Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 6. Setting up an IPsec VPN
Configure and manage a secure Virtual Private Network (VPN) by using the Libreswan implementation of the IPsec protocol suite to create encrypted tunnels for secure data transmission over the internet.
IPsec tunnels ensure the confidentiality and integrity of data in transit. Common use cases include connecting branch offices to headquarters or providing remote users with secure access to a corporate network.
RHEL provides different options to configure Libreswan:
- Manually edit the Libreswan configuration files for granular control over advanced options.
-
Use the
vpnRHEL system role to automate the process of creating Libreswan VPN configurations. - Use Nmstate to configure a Libreswan connection through a declarative API.
Libreswan does not use terms such as "client" and "server". Instead, IPsec refers to endpoints as "left" and "right". This design often enables you to use the same configuration on both hosts because Libreswan dynamically determines which role to adopt. As a convention, administrators typically use "left" for the local host and "right" for the remote host.
Libreswan is the only supported VPN technology in RHEL.
IPsec relies on standardized protocols, such as Internet Key Exchange (IKE), to ensure that different systems can communicate effectively. However, in practice, minor differences in how vendors implement these standards can lead to compatibility problems. If you encounter such interoperability issues when connecting Libreswan to a third-party IPsec peer, contact Red Hat Support.
6.1. Libreswan as an IPsec VPN implementation
In RHEL, you can configure a Virtual Private Network (VPN) by using the IPsec protocol, which is supported by the Libreswan application. Libreswan is a continuation of the Openswan application, and many examples from the Openswan documentation are interchangeable with Libreswan.
The IPsec protocol for a VPN is configured using the Internet Key Exchange (IKE) protocol. The terms IPsec and IKE are used interchangeably. An IPsec VPN is also called an IKE VPN, IKEv2 VPN, XAUTH VPN, Cisco VPN or IKE/IPsec VPN. A variant of an IPsec VPN that also uses the Layer 2 Tunneling Protocol (L2TP) is usually called an L2TP/IPsec VPN, which requires the xl2tpd package provided by the optional repository.
Libreswan is an open-source, user-space IKE implementation. IKE v1 and v2 are implemented as a user-level daemon. The IKE protocol is also encrypted. The IPsec protocol is implemented by the Linux kernel, and Libreswan configures the kernel to add and remove VPN tunnel configurations.
The IKE protocol uses UDP port 500 and 4500. The IPsec protocol consists of two protocols:
- Encapsulated Security Payload (ESP), which has protocol number 50.
- Authenticated Header (AH), which has protocol number 51.
The AH protocol is not recommended for use. Users of AH are recommended to migrate to ESP with null encryption.
The IPsec protocol provides two modes of operation:
- Tunnel Mode (the default)
- Transport Mode
You can configure the kernel with IPsec without IKE. This is called manual keying. You can also configure manual keying using the ip xfrm commands, however, this is strongly discouraged for security reasons. Libreswan communicates with the Linux kernel using the Netlink interface. The kernel performs packet encryption and decryption.
Libreswan uses the Network Security Services (NSS) cryptographic library. NSS is certified for use with the Federal Information Processing Standard (FIPS) Publication 140-2.
IKE/IPsec VPNs, implemented by Libreswan and the Linux kernel, is the only VPN technology recommended for use in RHEL. Do not use any other VPN technology without understanding the risks of doing so.
In RHEL, Libreswan follows system-wide cryptographic policies by default. This ensures that Libreswan uses secure settings for current threat models including IKEv2 as a default protocol. See Using system-wide crypto policies for more information.
Libreswan does not use the terms "source" and "destination" or "server" and "client" because IKE/IPsec are peer to peer protocols. Instead, it uses the terms "left" and "right" to refer to end points (the hosts). This also allows you to use the same configuration on both end points in most cases. However, administrators usually choose to always use "left" for the local host and "right" for the remote host.
The leftid and rightid options serve as identification of the respective hosts in the authentication process. See the ipsec.conf(5) man page for more information.
6.2. Authentication methods in Libreswan
Libreswan supports several authentication methods, each of which fits a different scenario.
Pre-Shared key (PSK)
Pre-Shared Key (PSK) is the simplest authentication method. For security reasons, do not use PSKs shorter than 64 random characters. In FIPS mode, PSKs must comply with a minimum-strength requirement depending on the integrity algorithm used. You can set PSK by using the authby=secret connection.
Raw RSA keys
Raw RSA keys are commonly used for static host-to-host or subnet-to-subnet IPsec configurations. Each host is manually configured with the public RSA keys of all other hosts, and Libreswan sets up an IPsec tunnel between each pair of hosts. This method does not scale well for large numbers of hosts.
You can generate a raw RSA key on a host using the ipsec newhostkey command. You can list generated keys by using the ipsec showhostkey command. The leftrsasigkey= line is required for connection configurations that use CKA ID keys. Use the authby=rsasig connection option for raw RSA keys.
X.509 certificates
X.509 certificates are commonly used for large-scale deployments with hosts that connect to a common IPsec gateway. A central certificate authority (CA) signs RSA certificates for hosts or users. This central CA is responsible for relaying trust, including the revocations of individual hosts or users.
For example, you can generate X.509 certificates using the openssl command and the NSS certutil command. Because Libreswan reads user certificates from the NSS database using the certificates' nickname in the leftcert= configuration option, provide a nickname when you create a certificate.
If you use a custom CA certificate, you must import it to the Network Security Services (NSS) database. You can import any certificate in the PKCS #12 format to the Libreswan NSS database by using the ipsec import command.
Libreswan requires an Internet Key Exchange (IKE) peer ID as a subject alternative name (SAN) for every peer certificate as described in section 3.1 of RFC 4945. Disabling this check by setting the require-id-on-certificate=no connection option can make the system vulnerable to man-in-the-middle attacks.
Use the authby=rsasig connection option for authentication based on X.509 certificates using RSA with SHA-2. You can further limit it for ECDSA digital signatures using SHA-2 by setting authby= to ecdsa and RSA Probabilistic Signature Scheme (RSASSA-PSS) digital signatures based authentication with SHA-2 through authby=rsa-sha2. The default value is authby=rsasig,ecdsa.
The certificates and the authby= signature methods should match. This increases interoperability and preserves authentication in one digital signature system.
NULL authentication
NULL authentication is used to gain mesh encryption without authentication. It protects against passive attacks but not against active attacks. However, because IKEv2 allows asymmetric authentication methods, NULL authentication can also be used for internet-scale opportunistic IPsec. In this model, clients authenticate the server, but servers do not authenticate the client. This model is similar to secure websites using TLS. Use authby=null for NULL authentication.
Protection against quantum computers
In addition to the previously mentioned authentication methods, you can use the Post-quantum Pre-shared Key (PPK) method to protect against possible attacks by quantum computers. Individual clients or groups of clients can use their own PPK by specifying a PPK ID that corresponds to an out-of-band configured pre-shared key.
Using IKEv1 with pre-shared keys protects against quantum attackers. The redesign of IKEv2 does not offer this protection natively. Libreswan offers the use of a Post-quantum Pre-shared Key (PPK) to protect IKEv2 connections against quantum attacks.
To enable optional PPK support, add ppk=yes to the connection definition. To require PPK, add ppk=insist. Then, each client can be given a PPK ID with a secret value that is communicated out-of-band (and preferably quantum-safe). The PPK’s should be very strong in randomness and not based on dictionary words. The PPK ID and PPK data are stored in the ipsec.secrets file, for example:
@west @east : PPKS "user1" "thestringismeanttobearandomstr"
@west @east : PPKS "user1" "thestringismeanttobearandomstr"
The PPKS option refers to static PPKs. This experimental function uses one-time-pad-based Dynamic PPKs. Upon each connection, a new part of the one-time pad is used as the PPK. When used, that part of the dynamic PPK inside the file is overwritten with zeros to prevent re-use. If there is no more one-time-pad material left, the connection fails. See the ipsec.secrets(5) man page for more information.
The implementation of dynamic PPKs is provided as an unsupported Technology Preview. Use with caution.
6.3. Installing Libreswan
Before you can set a VPN through the Libreswan IPsec/IKE implementation, you must install the corresponding packages, start the ipsec service, and allow the service in your firewall.
Prerequisites
-
The
AppStreamrepository is enabled.
Procedure
Install the
libreswanpackages:dnf install libreswan
# dnf install libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you are re-installing Libreswan, remove its old database files and create a new database:
systemctl stop ipsec rm /var/lib/ipsec/nss/*db ipsec initnss
# systemctl stop ipsec # rm /var/lib/ipsec/nss/*db # ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the
ipsecservice, and enable the service to be started automatically on boot:systemctl enable ipsec --now
# systemctl enable ipsec --nowCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the firewall to allow 500 and 4500/UDP ports for the IKE, ESP, and AH protocols by adding the
ipsecservice:firewall-cmd --add-service="ipsec" firewall-cmd --runtime-to-permanent
# firewall-cmd --add-service="ipsec" # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.4. Creating a host-to-host VPN
You can configure Libreswan to create a host-to-host IPsec VPN between two hosts referred to as left and right using authentication by raw RSA keys.
Prerequisites
-
Libreswan is installed and the
ipsecservice is started on each node.
Procedure
Generate a raw RSA key pair on each host:
ipsec newhostkey
# ipsec newhostkeyCopy to Clipboard Copied! Toggle word wrap Toggle overflow The previous step returned the generated key’s
ckaid. Use thatckaidwith the following command on left, for example:ipsec showhostkey --left --ckaid 2d3ea57b61c9419dfd6cf43a1eb6cb306c0e857d
# ipsec showhostkey --left --ckaid 2d3ea57b61c9419dfd6cf43a1eb6cb306c0e857dCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output of the previous command generated the
leftrsasigkey=line required for the configuration. Do the same on the second host (right):ipsec showhostkey --right --ckaid a9e1f6ce9ecd3608c24e8f701318383f41798f03
# ipsec showhostkey --right --ckaid a9e1f6ce9ecd3608c24e8f701318383f41798f03Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the
/etc/ipsec.d/directory, create a newmy_host-to-host.conffile. Write the RSA host keys from the output of theipsec showhostkeycommands in the previous step to the new file. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow After importing keys, restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow Load the connection:
ipsec auto --add mytunnel
# ipsec auto --add mytunnelCopy to Clipboard Copied! Toggle word wrap Toggle overflow Establish the tunnel:
ipsec auto --up mytunnel
# ipsec auto --up mytunnelCopy to Clipboard Copied! Toggle word wrap Toggle overflow To automatically start the tunnel when the
ipsecservice is started, add the following line to the connection definition:auto=start
auto=startCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
6.5. Configuring a site-to-site VPN
To create a site-to-site IPsec VPN, by joining two networks, an IPsec tunnel between the two hosts is created. The hosts thus act as the end points, which are configured to permit traffic from one or more subnets to pass through. Therefore you can think of the host as gateways to the remote portion of the network.
The configuration of the site-to-site VPN only differs from the host-to-host VPN in that one or more networks or subnets must be specified in the configuration file.
Prerequisites
- A host-to-host VPN is already configured.
Procedure
Copy the file with the configuration of your host-to-host VPN to a new file, for example:
cp /etc/ipsec.d/my_host-to-host.conf /etc/ipsec.d/my_site-to-site.conf
# cp /etc/ipsec.d/my_host-to-host.conf /etc/ipsec.d/my_site-to-site.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the subnet configuration to the file created in the previous step, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
6.6. Configuring a remote access VPN
Road warriors are traveling users with mobile clients and a dynamically assigned IP address. The mobile clients authenticate using X.509 certificates.
The following example shows configuration for IKEv2, and it avoids using the IKEv1 XAUTH protocol.
On the server:
On the mobile client, the road warrior’s device, use a slight variation of the previous configuration:
If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
6.7. Configuring a mesh VPN
A mesh VPN network, which is also known as an any-to-any VPN, is a network where all nodes communicate using IPsec. The configuration allows for exceptions for nodes that cannot use IPsec. The mesh VPN network can be configured in two ways:
- To require IPsec.
- To prefer IPsec but allow a fallback to clear-text communication.
Authentication between the nodes can be based on X.509 certificates or on DNS Security Extensions (DNSSEC).
You can use any regular IKEv2 authentication method for opportunistic IPsec, because these connections are regular Libreswan configurations, except for the opportunistic IPsec that is defined by right=%opportunisticgroup entry. A common authentication method is for hosts to authenticate each other based on X.509 certificates using a commonly shared certification authority (CA). Cloud deployments typically issue certificates for each node in the cloud as part of the standard procedure.
Do not use PreSharedKey (PSK) authentication because one compromised host would result in the group PSK secret being compromised as well.
You can use NULL authentication to deploy encryption between nodes without authentication, which protects only against passive attackers.
The following procedure uses X.509 certificates. You can generate these certificates by using any kind of CA management system, such as the Dogtag Certificate System. Dogtag assumes that the certificates for each node are available in the PKCS #12 format (.p12 files), which contain the private key, the node certificate, and the Root CA certificate used to validate other nodes' X.509 certificates.
Each node has an identical configuration with the exception of its X.509 certificate. This allows for adding new nodes without reconfiguring any of the existing nodes in the network. The PKCS #12 files require a "friendly name", for which we use the name "node" so that the configuration files referencing the friendly name can be identical for all nodes.
Prerequisites
-
Libreswan is installed, and the
ipsecservice is started on each node. A new NSS database is initialized.
If you already have an old NSS database, remove the old database files:
systemctl stop ipsec rm /var/lib/ipsec/nss/*db
# systemctl stop ipsec # rm /var/lib/ipsec/nss/*dbCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can initialize a new database with the following command:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure
On each node, import PKCS #12 files. This step requires the password used to generate the PKCS #12 files:
ipsec import nodeXXX.p12
# ipsec import nodeXXX.p12Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the following three connection definitions for the
IPsec required(private),IPsec optional(private-or-clear), andNo IPsec(clear) profiles:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
auto=<option>Specifies how Libreswan handles connection initiation. Valid options:
-
ondemand: Initiates a connection automatically when the kernel receives the first packet that matches a trap XFRM policy. Use this option for opportunistic IPsec or for connections that do not need to be active continuously. -
add: Prepares the connection and accepts incoming connection requests. To initiate the connection from the local peer, use theipsec auto --upcommand. -
start: Automatically activates the connection when the Libreswan service starts.
-
leftid=%fromcertandrightid=%fromcert- Configures Libreswan to retrieve the identity from the distinguished name (DN) field of the certificate.
leftcert="<server_certificate_nickname>"- Specifies the nickname of the server’s certificate used in the NSS database.
Add the IP address of the network to the corresponding category. For example, if all nodes reside in the
10.15.0.0/16network, and all nodes must use IPsec encryption:echo "10.15.0.0/16" >> /etc/ipsec.d/policies/private
# echo "10.15.0.0/16" >> /etc/ipsec.d/policies/privateCopy to Clipboard Copied! Toggle word wrap Toggle overflow To allow certain nodes, for example,
10.15.34.0/24, to work with and without IPsec, add those nodes to the private-or-clear group:echo "10.15.34.0/24" >> /etc/ipsec.d/policies/private-or-clear
# echo "10.15.34.0/24" >> /etc/ipsec.d/policies/private-or-clearCopy to Clipboard Copied! Toggle word wrap Toggle overflow To define a host, for example,
10.15.1.2, which is not capable of IPsec into the clear group, use:echo "10.15.1.2/32" >> /etc/ipsec.d/policies/clear
# echo "10.15.1.2/32" >> /etc/ipsec.d/policies/clearCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can create the files in the
/etc/ipsec.d/policiesdirectory from a template for each new node, or you can provision them by using Puppet or Ansible.Note that every node has the same list of exceptions or different traffic flow expectations. Two nodes, therefore, might not be able to communicate because one requires IPsec and the other cannot use IPsec.
Restart the node to add it to the configured mesh:
systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Open an IPsec tunnel by using the
pingcommand:ping <nodeYYY>
# ping <nodeYYY>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the NSS database with the imported certification:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow See which tunnels are open on the node:
ipsec trafficstatus
# ipsec trafficstatus 006 #2: "private#10.15.0.0/16"[1] ...<nodeYYY>, type=ESP, add_time=1691399301, inBytes=512, outBytes=512, maxBytes=2^63B, id='C=US, ST=NC, O=Example Organization, CN=east'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.8. Deploying a FIPS-compliant IPsec VPN
You can deploy a FIPS-compliant IPsec VPN solution with Libreswan. To do so, you can identify which cryptographic algorithms are available and which are disabled for Libreswan in FIPS mode.
Prerequisites
-
The
AppStreamrepository is enabled.
Procedure
Install the
libreswanpackages:dnf install libreswan
# dnf install libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you are re-installing Libreswan, remove its old NSS database:
systemctl stop ipsec rm /var/lib/ipsec/nss/*db
# systemctl stop ipsec # rm /var/lib/ipsec/nss/*dbCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the
ipsecservice, and enable the service to be started automatically on boot:systemctl enable ipsec --now
# systemctl enable ipsec --nowCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the firewall to allow
500and4500UDP ports for the IKE, ESP, and AH protocols by adding theipsecservice:firewall-cmd --add-service="ipsec" firewall-cmd --runtime-to-permanent
# firewall-cmd --add-service="ipsec" # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow Switch the system to FIPS mode:
fips-mode-setup --enable
# fips-mode-setup --enableCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart your system to allow the kernel to switch to FIPS mode:
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm Libreswan is running in FIPS mode:
ipsec whack --fipsstatus
# ipsec whack --fipsstatus 000 FIPS mode enabledCopy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, check entries for the
ipsecunit in thesystemdjournal:journalctl -u ipsec
$ journalctl -u ipsec ... Jan 22 11:26:50 localhost.localdomain pluto[3076]: FIPS Mode: YESCopy to Clipboard Copied! Toggle word wrap Toggle overflow To see the available algorithms in FIPS mode:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To query disabled algorithms in FIPS mode:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To list all allowed algorithms and ciphers in FIPS mode:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.9. Protecting the IPsec NSS database by a password
By default, the IPsec service creates its Network Security Services (NSS) database with an empty password during the first start. To enhance security, you can add password protection.
Prerequisites
-
The
/var/lib/ipsec/nss/directory contains NSS database files.
Procedure
Enable password protection for the
NSSdatabase for Libreswan:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
/etc/ipsec.d/nsspasswordfile that contains the password you have set in the previous step, for example:cat /etc/ipsec.d/nsspassword NSS Certificate DB:_<password>_
# cat /etc/ipsec.d/nsspassword NSS Certificate DB:_<password>_Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
nsspasswordfile use the following syntax:<token_1>:<password1> <token_2>:<password2>
<token_1>:<password1> <token_2>:<password2>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The default NSS software token is
NSS Certificate DB. If your system is running in FIPS mode, the name of the token isNSS FIPS 140-2 Certificate DB.Depending on your scenario, either start or restart the
ipsecservice after you finish thensspasswordfile:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Check that the
ipsecservice is running after you have added a non-empty password to its NSS database:systemctl status ipsec
# systemctl status ipsec ● ipsec.service - Internet Key Exchange (IKE) Protocol Daemon for IPsec Loaded: loaded (/usr/lib/systemd/system/ipsec.service; enabled; vendor preset: disable> Active: active (running)...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check that the
Journallog contains entries that confirm a successful initialization:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.10. Configuring an IPsec VPN to use TCP
Libreswan supports TCP encapsulation of IKE and IPsec packets as described in RFC 8229. With this feature, you can establish IPsec VPNs on networks that prevent traffic transmitted via UDP and Encapsulating Security Payload (ESP). You can configure VPN servers and clients to use TCP either as a fallback or as the main VPN transport protocol. Because TCP encapsulation has bigger performance costs, use TCP as the main VPN protocol only if UDP is permanently blocked in your scenario.
Prerequisites
- A remote-access VPN is already configured.
Procedure
Add the following option to the
/etc/ipsec.conffile in theconfig setupsection:listen-tcp=yes
listen-tcp=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow To use TCP encapsulation as a fallback option when the first attempt over UDP fails, add the following two options to the client’s connection definition:
enable-tcp=fallback tcp-remoteport=4500
enable-tcp=fallback tcp-remoteport=4500Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, if you know that UDP is permanently blocked, use the following options in the client’s connection configuration:
enable-tcp=yes tcp-remoteport=4500
enable-tcp=yes tcp-remoteport=4500Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.11. Configuring automatic detection and usage of ESP hardware offload to accelerate an IPsec connection
Offloading Encapsulating Security Payload (ESP) to the hardware accelerates IPsec connections over Ethernet. By default, Libreswan detects if hardware supports this feature and, as a result, enables ESP hardware offload. In case that the feature was disabled or explicitly enabled, you can switch back to automatic detection.
Prerequisites
- The network card supports ESP hardware offload.
- The network driver supports ESP hardware offload.
- The IPsec connection is configured and works.
Procedure
-
Edit the Libreswan configuration file in the
/etc/ipsec.d/directory of the connection that should use automatic detection of ESP hardware offload support. -
Ensure the
nic-offloadparameter is not set in the connection’s settings. If you removed
nic-offload, restart theipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the
tx_ipsecandrx_ipseccounters of the Ethernet device the IPsec connection uses:ethtool -S enp1s0 | grep -E "_ipsec"
# ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 10 rx_ipsec: 10Copy to Clipboard Copied! Toggle word wrap Toggle overflow Send traffic through the IPsec tunnel. For example, ping a remote IP address:
ping -c 5 remote_ip_address
# ping -c 5 remote_ip_addressCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the
tx_ipsecandrx_ipseccounters of the Ethernet device again:ethtool -S enp1s0 | grep -E "_ipsec"
# ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 15 rx_ipsec: 15Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the counter values have increased, ESP hardware offload works.
6.12. Configuring ESP hardware offload on a bond to accelerate an IPsec connection
Offloading Encapsulating Security Payload (ESP) to the hardware accelerates IPsec connections. If you use a network bond for fail-over reasons, the requirements and the procedure to configure ESP hardware offload are different from those using a regular Ethernet device. For example, in this scenario, you enable the offload support on the bond, and the kernel applies the settings to the ports of the bond.
Prerequisites
-
All network cards in the bond support ESP hardware offload. Use the
ethtool -k <interface_name> | grep "esp-hw-offload"command to verify whether each bond port supports this feature. - The bond is configured and works.
-
The bond uses the
active-backupmode. The bonding driver does not support any other modes for this feature. - The IPsec connection is configured and works.
Procedure
Enable ESP hardware offload support on the network bond:
nmcli connection modify bond0 ethtool.feature-esp-hw-offload on
# nmcli connection modify bond0 ethtool.feature-esp-hw-offload onCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command enables ESP hardware offload support on the
bond0connection.Reactivate the
bond0connection:nmcli connection up bond0
# nmcli connection up bond0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the Libreswan configuration file in the
/etc/ipsec.d/directory of the connection that should use ESP hardware offload, and append thenic-offload=yesstatement to the connection entry:conn example ... nic-offload=yesconn example ... nic-offload=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
The verification methods depend on various aspects, such as the kernel version and driver. For example, certain drivers provide counters, but their names can vary. See the documentation of your network driver for details.
The following verification steps work for the ixgbe driver on Red Hat Enterprise Linux 9:
Display the active port of the bond:
grep "Currently Active Slave" /proc/net/bonding/bond0
# grep "Currently Active Slave" /proc/net/bonding/bond0 Currently Active Slave: enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the
tx_ipsecandrx_ipseccounters of the active port:ethtool -S enp1s0 | grep -E "_ipsec"
# ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 10 rx_ipsec: 10Copy to Clipboard Copied! Toggle word wrap Toggle overflow Send traffic through the IPsec tunnel. For example, ping a remote IP address:
ping -c 5 remote_ip_address
# ping -c 5 remote_ip_addressCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the
tx_ipsecandrx_ipseccounters of the active port again:ethtool -S enp1s0 | grep -E "_ipsec"
# ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 15 rx_ipsec: 15Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the counter values have increased, ESP hardware offload works.
6.13. Configuring IPsec VPN connections by using RHEL system roles
Configure IPsec VPN connections to establish encrypted tunnels over untrusted networks and ensure the integrity of data in transit. By using the RHEL system roles, you can automate the setup for use cases, such as connecting branch offices to headquarters.
The vpn RHEL system role can only create VPN configurations that use pre-shared keys (PSKs) or certificates to authenticate peers to each other.
6.13.1. Configuring an IPsec host-to-host VPN with PSK authentication by using the vpn RHEL system role
A host-to-host VPN establishes an encrypted connection between two devices, allowing applications to communicate safely over an insecure network. By using the vpn RHEL system role, you can automate the process of creating IPsec host-to-host connections.
For authentication, a pre-shared key (PSK) is a straightforward method that uses a single, shared secret known only to the two peers. This approach is simple to configure and ideal for basic setups where ease of deployment is a priority. However, you must keep the key strictly confidential. An attacker with access to the key can compromise the connection.
Prerequisites
- You have prepared the control node and the managed nodes.
- You are logged in to the control node as a user who can run playbooks on the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions on them.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
hosts: <list>Defines a YAML dictionary with the peers between which you want to configure a VPN. If an entry is not an Ansible managed node, you must specify its fully-qualified domain name (FQDN) or IP address in the
hostnameparameter, for example:... - hosts: ... external-host.example.com: hostname: 192.0.2.1... - hosts: ... external-host.example.com: hostname: 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow The role configures the VPN connection on each managed node. The connections are named
<peer_A>-to-<peer_B>, for example,managed-node-01.example.com-to-managed-node-02.example.com. Note that the role cannot configure Libreswan on external (unmanaged) nodes. You must manually create the configuration on these peers.auth_method: psk-
Enables PSK authentication between the peers. The role uses
opensslon the control node to create the PSK. auto: <startup_method>-
Specifies the startup method of the connection. Valid values are
add,ondemand,start, andignore. For details, see theipsec.conf(5)man page on a system with Libreswan installed. The default value of this variable is null, which means no automatic startup operation. vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm that the connections are successfully started, for example:
ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"'
# ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"' ... 006 #3: "managed-node-01.example.com-to-managed-node-02.example.com", type=ESP, add_time=1741857153, inBytes=38622, outBytes=324626, maxBytes=2^63B, id='@managed-node-02.example.com'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only succeeds if the VPN connection is active. If you set the
autovariable in the playbook to a value other thanstart, you might need to manually activate the connection on the managed nodes first.
6.13.2. Configuring an IPsec host-to-host VPN with PSK authentication and separate data and control planes by using the vpn RHEL system role
Use the vpn RHEL system role to automate the process of creating an IPsec host-to-host VPN. To enhance security by minimizing the risk of control messages being intercepted or disrupted, configure separate connections for both the data traffic and the control traffic.
A host-to-host VPN establishes a direct, secure, and encrypted connection between two devices, allowing applications to communicate safely over an insecure network, such as the internet.
For authentication, a pre-shared key (PSK) is a straightforward method that uses a single, shared secret known only to the two peers. This approach is simple to configure and ideal for basic setups where ease of deployment is a priority. However, you must keep the key strictly confidential. An attacker with access to the key can compromise the connection.
Prerequisites
- You have prepared the control node and the managed nodes.
- You are logged in to the control node as a user who can run playbooks on the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions on them.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
hosts: <list>Defines a YAML dictionary with the hosts between which you want to configure a VPN. The connections are named
<name>-<IP_address_A>-to-<IP_address_B>, for examplecontrol_plane_vpn-203.0.113.1-to-198.51.100.2.The role configures the VPN connection on each managed node. Note that the role cannot configure Libreswan on external (unmanaged) nodes. You must manually create the configuration on these hosts.
auth_method: psk-
Enables PSK authentication between the hosts. The role uses
opensslon the control node to create the pre-shared key. auto: <startup_method>-
Specifies the startup method of the connection. Valid values are
add,ondemand,start, andignore. For details, see theipsec.conf(5)man page on a system with Libreswan installed. The default value of this variable is null, which means no automatic startup operation. vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm that the connections are successfully started, for example:
ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "control_plane_vpn-203.0.113.1-to-198.51.100.2"'
# ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "control_plane_vpn-203.0.113.1-to-198.51.100.2"' ... 006 #3: "control_plane_vpn-203.0.113.1-to-198.51.100.2", type=ESP, add_time=1741860073, inBytes=0, outBytes=0, maxBytes=2^63B, id='198.51.100.2'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only succeeds if the VPN connection is active. If you set the
autovariable in the playbook to a value other thanstart, you might need to manually activate the connection on the managed nodes first.
6.13.3. Configuring an IPsec site-to-site VPN with PSK authentication by using the vpn RHEL system role
A site-to-site VPN establishes an encrypted tunnel between two distinct networks, seamlessly linking them across an insecure public network. By using the vpn RHEL system role, you can automate the process of creating IPsec site-to-site VPN connections.
A site-to-site VPN enables devices in a branch office to access resources at a corporate headquarters just as if they were all part of the same local network.
For authentication, a pre-shared key (PSK) is a straightforward method that uses a single, shared secret known only to the two peers. This approach is simple to configure and ideal for basic setups where ease of deployment is a priority. However, you must keep the key strictly confidential. An attacker with access to the key can compromise the connection.
Prerequisites
- You have prepared the control node and the managed nodes.
- You are logged in to the control node as a user who can run playbooks on the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions on them.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
hosts: <list>Defines a YAML dictionary with the gateways between which you want to configure a VPN. If an entry is not an Ansible-managed node, you must specify its fully-qualified domain name (FQDN) or IP address in the
hostnameparameter, for example:... - hosts: ... external-host.example.com: hostname: 192.0.2.1... - hosts: ... external-host.example.com: hostname: 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow The role configures the VPN connection on each managed node. The connections are named
<gateway_A>-to-<gateway_B>, for example,managed-node-01.example.com-to-managed-node-02.example.com. Note that the role cannot configure Libreswan on external (unmanaged) nodes. You must manually create the configuration on these peers.subnets: <yaml_list_of_subnets>- Defines subnets in classless inter-domain routing (CIDR) format that are connected through the tunnel.
auth_method: psk-
Enables PSK authentication between the peers. The role uses
opensslon the control node to create the PSK. auto: <startup_method>-
Specifies the startup method of the connection. Valid values are
add,ondemand,start, andignore. For details, see theipsec.conf(5)man page on a system with Libreswan installed. The default value of this variable is null, which means no automatic startup operation. vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm that the connections are successfully started, for example:
ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"'
# ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"' ... 006 #3: "managed-node-01.example.com-to-managed-node-02.example.com", type=ESP, add_time=1741857153, inBytes=38622, outBytes=324626, maxBytes=2^63B, id='@managed-node-02.example.com'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only succeeds if the VPN connection is active. If you set the
autovariable in the playbook to a value other thanstart, you might need to manually activate the connection on the managed nodes first.
6.13.4. Configuring an IPsec mesh VPN with certificate-based authentication by using the vpn RHEL system role
An IPsec mesh creates a fully interconnected network where every server can communicate securely and directly with every other server. By using the vpn RHEL system role, you can automate configuring a VPN mesh with certificate-based authentication among managed nodes.
An IPsec mesh is ideal for distributed database clusters or high-availability environments that span multiple data centers or cloud providers. Establishing a direct, encrypted tunnel between each pair of servers ensures secure communication without a central bottleneck.
For authentication, using digital certificates managed by a Certificate Authority (CA) offers a highly secure and scalable solution. Each host in the mesh presents a certificate signed by a trusted CA. This method provides strong, verifiable authentication and simplifies user management. Access can be granted or revoked centrally at the CA, and Libreswan enforces this by checking each certificate against a certificate revocation list (CRL), denying access if a certificate appears on the list.
Prerequisites
- You have prepared the control node and the managed nodes.
- You are logged in to the control node as a user who can run playbooks on the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions on them. You prepared a PKCS #12 file for each managed node:
Each file contains:
- The private key of the server
- The server certificate
- The CA certificate
- If required, intermediate certificates
-
The files are named
<managed_node_name_as_in_the_inventory>.p12. - The files are stored in the same directory as the playbook.
The server certificate contains the following fields:
-
Extended Key Usage (EKU) is set to
TLS Web Server Authentication. - Common Name (CN) or Subject Alternative Name (SAN) is set to the fully-qualified domain name (FQDN) of the host.
- X509v3 CRL distribution points contains URLs to Certificate Revocation Lists (CRLs).
-
Extended Key Usage (EKU) is set to
Procedure
Edit the
~/inventoryfile, and append thecert_namevariable:managed-node-01.example.com cert_name=managed-node-01.example.com managed-node-02.example.com cert_name=managed-node-02.example.com managed-node-03.example.com cert_name=managed-node-03.example.com
managed-node-01.example.com cert_name=managed-node-01.example.com managed-node-02.example.com cert_name=managed-node-02.example.com managed-node-03.example.com cert_name=managed-node-03.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
cert_namevariable to the value of the common name (CN) field used in the certificate for each host. Typically, the CN field is set to the fully-qualified domain name (FQDN).Store your sensitive variables in an encrypted file:
Create the vault:
ansible-vault create ~/vault.yml
$ ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
ansible-vault createcommand opens an editor, enter the sensitive data in the<key>: <value>format:pkcs12_pwd: <password>
pkcs12_pwd: <password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the changes, and close the editor. Ansible encrypts the data in the vault.
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
opportunistic: true-
Enables an opportunistic mesh among multiple hosts. The
policiesvariable defines for which subnets and hosts traffic must or can be encrypted and which of them should continue using plain text connections. auth_method: cert- Enables certificate-based authentication. This requires that you specify the nickname of each managed node’s certificate in the inventory.
policies: <list_of_policies>Defines the Libreswan policies in YAML list format.
The default policy is
private-or-clear. To change it toprivate, the above playbook contains an according policy for the defaultcidrentry.To prevent a loss of the SSH connection during the execution of the playbook if the Ansible control node is in the same IP subnet as the managed nodes, add a
clearpolicy for the control node’s IP address. For example, if the mesh should be configured for the192.0.2.0/24subnet and the control node uses the IP address192.0.2.1, you require aclearpolicy for192.0.2.1/32as shown in the playbook.For details about policies, see the
ipsec.conf(5)man page on a system with Libreswan installed.vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --ask-vault-pass --syntax-check ~/playbook.yml
$ ansible-playbook --ask-vault-pass --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook --ask-vault-pass ~/playbook.yml
$ ansible-playbook --ask-vault-pass ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
On a node in the mesh, ping another node to activate the connection:
ping managed-node-02.example.com
[root@managed-node-01]# ping managed-node-02.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the connection is active:
ipsec trafficstatus
[root@managed-node-01]# ipsec trafficstatus 006 #2: "private#192.0.2.0/24"[1] ...192.0.2.2, type=ESP, add_time=1741938929, inBytes=372408, outBytes=545728, maxBytes=2^63B, id='CN=managed-node-02.example.com'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.14. Configuring IPsec connections that opt out of the system-wide crypto policies
Overriding system-wide crypto-policies for a connection
The RHEL system-wide cryptographic policies create a special connection called %default. This connection contains the default values for the ikev2, esp, and ike options. However, you can override the default values by specifying the mentioned option in the connection configuration file.
For example, the following configuration allows connections that use IKEv1 with AES and SHA-1 or SHA-2, and IPsec (ESP) with either AES-GCM or AES-CBC:
Note that AES-GCM is available for IPsec (ESP) and for IKEv2, but not for IKEv1.
Disabling system-wide crypto policies for all connections
To disable system-wide crypto policies for all IPsec connections, comment out the following line in the /etc/ipsec.conf file:
include /etc/crypto-policies/back-ends/libreswan.config
include /etc/crypto-policies/back-ends/libreswan.config
Then add the ikev2=never option to your connection configuration file.
6.15. Troubleshooting IPsec configurations
Diagnosing IPsec configuration failures can be challenging, because issues can be caused by mismatched settings, firewall rules, and kernel-level errors. The following information provides a systematic approach to resolving common problems with IPsec VPN connections.
6.15.1. Basic connection issues
Problems with VPN connections often occur due to mismatched configurations between the endpoints.
To confirm that an IPsec connection is established, enter:
ipsec trafficstatus
# ipsec trafficstatus
006 #8: "vpn.example.com"[1] 192.0.2.1, type=ESP, add_time=1595296930, inBytes=5999, outBytes=3231, id='@vpn.example.com', lease=198.51.100.1/32For a successful connection, the command shows an entry with the connection’s name and details. If the output is empty, the tunnel is not established.
6.15.3. Mismatched Configurations
VPN connections fail if the endpoints are not configured with matching Internet Key Exchange (IKE) versions, algorithms, IP address ranges, or pre-shared keys (PSK). If you identify a mismatch, you must align the settings on both endpoints to resolve the issue.
- Remote Peer Not Running IKE/IPsec
If the connection was refused, an ICMP error is displayed:
ipsec up vpn.example.com
# ipsec up vpn.example.com ... 000 "vpn.example.com"[1] 192.0.2.2 #16: ERROR: asynchronous network error report on wlp2s0 (192.0.2.2:500), complainant 198.51.100.1: Connection refused [errno 111, origin ICMP type 3 code 3 (not authenticated)]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IKE Algorithms
The connection fails with a
NO_PROPOSAL_CHOSENnotification during the initial setup:ipsec up vpn.example.com
# ipsec up vpn.example.com ... 003 "vpn.example.com"[1] 193.110.157.148 #3: dropping unexpected IKE_SA_INIT message containing NO_PROPOSAL_CHOSEN notification; message payloads: N; missing payloads: SA,KE,NiCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IPsec Algorithms
The connection fails with a
NO_PROPOSAL_CHOSENerror after the initial exchange:ipsec up vpn.example.com
# ipsec up vpn.example.com ... 182 "vpn.example.com"[1] 193.110.157.148 #5: STATE_PARENT_I2: sent v2I2, expected v2R2 {auth=IKEv2 cipher=AES_GCM_16_256 integ=n/a prf=HMAC_SHA2_256 group=MODP2048} 002 "vpn.example.com"[1] 193.110.157.148 #6: IKE_AUTH response contained the error notification NO_PROPOSAL_CHOSENCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IP Address Ranges (IKEv2)
The remote peer responds with a
TS_UNACCEPTABLEerror:ipsec up vpn.example.com
# ipsec up vpn.example.com ... 1v2 "vpn.example.com" #1: STATE_PARENT_I2: sent v2I2, expected v2R2 {auth=IKEv2 cipher=AES_GCM_16_256 integ=n/a prf=HMAC_SHA2_512 group=MODP2048} 002 "vpn.example.com" #2: IKE_AUTH response contained the error notification TS_UNACCEPTABLECopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IP Address Ranges (IKEv1)
The connection times out during quick mode, with a message indicating the peer did not accept the proposal:
ipsec up vpn.example.com
# ipsec up vpn.example.com ... 031 "vpn.example.com" #2: STATE_QUICK_I1: 60 second timeout exceeded after 0 retransmits. No acceptable response to our first Quick Mode message: perhaps peer likes no proposalCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched PSK (IKEv2)
The peer rejects the connection with an
AUTHENTICATION_FAILEDerror:ipsec up vpn.example.com
# ipsec up vpn.example.com ... 003 "vpn.example.com" #1: received Hash Payload does not match computed value 223 "vpn.example.com" #1: sending notification INVALID_HASH_INFORMATION to 192.0.2.23:500Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched PSK (IKEv1)
The hash payload does not match, making the IKE message unreadable and resulting in an
INVALID_HASH_INFORMATIONerror:ipsec up vpn.example.com
# ipsec up vpn.example.com ... 002 "vpn.example.com" #1: IKE SA authentication request rejected by peer: AUTHENTICATION_FAILEDCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.15.4. MTU issues
Diagnose intermittent IPsec connection failures caused by Maximum Transmission Unit (MTU) issues. Encryption increases packet size, leading to fragmentation and lost data when packets exceed the network’s MTU, often seen with larger data transfers.
A common symptom is that small packets, for example pings, work correctly, but larger packets, such as an SSH session, freeze after the login. To fix the problem, lower the MTU for the tunnel by adding the mtu=1400 option to the configuration file.
6.15.5. NAT conflicts
Resolve NAT conflicts that occur when an IPsec host also acts as a NAT router. Incorrect NAT application can translate source IP addresses before encryption, causing packets to be sent unencrypted over the network.
For example, if the source IP address of the packet is translated by a masquerade rule before IPsec encryption is applied, the packet’s source no longer matches the IPsec policy, and Libreswan sends it unencrypted over the network.
To solve this problem, add a firewall rule that excludes traffic between the IPsec subnets from NAT. This rule should be inserted at the beginning of the POSTROUTING chain to ensure it is processed before the general NAT rule.
Example 6.1. Solution by using the nftables framework
The following example uses nftables to set up a basic NAT environment that excludes traffic between the 192.0.2.0/24 and 198.51.100.0/24 subnets from address translation:
nft add table ip nat
nft add chain ip nat postrouting { type nat hook postrouting priority 100 \; }
nft add rule ip nat postrouting ip saddr 192.0.2.0/24 ip daddr 198.51.100.0/24 return
# nft add table ip nat
# nft add chain ip nat postrouting { type nat hook postrouting priority 100 \; }
# nft add rule ip nat postrouting ip saddr 192.0.2.0/24 ip daddr 198.51.100.0/24 return6.15.6. Kernel-level IPsec issues
Troubleshoot kernel-level IPsec issues when a VPN tunnel appears established but no traffic flows. In this case, inspect the kernel’s IPsec state to check if the tunnel policies and cryptographic keys were correctly installed.
This process involves checking two components:
- The Security Policy Database (SPD): The rule that instructs the kernel what traffic to encrypt.
- The Security Association Database (SAD): The keys that instruct the kernel how to encrypt that traffic.
First, check if the correct policy exists in the SPD:
ip xfrm policy
# ip xfrm policy
src 192.0.2.1/32 dst 10.0.0.0/8
dir out priority 666 ptype main
tmpl src 198.51.100.13 dst 203.0.113.22
proto esp reqid 16417 mode tunnel
The output should contain the policies matching your leftsubnet and rightsubnet parameters with both in and out directions. If you do not see a policy for your traffic, Libreswan failed to create the kernel rule, and traffic is not encrypted.
If the policy exists, check if it has a corresponding set of keys in the SAD:
ip xfrm state
# ip xfrm state
src 203.0.113.22 dst 198.51.100.13
proto esp spi 0xa78b3fdb reqid 16417 mode tunnel
auth-trunc hmac(sha1) 0x3763cd3b... 96
enc cbc(aes) 0xd9dba399...This command displays private cryptographic keys. Do not share this output, because attackers can use it to decrypt your VPN traffic.
If a policy exists but you see no corresponding state with the same reqid, it typically means the Internet Key Exchange (IKE) negotiation failed. The two VPN endpoints could not agree on a set of keys.
For more detailed diagnostics, use the -s option with either of the commands. This option adds traffic counters, which can help you identify if the kernel processes packets by a specific rule.
6.15.7. Kernel IPsec subsystem bugs
Under rare conditions, a defect in the IPsec subsystem of the kernel can cause it to lose synchronization with the Internet Key Exchange (IKE) user-space daemon. This de-synchronization can result in discrepancies between negotiated security associations and the actual enforcement of IPsec policies within the kernel, potentially disrupting secure network communication. To check for kernel-level errors, display the transform (XFRM) statistics:
cat /proc/net/xfrm_stat
# cat /proc/net/xfrm_stat
If any of the counters in the output, such as XfrmInError, show a nonzero value, it indicates a problem with the kernel subsystem. In this case, open a support case, and attach the output of the command along with the corresponding IKE logs.
6.15.8. Displaying Libreswan logs
Display Libreswan logs to diagnose and troubleshoot IPsec service events and issues. Access the journal for the ipsec service to gain insights into connection status and potential problems.
To display the journal, enter:
journalctl -xeu ipsec
# journalctl -xeu ipsec
If the default logging level does not provide enough details, enable comprehensive debug logging by adding the following settings to the config setup section in the /etc/ipsec.conf file:
plutodebug=all logfile=/var/log/pluto.log
plutodebug=all
logfile=/var/log/pluto.log
Because debug logging can produce many entries, redirecting the messages to a dedicated log file can prevent the journald and systemd services from rate-limiting the messages.
6.16. Configuring a VPN connection with control-center
If you use Red Hat Enterprise Linux with a graphical interface, you can configure a VPN connection in the GNOME control-center.
Prerequisites
-
The
NetworkManager-libreswan-gnomepackage is installed.
Procedure
-
Press the Super key, type
Settings, and press Enter to open thecontrol-centerapplication. -
Select the
Networkentry on the left. - Click the + icon.
-
Select
VPN. Select the
Identitymenu entry to see the basic configuration options:General
Gateway- The name orIPaddress of the remote VPN gateway.Authentication
Type-
IKEv2 (Certificate)- client is authenticated by certificate. It is more secure (default). IKEv1 (XAUTH)- client is authenticated by user name and password, or a pre-shared key (PSK).The following configuration settings are available under the
Advancedsection:Figure 6.1. Advanced options of a VPN connection
WarningWhen configuring an IPsec-based VPN connection using the
gnome-control-centerapplication, theAdvanceddialog displays the configuration, but it does not allow any changes. As a consequence, users cannot change any advanced IPsec options. Use thenm-connection-editorornmclitools instead to perform configuration of the advanced properties.Identification
Domain- If required, enter the Domain Name.Security
-
Phase1 Algorithms- corresponds to theikeLibreswan parameter - enter the algorithms to be used to authenticate and set up an encrypted channel. Phase2 Algorithms- corresponds to theespLibreswan parameter - enter the algorithms to be used for theIPsecnegotiations.Check the
Disable PFSfield to turn off Perfect Forward Secrecy (PFS) to ensure compatibility with old servers that do not support PFS.-
Phase1 Lifetime- corresponds to theikelifetimeLibreswan parameter - how long the key used to encrypt the traffic will be valid. Phase2 Lifetime- corresponds to thesalifetimeLibreswan parameter - how long a particular instance of a connection should last before expiring.Note that the encryption key should be changed from time to time for security reasons.
Remote network- corresponds to therightsubnetLibreswan parameter - the destination private remote network that should be reached through the VPN.Check the
narrowingfield to enable narrowing. Note that it is only effective in IKEv2 negotiation.-
Enable fragmentation- corresponds to thefragmentationLibreswan parameter - whether or not to allow IKE fragmentation. Valid values areyes(default) orno. -
Enable Mobike- corresponds to themobikeLibreswan parameter - whether or not to allow Mobility and Multihoming Protocol (MOBIKE, RFC 4555) to enable a connection to migrate its endpoint without needing to restart the connection from scratch. This is used on mobile devices that switch between wired, wireless, or mobile data connections. The values areno(default) oryes.
-
Select the menu entry:
IPv4 Method
-
Automatic (DHCP)- Choose this option if the network you are connecting to uses aDHCPserver to assign dynamicIPaddresses. -
Link-Local Only- Choose this option if the network you are connecting to does not have aDHCPserver and you do not want to assignIPaddresses manually. Random addresses will be assigned as per RFC 3927 with prefix169.254/16. -
Manual- Choose this option if you want to assignIPaddresses manually. Disable-IPv4is disabled for this connection.DNS
In the
DNSsection, whenAutomaticisON, switch it toOFFto enter the IP address of a DNS server you want to use separating the IPs by comma.Routes
Note that in the
Routessection, whenAutomaticisON, routes from DHCP are used, but you can also add additional static routes. WhenOFF, only static routes are used.-
Address- Enter theIPaddress of a remote network or host. -
Netmask- The netmask or prefix length of theIPaddress entered above. -
Gateway- TheIPaddress of the gateway leading to the remote network or host entered above. Metric- A network cost, a preference value to give to this route. Lower values will be preferred over higher values.Use this connection only for resources on its network
Select this check box to prevent the connection from becoming the default route. Selecting this option means that only traffic specifically destined for routes learned automatically over the connection or entered here manually is routed over the connection.
-
To configure
IPv6settings in aVPNconnection, select the menu entry:IPv6 Method
-
Automatic- Choose this option to useIPv6Stateless Address AutoConfiguration (SLAAC) to create an automatic, stateless configuration based on the hardware address and Router Advertisements (RA). -
Automatic, DHCP only- Choose this option to not use RA, but request information fromDHCPv6directly to create a stateful configuration. -
Link-Local Only- Choose this option if the network you are connecting to does not have aDHCPserver and you do not want to assignIPaddresses manually. Random addresses will be assigned as per RFC 4862 with prefixFE80::0. -
Manual- Choose this option if you want to assignIPaddresses manually. Disable-IPv6is disabled for this connection.Note that
DNS,Routes,Use this connection only for resources on its networkare common toIPv4settings.
-
-
Once you have finished editing the
VPNconnection, click the button to customize the configuration or the button to save it for the existing one. -
Switch the profile to
ONto activate theVPNconnection. - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
6.17. Configuring a VPN connection using nm-connection-editor
If you use Red Hat Enterprise Linux with a graphical interface, you can configure a VPN connection in the nm-connection-editor application.
Prerequisites
-
The
NetworkManager-libreswan-gnomepackage is installed. If you configure an Internet Key Exchange version 2 (IKEv2) connection:
- The certificate is imported into the IPsec network security services (NSS) database.
- The nickname of the certificate in the NSS database is known.
Procedure
Open a terminal, and enter:
nm-connection-editor
$ nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Click the button to add a new connection.
-
Select the
IPsec based VPNconnection type, and click . On the
VPNtab:Enter the host name or IP address of the VPN gateway into the
Gatewayfield, and select an authentication type. Based on the authentication type, you must enter different additional information:-
IKEv2 (Certifiate)authenticates the client by using a certificate, which is more secure. This setting requires the nickname of the certificate in the IPsec NSS database IKEv1 (XAUTH)authenticates the user by using a user name and password (pre-shared key). This setting requires that you enter the following values:- User name
- Password
- Group name
- Secret
-
If the remote server specifies a local identifier for the IKE exchange, enter the exact string in the
Remote IDfield. In the remote server runs Libreswan, this value is set in the server’sleftidparameter.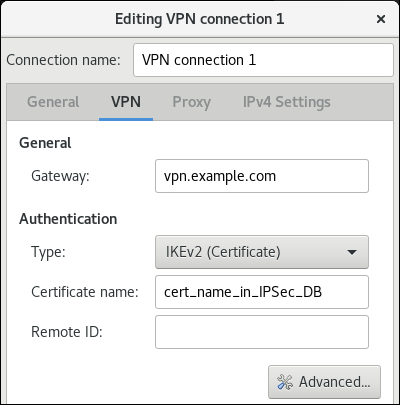
Optional: Configure additional settings by clicking the button. You can configure the following settings:
Identification
-
Domain- If required, enter the domain name.
-
Security
-
Phase1 Algorithmscorresponds to theikeLibreswan parameter. Enter the algorithms to be used to authenticate and set up an encrypted channel. Phase2 Algorithmscorresponds to theespLibreswan parameter. Enter the algorithms to be used for theIPsecnegotiations.Check the
Disable PFSfield to turn off Perfect Forward Secrecy (PFS) to ensure compatibility with old servers that do not support PFS.-
Phase1 Lifetimecorresponds to theikelifetimeLibreswan parameter. This parameter defines how long the key used to encrypt the traffic is valid. -
Phase2 Lifetimecorresponds to thesalifetimeLibreswan parameter. This parameter defines how long a security association is valid.
-
Connectivity
Remote networkcorresponds to therightsubnetLibreswan parameter and defines the destination private remote network that should be reached through the VPN.Check the
narrowingfield to enable narrowing. Note that it is only effective in the IKEv2 negotiation.-
Enable fragmentationcorresponds to thefragmentationLibreswan parameter and defines whether or not to allow IKE fragmentation. Valid values areyes(default) orno. -
Enable Mobikecorresponds to themobikeLibreswan parameter. The parameter defines whether or not to allow Mobility and Multihoming Protocol (MOBIKE) (RFC 4555) to enable a connection to migrate its endpoint without needing to restart the connection from scratch. This is used on mobile devices that switch between wired, wireless or mobile data connections. The values areno(default) oryes.
On the
IPv4 Settingstab, select the IP assignment method and, optionally, set additional static addresses, DNS servers, search domains, and routes.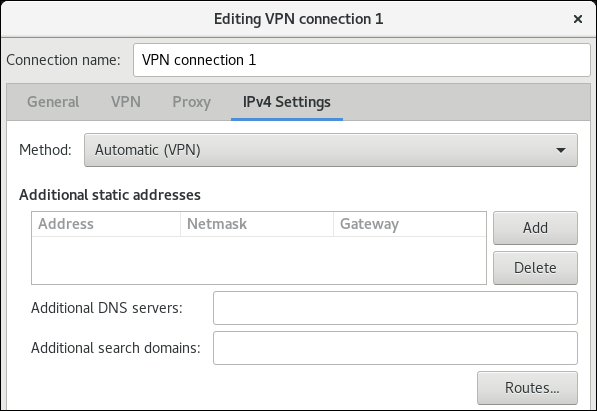
- Save the connection.
-
Close
nm-connection-editor. - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
When you add a new connection by clicking the button, NetworkManager creates a new configuration file for that connection and then opens the same dialog that is used for editing an existing connection. The difference between these dialogs is that an existing connection profile has a Details menu entry.
6.18. Configuring an IPsec based VPN connection by using nmstatectl
Configure IPsec VPN connections to establish encrypted tunnels over untrusted networks and ensure the integrity of data in transit. By using Nmstate, you can create IPsec VPN connections by using a declarative API.
You can use the nmstatectl utility to configure Libreswan IPsec VPN connections through the Nmstate API. The nmstatectl utility is a command-line tool to manage host networking through the declarative Nmstate API. Instead of running multiple imperative commands to configure an interface, you define the expected state in a YAML file. Nmstate then takes this definition and applies it to the system. A key advantage of this approach is an atomic result. Nmstate ensures that the resulting configuration precisely matches your YAML definition. If any part of the configuration fails to apply, it automatically rolls back all changes and prevents the system from entering an incorrect or broken network state.
Due to the design of the NetworkManager-libreswan plugin, you can use nmstatectl only on one peer and must manually configure Libreswan on the other peer.
6.18.1. Configuring an IPsec host-to-host VPN with raw RSA key authentication by using nmstatectl
You can use the declarative Nmstate API to configure a host-to-host VPN between two devices to communicate safely over an insecure network. Nmstate ensures that the result matches the configuration file or rolls back the changes.
For authentication, RSA keys are more secure than pre-shared keys (PSKs) because their asymmetric encryption eliminates the risk of a shared secret. Using RSA keys also simplifies deployment by avoiding the need for a certificate authority (CA), while still providing strong peer-to-peer authentication.
In general, the choice of which host is named left and right is arbitrary. However, NetworkManager always uses the term left for the local host and right for the remote host.
Prerequisites
The remote peer runs Libreswan IPsec and is prepared for a host-to-host connection.
Due to the design of the
NetworkManager-libreswanplugin, Nmstate cannot communicate with other peers that also use this plugin for the same connection.
Procedure
If Libreswan is not yet installed, perform the following steps:
Install the required packages:
dnf install nmstate libreswan NetworkManager-libreswan
# dnf install nmstate libreswan NetworkManager-libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the NetworkManager service:
systemctl restart NetworkManager
# systemctl restart NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Open the IPsec ports and protocols in the firewall:
firewall-cmd --permanent --add-service="ipsec" firewall-cmd --reload
# firewall-cmd --permanent --add-service="ipsec" # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an RSA key pair:
ipsec newhostkey
# ipsec newhostkeyCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
ipsecutility stores the key pair in the NSS database.Display the Certificate Key Attribute ID (CKAID) on both the left and right peers:
ipsec showhostkey --list
# ipsec showhostkey --list < 1> RSA keyid: <key_id> ckaid: <ckaid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the CKAIDs of both peers in the next steps.
Display the public keys:
On the left peer, enter:
ipsec showhostkey --left --ckaid <ckaid_of_left_peer>
# ipsec showhostkey --left --ckaid <ckaid_of_left_peer> # rsakey AwEAAdKCx leftrsasigkey=0sAwEAAdKCxpc9db48cehzQiQD...Copy to Clipboard Copied! Toggle word wrap Toggle overflow On the right peer, enter:
ipsec showhostkey --right --ckaid <ckaid_of_right_peer>
# ipsec showhostkey --right --ckaid <ckaid_of_right_peer> # rsakey AwEAAcNWC rightrsasigkey=0sAwEAAcNWCzZO+PR1j8WbO8X...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The commands display the public keys with the corresponding parameters that you must use in the configuration file.
Create a YAML file, for example
~/ipsec-host-to-host-rsa-auth.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example include the following:
ikev2: insist- Defines the modern IKEv2 protocol as the only allowed protocol without fallback to IKEv1. This setting is mandatory in a host-to-host configuration with Nmstate.
left=<ip_address_or_fqdn_of_left_peer>andright=<ip_address_or_fqdn_of_right_peer>- Defines the IP address or DNS name of the peers.
leftid=<id>andrightid=<id>-
Defines how each peer is identified during the Internet Key Exchange (IKE) negotiation process. This can be an IP address or a literal string. Note that NetworkManager interprets all values other than IP addresses as a literal string and internally adds a leading
@sign. This requires that the Libreswan peer also uses literal strings as IDs or authentication fails. leftrsasigkey=<public_key>andrightrsasigkey=<public_key>-
Specifies the public key of the peers. Use the values displayed by the
ipsec showhostkeycommand in a previous step. leftmodecfgclient: false- Disables dynamic configuration on this host. This setting is mandatory in a host-to-host configuration with Nmstate.
rightsubnet: <ip_address_of_right_peer>/32- Defines that the host can only access this peer. This setting is mandatory in a host-to-host configuration with Nmstate.
Apply the settings to the system:
nmstatectl apply ~/ipsec-host-to-host-rsa-auth.yml
# nmstatectl apply ~/ipsec-host-to-host-rsa-auth.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPsec status:
ipsec status
# ipsec statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the connection is successfully established, the output contains lines as follows:
Phase 1 of an Internet Key Exchange version 2 (IKEv2) negotiation has been successfully completed:
000 #1: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;
000 #1: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow The Security Association (SA) is now ready to negotiate the actual data encryption tunnels, known as child SAs or Phase 2 SAs.
A child SA has been established:
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #1; idle;
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #1; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow This is the actual tunnel that your data traffic flows through.
Troubleshooting
To display the actual configuration NetworkManager passes to Libreswan, enter:
nmcli connection export <connection_name>
# nmcli connection export <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output can help to identify deviating settings, such as IDs and keys, when you compare them with the Libreswan configuration on the remote host.
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
6.18.2. Configuring an IPsec site-to-site VPN with raw RSA key authentication by using nmstatectl
You can use the declarative Nmstate API to configure a site-to-site VPN between two distinct networks, seamlessly linking them across an insecure network. Nmstate ensures that the result matches the configuration file or rolls back the changes.
For authenticating the gateway devices, RSA keys are more secure than pre-shared keys (PSKs) because their asymmetric encryption eliminates the risk of a shared secret. Using RSA keys also simplifies deployment by avoiding the need for a certificate authority (CA), while still providing strong peer-to-peer authentication.
In general, the choice which host is named left and right is arbitrary. However, NetworkManager always uses the term left for the local host and right for the remote host.
Prerequisites
The remote gateway runs Libreswan IPsec and is prepared for a site-to-site connection.
Due to the design of the
NetworkManager-libreswanplugin, Nmstate cannot communicate with other peers that also use this plugin for the same connection.
Procedure
If Libreswan is not yet installed, perform the following steps:
Install the required packages:
dnf install nmstate libreswan NetworkManager-libreswan
# dnf install nmstate libreswan NetworkManager-libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the NetworkManager service:
systemctl restart NetworkManager
# systemctl restart NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Open the IPsec ports and protocols in the firewall:
firewall-cmd --permanent --add-service="ipsec" firewall-cmd --reload
# firewall-cmd --permanent --add-service="ipsec" # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an RSA key pair:
ipsec newhostkey
# ipsec newhostkeyCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
ipsecutility stores the key pair in the NSS database.Display the Certificate Key Attribute ID (CKAID) on both the left and right peer:
ipsec showhostkey --list
# ipsec showhostkey --list < 1> RSA keyid: <key_id> ckaid: <ckaid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the CKAIDs of both peers in the following steps.
Display the public keys:
On the left peer, enter:
ipsec showhostkey --left --ckaid <ckaid_of_left_peer>
# ipsec showhostkey --left --ckaid <ckaid_of_left_peer> # rsakey AwEAAdKCx leftrsasigkey=0sAwEAAdKCxpc9db48cehzQiQD...Copy to Clipboard Copied! Toggle word wrap Toggle overflow On the right peer, enter:
ipsec showhostkey --right --ckaid <ckaid_of_right_peer>
# ipsec showhostkey --right --ckaid <ckaid_of_right_peer> # rsakey AwEAAcNWC rightrsasigkey=0sAwEAAcNWCzZO+PR1j8WbO8X...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The commands display the public keys with the corresponding parameters that you must use in the configuration file.
Create a YAML file, for example
~/ipsec-site-to-site-rsa-auth.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example include the following:
ikev2: insist- Defines the modern IKEv2 protocol as the only allowed protocol without fallback to IKEv1. This setting is mandatory in a site-to-site configuration with Nmstate.
left=<ip_address_or_fqdn_of_left_peer>andright=<ip_address_or_fqdn_of_right_peer>- Defines the IP address or DNS name of the peers.
leftid=<id>andrightid=<id>-
Defines how each peer is identified during the Internet Key Exchange (IKE) negotiation process. This can be an IP address or a literal string. Note that NetworkManager interprets all values other than IP addresses as a literal string and internally adds a leading
@sign. This requires that the Libreswan peer also uses literal strings as IDs or authentication fails. leftrsasigkey=<public_key>andrightrsasigkey=<public_key>-
Specifies the public key of the peers. Use the values displayed by the
ipsec showhostkeycommand in a previous step. leftmodecfgclient: false- Disables dynamic configuration on this host. This setting is mandatory in a site-to-site configuration with Nmstate.
leftsubnet=<subnet>andrightsubnet=<subnet>- Defines subnets in classless inter-domain routing (CIDR) format that are connected through the tunnel.
Enable packet forwarding:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the settings to the system:
nmstatectl apply ~/ipsec-site-to-site-rsa-auth.yml
# nmstatectl apply ~/ipsec-site-to-site-rsa-auth.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPsec status:
ipsec status
# ipsec statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the connection is successfully established, the output contains lines as follows:
Phase 1 of an Internet Key Exchange version 2 (IKEv2) negotiation has been successfully completed:
000 #1: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;
000 #1: "<connection_name>":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); REKEY in 27935s; REPLACE in 28610s; newest; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow The Security Association (SA) is now ready to negotiate the actual data encryption tunnels, known as child SAs or Phase 2 SAs.
A child SA has been established:
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #1; idle;
000 #2: "<connection_name>":500 STATE_V2_ESTABLISHED_CHILD_SA (established Child SA); REKEY in 27671s; REPLACE in 28610s; IKE SA #1; idle;Copy to Clipboard Copied! Toggle word wrap Toggle overflow This is the actual tunnel that your data traffic flows through.
- From a client in the local subnet, ping a client in the remote subnet.
Troubleshooting
To display the actual configuration NetworkManager passes to Libreswan, enter:
nmcli connection export <connection_name>
# nmcli connection export <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output can help to identify deviating settings, such as IDs and keys, when you compare them with the Libreswan configuration on the remote host.
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
6.18.3. Configuring a client to connect to an IPsec VPN gateway by using nmstatectl
To access resources on a remote private network, users must first configure an IPsec VPN connection. By using Nmstate, you can create the connection with an existing Libreswan IPsec gateway by using a declarative API.
In general, the choice of which host is named left and right is arbitrary. However, NetworkManager always uses the term left for the local host and right for the remote host.
Prerequisites
The remote gateway runs Libreswan IPsec and is prepared for a host-to-site connection with certificate-based authentication.
Due to the design of the
NetworkManager-libreswanplugin, Nmstate cannot communicate with other peers that also use this plugin for the same connection.The PKCS#12 file
~/file.p12exists on the client with the following contents:- The private key of the user
- The user certificate
- The CA certificate
- If required, intermediate certificates
For details about creating a private key and certificate signing request (CSR), as well as about requesting a certificate from a CA, see your CA’s documentation.
-
The Extended Key Usage (EKU) in the certificate is set to
TLS Web Client Authentication.
Procedure
If Libreswan is not yet installed:
Install the required packages:
dnf install nmstate libreswan NetworkManager-libreswan
# dnf install nmstate libreswan NetworkManager-libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the NetworkManager service:
systemctl restart NetworkManager
# systemctl restart NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize the Network Security Services (NSS) database:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates the database in the
/var/lib/ipsec/nss/directory.Open the IPsec ports and protocols in the firewall:
firewall-cmd --permanent --add-service="ipsec" firewall-cmd --reload
# firewall-cmd --permanent --add-service="ipsec" # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Import the PKCS #12 file into the NSS database:
ipsec import ~/file.p12
# ipsec import ~/file.p12 Enter password for PKCS12 file: <password> pk12util: PKCS12 IMPORT SUCCESSFUL correcting trust bits for Example-CACopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the nicknames of the user and CA certificates:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require this information in the Nmstate YAML file.
Create a YAML file, for example,
~/ipsec-host-to-site-cert-auth.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example include the following:
ikev2: insist- Defines the modern IKEv2 protocol as the only allowed protocol without fallback to IKEv1. This setting is mandatory in a host-to-site configuration with Nmstate.
left=<ip_address_or_fqdn_of_left_peer>andright=<ip_address_or_fqdn_of_right_peer>- Defines the IP address or DNS name of the peers.
leftid=%fromcertandrightid=%fromcert- Configures Libreswan to retrieve the identity from the distinguished name (DN) field of the certificate.
leftcert="<server_certificate_nickname>"- Sets the nickname of the server’s certificate used in the NSS database.
rightsubnet: <subnet>- Defines the subnet in classless inter-domain routing (CIDR) format that is connected to the gateway.
Apply the settings to the system:
nmstatectl apply ~/ipsec-host-to-site-cert-auth.yml
# nmstatectl apply ~/ipsec-host-to-site-cert-auth.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
- Establish a connection to a host in the remote network or ping it.
Troubleshooting
To display the actual configuration NetworkManager passes to Libreswan, enter:
nmcli connection export <connection_name>
# nmcli connection export <connection_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output can help to identify deviating settings, such as IDs and keys, when you compare them with the Libreswan configuration on the remote host.
Next steps
- If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
6.19. Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel
To protect your VPN connection from traffic redirection attacks, assign it to a dedicated routing table. This prevents malicious network servers from bypassing the secure tunnel and compromising data integrity.
Both a DHCP server and Stateless Address Autoconfiguration (SLAAC) can add routes to a client’s routing table. For example, a malicious DHCP server can use this feature to force a host with VPN connection to redirect traffic through a physical interface instead of the VPN tunnel. This vulnerability is also known as TunnelVision and described in the CVE-2024-3661 vulnerability article.
To mitigate this vulnerability, you can assign the VPN connection to a dedicated routing table. This prevents the DHCP configuration or SLAAC from manipulating routing decisions for network packets intended for the VPN tunnel.
Follow the steps if at least one of the conditions applies to your environment:
- At least one network interface uses DHCP or SLAAC.
- Your network does not use mechanisms, such as DHCP snooping, that prevent a rogue DHCP server.
Routing the entire traffic through the VPN prevents the host from accessing local network resources.
Prerequisites
- You use NetworkManager 1.48.10-5 or later.
Procedure
- Decide which routing table you want to use. The following steps use table 75. By default, RHEL does not use the tables 1-254, and you can use any of them.
Configure the VPN connection profile to place the VPN routes in a dedicated routing table:
nmcli connection modify <vpn_connection_profile> ipv4.route-table 75 ipv6.route-table 75
# nmcli connection modify <vpn_connection_profile> ipv4.route-table 75 ipv6.route-table 75Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set a low priority value for the table you used in the previous command:
nmcli connection modify <vpn_connection_profile> ipv4.routing-rules "priority 32345 from all table 75" ipv6.routing-rules "priority 32345 from all table 75"
# nmcli connection modify <vpn_connection_profile> ipv4.routing-rules "priority 32345 from all table 75" ipv6.routing-rules "priority 32345 from all table 75"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The priority value can be any value between 1 and 32766. The lower the value, the higher the priority.
Reconnect the VPN connection:
nmcli connection down <vpn_connection_profile> nmcli connection up <vpn_connection_profile>
# nmcli connection down <vpn_connection_profile> # nmcli connection up <vpn_connection_profile>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 routes in table 75:
ip route show table 75
# ip route show table 75 ... 192.0.2.0/24 via 192.0.2.254 dev vpn_device proto static metric 50 default dev vpn_device proto static scope link metric 50Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that both the route to the remote network and the default gateway are assigned to routing table 75 and, therefore, all traffic is routed through the tunnel. If you set
ipv4.never-default truein the VPN connection profile, a default route is not created and, therefore, not visible in this output.Display the IPv6 routes in table 75:
ip -6 route show table 75
# ip -6 route show table 75 ... 2001:db8:1::/64 dev vpn_device proto kernel metric 50 pref medium default dev vpn_device proto static metric 50 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that both the route to the remote network and the default gateway are assigned to routing table 75 and, therefore, all traffic is routed through the tunnel. If you set
ipv6.never-default truein the VPN connection profile, a default route is not created and, therefore, not visible in this output.
