Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 6. Scanning the system for configuration compliance and vulnerabilities
A compliance audit is a process of determining whether a given object follows all the rules specified in a compliance policy. The compliance policy is defined by security professionals who specify the required settings, often in the form of a checklist, that a computing environment should use.
Compliance policies can vary substantially across organizations and even across different systems within the same organization. Differences among these policies are based on the purpose of each system and its importance for the organization. Custom software settings and deployment characteristics also raise a need for custom policy checklists.
6.1. Configuration compliance tools in RHEL
You can perform a fully automated compliance audit in Red Hat Enterprise Linux by using the following configuration compliance tools. These tools are based on the Security Content Automation Protocol (SCAP) standard and are designed for automated tailoring of compliance policies.
- SCAP Workbench
-
The
scap-workbenchgraphical utility is designed to perform configuration and vulnerability scans on a single local or remote system. You can also use it to generate security reports based on these scans and evaluations. - OpenSCAP
The
OpenSCAPlibrary, with the accompanyingoscapcommand-line utility, is designed to perform configuration and vulnerability scans on a local system, to validate configuration compliance content, and to generate reports and guides based on these scans and evaluations.ImportantYou can experience memory-consumption problems while using OpenSCAP, which can cause stopping the program prematurely and prevent generating any result files. See the OpenSCAP memory-consumption problems Knowledgebase article for details.
- SCAP Security Guide (SSG)
-
The
scap-security-guidepackage provides collections of security policies for Linux systems. The guidance consists of a catalog of practical hardening advice, linked to government requirements where applicable. The project bridges the gap between generalized policy requirements and specific implementation guidelines. - Script Check Engine (SCE)
-
With SCE, which is an extension to the SCAP protocol, administrators can write their security content by using a scripting language, such as Bash, Python, and Ruby. The SCE extension is provided in the
openscap-engine-scepackage. The SCE itself is not part of the SCAP standard.
To perform automated compliance audits on multiple systems remotely, you can use the OpenSCAP solution for Red Hat Satellite.
6.2. Vulnerability scanning
6.2.1. Red Hat Security Advisories OVAL feed
Red Hat Enterprise Linux security auditing capabilities are based on the Security Content Automation Protocol (SCAP) standard. SCAP is a multi-purpose framework of specifications that supports automated configuration, vulnerability and patch checking, technical control compliance activities, and security measurement.
SCAP specifications create an ecosystem where the format of security content is well-known and standardized although the implementation of the scanner or policy editor is not mandated. This enables organizations to build their security policy (SCAP content) once, no matter how many security vendors they employ.
The Open Vulnerability Assessment Language (OVAL) is the essential and oldest component of SCAP. Unlike other tools and custom scripts, OVAL describes a required state of resources in a declarative manner. OVAL code is never executed directly but using an OVAL interpreter tool called scanner. The declarative nature of OVAL ensures that the state of the assessed system is not accidentally modified.
Like all other SCAP components, OVAL is based on XML. The SCAP standard defines several document formats. Each of them includes a different kind of information and serves a different purpose.
Red Hat Product Security helps customers evaluate and manage risk by tracking and investigating all security issues affecting Red Hat customers. It provides timely and concise patches and security advisories on the Red Hat Customer Portal. Red Hat creates and supports OVAL patch definitions, providing machine-readable versions of our security advisories.
Because of differences between platforms, versions, and other factors, Red Hat Product Security qualitative severity ratings of vulnerabilities do not directly align with the Common Vulnerability Scoring System (CVSS) baseline ratings provided by third parties. Therefore, we recommend that you use the RHSA OVAL definitions instead of those provided by third parties.
The RHSA OVAL definitions are available individually and as a complete package, and are updated within an hour of a new security advisory being made available on the Red Hat Customer Portal.
Each OVAL patch definition maps one-to-one to a Red Hat Security Advisory (RHSA). Because an RHSA can contain fixes for multiple vulnerabilities, each vulnerability is listed separately by its Common Vulnerabilities and Exposures (CVE) name and has a link to its entry in our public bug database.
The RHSA OVAL definitions are designed to check for vulnerable versions of RPM packages installed on a system. It is possible to extend these definitions to include further checks, for example, to find out if the packages are being used in a vulnerable configuration. These definitions are designed to cover software and updates shipped by Red Hat. Additional definitions are required to detect the patch status of third-party software.
The Red Hat Lightspeed for Red Hat Enterprise Linux compliance service helps IT security and compliance administrators to assess, monitor, and report on the security policy compliance of Red Hat Enterprise Linux systems. You can also create and manage your SCAP security policies entirely within the compliance service UI.
6.2.2. Scanning the system for vulnerabilities
The oscap command-line utility enables you to scan local systems, validate configuration compliance content, and generate reports and guides based on these scans and evaluations. This utility serves as a front end to the OpenSCAP library and groups its functionalities to modules (sub-commands) based on the type of SCAP content it processes.
Prerequisites
-
The
openscap-scannerandbzip2packages are installed.
Procedure
Download the latest RHSA OVAL definitions for your system:
wget -O - https://www.redhat.com/security/data/oval/v2/RHEL8/rhel-8.oval.xml.bz2 | bzip2 --decompress > rhel-8.oval.xml
# wget -O - https://www.redhat.com/security/data/oval/v2/RHEL8/rhel-8.oval.xml.bz2 | bzip2 --decompress > rhel-8.oval.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Scan the system for vulnerabilities and save results to the vulnerability.html file:
oscap oval eval --report vulnerability.html rhel-8.oval.xml
# oscap oval eval --report vulnerability.html rhel-8.oval.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Check the results in a browser of your choice, for example:
firefox vulnerability.html &
$ firefox vulnerability.html &Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.2.3. Scanning remote systems for vulnerabilities
You can check remote systems for vulnerabilities with the OpenSCAP scanner by using the oscap-ssh tool over the SSH protocol.
Prerequisites
-
The
openscap-utilsandbzip2packages are installed on the system you use for scanning. -
The
openscap-scannerpackage is installed on the remote systems. - The SSH server is running on the remote systems.
Procedure
Download the latest RHSA OVAL definitions for your system:
wget -O - https://www.redhat.com/security/data/oval/v2/RHEL8/rhel-8.oval.xml.bz2 | bzip2 --decompress > rhel-8.oval.xml
# wget -O - https://www.redhat.com/security/data/oval/v2/RHEL8/rhel-8.oval.xml.bz2 | bzip2 --decompress > rhel-8.oval.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Scan a remote system for vulnerabilities and save the results to a file:
oscap-ssh <username>@<hostname> <port> oval eval --report <scan-report.html> rhel-8.oval.xml
# oscap-ssh <username>@<hostname> <port> oval eval --report <scan-report.html> rhel-8.oval.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace:
-
<username>@<hostname>with the user name and host name of the remote system. -
<port>with the port number through which you can access the remote system, for example,22. -
<scan-report.html>with the file name whereoscapsaves the scan results.
-
6.3. Configuration compliance scanning
6.3.1. Configuration compliance in RHEL
You can use configuration compliance scanning to conform to a baseline defined by a specific organization. For example, if you work with the US government, you might have to align your systems with the Operating System Protection Profile (OSPP), and if you are a payment processor, you might have to align your systems with the Payment Card Industry Data Security Standard (PCI-DSS). You can also perform configuration compliance scanning to harden your system security.
Red Hat recommends you follow the Security Content Automation Protocol (SCAP) content provided in the SCAP Security Guide package because it is in line with Red Hat best practices for affected components.
The SCAP Security Guide package provides content which conforms to the SCAP 1.2 and SCAP 1.3 standards. The openscap scanner utility is compatible with both SCAP 1.2 and SCAP 1.3 content provided in the SCAP Security Guide package.
Performing a configuration compliance scanning does not guarantee the system is compliant.
The SCAP Security Guide suite provides profiles for several platforms in a form of data stream documents. A data stream is a file that contains definitions, benchmarks, profiles, and individual rules. Each rule specifies the applicability and requirements for compliance. RHEL provides several profiles for compliance with security policies. In addition to the industry standard, Red Hat data streams also contain information for remediation of failed rules.
Structure of compliance scanning resources
A profile is a set of rules based on a security policy, such as OSPP, PCI-DSS, and Health Insurance Portability and Accountability Act (HIPAA). This enables you to audit the system in an automated way for compliance with security standards.
You can modify (tailor) a profile to customize certain rules, for example, password length. For more information about profile tailoring, see Customizing a security profile with SCAP Workbench.
6.3.2. Possible results of an OpenSCAP scan
Depending on the data stream and profile applied to an OpenSCAP scan, as well as various properties of your system, each rule may produce a specific result. These are the possible results with brief explanations of their meanings:
- Pass
- The scan did not find any conflicts with this rule.
- Fail
- The scan found a conflict with this rule.
- Not checked
- OpenSCAP does not perform an automatic evaluation of this rule. Check whether your system conforms to this rule manually.
- Not applicable
- This rule does not apply to the current configuration.
- Not selected
- This rule is not part of the profile. OpenSCAP does not evaluate this rule and does not display these rules in the results.
- Error
-
The scan encountered an error. For additional information, you can enter the
oscapcommand with the--verbose DEVELoption. File a support case on the Red Hat customer portal or open a ticket in the RHEL project in Red Hat Jira. - Unknown
-
The scan encountered an unexpected situation. For additional information, you can enter the
oscapcommand with the`--verbose DEVELoption. File a support case on the Red Hat customer portal or open a ticket in the RHEL project in Red Hat Jira.
6.3.3. Viewing profiles for configuration compliance
Before you decide to use profiles for scanning or remediation, you can list them and check their detailed descriptions using the oscap info subcommand.
Prerequisites
-
The
openscap-scannerandscap-security-guidepackages are installed.
Procedure
List all available files with security compliance profiles provided by the SCAP Security Guide project:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display detailed information about a selected data stream using the
oscap infosubcommand. XML files containing data streams are indicated by the-dsstring in their names. In theProfilessection, you can find a list of available profiles and their IDs:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Select a profile from the data stream file and display additional details about the selected profile. To do so, use
oscap infowith the--profileoption followed by the last section of the ID displayed in the output of the previous command. For example, the ID of the HIPPA profile isxccdf_org.ssgproject.content_profile_hipaa, and the value for the--profileoption ishipaa:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.4. Assessing configuration compliance with a specific baseline
You can determine whether your system or a remote system conforms to a specific baseline, and save the results in a report by using the oscap command-line tool.
Prerequisites
-
The
openscap-scannerandscap-security-guidepackages are installed. - You know the ID of the profile within the baseline with which the system should comply. To find the ID, see the Viewing profiles for configuration compliance section.
Procedure
Scan the local system for compliance with the selected profile and save the scan results to a file:
oscap xccdf eval --report <scan-report.html> --profile <profileID> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
$ oscap xccdf eval --report <scan-report.html> --profile <profileID> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace:
-
<scan-report.html>with the file name whereoscapsaves the scan results. -
<profileID>with the profile ID with which the system should comply, for example,hipaa.
-
Optional: Scan a remote system for compliance with the selected profile and save the scan results to a file:
oscap-ssh <username>@<hostname> <port> xccdf eval --report <scan-report.html> --profile <profileID> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
$ oscap-ssh <username>@<hostname> <port> xccdf eval --report <scan-report.html> --profile <profileID> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace:
-
<username>@<hostname>with the user name and host name of the remote system. -
<port>with the port number through which you can access the remote system. -
<scan-report.html>with the file name whereoscapsaves the scan results. -
<profileID>with the profile ID with which the system should comply, for example,hipaa.
-
6.4. Remediating the system to align with a specific baseline
You can remediate the RHEL system to align with a specific baseline. You can remediate the system to align with any profile provided by the SCAP Security Guide. For the details on listing the available profiles, see the Viewing profiles for configuration compliance section.
If not used carefully, running the system evaluation with the Remediate option enabled might render the system non-functional. Red Hat does not provide any automated method to revert changes made by security-hardening remediations. Remediations are supported on RHEL systems in the default configuration. If your system has been altered after the installation, running remediation might not make it compliant with the required security profile.
Prerequisites
-
The
scap-security-guidepackage is installed.
Procedure
Remediate the system by using the
oscapcommand with the--remediateoption:oscap xccdf eval --profile <profileID> --remediate /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
# oscap xccdf eval --profile <profileID> --remediate /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<profileID>with the profile ID with which the system should comply, for example,hipaa.- Restart your system.
Verification
Evaluate compliance of the system with the profile, and save the scan results to a file:
oscap xccdf eval --report <scan-report.html> --profile <profileID> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
$ oscap xccdf eval --report <scan-report.html> --profile <profileID> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace:
-
<scan-report.html>with the file name whereoscapsaves the scan results. -
<profileID>with the profile ID with which the system should comply, for example,hipaa.
-
6.5. Remediating the system to align with a specific baseline by using an SSG Ansible Playbook
You can remediate your system to align with a specific baseline by using an Ansible Playbook file from the SCAP Security Guide project. You can remediate to align with any profile provided by the SCAP Security Guide.
If not used carefully, running the system evaluation with the Remediate option enabled might render the system non-functional. Red Hat does not provide any automated method to revert changes made by security-hardening remediations. Remediations are supported on RHEL systems in the default configuration. If your system has been altered after the installation, running remediation might not make it compliant with the required security profile.
Prerequisites
-
The
scap-security-guidepackage is installed. -
The
ansible-corepackage is installed. See the Ansible Installation Guide for more information. -
The
rhc-worker-playbookpackage is installed. - You know the ID of the profile according to which you want to remediate your system. For details, see Viewing profiles for configuration compliance.
RHEL 8.6 or later is installed. For more information about installing RHEL, see Interactively installing RHEL from installation media.
NoteIn RHEL 8.5 and earlier versions, Ansible packages were provided through Ansible Engine instead of Ansible Core, and with a different level of support. Do not use Ansible Engine because the packages might not be compatible with Ansible automation content in RHEL 8.6 and later. For more information, see Scope of support for the Ansible Core package included in the RHEL 9 and RHEL 8.6 and later AppStream repositories.
Procedure
Remediate your system to align with a selected profile by using Ansible:
ANSIBLE_COLLECTIONS_PATH=/usr/share/rhc-worker-playbook/ansible/collections/ansible_collections/ ansible-playbook -i "localhost," -c local /usr/share/scap-security-guide/ansible/rhel8-playbook-<profileID>.yml
# ANSIBLE_COLLECTIONS_PATH=/usr/share/rhc-worker-playbook/ansible/collections/ansible_collections/ ansible-playbook -i "localhost," -c local /usr/share/scap-security-guide/ansible/rhel8-playbook-<profileID>.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
ANSIBLE_COLLECTIONS_PATHenvironment variable is necessary for the command to run the playbook.Replace
<profileID>with the profile ID of the selected profile.- Restart the system.
Verification
Evaluate the compliance of the system with the selected profile, and save the scan results to a file:
oscap xccdf eval --profile <profileID> --report <scan-report.html> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
# oscap xccdf eval --profile <profileID> --report <scan-report.html> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<scan-report.html>with the file name whereoscapsaves the scan results.
6.6. Creating a remediation Ansible Playbook to align the system with a specific baseline
You can create an Ansible Playbook that contains only the remediations that are required to align your system with a specific baseline. This playbook is smaller because it does not cover already satisfied requirements. Creating the playbook does not modify your system in any way, you only prepare a file for later application.
In RHEL 8.6, Ansible Engine is replaced by the ansible-core package, which contains only built-in modules. Note that many Ansible remediations use modules from the community and Portable Operating System Interface (POSIX) collections, which are not included in the built-in modules. In this case, you can use Bash remediations as a substitute for Ansible remediations. The Red Hat Connector in RHEL 8.6 includes the Ansible modules necessary for the remediation playbooks to function with Ansible Core.
Prerequisites
-
The
scap-security-guidepackage is installed. -
The
ansible-corepackage is installed. See the Ansible Installation Guide for more information. -
The
rhc-worker-playbookpackage is installed. - You know the ID of the profile according to which you want to remediate your system. For details, see Viewing profiles for configuration compliance.
Procedure
Scan the system and save the results:
oscap xccdf eval --profile <profileID> --results <profile-results.xml> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
# oscap xccdf eval --profile <profileID> --results <profile-results.xml> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Find the value of the result ID in the file with the results:
oscap info <profile-results.xml>
# oscap info <profile-results.xml>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Generate an Ansible Playbook based on the file generated in step 1:
oscap xccdf generate fix --fix-type ansible --result-id xccdf_org.open-scap_testresult_xccdf_org.ssgproject.content_profile_<profileID> --output <profile-remediations.yml> <profile-results.xml>
# oscap xccdf generate fix --fix-type ansible --result-id xccdf_org.open-scap_testresult_xccdf_org.ssgproject.content_profile_<profileID> --output <profile-remediations.yml> <profile-results.xml>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Review that the generated
<profile-remediations.yml>file contains Ansible remediations for rules that failed in the scan performed in step 1. Remediate your system to align with a selected profile by using Ansible:
ANSIBLE_COLLECTIONS_PATH=/usr/share/rhc-worker-playbook/ansible/collections/ansible_collections/ ansible-playbook -i "localhost," -c local <profile-remediations.yml>`
# ANSIBLE_COLLECTIONS_PATH=/usr/share/rhc-worker-playbook/ansible/collections/ansible_collections/ ansible-playbook -i "localhost," -c local <profile-remediations.yml>`Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
ANSIBLE_COLLECTIONS_PATHenvironment variable is necessary for the command to run the playbook.WarningIf not used carefully, running the system evaluation with the
Remediateoption enabled might render the system non-functional. Red Hat does not provide any automated method to revert changes made by security-hardening remediations. Remediations are supported on RHEL systems in the default configuration. If your system has been altered after the installation, running remediation might not make it compliant with the required security profile.
Verification
Evaluate the compliance of the system with the selected profile, and save the scan results to a file:
oscap xccdf eval --profile <profileID> --report <scan-report.html> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
# oscap xccdf eval --profile <profileID> --report <scan-report.html> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<scan-report.html>with the file name whereoscapsaves the scan results.
6.7. Creating a remediation Bash script for a later application
Use this procedure to create a Bash script containing remediations that align your system with a security profile such as HIPAA. Using the following steps, you do not do any modifications to your system, you only prepare a file for later application.
Prerequisites
-
The
scap-security-guidepackage is installed on your RHEL system.
Procedure
Use the
oscapcommand to scan the system and to save the results to an XML file. In the following example,oscapevaluates the system against thehipaaprofile:oscap xccdf eval --profile hipaa --results <hipaa-results.xml> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
# oscap xccdf eval --profile hipaa --results <hipaa-results.xml> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Find the value of the result ID in the file with the results:
oscap info <hipaa-results.xml>
# oscap info <hipaa-results.xml>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Generate a Bash script based on the results file generated in step 1:
oscap xccdf generate fix --fix-type bash --result-id <xccdf_org.open-scap_testresult_xccdf_org.ssgproject.content_profile_hipaa> --output <hipaa-remediations.sh> <hipaa-results.xml>
# oscap xccdf generate fix --fix-type bash --result-id <xccdf_org.open-scap_testresult_xccdf_org.ssgproject.content_profile_hipaa> --output <hipaa-remediations.sh> <hipaa-results.xml>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
The
<hipaa-remediations.sh>file contains remediations for rules that failed during the scan performed in step 1. After reviewing this generated file, you can apply it with the./<hipaa-remediations.sh>command when you are in the same directory as this file.
Verification
-
In a text editor of your choice, review that the
<hipaa-remediations.sh>file contains rules that failed in the scan performed in step 1.
6.8. Scanning the system with a customized profile using SCAP Workbench
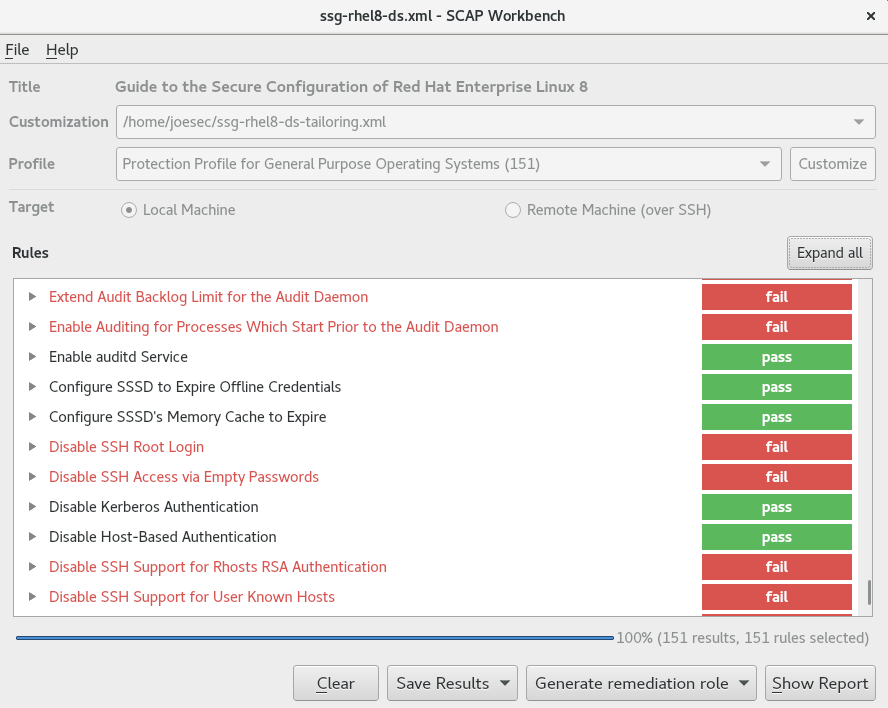
SCAP Workbench, which is contained in the scap-workbench package, is a graphical utility that enables users to perform configuration and vulnerability scans on a single local or a remote system, perform remediation of the system, and generate reports based on scan evaluations. Note that SCAP Workbench has limited functionality compared with the oscap command-line utility. SCAP Workbench processes security content in the form of data stream files.
6.8.1. Using SCAP Workbench to scan and remediate the system
To evaluate your system against the selected security policy, use the following procedure.
Prerequisites
-
The
scap-workbenchpackage is installed on your system.
Procedure
To run
SCAP Workbenchfrom theGNOME Classicdesktop environment, press the Super key to enter theActivities Overview, typescap-workbench, and then press Enter. Alternatively, use:scap-workbench &
$ scap-workbench &Copy to Clipboard Copied! Toggle word wrap Toggle overflow Select a security policy using either of the following options:
-
Load Contentbutton on the starting window -
Open content from SCAP Security Guide Open Other Contentin theFilemenu, and search the respective XCCDF, SCAP RPM, or data stream file.
-
You can allow automatic correction of the system configuration by selecting the check box. With this option enabled,
SCAP Workbenchattempts to change the system configuration in accordance with the security rules applied by the policy. This process should fix the related checks that fail during the system scan.WarningIf not used carefully, running the system evaluation with the
Remediateoption enabled might render the system non-functional. Red Hat does not provide any automated method to revert changes made by security-hardening remediations. Remediations are supported on RHEL systems in the default configuration. If your system has been altered after the installation, running remediation might not make it compliant with the required security profile.Scan your system with the selected profile by clicking the button.
-
To store the scan results in form of an XCCDF, ARF, or HTML file, click the combo box. Choose the
HTML Reportoption to generate the scan report in human-readable format. The XCCDF and ARF (data stream) formats are suitable for further automatic processing. You can repeatedly choose all three options. - To export results-based remediations to a file, use the pop-up menu.
6.8.2. Customizing a security profile with SCAP Workbench
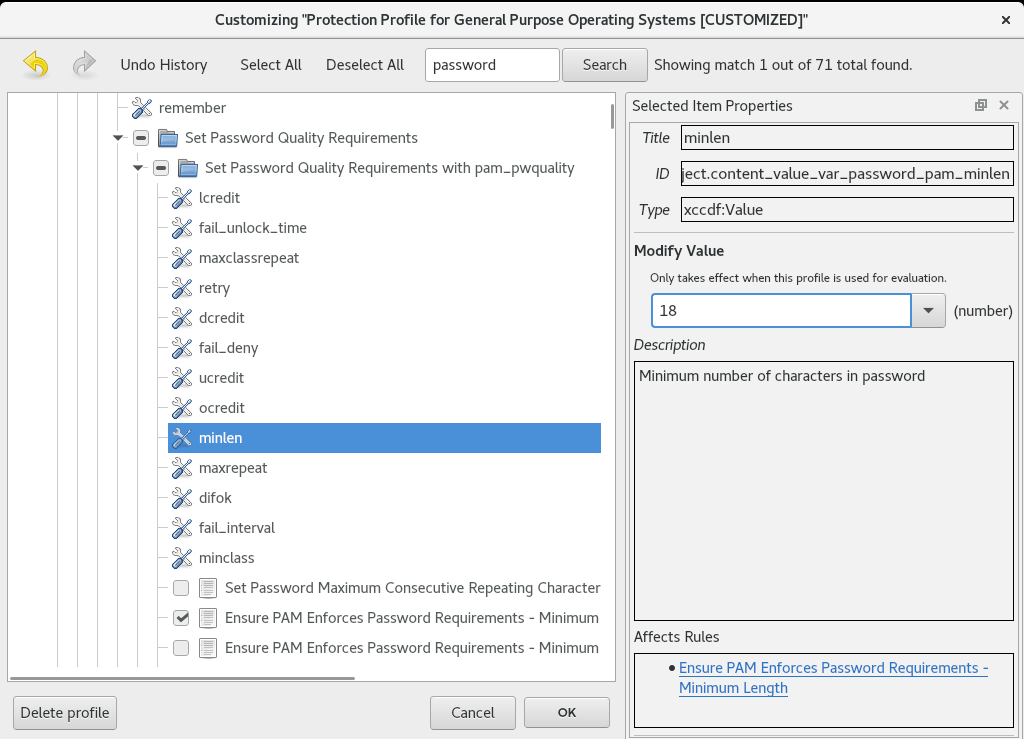
You can customize a security profile by changing parameters in certain rules (for example, minimum password length), removing rules that you cover in a different way, and selecting additional rules, to implement internal policies. You cannot define new rules by customizing a profile.
The following procedure demonstrates the use of SCAP Workbench for customizing (tailoring) a profile. You can also save the tailored profile for use with the oscap command-line utility.
Prerequisites
-
The
scap-workbenchpackage is installed on your system.
Procedure
-
Run
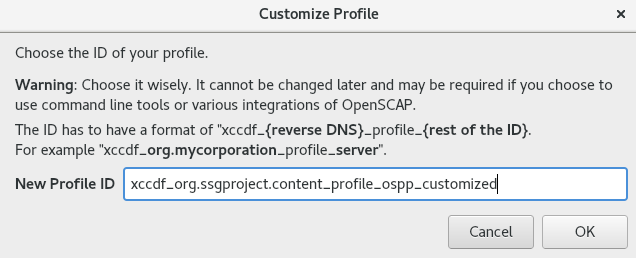
SCAP Workbench, and select the profile to customize by using eitherOpen content from SCAP Security GuideorOpen Other Contentin theFilemenu. To adjust the selected security profile according to your needs, click the button.
This opens the new Customization window that enables you to modify the currently selected profile without changing the original data stream file. Choose a new profile ID.
- Find a rule to modify using either the tree structure with rules organized into logical groups or the field.
Include or exclude rules using check boxes in the tree structure, or modify values in rules where applicable.
- Confirm the changes by clicking the button.
To store your changes permanently, use one of the following options:
-
Save a customization file separately by using
Save Customization Onlyin theFilemenu. Save all security content at once by
Save Allin theFilemenu.If you select the
Into a directoryoption,SCAP Workbenchsaves both the data stream file and the customization file to the specified location. You can use this as a backup solution.By selecting the
As RPMoption, you can instructSCAP Workbenchto create an RPM package containing the data stream file and the customization file. This is useful for distributing the security content to systems that cannot be scanned remotely, and for delivering the content for further processing.
-
Save a customization file separately by using
Because SCAP Workbench does not support results-based remediations for tailored profiles, use the exported remediations with the oscap command-line utility.
6.9. Deploying systems that are compliant with a security profile immediately after an installation
You can use the OpenSCAP suite to deploy RHEL systems that are compliant with a security profile, such as OSPP, PCI-DSS, and HIPAA profile, immediately after the installation process. Using this deployment method, you can apply specific rules that cannot be applied later using remediation scripts, for example, a rule for password strength and partitioning.
6.9.1. Profiles not compatible with Server with GUI
Certain security profiles provided as part of the SCAP Security Guide are not compatible with the extended package set included in the Server with GUI base environment. Therefore, do not select Server with GUI when installing systems compliant with one of the following profiles:
| Profile name | Profile ID | Justification | Notes |
|---|---|---|---|
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Server |
|
Packages | |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Server |
|
Packages | |
| Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171) |
|
The | |
| Protection Profile for General Purpose Operating Systems |
|
The | |
| DISA STIG for Red Hat Enterprise Linux 8 |
|
Packages | To install a RHEL system as a Server with GUI aligned with DISA STIG in RHEL version 8.4 and later, you can use the DISA STIG with GUI profile. |
6.9.2. Deploying baseline-compliant RHEL systems using the graphical installation
Use this procedure to deploy a RHEL system that is aligned with a specific baseline. This example uses Protection Profile for General Purpose Operating System (OSPP).
Certain security profiles provided as part of the SCAP Security Guide are not compatible with the extended package set included in the Server with GUI base environment. For additional details, see Profiles not compatible with a GUI server.
Prerequisites
-
You have booted into the
graphicalinstallation program. Note that the OSCAP Anaconda Add-on does not support interactive text-only installation. -
You have accessed the
Installation Summarywindow.
Procedure
-
From the
Installation Summarywindow, clickSoftware Selection. TheSoftware Selectionwindow opens. -
From the
Base Environmentpane, select theServerenvironment. You can select only one base environment. -
Click
Doneto apply the setting and return to theInstallation Summarywindow. -
Because OSPP has strict partitioning requirements that must be met, create separate partitions for
/boot,/home,/var,/tmp,/var/log,/var/tmp, and/var/log/audit. -
Click
Security Policy. TheSecurity Policywindow opens. -
To enable security policies on the system, toggle the
Apply security policyswitch toON. -
Select
Protection Profile for General Purpose Operating Systemsfrom the profile pane. -
Click
Select Profileto confirm the selection. -
Confirm the changes in the
Changes that were done or need to be donepane that is displayed at the bottom of the window. Complete any remaining manual changes. Complete the graphical installation process.
NoteThe graphical installation program automatically creates a corresponding Kickstart file after a successful installation. You can use the
/root/anaconda-ks.cfgfile to automatically install OSPP-compliant systems.
Verification
To check the current status of the system after installation is complete, reboot the system and start a new scan:
oscap xccdf eval --profile ospp --report eval_postinstall_report.html /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
# oscap xccdf eval --profile ospp --report eval_postinstall_report.html /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.9.3. Deploying baseline-compliant RHEL systems using Kickstart
You can deploy RHEL systems that are aligned with a specific baseline. This example uses Protection Profile for General Purpose Operating System (OSPP).
Prerequisites
-
The
scap-security-guidepackage is installed on your RHEL 8 system.
Procedure
-
Open the
/usr/share/scap-security-guide/kickstart/ssg-rhel8-ospp-ks.cfgKickstart file in an editor of your choice. -
Update the partitioning scheme to fit your configuration requirements. For OSPP compliance, the separate partitions for
/boot,/home,/var,/tmp,/var/log,/var/tmp, and/var/log/auditmust be preserved, and you can only change the size of the partitions. - Start a Kickstart installation as described in Performing an automated installation using Kickstart.
Passwords in Kickstart files are not checked for OSPP requirements.
Verification
To check the current status of the system after installation is complete, reboot the system and start a new scan:
oscap xccdf eval --profile ospp --report eval_postinstall_report.html /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
# oscap xccdf eval --profile ospp --report eval_postinstall_report.html /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.10. Scanning container and container images for vulnerabilities
Use this procedure to find security vulnerabilities in a container or a container image.
The oscap-podman command is available from RHEL 8.2. For RHEL 8.1 and 8.0, use the workaround described in the Using OpenSCAP for scanning containers in RHEL 8 Knowledgebase article.
Prerequisites
-
The
openscap-utilsandbzip2packages are installed.
Procedure
Download the latest RHSA OVAL definitions for your system:
wget -O - https://www.redhat.com/security/data/oval/v2/RHEL8/rhel-8.oval.xml.bz2 | bzip2 --decompress > rhel-8.oval.xml
# wget -O - https://www.redhat.com/security/data/oval/v2/RHEL8/rhel-8.oval.xml.bz2 | bzip2 --decompress > rhel-8.oval.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Get the ID of a container or a container image, for example:
podman images REPOSITORY TAG IMAGE ID CREATED SIZE registry.access.redhat.com/ubi8/ubi latest 096cae65a207 7 weeks ago 239 MB
# podman images REPOSITORY TAG IMAGE ID CREATED SIZE registry.access.redhat.com/ubi8/ubi latest 096cae65a207 7 weeks ago 239 MBCopy to Clipboard Copied! Toggle word wrap Toggle overflow Scan the container or the container image for vulnerabilities and save results to the vulnerability.html file:
oscap-podman 096cae65a207 oval eval --report vulnerability.html rhel-8.oval.xml
# oscap-podman 096cae65a207 oval eval --report vulnerability.html rhel-8.oval.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the
oscap-podmancommand requires root privileges, and the ID of a container is the first argument.
Verification
Check the results in a browser of your choice, for example:
firefox vulnerability.html &
$ firefox vulnerability.html &Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.11. Assessing security compliance of a container or a container image with a specific baseline
You can assess the compliance of your container or a container image with a specific security baseline, such as Operating System Protection Profile (OSPP), Payment Card Industry Data Security Standard (PCI-DSS), and Health Insurance Portability and Accountability Act (HIPAA).
The oscap-podman command is available from RHEL 8.2. For RHEL 8.1 and 8.0, use the workaround described in the Using OpenSCAP for scanning containers in RHEL 8 Knowledgebase article.
Prerequisites
-
The
openscap-utilsandscap-security-guidepackages are installed. - You have root access to the system.
Procedure
Find the ID of a container or a container image:
-
To find the ID of a container, enter the
podman ps -acommand. -
To find the ID of a container image, enter the
podman imagescommand.
-
To find the ID of a container, enter the
Evaluate the compliance of the container or container image with a profile and save the scan results into a file:
oscap-podman <ID> xccdf eval --report <scan-report.html> --profile <profileID> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xml
# oscap-podman <ID> xccdf eval --report <scan-report.html> --profile <profileID> /usr/share/xml/scap/ssg/content/ssg-rhel8-ds.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace:
-
<ID>with the ID of your container or container image -
<scan-report.html>with the file name whereoscapsaves the scan results -
<profileID>with the profile ID with which the system should comply, for example,hipaa,ospp, orpci-dss
-
Verification
Check the results in a browser of your choice, for example:
firefox <scan-report.html> &
$ firefox <scan-report.html> &Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The rules marked as notapplicable apply only to bare-metal and virtualized systems and not to containers or container images.
6.12. SCAP Security Guide profiles supported in RHEL 8
Use only the SCAP content provided in the particular minor release of RHEL. This is because components that participate in hardening are sometimes updated with new capabilities. SCAP content changes to reflect these updates, but it is not always compatible with earlier versions.
In the following tables, you can find the profiles provided in each minor version of RHEL, together with the version of the policy with which the profile aligns.
You can get the information relevant for the version of scap-security-guide RPM installed on your system by using the oscap info command. For more information, see Viewing profiles for configuration compliance.
| Profile name | Profile ID | Policy version |
|---|---|---|
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Enhanced Level |
| 2.0 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 High Level |
| 2.0 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Intermediary Level |
| 2.0 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Minimal Level |
| 2.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Server |
| 3.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Server |
| 3.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Workstation |
| 3.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Workstation |
| 3.0.0 |
| Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171) |
| r1 |
| Australian Cyber Security Centre (ACSC) Essential Eight |
| not versioned |
| Health Insurance Portability and Accountability Act (HIPAA) |
| not versioned |
| Australian Cyber Security Centre (ACSC) ISM Official |
| not versioned |
| Protection Profile for General Purpose Operating Systems |
| 4.2.1 |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
|
RHEL 8.10.0 to RHEL 8.10.4:4.0 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) for Red Hat Enterprise Linux 8 |
| V2R4 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) with GUI for Red Hat Enterprise Linux 8 |
| V2R4 |
| Profile name | Profile ID | Policy version |
|---|---|---|
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Enhanced Level |
| 2.0 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 High Level |
| 2.0 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Intermediary Level |
| 2.0 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Minimal Level |
| 2.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Server |
|
RHEL 8.9.0 and RHEL 8.9.2:2.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Server |
|
RHEL 8.9.0 and RHEL 8.9.2:2.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Workstation |
|
RHEL 8.9.0 and RHEL 8.9.2:2.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Workstation |
|
RHEL 8.9.0 and RHEL 8.9.2:2.0.0 |
| Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171) |
| r1 |
| Australian Cyber Security Centre (ACSC) Essential Eight |
| not versioned |
| Health Insurance Portability and Accountability Act (HIPAA) |
| not versioned |
| Australian Cyber Security Centre (ACSC) ISM Official |
| not versioned |
| Protection Profile for General Purpose Operating Systems |
| 4.2.1 |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
|
RHEL 8.9.0 and RHEL 8.9.2:3.2.1 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) for Red Hat Enterprise Linux 8 |
|
RHEL 8.9.0 and RHEL 8.9.2:V1R11 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) with GUI for Red Hat Enterprise Linux 8 |
|
RHEL 8.9.0 and RHEL 8.9.2:V1R11 |
| Profile name | Profile ID | Policy version |
|---|---|---|
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Enhanced Level |
| 2.0 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 High Level |
| 2.0 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Intermediary Level |
| 2.0 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Minimal Level |
| 2.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Server |
|
RHEL 8.8.0 and RHEL 8.8.5:2.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Server |
|
RHEL 8.8.0 and RHEL 8.8.5:2.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Workstation |
|
RHEL 8.8.0 and RHEL 8.8.5:2.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Workstation |
|
RHEL 8.8.0 and RHEL 8.8.5:2.0.0 |
| Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171) |
| r1 |
| Australian Cyber Security Centre (ACSC) Essential Eight |
| not versioned |
| Health Insurance Portability and Accountability Act (HIPAA) |
| not versioned |
| Australian Cyber Security Centre (ACSC) ISM Official |
| not versioned |
| Protection Profile for General Purpose Operating Systems |
| 4.2.1 |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
|
RHEL 8.8.0 and RHEL 8.8.5:3.2.1 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) for Red Hat Enterprise Linux 8 |
| V2R2 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) with GUI for Red Hat Enterprise Linux 8 |
| V2R2 |
| Profile name | Profile ID | Policy version |
|---|---|---|
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Enhanced Level |
| 1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 High Level |
| 1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Intermediary Level |
| 1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Minimal Level |
| 1.2 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Server |
| 2.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Server |
| 2.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Workstation |
| 2.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Workstation |
| 2.0.0 |
| Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171) |
| r1 |
| Australian Cyber Security Centre (ACSC) Essential Eight |
| not versioned |
| Health Insurance Portability and Accountability Act (HIPAA) |
| not versioned |
| Australian Cyber Security Centre (ACSC) ISM Official |
| not versioned |
| Protection Profile for General Purpose Operating Systems |
| 4.2.1 |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
| 3.2.1 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) for Red Hat Enterprise Linux 8 |
|
RHEL 8.7.0 and RHEL 8.7.1:V1R7 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) with GUI for Red Hat Enterprise Linux 8 |
|
RHEL 8.7.0 and RHEL 8.7.1:V1R7 |
| Profile name | Profile ID | Policy version |
|---|---|---|
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Enhanced Level |
|
RHEL 8.6.0 to 8.6.10:1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 High Level |
|
RHEL 8.6.0 to 8.6.10:1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Intermediary Level |
|
RHEL 8.6.0 to 8.6.10:1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Minimal Level |
|
RHEL 8.6.0 to 8.6.10:1.2 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Server |
|
RHEL 8.6.0 to RHEL 8.6.2:1.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Server |
|
RHEL 8.6.0 to RHEL 8.6.2:1.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Workstation |
|
RHEL 8.6.0 to RHEL 8.6.2:1.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Workstation |
|
RHEL 8.6.0 to RHEL 8.6.2:1.0.0 |
| Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171) |
| r1 |
| Australian Cyber Security Centre (ACSC) Essential Eight |
| not versioned |
| Health Insurance Portability and Accountability Act (HIPAA) |
| not versioned |
| Australian Cyber Security Centre (ACSC) ISM Official |
| not versioned |
| Protection Profile for General Purpose Operating Systems |
| 4.2.1 |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
| 3.2.1 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) for Red Hat Enterprise Linux 8 |
|
RHEL 8.6.0:V1R5 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) with GUI for Red Hat Enterprise Linux 8 |
|
RHEL 8.6.0:V1R5 |
| Profile name | Profile ID | Policy version |
|---|---|---|
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Enhanced Level |
| 1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 High Level |
| 1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Intermediary Level |
| 1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Minimal Level |
| 1.2 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Server |
| 1.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Server |
| 1.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Workstation |
| 1.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Workstation |
| 1.0.0 |
| Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171) |
| r1 |
| Australian Cyber Security Centre (ACSC) Essential Eight |
| not versioned |
| Health Insurance Portability and Accountability Act (HIPAA) |
| not versioned |
| Australian Cyber Security Centre (ACSC) ISM Official |
| not versioned |
| Protection Profile for General Purpose Operating Systems |
| 4.2.1 |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
| 3.2.1 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) for Red Hat Enterprise Linux 8 |
|
RHEL 8.5.0 to RHEL 8.5.3:V1R3 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) with GUI for Red Hat Enterprise Linux 8 |
|
RHEL 8.5.0 to RHEL 8.5.3:V1R3 |
| Profile name | Profile ID | Policy version |
|---|---|---|
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Enhanced Level |
| 1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 High Level |
| RHEL 8.4.4 and later:1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Intermediary Level |
| 1.2 |
| French National Agency for the Security of Information Systems (ANSSI) BP-028 Minimal Level |
| 1.2 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Server |
|
RHEL 8.4.3 and earlier:1.0.0 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Server |
|
RHEL 8.4.4 to RHEL 8.4.10:1.0.1 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 1 - Workstation |
|
RHEL 8.4.4 to RHEL 8.4.10:1.0.1 |
| CIS Red Hat Enterprise Linux 8 Benchmark for Level 2 - Workstation |
|
RHEL 8.4.4 to RHEL 8.4.10:1.0.1 |
| Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171) |
| r1 |
| Australian Cyber Security Centre (ACSC) Essential Eight |
| not versioned |
| Australian Cyber Security Centre (ACSC) ISM Official |
| RHEL 8.4.4 and later:not versioned |
| Health Insurance Portability and Accountability Act (HIPAA) |
| not versioned |
| Protection Profile for General Purpose Operating Systems |
| 4.2.1 |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
| 3.2.1 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) for Red Hat Enterprise Linux 8 |
|
RHEL 8.4.3 and earlier:V1R1 |
| The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) with GUI for Red Hat Enterprise Linux 8 |
|
RHEL 8.4.4 to RHEL 8.4.7:V1R3 |
| Profile name | Profile ID | Policy version |
|---|---|---|
| CIS Red Hat Enterprise Linux 8 Benchmark |
| 1.0.0 |
| Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171) |
| r1 |
| Australian Cyber Security Centre (ACSC) Essential Eight |
| not versioned |
| Health Insurance Portability and Accountability Act (HIPAA) |
| not versioned |
| Protection Profile for General Purpose Operating Systems |
| 4.2.1 |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
| 3.2.1 |
| [DRAFT] The Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) for Red Hat Enterprise Linux 8 |
| draft |
| Profile name | Profile ID | Policy version |
|---|---|---|
| Australian Cyber Security Centre (ACSC) Essential Eight |
| not versioned |
| Protection Profile for General Purpose Operating Systems |
| 4.2.1 |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
| 3.2.1 |
| [DRAFT] DISA STIG for Red Hat Enterprise Linux 8 |
| draft |
| Profile name | Profile ID | Policy version |
|---|---|---|
| Protection Profile for General Purpose Operating Systems |
| 4.2.1 |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
| 3.2.1 |
| Profile name | Profile ID | Policy version |
|---|---|---|
| OSPP - Protection Profile for General Purpose Operating Systems |
| draft |
| PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8 |
| 3.2.1 |