Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 2. Viewing, starting and stopping the Identity Management services
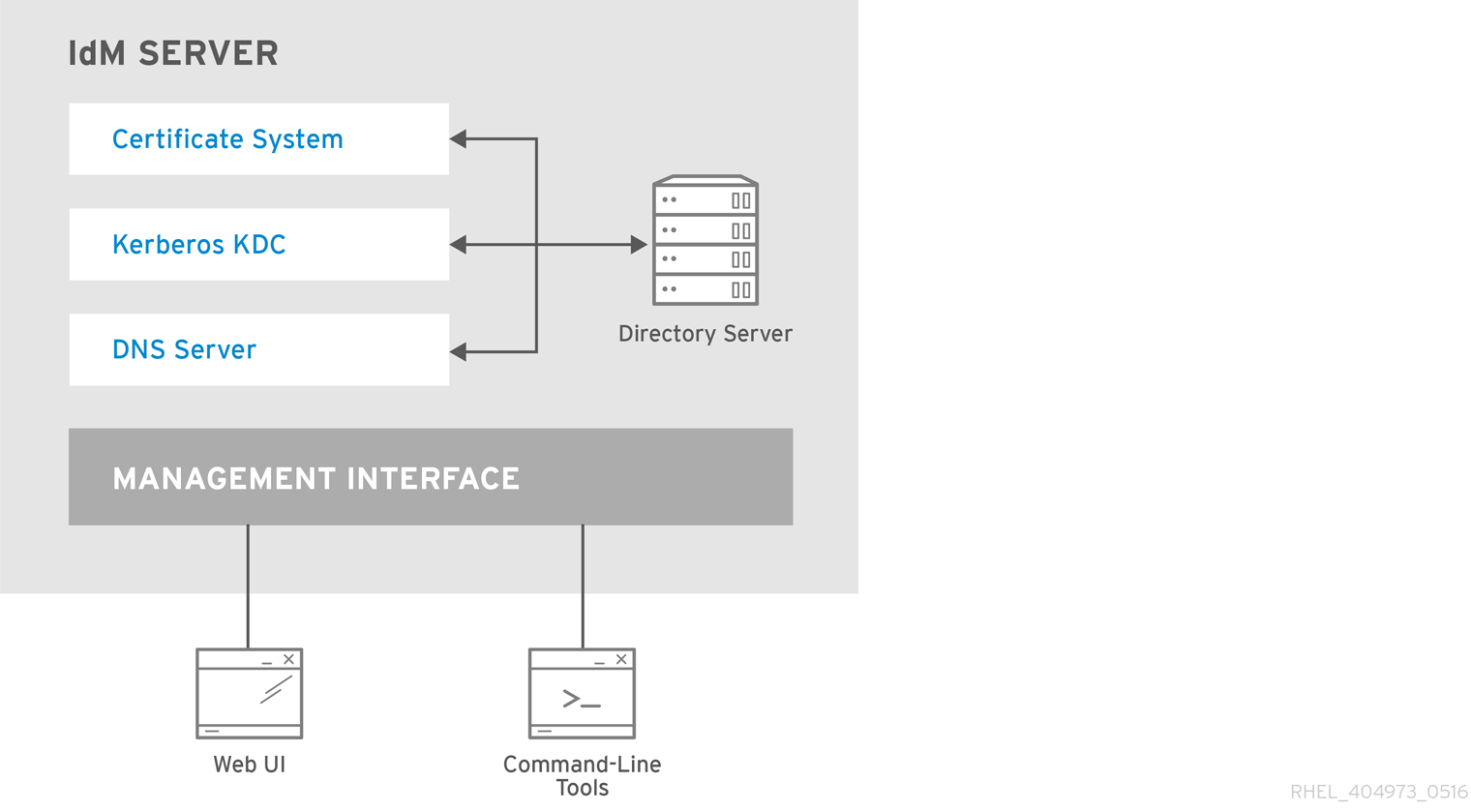
Identity Management (IdM) servers are Red Hat Enterprise Linux systems that work as domain controllers (DCs). A number of different services are running on IdM servers, most notably the Directory Server, Certificate Authority (CA), DNS, and Kerberos.
2.1. The IdM services
There are many different services that can be installed and run on the IdM servers and clients.
List of services hosted by IdM servers
Most of the following services are not strictly required to be installed on the IdM server. For example, you can install services such as a certificate authority (CA) or DNS server on an external server outside the IdM domain.
- Kerberos
-
the
krb5kdcandkadminservices
IdM uses the Kerberos protocol to support single sign-on. With Kerberos, users only need to present the correct username and password once and can access IdM services without the system prompting for credentials again.
Kerberos is divided into two parts:
-
The
krb5kdcservice is the Kerberos Authentication service and Key Distribution Center (KDC) daemon. -
The
kadminservice is the Kerberos database administration program.
For information about how to authenticate using Kerberos in IdM, see Logging in to Identity Management from the command line and Logging in to IdM in the Web UI: Using a Kerberos ticket.
- LDAP directory server
-
the
dirsrvservice
The IdM LDAP directory server instance stores all IdM information, such as information related to Kerberos, user accounts, host entries, services, policies, DNS, and others. The LDAP directory server instance is based on the same technology as Red Hat Directory Server. However, it is tuned to IdM-specific tasks.
- Certificate Authority
-
the
pki-tomcatdservice
The integrated certificate authority (CA) is based on the same technology as Red Hat Certificate System. pki is the command line for accessing Certificate System services.
You can also install the server without the integrated CA if you create and provide all required certificates independently.
For more information, see Planning your CA services.
- Domain Name System (DNS)
-
the
namedservice
IdM uses DNS for dynamic service discovery. The IdM client installation utility can use information from DNS to automatically configure the client machine. After the client is enrolled in the IdM domain, it uses DNS to locate IdM servers and services within the domain. The BIND (Berkeley Internet Name Domain) implementation of the DNS (Domain Name System) protocols in Red Hat Enterprise Linux includes the named DNS server.
For information, see Planning your DNS services and host names.
- Apache HTTP Server
-
the
httpdservice
The Apache HTTP web server provides the IdM Web UI, and also manages communication between the Certificate Authority and other IdM services.
- Samba / Winbind
-
smbandwinbindservices
Samba implements the Server Message Block (SMB) protocol, also known as the Common Internet File System (CIFS) protocol, in Red Hat Enterprise Linux. Via the smb service, the SMB protocol enables you to access resources on a server, such as file shares and shared printers. If you have configured a Trust with an Active Directory (AD) environment, the`Winbind` service manages communication between IdM servers and AD servers.
- One-time password (OTP) authentication
-
the
ipa-otpdservices
One-time passwords (OTP) are passwords that are generated by an authentication token for only one session, as part of two-factor authentication. OTP authentication is implemented in Red Hat Enterprise Linux via the ipa-otpd service.
For more information, see Logging in to the Identity Management Web UI using one time passwords.
- OpenDNSSEC
-
the
ipa-dnskeysyncdservice
OpenDNSSEC is a DNS manager that automates the process of keeping track of DNS security extensions (DNSSEC) keys and the signing of zones. The ipa-dnskeysyncd service manages synchronization between the IdM Directory Server and OpenDNSSEC.
DNSSEC is only available as Technology Preview in IdM.
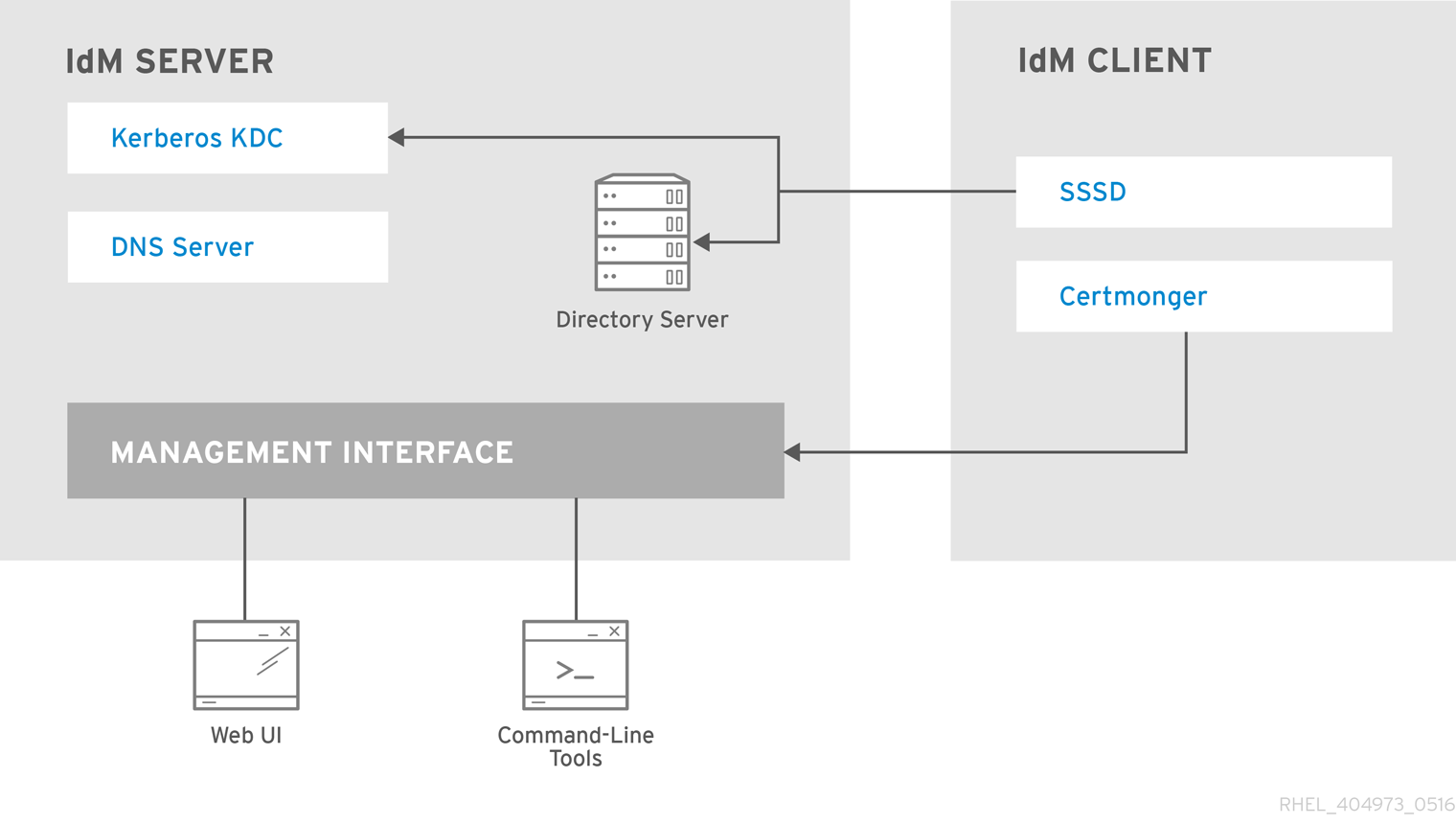
List of services hosted by IdM clients
-
System Security Services Daemon: the
sssdservice
The System Security Services Daemon (SSSD) is the client-side application that manages user authentication and caching credentials. Caching enables the local system to continue normal authentication operations if the IdM server becomes unavailable or if the client goes offline.
For more information, see Understanding SSSD and its benefits.
-
Certmonger: the
certmongerservice
The certmonger service monitors and renews the certificates on the client. It can request new certificates for the services on the system.
For more information, see Obtaining an IdM certificate for a service using certmonger.
2.2. Viewing the status of IdM services
To view the status of the IdM services that are configured on your IdM server, run the ipactl status command:
The output of the ipactl status command on your server depends on your IdM configuration. For example, if an IdM deployment does not include a DNS server, the named service is not present in the list.
You cannot use the IdM web UI to view the status of all the IdM services running on a particular IdM server. Kerberized services running on different servers can be viewed in the Identity
2.3. Starting and stopping the entire Identity Management server
Use the ipa systemd service to stop, start, or restart the entire IdM server along with all the installed services. Using the systemctl utility to control the ipa systemd service ensures all services are stopped, started, or restarted in the appropriate order. The ipa systemd service also upgrades the RHEL IdM configuration before starting the IdM services, and it uses the proper SELinux contexts when administrating with IdM services. You do not need to have a valid Kerberos ticket to run the systemctl ipa commands.
ipa systemd service commands
To start the entire IdM server:
systemctl start ipa
# systemctl start ipaTo stop the entire IdM server:
systemctl stop ipa
# systemctl stop ipaTo restart the entire IdM server:
systemctl restart ipa
# systemctl restart ipa
To show the status of all the services that make up IdM, use the ipactl utility:
ipactl status
# ipactl status-
Do not directly use the
ipactlutility to start, stop, or restart IdM services. Use thesystemctl ipacommands instead, which call theipactlutility in a predictable environment. -
You cannot use the IdM web UI to perform the
ipactlcommands.
2.4. Starting and stopping an individual Identity Management service
Changing IdM configuration files manually is generally not recommended. However, certain situations require that an administrator performs a manual configuration of specific services. In such situations, use the systemctl utility to stop, start, or restart an individual IdM service.
For example, use systemctl after customizing the Directory Server behavior, without modifying the other IdM services:
systemctl restart dirsrv@REALM-NAME.service
# systemctl restart dirsrv@REALM-NAME.service
Also, when initially deploying an IdM trust with Active Directory, modify the /etc/sssd/sssd.conf file, adding:
- Specific parameters to tune the timeout configuration options in an environment where remote servers have a high latency
- Specific parameters to tune the Active Directory site affinity
- Overrides for certain configuration options that are not provided by the global IdM settings
To apply the changes you have made in the /etc/sssd/sssd.conf file:
systemctl restart sssd.service
# systemctl restart sssd.service
Running systemctl restart sssd.service is required because the System Security Services Daemon (SSSD) does not automatically re-read or re-apply its configuration.
Note that for changes that affect IdM identity ranges, a complete server reboot is recommended.
To restart multiple IdM domain services, always use systemctl restart ipa. Because of dependencies between the services installed with the IdM server, the order in which they are started and stopped is critical. The ipa systemd service ensures that the services are started and stopped in the appropriate order.
Useful systemctl commands
To start a particular IdM service:
systemctl start name.service
# systemctl start name.serviceTo stop a particular IdM service:
systemctl stop name.service
# systemctl stop name.serviceTo restart a particular IdM service:
systemctl restart name.service
# systemctl restart name.serviceTo view the status of a particular IdM service:
systemctl status name.service
# systemctl status name.service
You cannot use the IdM web UI to start or stop the individual services running on IdM servers. You can only use the web UI to modify the settings of a Kerberized service by navigating to Identity Services and selecting the service.
2.5. Methods for displaying IdM software version
You can display the IdM version number with:
- The IdM WebUI
-
ipacommands -
rpmcommands
- Displaying version through the WebUI
In the IdM WebUI, the software version can be displayed by choosing
Aboutfrom the username menu at the upper-right.- Displaying version with
ipacommands From the command line, use the
ipa --versioncommand.ipa --version VERSION: 4.8.0, API_VERSION: 2.233
[root@server ~]# ipa --version VERSION: 4.8.0, API_VERSION: 2.233Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Displaying version with
rpmcommands If IdM services are not operating properly, you can use the
rpmutility to determine the version number of theipa-serverpackage that is currently installed.rpm -q ipa-server ipa-server-4.8.0-11.module+el8.1.0+4247+9f3fd721.x86_64
[root@server ~]# rpm -q ipa-server ipa-server-4.8.0-11.module+el8.1.0+4247+9f3fd721.x86_64Copy to Clipboard Copied! Toggle word wrap Toggle overflow