9.10. Using SELinux Policies
SELinux is a collection of mandatory access control rules which are enforced across a system to restrict unauthorized access and tampering. SELinux categorizes files, directories, ports, processes, users, and other objects on the server. Each object is placed in an appropriate security context to define how the object is allowed to behave on the server through its role, user, and security level. These roles for objects are grouped in domains, and SELinux rules define how the objects in one domain are allowed to interact with objects in another domain.
Directory Server has the following domains:
- dirsrv_t for the Directory Server
- dirsrv_snmp_t for the SNMP
Directory Server also uses one additional, default domains for LDAP ports: ldap_port_t
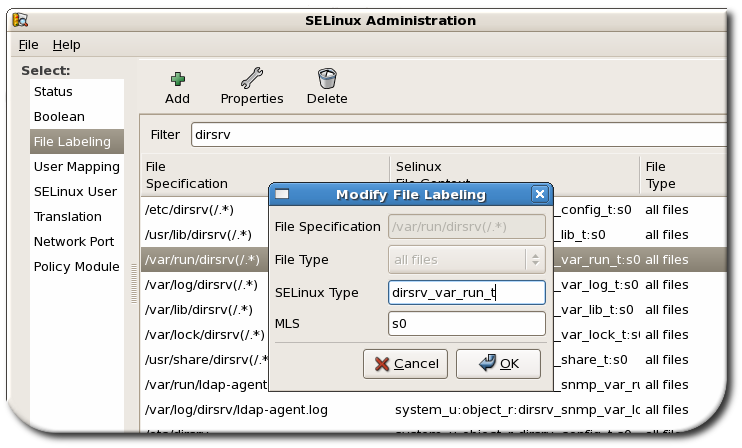
Figure 9.4. Editing Directory Server File Labeling
These domains provide security contexts for all of the processes, files, directories, ports, sockets, and users for the Directory Server.
- Files and directories for each instance are labeled with a specific SELinux context. (Most of the main directories used by Directory Server have subdirectories for all local instances, no matter how many, so a single policy is easily applied to new instances.)
- The ports for each instance are labeled with a specific SELinux context.
- All Directory Server processes are constrained within the appropriate domain.
- Each domain has specific rules that define what actions are authorized for the domain.
- Any access not specified in the SELinux policy is denied to the instance.
SELinux has three different levels of enforcement: disabled (no SELinux), permissive (where the rules are processed but not enforced), and enforcing (where all rules are strictly enforced). Red Hat Directory Server has defined SELinux policies that allow it to run as normal under strict SELinux enforcing mode, with a caveat. The Directory Server can run in different modes, one for normal operations and one for database operations like importing (ldif2db mode). The SELinux policies for the Directory Server only apply to normal mode.
By default, the Directory Server runs confined by SELinux policies.