Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 3. Selecting the Identity Store for Authentication with authconfig
The Identity & Authentication tab in the
authconfig UI sets how users should be authenticated. The default is to use local system authentication, meaning the users and their passwords are checked against local system accounts. A Red Hat Enterprise Linux machine can also use external resources which contain the users and credentials, including LDAP, NIS, and Winbind.
3.1. IPAv2
Link kopierenLink in die Zwischenablage kopiert!
There are two different ways to configure an Identity Management server as an identity back end. For IdM version 2 (Red Hat Enterprise Linux version 6.3 and earlier), version 3 (in Red Hat Enterprise Linux 6.4 and later), and version 4 (in Red Hat Enterprise Linux 7.1 and later), these are configured as IPAv2 providers in
authconfig. For previous IdM versions and for community FreeIPA servers, these are configured as LDAP providers.
3.1.1. Configuring IdM from the UI
Link kopierenLink in die Zwischenablage kopiert!
- Open the
authconfigUI. - Select in the User Account Database drop-down menu.
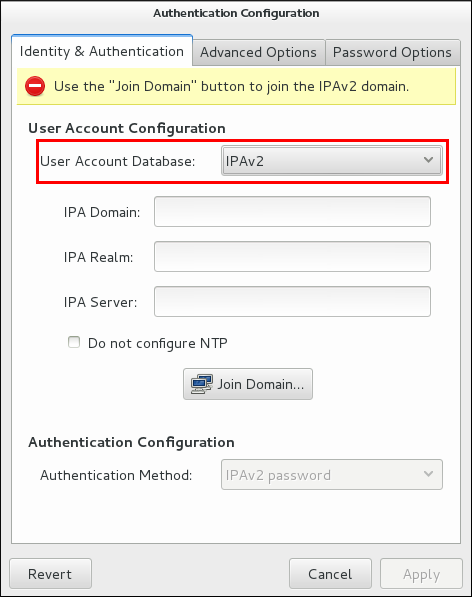
Figure 3.1. Authentication Configuration
- Set the information that is required to connect to the IdM server.
- IPA Domain gives the DNS domain of the IdM domain.
- IPA Realm gives the Kerberos domain of the IdM domain.
- IPA Server gives the host name of any IdM server within the IdM domain topology.
- Do not configure NTP optionally disables NTP services when the client is configured. This is usually not recommended, because the IdM server and all clients need to have synchronized clocks for Kerberos authentication and certificates to work properly. This could be disabled if the IdM servers are using a different NTP server rather than hosting it within the domain.
- Click the button.This runs the
ipa-client-installcommand and, if necessary, installs theipa-clientpackages. The installation script automatically configures all system files that are required for the local system and contacts the domain servers to update the domain information.
3.1.2. Configuring IdM from the Command Line
Link kopierenLink in die Zwischenablage kopiert!
An IdM domain centralizes several common and critical services in a single hierarchy, most notably DNS and Kerberos.
authconfig (much like realmd in Chapter 8, Using realmd to Connect to an Identity Domain) can be used to enroll a system in the IdM domain. That runs the ipa-client-install command and, if necessary, installs the ipa-client packages. The installation script automatically configures all system files that are required for the local system and contacts the domain servers to update the domain information.
Joining a domain requires three pieces of information to identify the domain: the DNS domain name (
--ipav2domain), the Kerberos realm name (--ipav2realm), and the IdM server to contact (--ipav2server). The --ipav2join option gives the administrator user name to use to connect to the IdM server; this is typically admin.
authconfig --enableipav2 --ipav2domain=IPAEXAMPLE --ipav2realm=IPAEXAMPLE --ipav2server=ipaexample.com --ipav2join=admin
[root@server ~]# authconfig --enableipav2 --ipav2domain=IPAEXAMPLE --ipav2realm=IPAEXAMPLE --ipav2server=ipaexample.com --ipav2join=admin
If the IdM domain is not running its own NTP services, then it is possible to use the
--disableipav2nontp option to prevent the setup script to use the IdM server as the NTP server. This is generally not recommended, because the IdM server and all clients need to have synchronized clocks for Kerberos authentication and certificates to work properly.