Chapter 1. Security options
You can configure security settings for Cryostat, so that you can better protect your Cryostat instance.
Cryostat can encrypt and store credentials for a target JVM application in a database that is stored on a persistent volume claim (PVC) on Red Hat OpenShift. Cryostat supports SSL/TLS on the HTTP request that adds credentials to the database and on the JMX connection that uses those credentials to connect to the target application. Cryostat also encrypts the credentials within the database by using a passphrase that is either provided by the user or that is generated by the Red Hat build of Cryostat Operator.
You can use the Cryostat Operator to configure Cryostat to trust SSL/TLS certificates from specific applications by adding these certificates to a secret and by configuring the Cryostat custom resource (CR) to include this secret. For more information, see Using the Red Hat build of Cryostat Operator to configure Cryostat: Configuring TLS certificates.
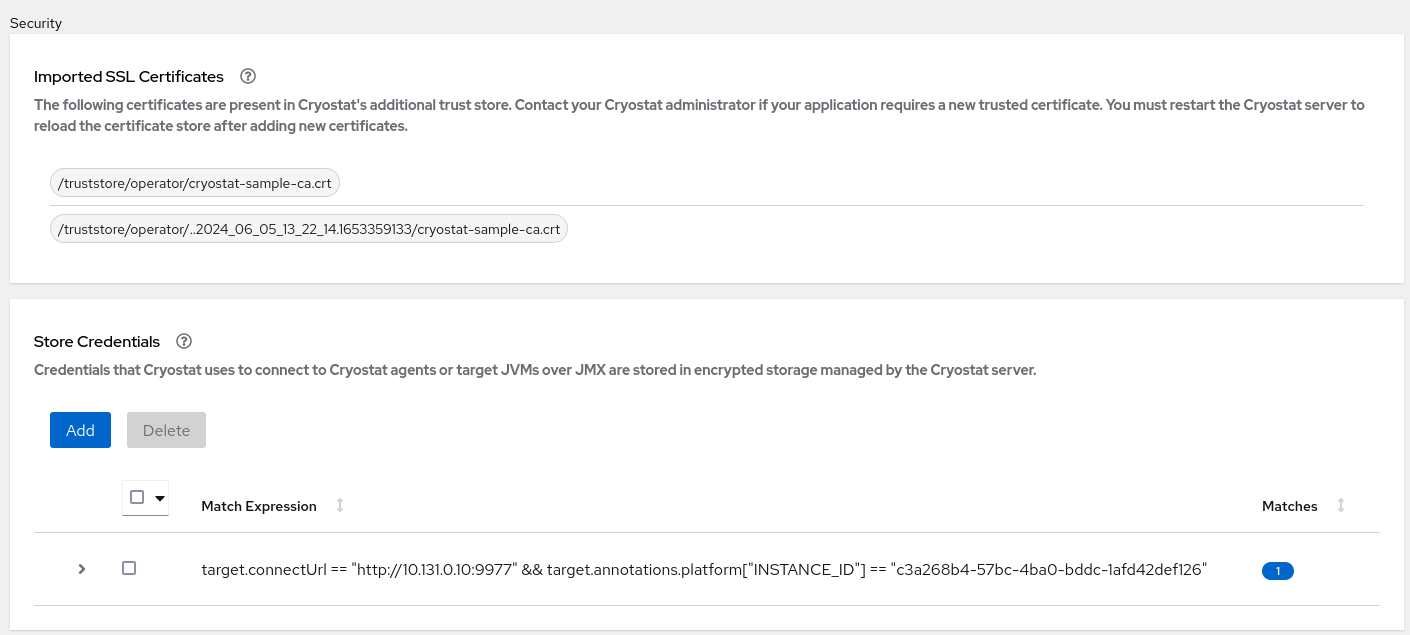
You can view the list of imported SSL/TLS certificates for a target JVM by clicking the Security menu in the Cryostat web console.
Figure 1.1. Viewing the list of imported SSL certificates for a target JVM
1.1. Storing and managing credentials
If you enable Java Management Extensions (JMX) authentication or HTTP authentication for your target JVM application, Cryostat prompts you to enter your credentials before Cryostat can access any of the application’s JFR recordings.
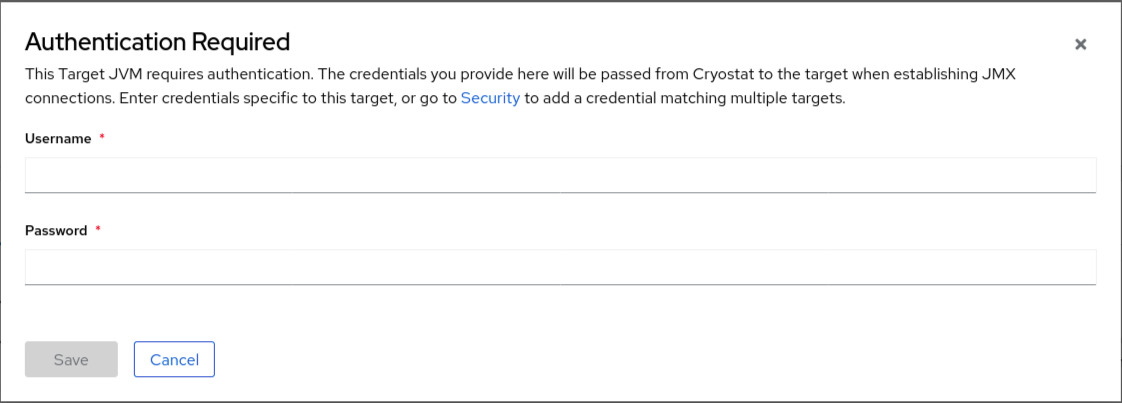
When you click the Recordings or Events menu item on the Cryostat web console, an Authentication Required window opens on the console. You must enter the username and password of the target JVM application. You can then view the recordings or perform any additional recording operations on the application.
Figure 1.2. Example of a Cryostat Authentication Required window
Cryostat stores credentials that it uses to connect to Cryostat agents or target JVMs.
If you need to restart your target JVM application, ensure that you complete one of the following tasks to avoid losing JFR recording data for the application:
- Click the Recordings menu item on the Cryostat web console and archive your JFR recording.
- Create an automated rule that schedules Cryostat to copy a snapshot recording to the storage location for the Cryostat archives.
When you want to monitor multiple target JVMs by creating an automated rule, you can configure Cryostat to store and then reuse your credentials for each target JVM connection. By using this configuration, you do not need to re-enter your credentials whenever you want to revisit the JFR recording for your application on the Cryostat web console.
Prerequisites
- Enabled JMX or HTTP authentication for your target JVM application.
Procedure
- Click the Security menu item.
From the Store Credentials window, click the Add button. The Store Credentials window opens.
Figure 1.3. Example of a Store Credentials window
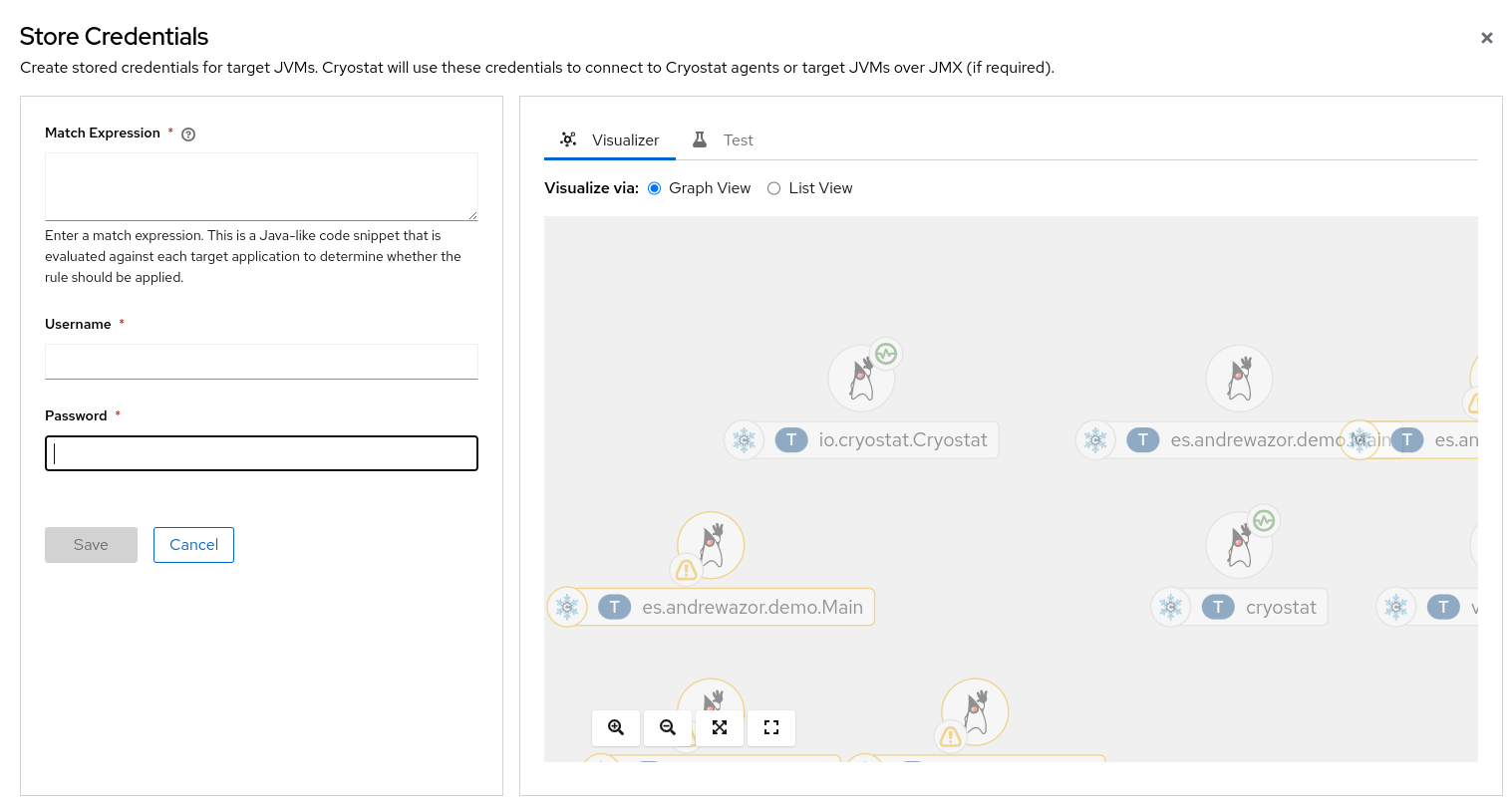
In the Match Expression field, specify the match expression details.
NoteSelect the question mark icon to view suggested syntax in a Match Expression Hint snippet.
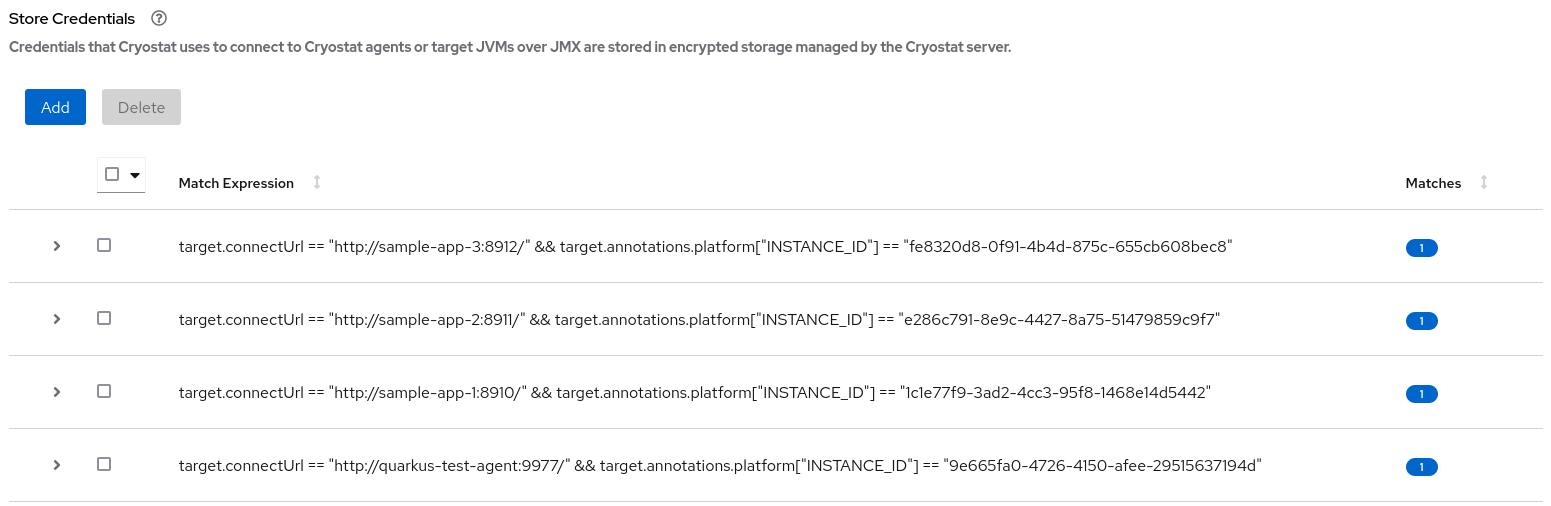
Click Save. A table entry is displayed in the Store Credentials window that shows the Match Expression for your target JVM.
Figure 1.4. Example of a table entry on the Store Credentials pane
 Important
ImportantFor security purposes, a table entry does not display your username or password.
- Optional: If you want to delete your stored credentials for a target JVM, you can select the checkbox next to the table entry for this target JVM and then click Delete.