A.3. Certificate Chaining
Certificate chain
Copy linkLink copied to clipboard!
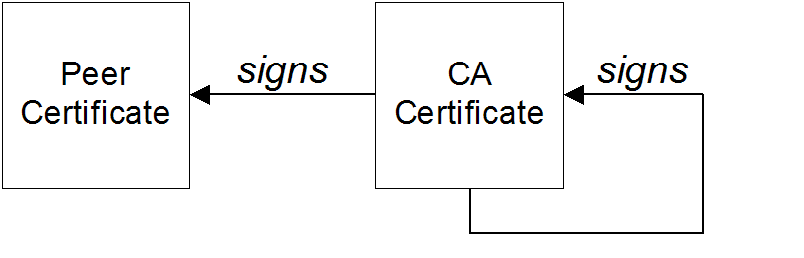
A certificate chain is a sequence of certificates, where each certificate in the chain is signed by the subsequent certificate.
Figure A.1, “A Certificate Chain of Depth 2” shows an example of a simple certificate chain.
Figure A.1. A Certificate Chain of Depth 2
Self-signed certificate
Copy linkLink copied to clipboard!
The last certificate in the chain is normally a self-signed certificate—a certificate that signs itself.
Chain of trust
Copy linkLink copied to clipboard!
The purpose of a certificate chain is to establish a chain of trust from a peer certificate to a trusted CA certificate. The CA vouches for the identity in the peer certificate by signing it. If the CA is one that you trust (indicated by the presence of a copy of the CA certificate in your root certificate directory), this implies you can trust the signed peer certificate as well.
Certificates signed by multiple CAs
Copy linkLink copied to clipboard!
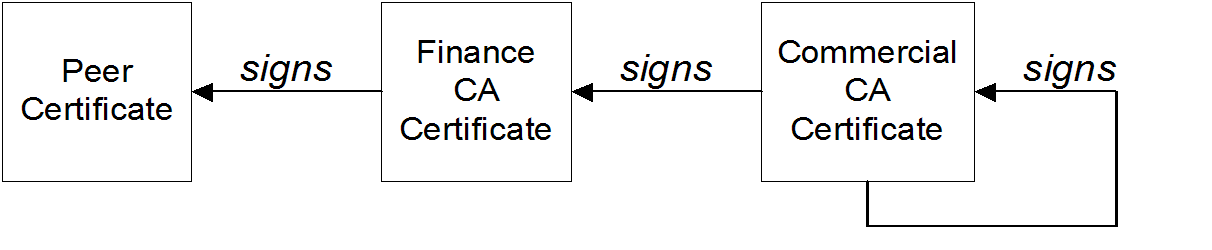
A CA certificate can be signed by another CA. For example, an application certificate could be signed by the CA for the finance department of Progress Software, which in turn is signed by a self-signed commercial CA.
Figure A.2, “A Certificate Chain of Depth 3” shows what this certificate chain looks like.
Figure A.2. A Certificate Chain of Depth 3
Trusted CAs
Copy linkLink copied to clipboard!
An application can accept a peer certificate, provided it trusts at least one of the CA certificates in the signing chain.