Chapter 12. Configuring Policy-based Routing to Define Alternative Routes
By default, the kernel in RHEL decides where to forward network packets based on the destination address using a routing table. Policy-based routing enables you to configure complex routing scenarios. For example, you can route packets based on various criteria, such as the source address, packet metadata, or protocol.
This section describes of how to configure policy-based routing using NetworkManager.
Note
On systems that use NetworkManager, only the
nmcli utility supports setting routing rules and assigning routes to specific tables.
12.1. Routing Traffic from a Specific Subnet to a Different Default Gateway
Copy linkLink copied to clipboard!
This section describes how to configure RHEL as a router that, by default, routes all traffic to internet provider A using the default route. Using policy-based routing, RHEL routes traffic received from the internal workstations subnet to provider B.
The procedure assumes the following network topology:
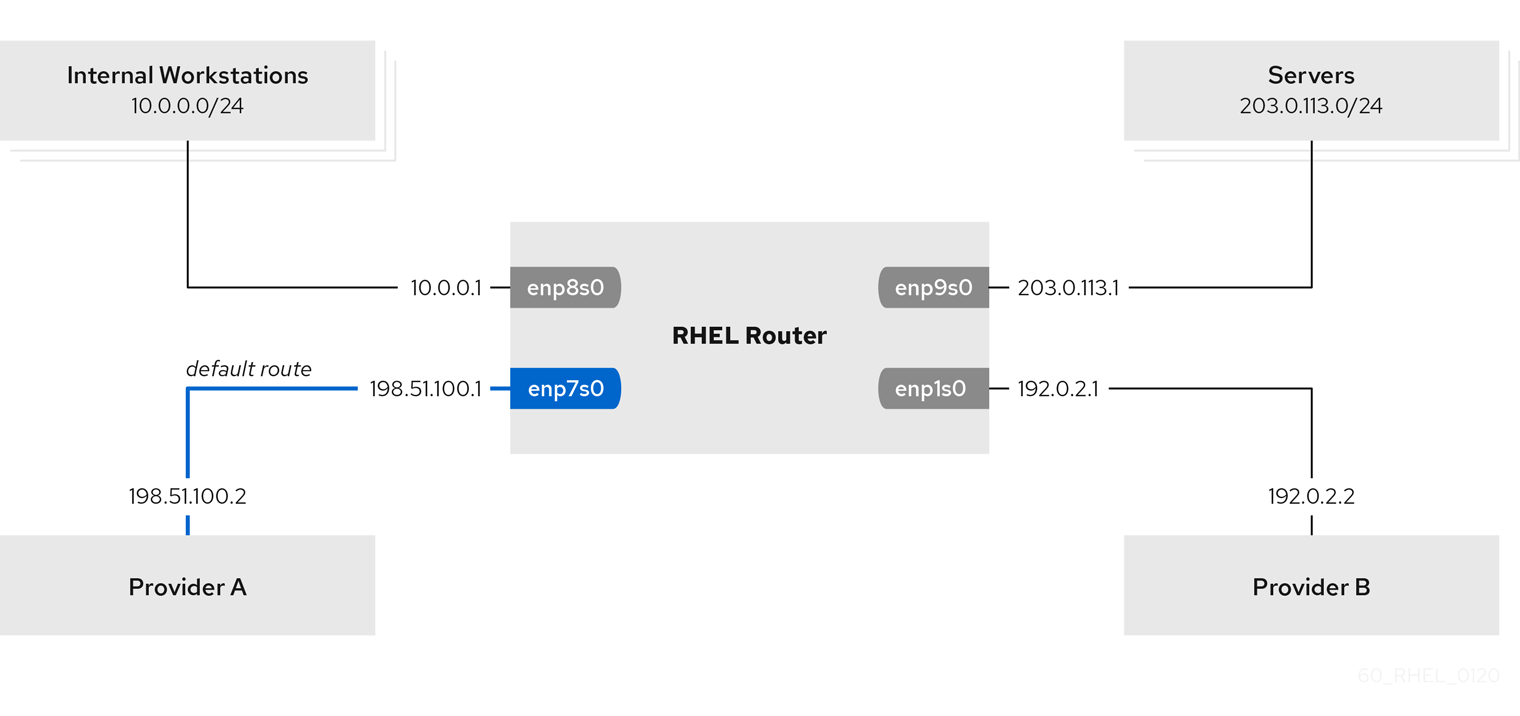
Figure 12.1. Activate a Connection
Prerequisites
- The RHEL router you want to set up in the procedure has four network interfaces:
- The
enp7s0interface is connected to the network of provider A. The gateway IP in the provider’s network is198.51.100.2, and the network uses a/30network mask. - The
enp1s0interface is connected to the network of provider B. The gateway IP in the provider’s network is192.0.2.2, and the network uses a/30network mask. - The
enp8s0interface is connected to the10.0.0.0/24subnet with internal workstations. - The
enp9s0interface is connected to the203.0.113.0/24subnet with the company’s servers.
- Hosts in the internal workstations subnet use
10.0.0.1as default gateway. In the procedure, you assign this IP address to theenp8s0network interface of the router. - Hosts in the server subnet use
203.0.113.1as default gateway. In the procedure, you assign this IP address to theenp9s0network interface of the router. - The
firewalldservice is enabled and active, which is the default.
Procedure
- Configure the network interface to provider A:
nmcli connection add type ethernet con-name Provider-A ifname enp7s0 ipv4.method manual ipv4.addresses 198.51.100.1/30 ipv4.gateway 198.51.100.2 ipv4.dns 198.51.100.200 connection.zone external
# nmcli connection add type ethernet con-name Provider-A ifname enp7s0 ipv4.method manual ipv4.addresses 198.51.100.1/30 ipv4.gateway 198.51.100.2 ipv4.dns 198.51.100.200 connection.zone externalCopy to Clipboard Copied! Toggle word wrap Toggle overflow Thenmcli connection addcommand creates a NetworkManager connection profile. The following list describes the options of the command:type ethernet: Defines that the connection type is Ethernet.con-name connection_name: Sets the name of the profile. Use a meaningful name to avoid confusion.ifname network_device: Sets the network interface.ipv4.method manual: Enables to configure a static IP address.ipv4.addresses IP_address/subnet_mask: Sets the IPv4 addresses and subnet mask.ipv4.gateway IP_address: Sets the default gateway address.ipv4.dns IP_of_DNS_server: Sets the IPv4 address of the DNS server.connection.zone firewalld_zone: Assigns the network interface to the definedfirewalldzone. Note thatfirewalldautomatically enables masquerading interfaces assigned to theexternalzone.
- Configure the network interface to provider B:
nmcli connection add type ethernet con-name Provider-B ifname enp1s0 ipv4.method manual ipv4.addresses 192.0.2.1/30 ipv4.routes "0.0.0.0/1 192.0.2.2 table=5000, 128.0.0.0/1 192.0.2.2 table=5000" connection.zone external
# nmcli connection add type ethernet con-name Provider-B ifname enp1s0 ipv4.method manual ipv4.addresses 192.0.2.1/30 ipv4.routes "0.0.0.0/1 192.0.2.2 table=5000, 128.0.0.0/1 192.0.2.2 table=5000" connection.zone externalCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command uses theipv4.routesparameter instead ofipv4.gatewayto set the default gateway. This is required to assign the default gateway for this connection to a different routing table (5000) than the default. NetworkManager automatically creates this new routing table when the connection is activated.Note
Thenmcliutility does not support using0.0.0.0/0for the default gateway inipv4.gateway. To work around this problem, the command creates separate routes for both the0.0.0.0/1and128.0.0.0/1subnets, which covers also the full IPv4 address space. - Configure the network interface to the internal workstations subnet:
nmcli connection add type ethernet con-name Internal-Workstations ifname enp8s0 ipv4.method manual ipv4.addresses 10.0.0.1/24 ipv4.routes "10.0.0.0/24 src=192.0.2.1 table=5000" ipv4.routing-rules "priority 5 from 10.0.0.0/24 table 5000" connection.zone trusted
# nmcli connection add type ethernet con-name Internal-Workstations ifname enp8s0 ipv4.method manual ipv4.addresses 10.0.0.1/24 ipv4.routes "10.0.0.0/24 src=192.0.2.1 table=5000" ipv4.routing-rules "priority 5 from 10.0.0.0/24 table 5000" connection.zone trustedCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command uses theipv4.routesparameter to add a static route to the routing table with ID5000. This static route for the10.0.0.0/24subnet uses the IP of the local network interface to provider B (192.0.2.1) as next hop.Additionally, the command uses theipv4.routing-rulesparameter to add a routing rule with priority5that routes traffic from the10.0.0.0/24subnet to table5000. Low values have a high priority.Note that the syntax in theipv4.routing-rulesparameter is the same as in anip route addcommand, except thatipv4.routing-rulesalways requires specifying a priority. - Configure the network interface to the server subnet:
nmcli connection add type ethernet con-name Servers ifname enp9s0 ipv4.method manual ipv4.addresses 203.0.113.1/24 connection.zone trusted
# nmcli connection add type ethernet con-name Servers ifname enp9s0 ipv4.method manual ipv4.addresses 203.0.113.1/24 connection.zone trustedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification Steps
- On a RHEL host in the internal workstation subnet:
- Install the traceroute package:
yum install traceroute
# yum install tracerouteCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
tracerouteutility to display the route to a host on the internet:traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 10.0.0.1 (10.0.0.1) 0.337 ms 0.260 ms 0.223 ms 2 192.0.2.1 (192.0.2.1) 0.884 ms 1.066 ms 1.248 ms ...
# traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 10.0.0.1 (10.0.0.1) 0.337 ms 0.260 ms 0.223 ms 2 192.0.2.1 (192.0.2.1) 0.884 ms 1.066 ms 1.248 ms ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output of the command displays that the router sends packets over192.0.2.1, which is the network of provider B.
- On a RHEL host in the server subnet:
- Install the traceroute package:
yum install traceroute
# yum install tracerouteCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
tracerouteutility to display the route to a host on the internet:traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 203.0.113.1 (203.0.113.1) 2.179 ms 2.073 ms 1.944 ms 2 198.51.100.2 (198.51.100.2) 1.868 ms 1.798 ms 1.549 ms ...
# traceroute redhat.com traceroute to redhat.com (209.132.183.105), 30 hops max, 60 byte packets 1 203.0.113.1 (203.0.113.1) 2.179 ms 2.073 ms 1.944 ms 2 198.51.100.2 (198.51.100.2) 1.868 ms 1.798 ms 1.549 ms ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output of the command displays that the router sends packets over198.51.100.2, which is the network of provider A.
Troubleshooting Steps
On the RHEL router:
- Display the rule list:
ip rule list 0: from all lookup local 5: from 10.0.0.0/24 lookup 5000 32766: from all lookup main 32767: from all lookup default
# ip rule list 0: from all lookup local 5: from 10.0.0.0/24 lookup 5000 32766: from all lookup main 32767: from all lookup defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Display the routes in table
5000:ip route list table 5000 0.0.0.0/1 via 192.0.2.2 dev enp1s0 proto static metric 100 10.0.0.0/24 dev enp8s0 proto static scope link src 192.0.2.1 metric 102 128.0.0.0/1 via 192.0.2.2 dev enp1s0 proto static metric 100
# ip route list table 5000 0.0.0.0/1 via 192.0.2.2 dev enp1s0 proto static metric 100 10.0.0.0/24 dev enp8s0 proto static scope link src 192.0.2.1 metric 102 128.0.0.0/1 via 192.0.2.2 dev enp1s0 proto static metric 100Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Display which interfaces are assigned to which firewall zones:
firewall-cmd --get-active-zones external interfaces: enp1s0 enp7s0 trusted interfaces: enp8s0 enp9s0
# firewall-cmd --get-active-zones external interfaces: enp1s0 enp7s0 trusted interfaces: enp8s0 enp9s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Verify that the
externalzone has masquerading enabled:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Additional Resources
- For further details about the
ipv4.*parameters you can set in thenmcli connection addcommand, see the IPv4 settings section in the nm-settings(5) man page. - For further details about the
connection.*parameters you can set in thenmcli connection addcommand, see the Connection settings section in the nm-settings(5) man page. - For further details about managing NetworkManager connections using
nmcli, see the Connection management commands section in the nmcli(1) man page.