Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 1. Identifying security updates
Keeping enterprise systems secure from current and future threats requires regular security updates. Red Hat Product Security provides the guidance you need to confidently deploy and maintain enterprise solutions.
1.1. What are security advisories?
Red Hat Security Advisories (RHSA) document the information about security flaws being fixed in Red Hat products and services.
Each RHSA includes the following information:
- Severity
- Type and status
- Affected products
- Summary of fixed issues
- Links to the tickets about the problem. Note that not all tickets are public.
- Common Vulnerabilities and Exposures (CVE) numbers and links with additional details, such as attack complexity.
Red Hat Customer Portal provides a list of Red Hat Security Advisories published by Red Hat. You can display details of a specific advisory by navigating to the advisory’s ID from the list of Red Hat Security Advisories.
Figure 1.1. List of security advisories
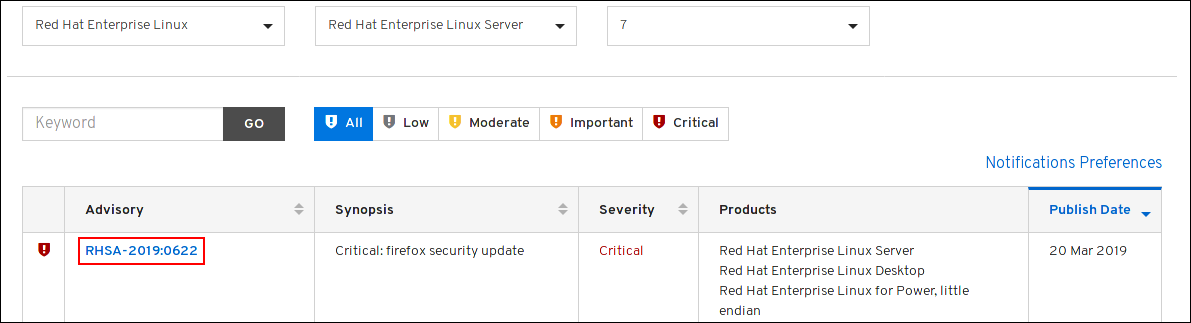
Optionally, you can also filter the results by specific product, variant, version, and architecture. For example, to display only advisories for Red Hat Enterprise Linux 8, you can set the following filters:
- Product: Red Hat Enterprise Linux
- Variant: All Variants
- Version: 8
- Optionally, select a minor version, such as 8.2.
Additional resources
1.2. Displaying security updates that are not installed on a host
You can list all available security updates for your system by using the yum utility.
Prerequisite
- A Red Hat subscription is attached to the host.
Procedure
List all available security updates which have not been installed on the host:
# yum updateinfo list updates security … RHSA-2019:0997 Important/Sec. platform-python-3.6.8-2.el8_0.x86_64 RHSA-2019:0997 Important/Sec. python3-libs-3.6.8-2.el8_0.x86_64 RHSA-2019:0990 Moderate/Sec. systemd-239-13.el8_0.3.x86_64 …
1.3. Displaying security updates that are installed on a host
You can list installed security updates for your system by using the yum utility.
Procedure
List all security updates which are installed on the host:
# yum updateinfo list security --installed … RHSA-2019:1234 Important/Sec. libssh2-1.8.0-7.module+el8+2833+c7d6d092 RHSA-2019:4567 Important/Sec. python3-libs-3.6.7.1.el8.x86_64 RHSA-2019:8901 Important/Sec. python3-libs-3.6.8-1.el8.x86_64 …If multiple updates of a single package are installed,
yumlists all advisories for the package. In the previous example, two security updates for thepython3-libspackage have been installed since the system installation.
1.4. Displaying a specific advisory by using YUM
You can use the yum utility to display a specific advisory information that is available for an update.
Prerequisites
- A Red Hat subscription is attached to the host.
- You know the ID of the security advisory.
- The update provided by the advisory is not installed.
Procedure
Display a specific advisory, for example:
# yum updateinfo info RHSA-2019:0997 ==================================================================== Important: python3 security update ==================================================================== Update ID: RHSA-2019:0997 Type: security Updated: 2019-05-07 05:41:52 Bugs: 1688543 - CVE-2019-9636 python: Information Disclosure due to urlsplit improper NFKC normalization CVEs: CVE-2019-9636 Description: …