CLI tools
Learning how to use the command-line tools for OpenShift Container Platform
Abstract
Chapter 1. OpenShift Container Platform CLI tools overview
A user performs a range of operations while working on OpenShift Container Platform such as the following:
- Managing clusters
- Building, deploying, and managing applications
- Managing deployment processes
- Developing Operators
- Creating and maintaining Operator catalogs
OpenShift Container Platform offers a set of command-line interface (CLI) tools that simplify these tasks by enabling users to perform various administration and development operations from the terminal. These tools expose simple commands to manage the applications, as well as interact with each component of the system.
1.1. List of CLI tools
The following set of CLI tools are available in OpenShift Container Platform:
-
OpenShift CLI (
oc): This is the most commonly used CLI tool by OpenShift Container Platform users. It helps both cluster administrators and developers to perform end-to-end operations across OpenShift Container Platform using the terminal. Unlike the web console, it allows the user to work directly with the project source code using command scripts. -
Knative CLI (kn): The Knative (
kn) CLI tool provides simple and intuitive terminal commands that can be used to interact with OpenShift Serverless components, such as Knative Serving and Eventing. -
Pipelines CLI (tkn): OpenShift Pipelines is a continuous integration and continuous delivery (CI/CD) solution in OpenShift Container Platform, which internally uses Tekton. The
tknCLI tool provides simple and intuitive commands to interact with OpenShift Pipelines using the terminal. -
opm CLI: The
opmCLI tool helps the Operator developers and cluster administrators to create and maintain the catalogs of Operators from the terminal. - Operator SDK: The Operator SDK, a component of the Operator Framework, provides a CLI tool that Operator developers can use to build, test, and deploy an Operator from the terminal. It simplifies the process of building Kubernetes-native applications, which can require deep, application-specific operational knowledge.
Chapter 2. OpenShift CLI (oc)
2.1. Getting started with the OpenShift CLI
2.1.1. About the OpenShift CLI
With the OpenShift CLI (oc), you can create applications and manage OpenShift Container Platform projects from a terminal. The OpenShift CLI is ideal in the following situations:
- Working directly with project source code
- Scripting OpenShift Container Platform operations
- Managing projects while restricted by bandwidth resources and the web console is unavailable
2.1.2. Installing the OpenShift CLI
You can install the OpenShift CLI (oc) either by downloading the binary or by using an RPM.
2.1.3. Installing the OpenShift CLI on Linux
To manage your cluster and deploy applications from the command line, install the OpenShift CLI (oc) binary on Linux.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.18. Download and install the new version of oc.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the architecture from the Product Variant drop-down list.
- Select the appropriate version from the Version drop-down list.
- Click Download Now next to the OpenShift v4.18 Linux Clients entry and save the file.
Unpack the archive:
tar xvf <file>
$ tar xvf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
After you install the OpenShift CLI, it is available using the
occommand:oc <command>
$ oc <command>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.1.4. Installing the OpenShift CLI on Windows
To manage your cluster and deploy applications from the command line, install OpenShift CLI (oc) binary on Windows.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform.
Download and install the new version of oc.
Procedure
- Navigate to the Download OpenShift Container Platform page on the Red Hat Customer Portal.
- Select the appropriate version from the Version list.
- Click Download Now next to the OpenShift v4.18 Windows Client entry and save the file.
- Extract the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATHvariable.To check your
PATHvariable, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
After you install the OpenShift CLI, it is available using the
occommand:oc <command>
C:\> oc <command>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.1.5. Installing the OpenShift CLI on macOS
To manage your cluster and deploy applications from the command line, install the OpenShift CLI (oc) binary on macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform.
Download and install the new version of oc.
Procedure
- Navigate to the Download OpenShift Container Platform page on the Red Hat Customer Portal.
- Select the architecture from the Product Variant list.
- Select the appropriate version from the Version list.
Click Download Now next to the OpenShift v4.18 macOS Clients entry and save the file.
NoteFor macOS arm64, choose the OpenShift v4.18 macOS arm64 Client entry.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on yourPATHvariable.To check your
PATHvariable, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify your installation by using an
occommand:oc <command>
$ oc <command>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.1.5.1. Installing the OpenShift CLI by using the web console
You can install the OpenShift CLI (oc) to interact with OpenShift Container Platform from a web console. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.18. Download and install the new version of oc.
2.1.5.1.1. Installing the OpenShift CLI on Linux using the web console
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
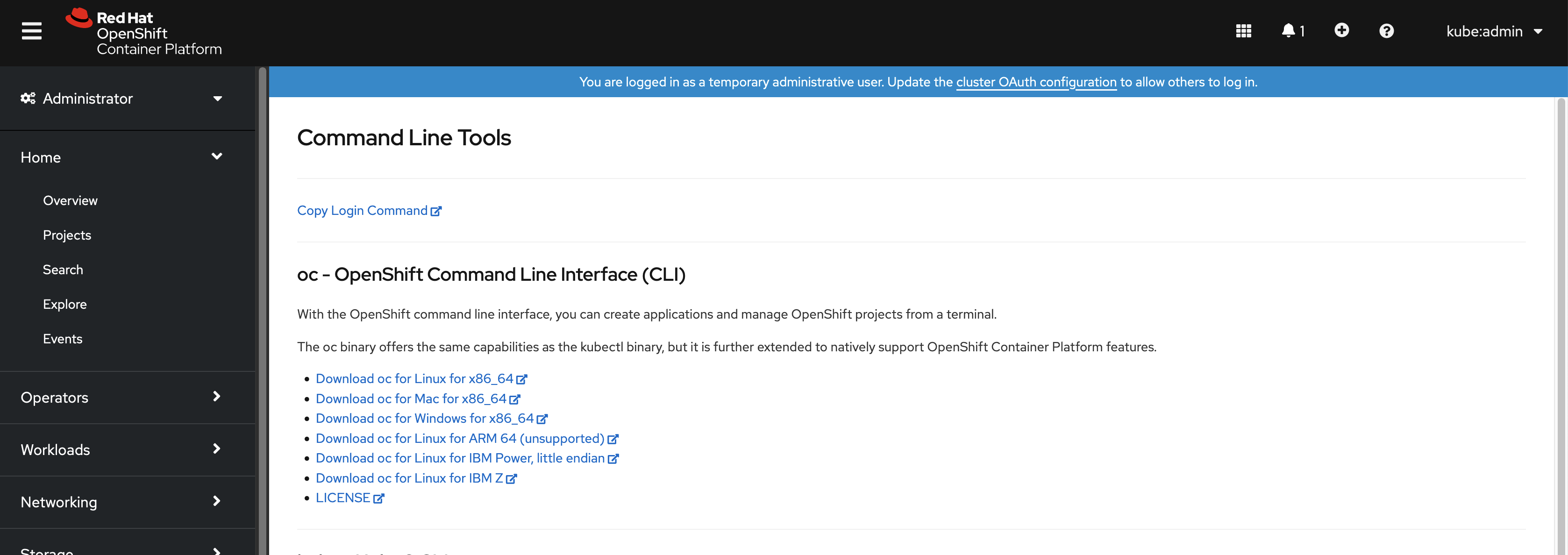
From the web console, click ?.
Click Command Line Tools.
-
Select appropriate
ocbinary for your Linux platform, and then click Download oc for Linux. - Save the file.
Unpack the archive.
tar xvf <file>
$ tar xvf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.1.5.1.2. Installing the OpenShift CLI on Windows using the web console
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
From the web console, click ?.
Click Command Line Tools.
-
Select the
ocbinary for Windows platform, and then click Download oc for Windows for x86_64. - Save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>2.1.5.1.3. Installing the OpenShift CLI on macOS using the web console
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
From the web console, click ?.
Click Command Line Tools.
Select the
ocbinary for macOS platform, and then click Download oc for Mac for x86_64.NoteFor macOS arm64, click Download oc for Mac for ARM 64.
- Save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.1.5.2. Installing the OpenShift CLI by using an RPM
For Red Hat Enterprise Linux (RHEL), you can install the OpenShift CLI (oc) as an RPM if you have an active OpenShift Container Platform subscription on your Red Hat account.
You must install oc for RHEL 9 by downloading the binary. Installing oc by using an RPM package is not supported on Red Hat Enterprise Linux (RHEL) 9.
Prerequisites
- You must have root or sudo privileges.
Procedure
Register with Red Hat Subscription Manager:
subscription-manager register
# subscription-manager registerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Pull the latest subscription data:
subscription-manager refresh
# subscription-manager refreshCopy to Clipboard Copied! Toggle word wrap Toggle overflow List the available subscriptions:
subscription-manager list --available --matches '*OpenShift*'
# subscription-manager list --available --matches '*OpenShift*'Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the output for the previous command, find the pool ID for an OpenShift Container Platform subscription and attach the subscription to the registered system:
subscription-manager attach --pool=<pool_id>
# subscription-manager attach --pool=<pool_id>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the repositories required by OpenShift Container Platform 4.18.
subscription-manager repos --enable="rhocp-4.18-for-rhel-8-x86_64-rpms"
# subscription-manager repos --enable="rhocp-4.18-for-rhel-8-x86_64-rpms"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Install the
openshift-clientspackage:yum install openshift-clients
# yum install openshift-clientsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify your installation by using an
occommand:oc <command>
$ oc <command>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.1.5.3. Installing the OpenShift CLI by using Homebrew
For macOS, you can install the OpenShift CLI (oc) by using the Homebrew package manager.
Prerequisites
-
You must have Homebrew (
brew) installed.
Procedure
Install the openshift-cli package by running the following command:
brew install openshift-cli
$ brew install openshift-cliCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
-
Verify your installation by using an
occommand:
oc <command>
$ oc <command>2.1.6. Logging in to the OpenShift CLI
You can log in to the OpenShift CLI (oc) to access and manage your cluster.
Prerequisites
- You must have access to an OpenShift Container Platform cluster.
-
The OpenShift CLI (
oc) is installed.
To access a cluster that is accessible only over an HTTP proxy server, you can set the HTTP_PROXY, HTTPS_PROXY and NO_PROXY variables. These environment variables are respected by the oc CLI so that all communication with the cluster goes through the HTTP proxy.
Authentication headers are sent only when using HTTPS transport.
Procedure
Enter the
oc logincommand and pass in a user name:oc login -u user1
$ oc login -u user1Copy to Clipboard Copied! Toggle word wrap Toggle overflow When prompted, enter the required information:
Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
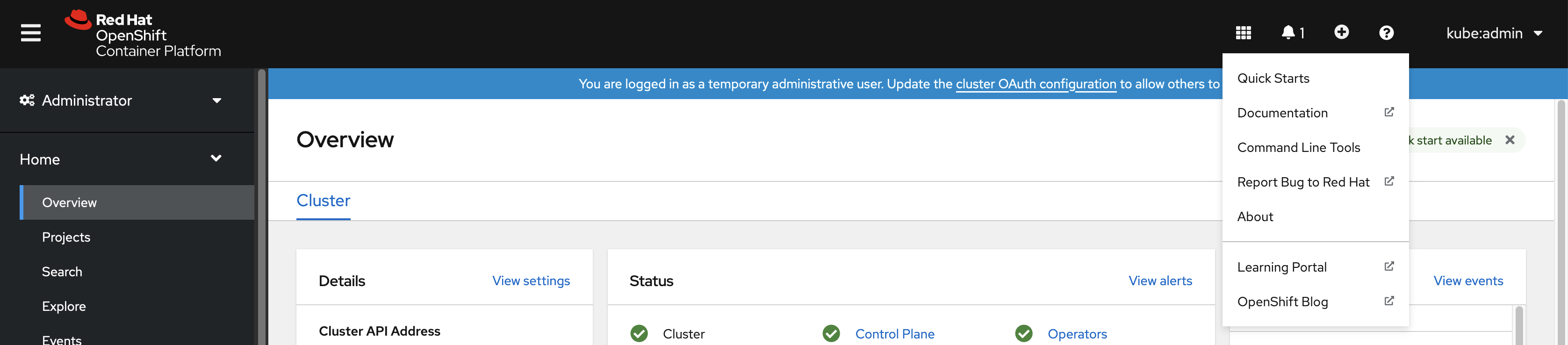
If you are logged in to the web console, you can generate an oc login command that includes your token and server information. You can use the command to log in to the OpenShift Container Platform CLI without the interactive prompts. To generate the command, select Copy login command from the username drop-down menu at the top right of the web console.
You can now create a project or issue other commands for managing your cluster.
2.1.7. Logging in to the OpenShift CLI using a web browser
You can log in to the OpenShift CLI (oc) with the help of a web browser to access and manage your cluster. This allows users to avoid inserting their access token into the command line.
Logging in to the CLI through the web browser runs a server on localhost with HTTP, not HTTPS; use with caution on multi-user workstations.
Prerequisites
- You must have access to an OpenShift Container Platform cluster.
-
You must have installed the OpenShift CLI (
oc). - You must have a browser installed.
Procedure
Enter the
oc logincommand with the--webflag:oc login <cluster_url> --web
$ oc login <cluster_url> --web1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Optionally, you can specify the server URL and callback port. For example,
oc login <cluster_url> --web --callback-port 8280 localhost:8443.
The web browser opens automatically. If it does not, click the link in the command output. If you do not specify the OpenShift Container Platform server
octries to open the web console of the cluster specified in the currentocconfiguration file. If noocconfiguration exists,ocprompts interactively for the server URL.Example output
Opening login URL in the default browser: https://openshift.example.com Opening in existing browser session.
Opening login URL in the default browser: https://openshift.example.com Opening in existing browser session.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If more than one identity provider is available, select your choice from the options provided.
-
Enter your username and password into the corresponding browser fields. After you are logged in, the browser displays the text
access token received successfully; please return to your terminal. Check the CLI for a login confirmation.
Example output
Login successful. You don't have any projects. You can try to create a new project, by running oc new-project <projectname>Login successful. You don't have any projects. You can try to create a new project, by running oc new-project <projectname>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The web console defaults to the profile used in the previous session. To switch between Administrator and Developer profiles, log out of the OpenShift Container Platform web console and clear the cache.
You can now create a project or issue other commands for managing your cluster.
2.1.8. Using the OpenShift CLI
Review the following sections to learn how to complete common tasks using the CLI.
2.1.8.1. Creating a project
Use the oc new-project command to create a new project.
oc new-project my-project
$ oc new-project my-projectExample output
Now using project "my-project" on server "https://openshift.example.com:6443".
Now using project "my-project" on server "https://openshift.example.com:6443".2.1.8.2. Creating a new app
Use the oc new-app command to create a new application.
oc new-app https://github.com/sclorg/cakephp-ex
$ oc new-app https://github.com/sclorg/cakephp-exExample output
--> Found image 40de956 (9 days old) in imagestream "openshift/php" under tag "7.2" for "php"
...
Run 'oc status' to view your app.
--> Found image 40de956 (9 days old) in imagestream "openshift/php" under tag "7.2" for "php"
...
Run 'oc status' to view your app.2.1.8.3. Viewing pods
Use the oc get pods command to view the pods for the current project.
When you run oc inside a pod and do not specify a namespace, the namespace of the pod is used by default.
oc get pods -o wide
$ oc get pods -o wideExample output
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE cakephp-ex-1-build 0/1 Completed 0 5m45s 10.131.0.10 ip-10-0-141-74.ec2.internal <none> cakephp-ex-1-deploy 0/1 Completed 0 3m44s 10.129.2.9 ip-10-0-147-65.ec2.internal <none> cakephp-ex-1-ktz97 1/1 Running 0 3m33s 10.128.2.11 ip-10-0-168-105.ec2.internal <none>
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE
cakephp-ex-1-build 0/1 Completed 0 5m45s 10.131.0.10 ip-10-0-141-74.ec2.internal <none>
cakephp-ex-1-deploy 0/1 Completed 0 3m44s 10.129.2.9 ip-10-0-147-65.ec2.internal <none>
cakephp-ex-1-ktz97 1/1 Running 0 3m33s 10.128.2.11 ip-10-0-168-105.ec2.internal <none>2.1.8.4. Viewing pod logs
Use the oc logs command to view logs for a particular pod.
oc logs cakephp-ex-1-deploy
$ oc logs cakephp-ex-1-deployExample output
--> Scaling cakephp-ex-1 to 1 --> Success
--> Scaling cakephp-ex-1 to 1
--> Success2.1.8.5. Viewing the current project
Use the oc project command to view the current project.
oc project
$ oc projectExample output
Using project "my-project" on server "https://openshift.example.com:6443".
Using project "my-project" on server "https://openshift.example.com:6443".2.1.8.6. Viewing the status for the current project
Use the oc status command to view information about the current project, such as services, deployments, and build configs.
oc status
$ oc statusExample output
2.1.8.7. Listing supported API resources
Use the oc api-resources command to view the list of supported API resources on the server.
oc api-resources
$ oc api-resourcesExample output
NAME SHORTNAMES APIGROUP NAMESPACED KIND bindings true Binding componentstatuses cs false ComponentStatus configmaps cm true ConfigMap ...
NAME SHORTNAMES APIGROUP NAMESPACED KIND
bindings true Binding
componentstatuses cs false ComponentStatus
configmaps cm true ConfigMap
...2.1.9. Getting help
You can get help with CLI commands and OpenShift Container Platform resources in the following ways:
Use
oc helpto get a list and description of all available CLI commands:Example: Get general help for the CLI
oc help
$ oc helpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
--helpflag to get help about a specific CLI command:Example: Get help for the
oc createcommandoc create --help
$ oc create --helpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
oc explaincommand to view the description and fields for a particular resource:Example: View documentation for the
Podresourceoc explain pods
$ oc explain podsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.1.10. Logging out of the OpenShift CLI
You can log out the OpenShift CLI to end your current session.
Use the
oc logoutcommand.oc logout
$ oc logoutCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Logged "user1" out on "https://openshift.example.com"
Logged "user1" out on "https://openshift.example.com"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
This deletes the saved authentication token from the server and removes it from your configuration file.
2.2. Configuring the OpenShift CLI
2.2.1. Enabling tab completion
You can enable tab completion for the Bash or Zsh shells.
2.2.1.1. Enabling tab completion for Bash
After you install the OpenShift CLI (oc), you can enable tab completion to automatically complete oc commands or suggest options when you press Tab. The following procedure enables tab completion for the Bash shell.
Prerequisites
-
You must have the OpenShift CLI (
oc) installed. -
You must have the package
bash-completioninstalled.
Procedure
Save the Bash completion code to a file:
oc completion bash > oc_bash_completion
$ oc completion bash > oc_bash_completionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy the file to
/etc/bash_completion.d/:sudo cp oc_bash_completion /etc/bash_completion.d/
$ sudo cp oc_bash_completion /etc/bash_completion.d/Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can also save the file to a local directory and source it from your
.bashrcfile instead. Tab completion is enabled when you open a new terminal.
2.2.1.2. Enabling tab completion for Zsh
After you install the OpenShift CLI (oc), you can enable tab completion to automatically complete oc commands or suggest options when you press Tab. The following procedure enables tab completion for the Zsh shell.
Prerequisites
-
You must have the OpenShift CLI (
oc) installed.
Procedure
To add tab completion for
octo your.zshrcfile, run the following command:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Tab completion is enabled when you open a new terminal.
2.2.2. Accessing kubeconfig by using the oc CLI
You can use the oc CLI to log in to your OpenShift cluster and retrieve a kubeconfig file for accessing the cluster from the command line.
Prerequisites
- You have access to the OpenShift Container Platform web console or API server endpoint.
Procedure
Log in to your OpenShift cluster by running the following command:
oc login <api-server-url> -u <username> -p <password>
$ oc login <api-server-url> -u <username> -p <password>1 2 3 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the full API server URL. For example:
https://api.my-cluster.example.com:6443. - 2
- Specify a valid username. For example:
kubeadmin. - 3
- Provide the password for the specified user. For example, the
kubeadminpassword generated during cluster installation.
Save the cluster configuration to a local file by running the following command:
oc config view --raw > kubeconfig
$ oc config view --raw > kubeconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
KUBECONFIGenvironment variable to point to the exported file by running the following command:export KUBECONFIG=./kubeconfig
$ export KUBECONFIG=./kubeconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use
octo interact with your OpenShift cluster by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
If you plan to reuse the exported kubeconfig file across sessions or machines, store it securely and avoid committing it to source control.
2.3. Usage of oc and kubectl commands
The Kubernetes command-line interface (CLI), kubectl, can be used to run commands against a Kubernetes cluster. Because OpenShift Container Platform is a certified Kubernetes distribution, you can use the supported kubectl binaries that ship with OpenShift Container Platform , or you can gain extended functionality by using the oc binary.
2.3.1. The oc binary
The oc binary offers the same capabilities as the kubectl binary, but it extends to natively support additional OpenShift Container Platform features, including:
Full support for OpenShift Container Platform resources
Resources such as
DeploymentConfig,BuildConfig,Route,ImageStream, andImageStreamTagobjects are specific to OpenShift Container Platform distributions, and build upon standard Kubernetes primitives.Authentication
The
ocbinary offers a built-inlogincommand for authentication and lets you work with projects, which map Kubernetes namespaces to authenticated users. Read Understanding authentication for more information.Additional commands
The additional command
oc new-app, for example, makes it easier to get new applications started using existing source code or pre-built images. Similarly, the additional commandoc new-projectmakes it easier to start a project that you can switch to as your default.
If you installed an earlier version of the oc binary, you cannot use it to complete all of the commands in OpenShift Container Platform 4.18 . If you want the latest features, you must download and install the latest version of the oc binary corresponding to your OpenShift Container Platform server version.
Non-security API changes will involve, at minimum, two minor releases (4.1 to 4.2 to 4.3, for example) to allow older oc binaries to update. Using new capabilities might require newer oc binaries. A 4.3 server might have additional capabilities that a 4.2 oc binary cannot use and a 4.3 oc binary might have additional capabilities that are unsupported by a 4.2 server.
|
X.Y ( |
X.Y+N [a] ( | |
| X.Y (Server) |
|
|
| X.Y+N [a] (Server) |
|
|
[a]
Where N is a number greater than or equal to 1.
| ||
 Fully compatible.
Fully compatible.

oc client might not be able to access server features.

oc client might provide options and features that might not be compatible with the accessed server.
2.3.2. The kubectl binary
The kubectl binary is provided as a means to support existing workflows and scripts for new OpenShift Container Platform users coming from a standard Kubernetes environment, or for those who prefer to use the kubectl CLI. Existing users of kubectl can continue to use the binary to interact with Kubernetes primitives, with no changes required to the OpenShift Container Platform cluster.
You can install the supported kubectl binary by following the steps to Install the OpenShift CLI. The kubectl binary is included in the archive if you download the binary, or is installed when you install the CLI by using an RPM.
For more information, see the kubectl documentation.
2.4. Managing CLI profiles
A CLI configuration file allows you to configure different profiles, or contexts, for use with the CLI tools overview. A context consists of user authentication an OpenShift Container Platform server information associated with a nickname.
2.4.1. About switches between CLI profiles
Contexts allow you to easily switch between multiple users across multiple OpenShift Container Platform servers, or clusters, when using CLI operations. Nicknames make managing CLI configurations easier by providing short-hand references to contexts, user credentials, and cluster details. After a user logs in with the oc CLI for the first time, OpenShift Container Platform creates a ~/.kube/config file if one does not already exist. As more authentication and connection details are provided to the CLI, either automatically during an oc login operation or by manually configuring CLI profiles, the updated information is stored in the configuration file:
CLI config file
- 1
- The
clusterssection defines connection details for OpenShift Container Platform clusters, including the address for their master server. In this example, one cluster is nicknamedopenshift1.example.com:8443and another is nicknamedopenshift2.example.com:8443. - 2
- This
contextssection defines two contexts: one nicknamedalice-project/openshift1.example.com:8443/alice, using thealice-projectproject,openshift1.example.com:8443cluster, andaliceuser, and another nicknamedjoe-project/openshift1.example.com:8443/alice, using thejoe-projectproject,openshift1.example.com:8443cluster andaliceuser. - 3
- The
current-contextparameter shows that thejoe-project/openshift1.example.com:8443/alicecontext is currently in use, allowing thealiceuser to work in thejoe-projectproject on theopenshift1.example.com:8443cluster. - 4
- The
userssection defines user credentials. In this example, the user nicknamealice/openshift1.example.com:8443uses an access token.
The CLI can support multiple configuration files which are loaded at runtime and merged together along with any override options specified from the command line. After you are logged in, you can use the oc status or oc project command to verify your current working environment:
Verify the current working environment
oc status
$ oc statusExample output
List the current project
oc project
$ oc projectExample output
Using project "joe-project" from context named "joe-project/openshift1.example.com:8443/alice" on server "https://openshift1.example.com:8443".
Using project "joe-project" from context named "joe-project/openshift1.example.com:8443/alice" on server "https://openshift1.example.com:8443".
You can run the oc login command again and supply the required information during the interactive process, to log in using any other combination of user credentials and cluster details. A context is constructed based on the supplied information if one does not already exist. If you are already logged in and want to switch to another project the current user already has access to, use the oc project command and enter the name of the project:
oc project alice-project
$ oc project alice-projectExample output
Now using project "alice-project" on server "https://openshift1.example.com:8443".
Now using project "alice-project" on server "https://openshift1.example.com:8443".
At any time, you can use the oc config view command to view your current CLI configuration, as seen in the output. Additional CLI configuration commands are also available for more advanced usage.
If you have access to administrator credentials but are no longer logged in as the default system user system:admin, you can log back in as this user at any time as long as the credentials are still present in your CLI config file. The following command logs in and switches to the default project:
oc login -u system:admin -n default
$ oc login -u system:admin -n default2.4.2. Manual configuration of CLI profiles
This section covers more advanced usage of CLI configurations. In most situations, you can use the oc login and oc project commands to log in and switch between contexts and projects.
If you want to manually configure your CLI config files, you can use the oc config command instead of directly modifying the files. The oc config command includes a number of helpful sub-commands for this purpose:
| Subcommand | Usage |
|---|---|
|
| Sets a cluster entry in the CLI config file. If the referenced cluster nickname already exists, the specified information is merged in. oc config set-cluster <cluster_nickname> [--server=<master_ip_or_fqdn>] [--certificate-authority=<path/to/certificate/authority>] [--api-version=<apiversion>] [--insecure-skip-tls-verify=true] |
|
| Sets a context entry in the CLI config file. If the referenced context nickname already exists, the specified information is merged in. oc config set-context <context_nickname> [--cluster=<cluster_nickname>] [--user=<user_nickname>] [--namespace=<namespace>] |
|
| Sets the current context using the specified context nickname. oc config use-context <context_nickname> |
|
| Sets an individual value in the CLI config file. oc config set <property_name> <property_value>
The |
|
| Unsets individual values in the CLI config file. oc config unset <property_name>
The |
|
| Displays the merged CLI configuration currently in use. oc config view Displays the result of the specified CLI config file. oc config view --config=<specific_filename> |
Example usage
-
Log in as a user that uses an access token. This token is used by the
aliceuser:
oc login https://openshift1.example.com --token=ns7yVhuRNpDM9cgzfhhxQ7bM5s7N2ZVrkZepSRf4LC0
$ oc login https://openshift1.example.com --token=ns7yVhuRNpDM9cgzfhhxQ7bM5s7N2ZVrkZepSRf4LC0- View the cluster entry automatically created:
oc config view
$ oc config viewExample output
- Update the current context to have users log in to the desired namespace:
oc config set-context `oc config current-context` --namespace=<project_name>
$ oc config set-context `oc config current-context` --namespace=<project_name>- Examine the current context, to confirm that the changes are implemented:
oc whoami -c
$ oc whoami -cAll subsequent CLI operations uses the new context, unless otherwise specified by overriding CLI options or until the context is switched.
2.4.3. Load and merge rules
You can follow these rules, when issuing CLI operations for the loading and merging order for the CLI configuration:
CLI config files are retrieved from your workstation, using the following hierarchy and merge rules:
-
If the
--configoption is set, then only that file is loaded. The flag is set once and no merging takes place. -
If the
$KUBECONFIGenvironment variable is set, then it is used. The variable can be a list of paths, and if so the paths are merged together. When a value is modified, it is modified in the file that defines the stanza. When a value is created, it is created in the first file that exists. If no files in the chain exist, then it creates the last file in the list. -
Otherwise, the
~/.kube/configfile is used and no merging takes place.
-
If the
The context to use is determined based on the first match in the following flow:
-
The value of the
--contextoption. -
The
current-contextvalue from the CLI config file. - An empty value is allowed at this stage.
-
The value of the
The user and cluster to use is determined. At this point, you may or may not have a context; they are built based on the first match in the following flow, which is run once for the user and once for the cluster:
-
The value of the
--userfor user name and--clusteroption for cluster name. -
If the
--contextoption is present, then use the context’s value. - An empty value is allowed at this stage.
-
The value of the
The actual cluster information to use is determined. At this point, you may or may not have cluster information. Each piece of the cluster information is built based on the first match in the following flow:
The values of any of the following command-line options:
-
--server, -
--api-version -
--certificate-authority -
--insecure-skip-tls-verify
-
- If cluster information and a value for the attribute is present, then use it.
- If you do not have a server location, then there is an error.
The actual user information to use is determined. Users are built using the same rules as clusters, except that you can only have one authentication technique per user; conflicting techniques cause the operation to fail. Command-line options take precedence over config file values. Valid command-line options are:
-
--auth-path -
--client-certificate -
--client-key -
--token
-
- For any information that is still missing, default values are used and prompts are given for additional information.
2.5. Extending the OpenShift CLI with plugins
You can write and install plugins to build on the default oc commands, allowing you to perform new and more complex tasks with the OpenShift Container Platform CLI.
2.5.1. Writing CLI plugins
You can write a plugin for the OpenShift Container Platform CLI in any programming language or script that allows you to write command-line commands. Note that you can not use a plugin to overwrite an existing oc command.
Procedure
This procedure creates a simple Bash plugin that prints a message to the terminal when the oc foo command is issued.
Create a file called
oc-foo.When naming your plugin file, keep the following in mind:
-
The file must begin with
oc-orkubectl-to be recognized as a plugin. -
The file name determines the command that invokes the plugin. For example, a plugin with the file name
oc-foo-barcan be invoked by a command ofoc foo bar. You can also use underscores if you want the command to contain dashes. For example, a plugin with the file nameoc-foo_barcan be invoked by a command ofoc foo-bar.
-
The file must begin with
Add the following contents to the file.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install this plugin for the OpenShift Container Platform CLI, it can be invoked using the oc foo command.
2.5.2. Installing and using CLI plugins
After you write a custom plugin for the OpenShift Container Platform CLI, you must install the plugin before use.
Prerequisites
-
You must have the
ocCLI tool installed. -
You must have a CLI plugin file that begins with
oc-orkubectl-.
Procedure
If necessary, update the plugin file to be executable.
chmod +x <plugin_file>
$ chmod +x <plugin_file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the file anywhere in your
PATH, such as/usr/local/bin/.sudo mv <plugin_file> /usr/local/bin/.
$ sudo mv <plugin_file> /usr/local/bin/.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run
oc plugin listto make sure that the plugin is listed.oc plugin list
$ oc plugin listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
The following compatible plugins are available: /usr/local/bin/<plugin_file>
The following compatible plugins are available: /usr/local/bin/<plugin_file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow If your plugin is not listed here, verify that the file begins with
oc-orkubectl-, is executable, and is on yourPATH.Invoke the new command or option introduced by the plugin.
For example, if you built and installed the
kubectl-nsplugin from the Sample plugin repository, you can use the following command to view the current namespace.oc ns
$ oc nsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the command to invoke the plugin depends on the plugin file name. For example, a plugin with the file name of
oc-foo-baris invoked by theoc foo barcommand.
2.6. OpenShift CLI developer command reference
This reference provides descriptions and example commands for OpenShift CLI (oc) developer commands. For administrator commands, see the OpenShift CLI administrator command reference.
Run oc help to list all commands or run oc <command> --help to get additional details for a specific command.
2.6.1. OpenShift CLI (oc) developer commands
2.6.1.1. oc annotate
Update the annotations on a resource
Example usage
2.6.1.2. oc api-resources
Print the supported API resources on the server
Example usage
2.6.1.3. oc api-versions
Print the supported API versions on the server, in the form of "group/version"
Example usage
# Print the supported API versions oc api-versions
# Print the supported API versions
oc api-versions2.6.1.4. oc apply
Apply a configuration to a resource by file name or stdin
Example usage
2.6.1.5. oc apply edit-last-applied
Edit latest last-applied-configuration annotations of a resource/object
Example usage
# Edit the last-applied-configuration annotations by type/name in YAML oc apply edit-last-applied deployment/nginx # Edit the last-applied-configuration annotations by file in JSON oc apply edit-last-applied -f deploy.yaml -o json
# Edit the last-applied-configuration annotations by type/name in YAML
oc apply edit-last-applied deployment/nginx
# Edit the last-applied-configuration annotations by file in JSON
oc apply edit-last-applied -f deploy.yaml -o json2.6.1.6. oc apply set-last-applied
Set the last-applied-configuration annotation on a live object to match the contents of a file
Example usage
2.6.1.7. oc apply view-last-applied
View the latest last-applied-configuration annotations of a resource/object
Example usage
# View the last-applied-configuration annotations by type/name in YAML oc apply view-last-applied deployment/nginx # View the last-applied-configuration annotations by file in JSON oc apply view-last-applied -f deploy.yaml -o json
# View the last-applied-configuration annotations by type/name in YAML
oc apply view-last-applied deployment/nginx
# View the last-applied-configuration annotations by file in JSON
oc apply view-last-applied -f deploy.yaml -o json2.6.1.8. oc attach
Attach to a running container
Example usage
2.6.1.9. oc auth can-i
Check whether an action is allowed
Example usage
2.6.1.10. oc auth reconcile
Reconciles rules for RBAC role, role binding, cluster role, and cluster role binding objects
Example usage
# Reconcile RBAC resources from a file oc auth reconcile -f my-rbac-rules.yaml
# Reconcile RBAC resources from a file
oc auth reconcile -f my-rbac-rules.yaml2.6.1.11. oc auth whoami
Experimental: Check self subject attributes
Example usage
# Get your subject attributes. oc auth whoami # Get your subject attributes in JSON format. oc auth whoami -o json
# Get your subject attributes.
oc auth whoami
# Get your subject attributes in JSON format.
oc auth whoami -o json2.6.1.12. oc autoscale
Autoscale a deployment config, deployment, replica set, stateful set, or replication controller
Example usage
# Auto scale a deployment "foo", with the number of pods between 2 and 10, no target CPU utilization specified so a default autoscaling policy will be used oc autoscale deployment foo --min=2 --max=10 # Auto scale a replication controller "foo", with the number of pods between 1 and 5, target CPU utilization at 80% oc autoscale rc foo --max=5 --cpu-percent=80
# Auto scale a deployment "foo", with the number of pods between 2 and 10, no target CPU utilization specified so a default autoscaling policy will be used
oc autoscale deployment foo --min=2 --max=10
# Auto scale a replication controller "foo", with the number of pods between 1 and 5, target CPU utilization at 80%
oc autoscale rc foo --max=5 --cpu-percent=802.6.1.13. oc cancel-build
Cancel running, pending, or new builds
Example usage
2.6.1.14. oc cluster-info
Display cluster information
Example usage
# Print the address of the control plane and cluster services oc cluster-info
# Print the address of the control plane and cluster services
oc cluster-info2.6.1.15. oc cluster-info dump
Dump relevant information for debugging and diagnosis
Example usage
2.6.1.16. oc completion
Output shell completion code for the specified shell (bash, zsh, fish, or powershell)
Example usage
2.6.1.17. oc config current-context
Display the current-context
Example usage
# Display the current-context oc config current-context
# Display the current-context
oc config current-context2.6.1.18. oc config delete-cluster
Delete the specified cluster from the kubeconfig
Example usage
# Delete the minikube cluster oc config delete-cluster minikube
# Delete the minikube cluster
oc config delete-cluster minikube2.6.1.19. oc config delete-context
Delete the specified context from the kubeconfig
Example usage
# Delete the context for the minikube cluster oc config delete-context minikube
# Delete the context for the minikube cluster
oc config delete-context minikube2.6.1.20. oc config delete-user
Delete the specified user from the kubeconfig
Example usage
# Delete the minikube user oc config delete-user minikube
# Delete the minikube user
oc config delete-user minikube2.6.1.21. oc config get-clusters
Display clusters defined in the kubeconfig
Example usage
# List the clusters that oc knows about oc config get-clusters
# List the clusters that oc knows about
oc config get-clusters2.6.1.22. oc config get-contexts
Describe one or many contexts
Example usage
# List all the contexts in your kubeconfig file oc config get-contexts # Describe one context in your kubeconfig file oc config get-contexts my-context
# List all the contexts in your kubeconfig file
oc config get-contexts
# Describe one context in your kubeconfig file
oc config get-contexts my-context2.6.1.23. oc config get-users
Display users defined in the kubeconfig
Example usage
# List the users that oc knows about oc config get-users
# List the users that oc knows about
oc config get-users2.6.1.24. oc config new-admin-kubeconfig
Generate, make the server trust, and display a new admin.kubeconfig
Example usage
# Generate a new admin kubeconfig oc config new-admin-kubeconfig
# Generate a new admin kubeconfig
oc config new-admin-kubeconfig2.6.1.25. oc config new-kubelet-bootstrap-kubeconfig
Generate, make the server trust, and display a new kubelet /etc/kubernetes/kubeconfig
Example usage
# Generate a new kubelet bootstrap kubeconfig oc config new-kubelet-bootstrap-kubeconfig
# Generate a new kubelet bootstrap kubeconfig
oc config new-kubelet-bootstrap-kubeconfig2.6.1.26. oc config refresh-ca-bundle
Update the OpenShift CA bundle by contacting the API server
Example usage
2.6.1.27. oc config rename-context
Rename a context from the kubeconfig file
Example usage
# Rename the context 'old-name' to 'new-name' in your kubeconfig file oc config rename-context old-name new-name
# Rename the context 'old-name' to 'new-name' in your kubeconfig file
oc config rename-context old-name new-name2.6.1.28. oc config set
Set an individual value in a kubeconfig file
Example usage
2.6.1.29. oc config set-cluster
Set a cluster entry in kubeconfig
Example usage
2.6.1.30. oc config set-context
Set a context entry in kubeconfig
Example usage
# Set the user field on the gce context entry without touching other values oc config set-context gce --user=cluster-admin
# Set the user field on the gce context entry without touching other values
oc config set-context gce --user=cluster-admin2.6.1.31. oc config set-credentials
Set a user entry in kubeconfig
Example usage
2.6.1.32. oc config unset
Unset an individual value in a kubeconfig file
Example usage
# Unset the current-context oc config unset current-context # Unset namespace in foo context oc config unset contexts.foo.namespace
# Unset the current-context
oc config unset current-context
# Unset namespace in foo context
oc config unset contexts.foo.namespace2.6.1.33. oc config use-context
Set the current-context in a kubeconfig file
Example usage
# Use the context for the minikube cluster oc config use-context minikube
# Use the context for the minikube cluster
oc config use-context minikube2.6.1.34. oc config view
Display merged kubeconfig settings or a specified kubeconfig file
Example usage
2.6.1.35. oc cp
Copy files and directories to and from containers
Example usage
2.6.1.36. oc create
Create a resource from a file or from stdin
Example usage
2.6.1.37. oc create build
Create a new build
Example usage
# Create a new build oc create build myapp
# Create a new build
oc create build myapp2.6.1.38. oc create clusterresourcequota
Create a cluster resource quota
Example usage
# Create a cluster resource quota limited to 10 pods oc create clusterresourcequota limit-bob --project-annotation-selector=openshift.io/requester=user-bob --hard=pods=10
# Create a cluster resource quota limited to 10 pods
oc create clusterresourcequota limit-bob --project-annotation-selector=openshift.io/requester=user-bob --hard=pods=102.6.1.39. oc create clusterrole
Create a cluster role
Example usage
2.6.1.40. oc create clusterrolebinding
Create a cluster role binding for a particular cluster role
Example usage
# Create a cluster role binding for user1, user2, and group1 using the cluster-admin cluster role oc create clusterrolebinding cluster-admin --clusterrole=cluster-admin --user=user1 --user=user2 --group=group1
# Create a cluster role binding for user1, user2, and group1 using the cluster-admin cluster role
oc create clusterrolebinding cluster-admin --clusterrole=cluster-admin --user=user1 --user=user2 --group=group12.6.1.41. oc create configmap
Create a config map from a local file, directory or literal value
Example usage
2.6.1.42. oc create cronjob
Create a cron job with the specified name
Example usage
# Create a cron job oc create cronjob my-job --image=busybox --schedule="*/1 * * * *" # Create a cron job with a command oc create cronjob my-job --image=busybox --schedule="*/1 * * * *" -- date
# Create a cron job
oc create cronjob my-job --image=busybox --schedule="*/1 * * * *"
# Create a cron job with a command
oc create cronjob my-job --image=busybox --schedule="*/1 * * * *" -- date2.6.1.43. oc create deployment
Create a deployment with the specified name
Example usage
2.6.1.44. oc create deploymentconfig
Create a deployment config with default options that uses a given image
Example usage
# Create an nginx deployment config named my-nginx oc create deploymentconfig my-nginx --image=nginx
# Create an nginx deployment config named my-nginx
oc create deploymentconfig my-nginx --image=nginx2.6.1.45. oc create identity
Manually create an identity (only needed if automatic creation is disabled)
Example usage
# Create an identity with identity provider "acme_ldap" and the identity provider username "adamjones" oc create identity acme_ldap:adamjones
# Create an identity with identity provider "acme_ldap" and the identity provider username "adamjones"
oc create identity acme_ldap:adamjones2.6.1.46. oc create imagestream
Create a new empty image stream
Example usage
# Create a new image stream oc create imagestream mysql
# Create a new image stream
oc create imagestream mysql2.6.1.47. oc create imagestreamtag
Create a new image stream tag
Example usage
# Create a new image stream tag based on an image in a remote registry oc create imagestreamtag mysql:latest --from-image=myregistry.local/mysql/mysql:5.0
# Create a new image stream tag based on an image in a remote registry
oc create imagestreamtag mysql:latest --from-image=myregistry.local/mysql/mysql:5.02.6.1.48. oc create ingress
Create an ingress with the specified name
Example usage
2.6.1.49. oc create job
Create a job with the specified name
Example usage
2.6.1.50. oc create namespace
Create a namespace with the specified name
Example usage
# Create a new namespace named my-namespace oc create namespace my-namespace
# Create a new namespace named my-namespace
oc create namespace my-namespace2.6.1.51. oc create poddisruptionbudget
Create a pod disruption budget with the specified name
Example usage
2.6.1.52. oc create priorityclass
Create a priority class with the specified name
Example usage
2.6.1.53. oc create quota
Create a quota with the specified name
Example usage
# Create a new resource quota named my-quota oc create quota my-quota --hard=cpu=1,memory=1G,pods=2,services=3,replicationcontrollers=2,resourcequotas=1,secrets=5,persistentvolumeclaims=10 # Create a new resource quota named best-effort oc create quota best-effort --hard=pods=100 --scopes=BestEffort
# Create a new resource quota named my-quota
oc create quota my-quota --hard=cpu=1,memory=1G,pods=2,services=3,replicationcontrollers=2,resourcequotas=1,secrets=5,persistentvolumeclaims=10
# Create a new resource quota named best-effort
oc create quota best-effort --hard=pods=100 --scopes=BestEffort2.6.1.54. oc create role
Create a role with single rule
Example usage
2.6.1.55. oc create rolebinding
Create a role binding for a particular role or cluster role
Example usage
# Create a role binding for user1, user2, and group1 using the admin cluster role oc create rolebinding admin --clusterrole=admin --user=user1 --user=user2 --group=group1 # Create a role binding for serviceaccount monitoring:sa-dev using the admin role oc create rolebinding admin-binding --role=admin --serviceaccount=monitoring:sa-dev
# Create a role binding for user1, user2, and group1 using the admin cluster role
oc create rolebinding admin --clusterrole=admin --user=user1 --user=user2 --group=group1
# Create a role binding for serviceaccount monitoring:sa-dev using the admin role
oc create rolebinding admin-binding --role=admin --serviceaccount=monitoring:sa-dev2.6.1.56. oc create route edge
Create a route that uses edge TLS termination
Example usage
2.6.1.57. oc create route passthrough
Create a route that uses passthrough TLS termination
Example usage
2.6.1.58. oc create route reencrypt
Create a route that uses reencrypt TLS termination
Example usage
2.6.1.59. oc create secret docker-registry
Create a secret for use with a Docker registry
Example usage
# If you do not already have a .dockercfg file, create a dockercfg secret directly oc create secret docker-registry my-secret --docker-server=DOCKER_REGISTRY_SERVER --docker-username=DOCKER_USER --docker-password=DOCKER_PASSWORD --docker-email=DOCKER_EMAIL # Create a new secret named my-secret from ~/.docker/config.json oc create secret docker-registry my-secret --from-file=.dockerconfigjson=path/to/.docker/config.json
# If you do not already have a .dockercfg file, create a dockercfg secret directly
oc create secret docker-registry my-secret --docker-server=DOCKER_REGISTRY_SERVER --docker-username=DOCKER_USER --docker-password=DOCKER_PASSWORD --docker-email=DOCKER_EMAIL
# Create a new secret named my-secret from ~/.docker/config.json
oc create secret docker-registry my-secret --from-file=.dockerconfigjson=path/to/.docker/config.json2.6.1.60. oc create secret generic
Create a secret from a local file, directory, or literal value
Example usage
2.6.1.61. oc create secret tls
Create a TLS secret
Example usage
# Create a new TLS secret named tls-secret with the given key pair oc create secret tls tls-secret --cert=path/to/tls.crt --key=path/to/tls.key
# Create a new TLS secret named tls-secret with the given key pair
oc create secret tls tls-secret --cert=path/to/tls.crt --key=path/to/tls.key2.6.1.62. oc create service clusterip
Create a ClusterIP service
Example usage
# Create a new ClusterIP service named my-cs oc create service clusterip my-cs --tcp=5678:8080 # Create a new ClusterIP service named my-cs (in headless mode) oc create service clusterip my-cs --clusterip="None"
# Create a new ClusterIP service named my-cs
oc create service clusterip my-cs --tcp=5678:8080
# Create a new ClusterIP service named my-cs (in headless mode)
oc create service clusterip my-cs --clusterip="None"2.6.1.63. oc create service externalname
Create an ExternalName service
Example usage
# Create a new ExternalName service named my-ns oc create service externalname my-ns --external-name bar.com
# Create a new ExternalName service named my-ns
oc create service externalname my-ns --external-name bar.com2.6.1.64. oc create service loadbalancer
Create a LoadBalancer service
Example usage
# Create a new LoadBalancer service named my-lbs oc create service loadbalancer my-lbs --tcp=5678:8080
# Create a new LoadBalancer service named my-lbs
oc create service loadbalancer my-lbs --tcp=5678:80802.6.1.65. oc create service nodeport
Create a NodePort service
Example usage
# Create a new NodePort service named my-ns oc create service nodeport my-ns --tcp=5678:8080
# Create a new NodePort service named my-ns
oc create service nodeport my-ns --tcp=5678:80802.6.1.66. oc create serviceaccount
Create a service account with the specified name
Example usage
# Create a new service account named my-service-account oc create serviceaccount my-service-account
# Create a new service account named my-service-account
oc create serviceaccount my-service-account2.6.1.67. oc create token
Request a service account token
Example usage
2.6.1.68. oc create user
Manually create a user (only needed if automatic creation is disabled)
Example usage
# Create a user with the username "ajones" and the display name "Adam Jones" oc create user ajones --full-name="Adam Jones"
# Create a user with the username "ajones" and the display name "Adam Jones"
oc create user ajones --full-name="Adam Jones"2.6.1.69. oc create useridentitymapping
Manually map an identity to a user
Example usage
# Map the identity "acme_ldap:adamjones" to the user "ajones" oc create useridentitymapping acme_ldap:adamjones ajones
# Map the identity "acme_ldap:adamjones" to the user "ajones"
oc create useridentitymapping acme_ldap:adamjones ajones2.6.1.70. oc debug
Launch a new instance of a pod for debugging
Example usage
2.6.1.71. oc delete
Delete resources by file names, stdin, resources and names, or by resources and label selector
Example usage
2.6.1.72. oc describe
Show details of a specific resource or group of resources
Example usage
2.6.1.73. oc diff
Diff the live version against a would-be applied version
Example usage
# Diff resources included in pod.json oc diff -f pod.json # Diff file read from stdin cat service.yaml | oc diff -f -
# Diff resources included in pod.json
oc diff -f pod.json
# Diff file read from stdin
cat service.yaml | oc diff -f -2.6.1.74. oc edit
Edit a resource on the server
Example usage
2.6.1.75. oc events
List events
Example usage
2.6.1.76. oc exec
Execute a command in a container
Example usage
2.6.1.77. oc explain
Get documentation for a resource
Example usage
2.6.1.78. oc expose
Expose a replicated application as a service or route
Example usage
2.6.1.79. oc extract
Extract secrets or config maps to disk
Example usage
2.6.1.80. oc get
Display one or many resources
Example usage
2.6.1.81. oc get-token
Experimental: Get token from external OIDC issuer as credentials exec plugin
Example usage
# Starts an auth code flow to the issuer URL with the client ID and the given extra scopes oc get-token --client-id=client-id --issuer-url=test.issuer.url --extra-scopes=email,profile # Starts an auth code flow to the issuer URL with a different callback address oc get-token --client-id=client-id --issuer-url=test.issuer.url --callback-address=127.0.0.1:8343
# Starts an auth code flow to the issuer URL with the client ID and the given extra scopes
oc get-token --client-id=client-id --issuer-url=test.issuer.url --extra-scopes=email,profile
# Starts an auth code flow to the issuer URL with a different callback address
oc get-token --client-id=client-id --issuer-url=test.issuer.url --callback-address=127.0.0.1:83432.6.1.82. oc idle
Idle scalable resources
Example usage
# Idle the scalable controllers associated with the services listed in to-idle.txt $ oc idle --resource-names-file to-idle.txt
# Idle the scalable controllers associated with the services listed in to-idle.txt
$ oc idle --resource-names-file to-idle.txt2.6.1.83. oc image append
Add layers to images and push them to a registry
Example usage
2.6.1.84. oc image extract
Copy files from an image to the file system
Example usage
2.6.1.85. oc image info
Display information about an image
Example usage
2.6.1.86. oc image mirror
Mirror images from one repository to another
Example usage
2.6.1.87. oc import-image
Import images from a container image registry
Example usage
2.6.1.88. oc kustomize
Build a kustomization target from a directory or URL
Example usage
2.6.1.89. oc label
Update the labels on a resource
Example usage
2.6.1.90. oc login
Log in to a server
Example usage
2.6.1.91. oc logout
End the current server session
Example usage
# Log out oc logout
# Log out
oc logout2.6.1.92. oc logs
Print the logs for a container in a pod
Example usage
2.6.1.93. oc new-app
Create a new application
Example usage
2.6.1.94. oc new-build
Create a new build configuration
Example usage
2.6.1.95. oc new-project
Request a new project
Example usage
# Create a new project with minimal information oc new-project web-team-dev # Create a new project with a display name and description oc new-project web-team-dev --display-name="Web Team Development" --description="Development project for the web team."
# Create a new project with minimal information
oc new-project web-team-dev
# Create a new project with a display name and description
oc new-project web-team-dev --display-name="Web Team Development" --description="Development project for the web team."2.6.1.96. oc observe
Observe changes to resources and react to them (experimental)
Example usage
2.6.1.97. oc patch
Update fields of a resource
Example usage
2.6.1.98. oc plugin list
List all visible plugin executables on a user’s PATH
Example usage
# List all available plugins oc plugin list
# List all available plugins
oc plugin list2.6.1.99. oc policy add-role-to-user
Add a role to users or service accounts for the current project
Example usage
# Add the 'view' role to user1 for the current project oc policy add-role-to-user view user1 # Add the 'edit' role to serviceaccount1 for the current project oc policy add-role-to-user edit -z serviceaccount1
# Add the 'view' role to user1 for the current project
oc policy add-role-to-user view user1
# Add the 'edit' role to serviceaccount1 for the current project
oc policy add-role-to-user edit -z serviceaccount12.6.1.100. oc policy scc-review
Check which service account can create a pod
Example usage
2.6.1.101. oc policy scc-subject-review
Check whether a user or a service account can create a pod
Example usage
2.6.1.102. oc port-forward
Forward one or more local ports to a pod
Example usage
2.6.1.103. oc process
Process a template into list of resources
Example usage
2.6.1.104. oc project
Switch to another project
Example usage
# Switch to the 'myapp' project oc project myapp # Display the project currently in use oc project
# Switch to the 'myapp' project
oc project myapp
# Display the project currently in use
oc project2.6.1.105. oc projects
Display existing projects
Example usage
# List all projects oc projects
# List all projects
oc projects2.6.1.106. oc proxy
Run a proxy to the Kubernetes API server
Example usage
2.6.1.107. oc registry login
Log in to the integrated registry
Example usage
# Log in to the integrated registry oc registry login # Log in to different registry using BASIC auth credentials oc registry login --registry quay.io/myregistry --auth-basic=USER:PASS
# Log in to the integrated registry
oc registry login
# Log in to different registry using BASIC auth credentials
oc registry login --registry quay.io/myregistry --auth-basic=USER:PASS2.6.1.108. oc replace
Replace a resource by file name or stdin
Example usage
2.6.1.109. oc rollback
Revert part of an application back to a previous deployment
Example usage
2.6.1.110. oc rollout cancel
Cancel the in-progress deployment
Example usage
# Cancel the in-progress deployment based on 'nginx' oc rollout cancel dc/nginx
# Cancel the in-progress deployment based on 'nginx'
oc rollout cancel dc/nginx2.6.1.111. oc rollout history
View rollout history
Example usage
# View the rollout history of a deployment oc rollout history dc/nginx # View the details of deployment revision 3 oc rollout history dc/nginx --revision=3
# View the rollout history of a deployment
oc rollout history dc/nginx
# View the details of deployment revision 3
oc rollout history dc/nginx --revision=32.6.1.112. oc rollout latest
Start a new rollout for a deployment config with the latest state from its triggers
Example usage
# Start a new rollout based on the latest images defined in the image change triggers oc rollout latest dc/nginx # Print the rolled out deployment config oc rollout latest dc/nginx -o json
# Start a new rollout based on the latest images defined in the image change triggers
oc rollout latest dc/nginx
# Print the rolled out deployment config
oc rollout latest dc/nginx -o json2.6.1.113. oc rollout pause
Mark the provided resource as paused
Example usage
# Mark the nginx deployment as paused. Any current state of # the deployment will continue its function, new updates to the deployment will not # have an effect as long as the deployment is paused oc rollout pause dc/nginx
# Mark the nginx deployment as paused. Any current state of
# the deployment will continue its function, new updates to the deployment will not
# have an effect as long as the deployment is paused
oc rollout pause dc/nginx2.6.1.114. oc rollout restart
Restart a resource
Example usage
2.6.1.115. oc rollout resume
Resume a paused resource
Example usage
# Resume an already paused deployment oc rollout resume dc/nginx
# Resume an already paused deployment
oc rollout resume dc/nginx2.6.1.116. oc rollout retry
Retry the latest failed rollout
Example usage
# Retry the latest failed deployment based on 'frontend' # The deployer pod and any hook pods are deleted for the latest failed deployment oc rollout retry dc/frontend
# Retry the latest failed deployment based on 'frontend'
# The deployer pod and any hook pods are deleted for the latest failed deployment
oc rollout retry dc/frontend2.6.1.117. oc rollout status
Show the status of the rollout
Example usage
# Watch the status of the latest rollout oc rollout status dc/nginx
# Watch the status of the latest rollout
oc rollout status dc/nginx2.6.1.118. oc rollout undo
Undo a previous rollout
Example usage
# Roll back to the previous deployment oc rollout undo dc/nginx # Roll back to deployment revision 3. The replication controller for that version must exist oc rollout undo dc/nginx --to-revision=3
# Roll back to the previous deployment
oc rollout undo dc/nginx
# Roll back to deployment revision 3. The replication controller for that version must exist
oc rollout undo dc/nginx --to-revision=32.6.1.119. oc rsh
Start a shell session in a container
Example usage
2.6.1.120. oc rsync
Copy files between a local file system and a pod
Example usage
# Synchronize a local directory with a pod directory oc rsync ./local/dir/ POD:/remote/dir # Synchronize a pod directory with a local directory oc rsync POD:/remote/dir/ ./local/dir
# Synchronize a local directory with a pod directory
oc rsync ./local/dir/ POD:/remote/dir
# Synchronize a pod directory with a local directory
oc rsync POD:/remote/dir/ ./local/dir2.6.1.121. oc run
Run a particular image on the cluster
Example usage
2.6.1.122. oc scale
Set a new size for a deployment, replica set, or replication controller
Example usage
2.6.1.123. oc secrets link
Link secrets to a service account
Example usage
# Add an image pull secret to a service account to automatically use it for pulling pod images oc secrets link serviceaccount-name pull-secret --for=pull # Add an image pull secret to a service account to automatically use it for both pulling and pushing build images oc secrets link builder builder-image-secret --for=pull,mount
# Add an image pull secret to a service account to automatically use it for pulling pod images
oc secrets link serviceaccount-name pull-secret --for=pull
# Add an image pull secret to a service account to automatically use it for both pulling and pushing build images
oc secrets link builder builder-image-secret --for=pull,mount2.6.1.124. oc secrets unlink
Detach secrets from a service account
Example usage
# Unlink a secret currently associated with a service account oc secrets unlink serviceaccount-name secret-name another-secret-name ...
# Unlink a secret currently associated with a service account
oc secrets unlink serviceaccount-name secret-name another-secret-name ...2.6.1.125. oc set build-hook
Update a build hook on a build config
Example usage
2.6.1.126. oc set build-secret
Update a build secret on a build config
Example usage
2.6.1.127. oc set data
Update the data within a config map or secret
Example usage
2.6.1.128. oc set deployment-hook
Update a deployment hook on a deployment config
Example usage
2.6.1.129. oc set env
Update environment variables on a pod template
Example usage
2.6.1.130. oc set image
Update the image of a pod template
Example usage
2.6.1.131. oc set image-lookup
Change how images are resolved when deploying applications
Example usage
2.6.1.132. oc set probe
Update a probe on a pod template
Example usage
2.6.1.133. oc set resources
Update resource requests/limits on objects with pod templates
Example usage
2.6.1.134. oc set route-backends
Update the backends for a route
Example usage
2.6.1.135. oc set selector
Set the selector on a resource
Example usage
# Set the labels and selector before creating a deployment/service pair. oc create service clusterip my-svc --clusterip="None" -o yaml --dry-run | oc set selector --local -f - 'environment=qa' -o yaml | oc create -f - oc create deployment my-dep -o yaml --dry-run | oc label --local -f - environment=qa -o yaml | oc create -f -
# Set the labels and selector before creating a deployment/service pair.
oc create service clusterip my-svc --clusterip="None" -o yaml --dry-run | oc set selector --local -f - 'environment=qa' -o yaml | oc create -f -
oc create deployment my-dep -o yaml --dry-run | oc label --local -f - environment=qa -o yaml | oc create -f -2.6.1.136. oc set serviceaccount
Update the service account of a resource
Example usage
# Set deployment nginx-deployment's service account to serviceaccount1 oc set serviceaccount deployment nginx-deployment serviceaccount1 # Print the result (in YAML format) of updated nginx deployment with service account from a local file, without hitting the API server oc set sa -f nginx-deployment.yaml serviceaccount1 --local --dry-run -o yaml
# Set deployment nginx-deployment's service account to serviceaccount1
oc set serviceaccount deployment nginx-deployment serviceaccount1
# Print the result (in YAML format) of updated nginx deployment with service account from a local file, without hitting the API server
oc set sa -f nginx-deployment.yaml serviceaccount1 --local --dry-run -o yaml2.6.1.137. oc set subject
Update the user, group, or service account in a role binding or cluster role binding
Example usage
2.6.1.138. oc set triggers
Update the triggers on one or more objects
Example usage
2.6.1.139. oc set volumes
Update volumes on a pod template
Example usage
2.6.1.140. oc start-build
Start a new build
Example usage
2.6.1.141. oc status
Show an overview of the current project
Example usage
2.6.1.142. oc tag
Tag existing images into image streams
Example usage
2.6.1.143. oc version
Print the client and server version information
Example usage
2.6.1.144. oc wait
Experimental: Wait for a specific condition on one or many resources
Example usage
2.6.1.145. oc whoami
Return information about the current session
Example usage
# Display the currently authenticated user oc whoami
# Display the currently authenticated user
oc whoami2.7. OpenShift CLI administrator command reference
This reference provides descriptions and example commands for OpenShift CLI (oc) administrator commands. You must have cluster-admin or equivalent permissions to use these commands.
For developer commands, see the OpenShift CLI developer command reference.
Run oc adm -h to list all administrator commands or run oc <command> --help to get additional details for a specific command.
2.7.1. OpenShift CLI (oc) administrator commands
2.7.1.1. oc adm build-chain
Output the inputs and dependencies of your builds
Example usage
2.7.1.2. oc adm catalog mirror
Mirror an operator-registry catalog
Example usage
2.7.1.3. oc adm certificate approve
Approve a certificate signing request
Example usage
# Approve CSR 'csr-sqgzp' oc adm certificate approve csr-sqgzp
# Approve CSR 'csr-sqgzp'
oc adm certificate approve csr-sqgzp2.7.1.4. oc adm certificate deny
Deny a certificate signing request
Example usage
# Deny CSR 'csr-sqgzp' oc adm certificate deny csr-sqgzp
# Deny CSR 'csr-sqgzp'
oc adm certificate deny csr-sqgzp2.7.1.5. oc adm copy-to-node
Copy specified files to the node
Example usage
# Copy a new bootstrap kubeconfig file to node-0 oc adm copy-to-node --copy=new-bootstrap-kubeconfig=/etc/kubernetes/kubeconfig node/node-0
# Copy a new bootstrap kubeconfig file to node-0
oc adm copy-to-node --copy=new-bootstrap-kubeconfig=/etc/kubernetes/kubeconfig node/node-02.7.1.6. oc adm cordon
Mark node as unschedulable
Example usage
# Mark node "foo" as unschedulable oc adm cordon foo
# Mark node "foo" as unschedulable
oc adm cordon foo2.7.1.7. oc adm create-bootstrap-project-template
Create a bootstrap project template
Example usage
# Output a bootstrap project template in YAML format to stdout oc adm create-bootstrap-project-template -o yaml
# Output a bootstrap project template in YAML format to stdout
oc adm create-bootstrap-project-template -o yaml2.7.1.8. oc adm create-error-template
Create an error page template
Example usage
# Output a template for the error page to stdout oc adm create-error-template
# Output a template for the error page to stdout
oc adm create-error-template2.7.1.9. oc adm create-login-template
Create a login template
Example usage
# Output a template for the login page to stdout oc adm create-login-template
# Output a template for the login page to stdout
oc adm create-login-template2.7.1.10. oc adm create-provider-selection-template
Create a provider selection template
Example usage
# Output a template for the provider selection page to stdout oc adm create-provider-selection-template
# Output a template for the provider selection page to stdout
oc adm create-provider-selection-template2.7.1.11. oc adm drain
Drain node in preparation for maintenance
Example usage
# Drain node "foo", even if there are pods not managed by a replication controller, replica set, job, daemon set, or stateful set on it oc adm drain foo --force # As above, but abort if there are pods not managed by a replication controller, replica set, job, daemon set, or stateful set, and use a grace period of 15 minutes oc adm drain foo --grace-period=900
# Drain node "foo", even if there are pods not managed by a replication controller, replica set, job, daemon set, or stateful set on it
oc adm drain foo --force
# As above, but abort if there are pods not managed by a replication controller, replica set, job, daemon set, or stateful set, and use a grace period of 15 minutes
oc adm drain foo --grace-period=9002.7.1.12. oc adm groups add-users
Add users to a group
Example usage
# Add user1 and user2 to my-group oc adm groups add-users my-group user1 user2
# Add user1 and user2 to my-group
oc adm groups add-users my-group user1 user22.7.1.13. oc adm groups new
Create a new group
Example usage
2.7.1.14. oc adm groups prune
Remove old OpenShift groups referencing missing records from an external provider
Example usage
2.7.1.15. oc adm groups remove-users
Remove users from a group
Example usage
# Remove user1 and user2 from my-group oc adm groups remove-users my-group user1 user2
# Remove user1 and user2 from my-group
oc adm groups remove-users my-group user1 user22.7.1.16. oc adm groups sync
Sync OpenShift groups with records from an external provider
Example usage
2.7.1.17. oc adm inspect
Collect debugging data for a given resource
Example usage
2.7.1.18. oc adm migrate icsp
Update imagecontentsourcepolicy file(s) to imagedigestmirrorset file(s)
Example usage
# Update the imagecontentsourcepolicy.yaml file to a new imagedigestmirrorset file under the mydir directory oc adm migrate icsp imagecontentsourcepolicy.yaml --dest-dir mydir
# Update the imagecontentsourcepolicy.yaml file to a new imagedigestmirrorset file under the mydir directory
oc adm migrate icsp imagecontentsourcepolicy.yaml --dest-dir mydir2.7.1.19. oc adm migrate template-instances
Update template instances to point to the latest group-version-kinds
Example usage
# Perform a dry-run of updating all objects oc adm migrate template-instances # To actually perform the update, the confirm flag must be appended oc adm migrate template-instances --confirm
# Perform a dry-run of updating all objects
oc adm migrate template-instances
# To actually perform the update, the confirm flag must be appended
oc adm migrate template-instances --confirm2.7.1.20. oc adm must-gather
Launch a new instance of a pod for gathering debug information
Example usage
2.7.1.21. oc adm new-project
Create a new project
Example usage
# Create a new project using a node selector oc adm new-project myproject --node-selector='type=user-node,region=east'
# Create a new project using a node selector
oc adm new-project myproject --node-selector='type=user-node,region=east'2.7.1.22. oc adm node-image create
Create an ISO image for booting the nodes to be added to the target cluster
Example usage
2.7.1.23. oc adm node-image monitor
Monitor new nodes being added to an OpenShift cluster
Example usage
2.7.1.24. oc adm node-logs
Display and filter node logs
Example usage
2.7.1.25. oc adm ocp-certificates monitor-certificates
Watch platform certificates
Example usage
# Watch platform certificates oc adm ocp-certificates monitor-certificates
# Watch platform certificates
oc adm ocp-certificates monitor-certificates2.7.1.26. oc adm ocp-certificates regenerate-leaf
Regenerate client and serving certificates of an OpenShift cluster
Example usage
# Regenerate a leaf certificate contained in a particular secret oc adm ocp-certificates regenerate-leaf -n openshift-config-managed secret/kube-controller-manager-client-cert-key
# Regenerate a leaf certificate contained in a particular secret
oc adm ocp-certificates regenerate-leaf -n openshift-config-managed secret/kube-controller-manager-client-cert-key2.7.1.27. oc adm ocp-certificates regenerate-machine-config-server-serving-cert
Regenerate the machine config operator certificates in an OpenShift cluster
Example usage
# Regenerate the MCO certs without modifying user-data secrets oc adm ocp-certificates regenerate-machine-config-server-serving-cert --update-ignition=false # Update the user-data secrets to use new MCS certs oc adm ocp-certificates update-ignition-ca-bundle-for-machine-config-server
# Regenerate the MCO certs without modifying user-data secrets
oc adm ocp-certificates regenerate-machine-config-server-serving-cert --update-ignition=false
# Update the user-data secrets to use new MCS certs
oc adm ocp-certificates update-ignition-ca-bundle-for-machine-config-server2.7.1.28. oc adm ocp-certificates regenerate-top-level
Regenerate the top level certificates in an OpenShift cluster
Example usage
# Regenerate the signing certificate contained in a particular secret oc adm ocp-certificates regenerate-top-level -n openshift-kube-apiserver-operator secret/loadbalancer-serving-signer-key
# Regenerate the signing certificate contained in a particular secret
oc adm ocp-certificates regenerate-top-level -n openshift-kube-apiserver-operator secret/loadbalancer-serving-signer-key2.7.1.29. oc adm ocp-certificates remove-old-trust
Remove old CAs from ConfigMaps representing platform trust bundles in an OpenShift cluster
Example usage
# Remove a trust bundled contained in a particular config map oc adm ocp-certificates remove-old-trust -n openshift-config-managed configmaps/kube-apiserver-aggregator-client-ca --created-before 2023-06-05T14:44:06Z # Remove only CA certificates created before a certain date from all trust bundles oc adm ocp-certificates remove-old-trust configmaps -A --all --created-before 2023-06-05T14:44:06Z
# Remove a trust bundled contained in a particular config map
oc adm ocp-certificates remove-old-trust -n openshift-config-managed configmaps/kube-apiserver-aggregator-client-ca --created-before 2023-06-05T14:44:06Z
# Remove only CA certificates created before a certain date from all trust bundles
oc adm ocp-certificates remove-old-trust configmaps -A --all --created-before 2023-06-05T14:44:06Z2.7.1.30. oc adm ocp-certificates update-ignition-ca-bundle-for-machine-config-server
Update user-data secrets in an OpenShift cluster to use updated MCO certfs
Example usage
# Regenerate the MCO certs without modifying user-data secrets oc adm ocp-certificates regenerate-machine-config-server-serving-cert --update-ignition=false # Update the user-data secrets to use new MCS certs oc adm ocp-certificates update-ignition-ca-bundle-for-machine-config-server
# Regenerate the MCO certs without modifying user-data secrets
oc adm ocp-certificates regenerate-machine-config-server-serving-cert --update-ignition=false
# Update the user-data secrets to use new MCS certs
oc adm ocp-certificates update-ignition-ca-bundle-for-machine-config-server2.7.1.31. oc adm pod-network isolate-projects
Isolate project network
Example usage
# Provide isolation for project p1 oc adm pod-network isolate-projects <p1> # Allow all projects with label name=top-secret to have their own isolated project network oc adm pod-network isolate-projects --selector='name=top-secret'
# Provide isolation for project p1
oc adm pod-network isolate-projects <p1>
# Allow all projects with label name=top-secret to have their own isolated project network
oc adm pod-network isolate-projects --selector='name=top-secret'2.7.1.32. oc adm pod-network join-projects
Join project network
Example usage
# Allow project p2 to use project p1 network oc adm pod-network join-projects --to=<p1> <p2> # Allow all projects with label name=top-secret to use project p1 network oc adm pod-network join-projects --to=<p1> --selector='name=top-secret'
# Allow project p2 to use project p1 network
oc adm pod-network join-projects --to=<p1> <p2>
# Allow all projects with label name=top-secret to use project p1 network
oc adm pod-network join-projects --to=<p1> --selector='name=top-secret'2.7.1.33. oc adm pod-network make-projects-global
Make project network global
Example usage
# Allow project p1 to access all pods in the cluster and vice versa oc adm pod-network make-projects-global <p1> # Allow all projects with label name=share to access all pods in the cluster and vice versa oc adm pod-network make-projects-global --selector='name=share'
# Allow project p1 to access all pods in the cluster and vice versa
oc adm pod-network make-projects-global <p1>
# Allow all projects with label name=share to access all pods in the cluster and vice versa
oc adm pod-network make-projects-global --selector='name=share'2.7.1.34. oc adm policy add-cluster-role-to-group
Add a role to groups for all projects in the cluster
Example usage
# Add the 'cluster-admin' cluster role to the 'cluster-admins' group oc adm policy add-cluster-role-to-group cluster-admin cluster-admins
# Add the 'cluster-admin' cluster role to the 'cluster-admins' group
oc adm policy add-cluster-role-to-group cluster-admin cluster-admins2.7.1.35. oc adm policy add-cluster-role-to-user
Add a role to users for all projects in the cluster
Example usage
# Add the 'system:build-strategy-docker' cluster role to the 'devuser' user oc adm policy add-cluster-role-to-user system:build-strategy-docker devuser
# Add the 'system:build-strategy-docker' cluster role to the 'devuser' user
oc adm policy add-cluster-role-to-user system:build-strategy-docker devuser2.7.1.36. oc adm policy add-role-to-user
Add a role to users or service accounts for the current project
Example usage
# Add the 'view' role to user1 for the current project oc adm policy add-role-to-user view user1 # Add the 'edit' role to serviceaccount1 for the current project oc adm policy add-role-to-user edit -z serviceaccount1
# Add the 'view' role to user1 for the current project
oc adm policy add-role-to-user view user1
# Add the 'edit' role to serviceaccount1 for the current project
oc adm policy add-role-to-user edit -z serviceaccount12.7.1.37. oc adm policy add-scc-to-group
Add a security context constraint to groups
Example usage
# Add the 'restricted' security context constraint to group1 and group2 oc adm policy add-scc-to-group restricted group1 group2
# Add the 'restricted' security context constraint to group1 and group2
oc adm policy add-scc-to-group restricted group1 group22.7.1.38. oc adm policy add-scc-to-user
Add a security context constraint to users or a service account
Example usage
# Add the 'restricted' security context constraint to user1 and user2 oc adm policy add-scc-to-user restricted user1 user2 # Add the 'privileged' security context constraint to serviceaccount1 in the current namespace oc adm policy add-scc-to-user privileged -z serviceaccount1
# Add the 'restricted' security context constraint to user1 and user2
oc adm policy add-scc-to-user restricted user1 user2
# Add the 'privileged' security context constraint to serviceaccount1 in the current namespace
oc adm policy add-scc-to-user privileged -z serviceaccount12.7.1.39. oc adm policy remove-cluster-role-from-group
Remove a role from groups for all projects in the cluster
Example usage
# Remove the 'cluster-admin' cluster role from the 'cluster-admins' group oc adm policy remove-cluster-role-from-group cluster-admin cluster-admins
# Remove the 'cluster-admin' cluster role from the 'cluster-admins' group
oc adm policy remove-cluster-role-from-group cluster-admin cluster-admins2.7.1.40. oc adm policy remove-cluster-role-from-user
Remove a role from users for all projects in the cluster
Example usage
# Remove the 'system:build-strategy-docker' cluster role from the 'devuser' user oc adm policy remove-cluster-role-from-user system:build-strategy-docker devuser
# Remove the 'system:build-strategy-docker' cluster role from the 'devuser' user
oc adm policy remove-cluster-role-from-user system:build-strategy-docker devuser2.7.1.41. oc adm policy scc-review
Check which service account can create a pod
Example usage
2.7.1.42. oc adm policy scc-subject-review
Check whether a user or a service account can create a pod
Example usage
2.7.1.43. oc adm prune builds
Remove old completed and failed builds
Example usage
2.7.1.44. oc adm prune deployments
Remove old completed and failed deployment configs
Example usage
# Dry run deleting all but the last complete deployment for every deployment config oc adm prune deployments --keep-complete=1 # To actually perform the prune operation, the confirm flag must be appended oc adm prune deployments --keep-complete=1 --confirm
# Dry run deleting all but the last complete deployment for every deployment config
oc adm prune deployments --keep-complete=1
# To actually perform the prune operation, the confirm flag must be appended
oc adm prune deployments --keep-complete=1 --confirm2.7.1.45. oc adm prune groups
Remove old OpenShift groups referencing missing records from an external provider
Example usage
2.7.1.46. oc adm prune images
Remove unreferenced images
Example usage
2.7.1.47. oc adm prune renderedmachineconfigs
Prunes rendered MachineConfigs in an OpenShift cluster
Example usage
2.7.1.48. oc adm prune renderedmachineconfigs list
Lists rendered MachineConfigs in an OpenShift cluster
Example usage
# List all rendered MachineConfigs for the worker MachineConfigPool in the cluster oc adm prune renderedmachineconfigs list --pool-name=worker # List all rendered MachineConfigs in use by the cluster's MachineConfigPools oc adm prune renderedmachineconfigs list --in-use
# List all rendered MachineConfigs for the worker MachineConfigPool in the cluster
oc adm prune renderedmachineconfigs list --pool-name=worker
# List all rendered MachineConfigs in use by the cluster's MachineConfigPools
oc adm prune renderedmachineconfigs list --in-use2.7.1.49. oc adm reboot-machine-config-pool
Initiate reboot of the specified MachineConfigPool
Example usage
2.7.1.50. oc adm release extract
Extract the contents of an update payload to disk
Example usage
2.7.1.51. oc adm release info
Display information about a release
Example usage
2.7.1.52. oc adm release mirror
Mirror a release to a different image registry location
Example usage
2.7.1.53. oc adm release new
Create a new OpenShift release
Example usage
2.7.1.54. oc adm restart-kubelet
Restart kubelet on the specified nodes
Example usage
2.7.1.55. oc adm taint
Update the taints on one or more nodes
Example usage
2.7.1.56. oc adm top images
Show usage statistics for images
Example usage
# Show usage statistics for images oc adm top images
# Show usage statistics for images
oc adm top images2.7.1.57. oc adm top imagestreams
Show usage statistics for image streams
Example usage
# Show usage statistics for image streams oc adm top imagestreams
# Show usage statistics for image streams
oc adm top imagestreams2.7.1.58. oc adm top node
Display resource (CPU/memory) usage of nodes
Example usage
# Show metrics for all nodes oc adm top node # Show metrics for a given node oc adm top node NODE_NAME
# Show metrics for all nodes
oc adm top node
# Show metrics for a given node
oc adm top node NODE_NAME2.7.1.59. oc adm top pod
Display resource (CPU/memory) usage of pods
Example usage
2.7.1.60. oc adm uncordon
Mark node as schedulable
Example usage
# Mark node "foo" as schedulable oc adm uncordon foo
# Mark node "foo" as schedulable
oc adm uncordon foo2.7.1.61. oc adm upgrade
Upgrade a cluster or adjust the upgrade channel
Example usage
# View the update status and available cluster updates oc adm upgrade # Update to the latest version oc adm upgrade --to-latest=true
# View the update status and available cluster updates
oc adm upgrade
# Update to the latest version
oc adm upgrade --to-latest=true2.7.1.62. oc adm verify-image-signature
Verify the image identity contained in the image signature
Example usage
2.7.1.63. oc adm wait-for-node-reboot
Wait for nodes to reboot after running oc adm reboot-machine-config-pool
Example usage
2.7.1.64. oc adm wait-for-stable-cluster
Wait for the platform operators to become stable
Example usage
# Wait for all cluster operators to become stable oc adm wait-for-stable-cluster # Consider operators to be stable if they report as such for 5 minutes straight oc adm wait-for-stable-cluster --minimum-stable-period 5m
# Wait for all cluster operators to become stable
oc adm wait-for-stable-cluster
# Consider operators to be stable if they report as such for 5 minutes straight
oc adm wait-for-stable-cluster --minimum-stable-period 5mChapter 3. OpenShift CLI Manager
3.1. CLI Manager Operator overview
To install and update CLI plugins in both connected and disconnected environments, you can use the CLI Manager Operator.
Using the CLI Manager Operator to install and manage plugins for the OpenShift CLI is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope.
3.1.1. About the CLI Manager Operator
You can use the CLI Manager Operator to streamline the installation and management of CLI plugins, especially in disconnected environments.
The CLI Manager Operator makes it easier to install and update CLI plugins. It runs in both connected and disconnected environments, and it is particularly useful in disconnected environments. Cluster administrators can add CLI plugins and plugin updates to the CLI Manager Operator, and users can then install and update CLI plugins when needed regardless of whether or not the environment is disconnected.
3.2. CLI Manager Operator release notes
Track the development of the CLI Manager Operator for OpenShift Container Platform, which enables you to install CLI plugins in both connected and disconnected environments.
Using the CLI Manager Operator to install and manage plugins for the OpenShift CLI is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope.
3.2.1. CLI Manager Operator 0.2.0 (Technology Preview)
Review the features, enhancements, and advisory for the Technology Preview release of CLI Manager Operator 0.2.0.
Issued: 9 December 2025
The following advisory is available for the CLI Manager Operator 0.2.0:
3.2.1.1. New features and enhancements
- This release of the CLI Manager Operator updates the Kubernetes version to 1.34.
-
The
readOnlyRootFilesystemflag is set totruefor additional hardening of OpenShift Container Platform pods.
3.2.2. CLI Manager Operator 0.1.1 (Technology Preview)
Review the features, enhancements, and advisory for the Technology Preview release of CLI Manager Operator 0.1.1.
Issued: 12 March 2025
The following advisory is available for the CLI Manager Operator 0.1.1:
3.2.2.1. New features and enhancements
This release of the CLI Manager updates the Kubernetes version to 1.32.
3.2.3. CLI Manager Operator 0.1.0 (Technology Preview)
Review the features, enhancements, and advisory for the initial Technology Preview release of CLI Manager Operator 0.1.0.
Issued: 19 November 2024
The following advisory is available for the CLI Manager Operator 0.1.0:
3.2.3.1. New features and enhancements
- This version is the initial Technology Preview release of the CLI Manager Operator. For installation information, see Installing the CLI Manager Operator.
Additional resources
3.3. Installing the CLI Manager Operator
You can simplify the installation and management of CLI plugins in connected and disconnected environments with the CLI Manager Operator. The CLI Manager Operator makes Krew compatible with the oc CLI, allowing cluster administrators to manage custom CLI plugin resources.
Using the CLI Manager Operator to install and manage plugins for the OpenShift CLI is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope.
3.3.1. Installing the CLI Manager Operator
You can install the CLI Manager Operator to facilitate adding CLI plugins in both connected and disconnected environments.
Krew always works with OpenShift CLI (oc) without the CLI Manager Operator installed. You can use the same commands outlined in this documentation to use Krew with oc. For more information, see Krew documentation.
Prerequisites
- Krew is installed.
-
You are logged in to OpenShift Container Platform as a user with the
cluster-adminrole. - You have access to the OpenShift Container Platform web console.
Procedure
- Log in to the OpenShift Container Platform web console.
Create the required namespace for the CLI Manager Operator:
- Navigate to Administration → Namespaces and click Create Namespace.
-
In the Name field, enter
openshift-cli-manager-operatorand click Create.
Install the CLI Manager Operator:
- Navigate to Operators → OperatorHub.
- In the filter box, enter CLI Manager Operator.
- Select the CLI Manager Operator and click Install.
On the Install Operator page, complete the following steps:
- Ensure that the Update channel is set to tech preview, which installs the latest Technology Preview release of the CLI Manager Operator.
- From the drop-down menu, select A specific namespace on the cluster and select openshift-cli-manager-operator.
- Click Install.
Create the
CliManagerresource by completing the following steps:- Navigate to Installed Operators.
- Select CLI Manager Operator.
- Select the CLI Manager tab.
- Click Create CliManager.
- Use the default Name.
Click Create.
-
The new
CliManagerresource is listed in the CLI Manager tab.
-
The new
Verification
- Navigate to Operators → Installed Operators.
- Verify that CLI Manager Operator is listed with a Status of Succeeded.
3.3.2. Adding the CLI Manager Operator custom index to Krew
You can use the terminal to add the CLI Manager Operator custom index to Krew so that the CLI Manager Operator will work in disconnected environments. This procedure is required for the CLI Manager Operator to function correctly and needs to be done only once.
If you use self-signed certificates, mark the certificate as trusted on your local operating system to use Krew.
Prerequisites
- Krew is installed.
- The CLI Manager Operator is installed.
Procedure
To establish the
ROUTEvariable, enter the following command:ROUTE=$(oc get route/openshift-cli-manager -n openshift-cli-manager-operator -o=jsonpath='{.spec.host}')$ ROUTE=$(oc get route/openshift-cli-manager -n openshift-cli-manager-operator -o=jsonpath='{.spec.host}')Copy to Clipboard Copied! Toggle word wrap Toggle overflow To add the custom index to Krew, enter the following command:
oc krew index add <custom_index_name> https://$ROUTE/cli-manager
$ oc krew index add <custom_index_name> https://$ROUTE/cli-managerCopy to Clipboard Copied! Toggle word wrap Toggle overflow To update Krew, enter the following command and check for any errors:
oc krew update
$ oc krew updateCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Updated the local copy of plugin index. Updated the local copy of plugin index <custom_index_name>. New plugins available: * ocp/<plugin_name>
Updated the local copy of plugin index. Updated the local copy of plugin index <custom_index_name>. New plugins available: * ocp/<plugin_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.3.3. Adding a plugin to the CLI Manager Operator
You can add a CLI plugin to the CLI Manager Operator by creating a new plugin resource in the OpenShift Container Platform web console’s YAML view.
Prerequisites
-
You are logged in to OpenShift Container Platform as a user with the
cluster-adminrole. - The CLI Manager Operator is installed.
Procedure
- Log in to the OpenShift Container Platform web console.
- Navigate to Operators → Installed Operators.
- From the list, select CLI Manager Operator.
- Select the CLI Plugin tab.
- Click Create Plugin.
In the text box, enter the information for the plugin you are installing. See the following example YAML file.
Example YAML file to add a plugin
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<plugin_name>- Specifies the name of the plugin you plan to use in commands.
bin- Specifies the path to the plugin executable.
imagePullSecret- Optional field if the registry is not public to add a pull secret to access your plugin image.
<platform>-
Add the architecture for your system; for example,
linux/amd64,darwin/arm64,windows/amd64, or another architecture. <version>- The version must be in v0.0.0 format.
- Click Save.
Verification
- Enter the following command to see if the plugin is listed and has been added successfully:
oc get plugin/<plugin_name> -o yaml
$ oc get plugin/<plugin_name> -o yaml- Example output:
<plugin_name> ready to be served.
<plugin_name> ready to be served.3.4. Using the CLI Manager Operator
To install, update, and uninstall CLI plugins in OpenShift Container Platform, you can set up and configure the CLI Manager Operator.
Using the CLI Manager Operator to install and manage plugins for the OpenShift CLI is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope.
3.4.1. Installing CLI plugins with the CLI Manager Operator
You can install CLI plugins with the CLI Manager Operator to extend OpenShift CLI functionality in both connected and disconnected environments.
Prerequisites
- You have installed Krew by following the installation procedure in the Krew documentation.
- The CLI Manager Operator is installed.
- The CLI Manager Operator custom index has been added to Krew.
- You are using OpenShift Container Platform 4.17 or later.
Procedure
To list all available plugins, run the following command:
oc krew search
$ oc krew searchCopy to Clipboard Copied! Toggle word wrap Toggle overflow To get information about a plugin, run the following command:
oc krew info <plugin_name>
$ oc krew info <plugin_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow To install a plugin, run the following command:
oc krew install <plugin_name>
$ oc krew install <plugin_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow To list all plugins that were installed by Krew, run the following command:
oc krew list
$ oc krew listCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.4.2. Upgrading a plugin with the CLI Manager Operator
You can upgrade a CLI plugin to a newer version with the CLI Manager Operator by directly editing the plugin’s resource YAML file.
Prerequisites
-
You are logged in to OpenShift Container Platform as a user with the
cluster-adminrole. - The CLI Manager Operator is installed.
- The plugin you are upgrading is installed.
Procedure
Using the CLI, enter the following command:
oc edit plugin/<plugin_name>
oc edit plugin/<plugin_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the YAML file to include the new specifications for your plugin.
Example YAML file to upgrade a plugin
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<plugin_name>- Specifies the name of the plugin you plan to use in commands.
bin- Specifies the path to the plugin executable.
imagePullSecret- Optional field if the registry is not public to add a pull secret to access your plugin image.
<platform>-
Add the architecture for your system; for example,
linux/amd64,darwin/arm64,windows/amd64, or another architecture. <version>- The version must be in v0.0.0 format.
- Save the file.
3.4.3. Updating CLI plugins with the CLI Manager Operator
You can update a plugin that was installed for the OpenShift CLI (oc) with the CLI Manager Operator and Krew to keep your plugins current with the latest features.
Prerequisites
- You have installed Krew by following the installation procedure in the Krew documentation.
- The CLI Manager Operator is installed.
- The custom index has been added to Krew by the cluster administrator.
- The plugin updates have been added to the CLI Manager Operator by the cluster administrator.
- The plugin you are updating is already installed.
Procedure
To update a single plugin, run the following command:
oc krew upgrade <plugin_name>
$ oc krew upgrade <plugin_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow To update all plugins that were installed by Krew, run the following command:
oc krew upgrade
$ oc krew upgradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.4.4. Uninstalling a CLI plugin with the CLI Manager Operator
You can uninstall a plugin that was installed for the OpenShift CLI (oc) with the CLI Manager Operator.
Prerequisites
- You have installed Krew by following the installation procedure in the Krew documentation.
- You have installed a plugin for the OpenShift CLI with the CLI Manager Operator.
Procedure
To uninstall a plugin, run the following command:
oc krew uninstall <plugin_name>
$ oc krew uninstall <plugin_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.5. Uninstalling the CLI Manager Operator
You can remove the CLI Manager Operator from OpenShift Container Platform by uninstalling the CLI Manager Operator and removing its related resources.
Using the CLI Manager Operator to install and manage plugins for the OpenShift CLI is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope.
3.5.1. Uninstalling the CLI Manager Operator
You can uninstall the CLI Manager Operator by using the web console.
Prerequisites
-
You are logged in to OpenShift Container Platform as a user with the
cluster-adminrole. - You have access to the OpenShift Container Platform web console.
- The CLI Manager Operator is installed.
Procedure
- Log in to the OpenShift Container Platform web console.
Uninstall the CLI Manager Operator by completing the following steps:
- Navigate to Operators → Installed Operators.
-
Click the Options menu
 next to the CLI Manager Operator entry and click Uninstall Operator.
next to the CLI Manager Operator entry and click Uninstall Operator.
- In the confirmation dialog, click Uninstall.
3.5.2. Removing CLI Manager Operator resources
Optionally, after you uninstall the CLI Manager Operator, you can remove its related resources from your cluster.
Prerequisites
-
You are logged in to OpenShift Container Platform as a user with the
cluster-adminrole. - You have access to the OpenShift Container Platform web console.
Procedure
- Log in to the OpenShift Container Platform web console.
Remove the
openshift-cli-manager-operatornamespace:- Navigate to Administration → Namespaces.
-
Click the Options menu
 next to the openshift-cli-manager-operator entry and select Delete Namespace.
next to the openshift-cli-manager-operator entry and select Delete Namespace.
-
In the confirmation dialog, enter
openshift-cli-manager-operatorin the field and click Delete.
Chapter 4. Important update on odo
Red Hat does not provide information about odo on the OpenShift Container Platform documentation site. See the documentation maintained by Red Hat and the upstream community for documentation information related to odo.
For the materials maintained by the upstream community, Red Hat provides support under Cooperative Community Support.
Chapter 5. Knative CLI for use with OpenShift Serverless
The Knative (kn) CLI enables simple interaction with Knative components on OpenShift Container Platform.
5.1. Key features
The Knative (kn) CLI is designed to make serverless computing tasks simple and concise. Key features of the Knative CLI include:
- Deploy serverless applications from the command line.
- Manage features of Knative Serving, such as services, revisions, and traffic-splitting.
- Create and manage Knative Eventing components, such as event sources and triggers.
- Create sink bindings to connect existing Kubernetes applications and Knative services.
-
Extend the Knative CLI with flexible plugin architecture, similar to the
kubectlCLI. - Configure autoscaling parameters for Knative services.
- Scripted usage, such as waiting for the results of an operation, or deploying custom rollout and rollback strategies.
5.2. Installing the Knative CLI
Chapter 6. Pipelines CLI (tkn)
6.1. Installing tkn
Use the CLI tool to manage Red Hat OpenShift Pipelines from a terminal. The following section describes how to install the CLI tool on different platforms.
You can also find the URL to the latest binaries from the OpenShift Container Platform web console by clicking the ? icon in the upper-right corner and selecting Command Line Tools.
Both the archives and the RPMs contain the following executables:
-
tkn -
tkn-pac -
opc
Running Red Hat OpenShift Pipelines with the opc CLI tool is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope.
6.1.1. Installing the Red Hat OpenShift Pipelines CLI on Linux
For Linux distributions, you can download the CLI as a tar.gz archive.
Procedure
Download the relevant CLI tool.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Add the location of your
tkn,tkn-pac, andopcfiles to yourPATHenvironment variable. To check your
PATH, run the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.1.2. Installing the Red Hat OpenShift Pipelines CLI on Linux using an RPM
For Red Hat Enterprise Linux (RHEL) version 8, you can install the Red Hat OpenShift Pipelines CLI as an RPM.
Prerequisites
- You have an active OpenShift Container Platform subscription on your Red Hat account.
- You have root or sudo privileges on your local system.
Procedure
Register with Red Hat Subscription Manager:
subscription-manager register
# subscription-manager registerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Pull the latest subscription data:
subscription-manager refresh
# subscription-manager refreshCopy to Clipboard Copied! Toggle word wrap Toggle overflow List the available subscriptions:
subscription-manager list --available --matches '*pipelines*'
# subscription-manager list --available --matches '*pipelines*'Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the output for the previous command, find the pool ID for your OpenShift Container Platform subscription and attach the subscription to the registered system:
subscription-manager attach --pool=<pool_id>
# subscription-manager attach --pool=<pool_id>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the repositories required by Red Hat OpenShift Pipelines:
Linux (x86_64, amd64)
subscription-manager repos --enable="pipelines-1.18-for-rhel-8-x86_64-rpms"
# subscription-manager repos --enable="pipelines-1.18-for-rhel-8-x86_64-rpms"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Linux on IBM Z® and IBM® LinuxONE (s390x)
subscription-manager repos --enable="pipelines-1.18-for-rhel-8-s390x-rpms"
# subscription-manager repos --enable="pipelines-1.18-for-rhel-8-s390x-rpms"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Linux on IBM Power® (ppc64le)
subscription-manager repos --enable="pipelines-1.18-for-rhel-8-ppc64le-rpms"
# subscription-manager repos --enable="pipelines-1.18-for-rhel-8-ppc64le-rpms"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Linux on ARM (aarch64, arm64)
subscription-manager repos --enable="pipelines-1.18-for-rhel-8-aarch64-rpms"
# subscription-manager repos --enable="pipelines-1.18-for-rhel-8-aarch64-rpms"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Install the
openshift-pipelines-clientpackage:yum install openshift-pipelines-client
# yum install openshift-pipelines-clientCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the CLI, it is available using the tkn command:
tkn version
$ tkn version6.1.3. Installing the Red Hat OpenShift Pipelines CLI on Windows
For Windows, you can download the CLI as a zip archive.
Procedure
- Download the CLI tool.
- Extract the archive with a ZIP program.
-
Add the location of your
tkn,tkn-pac, andopcfiles to yourPATHenvironment variable. To check your
PATH, run the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.1.4. Installing the Red Hat OpenShift Pipelines CLI on macOS
For macOS, you can download the CLI as a tar.gz archive.
Procedure
Download the relevant CLI tool.
- Unpack and extract the archive.
-
Add the location of your
tkn,tkn-pac, andopcfiles to yourPATHenvironment variable. To check your
PATH, run the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.2. Configuring the OpenShift Pipelines tkn CLI
Configure the Red Hat OpenShift Pipelines tkn CLI to enable tab completion.
6.2.1. Enabling tab completion
After you install the tkn CLI, you can enable tab completion to automatically complete tkn commands or suggest options when you press Tab.
Prerequisites
-
You must have the
tknCLI tool installed. -
You must have
bash-completioninstalled on your local system.
Procedure
The following procedure enables tab completion for Bash.
Save the Bash completion code to a file:
tkn completion bash > tkn_bash_completion
$ tkn completion bash > tkn_bash_completionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy the file to
/etc/bash_completion.d/:sudo cp tkn_bash_completion /etc/bash_completion.d/
$ sudo cp tkn_bash_completion /etc/bash_completion.d/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can save the file to a local directory and source it from your
.bashrcfile instead.
Tab completion is enabled when you open a new terminal.
6.3. OpenShift Pipelines tkn reference
This section lists the basic tkn CLI commands.
6.3.1. Basic syntax
tkn [command or options] [arguments…]
6.3.2. Global options
--help, -h
6.3.3. Utility commands
6.3.3.1. tkn
Parent command for tkn CLI.
Example: Display all options
tkn
$ tkn6.3.3.2. completion [shell]
Print shell completion code which must be evaluated to provide interactive completion. Supported shells are bash and zsh.
Example: Completion code for bash shell
tkn completion bash
$ tkn completion bash6.3.3.3. version
Print version information of the tkn CLI.
Example: Check the tkn version
tkn version
$ tkn version6.3.4. Pipelines management commands
6.3.4.1. pipeline
Manage pipelines.
Example: Display help
tkn pipeline --help
$ tkn pipeline --help6.3.4.2. pipeline delete
Delete a pipeline.
Example: Delete the mypipeline pipeline from a namespace
tkn pipeline delete mypipeline -n myspace
$ tkn pipeline delete mypipeline -n myspace6.3.4.3. pipeline describe
Describe a pipeline.
Example: Describe the mypipeline pipeline
tkn pipeline describe mypipeline
$ tkn pipeline describe mypipeline6.3.4.4. pipeline list
Display a list of pipelines.
Example: Display a list of pipelines
tkn pipeline list
$ tkn pipeline list6.3.4.5. pipeline logs
Display the logs for a specific pipeline.
Example: Stream the live logs for the mypipeline pipeline
tkn pipeline logs -f mypipeline
$ tkn pipeline logs -f mypipeline6.3.4.6. pipeline start
Start a pipeline.
Example: Start the mypipeline pipeline
tkn pipeline start mypipeline
$ tkn pipeline start mypipeline6.3.5. Pipeline run commands
6.3.5.1. pipelinerun
Manage pipeline runs.
Example: Display help
tkn pipelinerun -h
$ tkn pipelinerun -h6.3.5.2. pipelinerun cancel
Cancel a pipeline run.
Example: Cancel the mypipelinerun pipeline run from a namespace
tkn pipelinerun cancel mypipelinerun -n myspace
$ tkn pipelinerun cancel mypipelinerun -n myspace6.3.5.3. pipelinerun delete
Delete a pipeline run.
Example: Delete pipeline runs from a namespace
tkn pipelinerun delete mypipelinerun1 mypipelinerun2 -n myspace
$ tkn pipelinerun delete mypipelinerun1 mypipelinerun2 -n myspaceExample: Delete all pipeline runs from a namespace, except the five most recently executed pipeline runs
tkn pipelinerun delete -n myspace --keep 5
$ tkn pipelinerun delete -n myspace --keep 5 Example: Delete all pipelines
tkn pipelinerun delete --all
$ tkn pipelinerun delete --all
Starting with Red Hat OpenShift Pipelines 1.6, the tkn pipelinerun delete --all command does not delete any resources that are in the running state.
6.3.5.4. pipelinerun describe
Describe a pipeline run.
Example: Describe the mypipelinerun pipeline run in a namespace
tkn pipelinerun describe mypipelinerun -n myspace
$ tkn pipelinerun describe mypipelinerun -n myspace6.3.5.5. pipelinerun list
List pipeline runs.
Example: Display a list of pipeline runs in a namespace
tkn pipelinerun list -n myspace
$ tkn pipelinerun list -n myspace6.3.5.6. pipelinerun logs
Display the logs of a pipeline run.
Example: Display the logs of the mypipelinerun pipeline run with all tasks and steps in a namespace
tkn pipelinerun logs mypipelinerun -a -n myspace
$ tkn pipelinerun logs mypipelinerun -a -n myspace6.3.6. Task management commands
6.3.6.1. task
Manage tasks.
Example: Display help
tkn task -h
$ tkn task -h6.3.6.2. task delete
Delete a task.
Example: Delete mytask1 and mytask2 tasks from a namespace
tkn task delete mytask1 mytask2 -n myspace
$ tkn task delete mytask1 mytask2 -n myspace6.3.6.3. task describe
Describe a task.
Example: Describe the mytask task in a namespace
tkn task describe mytask -n myspace
$ tkn task describe mytask -n myspace6.3.6.4. task list
List tasks.
Example: List all the tasks in a namespace
tkn task list -n myspace
$ tkn task list -n myspace6.3.6.5. task logs
Display task logs.
Example: Display logs for the mytaskrun task run of the mytask task
tkn task logs mytask mytaskrun -n myspace
$ tkn task logs mytask mytaskrun -n myspace6.3.6.6. task start
Start a task.
Example: Start the mytask task in a namespace
tkn task start mytask -s <ServiceAccountName> -n myspace
$ tkn task start mytask -s <ServiceAccountName> -n myspace6.3.7. Task run commands
6.3.7.1. taskrun
Manage task runs.
Example: Display help
tkn taskrun -h
$ tkn taskrun -h6.3.7.2. taskrun cancel
Cancel a task run.
Example: Cancel the mytaskrun task run from a namespace
tkn taskrun cancel mytaskrun -n myspace
$ tkn taskrun cancel mytaskrun -n myspace6.3.7.3. taskrun delete
Delete a TaskRun.
Example: Delete the mytaskrun1 and mytaskrun2 task runs from a namespace
tkn taskrun delete mytaskrun1 mytaskrun2 -n myspace
$ tkn taskrun delete mytaskrun1 mytaskrun2 -n myspaceExample: Delete all but the five most recently executed task runs from a namespace
tkn taskrun delete -n myspace --keep 5
$ tkn taskrun delete -n myspace --keep 5 - 1
- Replace
5with the number of most recently executed task runs you want to retain.
6.3.7.4. taskrun describe
Describe a task run.
Example: Describe the mytaskrun task run in a namespace
tkn taskrun describe mytaskrun -n myspace
$ tkn taskrun describe mytaskrun -n myspace6.3.7.5. taskrun list
List task runs.
Example: List all the task runs in a namespace
tkn taskrun list -n myspace
$ tkn taskrun list -n myspace6.3.7.6. taskrun logs
Display task run logs.
Example: Display live logs for the mytaskrun task run in a namespace
tkn taskrun logs -f mytaskrun -n myspace
$ tkn taskrun logs -f mytaskrun -n myspace6.3.8. Condition management commands
6.3.8.1. condition
Manage Conditions.
Example: Display help
tkn condition --help
$ tkn condition --help6.3.8.2. condition delete
Delete a Condition.
Example: Delete the mycondition1 Condition from a namespace
tkn condition delete mycondition1 -n myspace
$ tkn condition delete mycondition1 -n myspace6.3.8.3. condition describe
Describe a Condition.
Example: Describe the mycondition1 Condition in a namespace
tkn condition describe mycondition1 -n myspace
$ tkn condition describe mycondition1 -n myspace6.3.8.4. condition list
List Conditions.
Example: List Conditions in a namespace
tkn condition list -n myspace
$ tkn condition list -n myspace6.3.9. Pipeline Resource management commands
6.3.9.1. resource
Manage Pipeline Resources.
Example: Display help
tkn resource -h
$ tkn resource -h6.3.9.2. resource create
Create a Pipeline Resource.
Example: Create a Pipeline Resource in a namespace
tkn resource create -n myspace
$ tkn resource create -n myspaceThis is an interactive command that asks for input on the name of the Resource, type of the Resource, and the values based on the type of the Resource.
6.3.9.3. resource delete
Delete a Pipeline Resource.
Example: Delete the myresource Pipeline Resource from a namespace
tkn resource delete myresource -n myspace
$ tkn resource delete myresource -n myspace6.3.9.4. resource describe
Describe a Pipeline Resource.
Example: Describe the myresource Pipeline Resource
tkn resource describe myresource -n myspace
$ tkn resource describe myresource -n myspace6.3.9.5. resource list
List Pipeline Resources.
Example: List all Pipeline Resources in a namespace
tkn resource list -n myspace
$ tkn resource list -n myspace6.3.10. ClusterTask management commands
In Red Hat OpenShift Pipelines 1.10, ClusterTask functionality of the tkn command-line utility is deprecated and is planned to be removed in a future release.
6.3.10.1. clustertask
Manage ClusterTasks.
Example: Display help
tkn clustertask --help
$ tkn clustertask --help6.3.10.2. clustertask delete
Delete a ClusterTask resource in a cluster.
Example: Delete mytask1 and mytask2 ClusterTasks
tkn clustertask delete mytask1 mytask2
$ tkn clustertask delete mytask1 mytask26.3.10.3. clustertask describe
Describe a ClusterTask.
Example: Describe the mytask ClusterTask
tkn clustertask describe mytask1
$ tkn clustertask describe mytask16.3.10.4. clustertask list
List ClusterTasks.
Example: List ClusterTasks
tkn clustertask list
$ tkn clustertask list6.3.10.5. clustertask start
Start ClusterTasks.
Example: Start the mytask ClusterTask
tkn clustertask start mytask
$ tkn clustertask start mytask6.3.11. Trigger management commands
6.3.11.1. eventlistener
Manage EventListeners.
Example: Display help
tkn eventlistener -h
$ tkn eventlistener -h6.3.11.2. eventlistener delete
Delete an EventListener.
Example: Delete mylistener1 and mylistener2 EventListeners in a namespace
tkn eventlistener delete mylistener1 mylistener2 -n myspace
$ tkn eventlistener delete mylistener1 mylistener2 -n myspace6.3.11.3. eventlistener describe
Describe an EventListener.
Example: Describe the mylistener EventListener in a namespace
tkn eventlistener describe mylistener -n myspace
$ tkn eventlistener describe mylistener -n myspace6.3.11.4. eventlistener list
List EventListeners.
Example: List all the EventListeners in a namespace
tkn eventlistener list -n myspace
$ tkn eventlistener list -n myspace6.3.11.5. eventlistener logs
Display logs of an EventListener.
Example: Display the logs of the mylistener EventListener in a namespace
tkn eventlistener logs mylistener -n myspace
$ tkn eventlistener logs mylistener -n myspace6.3.11.6. triggerbinding
Manage TriggerBindings.
Example: Display TriggerBindings help
tkn triggerbinding -h
$ tkn triggerbinding -h6.3.11.7. triggerbinding delete
Delete a TriggerBinding.
Example: Delete mybinding1 and mybinding2 TriggerBindings in a namespace
tkn triggerbinding delete mybinding1 mybinding2 -n myspace
$ tkn triggerbinding delete mybinding1 mybinding2 -n myspace6.3.11.8. triggerbinding describe
Describe a TriggerBinding.
Example: Describe the mybinding TriggerBinding in a namespace
tkn triggerbinding describe mybinding -n myspace
$ tkn triggerbinding describe mybinding -n myspace6.3.11.9. triggerbinding list
List TriggerBindings.
Example: List all the TriggerBindings in a namespace
tkn triggerbinding list -n myspace
$ tkn triggerbinding list -n myspace6.3.11.10. triggertemplate
Manage TriggerTemplates.
Example: Display TriggerTemplate help
tkn triggertemplate -h
$ tkn triggertemplate -h6.3.11.11. triggertemplate delete
Delete a TriggerTemplate.
Example: Delete mytemplate1 and mytemplate2 TriggerTemplates in a namespace
tkn triggertemplate delete mytemplate1 mytemplate2 -n `myspace`
$ tkn triggertemplate delete mytemplate1 mytemplate2 -n `myspace`6.3.11.12. triggertemplate describe
Describe a TriggerTemplate.
Example: Describe the mytemplate TriggerTemplate in a namespace
tkn triggertemplate describe mytemplate -n `myspace`
$ tkn triggertemplate describe mytemplate -n `myspace`6.3.11.13. triggertemplate list
List TriggerTemplates.
Example: List all the TriggerTemplates in a namespace
tkn triggertemplate list -n myspace
$ tkn triggertemplate list -n myspace6.3.11.14. clustertriggerbinding
Manage ClusterTriggerBindings.
Example: Display ClusterTriggerBindings help
tkn clustertriggerbinding -h
$ tkn clustertriggerbinding -h6.3.11.15. clustertriggerbinding delete
Delete a ClusterTriggerBinding.
Example: Delete myclusterbinding1 and myclusterbinding2 ClusterTriggerBindings
tkn clustertriggerbinding delete myclusterbinding1 myclusterbinding2
$ tkn clustertriggerbinding delete myclusterbinding1 myclusterbinding26.3.11.16. clustertriggerbinding describe
Describe a ClusterTriggerBinding.
Example: Describe the myclusterbinding ClusterTriggerBinding
tkn clustertriggerbinding describe myclusterbinding
$ tkn clustertriggerbinding describe myclusterbinding6.3.11.17. clustertriggerbinding list
List ClusterTriggerBindings.
Example: List all ClusterTriggerBindings
tkn clustertriggerbinding list
$ tkn clustertriggerbinding list6.3.12. Hub interaction commands
Interact with Tekton Hub for resources such as tasks and pipelines.
6.3.12.1. hub
Interact with hub.
Example: Display help
tkn hub -h
$ tkn hub -hExample: Interact with a hub API server
tkn hub --api-server https://api.hub.tekton.dev
$ tkn hub --api-server https://api.hub.tekton.dev
For each example, to get the corresponding sub-commands and flags, run tkn hub <command> --help.
6.3.12.2. hub downgrade
Downgrade an installed resource.
Example: Downgrade the mytask task in the mynamespace namespace to its older version
tkn hub downgrade task mytask --to version -n mynamespace
$ tkn hub downgrade task mytask --to version -n mynamespace6.3.12.3. hub get
Get a resource manifest by its name, kind, catalog, and version.
Example: Get the manifest for a specific version of the myresource pipeline or task from the tekton catalog
tkn hub get [pipeline | task] myresource --from tekton --version version
$ tkn hub get [pipeline | task] myresource --from tekton --version version6.3.12.4. hub info
Display information about a resource by its name, kind, catalog, and version.
Example: Display information about a specific version of the mytask task from the tekton catalog
tkn hub info task mytask --from tekton --version version
$ tkn hub info task mytask --from tekton --version version6.3.12.5. hub install
Install a resource from a catalog by its kind, name, and version.
Example: Install a specific version of the mytask task from the tekton catalog in the mynamespace namespace
tkn hub install task mytask --from tekton --version version -n mynamespace
$ tkn hub install task mytask --from tekton --version version -n mynamespace6.3.12.6. hub reinstall
Reinstall a resource by its kind and name.
Example: Reinstall a specific version of the mytask task from the tekton catalog in the mynamespace namespace
tkn hub reinstall task mytask --from tekton --version version -n mynamespace
$ tkn hub reinstall task mytask --from tekton --version version -n mynamespace6.3.12.7. hub search
Search a resource by a combination of name, kind, and tags.
Example: Search a resource with a tag cli
tkn hub search --tags cli
$ tkn hub search --tags cli6.3.12.8. hub upgrade
Upgrade an installed resource.
Example: Upgrade the installed mytask task in the mynamespace namespace to a new version
tkn hub upgrade task mytask --to version -n mynamespace
$ tkn hub upgrade task mytask --to version -n mynamespaceChapter 7. GitOps CLI for use with Red Hat OpenShift GitOps
The GitOps argocd CLI is a tool for configuring and managing Red Hat OpenShift GitOps and Argo CD resources from a terminal.
With the GitOps CLI, you can make GitOps computing tasks simple and concise. You can install this CLI tool on different platforms.
7.1. Installing the GitOps CLI
Chapter 8. opm CLI
8.1. Installing the opm CLI
8.1.1. About the opm CLI
The opm CLI tool is provided by the Operator Framework for use with the Operator bundle format. This tool allows you to create and maintain catalogs of Operators from a list of Operator bundles that are similar to software repositories. The result is a container image which can be stored in a container registry and then installed on a cluster.
A catalog contains a database of pointers to Operator manifest content that can be queried through an included API that is served when the container image is run. On OpenShift Container Platform, Operator Lifecycle Manager (OLM) can reference the image in a catalog source, defined by a CatalogSource object, which polls the image at regular intervals to enable frequent updates to installed Operators on the cluster.
8.1.2. Installing the opm CLI
You can install the opm CLI tool on your Linux, macOS, or Windows workstation.
Prerequisites
For Red Hat Enterprise Linux (RHEL) 9.0 and later, you must provide the following packages:
-
podmanversion 1.9.3+ (version 2.0+ recommended) -
glibcversion 2.28+
-
Procedure
- Navigate to the OpenShift mirror site and download the latest version of the tarball that matches your operating system.
Unpack the archive.
For Linux or macOS:
tar xvf <file>
$ tar xvf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - For Windows, unzip the archive with a ZIP program.
Place the file anywhere in your
PATH.For Linux or macOS:
Check your
PATH:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow Move the file. For example:
sudo mv ./opm /usr/local/bin/
$ sudo mv ./opm /usr/local/bin/Copy to Clipboard Copied! Toggle word wrap Toggle overflow
For Windows:
Check your
PATH:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow Move the file:
move opm.exe <directory>
C:\> move opm.exe <directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
After you install the
opmCLI, verify that it is available:opm version
$ opm versionCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.2. opm CLI reference
The opm command-line interface (CLI) is a tool for creating and maintaining Operator catalogs.
opm CLI syntax
opm <command> [<subcommand>] [<argument>] [<flags>]
$ opm <command> [<subcommand>] [<argument>] [<flags>]
The opm CLI is not forward compatible. The version of the opm CLI used to generate catalog content must be earlier than or equal to the version used to serve the content on a cluster.
| Flag | Description |
|---|---|
|
| Skip TLS certificate verification for container image registries while pulling bundles or indexes. |
|
| When you pull bundles, use plain HTTP for container image registries. |
The SQLite-based catalog format, including the related CLI commands, is a deprecated feature. Deprecated functionality is still included in OpenShift Container Platform and continues to be supported; however, it will be removed in a future release of this product and is not recommended for new deployments.
For the most recent list of major functionality that has been deprecated or removed within OpenShift Container Platform, refer to the Deprecated and removed features section of the OpenShift Container Platform release notes.
8.2.1. generate
Generate various artifacts for declarative config indexes.
Command syntax
opm generate <subcommand> [<flags>]
$ opm generate <subcommand> [<flags>]| Subcommand | Description |
|---|---|
|
| Generate a Dockerfile for a declarative config index. |
| Flags | Description |
|---|---|
|
| Help for generate. |
8.2.1.1. dockerfile
Generate a Dockerfile for a declarative config index.
This command creates a Dockerfile in the same directory as the <dcRootDir> (named <dcDirName>.Dockerfile) that is used to build the index. If a Dockerfile with the same name already exists, this command fails.
When specifying extra labels, if duplicate keys exist, only the last value of each duplicate key gets added to the generated Dockerfile.
Command syntax
opm generate dockerfile <dcRootDir> [<flags>]
$ opm generate dockerfile <dcRootDir> [<flags>]| Flag | Description |
|---|---|
|
|
Image in which to build catalog. The default value is |
|
|
Extra labels to include in the generated Dockerfile. Labels have the form |
|
| Help for Dockerfile. |
To build with the official Red Hat image, use the registry.redhat.io/openshift4/ose-operator-registry-rhel9:v4.18 value with the -i flag.
8.2.2. index
Generate Operator index for SQLite database format container images from pre-existing Operator bundles.
As of OpenShift Container Platform 4.11, the default Red Hat-provided Operator catalog releases in the file-based catalog format. The default Red Hat-provided Operator catalogs for OpenShift Container Platform 4.6 through 4.10 released in the deprecated SQLite database format.
The opm subcommands, flags, and functionality related to the SQLite database format are also deprecated and will be removed in a future release. The features are still supported and must be used for catalogs that use the deprecated SQLite database format.
Many of the opm subcommands and flags for working with the SQLite database format, such as opm index prune, do not work with the file-based catalog format.
For more information about working with file-based catalogs, see "Additional resources".
Command syntax
opm index <subcommand> [<flags>]
$ opm index <subcommand> [<flags>]| Subcommand | Description |
|---|---|
|
| Add Operator bundles to an index. |
|
| Prune an index of all but specified packages. |
|
| Prune an index of stranded bundles, which are bundles that are not associated with a particular image. |
|
| Delete an entire Operator from an index. |
8.2.2.1. add
Add Operator bundles to an index.
Command syntax
opm index add [<flags>]
$ opm index add [<flags>]| Flag | Description |
|---|---|
|
|
Container image for on-image |
|
|
Tool to build container images: |
|
| Comma-separated list of bundles to add. |
|
|
Tool to interact with container images, such as for saving and building: |
|
| Previous index to add to. |
|
| If enabled, only creates the Dockerfile and saves it to local disk. |
|
|
Graph update mode that defines how channel graphs are updated: |
|
| Optional: If generating the Dockerfile, specify a file name. |
|
| Allow registry load errors. |
|
|
Tool to pull container images: |
|
| Custom tag for container image being built. |
8.2.2.2. prune
Prune an index of all but specified packages.
Command syntax
opm index prune [<flags>]
$ opm index prune [<flags>]| Flag | Description |
|---|---|
|
|
Container image for on-image |
|
|
Tool to interact with container images, such as for saving and building: |
|
| Index to prune. |
|
| If enabled, only creates the Dockerfile and saves it to local disk. |
|
| Optional: If generating the Dockerfile, specify a file name. |
|
| Comma-separated list of packages to keep. |
|
| Allow registry load errors. |
|
| Custom tag for container image being built. |
8.2.2.3. prune-stranded
Prune an index of stranded bundles, which are bundles that are not associated with a particular image.
Command syntax
opm index prune-stranded [<flags>]
$ opm index prune-stranded [<flags>]| Flag | Description |
|---|---|
|
|
Container image for on-image |
|
|
Tool to interact with container images, such as for saving and building: |
|
| Index to prune. |
|
| If enabled, only creates the Dockerfile and saves it to local disk. |
|
| Optional: If generating the Dockerfile, specify a file name. |
|
| Comma-separated list of packages to keep. |
|
| Allow registry load errors. |
|
| Custom tag for container image being built. |
8.2.2.4. rm
Delete an entire Operator from an index.
Command syntax
opm index rm [<flags>]
$ opm index rm [<flags>]| Flag | Description |
|---|---|
|
|
Container image for on-image |
|
|
Tool to build container images: |
|
|
Tool to interact with container images, such as for saving and building: |
|
| Previous index to delete from. |
|
| If enabled, only creates the Dockerfile and saves it to local disk. |
|
| Comma-separated list of Operators to delete. |
|
| Optional: If generating the Dockerfile, specify a file name. |
|
| Comma-separated list of packages to keep. |
|
| Allow registry load errors. |
|
|
Tool to pull container images: |
|
| Custom tag for container image being built. |
8.2.3. init
Generate an olm.package declarative config blob.
Command syntax
opm init <package_name> [<flags>]
$ opm init <package_name> [<flags>]| Flag | Description |
|---|---|
|
| The channel that subscriptions will default to if unspecified. |
|
|
Path to the Operator’s |
|
| Path to package’s icon. |
|
|
Output format: |
8.2.4. migrate
Migrate a SQLite database format index image or database file to a file-based catalog.
The SQLite-based catalog format, including the related CLI commands, is a deprecated feature. Deprecated functionality is still included in OpenShift Container Platform and continues to be supported; however, it will be removed in a future release of this product and is not recommended for new deployments.
For the most recent list of major functionality that has been deprecated or removed within OpenShift Container Platform, refer to the Deprecated and removed features section of the OpenShift Container Platform release notes.
Command syntax
opm migrate <index_ref> <output_dir> [<flags>]
$ opm migrate <index_ref> <output_dir> [<flags>]| Flag | Description |
|---|---|
|
|
Output format: |
8.2.5. render
Generate a declarative config blob from the provided index images, bundle images, and SQLite database files.
Command syntax
opm render <index_image | bundle_image | sqlite_file> [<flags>]
$ opm render <index_image | bundle_image | sqlite_file> [<flags>]| Flag | Description |
|---|---|
|
|
Output format: |
8.2.6. serve
Serve declarative configs via a GRPC server.
The declarative config directory is loaded by the serve command at startup. Changes made to the declarative config after this command starts are not reflected in the served content.
Command syntax
opm serve <source_path> [<flags>]
$ opm serve <source_path> [<flags>]| Flag | Description |
|---|---|
|
| If this flag is set, it syncs and persists the server cache directory. |
|
|
Exits with an error if the cache is not present or is invalidated. The default value is |
|
| Syncs the serve cache and exits without serving. |
|
| Enables debug logging. |
|
| Help for serve. |
|
|
The port number for the service. The default value is |
|
|
The address of the startup profiling endpoint. The format is |
|
|
The path to a container termination log file. The default value is |
8.2.7. validate
Validate the declarative config JSON file(s) in a given directory.
Command syntax
opm validate <directory> [<flags>]
$ opm validate <directory> [<flags>]Chapter 9. Operator SDK
9.1. Installing the Operator SDK CLI
The Operator SDK provides a command-line interface (CLI) tool that Operator developers can use to build, test, and deploy an Operator. You can install the Operator SDK CLI on your workstation so that you are prepared to start authoring your own Operators.
The Red Hat-supported version of the Operator SDK CLI tool, including the related scaffolding and testing tools for Operator projects, is deprecated and is planned to be removed in a future release of OpenShift Container Platform. Red Hat will provide bug fixes and support for this feature during the current release lifecycle, but this feature will no longer receive enhancements and will be removed from future OpenShift Container Platform releases.
The Red Hat-supported version of the Operator SDK is not recommended for creating new Operator projects. Operator authors with existing Operator projects can use the version of the Operator SDK CLI tool released with OpenShift Container Platform 4.18 to maintain their projects and create Operator releases targeting newer versions of OpenShift Container Platform.
The following related base images for Operator projects are not deprecated. The runtime functionality and configuration APIs for these base images are still supported for bug fixes and for addressing CVEs.
- The base image for Ansible-based Operator projects
- The base image for Helm-based Operator projects
For the most recent list of major functionality that has been deprecated or removed within OpenShift Container Platform, refer to the Deprecated and removed features section of the OpenShift Container Platform release notes.
For information about the unsupported, community-maintained, version of the Operator SDK, see Operator SDK (Operator Framework).
Operator authors with cluster administrator access to a Kubernetes-based cluster, such as OpenShift Container Platform, can use the Operator SDK CLI to develop their own Operators based on Go, Ansible, Java, or Helm. Kubebuilder is embedded into the Operator SDK as the scaffolding solution for Go-based Operators, which means existing Kubebuilder projects can be used as is with the Operator SDK and continue to work. See Developing Operators for full documentation on the Operator SDK.
OpenShift Container Platform 4.18 supports Operator SDK 1.38.0.
9.1.1. Installing the Operator SDK CLI on Linux
You can install the OpenShift SDK CLI tool on Linux.
Prerequisites
- Go v1.19+
-
dockerv17.03+,podmanv1.9.3+, orbuildahv1.7+
Procedure
- Navigate to the OpenShift mirror site.
- From the latest 4.18 directory, download the latest version of the tarball for Linux.
Unpack the archive:
tar xvf operator-sdk-v1.38.0-ocp-linux-x86_64.tar.gz
$ tar xvf operator-sdk-v1.38.0-ocp-linux-x86_64.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow Make the file executable:
chmod +x operator-sdk
$ chmod +x operator-sdkCopy to Clipboard Copied! Toggle word wrap Toggle overflow Move the extracted
operator-sdkbinary to a directory that is on yourPATH.TipTo check your
PATH:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow sudo mv ./operator-sdk /usr/local/bin/operator-sdk
$ sudo mv ./operator-sdk /usr/local/bin/operator-sdkCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
After you install the Operator SDK CLI, verify that it is available:
operator-sdk version
$ operator-sdk versionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
operator-sdk version: "v1.38.0-ocp", ...
operator-sdk version: "v1.38.0-ocp", ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.1.2. Installing the Operator SDK CLI on macOS
You can install the OpenShift SDK CLI tool on macOS.
Prerequisites
- Go v1.19+
-
dockerv17.03+,podmanv1.9.3+, orbuildahv1.7+
Procedure
-
For the
amd64andarm64architectures, navigate to the OpenShift mirror site for theamd64architecture and OpenShift mirror site for thearm64architecture respectively. - From the latest 4.18 directory, download the latest version of the tarball for macOS.
Unpack the Operator SDK archive for
amd64architecture by running the following command:tar xvf operator-sdk-v1.38.0-ocp-darwin-x86_64.tar.gz
$ tar xvf operator-sdk-v1.38.0-ocp-darwin-x86_64.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow Unpack the Operator SDK archive for
arm64architecture by running the following command:tar xvf operator-sdk-v1.38.0-ocp-darwin-aarch64.tar.gz
$ tar xvf operator-sdk-v1.38.0-ocp-darwin-aarch64.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow Make the file executable by running the following command:
chmod +x operator-sdk
$ chmod +x operator-sdkCopy to Clipboard Copied! Toggle word wrap Toggle overflow Move the extracted
operator-sdkbinary to a directory that is on yourPATHby running the following command:TipCheck your
PATHby running the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow sudo mv ./operator-sdk /usr/local/bin/operator-sdk
$ sudo mv ./operator-sdk /usr/local/bin/operator-sdkCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
After you install the Operator SDK CLI, verify that it is available by running the following command::
operator-sdk version
$ operator-sdk versionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
operator-sdk version: "v1.38.0-ocp", ...
operator-sdk version: "v1.38.0-ocp", ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.2. Operator SDK CLI reference
The Operator SDK command-line interface (CLI) is a development kit designed to make writing Operators easier.
The Red Hat-supported version of the Operator SDK CLI tool, including the related scaffolding and testing tools for Operator projects, is deprecated and is planned to be removed in a future release of OpenShift Container Platform. Red Hat will provide bug fixes and support for this feature during the current release lifecycle, but this feature will no longer receive enhancements and will be removed from future OpenShift Container Platform releases.
The Red Hat-supported version of the Operator SDK is not recommended for creating new Operator projects. Operator authors with existing Operator projects can use the version of the Operator SDK CLI tool released with OpenShift Container Platform 4.18 to maintain their projects and create Operator releases targeting newer versions of OpenShift Container Platform.
The following related base images for Operator projects are not deprecated. The runtime functionality and configuration APIs for these base images are still supported for bug fixes and for addressing CVEs.
- The base image for Ansible-based Operator projects
- The base image for Helm-based Operator projects
For the most recent list of major functionality that has been deprecated or removed within OpenShift Container Platform, refer to the Deprecated and removed features section of the OpenShift Container Platform release notes.
For information about the unsupported, community-maintained, version of the Operator SDK, see Operator SDK (Operator Framework).
Operator SDK CLI syntax
operator-sdk <command> [<subcommand>] [<argument>] [<flags>]
$ operator-sdk <command> [<subcommand>] [<argument>] [<flags>]See Developing Operators for full documentation on the Operator SDK.
9.2.1. bundle
The operator-sdk bundle command manages Operator bundle metadata.
9.2.1.1. validate
The bundle validate subcommand validates an Operator bundle.
| Flag | Description |
|---|---|
|
|
Help output for the |
|
|
Tool to pull and unpack bundle images. Only used when validating a bundle image. Available options are |
|
| List all optional validators available. When set, no validators are run. |
|
|
Label selector to select optional validators to run. When run with the |
9.2.2. cleanup
The operator-sdk cleanup command destroys and removes resources that were created for an Operator that was deployed with the run command.
| Flag | Description |
|---|---|
|
|
Help output for the |
|
|
Path to the |
|
| If present, namespace in which to run the CLI request. |
|
|
Time to wait for the command to complete before failing. The default value is |
9.2.3. completion
The operator-sdk completion command generates shell completions to make issuing CLI commands quicker and easier.
| Subcommand | Description |
|---|---|
|
| Generate bash completions. |
|
| Generate zsh completions. |
| Flag | Description |
|---|---|
|
| Usage help output. |
For example:
operator-sdk completion bash
$ operator-sdk completion bashExample output
bash completion for operator-sdk -*- shell-script -*- ... ex: ts=4 sw=4 et filetype=sh
# bash completion for operator-sdk -*- shell-script -*-
...
# ex: ts=4 sw=4 et filetype=sh9.2.4. create
The operator-sdk create command is used to create, or scaffold, a Kubernetes API.
9.2.4.1. api
The create api subcommand scaffolds a Kubernetes API. The subcommand must be run in a project that was initialized with the init command.
| Flag | Description |
|---|---|
|
|
Help output for the |
9.2.5. generate
The operator-sdk generate command invokes a specific generator to generate code or manifests.
9.2.5.1. bundle
The generate bundle subcommand generates a set of bundle manifests, metadata, and a bundle.Dockerfile file for your Operator project.
Typically, you run the generate kustomize manifests subcommand first to generate the input Kustomize bases that are used by the generate bundle subcommand. However, you can use the make bundle command in an initialized project to automate running these commands in sequence.
| Flag | Description |
|---|---|
|
|
Comma-separated list of channels to which the bundle belongs. The default value is |
|
|
Root directory for |
|
| The default channel for the bundle. |
|
|
Root directory for Operator manifests, such as deployments and RBAC. This directory is different from the directory passed to the |
|
|
Help for |
|
|
Directory from which to read an existing bundle. This directory is the parent of your bundle |
|
|
Directory containing Kustomize bases and a |
|
| Generate bundle manifests. |
|
| Generate bundle metadata and Dockerfile. |
|
| Directory to write the bundle to. |
|
|
Overwrite the bundle metadata and Dockerfile if they exist. The default value is |
|
| Package name for the bundle. |
|
| Run in quiet mode. |
|
| Write bundle manifest to standard out. |
|
| Semantic version of the Operator in the generated bundle. Set only when creating a new bundle or upgrading the Operator. |
9.2.5.2. kustomize
The generate kustomize subcommand contains subcommands that generate Kustomize data for the Operator.
9.2.5.2.1. manifests
The generate kustomize manifests subcommand generates or regenerates Kustomize bases and a kustomization.yaml file in the config/manifests directory, which are used to build bundle manifests by other Operator SDK commands. This command interactively asks for UI metadata, an important component of manifest bases, by default unless a base already exists or you set the --interactive=false flag.
| Flag | Description |
|---|---|
|
| Root directory for API type definitions. |
|
|
Help for |
|
| Directory containing existing Kustomize files. |
|
|
When set to |
|
| Directory where to write Kustomize files. |
|
| Package name. |
|
| Run in quiet mode. |
9.2.6. init
The operator-sdk init command initializes an Operator project and generates, or scaffolds, a default project directory layout for the given plugin.
This command writes the following files:
- Boilerplate license file
-
PROJECTfile with the domain and repository -
Makefileto build the project -
go.modfile with project dependencies -
kustomization.yamlfile for customizing manifests - Patch file for customizing images for manager manifests
- Patch file for enabling Prometheus metrics
-
main.gofile to run
| Flag | Description |
|---|---|
|
|
Help output for the |
|
|
Name and optionally version of the plugin to initialize the project with. Available plugins are |
|
|
Project version. Available values are |
9.2.7. run
The operator-sdk run command provides options that can launch the Operator in various environments.
9.2.7.1. bundle
The run bundle subcommand deploys an Operator in the bundle format with Operator Lifecycle Manager (OLM).
| Flag | Description |
|---|---|
|
|
Index image in which to inject a bundle. The default image is |
|
|
Install mode supported by the cluster service version (CSV) of the Operator, for example |
|
|
Install timeout. The default value is |
|
|
Path to the |
|
| If present, namespace in which to run the CLI request. |
|
|
Specifies the security context to use for the catalog pod. Allowed values include |
|
|
Help output for the |
-
The
restrictedsecurity context is not compatible with thedefaultnamespace. To configure your Operator’s pod security admission in your production environment, see "Complying with pod security admission". For more information about pod security admission, see "Understanding and managing pod security admission".
9.2.7.2. bundle-upgrade
The run bundle-upgrade subcommand upgrades an Operator that was previously installed in the bundle format with Operator Lifecycle Manager (OLM).
| Flag | Description |
|---|---|
|
|
Upgrade timeout. The default value is |
|
|
Path to the |
|
| If present, namespace in which to run the CLI request. |
|
|
Specifies the security context to use for the catalog pod. Allowed values include |
|
|
Help output for the |
-
The
restrictedsecurity context is not compatible with thedefaultnamespace. To configure your Operator’s pod security admission in your production environment, see "Complying with pod security admission". For more information about pod security admission, see "Understanding and managing pod security admission".
9.2.8. scorecard
The operator-sdk scorecard command runs the scorecard tool to validate an Operator bundle and provide suggestions for improvements. The command takes one argument, either a bundle image or directory containing manifests and metadata. If the argument holds an image tag, the image must be present remotely.
| Flag | Description |
|---|---|
|
|
Path to scorecard configuration file. The default path is |
|
|
Help output for the |
|
|
Path to |
|
| List which tests are available to run. |
|
| Namespace in which to run the test images. |
|
|
Output format for results. Available values are |
|
|
Option to run scorecard with the specified security context. Allowed values include |
|
| Label selector to determine which tests are run. |
|
|
Service account to use for tests. The default value is |
|
| Disable resource cleanup after tests are run. |
|
|
Seconds to wait for tests to complete, for example |
-
The
restrictedsecurity context is not compatible with thedefaultnamespace. To configure your Operator’s pod security admission in your production environment, see "Complying with pod security admission". For more information about pod security admission, see "Understanding and managing pod security admission".
Legal Notice
Copyright © Red Hat
OpenShift documentation is licensed under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0).
Modified versions must remove all Red Hat trademarks.
Portions adapted from https://github.com/kubernetes-incubator/service-catalog/ with modifications by Red Hat.
Red Hat, Red Hat Enterprise Linux, the Red Hat logo, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries.
Linux® is the registered trademark of Linus Torvalds in the United States and other countries.
Java® is a registered trademark of Oracle and/or its affiliates.
XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries.
MySQL® is a registered trademark of MySQL AB in the United States, the European Union and other countries.
Node.js® is an official trademark of the OpenJS Foundation.
The OpenStack® Word Mark and OpenStack logo are either registered trademarks/service marks or trademarks/service marks of the OpenStack Foundation, in the United States and other countries and are used with the OpenStack Foundation’s permission. We are not affiliated with, endorsed or sponsored by the OpenStack Foundation, or the OpenStack community.
All other trademarks are the property of their respective owners.