Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 8. Backing up and restoring IdM
Identity Management lets you manually back up and restore the IdM system after a data loss event.
During a backup, the system creates a directory that stores information about your IdM setup. You can use this backup directory to restore your original IdM setup.
The IdM backup and restore features are designed to help prevent data loss. To mitigate the impact of server loss and ensure continued operation, provide alternative servers to clients. For information on establishing a replication topology see Preparing for server loss with replication.
8.1. IdM backup types
With the ipa-backup utility, you can create two types of backups:
- Full-server backup
- Contains all server configuration files related to IdM, and LDAP data in LDAP Data Interchange Format (LDIF) files
- IdM services must be offline.
- Suitable for rebuilding an IdM deployment from scratch.
- Data-only backup
- Contains LDAP data in LDIF files and the replication changelog
- IdM services can be online or offline.
- Suitable for restoring IdM data to a state in the past
8.2. Naming conventions for IdM backup files
By default, IdM stores backups as .tar archives in subdirectories of the /var/lib/ipa/backup/ directory.
The archives and subdirectories follow these naming conventions:
- Full-server backup
An archive named
ipa-full.tarin a directory namedipa-full-<YEAR-MM-DD-HH-MM-SS>, with the time specified in GMT time.ll /var/lib/ipa/backup/ipa-full-2021-01-29-12-11-46 total 3056 -rw-r--r--. 1 root root 158 Jan 29 12:11 header -rw-r--r--. 1 root root 3121511 Jan 29 12:11 ipa-full.tar
[root@server ~]# ll /var/lib/ipa/backup/ipa-full-2021-01-29-12-11-46 total 3056 -rw-r--r--. 1 root root 158 Jan 29 12:11 header -rw-r--r--. 1 root root 3121511 Jan 29 12:11 ipa-full.tarCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Data-only backup
An archive named
ipa-data.tarin a directory namedipa-data-<YEAR-MM-DD-HH-MM-SS>, with the time specified in GMT time.ll /var/lib/ipa/backup/ipa-data-2021-01-29-12-14-23 total 1072 -rw-r--r--. 1 root root 158 Jan 29 12:14 header -rw-r--r--. 1 root root 1090388 Jan 29 12:14 ipa-data.tar
[root@server ~]# ll /var/lib/ipa/backup/ipa-data-2021-01-29-12-14-23 total 1072 -rw-r--r--. 1 root root 158 Jan 29 12:14 header -rw-r--r--. 1 root root 1090388 Jan 29 12:14 ipa-data.tarCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Uninstalling an IdM server does not automatically remove any backup files.
8.3. Considerations when creating a backup
The important behaviors and limitations of the ipa-backup command include the following:
-
By default, the
ipa-backuputility runs in offline mode, which stops all IdM services. The utility automatically restarts IdM services after the backup is finished. - A full-server backup must always run with IdM services offline, but a data-only backup can be performed with services online.
-
By default, the
ipa-backuputility creates backups on the file system containing the/var/lib/ipa/backup/directory. Red Hat recommends creating backups regularly on a file system separate from the production filesystem used by IdM, and archiving the backups to a fixed medium, such as tape or optical storage.
- Consider performing backups on hidden replicas. IdM services can be shut down on hidden replicas without affecting IdM clients.
The
ipa-backuputility checks if all of the services used in your IdM cluster, such as a Certificate Authority (CA), Domain Name System (DNS), and Key Recovery Agent (KRA), are installed on the server where you are running the backup. If the server does not have all these services installed, theipa-backuputility exits with a warning, because backups taken on that host would not be sufficient for a full cluster restoration.For example, if your IdM deployment uses an integrated Certificate Authority (CA), a backup run on a non-CA replica will not capture CA data. Red Hat recommends verifying that the replica where you perform an
ipa-backuphas all of the IdM services used in the cluster installed.You can bypass the IdM server role check with the
ipa-backup --disable-role-checkcommand, but the resulting backup will not contain all the data necessary to restore IdM fully.
8.4. Creating an IdM backup
Create a full-server and data-only backup in offline and online modes using the ipa-backup command.
Prerequisites
-
You must have
rootprivileges to run theipa-backuputility.
Procedure
To create a full-server backup in offline mode, use the
ipa-backuputility without additional options.Copy to Clipboard Copied! Toggle word wrap Toggle overflow To create an offline data-only backup, specify the
--dataoption.ipa-backup --data
[root@server ~]# ipa-backup --dataCopy to Clipboard Copied! Toggle word wrap Toggle overflow To create a full-server backup that includes IdM log files, use the
--logsoption.ipa-backup --logs
[root@server ~]# ipa-backup --logsCopy to Clipboard Copied! Toggle word wrap Toggle overflow To create a data-only backup while IdM services are running, specify both
--dataand--onlineoptions.ipa-backup --data --online
[root@server ~]# ipa-backup --data --onlineCopy to Clipboard Copied! Toggle word wrap Toggle overflow
If the backup fails due to insufficient space in the /tmp directory, use the TMPDIR environment variable to change the destination for temporary files created by the backup process:
TMPDIR=/new/location ipa-backup
[root@server ~]# TMPDIR=/new/location ipa-backupVerification
Ensure the backup directory contains an archive with the backup.
ls /var/lib/ipa/backup/ipa-full-2020-01-14-11-26-06 header ipa-full.tar
[root@server ~]# ls /var/lib/ipa/backup/ipa-full-2020-01-14-11-26-06 header ipa-full.tarCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.5. Creating a GPG2-encrypted IdM backup
You can create encrypted backups using GNU Privacy Guard (GPG) encryption. The following procedure creates an IdM backup and encrypts it using a GPG2 key.
Prerequisites
- You have created a GPG2 key. See Creating a GPG2 key.
Procedure
Create a GPG-encrypted backup by specifying the
--gpgoption.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Ensure that the backup directory contains an encrypted archive with a
.gpgfile extension.ls /var/lib/ipa/backup/ipa-full-2020-01-13-14-38-00 header ipa-full.tar.gpg
[root@server ~]# ls /var/lib/ipa/backup/ipa-full-2020-01-13-14-38-00 header ipa-full.tar.gpgCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.6. Creating a GPG2 key
The following procedure describes how to generate a GPG2 key to use with encryption utilities.
Prerequisites
-
You need
rootprivileges.
Procedure
Install and configure the
pinentryutility.dnf install pinentry mkdir ~/.gnupg -m 700 echo "pinentry-program /usr/bin/pinentry-curses" >> ~/.gnupg/gpg-agent.conf
[root@server ~]# dnf install pinentry [root@server ~]# mkdir ~/.gnupg -m 700 [root@server ~]# echo "pinentry-program /usr/bin/pinentry-curses" >> ~/.gnupg/gpg-agent.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
key-inputfile used for generating a GPG keypair with your preferred details. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: By default, GPG2 stores its keyring in the
~/.gnupgfile. To use a custom keyring location, set theGNUPGHOMEenvironment variable to a directory that is only accessible by root.export GNUPGHOME=/root/backup mkdir -p $GNUPGHOME -m 700
[root@server ~]# export GNUPGHOME=/root/backup [root@server ~]# mkdir -p $GNUPGHOME -m 700Copy to Clipboard Copied! Toggle word wrap Toggle overflow Generate a new GPG2 key based on the contents of the
key-inputfile.gpg2 --batch --gen-key key-input
[root@server ~]# gpg2 --batch --gen-key key-inputCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enter a passphrase to protect the GPG2 key. You use this passphrase to access the private key for decryption.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm the correct passphrase by entering it again.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the new GPG2 key was created successfully.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
List the GPG keys on the server.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.7. When to restore from an IdM backup
You can respond to several disaster scenarios by restoring from an IdM backup:
- Undesirable changes were made to the LDAP content: Entries were modified or deleted, replication carried out those changes throughout the deployment, and you want to revert those changes. Restoring a data-only backup returns the LDAP entries to the previous state without affecting the IdM configuration itself.
- Total Infrastructure Loss, or loss of all CA instances: If a disaster damages all Certificate Authority replicas, the deployment has lost the ability to rebuild itself by deploying additional servers. In this situation, restore a backup of a CA Replica and build new replicas from it.
An upgrade on an isolated server failed: The operating system remains functional, but the IdM data is corrupted, which is why you want to restore the IdM system to a known good state. Red Hat recommends working with Technical Support to diagnose and troubleshoot the issue. If those efforts fail, restore from a full-server backup.
ImportantThe preferred solution for hardware or upgrade failure is to rebuild the lost server from a replica. For more information, see Recovering a single server with replication.
8.8. Considerations when restoring from an IdM backup
If you have a backup created with the ipa-backup utility, you can restore your IdM server or the LDAP content to the state they were in when the backup was performed.
The following are the key considerations while restoring from an IdM backup:
You can only restore a backup on a server that matches the configuration of the server where the backup was originally created. The server must have:
- The same hostname
- The same IP address
- The same version of IdM software
- If one IdM server among many is restored, the restored server becomes the only source of information for IdM. All other servers must be re-initialized from the restored server.
- Since any data created after the last backup will be lost, do not use the backup and restore solution for normal system maintenance.
- If a server is lost, Red Hat recommends rebuilding the server by reinstalling it as a replica, instead of restoring from a backup. Creating a new replica preserves data from the current working environment. For more information, see Preparing for server loss with replication.
- The backup and restore features can only be managed from the command line and are not available in the IdM web UI.
-
You cannot restore from backup files located in the
/tmpor/var/tmpdirectories. The IdM Directory Server uses a PrivateTmp directory and cannot access the/tmpor/var/tmpdirectories commonly available to the operating system.
Restoring from a backup requires the same software (RPM) versions on the target host as were installed when the backup was performed. Due to this, Red Hat recommends restoring from a Virtual Machine snapshot rather than a backup. For more information, see Recovering from data loss with VM snapshots.
8.9. Restoring an IdM server from a backup
Restore an IdM server, or its LDAP data, from an IdM backup.
Figure 8.1. Replication topology used in this example
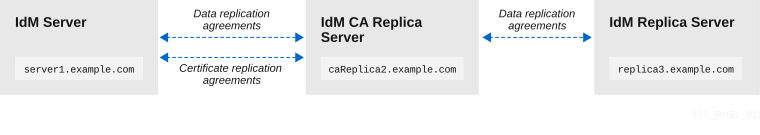
| Server host name | Function |
|---|---|
|
| The server that needs to be restored from backup. |
|
|
A Certificate Authority (CA) replica connected to the |
|
|
A replica connected to the |
Prerequisites
-
You have generated a full-server or data-only backup of the IdM server with the
ipa-backuputility. See Creating a backup. -
Your backup files are not in the
/tmpor/var/tmpdirectories. - Before performing a full-server restore from a full-server backup, uninstall IdM from the server and reinstall IdM using the same server configuration as before.
Procedure
Use the
ipa-restoreutility to restore a full-server or data-only backup.If the backup directory is in the default
/var/lib/ipa/backup/location, enter only the name of the directory:ipa-restore ipa-full-2020-01-14-12-02-32
[root@server1 ~]# ipa-restore ipa-full-2020-01-14-12-02-32Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the backup directory is not in the default location, enter its full path:
ipa-restore /mybackups/ipa-data-2020-02-01-05-30-00
[root@server1 ~]# ipa-restore /mybackups/ipa-data-2020-02-01-05-30-00Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe
ipa-restoreutility automatically detects the type of backup that the directory contains, and performs the same type of restore by default. To perform a data-only restore from a full-server backup, add the--dataoption to theipa-restorecommand:ipa-restore --data ipa-full-2020-01-14-12-02-32
[root@server1 ~]# ipa-restore --data ipa-full-2020-01-14-12-02-32Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Enter the Directory Manager password.
Directory Manager (existing master) password:
Directory Manager (existing master) password:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter
yesto confirm overwriting current data with the backup.Preparing restore from /var/lib/ipa/backup/ipa-full-2020-01-14-12-02-32 on server1.example.com Performing FULL restore from FULL backup Temporary setting umask to 022 Restoring data will overwrite existing live data. Continue to restore? [no]: yes
Preparing restore from /var/lib/ipa/backup/ipa-full-2020-01-14-12-02-32 on server1.example.com Performing FULL restore from FULL backup Temporary setting umask to 022 Restoring data will overwrite existing live data. Continue to restore? [no]: yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
ipa-restoreutility disables replication on all servers that are available:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The utility then stops IdM services, restores the backup, and restarts the services:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Re-initialize all replicas connected to the restored server:
List all replication topology segments for the
domainsuffix, taking note of topology segments involving the restored server.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Re-initialize the
domainsuffix for all topology segments with the restored server.In this example, perform a re-initialization of
caReplica2with data fromserver1.ipa-replica-manage re-initialize --from=server1.example.com Update in progress, 2 seconds elapsed Update succeeded
[root@caReplica2 ~]# ipa-replica-manage re-initialize --from=server1.example.com Update in progress, 2 seconds elapsed Update succeededCopy to Clipboard Copied! Toggle word wrap Toggle overflow Moving on to Certificate Authority data, list all replication topology segments for the
casuffix.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Re-initialize all CA replicas connected to the restored server.
In this example, perform a
csreplicare-initialization ofcaReplica2with data fromserver1.ipa-csreplica-manage re-initialize --from=server1.example.com Directory Manager password: Update in progress, 3 seconds elapsed Update succeeded
[root@caReplica2 ~]# ipa-csreplica-manage re-initialize --from=server1.example.com Directory Manager password: Update in progress, 3 seconds elapsed Update succeededCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Continue moving outward through the replication topology, re-initializing successive replicas, until all servers have been updated with the data from restored server
server1.example.com.In this example, we only have to re-initialize the
domainsuffix onreplica3with the data fromcaReplica2:ipa-replica-manage re-initialize --from=caReplica2.example.com Directory Manager password: Update in progress, 3 seconds elapsed Update succeeded
[root@replica3 ~]# ipa-replica-manage re-initialize --from=caReplica2.example.com Directory Manager password: Update in progress, 3 seconds elapsed Update succeededCopy to Clipboard Copied! Toggle word wrap Toggle overflow Clear SSSD’s cache on every server to avoid authentication problems due to invalid data:
Stop the SSSD service:
systemctl stop sssd
[root@server ~]# systemctl stop sssdCopy to Clipboard Copied! Toggle word wrap Toggle overflow Remove all cached content from SSSD:
sss_cache -E
[root@server ~]# sss_cache -ECopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the SSSD service:
systemctl start sssd
[root@server ~]# systemctl start sssdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot the server.
8.10. Restoring from an encrypted backup
This procedure restores an IdM server from an encrypted IdM backup. The ipa-restore utility automatically detects if an IdM backup is encrypted and restores it using the GPG2 root keyring.
Prerequisites
- A GPG-encrypted IdM backup. See Creating encrypted IdM backups.
- The LDAP Directory Manager password
- The passphrase used when creating the GPG key
Procedure
If you used a custom keyring location when creating the GPG2 keys, verify that the
$GNUPGHOMEenvironment variable is set to that directory. See Creating a GPG2 key.echo $GNUPGHOME /root/backup
[root@server ~]# echo $GNUPGHOME /root/backupCopy to Clipboard Copied! Toggle word wrap Toggle overflow Provide the
ipa-restoreutility with the backup directory location.ipa-restore ipa-full-2020-01-13-18-30-54
[root@server ~]# ipa-restore ipa-full-2020-01-13-18-30-54Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the Directory Manager password.
Directory Manager (existing master) password:
Directory Manager (existing master) password:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the passphrase you used when creating the GPG key.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Re-initialize all replicas connected to the restored server. See Restoring an IdM server from backup.