Chapter 3. Connectivity Link technologies and patterns
The main technologies and patterns provided by Connectivity Link include the following:
- Gateway API
Gateways play an essential role in application connectivity and security. In Kubernetes-based environments, Gateway API is the new standard for deploying ingress Gateways and managing application networking.
Gateway API provides standardized APIs for ingress traffic management and support for multiple protocols. Gateway API is user persona role-oriented by design, and provides configuration flexibility and portability. You can use Gateway API to set up ingress policies on each OpenShift cluster to be identical, consistent, and implemented with minimum effort.
Figure 3.1. Gateway API user persona-based design
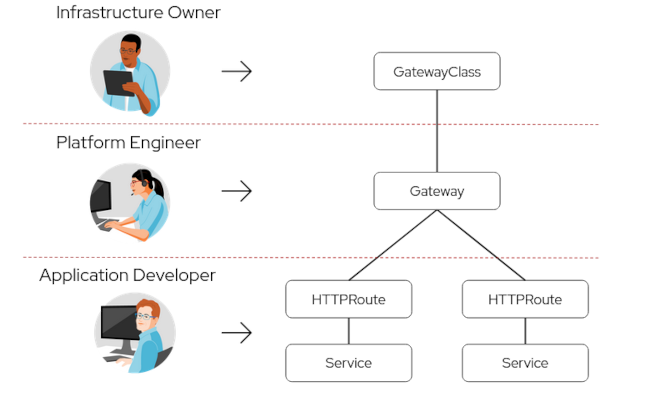
- Policy-based configuration
By using Connectivity Link policies defined as Kubernetes custom resource definitions (CRDs), platform engineers and application developers can easily secure, protect, and connect their applications and infrastructure. Connectivity Link provides policies for managing TLS, authentication and authorization, rate limiting, and DNS.
The policy attachment pattern provides a way to add behavior to an network object by using configuration that cannot be described in the object
specfield. Policy attachments also provide the concept of defaults and overrides, which allow different roles to operate with policy APIs at different levels of the object hierarchy. These policies are then merged with specific rules and strategies to form an effective policy.The following simple example of a rate limiting policy configures a specified limit of 5 requests per 10 seconds for every listener defined in the target Gateway that does not have its own rate limiting policy defined:
Simple rate limiting policy example
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - WebAssembly plug-in
Unlike other connectivity management systems, Connectivity Link is not a standalone Gateway. Connectivity Link is a WebAssembly (WASM) plug-in, which is developed for the Envoy proxy. This means that users of OpenShift Service Mesh, Istio, or Envoy for ingress do not require major changes to their existing ingress objects and policies to begin using Connectivity Link.
The WebAssembly plug-in design also means that Connectivity Link is lightweight, fast, hardware independent, non-intrusive, and secure.
- Multicluster configuration mirroring
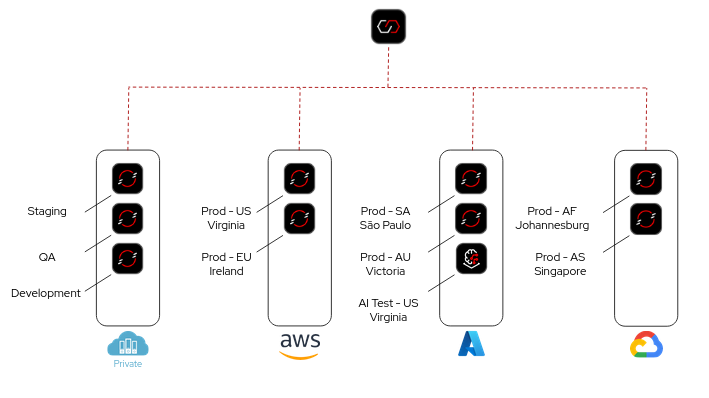
Connectivity Link uses multicluster configuration mirroring across multicloud and hybrid cloud environments to ensure that you can bring your routing, configuration, and policies wherever they are required. You must no longer set different policies in different ways based on the cloud service provider, and you can bring your own policies instead.
You can also ensure that your development, test, and production environments are set up in the same way to prevent surprises later. In this way, Connectivity Link provides consistency, simplicity, unified experience, global administration, and security compliance.
Figure 3.2. Multicluster configuration mirroring across multicloud and hybrid cloud environments
- API controller 1.0 Developer Preview
Connectivity Link introduces an API controller 1.0 Developer Preview component that provides a next-generation approach to API management, and which extends beyond traditional API management capabilities provided by other products.
API management requires connectivity, and Connectivity Link provides scalable multicluster and multi-Gateway connectivity management, along with API management features such as API design, API registry, API observability, authentication, and rate limiting.
For more details, see the Getting Started with API controller 1.0 Developer Preview.
ImportantDeveloper Preview features are not supported by Red Hat in any way and are not functionally complete or production-ready. Do not use Developer Preview features for production or business-critical workloads. Developer Preview features provide early access to functionality in advance of possible inclusion in a Red Hat product offering. Customers can use these features to test functionality and provide feedback during the development process.
Developer Preview features might not have any documentation, are subject to change or removal at any time, and have received limited testing. Red Hat might provide ways to submit feedback on Developer Preview features without an associated SLA. For more information, see Red Hat Developer Preview - Scope of Support.
Figure 3.3. Connectivity Link API management and connectivity
