support” in all “VirtualHost” sections. If you do not specify it in the per-domain VirtualHost section then it will inherit the settings from the global section. To make sure that a protocol version is being disabled the administrator should either only specify SSLProtocol in the “SSL Global Context” section, or specify it in all per-domain VirtualHost sections.
Procedure 18.1. Disable SSLv2 and SSLv3
- As
root, open the/etc/httpd/conf.d/ssl.conffile and search for all instances of theSSLProtocoldirective. By default, the configuration file contains one section that looks as follows:This section is within the VirtualHost section.vi /etc/httpd/conf.d/ssl.conf # SSL Protocol support: # List the enable protocol levels with which clients will be able to # connect. Disable SSLv2 access by default: SSLProtocol all -SSLv2
~]# vi /etc/httpd/conf.d/ssl.conf # SSL Protocol support: # List the enable protocol levels with which clients will be able to # connect. Disable SSLv2 access by default: SSLProtocol all -SSLv2Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the
SSLProtocolline as follows:Repeat this action for all VirtualHost sections. Save and close the file.# SSL Protocol support: # List the enable protocol levels with which clients will be able to connect. Disable SSLv2 access by default: SSLProtocol all -SSLv2 -SSLv3
# SSL Protocol support: # List the enable protocol levels with which clients will be able to # connect. Disable SSLv2 access by default: SSLProtocol all -SSLv2 -SSLv3Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Verify that all occurrences of the
SSLProtocoldirective have been changed as follows:This step is particularly important if you have more than the one default VirtualHost section.grep SSLProtocol /etc/httpd/conf.d/ssl.conf SSLProtocol all -SSLv2 -SSLv3
~]# grep SSLProtocol /etc/httpd/conf.d/ssl.conf SSLProtocol all -SSLv2 -SSLv3Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the Apache daemon as follows:Note that any sessions will be interrupted.
service httpd restart
~]# service httpd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 18.2. Disable All SSL and TLS Protocols Except TLS 1 and Up
- As
root, open the/etc/httpd/conf.d/ssl.conffile and search for all instances ofSSLProtocoldirective. By default the file contains one section that looks as follows:vi /etc/httpd/conf.d/ssl.conf # SSL Protocol support: # List the enable protocol levels with which clients will be able to # connect. Disable SSLv2 access by default: SSLProtocol all -SSLv2
~]# vi /etc/httpd/conf.d/ssl.conf # SSL Protocol support: # List the enable protocol levels with which clients will be able to # connect. Disable SSLv2 access by default: SSLProtocol all -SSLv2Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the
SSLProtocolline as follows:Save and close the file.# SSL Protocol support: # List the enable protocol levels with which clients will be able to connect. Disable SSLv2 access by default: SSLProtocol -all +TLSv1 +TLSv1.1 +TLSv1.2
# SSL Protocol support: # List the enable protocol levels with which clients will be able to # connect. Disable SSLv2 access by default: SSLProtocol -all +TLSv1 +TLSv1.1 +TLSv1.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Verify the change as follows:
grep SSLProtocol /etc/httpd/conf.d/ssl.conf SSLProtocol -all +TLSv1 +TLSv1.1 +TLSv1.2
~]# grep SSLProtocol /etc/httpd/conf.d/ssl.conf SSLProtocol -all +TLSv1 +TLSv1.1 +TLSv1.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the Apache daemon as follows:Note that any sessions will be interrupted.
service httpd restart
~]# service httpd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 18.3. Testing the Status of SSL and TLS Protocols
openssl s_client -connect command. The command has the following form: openssl s_client -connect hostname:port -protocol
openssl s_client -connect hostname:port -protocollocalhost as the host name. For example, to test the default port for secure HTTPS connections, port 443 to see if SSLv3 is enabled, issue a command as follows:
- The above output indicates that the handshake failed and therefore no cipher was negotiated.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The above output indicates that no failure of the handshake occurred and a set of ciphers was negotiated.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
openssl s_client command options are documented in the s_client(1) manual page.
18.1.10. Enabling the mod_nss Module
mod_nss, the HTTPS server cannot simultaneously use mod_ssl with its default settings as mod_ssl will use port 443 by default, however this is the default HTTPS port. If is recommend to remove the package if it is not required.
root:
yum remove mod_ssl
~]# yum remove mod_sslNote
mod_ssl is required for other purposes, modify the /etc/httpd/conf.d/ssl.conf file to use a port other than 443 to prevent mod_ssl conflicting with mod_nss when its port to listen on is changed to 443.
mod_nss and mod_ssl can only co-exist at the same time if they use unique ports. For this reason mod_nss by default uses 8443, but the default port for HTTPS is port 443. The port is specified by the Listen directive as well as in the VirtualHost name or address.
Procedure 18.4. Configuring mod_nss
- Install mod_nss as
root:yum install mod_nss
~]# yum install mod_nssCopy to Clipboard Copied! Toggle word wrap Toggle overflow This will create themod_nssconfiguration file at/etc/httpd/conf.d/nss.conf. The/etc/httpd/conf.d/directory is included in the main Apache HTTP Server configuration file by default. For the module to be loaded, restart thehttpdservice as described in Section 18.1.4.3, “Restarting the Service”. - As
root, open the/etc/httpd/conf.d/nss.conffile and search for all instances of theListendirective.Edit theListen 8443line as follows:PortListen 443
Listen 443Copy to Clipboard Copied! Toggle word wrap Toggle overflow 443is the default port forHTTPS. - Edit the default
VirtualHost _default_:8443line as follows:Edit any other non-default virtual host sections if they exist. Save and close the file.VirtualHost _default_:443
VirtualHost _default_:443Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Mozilla NSS stores certificates in a server certificate database indicated by the
NSSCertificateDatabasedirective in the/etc/httpd/conf.d/nss.conffile. By default the path is set to/etc/httpd/alias, the NSS database created during installation.To view the default NSS database, issue a command as follows:In the above command output,Copy to Clipboard Copied! Toggle word wrap Toggle overflow Server-Certis the defaultNSSNickname. The-Loption lists all the certificates, or displays information about a named certificate, in a certificate database. The-doption specifies the database directory containing the certificate and key database files. See thecertutil(1)man page for more command line options. - To configure mod_nss to use another database, edit the
NSSCertificateDatabaseline in the/etc/httpd/conf.d/nss.conffile. The default file has the following lines within the VirtualHost section.In the above command output,# Server Certificate Database: # The NSS security database directory that holds the certificates and # keys. The database consists of 3 files: cert8.db, key3.db and secmod.db. # Provide the directory that these files exist. NSSCertificateDatabase /etc/httpd/alias
# Server Certificate Database: # The NSS security database directory that holds the certificates and # keys. The database consists of 3 files: cert8.db, key3.db and secmod.db. # Provide the directory that these files exist. NSSCertificateDatabase /etc/httpd/aliasCopy to Clipboard Copied! Toggle word wrap Toggle overflow aliasis the default NSS database directory,/etc/httpd/alias/. - To apply a password to the default NSS certificate database, use the following command as
root:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Before deploying the HTTPS server, create a new certificate database using a certificate signed by a certificate authority (CA).
Example 18.81. Adding a Certificate to the Mozilla NSS database
Thecertutilcommand is used to add a CA certificate to the NSS database files:certutil -d /etc/httpd/nss-db-directory/ -A -n "CA_certificate" -t CT,, -a -i certificate.pem
certutil -d /etc/httpd/nss-db-directory/ -A -n "CA_certificate" -t CT,, -a -i certificate.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow The above command adds a CA certificate stored in a PEM-formatted file named certificate.pem. The-doption specifies the NSS database directory containing the certificate and key database files, the-noption sets a name for the certificate,-tCT,,means that the certificate is trusted to be used in TLS clients and servers. The-Aoption adds an existing certificate to a certificate database. If the database does not exist it will be created. The-aoption allows the use of ASCII format for input or output, and the-ioption passes thecertificate.peminput file to the command.See thecertutil(1)man page for more command line options. - The NSS database should be password protected to safeguard the private key.
Example 18.82. Setting_a_Password_for_a_Mozilla_NSS_database
Thecertutiltool can be used to set a password for an NSS database as follows:certutil -W -d /etc/httpd/nss-db-directory/
certutil -W -d /etc/httpd/nss-db-directory/Copy to Clipboard Copied! Toggle word wrap Toggle overflow For example, for the default database, issue a command asrootas follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure
mod_nssto use the NSS internal software token by changing the line with theNSSPassPhraseDialogdirective as follows:This is to avoid manual password entry on system start. The software token exists in the NSS database but you can also have a physical token containing your certificates.vi /etc/httpd/conf.d/nss.conf NSSPassPhraseDialog file:/etc/httpd/password.conf
~]# vi /etc/httpd/conf.d/nss.conf NSSPassPhraseDialog file:/etc/httpd/password.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If the SSL Server Certificate contained in the NSS database is an RSA certificate, make certain that the
NSSNicknameparameter is uncommented and matches the nickname displayed in step 4 above:vi /etc/httpd/conf.d/nss.conf NSSNickname Server-Cert
~]# vi /etc/httpd/conf.d/nss.conf NSSNickname Server-CertCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the SSL Server Certificate contained in the NSS database is an ECC certificate, make certain that theNSSECCNicknameparameter is uncommented and matches the nickname displayed in step 4 above:vi /etc/httpd/conf.d/nss.conf NSSECCNickname Server-Cert
~]# vi /etc/httpd/conf.d/nss.conf NSSECCNickname Server-CertCopy to Clipboard Copied! Toggle word wrap Toggle overflow Make certain that theNSSCertificateDatabaseparameter is uncommented and points to the NSS database directory displayed in step 4 or configured in step 5 above:Replacevi /etc/httpd/conf.d/nss.conf NSSCertificateDatabase /etc/httpd/alias
~]# vi /etc/httpd/conf.d/nss.conf NSSCertificateDatabase /etc/httpd/aliasCopy to Clipboard Copied! Toggle word wrap Toggle overflow /etc/httpd/aliaswith the path to the certificate database to be used. - Create the
/etc/httpd/password.conffile asroot:Add a line with the following form:vi /etc/httpd/password.conf
~]# vi /etc/httpd/password.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replacing password with the password that was applied to the NSS security databases in step 6 above.internal:password
internal:passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Apply the appropriate ownership and permissions to the
/etc/httpd/password.conffile:chgrp apache /etc/httpd/password.conf chmod 640 /etc/httpd/password.conf ls -l /etc/httpd/password.conf -rw-r-----. 1 root apache 10 Dec 4 17:13 /etc/httpd/password.conf
~]# chgrp apache /etc/httpd/password.conf ~]# chmod 640 /etc/httpd/password.conf ~]# ls -l /etc/httpd/password.conf -rw-r-----. 1 root apache 10 Dec 4 17:13 /etc/httpd/password.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To configure
mod_nssto use the NSS the software token in/etc/httpd/password.conf, edit/etc/httpd/conf.d/nss.confas follows:vi /etc/httpd/conf.d/nss.conf
~]# vi /etc/httpd/conf.d/nss.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the Apache server for the changes to take effect as described in Section 18.1.4.3, “Restarting the Service”
Important
SSL, if it is enabled, and using only TLSv1.1 or TLSv1.2. Backwards compatibility can be achieved using TLSv1.0. Many products Red Hat supports have the ability to use SSLv2 or SSLv3 protocols. However, the use of SSLv2 or SSLv3 is now strongly recommended against.
18.1.10.1. Enabling and Disabling SSL and TLS in mod_nss
NSSProtocol directive in the “## SSL Global Context” section of the configuration file and removing it everywhere else, or edit the default entry under “# SSL Protocol” in all “VirtualHost” sections. If you do not specify it in the per-domain VirtualHost section then it will inherit the settings from the global section. To make sure that a protocol version is being disabled the administrator should either only specify NSSProtocol in the “SSL Global Context” section, or specify it in all per-domain VirtualHost sections.
Procedure 18.5. Disable All SSL and TLS Protocols Except TLS 1 and Up in mod_nss
- As
root, open the/etc/httpd/conf.d/nss.conffile and search for all instances of theNSSProtocoldirective. By default, the configuration file contains one section that looks as follows:This section is within the VirtualHost section.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the
NSSProtocolline as follows:Repeat this action for all VirtualHost sections.# SSL Protocol: NSSProtocol TLSv1.0,TLSv1.1,TLSv1.2
# SSL Protocol: NSSProtocol TLSv1.0,TLSv1.1,TLSv1.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the
Listen 8443line as follows:Listen 443
Listen 443Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the default
VirtualHost _default_:8443line as follows:Edit any other non-default virtual host sections if they exist. Save and close the file.VirtualHost _default_:443
VirtualHost _default_:443Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Verify that all occurrences of the
NSSProtocoldirective have been changed as follows:This step is particularly important if you have more than one VirtualHost section.grep NSSProtocol /etc/httpd/conf.d/nss.conf # middle of a range may be excluded, the entry "NSSProtocol SSLv3,TLSv1.1" # is identical to the entry "NSSProtocol SSLv3,TLSv1.0,TLSv1.1". NSSProtocol TLSv1.0,TLSv1.1,TLSv1.2
~]# grep NSSProtocol /etc/httpd/conf.d/nss.conf # middle of a range may be excluded, the entry "NSSProtocol SSLv3,TLSv1.1" # is identical to the entry "NSSProtocol SSLv3,TLSv1.0,TLSv1.1". NSSProtocol TLSv1.0,TLSv1.1,TLSv1.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the Apache daemon as follows:Note that any sessions will be interrupted.
service httpd restart
~]# service httpd restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 18.6. Testing the Status of SSL and TLS Protocols in mod_nss
openssl s_client -connect command. Install the openssl package as root:
yum install openssl
~]# yum install opensslopenssl s_client -connect command has the following form: openssl s_client -connect hostname:port -protocol
openssl s_client -connect hostname:port -protocollocalhost as the host name. For example, to test the default port for secure HTTPS connections, port 443 to see if SSLv3 is enabled, issue a command as follows:
- The above output indicates that the handshake failed and therefore no cipher was negotiated.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The above output indicates that no failure of the handshake occurred and a set of ciphers was negotiated.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
openssl s_client command options are documented in the s_client(1) manual page.
18.1.11. Using an Existing Key and Certificate
- You are changing the IP address or domain name.Certificates are issued for a particular IP address and domain name pair. If one of these values changes, the certificate becomes invalid.
- You have a certificate from VeriSign, and you are changing the server software.VeriSign, a widely used certificate authority, issues certificates for a particular software product, IP address, and domain name. Changing the software product renders the certificate invalid.
/etc/pki/tls/private/ and /etc/pki/tls/certs/ directories respectively. You can do so by issuing the following commands as root:
mv key_file.key /etc/pki/tls/private/hostname.key mv certificate.crt /etc/pki/tls/certs/hostname.crt
~]# mv key_file.key /etc/pki/tls/private/hostname.key
~]# mv certificate.crt /etc/pki/tls/certs/hostname.crt/etc/httpd/conf.d/ssl.conf configuration file:
SSLCertificateFile /etc/pki/tls/certs/hostname.crt SSLCertificateKeyFile /etc/pki/tls/private/hostname.key
SSLCertificateFile /etc/pki/tls/certs/hostname.crt
SSLCertificateKeyFile /etc/pki/tls/private/hostname.keyhttpd service as described in Section 18.1.4.3, “Restarting the Service”.
Example 18.83. Using a key and certificate from the Red Hat Secure Web Server
mv /etc/httpd/conf/httpsd.key /etc/pki/tls/private/penguin.example.com.key mv /etc/httpd/conf/httpsd.crt /etc/pki/tls/certs/penguin.example.com.crt
~]# mv /etc/httpd/conf/httpsd.key /etc/pki/tls/private/penguin.example.com.key
~]# mv /etc/httpd/conf/httpsd.crt /etc/pki/tls/certs/penguin.example.com.crt18.1.12. Generating a New Key and Certificate
root:
yum install crypto-utils mod_ssl
~]# yum install crypto-utils mod_sslImportant
openssl req -x509 -new -set_serial number -key hostname.key -out hostname.crt
~]# openssl req -x509 -new -set_serial number -key hostname.key -out hostname.crtNote
root:
rm /etc/pki/tls/private/hostname.key
~]# rm /etc/pki/tls/private/hostname.keygenkey command as root, followed by the appropriate host name (for example, penguin.example.com):
genkey hostname
~]# genkey hostname- Review the target locations in which the key and certificate will be stored.
Figure 18.1. Running the genkey utility
Use the Tab key to select the button, and press Enter to proceed to the next screen. - Using the up and down arrow keys, select a suitable key size. Note that while a larger key increases the security, it also increases the response time of your server. The NIST recommends using
2048 bits. See NIST Special Publication 800-131A.Figure 18.2. Selecting the key size
Once finished, use the Tab key to select the button, and press Enter to initiate the random bits generation process. Depending on the selected key size, this may take some time. - Decide whether you want to send a certificate request to a certificate authority.
Figure 18.3. Generating a certificate request
Use the Tab key to select to compose a certificate request, or to generate a self-signed certificate. Then press Enter to confirm your choice. - Using the Spacebar key, enable (
[*]) or disable ([ ]) the encryption of the private key.Figure 18.4. Encrypting the private key
Use the Tab key to select the button, and press Enter to proceed to the next screen. - If you have enabled the private key encryption, enter an adequate passphrase. Note that for security reasons, it is not displayed as you type, and it must be at least five characters long.
Figure 18.5. Entering a passphrase
Use the Tab key to select the button, and press Enter to proceed to the next screen.Important
Entering the correct passphrase is required in order for the server to start. If you lose it, you will need to generate a new key and certificate. - Customize the certificate details.
Figure 18.6. Specifying certificate information
Use the Tab key to select the button, and press Enter to finish the key generation. - If you have previously enabled the certificate request generation, you will be prompted to send it to a certificate authority.
Figure 18.7. Instructions on how to send a certificate request
Press Enter to return to a shell prompt.
/etc/httpd/conf.d/ssl.conf configuration file:
SSLCertificateFile /etc/pki/tls/certs/hostname.crt SSLCertificateKeyFile /etc/pki/tls/private/hostname.key
SSLCertificateFile /etc/pki/tls/certs/hostname.crt
SSLCertificateKeyFile /etc/pki/tls/private/hostname.keyhttpd service as described in Section 18.1.4.3, “Restarting the Service”, so that the updated configuration is loaded.
18.1.13. Configure the Firewall for HTTP and HTTPS Using the Command Line
HTTP and HTTPS traffic by default. To enable the system to act as a web server, enable ports and protocols as required. The default port for HTTP is 80 and the default port for HTTPS is 443. In both cases the TCP should be allowed to pass through the firewall.
80 for HTTP using the command line, issue the following command as root:
lokkit --port=80:tcp --update
~]# lokkit --port=80:tcp --update--disabled option. Active connections will be terminated and time out on the initiating machine. Use the lokkit --help command to view the built in help.
443 for HTTPS using the command line, issue the following command as root:
lokkit --port=443:tcp --update
~]# lokkit --port=443:tcp --update--disabled option. Active connections will be terminated and time out on the initiating machine. See the /etc/services file for list of services and their associated ports.
/etc/sysconfig/system-config-firewall file thoroughly after editing. To apply the settings in /etc/sysconfig/system-config-firewall, issue the following command as root:
lokkit --update
~]# lokkit --updateHTTPS to pass through the firewall, by editing the configuration file, become the root user and add the following line to /etc/sysconfig/system-config-firewall:
--port=443:tcp
--port=443:tcp/etc/sysconfig/system-config-firewall, issue the following command as root:
lokkit --update
~]# lokkit --update18.1.13.1. Checking Network Access for Incoming HTTPS and HTTPS Using the Command Line
root:
less /etc/sysconfig/system-config-firewall # Configuration file for system-config-firewall --enabled --service=ssh
~]# less /etc/sysconfig/system-config-firewall
# Configuration file for system-config-firewall
--enabled
--service=sshHTTP and HTTPS have not been allowed to pass through.
HTTP is enabled, the following line appears as output in addition to the lines shown above:
--port=80:tcp
--port=80:tcpHTTP traffic for clients, issue the following command as root:
iptables -L -n | grep 'tcp.*80' ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:80
~]# iptables -L -n | grep 'tcp.*80'
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:80HTTPS is enabled, the following line appears as output in addition to the lines shown above:
--port=443:tcp
--port=443:tcpHTTPS traffic for clients, issue the following command as root:
iptables -L -n | grep 'tcp.*443' ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:443
~]# iptables -L -n | grep 'tcp.*443'
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:44318.1.14. Additional Resources
Installed Documentation
httpd(8)— The manual page for thehttpdservice containing the complete list of its command-line options.genkey(1)— The manual page forgenkeyutility, provided by the crypto-utils package.
Installable Documentation
- http://localhost/manual/ — The official documentation for the Apache HTTP Server with the full description of its directives and available modules. Note that in order to access this documentation, you must have the httpd-manual package installed, and the web server must be running.Before accessing the documentation, issue the following commands as
root:yum install httpd-manual service httpd graceful
~]# yum install httpd-manual ~]# service httpd gracefulCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Online Documentation
- http://httpd.apache.org/ — The official website for the Apache HTTP Server with documentation on all the directives and default modules.
- http://www.openssl.org/ — The OpenSSL home page containing further documentation, frequently asked questions, links to the mailing lists, and other useful resources.
Chapter 19. Mail Servers
19.1. Email Protocols
19.1.1. Mail Transport Protocols
19.1.1.1. SMTP
19.1.2. Mail Access Protocols
19.1.2.1. POP
Note
root:
yum install dovecot
~]# yum install dovecotPOP server, email messages are downloaded by email client applications. By default, most POP email clients are automatically configured to delete the message on the email server after it has been successfully transferred, however this setting usually can be changed.
POP is fully compatible with important Internet messaging standards, such as Multipurpose Internet Mail Extensions (MIME), which allow for email attachments.
POP works best for users who have one system on which to read email. It also works well for users who do not have a persistent connection to the Internet or the network containing the mail server. Unfortunately for those with slow network connections, POP requires client programs upon authentication to download the entire content of each message. This can take a long time if any messages have large attachments.
POP protocol is POP3.
POP protocol variants:
- APOP —
POP3withMD5authentication. An encoded hash of the user's password is sent from the email client to the server rather than sending an unencrypted password. - KPOP —
POP3with Kerberos authentication. - RPOP —
POP3withRPOPauthentication. This uses a per-user ID, similar to a password, to authenticate POP requests. However, this ID is not encrypted, soRPOPis no more secure than standardPOP.
pop3s service, or by using the stunnel application. For more information on securing email communication, see Section 19.5.1, “Securing Communication”.
19.1.2.2. IMAP
IMAP server under Red Hat Enterprise Linux is Dovecot and is provided by the dovecot package. See Section 19.1.2.1, “POP” for information on how to install Dovecot.
IMAP mail server, email messages remain on the server where users can read or delete them. IMAP also allows client applications to create, rename, or delete mail directories on the server to organize and store email.
IMAP is particularly useful for users who access their email using multiple machines. The protocol is also convenient for users connecting to the mail server via a slow connection, because only the email header information is downloaded for messages until opened, saving bandwidth. The user also has the ability to delete messages without viewing or downloading them.
IMAP client applications are capable of caching copies of messages locally, so the user can browse previously read messages when not directly connected to the IMAP server.
IMAP, like POP, is fully compatible with important Internet messaging standards, such as MIME, which allow for email attachments.
SSL encryption for client authentication and data transfer sessions. This can be enabled by using the imaps service, or by using the stunnel program. For more information on securing email communication, see Section 19.5.1, “Securing Communication”.
19.1.2.3. Dovecot
imap-login and pop3-login processes which implement the IMAP and POP3 protocols are spawned by the master dovecot daemon included in the dovecot package. The use of IMAP and POP is configured through the /etc/dovecot/dovecot.conf configuration file; by default dovecot runs IMAP and POP3 together with their secure versions using SSL. To configure dovecot to use POP, complete the following steps:
- Edit the
/etc/dovecot/dovecot.confconfiguration file to make sure theprotocolsvariable is uncommented (remove the hash sign (#) at the beginning of the line) and contains thepop3argument. For example:protocols = imap pop3 lmtp
protocols = imap pop3 lmtpCopy to Clipboard Copied! Toggle word wrap Toggle overflow When theprotocolsvariable is left commented out,dovecotwill use the default values as described above. - Make the change operational for the current session by running the following command:
service dovecot restart
~]# service dovecot restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Make the change operational after the next reboot by running the command:
chkconfig dovecot on
~]# chkconfig dovecot onCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
Please note thatdovecotonly reports that it started theIMAPserver, but also starts thePOP3server.
SMTP, both IMAP and POP3 require connecting clients to authenticate using a user name and password. By default, passwords for both protocols are passed over the network unencrypted.
SSL on dovecot:
- Edit the
/etc/dovecot/conf.d/10-ssl.confconfiguration to make sure thessl_cipher_listvariable is uncommented, and append:!SSLv3:ssl_cipher_list = ALL:!LOW:!SSLv2:!EXP:!aNULL:!SSLv3
ssl_cipher_list = ALL:!LOW:!SSLv2:!EXP:!aNULL:!SSLv3Copy to Clipboard Copied! Toggle word wrap Toggle overflow These values ensure thatdovecotavoids SSL versions 2 and also 3, which are both known to be insecure. This is due to the vulnerability described in POODLE: SSLv3 vulnerability (CVE-2014-3566). See Resolution for POODLE SSL 3.0 vulnerability (CVE-2014-3566) in Postfix and Dovecot for details. - Edit the
/etc/pki/dovecot/dovecot-openssl.cnfconfiguration file as you prefer. However, in a typical installation, this file does not require modification. - Rename, move or delete the files
/etc/pki/dovecot/certs/dovecot.pemand/etc/pki/dovecot/private/dovecot.pem. - Execute the
/usr/libexec/dovecot/mkcert.shscript which creates thedovecotself signed certificates. These certificates are copied in the/etc/pki/dovecot/certsand/etc/pki/dovecot/privatedirectories. To implement the changes, restartdovecot:service dovecot restart
~]# service dovecot restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
dovecot can be found online at http://www.dovecot.org.
19.2. Email Program Classifications
19.2.1. Mail Transport Agent
SMTP. A message may involve several MTAs as it moves to its intended destination.
19.2.2. Mail Delivery Agent
mail or Procmail.
19.2.3. Mail User Agent
POP or IMAP protocols, setting up mailboxes to store messages, and sending outbound messages to an MTA.
19.3. Mail Transport Agents
alternatives --config mta
~]# alternatives --config mtachkconfig service_name on | off
chkconfig service_name on | off19.3.1. Postfix
19.3.1.1. The Default Postfix Installation
/usr/sbin/postfix. This daemon launches all related processes needed to handle mail delivery.
/etc/postfix/ directory. The following is a list of the more commonly used files:
access— Used for access control, this file specifies which hosts are allowed to connect to Postfix.main.cf— The global Postfix configuration file. The majority of configuration options are specified in this file.master.cf— Specifies how Postfix interacts with various processes to accomplish mail delivery.transport— Maps email addresses to relay hosts.
aliases file can be found in the /etc/ directory. This file is shared between Postfix and Sendmail. It is a configurable list required by the mail protocol that describes user ID aliases.
Important
/etc/postfix/main.cf file does not allow Postfix to accept network connections from a host other than the local computer. For instructions on configuring Postfix as a server for other clients, see Section 19.3.1.2, “Basic Postfix Configuration”.
postfix service after changing any options in the configuration files under the /etc/postfix directory in order for those changes to take effect:
service postfix restart
~]# service postfix restart19.3.1.2. Basic Postfix Configuration
root to enable mail delivery for other hosts on the network:
- Edit the
/etc/postfix/main.cffile with a text editor, such asvi. - Uncomment the
mydomainline by removing the hash sign (#), and replace domain.tld with the domain the mail server is servicing, such asexample.com. - Uncomment the
myorigin = $mydomainline. - Uncomment the
myhostnameline, and replace host.domain.tld with the host name for the machine. - Uncomment the
mydestination = $myhostname, localhost.$mydomainline. - Uncomment the
mynetworksline, and replace 168.100.189.0/28 with a valid network setting for hosts that can connect to the server. - Uncomment the
inet_interfaces = allline. - Comment the
inet_interfaces = localhostline. - Restart the
postfixservice.
/etc/postfix/main.cf configuration file. Additional resources including information about Postfix configuration, SpamAssassin integration, or detailed descriptions of the /etc/postfix/main.cf parameters are available online at http://www.postfix.org/.
19.3.1.2.1. Configuring Postfix to Use Transport Layer Security
Important
SSL, if it is enabled, and using only TLSv1.1 or TLSv1.2. Backwards compatibility can be achieved using TLSv1.0. Many products Red Hat supports have the ability to use SSLv2 or SSLv3 protocols. However, the use of SSLv2 or SSLv3 is now strongly recommended against.
19.3.1.3. Using Postfix with LDAP
LDAP directory as a source for various lookup tables (e.g.: aliases, virtual, canonical, etc.). This allows LDAP to store hierarchical user information and Postfix to only be given the result of LDAP queries when needed. By not storing this information locally, administrators can easily maintain it.
19.3.1.3.1. The /etc/aliases lookup example
LDAP to look up the /etc/aliases file. Make sure your /etc/postfix/main.cf file contains the following:
alias_maps = hash:/etc/aliases, ldap:/etc/postfix/ldap-aliases.cf
alias_maps = hash:/etc/aliases, ldap:/etc/postfix/ldap-aliases.cf/etc/postfix/ldap-aliases.cf file if you do not have one already and make sure it contains the following:
server_host = ldap.example.com search_base = dc=example, dc=com
server_host = ldap.example.com
search_base = dc=example, dc=comldap.example.com, example, and com are parameters that need to be replaced with specification of an existing available LDAP server.
Note
/etc/postfix/ldap-aliases.cf file can specify various parameters, including parameters that enable LDAP SSL and STARTTLS. For more information, see the ldap_table(5) man page.
LDAP, see Section 20.1, “OpenLDAP”.
19.3.2. Sendmail
SMTP protocol. However, Sendmail is highly configurable, allowing control over almost every aspect of how email is handled, including the protocol used. Many system administrators elect to use Sendmail as their MTA due to its power and scalability.
19.3.2.1. Purpose and Limitations
POP or IMAP, to download their messages to their local machine. Or, they may prefer a Web interface to gain access to their mailbox. These other applications can work in conjunction with Sendmail, but they actually exist for different reasons and can operate separately from one another.
19.3.2.2. The Default Sendmail Installation
root:
yum install sendmail
~]# yum install sendmailroot:
yum install sendmail-cf
~]# yum install sendmail-cf/usr/sbin/sendmail.
/etc/mail/sendmail.cf. Avoid editing the sendmail.cf file directly. To make configuration changes to Sendmail, edit the /etc/mail/sendmail.mc file, back up the original /etc/mail/sendmail.cf file, and use the following alternatives to generate a new configuration file:
- Use the included makefile in
/etc/mail/to create a new/etc/mail/sendmail.cfconfiguration file:make all -C /etc/mail/
~]# make all -C /etc/mail/Copy to Clipboard Copied! Toggle word wrap Toggle overflow All other generated files in/etc/mail(db files) will be regenerated if needed. The old makemap commands are still usable. The make command is automatically used whenever you start or restart thesendmailservice. - Alternatively you may use the
m4macro processor to create a new/etc/mail/sendmail.cf. Them4macro processor is not installed by default. Before using it to create/etc/mail/sendmail.cf, install the m4 package as root:yum install m4
~]# yum install m4Copy to Clipboard Copied! Toggle word wrap Toggle overflow
/etc/mail/ directory including:
access— Specifies which systems can use Sendmail for outbound email.domaintable— Specifies domain name mapping.local-host-names— Specifies aliases for the host.mailertable— Specifies instructions that override routing for particular domains.virtusertable— Specifies a domain-specific form of aliasing, allowing multiple virtual domains to be hosted on one machine.
/etc/mail/, such as access, domaintable, mailertable and virtusertable, must actually store their information in database files before Sendmail can use any configuration changes. To include any changes made to these configurations in their database files, run the following command, as root:
makemap hash /etc/mail/<name> < /etc/mail/<name>
~]# makemap hash /etc/mail/<name> < /etc/mail/<name>sendmail service for the changes to take effect by running:
service sendmail restart
~]# service sendmail restartexample.com domain delivered to bob@other-example.com, add the following line to the virtusertable file:
@example.com bob@other-example.com
@example.com bob@other-example.comvirtusertable.db file must be updated:
makemap hash /etc/mail/virtusertable < /etc/mail/virtusertable
~]# makemap hash /etc/mail/virtusertable < /etc/mail/virtusertablevirtusertable.db file containing the new configuration.
19.3.2.3. Common Sendmail Configuration Changes
/etc/mail/sendmail.cf file.
Warning
sendmail.cf file, create a backup copy.
/etc/mail/sendmail.mc file as root. Once you are finished, restart the sendmail service and, if the m4 package is installed, the m4 macro processor will automatically generate a new sendmail.cf configuration file:
service sendmail restart
~]# service sendmail restartImportant
sendmail.cf file does not allow Sendmail to accept network connections from any host other than the local computer. To configure Sendmail as a server for other clients, edit the /etc/mail/sendmail.mc file, and either change the address specified in the Addr= option of the DAEMON_OPTIONS directive from 127.0.0.1 to the IP address of an active network device or comment out the DAEMON_OPTIONS directive all together by placing dnl at the beginning of the line. When finished, regenerate /etc/mail/sendmail.cf by restarting the service
service sendmail restart
~]# service sendmail restartSMTP-only sites. However, it does not work for UUCP (UNIX-to-UNIX Copy Protocol) sites. If using UUCP mail transfers, the /etc/mail/sendmail.mc file must be reconfigured and a new /etc/mail/sendmail.cf file must be generated.
/usr/share/sendmail-cf/README file before editing any files in the directories under the /usr/share/sendmail-cf directory, as they can affect the future configuration of the /etc/mail/sendmail.cf file.
19.3.2.4. Masquerading
mail.example.com that handles all of their email and assigns a consistent return address to all outgoing mail.
user@example.com instead of user@host.example.com.
/etc/mail/sendmail.mc:
sendmail.cf file using the m4 macro processor, this configuration makes all mail from inside the network appear as if it were sent from example.com.
19.3.2.5. Stopping Spam
SMTP messages, also called relaying, has been disabled by default since Sendmail version 8.9. Before this change occurred, Sendmail directed the mail host (x.edu) to accept messages from one party (y.com) and sent them to a different party (z.net). Now, however, Sendmail must be configured to permit any domain to relay mail through the server. To configure relay domains, edit the /etc/mail/relay-domains file and restart Sendmail
service sendmail restart
~]# service sendmail restart/etc/mail/access file can be used to prevent connections from unwanted hosts. The following example illustrates how this file can be used to both block and specifically allow access to the Sendmail server:
badspammer.com ERROR:550 "Go away and do not spam us anymore" tux.badspammer.com OK 10.0 RELAY
badspammer.com ERROR:550 "Go away and do not spam us anymore" tux.badspammer.com OK 10.0 RELAYbadspammer.com is blocked with a 550 RFC-821 compliant error code, with a message sent back. Email sent from the tux.badspammer.com sub-domain, is accepted. The last line shows that any email sent from the 10.0.*.* network can be relayed through the mail server.
/etc/mail/access.db file is a database, use the makemap command to update any changes. Do this using the following command as root:
makemap hash /etc/mail/access < /etc/mail/access
~]# makemap hash /etc/mail/access < /etc/mail/accessSMTP servers store information about an email's journey in the message header. As the message travels from one MTA to another, each puts in a Received header above all the other Received headers. It is important to note that this information may be altered by spammers.
/usr/share/sendmail-cf/README file for more information and examples.
19.3.2.6. Using Sendmail with LDAP
LDAP is a very quick and powerful way to find specific information about a particular user from a much larger group. For example, an LDAP server can be used to look up a particular email address from a common corporate directory by the user's last name. In this kind of implementation, LDAP is largely separate from Sendmail, with LDAP storing the hierarchical user information and Sendmail only being given the result of LDAP queries in pre-addressed email messages.
LDAP, where it uses LDAP to replace separately maintained files, such as /etc/aliases and /etc/mail/virtusertables, on different mail servers that work together to support a medium- to enterprise-level organization. In short, LDAP abstracts the mail routing level from Sendmail and its separate configuration files to a powerful LDAP cluster that can be leveraged by many different applications.
LDAP. To extend the Sendmail server using LDAP, first get an LDAP server, such as OpenLDAP, running and properly configured. Then edit the /etc/mail/sendmail.mc to include the following:
LDAPROUTE_DOMAIN('yourdomain.com')dnl
FEATURE('ldap_routing')dnl
LDAPROUTE_DOMAIN('yourdomain.com')dnl
FEATURE('ldap_routing')dnlNote
LDAP. The configuration can differ greatly from this depending on the implementation of LDAP, especially when configuring several Sendmail machines to use a common LDAP server.
/usr/share/sendmail-cf/README for detailed LDAP routing configuration instructions and examples.
/etc/mail/sendmail.cf file by running the m4 macro processor and again restarting Sendmail. See Section 19.3.2.3, “Common Sendmail Configuration Changes” for instructions.
LDAP, see Section 20.1, “OpenLDAP”.
19.3.3. Fetchmail
POP3 and IMAP. It can even forward email messages to an SMTP server, if necessary.
Note
root:
yum install fetchmail
~]# yum install fetchmail.fetchmailrc file in the user's home directory. If it does not already exist, create the .fetchmailrc file in your home directory
.fetchmailrc file, Fetchmail checks for email on a remote server and downloads it. It then delivers it to port 25 on the local machine, using the local MTA to place the email in the correct user's spool file. If Procmail is available, it is launched to filter the email and place it in a mailbox so that it can be read by an MUA.
19.3.3.1. Fetchmail Configuration Options
.fetchmailrc file is much easier. Place any desired configuration options in the .fetchmailrc file for those options to be used each time the fetchmail command is issued. It is possible to override these at the time Fetchmail is run by specifying that option on the command line.
.fetchmailrc file contains three classes of configuration options:
- global options — Gives Fetchmail instructions that control the operation of the program or provide settings for every connection that checks for email.
- server options — Specifies necessary information about the server being polled, such as the host name, as well as preferences for specific email servers, such as the port to check or number of seconds to wait before timing out. These options affect every user using that server.
- user options — Contains information, such as user name and password, necessary to authenticate and check for email using a specified email server.
.fetchmailrc file, followed by one or more server options, each of which designate a different email server that Fetchmail should check. User options follow server options for each user account checking that email server. Like server options, multiple user options may be specified for use with a particular server as well as to check multiple email accounts on the same server.
.fetchmailrc file by the use of a special option verb, poll or skip, that precedes any of the server information. The poll action tells Fetchmail to use this server option when it is run, which checks for email using the specified user options. Any server options after a skip action, however, are not checked unless this server's host name is specified when Fetchmail is invoked. The skip option is useful when testing configurations in the .fetchmailrc file because it only checks skipped servers when specifically invoked, and does not affect any currently working configurations.
.fetchmailrc file:
postmaster option) and all email errors are sent to the postmaster instead of the sender (bouncemail option). The set action tells Fetchmail that this line contains a global option. Then, two email servers are specified, one set to check using POP3, the other for trying various protocols to find one that works. Two users are checked using the second server option, but all email found for any user is sent to user1's mail spool. This allows multiple mailboxes to be checked on multiple servers, while appearing in a single MUA inbox. Each user's specific information begins with the user action.
Note
.fetchmailrc file. Omitting the with password '<password>' section causes Fetchmail to ask for a password when it is launched.
fetchmail man page explains each option in detail, but the most common ones are listed in the following three sections.
19.3.3.2. Global Options
set action.
daemon seconds— Specifies daemon-mode, where Fetchmail stays in the background. Replace seconds with the number of seconds Fetchmail is to wait before polling the server.postmaster— Specifies a local user to send mail to in case of delivery problems.syslog— Specifies the log file for errors and status messages. By default, this is/var/log/maillog.
19.3.3.3. Server Options
.fetchmailrc after a poll or skip action.
auth auth-type— Replace auth-type with the type of authentication to be used. By default,passwordauthentication is used, but some protocols support other types of authentication, includingkerberos_v5,kerberos_v4, andssh. If theanyauthentication type is used, Fetchmail first tries methods that do not require a password, then methods that mask the password, and finally attempts to send the password unencrypted to authenticate to the server.interval number— Polls the specified server everynumberof times that it checks for email on all configured servers. This option is generally used for email servers where the user rarely receives messages.port port-number— Replace port-number with the port number. This value overrides the default port number for the specified protocol.proto protocol— Replace protocol with the protocol, such aspop3orimap, to use when checking for messages on the server.timeout seconds— Replace seconds with the number of seconds of server inactivity after which Fetchmail gives up on a connection attempt. If this value is not set, a default of300seconds is used.
19.3.3.4. User Options
user option (defined below).
fetchall— Orders Fetchmail to download all messages in the queue, including messages that have already been viewed. By default, Fetchmail only pulls down new messages.fetchlimit number— Replace number with the number of messages to be retrieved before stopping.flush— Deletes all previously viewed messages in the queue before retrieving new messages.limit max-number-bytes— Replace max-number-bytes with the maximum size in bytes that messages are allowed to be when retrieved by Fetchmail. This option is useful with slow network links, when a large message takes too long to download.password 'password'— Replace password with the user's password.preconnect "command"— Replace command with a command to be executed before retrieving messages for the user.postconnect "command"— Replace command with a command to be executed after retrieving messages for the user.ssl— Activates SSL encryption. At the time of writing, the default action is to use the best available fromSSL2,SSL3,SSL23,TLS1,TLS1.1andTLS1.2. Note thatSSL2is considered obsolete and due to the POODLE: SSLv3 vulnerability (CVE-2014-3566),SSLv3should not be used. However there is no way to force the use of TLS1 or newer, therefore ensure the mail server being connected to is configured not to useSSLv2andSSLv3. Usestunnelwhere the server cannot be configured not to useSSLv2andSSLv3.sslproto— Defines allowed SSL or TLS protocols. Possible values areSSL2,SSL3,SSL23, andTLS1. The default value, ifsslprotois omitted, unset, or set to an invalid value, isSSL23. The default action is to use the best fromSSLv3,TLSv1,TLS1.1andTLS1.2. Note that setting any other value for SSL or TLS will disable all the other protocols. Due to the POODLE: SSLv3 vulnerability (CVE-2014-3566), it is recommend to omit this option, or set it toSSLv23, and configure the corresponding mail server not to useSSLv2andSSLv3. Usestunnelwhere the server cannot be configured not to useSSLv2andSSLv3.user "username"— Replace username with the username used by Fetchmail to retrieve messages. This option must precede all other user options.
19.3.3.5. Fetchmail Command Options
fetchmail command mirror the .fetchmailrc configuration options. In this way, Fetchmail may be used with or without a configuration file. These options are not used on the command line by most users because it is easier to leave them in the .fetchmailrc file.
fetchmail command with other options for a particular purpose. It is possible to issue command options to temporarily override a .fetchmailrc setting that is causing an error, as any options specified at the command line override configuration file options.
19.3.3.6. Informational or Debugging Options
fetchmail command can supply important information.
--configdump— Displays every possible option based on information from.fetchmailrcand Fetchmail defaults. No email is retrieved for any users when using this option.-s— Executes Fetchmail in silent mode, preventing any messages, other than errors, from appearing after thefetchmailcommand.-v— Executes Fetchmail in verbose mode, displaying every communication between Fetchmail and remote email servers.-V— Displays detailed version information, lists its global options, and shows settings to be used with each user, including the email protocol and authentication method. No email is retrieved for any users when using this option.
19.3.3.7. Special Options
.fetchmailrc file.
-a— Fetchmail downloads all messages from the remote email server, whether new or previously viewed. By default, Fetchmail only downloads new messages.-k— Fetchmail leaves the messages on the remote email server after downloading them. This option overrides the default behavior of deleting messages after downloading them.-l max-number-bytes— Fetchmail does not download any messages over a particular size and leaves them on the remote email server.--quit— Quits the Fetchmail daemon process.
.fetchmailrc options can be found in the fetchmail man page.
19.3.4. Mail Transport Agent (MTA) Configuration
/bin/mail command to send email containing log messages to the root user of the local system.
19.4. Mail Delivery Agents
mail. Both of the applications are considered LDAs and both move email from the MTA's spool file into the user's mailbox. However, Procmail provides a robust filtering system.
mail command, consult its man page (man mail).
/etc/procmailrc or of a ~/.procmailrc file (also called an rc file) in the user's home directory invokes Procmail whenever an MTA receives a new message.
rc files exist in the /etc/ directory and no .procmailrc files exist in any user's home directory. Therefore, to use Procmail, each user must construct a .procmailrc file with specific environment variables and rules.
rc file. If a message matches a recipe, then the email is placed in a specified file, is deleted, or is otherwise processed.
/etc/procmailrc file and rc files in the /etc/procmailrcs directory for default, system-wide, Procmail environmental variables and recipes. Procmail then searches for a .procmailrc file in the user's home directory. Many users also create additional rc files for Procmail that are referred to within the .procmailrc file in their home directory.
19.4.1. Procmail Configuration
~/.procmailrc file in the following format:
env-variable="value"
env-variable="value"env-variable is the name of the variable and value defines the variable.
DEFAULT— Sets the default mailbox where messages that do not match any recipes are placed.The defaultDEFAULTvalue is the same as$ORGMAIL.INCLUDERC— Specifies additionalrcfiles containing more recipes for messages to be checked against. This breaks up the Procmail recipe lists into individual files that fulfill different roles, such as blocking spam and managing email lists, that can then be turned off or on by using comment characters in the user's~/.procmailrcfile.For example, lines in a user's~/.procmailrcfile may look like this:MAILDIR=$HOME/Msgs INCLUDERC=$MAILDIR/lists.rc INCLUDERC=$MAILDIR/spam.rc
MAILDIR=$HOME/Msgs INCLUDERC=$MAILDIR/lists.rc INCLUDERC=$MAILDIR/spam.rcCopy to Clipboard Copied! Toggle word wrap Toggle overflow To turn off Procmail filtering of email lists but leaving spam control in place, comment out the firstINCLUDERCline with a hash sign (#). Note that it uses paths relative to the current directory.LOCKSLEEP— Sets the amount of time, in seconds, between attempts by Procmail to use a particular lockfile. The default is8seconds.LOCKTIMEOUT— Sets the amount of time, in seconds, that must pass after a lockfile was last modified before Procmail assumes that the lockfile is old and can be deleted. The default is1024seconds.LOGFILE— The file to which any Procmail information or error messages are written.MAILDIR— Sets the current working directory for Procmail. If set, all other Procmail paths are relative to this directory.ORGMAIL— Specifies the original mailbox, or another place to put the messages if they cannot be placed in the default or recipe-required location.By default, a value of/var/spool/mail/$LOGNAMEis used.SUSPEND— Sets the amount of time, in seconds, that Procmail pauses if a necessary resource, such as swap space, is not available.SWITCHRC— Allows a user to specify an external file containing additional Procmail recipes, much like theINCLUDERCoption, except that recipe checking is actually stopped on the referring configuration file and only the recipes on theSWITCHRC-specified file are used.VERBOSE— Causes Procmail to log more information. This option is useful for debugging.
LOGNAME, the login name; HOME, the location of the home directory; and SHELL, the default shell.
procmailrc man page.
19.4.2. Procmail Recipes
flags section specifies that a lockfile is created for this message. If a lockfile is created, the name can be specified by replacing lockfile-name.
*) can further control the condition.
action-to-perform argument specifies the action taken when the message matches one of the conditions. There can only be one action per recipe. In many cases, the name of a mailbox is used here to direct matching messages into that file, effectively sorting the email. Special action characters may also be used before the action is specified. See Section 19.4.2.4, “Special Conditions and Actions” for more information.
19.4.2.1. Delivering vs. Non-Delivering Recipes
{ }, that are performed on messages which match the recipe's conditions. Nesting blocks can be nested inside one another, providing greater control for identifying and performing actions on messages.
19.4.2.2. Flags
A— Specifies that this recipe is only used if the previous recipe without anAoraflag also matched this message.a— Specifies that this recipe is only used if the previous recipe with anAoraflag also matched this message and was successfully completed.B— Parses the body of the message and looks for matching conditions.b— Uses the body in any resulting action, such as writing the message to a file or forwarding it. This is the default behavior.c— Generates a carbon copy of the email. This is useful with delivering recipes, since the required action can be performed on the message and a copy of the message can continue being processed in thercfiles.D— Makes theegrepcomparison case-sensitive. By default, the comparison process is not case-sensitive.E— While similar to theAflag, the conditions in the recipe are only compared to the message if the immediately preceding recipe without anEflag did not match. This is comparable to an else action.e— The recipe is compared to the message only if the action specified in the immediately preceding recipe fails.f— Uses the pipe as a filter.H— Parses the header of the message and looks for matching conditions. This is the default behavior.h— Uses the header in a resulting action. This is the default behavior.w— Tells Procmail to wait for the specified filter or program to finish, and reports whether or not it was successful before considering the message filtered.W— Is identical towexcept that "Program failure" messages are suppressed.
procmailrc man page.
19.4.2.3. Specifying a Local Lockfile
:) after any flags on a recipe's first line. This creates a local lockfile based on the destination file name plus whatever has been set in the LOCKEXT global environment variable.
19.4.2.4. Special Conditions and Actions
*) at the beginning of a recipe's condition line:
!— In the condition line, this character inverts the condition, causing a match to occur only if the condition does not match the message.<— Checks if the message is under a specified number of bytes.>— Checks if the message is over a specified number of bytes.
!— In the action line, this character tells Procmail to forward the message to the specified email addresses.$— Refers to a variable set earlier in thercfile. This is often used to set a common mailbox that is referred to by various recipes.|— Starts a specified program to process the message.{and}— Constructs a nesting block, used to contain additional recipes to apply to matching messages.
19.4.2.5. Recipe Examples
grep(1) man page.
:0: new-mail.spool
:0:
new-mail.spoolLOCKEXT environment variable. No condition is specified, so every message matches this recipe and is placed in the single spool file called new-mail.spool, located within the directory specified by the MAILDIR environment variable. An MUA can then view messages in this file.
rc files to direct messages to a default location.
:0 * ^From: spammer@domain.com /dev/null
:0
* ^From: spammer@domain.com
/dev/nullspammer@domain.com are sent to the /dev/null device, deleting them.
Warning
/dev/null for permanent deletion. If a recipe inadvertently catches unintended messages, and those messages disappear, it becomes difficult to troubleshoot the rule.
/dev/null.
:0: * ^(From|Cc|To).*tux-lug tuxlug
:0:
* ^(From|Cc|To).*tux-lug
tuxlugtux-lug@domain.com mailing list are placed in the tuxlug mailbox automatically for the MUA. Note that the condition in this example matches the message if it has the mailing list's email address on the From, Cc, or To lines.
19.4.2.6. Spam Filters
Note
root:
yum install spamassassin
~]# yum install spamassassin~/.procmailrc file:
INCLUDERC=/etc/mail/spamassassin/spamassassin-default.rc
INCLUDERC=/etc/mail/spamassassin/spamassassin-default.rc/etc/mail/spamassassin/spamassassin-default.rc contains a simple Procmail rule that activates SpamAssassin for all incoming email. If an email is determined to be spam, it is tagged in the header as such and the title is prepended with the following pattern:
*****SPAM*****
*****SPAM*****:0 Hw * ^X-Spam-Status: Yes spam
:0 Hw * ^X-Spam-Status: Yes spamspam.
spamd) and the client application (spamc). Configuring SpamAssassin this way, however, requires root access to the host.
spamd daemon, type the following command:
service spamassassin start
~]# service spamassassin startsystem-config-services), to turn on the spamassassin service. See Chapter 12, Services and Daemons for more information about starting and stopping services.
~/.procmailrc file. For a system-wide configuration, place it in /etc/procmailrc:
INCLUDERC=/etc/mail/spamassassin/spamassassin-spamc.rc
INCLUDERC=/etc/mail/spamassassin/spamassassin-spamc.rc19.5. Mail User Agents
mutt.
19.5.1. Securing Communication
POP and IMAP protocols pass authentication information unencrypted, it is possible for an attacker to gain access to user accounts by collecting user names and passwords as they are passed over the network.
19.5.1.1. Secure Email Clients
IMAP and POP have known port numbers (993 and 995, respectively) that the MUA uses to authenticate and download messages.
19.5.1.2. Securing Email Client Communications
IMAP and POP users on the email server is a simple matter.
Warning
IMAP or POP, change to the /etc/pki/dovecot/ directory, edit the certificate parameters in the /etc/pki/dovecot/dovecot-openssl.cnf configuration file as you prefer, and type the following commands, as root:
dovecot]# rm -f certs/dovecot.pem private/dovecot.pem dovecot]# /usr/libexec/dovecot/mkcert.sh
dovecot]# rm -f certs/dovecot.pem private/dovecot.pem
dovecot]# /usr/libexec/dovecot/mkcert.sh/etc/dovecot/conf.d/10-ssl.conf file:
ssl_cert = </etc/pki/dovecot/certs/dovecot.pem ssl_key = </etc/pki/dovecot/private/dovecot.pem
ssl_cert = </etc/pki/dovecot/certs/dovecot.pem
ssl_key = </etc/pki/dovecot/private/dovecot.pem
service dovecot restart command to restart the dovecot daemon.
stunnel command can be used as an encryption wrapper around the standard, non-secure connections to IMAP or POP services.
stunnel utility uses external OpenSSL libraries included with Red Hat Enterprise Linux to provide strong cryptography and to protect the network connections. It is recommended to apply to a CA to obtain an SSL certificate, but it is also possible to create a self-signed certificate.
stunnel and create its basic configuration. To configure stunnel as a wrapper for IMAPS and POP3S, add the following lines to the /etc/stunnel/stunnel.conf configuration file:
stunnel. Once you start it, it is possible to use an IMAP or a POP email client and connect to the email server using SSL encryption.
19.6. Additional Resources
19.6.1. Installed Documentation
- Information on configuring Sendmail is included with the sendmail and sendmail-cf packages.
/usr/share/sendmail-cf/README— Contains information on them4macro processor, file locations for Sendmail, supported mailers, how to access enhanced features, and more.
In addition, thesendmailandaliasesman pages contain helpful information covering various Sendmail options and the proper configuration of the Sendmail/etc/mail/aliasesfile. /usr/share/doc/postfix-version-number/— Contains a large amount of information on how to configure Postfix. Replace version-number with the version number of Postfix./usr/share/doc/fetchmail-version-number— Contains a full list of Fetchmail features in theFEATURESfile and an introductoryFAQdocument. Replace version-number with the version number of Fetchmail./usr/share/doc/procmail-version-number/— Contains aREADMEfile that provides an overview of Procmail, aFEATURESfile that explores every program feature, and anFAQfile with answers to many common configuration questions. Replace version-number with the version number of Procmail.When learning how Procmail works and creating new recipes, the following Procmail man pages are invaluable:procmail— Provides an overview of how Procmail works and the steps involved with filtering email.procmailrc— Explains thercfile format used to construct recipes.procmailex— Gives a number of useful, real-world examples of Procmail recipes.procmailsc— Explains the weighted scoring technique used by Procmail to match a particular recipe to a message./usr/share/doc/spamassassin-version-number/— Contains a large amount of information pertaining to SpamAssassin. Replace version-number with the version number of the spamassassin package.
19.6.2. Online Documentation
- How to configure postfix with TLS? — A Red Hat Knowledgebase article that describes configuring postfix to use TLS.
- The Red Hat Knowledgebase article How to Configure a System to Manage Multiple Virtual Mailboxes Using Postfix and Dovecot describes managing multiple virtual users under one real-user account using Postfix as Mail Transporting Agent (MTA) and Dovecot as IMAP server.
- http://www.sendmail.org/ — Offers a thorough technical breakdown of Sendmail features, documentation and configuration examples.
- http://www.sendmail.com/ — Contains news, interviews and articles concerning Sendmail, including an expanded view of the many options available.
- http://www.postfix.org/ — The Postfix project home page contains a wealth of information about Postfix. The mailing list is a particularly good place to look for information.
- http://www.fetchmail.info/fetchmail-FAQ.html — A thorough FAQ about Fetchmail.
- http://www.procmail.org/ — The home page for Procmail with links to assorted mailing lists dedicated to Procmail as well as various FAQ documents.
- http://www.spamassassin.org/ — The official site of the SpamAssassin project.
Chapter 20. Directory Servers
20.1. OpenLDAP
LDAP (Lightweight Directory Access Protocol) is a set of open protocols used to access centrally stored information over a network. It is based on the X.500 standard for directory sharing, but is less complex and resource-intensive. For this reason, LDAP is sometimes referred to as “X.500 Lite”.
20.1.1. Introduction to LDAP
Important
Important
SSLv3 protocol for security. OpenLDAP is one of the system components that do not provide configuration parameters that allow SSLv3 to be effectively disabled. To mitigate the risk, it is recommended that you use the stunnel command to provide a secure tunnel, and disable stunnel from using SSLv3. For more information on using stunnel, see the Red Hat Enterprise Linux 6 Security Guide.
20.1.1.1. LDAP Terminology
- entry
- A single unit within an LDAP directory. Each entry is identified by its unique Distinguished Name (DN).
- attribute
- Information directly associated with an entry. For example, if an organization is represented as an LDAP entry, attributes associated with this organization might include an address, a fax number, etc. Similarly, people can be represented as entries with common attributes such as personal telephone number or email address.An attribute can either have a single value, or an unordered space-separated list of values. While certain attributes are optional, others are required. Required attributes are specified using the
objectClassdefinition, and can be found in schema files located in the/etc/openldap/slapd.d/cn=config/cn=schema/directory.The assertion of an attribute and its corresponding value is also referred to as a Relative Distinguished Name (RDN). Unlike distinguished names that are unique globally, a relative distinguished name is only unique per entry. - LDIF
- The LDAP Data Interchange Format (LDIF) is a plain text representation of an LDAP entry. It takes the following form:
[id] dn: distinguished_name attribute_type: attribute_value attribute_type: attribute_value ...
[id] dn: distinguished_name attribute_type: attribute_value attribute_type: attribute_value ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The optional id is a number determined by the application that is used to edit the entry. Each entry can contain as many attribute_type and attribute_value pairs as needed, as long as they are all defined in a corresponding schema file. A blank line indicates the end of an entry.
20.1.1.2. OpenLDAP Features
- LDAPv3 Support — Many of the changes in the protocol since LDAP version 2 are designed to make LDAP more secure. Among other improvements, this includes the support for Simple Authentication and Security Layer (SASL), and Transport Layer Security (TLS) protocols.
- LDAP Over IPC — The use of inter-process communication (IPC) enhances security by eliminating the need to communicate over a network.
- IPv6 Support — OpenLDAP is compliant with Internet Protocol version 6 (IPv6), the next generation of the Internet Protocol.
- LDIFv1 Support — OpenLDAP is fully compliant with LDIF version 1.
- Updated C API — The current C API improves the way programmers can connect to and use LDAP directory servers.
- Enhanced Standalone LDAP Server — This includes an updated access control system, thread pooling, better tools, and much more.
20.1.1.3. OpenLDAP Server Setup
- Install the OpenLDAP suite. See Section 20.1.2, “Installing the OpenLDAP Suite” for more information on required packages.
- Customize the configuration as described in Section 20.1.3, “Configuring an OpenLDAP Server”.
- Start the
slapdservice as described in Section 20.1.4, “Running an OpenLDAP Server”. - Use the
ldapaddutility to add entries to the LDAP directory. - Use the
ldapsearchutility to verify that theslapdservice is accessing the information correctly.
20.1.2. Installing the OpenLDAP Suite
| Package | Description |
|---|---|
| openldap | A package containing the libraries necessary to run the OpenLDAP server and client applications. |
| openldap-clients | A package containing the command-line utilities for viewing and modifying directories on an LDAP server. |
| openldap-servers | A package containing both the services and utilities to configure and run an LDAP server. This includes the Standalone LDAP Daemon, slapd. |
| compat-openldap | A package containing the OpenLDAP compatibility libraries. |
| Package | Description |
|---|---|
| sssd | A package containing the System Security Services Daemon (SSSD), a set of daemons to manage access to remote directories and authentication mechanisms. It provides the Name Service Switch (NSS) and the Pluggable Authentication Modules (PAM) interfaces toward the system and a pluggable back-end system to connect to multiple different account sources. |
| mod_authz_ldap |
A package containing
mod_authz_ldap, the LDAP authorization module for the Apache HTTP Server. This module uses the short form of the distinguished name for a subject and the issuer of the client SSL certificate to determine the distinguished name of the user within an LDAP directory. It is also capable of authorizing users based on attributes of that user's LDAP directory entry, determining access to assets based on the user and group privileges of the asset, and denying access for users with expired passwords. Note that the mod_ssl module is required when using the mod_authz_ldap module.
|
yum command in the following form:
yum install package
yum install packageyum install openldap openldap-clients openldap-servers
~]# yum install openldap openldap-clients openldap-serversroot) to run this command. For more information on how to install new packages in Red Hat Enterprise Linux, see Section 8.2.4, “Installing Packages”.
20.1.2.1. Overview of OpenLDAP Server Utilities
slapd service:
| Command | Description |
|---|---|
slapacl | Allows you to check the access to a list of attributes. |
slapadd | Allows you to add entries from an LDIF file to an LDAP directory. |
slapauth | Allows you to check a list of IDs for authentication and authorization permissions. |
slapcat | Allows you to pull entries from an LDAP directory in the default format and save them in an LDIF file. |
slapdn | Allows you to check a list of Distinguished Names (DNs) based on available schema syntax. |
slapindex | Allows you to re-index the slapd directory based on the current content. Run this utility whenever you change indexing options in the configuration file. |
slappasswd | Allows you to create an encrypted user password to be used with the ldapmodify utility, or in the slapd configuration file. |
slapschema | Allows you to check the compliance of a database with the corresponding schema. |
slaptest | Allows you to check the LDAP server configuration. |
Important
root can run slapadd, the slapd service runs as the ldap user. Because of this, the directory server is unable to modify any files created by slapadd. To correct this issue, after running the slapd utility, type the following at a shell prompt:
chown -R ldap:ldap /var/lib/ldap
~]# chown -R ldap:ldap /var/lib/ldapWarning
slapd service before using slapadd, slapcat, or slapindex. You can do so by typing the following at a shell prompt:
service slapd stop Stopping slapd: [ OK ]
~]# service slapd stop
Stopping slapd: [ OK ]slapd service, see Section 20.1.4, “Running an OpenLDAP Server”.
20.1.2.2. Overview of OpenLDAP Client Utilities
| Command | Description |
|---|---|
ldapadd | Allows you to add entries to an LDAP directory, either from a file, or from standard input. It is a symbolic link to ldapmodify -a. |
ldapcompare | Allows you to compare given attribute with an LDAP directory entry. |
ldapdelete | Allows you to delete entries from an LDAP directory. |
ldapexop | Allows you to perform extended LDAP operations. |
ldapmodify | Allows you to modify entries in an LDAP directory, either from a file, or from standard input. |
ldapmodrdn | Allows you to modify the RDN value of an LDAP directory entry. |
ldappasswd | Allows you to set or change the password for an LDAP user. |
ldapsearch | Allows you to search LDAP directory entries. |
ldapurl | Allows you to compose or decompose LDAP URLs. |
ldapwhoami | Allows you to perform a whoami operation on an LDAP server. |
ldapsearch, each of these utilities is more easily used by referencing a file containing the changes to be made rather than typing a command for each entry to be changed within an LDAP directory. The format of such a file is outlined in the man page for each utility.
20.1.2.3. Overview of Common LDAP Client Applications
20.1.3. Configuring an OpenLDAP Server
/etc/openldap/ directory. Table 20.5, “List of OpenLDAP configuration files and directories” highlights the most important files and directories within this directory.
slapd service uses a configuration database located in the /etc/openldap/slapd.d/ directory and only reads the old /etc/openldap/slapd.conf configuration file if this directory does not exist. If you have an existing slapd.conf file from a previous installation, you can either wait for the openldap-servers package to convert it to the new format the next time you update this package, or type the following at a shell prompt as root to convert it immediately:
slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/
~]# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/slapd configuration consists of LDIF entries organized in a hierarchical directory structure, and the recommended way to edit these entries is to use the server utilities described in Section 20.1.2.1, “Overview of OpenLDAP Server Utilities”.
Important
slapd service unable to start. Because of this, it is strongly advised that you avoid editing the LDIF files within the /etc/openldap/slapd.d/ directory directly.
20.1.3.1. Changing the Global Configuration
/etc/openldap/slapd.d/cn=config.ldif file. The following directives are commonly used:
-
olcAllows - The
olcAllowsdirective allows you to specify which features to enable. It takes the following form:olcAllows: feature
olcAllows: featureCopy to Clipboard Copied! Toggle word wrap Toggle overflow It accepts a space-separated list of features as described in Table 20.6, “Available olcAllows options”. The default option isbind_v2.Expand Table 20.6. Available olcAllows options Option Description bind_v2Enables the acceptance of LDAP version 2 bind requests. bind_anon_credEnables an anonymous bind when the Distinguished Name (DN) is empty. bind_anon_dnEnables an anonymous bind when the Distinguished Name (DN) is not empty. update_anonEnables processing of anonymous update operations. proxy_authz_anonEnables processing of anonymous proxy authorization control. Example 20.1. Using the olcAllows directive
olcAllows: bind_v2 update_anon
olcAllows: bind_v2 update_anonCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
olcConnMaxPending - The
olcConnMaxPendingdirective allows you to specify the maximum number of pending requests for an anonymous session. It takes the following form:olcConnMaxPending: number
olcConnMaxPending: numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow The default option is100.Example 20.2. Using the olcConnMaxPending directive
olcConnMaxPending: 100
olcConnMaxPending: 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
olcConnMaxPendingAuth - The
olcConnMaxPendingAuthdirective allows you to specify the maximum number of pending requests for an authenticated session. It takes the following form:olcConnMaxPendingAuth: number
olcConnMaxPendingAuth: numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow The default option is1000.Example 20.3. Using the olcConnMaxPendingAuth directive
olcConnMaxPendingAuth: 1000
olcConnMaxPendingAuth: 1000Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
olcDisallows - The
olcDisallowsdirective allows you to specify which features to disable. It takes the following form:olcDisallows: feature
olcDisallows: featureCopy to Clipboard Copied! Toggle word wrap Toggle overflow It accepts a space-separated list of features as described in Table 20.7, “Available olcDisallows options”. No features are disabled by default.Expand Table 20.7. Available olcDisallows options Option Description bind_anonDisables the acceptance of anonymous bind requests. bind_simpleDisables the simple bind authentication mechanism. tls_2_anonDisables the enforcing of an anonymous session when the STARTTLS command is received. tls_authcDisallows the STARTTLS command when authenticated. Example 20.4. Using the olcDisallows directive
olcDisallows: bind_anon
olcDisallows: bind_anonCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
olcIdleTimeout - The
olcIdleTimeoutdirective allows you to specify how many seconds to wait before closing an idle connection. It takes the following form:olcIdleTimeout: number
olcIdleTimeout: numberCopy to Clipboard Copied! Toggle word wrap Toggle overflow This option is disabled by default (that is, set to0).Example 20.5. Using the olcIdleTimeout directive
olcIdleTimeout: 180
olcIdleTimeout: 180Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
olcLogFile - The
olcLogFiledirective allows you to specify a file in which to write log messages. It takes the following form:olcLogFile: file_name
olcLogFile: file_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow The log messages are written to standard error by default.Example 20.6. Using the olcLogFile directive
olcLogFile: /var/log/slapd.log
olcLogFile: /var/log/slapd.logCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
olcReferral - The
olcReferraloption allows you to specify a URL of a server to process the request in case the server is not able to handle it. It takes the following form:olcReferral: URL
olcReferral: URLCopy to Clipboard Copied! Toggle word wrap Toggle overflow This option is disabled by default.Example 20.7. Using the olcReferral directive
olcReferral: ldap://root.openldap.org
olcReferral: ldap://root.openldap.orgCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
olcWriteTimeout - The
olcWriteTimeoutoption allows you to specify how many seconds to wait before closing a connection with an outstanding write request. It takes the following form:olcWriteTimeout
olcWriteTimeoutCopy to Clipboard Copied! Toggle word wrap Toggle overflow This option is disabled by default (that is, set to0).Example 20.8. Using the olcWriteTimeout directive
olcWriteTimeout: 180
olcWriteTimeout: 180Copy to Clipboard Copied! Toggle word wrap Toggle overflow
20.1.3.2. Changing the Database-Specific Configuration
/etc/openldap/slapd.d/cn=config/olcDatabase={2}bdb.ldif file. The following directives are commonly used in a database-specific configuration:
-
olcReadOnly - The
olcReadOnlydirective allows you to use the database in a read-only mode. It takes the following form:olcReadOnly: boolean
olcReadOnly: booleanCopy to Clipboard Copied! Toggle word wrap Toggle overflow It accepts eitherTRUE(enable the read-only mode), orFALSE(enable modifications of the database). The default option isFALSE.Example 20.9. Using the olcReadOnly directive
olcReadOnly: TRUE
olcReadOnly: TRUECopy to Clipboard Copied! Toggle word wrap Toggle overflow -
olcRootDN - The
olcRootDNdirective allows you to specify the user that is unrestricted by access controls or administrative limit parameters set for operations on the LDAP directory. It takes the following form:olcRootDN: distinguished_name
olcRootDN: distinguished_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow It accepts a Distinguished Name (DN). The default option iscn=Manager,dc=my-domain,dc=com.Example 20.10. Using the olcRootDN directive
olcRootDN: cn=root,dc=example,dc=com
olcRootDN: cn=root,dc=example,dc=comCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
olcRootPW - The
olcRootPWdirective allows you to set a password for the user that is specified using theolcRootDNdirective. It takes the following form:olcRootPW: password
olcRootPW: passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow It accepts either a plain text string, or a hash. To generate a hash, type the following at a shell prompt:slappaswd New password: Re-enter new password: {SSHA}WczWsyPEnMchFf1GRTweq2q7XJcvmSxD~]$ slappaswd New password: Re-enter new password: {SSHA}WczWsyPEnMchFf1GRTweq2q7XJcvmSxDCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example 20.11. Using the olcRootPW directive
olcRootPW: {SSHA}WczWsyPEnMchFf1GRTweq2q7XJcvmSxDolcRootPW: {SSHA}WczWsyPEnMchFf1GRTweq2q7XJcvmSxDCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
olcSuffix - The
olcSuffixdirective allows you to specify the domain for which to provide information. It takes the following form:olcSuffix: domain_name
olcSuffix: domain_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow It accepts a fully qualified domain name (FQDN). The default option isdc=my-domain,dc=com.Example 20.12. Using the olcSuffix directive
olcSuffix: dc=example,dc=com
olcSuffix: dc=example,dc=comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
20.1.3.3. Extending Schema
/etc/openldap/slapd.d/cn=config/cn=schema/ directory also contains LDAP definitions that were previously located in /etc/openldap/schema/. It is possible to extend the schema used by OpenLDAP to support additional attribute types and object classes using the default schema files as a guide. However, this task is beyond the scope of this chapter. For more information on this topic, see http://www.openldap.org/doc/admin/schema.html.
20.1.4. Running an OpenLDAP Server
20.1.4.1. Starting the Service
slapd service, type the following at a shell prompt:
service slapd start Starting slapd: [ OK ]
~]# service slapd start
Starting slapd: [ OK ]chkconfig slapd on
~]# chkconfig slapd on20.1.4.2. Stopping the Service
slapd service, type the following at a shell prompt:
service slapd stop Stopping slapd: [ OK ]
~]# service slapd stop
Stopping slapd: [ OK ]chkconfig slapd off
~]# chkconfig slapd off20.1.4.3. Restarting the Service
slapd service, type the following at a shell prompt:
service slapd restart Stopping slapd: [ OK ] Starting slapd: [ OK ]
~]# service slapd restart
Stopping slapd: [ OK ]
Starting slapd: [ OK ]20.1.4.4. Checking the Service Status
service slapd status slapd (pid 3672) is running...
~]# service slapd status
slapd (pid 3672) is running...20.1.5. Configuring a System to Authenticate Using OpenLDAP
yum install openldap openldap-clients sssd
~]# yum install openldap openldap-clients sssd20.1.5.1. Migrating Old Authentication Information to LDAP Format
yum install migrationtools
~]# yum install migrationtools/usr/share/migrationtools/ directory. Once installed, edit the /usr/share/migrationtools/migrate_common.ph file and change the following lines to reflect the correct domain, for example:
# Default DNS domain $DEFAULT_MAIL_DOMAIN = "example.com"; # Default base $DEFAULT_BASE = "dc=example,dc=com";
# Default DNS domain
$DEFAULT_MAIL_DOMAIN = "example.com";
# Default base
$DEFAULT_BASE = "dc=example,dc=com";migrate_all_online.sh script with the default base set to dc=example,dc=com, type:
export DEFAULT_BASE="dc=example,dc=com" \ /usr/share/migrationtools/migrate_all_online.sh
~]# export DEFAULT_BASE="dc=example,dc=com" \
/usr/share/migrationtools/migrate_all_online.sh| Existing Name Service | Is LDAP Running? | Script to Use |
|---|---|---|
/etc flat files | yes | migrate_all_online.sh |
/etc flat files | no | migrate_all_offline.sh |
| NetInfo | yes | migrate_all_netinfo_online.sh |
| NetInfo | no | migrate_all_netinfo_offline.sh |
| NIS (YP) | yes | migrate_all_nis_online.sh |
| NIS (YP) | no | migrate_all_nis_offline.sh |
README and the migration-tools.txt files in the /usr/share/doc/migrationtools-version/ directory.
20.1.6. Additional Resources
20.1.6.1. Installed Documentation
/usr/share/doc/openldap-servers-version/guide.html- A copy of the OpenLDAP Software Administrator's Guide.
/usr/share/doc/openldap-servers-version/README.schema- A README file containing the description of installed schema files.
- Client Applications
man ldapadd— Describes how to add entries to an LDAP directory.man ldapdelete— Describes how to delete entries within an LDAP directory.man ldapmodify— Describes how to modify entries within an LDAP directory.man ldapsearch— Describes how to search for entries within an LDAP directory.man ldappasswd— Describes how to set or change the password of an LDAP user.man ldapcompare— Describes how to use theldapcomparetool.man ldapwhoami— Describes how to use theldapwhoamitool.man ldapmodrdn— Describes how to modify the RDNs of entries.
- Server Applications
man slapd— Describes command-line options for the LDAP server.
- Administrative Applications
man slapadd— Describes command-line options used to add entries to aslapddatabase.man slapcat— Describes command-line options used to generate an LDIF file from aslapddatabase.man slapindex— Describes command-line options used to regenerate an index based upon the contents of aslapddatabase.man slappasswd— Describes command-line options used to generate user passwords for LDAP directories.
- Configuration Files
man ldap.conf— Describes the format and options available within the configuration file for LDAP clients.man slapd-config— Describes the format and options available within the configuration directory.
20.1.6.2. Useful Websites
- http://www.openldap.org/doc/admin24/
- The current version of the OpenLDAP Software Administrator's Guide.
Chapter 21. File and Print Servers
21.1. Samba
SMB) protocol. Modern versions of this protocol are also known as the common Internet file system (CIFS) protocol. It allows the networking of Microsoft Windows®, Linux, UNIX, and other operating systems together, enabling access to Windows-based file and printer shares. Samba's use of SMB allows it to appear as a Windows server to Windows clients.
Note
root:
yum install samba
~]# yum install samba21.1.1. Introduction to Samba
What Samba can do:
- Serve directory trees and printers to Linux, UNIX, and Windows clients
- Assist in network browsing (with NetBIOS)
- Authenticate Windows domain logins
- Provide Windows Internet Name Service (
WINS) name server resolution - Act as a Windows NT®-style Primary Domain Controller (PDC)
- Act as a Backup Domain Controller (BDC) for a Samba-based PDC
- Act as an Active Directory domain member server
- Join a Windows NT/2000/2003/2008 PDC
What Samba cannot do:
- Act as a BDC for a Windows PDC (and vice versa)
- Act as an Active Directory domain controller
21.1.2. Samba Daemons and Related Services
smbd, nmbd, and winbindd). Three services (smb, nmb, and winbind) control how the daemons are started, stopped, and other service-related features. These services act as different init scripts. Each daemon is listed in detail below, as well as which specific service has control over it.
smbd
smbd server daemon provides file sharing and printing services to Windows clients. In addition, it is responsible for user authentication, resource locking, and data sharing through the SMB protocol. The default ports on which the server listens for SMB traffic are TCP ports 139 and 445.
smbd daemon is controlled by the smb service.
nmbd
nmbd server daemon understands and replies to NetBIOS name service requests such as those produced by SMB/CIFS in Windows-based systems. These systems include Windows 95/98/ME, Windows NT, Windows 2000, Windows XP, and LanManager clients. It also participates in the browsing protocols that make up the Windows Network Neighborhood view. The default port that the server listens to for NMB traffic is UDP port 137.
nmbd daemon is controlled by the nmb service.
winbindd
winbind service resolves user and group information received from a server running Windows NT, 2000, 2003, Windows Server 2008, or Windows Server 2012. This makes Windows user and group information understandable by UNIX platforms. This is achieved by using Microsoft RPC calls, Pluggable Authentication Modules (PAM), and the Name Service Switch (NSS). This allows Windows NT domain and Active Directory users to appear and operate as UNIX users on a UNIX machine. Though bundled with the Samba distribution, the winbind service is controlled separately from the smb service.
winbind daemon is controlled by the winbind service and does not require the smb service to be started in order to operate. winbind is also used when Samba is an Active Directory member, and may also be used on a Samba domain controller (to implement nested groups and interdomain trust). Because winbind is a client-side service used to connect to Windows NT-based servers, further discussion of winbind is beyond the scope of this chapter.
winbind for authentication, see Section 13.1.2.3, “Configuring Winbind Authentication”.
Note
21.1.4. Configuring a Samba Server
/etc/samba/smb.conf) allows users to view their home directories as a Samba share. It also shares all printers configured for the system as Samba shared printers. You can attach a printer to the system and print to it from the Windows machines on your network.
21.1.4.1. Graphical Configuration
21.1.4.2. Command-Line Configuration
/etc/samba/smb.conf as its configuration file. If you change this configuration file, the changes do not take effect until you restart the Samba daemon with the following command as root:
service smb restart
~]# service smb restart/etc/samba/smb.conf file:
workgroup = WORKGROUPNAME server string = BRIEF COMMENT ABOUT SERVER
workgroup = WORKGROUPNAME
server string = BRIEF COMMENT ABOUT SERVER/etc/samba/smb.conf file (after modifying it to reflect your needs and your system):
Example 21.1. An Example Configuration of a Samba Server
tfox and carole to read and write to the directory /home/share/, on the Samba server, from a Samba client.
21.1.4.3. Encrypted Passwords
smbpasswd utility:
smbpasswd -a username
smbpasswd -a username21.1.5. Starting and Stopping Samba
root:
service smb start
~]# service smb startImportant
net join command before starting the smb service. Also it is recommended to run winbind before smbd.
root:
service smb stop
~]# service smb stoprestart option is a quick way of stopping and then starting Samba. This is the most reliable way to make configuration changes take effect after editing the configuration file for Samba. Note that the restart option starts the daemon even if it was not running originally.
root:
service smb restart
~]# service smb restartcondrestart (conditional restart) option only stops and starts smb on the condition that it is currently running. This option is useful for scripts, because it does not start the daemon if it is not running.
Note
/etc/samba/smb.conf file is changed, Samba automatically reloads it after a few minutes. Issuing a manual restart or reload is just as effective.
root:
service smb condrestart
~]# service smb condrestart/etc/samba/smb.conf file can be useful in case of a failed automatic reload by the smb service. To ensure that the Samba server configuration file is reloaded without restarting the service, type the following command, as root:
service smb reload
~]# service smb reloadsmb service does not start automatically at boot time. To configure Samba to start at boot time, use an initscript utility, such as /sbin/chkconfig, /usr/sbin/ntsysv, or the Services Configuration Tool program. See Chapter 12, Services and Daemons for more information regarding these tools.
21.1.6. Samba Server Types and the smb.conf File
/etc/samba/smb.conf configuration file. Although the default smb.conf file is well documented, it does not address complex topics such as LDAP, Active Directory, and the numerous domain controller implementations.
/etc/samba/smb.conf file for a successful configuration.
21.1.6.1. Stand-alone Server
Anonymous Read-Only
/etc/samba/smb.conf file shows a sample configuration needed to implement anonymous read-only file sharing. Two directives are used to configure anonymous access – map to guest = Bad user and guest account = nobody.
Example 21.2. An Example Configuration of a Anonymous Read-Only Samba Server
Anonymous Read/Write
/etc/samba/smb.conf file shows a sample configuration needed to implement anonymous read/write file sharing. To enable anonymous read/write file sharing, set the read only directive to no. The force user and force group directives are also added to enforce the ownership of any newly placed files specified in the share.
Note
force user) and group (force group) in the /etc/samba/smb.conf file.
Example 21.3. An Example Configuration of a Anonymous Read/Write Samba Server
Anonymous Print Server
/etc/samba/smb.conf file shows a sample configuration needed to implement an anonymous print server. Setting browseable to no as shown does not list the printer in Windows Network Neighborhood. Although hidden from browsing, configuring the printer explicitly is possible. By connecting to DOCS_SRV using NetBIOS, the client can have access to the printer if the client is also part of the DOCS workgroup. It is also assumed that the client has the correct local printer driver installed, as the use client driver directive is set to yes. In this case, the Samba server has no responsibility for sharing printer drivers to the client.
Example 21.4. An Example Configuration of a Anonymous Print Samba Server
Secure Read/Write File and Print Server
/etc/samba/smb.conf file shows a sample configuration needed to implement a secure read/write file and print server. Setting the security directive to user forces Samba to authenticate client connections. Notice the [homes] share does not have a force user or force group directive as the [public] share does. The [homes] share uses the authenticated user details for any files created as opposed to the force user and force group in [public].
Example 21.5. An Example Configuration of a Secure Read/Write File and Print Samba Server
21.1.6.2. Domain Member Server
Active Directory Domain Member Server
Procedure 21.3. Adding a Member Server to an Active Directory Domain
- Create the
/etc/samba/smb.confconfiguration file on a member server to be added to the Active Directory domain. Add the following lines to the configuration file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow With the above configuration, Samba authenticates users for services being run locally but is also a client of the Active Directory. Ensure that your kerberosrealmparameter is shown in all caps (for examplerealm = EXAMPLE.COM). Since Windows 2000/2003/2008 requires Kerberos for Active Directory authentication, therealmdirective is required. If Active Directory and Kerberos are running on different servers, thepassword serverdirective is required to help the distinction. - Configure Kerberos on the member server. Create the
/etc/krb5.confconfiguration file with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Uncomment the[realms]and[domain_realm]sections if DNS lookups are not working.For more information on Kerberos, and the/etc/krb5.conffile, see the Using Kerberos section of the Red Hat Enterprise Linux 6 Managing Single Sign-On and Smart Cards. - To join an Active Directory server, type the following command as
rooton the member server:net ads join -U administrator%password
~]# net ads join -U administrator%passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow Thenetcommand authenticates asAdministratorusing the NT LAN Manager (NTLM) protocol and creates the machine account. Thennetuses the machine account credentials to authenticate with Kerberos.Note
Sincesecurity = adsand notsecurity = useris used, a local password back end such assmbpasswdis not needed. Older clients that do not supportsecurity = adsare authenticated as ifsecurity = domainhad been set. This change does not affect functionality and allows local users not previously in the domain.
Windows NT4-based Domain Member Server
/etc/samba/smb.conf file shows a sample configuration needed to implement a Windows NT4-based domain member server. Becoming a member server of an NT4-based domain is similar to connecting to an Active Directory. The main difference is NT4-based domains do not use Kerberos in their authentication method, making the /etc/samba/smb.conf file simpler. In this instance, the Samba member server functions as a pass through to the NT4-based domain server.
Example 21.6. An Example Configuration of Samba Windows NT4-based Domain Member Server
/etc/samba/smb.conf file to convert the server to a Samba-based PDC. If Windows NT-based servers are upgraded to Windows 2000/2003/2008 the /etc/samba/smb.conf file is easily modifiable to incorporate the infrastructure change to Active Directory if needed.
Important
/etc/samba/smb.conf file, join the domain before starting Samba by typing the following command as root:
net rpc join -U administrator%password
~]# net rpc join -U administrator%password-S option, which specifies the domain server host name, does not need to be stated in the net rpc join command. Samba uses the host name specified by the workgroup directive in the /etc/samba/smb.conf file instead of it being stated explicitly.
21.1.6.3. Domain Controller
Important
Primary Domain Controller (PDC) Using tdbsam
tdbsam password database back end. Replacing the aging smbpasswd back end, tdbsam has numerous improvements that are explained in more detail in Section 21.1.8, “Samba Account Information Databases”. The passdb backend directive controls which back end is to be used for the PDC.
/etc/samba/smb.conf file shows a sample configuration needed to implement a tdbsam password database back end.
Example 21.7. An Example Configuration of Primary Domain Controller (PDC) Using tdbsam
tdbsam follow these steps:
- Adjust the
smb.confconfiguration file as shown in Example 21.7, “An Example Configuration of Primary Domain Controller (PDC) Usingtdbsam”. - Add the
rootuser to the Samba password database. You will be prompted to provide a new Samba password for therootuser:smbpasswd -a root New SMB password:
~]# smbpasswd -a root New SMB password:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Start the
smbservice:service smb start
~]# service smb startCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Make sure all profile, user, and netlogon directories are created.
- Add groups that users can be members of:
groupadd -f users groupadd -f nobody groupadd -f ntadmins
~]# groupadd -f users ~]# groupadd -f nobody ~]# groupadd -f ntadminsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Associate the UNIX groups with their respective Windows groups.
net groupmap add ntgroup="Domain Users" unixgroup=users net groupmap add ntgroup="Domain Guests" unixgroup=nobody net groupmap add ntgroup="Domain Admins" unixgroup=ntadmins
~]# net groupmap add ntgroup="Domain Users" unixgroup=users ~]# net groupmap add ntgroup="Domain Guests" unixgroup=nobody ~]# net groupmap add ntgroup="Domain Admins" unixgroup=ntadminsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Grant access rights to a user or a group. For example, to grant the right to add client machines to the domain on a Samba domain controller, to the members to the Domain Admins group, execute the following command:
net rpc rights grant 'DOCS\Domain Admins' SetMachineAccountPrivilege -S PDC -U root
~]# net rpc rights grant 'DOCS\Domain Admins' SetMachineAccountPrivilege -S PDC -U rootCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Note
tdbsam authentication back end. LDAP is recommended in these cases.
Primary Domain Controller (PDC) with Active Directory
21.1.7. Samba Security Modes
21.1.7.1. User-Level Security
security = user directive is not listed in the /etc/samba/smb.conf file, it is used by Samba. If the server accepts the client's user name and password, the client can then mount multiple shares without specifying a password for each instance. Samba can also accept session-based user name and password requests. The client maintains multiple authentication contexts by using a unique UID for each logon.
/etc/samba/smb.conf file, the security = user directive that sets user-level security is:
[GLOBAL] ... security = user ...
[GLOBAL]
...
security = user
...Samba Guest Shares
security = share parameter, follow the procedure below:
Procedure 21.4. Configuring Samba Guest Shares
- Create a username map file, in this example
/etc/samba/smbusers, and add the following line to it:nobody = guest
nobody = guestCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the following directives to the main section in the
/etc/samba/smb.conffile. Also, do not use thevalid usersdirective:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Theusername mapdirective provides a path to the username map file specified in the previous step. - Add the following directive to the share section in the
/ect/samba/smb.conffile. Do not use thevalid usersdirective.[SHARE] ... guest ok = yes ...
[SHARE] ... guest ok = yes ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Domain Security Mode (User-Level Security)
/etc/samba/smb.conf file:
[GLOBAL] ... security = domain workgroup = MARKETING ...
[GLOBAL]
...
security = domain
workgroup = MARKETING
...Active Directory Security Mode (User-Level Security)
/etc/samba/smb.conf file, the following directives make Samba an Active Directory member server:
21.1.8. Samba Account Information Databases
- Plain Text
- Plain text back ends are nothing more than the
/etc/passwdtype back ends. With a plain text back end, all user names and passwords are sent unencrypted between the client and the Samba server. This method is very insecure and is not recommended for use by any means. It is possible that different Windows clients connecting to the Samba server with plain text passwords cannot support such an authentication method. smbpasswd- The
smbpasswdback end utilizes a plain ASCII text layout that includes the MS Windows LanMan and NT account, and encrypted password information. Thesmbpasswdback end lacks the storage of the Windows NT/2000/2003 SAM extended controls. Thesmbpasswdback end is not recommended because it does not scale well or hold any Windows information, such as RIDs for NT-based groups. Thetdbsamback end solves these issues for use in a smaller database (250 users), but is still not an enterprise-class solution. ldapsam_compat- The
ldapsam_compatback end allows continued OpenLDAP support for use with upgraded versions of Samba. tdbsam- The default
tdbsampassword back end provides a database back end for local servers, servers that do not need built-in database replication, and servers that do not require the scalability or complexity of LDAP. Thetdbsamback end includes all of thesmbpasswddatabase information as well as the previously-excluded SAM information. The inclusion of the extended SAM data allows Samba to implement the same account and system access controls as seen with Windows NT/2000/2003/2008-based systems.Thetdbsamback end is recommended for 250 users at most. Larger organizations should require Active Directory or LDAP integration due to scalability and possible network infrastructure concerns. ldapsam- The
ldapsamback end provides an optimal distributed account installation method for Samba. LDAP is optimal because of its ability to replicate its database to any number of servers such as the Red Hat Directory Server or an OpenLDAP Server. LDAP databases are light-weight and scalable, and as such are preferred by large enterprises. Installation and configuration of directory servers is beyond the scope of this chapter. For more information on the Red Hat Directory Server, see the Red Hat Directory Server 9.0 Deployment Guide. For more information on LDAP, see Section 20.1, “OpenLDAP”.If you are upgrading from a previous version of Samba to 3.0, note that the OpenLDAP schema file (/usr/share/doc/samba-version/LDAP/samba.schema) and the Red Hat Directory Server schema file (/usr/share/doc/samba-version/LDAP/samba-schema-FDS.ldif) have changed. These files contain the attribute syntax definitions and objectclass definitions that theldapsamback end needs in order to function properly.As such, if you are using theldapsamback end for your Samba server, you will need to configureslapdto include one of these schema file. See Section 20.1.3.3, “Extending Schema” for directions on how to do this.Note
You need to have the openldap-servers package installed if you want to use theldapsamback end. To ensure that the package is installed, execute the following command asroots:yum install openldap-servers
~]# yum install openldap-serversCopy to Clipboard Copied! Toggle word wrap Toggle overflow
21.1.9. Samba Network Browsing
TCP/IP. NetBIOS-based networking uses broadcast (UDP) messaging to accomplish browse list management. Without NetBIOS and WINS as the primary method for TCP/IP host name resolution, other methods such as static files (/etc/hosts) or DNS, must be used.
21.1.9.1. Domain Browsing
/etc/samba/smb.conf file for a local master browser (or no browsing at all) in a domain controller environment is the same as workgroup configuration (see Section 21.1.4, “Configuring a Samba Server”).
21.1.9.2. WINS (Windows Internet Name Server)
/etc/samba/smb.conf file in which the Samba server is serving as a WINS server:
Example 21.8. An Example Configuration of WINS Server
[global] wins support = yes
[global]
wins support = yesNote
21.1.10. Samba with CUPS Printing Support
21.1.10.1. Simple smb.conf Settings
/etc/samba/smb.conf configuration for CUPS support:
Example 21.9. An Example Configuration of Samba with CUPS Support
print$ directive contains printer drivers for clients to access if not available locally. The print$ directive is optional and may not be required depending on the organization.
browseable to yes enables the printer to be viewed in the Windows Network Neighborhood, provided the Samba server is set up correctly in the domain or workgroup.
21.1.11. Samba Distribution Programs
findsmb
findsmb <subnet_broadcast_address>
findsmb <subnet_broadcast_address>findsmb program is a Perl script which reports information about SMB-aware systems on a specific subnet. If no subnet is specified the local subnet is used. Items displayed include IP address, NetBIOS name, workgroup or domain name, operating system, and version. The findsmb command is used in the following format:
findsmb as any valid user on a system:
net
net <protocol> <function> <misc_options> <target_options>
net <protocol> <function> <misc_options> <target_options>net utility is similar to the net utility used for Windows and MS-DOS. The first argument is used to specify the protocol to use when executing a command. The protocol option can be ads, rap, or rpc for specifying the type of server connection. Active Directory uses ads, Win9x/NT3 uses rap, and Windows NT4/2000/2003/2008 uses rpc. If the protocol is omitted, net automatically tries to determine it.
wakko:
wakko:
nmblookup
nmblookup <options> <netbios_name>
nmblookup <options> <netbios_name>nmblookup program resolves NetBIOS names into IP addresses. The program broadcasts its query on the local subnet until the target machine replies.
IP address of the NetBIOS name trek:
nmblookup trek querying trek on 10.1.59.255 10.1.56.45 trek<00>
~]$ nmblookup trek
querying trek on 10.1.59.255
10.1.56.45 trek<00>pdbedit
pdbedit <options>
pdbedit <options>pdbedit program manages accounts located in the SAM database. All back ends are supported including smbpasswd, LDAP, and the tdb database library.
rpcclient
rpcclient <server> <options>
rpcclient <server> <options>rpcclient program issues administrative commands using Microsoft RPCs, which provide access to the Windows administration graphical user interfaces (GUIs) for systems management. This is most often used by advanced users that understand the full complexity of Microsoft RPCs.
smbcacls
smbcacls <//server/share> <filename> <options>
smbcacls <//server/share> <filename> <options>smbcacls program modifies Windows ACLs on files and directories shared by a Samba server or a Windows server.
smbclient
smbclient <//server/share> <password> <options>
smbclient <//server/share> <password> <options>smbclient program is a versatile UNIX client which provides functionality similar to the ftp utility.
smbcontrol
smbcontrol -i <options>
smbcontrol -i <options>smbcontrol <options> <destination> <messagetype> <parameters>
smbcontrol <options> <destination> <messagetype> <parameters>smbcontrol program sends control messages to running smbd, nmbd, or winbindd daemons. Executing smbcontrol -i runs commands interactively until a blank line or a 'q' is entered.
smbpasswd
smbpasswd <options> <username> <password>
smbpasswd <options> <username> <password>smbpasswd program manages encrypted passwords. This program can be run by a superuser to change any user's password and also by an ordinary user to change their own Samba password.
smbspool
smbspool <job> <user> <title> <copies> <options> <filename>
smbspool <job> <user> <title> <copies> <options> <filename>smbspool program is a CUPS-compatible printing interface to Samba. Although designed for use with CUPS printers, smbspool can work with non-CUPS printers as well.
smbstatus
smbstatus <options>
smbstatus <options>smbstatus program displays the status of current connections to a Samba server.
smbtar
smbtar <options>
smbtar <options>smbtar program performs backup and restores of Windows-based share files and directories to a local tape archive. Though similar to the tar utility, the two are not compatible.
testparm
testparm <options> <filename> <hostname IP_address>
testparm <options> <filename> <hostname IP_address>testparm program checks the syntax of the /etc/samba/smb.conf file. If your smb.conf file is in the default location (/etc/samba/smb.conf) you do not need to specify the location. Specifying the host name and IP address to the testparm program verifies that the hosts.allow and host.deny files are configured correctly. The testparm program also displays a summary of your smb.conf file and the server's role (stand-alone, domain, etc.) after testing. This is convenient when debugging as it excludes comments and concisely presents information for experienced administrators to read. For example:
wbinfo
wbinfo <options>
wbinfo <options>wbinfo program displays information from the winbindd daemon. The winbindd daemon must be running for wbinfo to work.
21.1.12. Additional Resources
Installed Documentation
/usr/share/doc/samba-<version-number>/— All additional files included with the Samba distribution. This includes all helper scripts, sample configuration files, and documentation.- See the following man pages for detailed information specific Samba features:
- smb.conf(5)
- samba(7)
- smbd(8)
- nmbd(8)
- winbindd(8)
Related Books
- The Official Samba-3 HOWTO-Collection by John H. Terpstra and Jelmer R. Vernooij; Prentice Hall — The official Samba-3 documentation as issued by the Samba development team. This is more of a reference guide than a step-by-step guide.
- Samba-3 by Example by John H. Terpstra; Prentice Hall — This is another official release issued by the Samba development team which discusses detailed examples of OpenLDAP, DNS, DHCP, and printing configuration files. This has step-by-step related information that helps in real-world implementations.
- Using Samba, 2nd Edition by Jay Ts, Robert Eckstein, and David Collier-Brown; O'Reilly — A good resource for novice to advanced users, which includes comprehensive reference material.
Useful Websites
- http://www.samba.org/ — Homepage for the Samba distribution and all official documentation created by the Samba development team. Many resources are available in HTML and PDF formats, while others are only available for purchase. Although many of these links are not Red Hat Enterprise Linux specific, some concepts may apply.
- http://samba.org/samba/archives.html — Active email lists for the Samba community. Enabling digest mode is recommended due to high levels of list activity.
- Samba newsgroups — Samba threaded newsgroups, such as www.gmane.org, that use the
NNTPprotocol are also available. This an alternative to receiving mailing list emails.
21.2. FTP
FTP) is one of the oldest and most commonly used protocols found on the Internet today. Its purpose is to reliably transfer files between computer hosts on a network without requiring the user to log directly in to the remote host or to have knowledge of how to use the remote system. It allows users to access files on remote systems using a standard set of simple commands.
FTP protocol and introduces vsftpd, the primary FTP server shipped with Red Hat Enterprise Linux.
21.2.1. The File Transfer Protocol
TCP network protocol. Because FTP is a rather old protocol, it uses unencrypted user name and password authentication. For this reason, it is considered an insecure protocol and should not be used unless absolutely necessary. However, because FTP is so prevalent on the Internet, it is often required for sharing files to the public. System administrators, therefore, should be aware of FTP's unique characteristics.
TLS and how to secure an FTP server with the help of SELinux. A good substitute for FTP is sftp from the OpenSSH suite of tools. For information about configuring OpenSSH and about the SSH protocol in general, see Chapter 14, OpenSSH.
FTP requires multiple network ports to work properly. When an FTP client application initiates a connection to an FTP server, it opens port 21 on the server — known as the command port. This port is used to issue all commands to the server. Any data requested from the server is returned to the client via a data port. The port number for data connections, and the way in which data connections are initialized, vary depending upon whether the client requests the data in active or passive mode.
- active mode
- Active mode is the original method used by the
FTPprotocol for transferring data to the client application. When an active-mode data transfer is initiated by theFTPclient, the server opens a connection from port20on the server to theIPaddress and a random, unprivileged port (greater than1024) specified by the client. This arrangement means that the client machine must be allowed to accept connections over any port above1024. With the growth of insecure networks, such as the Internet, the use of firewalls for protecting client machines is now prevalent. Because these client-side firewalls often deny incoming connections from active-modeFTPservers, passive mode was devised. - passive mode
- Passive mode, like active mode, is initiated by the
FTPclient application. When requesting data from the server, theFTPclient indicates it wants to access the data in passive mode and the server provides theIPaddress and a random, unprivileged port (greater than1024) on the server. The client then connects to that port on the server to download the requested information.While passive mode does resolve issues for client-side firewall interference with data connections, it can complicate administration of the server-side firewall. You can reduce the number of open ports on a server by limiting the range of unprivileged ports on theFTPserver. This also simplifies the process of configuring firewall rules for the server. See Section 21.2.2.6.8, “Network Options” for more information about limiting passive ports.
21.2.2. The vsftpd Server
vsftpd) is designed from the ground up to be fast, stable, and, most importantly, secure. vsftpd is the only stand-alone FTP server distributed with Red Hat Enterprise Linux, due to its ability to handle large numbers of connections efficiently and securely.
vsftpd has three primary aspects:
- Strong separation of privileged and non-privileged processes — Separate processes handle different tasks, and each of these processes runs with the minimal privileges required for the task.
- Tasks requiring elevated privileges are handled by processes with the minimal privilege necessary — By taking advantage of compatibilities found in the
libcaplibrary, tasks that usually require full root privileges can be executed more safely from a less privileged process. - Most processes run in a
chrootjail — Whenever possible, processes are change-rooted to the directory being shared; this directory is then considered achrootjail. For example, if the/var/ftp/directory is the primary shared directory,vsftpdreassigns/var/ftp/to the new root directory, known as/. This disallows any potential malicious hacker activities for any directories not contained in the new root directory.
vsftpd deals with requests:
- The parent process runs with the least privileges required — The parent process dynamically calculates the level of privileges it requires to minimize the level of risk. Child processes handle direct interaction with the
FTPclients and run with as close to no privileges as possible. - All operations requiring elevated privileges are handled by a small parent process — Much like the Apache
HTTPServer,vsftpdlaunches unprivileged child processes to handle incoming connections. This allows the privileged, parent process to be as small as possible and handle relatively few tasks. - All requests from unprivileged child processes are distrusted by the parent process — Communication with child processes is received over a socket, and the validity of any information from child processes is checked before being acted on.
- Most interactions with
FTPclients are handled by unprivileged child processes in achrootjail — Because these child processes are unprivileged and only have access to the directory being shared, any crashed processes only allow the attacker access to the shared files.
21.2.2.1. Starting and Stopping vsftpd
/etc/rc.d/init.d/vsftpd script, which can be accessed using the service command.
root:
service vsftpd start
~]# service vsftpd startservice vsftpd stop
~]# service vsftpd stoprestart option is a shorthand way of stopping and then starting vsftpd. This is the most efficient way to make configuration changes take effect after editing the configuration file for vsftpd.
root:
service vsftpd restart
~]# service vsftpd restartcondrestart (conditional restart) option only stops and starts vsftpd if it is currently running. This option is useful for scripts, because it does not start the daemon if it is not running. The try-restart option is a synonym.
service vsftpd condrestart
~]# service vsftpd condrestartvsftpd service does not start automatically at boot time. To configure the vsftpd service to start at boot time, use an initscript utility, such as /sbin/chkconfig, /usr/sbin/ntsysv, or the Services Configuration Tool program. See Chapter 12, Services and Daemons for more information regarding these tools.
21.2.2.2. Starting Multiple Copies of vsftpd
FTP domains. This is a technique called multihoming. One way to multihome using vsftpd is by running multiple copies of the daemon, each with its own configuration file.
IP addresses to network devices or alias network devices on the system. For more information about configuring network devices, device aliases, see Chapter 10, NetworkManager. For additional information about network configuration scripts, see Chapter 11, Network Interfaces.
FTP domains must be configured to reference the correct machine. For information about BIND, the DNS protocol implementation used in Red Hat Enterprise Linux, and its configuration files, see Section 17.2, “BIND”.
vsftpd to answer requests on different IP addresses, multiple copies of the daemon must be running. In order to make this possible, a separate vsftpd configuration file for each required instance of the FTP server must be created and placed in the /etc/vsftpd/ directory. Note that each of these configuration files must have a unique name (such as /etc/vsftpd/vsftpd-site-2.conf) and must be readable and writable only by the root user.
FTP server listening on an IPv4 network, the following directive must be unique:
listen_address=N.N.N.N
listen_address=N.N.N.NIP address for the FTP site being served. If the site is using IPv6, use the listen_address6 directive instead.
/etc/vsftpd/ directory, all configured instances of the vsftpd daemon can be started by executing the following command as root:
service vsftpd start
~]# service vsftpd startservice commands.
vsftpd daemon can be launched from a root shell prompt using the following command:
vsftpd /etc/vsftpd/configuration-file
~]# vsftpd /etc/vsftpd/configuration-filevsftpd-site-2.conf.
anon_rootlocal_rootvsftpd_log_filexferlog_file
vsftpd daemon, see Section 21.2.2.5, “Files Installed with vsftpd”.
21.2.2.3. Encrypting vsftpd Connections Using TLS
FTP, which transmits user names, passwords, and data without encryption by default, the vsftpd daemon can be configured to utilize the TLS protocol to authenticate connections and encrypt all transfers. Note that an FTP client that supports TLS is needed to communicate with vsftpd with TLS enabled.
Note
SSL (Secure Sockets Layer) is the name of an older implementation of the security protocol. The new versions are called TLS (Transport Layer Security). Only the newer versions (TLS) should be used as SSL suffers from serious security vulnerabilities. The documentation included with the vsftpd server, as well as the configuration directives used in the vsftpd.conf file, use the SSL name when referring to security-related matters, but TLS is supported and used by default when the ssl_enable directive is set to YES.
ssl_enable configuration directive in the vsftpd.conf file to YES to turn on TLS support. The default settings of other TLS-related directives that become automatically active when the ssl_enable option is enabled provide for a reasonably well-configured TLS set up. This includes, among other things, the requirement to only use the TLS v1 protocol for all connections (the use of the insecure SSL protocol versions is disabled by default) or forcing all non-anonymous logins to use TLS for sending passwords and data transfers.
Example 21.10. Configuring vsftpd to Use TLS
SSL versions of the security protocol in the vsftpd.conf file:
ssl_enable=YES ssl_tlsv1=YES ssl_sslv2=NO ssl_sslv3=NO
ssl_enable=YES
ssl_tlsv1=YES
ssl_sslv2=NO
ssl_sslv3=NOvsftpd service after you modify its configuration:
service vsftpd restart
~]# service vsftpd restartTLS-related configuration directives for fine-tuning the use of TLS by vsftpd. Also, see Section 21.2.2.6, “vsftpd Configuration Options” for a description of other commonly used vsftpd.conf configuration directives.
21.2.2.4. SELinux Policy for vsftpd
vsftpd daemon (as well as other ftpd processes), defines a mandatory access control, which, by default, is based on least access required. In order to allow the FTP daemon to access specific files or directories, appropriate labels need to be assigned to them.
public_content_t label must be assigned to the files and directories to be shared. You can do this using the chcon command as root:
chcon -R -t public_content_t /path/to/directory
~]# chcon -R -t public_content_t /path/to/directorypublic_content_rw_t label. In addition to that, the allow_ftpd_anon_write SELinux Boolean option must be set to 1. Use the setsebool command as root to do that:
setsebool -P allow_ftpd_anon_write=1
~]# setsebool -P allow_ftpd_anon_write=1FTP, which is the default setting on Red Hat Enterprise Linux 6, the ftp_home_dir Boolean option needs to be set to 1. If vsftpd is to be allowed to run in standalone mode, which is also enabled by default on Red Hat Enterprise Linux 6, the ftpd_is_daemon option needs to be set to 1 as well.
FTP. Also, see the Red Hat Enterprise Linux 6 Security-Enhanced Linux for more detailed information about SELinux in general.
21.2.2.5. Files Installed with vsftpd
vsftpd), its configuration and related files, as well as FTP directories onto the system. The following lists the files and directories related to vsftpd configuration:
/etc/pam.d/vsftpd— The Pluggable Authentication Modules (PAM) configuration file forvsftpd. This file specifies the requirements a user must meet to log in to theFTPserver. For more information on PAM, see the Using Pluggable Authentication Modules (PAM) chapter of the Red Hat Enterprise Linux 6 Single Sign-On and Smart Cards guide./etc/vsftpd/vsftpd.conf— The configuration file forvsftpd. See Section 21.2.2.6, “vsftpd Configuration Options” for a list of important options contained within this file./etc/vsftpd/ftpusers— A list of users not allowed to log in tovsftpd. By default, this list includes theroot,bin, anddaemonusers, among others./etc/vsftpd/user_list— This file can be configured to either deny or allow access to the users listed, depending on whether theuserlist_denydirective is set toYES(default) orNOin/etc/vsftpd/vsftpd.conf. If/etc/vsftpd/user_listis used to grant access to users, the user names listed must not appear in/etc/vsftpd/ftpusers./var/ftp/— The directory containing files served byvsftpd. It also contains the/var/ftp/pub/directory for anonymous users. Both directories are world-readable, but writable only by therootuser.
21.2.2.6. vsftpd Configuration Options
FTP servers have, it offers enough options to satisfy most administrators' needs. The fact that it is not overly feature-laden limits configuration and programmatic errors.
vsftpd is handled by its configuration file, /etc/vsftpd/vsftpd.conf. Each directive is on its own line within the file and follows the following format:
directive=value
directive=valueImportant
#) and are ignored by the daemon.
vsftpd.conf. For an overview of ways to secure vsftpd, see the Red Hat Enterprise Linux 6 Security Guide.
/etc/vsftpd/vsftpd.conf. All directives not explicitly found or commented out within the vsftpd's configuration file are set to their default value.
21.2.2.6.1. Daemon Options
vsftpd daemon.
listen— When enabled,vsftpdruns in standalone mode, which means that the daemon is started independently, not by thexinetdsuper-server. Red Hat Enterprise Linux 6 sets this value toYES. Note that the SELinuxftpd_is_daemonBoolean option needs to be set forvsftpdto be allowed to run in standalone mode. See Section 21.2.2.4, “SELinux Policy for vsftpd” and toftpd_selinux(8)for more information onvsftpd's interaction with the default SELinux policy. This directive cannot be used in conjunction with thelisten_ipv6directive.The default value isNO. On Red Hat Enterprise Linux 6, this option is set toYESin the configuration file.listen_ipv6— When enabled,vsftpdruns in standalone mode, which means that the daemon is started independently, not by thexinetdsuper-server. With this directive, it only listens onIPv6sockets. Note that the SELinuxftpd_is_daemonBoolean option needs to be set forvsftpdto be allowed to run in standalone mode. See Section 21.2.2.4, “SELinux Policy for vsftpd” and toftpd_selinux(8)for more information onvsftpd's interaction with the default SELinux policy. This directive cannot be used in conjunction with thelistendirective.The default value isNO.session_support— When enabled,vsftpdattempts to maintain login sessions for each user through Pluggable Authentication Modules (PAM). For more information, see the Using Pluggable Authentication Modules (PAM) chapter of the Red Hat Enterprise Linux 6 Single Sign-On and Smart Cards and the PAM man pages. If session logging is not necessary, disabling this option allowsvsftpdto run with less processes and lower privileges.The default value isNO.
21.2.2.6.2. Log In Options and Access Controls
anonymous_enable— When enabled, anonymous users are allowed to log in. The user namesanonymousandftpare accepted.The default value isYES.See Section 21.2.2.6.3, “Anonymous User Options” for a list of directives affecting anonymous users.banned_email_file— If thedeny_email_enabledirective is set toYES, this directive specifies the file containing a list of anonymous email passwords that are not permitted access to the server.The default value is/etc/vsftpd/banned_emails.banner_file— Specifies the file containing text displayed when a connection is established to the server. This option overrides any text specified in theftpd_bannerdirective.There is no default value for this directive.cmds_allowed— Specifies a comma-delimited list ofFTPcommands allowed by the server. All other commands are rejected.There is no default value for this directive.deny_email_enable— When enabled, any anonymous user utilizing email passwords specified in/etc/vsftpd/banned_emailsare denied access to the server. The name of the file referenced by this directive can be specified using thebanned_email_filedirective.The default value isNO.ftpd_banner— When enabled, the string specified within this directive is displayed when a connection is established to the server. This option can be overridden by thebanner_filedirective.By default,vsftpddisplays its standard banner.local_enable— When enabled, local users are allowed to log in to the system. Note that the SELinuxftp_home_dirBoolean option needs to be set for this directive to work as expected. See Section 21.2.2.4, “SELinux Policy for vsftpd” and toftpd_selinux(8)for more information onvsftpd's interaction with the default SELinux policy.The default value isNO. On Red Hat Enterprise Linux 6, this option is set toYESin the configuration file.See Section 21.2.2.6.4, “Local-User Options” for a list of directives affecting local users.pam_service_name— Specifies the PAM service name forvsftpd.The default value isftp. On Red Hat Enterprise Linux 6, this option is set tovsftpdin the configuration file.tcp_wrappers— When enabled, TCP wrappers are used to grant access to the server. If the FTP server is configured on multiple IP addresses, theVSFTPD_LOAD_CONFenvironment variable can be used to load different configuration files based on the IP address being requested by the client.The default value isNO. On Red Hat Enterprise Linux 6, this option is set toYESin the configuration file.userlist_deny— When used in conjunction with theuserlist_enabledirective and set toNO, all local users are denied access unless their user name is listed in the file specified by theuserlist_filedirective. Because access is denied before the client is asked for a password, setting this directive toNOprevents local users from submitting unencrypted passwords over the network.The default value isYES.userlist_enable— When enabled, users listed in the file specified by theuserlist_filedirective are denied access. Because access is denied before the client is asked for a password, users are prevented from submitting unencrypted passwords over the network.The default value isNO. On Red Hat Enterprise Linux 6, this option is set toYESin the configuration file.userlist_file— Specifies the file referenced byvsftpdwhen theuserlist_enabledirective is enabled.The default value is/etc/vsftpd/user_list
21.2.2.6.3. Anonymous User Options
anonymous_enable directive must be set to YES.
anon_mkdir_write_enable— When enabled in conjunction with thewrite_enabledirective, anonymous users are allowed to create new directories within a parent directory that has write permissions.The default value isNO.anon_root— Specifies the directoryvsftpdchanges to after an anonymous user logs in.There is no default value for this directive.anon_upload_enable— When enabled in conjunction with thewrite_enabledirective, anonymous users are allowed to upload files within a parent directory that has write permissions.The default value isNO.anon_world_readable_only— When enabled, anonymous users are only allowed to download world-readable files.The default value isYES.ftp_username— Specifies the local user account (listed in/etc/passwd) used for the anonymousFTPuser. The home directory specified in/etc/passwdfor the user is the root directory of the anonymousFTPuser.The default value isftpno_anon_password— When enabled, the anonymous user is not asked for a password.The default value isNO.secure_email_list_enable— When enabled, only a specified list of email passwords for anonymous logins is accepted. This is a convenient way of offering limited security to public content without the need for virtual users.Anonymous logins are prevented unless the password provided is listed in/etc/vsftpd/email_passwords. The file format is one password per line, with no trailing white spaces.The default value isNO.
21.2.2.6.4. Local-User Options
local_enable directive must be set to YES. Note that the SELinux ftp_home_dir Boolean option needs to be set for users to be able to access their home directories. See Section 21.2.2.4, “SELinux Policy for vsftpd” and to ftpd_selinux(8) for more information on vsftpd's interaction with the default SELinux policy.
chmod_enable— When enabled, theFTPcommandSITE CHMODis allowed for local users. This command allows the users to change the permissions on files.The default value isYES.chroot_list_enable— When enabled, the local users listed in the file specified in thechroot_list_filedirective are placed in achrootjail upon log in.If enabled in conjunction with thechroot_local_userdirective, the local users listed in the file specified in thechroot_list_filedirective are not placed in achrootjail upon log in.The default value isNO.chroot_list_file— Specifies the file containing a list of local users referenced when thechroot_list_enabledirective is set toYES.The default value is/etc/vsftpd/chroot_listchroot_local_user— When enabled, local users are change-rooted to their home directories after logging in.The default value isNO.Warning
Enablingchroot_local_useropens up a number of security issues, especially for users with upload privileges. For this reason, it is not recommended.guest_enable— When enabled, all non-anonymous users are logged in as the userguest, which is the local user specified in theguest_usernamedirective.The default value isNO.guest_username— Specifies the user name theguestuser is mapped to.The default value isftplocal_root— Specifies the directoryvsftpdchanges to after a local user logs in.There is no default value for this directive.local_umask— Specifies the umask value for file creation. Note that the default value is in octal form (a numerical system with a base of eight), which includes a “0” prefix. Otherwise, the value is treated as a base-10 integer.The default value is077. On Red Hat Enterprise Linux 6, this option is set to022in the configuration file.passwd_chroot_enable— When enabled in conjunction with thechroot_local_userdirective,vsftpdchange-roots local users based on the occurrence of/./in the home-directory field within/etc/passwd.The default value isNO.user_config_dir— Specifies the path to a directory containing configuration files bearing the names of local system users that contain specific settings for those users. Any directive in a user's configuration file overrides those found in/etc/vsftpd/vsftpd.conf.There is no default value for this directive.
21.2.2.6.5. Directory Options
dirlist_enable— When enabled, users are allowed to view directory lists.The default value isYES.dirmessage_enable— When enabled, a message is displayed whenever a user enters a directory with a message file. This message resides within the current directory. The name of this file is specified in themessage_filedirective and is.messageby default.The default value isNO. On Red Hat Enterprise Linux 6, this option is set toYESin the configuration file.force_dot_files— When enabled, files beginning with a dot (.) are listed in directory listings, with the exception of the.and..files.The default value isNO.hide_ids— When enabled, all directory listings showftpas the user and group for each file.The default value isNO.message_file— Specifies the name of the message file when using thedirmessage_enabledirective.The default value is.messagetext_userdb_names— When enabled, text user names and group names are used in place of UID and GID entries. Enabling this option may negatively affect the performance of the server.The default value isNO.use_localtime— When enabled, directory listings reveal the local time for the computer instead of GMT.The default value isNO.
21.2.2.6.6. File Transfer Options
download_enable— When enabled, file downloads are permitted.The default value isYES.chown_uploads— When enabled, all files uploaded by anonymous users are owned by the user specified in thechown_usernamedirective.The default value isNO.chown_username— Specifies the ownership of anonymously uploaded files if thechown_uploadsdirective is enabled.The default value isrootwrite_enable— When enabled,FTPcommands which can change the file system are allowed, such asDELE,RNFR, andSTOR.The default value isNO. On Red Hat Enterprise Linux 6, this option is set toYESin the configuration file.
21.2.2.6.7. Logging Options
vsftpd's logging behavior.
dual_log_enable— When enabled in conjunction withxferlog_enable,vsftpdwrites two files simultaneously: awu-ftpd-compatible log to the file specified in thexferlog_filedirective (/var/log/xferlogby default) and a standardvsftpdlog file specified in thevsftpd_log_filedirective (/var/log/vsftpd.logby default).The default value isNO.log_ftp_protocol— When enabled in conjunction withxferlog_enableand withxferlog_std_formatset toNO, allFTPcommands and responses are logged. This directive is useful for debugging.The default value isNO.syslog_enable— When enabled in conjunction withxferlog_enable, all logging normally written to the standardvsftpdlog file specified in thevsftpd_log_filedirective (/var/log/vsftpd.logby default) is sent to the system logger instead under theFTPDfacility.The default value isNO.vsftpd_log_file— Specifies thevsftpdlog file. For this file to be used,xferlog_enablemust be enabled andxferlog_std_formatmust either be set toNOor, ifxferlog_std_formatis set toYES,dual_log_enablemust be enabled. It is important to note that ifsyslog_enableis set toYES, the system log is used instead of the file specified in this directive.The default value is/var/log/vsftpd.logxferlog_enable— When enabled,vsftpdlogs connections (vsftpdformat only) and file-transfer information to the log file specified in thevsftpd_log_filedirective (/var/log/vsftpd.logby default). Ifxferlog_std_formatis set toYES, file-transfer information is logged, but connections are not, and the log file specified inxferlog_file(/var/log/xferlogby default) is used instead. It is important to note that both log files and log formats are used ifdual_log_enableis set toYES.The default value isNO. On Red Hat Enterprise Linux 6, this option is set toYESin the configuration file.xferlog_file— Specifies thewu-ftpd-compatible log file. For this file to be used,xferlog_enablemust be enabled andxferlog_std_formatmust be set toYES. It is also used ifdual_log_enableis set toYES.The default value is/var/log/xferlogxferlog_std_format— When enabled in conjunction withxferlog_enable, only awu-ftpd-compatible file-transfer log is written to the file specified in thexferlog_filedirective (/var/log/xferlogby default). It is important to note that this file only logs file transfers and does not log connections to the server.The default value isNO. On Red Hat Enterprise Linux 6, this option is set toYESin the configuration file.
Important
wu-ftpd FTP server, the xferlog_std_format directive is set to YES under Red Hat Enterprise Linux 6. However, this setting means that connections to the server are not logged. To both log connections in vsftpd format and maintain a wu-ftpd-compatible file-transfer log, set dual_log_enable to YES. If maintaining a wu-ftpd-compatible file-transfer log is not important, either set xferlog_std_format to NO, comment the line with a hash symbol (“#”), or delete the line entirely.
21.2.2.6.8. Network Options
vsftpd interacts with the network.
accept_timeout— Specifies the amount of time for a client using passive mode to establish a connection.The default value is60.anon_max_rate— Specifies the maximum data transfer rate for anonymous users in bytes per second.The default value is0, which does not limit the transfer rate.connect_from_port_20— When enabled,vsftpdruns with enough privileges to open port20on the server during active-mode data transfers. Disabling this option allowsvsftpdto run with less privileges but may be incompatible with someFTPclients.The default value isNO. On Red Hat Enterprise Linux 6, this option is set toYESin the configuration file.connect_timeout— Specifies the maximum amount of time a client using active mode has to respond to a data connection, in seconds.The default value is60.data_connection_timeout— Specifies maximum amount of time data transfers are allowed to stall, in seconds. Once triggered, the connection to the remote client is closed.The default value is300.ftp_data_port— Specifies the port used for active data connections whenconnect_from_port_20is set toYES.The default value is20.idle_session_timeout— Specifies the maximum amount of time between commands from a remote client. Once triggered, the connection to the remote client is closed.The default value is300.listen_address— Specifies theIPaddress on whichvsftpdlistens for network connections.There is no default value for this directive.Note
If running multiple copies ofvsftpdserving differentIPaddresses, the configuration file for each copy of thevsftpddaemon must have a different value for this directive. See Section 21.2.2.2, “Starting Multiple Copies of vsftpd” for more information about multihomedFTPservers.listen_address6— Specifies theIPv6address on whichvsftpdlistens for network connections whenlisten_ipv6is set toYES.There is no default value for this directive.Note
If running multiple copies ofvsftpdserving differentIPaddresses, the configuration file for each copy of thevsftpddaemon must have a different value for this directive. See Section 21.2.2.2, “Starting Multiple Copies of vsftpd” for more information about multihomedFTPservers.listen_port— Specifies the port on whichvsftpdlistens for network connections.The default value is21.local_max_rate— Specifies the maximum rate at which data is transferred for local users logged in to the server in bytes per second.The default value is0, which does not limit the transfer rate.max_clients— Specifies the maximum number of simultaneous clients allowed to connect to the server when it is running in standalone mode. Any additional client connections would result in an error message.The default value is0, which does not limit connections.max_per_ip— Specifies the maximum number of clients allowed to connect from the same sourceIPaddress.The default value is50. The value0switches off the limit.pasv_address— Specifies theIPaddress for the public-facingIPaddress of the server for servers behind Network Address Translation (NAT) firewalls. This enablesvsftpdto hand out the correct return address for passive-mode connections.There is no default value for this directive.pasv_enable— When enabled, passive-mode connections are allowed.The default value isYES.pasv_max_port— Specifies the highest possible port sent toFTPclients for passive-mode connections. This setting is used to limit the port range so that firewall rules are easier to create.The default value is0, which does not limit the highest passive-port range. The value must not exceed65535.pasv_min_port— Specifies the lowest possible port sent toFTPclients for passive-mode connections. This setting is used to limit the port range so that firewall rules are easier to create.The default value is0, which does not limit the lowest passive-port range. The value must not be lower than1024.pasv_promiscuous— When enabled, data connections are not checked to make sure they are originating from the sameIPaddress. This setting is only useful for certain types of tunneling.Warning
Do not enable this option unless absolutely necessary as it disables an important security feature, which verifies that passive-mode connections originate from the sameIPaddress as the control connection that initiates the data transfer.The default value isNO.port_enable— When enabled, active-mode connects are allowed.The default value isYES.
21.2.2.6.9. Security Options
vsftpd security.
isolate_network— If enabled,vsftpduses theCLONE_NEWNETcontainer flag to isolate the unprivileged protocol handler processes, so that they cannot arbitrarily callconnect()and instead have to ask the privileged process for sockets (theport_promiscuousoption must be disabled).The default value isYES.isolate— If enabled,vsftpduses theCLONE_NEWPIDandCLONE_NEWIPCcontainer flags to isolate processes to their IPC and PID namespaces to prevent them from interacting with each other.The default value isYES.ssl_enable— Enablesvsftpd's support forSSL(includingTLS). SSL is used both for authentication and subsequent data transfers. Note that all otherSSL-related options are only applicable ifssl_enableis set toYES.The default value isNO.allow_anon_ssl— Specifies whether anonymous users should be allowed to use securedSSLconnections.The default value isNO.require_cert— If enabled, allSSLclient connections are required to present a client certificate.The default value isNO.
21.2.3. Additional Resources
vsftpd configuration, see the following resources.
21.2.3.1. Installed Documentation
- The
/usr/share/doc/vsftpd-version-number/directory — TheTUNINGfile contains basic performance-tuning tips and theSECURITY/directory contains information about the security model employed byvsftpd. vsftpd-related man pages — There are a number of man pages for the daemon and the configuration files. The following lists some of the more important man pages.- Server Applications
- vsftpd(8) — Describes available command-line options for
vsftpd.
- Configuration Files
- vsftpd.conf(5) — Contains a detailed list of options available within the configuration file for
vsftpd. - hosts_access(5) — Describes the format and options available within the
TCPwrappers configuration files:hosts.allowandhosts.deny.
- Interaction with SELinux
man ftpd_selinux— Contains a description of the SELinux policy governingftpdprocesses as well as an explanation of the way SELinux labels need to be assigned and Booleans set.
21.2.3.2. Online Documentation
- About vsftpd and FTP in General
- http://vsftpd.beasts.org/ — The
vsftpdproject page is a great place to locate the latest documentation and to contact the author of the software. - http://slacksite.com/other/ftp.html — This website provides a concise explanation of the differences between active and passive-mode
FTP.
- Red Hat Enterprise Linux Documentation
- Red Hat Enterprise Linux 6 Security-Enhanced Linux — The Security-Enhanced Linux for Red Hat Enterprise Linux 6 describes the basic principles of SELinux and documents in detail how to configure and use SELinux with various services such as the Apache HTTP Server, Postfix, PostgreSQL, or OpenShift. It explains how to configure SELinux access permissions for system services managed by systemd.
- Red Hat Enterprise Linux 6 Security Guide — The Security Guide for Red Hat Enterprise Linux 6 assists users and administrators in learning the processes and practices of securing their workstations and servers against local and remote intrusion, exploitation, and malicious activity. It also explains how to secure critical system services.
- Relevant RFC Documents
21.3. Printer Configuration
Important
cupsd.conf man page documents configuration of a CUPS server. It includes directives for enabling SSL support. However, CUPS does not allow control of the protocol versions used. Due to the vulnerability described in Resolution for POODLE SSLv3.0 vulnerability (CVE-2014-3566) for components that do not allow SSLv3 to be disabled via configuration settings, Red Hat recommends that you do not rely on this for security. It is recommend that you use stunnel to provide a secure tunnel and disable SSLv3. For more information on using stunnel, see the Red Hat Enterprise Linux 6 Security Guide.
SSH as described in Section 14.5.1, “X11 Forwarding”.
Note
21.3.1. Starting the Printer Configuration Tool
system-config-printer command from the command line to start the tool.
Figure 21.3. Printer Configuration window
21.3.2. Starting Printer Setup
- Start the Printer Configuration tool (see Section 21.3.1, “Starting the Printer Configuration Tool”).
- Go to → → .
- In the Authenticate dialog box, type the root user password and confirm.
- Select the printer connection type and provide its details in the area on the right.
21.3.3. Adding a Local Printer
- Open the
New Printerdialog (see Section 21.3.2, “Starting Printer Setup”). - If the device does not appear automatically, select the port to which the printer is connected in the list on the left (such as Serial Port #1 or LPT #1).
- On the right, enter the connection properties:
- for Other
- URI (for example file:/dev/lp0)
- for Serial Port
- Baud RateParityData BitsFlow Control
Figure 21.4. Adding a local printer
- Click .
- Select the printer model. See Section 21.3.8, “Selecting the Printer Model and Finishing” for details.
21.3.4. Adding an AppSocket/HP JetDirect printer
- Open the
New Printerdialog (see Section 21.3.1, “Starting the Printer Configuration Tool”). - In the list on the left, select → .
- On the right, enter the connection settings:
- Hostname
- Printer host name or IP address.
- Port Number
- Printer port listening for print jobs (
9100by default).
Figure 21.5. Adding a JetDirect printer
- Click .
- Select the printer model. See Section 21.3.8, “Selecting the Printer Model and Finishing” for details.
21.3.5. Adding an IPP Printer
- Open the
New Printerdialog (see Section 21.3.2, “Starting Printer Setup”). - In the list of devices on the left, select and or .
- On the right, enter the connection settings:
- Host
- The host name of the IPP printer.
- Queue
- The queue name to be given to the new queue (if the box is left empty, a name based on the device node will be used).
Figure 21.6. Adding an IPP printer
- Click to continue.
- Select the printer model. See Section 21.3.8, “Selecting the Printer Model and Finishing” for details.
21.3.6. Adding an LPD/LPR Host or Printer
- Open the
New Printerdialog (see Section 21.3.2, “Starting Printer Setup”). - In the list of devices on the left, select → .
- On the right, enter the connection settings:
- Host
- The host name of the LPD/LPR printer or host.Optionally, click to find queues on the LPD host.
- Queue
- The queue name to be given to the new queue (if the box is left empty, a name based on the device node will be used).
Figure 21.7. Adding an LPD/LPR printer
- Click to continue.
- Select the printer model. See Section 21.3.8, “Selecting the Printer Model and Finishing” for details.
21.3.7. Adding a Samba (SMB) printer
Note
root:
yum install samba-client
yum install samba-client- Open the
New Printerdialog (see Section 21.3.2, “Starting Printer Setup”). - In the list on the left, select → .
- Enter the SMB address in the smb:// field. Use the format computer name/printer share. In Figure 21.8, “Adding a SMB printer”, the computer name is
dellboxand the printer share isr2.Figure 21.8. Adding a SMB printer
- Click to see the available workgroups/domains. To display only queues of a particular host, type in the host name (NetBios name) and click .
- Select either of the options:
- Prompt user if authentication is required: user name and password are collected from the user when printing a document.
- Set authentication details now: provide authentication information now so it is not required later. In the Username field, enter the user name to access the printer. This user must exist on the SMB system, and the user must have permission to access the printer. The default user name is typically
guestfor Windows servers, ornobodyfor Samba servers.
- Enter the Password (if required) for the user specified in the Username field.
Warning
Samba printer user names and passwords are stored in the printer server as unencrypted files readable by root and the Linux Printing Daemon, lpd. Thus, other users that have root access to the printer server can view the user name and password you use to access the Samba printer.Therefore, when you choose a user name and password to access a Samba printer, it is advisable that you choose a password that is different from what you use to access your local Red Hat Enterprise Linux system.If there are files shared on the Samba print server, it is recommended that they also use a password different from what is used by the print queue. - Click to test the connection. Upon successful verification, a dialog box appears confirming printer share accessibility.
- Click .
- Select the printer model. See Section 21.3.8, “Selecting the Printer Model and Finishing” for details.
21.3.8. Selecting the Printer Model and Finishing
- In the window displayed after the automatic driver detection has failed, select one of the following options:
- Select a Printer from database — the system chooses a driver based on the selected make of your printer from the list of Makes. If your printer model is not listed, choose Generic.
- Provide PPD file — the system uses the provided PostScript Printer Description (PPD) file for installation. A PPD file may also be delivered with your printer as being normally provided by the manufacturer. If the PPD file is available, you can choose this option and use the browser bar below the option description to select the PPD file.
- Search for a printer driver to download — enter the make and model of your printer into the Make and model field to search on OpenPrinting.org for the appropriate packages.
Figure 21.9. Selecting a printer brand
- Depending on your previous choice provide details in the area displayed below:
- Printer brand for the Select printer from database option.
- PPD file location for the Provide PPD file option.
- Printer make and model for the Search for a printer driver to download option.
- Click to continue.
- If applicable for your option, window shown in Figure 21.10, “Selecting a printer model” appears. Choose the corresponding model in the Models column on the left.
Note
On the right, the recommended printer driver is automatically selected; however, you can select another available driver. The print driver processes the data that you want to print into a format the printer can understand. Since a local printer is attached directly to your computer, you need a printer driver to process the data that is sent to the printer.Figure 21.10. Selecting a printer model
- Click .
- Under the
Describe Printerenter a unique name for the printer in the Printer Name field. The printer name can contain letters, numbers, dashes (-), and underscores (_); it must not contain any spaces. You can also use the Description and Location fields to add further printer information. Both fields are optional, and may contain spaces.Figure 21.11. Printer setup
- Click to confirm your printer configuration and add the print queue if the settings are correct. Click to modify the printer configuration.
- After the changes are applied, a dialog box appears allowing you to print a test page. Click to print a test page now. Alternatively, you can print a test page later as described in Section 21.3.9, “Printing a Test Page”.
21.3.9. Printing a Test Page
- Right-click the printer in the Printing window and click .
- In the Properties window, click Settings on the left.
- On the displayed Settings tab, click the button.
21.3.10. Modifying Existing Printers
21.3.10.1. The Settings Page
Figure 21.12. Settings page
21.3.10.2. The Policies Page
21.3.10.2.1. Sharing Printers
Figure 21.13. Policies page
21.3.10.2.2. The Access Control Page
Figure 21.14. Access Control page
21.3.10.2.3. The Printer Options Page
Figure 21.15. Printer Options page
21.3.10.2.4. Job Options Page
Figure 21.16. Job Options page
21.3.10.2.5. Ink/Toner Levels Page
Figure 21.17. Ink/Toner Levels page
21.3.10.3. Managing Print Jobs
Figure 21.18. GNOME Print Status
lpstat -o. The last few lines look similar to the following:
Example 21.11. Example of lpstat -o output
lpstat -o Charlie-60 twaugh 1024 Tue 08 Feb 2011 16:42:11 GMT Aaron-61 twaugh 1024 Tue 08 Feb 2011 16:42:44 GMT Ben-62 root 1024 Tue 08 Feb 2011 16:45:42 GMT
$ lpstat -o
Charlie-60 twaugh 1024 Tue 08 Feb 2011 16:42:11 GMT
Aaron-61 twaugh 1024 Tue 08 Feb 2011 16:42:44 GMT
Ben-62 root 1024 Tue 08 Feb 2011 16:45:42 GMTlpstat -o and then use the command cancel job number. For example, cancel 60 would cancel the print job in Example 21.11, “Example of lpstat -o output”. You can not cancel print jobs that were started by other users with the cancel command. However, you can enforce deletion of such job by issuing the cancel -U root job_number command. To prevent such canceling change the printer operation policy to Authenticated to force root authentication.
lp sample.txt prints the text file sample.txt. The print filter determines what type of file it is and converts it into a format the printer can understand.
21.3.11. Additional Resources
21.3.11.1. Installed Documentation
man lp- The manual page for the
lpcommand that allows you to print files from the command line. man lpr- The manual page for the
lprcommand that allows you to print files from the command line. man cancel- The manual page for the command-line utility to remove print jobs from the print queue.
man mpage- The manual page for the command-line utility to print multiple pages on one sheet of paper.
man cupsd- The manual page for the CUPS printer daemon.
man cupsd.conf- The manual page for the CUPS printer daemon configuration file.
man classes.conf- The manual page for the class configuration file for CUPS.
man lpstat- The manual page for the
lpstatcommand, which displays status information about classes, jobs, and printers.
21.3.11.2. Useful Websites
- http://www.linuxprinting.org/
- GNU/Linux Printing contains a large amount of information about printing in Linux.
- http://www.cups.org/
- Documentation, FAQs, and newsgroups about CUPS.
Chapter 22. Configuring NTP Using ntpd
22.1. Introduction to NTP
NTP servers provide “Coordinated Universal Time” (UTC). Information about these time servers can found at www.pool.ntp.org.
NTP is implemented by a daemon running in user space. The default NTP daemon in Red Hat Enterprise Linux 6 is ntpd.
rtc(4) and hwclock(8) man pages for information on hardware clocks. The system clock can keep time by using various clock sources. Usually, the Time Stamp Counter (TSC) is used. The TSC is a CPU register which counts the number of cycles since it was last reset. It is very fast, has a high resolution, and there are no interrupts. On system start, the system clock reads the time and date from the RTC. The time kept by the RTC will drift away from actual time by up to 5 minutes per month due to temperature variations. Hence the need for the system clock to be constantly synchronized with external time references. When the system clock is being synchronized by ntpd, the kernel will in turn update the RTC every 11 minutes automatically.
22.2. NTP Strata
NTP servers are classified according to their synchronization distance from the atomic clocks which are the source of the time signals. The servers are thought of as being arranged in layers, or strata, from 1 at the top down to 15. Hence the word stratum is used when referring to a specific layer. Atomic clocks are referred to as Stratum 0 as this is the source, but no Stratum 0 packet is sent on the Internet, all stratum 0 atomic clocks are attached to a server which is referred to as stratum 1. These servers send out packets marked as Stratum 1. A server which is synchronized by means of packets marked stratum n belongs to the next, lower, stratum and will mark its packets as stratum n+1. Servers of the same stratum can exchange packets with each other but are still designated as belonging to just the one stratum, the stratum one below the best reference they are synchronized to. The designation Stratum 16 is used to indicate that the server is not currently synchronized to a reliable time source.
NTP clients act as servers for those systems in the stratum below them.
NTP Strata:
- Stratum 0:
- Atomic Clocks and their signals broadcast over Radio and GPS
- GPS (Global Positioning System)
- Mobile Phone Systems
- Low Frequency Radio Broadcasts WWVB (Colorado, USA.), JJY-40 and JJY-60 (Japan), DCF77 (Germany), and MSF (United Kingdom)
These signals can be received by dedicated devices and are usually connected by RS-232 to a system used as an organizational or site-wide time server. - Stratum 1:
- Computer with radio clock, GPS clock, or atomic clock attached
- Stratum 2:
- Reads from stratum 1; Serves to lower strata
- Stratum 3:
- Reads from stratum 2; Serves to lower strata
- Stratum n+1:
- Reads from stratum n; Serves to lower strata
- Stratum 15:
- Reads from stratum 14; This is the lowest stratum.
22.3. Understanding NTP
NTP used by Red Hat Enterprise Linux is as described in RFC 1305 Network Time Protocol (Version 3) Specification, Implementation and Analysis and RFC 5905 Network Time Protocol Version 4: Protocol and Algorithms Specification
NTP enables sub-second accuracy to be achieved. Over the Internet, accuracy to 10s of milliseconds is normal. On a Local Area Network (LAN), 1 ms accuracy is possible under ideal conditions. This is because clock drift is now accounted and corrected for, which was not done in earlier, simpler, time protocol systems. A resolution of 233 picoseconds is provided by using 64-bit time stamps. The first 32-bits of the time stamp is used for seconds, the last 32-bits are used for fractions of seconds.
NTP represents the time as a count of the number of seconds since 00:00 (midnight) 1 January, 1900 GMT. As 32-bits is used to count the seconds, this means the time will “roll over” in 2036. However NTP works on the difference between time stamps so this does not present the same level of problem as other implementations of time protocols have done. If a hardware clock that is within 68 years of the correct time is available at boot time then NTP will correctly interpret the current date. The NTP4 specification provides for an “Era Number” and an “Era Offset” which can be used to make software more robust when dealing with time lengths of more than 68 years. Note, please do not confuse this with the Unix Year 2038 problem.
NTP protocol provides additional information to improve accuracy. Four time stamps are used to allow the calculation of round-trip time and server response time. In order for a system in its role as NTP client to synchronize with a reference time server, a packet is sent with an “originate time stamp”. When the packet arrives, the time server adds a “receive time stamp”. After processing the request for time and date information and just before returning the packet, it adds a “transmit time stamp”. When the returning packet arrives at the NTP client, a “receive time stamp” is generated. The client can now calculate the total round trip time and by subtracting the processing time derive the actual traveling time. By assuming the outgoing and return trips take equal time, the single-trip delay in receiving the NTP data is calculated. The full NTP algorithm is much more complex than presented here.
ntpd has determined the time should be. The system clock is adjusted slowly, at most at a rate of 0.5ms per second, to reduce this offset by changing the frequency of the counter being used. It will take at least 2000 seconds to adjust the clock by 1 second using this method. This slow change is referred to as slewing and cannot go backwards. If the time offset of the clock is more than 128ms (the default setting), ntpd can “step” the clock forwards or backwards. If the time offset at system start is greater than 1000 seconds then the user, or an installation script, should make a manual adjustment. See Chapter 2, Date and Time Configuration. With the -g option to the ntpd command (used by default), any offset at system start will be corrected, but during normal operation only offsets of up to 1000 seconds will be corrected.
-x option (unrelated to the -g option). Using the -x option to increase the stepping limit from 0.128s to 600s has a drawback because a different method of controlling the clock has to be used. It disables the kernel clock discipline and may have a negative impact on the clock accuracy. The -x option can be added to the /etc/sysconfig/ntpd configuration file.
22.4. Understanding the Drift File
ntpd. The drift file is replaced, rather than just updated, and for this reason the drift file must be in a directory for which ntpd has write permissions.
22.5. UTC, Timezones, and DST
NTP is entirely in UTC (Universal Time, Coordinated), Timezones and DST (Daylight Saving Time) are applied locally by the system. The file /etc/localtime is a copy of, or symlink to, a zone information file from /usr/share/zoneinfo. The RTC may be in localtime or in UTC, as specified by the 3rd line of /etc/adjtime, which will be one of LOCAL or UTC to indicate how the RTC clock has been set. Users can easily change this setting using the check box System Clock Uses UTC in the system-config-date graphical configuration tool. See Chapter 2, Date and Time Configuration for information on how to use that tool. Running the RTC in UTC is recommended to avoid various problems when daylight saving time is changed.
ntpd is explained in more detail in the man page ntpd(8). The resources section lists useful sources of information. See Section 22.19, “Additional Resources”.
22.6. Authentication Options for NTP
NTPv4 added support for the Autokey Security Architecture, which is based on public asymmetric cryptography while retaining support for symmetric key cryptography. The Autokey Security Architecture is described in RFC 5906 Network Time Protocol Version 4: Autokey Specification. The man page ntp_auth(5) describes the authentication options and commands for ntpd.
NTP packets with incorrect time information. On systems using the public pool of NTP servers, this risk is mitigated by having more than three NTP servers in the list of public NTP servers in /etc/ntp.conf. If only one time source is compromised or spoofed, ntpd will ignore that source. You should conduct a risk assessment and consider the impact of incorrect time on your applications and organization. If you have internal time sources you should consider steps to protect the network over which the NTP packets are distributed. If you conduct a risk assessment and conclude that the risk is acceptable, and the impact to your applications minimal, then you can choose not to use authentication.
disable auth directive in the ntp.conf file. Alternatively, authentication needs to be configured by using SHA1 or MD5 symmetric keys, or by public (asymmetric) key cryptography using the Autokey scheme. The Autokey scheme for asymmetric cryptography is explained in the ntp_auth(8) man page and the generation of keys is explained in ntp-keygen(8). To implement symmetric key cryptography, see Section 22.16.12, “Configuring Symmetric Authentication Using a Key” for an explanation of the key option.
22.7. Managing the Time on Virtual Machines
kvm-clock. See the KVM guest timing management chapter of the Virtualization Host Configuration and Guest Installation Guide.
22.8. Understanding Leap Seconds
NTP transmits information about pending leap seconds and applies them automatically.
22.9. Understanding the ntpd Configuration File
ntpd, reads the configuration file at system start or when the service is restarted. The default location for the file is /etc/ntp.conf and you can view the file by entering the following command:
less /etc/ntp.conf
~]$ less /etc/ntp.confntp.conf(5) man page.
- The driftfile entry
- A path to the drift file is specified, the default entry on Red Hat Enterprise Linux is:If you change this be certain that the directory is writable by
driftfile /var/lib/ntp/drift
driftfile /var/lib/ntp/driftCopy to Clipboard Copied! Toggle word wrap Toggle overflow ntpd. The file contains one value used to adjust the system clock frequency after every system or service start. See Understanding the Drift File for more information. - The access control entries
- The following lines setup the default access control restrictions:The
restrict default kod nomodify notrap nopeer noquery restrict -6 default kod nomodify notrap nopeer noquery
restrict default kod nomodify notrap nopeer noquery restrict -6 default kod nomodify notrap nopeer noqueryCopy to Clipboard Copied! Toggle word wrap Toggle overflow kodoption means a “Kiss-o'-death” packet is to be sent to reduce unwanted queries. Thenomodifyoptions prevents any changes to the configuration. Thenotrapoption preventsntpdccontrol message protocol traps. Thenopeeroption prevents a peer association being formed. Thenoqueryoption preventsntpqandntpdcqueries, but not time queries, from being answered. The-6option is required before anIPv6address.Addresses within the range127.0.0.0/8are sometimes required by various processes or applications. As the "restrict default" line above prevents access to everything not explicitly allowed, access to the standard loopback address forIPv4andIPv6is permitted by means of the following lines:Addresses can be added underneath if specifically required by another application. The# the administrative functions. restrict 127.0.0.1 restrict -6 ::1
# the administrative functions. restrict 127.0.0.1 restrict -6 ::1Copy to Clipboard Copied! Toggle word wrap Toggle overflow -6option is required before anIPv6address.Hosts on the local network are not permitted because of the "restrict default" line above. To change this, for example to allow hosts from the192.0.2.0/24network to query the time and statistics but nothing more, a line in the following format is required:To allow unrestricted access from a specific host, for examplerestrict 192.0.2.0 mask 255.255.255.0 nomodify notrap nopeer
restrict 192.0.2.0 mask 255.255.255.0 nomodify notrap nopeerCopy to Clipboard Copied! Toggle word wrap Toggle overflow 192.0.2.250/32, a line in the following format is required:A mask ofrestrict 192.0.2.250
restrict 192.0.2.250Copy to Clipboard Copied! Toggle word wrap Toggle overflow 255.255.255.255is applied if none is specified.The restrict commands are explained in thentp_acc(5)man page. - The public servers entry
- By default, as of Red Hat Enterprise 6.5, the
ntp.conffile contains four public server entries:If upgrading from a previous minor release, and yourserver 0.rhel.pool.ntp.org iburst server 1.rhel.pool.ntp.org iburst server 2.rhel.pool.ntp.org iburst server 3.rhel.pool.ntp.org iburst
server 0.rhel.pool.ntp.org iburst server 1.rhel.pool.ntp.org iburst server 2.rhel.pool.ntp.org iburst server 3.rhel.pool.ntp.org iburstCopy to Clipboard Copied! Toggle word wrap Toggle overflow /etc/ntp.conffile has been modified, then the upgrade to Red Hat Enterprise Linux 6.5 will create a new file/etc/ntp.conf.rpmnewand will not alter the existing/etc/ntp.conffile. - The broadcast multicast servers entry
- By default, the
ntp.conffile contains some commented out examples. These are largely self explanatory. See the explanation of the specific commands Section 22.16, “Configure NTP”. If required, add your commands just below the examples.
Note
DHCP client program, dhclient, receives a list of NTP servers from the DHCP server, it adds them to ntp.conf and restarts the service. To disable that feature, add PEERNTP=no to /etc/sysconfig/network.
22.10. Understanding the ntpd Sysconfig File
ntpd init script on service start. The default contents is as follows:
# Drop root to id 'ntp:ntp' by default. OPTIONS="-u ntp:ntp -p /var/run/ntpd.pid -g"
# Drop root to id 'ntp:ntp' by default.
OPTIONS="-u ntp:ntp -p /var/run/ntpd.pid -g"-g option enables ntpd to ignore the offset limit of 1000s and attempt to synchronize the time even if the offset is larger than 1000s, but only on system start. Without that option ntpd will exit if the time offset is greater than 1000s. It will also exit after system start if the service is restarted and the offset is greater than 1000s even with the -g option.
-p option sets the path to the pid file and -u sets the user and group to which the daemon should drop the root privileges.
22.11. Checking if the NTP Daemon is Installed
ntpd is installed, enter the following command as root:
yum install ntp
~]# yum install ntpNTP is implemented by means of the daemon or service ntpd, which is contained within the ntp package.
22.12. Installing the NTP Daemon (ntpd)
ntpd, enter the following command as root:
yum install ntp
~]# yum install ntp/usr/sbin/.
22.13. Checking the Status of NTP
ntpd is configured to run at system start, issue the following command:
chkconfig --list ntpd ntpd 0:off 1:off 2:on 3:on 4:on 5:on 6:off
~]$ chkconfig --list ntpd
ntpd 0:off 1:off 2:on 3:on 4:on 5:on 6:offntpd is installed, it is configured to start at every system start.
ntpd is running, issue the following command:
- remote and refid: remote NTP server, and its NTP server
- st: stratum of server
- t: type of server (local, unicast, multicast, or broadcast)
- poll: how frequently to query server (in seconds)
- when: how long since last poll (in seconds)
- reach: octal bitmask of success or failure of last 8 queries (left-shifted); 377 = 11111111 = all recent queries were successful; 257 = 10101111 = 4 most recent were successful, 5 and 7 failed
- delay: network round trip time (in milliseconds)
- offset: difference between local clock and remote clock (in milliseconds)
- jitter: difference of successive time values from server (high jitter could be due to an unstable clock or, more likely, poor network performance)
ntpd, issue the following command:
ntpstat unsynchronised time server re-starting polling server every 64 s
~]$ ntpstat
unsynchronised
time server re-starting
polling server every 64 sntpstat synchronised to NTP server (10.5.26.10) at stratum 2 time correct to within 52 ms polling server every 1024 s
~]$ ntpstat
synchronised to NTP server (10.5.26.10) at stratum 2
time correct to within 52 ms
polling server every 1024 s22.14. Configure the Firewall to Allow Incoming NTP Packets
NTP traffic consists of UDP packets on port 123 and needs to be permitted through network and host-based firewalls in order for NTP to function.
22.14.1. Configure the Firewall Using the Graphical Tool
NTP to pass through the firewall, using the graphical tool system-config-firewall, issue the following command as root:
system-config-firewall
~]# system-config-firewall123. Select the “port 123” entry with udp as the protocol. Click . The Port and Protocol window closes. Click in the Firewall Configuration window to apply the changes. A dialog box will pop up to ask you to confirm the action, click . Note that any existing sessions will be terminated when you click .
22.14.2. Configure the Firewall Using the Command Line
NTP to pass through the firewall using the command line, issue the following command as root:
lokkit --port=123:udp --update
~]# lokkit --port=123:udp --update--disabled option. Active connections will be terminated and time out on the initiating machine.
/etc/sysconfig/system-config-firewall file thoroughly after editing.
NTP to pass through the firewall, by editing the configuration file, become the root user and add the following line to /etc/sysconfig/system-config-firewall:
--port=123:udp
--port=123:udp22.14.2.1. Checking Network Access for Incoming NTP Using the Command Line
NTP traffic for clients using the command line, issue the following command as root:
less /etc/sysconfig/system-config-firewall # Configuration file for system-config-firewall --enabled --service=ssh
~]# less /etc/sysconfig/system-config-firewall
# Configuration file for system-config-firewall
--enabled
--service=sshNTP has not been allowed to pass through. Once it is enabled, the following line appears as output in addition to the lines shown above:
--port=123:udp
--port=123:udpNTP traffic for clients, issue the following command as root:
iptables -L -n | grep 'udp.*123' ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 state NEW udp dpt:123
~]# iptables -L -n | grep 'udp.*123'
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 state NEW udp dpt:12322.15. Configure ntpdate Servers
ntpdate service is to set the clock during system boot. This can be used to ensure that the services started after ntpdate will have the correct time and will not observe a jump in the clock. The use of ntpdate and the list of step-tickers is considered deprecated and so Red Hat Enterprise Linux 6 uses the -g option to the ntpd command by default and not ntpdate. However, the -g option only enables ntpd to ignore the offset limit of 1000s and attempt to synchronize the time. It does not guarantee the time will be correct when other programs or services are started. Therefore the ntpdate service can be useful when ntpd is disabled or if there are services which need to be started with the correct time and not observe a jump in the clock.
ntpdate service is enabled to run at system start, issue the following command:
chkconfig --list ntpdate ntpdate 0:off 1:off 2:on 3:on 4:on 5:on 6:off
~]$ chkconfig --list ntpdate
ntpdate 0:off 1:off 2:on 3:on 4:on 5:on 6:offroot:
chkconfig ntpdate on
~]# chkconfig ntpdate onntpdate servers, using a text editor running as root, edit /etc/ntp/step-tickers to include one or more host names as follows:
clock1.example.com clock2.example.com
clock1.example.com
clock2.example.comntpdate will only use this to obtain the date information once when the system is starting. If you have an internal time server then use that host name for the first line. An additional host on the second line as a backup is sensible. The selection of backup servers and whether the second host is internal or external depends on your risk assessment. For example, what is the chance of any problem affecting the first server also affecting the second server? Would connectivity to an external server be more likely to be available than connectivity to internal servers in the event of a network failure disrupting access to the first server?
ntpdate service has a file that must contain a list of NTP servers to be used on system start. It is recommend to have at last four servers listed to reduce the chance of a “false ticker” (incorrect time source) influencing the quality of the time offset calculation. However, publicly accessible time sources are rarely incorrect.
22.16. Configure NTP
NTP service, use a text editor running as root user to edit the /etc/ntp.conf file. This file is installed together with ntpd and is configured to use time servers from the Red Hat pool by default. The man page ntp.conf(5) describes the command options that can be used in the configuration file apart from the access and rate limiting commands which are explained in the ntp_acc(5) man page.
22.16.1. Configure Access Control to an NTP Service
NTP service running on a system, make use of the restrict command in the ntp.conf file. See the commented out example:
# Hosts on local network are less restricted. #restrict 192.168.1.0 mask 255.255.255.0 nomodify notrap
# Hosts on local network are less restricted.
#restrict 192.168.1.0 mask 255.255.255.0 nomodify notraprestrict command takes the following form:
restrict address mask option
restrict address mask optionignore— All packets will be ignored, includingntpqandntpdcqueries.kod— a “Kiss-o'-death” packet is to be sent to reduce unwanted queries.limited— do not respond to time service requests if the packet violates the rate limit default values or those specified by thediscardcommand.ntpqandntpdcqueries are not affected. For more information on thediscardcommand and the default values, see Section 22.16.2, “Configure Rate Limiting Access to an NTP Service”.lowpriotrap— traps set by matching hosts to be low priority.nomodify— prevents any changes to the configuration.noquery— preventsntpqandntpdcqueries, but not time queries, from being answered.nopeer— prevents a peer association being formed.noserve— deny all packets exceptntpqandntpdcqueries.notrap— preventsntpdccontrol message protocol traps.notrust— deny packets that are not cryptographically authenticated.ntpport— modify the match algorithm to only apply the restriction if the source port is the standardNTPUDPport123.version— deny packets that do not match the currentNTPversion.
restrict command has to have the limited option. If ntpd should reply with a KoD packet, the restrict command needs to have both limited and kod options.
ntpq and ntpdc queries can be used in amplification attacks (see CVE-2013-5211 for more details), do not remove the noquery option from the restrict default command on publicly accessible systems.
22.16.2. Configure Rate Limiting Access to an NTP Service
NTP service running on a system, add the limited option to the restrict command as explained in Section 22.16.1, “Configure Access Control to an NTP Service”. If you do not want to use the default discard parameters, then also use the discard command as explained here.
discard command takes the following form:
discard [average value] [minimum value] [monitor value]
discard [average value] [minimum value] [monitor value]average— specifies the minimum average packet spacing to be permitted, it accepts an argument in log2 seconds. The default value is 3 (23 equates to 8 seconds).minimum— specifies the minimum packet spacing to be permitted, it accepts an argument in log2 seconds. The default value is 1 (21 equates to 2 seconds).monitor— specifies the discard probability for packets once the permitted rate limits have been exceeded. The default value is 3000 seconds. This option is intended for servers that receive 1000 or more requests per second.
discard command are as follows: discard average 4
discard average 4discard average 4 minimum 2
discard average 4 minimum 222.16.3. Adding a Peer Address
NTP service of the same stratum, make use of the peer command in the ntp.conf file.
peer command takes the following form:
peer address
peer addressIP unicast address or a DNS resolvable name. The address must only be that of a system known to be a member of the same stratum. Peers should have at least one time source that is different to each other. Peers are normally systems under the same administrative control.
22.16.4. Adding a Server Address
NTP service of a higher stratum, make use of the server command in the ntp.conf file.
server command takes the following form:
server address
server addressIP unicast address or a DNS resolvable name. The address of a remote reference server or local reference clock from which packets are to be received.
22.16.5. Adding a Broadcast or Multicast Server Address
NTP packets to, make use of the broadcast command in the ntp.conf file.
broadcast command takes the following form:
broadcast address
broadcast addressIP broadcast or multicast address to which packets are sent.
NTP broadcast server. The address used must be a broadcast or a multicast address. Broadcast address implies the IPv4 address 255.255.255.255. By default, routers do not pass broadcast messages. The multicast address can be an IPv4 Class D address, or an IPv6 address. The IANA has assigned IPv4 multicast address 224.0.1.1 and IPv6 address FF05::101 (site local) to NTP. Administratively scoped IPv4 multicast addresses can also be used, as described in RFC 2365 Administratively Scoped IP Multicast.
22.16.6. Adding a Manycast Client Address
NTP server discovery, make use of the manycastclient command in the ntp.conf file.
manycastclient command takes the following form:
manycastclient address
manycastclient addressIP multicast address from which packets are to be received. The client will send a request to the address and select the best servers from the responses and ignore other servers. NTP communication then uses unicast associations, as if the discovered NTP servers were listed in ntp.conf.
NTP client. Systems can be both client and server at the same time.
22.16.7. Adding a Broadcast Client Address
NTP packets, make use of the broadcastclient command in the ntp.conf file.
broadcastclient command takes the following form:
broadcastclient
broadcastclientNTP client. Systems can be both client and server at the same time.
22.16.8. Adding a Manycast Server Address
NTP packets, make use of the manycastserver command in the ntp.conf file.
manycastserver command takes the following form:
manycastserver address
manycastserver addressNTP server. Systems can be both client and server at the same time.
22.16.9. Adding a Multicast Client Address
NTP packets, make use of the multicastclient command in the ntp.conf file.
multicastclient command takes the following form:
multicastclient address
multicastclient addressNTP client. Systems can be both client and server at the same time.
22.16.10. Configuring the Burst Option
burst option against a public server is considered abuse. Do not use this option with public NTP servers. Use it only for applications within your own organization.
burst
burstserver command to improve the average quality of the time-offset calculations.
22.16.11. Configuring the iburst Option
iburst
iburstcalldelay command to allow additional time for a modem or ISDN call to complete. For use with the server command to reduce the time taken for initial synchronization. As of Red Hat Enterprise Linux 6.5, this is now a default option in the configuration file.
22.16.12. Configuring Symmetric Authentication Using a Key
key number
key number1 to 65534 inclusive. This option enables the use of a message authentication code (MAC) in packets. This option is for use with the peer, server, broadcast, and manycastclient commands.
/etc/ntp.conf file as follows:
server 192.168.1.1 key 10 broadcast 192.168.1.255 key 20 manycastclient 239.255.254.254 key 30
server 192.168.1.1 key 10
broadcast 192.168.1.255 key 20
manycastclient 239.255.254.254 key 3022.16.13. Configuring the Poll Interval
minpoll value and maxpoll value
minpoll value and maxpoll valueminpoll value is 6, 26 equates to 64s. The default value for maxpoll is 10, which equates to 1024s. Allowed values are in the range 3 to 17 inclusive, which equates to 8s to 36.4h respectively. These options are for use with the peer or server. Setting a shorter maxpoll may improve clock accuracy.
22.16.14. Configuring Server Preference
prefer
preferpeer or server commands.
22.16.15. Configuring the Time-to-Live for NTP Packets
ttl value
ttl valueNTP servers. Specify the maximum time-to-live value to use for the “expanding ring search” by a manycast client. The default value is 127.
22.16.16. Configuring the NTP Version to Use
NTP should be used in place of the default, add the following option to the end of a server or peer command:
version value
version valueNTP set in created NTP packets. The value can be in the range 1 to 4. The default is 4.
22.17. Configuring the Hardware Clock Update
/etc/sysconfig/ntpdate:
SYNC_HWCLOCK=yes
SYNC_HWCLOCK=yesroot:
hwclock --systohc
~]# hwclock --systohcntpd, the kernel will in turn update the RTC every 11 minutes automatically.
22.18. Configuring Clock Sources
cd /sys/devices/system/clocksource/clocksource0/ clocksource0]$ cat available_clocksource kvm-clock tsc hpet acpi_pm clocksource0]$ cat current_clocksource kvm-clock
~]$ cd /sys/devices/system/clocksource/clocksource0/
clocksource0]$ cat available_clocksource
kvm-clock tsc hpet acpi_pm
clocksource0]$ cat current_clocksource
kvm-clockgrub.conf:
clocksource=tsc
clocksource=tsc22.19. Additional Resources
NTP and ntpd.
22.19.1. Installed Documentation
ntpd(8)man page — Describesntpdin detail, including the command-line options.ntp.conf(5)man page — Contains information on how to configure associations with servers and peers.ntpq(8)man page — Describes theNTPquery utility for monitoring and querying anNTPserver.ntpdc(8)man page — Describes thentpdutility for querying and changing the state ofntpd.ntp_auth(5)man page — Describes authentication options, commands, and key management forntpd.ntp_keygen(8)man page — Describes generating public and private keys forntpd.ntp_acc(5)man page — Describes access control options using therestrictcommand.ntp_mon(5)man page — Describes monitoring options for the gathering of statistics.ntp_clock(5)man page — Describes commands for configuring reference clocks.ntp_misc(5)man page — Describes miscellaneous options.
22.19.2. Useful Websites
- http://doc.ntp.org/
- The NTP Documentation Archive
- http://www.eecis.udel.edu/~mills/ntp.html
- Network Time Synchronization Research Project.
- http://www.eecis.udel.edu/~mills/ntp/html/manyopt.html
- Information on Automatic Server Discovery in
NTPv4.
Chapter 23. Configuring PTP Using ptp4l
23.1. Introduction to PTP
PTP is capable of sub-microsecond accuracy, which is far better than is normally obtainable with NTP. PTP support is divided between the kernel and user space. The kernel in Red Hat Enterprise Linux 6 now includes support for PTP clocks, which are provided by network drivers. The actual implementation of the protocol is known as linuxptp, a PTPv2 implementation according to the IEEE standard 1588 for Linux.
PTP boundary clock and ordinary clock. With hardware time stamping, it is used to synchronize the PTP hardware clock to the master clock, and with software time stamping it synchronizes the system clock to the master clock. The phc2sys program is needed only with hardware time stamping, for synchronizing the system clock to the PTP hardware clock on the network interface card (NIC).
23.1.1. Understanding PTP
PTP are organized in a master-slave hierarchy. The slaves are synchronized to their masters which may be slaves to their own masters. The hierarchy is created and updated automatically by the best master clock (BMC) algorithm, which runs on every clock. When a clock has only one port, it can be master or slave, such a clock is called an ordinary clock (OC). A clock with multiple ports can be master on one port and slave on another, such a clock is called a boundary clock (BC). The top-level master is called the grandmaster clock, which can be synchronized by using a Global Positioning System (GPS) time source. By using a GPS-based time source, disparate networks can be synchronized with a high-degree of accuracy.
Figure 23.1. PTP grandmaster, boundary, and slave Clocks
23.1.2. Advantages of PTP
PTP has over the Network Time Protocol (NTP) is hardware support present in various network interface controllers (NIC) and network switches. This specialized hardware allows PTP to account for delays in message transfer, and greatly improves the accuracy of time synchronization. While it is possible to use non-PTP enabled hardware components within the network, this will often cause an increase in jitter or introduce an asymmetry in the delay resulting in synchronization inaccuracies, which add up with multiple non-PTP aware components used in the communication path. To achieve the best possible accuracy, it is recommended that all networking components between PTP clocks are PTP hardware enabled. Time synchronization in larger networks where not all of the networking hardware supports PTP might be better suited for NTP.
PTP support, the NIC has its own on-board clock, which is used to time stamp the received and transmitted PTP messages. It is this on-board clock that is synchronized to the PTP master, and the computer's system clock is synchronized to the PTP hardware clock on the NIC. With software PTP support, the system clock is used to time stamp the PTP messages and it is synchronized to the PTP master directly. Hardware PTP support provides better accuracy since the NIC can time stamp the PTP packets at the exact moment they are sent and received while software PTP support requires additional processing of the PTP packets by the operating system.
23.2. Using PTP
PTP, the kernel network driver for the intended interface has to support either software or hardware time stamping capabilities.
23.2.1. Checking for Driver and Hardware Support
SOF_TIMESTAMPING_SOFTWARE
SOF_TIMESTAMPING_TX_SOFTWARE
SOF_TIMESTAMPING_RX_SOFTWARE
SOF_TIMESTAMPING_RAW_HARDWARE
SOF_TIMESTAMPING_TX_HARDWARE
SOF_TIMESTAMPING_RX_HARDWARE
23.2.2. Installing PTP
PTP. User space support is provided by the tools in the linuxptp package. To install linuxptp, issue the following command as root:
yum install linuxptp
~]# yum install linuxptpPTP time using NTP, see Section 23.7, “Serving PTP Time With NTP”.
23.2.3. Starting ptp4l
-i option. Enter the following command as root:
ptp4l -i eth3 -m
~]# ptp4l -i eth3 -mPTP clock on the NIC is synchronized to a master:
s0, s1, s2 strings indicate the different clock servo states: s0 is unlocked, s1 is clock step and s2 is locked. Once the servo is in the locked state (s2), the clock will not be stepped (only slowly adjusted) unless the pi_offset_const option is set to a positive value in the configuration file (described in the ptp4l(8) man page). The freq value is the frequency adjustment of the clock in parts per billion (ppb). The path delay value is the estimated delay of the synchronization messages sent from the master in nanoseconds. Port 0 is a Unix domain socket used for local PTP management. Port 1 is the eth3 interface (based on the example above.) INITIALIZING, LISTENING, UNCALIBRATED and SLAVE are some of possible port states which change on the INITIALIZE, RS_SLAVE, MASTER_CLOCK_SELECTED events. In the last state change message, the port state changed from UNCALIBRATED to SLAVE indicating successful synchronization with a PTP master clock.
service ptp4l start
~]# service ptp4l start/etc/sysconfig/ptp4l file. More information on the different ptp4l options and the configuration file settings can be found in the ptp4l(8) man page.
/var/log/messages. However, specifying the -m option enables logging to standard output which can be useful for debugging purposes.
-S option needs to be used as follows:
ptp4l -i eth3 -m -S
~]# ptp4l -i eth3 -m -S23.2.3.1. Selecting a Delay Measurement Mechanism
ptp4l command as follows:
-P- The
-Pselects the peer-to-peer (P2P) delay measurement mechanism.The P2P mechanism is preferred as it reacts to changes in the network topology faster, and may be more accurate in measuring the delay, than other mechanisms. The P2P mechanism can only be used in topologies where each port exchanges PTP messages with at most one other P2P port. It must be supported and used by all hardware, including transparent clocks, on the communication path. -E- The
-Eselects the end-to-end (E2E) delay measurement mechanism. This is the default.The E2E mechanism is also referred to as the delay “request-response” mechanism. -A- The
-Aenables automatic selection of the delay measurement mechanism.The automatic option starts ptp4l in E2E mode. It will change to P2P mode if a peer delay request is received.
Note
PTP communication path must use the same mechanism to measure the delay. A warning will be printed when a peer delay request is received on a port using the E2E mechanism. A warning will be printed when a E2E delay request is received on a port using the P2P mechanism.
23.3. Specifying a Configuration File
-f option. For example:
ptp4l -f /etc/ptp4l.conf
~]# ptp4l -f /etc/ptp4l.conf-i eth3 -m -S options shown above would look as follows:
23.4. Using the PTP Management Client
PTP management client, pmc, can be used to obtain additional information from ptp4l as follows:
-b option to zero limits the boundary to the locally running ptp4l instance. A larger boundary value will retrieve the information also from PTP nodes further from the local clock. The retrievable information includes:
stepsRemovedis the number of communication paths to the grandmaster clock.offsetFromMasterand master_offset is the last measured offset of the clock from the master in nanoseconds.meanPathDelayis the estimated delay of the synchronization messages sent from the master in nanoseconds.- if
gmPresentis true, thePTPclock is synchronized to a master, the local clock is not the grandmaster clock. gmIdentityis the grandmaster's identity.
root:
pmc help
~]# pmc helppmc(8) man page.
23.5. Synchronizing the Clocks
PTP hardware clock (PHC) on the NIC. The phc2sys service is configured in the /etc/sysconfig/phc2sys configuration file. The default setting in the /etc/sysconfig/phc2sys file is as follows: OPTIONS="-a -r"
OPTIONS="-a -r"-a option causes phc2sys to read the clocks to be synchronized from the ptp4l application. It will follow changes in the PTP port states, adjusting the synchronization between the NIC hardware clocks accordingly. The system clock is not synchronized, unless the -r option is also specified. If you want the system clock to be eligible to become a time source, specify the -r option twice.
/etc/sysconfig/phc2sys, restart the phc2sys service from the command line by issuing a command as root:
service phc2sys restart
~]# service phc2sys restartservice commands to start, stop, and restart the phc2sys service.
root:
phc2sys -a -r
~]# phc2sys -a -r-a option causes phc2sys to read the clocks to be synchronized from the ptp4l application. If you want the system clock to be eligible to become a time source, specify the -r option twice.
-s option to synchronize the system clock to a specific interface's PTP hardware clock. For example:
phc2sys -s eth3 -w
~]# phc2sys -s eth3 -w-w option waits for the running ptp4l application to synchronize the PTP clock and then retrieves the TAI to UTC offset from ptp4l.
PTP operates in the International Atomic Time (TAI) timescale, while the system clock is kept in Coordinated Universal Time (UTC). The current offset between the TAI and UTC timescales is 36 seconds. The offset changes when leap seconds are inserted or deleted, which typically happens every few years. The -O option needs to be used to set this offset manually when the -w is not used, as follows:
phc2sys -s eth3 -O -36
~]# phc2sys -s eth3 -O -36-S option is used. This means that the phc2sys program should be started after the ptp4l program has synchronized the PTP hardware clock. However, with -w, it is not necessary to start phc2sys after ptp4l as it will wait for it to synchronize the clock.
service phc2sys start
~]# service phc2sys start/etc/sysconfig/phc2sys file. More information on the different phc2sys options can be found in the phc2sys(8) man page.
23.6. Verifying Time Synchronization
PTP time synchronization is working properly, new messages with offsets and frequency adjustments will be printed periodically to the ptp4l and phc2sys (if hardware time stamping is used) outputs. These values will eventually converge after a short period of time. These messages can be seen in /var/log/messages file. An example of the ptp4l output follows:
summary_interval, to reduce the output and print only statistics, as normally it will print a message every second or so. For example, to reduce the output to every 1024 seconds, add the following line to the /etc/ptp4l.conf file:
summary_interval 10
summary_interval 10summary_interval 6, follows:
-u option as follows:
phc2sys -u summary-updates
~]# phc2sys -u summary-updates23.7. Serving PTP Time With NTP
ntpd daemon can be configured to distribute the time from the system clock synchronized by ptp4l or phc2sys by using the LOCAL reference clock driver. To prevent ntpd from adjusting the system clock, the ntp.conf file must not specify any NTP servers. The following is a minimal example of ntp.conf:
~]# cat /etc/ntp.conf server 127.127.1.0 fudge 127.127.1.0 stratum 0
~]# cat /etc/ntp.conf
server 127.127.1.0
fudge 127.127.1.0 stratum 0Note
DHCP client program, dhclient, receives a list of NTP servers from the DHCP server, it adds them to ntp.conf and restarts the service. To disable that feature, add PEERNTP=no to /etc/sysconfig/network.
23.8. Serving NTP Time With PTP
NTP to PTP synchronization in the opposite direction is also possible. When ntpd is used to synchronize the system clock, ptp4l can be configured with the priority1 option (or other clock options included in the best master clock algorithm) to be the grandmaster clock and distribute the time from the system clock via PTP:
~]# cat /etc/ptp4l.conf [global] priority1 127 [eth3] ptp4l -f /etc/ptp4l.conf
~]# cat /etc/ptp4l.conf
[global]
priority1 127
[eth3]
# ptp4l -f /etc/ptp4l.confPTP hardware clock to the system clock:
phc2sys -c eth3 -s CLOCK_REALTIME -w
~]# phc2sys -c eth3 -s CLOCK_REALTIME -wPTP clock's frequency, the synchronization to the system clock can be loosened by using smaller P (proportional) and I (integral) constants of the PI servo:
phc2sys -c eth3 -s CLOCK_REALTIME -w -P 0.01 -I 0.0001
~]# phc2sys -c eth3 -s CLOCK_REALTIME -w -P 0.01 -I 0.000123.9. Synchronize to PTP or NTP Time Using timemaster
PTP domains available on the network, or fallback to NTP is needed, the timemaster program can be used to synchronize the system clock to all available time sources. The PTP time is provided by phc2sys and ptp4l via shared memory driver (SHM reference clocks to chronyd or ntpd (depending on the NTP daemon that has been configured on the system). The NTP daemon can then compare all time sources, both PTP and NTP, and use the best sources to synchronize the system clock.
NTP and PTP time sources, checks which network interfaces have their own or share a PTP hardware clock (PHC), generates configuration files for ptp4l and chronyd or ntpd, and starts the ptp4l, phc2sys, and chronyd or ntpd processes as needed. It will remove the generated configuration files on exit. It writes configuration files for chronyd, ntpd, and ptp4l to /var/run/timemaster/.
23.9.1. Starting timemaster as a Service
root:
service timemaster start
~]# service timemaster start /etc/timemaster.conf. For more information on managing system services in Red Hat Enterprise Linux 6, see Managing Services with systemd.
23.9.2. Understanding the timemaster Configuration File
/etc/timemaster.conf file with a number of sections containing default options. The section headings are enclosed in brackets.
[ntp_server address]
[ntp_server address]NTP server section, “ntp-server.local” is an example of a host name for an NTP server on the local LAN. Add more sections as required using a host name or IP address as part of the section name. Note that the short polling values in that example section are not suitable for a public server, see Chapter 22, Configuring NTP Using ntpd for an explanation of suitable minpoll and maxpoll values.
[ptp_domain number]
[ptp_domain number]PTP clocks that synchronize to each other. They may or may not be synchronized to clocks in another domain. Clocks that are configured with the same domain number make up the domain. This includes a PTP grandmaster clock. The domain number in each “PTP domain” section needs to correspond to one of the PTP domains configured on the network.
PTP clock and hardware time stamping is enabled automatically. Interfaces that support hardware time stamping have a PTP clock (PHC) attached, however it is possible for a group of interfaces on a NIC to share a PHC. A separate ptp4l instance will be started for each group of interfaces sharing the same PHC and for each interface that supports only software time stamping. All ptp4l instances are configured to run as a slave. If an interface with hardware time stamping is specified in more than one PTP domain, then only the first ptp4l instance created will have hardware time stamping enabled.
[timemaster]
[timemaster]ntpd and chrony configuration (/etc/ntp.conf or /etc/chronyd.conf) in order to include the configuration of access restrictions and authentication keys. That means any NTP servers specified there will be used with timemaster too.
[ntp_server ntp-server.local]— Specify polling intervals for this server. Create additional sections as required. Include the host name orIPaddress in the section heading.[ptp_domain 0]— Specify interfaces that havePTPclocks configured for this domain. Create additional sections with, the appropriate domain number, as required.[timemaster]— Specify theNTPdaemon to be used. Possible values arechronydandntpd.[chrony.conf]— Specify any additional settings to be copied to the configuration file generated forchronyd.[ntp.conf]— Specify any additional settings to be copied to the configuration file generated forntpd.[ptp4l.conf]— Specify options to be copied to the configuration file generated for ptp4l.[chronyd]— Specify any additional settings to be passed on the command line tochronyd.[ntpd]— Specify any additional settings to be passed on the command line tontpd.[phc2sys]— Specify any additional settings to be passed on the command line to phc2sys.[ptp4l]— Specify any additional settings to be passed on the command line to all instances of ptp4l.
timemaster(8) manual page.
23.9.3. Configuring timemaster Options
Procedure 23.1. Editing the timemaster Configuration File
- To change the default configuration, open the
/etc/timemaster.conffile for editing asroot:vi /etc/timemaster.conf
~]# vi /etc/timemaster.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - For each
NTPserver you want to control using timemaster, create[ntp_server address]sections . Note that the short polling values in the example section are not suitable for a public server, see Chapter 22, Configuring NTP Using ntpd for an explanation of suitableminpollandmaxpollvalues. - To add interfaces that should be used in a domain, edit the
#[ptp_domain 0]section and add the interfaces. Create additional domains as required. For example:[ptp_domain 0] interfaces eth0 [ptp_domain 1] interfaces eth1[ptp_domain 0] interfaces eth0 [ptp_domain 1] interfaces eth1Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If required to use
ntpdas theNTPdaemon on this system, change the default entry in the[timemaster]section fromchronydtontpd. See Configuring NTP Using the chrony Suite for information on the differences between ntpd and chronyd. - If using
chronydas theNTPserver on this system, add any additional options below the defaultinclude /etc/chrony.confentry in the[chrony.conf]section. Edit the defaultincludeentry if the path to/etc/chrony.confis known to have changed. - If using
ntpdas theNTPserver on this system, add any additional options below the defaultinclude /etc/ntp.confentry in the[ntp.conf]section. Edit the defaultincludeentry if the path to/etc/ntp.confis known to have changed. - In the
[ptp4l.conf]section, add any options to be copied to the configuration file generated for ptp4l. This chapter documents common options and more information is available in theptp4l(8)manual page. - In the
[chronyd]section, add any command line options to be passed tochronydwhen called by timemaster. See Configuring NTP Using the chrony Suite for information on usingchronyd. - In the
[ntpd]section, add any command line options to be passed tontpdwhen called by timemaster. See Chapter 22, Configuring NTP Using ntpd for information on usingntpd. - In the
[phc2sys]section, add any command line options to be passed to phc2sys when called by timemaster. This chapter documents common options and more information is available in thephy2sys(8)manual page. - In the
[ptp4l]section, add any command line options to be passed to ptp4l when called by timemaster. This chapter documents common options and more information is available in theptp4l(8)manual page. - Save the configuration file and restart timemaster by issuing the following command as
root:service timemaster restart
~]# service timemaster restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
23.10. Improving Accuracy
PTP synchronization accuracy (at the cost of increased power consumption). The kernel tickless mode can be disabled by adding nohz=off to the kernel boot option parameters. However, recent improvements applied to kernel-3.10.0-197.el7 have greatly improved the stability of the system clock and the difference in stability of the clock with and without nohz=off should be much smaller now for most users.
/etc/ptp4l.conf file: clock_servo linreg
clock_servo linreg/etc/ptp4l.conf, restart the ptp4l service from the command line by issuing the following command as root:
service ptp4l restart
~]# service ptp4l restart/etc/sysconfig/phc2sys file: -E linreg
-E linreg/etc/sysconfig/phc2sys, restart the phc2sys service from the command line by issuing the following command as root:
service phc2sys restart
~]# service phc2sys restart23.11. Additional Resources
PTP and the ptp4l tools.
23.11.1. Installed Documentation
ptp4l(8)man page — Describes ptp4l options including the format of the configuration file.pmc(8)man page — Describes thePTPmanagement client and its command options.phc2sys(8)man page — Describes a tool for synchronizing the system clock to aPTPhardware clock (PHC).
23.11.2. Useful Websites
- http://linuxptp.sourceforge.net/
- The Linux PTP project.
- http://www.nist.gov/el/isd/ieee/ieee1588.cfm
- The IEEE 1588 Standard.
Part VII. Monitoring and Automation
Chapter 24. System Monitoring Tools
24.1. Viewing System Processes
24.1.1. Using the ps Command
ps command allows you to display information about running processes. It produces a static list, that is, a snapshot of what is running when you execute the command. If you want a constantly updated list of running processes, use the top command or the System Monitor application instead.
ps ax
ps axps ax command displays the process ID (PID), the terminal that is associated with it (TTY), the current status (STAT), the cumulated CPU time (TIME), and the name of the executable file (COMMAND). For example:
ps aux
ps auxps ax command, ps aux displays the effective user name of the process owner (USER), the percentage of the CPU (%CPU) and memory (%MEM) usage, the virtual memory size in kilobytes (VSZ), the non-swapped physical memory size in kilobytes (RSS), and the time or date the process was started. For instance:
ps command in a combination with grep to see if a particular process is running. For example, to determine if Emacs is running, type:
ps ax | grep emacs 12056 pts/3 S+ 0:00 emacs 12060 pts/2 S+ 0:00 grep --color=auto emacs
~]$ ps ax | grep emacs
12056 pts/3 S+ 0:00 emacs
12060 pts/2 S+ 0:00 grep --color=auto emacs24.1.2. Using the top Command
top command displays a real-time list of processes that are running on the system. It also displays additional information about the system uptime, current CPU and memory usage, or total number of running processes, and allows you to perform actions such as sorting the list or killing a process.
top command, type the following at a shell prompt:
top
toptop command displays the process ID (PID), the effective user name of the process owner (USER), the priority (PR), the nice value (NI), the amount of virtual memory the process uses (VIRT), the amount of non-swapped physical memory the process uses (RES), the amount of shared memory the process uses (SHR), the process status field S), the percentage of the CPU (%CPU) and memory (%MEM) usage, the accumulated CPU time (TIME+), and the name of the executable file (COMMAND). For example:
top. For more information, see the top(1) manual page.
| Command | Description |
|---|---|
| Enter, Space | Immediately refreshes the display. |
| h, ? | Displays a help screen. |
| k | Kills a process. You are prompted for the process ID and the signal to send to it. |
| n | Changes the number of displayed processes. You are prompted to enter the number. |
| u | Sorts the list by user. |
| M | Sorts the list by memory usage. |
| P | Sorts the list by CPU usage. |
| q | Terminates the utility and returns to the shell prompt. |
24.1.3. Using the System Monitor Tool
root:
yum install gnome-system-monitor
~]# yum install gnome-system-monitorgnome-system-monitor at a shell prompt. Then click the Processes tab to view the list of running processes.
Figure 24.1. System Monitor — Processes
- view only active processes,
- view all processes,
- view your processes,
- view process dependencies,
- view a memory map of a selected process,
- view the files opened by a selected process, and
- refresh the list of processes.
- stop a process,
- continue running a stopped process,
- end a process,
- kill a process,
- change the priority of a selected process, and
- edit the System Monitor preferences, such as the refresh interval for the list of processes, or what information to show.
24.2. Viewing Memory Usage
24.2.1. Using the free Command
free command allows you to display the amount of free and used memory on the system. To do so, type the following at a shell prompt:
free
freefree command provides information about both the physical memory (Mem) and swap space (Swap). It displays the total amount of memory (total), as well as the amount of memory that is in use (used), free (free), shared (shared), in kernel buffers (buffers), and cached (cached). For example:
free
total used free shared buffers cached
Mem: 760752 661332 99420 0 6476 317200
-/+ buffers/cache: 337656 423096
Swap: 1540088 283652 1256436
~]$ free
total used free shared buffers cached
Mem: 760752 661332 99420 0 6476 317200
-/+ buffers/cache: 337656 423096
Swap: 1540088 283652 1256436free displays the values in kilobytes. To display the values in megabytes, supply the -m command-line option:
free -m
free -mfree -m
total used free shared buffers cached
Mem: 742 646 96 0 6 309
-/+ buffers/cache: 330 412
Swap: 1503 276 1227
~]$ free -m
total used free shared buffers cached
Mem: 742 646 96 0 6 309
-/+ buffers/cache: 330 412
Swap: 1503 276 122724.2.2. Using the System Monitor Tool
gnome-system-monitor at a shell prompt. Then click the Resources tab to view the system's memory usage.
Figure 24.2. System Monitor — Resources
24.3. Viewing CPU Usage
24.3.1. Using the System Monitor Tool
gnome-system-monitor at a shell prompt. Then click the Resources tab to view the system's CPU usage.
Figure 24.3. System Monitor — Resources
24.4. Viewing Block Devices and File Systems
24.4.1. Using the lsblk Command
lsblk command allows you to display a list of available block devices. To do so, type the following at a shell prompt:
lsblk
lsblklsblk command displays the device name (NAME), major and minor device number (MAJ:MIN), if the device is removable (RM), what is its size (SIZE), if the device is read-only (RO), what type is it (TYPE), and where the device is mounted (MOUNTPOINT). For example:
lsblk lists block devices in a tree-like format. To display the information as an ordinary list, add the -l command-line option:
lsblk -l
lsblk -l24.4.2. Using the blkid Command
blkid command allows you to display information about available block devices. To do so, type the following at a shell prompt as root:
blkid
blkidblkid command displays available attributes such as its universally unique identifier (UUID), file system type (TYPE), or volume label (LABEL). For example:
blkid /dev/vda1: UUID="7fa9c421-0054-4555-b0ca-b470a97a3d84" TYPE="ext4" /dev/vda2: UUID="7IvYzk-TnnK-oPjf-ipdD-cofz-DXaJ-gPdgBW" TYPE="LVM2_member" /dev/mapper/vg_kvm-lv_root: UUID="a07b967c-71a0-4925-ab02-aebcad2ae824" TYPE="ext4" /dev/mapper/vg_kvm-lv_swap: UUID="d7ef54ca-9c41-4de4-ac1b-4193b0c1ddb6" TYPE="swap"
~]# blkid
/dev/vda1: UUID="7fa9c421-0054-4555-b0ca-b470a97a3d84" TYPE="ext4"
/dev/vda2: UUID="7IvYzk-TnnK-oPjf-ipdD-cofz-DXaJ-gPdgBW" TYPE="LVM2_member"
/dev/mapper/vg_kvm-lv_root: UUID="a07b967c-71a0-4925-ab02-aebcad2ae824" TYPE="ext4"
/dev/mapper/vg_kvm-lv_swap: UUID="d7ef54ca-9c41-4de4-ac1b-4193b0c1ddb6" TYPE="swap"blkid command lists all available block devices. To display information about a particular device only, specify the device name on the command line:
blkid device_name
blkid device_name/dev/vda1, type:
blkid /dev/vda1 /dev/vda1: UUID="7fa9c421-0054-4555-b0ca-b470a97a3d84" TYPE="ext4"
~]# blkid /dev/vda1
/dev/vda1: UUID="7fa9c421-0054-4555-b0ca-b470a97a3d84" TYPE="ext4"-p and -o udev command-line options to obtain more detailed information. Note that root privileges are required to run this command:
blkid -po udev device_name
blkid -po udev device_name24.4.3. Using the findmnt Command
findmnt command allows you to display a list of currently mounted file systems. To do so, type the following at a shell prompt:
findmnt
findmntfindmnt command displays the target mount point (TARGET), source device (SOURCE), file system type (FSTYPE), and relevant mount options (OPTIONS). For example:
findmnt lists file systems in a tree-like format. To display the information as an ordinary list, add the -l command-line option:
findmnt -l
findmnt -l-t command-line option followed by a file system type:
findmnt -t type
findmnt -t typeext4 file systems, type:
findmnt -t ext4 TARGET SOURCE FSTYPE OPTIONS / /dev/mapper/vg_kvm-lv_root ext4 rw,relatime,seclabel,barrier=1,data=ord /boot /dev/vda1 ext4 rw,relatime,seclabel,barrier=1,data=ord
~]$ findmnt -t ext4
TARGET SOURCE FSTYPE OPTIONS
/ /dev/mapper/vg_kvm-lv_root ext4 rw,relatime,seclabel,barrier=1,data=ord
/boot /dev/vda1 ext4 rw,relatime,seclabel,barrier=1,data=ord24.4.4. Using the df Command
df command allows you to display a detailed report on the system's disk space usage. To do so, type the following at a shell prompt:
df
dfdf command displays its name (Filesystem), size (1K-blocks or Size), how much space is used (Used), how much space is still available (Available), the percentage of space usage (Use%), and where is the file system mounted (Mounted on). For example:
df Filesystem 1K-blocks Used Available Use% Mounted on /dev/mapper/vg_kvm-lv_root 18618236 4357360 13315112 25% / tmpfs 380376 288 380088 1% /dev/shm /dev/vda1 495844 77029 393215 17% /boot
~]$ df
Filesystem 1K-blocks Used Available Use% Mounted on
/dev/mapper/vg_kvm-lv_root 18618236 4357360 13315112 25% /
tmpfs 380376 288 380088 1% /dev/shm
/dev/vda1 495844 77029 393215 17% /bootdf command shows the partition size in 1 kilobyte blocks and the amount of used and available disk space in kilobytes. To view the information in megabytes and gigabytes, supply the -h command-line option, which causes df to display the values in a human-readable format:
df -h
df -hdf -h Filesystem Size Used Avail Use% Mounted on /dev/mapper/vg_kvm-lv_root 18G 4.2G 13G 25% / tmpfs 372M 288K 372M 1% /dev/shm /dev/vda1 485M 76M 384M 17% /boot
~]$ df -h
Filesystem Size Used Avail Use% Mounted on
/dev/mapper/vg_kvm-lv_root 18G 4.2G 13G 25% /
tmpfs 372M 288K 372M 1% /dev/shm
/dev/vda1 485M 76M 384M 17% /boot24.4.5. Using the du Command
du command allows you to displays the amount of space that is being used by files in a directory. To display the disk usage for each of the subdirectories in the current working directory, run the command with no additional command-line options:
du
dudu command displays the disk usage in kilobytes. To view the information in megabytes and gigabytes, supply the -h command-line option, which causes the utility to display the values in a human-readable format:
du -h
du -hdu command always shows the grand total for the current directory. To display only this information, supply the -s command-line option:
du -sh
du -shdu -sh 15M .
~]$ du -sh
15M .24.4.6. Using the System Monitor Tool
gnome-system-monitor at a shell prompt. Then click the File Systems tab to view a list of file systems.
Figure 24.4. System Monitor — File Systems
24.4.7. Monitoring Files and Directories with gamin
inotify. Changes on other file systems are monitored by the inotify monitor that is implemented in GLib directly.
/mnt/* or /media/* on Linux. Users can override or extend these settings by modifying the content of one of the following configuration files:
/etc/gamin/gaminrc$HOME/.gaminrc/etc/gamin/mandatory_gaminrc
Commands accepted by the configuration file
- notify
- To express that kernel monitoring should be used for matching paths.
- poll
- To express that polling should be used for matching paths.
- fsset
- To control what notification method is used on a filesystem type.
/etc/gamin/gaminrc~/.gaminrc/etc/gamin/mandatory_gaminrc
/etc/gamin/mandatory_gaminrc configuration file allows the system administrator to override any potentially dangerous preferences set by the user. When checking a path to guess whether polling or kernel notification should be used, gamin checks first the user-provided rules in their declaration order within the configuration file and then check the predefined rules. This way the first declaration for /mnt/local* in the example override the default one for /mnt/*.
24.5. Viewing Hardware Information
24.5.1. Using the lspci Command
lspci command allows you to display information about PCI buses and devices that are attached to them. To list all PCI devices that are in the system, type the following at a shell prompt:
lspci
lspci-v command-line option to display more verbose output, or -vv for very verbose output:
lspci -v|-vv
lspci -v|-vv24.5.2. Using the lsusb Command
lsusb command allows you to display information about USB buses and devices that are attached to them. To list all USB devices that are in the system, type the following at a shell prompt:
lsusb
lsusb-v command-line option to display more verbose output:
lsusb -v
lsusb -v24.5.3. Using the lspcmcia Command
lspcmcia command allows you to list all PCMCIA devices that are present in the system. To do so, type the following at a shell prompt:
lspcmcia
lspcmcialspcmcia Socket 0 Bridge: [yenta_cardbus] (bus ID: 0000:15:00.0)
~]$ lspcmcia
Socket 0 Bridge: [yenta_cardbus] (bus ID: 0000:15:00.0)-v command-line option to display more verbose information, or -vv to increase the verbosity level even further:
lspcmcia -v|-vv
lspcmcia -v|-vvlspcmcia -v
Socket 0 Bridge: [yenta_cardbus] (bus ID: 0000:15:00.0)
Configuration: state: on ready: unknown
~]$ lspcmcia -v
Socket 0 Bridge: [yenta_cardbus] (bus ID: 0000:15:00.0)
Configuration: state: on ready: unknown24.5.4. Using the lscpu Command
lscpu command allows you to list information about CPUs that are present in the system, including the number of CPUs, their architecture, vendor, family, model, CPU caches, etc. To do so, type the following at a shell prompt:
lscpu
lscpu24.6. Monitoring Performance with Net-SNMP
24.6.1. Installing Net-SNMP
| Package | Provides |
|---|---|
| net-snmp | The SNMP Agent Daemon and documentation. This package is required for exporting performance data. |
| net-snmp-libs | The netsnmp library and the bundled management information bases (MIBs). This package is required for exporting performance data. |
| net-snmp-utils | SNMP clients such as snmpget and snmpwalk. This package is required in order to query a system's performance data over SNMP. |
| net-snmp-perl | The mib2c utility and the NetSNMP Perl module. |
| net-snmp-python | An SNMP client library for Python. |
yum command in the following form:
yum install package
yum install packageyum install net-snmp net-snmp-libs net-snmp-utils
~]# yum install net-snmp net-snmp-libs net-snmp-utilsroot) to run this command. For more information on how to install new packages in Red Hat Enterprise Linux, see Section 8.2.4, “Installing Packages”.
24.6.2. Running the Net-SNMP Daemon
snmpd, the SNMP Agent Daemon. This section provides information on how to start, stop, and restart the snmpd service, and shows how to enable it in a particular runlevel. For more information on the concept of runlevels and how to manage system services in Red Hat Enterprise Linux in general, see Chapter 12, Services and Daemons.
24.6.2.1. Starting the Service
snmpd service in the current session, type the following at a shell prompt as root:
service snmpd start
service snmpd startchkconfig snmpd on
chkconfig snmpd on24.6.2.2. Stopping the Service
snmpd service, type the following at a shell prompt as root:
service snmpd stop
service snmpd stopchkconfig snmpd off
chkconfig snmpd off24.6.2.3. Restarting the Service
snmpd service, type the following at a shell prompt:
service snmpd restart
service snmpd restartservice snmpd reload
service snmpd reloadsnmpd service to reload the configuration.
24.6.3. Configuring Net-SNMP
/etc/snmp/snmpd.conf configuration file. The default snmpd.conf file shipped with Red Hat Enterprise Linux 6 is heavily commented and serves as a good starting point for agent configuration.
snmpconf which can be used to interactively generate a valid agent configuration.
snmpwalk utility described in this section.
Note
snmpd service to re-read the configuration by running the following command as root:
service snmpd reload
service snmpd reload24.6.3.1. Setting System Information
system tree. For example, the following snmpwalk command shows the system tree with a default agent configuration.
sysName object is set to the host name. The sysLocation and sysContact objects can be configured in the /etc/snmp/snmpd.conf file by changing the value of the syslocation and syscontact directives, for example:
syslocation Datacenter, Row 3, Rack 2 syscontact UNIX Admin <admin@example.com>
syslocation Datacenter, Row 3, Rack 2
syscontact UNIX Admin <admin@example.com>snmpwalk command again:
24.6.3.2. Configuring Authentication
Configuring SNMP Version 2c Community
rocommunity or rwcommunity directive in the /etc/snmp/snmpd.conf configuration file. The format of the directives is the following:
directive community [source [OID]]
directive community [source [OID]]system tree to a client using the community string “redhat” on the local machine:
rocommunity redhat 127.0.0.1 .1.3.6.1.2.1.1
rocommunity redhat 127.0.0.1 .1.3.6.1.2.1.1snmpwalk command with the -v and -c options.
Configuring SNMP Version 3 User
net-snmp-create-v3-user command. This command adds entries to the /var/lib/net-snmp/snmpd.conf and /etc/snmp/snmpd.conf files which create the user and grant access to the user. Note that the net-snmp-create-v3-user command may only be run when the agent is not running. The following example creates the “admin” user with the password “redhatsnmp”:
rwuser directive (or rouser when the -ro command-line option is supplied) that net-snmp-create-v3-user adds to /etc/snmp/snmpd.conf has a similar format to the rwcommunity and rocommunity directives:
directive user [noauth|auth|priv] [OID]
directive user [noauth|auth|priv] [OID]auth option). The noauth option allows you to permit unauthenticated requests, and the priv option enforces the use of encryption. The authpriv option specifies that requests must be authenticated and replies should be encrypted.
rwuser admin authpriv .1
rwuser admin authpriv .1.snmp directory in your user's home directory and a configuration file named snmp.conf in that directory (~/.snmp/snmp.conf) with the following lines:
defVersion 3 defSecurityLevel authPriv defSecurityName admin defPassphrase redhatsnmp
defVersion 3
defSecurityLevel authPriv
defSecurityName admin
defPassphrase redhatsnmpsnmpwalk command will now use these authentication settings when querying the agent:
snmpwalk -v3 localhost system SNMPv2-MIB::sysDescr.0 = STRING: Linux localhost.localdomain 2.6.32-122.el6.x86_64 #1 SMP Wed Mar 9 23:54:34 EST 2011 x86_64 [output truncated]
~]$ snmpwalk -v3 localhost system
SNMPv2-MIB::sysDescr.0 = STRING: Linux localhost.localdomain 2.6.32-122.el6.x86_64 #1 SMP Wed Mar 9 23:54:34 EST 2011 x86_64
[output truncated]24.6.4. Retrieving Performance Data over SNMP
24.6.4.1. Hardware Configuration
Host Resources MIB included with Net-SNMP presents information about the current hardware and software configuration of a host to a client utility. Table 24.3, “Available OIDs” summarizes the different OIDs available under that MIB.
| OID | Description |
|---|---|
HOST-RESOURCES-MIB::hrSystem | Contains general system information such as uptime, number of users, and number of running processes. |
HOST-RESOURCES-MIB::hrStorage | Contains data on memory and file system usage. |
HOST-RESOURCES-MIB::hrDevices | Contains a listing of all processors, network devices, and file systems. |
HOST-RESOURCES-MIB::hrSWRun | Contains a listing of all running processes. |
HOST-RESOURCES-MIB::hrSWRunPerf | Contains memory and CPU statistics on the process table from HOST-RESOURCES-MIB::hrSWRun. |
HOST-RESOURCES-MIB::hrSWInstalled | Contains a listing of the RPM database. |
HOST-RESOURCES-MIB::hrFSTable:
HOST-RESOURCES-MIB, see the /usr/share/snmp/mibs/HOST-RESOURCES-MIB.txt file.
24.6.4.2. CPU and Memory Information
UCD SNMP MIB. The systemStats OID provides a number of counters around processor usage:
ssCpuRawUser, ssCpuRawSystem, ssCpuRawWait, and ssCpuRawIdle OIDs provide counters which are helpful when determining whether a system is spending most of its processor time in kernel space, user space, or I/O. ssRawSwapIn and ssRawSwapOut can be helpful when determining whether a system is suffering from memory exhaustion.
UCD-SNMP-MIB::memory OID, which provides similar data to the free command:
UCD SNMP MIB. The SNMP table UCD-SNMP-MIB::laTable has a listing of the 1, 5, and 15 minute load averages:
24.6.4.3. File System and Disk Information
Host Resources MIB provides information on file system size and usage. Each file system (and also each memory pool) has an entry in the HOST-RESOURCES-MIB::hrStorageTable table:
HOST-RESOURCES-MIB::hrStorageSize and HOST-RESOURCES-MIB::hrStorageUsed can be used to calculate the remaining capacity of each mounted file system.
UCD-SNMP-MIB::systemStats (ssIORawSent.0 and ssIORawRecieved.0) and in UCD-DISKIO-MIB::diskIOTable. The latter provides much more granular data. Under this table are OIDs for diskIONReadX and diskIONWrittenX, which provide counters for the number of bytes read from and written to the block device in question since the system boot:
24.6.4.4. Network Information
Interfaces MIB provides information on network devices. IF-MIB::ifTable provides an SNMP table with an entry for each interface on the system, the configuration of the interface, and various packet counters for the interface. The following example shows the first few columns of ifTable on a system with two physical network interfaces:
IF-MIB::ifOutOctets and IF-MIB::ifInOctets. The following SNMP queries will retrieve network traffic for each of the interfaces on this system:
24.6.5. Extending Net-SNMP
24.6.5.1. Extending Net-SNMP with Shell Scripts
NET-SNMP-EXTEND-MIB) that can be used to query arbitrary shell scripts. To specify the shell script to run, use the extend directive in the /etc/snmp/snmpd.conf file. Once defined, the Agent will provide the exit code and any output of the command over SNMP. The example below demonstrates this mechanism with a script which determines the number of httpd processes in the process table.
Note
proc directive. See the snmpd.conf(5) manual page for more information.
httpd processes running on the system at a given point in time:
#!/bin/sh NUMPIDS=`pgrep httpd | wc -l` exit $NUMPIDS
#!/bin/sh
NUMPIDS=`pgrep httpd | wc -l`
exit $NUMPIDSextend directive to the /etc/snmp/snmpd.conf file. The format of the extend directive is the following:
extend name prog args
extend name prog args/usr/local/bin/check_apache.sh, the following directive will add the script to the SNMP tree:
extend httpd_pids /bin/sh /usr/local/bin/check_apache.sh
extend httpd_pids /bin/sh /usr/local/bin/check_apache.shNET-SNMP-EXTEND-MIB::nsExtendObjects:
extend directive. For example, the following shell script can be used to determine the number of processes matching an arbitrary string, and will also output a text string giving the number of processes:
/etc/snmp/snmpd.conf directives will give both the number of httpd PIDs as well as the number of snmpd PIDs when the above script is copied to /usr/local/bin/check_proc.sh:
extend httpd_pids /bin/sh /usr/local/bin/check_proc.sh httpd extend snmpd_pids /bin/sh /usr/local/bin/check_proc.sh snmpd
extend httpd_pids /bin/sh /usr/local/bin/check_proc.sh httpd
extend snmpd_pids /bin/sh /usr/local/bin/check_proc.sh snmpdsnmpwalk of the nsExtendObjects OID:
Warning
httpd processes. This query could be used during a performance test to determine the impact of the number of processes on memory pressure:
snmpget localhost \
'NET-SNMP-EXTEND-MIB::nsExtendResult."httpd_pids"' \
UCD-SNMP-MIB::memAvailReal.0
NET-SNMP-EXTEND-MIB::nsExtendResult."httpd_pids" = INTEGER: 8
UCD-SNMP-MIB::memAvailReal.0 = INTEGER: 799664 kB
~]$ snmpget localhost \
'NET-SNMP-EXTEND-MIB::nsExtendResult."httpd_pids"' \
UCD-SNMP-MIB::memAvailReal.0
NET-SNMP-EXTEND-MIB::nsExtendResult."httpd_pids" = INTEGER: 8
UCD-SNMP-MIB::memAvailReal.0 = INTEGER: 799664 kB24.6.5.2. Extending Net-SNMP with Perl
extend directive is a fairly limited method for exposing custom application metrics over SNMP. The Net-SNMP Agent also provides an embedded Perl interface for exposing custom objects. The net-snmp-perl package provides the NetSNMP::agent Perl module that is used to write embedded Perl plug-ins on Red Hat Enterprise Linux.
NetSNMP::agent Perl module provides an agent object which is used to handle requests for a part of the agent's OID tree. The agent object's constructor has options for running the agent as a sub-agent of snmpd or a standalone agent. No arguments are necessary to create an embedded agent:
use NetSNMP::agent (':all');
my $agent = new NetSNMP::agent();
use NetSNMP::agent (':all');
my $agent = new NetSNMP::agent();agent object has a register method which is used to register a callback function with a particular OID. The register function takes a name, OID, and pointer to the callback function. The following example will register a callback function named hello_handler with the SNMP Agent which will handle requests under the OID .1.3.6.1.4.1.8072.9999.9999:
$agent->register("hello_world", ".1.3.6.1.4.1.8072.9999.9999",
\&hello_handler);
$agent->register("hello_world", ".1.3.6.1.4.1.8072.9999.9999",
\&hello_handler);Note
.1.3.6.1.4.1.8072.9999.9999 (NET-SNMP-MIB::netSnmpPlaypen) is typically used for demonstration purposes only. If your organization does not already have a root OID, you can obtain one by contacting an ISO Name Registration Authority (ANSI in the United States).
HANDLER, REGISTRATION_INFO, REQUEST_INFO, and REQUESTS. The REQUESTS parameter contains a list of requests in the current call and should be iterated over and populated with data. The request objects in the list have get and set methods which allow for manipulating the OID and value of the request. For example, the following call will set the value of a request object to the string “hello world”:
$request->setValue(ASN_OCTET_STR, "hello world");
$request->setValue(ASN_OCTET_STR, "hello world");getMode method on the request_info object passed as the third parameter to the handler function. If the request is a GET request, the caller will expect the handler to set the value of the request object, depending on the OID of the request. If the request is a GETNEXT request, the caller will also expect the handler to set the OID of the request to the next available OID in the tree. This is illustrated in the following code example:
getMode returns MODE_GET, the handler analyzes the value of the getOID call on the request object. The value of the request is set to either string_value if the OID ends in “.1.0”, or set to integer_value if the OID ends in “.1.1”. If the getMode returns MODE_GETNEXT, the handler determines whether the OID of the request is “.1.0”, and then sets the OID and value for “.1.1”. If the request is higher on the tree than “.1.0”, the OID and value for “.1.0” is set. This in effect returns the “next” value in the tree so that a program like snmpwalk can traverse the tree without prior knowledge of the structure.
NetSNMP::ASN. See the perldoc for NetSNMP::ASN for a full list of available constants.
/usr/share/snmp/hello_world.pl and add the following line to the /etc/snmp/snmpd.conf configuration file:
perl do "/usr/share/snmp/hello_world.pl"
perl do "/usr/share/snmp/hello_world.pl"snmpwalk should return the new data:
snmpwalk localhost NET-SNMP-MIB::netSnmpPlaypen NET-SNMP-MIB::netSnmpPlaypen.1.0 = STRING: "hello world" NET-SNMP-MIB::netSnmpPlaypen.1.1 = INTEGER: 8675309
~]$ snmpwalk localhost NET-SNMP-MIB::netSnmpPlaypen
NET-SNMP-MIB::netSnmpPlaypen.1.0 = STRING: "hello world"
NET-SNMP-MIB::netSnmpPlaypen.1.1 = INTEGER: 8675309snmpget should also be used to exercise the other mode of the handler:
snmpget localhost \
NET-SNMP-MIB::netSnmpPlaypen.1.0 \
NET-SNMP-MIB::netSnmpPlaypen.1.1
NET-SNMP-MIB::netSnmpPlaypen.1.0 = STRING: "hello world"
NET-SNMP-MIB::netSnmpPlaypen.1.1 = INTEGER: 8675309
~]$ snmpget localhost \
NET-SNMP-MIB::netSnmpPlaypen.1.0 \
NET-SNMP-MIB::netSnmpPlaypen.1.1
NET-SNMP-MIB::netSnmpPlaypen.1.0 = STRING: "hello world"
NET-SNMP-MIB::netSnmpPlaypen.1.1 = INTEGER: 867530924.7. Additional Resources
24.7.1. Installed Documentation
- ps(1) — The manual page for the
pscommand. - top(1) — The manual page for the
topcommand. - free(1) — The manual page for the
freecommand. - df(1) — The manual page for the
dfcommand. - du(1) — The manual page for the
ducommand. - lspci(8) — The manual page for the
lspcicommand. - snmpd(8) — The manual page for the
snmpdservice. - snmpd.conf(5) — The manual page for the
/etc/snmp/snmpd.conffile containing full documentation of available configuration directives.
Chapter 25. Viewing and Managing Log Files
rsyslogd. The rsyslogd daemon is an enhanced replacement for previous sysklogd, and provides extended filtering, encryption protected relaying of messages, various configuration options, input and output modules, support for transportation via the TCP or UDP protocols. Note that rsyslog is compatible with sysklogd.
25.1. Installing rsyslog
root:
yum install rsyslog Loaded plugins: product-id, refresh-packagekit, subscription-manager Package rsyslog-5.8.10-10.el6_6.i686 already installed and latest version Nothing to do
~]# yum install rsyslog
Loaded plugins: product-id, refresh-packagekit, subscription-manager
Package rsyslog-5.8.10-10.el6_6.i686 already installed and latest version
Nothing to do25.1.1. Upgrading to rsyslog version 7
yum shell utility as described below.
Procedure 25.1. Upgrading to rsyslog 7
yum shell utility.
- Enter the following command as
rootto start the yum shell:The yum shell prompt appears.yum shell Loaded plugins: product-id, refresh-packagekit, subscription-manager
~]# yum shell Loaded plugins: product-id, refresh-packagekit, subscription-manager >Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter the following commands to install the rsyslog7 package and remove the rsyslog package.
> install rsyslog7 > remove rsyslog
> install rsyslog7 > remove rsyslogCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter
runto start the process:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter
ywhen prompted to start the upgrade. - When the upgrade is completed, the
yum shellprompt is displayed. Enterquitorexitto exit the shell:Finished Transaction > quit Leaving Shell ~]#
Finished Transaction > quit Leaving Shell ~]#Copy to Clipboard Copied! Toggle word wrap Toggle overflow
25.2. Locating Log Files
rsyslogd can be found in the /etc/rsyslog.conf configuration file. Most log files are located in the /var/log/ directory. Some applications such as httpd and samba have a directory within /var/log/ for their log files.
/var/log/ directory with numbers after them (for example, cron-20100906). These numbers represent a time stamp that has been added to a rotated log file. Log files are rotated so their file sizes do not become too large. The logrotate package contains a cron task that automatically rotates log files according to the /etc/logrotate.conf configuration file and the configuration files in the /etc/logrotate.d/ directory.
25.3. Basic Configuration of Rsyslog
/etc/rsyslog.conf. Here, you can specify global directives, modules, and rules that consist of filter and action parts. Also, you can add comments in the form of text following a hash sign (#).
25.3.1. Filters
/etc/rsyslog.conf configuration file, define both, a filter and an action, on one line and separate them with one or more spaces or tabs.
- Facility/Priority-based filters
- The most used and well-known way to filter syslog messages is to use the facility/priority-based filters which filter syslog messages based on two conditions: facility and priority separated by a dot. To create a selector, use the following syntax:
FACILITY.PRIORITY
FACILITY.PRIORITYCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:- FACILITY specifies the subsystem that produces a specific syslog message. For example, the
mailsubsystem handles all mail-related syslog messages. FACILITY can be represented by one of the following keywords (or by a numerical code):kern(0),user(1),mail(2),daemon(3),auth(4),syslog(5),lpr(6),news(7),uucp(8),cron(9),authpriv(10),ftp(11), andlocal0throughlocal7(16 - 23). - PRIORITY specifies a priority of a syslog message. PRIORITY can be represented by one of the following keywords (or by a number):
debug(7),info(6),notice(5),warning(4),err(3),crit(2),alert(1), andemerg(0).The aforementioned syntax selects syslog messages with the defined or higher priority. By preceding any priority keyword with an equal sign (=), you specify that only syslog messages with the specified priority will be selected. All other priorities will be ignored. Conversely, preceding a priority keyword with an exclamation mark (!) selects all syslog messages except those with the defined priority.
In addition to the keywords specified above, you may also use an asterisk (*) to define all facilities or priorities (depending on where you place the asterisk, before or after the comma). Specifying the priority keywordnoneserves for facilities with no given priorities. Both facility and priority conditions are case-insensitive.To define multiple facilities and priorities, separate them with a comma (,). To define multiple selectors on one line, separate them with a semi-colon (;). Note that each selector in the selector field is capable of overwriting the preceding ones, which can exclude some priorities from the pattern.Example 25.1. Facility/Priority-based Filters
The following are a few examples of simple facility/priority-based filters that can be specified in/etc/rsyslog.conf. To select all kernel syslog messages with any priority, add the following text into the configuration file:kern.*
kern.*Copy to Clipboard Copied! Toggle word wrap Toggle overflow To select all mail syslog messages with prioritycritand higher, use this form:mail.crit
mail.critCopy to Clipboard Copied! Toggle word wrap Toggle overflow To select all cron syslog messages except those with theinfoordebugpriority, set the configuration in the following form:cron.!info,!debug
cron.!info,!debugCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Property-based filters
- Property-based filters let you filter syslog messages by any property, such as
timegeneratedorsyslogtag. For more information on properties, see the section called “Properties”. You can compare each of the specified properties to a particular value using one of the compare-operations listed in Table 25.1, “Property-based compare-operations”. Both property names and compare operations are case-sensitive.Property-based filter must start with a colon (:). To define the filter, use the following syntax::PROPERTY, [!]COMPARE_OPERATION, "STRING"
:PROPERTY, [!]COMPARE_OPERATION, "STRING"Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:- The PROPERTY attribute specifies the desired property.
- The optional exclamation point (
!) negates the output of the compare-operation. Other Boolean operators are currently not supported in property-based filters. - The COMPARE_OPERATION attribute specifies one of the compare-operations listed in Table 25.1, “Property-based compare-operations”.
- The STRING attribute specifies the value that the text provided by the property is compared to. This value must be enclosed in quotation marks. To escape certain character inside the string (for example a quotation mark (
")), use the backslash character (\).
Expand Table 25.1. Property-based compare-operations Compare-operation Description containsChecks whether the provided string matches any part of the text provided by the property. To perform case-insensitive comparisons, use contains_i.isequalCompares the provided string against all of the text provided by the property. These two values must be exactly equal to match. startswithChecks whether the provided string is found exactly at the beginning of the text provided by the property. To perform case-insensitive comparisons, use startswith_i.regexCompares the provided POSIX BRE (Basic Regular Expression) against the text provided by the property. ereregexCompares the provided POSIX ERE (Extended Regular Expression) regular expression against the text provided by the property. isemptyChecks if the property is empty. The value is discarded. This is especially useful when working with normalized data, where some fields may be populated based on normalization result. Example 25.2. Property-based Filters
The following are a few examples of property-based filters that can be specified in/etc/rsyslog.conf. To select syslog messages which contain the stringerrorin their message text, use::msg, contains, "error"
:msg, contains, "error"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The following filter selects syslog messages received from the host namehost1::hostname, isequal, "host1"
:hostname, isequal, "host1"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To select syslog messages which do not contain any mention of the wordsfatalanderrorwith any or no text between them (for example,fatal lib error), type::msg, !regex, "fatal .* error"
:msg, !regex, "fatal .* error"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Expression-based filters
- Expression-based filters select syslog messages according to defined arithmetic, Boolean or string operations. Expression-based filters use rsyslog's own scripting language called RainerScript to build complex filters.The basic syntax of expression-based filter looks as follows:
if EXPRESSION then ACTION else ACTION
if EXPRESSION then ACTION else ACTIONCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:- The EXPRESSION attribute represents an expression to be evaluated, for example:
$msg startswith 'DEVNAME'or$syslogfacility-text == 'local0'. You can specify more than one expression in a single filter by usingandandoroperators. - The ACTION attribute represents an action to be performed if the expression returns the value
true. This can be a single action, or an arbitrary complex script enclosed in curly braces. - Expression-based filters are indicated by the keyword if at the start of a new line. The then keyword separates the EXPRESSION from the ACTION. Optionally, you can employ the else keyword to specify what action is to be performed in case the condition is not met.
With expression-based filters, you can nest the conditions by using a script enclosed in curly braces as in Example 25.3, “Expression-based Filters”. The script allows you to use facility/priority-based filters inside the expression. On the other hand, property-based filters are not recommended here. RainerScript supports regular expressions with specialized functionsre_match()andre_extract().Example 25.3. Expression-based Filters
The following expression contains two nested conditions. The log files created by a program called prog1 are split into two files based on the presence of the "test" string in the message.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
25.3.2. Actions
- Saving syslog messages to log files
- The majority of actions specify to which log file a syslog message is saved. This is done by specifying a file path after your already-defined selector:
FILTER PATH
FILTER PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow where FILTER stands for user-specified selector and PATH is a path of a target file.For instance, the following rule is comprised of a selector that selects all cron syslog messages and an action that saves them into the/var/log/cron.loglog file:cron.* /var/log/cron.log
cron.* /var/log/cron.logCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, the log file is synchronized every time a syslog message is generated. Use a dash mark (-) as a prefix of the file path you specified to omit syncing:FILTER -PATH
FILTER -PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that you might lose information if the system terminates right after a write attempt. However, this setting can improve performance, especially if you run programs that produce very verbose log messages.Your specified file path can be either static or dynamic. Static files are represented by a fixed file path as shown in the example above. Dynamic file paths can differ according to the received message. Dynamic file paths are represented by a template and a question mark (?) prefix:FILTER ?DynamicFile
FILTER ?DynamicFileCopy to Clipboard Copied! Toggle word wrap Toggle overflow where DynamicFile is a name of a predefined template that modifies output paths. You can use the dash prefix (-) to disable syncing, also you can use multiple templates separated by a colon (;). For more information on templates, see the section called “Generating Dynamic File Names”.If the file you specified is an existing terminal or/dev/consoledevice, syslog messages are sent to standard output (using special terminal-handling) or your console (using special/dev/console-handling) when using the X Window System, respectively. - Sending syslog messages over the network
- rsyslog allows you to send and receive syslog messages over the network. This feature allows you to administer syslog messages of multiple hosts on one machine. To forward syslog messages to a remote machine, use the following syntax:
@[(zNUMBER)]HOST:[PORT]
@[(zNUMBER)]HOST:[PORT]Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:- The at sign (
@) indicates that the syslog messages are forwarded to a host using theUDPprotocol. To use theTCPprotocol, use two at signs with no space between them (@@). - The optional
zNUMBERsetting enables zlib compression for syslog messages. The NUMBER attribute specifies the level of compression (from 1 – lowest to 9 – maximum). Compression gain is automatically checked byrsyslogd, messages are compressed only if there is any compression gain and messages below 60 bytes are never compressed. - The HOST attribute specifies the host which receives the selected syslog messages.
- The PORT attribute specifies the host machine's port.
When specifying anIPv6address as the host, enclose the address in square brackets ([,]).Example 25.4. Sending syslog Messages over the Network
The following are some examples of actions that forward syslog messages over the network (note that all actions are preceded with a selector that selects all messages with any priority). To forward messages to192.168.0.1via theUDPprotocol, type:*.* @192.168.0.1
*.* @192.168.0.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow To forward messages to "example.com" using port 6514 and theTCPprotocol, use:*.* @@example.com:6514
*.* @@example.com:6514Copy to Clipboard Copied! Toggle word wrap Toggle overflow The following compresses messages with zlib (level 9 compression) and forwards them to2001:db8::1using theUDPprotocol*.* @(z9)[2001:db8::1]
*.* @(z9)[2001:db8::1]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Output channels
- Output channels are primarily used to specify the maximum size a log file can grow to. This is very useful for log file rotation (for more information see Section 25.3.5, “Log Rotation”). An output channel is basically a collection of information about the output action. Output channels are defined by the
$outchanneldirective. To define an output channel in/etc/rsyslog.conf, use the following syntax:$outchannel NAME, FILE_NAME, MAX_SIZE, ACTION
$outchannel NAME, FILE_NAME, MAX_SIZE, ACTIONCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:- The NAME attribute specifies the name of the output channel.
- The FILE_NAME attribute specifies the name of the output file. Output channels can write only into files, not pipes, terminal, or other kind of output.
- The MAX_SIZE attribute represents the maximum size the specified file (in FILE_NAME) can grow to. This value is specified in bytes.
- The ACTION attribute specifies the action that is taken when the maximum size, defined in MAX_SIZE, is hit.
To use the defined output channel as an action inside a rule, type:FILTER :omfile:$NAME
FILTER :omfile:$NAMECopy to Clipboard Copied! Toggle word wrap Toggle overflow Example 25.5. Output channel log rotation
The following output shows a simple log rotation through the use of an output channel. First, the output channel is defined via the$outchanneldirective:$outchannel log_rotation, /var/log/test_log.log, 104857600, /home/joe/log_rotation_script
$outchannel log_rotation, /var/log/test_log.log, 104857600, /home/joe/log_rotation_scriptCopy to Clipboard Copied! Toggle word wrap Toggle overflow and then it is used in a rule that selects every syslog message with any priority and executes the previously-defined output channel on the acquired syslog messages:*.* :omfile:$log_rotation
*.* :omfile:$log_rotationCopy to Clipboard Copied! Toggle word wrap Toggle overflow Once the limit (in the example100 MB) is hit, the/home/joe/log_rotation_scriptis executed. This script can contain anything from moving the file into a different folder, editing specific content out of it, or simply removing it. - Sending syslog messages to specific users
- rsyslog can send syslog messages to specific users by specifying a user name of the user you want to send the messages to (as in Example 25.7, “Specifying Multiple Actions”). To specify more than one user, separate each user name with a comma (
,). To send messages to every user that is currently logged on, use an asterisk (*). - Executing a program
- rsyslog lets you execute a program for selected syslog messages and uses the
system()call to execute the program in shell. To specify a program to be executed, prefix it with a caret character (^). Consequently, specify a template that formats the received message and passes it to the specified executable as a one line parameter (for more information on templates, see Section 25.3.3, “Templates”).FILTER ^EXECUTABLE; TEMPLATE
FILTER ^EXECUTABLE; TEMPLATECopy to Clipboard Copied! Toggle word wrap Toggle overflow Here an output of the FILTER condition is processed by a program represented by EXECUTABLE. This program can be any valid executable. Replace TEMPLATE with the name of the formatting template.Example 25.6. Executing a Program
In the following example, any syslog message with any priority is selected, formatted with thetemplatetemplate and passed as a parameter to the test-program program, which is then executed with the provided parameter:*.* ^test-program;template
*.* ^test-program;templateCopy to Clipboard Copied! Toggle word wrap Toggle overflow Warning
When accepting messages from any host, and using the shell execute action, you may be vulnerable to command injection. An attacker may try to inject and execute commands in the program you specified to be executed in your action. To avoid any possible security threats, thoroughly consider the use of the shell execute action. - Storing syslog messages in a database
- Selected syslog messages can be directly written into a database table using the database writer action. The database writer uses the following syntax:
:PLUGIN:DB_HOST,DB_NAME,DB_USER,DB_PASSWORD;[TEMPLATE]
:PLUGIN:DB_HOST,DB_NAME,DB_USER,DB_PASSWORD;[TEMPLATE]Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:- The PLUGIN calls the specified plug-in that handles the database writing (for example, the
ommysqlplug-in). - The DB_HOST attribute specifies the database host name.
- The DB_NAME attribute specifies the name of the database.
- The DB_USER attribute specifies the database user.
- The DB_PASSWORD attribute specifies the password used with the aforementioned database user.
- The TEMPLATE attribute specifies an optional use of a template that modifies the syslog message. For more information on templates, see Section 25.3.3, “Templates”.
Important
Currently, rsyslog provides support forMySQLandPostgreSQLdatabases only. In order to use theMySQLandPostgreSQLdatabase writer functionality, install the rsyslog-mysql and rsyslog-pgsql packages, respectively. Also, make sure you load the appropriate modules in your/etc/rsyslog.confconfiguration file:$ModLoad ommysql # Output module for MySQL support $ModLoad ompgsql # Output module for PostgreSQL support
$ModLoad ommysql # Output module for MySQL support $ModLoad ompgsql # Output module for PostgreSQL supportCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information on rsyslog modules, see Section 25.7, “Using Rsyslog Modules”.Alternatively, you may use a generic database interface provided by theomlibdbmodule (supports: Firebird/Interbase, MS SQL, Sybase, SQLLite, Ingres, Oracle, mSQL). - Discarding syslog messages
- To discard your selected messages, use the tilde character (
~).FILTER ~
FILTER ~Copy to Clipboard Copied! Toggle word wrap Toggle overflow The discard action is mostly used to filter out messages before carrying on any further processing. It can be effective if you want to omit some repeating messages that would otherwise fill the log files. The results of discard action depend on where in the configuration file it is specified, for the best results place these actions on top of the actions list. Please note that once a message has been discarded there is no way to retrieve it in later configuration file lines.For instance, the following rule discards any cron syslog messages:cron.* ~
cron.* ~Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Specifying Multiple Actions
FILTER ACTION & ACTION & ACTION
FILTER ACTION
& ACTION
& ACTIONExample 25.7. Specifying Multiple Actions
crit) are sent to user user1, processed by the template temp and passed on to the test-program executable, and forwarded to 192.168.0.1 via the UDP protocol.
kern.=crit user1 & ^test-program;temp & @192.168.0.1
kern.=crit user1
& ^test-program;temp
& @192.168.0.1
;) and specify the name of the template. For more information on templates, see Section 25.3.3, “Templates”.
Warning
/etc/rsyslog.conf.
25.3.3. Templates
/etc/rsyslog.conf:
$template TEMPLATE_NAME,"text %PROPERTY% more text", [OPTION]
$template TEMPLATE_NAME,"text %PROPERTY% more text", [OPTION]$templateis the template directive that indicates that the text following it, defines a template.TEMPLATE_NAMEis the name of the template. Use this name to refer to the template.- Anything between the two quotation marks (
"…") is the actual template text. Within this text, special characters, such as\nfor new line or\rfor carriage return, can be used. Other characters, such as%or", have to be escaped if you want to use those characters literally. - The text specified between two percent signs (
%) specifies a property that allows you to access specific contents of a syslog message. For more information on properties, see the section called “Properties”. - The
OPTIONattribute specifies any options that modify the template functionality. The currently supported template options aresqlandstdsql, which are used for formatting the text as an SQL query.Note
Note that the database writer checks whether thesqlorstdsqloptions are specified in the template. If they are not, the database writer does not perform any action. This is to prevent any possible security threats, such as SQL injection.See section Storing syslog messages in a database in Section 25.3.2, “Actions” for more information.
Generating Dynamic File Names
timegenerated property, which extracts a time stamp from the message, to generate a unique file name for each syslog message:
$template DynamicFile,"/var/log/test_logs/%timegenerated%-test.log"
$template DynamicFile,"/var/log/test_logs/%timegenerated%-test.log"$template directive only specifies the template. You must use it inside a rule for it to take effect. In /etc/rsyslog.conf, use the question mark (?) in an action definition to mark the dynamic file name template:
*.* ?DynamicFile
*.* ?DynamicFileProperties
%)) enable access various contents of a syslog message through the use of a property replacer. To define a property inside a template (between the two quotation marks ("…")), use the following syntax:
%PROPERTY_NAME[:FROM_CHAR:TO_CHAR:OPTION]%
%PROPERTY_NAME[:FROM_CHAR:TO_CHAR:OPTION]%- The PROPERTY_NAME attribute specifies the name of a property. A list of all available properties and their detailed description can be found in the
rsyslog.conf(5)manual page under the section Available Properties. - FROM_CHAR and TO_CHAR attributes denote a range of characters that the specified property will act upon. Alternatively, regular expressions can be used to specify a range of characters. To do so, set the letter
Ras the FROM_CHAR attribute and specify your desired regular expression as the TO_CHAR attribute. - The OPTION attribute specifies any property options, such as the
lowercaseoption to convert the input to lowercase. A list of all available property options and their detailed description can be found in thersyslog.conf(5)manual page under the section Property Options.
- The following property obtains the whole message text of a syslog message:
%msg%
%msg%Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The following property obtains the first two characters of the message text of a syslog message:
%msg:1:2%
%msg:1:2%Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The following property obtains the whole message text of a syslog message and drops its last line feed character:
%msg:::drop-last-lf%
%msg:::drop-last-lf%Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The following property obtains the first 10 characters of the time stamp that is generated when the syslog message is received and formats it according to the RFC 3999 date standard.
%timegenerated:1:10:date-rfc3339%
%timegenerated:1:10:date-rfc3339%Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Template Examples
Example 25.8. A verbose syslog message template
$template verbose, "%syslogseverity%, %syslogfacility%, %timegenerated%, %HOSTNAME%, %syslogtag%, %msg%\n"
$template verbose, "%syslogseverity%, %syslogfacility%, %timegenerated%, %HOSTNAME%, %syslogtag%, %msg%\n"mesg(1) permission set to yes). This template outputs the message text, along with a host name, message tag and a time stamp, on a new line (using \r and \n) and rings the bell (using \7).
Example 25.9. A wall message template
$template wallmsg,"\r\n\7Message from syslogd@%HOSTNAME% at %timegenerated% ...\r\n %syslogtag% %msg%\n\r"
$template wallmsg,"\r\n\7Message from syslogd@%HOSTNAME% at %timegenerated% ...\r\n %syslogtag% %msg%\n\r"sql option at the end of the template specified as the template option. It tells the database writer to format the message as an MySQL SQL query.
Example 25.10. A database formatted message template
$template dbFormat,"insert into SystemEvents (Message, Facility, FromHost, Priority, DeviceReportedTime, ReceivedAt, InfoUnitID, SysLogTag) values ('%msg%', %syslogfacility%, '%HOSTNAME%', %syslogpriority%, '%timereported:::date-mysql%', '%timegenerated:::date-mysql%', %iut%, '%syslogtag%')", sql
$template dbFormat,"insert into SystemEvents (Message, Facility, FromHost, Priority, DeviceReportedTime, ReceivedAt, InfoUnitID, SysLogTag) values ('%msg%', %syslogfacility%, '%HOSTNAME%', %syslogpriority%, '%timereported:::date-mysql%', '%timegenerated:::date-mysql%', %iut%, '%syslogtag%')", sqlRSYSLOG_ prefix. These are reserved for the syslog's use and it is advisable to not create a template using this prefix to avoid conflicts. The following list shows these predefined templates along with their definitions.
RSYSLOG_DebugFormat- A special format used for troubleshooting property problems.
"Debug line with all properties:\nFROMHOST: '%FROMHOST%', fromhost-ip: '%fromhost-ip%', HOSTNAME: '%HOSTNAME%', PRI: %PRI%,\nsyslogtag '%syslogtag%', programname: '%programname%', APP-NAME: '%APP-NAME%', PROCID: '%PROCID%', MSGID: '%MSGID%',\nTIMESTAMP: '%TIMESTAMP%', STRUCTURED-DATA: '%STRUCTURED-DATA%',\nmsg: '%msg%'\nescaped msg: '%msg:::drop-cc%'\nrawmsg: '%rawmsg%'\n\n\"
"Debug line with all properties:\nFROMHOST: '%FROMHOST%', fromhost-ip: '%fromhost-ip%', HOSTNAME: '%HOSTNAME%', PRI: %PRI%,\nsyslogtag '%syslogtag%', programname: '%programname%', APP-NAME: '%APP-NAME%', PROCID: '%PROCID%', MSGID: '%MSGID%',\nTIMESTAMP: '%TIMESTAMP%', STRUCTURED-DATA: '%STRUCTURED-DATA%',\nmsg: '%msg%'\nescaped msg: '%msg:::drop-cc%'\nrawmsg: '%rawmsg%'\n\n\"Copy to Clipboard Copied! Toggle word wrap Toggle overflow RSYSLOG_SyslogProtocol23Format- The format specified in IETF's internet-draft ietf-syslog-protocol-23, which is assumed to become the new syslog standard RFC.
"%PRI%1 %TIMESTAMP:::date-rfc3339% %HOSTNAME% %APP-NAME% %PROCID% %MSGID% %STRUCTURED-DATA% %msg%\n\"
"%PRI%1 %TIMESTAMP:::date-rfc3339% %HOSTNAME% %APP-NAME% %PROCID% %MSGID% %STRUCTURED-DATA% %msg%\n\"Copy to Clipboard Copied! Toggle word wrap Toggle overflow RSYSLOG_FileFormat- A modern-style logfile format similar to TraditionalFileFormat, but with high-precision time stamps and time zone information.
"%TIMESTAMP:::date-rfc3339% %HOSTNAME% %syslogtag%%msg:::sp-if-no-1st-sp%%msg:::drop-last-lf%\n\"
"%TIMESTAMP:::date-rfc3339% %HOSTNAME% %syslogtag%%msg:::sp-if-no-1st-sp%%msg:::drop-last-lf%\n\"Copy to Clipboard Copied! Toggle word wrap Toggle overflow RSYSLOG_TraditionalFileFormat- The older default log file format with low-precision time stamps.
"%TIMESTAMP% %HOSTNAME% %syslogtag%%msg:::sp-if-no-1st-sp%%msg:::drop-last-lf%\n\"
"%TIMESTAMP% %HOSTNAME% %syslogtag%%msg:::sp-if-no-1st-sp%%msg:::drop-last-lf%\n\"Copy to Clipboard Copied! Toggle word wrap Toggle overflow RSYSLOG_ForwardFormat- A forwarding format with high-precision time stamps and time zone information.
"%PRI%%TIMESTAMP:::date-rfc3339% %HOSTNAME% %syslogtag:1:32%%msg:::sp-if-no-1st-sp%%msg%\"
"%PRI%%TIMESTAMP:::date-rfc3339% %HOSTNAME% %syslogtag:1:32%%msg:::sp-if-no-1st-sp%%msg%\"Copy to Clipboard Copied! Toggle word wrap Toggle overflow RSYSLOG_TraditionalForwardFormat- The traditional forwarding format with low-precision time stamps.
"%PRI%%TIMESTAMP% %HOSTNAME% %syslogtag:1:32%%msg:::sp-if-no-1st-sp%%msg%\"
"%PRI%%TIMESTAMP% %HOSTNAME% %syslogtag:1:32%%msg:::sp-if-no-1st-sp%%msg%\"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
25.3.4. Global Directives
rsyslogd daemon. They usually specify a value for a specific predefined variable that affects the behavior of the rsyslogd daemon or a rule that follows. All of the global directives must start with a dollar sign ($). Only one directive can be specified per line. The following is an example of a global directive that specifies the maximum size of the syslog message queue:
$MainMsgQueueSize 50000
$MainMsgQueueSize 50000
10,000 messages) can be overridden by specifying a different value (as shown in the example above).
/etc/rsyslog.conf configuration file. A directive affects the behavior of all configuration options until another occurrence of that same directive is detected. Global directives can be used to configure actions, queues and for debugging. A comprehensive list of all available configuration directives can be found in the section called “Online Documentation”. Currently, a new configuration format has been developed that replaces the $-based syntax (see Section 25.4, “Using the New Configuration Format”). However, classic global directives remain supported as a legacy format.
25.3.5. Log Rotation
/etc/logrotate.conf configuration file:
.gz format. Any lines that begin with a hash sign (#) are comments and are not processed.
/etc/logrotate.d/ directory and define any configuration options there.
/etc/logrotate.d/ directory:
/var/log/messages log file only. The settings specified here override the global settings where possible. Thus the rotated /var/log/messages log file will be kept for five weeks instead of four weeks as was defined in the global options.
weekly— Specifies the rotation of log files to be done weekly. Similar directives include:dailymonthlyyearly
compress— Enables compression of rotated log files. Similar directives include:nocompresscompresscmd— Specifies the command to be used for compressing.uncompresscmdcompressext— Specifies what extension is to be used for compressing.compressoptions— Specifies any options to be passed to the compression program used.delaycompress— Postpones the compression of log files to the next rotation of log files.
rotate INTEGER— Specifies the number of rotations a log file undergoes before it is removed or mailed to a specific address. If the value0is specified, old log files are removed instead of rotated.mail ADDRESS— This option enables mailing of log files that have been rotated as many times as is defined by therotatedirective to the specified address. Similar directives include:nomailmailfirst— Specifies that the just-rotated log files are to be mailed, instead of the about-to-expire log files.maillast— Specifies that the about-to-expire log files are to be mailed, instead of the just-rotated log files. This is the default option whenmailis enabled.
logrotate(5) manual page.
25.4. Using the New Configuration Format
/etc/rsyslog.conf configuration file. To install rsyslog 7, see Section 25.1.1, “Upgrading to rsyslog version 7”.
input() and ruleset() statements, which permit the /etc/rsyslog.conf configuration file to be written in the new syntax. The new syntax differs mainly in that it is much more structured; parameters are passed as arguments to statements, such as input, action, template, and module load. The scope of options is limited by blocks. This enhances readability and reduces the number of bugs caused by misconfiguration. There is also a significant performance gain. Some functionality is exposed in both syntaxes, some only in the new one.
$InputFileName /tmp/inputfile $InputFileTag tag1: $InputFileStateFile inputfile-state $InputRunFileMonitor
$InputFileName /tmp/inputfile
$InputFileTag tag1:
$InputFileStateFile inputfile-state
$InputRunFileMonitor
input(type="imfile" file="/tmp/inputfile" tag="tag1:" statefile="inputfile-state")
input(type="imfile" file="/tmp/inputfile" tag="tag1:" statefile="inputfile-state")
25.4.1. Rulesets
/etc/rsyslog.conf file, all rules are evaluated in order of appearance for every input message. This process starts with the first rule and continues until all rules have been processed or until the message is discarded by one of the rules.
/etc/rsyslog.conf can look as follows:
$RuleSet rulesetname rule rule2
$RuleSet rulesetname
rule
rule2$RuleSet RSYSLOG_DefaultRuleset
$RuleSet RSYSLOG_DefaultRulesetinput() and ruleset() statements are reserved for this operation. The new format ruleset definition in /etc/rsyslog.conf can look as follows:
RSYSLOG_ since this namespace is reserved for use by rsyslog. RSYSLOG_DefaultRuleset then defines the default set of rules to be performed if the message has no other ruleset assigned. With rule and rule2 you can define rules in filter-action format mentioned above. With the call parameter, you can nest rulesets by calling them from inside other ruleset blocks.
input(type="input_type" port="port_num" ruleset="rulesetname");
input(type="input_type" port="port_num" ruleset="rulesetname");input(). Replace rulesetname with a name of the ruleset to be evaluated against the message. In case an input message is not explicitly bound to a ruleset, the default ruleset is triggered.
Example 25.11. Using rulesets
/etc/rsyslog.conf:
601, messages are sorted according to the facility. Then, the TCP input is enabled and bound to rulesets. Note that you must load the required modules (imtcp) for this configuration to work.
25.4.2. Compatibility with sysklogd
-c option exists in rsyslog version 5 but not in version 7. Also, the sysklogd-style command-line options are deprecated and configuring rsyslog through these command-line options should be avoided. However, you can use several templates and directives to configure rsyslogd to emulate sysklogd-like behavior.
rsyslogd options, see the rsyslogd(8)manual page.
25.5. Working with Queues in Rsyslog
Figure 25.1. Message Flow in Rsyslog
/etc/rsyslog.conf are applied. Based on these rules, the rule processor evaluates which actions are to be performed. Each action has its own action queue. Messages are passed through this queue to the respective action processor which creates the final output. Note that at this point, several actions can run simultaneously on one message. For this purpose, a message is duplicated and passed to multiple action processors.
- they serve as buffers that decouple producers and consumers in the structure of rsyslog
- they allow for parallelization of actions performed on messages
Warning
SSH logging, which in turn can prevent SSH access. Therefore it is advised to use dedicated action queues for outputs which are forwarded over a network or to a database.
25.5.1. Defining Queues
/etc/rsyslog.conf:
$objectQueueType queue_type
$objectQueueType queue_typeMainMsg) or for an action queue (replace object with Action). Replace queue_type with one of direct, linkedlist or fixedarray (which are in-memory queues), or disk.
Direct Queues
$objectQueueType Direct
$objectQueueType DirectMainMsg or with Action to use this option to the main message queue or for an action queue respectively. With direct queue, messages are passed directly and immediately from the producer to the consumer.
Disk Queues
/etc/rsyslog.conf:
$objectQueueType Disk
$objectQueueType DiskMainMsg or with Action to use this option to the main message queue or for an action queue respectively. Disk queues are written in parts, with a default size 10 Mb. This default size can be modified with the following configuration directive:
$objectQueueMaxFileSize size
$objectQueueMaxFileSize size$objectQueueFilename name
$objectQueueFilename nameIn-memory Queues
$ActionQueueSaveOnShutdown setting to save the data before shutdown. There are two types of in-memory queues:
- FixedArray queue — the default mode for the main message queue, with a limit of 10,000 elements. This type of queue uses a fixed, pre-allocated array that holds pointers to queue elements. Due to these pointers, even if the queue is empty a certain amount of memory is consumed. However, FixedArray offers the best run time performance and is optimal when you expect a relatively low number of queued messages and high performance.
- LinkedList queue — here, all structures are dynamically allocated in a linked list, thus the memory is allocated only when needed. LinkedList queues handle occasional message bursts very well.
$objectQueueType LinkedList
$objectQueueType LinkedList$objectQueueType FixedArray
$objectQueueType FixedArrayMainMsg or with Action to use this option to the main message queue or for an action queue respectively.
Disk-Assisted In-memory Queues
$objectQueueFileName directive to define a file name for disk assistance. This queue then becomes disk-assisted, which means it couples an in-memory queue with a disk queue to work in tandem.
$objectQueueHighWatermark number
$objectQueueHighWatermark number$objectQueueLowWatermark number
$objectQueueLowWatermark numberMainMsg or with Action to use this option to the main message queue or for an action queue respectively. Replace number with a number of enqueued messages. When an in-memory queue reaches the number defined by the high watermark, it starts writing messages to disk and continues until the in-memory queue size drops to the number defined with the low watermark. Correctly set watermarks minimize unnecessary disk writes, but also leave memory space for message bursts since writing to disk files is rather lengthy. Therefore, the high watermark must be lower than the whole queue capacity set with $objectQueueSize. The difference between the high watermark and the overall queue size is a spare memory buffer reserved for message bursts. On the other hand, setting the high watermark too low will turn on disk assistance unnecessarily often.
Example 25.12. Reliable Forwarding of Log Messages to a Server
UDP protocol. To establish a fully reliable connection, for example when your logging server is outside of your private network, consider using the RELP protocol described in Section 25.7.4, “Using RELP”.
Procedure 25.2. Forwarding To a Single Server
- Use the following configuration in
/etc/rsyslog.confor create a file with the following content in the/etc/rsyslog.d/directory:$ActionQueueType LinkedList $ActionQueueFileName example_fwd $ActionResumeRetryCount -1 $ActionQueueSaveOnShutdown on *.* @@example.com:6514
$ActionQueueType LinkedList $ActionQueueFileName example_fwd $ActionResumeRetryCount -1 $ActionQueueSaveOnShutdown on *.* @@example.com:6514Copy to Clipboard Copied! Toggle word wrap Toggle overflow Where:$ActionQueueTypeenables a LinkedList in-memory queue,$ActionFileNamedefines a disk storage, in this case the backup files are created in the/var/lib/rsyslog/directory with the example_fwd prefix,- the
$ActionResumeRetryCount -1setting prevents rsyslog from dropping messages when retrying to connect if server is not responding, - enabled
$ActionQueueSaveOnShutdownsaves in-memory data if rsyslog shuts down, - the last line forwards all received messages to the logging server, port specification is optional.
With the above configuration, rsyslog keeps messages in memory if the remote server is not reachable. A file on disk is created only if rsyslog runs out of the configured memory queue space or needs to shut down, which benefits the system performance.
Procedure 25.3. Forwarding To Multiple Servers
- Each destination server requires a separate forwarding rule, action queue specification, and backup file on disk. For example, use the following configuration in
/etc/rsyslog.confor create a file with the following content in the/etc/rsyslog.d/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
25.5.2. Creating a New Directory for rsyslog Log Files
syslogd daemon and is managed by SELinux. Therefore all files to which rsyslog is required to write to, must have the appropriate SELinux file context.
Procedure 25.4. Creating a New Working Directory
- If required to use a different directory to store working files, create a directory as follows:
mkdir /rsyslog
~]# mkdir /rsyslogCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Install utilities to manage SELinux policy:
yum install policycoreutils-python
~]# yum install policycoreutils-pythonCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Set the SELinux directory context type to be the same as the
/var/lib/rsyslog/directory:semanage fcontext -a -t syslogd_var_lib_t /rsyslog
~]# semanage fcontext -a -t syslogd_var_lib_t /rsyslogCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Apply the SELinux context:
restorecon -R -v /rsyslog restorecon reset /rsyslog context unconfined_u:object_r:default_t:s0->unconfined_u:object_r:syslogd_var_lib_t:s0
~]# restorecon -R -v /rsyslog restorecon reset /rsyslog context unconfined_u:object_r:default_t:s0->unconfined_u:object_r:syslogd_var_lib_t:s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If required, check the SELinux context as follows:
ls -Zd /rsyslog drwxr-xr-x. root root system_u:object_r:syslogd_var_lib_t:s0 /rsyslog
~]# ls -Zd /rsyslog drwxr-xr-x. root root system_u:object_r:syslogd_var_lib_t:s0 /rsyslogCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Create subdirectories as required. For example:The subdirectories will be created with the same SELinux context as the parent directory.
mkdir /rsyslog/work
~]# mkdir /rsyslog/workCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the following line in
/etc/rsyslog.confimmediately before it is required to take effect:This setting will remain in effect until the next$WorkDirectory /rsyslog/work
$WorkDirectory /rsyslog/workCopy to Clipboard Copied! Toggle word wrap Toggle overflow WorkDirectorydirective is encountered while parsing the configuration files.
25.5.3. Managing Queues
Limiting Queue Size
$objectQueueHighWatermark number
$objectQueueHighWatermark numberMainMsg or with Action to use this option to the main message queue or for an action queue respectively. Replace number with a number of enqueued messages. You can set the queue size only as the number of messages, not as their actual memory size. The default queue size is 10,000 messages for the main message queue and ruleset queues, and 1000 for action queues.
$objectQueueMaxDiscSpace number
$objectQueueMaxDiscSpace numberMainMsg or with Action. When the size limit specified by number is hit, messages are discarded until sufficient amount of space is freed by dequeued messages.
Discarding Messages
$objectQueueDiscardMark number
$objectQueueDiscardMark numberMainMsg or with Action to use this option to the main message queue or for an action queue respectively. Here, number stands for a number of messages that have to be in the queue to start the discarding process. To define which messages to discard, use:
$objectQueueDiscardSeverity priority
$objectQueueDiscardSeverity prioritydebug (7), info (6), notice (5), warning (4), err (3), crit (2), alert (1), and emerg (0). With this setting, both newly incoming and already queued messages with lower than defined priority are erased from the queue immediately after the discard mark is reached.
Using Timeframes
$objectQueueDequeueTimeBegin hour
$objectQueueDequeueTimeBegin hour$objectQueueDequeueTimeEnd hour
$objectQueueDequeueTimeEnd hourConfiguring Worker Threads
$objectQueueWorkerThreadMinimumMessages number
$objectQueueWorkerThreadMinimumMessages number$objectQueueWorkerThreads number
$objectQueueWorkerThreads number$objectQueueWorkerTimeoutThreadShutdown time
$objectQueueWorkerTimeoutThreadShutdown time-1, no thread will be closed.
Batch Dequeuing
$objectQueueDequeueBatchSize number
$objectQueueDequeueBatchSize numberTerminating Queues
$objectQueueTimeoutShutdown time
$objectQueueTimeoutShutdown time$objectQueueTimeoutActionCompletion time
$objectQueueTimeoutActionCompletion time$objectQueueTimeoutSaveOnShutdown time
$objectQueueTimeoutSaveOnShutdown time25.5.4. Using the New Syntax for rsyslog queues
action() object that can be used both separately or inside a ruleset in /etc/rsyslog.conf. The format of an action queue is as follows:
action(type="action_type" queue.size="queue_size" queue.type="queue_type" queue.filename="file_name")
action(type="action_type" queue.size="queue_size" queue.type="queue_type" queue.filename="file_name")disk or select from one of the in-memory queues: direct, linkedlist or fixedarray. For file_name specify only a file name, not a path. Note that if creating a new directory to hold log files, the SELinux context must be set. See Section 25.5.2, “Creating a New Directory for rsyslog Log Files” for an example.
Example 25.13. Defining an Action Queue
action(type="omfile" queue.size="10000" queue.type="linkedlist" queue.filename="logfile")
action(type="omfile" queue.size="10000" queue.type="linkedlist" queue.filename="logfile")*.* action(type="omfile" file="/var/lib/rsyslog/log_file
)
*.* action(type="omfile" file="/var/lib/rsyslog/log_file
)*.* action(type="omfile"
queue.filename="log_file"
queue.type="linkedlist"
queue.size="10000"
)
*.* action(type="omfile"
queue.filename="log_file"
queue.type="linkedlist"
queue.size="10000"
)global(workDirectory="/directory")
global(workDirectory="/directory")Example 25.14. Forwarding To a Single Server Using the New Syntax
omfwd plug-in is used to provide forwarding over UDP or TCP. The default is UDP. As the plug-in is built in it does not have to be loaded.
/etc/rsyslog.conf or create a file with the following content in the /etc/rsyslog.d/ directory:
queue.type="linkedlist"enables a LinkedList in-memory queue,queue.filenamedefines a disk storage. The backup files are created with the example_fwd prefix, in the working directory specified by the preceding globalworkDirectorydirective,- the
action.resumeRetryCount -1setting prevents rsyslog from dropping messages when retrying to connect if server is not responding, - enabled
queue.saveOnShutdown="on"saves in-memory data if rsyslog shuts down, - the last line forwards all received messages to the logging server, port specification is optional.
25.6. Configuring rsyslog on a Logging Server
rsyslog service provides facilities both for running a logging server and for configuring individual systems to send their log files to the logging server. See Example 25.12, “Reliable Forwarding of Log Messages to a Server” for information on client rsyslog configuration.
rsyslog service must be installed on the system that you intend to use as a logging server and all systems that will be configured to send logs to it. Rsyslog is installed by default in Red Hat Enterprise Linux 6. If required, to ensure that it is, enter the following command as root:
yum install rsyslog
~]# yum install rsyslogUDP and 514, as listed in the /etc/services file. However, rsyslog defaults to using TCP on port 514. In the configuration file, /etc/rsyslog.conf, TCP is indicated by @@.
semanage port -l | grep syslog syslogd_port_t tcp 6514, 601 syslogd_port_t udp 514, 6514, 601
~]# semanage port -l | grep syslog
syslogd_port_t tcp 6514, 601
syslogd_port_t udp 514, 6514, 601semanage utility is provided as part of the policycoreutils-python package. If required, install the package as follows:
yum install policycoreutils-python
~]# yum install policycoreutils-pythonrsyslog, rsyslogd_t, is configured to permit sending and receiving to the remote shell (rsh) port with SELinux type rsh_port_t, which defaults to TCP on port 514. Therefore it is not necessary to use semanage to explicitly permit TCP on port 514. For example, to check what SELinux is set to permit on port 514, enter a command as follows:
semanage port -l | grep 514 output omitted rsh_port_t tcp 514 syslogd_port_t tcp 6514, 601 syslogd_port_t udp 514, 6514, 601
~]# semanage port -l | grep 514
output omitted
rsh_port_t tcp 514
syslogd_port_t tcp 6514, 601
syslogd_port_t udp 514, 6514, 601root user.
Procedure 25.5. Configure SELinux to Permit rsyslog Traffic on a Port
rsyslog traffic, follow this procedure on the logging server and the clients. For example, to send and receive TCP traffic on port 10514, proceed as follows:
semanage port -a -t syslogd_port_t -p tcp 10514
~]# semanage port -a -t syslogd_port_t -p tcp 10514Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Review the SELinux ports by entering the following command:
semanage port -l | grep syslog
~]# semanage port -l | grep syslogCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If the new port was already configured in
/etc/rsyslog.conf, restartrsyslognow for the change to take effect:service rsyslog restart
~]# service rsyslog restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Verify which ports
rsyslogis now listening to:netstat -tnlp | grep rsyslog tcp 0 0 0.0.0.0:10514 0.0.0.0:* LISTEN 2528/rsyslogd tcp 0 0 :::10514 :::* LISTEN 2528/rsyslogd
~]# netstat -tnlp | grep rsyslog tcp 0 0 0.0.0.0:10514 0.0.0.0:* LISTEN 2528/rsyslogd tcp 0 0 :::10514 :::* LISTEN 2528/rsyslogdCopy to Clipboard Copied! Toggle word wrap Toggle overflow
semanage-port(8) manual page for more information on the semanage port command.
Procedure 25.6. Configuring The iptables Firewall
iptables firewall to allow incoming rsyslog traffic. For example, to allow TCP traffic on port 10514, proceed as follows:
- Open the
/etc/sysconfig/iptablesfile in a text editor. - Add an
INPUTrule allowingTCPtraffic on port10514to the file. The new rule must appear before anyINPUTrules thatREJECTtraffic.-A INPUT -m state --state NEW -m tcp -p tcp --dport 10514 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 10514 -j ACCEPTCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the changes to the
/etc/sysconfig/iptablesfile. - Restart the
iptablesservice for the firewall changes to take effect.service iptables restart
~]# service iptables restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure 25.7. Configuring rsyslog to Receive and Sort Remote Log Messages
- Open the
/etc/rsyslog.conffile in a text editor and proceed as follows:- Add these lines below the modules section but above the
Provides UDP syslog receptionsection:# Define templates before the rules that use them ### Per-Host Templates for Remote Systems ### $template TmplAuthpriv, "/var/log/remote/auth/%HOSTNAME%/%PROGRAMNAME:::secpath-replace%.log" $template TmplMsg, "/var/log/remote/msg/%HOSTNAME%/%PROGRAMNAME:::secpath-replace%.log"
# Define templates before the rules that use them ### Per-Host Templates for Remote Systems ### $template TmplAuthpriv, "/var/log/remote/auth/%HOSTNAME%/%PROGRAMNAME:::secpath-replace%.log" $template TmplMsg, "/var/log/remote/msg/%HOSTNAME%/%PROGRAMNAME:::secpath-replace%.log"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Replace the default
Provides TCP syslog receptionsection with the following:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Save the changes to the/etc/rsyslog.conffile. - The
rsyslogservice must be running on both the logging server and the systems attempting to log to it.- Use the
servicecommand to start thersyslogservice.service rsyslog start
~]# service rsyslog startCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To ensure the
rsyslogservice starts automatically in future, enter the following command as root:chkconfig rsyslog on
~]# chkconfig rsyslog onCopy to Clipboard Copied! Toggle word wrap Toggle overflow
25.6.1. Using The New Template Syntax on a Logging Server
25.7. Using Rsyslog Modules
$ModLoad MODULE
$ModLoad MODULE$ModLoad is the global directive that loads the specified module and MODULE represents your desired module. For example, if you want to load the Text File Input Module (imfile) that enables rsyslog to convert any standard text files into syslog messages, specify the following line in the /etc/rsyslog.conf configuration file:
$ModLoad imfile
$ModLoad imfile
- Input Modules — Input modules gather messages from various sources. The name of an input module always starts with the
imprefix, such asimfile. - Output Modules — Output modules provide a facility to issue message to various targets such as sending across a network, storing in a database, or encrypting. The name of an output module always starts with the
omprefix, such asomsnmp,omrelp, and so on. - Parser Modules — These modules are useful in creating custom parsing rules or to parse malformed messages. With moderate knowledge of the C programming language, you can create your own message parser. The name of a parser module always starts with the
pmprefix, such aspmrfc5424,pmrfc3164, and so on. - Message Modification Modules — Message modification modules change content of syslog messages. Names of these modules start with the
mmprefix. Message Modification Modules such asmmanon,mmnormalize, ormmjsonparseare used for anonymization or normalization of messages. - String Generator Modules — String generator modules generate strings based on the message content and strongly cooperate with the template feature provided by rsyslog. For more information on templates, see Section 25.3.3, “Templates”. The name of a string generator module always starts with the
smprefix, such assmfileorsmtradfile. - Library Modules — Library modules provide functionality for other loadable modules. These modules are loaded automatically by rsyslog when needed and cannot be configured by the user.
Warning
25.7.1. Importing Text Files
imfile, enables rsyslog to convert any text file into a stream of syslog messages. You can use imfile to import log messages from applications that create their own text file logs. To load imfile, add the following into /etc/rsyslog.conf:
$ModLoad imfile $InputFilePollInterval int
$ModLoad imfile
$InputFilePollInterval intimfile once, even when importing multiple files. The $InputFilePollInterval global directive specifies how often rsyslog checks for changes in connected text files. The default interval is 10 seconds, to change it, replace int with a time interval specified in seconds.
/etc/rsyslog.conf:
- replace path_to_file with a path to the text file.
- replace tag: with a tag name for this message.
- replace state_file_name with a unique name for the state file. State files, which are stored in the rsyslog working directory, keep cursors for the monitored files, marking what partition has already been processed. If you delete them, whole files will be read in again. Make sure that you specify a name that does not already exist.
- add the $InputRunFileMonitor directive that enables the file monitoring. Without this setting, the text file will be ignored.
Example 25.15. Importing Text Files
imfile module to import the messages. Add the following into /etc/rsyslog.conf:
25.7.2. Exporting Messages to a Database
ommysql, ompgsql, omoracle, or ommongodb. As an alternative, use the generic omlibdbi output module that relies on the libdbi library. The omlibdbi module supports database systems Firebird/Interbase, MS SQL, Sybase, SQLite, Ingres, Oracle, mSQL, MySQL, and PostgreSQL.
Example 25.16. Exporting Rsyslog Messages to a Database
/etc/rsyslog.conf:
$ModLoad ommysql $ActionOmmysqlServerPort 1234 *.* :ommysql:database-server,database-name,database-userid,database-password
$ModLoad ommysql
$ActionOmmysqlServerPort 1234
*.* :ommysql:database-server,database-name,database-userid,database-password
25.7.3. Enabling Encrypted Transport
25.7.4. Using RELP
yum install rsyslog-relp
~]# yum install rsyslog-relp- To configure the client, configure:
- loading the required modules
- the TCP input port
- the transport settings
by adding the following configuration to the/etc/rsyslog.conffile:$ModLoad omrelp $ModLoad imuxsock $ModLoad imtcp $InputTCPServerRun "port" *.* :omrelp:"target_IP":"target_port"
$ModLoad omrelp $ModLoad imuxsock $ModLoad imtcp $InputTCPServerRun "port" *.* :omrelp:"target_IP":"target_port"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace port to start a listener at the required port.Replace target_IP and target_port with the IP address and port that identify the target server. - To configure the server:
- configure loading the modules
- configure the TCP input similarly to the client configuration
- configure the rules and choose an action to be performed
by adding the following configuration to the/etc/rsyslog.conffile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace target_port with the same value as on the clients.In the previous example, log_path specifies the path for storing messages.
25.8. Debugging Rsyslog
rsyslogd in debugging mode, use the following command:
rsyslogd -dn
rsyslogd -dnrsyslogd produces debugging information and prints it to the standard output. The -n stands for "no fork". You can modify debugging with environmental variables, for example, you can store the debug output in a log file. Before starting rsyslogd, type the following on the command line:
export RSYSLOG_DEBUGLOG="path" export RSYSLOG_DEBUG="Debug"
export RSYSLOG_DEBUGLOG="path"
export RSYSLOG_DEBUG="Debug"
rsyslogd(8) manual page.
/etc/rsyslog.conf file is valid use:
rsyslogd -N 1
rsyslogd -N 11 represents level of verbosity of the output message. This is a forward compatibility option because currently, only one level is provided. However, you must add this argument to run the validation.
25.9. Managing Log Files in a Graphical Environment
25.9.1. Viewing Log Files
Vi or Emacs. Some log files are readable by all users on the system; however, root privileges are required to read most log files.
Note
root:
yum install gnome-system-log
~]# yum install gnome-system-loggnome-system-log
~]$ gnome-system-logFigure 25.2. Log File Viewer
Figure 25.3. Log File Viewer - Filters
Figure 25.4. Log File Viewer - defining a filter
- Name — Specifies the name of the filter.
- Regular Expression — Specifies the regular expression that will be applied to the log file and will attempt to match any possible strings of text in it.
- Effect
- Highlight — If checked, the found results will be highlighted with the selected color. You may select whether to highlight the background or the foreground of the text.
- Hide — If checked, the found results will be hidden from the log file you are viewing.
Figure 25.5. Log File Viewer - enabling a filter
25.9.2. Adding a Log File
Figure 25.6. Log File Viewer - adding a log file
Note
.gz format.
25.9.3. Monitoring Log Files
Figure 25.7. Log File Viewer - new log alert
25.10. Additional Resources
rsyslog daemon and how to locate, view, and monitor log files, see the resources listed below.
Installed Documentation
rsyslogd(8) — The manual page for thersyslogddaemon documents its usage.rsyslog.conf(5) — The manual page namedrsyslog.confdocuments available configuration options.logrotate(8) — The manual page for the logrotate utility explains in greater detail how to configure and use it.
Online Documentation
- rsyslog version 5 documentation on the rsyslog home page — The default version of rsyslog in Red Hat Enterprise Linux 6 is version 5.
- rsyslog version 7 documentation on the rsyslog home page — Version 7 of rsyslog is available for Red Hat Enterprise Linux 6 in the rsyslog7 package.
- Description of queues on the rsyslog Home Page — General information on various types of message queues and their usage.
See Also
- Chapter 4, Gaining Privileges documents how to gain administrative privileges by using the
suandsudocommands.
Chapter 26. Upgrading MySQL
Chapter 27. Automating System Tasks
locate command is updated daily. A system administrator can use automated tasks to perform periodic backups, monitor the system, run custom scripts, and so on.
cron, anacron, at, and batch.
27.1. Cron and Anacron
27.1.1. Installing Cron and Anacron
rpm -q cronie cronie-anacron command. The command returns full names of the cronie and cronie-anacron packages if already installed or notifies you that the packages are not available.
yum command in the following form:
yum install package
yum install package yum install cronie cronie-anacron
~]# yum install cronie cronie-anacronroot) to run this command. For more information on how to install new packages in Red Hat Enterprise Linux, see Section 8.2.4, “Installing Packages”.
27.1.2. Running the Crond Service
crond service. This section provides information on how to start, stop, and restart the crond service, and shows how to enable it in a particular runlevel. For more information on the concept of runlevels and how to manage system services in Red Hat Enterprise Linux in general, see Chapter 12, Services and Daemons.
27.1.2.1. Starting and Stopping the Cron Service
service crond status.
crond service in the current session, type the following at a shell prompt as root:
service crond start
service crond start chkconfig crond on
chkconfig crond on 27.1.2.2. Stopping the Cron Service
crond service, type the following at a shell prompt as root
service crond stop
service crond stop chkconfig crond off
chkconfig crond off 27.1.2.3. Restarting the Cron Service
crond service, type the following at a shell prompt:
service crond restart
service crond restart 27.1.3. Configuring Anacron Jobs
/etc/anacrontab file, which can be only accessed by the root user. The file contains the following:
SHELL— shell environment used for running jobs (in the example, the Bash shell)PATH— paths to executable programsMAILTO— user name of the user who receives the output of the anacron jobs by emailIf theMAILTOvariable is not defined (MAILTO=), the email is not sent.
RANDOM_DELAY— maximum number of minutes that will be added to thedelay in minutesvariable which is specified for each jobThe minimum delay value is set, by default, to 6 minutes.IfRANDOM_DELAYis, for example, set to12, then between 6 and 12 minutes are added to thedelay in minutesfor each job in that particular anacrontab.RANDOM_DELAYcan also be set to a value below6, including0. When set to0, no random delay is added. This proves to be useful when, for example, more computers that share one network connection need to download the same data every day.START_HOURS_RANGE— interval, when scheduled jobs can be run, in hoursIn case the time interval is missed, for example due to a power failure, the scheduled jobs are not executed that day.
/etc/anacrontab file represent scheduled jobs and follow this format:
period in days delay in minutes job-identifier command
period in days delay in minutes job-identifier command
period in days— frequency of job execution in daysThe property value can be defined as an integer or a macro (@daily,@weekly,@monthly), where@dailydenotes the same value as integer 1,@weeklythe same as 7, and@monthlyspecifies that the job is run once a month regarless of the length of the month.delay in minutes— number of minutes anacron waits before executing the jobThe property value is defined as an integer. If the value is set to0, no delay applies.job-identifier— unique name referring to a particular job used in the log filescommand— command to be executedThe command can be either a command such asls /proc >> /tmp/procor a command which executes a custom script.
27.1.3.1. Examples of Anacron Jobs
/etc/anacrontab file:
anacrontab file are randomly delayed by 6-30 minutes and can be executed between 16:00 and 20:00.
/etc/cron.daily directory using the run-parts script (the run-parts scripts accepts a directory as a command-line argument and sequentially executes every program in the directory).
weeklyjob.bash script in the /etc directory once a week.
/proc to the /tmp/proc file (ls /proc >> /tmp/proc) once a month.
27.1.4. Configuring Cron Jobs
/etc/crontab, which can be only modified by the root user. The file contains the following:
anacrontab file: SHELL, PATH, and MAILTO. For more information about these variables, see Section 27.1.3, “Configuring Anacron Jobs”.
HOME variable. The HOME variable defines the directory, which will be used as the home directory when executing commands or scripts run by the job.
/etc/crontab file represent scheduled jobs and have the following format:
minute hour day month day of week username command
minute hour day month day of week username commandminute— any integer from 0 to 59hour— any integer from 0 to 23day— any integer from 1 to 31 (must be a valid day if a month is specified)month— any integer from 1 to 12 (or the short name of the month such as jan or feb)day of week— any integer from 0 to 7, where 0 or 7 represents Sunday (or the short name of the week such as sun or mon)
username— specifies the user under which the jobs are runcommand— the command to be executedThe command can be either a command such asls /proc /tmp/procor a command which executes a custom script.
1-4 means the integers 1, 2, 3, and 4.
3, 4, 6, 8 indicates exactly these four integers.
/integer. For example, minute value defined as 0-59/2 denotes every other minute in the minute field. Step values can also be used with an asterisk. For instance, if the month value is defined as */3, the task will run every third month.
crontab utility. The user-defined crontabs are stored in the /var/spool/cron/ directory and executed as if run by the users that created them.
crontab -e to edit the user's crontab with the editor specified in the VISUAL or EDITOR environment variable. The file uses the same format as /etc/crontab. When the changes to the crontab are saved, the crontab is stored according to user name and written to the file /var/spool/cron/username. To list the contents of your crontab file, use the crontab -l command.
Note
crontab utility.
/etc/cron.d/ directory contains files that have the same syntax as the /etc/crontab file. Only root is allowed to create and modify files in this directory.
Note
/etc/anacrontab file, the /etc/crontab file, the /etc/cron.d/ directory, and the /var/spool/cron/ directory every minute for changes and the detected changes are loaded into memory. It is therefore not necessary to restart the daemon after an anacrontab or a crontab file have been changed.
27.1.5. Controlling Access to Cron
/etc/cron.allow and /etc/cron.deny files. These access control files use the same format with one user name on each line. Mind that no whitespace characters are permitted in either file.
cron.allow file exists, only users listed in the file are allowed to use cron, and the cron.deny file is ignored.
cron.allow file does not exist, users listed in the cron.deny file are not allowed to use Cron.
crond) does not have to be restarted if the access control files are modified. The access control files are checked each time a user tries to add or delete a cron job.
/etc/security/access.conf file. For example, after adding the following line to the file, no other user but the root user can create crontabs:
-:ALL EXCEPT root :cron
-:ALL EXCEPT root :cronaccess.conf.5 (that is, man 5 access.conf).
27.1.6. Black and White Listing of Cron Jobs
/etc/cron.daily: if the user adds programs located in the directory to the job black list, the run-parts script will not execute these programs.
jobs.deny file in the directory that run-parts scripts will be executing from. For example, if you need to omit a particular program from /etc/cron.daily, create the /etc/cron.daily/jobs.deny file. In this file, specify the names of the programs to be omitted from execution (only programs located in the same directory can be enlisted). If a job runs a command which runs the programs from the cron.daily directory, such as run-parts /etc/cron.daily, the programs defined in the jobs.deny file will not be executed.
jobs.allow file.
jobs.deny and jobs.allow are the same as those of cron.deny and cron.allow described in section Section 27.1.5, “Controlling Access to Cron”.
27.2. At and Batch
27.2.1. Installing At and Batch
rpm -q at command. The command returns the full name of the at package if already installed or notifies you that the package is not available.
yum command in the following form:
yum install package
yum install package yum install at
~]# yum install atroot) to run this command. For more information on how to install new packages in Red Hat Enterprise Linux, see Section 8.2.4, “Installing Packages”.
27.2.2. Running the At Service
atd service. This section provides information on how to start, stop, and restart the atd service, and shows how to enable it in a particular runlevel. For more information on the concept of runlevels and how to manage system services in Red Hat Enterprise Linux in general, see Chapter 12, Services and Daemons.
27.2.2.1. Starting and Stopping the At Service
service atd status.
atd service in the current session, type the following at a shell prompt as root:
service atd start
service atd start chkconfig atd on
chkconfig atd on Note
27.2.2.2. Stopping the At Service
atd service, type the following at a shell prompt as root
service atd stop
service atd stop chkconfig atd off
chkconfig atd off 27.2.2.3. Restarting the At Service
atd service, type the following at a shell prompt:
service atd restart
service atd restart 27.2.3. Configuring an At Job
- On the command line, type the command
at TIME, whereTIMEis the time when the command is to be executed.The TIME argument can be defined in any of the following formats:HH:MMspecifies the exact hour and minute; For example,04:00specifies 4:00 a.m.midnightspecifies 12:00 a.m.noonspecifies 12:00 p.m.teatimespecifies 4:00 p.m.MONTHDAYYEARformat; For example,January 15 2012specifies the 15th day of January in the year 2012. The year value is optional.MMDDYY,MM/DD/YY, orMM.DD.YYformats; For example,011512for the 15th day of January in the year 2012.now + TIMEwhere TIME is defined as an integer and the value type: minutes, hours, days, or weeks. For example,now + 5 daysspecifies that the command will be executed at the same time five days from now.The time must be specified first, followed by the optional date. For more information about the time format, see the/usr/share/doc/at-<version>/timespectext file.
If the specified time has past, the job is executed at the time the next day. - In the displayed
at>prompt, define the job commands:- Type the command the job should execute and press Enter. Optionally, repeat the step to provide multiple commands.
- Enter a shell script at the prompt and press Enter after each line in the script.The job will use the shell set in the user's
SHELLenvironment, the user's login shell, or/bin/sh(whichever is found first).
- Once finished, press Ctrl+D on an empty line to exit the prompt.
atq command. See Section 27.2.5, “Viewing Pending Jobs” for more information.
at command. For more information, see Section 27.2.7, “Controlling Access to At and Batch” for details.
27.2.4. Configuring a Batch Job
- On the command line, type the command
batch. - In the displayed
at>prompt, define the job commands:- Type the command the job should execute and press Enter. Optionally, repeat the step to provide multiple commands.
- Enter a shell script at the prompt and press Enter after each line in the script.If a script is entered, the job uses the shell set in the user's
SHELLenvironment, the user's login shell, or/bin/sh(whichever is found first).
- Once finished, press Ctrl+D on an empty line to exit the prompt.
atq command. See Section 27.2.5, “Viewing Pending Jobs” for more information.
batch command. For more information, see Section 27.2.7, “Controlling Access to At and Batch” for details.
27.2.5. Viewing Pending Jobs
At and Batch jobs, run the atq command. The atq command displays a list of pending jobs, with each job on a separate line. Each line follows the job number, date, hour, job class, and user name format. Users can only view their own jobs. If the root user executes the atq command, all jobs for all users are displayed.
27.2.6. Additional Command-Line Options
at and batch include the following:
| Option | Description |
|---|---|
-f | Read the commands or shell script from a file instead of specifying them at the prompt. |
-m | Send email to the user when the job has been completed. |
-v | Display the time that the job is executed. |
27.2.7. Controlling Access to At and Batch
at and batch commands using the /etc/at.allow and /etc/at.deny files. These access control files use the same format defining one user name on each line. Mind that no whitespace are permitted in either file.
at.allow exists, only users listed in the file are allowed to use at or batch, and the at.deny file is ignored.
at.allow does not exist, users listed in at.deny are not allowed to use at or batch.
at daemon (atd) does not have to be restarted if the access control files are modified. The access control files are read each time a user tries to execute the at or batch commands.
at and batch commands, regardless of the content of the access control files.
27.3. Additional Resources
cronman page contains an overview of cron.crontabman pages in sections 1 and 5:- The manual page in section 1 contains an overview of the
crontabfile. - The man page in section 5 contains the format for the file and some example entries.
anacronmanual page contains an overview of anacron.anacrontabmanual page contains an overview of theanacrontabfile./usr/share/doc/at-<version>/timespeccontains detailed information about the time values that can be used in cron job definitions.atmanual page contains descriptions ofatandbatchand their command-line options.
Chapter 28. Automatic Bug Reporting Tool (ABRT)
abrtd daemon and a number of system services and utilities to process, analyze, and report detected problems. The daemon runs silently in the background most of the time, and springs into action when an application crashes or a kernel oops is detected. The daemon then collects the relevant problem data such as a core file if there is one, the crashing application's command-line parameters, and other data of forensic utility. For a brief overview of the most important ABRT components, see Table 28.1, “Basic ABRT components”.
Important
| Component | Package | Description |
|---|---|---|
abrtd | abrt | The ABRT daemon which runs under the root user as a background service. |
abrt-applet | abrt-gui | The program that receives messages from abrtd and informs you whenever a new problem occurs. |
abrt-gui | abrt-gui | The GUI application that shows collected problem data and allows you to further process it. |
abrt-cli | abrt-cli | The command-line interface that provides similar functionality to the GUI. |
abrt-ccpp | abrt-addon-ccpp | The ABRT service that provides the C/C++ problems analyzer. |
abrt-oops | abrt-addon-kerneloops | The ABRT service that provides the kernel oopses analyzer. |
abrt-vmcore | abrt-addon-vmcore[a] | The ABRT service that provides the kernel panic analyzer and reporter. |
[a]
The abrt-addon-vmcore package is provided by the Optional subscription channel. See Section 8.4.8, “Adding the Optional and Supplementary Repositories” for more information on Red Hat additional channels.
| ||
kdump crash dumping mechanism is enabled and configured on the system accordingly.
FTP/SCP, email it, or write it to a file.
analyzer, architecture, coredump, cmdline, executable, kernel, os_release, reason, time and uid.
backtrace, can be created during analysis depending on which analyzer method is used and its configuration settings. Each of these files holds specific information about the system and the problem itself. For example, the kernel file records the version of the crashed kernel.
Note
report [-v] --target target --ticket ID file
report [-v] --target target --ticket ID file report-cli -r dump_directory
report-cli -r dump_directory libreport. For more information on report-cli, see man report-cli.
28.1. Installing ABRT and Starting its Services
abrtd daemon requires the abrt user to exist for file system operations in the /var/spool/abrt directory. When the abrt package is installed, it automatically creates the abrt user whose UID and GID is 173, if such user does not already exist. Otherwise, the abrt user can be created manually. In that case, any UID and GID can be chosen, because abrtd does not require a specific UID and GID.
yum install abrt-desktop
~]# yum install abrt-desktopyum install abrt-cli
~]# yum install abrt-cliabrtd is running. The daemon is typically configured to start up at boot time. You can use the following command as root to verify its current status:
service abrtd status abrtd (pid 1535) is running...
~]# service abrtd status
abrtd (pid 1535) is running...service command returns the abrt is stopped message, the daemon is not running. It can be started for the current session by entering this command:
service abrtd start Starting abrt daemon: [ OK ]
~]# service abrtd start
Starting abrt daemon: [ OK ]abrt-ccpp service if you want ABRT to catch C/C++ crashes. To set ABRT to detect kernel oopses, use the same steps for the abrt-oops service. Note that this service cannot catch kernel oopses which cause the system to fail, to become unresponsive or to reboot immediately. To be able to detect such kernel oopses with ABRT, you need to install the abrt-vmcore service. If you require this functionality, see Section 28.4.5, “Configuring ABRT to Detect a Kernel Panic” for more information.
runlevels 3 and 5. You can disable or enable any ABRT service for the desired runlevels using the chkconfig utility. See Section 12.2.3, “Using the chkconfig Utility” for more information.
Warning
/proc/sys/kernel/core_pattern file which can contain a template used to name core dump files. The content of this file will be overwritten to:
|/usr/libexec/abrt-hook-ccpp %s %c %p %u %g %t e
|/usr/libexec/abrt-hook-ccpp %s %c %p %u %g %t eABRT notification applet is running:
ps -el | grep abrt-applet 0 S 500 2036 1824 0 80 0 - 61604 poll_s ? 00:00:00 abrt-applet
~]$ ps -el | grep abrt-applet
0 S 500 2036 1824 0 80 0 - 61604 poll_s ? 00:00:00 abrt-appletabrt-applet program:
abrt-applet & [1] 2261
~]$ abrt-applet &
[1] 2261Figure 28.1. Setting ABRT notification applet to run automatically.
28.2. Using the Graphical User Interface
abrt-gui &
~]$ abrt-gui &Figure 28.2. An example of running ABRT GUI.
Figure 28.3. A detailed problem data example
Figure 28.4. Selecting how to analyze the problem
Figure 28.5. ABRT analyzing the problem
Figure 28.6. Selecting a problem reporter
Figure 28.7. Warning - missing Red Hat Customer Support configuration
Figure 28.8. Red Hat Customer Support configuration window
Figure 28.9. Reviewing the problem backtrace
Figure 28.10. Confirming the data to report
Figure 28.11. Problem is being reported to the Red Hat Customer Support database
28.3. Using the Command-Line Interface
abrtd can be viewed, reported, and deleted using the command-line interface.
abrt-cli [--version] command [args]
abrt-cli [--version] command [args] list— lists problems and views the problem data.report— analyzes and reports problems.rm— removes unneeded problems.info— provides information about a particular problem.
abrt-cli command use:
abrt-cli command --help
abrt-cli command --help 28.3.1. Viewing Problems
abrt-cli list command:
Directory— Shows the problem data directory that contains all information about the problem.count— Shows how many times this particular problem occurred.executable— Indicates which binary or executable script crashed.package— Shows the name of the package that contains the program that caused the problem.time— Shows the date and time of the last occurrence of the problem.uid— Shows the ID of the user which ran the program that crashed.
abrt-cli list command. All options are mutually inclusive so you can combine them according to your need. The command output will be the most comprehensive if you combine all options, and you will receive the least details if you use no additional options.
| Option | Description |
|---|---|
With no additional option, the abrt-cli list command displays only basic information for problems that have not been reported yet. | |
-d, --detailed | Displays all stored information about problems listed, including a backtrace if it has already been generated. |
-f, --full | Displays basic information for all problems including the already-reported ones. |
-v, --verbose | Provides additional information on its actions. |
abrt-cli info directory
abrt-cli info directory abrt-cli info command. All options are mutually inclusive so you can combine them according to your need. The command output will be the most comprehensive if you combine all options, and you will receive the least details if you use no additional options.
| Option | Description |
|---|---|
With no additional option, the abrt-cli info command displays only basic information for the problem specified by the problem data directory argument. | |
-d, --detailed | Displays all stored information for the problem specified by the problem data directory argument, including a backtrace if it has already been generated. |
-v, --verbose | abrt-cli info provides additional information on its actions. |
28.3.2. Reporting Problems
abrt-cli report directory
abrt-cli report directory abrt-cli report /var/spool/abrt/ccpp-2011-09-13-10:18:14-2895 How you would like to analyze the problem? 1) Collect .xsession-errors 2) Local GNU Debugger Select analyzer: _
~]$ abrt-cli report /var/spool/abrt/ccpp-2011-09-13-10:18:14-2895
How you would like to analyze the problem?
1) Collect .xsession-errors
2) Local GNU Debugger
Select analyzer: _abrt-cli opens a text editor with the content of the report. You can see what is being reported, and you can fill in instructions on how to reproduce the crash and other comments. You should also check the backtrace, because the backtrace might be sent to a public server and viewed by anyone, depending on the problem reporter event settings.
Note
abrt-cli uses the editor defined in the ABRT_EDITOR environment variable. If the variable is not defined, it checks the VISUAL and EDITOR variables. If none of these variables is set, vi is used. You can set the preferred editor in your .bashrc configuration file. For example, if you prefer GNU Emacs, add the following line to the file:
export VISUAL=emacs
export VISUAL=emacsHow would you like to report the problem? 1) Logger 2) Red Hat Customer Support Select reporter(s): _
How would you like to report the problem?
1) Logger
2) Red Hat Customer Support
Select reporter(s): _abrt-cli report command.
| Option | Description |
|---|---|
With no additional option, the abrt-cli report command provides the usual output. | |
-v, --verbose | abrt-cli report provides additional information on its actions. |
28.3.3. Deleting Problems
abrt-cli rm directory
abrt-cli rm directory abrt-cli rm /var/spool/abrt/ccpp-2011-09-12-18:37:24-4413 rm '/var/spool/abrt/ccpp-2011-09-12-18:37:24-4413'
~]$ abrt-cli rm /var/spool/abrt/ccpp-2011-09-12-18:37:24-4413
rm '/var/spool/abrt/ccpp-2011-09-12-18:37:24-4413'Note
abrt-cli rm command.
| Option | Description |
|---|---|
With no additional option, the abrt-cli rm command removes the specified problem data directory with all its contents. | |
-v, --verbose | abrt-cli rm provides additional information on its actions. |
28.4. Configuring ABRT
- Event 1 — a problem data directory is created.
- Event 2 — problem data is analyzed.
- Event 3 — a problem is reported to Bugzilla.
/etc/libreport/— contains thereport_event.confmain configuration file. More information about this configuration file can be found in Section 28.4.1, “ABRT Events”./etc/libreport/events/— holds files specifying the default setting of predefined events./etc/libreport/events.d/— keeps configuration files defining events./etc/libreport/plugins/— contains configuration files of programs that take part in events./etc/abrt/— holds ABRT specific configuration files used to modify the behavior of ABRT's services and programs. More information about certain specific configuration files can be found in Section 28.4.4, “ABRT Specific Configuration”./etc/abrt/plugins/— keeps configuration files used to override the default setting of ABRT's services and programs. For more information on some specific configuration files see Section 28.4.4, “ABRT Specific Configuration”.
28.4.1. ABRT Events
/etc/libreport/events.d/ directory. These configuration files are used by the main configuration file, /etc/libreport/report_event.conf.
/etc/libreport/report_event.conf file consists of include directives and rules. Rules are typically stored in other configuration files in the /etc/libreport/events.d/ directory. In the standard installation, the /etc/libreport/report_event.conf file contains only one include directive:
include events.d/*.conf
include events.d/*.confspace character or the tab character are considered a part of this rule. Each rule consists of two parts, a condition part and a program part. The condition part contains conditions in one of the following forms:
- VAR=VAL,
- VAR!=VAL, or
- VAL~=REGEX
- VAR is either the
EVENTkey word or a name of a problem data directory element (such asexecutable,package,hostname, etc.), - VAL is either a name of an event or a problem data element, and
- REGEX is a regular expression.
EVENT=post-create date > /tmp/dt
echo $HOSTNAME `uname -r`
EVENT=post-create date > /tmp/dt
echo $HOSTNAME `uname -r`/tmp/dt file with the current date and time, and print the host name of the machine and its kernel version on the standard output.
~/.xsession-errors file to the problem report for any problem for which the abrt-ccpp services has been used to process that problem, and the crashed application has loaded any X11 libraries at the time of crash:
-
post-create - This event is run by
abrtdon newly created problem data directories. When thepost-createevent is run,abrtdchecks whether the UUID identifier of the new problem data matches the UUID of any already existing problem directories. If such a problem directory exists, the new problem data is deleted. -
analyze_name_suffix - …where name_suffix is the adjustable part of the event name. This event is used to process collected data. For example, the
analyze_LocalGDBruns the GNU Debugger (GDB) utility on a core dump of an application and produces a backtrace of a program. You can view the list of analyze events and choose from it using abrt-gui. -
collect_name_suffix - …where name_suffix is the adjustable part of the event name. This event is used to collect additional information on a problem. You can view the list of collect events and choose from it using abrt-gui.
-
report_name_suffix - …where name_suffix is the adjustable part of the event name. This event is used to report a problem. You can view the list of report events and choose from it using abrt-gui.
/etc/libreport/events/event_name.xml files. These files are used by abrt-gui and abrt-cli to make the user interface more friendly. Do not edit these files unless you want to modify the standard installation.
28.4.2. Standard ABRT Installation Supported Events
analyze_xsession_errors event is shown as Collect .xsession-errors in ABRT GUI. The following is a list of default analyzing, collecting and reporting events provided by the standard installation of ABRT:
- analyze_VMcore — Analyze VM core
- Runs GDB (the GNU debugger) on problem data of an application and generates a
backtraceof the kernel. It is defined in the/etc/libreport/events.d/vmcore_event.confconfiguration file. - analyze_LocalGDB — Local GNU Debugger
- Runs GDB (the GNU debugger) on problem data of an application and generates a
backtraceof a program. It is defined in the/etc/libreport/events.d/ccpp_event.confconfiguration file. - analyze_xsession_errors — Collect .xsession-errors
- Saves relevant lines from the
~/.xsession-errorsfile to the problem report. It is defined in the/etc/libreport/events.d/ccpp_event.confconfiguration file. - report_Logger — Logger
- Creates a problem report and saves it to a specified local file. It is defined in the
/etc/libreport/events.d/print_event.confconfiguration file. - report_RHTSupport — Red Hat Customer Support
- Reports problems to the Red Hat Technical Support system. This possibility is intended for users of Red Hat Enterprise Linux. It is defined in the
/etc/libreport/events.d/rhtsupport_event.confconfiguration file. - report_Mailx — Mailx
- Sends a problem report via the Mailx utility to a specified email address. It is defined in the
/etc/libreport/events.d/mailx_event.confconfiguration file. - report_Kerneloops — Kerneloops.org
- Sends a kernel problem to the oops tracker. It is defined in the
/etc/libreport/events.d/koops_event.confconfiguration file. - report_Uploader — Report uploader
- Uploads a tarball (.tar.gz) archive with problem data to the chosen destination using the
FTPor theSCPprotocol. It is defined in the/etc/libreport/events.d/uploader_event.confconfiguration file.
28.4.3. Event Configuration in ABRT GUI
report_Logger event accepts an output file name as a parameter). Using the respective /etc/libreport/events/event_name.xml file, ABRT GUI determines which parameters can be specified for a selected event and allows a user to set the values for these parameters. These values are saved by ABRT GUI and reused on subsequent invocations of these events.
Note
/etc/libreport/ directory hierarchy are world readable and are meant to be used as global settings. Thus, it is not advisable to store user names, passwords or any other sensitive data in them. The per-user settings (set in the GUI application and readable by the owner of $HOME only) are stored in the Gnome keyring or can be stored in a text file in $HOME/.abrt/*.conf for use in abrt-cli.
Figure 28.12. The Event Configuration Window
- Logger
- In the Logger event configuration window, you can configure the following parameter:
- Log file — Specifies a file into which the crash reports are saved (by default, set to
/var/log/abrt.log).
When the Append option is checked, the Logger event will append new crash reports to the log file specified in the Logger file option. When unchecked, the new crash report always replaces the previous one. - Red Hat Customer Support
- In the Red Hat Customer Support event configuration window, you can configure the following parameters:
- RH Portal URL — Specifies the Red Hat Customer Support URL where crash dumps are sent (by default, set to https://api.access.redhat.com/rs).
- Username — User login which is used to log into Red Hat Customer Support and create a Red Hat Customer Support database entry for a reported crash. Use your Red Hat Login acquired by creating an account on https://www.redhat.com/en, the Red Hat Customer Portal (https://access.redhat.com/home) or the Red Hat Network (https://rhn.redhat.com/).
- Password — Password used to log into Red Hat Customer Support (that is, password associated with your Red Hat Login)
When the SSL verify option is checked, theSSLprotocol is used when sending the data over the network. - MailX
- In the MailX event configuration window, you can configure the following parameters:
- Subject — A string that appears in the
Subjectfield of a problem report email sent by Mailx (by default, set to"[abrt] detected a crash"). - Sender — A string that appears in the
Fromfield of a problem report email. - Recipient — Email address of the recipient of a problem report email.
When the Send Binary Data option is checked, the problem report email will also contain all binary files associated with the problem in an attachment. The core dump file is also sent as an attachment. - Kerneloops.org
- In the Kerneloops.org event configuration window, you can configure the following parameter:
- Kerneloops URL — Specifies the URL where Kernel problems are reported to (by default, set to http://submit.kerneloops.org/submitoops.php)
- Report Uploader
- In the Report Uploader event configuration widow, you can configure the following parameter:
- URL — Specifies the URL where a tarball containing compressed problem data is uploaded using the
FTPorSCPprotocol (by default, set toftp://localhost:/tmp/upload).
28.4.4. ABRT Specific Configuration
/etc/abrt/abrt.conf— allows you to modify the behavior of theabrtdservice./etc/abrt/abrt-action-save-package-data.conf— allows you to modify the behavior of the abrt-action-save-package-data program./etc/abrt/plugins/CCpp.conf— allows you to modify the behavior of ABRT's core catching hook.
/etc/abrt/abrt.conf file:
- WatchCrashdumpArchiveDir = /var/spool/abrt-upload
- This directive is commented out by default. Enable it if you want
abrtdto auto-unpack crashdump tarball archives (.tar.gz) which are located in the specified directory. In the example above, it is the/var/spool/abrt-upload/directory. Whichever directory you specify in this directive, you must ensure that it exists and it is writable forabrtd. The ABRT daemon will not create it automatically. If you change the default value of this option, be aware that in order to ensure proper functionality of ABRT, this directory must not be the same as the directory specified for theDumpLocationoption.Warning
Changing the location for crashdump archives will cause SELinux denials unless you reflect the change in respective SELinux rules first. See theabrt_selinux(8)manual page for more information on running ABRT in SELinux.Remember that if you enable this option when using SELinux, you need to execute the following command in order to set the appropriate Boolean allowing ABRT to write into the public_content_rw_t domain:setsebool -P abrt_anon_write 1
setsebool -P abrt_anon_write 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow - MaxCrashReportsSize = size_in_megabytes
- This option sets the amount of storage space, in megabytes, used by ABRT to store all problem information from all users. The default setting is
1000MB. Once the quota specified here has been met, ABRT will continue catching problems, and in order to make room for the new crash dumps, it will delete the oldest and largest ones. - DumpLocation = /var/spool/abrt
- This directive is commented out by default. It specifies the location where problem data directories are created and in which problem core dumps and all other problem data are stored. The default location is set to the
/var/spool/abrtdirectory. Whichever directory you specify in this directive, you must ensure that it exists and it is writable forabrtd. If you change the default value of this option, be aware that in order to ensure proper functionality of ABRT, this directory must not be the same as the directory specified for theWatchCrashdumpArchiveDiroption.Warning
Changing the dump location will cause SELinux denials unless you reflect the change in respective SELinux rules first. See theabrt_selinux(8)manual page for more information on running ABRT in SELinux.Remember that if you enable this option when using SELinux, you need to execute the following command in order to set the appropriate Boolean allowing ABRT to write into the public_content_rw_t domain:setsebool -P abrt_anon_write 1
setsebool -P abrt_anon_write 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
/etc/abrt/abrt-action-save-package-data.conf file:
- OpenGPGCheck = yes/no
- Setting the
OpenGPGCheckdirective toyes(the default setting) tells ABRT to only analyze and handle crashes in applications provided by packages which are signed by the GPG keys whose locations are listed in the/etc/abrt/gpg_keysfile. SettingOpenGPGChecktonotells ABRT to catch crashes in all programs. - BlackList = nspluginwrapper, valgrind, strace, [more_packages ]
- Crashes in packages and binaries listed after the
BlackListdirective will not be handled by ABRT. If you want ABRT to ignore other packages and binaries, list them here separated by commas. - ProcessUnpackaged = yes/no
- This directive tells ABRT whether to process crashes in executables that do not belong to any package. The default setting is no.
- BlackListedPaths =
/usr/share/doc/*,*/example* - Crashes in executables in these paths will be ignored by ABRT.
/etc/abrt/plugins/CCpp.conf file:
- MakeCompatCore = yes/no
- This directive specifies whether ABRT's core catching hook should create a core file, as it could be done if ABRT would not be installed. The core file is typically created in the current directory of the crashed program but only if the
ulimit -csetting allows it. The directive is set to yes by default. - SaveBinaryImage = yes/no
- This directive specifies whether ABRT's core catching hook should save a binary image to a core dump. It is useful when debugging crashes which occurred in binaries that were deleted. The default setting is no.
28.4.5. Configuring ABRT to Detect a Kernel Panic
abrt-vmcore service, which is provided by the abrt-addon-vmcore package. The service starts automatically on system boot and searches for a core dump file in the /var/crash/ directory. If a core dump file is found, abrt-vmcore creates the problem data directory in the /var/spool/abrt/ directory and moves the core dump file to the newly created problem data directory. After the /var/crash/ directory is searched through, the service is stopped until the next system boot.
- Ensure that the
kdumpservice is enabled on the system. Especially, the amount of memory that is reserved for the kdump kernel has to be set correctly. You can set it by using the system-config-kdump graphical tool, or by specifying thecrashkernelparameter in the list of kernel options in the/etc/grub.confconfiguration file. See Chapter 32, The kdump Crash Recovery Service for details on how to enable and configurekdump. - Install the abrt-addon-vmcore package using the Yum package installer:
yum install abrt-addon-vmcore
~]# yum install abrt-addon-vmcoreCopy to Clipboard Copied! Toggle word wrap Toggle overflow This installs theabrt-vmcoreservice with respective support and configuration files. Please note that the abrt-addon-vmcore package is provided by the Optional subscription channel. See Section 8.4.8, “Adding the Optional and Supplementary Repositories” for more information on Red Hat additional channels. - Reboot the system for the changes to take effect.
/var/spool/abrt/ directory and can be further processed by ABRT just as any other detected kernel oops.
28.4.6. Automatic Downloads and Installation of Debuginfo Packages
- The
/etc/libreport/events.d/ccpp_event.conffile contains the following analyzer event, which is present uncommented in default configuration:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The
/etc/libreport/events.d/ccpp_event.conffile contains the following line, which allows ABRT to run binary to install debuginfo packages for the problems being analyzed. This line is, in order to avoid installations of unnecessary content, commented out by default so you have to remove the leading#character to enable it:/usr/libexec/abrt-action-install-debuginfo-to-abrt-cache --size_mb=4096 &&
/usr/libexec/abrt-action-install-debuginfo-to-abrt-cache --size_mb=4096 &&Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- The gdb package, which allows you to generate a backtrace during a problem analysis, is installed on your system. If needed, see Section 8.2.4, “Installing Packages” for more information on how to install packages with the Yum package manager.
Important
root to be able to install debuginfo packages.
28.4.7. Configuring Automatic Reporting for Specific Types of Crashes
EVENT=report_Bugzilla condition with the EVENT=post-create condition in the /etc/libreport/events.d/python_event.conf file. The new rule will look like the follows:
EVENT=post-create analyzer=Python
test -f component || abrt-action-save-package-data
reporter-bugzilla -c /etc/abrt/plugins/bugzilla.conf
EVENT=post-create analyzer=Python
test -f component || abrt-action-save-package-data
reporter-bugzilla -c /etc/abrt/plugins/bugzilla.confWarning
post-create event is run by abrtd, which usually runs with root privileges.
28.4.8. Uploading and Reporting Using a Proxy Server
http_proxy and the ftp_proxy environment variables. When you use environment variables as a part of a reporting event, they inherit their values from the process which performs reporting, usually abrt-gui or abrt-cli. Therefore, you can specify HTTP or FTP proxy servers by using these variables in your working environment.
post-create event, they will run as children of the abrtd process. You should either adjust the environment of abrtd or modify the rules to set these variables. For example:
EVENT=post-create analyzer=Python
test -f component || abrt-action-save-package-data
export http_proxy=http://proxy.server:8888/
reporter-bugzilla -c /etc/abrt/plugins/bugzilla.conf
EVENT=post-create analyzer=Python
test -f component || abrt-action-save-package-data
export http_proxy=http://proxy.server:8888/
reporter-bugzilla -c /etc/abrt/plugins/bugzilla.conf28.4.9. Configuring Automatic Reporting
- Once enabled, μReports are sent automatically, without user interaction. In contrast, the normal reports are not sent until manually triggered by the user.
- μReports are anonymous and do not contain sensitive information. This eliminates the risk that unwanted data will be submitted automatically.
- A μReport represents the detected problem as a JSON object. Therefore, it is machine-readable and can be created and processed automatically.
- μReports are smaller than full bug reports.
- μReports do not require downloading large amounts of debugging information.
- a call stack trace of a program without any variables, or, in case of multi-threaded C, C++, and Java programs, multiple stack traces
- which operating system is used
- versions of the RPM packages involved in the crash
- whether the program ran under the
rootuser - for kernel oops, possibly information about host hardware
Warning
Do not enable μReports if you do not want to share information about your hardware with Red Hat.
- ABRT submits a μReport with basic information about the problem to Red Hat's ABRT server.
- The server determines whether the problem is already in the bug database.
- If it is, the server returns a short description of the problem along with a URL of the reported case.If not, the server invites the user to submit a full problem report.
root:
abrt-auto-reporting enabled
~]# abrt-auto-reporting enabled/etc/abrt/abrt.conf file:
AutoreportingEnabled = yes
AutoreportingEnabled = yes$USER/.config/abrt/ directory. It overrides the system-wide configuration.
service abrtd restart
~]# service abrtd restartAutoreportingEvent directive in the /etc/abrt/abrt.conf configuration file. See Section 28.4.2, “Standard ABRT Installation Supported Events” for an overview of the standard events.
/etc/machine-id file), and RHN account number. The advantage of authenticated μReports is that they go directly to the Red Hat Customer Portal, and not only to Red Hat's private crash-report server, as the regular μReports do. This enables Red Hat to provide customers with instant solutions to crashes.
root:
abrt-auto-reporting enabled -u RHN_username
~]# abrt-auto-reporting enabled -u RHN_username/etc/libreport/plugins/rhtsupport.conf file.
28.5. Configuring Centralized Crash Collection
yum install libreport-plugin-reportuploader). See the following sections on how to configure systems to use ABRT's centralized crash collection.
28.5.1. Configuration Steps Required on a Dedicated System
- Create a directory to which you want the crash reports to be uploaded to. Usually,
/var/spool/abrt-upload/is used (the rest of the document assumes you are using this directory). Make sure this directory is writable by the abrt user.Note
When the abrt-desktop package is installed, it creates a new system user and a group, both namedabrt. This user is used by theabrtddaemon, for example, as the owner:group of/var/spool/abrt/*directories. - In the
/etc/abrt/abrt.confconfiguration file, set theWatchCrashdumpArchiveDirdirective to the following:WatchCrashdumpArchiveDir = /var/spool/abrt-upload/
WatchCrashdumpArchiveDir = /var/spool/abrt-upload/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Choose your preferred upload mechanism; for example,
FTPorSCP. For more information on how to configureFTP, see Section 21.2, “FTP”. For more information on how to configureSCP, see Section 14.4.2, “Using thescpUtility”.It is advisable to check whether your upload method works. For example, if you useFTP, upload a file using an interactiveFTPclient:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check whethertestfileappeared in the correct directory on the server system. - The
MaxCrashReportsSizedirective (in the/etc/abrt/abrt.confconfiguration file) needs to be set to a larger value if the expected volume of crash data is larger than the default1000MB. - Consider whether you would like to generate a backtrace of C/C++ crashes.You can disable backtrace generation on the server if you do not want to generate backtraces at all, or if you decide to create them locally on the machine where a problem occurred. In the standard ABRT installation, a backtrace of a C/C++ crash is generated using the following rule in the
/etc/libreport/events.d/ccpp_events.confconfiguration file:EVENT=analyze_LocalGDB analyzer=CCpp abrt-action-analyze-core.py --core=coredump -o build_ids && abrt-action-install-debuginfo-to-abrt-cache --size_mb=4096 && abrt-action-generate-backtrace && abrt-action-analyze-backtraceEVENT=analyze_LocalGDB analyzer=CCpp abrt-action-analyze-core.py --core=coredump -o build_ids && abrt-action-install-debuginfo-to-abrt-cache --size_mb=4096 && abrt-action-generate-backtrace && abrt-action-analyze-backtraceCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can ensure that this rule is not applied for uploaded problem data by adding theremote!=1condition to the rule. - Decide whether you want to collect package information (the
packageand thecomponentelements) in the problem data. See Section 28.5.3, “Saving Package Information” to find out whether you need to collect package information in your centralized crash collection configuration and how to configure it properly.
28.5.2. Configuration Steps Required on a Client System
- If you do not want to generate a backtrace, or if you decided to generate it on a server system, you need to delete or comment out the corresponding rules in the
/etc/libreport/events.d/ccpp_events.conffile. See Section 28.5.1, “Configuration Steps Required on a Dedicated System” for an example of such a example. - If you decided to not collect package information on client machines, delete, comment out or modify the rule which runs abrt-action-save-package-data in the
/etc/libreport/events.d/abrt_event.conffile. See Section 28.5.3, “Saving Package Information” to find out whether you need to collect package information in your centralized crash collection configuration and how to configure it properly. - Add a rule for uploading problem reports to the server system in the corresponding configuration file. For example, if you want to upload all problems automatically as soon as they are detected, you can use the following rule in the
/etc/libreport/events.d/abrt_event.confconfiguration file:EVENT=post-create reporter-upload -u scp://user:password@server.name/directoryEVENT=post-create reporter-upload -u scp://user:password@server.name/directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can use a similar rule that runs the reporter-upload program as thereport_SFXevent if you want to store problem data locally on clients and upload it later using ABRT GUI/CLI. The following is an example of such an event:EVENT=report_UploadToMyServer reporter-upload -u scp://user:password@server.name/directoryEVENT=report_UploadToMyServer reporter-upload -u scp://user:password@server.name/directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
28.5.3. Saving Package Information
post-create event runs the abrt-action-save-package-data tool (among other steps) in order to provide this information in the standard ABRT installation.
- Internal analysis of problems
- After collecting problem data, you do not need to collect package information if you plan to analyze problems in-house, without reporting them to any external bug databases. You might be also interested in collecting crashes that occur in programs written by your organization or third-party applications installed on your system. If such a program is a part of an RPM package, then on client systems and a dedicated crash collecting system, you can only add the respective GPG key to the
/etc/abrt/gpg_keysfile or set the following line in the/etc/abrt/abrt-action-save-package-data.conffile:OpenGPGCheck = no
OpenGPGCheck = noCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the program does not belong to any RPM package, take the following steps on both, client systems and a dedicated crash collecting system:- Remove the following rule from the
/etc/libreport/events.d/abrt_event.conffile:EVENT=post-create component= abrt-action-save-package-dataEVENT=post-create component= abrt-action-save-package-dataCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Prevent deletion of problem data directories which do not correspond to any installed package by setting the following directive in the
/etc/abrt/abrt-action-save-package-data.conffile:ProcessUnpackaged = yes
ProcessUnpackaged = yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Reporting to external bug database
- Alternatively, you may want to report crashes to RHTSupport or Bugzilla. In this case, you need to collect package information. Generally, client machines and dedicated crash collecting systems have non-identical sets of installed packages. Therefore, it may happen that problem data uploaded from a client does not correspond to any package installed on the dedicated crash collecting system. In the standard ABRT configuration, this will lead to deletion of problem data (ABRT will consider it to be a crash in an unpackaged executable). To prevent this from happening, it is necessary to modify ABRT's configuration on the dedicated system in the following way:
- Prevent inadvertent collection of package information for problem data uploaded from client machines, by adding the
remote!=1condition in the/etc/libreport/events.d/abrt_event.conffile:EVENT=post-create remote!=1 component= abrt-action-save-package-dataEVENT=post-create remote!=1 component= abrt-action-save-package-dataCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Prevent deletion of problem data directories which do not correspond to any installed package by setting the following directive in
/etc/abrt/abrt-action-save-package-data.conf:ProcessUnpackaged = yes
ProcessUnpackaged = yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Note
Note that in this case, no such modifications are necessary on client systems: they continue to collect package information, and continue to ignore crashes in unpackaged executables.
28.5.4. Testing ABRT's Crash Detection
kill -s SEGV PID command to terminate a process on a client system. For example, start a sleep process and terminate it with the kill command in the following way:
sleep 100 & [1] 2823 kill -s SIGSEGV 2823
~]$ sleep 100 &
[1] 2823
~]$ kill -s SIGSEGV 2823kill command. Check that the crash was detected by ABRT on the client system (this can be checked by examining the appropriate syslog file, by running the abrt-cli list --full command, or by examining the crash dump created in the /var/spool/abrt directory), copied to the server system, unpacked on the server system and can be seen and acted upon using abrt-cli or abrt-gui on the server system.
Chapter 29. OProfile
- Use of shared libraries — Samples for code in shared libraries are not attributed to the particular application unless the
--separate=libraryoption is used. - Performance monitoring samples are inexact — When a performance monitoring register triggers a sample, the interrupt handling is not precise like a divide by zero exception. Due to the out-of-order execution of instructions by the processor, the sample may be recorded on a nearby instruction.
opreportdoes not associate samples for inline functions properly —opreportuses a simple address range mechanism to determine which function an address is in. Inline function samples are not attributed to the inline function but rather to the function the inline function was inserted into.- OProfile accumulates data from multiple runs — OProfile is a system-wide profiler and expects processes to start up and shut down multiple times. Thus, samples from multiple runs accumulate. Use the command
opcontrol --resetto clear out the samples from previous runs. - Hardware performance counters do not work on guest virtual machines — Because the hardware performance counters are not available on virtual systems, you need to use the
timermode. Run the commandopcontrol --deinit, and then executemodprobe oprofile timer=1to enable thetimermode. - Non-CPU-limited performance problems — OProfile is oriented to finding problems with CPU-limited processes. OProfile does not identify processes that are asleep because they are waiting on locks or for some other event to occur (for example an I/O device to finish an operation).
29.1. Overview of Tools
| Command | Description |
|---|---|
ophelp |
Displays available events for the system's processor along with a brief description of each.
|
opimport |
Converts sample database files from a foreign binary format to the native format for the system. Only use this option when analyzing a sample database from a different architecture.
|
opannotate | Creates annotated source for an executable if the application was compiled with debugging symbols. See Section 29.5.4, “Using opannotate” for details. |
opcontrol |
Configures what data is collected. See Section 29.2, “Configuring OProfile” for details.
|
opreport |
Retrieves profile data. See Section 29.5.1, “Using
opreport” for details.
|
oprofiled |
Runs as a daemon to periodically write sample data to disk.
|
29.2. Configuring OProfile
opcontrol utility to configure OProfile. As the opcontrol commands are executed, the setup options are saved to the /root/.oprofile/daemonrc file.
29.2.1. Specifying the Kernel
opcontrol --setup --vmlinux=/usr/lib/debug/lib/modules/`uname -r`/vmlinux
~]# opcontrol --setup --vmlinux=/usr/lib/debug/lib/modules/`uname -r`/vmlinuxImportant
opcontrol --setup --no-vmlinux
~]# opcontrol --setup --no-vmlinuxoprofile kernel module, if it is not already loaded, and creates the /dev/oprofile/ directory, if it does not already exist. See Section 29.6, “Understanding /dev/oprofile/” for details about this directory.
29.2.2. Setting Events to Monitor
| Processor | cpu_type | Number of Counters |
|---|---|---|
| AMD64 | x86-64/hammer | 4 |
| AMD Athlon | i386/athlon | 4 |
| AMD Family 10h | x86-64/family10 | 4 |
| AMD Family 11h | x86-64/family11 | 4 |
| AMD Family 12h | x86-64/family12 | 4 |
| AMD Family 14h | x86-64/family14 | 4 |
| AMD Family 15h | x86-64/family15 | 6 |
| IBM eServer System i and IBM eServer System p | timer | 1 |
| IBM POWER4 | ppc64/power4 | 8 |
| IBM POWER5 | ppc64/power5 | 6 |
| IBM PowerPC 970 | ppc64/970 | 8 |
| IBM S/390 and IBM System z | timer | 1 |
| Intel Core i7 | i386/core_i7 | 4 |
| Intel Nehalem microarchitecture | i386/nehalem | 4 |
| Intel Pentium 4 (non-hyper-threaded) | i386/p4 | 8 |
| Intel Pentium 4 (hyper-threaded) | i386/p4-ht | 4 |
| Intel Westmere microarchitecture | i386/westmere | 4 |
| TIMER_INT | timer | 1 |
timer is used as the processor type if the processor does not have supported performance monitoring hardware.
timer is used, events cannot be set for any processor because the hardware does not have support for hardware performance counters. Instead, the timer interrupt is used for profiling.
timer is not used as the processor type, the events monitored can be changed, and counter 0 for the processor is set to a time-based event by default. If more than one counter exists on the processor, the counters other than counter 0 are not set to an event by default. The default events monitored are shown in Table 29.3, “Default Events”.
| Processor | Default Event for Counter | Description |
|---|---|---|
| AMD Athlon and AMD64 | CPU_CLK_UNHALTED | The processor's clock is not halted |
| AMD Family 10h, AMD Family 11h, AMD Family 12h | CPU_CLK_UNHALTED | The processor's clock is not halted |
| AMD Family 14h, AMD Family 15h | CPU_CLK_UNHALTED | The processor's clock is not halted |
| IBM POWER4 | CYCLES | Processor Cycles |
| IBM POWER5 | CYCLES | Processor Cycles |
| IBM PowerPC 970 | CYCLES | Processor Cycles |
| Intel Core i7 | CPU_CLK_UNHALTED | The processor's clock is not halted |
| Intel Nehalem microarchitecture | CPU_CLK_UNHALTED | The processor's clock is not halted |
| Intel Pentium 4 (hyper-threaded and non-hyper-threaded) | GLOBAL_POWER_EVENTS | The time during which the processor is not stopped |
| Intel Westmere microarchitecture | CPU_CLK_UNHALTED | The processor's clock is not halted |
| TIMER_INT | (none) | Sample for each timer interrupt |
ls -d /dev/oprofile/[0-9]*
~]# ls -d /dev/oprofile/[0-9]*ophelp
~]# ophelpNote
ophelp fails with the following error message:
Unable to open cpu_type file for reading Make sure you have done opcontrol --init cpu_type 'unset' is not valid you should upgrade oprofile or force the use of timer mode
Unable to open cpu_type file for reading
Make sure you have done opcontrol --init
cpu_type 'unset' is not valid
you should upgrade oprofile or force the use of timer modeopcontrol:
opcontrol --event=event-name:sample-rate
~]# opcontrol --event=event-name:sample-rateophelp, and replace sample-rate with the number of events between samples.
29.2.2.1. Sampling Rate
cpu_type is not timer, each event can have a sampling rate set for it. The sampling rate is the number of events between each sample snapshot.
opcontrol --event=event-name:sample-rate
~]# opcontrol --event=event-name:sample-rateWarning
29.2.2.2. Unit Masks
ophelp command. The values for each unit mask are listed in hexadecimal format. To specify more than one unit mask, the hexadecimal values must be combined using a bitwise or operation.
opcontrol --event=event-name:sample-rate:unit-mask
~]# opcontrol --event=event-name:sample-rate:unit-mask29.2.3. Separating Kernel and User-space Profiles
opcontrol --event=event-name:sample-rate:unit-mask:0
~]# opcontrol --event=event-name:sample-rate:unit-mask:0opcontrol --event=event-name:sample-rate:unit-mask:1
~]# opcontrol --event=event-name:sample-rate:unit-mask:1opcontrol --event=event-name:sample-rate:unit-mask:kernel:0
~]# opcontrol --event=event-name:sample-rate:unit-mask:kernel:0opcontrol --event=event-name:sample-rate:unit-mask:kernel:1
~]# opcontrol --event=event-name:sample-rate:unit-mask:kernel:1opcontrol --separate=choice
~]# opcontrol --separate=choicenone— Do not separate the profiles (default).library— Generate per-application profiles for libraries.kernel— Generate per-application profiles for the kernel and kernel modules.all— Generate per-application profiles for libraries and per-application profiles for the kernel and kernel modules.
--separate=library is used, the sample file name includes the name of the executable as well as the name of the library.
Note
29.3. Starting and Stopping OProfile
opcontrol --start
~]# opcontrol --startUsing log file /var/lib/oprofile/oprofiled.log Daemon started. Profiler running.
Using log file /var/lib/oprofile/oprofiled.log Daemon started. Profiler running./root/.oprofile/daemonrc are used.
oprofiled, is started; it periodically writes the sample data to the /var/lib/oprofile/samples/ directory. The log file for the daemon is located at /var/lib/oprofile/oprofiled.log.
Important
nmi_watchdog registers with the perf subsystem. Due to this, the perf subsystem grabs control of the performance counter registers at boot time, blocking OProfile from working.
nmi_watchdog=0 kernel parameter set, or run the following command to disable nmi_watchdog at run time:
echo 0 > /proc/sys/kernel/nmi_watchdog
~]# echo 0 > /proc/sys/kernel/nmi_watchdognmi_watchdog, use the following command:
echo 1 > /proc/sys/kernel/nmi_watchdog
~]# echo 1 > /proc/sys/kernel/nmi_watchdogopcontrol --shutdown
~]# opcontrol --shutdown29.4. Saving Data
opcontrol --save=name
~]# opcontrol --save=name/var/lib/oprofile/samples/name/ is created and the current sample files are copied to it.
29.5. Analyzing the Data
oprofiled, collects the samples and writes them to the /var/lib/oprofile/samples/ directory. Before reading the data, make sure all data has been written to this directory by executing the following command as root:
opcontrol --dump
~]# opcontrol --dump/bin/bash becomes:
\{root\}/bin/bash/\{dep\}/\{root\}/bin/bash/CPU_CLK_UNHALTED.100000
\{root\}/bin/bash/\{dep\}/\{root\}/bin/bash/CPU_CLK_UNHALTED.100000opreportopannotate
Warning
oparchive can be used to address this problem.
29.5.1. Using opreport
opreport tool provides an overview of all the executables being profiled.
opreport man page for a list of available command-line options, such as the -r option used to sort the output from the executable with the smallest number of samples to the one with the largest number of samples.
29.5.2. Using opreport on a Single Executable
opreport:
opreport mode executable
~]# opreport mode executable-
-l - List sample data by symbols. For example, the following is part of the output from running the command
opreport -l /lib/tls/libc-version.so:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The first column is the number of samples for the symbol, the second column is the percentage of samples for this symbol relative to the overall samples for the executable, and the third column is the symbol name.To sort the output from the largest number of samples to the smallest (reverse order), use-rin conjunction with the-loption. -
-i symbol-name - List sample data specific to a symbol name. For example, the following output is from the command
opreport -l -i __gconv_transform_utf8_internal /lib/tls/libc-version.so:samples % symbol name 12 100.000 __gconv_transform_utf8_internal
samples % symbol name 12 100.000 __gconv_transform_utf8_internalCopy to Clipboard Copied! Toggle word wrap Toggle overflow The first line is a summary for the symbol/executable combination.The first column is the number of samples for the memory symbol. The second column is the percentage of samples for the memory address relative to the total number of samples for the symbol. The third column is the symbol name. -
-d - List sample data by symbols with more detail than
-l. For example, the following output is from the commandopreport -l -d __gconv_transform_utf8_internal /lib/tls/libc-version.so:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The data is the same as the-loption except that for each symbol, each virtual memory address used is shown. For each virtual memory address, the number of samples and percentage of samples relative to the number of samples for the symbol is displayed. -
-xsymbol-name - Exclude the comma-separated list of symbols from the output.
-
session:name - Specify the full path to the session or a directory relative to the
/var/lib/oprofile/samples/directory.
29.5.3. Getting more detailed output on the modules
initrd file on boot up, the directory with the various kernel modules, or a locally created kernel module. As a result, when OProfile records sample for a module, it just lists the samples for the modules for an executable in the root directory, but this is unlikely to be the place with the actual code for the module. You will need to take some steps to make sure that analysis tools get the executable.
uname -a command, obtain the appropriate debuginfo package and install it on the machine.
opcontrol --reset
~]# opcontrol --resetopcontrol --setup --vmlinux=/usr/lib/debug/lib/modules/`uname -r`/vmlinux --event=CPU_CLK_UNHALTED:500000
~]# opcontrol --setup --vmlinux=/usr/lib/debug/lib/modules/`uname -r`/vmlinux --event=CPU_CLK_UNHALTED:50000029.5.4. Using opannotate
opannotate tool tries to match the samples for particular instructions to the corresponding lines in the source code. The resulting files generated should have the samples for the lines at the left. It also puts in a comment at the beginning of each function listing the total samples for the function.
opannotate is as follows:
opannotate --search-dirs src-dir --source executable
~]# opannotate --search-dirs src-dir --source executableopannotate man page for a list of additional command-line options.
29.6. Understanding /dev/oprofile/
/dev/oprofile/ directory contains the file system for OProfile. Use the cat command to display the values of the virtual files in this file system. For example, the following command displays the type of processor OProfile detected:
cat /dev/oprofile/cpu_type
~]# cat /dev/oprofile/cpu_type/dev/oprofile/ for each counter. For example, if there are 2 counters, the directories /dev/oprofile/0/ and dev/oprofile/1/ exist.
count— The interval between samples.enabled— If 0, the counter is off and no samples are collected for it; if 1, the counter is on and samples are being collected for it.event— The event to monitor.extra— Used on machines with Nehalem processors to further specify the event to monitor.kernel— If 0, samples are not collected for this counter event when the processor is in kernel-space; if 1, samples are collected even if the processor is in kernel-space.unit_mask— Defines which unit masks are enabled for the counter.user— If 0, samples are not collected for the counter event when the processor is in user-space; if 1, samples are collected even if the processor is in user-space.
cat command. For example:
cat /dev/oprofile/0/count
~]# cat /dev/oprofile/0/count29.7. Example Usage
- Determine which applications and services are used the most on a system —
opreportcan be used to determine how much processor time an application or service uses. If the system is used for multiple services but is under performing, the services consuming the most processor time can be moved to dedicated systems. - Determine processor usage — The
CPU_CLK_UNHALTEDevent can be monitored to determine the processor load over a given period of time. This data can then be used to determine if additional processors or a faster processor might improve system performance.
29.8. OProfile Support for Java
29.8.1. Profiling Java Code
-agentlib:jvmti_oprofile
-agentlib:jvmti_oprofileNote
29.9. Graphical Interface
oprof_start command as root at a shell prompt. To use the graphical interface, you will need to have the oprofile-gui package installed.
/root/.oprofile/daemonrc, and the application exits.
Note
Figure 29.1. OProfile Setup
vmlinux file for the kernel to monitor in the Kernel image file text field. To configure OProfile not to monitor the kernel, select No kernel image.
Figure 29.2. OProfile Configuration
oprofiled daemon log includes more information.
opcontrol --separate=library command. If Per-application profiles, including kernel is selected, OProfile generates per-application profiles for the kernel and kernel modules as discussed in Section 29.2.3, “Separating Kernel and User-space Profiles”. This is equivalent to the opcontrol --separate=kernel command.
opcontrol --dump command.
29.10. OProfile and SystemTap
netstat, ps, top, and iostat; however, SystemTap is designed to provide more filtering and analysis options for collected information.
29.11. Additional Resources
29.11.1. Installed Docs
/usr/share/doc/oprofile-version/oprofile.html— OProfile Manualoprofileman page — Discussesopcontrol,opreport,opannotate, andophelp
29.11.2. Useful Websites
- http://oprofile.sourceforge.net/ — Contains the latest documentation, mailing lists, IRC channels, and more.
- SystemTap Beginners Guide — Provides basic instructions on how to use SystemTap to monitor different subsystems of Red Hat Enterprise Linux in finer detail.
Part VIII. Kernel, Module and Driver Configuration
Chapter 30. Manually Upgrading the Kernel
rpm command instead of yum.
Warning
Warning
30.1. Overview of Kernel Packages
- kernel — Contains the kernel for single, multicore and multiprocessor systems.
- kernel-debug — Contains a kernel with numerous debugging options enabled for kernel diagnosis, at the expense of reduced performance.
- kernel-devel — Contains the kernel headers and makefiles sufficient to build modules against the kernel package.
- kernel-debug-devel — Contains the development version of the kernel with numerous debugging options enabled for kernel diagnosis, at the expense of reduced performance.
- kernel-doc — Documentation files from the kernel source. Various portions of the Linux kernel and the device drivers shipped with it are documented in these files. Installation of this package provides a reference to the options that can be passed to Linux kernel modules at load time.By default, these files are placed in the
/usr/share/doc/kernel-doc-<kernel_version>/directory. - kernel-headers — Includes the C header files that specify the interface between the Linux kernel and user-space libraries and programs. The header files define structures and constants that are needed for building most standard programs.
- kernel-firmware — Contains all of the firmware files that are required by various devices to operate.
- perf — This package contains supporting scripts and documentation for the perf tool shipped in each kernel image subpackage.
30.2. Preparing to Upgrade
VFAT file system. You can create bootable USB media on media formatted as ext2, ext3, or VFAT.
4 GB is required for a distribution DVD image, around 700 MB for a distribution CD image, or around 10 MB for a minimal boot media image.
boot.iso file from a Red Hat Enterprise Linux installation DVD, or installation CD-ROM #1, and you need a USB storage device formatted with the VFAT file system and around 16 MB of free space. The following procedure will not affect existing files on the USB storage device unless they have the same path names as the files that you copy onto it. To create USB boot media, perform the following commands as root:
- Install the SYSLINUX boot loader on the USB storage device:
syslinux /dev/sdX1
~]# syslinux /dev/sdX1Copy to Clipboard Copied! Toggle word wrap Toggle overflow ...where sdX is the device name. - Create mount points for
boot.isoand the USB storage device:mkdir /mnt/isoboot /mnt/diskboot
~]# mkdir /mnt/isoboot /mnt/diskbootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mount
boot.iso:mount -o loop boot.iso /mnt/isoboot
~]# mount -o loop boot.iso /mnt/isobootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mount the USB storage device:
mount /dev/<sdX1> /mnt/diskboot
~]# mount /dev/<sdX1> /mnt/diskbootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the ISOLINUX files from the
boot.isoto the USB storage device:cp /mnt/isoboot/isolinux/* /mnt/diskboot
~]# cp /mnt/isoboot/isolinux/* /mnt/diskbootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
isolinux.cfgfile fromboot.isoas thesyslinux.cfgfile for the USB device:grep -v local /mnt/isoboot/isolinux/isolinux.cfg > /mnt/diskboot/syslinux.cfg
~]# grep -v local /mnt/isoboot/isolinux/isolinux.cfg > /mnt/diskboot/syslinux.cfgCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Unmount
boot.isoand the USB storage device:umount /mnt/isoboot /mnt/diskboot
~]# umount /mnt/isoboot /mnt/diskbootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - You should reboot the machine with the boot media and verify that you are able to boot with it before continuing.
mkbootdisk command as root. See man mkbootdisk man page after installing the package for usage information.
yum list installed "kernel-*" at a shell prompt. The output will comprise some or all of the following packages, depending on the system's architecture, and the version numbers may differ:
yum list installed "kernel-*" kernel.x86_64 2.6.32-17.el6 @rhel-x86_64-server-6 kernel-doc.noarch 2.6.32-17.el6 @rhel-x86_64-server-6 kernel-firmware.noarch 2.6.32-17.el6 @rhel-x86_64-server-6 kernel-headers.x86_64 2.6.32-17.el6 @rhel-x86_64-server-6
~]# yum list installed "kernel-*"
kernel.x86_64 2.6.32-17.el6 @rhel-x86_64-server-6
kernel-doc.noarch 2.6.32-17.el6 @rhel-x86_64-server-6
kernel-firmware.noarch 2.6.32-17.el6 @rhel-x86_64-server-6
kernel-headers.x86_64 2.6.32-17.el6 @rhel-x86_64-server-630.3. Downloading the Upgraded Kernel
- Security Errata — See http://www.redhat.com/security/updates/ for information on security errata, including kernel upgrades that fix security issues.
- The Red Hat Network — For a system subscribed to the Red Hat Network, the yum package manager can download the latest kernel and upgrade the kernel on the system. The Dracut utility will create an initial RAM disk image if needed, and configure the boot loader to boot the new kernel. For more information on installing packages from the Red Hat Network, see Chapter 8, Yum. For more information on subscribing a system to the Red Hat Network, see Chapter 6, Registering the System and Managing Subscriptions.
30.4. Performing the Upgrade
Important
-i argument with the rpm command to keep the old kernel. Do not use the -U option, since it overwrites the currently installed kernel, which creates boot loader problems. For example:
rpm -ivh kernel-<kernel_version>.<arch>.rpm
~]# rpm -ivh kernel-<kernel_version>.<arch>.rpm 30.5. Verifying the Initial RAM Disk Image
initramfs by running the dracut command. However, you usually don't need to create an initramfs manually: this step is automatically performed if the kernel and its associated packages are installed or upgraded from RPM packages distributed by Red Hat.
initramfs corresponding to your current kernel version exists and is specified correctly in the grub.conf configuration file by following this procedure:
Procedure 30.1. Verifying the Initial RAM Disk Image
- As root, list the contents in the
/boot/directory and find the kernel (vmlinuz-<kernel_version>) andinitramfs-<kernel_version>with the latest (most recent) version number:Example 30.1. Ensuring that the kernel and initramfs versions match
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - we have three kernels installed (or, more correctly, three kernel files are present in
/boot/), - the latest kernel is
vmlinuz-2.6.32-22.el6.x86_64, and - an
initramfsfile matching our kernel version,initramfs-2.6.32-22.el6.x86_64.img, also exists.
Important
In the/boot/directory you may find severalinitrd-<version>kdump.imgfiles. These are special files created by the Kdump mechanism for kernel debugging purposes, are not used to boot the system, and can safely be ignored. - (Optional) If your
initramfs-<kernel_version>file does not match the version of the latest kernel in/boot/, or, in certain other situations, you may need to generate aninitramfsfile with the Dracut utility. Simply invokingdracutas root without options causes it to generate aninitramfsfile in the/boot/directory for the latest kernel present in that directory:dracut
~]# dracutCopy to Clipboard Copied! Toggle word wrap Toggle overflow You must use the--forceoption if you wantdracutto overwrite an existinginitramfs(for example, if yourinitramfshas become corrupt). Otherwisedracutwill refuse to overwrite the existinginitramfsfile:dracut Will not override existing initramfs (/boot/initramfs-2.6.32-22.el6.x86_64.img) without --force
~]# dracut Will not override existing initramfs (/boot/initramfs-2.6.32-22.el6.x86_64.img) without --forceCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can create an initramfs in the current directory by callingdracut <initramfs_name> <kernel_version>:dracut "initramfs-$(uname -r).img" $(uname -r)
~]# dracut "initramfs-$(uname -r).img" $(uname -r)Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you need to specify specific kernel modules to be preloaded, add the names of those modules (minus any file name suffixes such as.ko) inside the parentheses of theadd_dracutmodules="<module> [<more_modules>]"directive of the/etc/dracut.confconfiguration file. You can list the file contents of aninitramfsimage file created by dracut by using thelsinitrd <initramfs_file>command:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Seeman dracutandman dracut.conffor more information on options and usage. - Examine the
grub.confconfiguration file in the/boot/grub/directory to ensure that aninitrdexists for the kernel version you are booting. See Section 30.6, “Verifying the Boot Loader” for more information.initramfs-<kernel_version>.img
Verifying the Initial RAM Disk Image and Kernel on IBM eServer System i
addRamDisk command. This step is performed automatically if the kernel and its associated packages are installed or upgraded from the RPM packages distributed by Red Hat; thus, it does not need to be executed manually. To verify that it was created, use the command ls -l /boot/ to make sure the /boot/vmlinitrd-<kernel_version> file already exists (the <kernel_version> should match the version of the kernel just installed).
30.6. Verifying the Boot Loader
rpm, the kernel package creates an entry in the boot loader configuration file for that new kernel. However, rpm does not configure the new kernel to boot as the default kernel. You must do this manually when installing a new kernel with rpm.
rpm to ensure that the configuration is correct. Otherwise, the system may not be able to boot into Red Hat Enterprise Linux properly. If this happens, boot the system with the boot media created earlier and re-configure the boot loader.
| Architecture | Boot Loader | See |
|---|---|---|
| x86 | GRUB | Section 30.6.1, “Configuring the GRUB Boot Loader” |
| AMD AMD64 or Intel 64 | GRUB | Section 30.6.1, “Configuring the GRUB Boot Loader” |
| IBM eServer System i | OS/400 | Section 30.6.3, “Configuring the OS/400 Boot Loader” |
| IBM eServer System p | YABOOT | Section 30.6.4, “Configuring the YABOOT Boot Loader” |
| IBM System z | z/IPL |
30.6.1. Configuring the GRUB Boot Loader
/boot/grub/grub.conf, contains a few lines with directives, such as default, timeout, splashimage and hiddenmenu (the last directive has no argument). The remainder of the file contains 4-line stanzas that each refer to an installed kernel. These stanzas always start with a title entry, after which the associated root, kernel and initrd directives should always be indented. Ensure that each stanza starts with a title that contains a version number (in parentheses) that matches the version number in the kernel /vmlinuz-<version_number> line of the same stanza.
Example 30.2. /boot/grub/grub.conf
/boot/ partition was created, the paths to the kernel and the initramfs image are relative to /boot/. This is the case in Example 30.2, “/boot/grub/grub.conf”, above. Therefore the initrd /initramfs-2.6.32-22.el6.x86_64.img line in the first kernel stanza means that the initramfs image is actually located at /boot/initramfs-2.6.32-22.el6.x86_64.img when the root file system is mounted, and likewise for the kernel path (for example: kernel /vmlinuz-2.6.32-22.el6.x86_64) in each stanza of grub.conf.
Note
grub.conf, the initrd directive must point to the location (relative to the /boot/ directory if it is on a separate partition) of the initramfs file corresponding to the same kernel version. This directive is called initrd because the previous tool which created initial RAM disk images, mkinitrd, created what were known as initrd files. Thus the grub.conf directive remains initrd to maintain compatibility with other tools. The file-naming convention of systems using the dracut utility to create the initial RAM disk image is: initramfs-<kernel_version>.img
mkinitrd. For information on using Dracut, see Section 30.5, “Verifying the Initial RAM Disk Image”.
kernel /vmlinuz-<kernel_version> line matches the version number of the initramfs image given on the initrd /initramfs-<kernel_version>.img line of each stanza. See Procedure 30.1, “Verifying the Initial RAM Disk Image” for more information.
default= directive tells GRUB which kernel to boot by default. Each title in grub.conf represents a bootable kernel. GRUB counts the titled stanzas representing bootable kernels starting with 0. In Example 30.2, “/boot/grub/grub.conf”, the line default=1 indicates that GRUB will boot, by default, the second kernel entry, i.e. title Red Hat Enterprise Linux (2.6.32-19.el6.x86_64).
title entry in grub.conf, we would need to change the default value to 0.
rpm, verify that /boot/grub/grub.conf is correct, change the default= value to the new kernel (while remembering to count from 0), and reboot the computer into the new kernel. Ensure your hardware is detected by watching the boot process output.
Important
timeout directive in grub.conf to 0, GRUB will not display its list of bootable kernels when the system starts up. In order to display this list when booting, press and hold any alphanumeric key while and immediately after BIOS information is displayed. GRUB will present you with the GRUB menu.
30.6.2. Configuring the Loopback Device Limit
max_loop kernel option. For example, to set the maximum number of loopback devices to 64, edit the /etc/grub.conf file, and add max_loop=64 at the end of the kernel line. The line in /etc/grub.conf would then look something like this:
kernel /vmlinuz-2.6.32-131.0.15.el6.x86_64 ro root=/dev/mapper/root rhgb quiet max_loop=64 initrd /initramfs-2.6.32-131.0.15.el6.x86_64.img
kernel /vmlinuz-2.6.32-131.0.15.el6.x86_64 ro root=/dev/mapper/root rhgb quiet max_loop=64
initrd /initramfs-2.6.32-131.0.15.el6.x86_64.img/dev/loop* devices (/dev/loop0 to /dev/loop7) are automatically generated, but others can be created as desired. For example, to set up a ninth loop device named /dev/loop8, issue the following command as root:
mknod /dev/loop8 b 7 8
~]# mknod /dev/loop8 b 7 8udev rule.
max_loop has been set before the system booted, max_loop becomes a hard limit on the number of loopback devices, and the number of loopback devices cannot be dynamically grown beyond the limit.
30.6.3. Configuring the OS/400 Boot Loader
/boot/vmlinitrd-<kernel-version> file is installed when you upgrade the kernel. However, you must use the dd command to configure the system to boot the new kernel.
- As root, issue the command
cat /proc/iSeries/mf/sideto determine the default side (either A, B, or C). - As root, issue the following command, where <kernel-version> is the version of the new kernel and <side> is the side from the previous command:
dd if=/boot/vmlinitrd-<kernel-version> of=/proc/iSeries/mf/<side>/vmlinux bs=8k
dd if=/boot/vmlinitrd-<kernel-version> of=/proc/iSeries/mf/<side>/vmlinux bs=8kCopy to Clipboard Copied! Toggle word wrap Toggle overflow
30.6.4. Configuring the YABOOT Boot Loader
/etc/yaboot.conf as its configuration file. Confirm that the file contains an image section with the same version as the kernel package just installed, and likewise for the initramfs image:
default and set it to the label of the image stanza that contains the new kernel.
Chapter 31. Working with Kernel Modules
- a device driver which adds support for new hardware; or,
- support for a file system such as
btrfsorNFS.
- use the user-space module-init-tools package to display, query, load and unload kernel modules and their dependencies;
- set module parameters both dynamically on the command line and permanently so that you can customize the behavior of your kernel modules; and,
- load modules at boot time.
Note
yum install module-init-tools
~]# yum install module-init-tools31.1. Listing Currently-Loaded Modules
lsmod command:
lsmod output specifies:
- the name of a kernel module currently loaded in memory;
- the amount of memory it uses; and,
- the sum total of processes that are using the module and other modules which depend on it, followed by a list of the names of those modules, if there are any. Using this list, you can first unload all the modules depending the module you want to unload. For more information, see Section 31.4, “Unloading a Module”.
lsmod output is less verbose and considerably easier to read than the content of the /proc/modules pseudo-file.
31.2. Displaying Information About a Module
modinfo <module_name> command.
Note
.ko extension to the end of the name. Kernel module names do not have extensions: their corresponding files do.
e1000e module, which is the Intel PRO/1000 network driver, run:
Example 31.1. Listing information about a kernel module with lsmod
modinfo output:
- filename
- The absolute path to the
.kokernel object file. You can usemodinfo -nas a shortcut command for printing only thefilenamefield. - description
- A short description of the module. You can use
modinfo -das a shortcut command for printing only the description field. - alias
- The
aliasfield appears as many times as there are aliases for a module, or is omitted entirely if there are none. - depends
- This field contains a comma-separated list of all the modules this module depends on.
Note
If a module has no dependencies, thedependsfield may be omitted from the output. - parm
- Each
parmfield presents one module parameter in the formparameter_name:description, where:- parameter_name is the exact syntax you should use when using it as a module parameter on the command line, or in an option line in a
.conffile in the/etc/modprobe.d/directory; and, - description is a brief explanation of what the parameter does, along with an expectation for the type of value the parameter accepts (such as int, unit or array of int) in parentheses.
You can list all parameters that the module supports by using the-poption. However, because useful value type information is omitted frommodinfo -poutput, it is more useful to run:Example 31.2. Listing module parameters
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
31.3. Loading a Module
modprobe <module_name> command as root. For example, to load the wacom module, run:
modprobe wacom
~]# modprobe wacommodprobe attempts to load the module from the /lib/modules/<kernel_version>/kernel/drivers/ directory. In this directory, each type of module has its own subdirectory, such as net/ and scsi/, for network and SCSI interface drivers respectively.
/lib/modules/<kernel_version>/modules.dep file. The modprobe command always reads the modules.dep file when performing operations. When you ask modprobe to load a specific kernel module, it first examines the dependencies of that module, if there are any, and loads them if they are not already loaded into the kernel. modprobe resolves dependencies recursively: If necessary, it loads all dependencies of dependencies, and so on, thus ensuring that all dependencies are always met.
-v (or --verbose) option to cause modprobe to display detailed information about what it is doing, which may include loading module dependencies. The following is an example of loading the Fibre Channel over Ethernet module verbosely:
Example 31.3. modprobe -v shows module dependencies as they are loaded
modprobe loaded the scsi_tgt, scsi_transport_fc, libfc and libfcoe modules as dependencies before finally loading fcoe. Also note that modprobe used the more “primitive” insmod command to insert the modules into the running kernel.
Important
insmod command can also be used to load kernel modules, it does not resolve dependencies. Because of this, you should always load modules using modprobe instead.
31.4. Unloading a Module
modprobe -r <module_name> as root. For example, assuming that the wacom module is already loaded into the kernel, you can unload it by running:
modprobe -r wacom
~]# modprobe -r wacom- the
wacommodule, - a module that
wacomdirectly depends on, or, - any module that
wacom—through the dependency tree—depends on indirectly.
lsmod to obtain the names of the modules which are preventing you from unloading a certain module.
firewire_ohci module (because you believe there is a bug in it that is affecting system stability, for example), your terminal session might look similar to this:
firewire_ohci depends on firewire_core, which itself depends on crc-itu-t.
firewire_ohci using the modprobe -v -r <module_name> command, where -r is short for --remove and -v for --verbose:
modprobe -r -v firewire_ohci rmmod /lib/modules/2.6.32-71.el6.x86_64/kernel/drivers/firewire/firewire-ohci.ko rmmod /lib/modules/2.6.32-71.el6.x86_64/kernel/drivers/firewire/firewire-core.ko rmmod /lib/modules/2.6.32-71.el6.x86_64/kernel/lib/crc-itu-t.ko
~]# modprobe -r -v firewire_ohci
rmmod /lib/modules/2.6.32-71.el6.x86_64/kernel/drivers/firewire/firewire-ohci.ko
rmmod /lib/modules/2.6.32-71.el6.x86_64/kernel/drivers/firewire/firewire-core.ko
rmmod /lib/modules/2.6.32-71.el6.x86_64/kernel/lib/crc-itu-t.koImportant
rmmod command can be used to unload kernel modules, it is recommended to use modprobe -r instead.
31.5. Blacklisting a Module
/etc/modprobe.d/ directory as root:
blacklist <module_name>
blacklist <module_name>/etc/modprobe.d/blacklist.conf file that already exists on the system by default. However, the preferred method is to create a separate configuration file, /etc/modprobe.d/<module_name>.conf, that will contain settings specific only to the given kernel module.
Example 31.4. An example of /etc/modprobe.d/blacklist.conf
blacklist <module_name> command, however, does not prevent the module from being loaded manually, or from being loaded as a dependency for another kernel module that is not blacklisted. To ensure that a module cannot be loaded on the system at all, modify the specified configuration file in the /etc/modprobe.d/ directory as root with the following line:
install <module_name> /bin/true
install <module_name> /bin/trueExample 31.5. Using module blacklisting as a temporary problem solution
pppol2pt) has been found, and this flaw could be misused to compromise your system. If your system does not require the pppol2pt module to function, you can follow this procedure to blacklist pppol2pt completely until this problem is fixed:
- Verify whether
pppol2ptis currently loaded in the kernel by running the following command:lsmod | grep ^pppol2tp && echo "The module is loaded" || echo "The module is not loaded"
~]# lsmod | grep ^pppol2tp && echo "The module is loaded" || echo "The module is not loaded"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If the module is loaded, you need to unload it and all its dependencies to prevent its possible misuse. See Section 31.4, “Unloading a Module” for instructions on how to safely unload it.
- Run the following command to ensure that
pppol2ptcannot be loaded to the kernel:echo "install pppol2tp /bin/true" > /etc/modprobe.d/pppol2tp.conf
~]# echo "install pppol2tp /bin/true" > /etc/modprobe.d/pppol2tp.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command overwrites the content of the/etc/modprobe.d/pppol2tp.conffile if it already exists on your system. Check and back up your existingpppol2tp.confbefore running this command. Also, if you were unable to unload the module, you have to reboot the system for this command to take effect.
pppol2pt module has been properly fixed, you can delete the /etc/modprobe.d/pppol2tp.conf file or restore its previous content, which will allow your system to load the pppol2pt module with its original configuration.
Important
31.6. Setting Module Parameters
- Load a kernel module by running the
modprobecommand along with a list of customized parameters on the command line. If the module is already loaded, you need to first unload all its dependencies and the module itself using themodprobe -rcommand. This method allows you to run a kernel module with specific settings without making the changes persistent. See Section 31.6.1, “Loading a Customized Module - Temporary Changes” for more information. - Alternatively, specify a list of the customized parameters in an existing or newly-created file in the
/etc/modprobe.d/directory. This method ensures that the module customization is persistent by setting the specified parameters accordingly each time the module is loaded, such as after every reboot ormodprobecommand. See Section 31.6.2, “Loading a Customized Module - Persistent Changes” for more information.
31.6.1. Loading a Customized Module - Temporary Changes
modprobe in the following format as root:
modprobe <module_name> [parameter=value]
~]# modprobe <module_name> [parameter=value]- You can enter multiple parameters and values by separating them with spaces.
- Some module parameters expect a list of comma-separated values as their argument. When entering the list of values, do not insert a space after each comma, or
modprobewill incorrectly interpret the values following spaces as additional parameters. - The
modprobecommand silently succeeds with an exit status of0if it successfully loads the module, or the module is already loaded into the kernel. Thus, you must ensure that the module is not already loaded before attempting to load it with custom parameters. Themodprobecommand does not automatically reload the module, or alert you that it is already loaded.
e1000e module, which is the network driver for Intel PRO/1000 network adapters, as an example:
Procedure 31.1. Loading a Kernel Module with Custom Parameters
- Verify whether the module is not already loaded into the kernel by running the following command:
lsmod|grep e1000e e1000e 236338 0 ptp 9614 1 e1000e
~]# lsmod|grep e1000e e1000e 236338 0 ptp 9614 1 e1000eCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the output of the command in this example indicates that thee1000emodule is already loaded into the kernel. It also shows that this module has one dependency, theptpmodule. - If the module is already loaded into the kernel, you must unload the module and all its dependencies before proceeding with the next step. See Section 31.4, “Unloading a Module” for instructions on how to safely unload it.
- Load the module and list all custom parameters after the module name. For example, if you wanted to load the Intel PRO/1000 network driver with the interrupt throttle rate set to 3000 interrupts per second for the first, second and third instances of the driver, and Energy Efficient Ethernet (EEE) turned on [5], you would run, as root:
modprobe e1000e InterruptThrottleRate=3000,3000,3000 EEE=1
~]# modprobe e1000e InterruptThrottleRate=3000,3000,3000 EEE=1Copy to Clipboard Copied! Toggle word wrap Toggle overflow This example illustrates passing multiple values to a single parameter by separating them with commas and omitting any spaces between them.
31.6.2. Loading a Customized Module - Persistent Changes
/etc/modprobe.d/ directory with a line in the following format.
options <module_name> [parameter=value]
~]# options <module_name> [parameter=value]b43 module for Open Firmware for wireless networks, ensuring that changes persist between module reloads.
Procedure 31.2. Loading a Kernel Module with Custom Parameters - Persistent Changes
- Add the following line to the
/etc/modprobe.d/openfwwf.conffile, which ensures that theb43module is always loaded with QoS and hardware-accelerated cryptography disabled:options b43 nohwcrypt=1 qos=0
options b43 nohwcrypt=1 qos=0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Verify whether the module is not already loaded into the kernel by running the following command:
lsmod|grep ^b43 ~]#
~]# lsmod|grep ^b43 ~]#Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the output of the command in this example indicates that the module is currently not loaded into the kernel. - If the module is already loaded into the kernel, you must unload the module and all its dependencies before proceeding with the next step. See Section 31.4, “Unloading a Module” for instructions on how to safely unload it.
- Load the
b43module by running the following command:modprobe b43
~]# modprobe b43Copy to Clipboard Copied! Toggle word wrap Toggle overflow
31.7. Persistent Module Loading
<file_name>.modules file in the /etc/sysconfig/modules/ directory, where <file_name> is any descriptive name of your choice. Your <file_name>.modules files are treated by the system startup scripts as shell scripts, and as such should begin with an interpreter directive (also called a “bang line”) as their first line:
Example 31.6. First line of a file_name.modules file
#!/bin/sh
#!/bin/sh<file_name>.modules file should be executable. You can make it executable by running:
modules]# chmod +x <file_name>.modules
modules]# chmod +x <file_name>.modulesbluez-uinput.modules script loads the uinput module:
Example 31.7. /etc/sysconfig/modules/bluez-uinput.modules
#!/bin/sh
if [ ! -c /dev/input/uinput ] ; then
exec /sbin/modprobe uinput >/dev/null 2>&1
fi
#!/bin/sh
if [ ! -c /dev/input/uinput ] ; then
exec /sbin/modprobe uinput >/dev/null 2>&1
fiif-conditional statement on the third line ensures that the /dev/input/uinput file does not already exist (the ! symbol negates the condition), and, if that is the case, loads the uinput module by calling exec /sbin/modprobe uinput. Note that the uinput module creates the /dev/input/uinput file, so testing to see if that file exists serves as verification of whether the uinput module is loaded into the kernel.
>/dev/null 2>&1 clause at the end of that line redirects any output to /dev/null so that the modprobe command remains quiet.
31.8. Specific Kernel Module Capabilities
31.8.1. Using Channel Bonding
bonding kernel module and a special network interface, called a channel bonding interface. Channel bonding enables two or more network interfaces to act as one, simultaneously increasing the bandwidth and providing redundancy.
- Configure a channel bonding interface as outlined in Section 11.2.4, “Channel Bonding Interfaces”.
- To enhance performance, adjust available module options to ascertain what combination works best. Pay particular attention to the
miimonorarp_intervaland thearp_ip_targetparameters. See Section 31.8.1.1, “Bonding Module Directives” for a list of available options and how to quickly determine the best ones for your bonded interface.
31.8.1.1. Bonding Module Directives
BONDING_OPTS="<bonding parameters>" directive in your bonding interface configuration file (ifcfg-bond0 for example). Parameters to bonded interfaces can be configured without unloading (and reloading) the bonding module by manipulating files in the sysfs file system.
sysfs is a virtual file system that represents kernel objects as directories, files and symbolic links. sysfs can be used to query for information about kernel objects, and can also manipulate those objects through the use of normal file system commands. The sysfs virtual file system has a line in /etc/fstab, and is mounted under the /sys/ directory. All bonding interfaces can be configured dynamically by interacting with and manipulating files under the /sys/class/net/ directory.
ifcfg-bond0 by following the instructions in Section 11.2.4, “Channel Bonding Interfaces”. Insert the SLAVE=yes and MASTER=bond0 directives in the configuration files for each interface bonded to bond0. Once this is completed, you can proceed to testing the parameters.
ifconfig bond<N> up as root:
ifconfig bond0 up
~]# ifconfig bond0 upifcfg-bond0 bonding interface file, you will be able to see bond0 listed in the output of running ifconfig (without any options):
~]# cat /sys/class/net/bonding_masters bond0
~]# cat /sys/class/net/bonding_masters
bond0/sys/class/net/bond<N>/bonding/ directory. First, the bond you are configuring must be taken down:
ifconfig bond0 down
~]# ifconfig bond0 downecho 1000 > /sys/class/net/bond0/bonding/miimon
~]# echo 1000 > /sys/class/net/bond0/bonding/miimonbalance-alb mode, you could run either:
echo 6 > /sys/class/net/bond0/bonding/mode
~]# echo 6 > /sys/class/net/bond0/bonding/modeecho balance-alb > /sys/class/net/bond0/bonding/mode
~]# echo balance-alb > /sys/class/net/bond0/bonding/modeifconfig bond<N> up. If you decide to change the options, take the interface down, modify its parameters using sysfs, bring it back up, and re-test.
BONDING_OPTS= directive of the /etc/sysconfig/network-scripts/ifcfg-bond<N> file for the bonding interface you are configuring. Whenever that bond is brought up (for example, by the system during the boot sequence if the ONBOOT=yes directive is set), the bonding options specified in the BONDING_OPTS will take effect for that bond. For more information on configuring bonding interfaces (and BONDING_OPTS), see Section 11.2.4, “Channel Bonding Interfaces”.
parm in modinfo bonding output, or the exhaustive descriptions in the bonding.txt file in the kernel-doc package (see Section 31.9, “Additional Resources”).
Bonding Interface Parameters
-
arp_interval=<time_in_milliseconds> - Specifies (in milliseconds) how often ARP monitoring occurs. When configuring this setting, a good starting point for this parameter is
1000.Important
It is essential that botharp_intervalandarp_ip_targetparameters are specified, or, alternatively, themiimonparameter is specified. Failure to do so can cause degradation of network performance in the event that a link fails.If using this setting while inmode=0ormode=2(the two load-balancing modes), the network switch must be configured to distribute packets evenly across the NICs. For more information on how to accomplish this, see thebonding.txtfile in the kernel-doc package (see Section 31.9, “Additional Resources”).The value is set to0by default, which disables it. -
arp_ip_target=<ip_address>[,<ip_address_2>,…<ip_address_16>] - Specifies the target IP address of ARP requests when the
arp_intervalparameter is enabled. Up to 16 IP addresses can be specified in a comma separated list. -
arp_validate=<value> - Validate source/distribution of ARP probes; default is
none. Other valid values areactive,backup, andall. -
downdelay=<time_in_milliseconds> - Specifies (in milliseconds) how long to wait after link failure before disabling the link. The value must be a multiple of the value specified in the
miimonparameter. The value is set to0by default, which disables it. - lacp_rate=<value>
- Specifies the rate at which link partners should transmit LACPDU packets in 802.3ad mode. Possible values are:
slowor0— Default setting. This specifies that partners should transmit LACPDUs every 30 seconds.fastor1— Specifies that partners should transmit LACPDUs every 1 second.
-
miimon=<time_in_milliseconds> - Specifies (in milliseconds) how often MII link monitoring occurs. This is useful if high availability is required because MII is used to verify that the NIC is active. To verify that the driver for a particular NIC supports the MII tool, type the following command as root:
ethtool <interface_name> | grep "Link detected:"
~]# ethtool <interface_name> | grep "Link detected:"Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this command, replace <interface_name> with the name of the device interface, such aseth0, not the bond interface. If MII is supported, the command returns:Link detected: yes
Link detected: yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow If using a bonded interface for high availability, the module for each NIC must support MII. Setting the value to0(the default), turns this feature off. When configuring this setting, a good starting point for this parameter is100.Important
It is essential that botharp_intervalandarp_ip_targetparameters are specified, or, alternatively, themiimonparameter is specified. Failure to do so can cause degradation of network performance in the event that a link fails. -
mode=<value> - Allows you to specify the bonding policy. The <value> can be one of:
balance-rror0— Sets a round-robin policy for fault tolerance and load balancing. Transmissions are received and sent out sequentially on each bonded slave interface beginning with the first one available.active-backupor1— Sets an active-backup policy for fault tolerance. Transmissions are received and sent out via the first available bonded slave interface. Another bonded slave interface is only used if the active bonded slave interface fails.balance-xoror2— Sets an XOR (exclusive-or) policy for fault tolerance and load balancing. Using this method, the interface matches up the incoming request's MAC address with the MAC address for one of the slave NICs. Once this link is established, transmissions are sent out sequentially beginning with the first available interface.broadcastor3— Sets a broadcast policy for fault tolerance. All transmissions are sent on all slave interfaces.802.3ador4— Sets an IEEE 802.3ad dynamic link aggregation policy. Creates aggregation groups that share the same speed and duplex settings. Transmits and receives on all slaves in the active aggregator. Requires a switch that is 802.3ad compliant.balance-tlbor5— Sets a Transmit Load Balancing (TLB) policy for fault tolerance and load balancing. The outgoing traffic is distributed according to the current load on each slave interface. Incoming traffic is received by the current slave. If the receiving slave fails, another slave takes over the MAC address of the failed slave. This mode is only suitable for local addresses known to the kernel bonding module and therefore cannot be used behind a bridge with virtual machines.balance-albor6— Sets an Adaptive Load Balancing (ALB) policy for fault tolerance and load balancing. Includes transmit and receive load balancing forIPv4traffic. Receive load balancing is achieved throughARPnegotiation. This mode is only suitable for local addresses known to the kernel bonding module and therefore cannot be used behind a bridge with virtual machines.
-
num_unsol_na=<number> - Specifies the number of unsolicited IPv6 Neighbor Advertisements to be issued after a failover event. One unsolicited NA is issued immediately after the failover.The valid range is
0 - 255; the default value is1. This parameter affects only the active-backup mode. -
primary=<interface_name> - Specifies the interface name, such as
eth0, of the primary device. Theprimarydevice is the first of the bonding interfaces to be used and is not abandoned unless it fails. This setting is particularly useful when one NIC in the bonding interface is faster and, therefore, able to handle a bigger load.This setting is only valid when the bonding interface is inactive-backupmode. See thebonding.txtfile in the kernel-doc package (see Section 31.9, “Additional Resources”). -
primary_reselect=<value> - Specifies the reselection policy for the primary slave. This affects how the primary slave is chosen to become the active slave when failure of the active slave or recovery of the primary slave occurs. This parameter is designed to prevent flip-flopping between the primary slave and other slaves. Possible values are:
alwaysor0(default) — The primary slave becomes the active slave whenever it comes back up.betteror1— The primary slave becomes the active slave when it comes back up, if the speed and duplex of the primary slave is better than the speed and duplex of the current active slave.failureor2— The primary slave becomes the active slave only if the current active slave fails and the primary slave is up.
Theprimary_reselectsetting is ignored in two cases:- If no slaves are active, the first slave to recover is made the active slave.
- When initially enslaved, the primary slave is always made the active slave.
Changing theprimary_reselectpolicy viasysfswill cause an immediate selection of the best active slave according to the new policy. This may or may not result in a change of the active slave, depending upon the circumstances -
updelay=<time_in_milliseconds> - Specifies (in milliseconds) how long to wait before enabling a link. The value must be a multiple of the value specified in the
miimonparameter. The value is set to0by default, which disables it. -
use_carrier=<number> - Specifies whether or not
miimonshould use MII/ETHTOOL ioctls ornetif_carrier_ok()to determine the link state. Thenetif_carrier_ok()function relies on the device driver to maintains its state withnetif_carrier_on/off; most device drivers support this function.The MII/ETHROOL ioctls tools utilize a deprecated calling sequence within the kernel. However, this is still configurable in case your device driver does not supportnetif_carrier_on/off.Valid values are:1— Default setting. Enables the use ofnetif_carrier_ok().0— Enables the use of MII/ETHTOOL ioctls.
Note
If the bonding interface insists that the link is up when it should not be, it is possible that your network device driver does not supportnetif_carrier_on/off. -
xmit_hash_policy=<value> - Selects the transmit hash policy used for slave selection in
balance-xorand802.3admodes. Possible values are:0orlayer2— Default setting. This parameter uses the XOR of hardware MAC addresses to generate the hash. The formula used is:(<source_MAC_address> XOR <destination_MAC>) MODULO <slave_count>
(<source_MAC_address> XOR <destination_MAC>) MODULO <slave_count>Copy to Clipboard Copied! Toggle word wrap Toggle overflow This algorithm will place all traffic to a particular network peer on the same slave, and is 802.3ad compliant.1orlayer3+4— Uses upper layer protocol information (when available) to generate the hash. This allows for traffic to a particular network peer to span multiple slaves, although a single connection will not span multiple slaves.The formula for unfragmented TCP and UDP packets used is:((<source_port> XOR <dest_port>) XOR ((<source_IP> XOR <dest_IP>) AND 0xffff) MODULO <slave_count>((<source_port> XOR <dest_port>) XOR ((<source_IP> XOR <dest_IP>) AND 0xffff) MODULO <slave_count>Copy to Clipboard Copied! Toggle word wrap Toggle overflow For fragmented TCP or UDP packets and all other IP protocol traffic, the source and destination port information is omitted. For non-IP traffic, the formula is the same as thelayer2transmit hash policy.This policy intends to mimic the behavior of certain switches; particularly, Cisco switches with PFC2 as well as some Foundry and IBM products.The algorithm used by this policy is not 802.3ad compliant.2orlayer2+3— Uses a combination of layer2 and layer3 protocol information to generate the hash.Uses XOR of hardware MAC addresses and IP addresses to generate the hash. The formula is:(((<source_IP> XOR <dest_IP>) AND 0xffff) XOR ( <source_MAC> XOR <destination_MAC> )) MODULO <slave_count>(((<source_IP> XOR <dest_IP>) AND 0xffff) XOR ( <source_MAC> XOR <destination_MAC> )) MODULO <slave_count>Copy to Clipboard Copied! Toggle word wrap Toggle overflow This algorithm will place all traffic to a particular network peer on the same slave. For non-IP traffic, the formula is the same as for the layer2 transmit hash policy.This policy is intended to provide a more balanced distribution of traffic than layer2 alone, especially in environments where a layer3 gateway device is required to reach most destinations.This algorithm is 802.3ad compliant.
31.9. Additional Resources
Installed Documentation
lsmod(8)— The manual page for thelsmodcommand.modinfo(8)— The manual page for themodinfocommand.modprobe(8)> — The manual page for themodprobecommand.rmmod(8)— The manual page for thermmodcommand.ethtool(8)— The manual page for theethtoolcommand.mii-tool(8)— The manual page for themii-toolcommand.
Installable Documentation
/usr/share/doc/kernel-doc-<kernel_version>/Documentation/— This directory, which is provided by the kernel-doc package, contains information on the kernel, kernel modules, and their respective parameters. Before accessing the kernel documentation, you must run the following command as root:yum install kernel-doc
~]# yum install kernel-docCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Online Documentation
e1000e driver.
Chapter 32. The kdump Crash Recovery Service
kdump crash dumping mechanism is enabled, the system is booted from the context of another kernel. This second kernel reserves a small amount of memory and its only purpose is to capture the core dump image in case the system crashes.
kdump service in Red Hat Enterprise Linux, and provides a brief overview of how to analyze the resulting core dump using the crash debugging utility.
32.1. Installing the kdump Service
kdump service on your system, make sure you have the kexec-tools package installed. To do so, type the following at a shell prompt as root:
yum install kexec-tools
~]# yum install kexec-tools32.2. Configuring the kdump Service
kdump service: at the first boot, using the Kernel Dump Configuration graphical utility, and doing so manually on the command line.
Important
Intel IOMMU driver can occasionally prevent the kdump service from capturing the core dump image. To use kdump on Intel architectures reliably, it is advised that the IOMMU support is disabled.
Warning
kdump service does not work reliably on certain combinations of HP Smart Array devices and system boards from the same vendor. Consequent to this, users are strongly advised to test the configuration before using it in production environment, and if necessary, configure kdump to store the kernel crash dump to a remote machine over a network. For more information on how to test the kdump configuration, see Section 32.2.4, “Testing the Configuration”.
32.2.1. Configuring kdump at First Boot
kdump, navigate to the Kdump section and follow the instructions below.
- Select the Enable kdump? check box to allow the
kdumpdaemon to start at boot time. This will enable the service for runlevels2,3,4, and5, and start it for the current session. Similarly, unselecting the check box will disable it for all runlevels and stop the service immediately. - Click the up and down arrow buttons next to the Kdump Memory field to increase or decrease the value to configure the amount of memory that is reserved for the
kdumpkernel. Notice that the Usable System Memory field changes accordingly showing you the remaining memory that will be available to the system.
Important
kdump crash recovery is enabled, the minimum memory requirements increase by the amount of memory reserved for it. This value is determined by the user, and defaults to 128 MB plus 64 MB for each TB of physical memory (that is, a total of 192 MB for a system with 1 TB of physical memory). The memory can be attempted up to the maximum of 896 MB if required. This is recommended especially in large environments, for example in systems with a large number of Logical Unit Numbers (LUNs).
32.2.2. Using the Kernel Dump Configuration Utility
system-config-kdump at a shell prompt. You will be presented with a window as shown in Figure 32.1, “Basic Settings”.
kdump as well as to enable or disable starting the service at boot time. When you are done, click to save the changes. The system reboot will be requested, and unless you are already authenticated, you will be prompted to enter the superuser password.
Important
kdumpgui_run_bootloader Boolean must be enabled before launching the Kernel Dump Configuration utility. This Boolean allows system-config-kdump to run the boot loader in the bootloader_t SELinux domain. To permanently enable the Boolean, run the following command as root:
setsebool -P kdumpgui_run_bootloader 1
~]# setsebool -P kdumpgui_run_bootloader 1Enabling the Service
kdump daemon at boot time, click the button on the toolbar. This will enable the service for runlevels 2, 3, 4, and 5, and start it for the current session. Similarly, clicking the button will disable it for all runlevels and stop the service immediately.
The Basic Settings Tab
kdump kernel. To do so, select the Manual kdump memory settings radio button, and click the up and down arrow buttons next to the New kdump Memory field to increase or decrease the value. Notice that the Usable Memory field changes accordingly showing you the remaining memory that will be available to the system.
Figure 32.1. Basic Settings
Important
kdump crash recovery is enabled, the minimum memory requirements increase by the amount of memory reserved for it. This value is determined by the user, and defaults to 128 MB plus 64 MB for each TB of physical memory (that is, a total of 192 MB for a system with 1 TB of physical memory). The memory can be attempted up to the maximum of 896 MB if required. This is recommended especially in large environments, for example in systems with a large number of Logical Unit Numbers (LUNs).
The Target Settings Tab
vmcore dump. It can be either stored as a file in a local file system, written directly to a device, or sent over a network using the NFS (Network File System) or SSH (Secure Shell) protocol.
Figure 32.2. Target Settings
Note
/etc/dasd.conf file with other DASDs, for example:
0.0.2098 0.0.2198 0.0.2298 0.0.2398
0.0.2098
0.0.2198
0.0.2298
0.0.23980.0.2298 and 0.0.2398 are the DASDs used as the kdump target.
/etc/zfcp.conf file with other FCP-Attached SCSI disks, for example:
0.0.3d0c 0x500507630508c1ae 0x402424aa00000000 0.0.3d0c 0x500507630508c1ae 0x402424ab00000000 0.0.3d0c 0x500507630508c1ae 0x402424ac00000000
0.0.3d0c 0x500507630508c1ae 0x402424aa00000000
0.0.3d0c 0x500507630508c1ae 0x402424ab00000000
0.0.3d0c 0x500507630508c1ae 0x402424ac000000000.0.3d0c 0x500507630508c1ae 0x402424ab00000000 and 0.0.3d0c 0x500507630508c1ae 0x402424ac00000000 are the FCP-attached SCSI disks used as the kdump target.
Important
vmcore.flat file in the /var/crash/ directory on the target system, which is unreadable by the crash utility. To convert vmcore.flat to a dump file that is readable by crash, run the following command as root on the target system:
/usr/sbin/makedumpfile -R */tmp/vmcore-rearranged* < *vmcore.flat*
~]# /usr/sbin/makedumpfile -R */tmp/vmcore-rearranged* < *vmcore.flat*| Type | Supported Targets | Unsupported Targets |
|---|---|---|
| Raw device | All locally attached raw disks and partitions. | — |
| Local file system | ext2, ext3, ext4, minix, btrfs and xfs file systems on directly attached disk drives, hardware RAID logical drives, LVM devices, and mdraid arrays. | Any local file system not explicitly listed as supported in this table, including the auto type (automatic file system detection). |
| Remote directory | Remote directories accessed using the NFS or SSH protocol over IPv4. | Remote directories on the rootfs file system accessed using the NFS protocol. |
| iSCSI | Remote directories accessed using the iSCSI protocol over software initiators, unless iBFT (iSCSI Boot Firmware Table) is utilized. | Remote directories accessed using the iSCSI protocol using iBFT. |
| Multipath | Multipath-based storage.[a] | Remote directories accessed using the iSCSI protocol over hardware initiators. |
| — | — | Remote directories accessed over IPv6. |
| . | . | Remote directories accessed using the SMB/CIFS protocol. |
| . | . | Remote directories accessed using the FCoE (Fibre Channel over Ethernet) protocol. |
| . | . | Remote directories accessed using wireless network interfaces. |
[a]
Supported in Red Hat Enterprise Linux 6 from kexec-tools-2.0.0-245.el6 onwards.
| ||
The Filtering Settings Tab
vmcore dump.
Figure 32.3. Filtering Settings
The Expert Settings Tab
Figure 32.4. Expert Settings
kdump fails to create a core dump, select an appropriate option from the Default action pulldown list. Available options are (the default action), (to reboot the system), (to present a user with an interactive shell prompt), (to halt the system), and (to power the system off).
makedumpfile core collector, edit the Core collector text field; see the section called “Configuring the Core Collector” for more information.
32.2.3. Configuring kdump on the Command Line
Configuring the Memory Usage
GRUB boot loader, and on IBM System z using zipl. To configure the amount of memory to be reserved for the kdump kernel, edit the /boot/grub/grub.conf file and add crashkernel=<size>M or crashkernel=auto to the list of kernel options as shown in Example 32.1, “A sample /boot/grub/grub.conf file”. Note that the crashkernel=auto option only reserves the memory if the physical memory of the system is equal to or greater than:
- 2 GB on 32-bit and 64-bit x86 architectures;
- 2 GB on PowerPC if the page size is 4 KB, or 8 GB otherwise;
- 4 GB on IBM S/390.
Example 32.1. A sample /boot/grub/grub.conf file
Important
kdump crash recovery is enabled, the minimum memory requirements increase by the amount of memory reserved for it. This value is determined by the user, and defaults to 128 MB plus 64 MB for each TB of physical memory (that is, a total of 192 MB for a system with 1 TB of physical memory). The memory can be attempted up to the maximum of 896 MB if required. This is recommended especially in large environments, for example in systems with a large number of Logical Unit Numbers (LUNs).
Configuring the Target Type
vmcore file in the /var/crash/ directory of the local file system. To change this, as root, open the /etc/kdump.conf configuration file in a text editor and edit the options as described below.
#path /var/crash line, and replace the value with a desired directory path. Optionally, if you want to write the file to a different partition, follow the same procedure with the #ext4 /dev/sda3 line as well, and change both the file system type and the device (a device name, a file system label, and UUID are all supported) accordingly. For example:
ext3 /dev/sda4
path /usr/local/cores
ext3 /dev/sda4
path /usr/local/cores#raw /dev/sda5 line, and replace the value with a desired device name. For example:
raw /dev/sdb1
raw /dev/sdb1#net my.server.com:/export/tmp line, and replace the value with a valid host name and directory path. For example:
net penguin.example.com:/export/cores
net penguin.example.com:/export/cores#net user@my.server.com line, and replace the value with a valid user name and host name. For example:
net john@penguin.example.com
net john@penguin.example.comNote
/etc/dasd.conf file with other DASDs, for example:
0.0.2098 0.0.2198 0.0.2298 0.0.2398
0.0.2098
0.0.2198
0.0.2298
0.0.23980.0.2298 and 0.0.2398 are the DASDs used as the kdump target.
/etc/zfcp.conf file with other FCP-Attached SCSI disks, for example:
0.0.3d0c 0x500507630508c1ae 0x402424aa00000000 0.0.3d0c 0x500507630508c1ae 0x402424ab00000000 0.0.3d0c 0x500507630508c1ae 0x402424ac00000000
0.0.3d0c 0x500507630508c1ae 0x402424aa00000000
0.0.3d0c 0x500507630508c1ae 0x402424ab00000000
0.0.3d0c 0x500507630508c1ae 0x402424ac000000000.0.3d0c 0x500507630508c1ae 0x402424ab00000000 and 0.0.3d0c 0x500507630508c1ae 0x402424ac00000000 are the FCP-attached SCSI disks used as the kdump target.
Important
vmcore.flat file in the /var/crash/ directory on the target system, which is unreadable by the crash utility. To convert vmcore.flat to a dump file that is readable by crash, run the following command as root on the target system:
/usr/sbin/makedumpfile -R */tmp/vmcore-rearranged* < *vmcore.flat*
~]# /usr/sbin/makedumpfile -R */tmp/vmcore-rearranged* < *vmcore.flat*Configuring the Core Collector
vmcore dump file, kdump allows you to specify an external application (that is, a core collector) to compress the data, and optionally leave out all irrelevant information. Currently, the only fully supported core collector is makedumpfile.
root, open the /etc/kdump.conf configuration file in a text editor, remove the hash sign (“#”) from the beginning of the #core_collector makedumpfile -c --message-level 1 -d 31 line, and edit the command-line options as described below.
-c parameter. For example:
core_collector makedumpfile -c
core_collector makedumpfile -c-d value parameter, where value is a sum of values of pages you want to omit as described in Table 32.2, “Supported filtering levels”. For example, to remove both zero and free pages, use the following:
core_collector makedumpfile -d 17 -c
core_collector makedumpfile -d 17 -cmakedumpfile for a complete list of available options.
| Option | Description |
|---|---|
1 | Zero pages |
2 | Cache pages |
4 | Cache private |
8 | User pages |
16 | Free pages |
Changing the Default Action
kdump fails to create a core dump, the root file system is mounted and /sbin/init is run.
kdump could operate reliably using less reserved memory. To allow the previous behavior, the mount_root_run_init option has been added to Table 32.3, “Supported actions”.
root, open the /etc/kdump.conf configuration file in a text editor, remove the hash sign (“#”) from the beginning of the #default shell line, and replace the value with a desired action as described in Table 32.3, “Supported actions”.
| Option | Description |
|---|---|
reboot | Reboot the system, losing the core in the process. |
halt | Halt the system. |
poweroff | Power off the system. |
shell | Run the msh session from within the initramfs, allowing a user to record the core manually. |
mount_root_run_init | Enable the default failback behavior from Red Hat Enterprise Linux 6.2 and earlier. |
default halt
default haltEnabling the Service
kdump daemon at boot time, type the following at a shell prompt as root:
chkconfig kdump on
chkconfig kdump on2, 3, 4, and 5. Similarly, typing chkconfig kdump off will disable it for all runlevels. To start the service in the current session, use the following command as root:
service kdump start
service kdump start32.2.4. Testing the Configuration
Warning
kdump enabled, and make sure that the service is running (see Section 12.3, “Running Services” for more information on how to run a service in Red Hat Enterprise Linux):
service kdump status Kdump is operational
~]# service kdump status
Kdump is operationalecho 1 > /proc/sys/kernel/sysrq echo c > /proc/sysrq-trigger
echo 1 > /proc/sys/kernel/sysrq
echo c > /proc/sysrq-triggeraddress-YYYY-MM-DD-HH:MM:SS/vmcore file will be copied to the location you have selected in the configuration (that is, to /var/crash/ by default).
32.3. Analyzing the Core Dump
netdump, diskdump, xendump, or kdump.
Important
vmcore dump file, you must have the crash and kernel-debuginfo packages installed. To install the crash package in your system, type the following at a shell prompt as root:
yum install crash
yum install crashroot:
debuginfo-install kernel
debuginfo-install kernelrhel-6-variant-debug-rpms repository as described in Section 8.4.4, “Viewing the Current Configuration”. If your system is registered with RHN Classic, subscribe the system to the rhel-architecture-variant-6-debuginfo channel as documented here: https://access.redhat.com/site/solutions/9907.
32.3.1. Running the crash Utility
crash /usr/lib/debug/lib/modules/kernel/vmlinux /var/crash/timestamp/vmcore
crash /usr/lib/debug/lib/modules/kernel/vmlinux /var/crash/timestamp/vmcorekdump. To find out which kernel you are currently running, use the uname -r command.
Example 32.2. Running the crash utility
32.3.2. Displaying the Message Buffer
log command at the interactive prompt.
Example 32.3. Displaying the kernel message buffer
help log for more information on the command usage.
Note
vmcore-dmesg.txt file. This is useful when an attempt to get the full vmcore file failed, for example because of lack of space on the target location. By default, vmcore-dmesg.txt is located in the /var/crash/ directory.
32.3.3. Displaying a Backtrace
bt command at the interactive prompt. You can use bt pid to display the backtrace of the selected process.
Example 32.4. Displaying the kernel stack trace
help bt for more information on the command usage.
32.3.4. Displaying a Process Status
ps command at the interactive prompt. You can use ps pid to display the status of the selected process.
Example 32.5. Displaying status of processes in the system
help ps for more information on the command usage.
32.3.5. Displaying Virtual Memory Information
vm command at the interactive prompt. You can use vm pid to display information on the selected process.
Example 32.6. Displaying virtual memory information of the current context
help vm for more information on the command usage.
32.3.6. Displaying Open Files
files command at the interactive prompt. You can use files pid to display files opened by the selected process.
Example 32.7. Displaying information about open files of the current context
help files for more information on the command usage.
32.3.7. Exiting the Utility
exit or q.
Example 32.8. Exiting the crash utility
crash> exit ~]#
crash> exit
~]#32.4. Using fadump on IBM PowerPC hardware
kdump, the firmware-assisted dump (fadump), is available. The fadump feature is supported only on IBM Power Systems. The goal of fadump is to enable the dump of a crashed system, and to do so from a fully-reset system, and to minimize the total elapsed time until the system is back in production use. The fadump feature is integrated with kdump infrastructure present in the user space to seemlessly switch between kdump and fadump mechanisms.
fadump) is a reliable alternative to kexec-kdump available on IBM PowerPC LPARS. It captures vmcore from a fully-reset system with PCI and I/O devices reinitialized. While this mechanism uses the firmware to preserve the memory in case of a crash, it reuses the kdump userspace scripts to save the vmcore"
fadump registers the regions of memory that must be preserved in the event of a crash with the system firmware. These regions consist of all the system memory contents, except the boot memory, system registers and hardware Page Table Entries (PTEs).
Note
boot memory is the amount of RAM required to successfully boot the kernel after a crash event. By default, the boot memory size is 256MB or 5% of total system RAM, whichever is larger.
kexec-initiated event, the fadump process uses the production kernel to recover a crash dump. When booting after a crash, PowerPC hardware makes the device node /proc/device-tree/rtas/ibm,kernel-dump available to procfs, which the fadump-aware kdump scripts check for to save the vmcore. After this has completed, the system is rebooted cleanly.
Enabling fadump
- Install and configure
kdumpas described in Section 32.1, “Installing the kdump Service” and Section 32.2, “Configuring the kdump Service”. - Add
fadump=onto theGRUB_CMDLINE_LINUXline in/etc/default/grub:GRUB_CMDLINE_LINUX="rd.lvm.lv=rhel/swap crashkernel=auto rd.lvm.lv=rhel/root rhgb quiet fadump=on"
GRUB_CMDLINE_LINUX="rd.lvm.lv=rhel/swap crashkernel=auto rd.lvm.lv=rhel/root rhgb quiet fadump=on"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - (optional) If you want to specify reserved boot memory instead of accepting the defaults, add
fadump_reserve_mem=xxMtoGRUB_CMDLINE_LINUXin/etc/default/grub, where xx is the amount of the memory required in megabytes:GRUB_CMDLINE_LINUX="rd.lvm.lv=rhel/swap crashkernel=auto rd.lvm.lv=rhel/root rhgb quiet fadump=on fadump_reserve_mem=xxM"
GRUB_CMDLINE_LINUX="rd.lvm.lv=rhel/swap crashkernel=auto rd.lvm.lv=rhel/root rhgb quiet fadump=on fadump_reserve_mem=xxM"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Important
fadump_reserve_mem= until the crash kernel can boot cleanly. Some trial and error may be required in this case.
32.5. Using sadump on Fujitsu PRIMEQUEST systems
Note
- Red Hat Enterprise Linux panic or hang before kdump starts
- An error while kdump is working
How to use sadump
- Install the following packages according to the kernel version in use:
yum install kernel-debuginfo kernel-debuginfo-common
# yum install kernel-debuginfo kernel-debuginfo-commonCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure UEFI for sadumpFor more details, see the FUJITSU Server PRIMEQUEST 2000 Series Installation Manual.
- Configure Red Hat Enterprise Linux for sadumpFor more details, see Section 32.5.1, “Configure Red Hat Enterprise Linux for sadump”.
- Start sadumpFor more details, see the FUJITSU Server PRIMEQUEST 2000 Series Installation Manual.
- Check the memory dumpFor more details, see Section 32.5.2, “Check the memory dump”.
32.5.1. Configure Red Hat Enterprise Linux for sadump
- Install and configure
kdumpas described in Section 32.1, “Installing the kdump Service” and Section 32.2, “Configuring the kdump Service”. - Ensure that
kdumpstarts as expected for sadump:- Configure Red Hat Enterprise Linux to not reboot after a kernel panic:By default, Red Hat Enterprise Linux reboots automatically after a kernel panic, which prevents sadump to start. To avoid this behavior, configure the
/etc/sysctl.conffile as follows:kernel.panic=0
kernel.panic=0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure Red Hat Enterprise Linux to start kdump by Nonmaskable Interrupt (NMI):In the procedure of starting sadump, starting kdump by NMI is needed at first.Configure
/etc/sysctl.confas follows:kernel.unknown_nmi_panic=1
kernel.unknown_nmi_panic=1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Ensure that
kdumpbehaves correctly for sadump:- Configure Red Hat Enterprise Linux to stop after kdump:By default, Red Hat Enterprise Linux reboots automatically when kdump fails, which prevents sadump to start. To avoid this behavior, configure the
/etc/kdump.conffile as follows:default halt
default haltCopy to Clipboard Copied! Toggle word wrap Toggle overflow ordefault shell
default shellCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure Red Hat Enterprise Linux to start sadump:Configure
/etc/kdump.confto not block the System Management Interrupt (SMI) and thus to enable sadump to start:blacklist kvm-intel
blacklist kvm-intelCopy to Clipboard Copied! Toggle word wrap Toggle overflow
32.5.2. Check the memory dump
crash command by opening the special device file.
Example 32.9. Checking Dump Integrity
crash /usr/lib/debug/lib/modules/2.6.32-358.el6.x86_64/vmlinux /dev/sdb1
crash /usr/lib/debug/lib/modules/2.6.32-358.el6.x86_64/vmlinux /dev/sdb1
32.6. Additional Resources
Installed Documentation
- kdump.conf(5) — a manual page for the
/etc/kdump.confconfiguration file containing the full documentation of available options. - makedumpfile(8) — a manual page for the
makedumpfilecore collector. - kexec(8) — a manual page for kexec.
- crash(8) — a manual page for the crash utility.
/usr/share/doc/kexec-tools-version/kexec-kdump-howto.txt— an overview of thekdumpand kexec installation and usage./usr/share/doc/kexec-tools-version/fadump-howto.txt— more details about the fadump mechanism, including PowerPC-specific methods of resetting hardware. Replace version with kexec-tools version installed on your system.
Useful Websites
- https://access.redhat.com/kb/docs/DOC-6039
- The Red Hat Knowledgebase article about the
kexecandkdumpconfiguration. - https://access.redhat.com/kb/docs/DOC-45183
- The Red Hat Knowledgebase article about supported
kdumptargets. - http://people.redhat.com/anderson/
- The crash utility homepage.
Part IX. System Recovery
Chapter 33. System Recovery
rescue mode, single-user mode, and emergency mode that can be used to repair malfunctioning systems. This chapter describes how to boot into each system recovery mode and gives guidance to resolve certain problems that can only be solved with help of system recovery modes.
- You are unable to boot normally into Red Hat Enterprise Linux (runlevel 3 or 5).
- You need to resolve hardware or software problems that cannot be resolved while the system is running normally, or you want to access some important files off of your hard drive.
- You forgot the root password.
33.1. Rescue Mode
Rescue mode provides the ability to boot a small Red Hat Enterprise Linux environment entirely from external media, such as CD-ROM or USB drive, instead of the system's hard drive. It contains command-line utilities for repairing a wide variety of issues. In this mode, you can mount file systems as read-only or even to not mount them at all, blacklist or add drivers provided on a driver disc, install or upgrade system packages, or manage partitions.
rescue mode follow this procedure:
Procedure 33.1. Booting into Rescue Mode
- Boot the system from either minimal boot media, or a full installation DVD or USB drive, and wait for the boot menu to appear. For details about booting the system from the chosen media, see the respective chapters in the Installation Guide.
- From the boot menu, append the
rescuekeyword as a kernel parameter to the boot command line. - If your system requires a third-party driver provided on a driver disc to boot, append the additional option
ddto the boot command line to load that driver:rescue dd
rescue ddCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information about using a disc driver at boot time, see the respective chapters in the Installation Guide. - If a driver that is a part of the Red Hat Enterprise Linux 6 distribution prevents the system from booting, blacklist that driver by appending the
rdblacklistoption to the boot command line:rescue rdblacklist=driver_name
rescue rdblacklist=driver_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Answer a few basic questions and select the location of a valid rescue image as you are prompted to. Select the relevant type from Local CD-ROM, Hard Drive, NFS image, FTP, or HTTP. The selected location must contain a valid installation tree, and the installation tree must be for the same version of Red Hat Enterprise Linux as is the disk from which you booted. For more information about how to setup an installation tree on a hard drive, NFS server, FTP server, or HTTP server, see the respective chapters in the Installation Guide.If you select a rescue image that does not require a network connection, you are asked whether or not you want to establish a network connection. A network connection is useful if you need to backup files to a different computer or install some RPM packages from a shared network location.
- The following message is displayed:
The rescue environment will now attempt to find your Linux installation and mount it under the directory /mnt/sysimage. You can then make any changes required to your system. If you want to proceed with this step choose 'Continue'. You can also choose to mount your file systems read-only instead of read-write by choosing 'Read-only'. If for some reason this process fails you can choose 'Skip' and this step will be skipped and you will go directly to a command shell.
The rescue environment will now attempt to find your Linux installation and mount it under the directory /mnt/sysimage. You can then make any changes required to your system. If you want to proceed with this step choose 'Continue'. You can also choose to mount your file systems read-only instead of read-write by choosing 'Read-only'. If for some reason this process fails you can choose 'Skip' and this step will be skipped and you will go directly to a command shell.Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you select , the system attempts to mount your root partition under the/mnt/sysimage/directory. The root partition typically contains several file systems, such as/home/,/boot/, and/var/, which are automatically mounted to the correct locations. If mounting the partition fails, you will be notified. If you select , the system attempts to mount your file systems under the directory/mnt/sysimage/, but in read-only mode. If you select , your file systems will not be mounted. Choose if you think your file system is corrupted. - Once you have your system in rescue mode, the following prompt appears on the virtual console (VC) 1 and VC 2. Use the Ctrl-Alt-F1 key combination to access VC 1 and Ctrl-Alt-F2 to access VC 2:
sh-3.00b#
sh-3.00b#Copy to Clipboard Copied! Toggle word wrap Toggle overflow
single-user mode.
rescue mode is a temporary root partition, not the root partition of the file system used during normal user mode (runlevel 3 or 5). If you selected to mount your file system and it mounted successfully, you can change the root partition of the rescue mode environment to the root partition of your file system by executing the following command:
sh-3.00b# chroot /mnt/sysimage
sh-3.00b# chroot /mnt/sysimagerpm, that require your root partition to be mounted as /. To exit the chroot environment, type exit to return to the prompt.
rescue mode by creating a directory and typing the following command:
sh-3.00b# mkdir /directory sh-3.00b# mount -t ext4 /dev/mapper/VolGroup00-LogVol02 /directory
sh-3.00b# mkdir /directory
sh-3.00b# mount -t ext4 /dev/mapper/VolGroup00-LogVol02 /directory/directory is a directory that you have created and /dev/mapper/VolGroup00-LogVol02 is the LVM2 logical volume you want to mount. If the partition is of ext2 or ext3 type, replace ext4 with ext2 or ext3 respectively.
sh-3.00b# fdisk -l
sh-3.00b# fdisk -lpvdisplay, vgdisplay or lvdisplay commands, respectively.
ssh,scp, andpingif the network is starteddumpandrestorefor users with tape drivespartedandfdiskfor managing partitionsrpmfor installing or upgrading softwarevifor editing text files
33.2. Single-User Mode
Single-user mode provides a Linux environment for a single user that allows you to recover your system from problems that cannot be resolved in networked multi-user environment. You do not need an external boot device to be able to boot into single-user mode, and you can switch into it directly while the system is running. To switch into single-user mode on the running system, issue the following command from the command line:
init 1
~]# init 1single-user mode, the system boots with your local file systems mounted, many important services running, and a usable maintenance shell that allows you to perform many of the usual system commands. Therefore, single-user mode is mostly useful for resolving problems when the system boots but does not function properly or you cannot log into it.
Warning
single-user mode automatically tries to mount your local file systems. Booting to single-user mode could result in loss of data if any of your local file systems cannot be successfully mounted.
single-user mode follow this procedure:
Procedure 33.2. Booting into Single-User Mode
- At the GRUB boot screen, press any key to enter the GRUB interactive menu.
- Select Red Hat Enterprise Linux with the version of the kernel that you want to boot and press the a to append the line.
- Type
singleas a separate word at the end of the line and press Enter to exit GRUB edit mode. Alternatively, you can type1instead of single.
33.3. Emergency Mode
Emergency mode, provides the minimal bootable environment and allows you to repair your system even in situations when rescue mode is unavailable. In emergency mode, the system mounts only the root file system, and it is mounted as read-only. Also, the system does not activate any network interfaces and only a minimum of the essential services are set up. The system does not load any init scripts, therefore you can still mount file systems to recover data that would be lost during a re-installation if init is corrupted or not working.
emergency mode follow this procedure:
Procedure 33.3. Booting into Emergency Mode
- At the GRUB boot screen, press any key to enter the GRUB interactive menu.
- Select Red Hat Enterprise Linux with the version of the kernel that you want to boot and press the a to append the line.
- Type
emergencyas a separate word at the end of the line and press Enter to exit GRUB edit mode.
33.4. Resolving Problems in System Recovery Modes
root password:
Procedure 33.4. Resetting a Root Password
- Boot to
single-user modeas described in Procedure 33.2, “Booting into Single-User Mode”. - Run the
passwdcommand from the maintenance shell command line.
rescue mode.
Procedure 33.5. Reinstalling the GRUB Boot Loader
- Boot to
rescue modeas described in Procedure 33.1, “Booting into Rescue Mode”. Ensure that you mount the system's root partition in read-write mode. - Execute the following command to change the root partition:
sh-3.00b# chroot /mnt/sysimage
sh-3.00b# chroot /mnt/sysimageCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the following command to reinstall the GRUB boot loader:
sh-3.00b# /sbin/grub-install boot_part
sh-3.00b# /sbin/grub-install boot_partCopy to Clipboard Copied! Toggle word wrap Toggle overflow where boot_part is your boot partition (typically,/dev/sda). - Review the
/boot/grub/grub.conffile, as additional entries may be needed for GRUB to control additional operating systems. - Reboot the system.
rescue mode and modify the /boot/grub/grub.conf file.
rescue mode. If you cannot remove a malfunctioning driver for some reason, you can instead blacklist the driver so that it does not load at boot time.
Note
Procedure 33.6. Remove a Driver in Rescue Mode
- Boot to
rescue modeas described in Procedure 33.1, “Booting into Rescue Mode”. Ensure that you mount the system's root partition in read-write mode. - Change the root directory to
/mnt/sysimage/:sh-3.00b# chroot /mnt/sysimage
sh-3.00b# chroot /mnt/sysimageCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the following command to remove the driver package:
sh-3.00b# rpm -e driver_name
sh-3.00b# rpm -e driver_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Exit the
chrootenvironment:sh-3.00b# exit
sh-3.00b# exitCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot the system.
Procedure 33.7. Installing a Driver in Rescue Mode
- Boot to
rescue modeas described in Procedure 33.1, “Booting into Rescue Mode”. Ensure that you mount the system's root partition in read-write mode. - Mount a media with an RPM package that contains the driver and copy the package to a location of your choice under the
/mnt/sysimage/directory, for example:/mnt/sysimage/root/drivers/. - Change the root directory to
/mnt/sysimage/:sh-3.00b# chroot /mnt/sysimage
sh-3.00b# chroot /mnt/sysimageCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the following command to install the driver package:
sh-3.00b# rpm -ihv /root/drivers/package_name
sh-3.00b# rpm -ihv /root/drivers/package_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that/root/drivers/in this chroot environment is/mnt/sysimage/root/drivers/in the original rescue environment. - Exit the
chrootenvironment:sh-3.00b# exit
sh-3.00b# exitCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot the system.
Procedure 33.8. Blacklisting a Driver in Rescue Mode
- Boot to
rescue modewith the commandlinux rescue rdblacklist=driver_name, where driver_name is the driver that you need to blacklist. Follow the instructions in Procedure 33.1, “Booting into Rescue Mode” and ensure that you mount the system's root partition in read-write mode. - Open the
/boot/grub/grub.conffile in the vi editor:sh-3.00b# vi /boot/grub/grub.conf
sh-3.00b# vi /boot/grub/grub.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Identify the default kernel used to boot the system. Each kernel is specified in the
grub.conffile with a group of lines that beginstitle. The default kernel is specified by thedefaultparameter near the start of the file. A value of0refers to the kernel described in the first group of lines, a value of1refers to the kernel described in the second group, and higher values refer to subsequent kernels in turn. - Edit the
kernelline of the group to include the optionrdblacklist=driver_name, where driver_name is the driver that you need to blacklist. For example:kernel /vmlinuz-2.6.32-71.18-2.el6.i686 ro root=/dev/sda1 rhgb quiet rdblacklist=driver_name
kernel /vmlinuz-2.6.32-71.18-2.el6.i686 ro root=/dev/sda1 rhgb quiet rdblacklist=driver_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the file and exit the vi editor by typing:
:wq
:wqCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the following command to create a new file
/etc/modprobe.d/driver_name.confthat will ensure blacklisting of the driver after the root partition is mounted:echo "install driver_name" > /mnt/sysimage/etc/modprobe.d/driver_name.conf
echo "install driver_name" > /mnt/sysimage/etc/modprobe.d/driver_name.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot the system.
Chapter 34. Relax-and-Recover (ReaR)
- booting a rescue system on the new hardware
- replicating the original storage layout
- restoring user and system files
rear recover command, which starts the recovery process. During this process, ReaR replicates the partition layout and filesystems, prompts for restoring user and system files from the backup created by backup software, and finally installs the boot loader. By default, the rescue system created by ReaR only restores the storage layout and the boot loader, but not the actual user and system files.
34.1. Basic ReaR Usage
34.1.1. Installing ReaR
yum install rear
~]# yum install rear34.1.2. Configuring ReaR
/etc/rear/local.conf file. Specify the rescue system configuration by adding these lines:
OUTPUT=output format OUTPUT_URL=output location
OUTPUT=output format
OUTPUT_URL=output locationISO for an ISO disk image or USB for a bootable USB.
file:///mnt/rescue_system/ for a local filesystem directory or sftp://backup:password@192.168.0.0/ for an SFTP directory.
Example 34.1. Configuring Rescue System Format and Location
/mnt/rescue_system/ directory, add these lines to the /etc/rear/local.conf file:
OUTPUT=ISO OUTPUT_URL=file:///mnt/rescue_system/
OUTPUT=ISO
OUTPUT_URL=file:///mnt/rescue_system/34.1.3. Creating a Rescue System
/mnt/rescue_system/. Because the system's host name is rhel-68, the backup location now contains directory rhel-68/ with the rescue system and auxiliary files:
34.1.4. Scheduling ReaR
/etc/crontab file:
minute hour day_of_month month day_of_week root /usr/sbin/rear mkrescue
minute hour day_of_month month day_of_week root /usr/sbin/rear mkrescueExample 34.2. Scheduling ReaR
/etc/crontab file:
0 22 * * 1-5 root /usr/sbin/rear mkrescue
0 22 * * 1-5 root /usr/sbin/rear mkrescue34.1.5. Performing a System Rescue
- Boot the rescue system on the new hardware. For example, burn the ISO image to a DVD and boot from the DVD.
- In the console interface, select the "Recover" option:
- You are taken to the prompt:
Figure 34.2. Rescue system: prompt
Warning
Once you have started recovery in the next step, it probably cannot be undone and you may lose anything stored on the physical disks of the system. - Run the
rear recovercommand to perform the restore or migration. The rescue system then recreates the partition layout and filesystems:Figure 34.3. Rescue system: running "rear recover"
- Restore user and system files from the backup into the
/mnt/local/directory.Example 34.3. Restoring User and System Files
In this example, the backup file is a tar archive created per instructions in Section 34.2.1.1, “Configuring the Internal Backup Method”. First, copy the archive from its storage, then unpack the files into/mnt/local/, then delete the archive:scp root@192.168.122.6:/srv/backup/rhel68/backup.tar.gz /mnt/local/ tar xf /mnt/local/backup.tar.gz -C /mnt/local/ rm -f /mnt/local/backup.tar.gz
~]# scp root@192.168.122.6:/srv/backup/rhel68/backup.tar.gz /mnt/local/ ~]# tar xf /mnt/local/backup.tar.gz -C /mnt/local/ ~]# rm -f /mnt/local/backup.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow The new storage has to have enough space both for the archive and the extracted files. - Verify that the files have been restored:
ls /mnt/local/
~]# ls /mnt/local/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Figure 34.4. Rescue system: restoring user and system files from the backup
- Ensure that SELinux relabels the files on the next boot:
touch /mnt/local/.autorelabel
~]# touch /mnt/local/.autorelabelCopy to Clipboard Copied! Toggle word wrap Toggle overflow Otherwise you may be unable to log in the system, because the/etc/passwdfile may have the incorrect SELinux context. - Finish the recovery and reboot the system:
Figure 34.5. Rescue system: finishing recovery
ReaR will then reinstall the boot loader. Upon reboot, SELinux will relabel the whole filesystem.Then you will be able to log in to the recovered system.
34.2. Integrating ReaR with Backup Software
34.2.1. The Built-in Backup Method
- a rescue system and a full-system backup can be created using a single
rear mkbackupcommand - the rescue system restores files from the backup automatically
34.2.1.1. Configuring the Internal Backup Method
/etc/rear/local.conf:
BACKUP=NETFS BACKUP_URL=backup location
BACKUP=NETFS
BACKUP_URL=backup locationtar command. Substitute backup location with one of the options from the "Backup Software Integration" section of the rear(8) man page. Make sure that the backup location has enough space.
Example 34.4. Adding tar Backups
/srv/backup/ directory:
OUTPUT=ISO OUTPUT_URL=file:///mnt/rescue_system/ BACKUP=NETFS BACKUP_URL=file:///srv/backup/
OUTPUT=ISO
OUTPUT_URL=file:///mnt/rescue_system/
BACKUP=NETFS
BACKUP_URL=file:///srv/backup/- To keep old backup archives when new ones are created, add this line:
NETFS_KEEP_OLD_BACKUP_COPY=y
NETFS_KEEP_OLD_BACKUP_COPY=yCopy to Clipboard Copied! Toggle word wrap Toggle overflow - By default, ReaR creates a full backup on each run. To make the backups incremental, meaning that only the changed files are backed up on each run, add this line:
BACKUP_TYPE=incremental
BACKUP_TYPE=incrementalCopy to Clipboard Copied! Toggle word wrap Toggle overflow This automatically setsNETFS_KEEP_OLD_BACKUP_COPYtoy. - To ensure that a full backup is done regularly in addition to incremental backups, add this line:
FULLBACKUPDAY="Day"
FULLBACKUPDAY="Day"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Substitute "Day" with one of the "Mon", "Tue", "Wed", "Thu". "Fri", "Sat", "Sun". - ReaR can also include both the rescue system and the backup in the ISO image. To achieve this, set the
BACKUP_URLdirective toiso:///backup/:BACKUP_URL=iso:///backup/
BACKUP_URL=iso:///backup/Copy to Clipboard Copied! Toggle word wrap Toggle overflow This is the simplest method of full-system backup, because the rescue system does not need the user to fetch the backup during recovery. However, it needs more storage. Also, single-ISO backups cannot be incremental.Note
Currently ReaR creates two copies of the ISO image, thus consuming two times more storage. For more information, see note ReaR creates two ISO images instead of one in Red Hat Enterprise Linux 6 Release Notes.Example 34.5. Configuring Single-ISO Rescue System and Backups
This configuration creates a rescue system and a backup file as a single ISO image and puts it into the/srv/backup/directory:OUTPUT=ISO OUTPUT_URL=file:///srv/backup/ BACKUP=NETFS BACKUP_URL=iso:///backup/
OUTPUT=ISO OUTPUT_URL=file:///srv/backup/ BACKUP=NETFS BACKUP_URL=iso:///backup/Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To use
rsyncinstead oftar, add this line:BACKUP_PROG=rsync
BACKUP_PROG=rsyncCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that incremental backups are only supported when usingtar.
34.2.1.2. Creating a Backup Using the Internal Backup Method
BACKUP=NETFS set, ReaR can create either a rescue system, a backup file, or both.
- To create a rescue system only, run:
rear mkrescue
rear mkrescueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To create a backup only, run:
rear mkbackuponly
rear mkbackuponlyCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To create a rescue system and a backup, run:
rear mkbackup
rear mkbackupCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Note
BACKUP=NETFS setting expects the backup to be present before executing rear recover. Hence, once the rescue system boots, copy the backup file into the directory specified in BACKUP_URL, unless using a single ISO image. Only then run rear recover.
rear checklayout echo $?
~]# rear checklayout
~]# echo $?Important
rear checklayout command does not check whether a rescue system is currently present in the output location, and can return 0 even if it is not there. So it does not guarantee that a rescue system is available, only that the layout has not changed since the last rescue system has been created.
Example 34.6. Using rear checklayout
rear checklayout || rear mkrescue
~]# rear checklayout || rear mkrescue34.2.2. Supported Backup Methods
34.2.3. Unsupported Backup Methods
- The rescue system prompts the user to manually restore the files. This scenario is the one described in "Basic ReaR Usage", except for the backup file format, which may take a different form than a tar archive.
- ReaR executes the custom commands provided by the user. To configure this, set the
BACKUPdirective toEXTERNAL. Then specify the commands to be run during backing up and restoration using theEXTERNAL_BACKUPandEXTERNAL_RESTOREdirectives. Optionally, also specify theEXTERNAL_IGNORE_ERRORSandEXTERNAL_CHECKdirectives. See/usr/share/rear/conf/default.conffor an example configuration.
Appendix A. Consistent Network Device Naming
eth[0123…], but these names do not necessarily correspond to actual labels on the chassis. Modern server platforms with multiple network adapters can encounter non-deterministic and counter-intuitive naming of these interfaces. This affects both network adapters embedded on the motherboard (Lan-on-Motherboard, or LOM) and add-in (single and multiport) adapters.
eth[0123…] to the new naming convention as shown in Table A.1, “The new naming convention”.
| Device | Old Name | New Name |
|---|---|---|
| Embedded network interface (LOM) | eth[0123…] | em[1234…][a] |
| PCI card network interface | eth[0123…] | p<slot>p<ethernet port>[b] |
| Virtual function | eth[0123…] | p<slot>p<ethernet port>_<virtual interface>[c] |
[a]
New enumeration starts at 1.
[b]
For example: p3p4
[c]
For example: p3p4_1
| ||
/etc/udev/rules.d/70-persistent-net.rules to change the device names to anything desired; those will take precedence over this physical location naming convention.
A.1. Affected Systems
Dell PowerEdge, C Series, and Precision Workstation systems. For more details regarding the impact on Dell systems, visit https://access.redhat.com/kb/docs/DOC-47318.
eth[0123…] naming convention will continue to be used.
A.2. System Requirements
base package group in Red Hat Enterprise Linux 6. All install options, except for , include this package. It is not installed on upgrades of Red Hat Enterprise Linux 6.0 to RHEL 6.1.
A.3. Enabling and Disabling the Feature
biosdevname=0
biosdevname=0biosdevname=1
biosdevname=1biosdevname install option is specified, it must remain as a boot option for the lifetime of the system.
A.4. Notes for Administrators
ksdevice parameter; these kickstart files will need to be updated to use the network device's MAC address or the network device's new name.
/etc/udev/rules.d/70-persistent-net.rules file and the HWADDR lines from all /etc/sysconfig/network-scripts/ifcfg-* files. In addition, rename those ifcfg-* files to use this new naming convention. The new names will be in effect after reboot. Remember to update any custom scripts, iptables rules, and service configuration files that might include network interface names.
Appendix B. RPM
Warning
Important
x86_64.rpm.
.tar.gz files.
Note
B.1. RPM Design Goals
- Upgradability
- With RPM, you can upgrade individual components of your system without completely reinstalling. When you get a new release of an operating system based on RPM, such as Red Hat Enterprise Linux, you do not need to reinstall a fresh copy of the operating system your machine (as you might need to with operating systems based on other packaging systems). RPM allows intelligent, fully-automated, in-place upgrades of your system. In addition, configuration files in packages are preserved across upgrades, so you do not lose your customizations. There are no special upgrade files needed to upgrade a package because the same RPM file is used to both install and upgrade the package on your system.
- Powerful Querying
- RPM is designed to provide powerful querying options. You can perform searches on your entire database for packages or even just certain files. You can also easily find out what package a file belongs to and from where the package came. The files an RPM package contains are in a compressed archive, with a custom binary header containing useful information about the package and its contents, allowing you to query individual packages quickly and easily.
- System Verification
- Another powerful RPM feature is the ability to verify packages. If you are worried that you deleted an important file for some package, you can verify the package. You are then notified of anomalies, if any—at which point you can reinstall the package, if necessary. Any configuration files that you modified are preserved during reinstallation.
- Pristine Sources
- A crucial design goal was to allow the use of pristine software sources, as distributed by the original authors of the software. With RPM, you have the pristine sources along with any patches that were used, plus complete build instructions. This is an important advantage for several reasons. For instance, if a new version of a program is released, you do not necessarily have to start from scratch to get it to compile. You can look at the patch to see what you might need to do. All the compiled-in defaults, and all of the changes that were made to get the software to build properly, are easily visible using this technique.The goal of keeping sources pristine may seem important only for developers, but it results in higher quality software for end users, too.
B.2. Using RPM
rpm --help or man rpm. You can also see Section B.5, “Additional Resources” for more information on RPM.
B.2.1. Finding RPM Packages
- The initial RPM repositories provided with the YUM package manager. See Chapter 8, Yum for details on how to use the official Red Hat Enterprise Linux package repositories.
- The Extra Packages for Enterprise Linux (EPEL) is a community effort to provide high-quality add-on packages for Red Hat Enterprise Linux. See http://fedoraproject.org/wiki/EPEL for details on EPEL RPM packages.
- Unofficial, third-party repositories not affiliated with Red Hat also provide RPM packages.
Important
When considering third-party repositories for use with your Red Hat Enterprise Linux system, pay close attention to the repository's web site with regard to package compatibility before adding the repository as a package source. Alternate package repositories may offer different, incompatible versions of the same software, including packages already included in the Red Hat Enterprise Linux repositories. - The Red Hat Errata Page, available at http://www.redhat.com/apps/support/errata/.
B.2.2. Installing and Upgrading
tree-1.5.3-2.el6.x86_64.rpm. The file name includes the package name (tree), version (1.5.3), release (2), operating system major version (el6) and CPU architecture (x86_64).
rpm's -U option to:
- upgrade an existing but older package on the system to a newer version, or
- install the package even if an older version is not already installed.
rpm -U <rpm_file> is able to perform the function of either upgrading or installing as is appropriate for the package.
tree-1.5.3-2.el6.x86_64.rpm package is in the current directory, log in as root and type the following command at a shell prompt to either upgrade or install the tree package as determined by rpm:
rpm -Uvh tree-1.5.3-2.el6.x86_64.rpm
rpm -Uvh tree-1.5.3-2.el6.x86_64.rpmNote
-v and -h options (which are combined with -U) cause rpm to print more verbose output and display a progress meter using hash signs.
Preparing... ########################################### [100%] 1:tree ########################################### [100%]
Preparing... ########################################### [100%]
1:tree ########################################### [100%]Warning
rpm provides two different options for installing packages: the aforementioned -U option (which historically stands for upgrade), and the -i option, historically standing for install. Because the -U option subsumes both install and upgrade functions, we recommend to use rpm -Uvh with all packages except kernel packages.
-i option to install a new kernel package instead of upgrading it. This is because using the -U option to upgrade a kernel package removes the previous (older) kernel package, which could render the system unable to boot if there is a problem with the new kernel. Therefore, use the rpm -i <kernel_package> command to install a new kernel without replacing any older kernel packages. For more information on installing kernel packages, see Chapter 30, Manually Upgrading the Kernel.
error: tree-1.5.3-2.el6.x86_64.rpm: Header V3 RSA/SHA256 signature: BAD, key ID d22e77f2
error: tree-1.5.3-2.el6.x86_64.rpm: Header V3 RSA/SHA256 signature: BAD, key ID
d22e77f2error: tree-1.5.3-2.el6.x86_64.rpm: Header V3 RSA/SHA256 signature: BAD, key ID d22e77f2
error: tree-1.5.3-2.el6.x86_64.rpm: Header V3 RSA/SHA256 signature: BAD,
key ID d22e77f2NOKEY:
warning: tree-1.5.3-2.el6.x86_64.rpm: Header V3 RSA/SHA1 signature: NOKEY, key ID 57bbccba
warning: tree-1.5.3-2.el6.x86_64.rpm: Header V3 RSA/SHA1 signature: NOKEY, key ID 57bbccbaB.2.2.1. Package Already Installed
Preparing... ########################################### [100%] package tree-1.5.3-2.el6.x86_64 is already installed
Preparing... ########################################### [100%]
package tree-1.5.3-2.el6.x86_64 is already installed--replacepkgs option, which tells RPM to ignore the error:
rpm -Uvh --replacepkgs tree-1.5.3-2.el6.x86_64.rpm
rpm -Uvh --replacepkgs tree-1.5.3-2.el6.x86_64.rpmB.2.2.2. Conflicting Files
Preparing... ################################################## file /usr/bin/foobar from install of foo-1.0-1.el6.x86_64 conflicts with file from package bar-3.1.1.el6.x86_64
Preparing... ##################################################
file /usr/bin/foobar from install of foo-1.0-1.el6.x86_64 conflicts
with file from package bar-3.1.1.el6.x86_64--replacefiles option:
rpm -Uvh --replacefiles foo-1.0-1.el6.x86_64.rpm
rpm -Uvh --replacefiles foo-1.0-1.el6.x86_64.rpmB.2.2.3. Unresolved Dependency
error: Failed dependencies: bar.so.3()(64bit) is needed by foo-1.0-1.el6.x86_64
error: Failed dependencies:
bar.so.3()(64bit) is needed by foo-1.0-1.el6.x86_64rpm -Uvh foo-1.0-1.el6.x86_64.rpm bar-3.1.1.el6.x86_64.rpm
rpm -Uvh foo-1.0-1.el6.x86_64.rpm bar-3.1.1.el6.x86_64.rpmPreparing... ########################################### [100%] 1:foo ########################################### [ 50%] 2:bar ########################################### [100%]
Preparing... ########################################### [100%]
1:foo ########################################### [ 50%]
2:bar ########################################### [100%]--whatprovides option to determine which package contains the required file.
rpm -q --whatprovides "bar.so.3"
rpm -q --whatprovides "bar.so.3"bar.so.3 is in the RPM database, the name of the package is displayed:
bar-3.1.1.el6.i586.rpm
bar-3.1.1.el6.i586.rpmWarning
rpm to install a package that gives us a Failed dependencies error (using the --nodeps option), this is not recommended, and will usually result in the installed package failing to run. Installing or removing packages with rpm --nodeps can cause applications to misbehave and/or crash, and can cause serious package management problems or, possibly, system failure. For these reasons, it is best to heed such warnings; the package manager—whether RPM, Yum or PackageKit—shows us these warnings and suggests possible fixes because accounting for dependencies is critical. The Yum package manager can perform dependency resolution and fetch dependencies from online repositories, making it safer, easier and smarter than forcing rpm to carry out actions without regard to resolving dependencies.
B.2.3. Configuration File Changes
saving /etc/foo.conf as /etc/foo.conf.rpmsave
saving /etc/foo.conf as /etc/foo.conf.rpmsavefoo.conf.rpmnew, and leave the configuration file you modified untouched. You should still resolve any conflicts between your modified configuration file and the new one, usually by merging changes from the old one to the new one with a diff program.
package foo-2.0-1.el6.x86_64.rpm (which is newer than foo-1.0-1) is already installed
package foo-2.0-1.el6.x86_64.rpm (which is newer than foo-1.0-1) is already installed--oldpackage option:
rpm -Uvh --oldpackage foo-1.0-1.el6.x86_64.rpm
rpm -Uvh --oldpackage foo-1.0-1.el6.x86_64.rpmB.2.4. Uninstalling
rpm -e foo
rpm -e fooNote
foo, not the name of the original package file, foo-1.0-1.el6.x86_64. If you attempt to uninstall a package using the rpm -e command and the original full file name, you will receive a package name error.
<library_name>.so.<number> file) in Section B.2.2.3, “Unresolved Dependency”, we can search for a 64-bit shared object library using this exact syntax (and making sure to quote the file name):
rpm -q --whatprovides "libgs.so.8()(64bit)" ghostscript-8.70-1.el6.x86_64
~]# rpm -q --whatprovides "libgs.so.8()(64bit)"
ghostscript-8.70-1.el6.x86_64Warning
rpm to remove a package that gives us a Failed dependencies error (using the --nodeps option), this is not recommended, and may cause harm to other installed applications. Installing or removing packages with rpm --nodeps can cause applications to misbehave and/or crash, and can cause serious package management problems or, possibly, system failure. For these reasons, it is best to heed such warnings; the package manager—whether RPM, Yum or PackageKit—shows us these warnings and suggests possible fixes because accounting for dependencies is critical. The Yum package manager can perform dependency resolution and fetch dependencies from online repositories, making it safer, easier and smarter than forcing rpm to carry out actions without regard to resolving dependencies.
B.2.5. Freshening
rpm -Fvh foo-2.0-1.el6.x86_64.rpm
rpm -Fvh foo-2.0-1.el6.x86_64.rpm*.rpm glob:
rpm -Fvh *.rpm
rpm -Fvh *.rpmB.2.6. Querying
/var/lib/rpm/, and is used to query what packages are installed, what versions each package is, and to calculate any changes to any files in the package since installation, among other use cases.
-q option. The rpm -q package name command displays the package name, version, and release number of the installed package <package_name>. For example, using rpm -q tree to query installed package tree might generate the following output:
tree-1.5.2.2-4.el6.x86_64
tree-1.5.2.2-4.el6.x86_64man rpm for details) to further refine or qualify your query:
-a— queries all currently installed packages.-f— queries the RPM database for which package owns<file_name><file_name>. Specify the absolute path of the file (for example,rpm -qfinstead of/bin/lsrpm -qf ls).-p— queries the uninstalled package<package_file><package_file>.
-idisplays package information including name, description, release, size, build date, install date, vendor, and other miscellaneous information.-ldisplays the list of files that the package contains.-sdisplays the state of all the files in the package.-ddisplays a list of files marked as documentation (man pages, info pages, READMEs, etc.) in the package.-cdisplays a list of files marked as configuration files. These are the files you edit after installation to adapt and customize the package to your system (for example,sendmail.cf,passwd,inittab, etc.).
-v to the command to display the lists in a familiar ls -l format.
B.2.7. Verifying
rpm -V verifies a package. You can use any of the Verify Options listed for querying to specify the packages you want to verify. A simple use of verifying is rpm -V tree, which verifies that all the files in the tree package are as they were when they were originally installed. For example:
- To verify a package containing a particular file:
rpm -Vf /usr/bin/tree
rpm -Vf /usr/bin/treeCopy to Clipboard Copied! Toggle word wrap Toggle overflow In this example,/usr/bin/treeis the absolute path to the file used to query a package. - To verify ALL installed packages throughout the system (which will take some time):
rpm -Va
rpm -VaCopy to Clipboard Copied! Toggle word wrap Toggle overflow - To verify an installed package against an RPM package file:
rpm -Vp tree-1.5.3-2.el6.x86_64.rpm
rpm -Vp tree-1.5.3-2.el6.x86_64.rpmCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command can be useful if you suspect that your RPM database is corrupt.
c" denotes a configuration file) and then the file name. Each of the eight characters denotes the result of a comparison of one attribute of the file to the value of that attribute recorded in the RPM database. A single period (.) means the test passed. The following characters denote specific discrepancies:
5— MD5 checksumS— file sizeL— symbolic linkT— file modification timeD— deviceU— userG— groupM— mode (includes permissions and file type)?— unreadable file (file permission errors, for example)
B.3. Checking a Package's Signature
rpm -K --nosignature <rpm_file>
rpm -K --nosignature <rpm_file><rpm_file>: rsa sha1 (md5) pgp md5 OK (specifically the OK part of it) is displayed. This brief message means that the file was not corrupted during download. To see a more verbose message, replace -K with -Kvv in the command.
B.3.1. Importing Keys
rpm --import /usr/share/rhn/RPM-GPG-KEY
rpm --import /usr/share/rhn/RPM-GPG-KEYrpm -qa gpg-pubkey*
rpm -qa gpg-pubkey*gpg-pubkey-db42a60e-37ea5438
gpg-pubkey-db42a60e-37ea5438rpm -qi followed by the output from the previous command:
rpm -qi gpg-pubkey-db42a60e-37ea5438
rpm -qi gpg-pubkey-db42a60e-37ea5438B.3.2. Verifying Signature of Packages
rpm -K <rpm-file>
rpm -K <rpm-file>md5 gpg OK. This means that the signature of the package has been verified, that it is not corrupt, and therefore is safe to install and use.
B.4. Practical and Common Examples of RPM Usage
- Perhaps you have deleted some files by accident, but you are not sure what you deleted. To verify your entire system and see what might be missing, you could try the following command:
rpm -Va
rpm -VaCopy to Clipboard Copied! Toggle word wrap Toggle overflow If some files are missing or appear to have been corrupted, you should probably either re-install the package or uninstall and then re-install the package. - At some point, you might see a file that you do not recognize. To find out which package owns it, enter:
rpm -qf /usr/bin/ghostscript
rpm -qf /usr/bin/ghostscriptCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output would look like the following:ghostscript-8.70-1.el6.x86_64
ghostscript-8.70-1.el6.x86_64Copy to Clipboard Copied! Toggle word wrap Toggle overflow - We can combine the above two examples in the following scenario. Say you are having problems with
/usr/bin/paste. You would like to verify the package that owns that program, but you do not know which package ownspaste. Enter the following command,rpm -Vf /usr/bin/paste
rpm -Vf /usr/bin/pasteCopy to Clipboard Copied! Toggle word wrap Toggle overflow and the appropriate package is verified. - Do you want to find out more information about a particular program? You can try the following command to locate the documentation which came with the package that owns that program:
rpm -qdf /usr/bin/free
rpm -qdf /usr/bin/freeCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output would be similar to the following:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - You may find a new RPM, but you do not know what it does. To find information about it, use the following command:
rpm -qip crontabs-1.10-32.1.el6.noarch.rpm
rpm -qip crontabs-1.10-32.1.el6.noarch.rpmCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output would be similar to the following:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Perhaps you now want to see what files the
crontabsRPM package installs. You would enter the following:rpm -qlp crontabs-1.10-32.1.el6.noarch.rpm
rpm -qlp crontabs-1.10-32.1.el6.noarch.rpmCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output is similar to the following:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
B.5. Additional Resources
B.5.1. Installed Documentation
rpm --help— This command displays a quick reference of RPM parameters.man rpm— The RPM man page gives more detail about RPM parameters than therpm --helpcommand.
B.5.2. Useful Websites
- The RPM website — http://www.rpm.org/
- The RPM mailing list can be subscribed to, and its archives read from, here — https://lists.rpm.org/mailman/listinfo/rpm-list
Appendix C. The X Window System
Xorg binary) listens for connections from X client applications via a network or local loopback interface. The server communicates with the hardware, such as the video card, monitor, keyboard, and mouse. X client applications exist in the user space, creating a graphical user interface (GUI) for the user and passing user requests to the X server.
C.1. The X Server
evdev, that supports all input devices that the kernel knows about, including most mice and keyboards.
/usr/ directory. The /etc/X11/ directory contains configuration files for X client and server applications. This includes configuration files for the X server itself, the X display managers, and many other base components.
/etc/fonts/fonts.conf. For more information on configuring and adding fonts, see Section C.4, “Fonts”.
C.2. Desktop Environments and Window Managers
C.2.1. Maximum number of concurrent GUI sessions
C.2.2. Desktop Environments
- GNOME — The default desktop environment for Red Hat Enterprise Linux based on the GTK+ 2 graphical toolkit.
- KDE — An alternative desktop environment based on the Qt 4 graphical toolkit.
C.2.3. Window Managers
-
metacity - The Metacity window manager is the default window manager for GNOME. It is a simple and efficient window manager which supports custom themes. This window manager is automatically pulled in as a dependency when the GNOME desktop is installed.
-
kwin - The KWin window manager is the default window manager for KDE. It is an efficient window manager which supports custom themes. This window manager is automatically pulled in as a dependency when the KDE desktop is installed.
-
compiz - The Compiz compositing window manager is based on OpenGL and can use 3D graphics hardware to create fast compositing desktop effects for window management. Advanced features, such as a cube workspace, are implemented as loadable plug-ins. To run this window manager, you need to install the compiz package.
-
mwm - The Motif Window Manager (
mwm) is a basic, stand-alone window manager. Since it is designed to be stand-alone, it should not be used in conjunction with GNOME or KDE. To run this window manager, you need to install the openmotif package. -
twm - The minimalist Tab Window Manager (
twm), which provides the most basic tool set among the available window managers, can be used either as a stand-alone or with a desktop environment. To run this window manager, you need to install the xorg-x11-twm package.
C.3. X Server Configuration Files
/usr/bin/Xorg; a symbolic link X pointing to this file is also provided. Associated configuration files are stored in the /etc/X11/ and /usr/share/X11/ directories.
xorg.conf.d directory contain preconfigured settings from vendors and from distribution, and these files should not be edited by hand. Configuration in the xorg.conf file, on the other hand, is done completely by hand but is not necessary in most scenarios.
Note
/etc/X11/xorg.conf, that was necessary in previous releases, is not supplied with the current release of the X Window System. It can still be useful to create the file manually to configure new hardware, to set up an environment with multiple video cards, or for debugging purposes.
/usr/lib/xorg/modules/ (or /usr/lib64/xorg/modules/) directory contains X server modules that can be loaded dynamically at runtime. By default, only some modules in /usr/lib/xorg/modules/ are automatically loaded by the X server.
mouse, kbd, or vmmouse driver configured in the xorg.conf file are, by default, ignored by the X server. See Section C.3.3.3, “The ServerFlags section” for further details. Additional configuration is provided in the /etc/X11/xorg.conf.d/ directory and it can override or augment any configuration that has been obtained through HAL.
C.3.1. The Structure of the Configuration
Section "section-name" line, where "section-name" is the title for the section, and ends with an EndSection line. Each section contains lines that include option names and one or more option values. Some of these are sometimes enclosed in double quotes (").
/etc/X11/xorg.conf file accept a Boolean switch which turns the feature on or off. The acceptable values are:
1,on,true, oryes— Turns the option on.0,off,false, orno— Turns the option off.
#) are not read by the X server and are used for human-readable comments.
C.3.2. The xorg.conf.d Directory
/usr/share/X11/xorg.conf.d/ provides separate configuration files from vendors or third-party packages; changes to files in this directory may be overwritten by settings specified in the /etc/X11/xorg.conf file. The /etc/X11/xorg.conf.d/ directory stores user-specific configuration.
.conf in configuration directories are parsed by the X server upon startup and are treated like part of the traditional xorg.conf configuration file. These files may contain one or more sections; for a description of the options in a section and the general layout of the configuration file, see Section C.3.3, “The xorg.conf File” or to the xorg.conf(5) man page. The X server essentially treats the collection of configuration files as one big file with entries from xorg.conf at the end. Users are encouraged to put custom configuration into /etc/xorg.conf and leave the directory for configuration snippets provided by the distribution.
C.3.3. The xorg.conf File
/etc/X11/xorg.conf file was used to store initial setup for X. When a change occurred with the monitor, video card or other device managed by the X server, the file needed to be edited manually. In Red Hat Enterprise Linux, there is rarely a need to manually create and edit the /etc/X11/xorg.conf file. Nevertheless, it is still useful to understand various sections and optional parameters available, especially when troubleshooting or setting up unusual hardware configuration.
/etc/X11/xorg.conf file. More detailed information about the X server configuration file can be found in the xorg.conf(5) man page. This section is mostly intended for advanced users as most configuration options described below are not needed in typical configuration scenarios.
C.3.3.1. The InputClass section
InputClass is a new type of configuration section that does not apply to a single device but rather to a class of devices, including hot-plugged devices. An InputClass section's scope is limited by the matches specified; in order to apply to an input device, all matches must apply to the device as seen in the example below:
Section "InputClass" Identifier "touchpad catchall" MatchIsTouchpad "on" Driver "synaptics" EndSection
Section "InputClass"
Identifier "touchpad catchall"
MatchIsTouchpad "on"
Driver "synaptics"
EndSectionxorg.conf file or an xorg.conf.d directory, any touchpad present in the system is assigned the synaptics driver.
Note
xorg.conf.d directory, the Driver setting in the example above overwrites previously set driver options. The more generic the class, the earlier it should be listed.
InputClass section:
MatchIsPointer,MatchIsKeyboard,MatchIsTouchpad,MatchIsTouchscreen,MatchIsJoystick— Boolean options to specify a type of a device.MatchProduct "product_name"— this option matches if the product_name substring occurs in the product name of the device.MatchVendor "vendor_name"— this option matches if the vendor_name substring occurs in the vendor name of the device.MatchDevicePath "/path/to/device"— this option matches any device if its device path corresponds to the patterns given in the "/path/to/device" template, for example/dev/input/event*. See thefnmatch(3)man page for further details.MatchTag "tag_pattern"— this option matches if at least one tag assigned by the HAL configuration back end matches the tag_pattern pattern.
InputClass sections. These sections are optional and are used to configure a class of input devices as they are automatically added. An input device can match more than one InputClass section. When arranging these sections, it is recommended to put generic matches above specific ones because each input class can override settings from a previous one if an overlap occurs.
C.3.3.2. The InputDevice section
InputDevice section configures one input device for the X server. Previously, systems typically had at least one InputDevice section for the keyboard, and most mouse settings were automatically detected.
InputDevice configuration is needed for most setups, and the xorg-x11-drv-* input driver packages provide the automatic configuration through HAL. The default driver for both keyboards and mice is evdev.
InputDevice section for a keyboard:
InputDevice section:
Identifier— Specifies a unique name for thisInputDevicesection. This is a required entry.Driver— Specifies the name of the device driver X must load for the device. If theAutoAddDevicesoption is enabled (which is the default setting), any input device section withDriver "mouse"orDriver "kbd"will be ignored. This is necessary due to conflicts between the legacy mouse and keyboard drivers and the newevdevgeneric driver. Instead, the server will use the information from the back end for any input devices. Any custom input device configuration in thexorg.confshould be moved to the back end. In most cases, the back end will be HAL and the configuration location will be the/etc/X11/xorg.conf.ddirectory.Option— Specifies necessary options pertaining to the device.A mouse may also be specified to override any auto-detected values for the device. The following options are typically included when adding a mouse in thexorg.conffile:Protocol— Specifies the protocol used by the mouse, such asIMPS/2.Device— Specifies the location of the physical device.Emulate3Buttons— Specifies whether to allow a two-button mouse to act like a three-button mouse when both mouse buttons are pressed simultaneously.
Consult thexorg.conf(5)man page for a complete list of valid options for this section.
C.3.3.3. The ServerFlags section
ServerFlags section contains miscellaneous global X server settings. Any settings in this section may be overridden by options placed in the ServerLayout section (see Section C.3.3.4, “The ServerLayout Section” for details).
ServerFlags section occupies a single line and begins with the term Option followed by an option enclosed in double quotation marks (").
ServerFlags section:
Section "ServerFlags" Option "DontZap" "true" EndSection
Section "ServerFlags"
Option "DontZap" "true"
EndSection"DontZap" "boolean"— When the value of <boolean> is set totrue, this setting prevents the use of the Ctrl+Alt+Backspace key combination to immediately terminate the X server.Note
Even if this option is enabled, the key combination still must be configured in the X Keyboard Extension (XKB) map before it can be used. One way how to add the key combination to the map is to run the following command:setxkbmap -option "terminate:ctrl_alt_bksp"
setxkbmap -option "terminate:ctrl_alt_bksp"Copy to Clipboard Copied! Toggle word wrap Toggle overflow "DontZoom" "boolean"— When the value of <boolean> is set totrue, this setting prevents cycling through configured video resolutions using the Ctrl+Alt+Keypad-Plus and Ctrl+Alt+Keypad-Minus key combinations."AutoAddDevices" "boolean"— When the value of <boolean> is set tofalse, the server will not hot plug input devices and instead rely solely on devices configured in thexorg.conffile. See Section C.3.3.2, “TheInputDevicesection” for more information concerning input devices. This option is enabled by default and HAL (hardware abstraction layer) is used as a back end for device discovery.
C.3.3.4. The ServerLayout Section
ServerLayout section binds together the input and output devices controlled by the X server. At a minimum, this section must specify one input device and one output device. By default, a monitor (output device) and a keyboard (input device) are specified.
ServerLayout section:
ServerLayout section:
Identifier— Specifies a unique name for thisServerLayoutsection.Screen— Specifies the name of aScreensection to be used with the X server. More than oneScreenoption may be present.The following is an example of a typicalScreenentry:Screen 0 "Screen0" 0 0
Screen 0 "Screen0" 0 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The first number in this exampleScreenentry (0) indicates that the first monitor connector, or head on the video card, uses the configuration specified in theScreensection with the identifier"Screen0".An example of aScreensection with the identifier"Screen0"can be found in Section C.3.3.8, “TheScreensection”.If the video card has more than one head, anotherScreenentry with a different number and a differentScreensection identifier is necessary.The numbers to the right of"Screen0"give the absolute X and Y coordinates for the upper left corner of the screen (0 0by default).InputDevice— Specifies the name of anInputDevicesection to be used with the X server.It is advisable that there be at least twoInputDeviceentries: one for the default mouse and one for the default keyboard. The optionsCorePointerandCoreKeyboardindicate that these are the primary mouse and keyboard. If theAutoAddDevicesoption is enabled, this entry needs not to be specified in theServerLayoutsection. If theAutoAddDevicesoption is disabled, both mouse and keyboard are auto-detected with the default values.Option "option-name"— An optional entry which specifies extra parameters for the section. Any options listed here override those listed in theServerFlagssection.Replace <option-name> with a valid option listed for this section in thexorg.conf(5)man page.
ServerLayout section in the /etc/X11/xorg.conf file. By default, the server only reads the first one it encounters, however. If there is an alternative ServerLayout section, it can be specified as a command-line argument when starting an X session; as in the Xorg -layout <layoutname> command.
C.3.3.5. The Files section
Files section sets paths for services vital to the X server, such as the font path. This is an optional section, as these paths are normally detected automatically. This section can be used to override automatically detected values.
Files section:
Section "Files" RgbPath "/usr/share/X11/rgb.txt" FontPath "unix/:7100" EndSection
Section "Files"
RgbPath "/usr/share/X11/rgb.txt"
FontPath "unix/:7100"
EndSectionFiles section:
ModulePath— An optional parameter which specifies alternate directories which store X server modules.
C.3.3.6. The Monitor section
Monitor section configures one type of monitor used by the system. This is an optional entry as most monitors are now detected automatically.
Monitor section for a monitor:
Monitor section:
Identifier— Specifies a unique name for thisMonitorsection. This is a required entry.VendorName— An optional parameter which specifies the vendor of the monitor.ModelName— An optional parameter which specifies the monitor's model name.DisplaySize— An optional parameter which specifies, in millimeters, the physical size of the monitor's picture area.HorizSync— Specifies the range of horizontal sync frequencies compatible with the monitor, in kHz. These values help the X server determine the validity of built-in or specifiedModelineentries for the monitor.VertRefresh— Specifies the range of vertical refresh frequencies supported by the monitor, in kHz. These values help the X server determine the validity of built-in or specifiedModelineentries for the monitor.Modeline— An optional parameter which specifies additional video modes for the monitor at particular resolutions, with certain horizontal sync and vertical refresh resolutions. See thexorg.conf(5)man page for a more detailed explanation ofModelineentries.Option "option-name"— An optional entry which specifies extra parameters for the section. Replace <option-name> with a valid option listed for this section in thexorg.conf(5)man page.
C.3.3.7. The Device section
Device section configures one video card on the system. While one Device section is the minimum, additional instances may occur for each video card installed on the machine.
Device section for a video card:
Device section:
Identifier— Specifies a unique name for thisDevicesection. This is a required entry.Driver— Specifies which driver the X server must load to utilize the video card. A list of drivers can be found in/usr/share/hwdata/videodrivers, which is installed with the hwdata package.VendorName— An optional parameter which specifies the vendor of the video card.BoardName— An optional parameter which specifies the name of the video card.VideoRam— An optional parameter which specifies the amount of RAM available on the video card, in kilobytes. This setting is only necessary for video cards the X server cannot probe to detect the amount of video RAM.BusID— An entry which specifies the bus location of the video card. On systems with only one video card aBusIDentry is optional and may not even be present in the default/etc/X11/xorg.conffile. On systems with more than one video card, however, aBusIDentry is required.Screen— An optional entry which specifies which monitor connector or head on the video card theDevicesection configures. This option is only useful for video cards with multiple heads.If multiple monitors are connected to different heads on the same video card, separateDevicesections must exist and each of these sections must have a differentScreenvalue.Values for theScreenentry must be an integer. The first head on the video card has a value of0. The value for each additional head increments this value by one.Option "option-name"— An optional entry which specifies extra parameters for the section. Replace <option-name> with a valid option listed for this section in thexorg.conf(5)man page.One of the more common options is"dpms"(for Display Power Management Signaling, a VESA standard), which activates the Energy Star energy compliance setting for the monitor.
C.3.3.8. The Screen section
Screen section binds one video card (or video card head) to one monitor by referencing the Device section and the Monitor section for each. While one Screen section is the minimum, additional instances may occur for each video card and monitor combination present on the machine.
Screen section:
Screen section:
Identifier— Specifies a unique name for thisScreensection. This is a required entry.Device— Specifies the unique name of aDevicesection. This is a required entry.Monitor— Specifies the unique name of aMonitorsection. This is only required if a specificMonitorsection is defined in thexorg.conffile. Normally, monitors are detected automatically.DefaultDepth— Specifies the default color depth in bits. In the previous example,16(which provides thousands of colors) is the default. Only oneDefaultDepthentry is permitted, although this can be overridden with the Xorg command-line option-depth <n>, where<n>is any additional depth specified.SubSection "Display"— Specifies the screen modes available at a particular color depth. TheScreensection can have multipleDisplaysubsections, which are entirely optional since screen modes are detected automatically.This subsection is normally used to override auto-detected modes.Option "option-name"— An optional entry which specifies extra parameters for the section. Replace <option-name> with a valid option listed for this section in thexorg.conf(5)man page.
C.3.3.9. The DRI section
DRI section specifies parameters for the Direct Rendering Infrastructure (DRI). DRI is an interface which allows 3D software applications to take advantage of 3D hardware acceleration capabilities built into most modern video hardware. In addition, DRI can improve 2D performance via hardware acceleration, if supported by the video card driver.
xorg.conf file will override the default values.
DRI section:
Section "DRI" Group 0 Mode 0666 EndSection
Section "DRI"
Group 0
Mode 0666
EndSectionC.4. Fonts
Qt 3 or GTK+ 2 graphical toolkits, or their newer versions.
Note
/etc/fonts/fonts.conf configuration file, which should not be edited by hand.
Warning
fonts group installed. This can be done by selecting the group in the installer, and also by running the yum groupinstall fonts command after installation.
C.4.1. Adding Fonts to Fontconfig
- To add fonts for an individual user, copy the new fonts into the
.fonts/directory in the user's home directory.To add fonts system-wide, copy the new fonts into the/usr/share/fonts/directory. It is a good idea to create a new subdirectory, such aslocal/or similar, to help distinguish between user-installed and default fonts. - Run the
fc-cachecommand as root to update the font information cache:fc-cache <path-to-font-directory>
fc-cache <path-to-font-directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this command, replace <path-to-font-directory> with the directory containing the new fonts (either/usr/share/fonts/local/or/home/<user>/.fonts/).
Note
fonts:/// into the Nautilus address bar, and dragging the new font files there.
C.5. Runlevels and X
C.5.1. Runlevel 3
startx. The startx command is a front-end to the xinit command, which launches the X server (Xorg) and connects X client applications to it. Because the user is already logged into the system at runlevel 3, startx does not launch a display manager or authenticate users. See Section C.5.2, “Runlevel 5” for more information about display managers.
- When the
startxcommand is executed, it searches for the.xinitrcfile in the user's home directory to define the desktop environment and possibly other X client applications to run. If no.xinitrcfile is present, it uses the system default/etc/X11/xinit/xinitrcfile instead. - The default
xinitrcscript then searches for user-defined files and default system files, including.Xresources,.Xmodmap, and.Xkbmapin the user's home directory, andXresources,Xmodmap, andXkbmapin the/etc/X11/directory. TheXmodmapandXkbmapfiles, if they exist, are used by thexmodmaputility to configure the keyboard. TheXresourcesfile is read to assign specific preference values to applications. - After setting the above options, the
xinitrcscript executes all scripts located in the/etc/X11/xinit/xinitrc.d/directory. One important script in this directory isxinput.sh, which configures settings such as the default language. - The
xinitrcscript attempts to execute.Xclientsin the user's home directory and turns to/etc/X11/xinit/Xclientsif it cannot be found. The purpose of theXclientsfile is to start the desktop environment or, possibly, just a basic window manager. The.Xclientsscript in the user's home directory starts the user-specified desktop environment in the.Xclients-defaultfile. If.Xclientsdoes not exist in the user's home directory, the standard/etc/X11/xinit/Xclientsscript attempts to start another desktop environment, trying GNOME first, then KDE, followed bytwm.
C.5.2. Runlevel 5
GDM(GNOME Display Manager) — The default display manager for Red Hat Enterprise Linux.GNOMEallows the user to configure language settings, shutdown, restart or log in to the system.KDM— KDE's display manager which allows the user to shutdown, restart or log in to the system.xdm(X Window Display Manager) — A very basic display manager which only lets the user log in to the system.
/etc/X11/prefdm script determines the preferred display manager by referencing the /etc/sysconfig/desktop file. A list of options for this file is available in this file:
/usr/share/doc/initscripts-<version-number>/sysconfig.txt
/usr/share/doc/initscripts-<version-number>/sysconfig.txt/etc/X11/xdm/Xsetup_0 file to set up the login screen. Once the user logs into the system, the /etc/X11/xdm/GiveConsole script runs to assign ownership of the console to the user. Then, the /etc/X11/xdm/Xsession script runs to accomplish many of the tasks normally performed by the xinitrc script when starting X from runlevel 3, including setting system and user resources, as well as running the scripts in the /etc/X11/xinit/xinitrc.d/ directory.
GNOME or KDE display managers by selecting it from the menu item accessed by selecting → → → . If the desktop environment is not specified in the display manager, the /etc/X11/xdm/Xsession script checks the .xsession and .Xclients files in the user's home directory to decide which desktop environment to load. As a last resort, the /etc/X11/xinit/Xclients file is used to select a desktop environment or window manager to use in the same way as runlevel 3.
:0) and logs out, the /etc/X11/xdm/TakeConsole script runs and reassigns ownership of the console to the root user. The original display manager, which continues running after the user logged in, takes control by spawning a new display manager. This restarts the X server, displays a new login window, and starts the entire process over again.
/usr/share/doc/gdm-<version-number>/README, where <version-number> is the version number for the gdm package installed, or the xdm man page.
C.6. Accessing Graphical Applications Remotely
- You can start a separate application directly from your SSH session in your local X server. For that, you need to enable X11 forwarding. See Section 14.5.1, “X11 Forwarding” for details.
- You can run the whole X session over network using VNC. This method can be useful, especially when you are using a workstation without X server, for example, a non-Linux system. See Chapter 15, TigerVNC for details.
C.7. Additional Resources
C.7.1. Installed Documentation
/usr/share/X11/doc/— contains detailed documentation on the X Window System architecture, as well as how to get additional information about the Xorg project as a new user./usr/share/doc/gdm-<version-number>/README— contains information on how display managers control user authentication.man xorg.conf— Contains information about thexorg.confconfiguration files, including the meaning and syntax for the different sections within the files.man Xorg— Describes theXorgdisplay server.
C.7.2. Useful Websites
- http://www.X.org/ — Home page of the X.Org Foundation, which produces major releases of the X Window System bundled with Red Hat Enterprise Linux to control the necessary hardware and provide a GUI environment.
- http://dri.sourceforge.net/ — Home page of the DRI (Direct Rendering Infrastructure) project. The DRI is the core hardware 3D acceleration component of X.
- http://www.gnome.org/ — Home of the GNOME project.
- http://www.kde.org/ — Home of the KDE desktop environment.
Appendix D. The sysconfig Directory
/etc/sysconfig/ directory, their function, and their contents. The information in this appendix is not intended to be complete, as many of these files have a variety of options that are only used in very specific or rare circumstances.
Note
/etc/sysconfig/ directory depends on the programs you have installed on your machine. To find the name of the package the configuration file belongs to, type the following at a shell prompt:
yum provides /etc/sysconfig/filename
~]$ yum provides /etc/sysconfig/filename D.1. Files in the /etc/sysconfig/ Directory
/etc/sysconfig/ directory.
D.1.1. /etc/sysconfig/arpwatch
/etc/sysconfig/arpwatch file is used to pass arguments to the arpwatch daemon at boot time. By default, it contains the following option:
-
OPTIONS=value - Additional options to be passed to the
arpwatchdaemon. For example:OPTIONS="-u arpwatch -e root -s 'root (Arpwatch)'"
OPTIONS="-u arpwatch -e root -s 'root (Arpwatch)'"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.2. /etc/sysconfig/authconfig
/etc/sysconfig/authconfig file sets the authorization to be used on the host. By default, it contains the following options:
-
USEMKHOMEDIR=boolean - A Boolean to enable (
yes) or disable (no) creating a home directory for a user on the first login. For example:USEMKHOMEDIR=no
USEMKHOMEDIR=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USEPAMACCESS=boolean - A Boolean to enable (
yes) or disable (no) the PAM authentication. For example:USEPAMACCESS=no
USEPAMACCESS=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USESSSDAUTH=boolean - A Boolean to enable (
yes) or disable (no) the SSSD authentication. For example:USESSSDAUTH=no
USESSSDAUTH=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USESHADOW=boolean - A Boolean to enable (
yes) or disable (no) shadow passwords. For example:USESHADOW=yes
USESHADOW=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USEWINBIND=boolean - A Boolean to enable (
yes) or disable (no) using Winbind for user account configuration. For example:USEWINBIND=no
USEWINBIND=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USEDB=boolean - A Boolean to enable (
yes) or disable (no) the FAS authentication. For example:USEDB=no
USEDB=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USEFPRINTD=boolean - A Boolean to enable (
yes) or disable (no) the fingerprint authentication. For example:USEFPRINTD=yes
USEFPRINTD=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
FORCESMARTCARD=boolean - A Boolean to enable (
yes) or disable (no) enforcing the smart card authentication. For example:FORCESMARTCARD=no
FORCESMARTCARD=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
PASSWDALGORITHM=value - The password algorithm. The value can be
bigcrypt,descrypt,md5,sha256, orsha512. For example:PASSWDALGORITHM=sha512
PASSWDALGORITHM=sha512Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
USELDAPAUTH=boolean - A Boolean to enable (
yes) or disable (no) the LDAP authentication. For example:USELDAPAUTH=no
USELDAPAUTH=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USELOCAUTHORIZE=boolean - A Boolean to enable (
yes) or disable (no) the local authorization for local users. For example:USELOCAUTHORIZE=yes
USELOCAUTHORIZE=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USECRACKLIB=boolean - A Boolean to enable (
yes) or disable (no) using the CrackLib. For example:USECRACKLIB=yes
USECRACKLIB=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USEWINBINDAUTH=boolean - A Boolean to enable (
yes) or disable (no) the Winbind authentication. For example:USEWINBINDAUTH=no
USEWINBINDAUTH=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USESMARTCARD=boolean - A Boolean to enable (
yes) or disable (no) the smart card authentication. For example:USESMARTCARD=no
USESMARTCARD=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USELDAP=boolean - A Boolean to enable (
yes) or disable (no) using LDAP for user account configuration. For example:USELDAP=no
USELDAP=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USENIS=boolean - A Boolean to enable (
yes) or disable (no) using NIS for user account configuration. For example:USENIS=no
USENIS=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USEKERBEROS=boolean - A Boolean to enable (
yes) or disable (no) the Kerberos authentication. For example:USEKERBEROS=no
USEKERBEROS=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USESYSNETAUTH=boolean - A Boolean to enable (
yes) or disable (no) authenticating system accounts with network services. For example:USESYSNETAUTH=no
USESYSNETAUTH=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USESMBAUTH=boolean - A Boolean to enable (
yes) or disable (no) the SMB authentication. For example:USESMBAUTH=no
USESMBAUTH=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USESSSD=boolean - A Boolean to enable (
yes) or disable (no) using SSSD for obtaining user information. For example:USESSSD=no
USESSSD=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
USEHESIOD=boolean - A Boolean to enable (
yes) or disable (no) using the Hesoid name service. For example:USEHESIOD=no
USEHESIOD=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.3. /etc/sysconfig/autofs
/etc/sysconfig/autofs file defines custom options for the automatic mounting of devices. This file controls the operation of the automount daemons, which automatically mount file systems when you use them and unmount them after a period of inactivity. File systems can include network file systems, CD-ROM drives, diskettes, and other media.
-
MASTER_MAP_NAME=value - The default name for the master map. For example:
MASTER_MAP_NAME="auto.master"
MASTER_MAP_NAME="auto.master"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
TIMEOUT=value - The default mount timeout. For example:
TIMEOUT=300
TIMEOUT=300Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
NEGATIVE_TIMEOUT=value - The default negative timeout for unsuccessful mount attempts. For example:
NEGATIVE_TIMEOUT=60
NEGATIVE_TIMEOUT=60Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MOUNT_WAIT=value - The time to wait for a response from
mount. For example:MOUNT_WAIT=-1
MOUNT_WAIT=-1Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
UMOUNT_WAIT=value - The time to wait for a response from
umount. For example:UMOUNT_WAIT=12
UMOUNT_WAIT=12Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
BROWSE_MODE=boolean - A Boolean to enable (
yes) or disable (no) browsing the maps. For example:BROWSE_MODE="no"
BROWSE_MODE="no"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MOUNT_NFS_DEFAULT_PROTOCOL=value - The default protocol to be used by
mount.nfs. For example:MOUNT_NFS_DEFAULT_PROTOCOL=4
MOUNT_NFS_DEFAULT_PROTOCOL=4Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
APPEND_OPTIONS=boolean - A Boolean to enable (
yes) or disable (no) appending the global options instead of replacing them. For example:APPEND_OPTIONS="yes"
APPEND_OPTIONS="yes"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
LOGGING=value - The default logging level. The value has to be either
none,verbose, ordebug. For example:LOGGING="none"
LOGGING="none"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
LDAP_URI=value - A space-separated list of server URIs in the form of
protocol://server. For example:LDAP_URI="ldaps://ldap.example.com/"
LDAP_URI="ldaps://ldap.example.com/"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
LDAP_TIMEOUT=value - The synchronous API calls timeout. For example:
LDAP_TIMEOUT=-1
LDAP_TIMEOUT=-1Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
LDAP_NETWORK_TIMEOUT=value - The network response timeout. For example:
LDAP_NETWORK_TIMEOUT=8
LDAP_NETWORK_TIMEOUT=8Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SEARCH_BASE=value - The base Distinguished Name (DN) for the map search. For example:
SEARCH_BASE=""
SEARCH_BASE=""Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
AUTH_CONF_FILE=value - The default location of the SASL authentication configuration file. For example:
AUTH_CONF_FILE="/etc/autofs_ldap_auth.conf"
AUTH_CONF_FILE="/etc/autofs_ldap_auth.conf"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MAP_HASH_TABLE_SIZE=value - The hash table size for the map cache. For example:
MAP_HASH_TABLE_SIZE=1024
MAP_HASH_TABLE_SIZE=1024Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
USE_MISC_DEVICE=boolean - A Boolean to enable (
yes) or disable (no) using the autofs miscellaneous device. For example:USE_MISC_DEVICE="yes"
USE_MISC_DEVICE="yes"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
OPTIONS=value - Additional options to be passed to the LDAP daemon. For example:
OPTIONS=""
OPTIONS=""Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.4. /etc/sysconfig/clock
/etc/sysconfig/clock file controls the interpretation of values read from the system hardware clock. It is used by the Date/Time Properties tool, and should not be edited by hand. By default, it contains the following option:
-
ZONE=value - The time zone file under
/usr/share/zoneinfothat/etc/localtimeis a copy of. For example:ZONE="Europe/Prague"
ZONE="Europe/Prague"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.5. /etc/sysconfig/dhcpd
/etc/sysconfig/dhcpd file is used to pass arguments to the dhcpd daemon at boot time. By default, it contains the following options:
-
DHCPDARGS=value - Additional options to be passed to the
dhcpddaemon. For example:DHCPDARGS=
DHCPDARGS=Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.6. /etc/sysconfig/firstboot
/etc/sysconfig/firstboot file defines whether to run the firstboot utility. By default, it contains the following option:
-
RUN_FIRSTBOOT=boolean - A Boolean to enable (
YES) or disable (NO) running thefirstbootprogram. For example:RUN_FIRSTBOOT=NO
RUN_FIRSTBOOT=NOCopy to Clipboard Copied! Toggle word wrap Toggle overflow
init program calls the /etc/rc.d/init.d/firstboot script, which looks for the /etc/sysconfig/firstboot file. If this file does not contain the RUN_FIRSTBOOT=NO option, the firstboot program is run, guiding a user through the initial configuration of the system.
Note
firstboot program the next time the system boots, change the value of RUN_FIRSTBOOT option to YES, and type the following at a shell prompt:
chkconfig firstboot on
~]# chkconfig firstboot onD.1.7. /etc/sysconfig/i18n
/etc/sysconfig/i18n configuration file defines the default language, any supported languages, and the default system font. By default, it contains the following options:
-
LANG=value - The default language. For example:
LANG="en_US.UTF-8"
LANG="en_US.UTF-8"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SUPPORTED=value - A colon-separated list of supported languages. For example:
SUPPORTED="en_US.UTF-8:en_US:en"
SUPPORTED="en_US.UTF-8:en_US:en"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SYSFONT=value - The default system font. For example:
SYSFONT="latarcyrheb-sun16"
SYSFONT="latarcyrheb-sun16"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.8. /etc/sysconfig/init
/etc/sysconfig/init file controls how the system appears and functions during the boot process. By default, it contains the following options:
-
BOOTUP=value - The bootup style. The value has to be either
color(the standard color boot display),verbose(an old style display which provides more information), or anything else for the new style display, but without ANSI formatting. For example:BOOTUP=color
BOOTUP=colorCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
RES_COL=value - The number of the column in which the status labels start. For example:
RES_COL=60
RES_COL=60Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MOVE_TO_COL=value - The terminal sequence to move the cursor to the column specified in
RES_COL(see above). For example:MOVE_TO_COL="echo -en \\033[${RES_COL}G"MOVE_TO_COL="echo -en \\033[${RES_COL}G"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SETCOLOR_SUCCESS=value - The terminal sequence to set the success color. For example:
SETCOLOR_SUCCESS="echo -en \\033[0;32m"
SETCOLOR_SUCCESS="echo -en \\033[0;32m"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SETCOLOR_FAILURE=value - The terminal sequence to set the failure color. For example:
SETCOLOR_FAILURE="echo -en \\033[0;31m"
SETCOLOR_FAILURE="echo -en \\033[0;31m"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SETCOLOR_WARNING=value - The terminal sequence to set the warning color. For example:
SETCOLOR_WARNING="echo -en \\033[0;33m"
SETCOLOR_WARNING="echo -en \\033[0;33m"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SETCOLOR_NORMAL=value - The terminal sequence to set the default color. For example:
SETCOLOR_NORMAL="echo -en \\033[0;39m"
SETCOLOR_NORMAL="echo -en \\033[0;39m"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
LOGLEVEL=value - The initial console logging level. The value has to be in the range from
1(kernel panics only) to8(everything, including the debugging information). For example:LOGLEVEL=3
LOGLEVEL=3Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
PROMPT=boolean - A Boolean to enable (
yes) or disable (no) the hotkey interactive startup. For example:PROMPT=yes
PROMPT=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
AUTOSWAP=boolean - A Boolean to enable (
yes) or disable (no) probing for devices with swap signatures. For example:AUTOSWAP=no
AUTOSWAP=noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ACTIVE_CONSOLES=value - The list of active consoles. For example:
ACTIVE_CONSOLES=/dev/tty[1-6]
ACTIVE_CONSOLES=/dev/tty[1-6]Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SINGLE=value - The single-user mode type. The value has to be either
/sbin/sulogin(a user will be prompted for a password to log in), or/sbin/sushell(the user will be logged in directly). For example:SINGLE=/sbin/sushell
SINGLE=/sbin/sushellCopy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.9. /etc/sysconfig/ip6tables-config
/etc/sysconfig/ip6tables-config file stores information used by the kernel to set up IPv6 packet filtering at boot time or whenever the ip6tables service is started. Note that you should not modify it unless you are familiar with ip6tables rules. By default, it contains the following options:
-
IP6TABLES_MODULES=value - A space-separated list of helpers to be loaded after the firewall rules are applied. For example:
IP6TABLES_MODULES="ip_nat_ftp ip_nat_irc"
IP6TABLES_MODULES="ip_nat_ftp ip_nat_irc"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
IP6TABLES_MODULES_UNLOAD=boolean - A Boolean to enable (
yes) or disable (no) module unloading when the firewall is stopped or restarted. For example:IP6TABLES_MODULES_UNLOAD="yes"
IP6TABLES_MODULES_UNLOAD="yes"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
IP6TABLES_SAVE_ON_STOP=boolean - A Boolean to enable (
yes) or disable (no) saving the current firewall rules when the firewall is stopped. For example:IP6TABLES_SAVE_ON_STOP="no"
IP6TABLES_SAVE_ON_STOP="no"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
IP6TABLES_SAVE_ON_RESTART=boolean - A Boolean to enable (
yes) or disable (no) saving the current firewall rules when the firewall is restarted. For example:IP6TABLES_SAVE_ON_RESTART="no"
IP6TABLES_SAVE_ON_RESTART="no"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
IP6TABLES_SAVE_COUNTER=boolean - A Boolean to enable (
yes) or disable (no) saving the rule and chain counters. For example:IP6TABLES_SAVE_COUNTER="no"
IP6TABLES_SAVE_COUNTER="no"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
IP6TABLES_STATUS_NUMERIC=boolean - A Boolean to enable (
yes) or disable (no) printing IP addresses and port numbers in a numeric format in the status output. For example:IP6TABLES_STATUS_NUMERIC="yes"
IP6TABLES_STATUS_NUMERIC="yes"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
IP6TABLES_STATUS_VERBOSE=boolean - A Boolean to enable (
yes) or disable (no) printing information about the number of packets and bytes in the status output. For example:IP6TABLES_STATUS_VERBOSE="no"
IP6TABLES_STATUS_VERBOSE="no"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
IP6TABLES_STATUS_LINENUMBERS=boolean - A Boolean to enable (
yes) or disable (no) printing line numbers in the status output. For example:IP6TABLES_STATUS_LINENUMBERS="yes"
IP6TABLES_STATUS_LINENUMBERS="yes"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Note
ip6tables command. Once created, type the following at a shell prompt:
service ip6tables save
~]# service ip6tables save/etc/sysconfig/ip6tables. Once this file exists, any firewall rules saved in it persist through a system reboot or a service restart.
D.1.10. /etc/sysconfig/kernel
/etc/sysconfig/kernel configuration file controls the kernel selection at boot by using these two options:
UPDATEDEFAULT=yes- This option makes a newly installed kernel as the default in the boot entry selection.
DEFAULTKERNEL=kernel- This option specifies what package type will be used as the default.
D.1.10.1. Keeping an old kernel version as the default
- Comment out the UPDATEDEFAULT option in /etc/sysconfig/kernel as follows:
UPDATEDEFAULT=yes
# UPDATEDEFAULT=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.10.2. Setting a kernel debugger as the default kernel
- Edit the /etc/sysconfig/kernel configuration file as follows:
DEFAULTKERNEL=kernel-debug
DEFAULTKERNEL=kernel-debugCopy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.11. /etc/sysconfig/keyboard
/etc/sysconfig/keyboard file controls the behavior of the keyboard. By default, it contains the following options:
-
KEYTABLE=value - The name of a keytable file. The files that can be used as keytables start in the
/lib/kbd/keymaps/i386/directory, and branch into different keyboard layouts from there, all labeledvalue.kmap.gz. The first file name that matches theKEYTABLEsetting is used. For example:KEYTABLE="us"
KEYTABLE="us"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
MODEL=value - The keyboard model. For example:
MODEL="pc105+inet"
MODEL="pc105+inet"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
LAYOUT=value - The keyboard layout. For example:
LAYOUT="us"
LAYOUT="us"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
KEYBOARDTYPE=value - The keyboard type. Allowed values are
pc(a PS/2 keyboard), orsun(a Sun keyboard). For example:KEYBOARDTYPE="pc"
KEYBOARDTYPE="pc"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.12. /etc/sysconfig/ldap
/etc/sysconfig/ldap file holds the basic configuration for the LDAP server. By default, it contains the following options:
-
SLAPD_OPTIONS=value - Additional options to be passed to the
slapddaemon. For example:SLAPD_OPTIONS="-4"
SLAPD_OPTIONS="-4"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SLURPD_OPTIONS=value - Additional options to be passed to the
slurpddaemon. For example:SLURPD_OPTIONS=""
SLURPD_OPTIONS=""Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SLAPD_LDAP=boolean - A Boolean to enable (
yes) or disable (no) using the LDAP over TCP (that is,ldap:///). For example:SLAPD_LDAP="yes"
SLAPD_LDAP="yes"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SLAPD_LDAPI=boolean - A Boolean to enable (
yes) or disable (no) using the LDAP over IPC (that is,ldapi:///). For example:SLAPD_LDAPI="no"
SLAPD_LDAPI="no"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SLAPD_LDAPS=boolean - A Boolean to enable (
yes) or disable (no) using the LDAP over TLS (that is,ldaps:///). For example:SLAPD_LDAPS="no"
SLAPD_LDAPS="no"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SLAPD_URLS=value - A space-separated list of URLs. For example:
SLAPD_URLS="ldapi:///var/lib/ldap_root/ldapi ldapi:/// ldaps:///"
SLAPD_URLS="ldapi:///var/lib/ldap_root/ldapi ldapi:/// ldaps:///"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SLAPD_SHUTDOWN_TIMEOUT=value - The time to wait for
slapdto shut down. For example:SLAPD_SHUTDOWN_TIMEOUT=3
SLAPD_SHUTDOWN_TIMEOUT=3Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SLAPD_ULIMIT_SETTINGS=value - The parameters to be passed to
ulimitbefore theslapddaemon is started. For example:SLAPD_ULIMIT_SETTINGS=""
SLAPD_ULIMIT_SETTINGS=""Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.13. /etc/sysconfig/named
/etc/sysconfig/named file is used to pass arguments to the named daemon at boot time. By default, it contains the following options:
-
ROOTDIR=value - The chroot environment under which the
nameddaemon runs. The value has to be a full directory path. For example:ROOTDIR="/var/named/chroot"
ROOTDIR="/var/named/chroot"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the chroot environment has to be configured first (typeinfo chrootat a shell prompt for more information). -
OPTIONS=value - Additional options to be passed to
named. For example:OPTIONS="-6"
OPTIONS="-6"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that you should not use the-toption. Instead, useROOTDIRas described above. -
KEYTAB_FILE=value - The keytab file name. For example:
KEYTAB_FILE="/etc/named.keytab"
KEYTAB_FILE="/etc/named.keytab"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.14. /etc/sysconfig/network
/etc/sysconfig/network file is used to specify information about the desired network configuration. By default, it contains the following options:
-
NETWORKING=boolean - A Boolean to enable (
yes) or disable (no) networking. For example:NETWORKING=yes
NETWORKING=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
HOSTNAME=value - The host name of the machine. For example:
HOSTNAME=penguin.example.com
HOSTNAME=penguin.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
-
GATEWAY=value - The IP address of the network's gateway. For example:
GATEWAY=192.168.1.1
GATEWAY=192.168.1.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow This is used as the default gateway when there is noGATEWAYdirective in an interface'sifcfgfile. -
NM_BOND_VLAN_ENABLED=boolean - A Boolean to allow (
yes) or disallow (no) the NetworkManager application from detecting and managing bonding, bridging, and VLAN interfaces. For example:NM_BOND_VLAN_ENABLED=yes
NM_BOND_VLAN_ENABLED=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow TheNM_CONTROLLEDdirective is dependent on this option.
Note
net.ipv6.conf.all.disable_ipv6=1
net.ipv6.conf.all.disable_ipv6=1net.ipv6.conf.default.disable_ipv6=1
net.ipv6.conf.default.disable_ipv6=1ipv6.disable=1 to the kernel command line will disable the kernel module net-pf-10 which implements IPv6.
Warning
D.1.15. /etc/sysconfig/ntpd
/etc/sysconfig/ntpd file is used to pass arguments to the ntpd daemon at boot time. By default, it contains the following option:
-
OPTIONS=value - Additional options to be passed to
ntpd. For example:OPTIONS="-u ntp:ntp -p /var/run/ntpd.pid -g"
OPTIONS="-u ntp:ntp -p /var/run/ntpd.pid -g"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
ntpd daemon.
D.1.16. /etc/sysconfig/quagga
/etc/sysconfig/quagga file holds the basic configuration for Quagga daemons. By default, it contains the following options:
-
QCONFDIR=value - The directory with the configuration files for Quagga daemons. For example:
QCONFDIR="/etc/quagga"
QCONFDIR="/etc/quagga"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
BGPD_OPTS=value - Additional options to be passed to the
bgpddaemon. For example:BGPD_OPTS="-A 127.0.0.1 -f ${QCONFDIR}/bgpd.conf"BGPD_OPTS="-A 127.0.0.1 -f ${QCONFDIR}/bgpd.conf"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
OSPF6D_OPTS=value - Additional options to be passed to the
ospf6ddaemon. For example:OSPF6D_OPTS="-A ::1 -f ${QCONFDIR}/ospf6d.conf"OSPF6D_OPTS="-A ::1 -f ${QCONFDIR}/ospf6d.conf"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
OSPFD_OPTS=value - Additional options to be passed to the
ospfddaemon. For example:OSPFD_OPTS="-A 127.0.0.1 -f ${QCONFDIR}/ospfd.conf"OSPFD_OPTS="-A 127.0.0.1 -f ${QCONFDIR}/ospfd.conf"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
RIPD_OPTS=value - Additional options to be passed to the
ripddaemon. For example:RIPD_OPTS="-A 127.0.0.1 -f ${QCONFDIR}/ripd.conf"RIPD_OPTS="-A 127.0.0.1 -f ${QCONFDIR}/ripd.conf"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
RIPNGD_OPTS=value - Additional options to be passed to the
ripngddaemon. For example:RIPNGD_OPTS="-A ::1 -f ${QCONFDIR}/ripngd.conf"RIPNGD_OPTS="-A ::1 -f ${QCONFDIR}/ripngd.conf"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
ZEBRA_OPTS=value - Additional options to be passed to the
zebradaemon. For example:ZEBRA_OPTS="-A 127.0.0.1 -f ${QCONFDIR}/zebra.conf"ZEBRA_OPTS="-A 127.0.0.1 -f ${QCONFDIR}/zebra.conf"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
ISISD_OPTS=value - Additional options to be passed to the
isisddaemon. For example:ISISD_OPTS="-A ::1 -f ${QCONFDIR}/isisd.conf"ISISD_OPTS="-A ::1 -f ${QCONFDIR}/isisd.conf"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
WATCH_OPTS=value - Additional options to be passed to the
watchquaggadaemon. For example:WATCH_OPTS="-Az -b_ -r/sbin/service_%s_restart -s/sbin/service_%s_start -k/sbin/service_%s_stop"
WATCH_OPTS="-Az -b_ -r/sbin/service_%s_restart -s/sbin/service_%s_start -k/sbin/service_%s_stop"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
WATCH_DAEMONS=value - A space separated list of monitored daemons. For example:
WATCH_DAEMONS="zebra bgpd ospfd ospf6d ripd ripngd"
WATCH_DAEMONS="zebra bgpd ospfd ospf6d ripd ripngd"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.17. /etc/sysconfig/radvd
/etc/sysconfig/radvd file is used to pass arguments to the radvd daemon at boot time. By default, it contains the following option:
-
OPTIONS=value - Additional options to be passed to the
radvddaemon. For example:OPTIONS="-u radvd"
OPTIONS="-u radvd"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.18. /etc/sysconfig/samba
/etc/sysconfig/samba file is used to pass arguments to the Samba daemons at boot time. By default, it contains the following options:
-
SMBDOPTIONS=value - Additional options to be passed to
smbd. For example:SMBDOPTIONS="-D"
SMBDOPTIONS="-D"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
NMBDOPTIONS=value - Additional options to be passed to
nmbd. For example:NMBDOPTIONS="-D"
NMBDOPTIONS="-D"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
WINBINDOPTIONS=value - Additional options to be passed to
winbindd. For example:WINBINDOPTIONS=""
WINBINDOPTIONS=""Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.19. /etc/sysconfig/saslauthd
/etc/sysconfig/saslauthd file is used to control which arguments are passed to saslauthd, the SASL authentication server. By default, it contains the following options:
- SOCKETDIR=value
- The directory for the
saslauthd's listening socket. For example:SOCKETDIR=/var/run/saslauthd
SOCKETDIR=/var/run/saslauthdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - MECH=value
- The authentication mechanism to use to verify user passwords. For example:
MECH=pam
MECH=pamCopy to Clipboard Copied! Toggle word wrap Toggle overflow - DAEMONOPTS=value
- Options to be passed to the
daemon()function that is used by the/etc/rc.d/init.d/saslauthdinit script to start thesaslauthdservice. For example:DAEMONOPTS="--user saslauth"
DAEMONOPTS="--user saslauth"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - FLAGS=value
- Additional options to be passed to the
saslauthdservice. For example:FLAGS=
FLAGS=Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.20. /etc/sysconfig/selinux
/etc/sysconfig/selinux file contains the basic configuration options for SELinux. It is a symbolic link to /etc/selinux/config, and by default, it contains the following options:
-
SELINUX=value - The security policy. The value can be either
enforcing(the security policy is always enforced),permissive(instead of enforcing the policy, appropriate warnings are displayed), ordisabled(no policy is used). For example:SELINUX=enforcing
SELINUX=enforcingCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
SELINUXTYPE=value - The protection type. The value can be either
targeted(the targeted processes are protected), ormls(the Multi Level Security protection). For example:SELINUXTYPE=targeted
SELINUXTYPE=targetedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.21. /etc/sysconfig/sendmail
/etc/sysconfig/sendmail is used to set the default values for the Sendmail application. By default, it contains the following values:
-
DAEMON=boolean - A Boolean to enable (
yes) or disable (no) runningsendmailas a daemon. For example:DAEMON=yes
DAEMON=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
QUEUE=value - The interval at which the messages are to be processed. For example:
QUEUE=1h
QUEUE=1hCopy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.22. /etc/sysconfig/spamassassin
/etc/sysconfig/spamassassin file is used to pass arguments to the spamd daemon (a daemonized version of Spamassassin) at boot time. By default, it contains the following option:
-
SPAMDOPTIONS=value - Additional options to be passed to the
spamddaemon. For example:SPAMDOPTIONS="-d -c -m5 -H"
SPAMDOPTIONS="-d -c -m5 -H"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.23. /etc/sysconfig/squid
/etc/sysconfig/squid file is used to pass arguments to the squid daemon at boot time. By default, it contains the following options:
-
SQUID_OPTS=value - Additional options to be passed to the
squiddaemon. For example:SQUID_OPTS=""
SQUID_OPTS=""Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SQUID_SHUTDOWN_TIMEOUT=value - The time to wait for
squiddaemon to shut down. For example:SQUID_SHUTDOWN_TIMEOUT=100
SQUID_SHUTDOWN_TIMEOUT=100Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SQUID_CONF=value - The default configuration file. For example:
SQUID_CONF="/etc/squid/squid.conf"
SQUID_CONF="/etc/squid/squid.conf"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.24. /etc/sysconfig/system-config-users
/etc/sysconfig/system-config-users file is the configuration file for the User Manager utility, and should not be edited by hand. By default, it contains the following options:
-
FILTER=boolean - A Boolean to enable (
true) or disable (false) filtering of system users. For example:FILTER=true
FILTER=trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ASSIGN_HIGHEST_UID=boolean - A Boolean to enable (
true) or disable (false) assigning the highest available UID to newly added users. For example:ASSIGN_HIGHEST_UID=true
ASSIGN_HIGHEST_UID=trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
ASSIGN_HIGHEST_GID=boolean - A Boolean to enable (
true) or disable (false) assigning the highest available GID to newly added groups. For example:ASSIGN_HIGHEST_GID=true
ASSIGN_HIGHEST_GID=trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
PREFER_SAME_UID_GID=boolean - A Boolean to enable (
true) or disable (false) using the same UID and GID for newly added users when possible. For example:PREFER_SAME_UID_GID=true
PREFER_SAME_UID_GID=trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.25. /etc/sysconfig/vncservers
/etc/sysconfig/vncservers file configures the way the Virtual Network Computing (VNC) server starts up. By default, it contains the following options:
-
VNCSERVERS=value - A list of space separated
display:usernamepairs. For example:VNCSERVERS="2:myusername"
VNCSERVERS="2:myusername"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
VNCSERVERARGS[display]=value - Additional arguments to be passed to the VNC server running on the specified display. For example:
VNCSERVERARGS[2]="-geometry 800x600 -nolisten tcp -localhost"
VNCSERVERARGS[2]="-geometry 800x600 -nolisten tcp -localhost"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
D.1.26. /etc/sysconfig/xinetd
/etc/sysconfig/xinetd file is used to pass arguments to the xinetd daemon at boot time. By default, it contains the following options:
-
EXTRAOPTIONS=value - Additional options to be passed to
xinetd. For example:EXTRAOPTIONS=""
EXTRAOPTIONS=""Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
XINETD_LANG=value - The locale information to be passed to every service started by
xinetd. Note that to remove locale information from thexinetdenvironment, you can use an empty string ("") ornone. For example:XINETD_LANG="en_US"
XINETD_LANG="en_US"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
xinetd services.
D.2. Directories in the /etc/sysconfig/ Directory
/etc/sysconfig/.
-
/etc/sysconfig/cbq/ -
/etc/sysconfig/networking/ - This directory is used by the now deprecated Network Administration Tool (
system-config-network), and its contents should not be edited manually. For more information about configuring network interfaces using graphical configuration tools, see Chapter 10, NetworkManager. -
/etc/sysconfig/network-scripts/ - Network configuration files for each configured network interface, such as
ifcfg-eth0for theeth0Ethernet interface. - Scripts used to bring network interfaces up and down, such as
ifupandifdown. - Scripts used to bring ISDN interfaces up and down, such as
ifup-isdnandifdown-isdn. - Various shared network function scripts which should not be edited directly.
For more information on the/etc/sysconfig/network-scripts/directory, see Chapter 11, Network Interfaces.-
/etc/sysconfig/rhn/ - This directory contains the configuration files and GPG keys for Red Hat Network. No files in this directory should be edited by hand. For more information on Red Hat Network, see the Red Hat Network website online at https://rhn.redhat.com/.
D.3. Additional Resources
/etc/sysconfig/ directory. The following source contains more comprehensive information.
D.3.1. Installed Documentation
-
/usr/share/doc/initscripts-version/sysconfig.txt - A more authoritative listing of the files found in the
/etc/sysconfig/directory and the configuration options available for them.
Appendix E. The proc File System
/proc/ directory (also called the proc file system) contains a hierarchy of special files which represent the current state of the kernel, allowing applications and users to peer into the kernel's view of the system.
/proc/ directory contains a wealth of information detailing system hardware and any running processes. In addition, some of the files within /proc/ can be manipulated by users and applications to communicate configuration changes to the kernel.
Note
/proc/ide/ and /proc/pci/ directories obsolete. The /proc/ide/ file system is now superseded by files in sysfs; to retrieve information on PCI devices, use lspci instead. For more information on sysfs or lspci, see their respective man pages.
E.1. A Virtual File System
/proc/ directory contains another type of file called a virtual file. As such, /proc/ is often referred to as a virtual file system.
/proc/interrupts, /proc/meminfo, /proc/mounts, and /proc/partitions provide an up-to-the-moment glimpse of the system's hardware. Others, like the /proc/filesystems file and the /proc/sys/ directory provide system configuration information and interfaces.
E.1.1. Viewing Virtual Files
/proc/ files operate similarly to text files, storing useful system and hardware data in human-readable text format. As such, you can use cat, more, or less to view them. For example, to display information about the system's CPU, run cat /proc/cpuinfo. This will return output similar to the following:
/proc/ contain information that is not human-readable. To retrieve information from such files, use tools such as lspci, apm, free, and top.
Note
/proc/ directory are readable only by the root user.
E.1.2. Changing Virtual Files
/proc/ directory are read-only. However, some can be used to adjust settings in the kernel. This is especially true for files in the /proc/sys/ subdirectory.
echo value > /proc/file
echo www.example.com > /proc/sys/kernel/hostname
cat /proc/sys/net/ipv4/ip_forward returns either a 0 (off or false) or a 1 (on or true). A 0 indicates that the kernel is not forwarding network packets. To turn packet forwarding on, run echo 1 > /proc/sys/net/ipv4/ip_forward.
Note
/proc/sys/ subdirectory is /sbin/sysctl. For more information on this command, see Section E.4, “Using the sysctl Command”
/proc/sys/ subdirectory, see Section E.3.9, “/proc/sys/”.
E.2. Top-level Files within the proc File System
/proc/ directory.
Note
E.2.1. /proc/buddyinfo
/proc/buddyinfo file is used primarily for diagnosing memory fragmentation issues. The output depends on the memory layout used, which is architecture specific. The following is an example from a 32-bit system:
Node 0, zone DMA 90 6 2 1 1 ... Node 0, zone Normal 1650 310 5 0 0 ... Node 0, zone HighMem 2 0 0 1 1 ...
Node 0, zone DMA 90 6 2 1 1 ...
Node 0, zone Normal 1650 310 5 0 0 ...
Node 0, zone HighMem 2 0 0 1 1 ...
DMA row references the first 16 MB of memory on the system, the HighMem row references all memory greater than 896 MB on the system, and the Normal row references the memory in between.
Node 0, zone DMA 0 3 1 2 4 3 1 2 3 3 1 Node 0, zone DMA32 295 25850 7065 1645 835 220 78 6 0 1 0 Node 0, zone Normal 3824 3359 736 159 31 3 1 1 1 1 0
Node 0, zone DMA 0 3 1 2 4 3 1 2 3 3 1
Node 0, zone DMA32 295 25850 7065 1645 835 220 78 6 0 1 0
Node 0, zone Normal 3824 3359 736 159 31 3 1 1 1 1 0DMA row references the first 16 MB of memory on the system, the DMA32 row references all memory allocated for devices that cannot address memory greater than 4 GB, and the Normal row references all memory above the DMA32 allocation, which includes all memory above 4 GB on the system.
E.2.2. /proc/cmdline
/proc/cmdline file looks like the following:
ro root=/dev/VolGroup00/LogVol00 rhgb quiet 3
ro root=/dev/VolGroup00/LogVol00 rhgb quiet 3
(ro)), located on the first logical volume (LogVol00) of the first volume group (/dev/VolGroup00). LogVol00 is the equivalent of a disk partition in a non-LVM system (Logical Volume Management), just as /dev/VolGroup00 is similar in concept to /dev/hda1, but much more extensible.
rhgb signals that the rhgb package has been installed, and graphical booting is supported, assuming /etc/inittab shows a default runlevel set to id:5:initdefault:.
quiet indicates all verbose kernel messages are suppressed at boot time.
E.2.3. /proc/cpuinfo
/proc/cpuinfo:
processor— Provides each processor with an identifying number. On systems that have one processor, only a0is present.cpu family— Authoritatively identifies the type of processor in the system. For an Intel-based system, place the number in front of "86" to determine the value. This is particularly helpful for those attempting to identify the architecture of an older system such as a 586, 486, or 386. Because some RPM packages are compiled for each of these particular architectures, this value also helps users determine which packages to install.model name— Displays the common name of the processor, including its project name.cpu MHz— Shows the precise speed in megahertz for the processor to the thousandths decimal place.cache size— Displays the amount of level 2 memory cache available to the processor.siblings— Displays the total number of sibling CPUs on the same physical CPU for architectures which use hyper-threading.flags— Defines a number of different qualities about the processor, such as the presence of a floating point unit (FPU) and the ability to process MMX instructions.
E.2.4. /proc/crypto
/proc/crypto file looks like the following:
E.2.5. /proc/devices
/proc/devices includes the major number and name of the device, and is broken into two major sections: Character devices and Block devices.
- Character devices do not require buffering. Block devices have a buffer available, allowing them to order requests before addressing them. This is important for devices designed to store information — such as hard drives — because the ability to order the information before writing it to the device allows it to be placed in a more efficient order.
- Character devices send data with no preconfigured size. Block devices can send and receive information in blocks of a size configured per device.
devices.txt file in the kernel-doc package (see Section E.5, “Additional Resources”).
E.2.6. /proc/dma
/proc/dma files looks like the following:
4: cascade
4: cascade
E.2.7. /proc/execdomains
0-0 Linux [kernel]
0-0 Linux [kernel]
PER_LINUX execution domain, different personalities can be implemented as dynamically loadable modules.
E.2.8. /proc/fb
/proc/fb for systems which contain frame buffer devices looks similar to the following:
0 VESA VGA
0 VESA VGA
E.2.9. /proc/filesystems
/proc/filesystems file looks similar to the following:
nodev are not mounted on a device. The second column lists the names of the file systems supported.
mount command cycles through the file systems listed here when one is not specified as an argument.
E.2.10. /proc/interrupts
/proc/interrupts looks similar to the following:
XT-PIC— This is the old AT computer interrupts.IO-APIC-edge— The voltage signal on this interrupt transitions from low to high, creating an edge, where the interrupt occurs and is only signaled once. This kind of interrupt, as well as theIO-APIC-levelinterrupt, are only seen on systems with processors from the 586 family and higher.IO-APIC-level— Generates interrupts when its voltage signal is high until the signal is low again.
E.2.11. /proc/iomem
E.2.12. /proc/ioports
/proc/ioports provides a list of currently registered port regions used for input or output communication with a device. This file can be quite long. The following is a partial listing:
E.2.13. /proc/kcore
/proc/ files, kcore displays a size. This value is given in bytes and is equal to the size of the physical memory (RAM) used plus 4 KB.
gdb, and is not human readable.
Warning
/proc/kcore virtual file. The contents of the file scramble text output on the terminal. If this file is accidentally viewed, press Ctrl+C to stop the process and then type reset to bring back the command line prompt.
E.2.14. /proc/kmsg
/sbin/klogd or /bin/dmesg.
E.2.15. /proc/loadavg
uptime and other commands. A sample /proc/loadavg file looks similar to the following:
0.20 0.18 0.12 1/80 11206
0.20 0.18 0.12 1/80 11206
E.2.16. /proc/locks
/proc/locks file for a lightly loaded system looks similar to the following:
FLOCK signifying the older-style UNIX file locks from a flock system call and POSIX representing the newer POSIX locks from the lockf system call.
ADVISORY or MANDATORY. ADVISORY means that the lock does not prevent other people from accessing the data; it only prevents other attempts to lock it. MANDATORY means that no other access to the data is permitted while the lock is held. The fourth column reveals whether the lock is allowing the holder READ or WRITE access to the file. The fifth column shows the ID of the process holding the lock. The sixth column shows the ID of the file being locked, in the format of MAJOR-DEVICE:MINOR-DEVICE:INODE-NUMBER. The seventh and eighth column shows the start and end of the file's locked region.
E.2.17. /proc/mdstat
/proc/mdstat looks similar to the following:
Personalities : read_ahead not set unused devices: <none>
Personalities : read_ahead not set unused devices: <none>
md device is present. In that case, view /proc/mdstat to find the current status of mdX RAID devices.
/proc/mdstat file below shows a system with its md0 configured as a RAID 1 device, while it is currently re-syncing the disks:
Personalities : [linear] [raid1] read_ahead 1024 sectors md0: active raid1 sda2[1] sdb2[0] 9940 blocks [2/2] [UU] resync=1% finish=12.3min algorithm 2 [3/3] [UUU] unused devices: <none>
Personalities : [linear] [raid1] read_ahead 1024 sectors
md0: active raid1 sda2[1] sdb2[0] 9940 blocks [2/2] [UU] resync=1% finish=12.3min algorithm 2 [3/3] [UUU]
unused devices: <none>
E.2.18. /proc/meminfo
/proc/ directory, as it reports a large amount of valuable information about the system's RAM usage.
/proc/meminfo virtual file is from a system with 2 GB of RAM and 1 GB of swap space:
/proc/meminfo is known, but is not corrected due to legacy concerns - programs rely on /proc/meminfo to specify size with the "kB" string.
/proc/meminfo is used by the free, top, and ps commands. In fact, the output of the free command is similar in appearance to the contents and structure of /proc/meminfo. However, /proc/meminfo itself has more details:
MemTotal— Total amount of usable RAM, in kibibytes, which is physical RAM minus a number of reserved bits and the kernel binary code.MemFree— The amount of physical RAM, in kibibytes, left unused by the system.Buffers— The amount, in kibibytes, of temporary storage for raw disk blocks.Cached— The amount of physical RAM, in kibibytes, used as cache memory.SwapCached— The amount of memory, in kibibytes, that has once been moved into swap, then back into the main memory, but still also remains in the swapfile. This saves I/O, because the memory does not need to be moved into swap again.Active— The amount of memory, in kibibytes, that has been used more recently and is usually not reclaimed unless absolutely necessary.Inactive— The amount of memory, in kibibytes, that has been used less recently and is more eligible to be reclaimed for other purposes.Active(anon)— The amount of anonymous and tmpfs/shmem memory, in kibibytes, that is in active use, or was in active use since the last time the system moved something to swap.Inactive(anon)— The amount of anonymous and tmpfs/shmem memory, in kibibytes, that is a candidate for eviction.Active(file)— The amount of file cache memory, in kibibytes, that is in active use, or was in active use since the last time the system reclaimed memory.Inactive(file)— The amount of file cache memory, in kibibytes, that is newly loaded from the disk, or is a candidate for reclaiming.Unevictable— The amount of memory, in kibibytes, discovered by the pageout code, that is not evictable because it is locked into memory by user programs.Mlocked— The total amount of memory, in kibibytes, that is not evictable because it is locked into memory by user programs.SwapTotal— The total amount of swap available, in kibibytes.SwapFree— The total amount of swap free, in kibibytes.Dirty— The total amount of memory, in kibibytes, waiting to be written back to the disk.Writeback— The total amount of memory, in kibibytes, actively being written back to the disk.AnonPages— The total amount of memory, in kibibytes, used by pages that are not backed by files and are mapped into userspace page tables.Mapped— The memory, in kibibytes, used for files that have been mmaped, such as libraries.Shmem— The total amount of memory, in kibibytes, used by shared memory (shmem) and tmpfs.Slab— The total amount of memory, in kibibytes, used by the kernel to cache data structures for its own use.SReclaimable— The part of Slab that can be reclaimed, such as caches.SUnreclaim— The part of Slab that cannot be reclaimed even when lacking memory.KernelStack— The amount of memory, in kibibytes, used by the kernel stack allocations done for each task in the system.PageTables— The total amount of memory, in kibibytes, dedicated to the lowest page table level.NFS_Unstable— The amount, in kibibytes, of NFS pages sent to the server but not yet committed to the stable storage.Bounce— The amount of memory, in kibibytes, used for the block device "bounce buffers".WritebackTmp— The amount of memory, in kibibytes, used by FUSE for temporary writeback buffers.CommitLimit— The total amount of memory currently available to be allocated on the system based on the overcommit ratio (vm.overcommit_ratio). This limit is only adhered to if strict overcommit accounting is enabled (mode 2 invm.overcommit_memory).CommitLimitis calculated with the following formula:([total RAM pages] - [total huge TLB pages]) * overcommit_ratio ───────────────────────────────────────────────────────────────── + [total swap pages] 100([total RAM pages] - [total huge TLB pages]) * overcommit_ratio ───────────────────────────────────────────────────────────────── + [total swap pages] 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow For example, on a system with 1 GB of physical RAM and 7 GB of swap with avm.overcommit_ratioof 30 it would yield aCommitLimitof 7.3 GB.Committed_AS— The total amount of memory, in kibibytes, estimated to complete the workload. This value represents the worst case scenario value, and also includes swap memory.VMallocTotal— The total amount of memory, in kibibytes, of total allocated virtual address space.VMallocUsed— The total amount of memory, in kibibytes, of used virtual address space.VMallocChunk— The largest contiguous block of memory, in kibibytes, of available virtual address space.HardwareCorrupted— The amount of memory, in kibibytes, with physical memory corruption problems, identified by the hardware and set aside by the kernel so it does not get used.AnonHugePages— The total amount of memory, in kibibytes, used by huge pages that are not backed by files and are mapped into userspace page tables.HugePages_Total— The total number of hugepages for the system. The number is derived by dividingHugepagesizeby the megabytes set aside for hugepages specified in/proc/sys/vm/hugetlb_pool. This statistic only appears on the x86, Itanium, and AMD64 architectures.HugePages_Free— The total number of hugepages available for the system. This statistic only appears on the x86, Itanium, and AMD64 architectures.HugePages_Rsvd— The number of unused huge pages reserved for hugetlbfs.HugePages_Surp— The number of surplus huge pages.Hugepagesize— The size for each hugepages unit in kibibytes. By default, the value is 4096 KB on uniprocessor kernels for 32 bit architectures. For SMP, hugemem kernels, and AMD64, the default is 2048 KB. For Itanium architectures, the default is 262144 KB. This statistic only appears on the x86, Itanium, and AMD64 architectures.DirectMap4k— The amount of memory, in kibibytes, mapped into kernel address space with 4 kB page mappings.DirectMap2M— The amount of memory, in kibibytes, mapped into kernel address space with 2 MB page mappings.
E.2.19. /proc/misc
63 device-mapper 175 agpgart 135 rtc 134 apm_bios
63 device-mapper 175 agpgart 135 rtc 134 apm_bios
E.2.20. /proc/modules
/proc/modules file output:
Note
/sbin/lsmod command.
Live, Loading, or Unloading are the only possible values.
oprofile.
E.2.21. /proc/mounts
/etc/mtab, except that /proc/mounts is more up-to-date.
ro) or read-write (rw). The fifth and sixth columns are dummy values designed to match the format used in /etc/mtab.
E.2.22. /proc/mtrr
/proc/mtrr file may look similar to the following:
reg00: base=0x00000000 ( 0MB), size= 256MB: write-back, count=1 reg01: base=0xe8000000 (3712MB), size= 32MB: write-combining, count=1
reg00: base=0x00000000 ( 0MB), size= 256MB: write-back, count=1
reg01: base=0xe8000000 (3712MB), size= 32MB: write-combining, count=1
/proc/mtrr file can increase performance more than 150%.
/usr/share/doc/kernel-doc-<kernel_version>/Documentation/<arch>/mtrr.txt
/usr/share/doc/kernel-doc-<kernel_version>/Documentation/<arch>/mtrr.txtE.2.23. /proc/partitions
major— The major number of the device with this partition. The major number in the/proc/partitions, (3), corresponds with the block deviceide0, in/proc/devices.minor— The minor number of the device with this partition. This serves to separate the partitions into different physical devices and relates to the number at the end of the name of the partition.#blocks— Lists the number of physical disk blocks contained in a particular partition.name— The name of the partition.
E.2.24. /proc/slabinfo
/proc/slabinfo file manually, the /usr/bin/slabtop program displays kernel slab cache information in real time. This program allows for custom configurations, including column sorting and screen refreshing.
/usr/bin/slabtop usually looks like the following example:
/proc/slabinfo that are included into /usr/bin/slabtop include:
OBJS— The total number of objects (memory blocks), including those in use (allocated), and some spares not in use.ACTIVE— The number of objects (memory blocks) that are in use (allocated).USE— Percentage of total objects that are active. ((ACTIVE/OBJS)(100))OBJ SIZE— The size of the objects.SLABS— The total number of slabs.OBJ/SLAB— The number of objects that fit into a slab.CACHE SIZE— The cache size of the slab.NAME— The name of the slab.
/usr/bin/slabtop program, refer to the slabtop man page.
E.2.25. /proc/stat
/proc/stat, which can be quite long, usually begins like the following example:
cpu— Measures the number of jiffies (1/100 of a second for x86 systems) that the system has been in user mode, user mode with low priority (nice), system mode, idle task, I/O wait, IRQ (hardirq), and softirq respectively. The IRQ (hardirq) is the direct response to a hardware event. The IRQ takes minimal work for queuing the "heavy" work up for the softirq to execute. The softirq runs at a lower priority than the IRQ and therefore may be interrupted more frequently. The total for all CPUs is given at the top, while each individual CPU is listed below with its own statistics. The following example is a 4-way Intel Pentium Xeon configuration with multi-threading enabled, therefore showing four physical processors and four virtual processors totaling eight processors.page— The number of memory pages the system has written in and out to disk.swap— The number of swap pages the system has brought in and out.intr— The number of interrupts the system has experienced.btime— The boot time, measured in the number of seconds since January 1, 1970, otherwise known as the epoch.
E.2.26. /proc/swaps
/proc/swaps may look similar to the following:
Filename Type Size Used Priority /dev/mapper/VolGroup00-LogVol01 partition 524280 0 -1
Filename Type Size Used Priority
/dev/mapper/VolGroup00-LogVol01 partition 524280 0 -1
/proc/ directory, /proc/swap provides a snapshot of every swap file name, the type of swap space, the total size, and the amount of space in use (in kilobytes). The priority column is useful when multiple swap files are in use. The lower the priority, the more likely the swap file is to be used.
E.2.27. /proc/sysrq-trigger
echo command to write to this file, a remote root user can execute most System Request Key commands remotely as if at the local terminal. To echo values to this file, the /proc/sys/kernel/sysrq must be set to a value other than 0. For more information about the System Request Key, see Section E.3.9.3, “/proc/sys/kernel/”.
E.2.28. /proc/uptime
/proc/uptime is quite minimal:
350735.47 234388.90
350735.47 234388.90E.2.29. /proc/version
gcc used to compile the kernel, and the time of kernel compilation. It also contains the kernel compiler's user name (in parentheses).
Linux version 2.6.8-1.523 (user@foo.redhat.com) (gcc version 3.4.1 20040714 \ (Red Hat Enterprise Linux 3.4.1-7)) #1 Mon Aug 16 13:27:03 EDT 2004
Linux version 2.6.8-1.523 (user@foo.redhat.com) (gcc version 3.4.1 20040714 \ (Red Hat Enterprise Linux 3.4.1-7)) #1 Mon Aug 16 13:27:03 EDT 2004
E.3. Directories within /proc/
/proc/ directory.
E.3.1. Process Directories
/proc/ directory contains a number of directories with numerical names. A listing of them may be similar to the following:
/proc/ process directory vanishes.
cmdline— Contains the command issued when starting the process.cwd— A symbolic link to the current working directory for the process.environ— A list of the environment variables for the process. The environment variable is given in all upper-case characters, and the value is in lower-case characters.exe— A symbolic link to the executable of this process.fd— A directory containing all of the file descriptors for a particular process. These are given in numbered links:Copy to Clipboard Copied! Toggle word wrap Toggle overflow maps— A list of memory maps to the various executables and library files associated with this process. This file can be rather long, depending upon the complexity of the process, but sample output from thesshdprocess begins like the following:Copy to Clipboard Copied! Toggle word wrap Toggle overflow mem— The memory held by the process. This file cannot be read by the user.root— A link to the root directory of the process.stat— The status of the process.statm— The status of the memory in use by the process. Below is a sample/proc/statmfile:263 210 210 5 0 205 0
263 210 210 5 0 205 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The seven columns relate to different memory statistics for the process. From left to right, they report the following aspects of the memory used:- Total program size, in kilobytes.
- Size of memory portions, in kilobytes.
- Number of pages that are shared.
- Number of pages that are code.
- Number of pages of data/stack.
- Number of library pages.
- Number of dirty pages.
status— The status of the process in a more readable form thanstatorstatm. Sample output forsshdlooks similar to the following:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The information in this output includes the process name and ID, the state (such asS (sleeping)orR (running)), user/group ID running the process, and detailed data regarding memory usage.
E.3.1.1. /proc/self/
/proc/self/ directory is a link to the currently running process. This allows a process to look at itself without having to know its process ID.
/proc/self/ directory produces the same contents as listing the process directory for that process.
E.3.2. /proc/bus/
/proc/bus/ by the same name, such as /proc/bus/pci/.
/proc/bus/ vary depending on the devices connected to the system. However, each bus type has at least one directory. Within these bus directories are normally at least one subdirectory with a numerical name, such as 001, which contain binary files.
/proc/bus/usb/ subdirectory contains files that track the various devices on any USB buses, as well as the drivers required for them. The following is a sample listing of a /proc/bus/usb/ directory:
total 0 dr-xr-xr-x 1 root root 0 May 3 16:25 001 -r--r--r-- 1 root root 0 May 3 16:25 devices -r--r--r-- 1 root root 0 May 3 16:25 drivers
total 0 dr-xr-xr-x 1 root root 0 May 3 16:25 001
-r--r--r-- 1 root root 0 May 3 16:25 devices
-r--r--r-- 1 root root 0 May 3 16:25 drivers
/proc/bus/usb/001/ directory contains all devices on the first USB bus and the devices file identifies the USB root hub on the motherboard.
/proc/bus/usb/devices file:
E.3.3. /proc/bus/pci
/proc/pci directory in favor of the /proc/bus/pci directory. Although you can get a list of all PCI devices present on the system using the command cat /proc/bus/pci/devices, the output is difficult to read and interpret.
E.3.4. /proc/driver/
rtc which provides output from the driver for the system's Real Time Clock (RTC), the device that keeps the time while the system is switched off. Sample output from /proc/driver/rtc looks like the following:
/usr/share/doc/kernel-doc-<kernel_version>/Documentation/rtc.txt.
E.3.5. /proc/fs
cat /proc/fs/nfsd/exports displays the file systems being shared and the permissions granted for those file systems. For more on file system sharing with NFS, see the Network File System (NFS) chapter of the Storage Administration Guide.
E.3.6. /proc/irq/
/proc/irq/prof_cpu_mask file is a bitmask that contains the default values for the smp_affinity file in the IRQ directory. The values in smp_affinity specify which CPUs handle that particular IRQ.
/proc/irq/ directory, see the following installed documentation:
/usr/share/doc/kernel-doc-kernel_version/Documentation/filesystems/proc.txt
/usr/share/doc/kernel-doc-kernel_version/Documentation/filesystems/proc.txt
E.3.7. /proc/net/
/proc/net/ directory:
arp— Lists the kernel's ARP table. This file is particularly useful for connecting a hardware address to an IP address on a system.atm/directory — The files within this directory contain Asynchronous Transfer Mode (ATM) settings and statistics. This directory is primarily used with ATM networking and ADSL cards.dev— Lists the various network devices configured on the system, complete with transmit and receive statistics. This file displays the number of bytes each interface has sent and received, the number of packets inbound and outbound, the number of errors seen, the number of packets dropped, and more.dev_mcast— Lists Layer2 multicast groups on which each device is listening.igmp— Lists the IP multicast addresses which this system joined.ip_conntrack— Lists tracked network connections for machines that are forwarding IP connections.ip_tables_names— Lists the types ofiptablesin use. This file is only present ifiptablesis active on the system and contains one or more of the following values:filter,mangle, ornat.ip_mr_cache— Lists the multicast routing cache.ip_mr_vif— Lists multicast virtual interfaces.netstat— Contains a broad yet detailed collection of networking statistics, including TCP timeouts, SYN cookies sent and received, and much more.psched— Lists global packet scheduler parameters.raw— Lists raw device statistics.route— Lists the kernel's routing table.rt_cache— Contains the current routing cache.snmp— List of Simple Network Management Protocol (SNMP) data for various networking protocols in use.sockstat— Provides socket statistics.tcp— Contains detailed TCP socket information.tr_rif— Lists the token ring RIF routing table.udp— Contains detailed UDP socket information.unix— Lists UNIX domain sockets currently in use.wireless— Lists wireless interface data.
E.3.8. /proc/scsi/
/proc/scsi/scsi, which contains a list of every recognized SCSI device. From this listing, the type of device, as well as the model name, vendor, SCSI channel and ID data is available.
/proc/scsi/, which contains files specific to each SCSI controller using that driver. From the previous example, aic7xxx/ and megaraid/ directories are present, since two drivers are in use. The files in each of the directories typically contain an I/O address range, IRQ information, and statistics for the SCSI controller using that driver. Each controller can report a different type and amount of information. The Adaptec AIC-7880 Ultra SCSI host adapter's file in this example system produces the following output:
E.3.9. /proc/sys/
/proc/sys/ directory is different from others in /proc/ because it not only provides information about the system but also allows the system administrator to immediately enable and disable kernel features.
Warning
/proc/sys/ directory. Changing the wrong setting may render the kernel unstable, requiring a system reboot.
/proc/sys/.
-l option at the shell prompt. If the file is writable, it may be used to configure the kernel. For example, a partial listing of /proc/sys/fs looks like the following:
-r--r--r-- 1 root root 0 May 10 16:14 dentry-state -rw-r--r-- 1 root root 0 May 10 16:14 dir-notify-enable -rw-r--r-- 1 root root 0 May 10 16:14 file-max -r--r--r-- 1 root root 0 May 10 16:14 file-nr
-r--r--r-- 1 root root 0 May 10 16:14 dentry-state
-rw-r--r-- 1 root root 0 May 10 16:14 dir-notify-enable
-rw-r--r-- 1 root root 0 May 10 16:14 file-max
-r--r--r-- 1 root root 0 May 10 16:14 file-nr
dir-notify-enable and file-max can be written to and, therefore, can be used to configure the kernel. The other files only provide feedback on current settings.
/proc/sys/ file is done by echoing the new value into the file. For example, to enable the System Request Key on a running kernel, type the command:
echo 1 > /proc/sys/kernel/sysrq
echo 1 > /proc/sys/kernel/sysrq
sysrq from 0 (off) to 1 (on).
/proc/sys/ configuration files contain more than one value. To correctly send new values to them, place a space character between each value passed with the echo command, such as is done in this example:
echo 4 2 45 > /proc/sys/kernel/acct
echo 4 2 45 > /proc/sys/kernel/acct
Note
echo command disappear when the system is restarted. To make configuration changes take effect after the system is rebooted, see Section E.4, “Using the sysctl Command”.
/proc/sys/ directory contains several subdirectories controlling different aspects of a running kernel.
E.3.9.1. /proc/sys/dev/
cdrom/ and raid/. Customized kernels can have other directories, such as parport/, which provides the ability to share one parallel port between multiple device drivers.
cdrom/ directory contains a file called info, which reveals a number of important CD-ROM parameters:
/proc/sys/dev/cdrom, such as autoclose and checkmedia, can be used to control the system's CD-ROM. Use the echo command to enable or disable these features.
/proc/sys/dev/raid/ directory becomes available with at least two files in it: speed_limit_min and speed_limit_max. These settings determine the acceleration of RAID devices for I/O intensive tasks, such as resyncing the disks.
E.3.9.2. /proc/sys/fs/
binfmt_misc/ directory is used to provide kernel support for miscellaneous binary formats.
/proc/sys/fs/ include:
dentry-state— Provides the status of the directory cache. The file looks similar to the following:57411 52939 45 0 0 0
57411 52939 45 0 0 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The first number reveals the total number of directory cache entries, while the second number displays the number of unused entries. The third number tells the number of seconds between when a directory has been freed and when it can be reclaimed, and the fourth measures the pages currently requested by the system. The last two numbers are not used and display only zeros.file-max— Lists the maximum number of file handles that the kernel allocates. Raising the value in this file can resolve errors caused by a lack of available file handles.file-nr— Lists the number of allocated file handles, used file handles, and the maximum number of file handles.overflowgidandoverflowuid— Defines the fixed group ID and user ID, respectively, for use with file systems that only support 16-bit group and user IDs.
E.3.9.3. /proc/sys/kernel/
acct— Controls the suspension of process accounting based on the percentage of free space available on the file system containing the log. By default, the file looks like the following:4 2 30
4 2 30Copy to Clipboard Copied! Toggle word wrap Toggle overflow The first value dictates the percentage of free space required for logging to resume, while the second value sets the threshold percentage of free space when logging is suspended. The third value sets the interval, in seconds, that the kernel polls the file system to see if logging should be suspended or resumed.ctrl-alt-del— Controls whether Ctrl+Alt+Delete gracefully restarts the computer usinginit(0) or forces an immediate reboot without syncing the dirty buffers to disk (1).domainname— Configures the system domain name, such asexample.com.exec-shield— Configures the Exec Shield feature of the kernel. Exec Shield provides protection against certain types of buffer overflow attacks.There are two possible values for this virtual file:0— Disables Exec Shield.1— Enables Exec Shield. This is the default value.
Important
If a system is running security-sensitive applications that were started while Exec Shield was disabled, these applications must be restarted when Exec Shield is enabled in order for Exec Shield to take effect.hostname— Configures the system host name, such aswww.example.com.hotplug— Configures the utility to be used when a configuration change is detected by the system. This is primarily used with USB and Cardbus PCI. The default value of/sbin/hotplugshould not be changed unless testing a new program to fulfill this role.modprobe— Sets the location of the program used to load kernel modules. The default value is/sbin/modprobewhich meanskmodcalls it to load the module when a kernel thread callskmod.msgmax— Sets the maximum size of any message sent from one process to another and is set to8192bytes by default. Be careful when raising this value, as queued messages between processes are stored in non-swappable kernel memory. Any increase inmsgmaxwould increase RAM requirements for the system.msgmnb— Sets the maximum number of bytes in a single message queue. The default is16384.msgmni— Sets the maximum number of message queue identifiers. The default is4008.osrelease— Lists the Linux kernel release number. This file can only be altered by changing the kernel source and recompiling.ostype— Displays the type of operating system. By default, this file is set toLinux, and this value can only be changed by changing the kernel source and recompiling.overflowgidandoverflowuid— Defines the fixed group ID and user ID, respectively, for use with system calls on architectures that only support 16-bit group and user IDs.panic— Defines the number of seconds the kernel postpones rebooting when the system experiences a kernel panic. By default, the value is set to0, which disables automatic rebooting after a panic.printk— This file controls a variety of settings related to printing or logging error messages. Each error message reported by the kernel has a loglevel associated with it that defines the importance of the message. The loglevel values break down in this order:0— Kernel emergency. The system is unusable.1— Kernel alert. Action must be taken immediately.2— Condition of the kernel is considered critical.3— General kernel error condition.4— General kernel warning condition.5— Kernel notice of a normal but significant condition.6— Kernel informational message.7— Kernel debug-level messages.
Four values are found in theprintkfile:6 4 1 7
6 4 1 7Copy to Clipboard Copied! Toggle word wrap Toggle overflow Each of these values defines a different rule for dealing with error messages. The first value, called the console loglevel, defines the lowest priority of messages printed to the console. (Note that, the lower the priority, the higher the loglevel number.) The second value sets the default loglevel for messages without an explicit loglevel attached to them. The third value sets the lowest possible loglevel configuration for the console loglevel. The last value sets the default value for the console loglevel.random/directory — Lists a number of values related to generating random numbers for the kernel.sem— Configures semaphore settings within the kernel. A semaphore is a System V IPC object that is used to control utilization of a particular process.shmall— Sets the total amount of shared memory that can be used at one time on the system, in bytes. By default, this value is2097152.shmmax— Sets the largest shared memory segment size allowed by the kernel. By default, this value is33554432. However, the kernel supports much larger values than this.shmmni— Sets the maximum number of shared memory segments for the whole system. By default, this value is4096.sysrq— Activates the System Request Key, if this value is set to anything other than zero (0), the default.The System Request Key allows immediate input to the kernel through simple key combinations. For example, the System Request Key can be used to immediately shut down or restart a system, sync all mounted file systems, or dump important information to the console. To initiate a System Request Key, type Alt+SysRq+system request code. Replace system request code with one of the following system request codes:r— Disables raw mode for the keyboard and sets it to XLATE (a limited keyboard mode which does not recognize modifiers such as Alt, Ctrl, or Shift for all keys).k— Kills all processes active in a virtual console. Also called Secure Access Key (SAK), it is often used to verify that the login prompt is spawned frominitand not a trojan copy designed to capture user names and passwords.b— Reboots the kernel without first unmounting file systems or syncing disks attached to the system.c— Crashes the system without first unmounting file systems or syncing disks attached to the system.o— Shuts off the system.s— Attempts to sync disks attached to the system.u— Attempts to unmount and remount all file systems as read-only.p— Outputs all flags and registers to the console.t— Outputs a list of processes to the console.m— Outputs memory statistics to the console.0through9— Sets the log level for the console.e— Kills all processes exceptinitusing SIGTERM.i— Kills all processes exceptinitusing SIGKILL.l— Kills all processes using SIGKILL (includinginit). The system is unusable after issuing this System Request Key code.h— Displays help text.
This feature is most beneficial when using a development kernel or when experiencing system freezes.Warning
The System Request Key feature is considered a security risk because an unattended console provides an attacker with access to the system. For this reason, it is turned off by default.See/usr/share/doc/kernel-doc-kernel_version/Documentation/sysrq.txtfor more information about the System Request Key.tainted— Indicates whether a non-GPL module is loaded.0— No non-GPL modules are loaded.1— At least one module without a GPL license (including modules with no license) is loaded.2— At least one module was force-loaded with the commandinsmod -f.
threads-max— Sets the maximum number of threads to be used by the kernel, with a default value of2048.version— Displays the date and time the kernel was last compiled. The first field in this file, such as#3, relates to the number of times a kernel was built from the source base.
E.3.9.4. /proc/sys/net/
ethernet/, ipv4/, ipx/, and ipv6/. By altering the files within these directories, system administrators are able to adjust the network configuration on a running system.
/proc/sys/net/ directories are discussed.
/proc/sys/net/core/ directory contains a variety of settings that control the interaction between the kernel and networking layers. The most important of these files are:
message_burst— Sets the maximum number of new warning messages to be written to the kernel log in the time interval defined bymessage_cost. The default value of this file is10.In combination withmessage_cost, this setting is used to enforce a rate limit on warning messages written to the kernel log from the networking code and mitigate Denial of Service (DoS) attacks. The idea of a DoS attack is to bombard the targeted system with requests that generate errors and either fill up disk partitions with log files or require all of the system's resources to handle the error logging.The settings inmessage_burstandmessage_costare designed to be modified based on the system's acceptable risk versus the need for comprehensive logging. For example, by settingmessage_burstto 10 andmessage_costto 5, you allow the system to write the maximum number of 10 messages every 5 seconds.message_cost— Sets a cost on every warning message by defining a time interval formessage_burst. The higher the value is, the more likely the warning message is ignored. The default value of this file is5.netdev_max_backlog— Sets the maximum number of packets allowed to queue when a particular interface receives packets faster than the kernel can process them. The default value for this file is1000.optmem_max— Configures the maximum ancillary buffer size allowed per socket.rmem_default— Sets the receive socket buffer default size in bytes.rmem_max— Sets the receive socket buffer maximum size in bytes.wmem_default— Sets the send socket buffer default size in bytes.wmem_max— Sets the send socket buffer maximum size in bytes.
/proc/sys/net/ipv4/ directory contains additional networking settings. Many of these settings, used in conjunction with one another, are useful in preventing attacks on the system or when using the system to act as a router.
Warning
/proc/sys/net/ipv4/ directory:
icmp_echo_ignore_allandicmp_echo_ignore_broadcasts— Allows the kernel to ignore ICMP ECHO packets from every host or only those originating from broadcast and multicast addresses, respectively. A value of0allows the kernel to respond, while a value of1ignores the packets.ip_default_ttl— Sets the default Time To Live (TTL), which limits the number of hops a packet may make before reaching its destination. Increasing this value can diminish system performance.ip_forward— Permits interfaces on the system to forward packets. By default, this file is set to0. Setting this file to1enables network packet forwarding.ip_local_port_range— Specifies the range of ports to be used by TCP or UDP when a local port is needed. The first number is the lowest port to be used and the second number specifies the highest port. Any systems that expect to require more ports than the default 1024 to 4999 should use a range from 32768 to 61000.tcp_syn_retries— Provides a limit on the number of times the system re-transmits a SYN packet when attempting to make a connection.tcp_retries1— Sets the number of permitted re-transmissions attempting to answer an incoming connection. Default of3.tcp_retries2— Sets the number of permitted re-transmissions of TCP packets. Default of15.
/usr/share/doc/kernel-doc-kernel_version/Documentation/networking/ip-sysctl.txt file contains a list of files and options available in the /proc/sys/net/ipv4/ and /proc/sys/net/ipv6/ directories. Use the sysctl -a command to list the parameters in the sysctl key format.
/proc/sys/net/ipv4/ directory and each covers a different aspect of the network stack. The /proc/sys/net/ipv4/conf/ directory allows each system interface to be configured in different ways, including the use of default settings for unconfigured devices (in the /proc/sys/net/ipv4/conf/default/ subdirectory) and settings that override all special configurations (in the /proc/sys/net/ipv4/conf/all/ subdirectory).
Important
rp_filter file, see the entry on Reverse Path Forwarding in the Red Hat Enterprise Linux 6 Security Guide and The Red Hat Knowledgebase article about rp_filter.
/proc/sys/net/ipv4/neigh/ directory contains settings for communicating with a host directly connected to the system (called a network neighbor) and also contains different settings for systems more than one hop away.
/proc/sys/net/ipv4/route/. Unlike conf/ and neigh/, the /proc/sys/net/ipv4/route/ directory contains specifications that apply to routing with any interfaces on the system. Many of these settings, such as max_size, max_delay, and min_delay, relate to controlling the size of the routing cache. To clear the routing cache, write any value to the flush file.
/usr/share/doc/kernel-doc-kernel_version/Documentation/filesystems/proc.txt
/usr/share/doc/kernel-doc-kernel_version/Documentation/filesystems/proc.txt
E.3.9.5. /proc/sys/vm/
/proc/sys/vm/ directory:
block_dump— Configures block I/O debugging when enabled. All read/write and block dirtying operations done to files are logged accordingly. This can be useful if diagnosing disk spin up and spin downs for laptop battery conservation. All output whenblock_dumpis enabled can be retrieved viadmesg. The default value is0.Note
Ifblock_dumpis enabled at the same time as kernel debugging, it is prudent to stop theklogddaemon, as it generates erroneous disk activity caused byblock_dump.dirty_background_ratio— Starts background writeback of dirty data at this percentage of total memory, via a pdflush daemon. The default value is10.dirty_expire_centisecs— Defines when dirty in-memory data is old enough to be eligible for writeout. Data which has been dirty in-memory for longer than this interval is written out next time a pdflush daemon wakes up. The default value is3000, expressed in hundredths of a second.dirty_ratio— Starts active writeback of dirty data at this percentage of total memory for the generator of dirty data, via pdflush. The default value is20.dirty_writeback_centisecs— Defines the interval between pdflush daemon wakeups, which periodically writes dirty in-memory data out to disk. The default value is500, expressed in hundredths of a second.laptop_mode— Minimizes the number of times that a hard disk needs to spin up by keeping the disk spun down for as long as possible, therefore conserving battery power on laptops. This increases efficiency by combining all future I/O processes together, reducing the frequency of spin ups. The default value is0, but is automatically enabled in case a battery on a laptop is used.This value is controlled automatically by the acpid daemon once a user is notified battery power is enabled. No user modifications or interactions are necessary if the laptop supports the ACPI (Advanced Configuration and Power Interface) specification.For more information, see the following installed documentation:/usr/share/doc/kernel-doc-kernel_version/Documentation/laptop-mode.txtmax_map_count— Configures the maximum number of memory map areas a process may have. In most cases, the default value of65536is appropriate.min_free_kbytes— Forces the Linux VM (virtual memory manager) to keep a minimum number of kilobytes free. The VM uses this number to compute apages_minvalue for eachlowmemzone in the system. The default value is in respect to the total memory on the machine.nr_hugepages— Indicates the current number of configuredhugetlbpages in the kernel.For more information, see the following installed documentation:/usr/share/doc/kernel-doc-kernel_version/Documentation/vm/hugetlbpage.txtnr_pdflush_threads— Indicates the number of pdflush daemons that are currently running. This file is read-only, and should not be changed by the user. Under heavy I/O loads, the default value of two is increased by the kernel.overcommit_memory— Configures the conditions under which a large memory request is accepted or denied. The following three modes are available:0— The kernel performs heuristic memory over commit handling by estimating the amount of memory available and failing requests that are blatantly invalid. Unfortunately, since memory is allocated using a heuristic rather than a precise algorithm, this setting can sometimes allow available memory on the system to be overloaded. This is the default setting.1— The kernel performs no memory over commit handling. Under this setting, the potential for memory overload is increased, but so is performance for memory intensive tasks (such as those executed by some scientific software).2— The kernel fails any request for memory that would cause the total address space to exceed the sum of the allocated swap space and the percentage of physical RAM specified in/proc/sys/vm/overcommit_ratio. This setting is best for those who desire less risk of memory overcommitment.Note
This setting is only recommended for systems with swap areas larger than physical memory.
overcommit_ratio— Specifies the percentage of physical RAM considered when/proc/sys/vm/overcommit_memoryis set to2. The default value is50.page-cluster— Sets the number of pages read in a single attempt. The default value of3, which actually relates to 16 pages, is appropriate for most systems.swappiness— Determines how much a machine should swap. The higher the value, the more swapping occurs. The default value, as a percentage, is set to60.
/usr/share/doc/kernel-doc-kernel_version/Documentation/, which contains additional information.
E.3.10. /proc/sysvipc/
msg), semaphores (sem), and shared memory (shm).
E.3.11. /proc/tty/
drivers file is a list of the current tty devices in use, as in the following example:
/proc/tty/driver/serial file lists the usage statistics and status of each of the serial tty lines.
E.3.12. /proc/PID/
/proc/sys/vm/panic_on_oom. When set to 1 the kernel will panic on OOM. A setting of 0 instructs the kernel to call a function named oom_killer on an OOM. Usually, oom_killer can kill rogue processes and the system will survive.
/proc/sys/vm/panic_on_oom.
oom_killer score. In /proc/PID/ there are two tools labeled oom_adj and oom_score. Valid scores for oom_adj are in the range -16 to +15. To see the current oom_killer score, view the oom_score for the process. oom_killer will kill processes with the highest scores first.
oom_killer will kill it.
oom_killer for that process. In the example below, oom_score returns a value of 0, indicating that this process would not be killed.
badness() is used to determine the actual score for each process. This is done by adding up 'points' for each examined process. The process scoring is done in the following way:
- The basis of each process's score is its memory size.
- The memory size of any of the process's children (not including a kernel thread) is also added to the score
- The process's score is increased for 'niced' processes and decreased for long running processes.
- Processes with the
CAP_SYS_ADMINandCAP_SYS_RAWIOcapabilities have their scores reduced. - The final score is then bitshifted by the value saved in the
oom_adjfile.
oom_score value will most probably be a non-privileged, recently started process that, along with its children, uses a large amount of memory, has been 'niced', and handles no raw I/O.
E.4. Using the sysctl Command
/sbin/sysctl command is used to view, set, and automate kernel settings in the /proc/sys/ directory.
/proc/sys/ directory, type the /sbin/sysctl -a command as root. This creates a large, comprehensive list, a small portion of which looks something like the following:
net.ipv4.route.min_pmtu = 552 kernel.sysrq = 0 kernel.sem = 250 32000 32 128
net.ipv4.route.min_pmtu = 552
kernel.sysrq = 0
kernel.sem = 250 32000 32 128/proc/sys/net/ipv4/route/min_pmtu file is listed as net.ipv4.route.min_pmtu, with the directory slashes replaced by dots and the proc.sys portion assumed.
sysctl command can be used in place of echo to assign values to writable files in the /proc/sys/ directory. For example, instead of using the command
echo 1 > /proc/sys/kernel/sysrq
echo 1 > /proc/sys/kernel/sysrq
sysctl command as follows:
sysctl -w kernel.sysrq="1" kernel.sysrq = 1
sysctl -w kernel.sysrq="1"
kernel.sysrq = 1
/proc/sys/ is helpful during testing, this method does not work as well on a production system as special settings within /proc/sys/ are lost when the machine is rebooted. To preserve custom settings, add them to the /etc/sysctl.conf file.
/etc/sysctl.conf file is installed by the initscripts package to override some kernel default values and therefore only contains a few of the possible parameters. Use the sysctl -a command to list the parameters in the sysctl key format. See the /usr/share/doc/kernel-doc-kernel_version/Documentation/networking/ip-sysctl.txt file for more information on the possible settings.
init program runs the /etc/rc.d/rc.sysinit script. This script contains a command to execute sysctl using /etc/sysctl.conf to determine the values passed to the kernel. Any values added to /etc/sysctl.conf therefore take effect each time the system boots. Note that modules loaded after sysctl has parsed this file might override the settings.
E.5. Additional Resources
proc file system.
Installable Documentation
/usr/share/doc/kernel-doc-kernel_version/Documentation/— This directory, which is provided by the kernel-doc package, contains documentation about theprocfile system. Before accessing the kernel documentation, you must run the following command as root:yum install kernel-doc
~]# yum install kernel-docCopy to Clipboard Copied! Toggle word wrap Toggle overflow /usr/share/doc/kernel-doc-kernel_version/Documentation/filesystems/proc.txt— Contains assorted, but limited, information about all aspects of the/proc/directory./usr/share/doc/kernel-doc-kernel_version/Documentation/sysrq.txt— An overview of System Request Key options./usr/share/doc/kernel-doc-kernel_version/Documentation/sysctl/— A directory containing a variety ofsysctltips, including modifying values that concern the kernel (kernel.txt), accessing file systems (fs.txt), and virtual memory use (vm.txt)./usr/share/doc/kernel-doc-kernel_version/Documentation/networking/ip-sysctl.txt— A detailed overview of IP networking options.
Appendix F. Revision History
| Revision History | |||
|---|---|---|---|
| Revision 9-3 | Wed Mar 15 2017 | ||
| |||
| Revision 8-3 | Mon May 30 2016 | ||
| |||
| Revision 8-2 | Wed May 25 2016 | ||
| |||
| Revision 8-1 | Thu May 10 2016 | ||
| |||
| Revision 7-1 | Tue Jul 14 2015 | ||
| |||
| Revision 7-0 | Fri Apr 17 2015 | ||
| |||
| Revision 6-3 | Thu Apr 2 2015 | ||
| |||
| Revision 6-2 | Fri Oct 14 2014 | ||
| |||
| Revision 6-1 | Fri Aug 22 2014 | ||
| |||
| Revision 6-0 | Mon Aug 11 2014 | ||
| |||
| Revision 5-1 | Thu Nov 21 2013 | ||
| |||
| Revision 5-0 | Thu Oct 3 2013 | ||
| |||
| Revision 4-1 | Thu Feb 21 2013 | ||
| |||
| Revision 4-0 | Thu Dec 6 2012 | ||
| |||
| Revision 3-1 | Wed Jun 20 2012 | ||
| |||
| Revision 3-0 | Tue Apr 24 2012 | ||
| |||
| Revision 2-1 | Tue Dec 6 2011 | ||
| |||
| Revision 2-0 | Mon Oct 3 2011 | ||
| |||
| Revision 1-1 | Wed May 19 2011 | ||
| |||
| Revision 1-0 | Tue Mar 22 2011 | ||
| |||
| Revision 0-1 | Tue Nov 9 2010 | ||
| |||
| Revision 0-0 | Mon Nov 16 2009 | ||
| |||
Index
Symbols
- .fetchmailrc, Fetchmail Configuration Options
- server options, Server Options
- user options, User Options
- .htaccess , Common httpd.conf Directives
- (see also Apache HTTP Server )
- .htpasswd , Common httpd.conf Directives
- (see also Apache HTTP Server )
- .procmailrc, Procmail Configuration
- /dev/oprofile/, Understanding /dev/oprofile/
- /etc/named.conf (see BIND)
- /etc/sysconfig/ directory (see sysconfig directory)
- /etc/sysconfig/dhcpd, Starting and Stopping the Server
- /proc/ directory (see proc file system)
- /var/spool/anacron , Configuring Anacron Jobs
- /var/spool/cron , Configuring Cron Jobs
- (see OProfile)
A
- Access Control
- configuring in SSSD, Creating Domains: Access Control
- SSSD rules, Creating Domains: Access Control
- anacron, Cron and Anacron
- anacron configuration file, Configuring Anacron Jobs
- user-defined tasks, Configuring Anacron Jobs
- anacrontab , Configuring Anacron Jobs
- Apache HTTP Server
- additional resources
- installable documentation, Additional Resources
- installed documentation, Additional Resources
- useful websites, Additional Resources
- checking configuration, Editing the Configuration Files
- checking status, Verifying the Service Status
- directives
- <Directory> , Common httpd.conf Directives
- <IfDefine> , Common httpd.conf Directives
- <IfModule> , Common httpd.conf Directives
- <Location> , Common httpd.conf Directives
- <Proxy> , Common httpd.conf Directives
- <VirtualHost> , Common httpd.conf Directives
- AccessFileName , Common httpd.conf Directives
- Action , Common httpd.conf Directives
- AddDescription , Common httpd.conf Directives
- AddEncoding , Common httpd.conf Directives
- AddHandler , Common httpd.conf Directives
- AddIcon , Common httpd.conf Directives
- AddIconByEncoding , Common httpd.conf Directives
- AddIconByType , Common httpd.conf Directives
- AddLanguage , Common httpd.conf Directives
- AddType , Common httpd.conf Directives
- Alias , Common httpd.conf Directives
- Allow , Common httpd.conf Directives
- AllowOverride , Common httpd.conf Directives
- BrowserMatch , Common httpd.conf Directives
- CacheDefaultExpire , Common httpd.conf Directives
- CacheDisable , Common httpd.conf Directives
- CacheEnable , Common httpd.conf Directives
- CacheLastModifiedFactor , Common httpd.conf Directives
- CacheMaxExpire , Common httpd.conf Directives
- CacheNegotiatedDocs , Common httpd.conf Directives
- CacheRoot , Common httpd.conf Directives
- CustomLog , Common httpd.conf Directives
- DefaultIcon , Common httpd.conf Directives
- DefaultType , Common httpd.conf Directives
- Deny , Common httpd.conf Directives
- DirectoryIndex , Common httpd.conf Directives
- DocumentRoot , Common httpd.conf Directives
- ErrorDocument , Common httpd.conf Directives
- ErrorLog , Common httpd.conf Directives
- ExtendedStatus , Common httpd.conf Directives
- Group , Common httpd.conf Directives
- HeaderName , Common httpd.conf Directives
- HostnameLookups , Common httpd.conf Directives
- Include , Common httpd.conf Directives
- IndexIgnore , Common httpd.conf Directives
- IndexOptions , Common httpd.conf Directives
- KeepAlive , Common httpd.conf Directives
- KeepAliveTimeout , Common httpd.conf Directives
- LanguagePriority , Common httpd.conf Directives
- Listen , Common httpd.conf Directives
- LoadModule , Common httpd.conf Directives
- LogFormat , Common httpd.conf Directives
- LogLevel , Common httpd.conf Directives
- MaxClients , Common Multi-Processing Module Directives
- MaxKeepAliveRequests , Common httpd.conf Directives
- MaxSpareServers , Common Multi-Processing Module Directives
- MaxSpareThreads , Common Multi-Processing Module Directives
- MinSpareServers , Common Multi-Processing Module Directives
- MinSpareThreads , Common Multi-Processing Module Directives
- NameVirtualHost , Common httpd.conf Directives
- Options , Common httpd.conf Directives
- Order , Common httpd.conf Directives
- PidFile , Common httpd.conf Directives
- ProxyRequests , Common httpd.conf Directives
- ReadmeName , Common httpd.conf Directives
- Redirect , Common httpd.conf Directives
- ScriptAlias , Common httpd.conf Directives
- ServerAdmin , Common httpd.conf Directives
- ServerName , Common httpd.conf Directives
- ServerRoot , Common httpd.conf Directives
- ServerSignature , Common httpd.conf Directives
- ServerTokens , Common httpd.conf Directives
- SetEnvIf , Common ssl.conf Directives
- StartServers , Common Multi-Processing Module Directives
- SuexecUserGroup , Common httpd.conf Directives
- ThreadsPerChild , Common Multi-Processing Module Directives
- Timeout , Common httpd.conf Directives
- TypesConfig , Common httpd.conf Directives
- UseCanonicalName , Common httpd.conf Directives
- User , Common httpd.conf Directives
- UserDir , Common httpd.conf Directives
- directories
- /etc/httpd/ , Common httpd.conf Directives
- /etc/httpd/conf.d/ , Editing the Configuration Files, Common httpd.conf Directives
- /usr/lib/httpd/modules/ , Common httpd.conf Directives, Working with Modules
- /usr/lib64/httpd/modules/ , Common httpd.conf Directives, Working with Modules
- /var/cache/mod_proxy/ , Common httpd.conf Directives
- /var/www/cgi-bin/ , Common httpd.conf Directives
- /var/www/html/ , Common httpd.conf Directives
- /var/www/icons/ , Common httpd.conf Directives
- ~/public_html/ , Common httpd.conf Directives
- files
- .htaccess , Common httpd.conf Directives
- .htpasswd , Common httpd.conf Directives
- /etc/httpd/conf.d/nss.conf , Enabling the mod_nss Module
- /etc/httpd/conf.d/ssl.conf , Common ssl.conf Directives, Enabling the mod_ssl Module
- /etc/httpd/conf/httpd.conf , Editing the Configuration Files, Common httpd.conf Directives, Common Multi-Processing Module Directives
- /etc/httpd/logs/access_log , Common httpd.conf Directives
- /etc/httpd/logs/error_log , Common httpd.conf Directives
- /etc/httpd/run/httpd.pid , Common httpd.conf Directives
- /etc/mime.types , Common httpd.conf Directives
- modules
- developing, Writing a Module
- loading, Loading a Module
- mod_asis, Notable Changes
- mod_cache, New Features
- mod_cern_meta, Notable Changes
- mod_disk_cache, New Features
- mod_ext_filter, Notable Changes
- mod_proxy_balancer, New Features
- mod_rewrite , Common httpd.conf Directives
- mod_ssl , Setting Up an SSL Server
- mod_userdir, Updating the Configuration
- restarting, Restarting the Service
- SSL server
- certificate, An Overview of Certificates and Security, Using an Existing Key and Certificate, Generating a New Key and Certificate
- certificate authority, An Overview of Certificates and Security
- private key, An Overview of Certificates and Security, Using an Existing Key and Certificate, Generating a New Key and Certificate
- public key, An Overview of Certificates and Security
- starting, Starting the Service
- stopping, Stopping the Service
- version 2.2
- changes, Notable Changes
- features, New Features
- updating from version 2.0, Updating the Configuration
- virtual host, Setting Up Virtual Hosts
- at , At and Batch
- additional resources, Additional Resources
- authconfig (see Authentication Configuration Tool)
- authentication
- Authentication Configuration Tool, Configuring System Authentication
- using fingerprint support, Using Fingerprint Authentication
- using smart card authentication, Enabling Smart Card Authentication
- Authentication Configuration Tool
- and Kerberos authentication, Using Kerberos with LDAP or NIS Authentication
- and LDAP, Configuring LDAP Authentication
- and NIS, Configuring NIS Authentication
- and Winbind, Configuring Winbind Authentication
- and Winbind authentication, Configuring Winbind Authentication
- authoritative nameserver (see BIND)
- Automated Tasks, Automating System Tasks
B
- batch , At and Batch
- additional resources, Additional Resources
- Berkeley Internet Name Domain (see BIND)
- BIND
- additional resources
- installed documentation, Installed Documentation
- related books, Related Books
- useful websites, Useful Websites
- common mistakes, Common Mistakes to Avoid
- configuration
- acl statement, Common Statement Types
- comment tags, Comment Tags
- controls statement, Other Statement Types
- include statement, Common Statement Types
- key statement, Other Statement Types
- logging statement, Other Statement Types
- options statement, Common Statement Types
- server statement, Other Statement Types
- trusted-keys statement, Other Statement Types
- view statement, Other Statement Types
- zone statement, Common Statement Types
- directories
- /etc/named/ , Configuring the named Service
- /var/named/ , Editing Zone Files
- /var/named/data/ , Editing Zone Files
- /var/named/dynamic/ , Editing Zone Files
- /var/named/slaves/ , Editing Zone Files
- features
- Automatic Zone Transfer (AXFR), Incremental Zone Transfers (IXFR)
- DNS Security Extensions (DNSSEC), DNS Security Extensions (DNSSEC)
- Incremental Zone Transfer (IXFR), Incremental Zone Transfers (IXFR)
- Internet Protocol version 6 (IPv6), Internet Protocol version 6 (IPv6)
- multiple views, Multiple Views
- Transaction SIGnature (TSIG), Transaction SIGnatures (TSIG)
- files
- /etc/named.conf , Configuring the named Service, Configuring the Utility
- /etc/rndc.conf , Configuring the Utility
- /etc/rndc.key , Configuring the Utility
- resource record, Nameserver Zones
- types
- authoritative nameserver, Nameserver Types
- primary (master) nameserver, Nameserver Zones, Nameserver Types
- recursive nameserver, Nameserver Types
- secondary (slave) nameserver, Nameserver Zones, Nameserver Types
- utilities
- zones
- $INCLUDE directive, Common Directives
- $ORIGIN directive, Common Directives
- $TTL directive, Common Directives
- A (Address) resource record, Common Resource Records
- CNAME (Canonical Name) resource record, Common Resource Records
- comment tags, Comment Tags
- description, Nameserver Zones
- example usage, A Simple Zone File, A Reverse Name Resolution Zone File
- MX (Mail Exchange) resource record, Common Resource Records
- NS (Nameserver) resource record, Common Resource Records
- PTR (Pointer) resource record, Common Resource Records
- SOA (Start of Authority) resource record, Common Resource Records
- blkid, Using the blkid Command
- block devices, /proc/devices
- (see also /proc/devices)
- definition of, /proc/devices
- bonding (see channel bonding)
- boot loader
- verifying, Verifying the Boot Loader
- boot media, Preparing to Upgrade
C
- ch-email .fetchmailrc
- global options, Global Options
- channel bonding
- configuration, Using Channel Bonding
- description, Using Channel Bonding
- interface
- configuration of, Channel Bonding Interfaces
- parameters to bonded interfaces, Bonding Module Directives
- channel bonding interface (see kernel module)
- character devices, /proc/devices
- (see also /proc/devices)
- definition of, /proc/devices
- chkconfig (see services configuration)
- Configuration File Changes, Preserving Configuration File Changes
- CPU usage, Viewing CPU Usage
- crash
- analyzing the dump
- message buffer, Displaying the Message Buffer
- open files, Displaying Open Files
- processes, Displaying a Process Status
- stack trace, Displaying a Backtrace
- virtual memory, Displaying Virtual Memory Information
- opening the dump image, Running the crash Utility
- system requirements, Analyzing the Core Dump
- createrepo, Creating a Yum Repository
- cron, Cron and Anacron
- additional resources, Additional Resources
- cron configuration file, Configuring Cron Jobs
- user-defined tasks, Configuring Cron Jobs
- crontab , Configuring Cron Jobs
- CUPS (see Printer Configuration)
D
- date (see date configuration)
- date configuration
- date, Date and Time Setup
- system-config-date, Date and Time Properties
- default gateway, Static Routes and the Default Gateway
- deleting cache files
- in SSSD, Managing the SSSD Cache
- Denial of Service attack, /proc/sys/net/
- (see also /proc/sys/net/ directory)
- definition of, /proc/sys/net/
- desktop environments (see X)
- df, Using the df Command
- DHCP, DHCP Servers
- additional resources, Additional Resources
- client configuration, Configuring a DHCPv4 Client
- command-line options, Starting and Stopping the Server
- connecting to, Configuring a DHCPv4 Client
- dhcpd.conf, Configuration File
- dhcpd.leases, Starting and Stopping the Server
- dhcpd6.conf, DHCP for IPv6 (DHCPv6)
- DHCPv6, DHCP for IPv6 (DHCPv6)
- dhcrelay, DHCP Relay Agent
- global parameters, Configuration File
- group, Configuration File
- options, Configuration File
- reasons for using, Why Use DHCP?
- Relay Agent, DHCP Relay Agent
- shared-network, Configuration File
- starting the server, Starting and Stopping the Server
- stopping the server, Starting and Stopping the Server
- subnet, Configuration File
- dhcpd.conf, Configuration File
- dhcpd.leases, Starting and Stopping the Server
- DHCPv4
- server configuration, Configuring a DHCPv4 Server
- dhcrelay, DHCP Relay Agent
- dig (see BIND)
- directory server (see OpenLDAP)
- display managers (see X)
- DNS
- definition, DNS Servers
- (see also BIND)
- documentation
- finding installed, Practical and Common Examples of RPM Usage
- DoS attack (see Denial of Service attack)
- downgrade
- and SSSD, Downgrading SSSD
- drivers (see kernel module)
- DSA keys
- generating, Generating Key Pairs
- du, Using the du Command
- Dynamic Host Configuration Protocol (see DHCP)
E
- additional resources, Additional Resources
- installed documentation, Installed Documentation
- online documentation, Online Documentation
- related books, Related Books
- Fetchmail, Fetchmail
- mail server
- Dovecot, Dovecot
- Postfix, Postfix
- Procmail, Mail Delivery Agents
- program classifications, Email Program Classifications
- protocols, Email Protocols
- security, Securing Communication
- clients, Secure Email Clients
- servers, Securing Email Client Communications
- Sendmail, Sendmail
- spam
- filtering out, Spam Filters
- types
- Mail Delivery Agent, Mail Delivery Agent
- Mail Transport Agent, Mail Transport Agent
- Mail User Agent, Mail User Agent
- epoch, /proc/stat
- (see also /proc/stat)
- definition of, /proc/stat
- Ethernet (see network)
- Ethtool
- command
- devname , Ethtool
- option
- --advertise , Ethtool
- --autoneg , Ethtool
- --duplex , Ethtool
- --features , Ethtool
- --identify , Ethtool
- --msglvl , Ethtool
- --phyad , Ethtool
- --port , Ethtool
- --show-features , Ethtool
- --show-time-stamping , Ethtool
- --sopass , Ethtool
- --speed , Ethtool
- --statistics , Ethtool
- --test , Ethtool
- --wol , Ethtool
- --xcvr , Ethtool
- exec-shield
- enabling, /proc/sys/kernel/
- introducing, /proc/sys/kernel/
- execution domains, /proc/execdomains
- (see also /proc/execdomains)
- definition of, /proc/execdomains
- extra packages for Enterprise Linux (EPEL)
- installable packages, Finding RPM Packages
F
- Fetchmail, Fetchmail
- additional resources, Additional Resources
- command options, Fetchmail Command Options
- informational, Informational or Debugging Options
- special, Special Options
- configuration options, Fetchmail Configuration Options
- global options, Global Options
- server options, Server Options
- user options, User Options
- file system
- virtual (see proc file system)
- file systems, Viewing Block Devices and File Systems
- files, proc file system
- changing, Changing Virtual Files, Using the sysctl Command
- viewing, Viewing Virtual Files, Using the sysctl Command
- findmnt, Using the findmnt Command
- findsmb, Connecting to a Samba Share
- findsmb program, Samba Distribution Programs
- FQDN (see fully qualified domain name)
- frame buffer device, /proc/fb
- (see also /proc/fb)
- free, Using the free Command
- FTP, FTP
- (see also vsftpd)
- active mode, The File Transfer Protocol
- command port, The File Transfer Protocol
- data port, The File Transfer Protocol
- definition of, FTP
- introducing, The File Transfer Protocol
- passive mode, The File Transfer Protocol
- fully qualified domain name, Nameserver Zones
G
- gamin, Monitoring Files and Directories with gamin
- GNOME, Desktop Environments
- (see also X)
- gnome-system-log (see Log File Viewer)
- gnome-system-monitor, Using the System Monitor Tool, Using the System Monitor Tool, Using the System Monitor Tool, Using the System Monitor Tool
- GnuPG
- checking RPM package signatures, Checking a Package's Signature
- group configuration
- modifying group properties, Modifying Group Properties
- groups
- additional resources, Additional Resources
- installed documentation, Installed Documentation
- GRUB boot loader
- configuration file, Configuring the GRUB Boot Loader
- configuring, Configuring the GRUB Boot Loader
H
- hardware
- viewing, Viewing Hardware Information
- HTTP server (see Apache HTTP Server)
- httpd (see Apache HTTP Server )
- hugepages
- configuration of, /proc/sys/vm/
I
- ifdown, Interface Control Scripts
- ifup, Interface Control Scripts
- information
- about your system, System Monitoring Tools
- initial RAM disk image
- verifying, Verifying the Initial RAM Disk Image
- IBM eServer System i, Verifying the Initial RAM Disk Image
- initial RPM repositories
- installable packages, Finding RPM Packages
- insmod, Loading a Module
- (see also kernel module)
- installing package groups
- installing package groups with PackageKit, Installing and Removing Package Groups
- installing the kernel, Manually Upgrading the Kernel
K
- KDE, Desktop Environments
- (see also X)
- kdump
- additional resources
- manual pages, Additional Resources
- websites, Additional Resources
- analyzing the dump (see crash)
- configuring the service
- default action, Using the Kernel Dump Configuration Utility, Configuring kdump on the Command Line
- dump image compression, Using the Kernel Dump Configuration Utility, Configuring kdump on the Command Line
- filtering level, Using the Kernel Dump Configuration Utility, Configuring kdump on the Command Line
- initial RAM disk, Using the Kernel Dump Configuration Utility, Configuring kdump on the Command Line
- kernel image, Using the Kernel Dump Configuration Utility, Configuring kdump on the Command Line
- kernel options, Using the Kernel Dump Configuration Utility, Configuring kdump on the Command Line
- memory usage, Configuring kdump at First Boot, Using the Kernel Dump Configuration Utility, Configuring kdump on the Command Line
- supported targets, Using the Kernel Dump Configuration Utility, Configuring kdump on the Command Line
- target location, Using the Kernel Dump Configuration Utility, Configuring kdump on the Command Line
- enabling the service, Configuring kdump at First Boot, Using the Kernel Dump Configuration Utility, Configuring kdump on the Command Line
- fadump, Using fadump on IBM PowerPC hardware
- installing, Installing the kdump Service
- running the service, Configuring kdump on the Command Line
- sadump, Using sadump on Fujitsu PRIMEQUEST systems
- system requirements, Configuring the kdump Service
- testing the configuration, Testing the Configuration
- kernel
- downloading, Downloading the Upgraded Kernel
- installing kernel packages, Manually Upgrading the Kernel
- kernel packages, Overview of Kernel Packages
- package, Manually Upgrading the Kernel
- performing kernel upgrade, Performing the Upgrade
- RPM package, Manually Upgrading the Kernel
- upgrade kernel available, Downloading the Upgraded Kernel
- Red Hat network, Downloading the Upgraded Kernel
- Security Errata, Downloading the Upgraded Kernel
- upgrading
- preparing, Preparing to Upgrade
- working boot media, Preparing to Upgrade
- upgrading the kernel, Manually Upgrading the Kernel
- Kernel Dump Configuration (see kdump)
- kernel module
- bonding module, Using Channel Bonding
- description, Using Channel Bonding
- parameters to bonded interfaces, Bonding Module Directives
- definition, Working with Kernel Modules
- directories
- /etc/sysconfig/modules/, Persistent Module Loading
- /lib/modules/<kernel_version>/kernel/drivers/, Loading a Module
- files
- /proc/modules, Listing Currently-Loaded Modules
- listing
- currently loaded modules, Listing Currently-Loaded Modules
- module information, Displaying Information About a Module
- loading
- at the boot time, Persistent Module Loading
- for the current session, Loading a Module
- module parameters
- bonding module parameters, Bonding Module Directives
- supplying, Setting Module Parameters
- unloading, Unloading a Module
- utilities
- insmod, Loading a Module
- lsmod, Listing Currently-Loaded Modules
- modinfo, Displaying Information About a Module
- modprobe, Loading a Module, Unloading a Module
- rmmod, Unloading a Module
- kernel package
- kernel
- for single,multicore and multiprocessor systems, Overview of Kernel Packages
- kernel-devel
- kernel headers and makefiles, Overview of Kernel Packages
- kernel-doc
- documentation files, Overview of Kernel Packages
- kernel-firmware
- firmware files, Overview of Kernel Packages
- kernel-headers
- C header files files, Overview of Kernel Packages
- perf
- firmware files, Overview of Kernel Packages
- kernel upgrading
- preparing, Preparing to Upgrade
- keyboard configuration, Keyboard Configuration
- Keyboard Indicator applet, Adding the Keyboard Layout Indicator
- Keyboard Preferences utility, Changing the Keyboard Layout
- layout, Changing the Keyboard Layout
- typing break, Setting Up a Typing Break
- Keyboard Indicator (see keyboard configuration)
- Keyboard Preferences (see keyboard configuration)
- kwin, Window Managers
- (see also X)
L
- LDAP (see OpenLDAP)
- Log File Viewer, Managing Log Files in a Graphical Environment
- filtering, Viewing Log Files
- monitoring, Monitoring Log Files
- refresh rate, Viewing Log Files
- searching, Viewing Log Files
- log files, Viewing and Managing Log Files
- (see also Log File Viewer)
- description, Viewing and Managing Log Files
- locating, Locating Log Files
- monitoring, Monitoring Log Files
- rotating, Locating Log Files
- rsyslogd daemon, Viewing and Managing Log Files
- viewing, Viewing Log Files
- logrotate, Locating Log Files
- lsblk, Using the lsblk Command
- lscpu, Using the lscpu Command
- lsmod, Listing Currently-Loaded Modules
- (see also kernel module)
- lspci, Using the lspci Command, /proc/bus/pci
- lspcmcia, Using the lspcmcia Command
- lsusb, Using the lsusb Command
M
- Mail Delivery Agent (see email)
- Mail Transport Agent (see email) (see MTA)
- Mail Transport Agent Switcher, Mail Transport Agent (MTA) Configuration
- Mail User Agent, Mail Transport Agent (MTA) Configuration (see email)
- MDA (see Mail Delivery Agent)
- memory usage, Viewing Memory Usage
- metacity, Window Managers
- (see also X)
- modinfo, Displaying Information About a Module
- (see also kernel module)
- modprobe, Loading a Module, Unloading a Module
- (see also kernel module)
- module (see kernel module)
- module parameters (see kernel module)
- MTA (see Mail Transport Agent)
- setting default, Mail Transport Agent (MTA) Configuration
- switching with Mail Transport Agent Switcher, Mail Transport Agent (MTA) Configuration
- MUA, Mail Transport Agent (MTA) Configuration (see Mail User Agent)
- Multihomed DHCP
- host configuration, Host Configuration
- server configuration, Configuring a Multihomed DHCP Server
- mwm, Window Managers
- (see also X)
N
- named (see BIND)
- nameserver (see DNS)
- net program, Samba Distribution Programs
- network
- additional resources, Additional Resources
- bridge
- bridging, Network Bridge
- commands
- /sbin/ifdown, Interface Control Scripts
- /sbin/ifup, Interface Control Scripts
- /sbin/service network, Interface Control Scripts
- configuration, Interface Configuration Files
- configuration files, Network Configuration Files
- functions, Network Function Files
- interface configuration files, Interface Configuration Files
- interfaces
- 802.1Q, Setting Up 802.1Q VLAN Tagging
- alias, Alias and Clone Files
- channel bonding, Channel Bonding Interfaces
- clone, Alias and Clone Files
- dialup, Dialup Interfaces
- Ethernet, Ethernet Interfaces
- ethtool, Ethtool
- VLAN, Setting Up 802.1Q VLAN Tagging
- scripts, Network Interfaces
- Network Time Protocol (see NTP)
- NIC
- binding into single channel, Using Channel Bonding
- nmblookup program, Samba Distribution Programs
- NSCD
- and SSSD, Using NSCD with SSSD
- NTP
- ntpd (see NTP)
- ntpdate (see NTP)
- ntsysv (see services configuration)
O
- opannotate (see OProfile)
- opcontrol (see OProfile)
- OpenLDAP
- checking status, Checking the Service Status
- client applications, Overview of Common LDAP Client Applications
- configuration
- database, Changing the Database-Specific Configuration
- global, Changing the Global Configuration
- overview, OpenLDAP Server Setup
- directives
- olcAllows, Changing the Global Configuration
- olcConnMaxPending, Changing the Global Configuration
- olcConnMaxPendingAuth, Changing the Global Configuration
- olcDisallows, Changing the Global Configuration
- olcIdleTimeout, Changing the Global Configuration
- olcLogFile, Changing the Global Configuration
- olcReadOnly, Changing the Database-Specific Configuration
- olcReferral, Changing the Global Configuration
- olcRootDN, Changing the Database-Specific Configuration
- olcRootPW, Changing the Database-Specific Configuration
- olcSuffix, Changing the Database-Specific Configuration
- olcWriteTimeout, Changing the Global Configuration
- directories
- /etc/openldap/slapd.d/, Configuring an OpenLDAP Server
- /etc/openldap/slapd.d/cn=config/cn=schema/, Extending Schema
- features, OpenLDAP Features
- files
- /etc/openldap/ldap.conf, Configuring an OpenLDAP Server
- /etc/openldap/slapd.d/cn=config.ldif, Changing the Global Configuration
- /etc/openldap/slapd.d/cn=config/olcDatabase={2}bdb.ldif, Changing the Database-Specific Configuration
- installation, Installing the OpenLDAP Suite
- migrating authentication information, Migrating Old Authentication Information to LDAP Format
- packages, Installing the OpenLDAP Suite
- restarting, Restarting the Service
- running, Starting the Service
- schema, Extending Schema
- stopping, Stopping the Service
- terminology
- attribute, LDAP Terminology
- entry, LDAP Terminology
- LDIF, LDAP Terminology
- utilities, Overview of OpenLDAP Server Utilities, Overview of OpenLDAP Client Utilities
- OpenSSH, OpenSSH, Main Features
- (see also SSH)
- additional resources, Additional Resources
- client, OpenSSH Clients
- scp, Using the scp Utility
- sftp, Using the sftp Utility
- ssh, Using the ssh Utility
- DSA keys
- generating, Generating Key Pairs
- RSA keys
- generating, Generating Key Pairs
- RSA Version 1 keys
- generating, Generating Key Pairs
- server, Starting an OpenSSH Server
- starting, Starting an OpenSSH Server
- stopping, Starting an OpenSSH Server
- ssh-add, Configuring ssh-agent
- ssh-agent, Configuring ssh-agent
- ssh-keygen
- DSA, Generating Key Pairs
- RSA, Generating Key Pairs
- RSA Version 1, Generating Key Pairs
- using key-based authentication, Using Key-Based Authentication
- OpenSSL
- additional resources, Additional Resources
- SSL (see SSL )
- TLS (see TLS )
- ophelp, Setting Events to Monitor
- opreport (see OProfile)
- OProfile, OProfile
- /dev/oprofile/, Understanding /dev/oprofile/
- additional resources, Additional Resources
- configuring, Configuring OProfile
- separating profiles, Separating Kernel and User-space Profiles
- events
- sampling rate, Sampling Rate
- setting, Setting Events to Monitor
- Java, OProfile Support for Java
- monitoring the kernel, Specifying the Kernel
- opannotate, Using opannotate
- opcontrol, Configuring OProfile
- --no-vmlinux, Specifying the Kernel
- --start, Starting and Stopping OProfile
- --vmlinux=, Specifying the Kernel
- ophelp, Setting Events to Monitor
- opreport, Using opreport, Getting more detailed output on the modules
- on a single executable, Using opreport on a Single Executable
- oprofiled, Starting and Stopping OProfile
- log file, Starting and Stopping OProfile
- overview of tools, Overview of Tools
- reading data, Analyzing the Data
- saving data, Saving Data
- starting, Starting and Stopping OProfile
- SystemTap, OProfile and SystemTap
- unit mask, Unit Masks
- oprofiled (see OProfile)
- oprof_start, Graphical Interface
- OS/400 boot loader
- configuration file, Configuring the OS/400 Boot Loader
- configuring, Configuring the OS/400 Boot Loader
P
- package
- kernel RPM, Manually Upgrading the Kernel
- PackageKit, PackageKit
- adding and removing, Using Add/Remove Software
- architecture, PackageKit Architecture
- installing and removing package groups, Installing and Removing Package Groups
- installing packages, PackageKit
- managing packages, PackageKit
- PolicyKit
- authentication, Updating Packages with Software Update
- uninstalling packages, PackageKit
- updating packages, PackageKit
- viewing packages, PackageKit
- viewing transaction log, Viewing the Transaction Log
- packages
- adding and removing with PackageKit, Using Add/Remove Software
- dependencies, Unresolved Dependency
- determining file ownership with, Practical and Common Examples of RPM Usage
- displaying packages
- yum info, Displaying Package Information
- displaying packages with Yum
- yum info, Displaying Package Information
- extra packages for Enterprise Linux (EPEL), Finding RPM Packages
- filtering with PackageKit, Finding Packages with Filters
- Development, Finding Packages with Filters
- Free, Finding Packages with Filters
- Hide subpackages, Finding Packages with Filters
- Installed, Finding Packages with Filters
- No filter, Finding Packages with Filters
- Only available, Finding Packages with Filters
- Only development, Finding Packages with Filters
- Only end user files, Finding Packages with Filters
- Only graphical, Finding Packages with Filters
- Only installed, Finding Packages with Filters
- Only native packages, Finding Packages with Filters
- Only newest packages, Finding Packages with Filters
- filtering with PackageKit for packages, Finding Packages with Filters
- finding deleted files from, Practical and Common Examples of RPM Usage
- finding RPM packages, Finding RPM Packages
- initial RPM repositories, Finding RPM Packages
- installing a package group with Yum, Installing Packages
- installing and removing package groups, Installing and Removing Package Groups
- installing packages with PackageKit, PackageKit, Installing and Removing Packages (and Dependencies)
- dependencies, Installing and Removing Packages (and Dependencies)
- installing RPM, Installing and Upgrading
- installing with Yum, Installing Packages
- iRed Hat Enterprise Linux installation media, Finding RPM Packages
- kernel
- for single,multicore and multiprocessor systems, Overview of Kernel Packages
- kernel-devel
- kernel headers and makefiles, Overview of Kernel Packages
- kernel-doc
- documentation files, Overview of Kernel Packages
- kernel-firmware
- firmware files, Overview of Kernel Packages
- kernel-headers
- C header files files, Overview of Kernel Packages
- listing packages with Yum
- Glob expressions, Listing Packages
- yum grouplist, Listing Packages
- yum list all, Listing Packages
- yum list available, Listing Packages
- yum list installed, Listing Packages
- yum repolist, Listing Packages
- yum search, Listing Packages
- locating documentation for, Practical and Common Examples of RPM Usage
- managing packages with PackageKit, PackageKit
- obtaining list of files, Practical and Common Examples of RPM Usage
- packages and package groups, Packages and Package Groups
- perf
- firmware files, Overview of Kernel Packages
- querying uninstalled, Practical and Common Examples of RPM Usage
- removing, Uninstalling
- removing package groups with Yum, Removing Packages
- removing packages with PackageKit, Installing and Removing Packages (and Dependencies)
- RPM, RPM
- already installed, Package Already Installed
- configuration file changes, Configuration File Changes
- conflict, Conflicting Files
- failed dependencies, Unresolved Dependency
- freshening, Freshening
- pristine sources, RPM Design Goals
- querying, Querying
- removing, Uninstalling
- source and binary packages, RPM
- tips, Practical and Common Examples of RPM Usage
- uninstalling, Uninstalling
- verifying, Verifying
- searching packages with Yum
- yum search, Searching Packages
- setting packages with PackageKit
- checking interval, Updating Packages with Software Update
- uninstalling packages with PackageKit, PackageKit
- uninstalling packages with Yum, Removing Packages
- yum remove package_name, Removing Packages
- updating currently installed packages
- available updates, Updating Packages with Software Update
- updating packages with PackageKit, PackageKit
- PolicyKit, Updating Packages with Software Update
- Software Update, Updating Packages with Software Update
- upgrading RPM, Installing and Upgrading
- viewing packages with PackageKit, PackageKit
- viewing transaction log, Viewing the Transaction Log
- viewing Yum repositories with PackageKit, Refreshing Software Sources (Yum Repositories)
- Yum instead of RPM, RPM
- pdbedit program, Samba Distribution Programs
- PolicyKit, Updating Packages with Software Update
- Postfix, Postfix
- default installation, The Default Postfix Installation
- postfix, Mail Transport Agent (MTA) Configuration
- prefdm (see X)
- primary nameserver (see BIND)
- Printer Configuration
- CUPS, Printer Configuration
- IPP Printers, Adding an IPP Printer
- LDP/LPR Printers, Adding an LPD/LPR Host or Printer
- Local Printers, Adding a Local Printer
- New Printer, Starting Printer Setup
- Print Jobs, Managing Print Jobs
- Samba Printers, Adding a Samba (SMB) printer
- Settings, The Settings Page
- Sharing Printers, Sharing Printers
- printers (see Printer Configuration)
- proc file system
- /proc/buddyinfo, /proc/buddyinfo
- /proc/bus/ directory, /proc/bus/
- /proc/bus/pci
- viewing using lspci, /proc/bus/pci
- /proc/cmdline, /proc/cmdline
- /proc/cpuinfo, /proc/cpuinfo
- /proc/crypto, /proc/crypto
- /proc/devices
- block devices, /proc/devices
- character devices, /proc/devices
- /proc/dma, /proc/dma
- /proc/driver/ directory, /proc/driver/
- /proc/execdomains, /proc/execdomains
- /proc/fb, /proc/fb
- /proc/filesystems, /proc/filesystems
- /proc/fs/ directory, /proc/fs
- /proc/interrupts, /proc/interrupts
- /proc/iomem, /proc/iomem
- /proc/ioports, /proc/ioports
- /proc/irq/ directory, /proc/irq/
- /proc/kcore, /proc/kcore
- /proc/kmsg, /proc/kmsg
- /proc/loadavg, /proc/loadavg
- /proc/locks, /proc/locks
- /proc/mdstat, /proc/mdstat
- /proc/meminfo, /proc/meminfo
- /proc/misc, /proc/misc
- /proc/modules, /proc/modules
- /proc/mounts, /proc/mounts
- /proc/mtrr, /proc/mtrr
- /proc/net/ directory, /proc/net/
- /proc/partitions, /proc/partitions
- /proc/PID/ directory, /proc/PID/
- /proc/scsi/ directory, /proc/scsi/
- /proc/self/ directory, /proc/self/
- /proc/slabinfo, /proc/slabinfo
- /proc/stat, /proc/stat
- /proc/swaps, /proc/swaps
- /proc/sys/ directory, /proc/sys/, Using the sysctl Command
- (see also sysctl)
- /proc/sys/dev/ directory, /proc/sys/dev/
- /proc/sys/fs/ directory, /proc/sys/fs/
- /proc/sys/kernel/ directory, /proc/sys/kernel/
- /proc/sys/kernel/exec-shield, /proc/sys/kernel/
- /proc/sys/kernel/sysrq (see system request key)
- /proc/sys/net/ directory, /proc/sys/net/
- /proc/sys/vm/ directory, /proc/sys/vm/
- /proc/sysrq-trigger, /proc/sysrq-trigger
- /proc/sysvipc/ directory, /proc/sysvipc/
- /proc/tty/ directory, /proc/tty/
- /proc/uptime, /proc/uptime
- /proc/version, /proc/version
- additional resources, Additional Resources
- installed documentation, Additional Resources
- changing files within, Changing Virtual Files, /proc/sys/, Using the sysctl Command
- files within, top-level, Top-level Files within the proc File System
- introduced, The proc File System
- process directories, Process Directories
- subdirectories within, Directories within /proc/
- viewing files within, Viewing Virtual Files
- processes, Viewing System Processes
- Procmail, Mail Delivery Agents
- additional resources, Additional Resources
- configuration, Procmail Configuration
- recipes, Procmail Recipes
- delivering, Delivering vs. Non-Delivering Recipes
- examples, Recipe Examples
- flags, Flags
- local lockfiles, Specifying a Local Lockfile
- non-delivering, Delivering vs. Non-Delivering Recipes
- SpamAssassin, Spam Filters
- special actions, Special Conditions and Actions
- special conditions, Special Conditions and Actions
- ps, Using the ps Command
R
- RAM, Viewing Memory Usage
- rcp, Using the scp Utility
- ReaR
- basic usage, Basic ReaR Usage
- recursive nameserver (see BIND)
- Red Hat Support Tool
- getting support on the command line, Accessing Support Using the Red Hat Support Tool
- Red Hat Enterprise Linux installation media
- installable packages, Finding RPM Packages
- Red Hat Subscription Management
- subscription, Registering the System and Attaching Subscriptions
- removing package groups
- removing package groups with PackageKit, Installing and Removing Package Groups
- resource record (see BIND)
- rmmod, Unloading a Module
- (see also kernel module)
- rndc (see BIND)
- root nameserver (see BIND)
- rpcclient program, Samba Distribution Programs
- RPM, RPM
- additional resources, Additional Resources
- already installed, Package Already Installed
- basic modes, Using RPM
- checking package signatures, Checking a Package's Signature
- configuration file changes, Configuration File Changes
- conf.rpmsave, Configuration File Changes
- conflicts, Conflicting Files
- dependencies, Unresolved Dependency
- design goals, RPM Design Goals
- powerful querying, RPM Design Goals
- system verification, RPM Design Goals
- upgradability, RPM Design Goals
- determining file ownership with, Practical and Common Examples of RPM Usage
- documentation with, Practical and Common Examples of RPM Usage
- failed dependencies, Unresolved Dependency
- file conflicts
- resolving, Conflicting Files
- file name, Installing and Upgrading
- finding deleted files with, Practical and Common Examples of RPM Usage
- finding RPM packages, Finding RPM Packages
- freshening, Freshening
- GnuPG, Checking a Package's Signature
- installing, Installing and Upgrading
- md5sum, Checking a Package's Signature
- querying, Querying
- querying for file list, Practical and Common Examples of RPM Usage
- querying uninstalled packages, Practical and Common Examples of RPM Usage
- tips, Practical and Common Examples of RPM Usage
- uninstalling, Uninstalling
- upgrading, Installing and Upgrading
- verifying, Verifying
- website, Useful Websites
- RPM Package Manager (see RPM)
- RSA keys
- generating, Generating Key Pairs
- RSA Version 1 keys
- generating, Generating Key Pairs
- rsyslog, Viewing and Managing Log Files
- actions, Actions
- configuration, Basic Configuration of Rsyslog
- debugging, Debugging Rsyslog
- filters, Filters
- global directives, Global Directives
- log rotation, Log Rotation
- modules, Using Rsyslog Modules
- new configuration format, Using the New Configuration Format
- queues, Working with Queues in Rsyslog
- rulesets, Rulesets
- templates, Templates
- runlevel (see services configuration)
S
- sadump
- additional resources
- installed documents, Additional Resources
- Samba (see Samba)
- Abilities, Introduction to Samba
- Account Information Databases, Samba Account Information Databases
- ldapsam, Samba Account Information Databases
- ldapsam_compat, Samba Account Information Databases
- mysqlsam, Samba Account Information Databases
- Plain Text, Samba Account Information Databases
- smbpasswd, Samba Account Information Databases
- tdbsam, Samba Account Information Databases
- xmlsam, Samba Account Information Databases
- Additional Resources, Additional Resources
- installed documentation, Additional Resources
- related books, Additional Resources
- useful websites, Additional Resources
- Backward Compatible Database Back Ends, Samba Account Information Databases
- Browsing, Samba Network Browsing
- configuration, Configuring a Samba Server, Command-Line Configuration
- default, Configuring a Samba Server
- CUPS Printing Support, Samba with CUPS Printing Support
- CUPS smb.conf, Simple smb.conf Settings
- daemon
- encrypted passwords, Encrypted Passwords
- findsmb, Connecting to a Samba Share
- graphical configuration, Graphical Configuration
- Introduction, Introduction to Samba
- Network Browsing, Samba Network Browsing
- Domain Browsing, Domain Browsing
- WINS, WINS (Windows Internet Name Server)
- New Database Back Ends, Samba Account Information Databases
- Programs, Samba Distribution Programs
- findsmb, Samba Distribution Programs
- net, Samba Distribution Programs
- nmblookup, Samba Distribution Programs
- pdbedit, Samba Distribution Programs
- rpcclient, Samba Distribution Programs
- smbcacls, Samba Distribution Programs
- smbclient, Samba Distribution Programs
- smbcontrol, Samba Distribution Programs
- smbpasswd, Samba Distribution Programs
- smbspool, Samba Distribution Programs
- smbstatus, Samba Distribution Programs
- smbtar, Samba Distribution Programs
- testparm, Samba Distribution Programs
- wbinfo, Samba Distribution Programs
- Reference, Samba
- Samba Printers, Adding a Samba (SMB) printer
- Security Modes, Samba Security Modes, User-Level Security
- Active Directory Security Mode, User-Level Security
- Domain Security Mode, User-Level Security
- Share-Level Security, Share-Level Security
- User Level Security, User-Level Security
- Server Types, Samba Server Types and the smb.conf File
- server types
- Domain Controller, Domain Controller
- Domain Member, Domain Member Server
- Stand Alone, Stand-alone Server
- service
- conditional restarting, Starting and Stopping Samba
- reloading, Starting and Stopping Samba
- restarting, Starting and Stopping Samba
- starting, Starting and Stopping Samba
- stopping, Starting and Stopping Samba
- share
- connecting to via the command line, Connecting to a Samba Share
- connecting to with Nautilus, Connecting to a Samba Share
- mounting, Mounting the Share
- smb.conf, Samba Server Types and the smb.conf File
- Active Directory Member Server example, Domain Member Server
- Anonymous Print Server example, Stand-alone Server
- Anonymous Read Only example, Stand-alone Server
- Anonymous Read/Write example, Stand-alone Server
- NT4-style Domain Member example, Domain Member Server
- PDC using Active Directory, Domain Controller
- PDC using tdbsam, Domain Controller
- Secure File and Print Server example, Stand-alone Server
- smbclient, Connecting to a Samba Share
- WINS, WINS (Windows Internet Name Server)
- scp (see OpenSSH)
- secondary nameserver (see BIND)
- security plug-in (see Security)
- Security-Related Packages
- updating security-related packages, Updating Packages
- Sendmail, Sendmail
- additional resources, Additional Resources
- aliases, Masquerading
- common configuration changes, Common Sendmail Configuration Changes
- default installation, The Default Sendmail Installation
- LDAP and, Using Sendmail with LDAP
- limitations, Purpose and Limitations
- masquerading, Masquerading
- purpose, Purpose and Limitations
- spam, Stopping Spam
- with UUCP, Common Sendmail Configuration Changes
- sendmail, Mail Transport Agent (MTA) Configuration
- service (see services configuration)
- services configuration, Services and Daemons
- chkconfig, Using the chkconfig Utility
- ntsysv, Using the ntsysv Utility
- runlevel, Configuring the Default Runlevel
- service, Running Services
- system-config-services, Using the Service Configuration Utility
- sftp (see OpenSSH)
- slab pools (see /proc/slabinfo)
- slapd (see OpenLDAP)
- smbcacls program, Samba Distribution Programs
- smbclient, Connecting to a Samba Share
- smbclient program, Samba Distribution Programs
- smbcontrol program, Samba Distribution Programs
- smbpasswd program, Samba Distribution Programs
- smbspool program, Samba Distribution Programs
- smbstatus program, Samba Distribution Programs
- smbtar program, Samba Distribution Programs
- SpamAssassin
- using with Procmail, Spam Filters
- ssh (see OpenSSH)
- SSH protocol
- authentication, Authentication
- configuration files, Configuration Files
- system-wide configuration files, Configuration Files
- user-specific configuration files, Configuration Files
- connection sequence, Event Sequence of an SSH Connection
- features, Main Features
- insecure protocols, Requiring SSH for Remote Connections
- layers
- channels, Channels
- transport layer, Transport Layer
- port forwarding, Port Forwarding
- requiring for remote login, Requiring SSH for Remote Connections
- security risks, Why Use SSH?
- version 1, Protocol Versions
- version 2, Protocol Versions
- X11 forwarding, X11 Forwarding
- ssh-add, Configuring ssh-agent
- SSL , Setting Up an SSL Server
- (see also Apache HTTP Server )
- SSL server (see Apache HTTP Server )
- SSSD
- and NSCD, Using NSCD with SSSD
- configuration file
- creating, Setting up the sssd.conf File
- location, Using a Custom Configuration File
- sections, Creating the sssd.conf File
- downgrading, Downgrading SSSD
- identity provider
- local, Creating the sssd.conf File
- Kerberos authentication, Creating Domains: Kerberos Authentication
- LDAP domain, Creating Domains: LDAP
- supported LDAP directories, Creating Domains: LDAP
- Microsoft Active Directory domain, Creating Domains: Active Directory, Configuring Domains: Active Directory as an LDAP Provider (Alternative)
- proxy domain, Creating Domains: Proxy
- sudo rules
- rules stored per host, Configuring Services: sudo
- startx, Runlevel 3 (see X)
- (see also X)
- static route, Static Routes and the Default Gateway
- stunnel, Securing Email Client Communications
- subscriptions, Registering the System and Managing Subscriptions
- sysconfig directory
- /etc/sysconfig/apm-scripts/ directory, Directories in the /etc/sysconfig/ Directory
- /etc/sysconfig/arpwatch, /etc/sysconfig/arpwatch
- /etc/sysconfig/authconfig, /etc/sysconfig/authconfig
- /etc/sysconfig/autofs, /etc/sysconfig/autofs
- /etc/sysconfig/cbq/ directory, Directories in the /etc/sysconfig/ Directory
- /etc/sysconfig/clock, /etc/sysconfig/clock
- /etc/sysconfig/dhcpd, /etc/sysconfig/dhcpd
- /etc/sysconfig/firstboot, /etc/sysconfig/firstboot
- /etc/sysconfig/init, /etc/sysconfig/init
- /etc/sysconfig/ip6tables-config, /etc/sysconfig/ip6tables-config
- /etc/sysconfig/kernel, /etc/sysconfig/kernel
- /etc/sysconfig/keyboard, /etc/sysconfig/keyboard
- /etc/sysconfig/ldap, /etc/sysconfig/ldap
- /etc/sysconfig/named, /etc/sysconfig/named
- /etc/sysconfig/network, /etc/sysconfig/network
- /etc/sysconfig/network-scripts/ directory, Network Interfaces, Directories in the /etc/sysconfig/ Directory
- (see also network)
- /etc/sysconfig/networking/ directory, Directories in the /etc/sysconfig/ Directory
- /etc/sysconfig/ntpd, /etc/sysconfig/ntpd
- /etc/sysconfig/quagga, /etc/sysconfig/quagga
- /etc/sysconfig/radvd, /etc/sysconfig/radvd
- /etc/sysconfig/rhn/ directory, Directories in the /etc/sysconfig/ Directory
- /etc/sysconfig/samba, /etc/sysconfig/samba
- /etc/sysconfig/saslauthd, /etc/sysconfig/saslauthd
- /etc/sysconfig/selinux, /etc/sysconfig/selinux
- /etc/sysconfig/sendmail, /etc/sysconfig/sendmail
- /etc/sysconfig/spamassassin, /etc/sysconfig/spamassassin
- /etc/sysconfig/squid, /etc/sysconfig/squid
- /etc/sysconfig/system-config-users, /etc/sysconfig/system-config-users
- /etc/sysconfig/vncservers, /etc/sysconfig/vncservers
- /etc/sysconfig/xinetd, /etc/sysconfig/xinetd
- additional information about, The sysconfig Directory
- additional resources, Additional Resources
- installed documentation, Installed Documentation
- directories in, Directories in the /etc/sysconfig/ Directory
- files found in, Files in the /etc/sysconfig/ Directory
- sysctl
- configuring with /etc/sysctl.conf, Using the sysctl Command
- controlling /proc/sys/, Using the sysctl Command
- SysRq (see system request key)
- system analysis
- OProfile (see OProfile)
- system information
- cpu usage, Viewing CPU Usage
- file systems, Viewing Block Devices and File Systems
- gathering, System Monitoring Tools
- hardware, Viewing Hardware Information
- memory usage, Viewing Memory Usage
- processes, Viewing System Processes
- currently running, Using the top Command
- System Monitor, Using the System Monitor Tool, Using the System Monitor Tool, Using the System Monitor Tool, Using the System Monitor Tool
- system request key
- enabling, /proc/sys/
- System Request Key
- definition of, /proc/sys/
- setting timing for, /proc/sys/kernel/
- system-config-authentication (see Authentication Configuration Tool)
- system-config-date (see time configuration, date configuration)
- system-config-kdump (see kdump)
- system-config-services (see services configuration)
- systems
- registration, Registering the System and Managing Subscriptions
- subscription management, Registering the System and Managing Subscriptions
T
- testparm program, Samba Distribution Programs
- time configuration
- date, Date and Time Setup
- synchronize with NTP server, Network Time Protocol Properties, Network Time Protocol Setup
- system-config-date, Date and Time Properties
- time zone configuration, Time Zone Properties
- TLB cache (see hugepages)
- TLS , Setting Up an SSL Server
- (see also Apache HTTP Server )
- tool
- Authentication Configuration Tool, Configuring System Authentication
- top, Using the top Command
- twm, Window Managers
- (see also X)
U
- updating currently installed packages
- available updates, Updating Packages with Software Update
- updating packages with PackageKit
- PolicyKit, Updating Packages with Software Update
- users
- additional resources, Additional Resources
- installed documentation, Installed Documentation
V
- virtual file system (see proc file system)
- virtual files (see proc file system)
- virtual host (see Apache HTTP Server )
- vsftpd
- additional resources, Additional Resources
- installed documentation, Installed Documentation
- online documentation, Online Documentation
- condrestart, Starting and Stopping vsftpd
- configuration file
- /etc/vsftpd/vsftpd.conf, vsftpd Configuration Options
- access controls, Log In Options and Access Controls
- anonymous user options, Anonymous User Options
- daemon options, Daemon Options
- directory options, Directory Options
- file transfer options, File Transfer Options
- format of, vsftpd Configuration Options
- local-user options, Local-User Options
- logging options, Logging Options
- login options, Log In Options and Access Controls
- network options, Network Options
- security options, Security Options
- encrypting, Encrypting vsftpd Connections Using TLS
- multihome configuration, Starting Multiple Copies of vsftpd
- restarting, Starting and Stopping vsftpd
- RPM
- files installed by, Files Installed with vsftpd
- securing, Encrypting vsftpd Connections Using TLS, SELinux Policy for vsftpd
- SELinux, SELinux Policy for vsftpd
- starting, Starting and Stopping vsftpd
- starting multiple copies of, Starting Multiple Copies of vsftpd
- status, Starting and Stopping vsftpd
- stopping, Starting and Stopping vsftpd
- TLS, Encrypting vsftpd Connections Using TLS
W
- wbinfo program, Samba Distribution Programs
- web server (see Apache HTTP Server)
- window managers (see X)
X
- X
- /etc/X11/xorg.conf
- Boolean values for, The Structure of the Configuration
- Device, The Device section
- DRI, The DRI section
- Files section, The Files section
- InputDevice section, The InputDevice section
- introducing, The xorg.conf.d Directory, The xorg.conf File
- Monitor, The Monitor section
- Screen, The Screen section
- Section tag, The Structure of the Configuration
- ServerFlags section, The ServerFlags section
- ServerLayout section, The ServerLayout Section
- structure of, The Structure of the Configuration
- additional resources, Additional Resources
- installed documentation, Installed Documentation
- useful websites, Useful Websites
- configuration directory
- /etc/X11/xorg.conf.d, The xorg.conf.d Directory
- configuration files
- /etc/X11/ directory, X Server Configuration Files
- /etc/X11/xorg.conf, The xorg.conf File
- options within, X Server Configuration Files
- server options, The xorg.conf.d Directory, The xorg.conf File
- desktop environments
- GNOME, Desktop Environments
- KDE, Desktop Environments
- display managers
- configuration of preferred, Runlevel 5
- definition of, Runlevel 5
- GNOME, Runlevel 5
- KDE, Runlevel 5
- prefdm script, Runlevel 5
- xdm, Runlevel 5
- fonts
- Fontconfig, Fonts
- Fontconfig, adding fonts to, Adding Fonts to Fontconfig
- FreeType, Fonts
- introducing, Fonts
- Xft, Fonts
- introducing, The X Window System
- runlevels
- 3, Runlevel 3
- 5, Runlevel 5
- runlevels and, Runlevels and X
- window managers
- kwin, Window Managers
- metacity, Window Managers
- mwm, Window Managers
- twm, Window Managers
- X clients, The X Window System, Desktop Environments and Window Managers
- desktop environments, Desktop Environments
- startx command, Runlevel 3
- window managers, Window Managers
- xinit command, Runlevel 3
- X server, The X Window System
- features of, The X Server
- X Window System (see X)
- X.500 (see OpenLDAP)
- X.500 Lite (see OpenLDAP)
- xinit (see X)
- Xorg (see Xorg)
Y
- Yum
- configuring plug-ins, Enabling, Configuring, and Disabling Yum Plug-ins
- configuring Yum and Yum repositories, Configuring Yum and Yum Repositories
- disabling plug-ins, Enabling, Configuring, and Disabling Yum Plug-ins
- displaying packages
- yum info, Displaying Package Information
- displaying packages with Yum
- yum info, Displaying Package Information
- enabling plug-ins, Enabling, Configuring, and Disabling Yum Plug-ins
- installing a package group with Yum, Installing Packages
- installing with Yum, Installing Packages
- listing packages with Yum
- Glob expressions, Listing Packages
- yum grouplist, Listing Packages
- yum list, Listing Packages
- yum list all, Listing Packages
- yum list available, Listing Packages
- yum list installed, Listing Packages
- yum repolist, Listing Packages
- packages and package groups, Packages and Package Groups
- plug-ins
- kabi, Plug-in Descriptions
- presto, Plug-in Descriptions
- product-id, Plug-in Descriptions
- refresh-packagekit, Plug-in Descriptions
- rhnplugin, Plug-in Descriptions
- search-disabled-repos, Plug-in Descriptions
- security, Plug-in Descriptions
- subscription-manager, Plug-in Descriptions
- yum-downloadonly, Plug-in Descriptions
- repository, Adding, Enabling, and Disabling a Yum Repository, Creating a Yum Repository
- searching packages with Yum
- yum search, Searching Packages
- setting [main] options, Setting [main] Options
- setting [repository] options, Setting [repository] Options
- uninstalling package groups with Yum, Removing Packages
- uninstalling packages with Yum, Removing Packages
- yum remove package_name, Removing Packages
- variables, Using Yum Variables
- yum cache, Working with Yum Cache
- yum clean, Working with Yum Cache
- Yum plug-ins, Yum Plug-ins
- Yum repositories
- configuring Yum and Yum repositories, Configuring Yum and Yum Repositories
- yum update, Upgrading the System Off-line with ISO and Yum
- Yum repositories
- viewing Yum repositories with PackageKit, Refreshing Software Sources (Yum Repositories)
- Yum Updates
- checking for updates, Checking For Updates
- updating a single package, Updating Packages
- updating all packages and dependencies, Updating Packages
- updating packages, Updating Packages
- updating packages automatically, Updating Packages
- updating security-related packages, Updating Packages