Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 3. Reports by CVEs
You can create PDF reports showing a filtered list of CVEs your systems are exposed to. Give each report a relevant name, apply filters, and add user notes to present focused data to specific stakeholders.
You can apply the following filters when setting up the PDF report:
- Security rules. Show only CVEs with the security rules label.
- Known exploit. Show only CVEs with the Known exploit label.
- Severity. Select one or more values: Critical, Important, Moderate, Low, or Unknown.
- CVSS base score. Select one or more ranges: All, 0.0-3.9, 4.0-7.9, 8.0-10.0, N/A (not applicable)
- Business risk. Select one or more values: High, Medium, Low, Not defined.
- Status. Select one or more values: Not reviewed, In review, On-hold, Scheduled for patch, Resolved, No action - risk accepted, Resolved via mitigation.
- Publish date. Select from All, Last 7 days, Last 30 days, Last 90 days, Last year, or More than 1 year ago.
- Applies to OS. Select the RHEL minor version(s) of systems to filter and view.
- Tags. Select groups of tagged systems.
For more information about tags and system groups, see System tags and groups
- Advisory. Select whether to display only CVEs that have associated advisories (errata), only CVEs without advisories, or all CVEs.
The CVE report lists the CVEs, linking each to the respective CVE page in the Red Hat CVE database so you can learn more about it. The list is ordered primarily by the publish date of the CVE, with the most recently published CVEs at the top of the list.
Example of an Insights Vulnerability CVE report

3.1. Creating a PDF report of CVEs
Use the following procedure to create a point-in-time snapshot of CVEs that potentially affect your systems.
Prerequisites
- You must be logged in to Red Hat Hybrid Cloud Console.
Procedure
- Navigate to the Security > Vulnerability > Reports page in the Insights for Red Hat Enterprise Linux application.
- On the Report by CVEs card, click Create report.
Make selections as needed in the pop-up card:
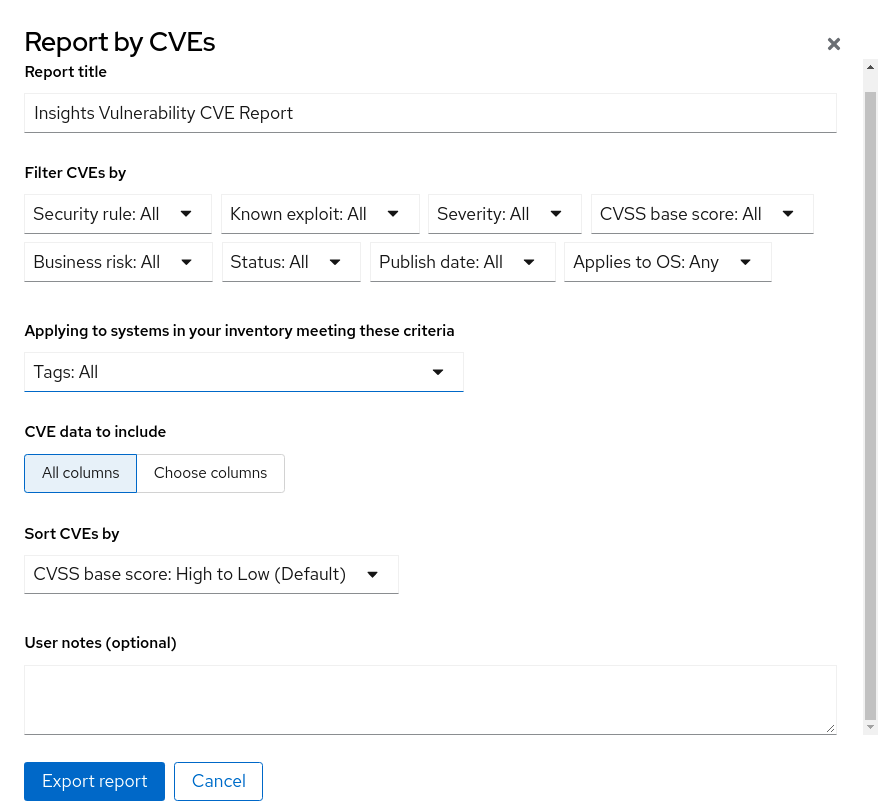
- Optionally, customize the report title.
- Under Filter CVEs by, click each filter dropdown and select a value.
- Select Tags to only include systems in a tagged group of systems.
- Under CVE data to include, Choose columns is activate by default, allowing you to deselect columns you do not want to include. Leave all boxes checked, or click All columns to show everything.
- Optionally, add notes to give the report context for the intended audience.
- Click Export report and allow the application a minute to generate the report.
- Select to open or save the PDF file, if your OS asks, and click OK.