Securing networks
Configuring secured networks and network communication
Abstract
Providing feedback on Red Hat documentation
We are committed to providing high-quality documentation and value your feedback. To help us improve, you can submit suggestions or report errors through the Red Hat Jira tracking system.
Procedure
Log in to the Jira website.
If you do not have an account, select the option to create one.
- Click Create in the top navigation bar.
- Enter a descriptive title in the Summary field.
- Enter your suggestion for improvement in the Description field. Include links to the relevant parts of the documentation.
- Click Create at the bottom of the dialogue.
Chapter 1. Using secure communications between two systems with OpenSSH
SSH (Secure Shell) is a protocol which provides secure communications between two systems using a client-server architecture and allows users to log in to server host systems remotely. Unlike other remote communication protocols, such as FTP or Telnet, SSH encrypts the login session, which prevents intruders from collecting unencrypted passwords from the connection.
1.1. SSH and OpenSSH
SSH (Secure Shell) is a program for logging into a remote machine and executing commands on that machine. The SSH protocol provides secure encrypted communications between two untrusted hosts over an insecure network. You can also forward X11 connections and arbitrary TCP/IP ports over the secure channel.
The SSH protocol mitigates security threats, such as interception of communication between two systems and impersonation of a particular host, when you use it for remote shell login or file copying. This is because the SSH client and server use digital signatures to verify their identities. Additionally, all communication between the client and server systems is encrypted.
A host key authenticates hosts in the SSH protocol. Host keys are cryptographic keys that are generated automatically when OpenSSH is started for the first time or when the host boots for the first time.
OpenSSH is an implementation of the SSH protocol supported by Linux, UNIX, and similar operating systems. It includes the core files necessary for both the OpenSSH client and server. The OpenSSH suite consists of the following user-space tools:
-
sshis a remote login program (SSH client). -
sshdis an OpenSSH SSH daemon. -
scpis a secure remote file copy program. -
sftpis a secure file transfer program. -
ssh-agentis an authentication agent for caching private keys. -
ssh-addadds private key identities tossh-agent. -
ssh-keygengenerates, manages, and converts authentication keys forssh. -
ssh-copy-idis a script that adds local public keys to theauthorized_keysfile on a remote SSH server. -
ssh-keyscangathers SSH public host keys.
The OpenSSH suite in RHEL supports only SSH version 2. It has an enhanced key-exchange algorithm that is not vulnerable to exploits known in the older version 1.
Red Hat Enterprise Linux includes the following OpenSSH packages: the general openssh package, the openssh-server package, and the openssh-clients package. The OpenSSH packages require the OpenSSL package openssl-libs, which installs several important cryptographic libraries that enable OpenSSH to provide encrypted communications.
OpenSSH, as one of core cryptographic subsystems of RHEL, uses system-wide crypto policies. This ensures that weak cipher suites and cryptographic algorithms are disabled in the default configuration. To modify the policy, the administrator must either use the update-crypto-policies command to adjust the settings or manually opt out of the system-wide crypto policies. See the Excluding an application from following system-wide crypto policies section for more information.
The OpenSSH suite uses two sets of configuration files: one for client programs (that is, ssh, scp, and sftp), and another for the server (the sshd daemon).
System-wide SSH configuration information is stored in the /etc/ssh/ directory. The /etc/ssh/ssh_config file contains the client configuration, and the /etc/ssh/sshd_config file is the default OpenSSH server configuration file.
User-specific SSH configuration information is stored in ~/.ssh/ in the user’s home directory. For a detailed list of OpenSSH configuration files, see the FILES section in the sshd(8) man page on your system.
1.2. Generating SSH key pairs
You can log in to an OpenSSH server without entering a password by generating an SSH key pair on a local system and copying the generated public key to the OpenSSH server. Each user who wants to create a key must run this procedure.
To preserve previously generated key pairs after you reinstall the system, back up the ~/.ssh/ directory before you create new keys. After reinstalling, copy it back to your home directory. You can do this for all users on your system, including root.
Prerequisites
- You are logged in as a user who wants to connect to the OpenSSH server by using keys.
- The OpenSSH server is configured to allow key-based authentication.
Procedure
Generate an ECDSA key pair:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can also generate an RSA key pair by using the
ssh-keygencommand without any parameter or an Ed25519 key pair by entering thessh-keygen -t ed25519command. Note that the Ed25519 algorithm is not FIPS-140-compliant, and OpenSSH does not work with Ed25519 keys in FIPS mode.Copy the public key to a remote machine:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<username>@<ssh-server-example.com>with your credentials.If you do not use the
ssh-agentprogram in your session, the previous command copies the most recently modified~/.ssh/id*.pubpublic key if it is not yet installed. To specify another public-key file or to prioritize keys in files over keys cached in memory byssh-agent, use thessh-copy-idcommand with the-ioption.
Verification
Log in to the OpenSSH server by using the key file:
ssh -o PreferredAuthentications=publickey <username>@<ssh-server-example.com>
$ ssh -o PreferredAuthentications=publickey <username>@<ssh-server-example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
1.3. Setting key-based authentication as the only method on an OpenSSH server
To improve system security, enforce key-based authentication by disabling password authentication on your OpenSSH server.
Prerequisites
-
The
openssh-serverpackage is installed. -
The
sshddaemon is running on the server. You can already connect to the OpenSSH server by using a key.
See the Generating SSH key pairs section for details.
Procedure
Open the
/etc/ssh/sshd_configconfiguration in a text editor, for example:vi /etc/ssh/sshd_config
# vi /etc/ssh/sshd_configCopy to Clipboard Copied! Toggle word wrap Toggle overflow Change the
PasswordAuthenticationoption tono:PasswordAuthentication no
PasswordAuthentication noCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
On a system other than a new default installation, check that the
PubkeyAuthenticationparameter is either not set or set toyes. Set the
ChallengeResponseAuthenticationdirective tono.Note that the corresponding entry is commented out in the configuration file and the default value is
yes.To use key-based authentication with NFS-mounted home directories, enable the
use_nfs_home_dirsSELinux boolean:setsebool -P use_nfs_home_dirs 1
# setsebool -P use_nfs_home_dirs 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If you are connected remotely, not using console or out-of-band access, test the key-based login process before disabling password authentication.
Reload the
sshddaemon to apply the changes:systemctl reload sshd
# systemctl reload sshdCopy to Clipboard Copied! Toggle word wrap Toggle overflow
1.4. Caching your SSH credentials by using ssh-agent
To avoid entering a passphrase each time you initiate an SSH connection, you can use the ssh-agent utility to cache the private SSH key for a login session. If the agent is running and your keys are unlocked, you can log in to SSH servers by using these keys but without having to enter the key’s password again. The private key and the passphrase remain secure.
Prerequisites
- You have a remote host with the SSH daemon running and reachable through the network.
- You know the IP address or hostname and credentials to log in to the remote host.
You have generated an SSH key pair with a passphrase and transferred the public key to the remote machine.
See the Generating SSH key pairs section for details.
Procedure
Add the command for automatically starting
ssh-agentin your session to the~/.bashrcfile:Open
~/.bashrcin a text editor of your choice, for example:vi ~/.bashrc
$ vi ~/.bashrcCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the following line to the file:
eval $(ssh-agent)
eval $(ssh-agent)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the changes, and quit the editor.
Add the following line to the
~/.ssh/configfile:AddKeysToAgent yes
AddKeysToAgent yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow With this option and
ssh-agentstarted in your session, the agent prompts for a password only for the first time when you connect to a host.
Verification
Log in to a host which uses the corresponding public key of the cached private key in the agent, for example:
ssh <example.user>@<ssh-server@example.com>
$ ssh <example.user>@<ssh-server@example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that you did not have to enter the passphrase.
1.5. Authenticating by SSH keys stored on a smart card
You can create and store ECDSA and RSA keys on a smart card and authenticate by the smart card on an OpenSSH client. Smart-card authentication replaces the default password authentication.
Prerequisites
-
On the client side, the
openscpackage is installed and thepcscdservice is running.
Procedure
List all keys provided by the OpenSC PKCS #11 module including their PKCS #11 URIs and save the output to the
keys.pubfile:ssh-keygen -D pkcs11: > keys.pub
$ ssh-keygen -D pkcs11: > keys.pubCopy to Clipboard Copied! Toggle word wrap Toggle overflow Transfer the public key to the remote server. Use the
ssh-copy-idcommand with thekeys.pubfile created in the previous step:ssh-copy-id -f -i keys.pub <username@ssh-server-example.com>
$ ssh-copy-id -f -i keys.pub <username@ssh-server-example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Connect to <ssh-server-example.com> by using the ECDSA key. You can use just a subset of the URI, which uniquely references your key, for example:
ssh -i "pkcs11:id=%01?module-path=/usr/lib64/pkcs11/opensc-pkcs11.so" <ssh-server-example.com> Enter PIN for 'SSH key': [ssh-server-example.com] $
$ ssh -i "pkcs11:id=%01?module-path=/usr/lib64/pkcs11/opensc-pkcs11.so" <ssh-server-example.com> Enter PIN for 'SSH key': [ssh-server-example.com] $Copy to Clipboard Copied! Toggle word wrap Toggle overflow Because OpenSSH uses the
p11-kit-proxywrapper and the OpenSC PKCS #11 module is registered to thep11-kittool, you can simplify the previous command:ssh -i "pkcs11:id=%01" <ssh-server-example.com> Enter PIN for 'SSH key': [ssh-server-example.com] $
$ ssh -i "pkcs11:id=%01" <ssh-server-example.com> Enter PIN for 'SSH key': [ssh-server-example.com] $Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you skip the
id=part of a PKCS #11 URI, OpenSSH loads all keys that are available in the proxy module. This can reduce the amount of typing required:ssh -i pkcs11: <ssh-server-example.com> Enter PIN for 'SSH key': [ssh-server-example.com] $
$ ssh -i pkcs11: <ssh-server-example.com> Enter PIN for 'SSH key': [ssh-server-example.com] $Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: You can use the same URI string in the
~/.ssh/configfile to make the configuration permanent:cat ~/.ssh/config IdentityFile "pkcs11:id=%01?module-path=/usr/lib64/pkcs11/opensc-pkcs11.so" $ ssh <ssh-server-example.com> Enter PIN for 'SSH key': [ssh-server-example.com] $
$ cat ~/.ssh/config IdentityFile "pkcs11:id=%01?module-path=/usr/lib64/pkcs11/opensc-pkcs11.so" $ ssh <ssh-server-example.com> Enter PIN for 'SSH key': [ssh-server-example.com] $Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
sshclient utility now automatically uses this URI and the key from the smart card.
1.6. Making OpenSSH more secure
You can tweak the system to increase security when using OpenSSH.
Note that changes in the /etc/ssh/sshd_config OpenSSH server configuration file require reloading the sshd daemon to take effect:
systemctl reload sshd
# systemctl reload sshdThe majority of security hardening configuration changes reduce compatibility with clients that do not support up-to-date algorithms or cipher suites.
- Disabling insecure connection protocols
- To make SSH truly effective, prevent the use of insecure connection protocols that are replaced by the OpenSSH suite. Otherwise, a user’s password might be protected using SSH for one session only to be captured later when logging in using Telnet.
- Disabling password-based authentication
- Disabling passwords for authentication and allowing only key pairs reduces the attack surface. See the Setting key-based authentication as the only method on an OpenSSH server section for more information.
- Stronger key types
Although the
ssh-keygencommand generates a pair of RSA keys by default, you can instruct it to generate Elliptic Curve Digital Signature Algorithm (ECDSA) or Edwards-Curve 25519 (Ed25519) keys by using the-toption. The ECDSA offers better performance than RSA at the equivalent symmetric key strength. It also generates shorter keys. The Ed25519 public-key algorithm is an implementation of twisted Edwards curves that is more secure and also faster than RSA, DSA, and ECDSA.OpenSSH creates RSA, ECDSA, and Ed25519 server host keys automatically if they are missing. To configure the host key creation in RHEL, use the
sshd-keygen@.serviceinstantiated service. For example, to disable the automatic creation of the RSA key type:systemctl mask sshd-keygen@rsa.service rm -f /etc/ssh/ssh_host_rsa_key* systemctl restart sshd
# systemctl mask sshd-keygen@rsa.service # rm -f /etc/ssh/ssh_host_rsa_key* # systemctl restart sshdCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIn images with the
cloud-initmethod enabled, thessh-keygenunits are automatically disabled. This is because thessh-keygen templateservice can interfere with thecloud-inittool and cause problems with host key generation. To prevent these problems theetc/systemd/system/sshd-keygen@.service.d/disable-sshd-keygen-if-cloud-init-active.confdrop-in configuration file disables thessh-keygenunits ifcloud-initis running.To allow only a particular key type for SSH connections, remove a comment out at the beginning of the relevant line in
/etc/ssh/sshd_config, and reload thesshdservice. For example, to allow only Ed25519 host keys, the corresponding lines must be as follows:# HostKey /etc/ssh/ssh_host_rsa_key # HostKey /etc/ssh/ssh_host_ecdsa_key HostKey /etc/ssh/ssh_host_ed25519_key
# HostKey /etc/ssh/ssh_host_rsa_key # HostKey /etc/ssh/ssh_host_ecdsa_key HostKey /etc/ssh/ssh_host_ed25519_keyCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantThe Ed25519 algorithm is not FIPS-140-compliant, and OpenSSH does not work with Ed25519 keys in FIPS mode.
- Non-default port
By default, the
sshddaemon listens on TCP port 22. Changing the port reduces the exposure of the system to attacks based on automated network scanning on the default port and therefore increases security through obscurity. You can specify the port using thePortdirective in the/etc/ssh/sshd_configconfiguration file.You also have to update the default SELinux policy to allow the use of a non-default port. To do so, use the
semanagetool from thepolicycoreutils-python-utilspackage:semanage port -a -t ssh_port_t -p tcp <port-number>
# semanage port -a -t ssh_port_t -p tcp <port-number>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Furthermore, update
firewalldconfiguration:firewall-cmd --add-port <port-number>/tcp firewall-cmd --remove-port=22/tcp firewall-cmd --runtime-to-permanent
# firewall-cmd --add-port <port-number>/tcp # firewall-cmd --remove-port=22/tcp # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow In the previous commands, replace <port-number> with the new port number specified using the
Portdirective.- No root login
If your particular use case does not require the possibility of logging in as the root user, you can set the
PermitRootLoginconfiguration directive tonoin the/etc/ssh/sshd_configfile. By disabling the possibility of logging in as the root user, the administrator can audit which users run what privileged commands after they log in as regular users and then gain root rights.Alternatively, set
PermitRootLogintoprohibit-password:PermitRootLogin prohibit-password
PermitRootLogin prohibit-passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow This enforces the use of key-based authentication instead of the use of passwords for logging in as root and reduces risks by preventing brute-force attacks.
- Using the X Security extension
The X server in Red Hat Enterprise Linux clients does not provide the X Security extension. Therefore, clients cannot request another security layer when connecting to untrusted SSH servers with X11 forwarding. Most applications are not able to run with this extension enabled anyway.
By default, the
ForwardX11Trustedoption in the/etc/ssh/ssh_config.d/05-redhat.conffile is set toyes, and there is no difference between thessh -X remote_machine(untrusted host) andssh -Y remote_machine(trusted host) command.If your scenario does not require the X11 forwarding feature at all, set the
X11Forwardingdirective in the/etc/ssh/sshd_configconfiguration file tono.- Restricting SSH access to specific users, groups, or IP ranges
The
AllowUsersandAllowGroupsdirectives in the/etc/ssh/sshd_configconfiguration file server enable you to permit only certain users, domains, or groups to connect to your OpenSSH server. You can combineAllowUsersandAllowGroupsto restrict access more precisely, for example:AllowUsers *@192.168.1.* *@10.0.0.* !*@192.168.1.2 AllowGroups example-group
AllowUsers *@192.168.1.* *@10.0.0.* !*@192.168.1.2 AllowGroups example-groupCopy to Clipboard Copied! Toggle word wrap Toggle overflow This configuration allows only connections if all of the following conditions meet:
- The connection’s source IP is within the 192.168.1.0/24 or 10.0.0.0/24 subnet.
- The source IP is not 192.168.1.2.
- The user is a member of the example-group group.
The OpenSSH server permits only connections that pass all Allow and Deny directives in
/etc/ssh/sshd_config. For example, if theAllowUsersdirective lists a user that is not part of a group listed in theAllowGroupsdirective, then the user cannot log in.Note that using allowlists (directives starting with Allow) is more secure than using blocklists (options starting with Deny) because allowlists block also new unauthorized users or groups.
- Changing system-wide cryptographic policies
OpenSSH uses RHEL system-wide cryptographic policies, and the default system-wide cryptographic policy level offers secure settings for current threat models. To make your cryptographic settings more strict, change the current policy level:
update-crypto-policies --set FUTURE Setting system policy to FUTURE
# update-crypto-policies --set FUTURE Setting system policy to FUTURECopy to Clipboard Copied! Toggle word wrap Toggle overflow WarningIf your system communicates with legacy systems, you might face interoperability problems due to the strict setting of the
FUTUREpolicy.
You can also disable only specific ciphers for the SSH protocol through the system-wide cryptographic policies. See the Customizing system-wide cryptographic policies with subpolicies section in the Security hardening document for more information.
- Opting out of system-wide cryptographic policies
To opt out of the system-wide cryptographic policies for your OpenSSH server, uncomment the line with the
CRYPTO_POLICY=variable in the/etc/sysconfig/sshdfile. After this change, values that you specify in theCiphers,MACs,KexAlgoritms, andGSSAPIKexAlgorithmssections in the/etc/ssh/sshd_configfile are not overridden.See the
sshd_config(5)man page for more information.To opt out of system-wide cryptographic policies for your OpenSSH client, perform one of the following tasks:
-
For a given user, override the global
ssh_configwith a user-specific configuration in the~/.ssh/configfile. -
For the entire system, specify the cryptographic policy in a drop-in configuration file located in the
/etc/ssh/ssh_config.d/directory, with a two-digit number prefix smaller than 5, so that it lexicographically precedes the05-redhat.conffile, and with a.confsuffix, for example,04-crypto-policy-override.conf.
-
For a given user, override the global
1.7. Connecting to a remote server through an SSH jump host
You can connect from your local system to a remote server through an intermediary server, also called jump host. A jump server bridges hosts from different security zones and can manage multiple client-server connections.
Prerequisites
- A jump host accepts SSH connections from your local system.
- A remote server accepts SSH connections from the jump host.
Procedure
If you connect through a jump server or more intermediary servers once, use the
ssh -Jcommand and specify the jump servers directly, for example:ssh -J <jump-1.example.com>,<jump-2.example.com>,<jump-3.example.com> <target-server-1.example.com>
$ ssh -J <jump-1.example.com>,<jump-2.example.com>,<jump-3.example.com> <target-server-1.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Change the host name-only notation in the previous command if the user names or SSH ports on the jump servers differ from the names and ports on the remote server, for example:
ssh -J <example.user.1>@<jump-1.example.com>:<75>,<example.user.2>@<jump-2.example.com>:<75>,<example.user.3>@<jump-3.example.com>:<75> <example.user.f>@<target-server-1.example.com>:<220>
$ ssh -J <example.user.1>@<jump-1.example.com>:<75>,<example.user.2>@<jump-2.example.com>:<75>,<example.user.3>@<jump-3.example.com>:<75> <example.user.f>@<target-server-1.example.com>:<220>Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you connect to a remote server through jump servers regularly, store the jump-server configuration in your SSH configuration file:
Define the jump host by editing the
~/.ssh/configfile on your local system, for example:Host <jump-server-1> HostName <jump-1.example.com>
Host <jump-server-1> HostName <jump-1.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
The
Hostparameter defines a name or alias for the host you can use insshcommands. The value can match the real host name, but can also be any string. -
The
HostNameparameter sets the actual host name or IP address of the jump host.
-
The
Add the remote server jump configuration with the
ProxyJumpdirective to~/.ssh/configfile on your local system, for example:Host <remote-server-1> HostName <target-server-1.example.com> ProxyJump <jump-server-1>
Host <remote-server-1> HostName <target-server-1.example.com> ProxyJump <jump-server-1>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use your local system to connect to the remote server through the jump server:
ssh <remote-server-1>
$ ssh <remote-server-1>Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command is equivalent to the
ssh -J jump-server1 remote-servercommand if you omit the previous configuration steps.
1.8. Configuring secure communication with the ssh system roles
As an administrator, you can use the sshd system role to configure SSH servers and the ssh system role to configure SSH clients consistently on any number of RHEL systems at the same time by using Red Hat Ansible Automation Platform.
1.8.1. How the sshd RHEL system role maps settings from a playbook to the configuration file
In the sshd RHEL system role playbook, you can define the parameters for the server SSH configuration file. If you do not specify these settings, the role produces the sshd_config file that matches the RHEL defaults.
In all cases, booleans correctly render as yes and no in the final configuration on your managed nodes. You can use lists to define multi-line configuration items. For example:
sshd_ListenAddress: - 0.0.0.0 - '::'
sshd_ListenAddress:
- 0.0.0.0
- '::'renders as:
ListenAddress 0.0.0.0 ListenAddress ::
ListenAddress 0.0.0.0
ListenAddress ::1.8.2. Configuring OpenSSH servers by using the sshd RHEL system role
You can use the sshd RHEL system role to configure multiple OpenSSH servers for secure remote access.
The role ensures secure communication environment for remote users by providing namely:
- Management of incoming SSH connections from remote clients
- Credentials verification
- Secure data transfer and command execution
You can use the sshd RHEL system role alongside with other RHEL system roles that change SSHD configuration, for example the Identity Management in Red Hat Enterprise Linux RHEL system roles. To prevent the configuration from being overwritten, ensure the sshd RHEL system role uses namespaces (RHEL 8 and earlier versions) or a drop-in directory (RHEL 9).
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
PasswordAuthentication: yes|no-
Controls whether the OpenSSH server (
sshd) accepts authentication from clients that use the username and password combination. Match:-
The match block allows the
rootuser to login by using a password only from the subnet192.0.2.0/24.
For details about the role variables and the OpenSSH configuration options used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.sshd/README.mdfile and thesshd_config(5)manual page on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Log in to the SSH server:
ssh <username>@<ssh_server>
$ ssh <username>@<ssh_server>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify the contents of the
sshd_configfile on the SSH server:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check that you can connect to the server as root from the
192.0.2.0/24subnet:Determine your IP address:
hostname -I 192.0.2.1
$ hostname -I 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the IP address is within the
192.0.2.1-192.0.2.254range, you can connect to the server.Connect to the server as
root:ssh root@<ssh_server>
$ ssh root@<ssh_server>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
1.8.3. How the ssh RHEL system role maps settings from a playbook to the configuration file
In the ssh RHEL system role playbook, you can define the parameters for the client SSH configuration file. If you do not specify these settings, the role produces a global ssh_config file that matches the RHEL defaults.
In all the cases, booleans correctly render as yes or no in the final configuration on your managed nodes. You can use lists to define multi-line configuration items. For example:
LocalForward: - 22 localhost:2222 - 403 localhost:4003
LocalForward:
- 22 localhost:2222
- 403 localhost:4003renders as:
LocalForward 22 localhost:2222 LocalForward 403 localhost:4003
LocalForward 22 localhost:2222
LocalForward 403 localhost:4003The configuration options are case sensitive.
1.8.4. Configuring OpenSSH clients by using the ssh RHEL system role
You can use the ssh RHEL system role to configure multiple OpenSSH clients.
OpenSSH clients enable the local user to establish a secure connection with the remote OpenSSH server by ensuring namely:
- Secure connection initiation
- Credentials provision
- Negotiation with the OpenSSH server on the encryption method used for the secure communication channel
- Ability to send files securely to and from the OpenSSH server
You can use the ssh RHEL system role alongside with other system roles that change SSH configuration, for example the Identity Management in Red Hat Enterprise Linux RHEL system roles. To prevent the configuration from being overwritten, make sure that the ssh RHEL system role uses a drop-in directory (default in RHEL 8 and later).
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
ssh_user: root-
Configures the
rootuser’s SSH client preferences on the managed nodes with certain configuration specifics. Compression: true- Compression is enabled.
ControlMaster: auto-
ControlMaster multiplexing is set to
auto. Host-
Creates alias
examplefor connecting to theserver.example.comhost as a user calleduser1. ssh_ForwardX11: no- X11 forwarding is disabled.
For details about the role variables and the OpenSSH configuration options used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.ssh/README.mdfile and thessh_config(5)manual page on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the managed node has the correct configuration by displaying the SSH configuration file:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
1.8.5. Using the sshd RHEL system role for non-exclusive configuration
By default, applying the sshd RHEL system role overwrites the entire configuration. This may be problematic if you have previously adjusted the configuration with a different playbook. You can use the non-exclusive configuration to apply changes only to selected configuration options.
You can apply a non-exclusive configuration:
- In RHEL 8 and earlier by using a configuration snippet.
-
In RHEL 9 and later by using files in a drop-in directory. The default configuration file is already placed in the drop-in directory as
/etc/ssh/sshd_config.d/00-ansible_system_role.conf.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:For managed nodes that run RHEL 8 or earlier:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow For managed nodes that run RHEL 9 or later:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbooks include the following:
sshd_config_namespace: <my-application>- The role places the configuration that you specify in the playbook to configuration snippets in the existing configuration file under the given namespace. You need to select a different namespace when running the role from a different context.
sshd_config_file: /etc/ssh/sshd_config.d/<42-my-application>.conf-
In the
sshd_config_filevariable, define the.conffile into which thesshdsystem role writes the configuration options. Use a two-digit prefix, for example42-to specify the order in which the configuration files will be applied. AcceptEnv:Controls which environment variables the OpenSSH server (
sshd) will accept from a client:-
LANG: defines the language and locale settings. -
LS_COLORS: defines the displaying color scheme for thelscommand in the terminal. -
EDITOR: specifies the default text editor for the command-line programs that need to open an editor.
-
For details about the role variables and the OpenSSH configuration options used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.sshd/README.mdfile and thesshd_config(5)manual page on the control node.
Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify the configuration on the SSH server:
For managed nodes that run RHEL 8 or earlier:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow For managed nodes that run RHEL 9 or later:
cat /etc/ssh/sshd_config.d/42-my-application.conf # Ansible managed # AcceptEnv LANG LS_COLORS EDITOR
# cat /etc/ssh/sshd_config.d/42-my-application.conf # Ansible managed # AcceptEnv LANG LS_COLORS EDITORCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 2. Creating and managing TLS keys and certificates
You can encrypt communication transmitted between two systems by using the TLS (Transport Layer Security) protocol. This standard uses asymmetric cryptography with private and public keys, digital signatures, and certificates.
2.1. TLS certificates
TLS (Transport Layer Security) is a protocol that enables client-server applications to pass information securely. TLS uses a system of public and private key pairs to encrypt communication transmitted between clients and servers. TLS is the successor protocol to SSL (Secure Sockets Layer).
TLS uses X.509 certificates to bind identities, such as hostnames or organizations, to public keys using digital signatures. X.509 is a standard that defines the format of public key certificates.
Authentication of a secure application depends on the integrity of the public key value in the application’s certificate. If an attacker replaces the public key with its own public key, it can impersonate the true application and gain access to secure data. To prevent this type of attack, all certificates must be signed by a certification authority (CA). A CA is a trusted node that confirms the integrity of the public key value in a certificate.
A CA signs a public key by adding its digital signature and issues a certificate. A digital signature is a message encoded with the CA’s private key. The CA’s public key is made available to applications by distributing the certificate of the CA. Applications verify that certificates are validly signed by decoding the CA’s digital signature with the CA’s public key.
To have a certificate signed by a CA, you must generate a public key, and send it to a CA for signing. This is referred to as a certificate signing request (CSR). A CSR contains also a distinguished name (DN) for the certificate. The DN information that you can provide for either type of certificate can include a two-letter country code for your country, a full name of your state or province, your city or town, a name of your organization, your email address, and it can also be empty. Many current commercial CAs prefer the Subject Alternative Name extension and ignore DNs in CSRs.
RHEL provides two main toolkits for working with TLS certificates: GnuTLS and OpenSSL. You can create, read, sign, and verify certificates using the openssl utility from the openssl package. The certtool utility provided by the gnutls-utils package can do the same operations using a different syntax and above all a different set of libraries in the back end.
2.2. Creating a private CA using OpenSSL
Private certificate authorities (CA) are useful when your scenario requires verifying entities within your internal network. For example, use a private CA when you create a VPN gateway with authentication based on certificates signed by a CA under your control or when you do not want to pay a commercial CA. To sign certificates in such use cases, the private CA uses a self-signed certificate.
Prerequisites
-
You have
rootprivileges or permissions to enter administrative commands withsudo. Commands that require such privileges are marked with#.
Procedure
Generate a private key for your CA. For example, the following command creates a 256-bit Elliptic Curve Digital Signature Algorithm (ECDSA) key:
openssl genpkey -algorithm ec -pkeyopt ec_paramgen_curve:P-256 -out <ca.key>
$ openssl genpkey -algorithm ec -pkeyopt ec_paramgen_curve:P-256 -out <ca.key>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The time for the key-generation process depends on the hardware and entropy of the host, the selected algorithm, and the length of the key.
Create a certificate signed using the private key generated in the previous command:
openssl req -key <ca.key> -new -x509 -days 3650 -addext keyUsage=critical,keyCertSign,cRLSign -subj "/CN=<Example_CA>" -out <ca.crt>
$ openssl req -key <ca.key> -new -x509 -days 3650 -addext keyUsage=critical,keyCertSign,cRLSign -subj "/CN=<Example_CA>" -out <ca.crt>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The generated
ca.crtfile is a self-signed CA certificate that you can use to sign other certificates for ten years. In the case of a private CA, you can replace <Example_CA> with any string as the common name (CN).Set secure permissions on the private key of your CA, for example:
chown <root>:<root> <ca.key> chmod 600 <ca.key>
# chown <root>:<root> <ca.key> # chmod 600 <ca.key>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
To use a self-signed CA certificate as a trust anchor on client systems, copy the CA certificate to the client and add it to the clients' system-wide truststore as
root:trust anchor <ca.crt>
# trust anchor <ca.crt>Copy to Clipboard Copied! Toggle word wrap Toggle overflow See Chapter 3, Using shared system certificates for more information.
Verification
Create a certificate signing request (CSR), and use your CA to sign the request. The CA must successfully create a certificate based on the CSR, for example:
openssl x509 -req -in <client-cert.csr> -CA <ca.crt> -CAkey <ca.key> -CAcreateserial -days 365 -extfile <openssl.cnf> -extensions <client-cert> -out <client-cert.crt> Signature ok subject=C = US, O = Example Organization, CN = server.example.com Getting CA Private Key
$ openssl x509 -req -in <client-cert.csr> -CA <ca.crt> -CAkey <ca.key> -CAcreateserial -days 365 -extfile <openssl.cnf> -extensions <client-cert> -out <client-cert.crt> Signature ok subject=C = US, O = Example Organization, CN = server.example.com Getting CA Private KeyCopy to Clipboard Copied! Toggle word wrap Toggle overflow See Section 2.5, “Using a private CA to issue certificates for CSRs with OpenSSL” for more information.
Display the basic information about your self-signed CA:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify the consistency of the private key:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.3. Creating a private key and a CSR for a TLS server certificate using OpenSSL
You can use TLS-encrypted communication channels only if you have a valid TLS certificate from a certificate authority (CA). To obtain the certificate, you must create a private key and a certificate signing request (CSR) for your server first.
Procedure
Generate a private key on your server system, for example:
openssl genpkey -algorithm ec -pkeyopt ec_paramgen_curve:P-256 -out <server-private.key>
$ openssl genpkey -algorithm ec -pkeyopt ec_paramgen_curve:P-256 -out <server-private.key>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Use a text editor of your choice to prepare a configuration file that simplifies creating your CSR, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
extendedKeyUsage = serverAuthoption limits the use of a certificate.Create a CSR using the private key you created previously:
openssl req -key <server-private.key> -config <example_server.cnf> -new -out <server-cert.csr>
$ openssl req -key <server-private.key> -config <example_server.cnf> -new -out <server-cert.csr>Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you omit the
-configoption, therequtility prompts you for additional information, for example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- Submit the CSR to a CA of your choice for signing. Alternatively, for an internal use scenario within a trusted network, use your private CA for signing. See Section 2.5, “Using a private CA to issue certificates for CSRs with OpenSSL” for more information.
Verification
After you obtain the requested certificate from the CA, check that the human-readable parts of the certificate match your requirements, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.4. Creating a private key and a CSR for a TLS client certificate using OpenSSL
You can use TLS-encrypted communication channels only if you have a valid TLS certificate from a certificate authority (CA). To obtain the certificate, you must create a private key and a certificate signing request (CSR) for your client first.
Procedure
Generate a private key on your client system, for example:
openssl genpkey -algorithm ec -pkeyopt ec_paramgen_curve:P-256 -out <client-private.key>
$ openssl genpkey -algorithm ec -pkeyopt ec_paramgen_curve:P-256 -out <client-private.key>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Use a text editor of your choice to prepare a configuration file that simplifies creating your CSR, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
extendedKeyUsage = clientAuthoption limits the use of a certificate.Create a CSR using the private key you created previously:
openssl req -key <client-private.key> -config <example_client.cnf> -new -out <client-cert.csr>
$ openssl req -key <client-private.key> -config <example_client.cnf> -new -out <client-cert.csr>Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you omit the
-configoption, therequtility prompts you for additional information, for example:You are about to be asked to enter information that will be incorporated into your certificate request. … Common Name (eg, your name or your server's hostname) []: <client.example.com> Email Address []: <client@example.com>
You are about to be asked to enter information that will be incorporated into your certificate request. … Common Name (eg, your name or your server's hostname) []: <client.example.com> Email Address []: <client@example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- Submit the CSR to a CA of your choice for signing. Alternatively, for an internal use scenario within a trusted network, use your private CA for signing. See Section 2.5, “Using a private CA to issue certificates for CSRs with OpenSSL” for more information.
Verification
Check that the human-readable parts of the certificate match your requirements, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.5. Using a private CA to issue certificates for CSRs with OpenSSL
To enable systems to establish a TLS-encrypted communication channel, a certificate authority (CA) must provide valid certificates to them. If you have a private CA, you can create the requested certificates by signing certificate signing requests (CSRs) from the systems.
Prerequisites
- You have already configured a private CA. See the Creating a private CA by using OpenSSL section for more information.
- You have a file containing a CSR. You can find an example of creating the CSR in the Section 2.3, “Creating a private key and a CSR for a TLS server certificate using OpenSSL” section.
Procedure
Optional: Use a text editor of your choice to prepare an OpenSSL configuration file for adding extensions to certificates, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the previous example illustrates only the principle and
openssldoes not add all extensions to the certificate automatically. You must add the extensions you require either to the CNF file or append them to parameters of theopensslcommand.Use the
x509utility to create a certificate based on a CSR, for example:openssl x509 -req -in <server-cert.csr> -CA <ca.crt> -CAkey <ca.key> -CAcreateserial -days 365 -extfile <openssl.cnf> -extensions <server-cert> -out <server-cert.crt> Signature ok subject=C = US, O = Example Organization, CN = server.example.com Getting CA Private Key
$ openssl x509 -req -in <server-cert.csr> -CA <ca.crt> -CAkey <ca.key> -CAcreateserial -days 365 -extfile <openssl.cnf> -extensions <server-cert> -out <server-cert.crt> Signature ok subject=C = US, O = Example Organization, CN = server.example.com Getting CA Private KeyCopy to Clipboard Copied! Toggle word wrap Toggle overflow To increase security, delete the serial-number file before you create another certificate from a CSR. This way, you ensure that the serial number is always random. If you omit the
CAserialoption for specifying a custom file name, the serial-number file name is the same as the file name of the certificate, but its extension is replaced with the.srlextension (server-cert.srlin the previous example).
2.6. Creating a private CA using GnuTLS
Private certificate authorities (CA) are useful when your scenario requires verifying entities within your internal network. For example, use a private CA when you create a VPN gateway with authentication based on certificates signed by a CA under your control or when you do not want to pay a commercial CA. To sign certificates in such use cases, the private CA uses a self-signed certificate.
Prerequisites
-
You have
rootprivileges or permissions to enter administrative commands withsudo. Commands that require such privileges are marked with#. You have already installed GnuTLS on your system. If you did not, you can use this command:
yum install gnutls-utils
$ yum install gnutls-utilsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure
Generate a private key for your CA. For example, the following command creates a 256-bit ECDSA (Elliptic Curve Digital Signature Algorithm) key:
certtool --generate-privkey --sec-param High --key-type=ecdsa --outfile <ca.key>
$ certtool --generate-privkey --sec-param High --key-type=ecdsa --outfile <ca.key>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The time for the key-generation process depends on the hardware and entropy of the host, the selected algorithm, and the length of the key.
Create a template file for a certificate.
Create a file with a text editor of your choice, for example:
vi <ca.cfg>
$ vi <ca.cfg>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the file to include the necessary certification details:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a certificate signed using the private key generated in step 1:
The generated <ca.crt> file is a self-signed CA certificate that you can use to sign other certificates for one year. <ca.crt> file is the public key (certificate). The loaded file <ca.key> is the private key. You should keep this file in safe location.
certtool --generate-self-signed --load-privkey <ca.key> --template <ca.cfg> --outfile <ca.crt>
$ certtool --generate-self-signed --load-privkey <ca.key> --template <ca.cfg> --outfile <ca.crt>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set secure permissions on the private key of your CA, for example:
chown <root>:<root> <ca.key> chmod 600 <ca.key>
# chown <root>:<root> <ca.key> # chmod 600 <ca.key>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
To use a self-signed CA certificate as a trust anchor on client systems, copy the CA certificate to the client and add it to the clients' system-wide truststore as
root:trust anchor <ca.crt>
# trust anchor <ca.crt>Copy to Clipboard Copied! Toggle word wrap Toggle overflow See Chapter 3, Using shared system certificates for more information.
Verification
Display the basic information about your self-signed CA:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a certificate signing request (CSR), and use your CA to sign the request. The CA must successfully create a certificate based on the CSR, for example:
Generate a private key for your CA:
certtool --generate-privkey --outfile <example-server.key>
$ certtool --generate-privkey --outfile <example-server.key>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Open a new configuration file in a text editor of your choice, for example:
vi <example-server.cfg>
$ vi <example-server.cfg>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the file to include the necessary certification details:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Generate a request with the previously created private key:
certtool --generate-request --load-privkey <example-server.key> --template <example-server.cfg> --outfile <example-server.crq>
$ certtool --generate-request --load-privkey <example-server.key> --template <example-server.cfg> --outfile <example-server.crq>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Generate the certificate and sign it with the private key of the CA:
certtool --generate-certificate --load-request <example-server.crq> --load-ca-certificate <ca.crt> --load-ca-privkey <ca.key> --outfile <example-server.crt>
$ certtool --generate-certificate --load-request <example-server.crq> --load-ca-certificate <ca.crt> --load-ca-privkey <ca.key> --outfile <example-server.crt>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.7. Creating a private key and a CSR for a TLS server certificate using GnuTLS
To obtain the certificate, you must create a private key and a certificate signing request (CSR) for your server first.
Procedure
Generate a private key on your server system, for example:
certtool --generate-privkey --sec-param High --outfile <example-server.key>
$ certtool --generate-privkey --sec-param High --outfile <example-server.key>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Use a text editor of your choice to prepare a configuration file that simplifies creating your CSR, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a CSR using the private key you created previously:
certtool --generate-request --template <example-server.cfg> --load-privkey <example-server.key> --outfile <example-server.crq>
$ certtool --generate-request --template <example-server.cfg> --load-privkey <example-server.key> --outfile <example-server.crq>Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you omit the
--templateoption, thecertoolutility prompts you for additional information, for example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- Submit the CSR to a CA of your choice for signing. Alternatively, for an internal use scenario within a trusted network, use your private CA for signing. See the Using a private CA to issue certificates for CSRs with GnuTLS section for more information.
Verification
After you obtain the requested certificate from the CA, check that the human-readable parts of the certificate match your requirements, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.8. Creating a private key and a CSR for a TLS client certificate using GnuTLS
To obtain the certificate, you must create a private key and a certificate signing request (CSR) for your client first.
Procedure
Generate a private key on your client system, for example:
certtool --generate-privkey --sec-param High --outfile <example-client.key>
$ certtool --generate-privkey --sec-param High --outfile <example-client.key>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Use a text editor of your choice to prepare a configuration file that simplifies creating your CSR, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a CSR using the private key you created previously:
certtool --generate-request --template <example-client.cfg> --load-privkey <example-client.key> --outfile <example-client.crq>
$ certtool --generate-request --template <example-client.cfg> --load-privkey <example-client.key> --outfile <example-client.crq>Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you omit the
--templateoption, thecerttoolutility prompts you for additional information, for example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- Submit the CSR to a CA of your choice for signing. Alternatively, for an internal use scenario within a trusted network, use your private CA for signing. See Section 2.9, “Using a private CA to issue certificates for CSRs with GnuTLS” for more information.
Verification
Check that the human-readable parts of the certificate match your requirements, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.9. Using a private CA to issue certificates for CSRs with GnuTLS
To enable systems to establish a TLS-encrypted communication channel, a certificate authority (CA) must provide valid certificates to them. If you have a private CA, you can create the requested certificates by signing certificate signing requests (CSRs) from the systems.
Prerequisites
- You have already configured a private CA. See Section 2.6, “Creating a private CA using GnuTLS” for more information.
- You have a file containing a CSR. You can find an example of creating the CSR in Section 2.7, “Creating a private key and a CSR for a TLS server certificate using GnuTLS” .
Procedure
Optional: Use a text editor of your choice to prepare an GnuTLS configuration file for adding extensions to certificates, for example:
vi <server-extensions.cfg> honor_crq_extensions ocsp_uri = "http://ocsp.example.com"
$ vi <server-extensions.cfg> honor_crq_extensions ocsp_uri = "http://ocsp.example.com"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
certtoolutility to create a certificate based on a CSR, for example:certtool --generate-certificate --load-request <example-server.crq> --load-ca-privkey <ca.key> --load-ca-certificate <ca.crt> --template <server-extensions.cfg> --outfile <example-server.crt>
$ certtool --generate-certificate --load-request <example-server.crq> --load-ca-privkey <ca.key> --load-ca-certificate <ca.crt> --template <server-extensions.cfg> --outfile <example-server.crt>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 4. Planning and implementing TLS
TLS (Transport Layer Security) is a cryptographic protocol used to secure network communications. When hardening system security settings by configuring preferred key-exchange protocols, authentication methods, and encryption algorithms, it is necessary to bear in mind that the broader the range of supported clients, the lower the resulting security. Conversely, strict security settings lead to limited compatibility with clients, which can result in some users being locked out of the system. Be sure to target the strictest available configuration and only relax it when it is required for compatibility reasons.
4.1. SSL and TLS protocols
The Secure Sockets Layer (SSL) protocol was originally developed by Netscape Corporation to provide a mechanism for secure communication over the Internet. Subsequently, the protocol was adopted by the Internet Engineering Task Force (IETF) and renamed to Transport Layer Security (TLS).
The TLS protocol sits between an application protocol layer and a reliable transport layer, such as TCP/IP. It is independent of the application protocol and can thus be layered underneath many different protocols, for example: HTTP, FTP, SMTP, and so on.
| Protocol version | Usage recommendation |
|---|---|
| SSL v2 | Do not use. Has serious security vulnerabilities. Removed from the core crypto libraries since RHEL 7. |
| SSL v3 | Do not use. Has serious security vulnerabilities. Removed from the core crypto libraries since RHEL 8. |
| TLS 1.0 |
Not recommended to use. Has known issues that cannot be mitigated in a way that guarantees interoperability, and does not support modern cipher suites. In RHEL 8, enabled only in the |
| TLS 1.1 |
Use for interoperability purposes where needed. Does not support modern cipher suites. In RHEL 8, enabled only in the |
| TLS 1.2 | Supports the modern AEAD cipher suites. This version is enabled in all system-wide crypto policies, but optional parts of this protocol contain vulnerabilities and TLS 1.2 also allows outdated algorithms. |
| TLS 1.3 | Recommended version. TLS 1.3 removes known problematic options, provides additional privacy by encrypting more of the negotiation handshake and can be faster thanks usage of more efficient modern cryptographic algorithms. TLS 1.3 is also enabled in all system-wide cryptographic policies. |
4.2. Security considerations for TLS in RHEL 8
In RHEL 8, cryptography-related considerations are significantly simplified thanks to the system-wide crypto policies. The DEFAULT crypto policy allows only TLS 1.2 and 1.3. To allow your system to negotiate connections using the earlier versions of TLS, you need to either opt out from following crypto policies in an application or switch to the LEGACY policy with the update-crypto-policies command. See Using system-wide cryptographic policies for more information.
The default settings provided by libraries included in RHEL 8 are secure enough for most deployments. The TLS implementations use secure algorithms where possible while not preventing connections from or to legacy clients or servers. Apply hardened settings in environments with strict security requirements where legacy clients or servers that do not support secure algorithms or protocols are not expected or allowed to connect.
The most straightforward way to harden your TLS configuration is switching the system-wide cryptographic policy level to FUTURE using the update-crypto-policies --set FUTURE command.
Algorithms disabled for the LEGACY cryptographic policy do not conform to Red Hat’s vision of RHEL 8 security, and their security properties are not reliable. Consider moving away from using these algorithms instead of re-enabling them. If you do decide to re-enable them, for example for interoperability with old hardware, treat them as insecure and apply extra protection measures, such as isolating their network interactions to separate network segments. Do not use them across public networks.
If you decide to not follow RHEL system-wide crypto policies or create custom cryptographic policies tailored to your setup, use the following recommendations for preferred protocols, cipher suites, and key lengths on your custom configuration:
4.2.1. Protocols
The latest version of TLS provides the best security mechanism. Unless you have a compelling reason to include support for older versions of TLS, allow your systems to negotiate connections using at least TLS version 1.2.
Note that even though RHEL 8 supports TLS version 1.3, not all features of this protocol are fully supported by RHEL 8 components. For example, the 0-RTT (Zero Round Trip Time) feature, which reduces connection latency, is not yet fully supported by the Apache web server.
4.2.2. Cipher suites
Modern, more secure cipher suites should be preferred to old, insecure ones. Always disable the use of eNULL and aNULL cipher suites, which do not offer any encryption or authentication at all. If at all possible, ciphers suites based on RC4 or HMAC-MD5, which have serious shortcomings, should also be disabled. The same applies to the so-called export cipher suites, which have been intentionally made weaker, and thus are easy to break.
While not immediately insecure, cipher suites that offer less than 128 bits of security should not be considered for their short useful life. Algorithms that use 128 bits of security or more can be expected to be unbreakable for at least several years, and are thus strongly recommended. Note that while 3DES ciphers advertise the use of 168 bits, they actually offer 112 bits of security.
Always prefer cipher suites that support (perfect) forward secrecy (PFS), which ensures the confidentiality of encrypted data even in case the server key is compromised. This rules out the fast RSA key exchange, but allows for the use of ECDHE and DHE. Of the two, ECDHE is the faster and therefore the preferred choice.
You should also prefer AEAD ciphers, such as AES-GCM, over CBC-mode ciphers as they are not vulnerable to padding oracle attacks. Additionally, in many cases, AES-GCM is faster than AES in CBC mode, especially when the hardware has cryptographic accelerators for AES.
Note also that when using the ECDHE key exchange with ECDSA certificates, the transaction is even faster than a pure RSA key exchange. To provide support for legacy clients, you can install two pairs of certificates and keys on a server: one with ECDSA keys (for new clients) and one with RSA keys (for legacy ones).
4.2.3. Public key length
When using RSA keys, always prefer key lengths of at least 3072 bits signed by at least SHA-256, which is sufficiently large for true 128 bits of security.
The security of your system is only as strong as the weakest link in the chain. For example, a strong cipher alone does not guarantee good security. The keys and the certificates are just as important, as well as the hash functions and keys used by the Certification Authority (CA) to sign your keys.
4.3. Hardening TLS configuration in applications
In RHEL, system-wide crypto policies provide a convenient way to ensure that your applications that use cryptographic libraries do not allow known insecure protocols, ciphers, or algorithms.
If you want to harden your TLS-related configuration with your customized cryptographic settings, you can use the cryptographic configuration options described in this section, and override the system-wide crypto policies just in the minimum required amount.
Regardless of the configuration you choose to use, always ensure that your server application enforces server-side cipher order, so that the cipher suite to be used is determined by the order you configure.
4.3.1. Configuring the Apache HTTP server to use TLS
The Apache HTTP Server can use both OpenSSL and NSS libraries for its TLS needs. RHEL 8 provides the mod_ssl functionality through eponymous packages:
yum install mod_ssl
# yum install mod_ssl
The mod_ssl package installs the /etc/httpd/conf.d/ssl.conf configuration file, which can be used to modify the TLS-related settings of the Apache HTTP Server.
Install the httpd-manual package to obtain complete documentation for the Apache HTTP Server, including TLS configuration. The directives available in the /etc/httpd/conf.d/ssl.conf configuration file are described in detail in the /usr/share/httpd/manual/mod/mod_ssl.html file. Examples of various settings are described in the /usr/share/httpd/manual/ssl/ssl_howto.html file.
When modifying the settings in the /etc/httpd/conf.d/ssl.conf configuration file, be sure to consider the following three directives at the minimum:
SSLProtocol- Use this directive to specify the version of TLS or SSL you want to allow.
SSLCipherSuite- Use this directive to specify your preferred cipher suite or disable the ones you want to disallow.
SSLHonorCipherOrder-
Uncomment and set this directive to
onto ensure that the connecting clients adhere to the order of ciphers you specified.
For example, to use only the TLS 1.2 and 1.3 protocol:
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1See the Configuring TLS encryption on an Apache HTTP Server chapter in the Deploying different types of servers document for more information.
4.3.2. Configuring the Nginx HTTP and proxy server to use TLS
To enable TLS 1.3 support in Nginx, add the TLSv1.3 value to the ssl_protocols option in the server section of the /etc/nginx/nginx.conf configuration file:
See the Adding TLS encryption to an Nginx web server chapter in the Deploying different types of servers document for more information.
4.3.3. Configuring the Dovecot mail server to use TLS
To configure your installation of the Dovecot mail server to use TLS, modify the /etc/dovecot/conf.d/10-ssl.conf configuration file. You can find an explanation of some of the basic configuration directives available in that file in the /usr/share/doc/dovecot/wiki/SSL.DovecotConfiguration.txt file, which is installed along with the standard installation of Dovecot.
When modifying the settings in the /etc/dovecot/conf.d/10-ssl.conf configuration file, be sure to consider the following three directives at the minimum:
ssl_protocols- Use this directive to specify the version of TLS or SSL you want to allow or disable.
ssl_cipher_list- Use this directive to specify your preferred cipher suites or disable the ones you want to disallow.
ssl_prefer_server_ciphers-
Uncomment and set this directive to
yesto ensure that the connecting clients adhere to the order of ciphers you specified.
For example, the following line in /etc/dovecot/conf.d/10-ssl.conf allows only TLS 1.1 and later:
ssl_protocols = !SSLv2 !SSLv3 !TLSv1
ssl_protocols = !SSLv2 !SSLv3 !TLSv1Chapter 5. Setting up an IPsec VPN
Configure and manage a secure Virtual Private Network (VPN) by using the Libreswan implementation of the IPsec protocol suite to create encrypted tunnels for secure data transmission over the internet.
IPsec tunnels ensure the confidentiality and integrity of data in transit. Common use cases include connecting branch offices to headquarters or providing remote users with secure access to a corporate network.
RHEL provides different options to configure Libreswan:
- Manually edit the Libreswan configuration files for granular control over advanced options.
-
Use the
vpnRHEL system role to automate the process of creating Libreswan VPN configurations.
Libreswan does not use terms such as "client" and "server". Instead, IPsec refers to endpoints as "left" and "right". This design often enables you to use the same configuration on both hosts because Libreswan dynamically determines which role to adopt. As a convention, administrators typically use "left" for the local host and "right" for the remote host.
Libreswan is the only supported VPN technology in RHEL.
IPsec relies on standardized protocols, such as Internet Key Exchange (IKE), to ensure that different systems can communicate effectively. However, in practice, minor differences in how vendors implement these standards can lead to compatibility problems. If you encounter such interoperability issues when connecting Libreswan to a third-party IPsec peer, contact Red Hat Support.
5.1. Components in an IPsec VPN
Before setting up an IPsec VPN, it is important to understand its main components: Internet Key Exchange (IKE) for authentication and negotiation, and IPsec for data encryption and transport.
IKE is the protocol two endpoints use to authenticate each other and negotiate connection rules, including encryption algorithms. Libreswan implements IKE in a daemon called pluto.
IPsec is the part of the protocol that actually encrypts and transports data according to the policy agreed upon during the IKE negotiation. The Linux kernel implements the IPsec protocol suite.
5.2. Libreswan authentication methods
Select the appropriate authentication method to establish a secure VPN connection based on your security needs and network environment.
Libreswan supports the following authentication methods:
- Pre-Shared key
- The Pre-Shared Key (PSK) method involves both endpoints by using the same secret to authenticate each other. PSKs offer simplicity and broad compatibility, making them suitable for small-scale deployments. However, managing PSKs is risky if the key is reused or not rotated frequently. For security, PSKs should consist of more than 64 random characters and must meet FIPS strength requirements if your host operates in FIPS mode.
- Raw RSA key
- This method uses an RSA public and private key pair on each peer for mutual identification. Raw RSA keys provide stronger security than PSKs and are ideal for environments where a full certificate infrastructure is not required.
- X.509 certificates
- This method uses X.509 certificates issued by a trusted Certificate Authority (CA). Each peer proves its identity by using its certificate and private key, which the other peer verifies against the trusted CA. While providing the highest level of security and scalability for large enterprises, this method is more complex as it requires deploying and maintaining a public key infrastructure (PKI).
- NULL authentication
- This method provides only encryption with no authentication between peers. Because it does not verify the identity of the remote endpoint, NULL authentication is insecure and offers no protection against man-in-the-middle attacks.
- Protection against quantum computers
- While not a standalone authentication method, Libreswan offers Post-quantum Pre-shared Keys (PPKs) to protect modern IKEv2 connections from future attacks by quantum computers. This feature is necessary because neither the older IKEv1 protocol nor standard IKEv2 is inherently quantum-resistant on its own. A PPK adds another layer of security on top of the primary authentication method, and its security relies on using a cryptographically strong key that has been distributed securely through an external communication channel.
5.3. Installing Libreswan
Before you can set a VPN through the Libreswan IPsec/IKE implementation, you must install the corresponding packages, start the ipsec service, and allow the service in your firewall.
Prerequisites
-
The
AppStreamrepository is enabled.
Procedure
Install the
libreswanpackages:yum install libreswan
# yum install libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you are re-installing Libreswan, remove its old database files and create a new database:
systemctl stop ipsec rm /etc/ipsec.d/*db ipsec initnss
# systemctl stop ipsec # rm /etc/ipsec.d/*db # ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the
ipsecservice, and enable the service to be started automatically on boot:systemctl enable ipsec --now
# systemctl enable ipsec --nowCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the firewall to allow 500 and 4500/UDP ports for the IKE, ESP, and AH protocols by adding the
ipsecservice:firewall-cmd --add-service="ipsec" firewall-cmd --runtime-to-permanent
# firewall-cmd --add-service="ipsec" # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.4. Creating a host-to-host VPN
You can configure Libreswan to create a host-to-host IPsec VPN between two hosts referred to as left and right using authentication by raw RSA keys.
Prerequisites
-
Libreswan is installed and the
ipsecservice is started on each node.
Procedure
Generate a raw RSA key pair on each host:
ipsec newhostkey
# ipsec newhostkeyCopy to Clipboard Copied! Toggle word wrap Toggle overflow The previous step returned the generated key’s
ckaid. Use thatckaidwith the following command on left, for example:ipsec showhostkey --left --ckaid 2d3ea57b61c9419dfd6cf43a1eb6cb306c0e857d
# ipsec showhostkey --left --ckaid 2d3ea57b61c9419dfd6cf43a1eb6cb306c0e857dCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output of the previous command generated the
leftrsasigkey=line required for the configuration. Do the same on the second host (right):ipsec showhostkey --right --ckaid a9e1f6ce9ecd3608c24e8f701318383f41798f03
# ipsec showhostkey --right --ckaid a9e1f6ce9ecd3608c24e8f701318383f41798f03Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the
/etc/ipsec.d/directory, create a newmy_host-to-host.conffile. Write the RSA host keys from the output of theipsec showhostkeycommands in the previous step to the new file. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow After importing keys, restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow Load the connection:
ipsec auto --add mytunnel
# ipsec auto --add mytunnelCopy to Clipboard Copied! Toggle word wrap Toggle overflow Establish the tunnel:
ipsec auto --up mytunnel
# ipsec auto --up mytunnelCopy to Clipboard Copied! Toggle word wrap Toggle overflow To automatically start the tunnel when the
ipsecservice is started, add the following line to the connection definition:auto=start
auto=startCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
5.5. Configuring a site-to-site VPN
To create a site-to-site IPsec VPN, by joining two networks, an IPsec tunnel between the two hosts is created. The hosts thus act as the end points, which are configured to permit traffic from one or more subnets to pass through. Therefore you can think of the host as gateways to the remote portion of the network.
The configuration of the site-to-site VPN only differs from the host-to-host VPN in that one or more networks or subnets must be specified in the configuration file.
Prerequisites
- A host-to-host VPN is already configured.
Procedure
Copy the file with the configuration of your host-to-host VPN to a new file, for example:
cp /etc/ipsec.d/my_host-to-host.conf /etc/ipsec.d/my_site-to-site.conf
# cp /etc/ipsec.d/my_host-to-host.conf /etc/ipsec.d/my_site-to-site.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the subnet configuration to the file created in the previous step, for example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
5.6. Configuring a remote access VPN
Road warriors are traveling users with mobile clients and a dynamically assigned IP address. The mobile clients authenticate using X.509 certificates.
The following example shows configuration for IKEv2, and it avoids using the IKEv1 XAUTH protocol.
On the server:
On the mobile client, the road warrior’s device, use a slight variation of the previous configuration:
If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
5.7. Configuring a mesh VPN
An IPsec mesh creates a fully interconnected network where every server can communicate securely and directly with every other server. This is ideal for distributed database clusters or high-availability environments that span multiple data centers or cloud providers.
The mesh VPN network can be configured in two ways:
- To require IPsec.
- To prefer IPsec but allow a fallback to clear-text communication.
Authentication between the nodes can be based on X.509 certificates or on DNS Security Extensions (DNSSEC).
You can use any regular IKEv2 authentication method for opportunistic IPsec, because these connections are regular Libreswan configurations, except for the opportunistic IPsec that is defined by right=%opportunisticgroup entry. A common authentication method is for hosts to authenticate each other based on X.509 certificates using a commonly shared certification authority (CA). Cloud deployments typically issue certificates for each node in the cloud as part of the standard procedure.
Do not use PreSharedKey (PSK) authentication because one compromised host would result in the group PSK secret being compromised as well.
You can use NULL authentication to deploy encryption between nodes without authentication, which protects only against passive attackers.
The following procedure uses X.509 certificates. You can generate these certificates by using any kind of CA management system, such as the Dogtag Certificate System. Dogtag assumes that the certificates for each node are available in the PKCS #12 format (.p12 files), which contain the private key, the node certificate, and the Root CA certificate used to validate other nodes' X.509 certificates.
Each node has an identical configuration with the exception of its X.509 certificate. This allows for adding new nodes without reconfiguring any of the existing nodes in the network. The PKCS #12 files require a "friendly name", for which we use the name "node" so that the configuration files referencing the friendly name can be identical for all nodes.
Prerequisites
-
Libreswan is installed, and the
ipsecservice is started on each node. A new NSS database is initialized.
If you already have an old NSS database, remove the old database files:
systemctl stop ipsec rm /etc/ipsec.d/*db
# systemctl stop ipsec # rm /etc/ipsec.d/*dbCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can initialize a new database with the following command:
ipsec initnss
# ipsec initnssCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure
On each node, import PKCS #12 files. This step requires the password used to generate the PKCS #12 files:
ipsec import nodeXXX.p12
# ipsec import nodeXXX.p12Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the following three connection definitions for the
IPsec required(private),IPsec optional(private-or-clear), andNo IPsec(clear) profiles:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
auto=<option>Specifies how Libreswan handles connection initiation. Valid options:
-
ondemand: Initiates a connection automatically when the kernel receives the first packet that matches a trap XFRM policy. Use this option for opportunistic IPsec or for connections that do not need to be active continuously. -
add: Prepares the connection and accepts incoming connection requests. To initiate the connection from the local peer, use theipsec auto --upcommand. -
start: Automatically activates the connection when the Libreswan service starts.
-
leftid=%fromcertandrightid=%fromcert- Configures Libreswan to retrieve the identity from the distinguished name (DN) field of the certificate.
leftcert="<server_certificate_nickname>"- Specifies the nickname of the server’s certificate used in the NSS database.
Add the IP address of the network to the corresponding category. For example, if all nodes reside in the
10.15.0.0/16network, and all nodes must use IPsec encryption:echo "10.15.0.0/16" >> /etc/ipsec.d/policies/private
# echo "10.15.0.0/16" >> /etc/ipsec.d/policies/privateCopy to Clipboard Copied! Toggle word wrap Toggle overflow To allow certain nodes, for example,
10.15.34.0/24, to work with and without IPsec, add those nodes to the private-or-clear group:echo "10.15.34.0/24" >> /etc/ipsec.d/policies/private-or-clear
# echo "10.15.34.0/24" >> /etc/ipsec.d/policies/private-or-clearCopy to Clipboard Copied! Toggle word wrap Toggle overflow To define a host, for example,
10.15.1.2, which is not capable of IPsec into the clear group, use:echo "10.15.1.2/32" >> /etc/ipsec.d/policies/clear
# echo "10.15.1.2/32" >> /etc/ipsec.d/policies/clearCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can create the files in the
/etc/ipsec.d/policiesdirectory from a template for each new node, or you can provision them by using Puppet or Ansible.Note that every node has the same list of exceptions or different traffic flow expectations. Two nodes, therefore, might not be able to communicate because one requires IPsec and the other cannot use IPsec.
Restart the node to add it to the configured mesh:
systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
Verification
Open an IPsec tunnel by using the
pingcommand:ping <nodeYYY>
# ping <nodeYYY>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the NSS database with the imported certification:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow See which tunnels are open on the node:
ipsec trafficstatus 006 #2: "private#10.15.0.0/16"[1] ...<nodeYYY>, type=ESP, add_time=1691399301, inBytes=512, outBytes=512, maxBytes=2^63B, id='C=US, ST=NC, O=Example Organization, CN=east'
# ipsec trafficstatus 006 #2: "private#10.15.0.0/16"[1] ...<nodeYYY>, type=ESP, add_time=1691399301, inBytes=512, outBytes=512, maxBytes=2^63B, id='C=US, ST=NC, O=Example Organization, CN=east'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.8. Deploying a FIPS-compliant IPsec VPN
RHEL in Federal Information Processing Standard (FIPS) mode exclusively uses validated cryptographic modules, automatically disabling legacy protocols and ciphers. Enabling FIPS mode is often a requirement for federal compliance and enhances system security.
The Libreswan IPsec implementation provided by RHEL is fully FIPS-compliant. When the system is in FIPS mode, Libreswan automatically uses the certified cryptographic modules without requiring any additional configuration, regardless of whether Libreswan is installed on a new FIPS-enabled system or when FIPS mode is activated on a system with an existing Libreswan VPN.
Prerequisites
-
The
AppStreamrepository is enabled.
Procedure
Install the
libreswanpackages:yum install libreswan
# yum install libreswanCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you are re-installing Libreswan, remove its old NSS database:
systemctl stop ipsec rm /etc/ipsec.d/*db
# systemctl stop ipsec # rm /etc/ipsec.d/*dbCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the
ipsecservice, and enable the service to be started automatically on boot:systemctl enable ipsec --now
# systemctl enable ipsec --nowCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the firewall to allow
500and4500UDP ports for the IKE, ESP, and AH protocols by adding theipsecservice:firewall-cmd --add-service="ipsec" firewall-cmd --runtime-to-permanent
# firewall-cmd --add-service="ipsec" # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow Switch the system to FIPS mode:
fips-mode-setup --enable
# fips-mode-setup --enableCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart your system to allow the kernel to switch to FIPS mode:
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm Libreswan is running in FIPS mode:
ipsec whack --fipsstatus 000 FIPS mode enabled
# ipsec whack --fipsstatus 000 FIPS mode enabledCopy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, check entries for the
ipsecunit in thesystemdjournal:journalctl -u ipsec ... Jan 22 11:26:50 localhost.localdomain pluto[3076]: FIPS Product: YES Jan 22 11:26:50 localhost.localdomain pluto[3076]: FIPS Kernel: YES Jan 22 11:26:50 localhost.localdomain pluto[3076]: FIPS Mode: YES
$ journalctl -u ipsec ... Jan 22 11:26:50 localhost.localdomain pluto[3076]: FIPS Product: YES Jan 22 11:26:50 localhost.localdomain pluto[3076]: FIPS Kernel: YES Jan 22 11:26:50 localhost.localdomain pluto[3076]: FIPS Mode: YESCopy to Clipboard Copied! Toggle word wrap Toggle overflow To see the available algorithms in FIPS mode:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To query disabled algorithms in FIPS mode:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To list all allowed algorithms and ciphers in FIPS mode:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.9. Protecting the IPsec NSS database by a password
By default, only the root user can access the IPsec Network Security Services (NSS) database in the /etc/ipsec.d/ directory. You can additionally protect the database with a password. This is required if you run RHEL in Federal Information Processing Standard (FIPS) mode.
In the previous releases of RHEL up to version 6.6, you had to protect the IPsec NSS database with a password to meet the FIPS 140-2 requirements because the NSS cryptographic libraries were certified for the FIPS 140-2 Level 2 standard. In RHEL 8, NIST certified NSS to Level 1 of this standard, and this status does not require password protection for the database.
Prerequisites
-
The
/etc/ipsec.d/directory contains NSS database files.
Procedure
Enable password protection for the
NSSdatabase for Libreswan:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
/etc/ipsec.d/nsspasswordfile that contains the password you have set in the previous step, for example:cat /etc/ipsec.d/nsspassword NSS Certificate DB:_<password>_
# cat /etc/ipsec.d/nsspassword NSS Certificate DB:_<password>_Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
nsspasswordfile use the following syntax:<token_1>:<password1> <token_2>:<password2>
<token_1>:<password1> <token_2>:<password2>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The default NSS software token is
NSS Certificate DB. If your system is running in FIPS mode, the name of the token isNSS FIPS 140-2 Certificate DB.Depending on your scenario, either start or restart the
ipsecservice after you finish thensspasswordfile:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Check that the
ipsecservice is running after you have added a non-empty password to its NSS database:systemctl status ipsec ● ipsec.service - Internet Key Exchange (IKE) Protocol Daemon for IPsec Loaded: loaded (/usr/lib/systemd/system/ipsec.service; enabled; vendor preset: disable> Active: active (running)...
# systemctl status ipsec ● ipsec.service - Internet Key Exchange (IKE) Protocol Daemon for IPsec Loaded: loaded (/usr/lib/systemd/system/ipsec.service; enabled; vendor preset: disable> Active: active (running)...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check that the
Journallog contains entries that confirm a successful initialization:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.10. Configuring TCP fallback for an IPsec VPN connection
Standard IPsec VPNs can fail on restrictive networks that block the UDP and Encapsulating Security Payload (ESP) protocols. To ensure connectivity in such environments, Libreswan can encapsulate all VPN traffic within a TCP connection.
Encapsulating VPN packets within TCP can reduce throughput and increase latency. For this reason, use TCP encapsulation only as a fallback option or if UDP-based connections are consistently blocked in your environment.
Prerequisites
- The IPsec connection is configured.
Procedure
Edit the
/etc/ipsec.conffile, and make the following changes in theconfig setupsection:Configure Libreswan to listen on a TCP port:
listen-tcp=yes
listen-tcp=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, Libreswan listens on port 4500. If you want to use a different port, enter:
tcp-remoteport=<port_number>
tcp-remoteport=<port_number>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Decide whether TCP should be used as a fallback option if UDP is not available or permanent:
As a fallback option, enter:
enable-tcp=fallback retransmit-timeout=5s
enable-tcp=fallback retransmit-timeout=5sCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, Libreswan waits 60 seconds after a failed attempt to connect by using UDP before retrying the connection over TCP. Lowering the
retransmit-timeoutvalue shortens the delay, enabling the fallback protocol to initiate more quickly.As a permanent replacement for UDP, enter:
enable-tcp=yes
enable-tcp=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you configured a TCP port other than the default 4500, open the port in the firewall:
firewall-cmd --permanent --add-port=<tcp_port>/tcp firewall-cmd --reload
# firewall-cmd --permanent --add-port=<tcp_port>/tcp # firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Repeat the procedure on the peers that use this gateway.
5.11. Configuring automatic detection and usage of ESP hardware offload to accelerate an IPsec connection
Offloading Encapsulating Security Payload (ESP) to the hardware accelerates IPsec connections over Ethernet. By default, Libreswan detects and enables hardware support. In case that the feature was disabled or explicitly enabled, you can switch back to automatic detection.
Prerequisites
- The network card supports ESP hardware offload.
- The network driver supports ESP hardware offload.
- The IPsec connection is configured and works.
Procedure
-
Edit the Libreswan configuration file in the
/etc/ipsec.d/directory of the connection that should use automatic detection of ESP hardware offload support. -
Ensure the
nic-offloadparameter is not set in the connection’s settings. If you removed
nic-offload, restart theipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the
tx_ipsecandrx_ipseccounters of the Ethernet device the IPsec connection uses:ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 10 rx_ipsec: 10# ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 10 rx_ipsec: 10Copy to Clipboard Copied! Toggle word wrap Toggle overflow Send traffic through the IPsec tunnel. For example, ping a remote IP address:
ping -c 5 remote_ip_address
# ping -c 5 remote_ip_addressCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the
tx_ipsecandrx_ipseccounters of the Ethernet device again:ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 15 rx_ipsec: 15# ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 15 rx_ipsec: 15Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the counter values have increased, ESP hardware offload works.
5.12. Configuring ESP hardware offload on a bond to accelerate an IPsec connection
Offloading Encapsulating Security Payload (ESP) to the hardware accelerates IPsec connections. If you use a network bond for fail-over reasons, the requirements and the procedure to configure ESP hardware offload are different from those using a regular Ethernet device. For example, in this scenario, you enable the offload support on the bond, and the kernel applies the settings to the ports of the bond.
Prerequisites
-
All network cards in the bond support ESP hardware offload. Use the
ethtool -k <interface_name> | grep "esp-hw-offload"command to verify whether each bond port supports this feature. - The bond is configured and works.
-
The bond uses the
active-backupmode. The bonding driver does not support any other modes for this feature. - The IPsec connection is configured and works.
Procedure
Enable ESP hardware offload support on the network bond:
nmcli connection modify bond0 ethtool.feature-esp-hw-offload on
# nmcli connection modify bond0 ethtool.feature-esp-hw-offload onCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command enables ESP hardware offload support on the
bond0connection.Reactivate the
bond0connection:nmcli connection up bond0
# nmcli connection up bond0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the Libreswan configuration file in the
/etc/ipsec.d/directory of the connection that should use ESP hardware offload, and append thenic-offload=yesstatement to the connection entry:conn example ... nic-offload=yesconn example ... nic-offload=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
The verification methods depend on various aspects, such as the kernel version and driver. For example, certain drivers provide counters, but their names can vary. See the documentation of your network driver for details.
The following verification steps work for the ixgbe driver on Red Hat Enterprise Linux 8:
Display the active port of the bond:
grep "Currently Active Slave" /proc/net/bonding/bond0 Currently Active Slave: enp1s0
# grep "Currently Active Slave" /proc/net/bonding/bond0 Currently Active Slave: enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the
tx_ipsecandrx_ipseccounters of the active port:ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 10 rx_ipsec: 10# ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 10 rx_ipsec: 10Copy to Clipboard Copied! Toggle word wrap Toggle overflow Send traffic through the IPsec tunnel. For example, ping a remote IP address:
ping -c 5 remote_ip_address
# ping -c 5 remote_ip_addressCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the
tx_ipsecandrx_ipseccounters of the active port again:ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 15 rx_ipsec: 15# ethtool -S enp1s0 | grep -E "_ipsec" tx_ipsec: 15 rx_ipsec: 15Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the counter values have increased, ESP hardware offload works.
5.13. Configuring IPsec VPN connections by using RHEL system roles
Configure IPsec VPN connections to establish encrypted tunnels over untrusted networks and ensure the integrity of data in transit. By using the RHEL system roles, you can automate the setup for use cases, such as connecting branch offices to headquarters.
The vpn RHEL system role can only create VPN configurations that use pre-shared keys (PSKs) or certificates to authenticate peers to each other.
5.13.1. Configuring an IPsec host-to-host VPN with PSK authentication by using the vpn RHEL system role
A host-to-host VPN establishes an encrypted connection between two devices, allowing applications to communicate safely over an insecure network. By using the vpn RHEL system role, you can automate the process of creating IPsec host-to-host connections.
For authentication, a pre-shared key (PSK) is a straightforward method that uses a single, shared secret known only to the two peers. This approach is simple to configure and ideal for basic setups where ease of deployment is a priority. However, you must keep the key strictly confidential. An attacker with access to the key can compromise the connection.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
hosts: <list>Defines a YAML dictionary with the peers between which you want to configure a VPN. If an entry is not an Ansible managed node, you must specify its fully-qualified domain name (FQDN) or IP address in the
hostnameparameter, for example:... - hosts: ... external-host.example.com: hostname: 192.0.2.1... - hosts: ... external-host.example.com: hostname: 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow The role configures the VPN connection on each managed node. The connections are named
<peer_A>-to-<peer_B>, for example,managed-node-01.example.com-to-managed-node-02.example.com. Note that the role cannot configure Libreswan on external (unmanaged) nodes. You must manually create the configuration on these peers.auth_method: psk-
Enables PSK authentication between the peers. The role uses
opensslon the control node to create the PSK. auto: <startup_method>-
Specifies the startup method of the connection. Valid values are
add,ondemand,start, andignore. For details, see theipsec.conf(5)man page on a system with Libreswan installed. The default value of this variable is null, which means no automatic startup operation. vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm that the connections are successfully started, for example:
ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"' ... 006 #3: "managed-node-01.example.com-to-managed-node-02.example.com", type=ESP, add_time=1741857153, inBytes=38622, outBytes=324626, maxBytes=2^63B, id='@managed-node-02.example.com'
# ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"' ... 006 #3: "managed-node-01.example.com-to-managed-node-02.example.com", type=ESP, add_time=1741857153, inBytes=38622, outBytes=324626, maxBytes=2^63B, id='@managed-node-02.example.com'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only succeeds if the VPN connection is active. If you set the
autovariable in the playbook to a value other thanstart, you might need to manually activate the connection on the managed nodes first.
Use the vpn RHEL system role to automate the process of creating an IPsec host-to-host VPN. To enhance security by minimizing the risk of control messages being intercepted or disrupted, configure separate connections for both the data traffic and the control traffic.
A host-to-host VPN establishes a direct, secure, and encrypted connection between two devices, allowing applications to communicate safely over an insecure network, such as the internet.
For authentication, a pre-shared key (PSK) is a straightforward method that uses a single, shared secret known only to the two peers. This approach is simple to configure and ideal for basic setups where ease of deployment is a priority. However, you must keep the key strictly confidential. An attacker with access to the key can compromise the connection.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
hosts: <list>Defines a YAML dictionary with the hosts between which you want to configure a VPN. The connections are named
<name>-<IP_address_A>-to-<IP_address_B>, for examplecontrol_plane_vpn-203.0.113.1-to-198.51.100.2.The role configures the VPN connection on each managed node. Note that the role cannot configure Libreswan on external (unmanaged) nodes. You must manually create the configuration on these hosts.
auth_method: psk-
Enables PSK authentication between the hosts. The role uses
opensslon the control node to create the pre-shared key. auto: <startup_method>-
Specifies the startup method of the connection. Valid values are
add,ondemand,start, andignore. For details, see theipsec.conf(5)man page on a system with Libreswan installed. The default value of this variable is null, which means no automatic startup operation. vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm that the connections are successfully started, for example:
ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "control_plane_vpn-203.0.113.1-to-198.51.100.2"' ... 006 #3: "control_plane_vpn-203.0.113.1-to-198.51.100.2", type=ESP, add_time=1741860073, inBytes=0, outBytes=0, maxBytes=2^63B, id='198.51.100.2'
# ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "control_plane_vpn-203.0.113.1-to-198.51.100.2"' ... 006 #3: "control_plane_vpn-203.0.113.1-to-198.51.100.2", type=ESP, add_time=1741860073, inBytes=0, outBytes=0, maxBytes=2^63B, id='198.51.100.2'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only succeeds if the VPN connection is active. If you set the
autovariable in the playbook to a value other thanstart, you might need to manually activate the connection on the managed nodes first.
5.13.3. Configuring an IPsec site-to-site VPN with PSK authentication by using the vpn RHEL system role
A site-to-site VPN establishes an encrypted tunnel between two distinct networks, seamlessly linking them across an insecure public network. By using the vpn RHEL system role, you can automate the process of creating IPsec site-to-site VPN connections.
A site-to-site VPN enables devices in a branch office to access resources at a corporate headquarters just as if they were all part of the same local network.
For authentication, a pre-shared key (PSK) is a straightforward method that uses a single, shared secret known only to the two peers. This approach is simple to configure and ideal for basic setups where ease of deployment is a priority. However, you must keep the key strictly confidential. An attacker with access to the key can compromise the connection.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
hosts: <list>Defines a YAML dictionary with the gateways between which you want to configure a VPN. If an entry is not an Ansible-managed node, you must specify its fully-qualified domain name (FQDN) or IP address in the
hostnameparameter, for example:... - hosts: ... external-host.example.com: hostname: 192.0.2.1... - hosts: ... external-host.example.com: hostname: 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow The role configures the VPN connection on each managed node. The connections are named
<gateway_A>-to-<gateway_B>, for example,managed-node-01.example.com-to-managed-node-02.example.com. Note that the role cannot configure Libreswan on external (unmanaged) nodes. You must manually create the configuration on these peers.subnets: <yaml_list_of_subnets>- Defines subnets in classless inter-domain routing (CIDR) format that are connected through the tunnel.
auth_method: psk-
Enables PSK authentication between the peers. The role uses
opensslon the control node to create the PSK. auto: <startup_method>-
Specifies the startup method of the connection. Valid values are
add,ondemand,start, andignore. For details, see theipsec.conf(5)man page on a system with Libreswan installed. The default value of this variable is null, which means no automatic startup operation. vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Confirm that the connections are successfully started, for example:
ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"' ... 006 #3: "managed-node-01.example.com-to-managed-node-02.example.com", type=ESP, add_time=1741857153, inBytes=38622, outBytes=324626, maxBytes=2^63B, id='@managed-node-02.example.com'
# ansible managed-node-01.example.com -m shell -a 'ipsec trafficstatus | grep "managed-node-01.example.com-to-managed-node-02.example.com"' ... 006 #3: "managed-node-01.example.com-to-managed-node-02.example.com", type=ESP, add_time=1741857153, inBytes=38622, outBytes=324626, maxBytes=2^63B, id='@managed-node-02.example.com'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only succeeds if the VPN connection is active. If you set the
autovariable in the playbook to a value other thanstart, you might need to manually activate the connection on the managed nodes first.
5.13.4. Configuring an IPsec mesh VPN with certificate-based authentication by using the vpn RHEL system role
An IPsec mesh creates a fully interconnected network where every server can communicate securely and directly with every other server. By using the vpn RHEL system role, you can automate configuring a VPN mesh with certificate-based authentication among managed nodes.
An IPsec mesh is ideal for distributed database clusters or high-availability environments that span multiple data centers or cloud providers. Establishing a direct, encrypted tunnel between each pair of servers ensures secure communication without a central bottleneck.
For authentication, using digital certificates managed by a Certificate Authority (CA) offers a highly secure and scalable solution. Each host in the mesh presents a certificate signed by a trusted CA. This method provides strong, verifiable authentication and simplifies user management. Access can be granted or revoked centrally at the CA, and Libreswan enforces this by checking each certificate against a certificate revocation list (CRL), denying access if a certificate appears on the list.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes. You prepared a PKCS #12 file for each managed node:
Each file contains:
- The private key of the server
- The server certificate
- The CA certificate
- If required, intermediate certificates
-
The files are named
<managed_node_name_as_in_the_inventory>.p12. - The files are stored in the same directory as the playbook.
The server certificate contains the following fields:
-
Extended Key Usage (EKU) is set to
TLS Web Server Authentication. - Common Name (CN) or Subject Alternative Name (SAN) is set to the fully-qualified domain name (FQDN) of the host.
- X509v3 CRL distribution points contain URLs to Certificate Revocation Lists (CRLs).
-
Extended Key Usage (EKU) is set to
Procedure
Edit the
~/inventoryfile, and append thecert_namevariable:managed-node-01.example.com cert_name=managed-node-01.example.com managed-node-02.example.com cert_name=managed-node-02.example.com managed-node-03.example.com cert_name=managed-node-03.example.com
managed-node-01.example.com cert_name=managed-node-01.example.com managed-node-02.example.com cert_name=managed-node-02.example.com managed-node-03.example.com cert_name=managed-node-03.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
cert_namevariable to the value of the common name (CN) field used in the certificate for each host. Typically, the CN field is set to the fully-qualified domain name (FQDN).Store your sensitive variables in an encrypted file:
Create the vault:
ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>
$ ansible-vault create ~/vault.yml New Vault password: <vault_password> Confirm New Vault password: <vault_password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
ansible-vault createcommand opens an editor, enter the sensitive data in the<key>: <value>format:pkcs12_pwd: <password>
pkcs12_pwd: <password>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the changes, and close the editor. Ansible encrypts the data in the vault.
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
opportunistic: true-
Enables an opportunistic mesh among multiple hosts. The
policiesvariable defines for which subnets and hosts traffic must or can be encrypted and which of them should continue using plain text connections. auth_method: cert- Enables certificate-based authentication. This requires that you specify the nickname of each managed node’s certificate in the inventory.
policies: <list_of_policies>Defines the Libreswan policies in YAML list format.
The default policy is
private-or-clear. To change it toprivate, the above playbook contains an according policy for the defaultcidrentry.To prevent a loss of the SSH connection during the execution of the playbook if the Ansible control node is in the same IP subnet as the managed nodes, add a
clearpolicy for the control node’s IP address. For example, if the mesh should be configured for the192.0.2.0/24subnet and the control node uses the IP address192.0.2.1, you require aclearpolicy for192.0.2.1/32as shown in the playbook.For details about policies, see the
ipsec.conf(5)man page on a system with Libreswan installed.vpn_manage_firewall: true-
Defines that the role opens the required ports in the
firewalldservice on the managed nodes. vpn_manage_selinux: true- Defines that the role sets the required SELinux port type on the IPsec ports.
For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.vpn/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --ask-vault-pass --syntax-check ~/playbook.yml
$ ansible-playbook --ask-vault-pass --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook --ask-vault-pass ~/playbook.yml
$ ansible-playbook --ask-vault-pass ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
On a node in the mesh, ping another node to activate the connection:
ping managed-node-02.example.com
[root@managed-node-01]# ping managed-node-02.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the connection is active:
ipsec trafficstatus 006 #2: "private#192.0.2.0/24"[1] ...192.0.2.2, type=ESP, add_time=1741938929, inBytes=372408, outBytes=545728, maxBytes=2^63B, id='CN=managed-node-02.example.com'
[root@managed-node-01]# ipsec trafficstatus 006 #2: "private#192.0.2.0/24"[1] ...192.0.2.2, type=ESP, add_time=1741938929, inBytes=372408, outBytes=545728, maxBytes=2^63B, id='CN=managed-node-02.example.com'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.14. Enabling legacy ciphers and algorithms in Libreswan
Enable legacy ciphers and algorithms in Libreswan for backward compatibility with other IPsec peers. This overrides the RHEL system-wide cryptographic policies which, by default, enforce strong encryption ciphers and algorithms for IPsec and Internet Key Exchange (IKE).
The RHEL system-wide cryptographic policies create a special connection called %default. This connection sets the default values for the keyexchange, esp, and ike parameters.
Prerequisites
- Libreswan is installed.
Procedure
To override the defaults set by the RHEL system-wide cryptographic policies, add the
keyexchange,esp, andikeparameters to your connection configuration and set them to the values you require. For example:conn <connection_name> ikev2=no ike=aes-sha2,aes-sha1;modp2048 esp=aes-sha2,aes-sha1 ...conn <connection_name> ikev2=no ike=aes-sha2,aes-sha1;modp2048 esp=aes-sha2,aes-sha1 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
ipsecservice:systemctl restart ipsec
# systemctl restart ipsecCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.15. Troubleshooting IPsec configurations
Diagnosing IPsec configuration failures can be challenging, because issues can be caused by mismatched settings, firewall rules, and kernel-level errors. The following information provides a systematic approach to resolving common problems with IPsec VPN connections.
5.15.1. Basic connection issues
Problems with VPN connections often occur due to mismatched configurations between the endpoints.
To confirm that an IPsec connection is established, enter:
ipsec trafficstatus 006 #8: "vpn.example.com"[1] 192.0.2.1, type=ESP, add_time=1595296930, inBytes=5999, outBytes=3231, id='@vpn.example.com', lease=198.51.100.1/32
# ipsec trafficstatus
006 #8: "vpn.example.com"[1] 192.0.2.1, type=ESP, add_time=1595296930, inBytes=5999, outBytes=3231, id='@vpn.example.com', lease=198.51.100.1/32For a successful connection, the command shows an entry with the connection’s name and details. If the output is empty, the tunnel is not established.
5.15.3. Mismatched Configurations
VPN connections fail if the endpoints are not configured with matching Internet Key Exchange (IKE) versions, algorithms, IP address ranges, or pre-shared keys (PSK). If you identify a mismatch, you must align the settings on both endpoints to resolve the issue.
- Remote Peer Not Running IKE/IPsec
If the connection was refused, an ICMP error is displayed:
ipsec auto --up vpn.example.com ... 000 "vpn.example.com"[1] 192.0.2.2 #16: ERROR: asynchronous network error report on wlp2s0 (192.0.2.2:500), complainant 198.51.100.1: Connection refused [errno 111, origin ICMP type 3 code 3 (not authenticated)]
# ipsec auto --up vpn.example.com ... 000 "vpn.example.com"[1] 192.0.2.2 #16: ERROR: asynchronous network error report on wlp2s0 (192.0.2.2:500), complainant 198.51.100.1: Connection refused [errno 111, origin ICMP type 3 code 3 (not authenticated)]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IKE Algorithms
The connection fails with a
NO_PROPOSAL_CHOSENnotification during the initial setup:ipsec auto --up vpn.example.com ... 003 "vpn.example.com"[1] 193.110.157.148 #3: dropping unexpected IKE_SA_INIT message containing NO_PROPOSAL_CHOSEN notification; message payloads: N; missing payloads: SA,KE,Ni
# ipsec auto --up vpn.example.com ... 003 "vpn.example.com"[1] 193.110.157.148 #3: dropping unexpected IKE_SA_INIT message containing NO_PROPOSAL_CHOSEN notification; message payloads: N; missing payloads: SA,KE,NiCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IPsec Algorithms
The connection fails with a
NO_PROPOSAL_CHOSENerror after the initial exchange:ipsec auto --up vpn.example.com ... 182 "vpn.example.com"[1] 193.110.157.148 #5: STATE_PARENT_I2: sent v2I2, expected v2R2 {auth=IKEv2 cipher=AES_GCM_16_256 integ=n/a prf=HMAC_SHA2_256 group=MODP2048} 002 "vpn.example.com"[1] 193.110.157.148 #6: IKE_AUTH response contained the error notification NO_PROPOSAL_CHOSEN# ipsec auto --up vpn.example.com ... 182 "vpn.example.com"[1] 193.110.157.148 #5: STATE_PARENT_I2: sent v2I2, expected v2R2 {auth=IKEv2 cipher=AES_GCM_16_256 integ=n/a prf=HMAC_SHA2_256 group=MODP2048} 002 "vpn.example.com"[1] 193.110.157.148 #6: IKE_AUTH response contained the error notification NO_PROPOSAL_CHOSENCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IP Address Ranges (IKEv2)
The remote peer responds with a
TS_UNACCEPTABLEerror:ipsec auto --up vpn.example.com ... 1v2 "vpn.example.com" #1: STATE_PARENT_I2: sent v2I2, expected v2R2 {auth=IKEv2 cipher=AES_GCM_16_256 integ=n/a prf=HMAC_SHA2_512 group=MODP2048} 002 "vpn.example.com" #2: IKE_AUTH response contained the error notification TS_UNACCEPTABLE# ipsec auto --up vpn.example.com ... 1v2 "vpn.example.com" #1: STATE_PARENT_I2: sent v2I2, expected v2R2 {auth=IKEv2 cipher=AES_GCM_16_256 integ=n/a prf=HMAC_SHA2_512 group=MODP2048} 002 "vpn.example.com" #2: IKE_AUTH response contained the error notification TS_UNACCEPTABLECopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched IP Address Ranges (IKEv1)
The connection times out during quick mode, with a message indicating the peer did not accept the proposal:
ipsec auto --up vpn.example.com ... 031 "vpn.example.com" #2: STATE_QUICK_I1: 60 second timeout exceeded after 0 retransmits. No acceptable response to our first Quick Mode message: perhaps peer likes no proposal
# ipsec auto --up vpn.example.com ... 031 "vpn.example.com" #2: STATE_QUICK_I1: 60 second timeout exceeded after 0 retransmits. No acceptable response to our first Quick Mode message: perhaps peer likes no proposalCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched PSK (IKEv2)
The peer rejects the connection with an
AUTHENTICATION_FAILEDerror:ipsec auto --up vpn.example.com ... 003 "vpn.example.com" #1: received Hash Payload does not match computed value 223 "vpn.example.com" #1: sending notification INVALID_HASH_INFORMATION to 192.0.2.23:500
# ipsec auto --up vpn.example.com ... 003 "vpn.example.com" #1: received Hash Payload does not match computed value 223 "vpn.example.com" #1: sending notification INVALID_HASH_INFORMATION to 192.0.2.23:500Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Mismatched PSK (IKEv1)
The hash payload does not match, making the IKE message unreadable and resulting in an
INVALID_HASH_INFORMATIONerror:ipsec auto --up vpn.example.com ... 002 "vpn.example.com" #1: IKE SA authentication request rejected by peer: AUTHENTICATION_FAILED
# ipsec auto --up vpn.example.com ... 002 "vpn.example.com" #1: IKE SA authentication request rejected by peer: AUTHENTICATION_FAILEDCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.15.4. MTU issues
Diagnose intermittent IPsec connection failures caused by Maximum Transmission Unit (MTU) issues. Encryption increases packet size, leading to fragmentation and lost data when packets exceed the network’s MTU, often seen with larger data transfers.
A common symptom is that small packets, for example pings, work correctly, but larger packets, such as an SSH session, freeze after the login. To fix the problem, lower the MTU for the tunnel by adding the mtu=1400 option to the configuration file.
5.15.5. NAT conflicts
Resolve NAT conflicts that occur when an IPsec host also acts as a NAT router. Incorrect NAT application can translate source IP addresses before encryption, causing packets to be sent unencrypted over the network.
For example, if the source IP address of the packet is translated by a masquerade rule before IPsec encryption is applied, the packet’s source no longer matches the IPsec policy, and Libreswan sends it unencrypted over the network.
To solve this problem, add a firewall rule that excludes traffic between the IPsec subnets from NAT. This rule should be inserted at the beginning of the POSTROUTING chain to ensure it is processed before the general NAT rule.
Example 5.1. Solution by using the nftables framework
The following example uses nftables to set up a basic NAT environment that excludes traffic between the 192.0.2.0/24 and 198.51.100.0/24 subnets from address translation:
nft add table ip nat
nft add chain ip nat postrouting { type nat hook postrouting priority 100 \; }
nft add rule ip nat postrouting ip saddr 192.0.2.0/24 ip daddr 198.51.100.0/24 return
# nft add table ip nat
# nft add chain ip nat postrouting { type nat hook postrouting priority 100 \; }
# nft add rule ip nat postrouting ip saddr 192.0.2.0/24 ip daddr 198.51.100.0/24 return5.15.6. Kernel-level IPsec issues
Troubleshoot kernel-level IPsec issues when a VPN tunnel appears established but no traffic flows. In this case, inspect the kernel’s IPsec state to check if the tunnel policies and cryptographic keys were correctly installed.
This process involves checking two components:
- The Security Policy Database (SPD): The rule that instructs the kernel what traffic to encrypt.
- The Security Association Database (SAD): The keys that instruct the kernel how to encrypt that traffic.
First, check if the correct policy exists in the SPD:
ip xfrm policy src 192.0.2.1/32 dst 10.0.0.0/8 dir out priority 666 ptype main tmpl src 198.51.100.13 dst 203.0.113.22 proto esp reqid 16417 mode tunnel
# ip xfrm policy
src 192.0.2.1/32 dst 10.0.0.0/8
dir out priority 666 ptype main
tmpl src 198.51.100.13 dst 203.0.113.22
proto esp reqid 16417 mode tunnel
The output should contain the policies matching your leftsubnet and rightsubnet parameters with both in and out directions. If you do not see a policy for your traffic, Libreswan failed to create the kernel rule, and traffic is not encrypted.
If the policy exists, check if it has a corresponding set of keys in the SAD:
ip xfrm state src 203.0.113.22 dst 198.51.100.13 proto esp spi 0xa78b3fdb reqid 16417 mode tunnel auth-trunc hmac(sha1) 0x3763cd3b... 96 enc cbc(aes) 0xd9dba399...
# ip xfrm state
src 203.0.113.22 dst 198.51.100.13
proto esp spi 0xa78b3fdb reqid 16417 mode tunnel
auth-trunc hmac(sha1) 0x3763cd3b... 96
enc cbc(aes) 0xd9dba399...This command displays private cryptographic keys. Do not share this output, because attackers can use it to decrypt your VPN traffic.
If a policy exists but you see no corresponding state with the same reqid, it typically means the Internet Key Exchange (IKE) negotiation failed. The two VPN endpoints could not agree on a set of keys.
For more detailed diagnostics, use the -s option with either of the commands. This option adds traffic counters, which can help you identify if the kernel processes packets by a specific rule.
5.15.7. Kernel IPsec subsystem bugs
A defect in the kernel’s IPsec subsystem can cause it to lose sync with the IKE daemon. This can lead to discrepancies between negotiated security associations and actual IPsec policy enforcement, disrupting secure network communication.
To check for kernel-level errors, display the transform (XFRM) statistics:
cat /proc/net/xfrm_stat
# cat /proc/net/xfrm_stat
If any of the counters in the output, such as XfrmInError, show a nonzero value, it indicates a problem with the kernel subsystem. In this case, open a support case, and attach the output of the command along with the corresponding IKE logs.
5.15.8. Displaying Libreswan logs
Display Libreswan logs to diagnose and troubleshoot IPsec service events and issues. Access the journal for the ipsec service to gain insights into connection status and potential problems.
To display the journal, enter:
journalctl -xeu ipsec
# journalctl -xeu ipsec
If the default logging level does not provide enough details, enable comprehensive debug logging by adding the following settings to the config setup section in the /etc/ipsec.conf file:
plutodebug=all logfile=/var/log/pluto.log
plutodebug=all
logfile=/var/log/pluto.log
Because debug logging can produce many entries, redirecting the messages to a dedicated log file can prevent the journald and systemd services from rate-limiting the messages.
5.16. Configuring a VPN connection with control-center
If you use Red Hat Enterprise Linux with a graphical interface, you can configure a VPN connection in the GNOME control-center.
Prerequisites
-
The
NetworkManager-libreswan-gnomepackage is installed.
Procedure
-
Press the Super key, type
Settings, and press Enter to open thecontrol-centerapplication. -
Select the
Networkentry on the left. - Click the + icon.
-
Select
VPN. Select the
Identitymenu entry to see the basic configuration options:General
Gateway- The name orIPaddress of the remote VPN gateway.Authentication
Type-
IKEv2 (Certificate)- client is authenticated by certificate. It is more secure (default). IKEv1 (XAUTH)- client is authenticated by user name and password, or a pre-shared key (PSK).The following configuration settings are available under the
Advancedsection:Figure 5.1. Advanced options of a VPN connection
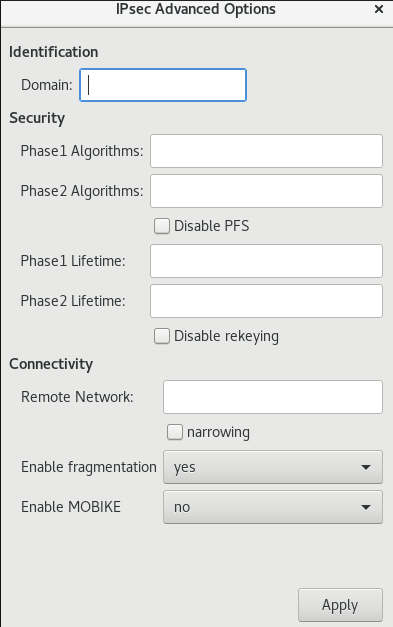 Warning
WarningWhen configuring an IPsec-based VPN connection using the
gnome-control-centerapplication, theAdvanceddialog displays the configuration, but it does not allow any changes. As a consequence, users cannot change any advanced IPsec options. Use thenm-connection-editorornmclitools instead to perform configuration of the advanced properties.Identification
Domain- If required, enter the Domain Name.Security
-
Phase1 Algorithms- corresponds to theikeLibreswan parameter - enter the algorithms to be used to authenticate and set up an encrypted channel. Phase2 Algorithms- corresponds to theespLibreswan parameter - enter the algorithms to be used for theIPsecnegotiations.Check the
Disable PFSfield to turn off Perfect Forward Secrecy (PFS) to ensure compatibility with old servers that do not support PFS.-
Phase1 Lifetime- corresponds to theikelifetimeLibreswan parameter - how long the key used to encrypt the traffic will be valid. Phase2 Lifetime- corresponds to thesalifetimeLibreswan parameter - how long a particular instance of a connection should last before expiring.Note that the encryption key should be changed from time to time for security reasons.
Remote network- corresponds to therightsubnetLibreswan parameter - the destination private remote network that should be reached through the VPN.Check the
narrowingfield to enable narrowing. Note that it is only effective in IKEv2 negotiation.-
Enable fragmentation- corresponds to thefragmentationLibreswan parameter - whether or not to allow IKE fragmentation. Valid values areyes(default) orno. -
Enable Mobike- corresponds to themobikeLibreswan parameter - whether or not to allow Mobility and Multihoming Protocol (MOBIKE, RFC 4555) to enable a connection to migrate its endpoint without needing to restart the connection from scratch. This is used on mobile devices that switch between wired, wireless, or mobile data connections. The values areno(default) oryes.
-
Select the menu entry:
IPv4 Method
-
Automatic (DHCP)- Choose this option if the network you are connecting to uses aDHCPserver to assign dynamicIPaddresses. -
Link-Local Only- Choose this option if the network you are connecting to does not have aDHCPserver and you do not want to assignIPaddresses manually. Random addresses will be assigned as per RFC 3927 with prefix169.254/16. -
Manual- Choose this option if you want to assignIPaddresses manually. Disable-IPv4is disabled for this connection.DNS
In the
DNSsection, whenAutomaticisON, switch it toOFFto enter the IP address of a DNS server you want to use separating the IPs by comma.Routes
Note that in the
Routessection, whenAutomaticisON, routes from DHCP are used, but you can also add additional static routes. WhenOFF, only static routes are used.-
Address- Enter theIPaddress of a remote network or host. -
Netmask- The netmask or prefix length of theIPaddress entered above. -
Gateway- TheIPaddress of the gateway leading to the remote network or host entered above. Metric- A network cost, a preference value to give to this route. Lower values will be preferred over higher values.Use this connection only for resources on its network
Select this check box to prevent the connection from becoming the default route. Selecting this option means that only traffic specifically destined for routes learned automatically over the connection or entered here manually is routed over the connection.
-
To configure
IPv6settings in aVPNconnection, select the menu entry:IPv6 Method
-
Automatic- Choose this option to useIPv6Stateless Address AutoConfiguration (SLAAC) to create an automatic, stateless configuration based on the hardware address and Router Advertisements (RA). -
Automatic, DHCP only- Choose this option to not use RA, but request information fromDHCPv6directly to create a stateful configuration. -
Link-Local Only- Choose this option if the network you are connecting to does not have aDHCPserver and you do not want to assignIPaddresses manually. Random addresses will be assigned as per RFC 4862 with prefixFE80::0. -
Manual- Choose this option if you want to assignIPaddresses manually. Disable-IPv6is disabled for this connection.Note that
DNS,Routes,Use this connection only for resources on its networkare common toIPv4settings.
-
-
Once you have finished editing the
VPNconnection, click the button to customize the configuration or the button to save it for the existing one. -
Switch the profile to
ONto activate theVPNconnection. - If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
5.17. Configuring a VPN connection using nm-connection-editor
If you use Red Hat Enterprise Linux with a graphical interface, you can configure a VPN connection in the nm-connection-editor application.
Prerequisites
-
The
NetworkManager-libreswan-gnomepackage is installed. If you configure an Internet Key Exchange version 2 (IKEv2) connection:
- The certificate is imported into the IPsec network security services (NSS) database.
- The nickname of the certificate in the NSS database is known.
Procedure
Open a terminal, and enter:
nm-connection-editor
$ nm-connection-editorCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Click the button to add a new connection.
-
Select the
IPsec based VPNconnection type, and click . On the
VPNtab:Enter the host name or IP address of the VPN gateway into the
Gatewayfield, and select an authentication type. Based on the authentication type, you must enter different additional information:-
IKEv2 (Certifiate)authenticates the client by using a certificate, which is more secure. This setting requires the nickname of the certificate in the IPsec NSS database IKEv1 (XAUTH)authenticates the user by using a user name and password (pre-shared key). This setting requires that you enter the following values:- User name
- Password
- Group name
- Secret
-
If the remote server specifies a local identifier for the IKE exchange, enter the exact string in the
Remote IDfield. If the remote server runs Libreswan, this value is set in the server’sleftidparameter.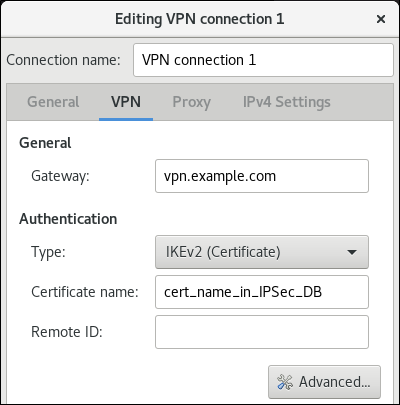
Optional: Configure additional settings by clicking the button. You can configure the following settings:
Identification
-
Domain- If required, enter the domain name.
-
Security
-
Phase1 Algorithmscorresponds to theikeLibreswan parameter. Enter the algorithms to be used to authenticate and set up an encrypted channel. Phase2 Algorithmscorresponds to theespLibreswan parameter. Enter the algorithms to be used for theIPsecnegotiations.Check the
Disable PFSfield to turn off Perfect Forward Secrecy (PFS) to ensure compatibility with old servers that do not support PFS.-
Phase1 Lifetimecorresponds to theikelifetimeLibreswan parameter. This parameter defines how long the key used to encrypt the traffic is valid. -
Phase2 Lifetimecorresponds to thesalifetimeLibreswan parameter. This parameter defines how long a security association is valid.
-
Connectivity
Remote networkcorresponds to therightsubnetLibreswan parameter and defines the destination private remote network that should be reached through the VPN.Check the
narrowingfield to enable narrowing. Note that it is only effective in the IKEv2 negotiation.-
Enable fragmentationcorresponds to thefragmentationLibreswan parameter and defines whether or not to allow IKE fragmentation. Valid values areyes(default) orno. -
Enable Mobikecorresponds to themobikeLibreswan parameter. The parameter defines whether or not to allow Mobility and Multihoming Protocol (MOBIKE) (RFC 4555) to enable a connection to migrate its endpoint without needing to restart the connection from scratch. This is used on mobile devices that switch between wired, wireless or mobile data connections. The values areno(default) oryes.
On the
IPv4 Settingstab, select the IP assignment method and, optionally, set additional static addresses, DNS servers, search domains, and routes.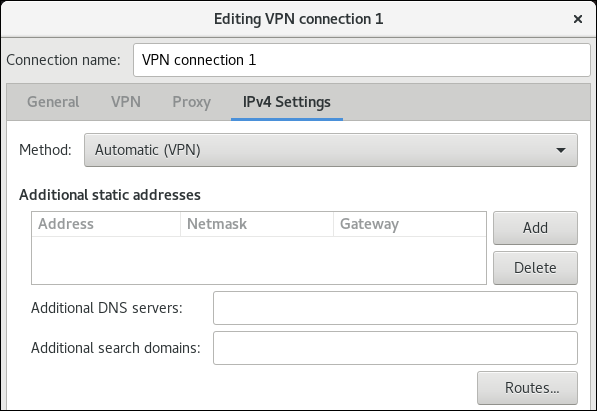
- Save the connection.
-
Close
nm-connection-editor. If you use this host in a network with DHCP or Stateless Address Autoconfiguration (SLAAC), the connection can be vulnerable to being redirected. For details and mitigation steps, see Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel.
NoteWhen you add a new connection by clicking the button, NetworkManager creates a new configuration file for that connection and then opens the same dialog that is used for editing an existing connection. The difference between these dialogs is that an existing connection profile has a Details menu entry.
5.18. Assigning a VPN connection to a dedicated routing table to prevent the connection from bypassing the tunnel
To protect your VPN connection from traffic redirection attacks, assign it to a dedicated routing table. This prevents malicious network servers from bypassing the secure tunnel and compromising data integrity.
Both a DHCP server and Stateless Address Autoconfiguration (SLAAC) can add routes to a client’s routing table. For example, a malicious DHCP server can use this feature to force a host with VPN connection to redirect traffic through a physical interface instead of the VPN tunnel. This vulnerability is also known as TunnelVision and described in the CVE-2024-3661 vulnerability article.
To mitigate this vulnerability, you can assign the VPN connection to a dedicated routing table. This prevents the DHCP configuration or SLAAC from manipulating routing decisions for network packets intended for the VPN tunnel.
Follow the steps if at least one of the conditions applies to your environment:
- At least one network interface uses DHCP or SLAAC.
- Your network does not use mechanisms, such as DHCP snooping, that prevent a rogue DHCP server.
Routing the entire traffic through the VPN prevents the host from accessing local network resources.
Prerequisites
- You use NetworkManager 1.40.16-18 or later.
Procedure
- Decide which routing table you want to use. The following steps use table 75. By default, RHEL does not use the tables 1-254, and you can use any of them.
Configure the VPN connection profile to place the VPN routes in a dedicated routing table:
nmcli connection modify <vpn_connection_profile> ipv4.route-table 75 ipv6.route-table 75
# nmcli connection modify <vpn_connection_profile> ipv4.route-table 75 ipv6.route-table 75Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set a low priority value for the table you used in the previous command:
nmcli connection modify <vpn_connection_profile> ipv4.routing-rules "priority 32345 from all table 75" ipv6.routing-rules "priority 32345 from all table 75"
# nmcli connection modify <vpn_connection_profile> ipv4.routing-rules "priority 32345 from all table 75" ipv6.routing-rules "priority 32345 from all table 75"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The priority value can be any value between 1 and 32766. The lower the value, the higher the priority.
Reconnect the VPN connection:
nmcli connection down <vpn_connection_profile> nmcli connection up <vpn_connection_profile>
# nmcli connection down <vpn_connection_profile> # nmcli connection up <vpn_connection_profile>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the IPv4 routes in table 75:
ip route show table 75 ... 192.0.2.0/24 via 192.0.2.254 dev vpn_device proto static metric 50 default dev vpn_device proto static scope link metric 50
# ip route show table 75 ... 192.0.2.0/24 via 192.0.2.254 dev vpn_device proto static metric 50 default dev vpn_device proto static scope link metric 50Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that both the route to the remote network and the default gateway are assigned to routing table 75 and, therefore, all traffic is routed through the tunnel. If you set
ipv4.never-default truein the VPN connection profile, a default route is not created and, therefore, not visible in this output.Display the IPv6 routes in table 75:
ip -6 route show table 75 ... 2001:db8:1::/64 dev vpn_device proto kernel metric 50 pref medium default dev vpn_device proto static metric 50 pref medium
# ip -6 route show table 75 ... 2001:db8:1::/64 dev vpn_device proto kernel metric 50 pref medium default dev vpn_device proto static metric 50 pref mediumCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output confirms that both the route to the remote network and the default gateway are assigned to routing table 75 and, therefore, all traffic is routed through the tunnel. If you set
ipv6.never-default truein the VPN connection profile, a default route is not created and, therefore, not visible in this output.
Chapter 6. Using MACsec to encrypt layer-2 traffic in the same physical network
MACsec secures point-to-point communication between devices. For example, you can configure MACsec on the two hosts connecting your branch and central offices over a Metro-Ethernet connection to increase security.
6.1. How MACsec increases security
Media Access Control security (MACsec) is a layer-2 protocol that encrypts and authenticates all LAN traffic. It uses a pre-shared key to establish connections. To change this key, you must update the NetworkManager configuration on all hosts that use MACsec.
MACsec secures different traffic types over the Ethernet links, including:
- Dynamic host configuration protocol (DHCP)
- address resolution protocol (ARP)
- IPv4 and IPv6 traffic
- Any traffic over IP such as TCP or UDP
A MACsec connection uses an Ethernet device, such as an Ethernet network card, Virtual Local Area Network (VLAN), or tunnel device, as a parent. You can either set an IP configuration only on the MACsec device to communicate with other hosts only by using the encrypted connection, or you can also set an IP configuration on the parent device. In the latter case, you can use the parent device to communicate with other hosts using an unencrypted connection and the MACsec device for encrypted connections.
MACsec does not require any special hardware. For example, you can use any switch, except if you want to encrypt traffic only between a host and a switch. In this scenario, the switch must also support MACsec.
In other words, you can configure MACsec for two common scenarios:
- Host-to-host
- Host-to-switch and switch-to-other-hosts
You can use MACsec only between hosts being in the same physical or virtual LAN.
Using the MACsec security standard for securing communication at the link layer, also known as layer 2 of the Open Systems Interconnection (OSI) model provides the following notable benefits:
- Encryption at layer 2 eliminates the need for encrypting individual services at layer 7. This reduces the overhead associated with managing a large number of certificates for each endpoint on each host.
- Point-to-point security between directly connected network devices such as routers and switches.
- No changes needed for applications and higher-layer protocols.
6.2. Configuring a MACsec connection by using nmcli
You can use the nmcli utility to configure Ethernet interfaces to use MACsec. For example, you can create a MACsec connection between two hosts that are connected over Ethernet.
Procedure
On the first host on which you configure MACsec:
Create the connectivity association key (CAK) and connectivity-association key name (CKN) for the pre-shared key:
Create a 16-byte hexadecimal CAK:
dd if=/dev/urandom count=16 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' 50b71a8ef0bd5751ea76de6d6c98c03a
# dd if=/dev/urandom count=16 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' 50b71a8ef0bd5751ea76de6d6c98c03aCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a 32-byte hexadecimal CKN:
dd if=/dev/urandom count=32 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' f2b4297d39da7330910a74abc0449feb45b5c0b9fc23df1430e1898fcf1c4550
# dd if=/dev/urandom count=32 bs=1 2> /dev/null | hexdump -e '1/2 "%04x"' f2b4297d39da7330910a74abc0449feb45b5c0b9fc23df1430e1898fcf1c4550Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- On both hosts you want to connect over a MACsec connection:
Create the MACsec connection:
nmcli connection add type macsec con-name macsec0 ifname macsec0 connection.autoconnect yes macsec.parent enp1s0 macsec.mode psk macsec.mka-cak 50b71a8ef0bd5751ea76de6d6c98c03a macsec.mka-ckn f2b4297d39da7330910a74abc0449feb45b5c0b9fc23df1430e1898fcf1c4550
# nmcli connection add type macsec con-name macsec0 ifname macsec0 connection.autoconnect yes macsec.parent enp1s0 macsec.mode psk macsec.mka-cak 50b71a8ef0bd5751ea76de6d6c98c03a macsec.mka-ckn f2b4297d39da7330910a74abc0449feb45b5c0b9fc23df1430e1898fcf1c4550Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the CAK and CKN generated in the previous step in the
macsec.mka-cakandmacsec.mka-cknparameters. The values must be the same on every host in the MACsec-protected network.Configure the IP settings on the MACsec connection.
Configure the
IPv4settings. For example, to set a staticIPv4address, network mask, default gateway, and DNS server to themacsec0connection, enter:nmcli connection modify macsec0 ipv4.method manual ipv4.addresses '192.0.2.1/24' ipv4.gateway '192.0.2.254' ipv4.dns '192.0.2.253'
# nmcli connection modify macsec0 ipv4.method manual ipv4.addresses '192.0.2.1/24' ipv4.gateway '192.0.2.254' ipv4.dns '192.0.2.253'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the
IPv6settings. For example, to set a staticIPv6address, network mask, default gateway, and DNS server to themacsec0connection, enter:nmcli connection modify macsec0 ipv6.method manual ipv6.addresses '2001:db8:1::1/32' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd'
# nmcli connection modify macsec0 ipv6.method manual ipv6.addresses '2001:db8:1::1/32' ipv6.gateway '2001:db8:1::fffe' ipv6.dns '2001:db8:1::fffd'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Activate the connection:
nmcli connection up macsec0
# nmcli connection up macsec0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the traffic is encrypted:
tcpdump -nn -i enp1s0
# tcpdump -nn -i enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Display the unencrypted traffic:
tcpdump -nn -i macsec0
# tcpdump -nn -i macsec0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display MACsec statistics:
ip macsec show
# ip macsec showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display individual counters for each type of protection: integrity-only (encrypt off) and encryption (encrypt on)
ip -s macsec show
# ip -s macsec showCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 7. Using and configuring firewalld
A firewall is a way to protect machines from any unwanted traffic from outside. It enables users to control incoming network traffic on host machines by defining a set of firewall rules. These rules are used to sort the incoming traffic and either block it or allow it through.
firewalld is a firewall service daemon that provides a dynamic, customizable firewall with a D-Bus interface. Being dynamic, it enables creating, changing, and deleting rules without the necessity of restarting the firewall daemon each time the rules are changed.
You can use firewalld to configure packet filtering required by the majority of typical cases. If firewalld does not cover your scenario, or you want to have complete control of rules, use the nftables framework.
firewalld uses the concepts of zones, policies, and services to simplify traffic management. Zones logically separate a network. Network interfaces and sources can be assigned to a zone. Policies are used to deny or allow traffic flowing between zones. Firewall services are predefined rules that cover all necessary settings to allow incoming traffic for a specific service, and they apply within a zone.
Services use one or more ports or addresses for network communication. Firewalls filter communication based on ports. To allow network traffic for a service, its ports must be open. firewalld blocks all traffic on ports that are not explicitly set as open. Some zones, such as trusted, allow all traffic by default.
firewalld maintains separate runtime and permanent configurations. This allows runtime-only changes. The runtime configuration does not persist after firewalld reload or restart. At startup, it is populated from the permanent configuration.
Note that firewalld with nftables back end does not support passing custom nftables rules to firewalld, using the --direct option.
7.1. When to use firewalld, nftables, or iptables
On RHEL 8, you can use the following packet-filtering utilities depending on your scenario:
-
firewalld: Thefirewalldutility simplifies firewall configuration for common use cases. -
nftables: Use thenftablesutility to set up complex and performance-critical firewalls, such as for a whole network. -
iptables: Theiptablesutility on Red Hat Enterprise Linux uses thenf_tableskernel API instead of thelegacyback end. Thenf_tablesAPI provides backward compatibility so that scripts that useiptablescommands still work on Red Hat Enterprise Linux. For new firewall scripts, usenftables.
To prevent the different firewall-related services (firewalld, nftables, or iptables) from influencing each other, run only one of them on a RHEL host, and disable the other services.
7.2. Firewall zones
You can use the firewalld utility to separate networks into different zones according to the level of trust that you have with the interfaces and traffic within that network. A connection can only be part of one zone, but you can use that zone for many network connections.
firewalld follows strict principles in regards to zones:
- Traffic ingresses only one zone.
- Traffic egresses only one zone.
- A zone defines a level of trust.
- Intrazone traffic (within the same zone) is allowed by default.
- Interzone traffic (from zone to zone) is denied by default.
Principles 4 and 5 are a consequence of principle 3.
Principle 4 is configurable through the zone option --remove-forward. Principle 5 is configurable by adding new policies.
NetworkManager notifies firewalld of the zone of an interface. You can assign zones to interfaces with the following utilities:
-
NetworkManager -
firewall-configutility -
firewall-cmdutility - The RHEL web console
The RHEL web console, firewall-config, and firewall-cmd can only edit the appropriate NetworkManager configuration files. If you change the zone of the interface using the web console, firewall-cmd, or firewall-config, the request is forwarded to NetworkManager and is not handled by firewalld.
The /usr/lib/firewalld/zones/ directory stores the predefined zones, and you can instantly apply them to any available network interface. These files are copied to the /etc/firewalld/zones/ directory only after they are modified. The default settings of the predefined zones are as follows:
block-
Suitable for: Any incoming network connections are rejected with an icmp-host-prohibited message for
IPv4and icmp6-adm-prohibited forIPv6. - Accepts: Only network connections initiated from within the system.
-
Suitable for: Any incoming network connections are rejected with an icmp-host-prohibited message for
dmz- Suitable for: Computers in your DMZ that are publicly-accessible with limited access to your internal network.
- Accepts: Only selected incoming connections.
dropSuitable for: Any incoming network packets are dropped without any notification.
- Accepts: Only outgoing network connections.
external- Suitable for: External networks with masquerading enabled, especially for routers. Situations when you do not trust the other computers on the network.
- Accepts: Only selected incoming connections.
home- Suitable for: Home environment where you mostly trust the other computers on the network.
- Accepts: Only selected incoming connections.
internal- Suitable for: Internal networks where you mostly trust the other computers on the network.
- Accepts: Only selected incoming connections.
public- Suitable for: Public areas where you do not trust other computers on the network.
- Accepts: Only selected incoming connections.
trusted- Accepts: All network connections.
workSuitable for: Work environment where you mostly trust the other computers on the network.
- Accepts: Only selected incoming connections.
One of these zones is set as the default zone. When interface connections are added to NetworkManager, they are assigned to the default zone. On installation, the default zone in firewalld is the public zone. You can change the default zone.
Make network zone names self-explanatory to help users understand them quickly.
To avoid any security problems, review the default zone configuration and disable any unnecessary services according to your needs and risk assessments.
7.3. Firewall policies
The firewall policies specify the desired security state of your network. They outline rules and actions to take for different types of traffic.
Typically, the policies contain rules for the following types of traffic:
- Incoming traffic
- Outgoing traffic
- Forward traffic
- Specific services and applications
- Network address translations (NAT)
Firewall policies use the concept of firewall zones. Each zone is associated with a specific set of firewall rules that determine the traffic allowed. Policies apply firewall rules in a stateful, unidirectional manner. This means you only consider one direction of the traffic. The traffic return path is implicitly allowed due to stateful filtering of firewalld.
Policies are associated with an ingress zone and an egress zone. The ingress zone is where the traffic originated (received). The egress zone is where the traffic leaves (sent).
The firewall rules defined in a policy can reference the firewall zones to apply consistent configurations across multiple network interfaces.
7.4. Firewall rules
You can use the firewall rules to implement specific configurations for allowing or blocking network traffic. As a result, you can control the flow of network traffic to protect your system from security threats.
Firewall rules typically define certain criteria based on various attributes. The attributes can be as:
- Source IP addresses
- Destination IP addresses
- Transfer Protocols (TCP, UDP, …)
- Ports
- Network interfaces
The firewalld utility organizes the firewall rules into zones (such as public, internal, and others) and policies. Each zone has its own set of rules that determine the level of traffic freedom for network interfaces associated with a particular zone.
7.5. Firewall direct rules
The firewalld service provides multiple ways with which to configure rules, including regular rules and direct rules.
One difference between these is how each method interacts with the underlying backend (iptables or nftables).
The direct rules are advanced, low-level rules that allow direct interaction with iptables. They bypass the structured zone-based management of firewalld to give you more control. You manually define the direct rules with the firewall-cmd command by using the raw iptables syntax. For example, firewall-cmd --direct --add-rule ipv4 filter INPUT 0 -s 198.51.100.1 -j DROP. This command adds an iptables rule to drop traffic from the 198.51.100.1 source IP address.
However, using the direct rules also has its drawbacks. Especially when nftables is your primary firewall backend. For example:
-
The direct rules are harder to maintain and can conflict with
nftablesbasedfirewalldconfigurations. -
The direct rules do not support advanced features that you can find in
nftablessuch as raw expressions and stateful objects. -
Direct rules are not future-proof. The
iptablescomponent is deprecated and will eventually be removed from RHEL.
For the previous reasons, you might consider replacing firewalld direct rules with nftables. Review the knowledgebase solution How to replace firewalld direct rules with nftables? to see more details.
7.6. Predefined firewalld services
Predefined firewalld services offer an abstraction layer for low-level firewall rules. They map common network services, such as SSH or HTTP, to their specific ports and protocols, simplifying firewall management and reducing errors by using a named service instead of manual configuration.
To see available predefined services:
firewall-cmd --get-services RH-Satellite-6 RH-Satellite-6-capsule afp amanda-client amanda-k5-client amqp amqps apcupsd audit ausweisapp2 bacula bacula-client bareos-director bareos-filedaemon bareos-storage bb bgp bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc bittorrent-lsd ceph ceph-exporter ceph-mon cfengine checkmk-agent cockpit collectd condor-collector cratedb ctdb dds...
# firewall-cmd --get-services RH-Satellite-6 RH-Satellite-6-capsule afp amanda-client amanda-k5-client amqp amqps apcupsd audit ausweisapp2 bacula bacula-client bareos-director bareos-filedaemon bareos-storage bb bgp bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc bittorrent-lsd ceph ceph-exporter ceph-mon cfengine checkmk-agent cockpit collectd condor-collector cratedb ctdb dds...Copy to Clipboard Copied! Toggle word wrap Toggle overflow To further inspect a particular predefined service:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The example output shows that the
RH-Satellite-6predefined service listens on ports 5000/tcp 5646-5647/tcp 5671/tcp 8000/tcp 8080/tcp 9090/tcp. Additionally,RH-Satellite-6inherits rules from another predefined service. In this caseforeman.
Each predefined service is stored as an XML file with the same name in the /usr/lib/firewalld/services/ directory.
7.7. Working with firewalld zones
Zones represent a concept to manage incoming traffic more transparently. Network interfaces and source addresses are assigned to zones. You manage firewall rules for each zone independently, which enables you to define complex firewall settings and apply them to the traffic.
7.7.1. Customizing firewall settings for a specific zone to enhance security
To strengthen network security, modify the firewalld settings by associating a specific network interface or connection with a particular firewall zone. By defining granular rules for a zone, you can control inbound and outbound traffic according to your security needs.
For example, you can achieve the following benefits:
- Protection of sensitive data
- Prevention of unauthorized access
- Mitigation of potential network threats
Prerequisites
-
The
firewalldservice is running.
Procedure
List the available firewall zones:
firewall-cmd --get-zones
# firewall-cmd --get-zonesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
firewall-cmd --get-zonescommand displays all zones that are available on the system, but it does not show any details for particular zones. To see more detailed information for all zones, use thefirewall-cmd --list-all-zonescommand.- Choose the zone you want to use for this configuration.
Modify firewall settings for the chosen zone. For example, to allow the
SSHservice and remove theftpservice:firewall-cmd --add-service=ssh --zone=<your_chosen_zone> firewall-cmd --remove-service=ftp --zone=<same_chosen_zone>
# firewall-cmd --add-service=ssh --zone=<your_chosen_zone> # firewall-cmd --remove-service=ftp --zone=<same_chosen_zone>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Assign a network interface to the firewall zone:
List the available network interfaces:
firewall-cmd --get-active-zones
# firewall-cmd --get-active-zonesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Activity of a zone is determined by the presence of network interfaces or source address ranges that match its configuration. The default zone is active for unclassified traffic but is not always active if no traffic matches its rules.
Assign a network interface to the chosen zone:
firewall-cmd --zone=<your_chosen_zone> --change-interface=<interface_name> --permanent
# firewall-cmd --zone=<your_chosen_zone> --change-interface=<interface_name> --permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow Assigning a network interface to a zone is more suitable for applying consistent firewall settings to all traffic on a particular interface (physical or virtual).
The
firewall-cmdcommand, when used with the--permanentoption, often involves updating NetworkManager connection profiles to make changes to the firewall configuration permanent. This integration betweenfirewalldand NetworkManager ensures consistent network and firewall settings.
Verification
Display the updated settings for your chosen zone:
firewall-cmd --zone=<your_chosen_zone> --list-all
# firewall-cmd --zone=<your_chosen_zone> --list-allCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command output displays all zone settings including the assigned services, network interface, and network connections (sources).
7.7.2. Changing the default zone
If an interface is not assigned to a specific zone, it is assigned to the default zone. After each restart of the firewalld service, firewalld loads the settings for the default zone and makes it active. Settings for all other zones are preserved and ready to be used.
Typically, zones are assigned to interfaces by NetworkManager according to the connection.zone setting in NetworkManager connection profiles. Also, after a reboot NetworkManager manages assignments for "activating" those zones.
Prerequisites
-
The
firewalldservice is running.
Procedure
Display the current default zone:
firewall-cmd --get-default-zone
# firewall-cmd --get-default-zoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the new default zone:
firewall-cmd --set-default-zone <zone_name>
# firewall-cmd --set-default-zone <zone_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteFollowing this procedure, the setting is a permanent setting, even without the
--permanentoption.
7.7.3. Assigning a network interface to a zone
It is possible to define different sets of rules for different zones and then change the settings quickly by changing the zone for the interface that is being used. With multiple interfaces, a specific zone can be set for each of them to distinguish traffic that is coming through them.
Procedure
List the active zones and the interfaces assigned to them:
firewall-cmd --get-active-zones
# firewall-cmd --get-active-zonesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Assign the interface to a different zone:
firewall-cmd --zone=zone_name --change-interface=interface_name --permanent
# firewall-cmd --zone=zone_name --change-interface=interface_name --permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.7.4. Adding a source
To route incoming traffic into a specific zone, add the source to that zone. The source can be an IP address or an IP mask in the classless inter-domain routing (CIDR) notation.
In case you add multiple zones with an overlapping network range, they are ordered alphanumerically by zone name and only the first one is considered.
To set the source in the current zone:
firewall-cmd --add-source=<source>
# firewall-cmd --add-source=<source>Copy to Clipboard Copied! Toggle word wrap Toggle overflow To set the source IP address for a specific zone:
firewall-cmd --zone=zone-name --add-source=<source>
# firewall-cmd --zone=zone-name --add-source=<source>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The following procedure allows all incoming traffic from 192.168.2.15 in the trusted zone:
Procedure
List all available zones:
firewall-cmd --get-zones
# firewall-cmd --get-zonesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the source IP to the trusted zone in the permanent mode:
firewall-cmd --zone=trusted --add-source=192.168.2.15
# firewall-cmd --zone=trusted --add-source=192.168.2.15Copy to Clipboard Copied! Toggle word wrap Toggle overflow Make the new settings persistent:
firewall-cmd --runtime-to-permanent
# firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.7.5. Removing a source
When you remove a source from a firewalld zone, its traffic is no longer directed by that source’s rules. Instead, it falls back to the rules of the interface’s zone or the default zone.
Procedure
List allowed sources for the required zone:
firewall-cmd --zone=zone-name --list-sources
# firewall-cmd --zone=zone-name --list-sourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the source from the zone permanently:
firewall-cmd --zone=zone-name --remove-source=<source>
# firewall-cmd --zone=zone-name --remove-source=<source>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Make the new settings persistent:
firewall-cmd --runtime-to-permanent
# firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.7.6. Assigning a zone to a connection by using nmcli
You can add a firewalld zone to a NetworkManager connection using the nmcli utility.
Procedure
Assign the zone to the
NetworkManagerconnection profile:nmcli connection modify profile connection.zone zone_name
# nmcli connection modify profile connection.zone zone_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Activate the connection:
nmcli connection up profile
# nmcli connection up profileCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.7.7. Manually assigning a zone to a network connection in an ifcfg file
When the connection is managed by NetworkManager, it must be aware of a zone that it uses. For every network connection profile, a zone can be specified, which provides the flexibility of various firewall settings according to the location of the computer with portable devices. Thus, zones and settings can be specified for different locations, such as company or home.
Procedure
To set a zone for a connection, edit the
/etc/sysconfig/network-scripts/ifcfg-connection_namefile and add a line that assigns a zone to this connection:ZONE=zone_name
ZONE=zone_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.7.8. Creating a new zone
To use custom zones, create a new zone and use it just like a predefined zone. New zones require the --permanent option, otherwise the command does not work.
Prerequisites
-
The
firewalldservice is running.
Procedure
Create a new zone:
firewall-cmd --permanent --new-zone=zone-name
# firewall-cmd --permanent --new-zone=zone-nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Make the new zone usable:
firewall-cmd --reload
# firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command applies recent changes to the firewall configuration without interrupting network services that are already running.
Verification
Check if the new zone is added to your permanent settings:
firewall-cmd --get-zones --permanent
# firewall-cmd --get-zones --permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.7.9. Enabling zones by using the web console
You can apply predefined and existing firewall zones on a particular interface or a range of IP addresses through the RHEL web console.
Prerequisites
- You have installed the RHEL 8 web console.
- You have enabled the cockpit service.
Your user account is allowed to log in to the web console.
For instructions, see Installing and enabling the web console.
- You enabled administrative access in the web console.
-
The
firewalldservice is running.
Procedure
Log in to the RHEL 8 web console.
For details, see Logging in to the web console.
- Click Networking.
Click the button.
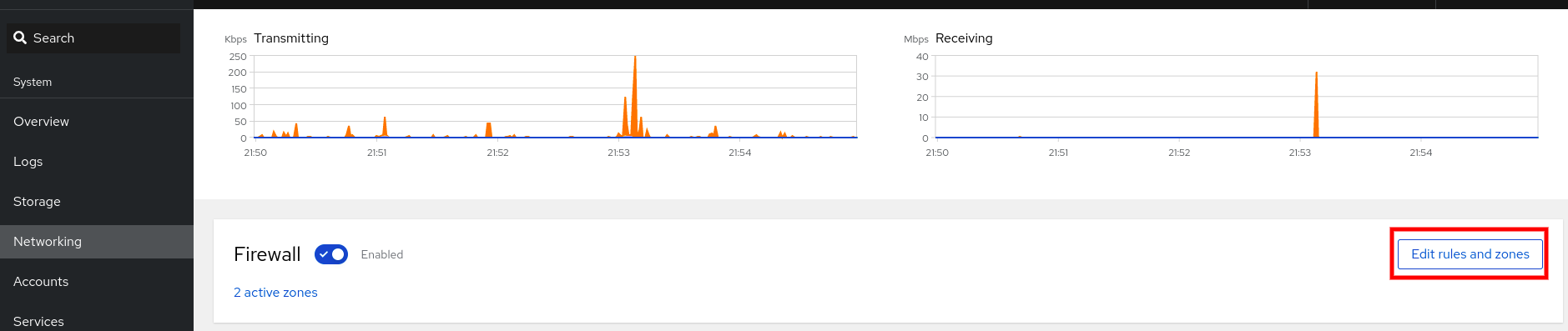
If you do not see the button, log in to the web console with the administrator privileges.
- In the Firewall section, click Add new zone.
In the Add zone dialog box, select a zone from the Trust level options.
The web console displays all zones predefined in the
firewalldservice.- In the Interfaces part, select an interface or interfaces to which you want to apply the selected zone.
In the Allowed Addresses part, you can select whether the zone is applied to:
- the whole subnet
a range of IP addresses in the following format:
- 192.168.1.0
- 192.168.1.0/24
- 192.168.1.0/24, 192.168.1.0
Click the button.
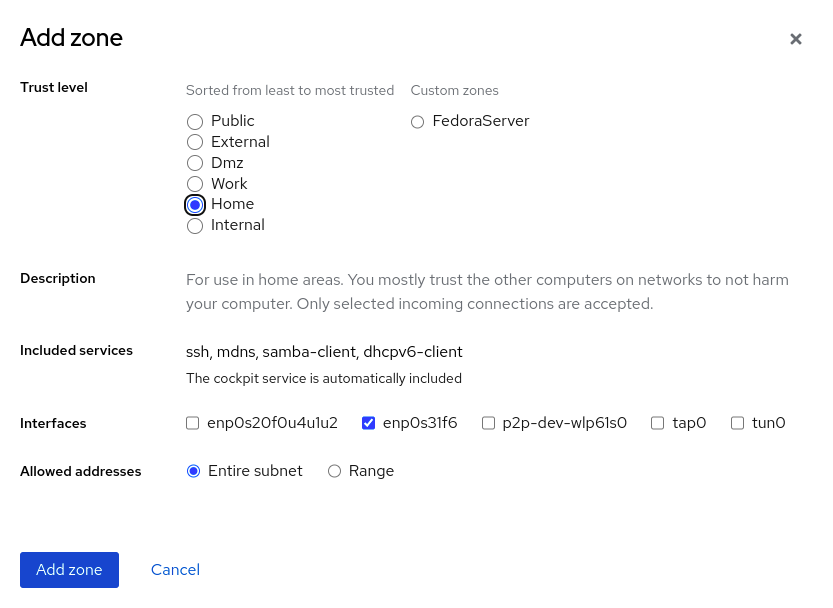
Verification
Check the configuration in the Firewall section:
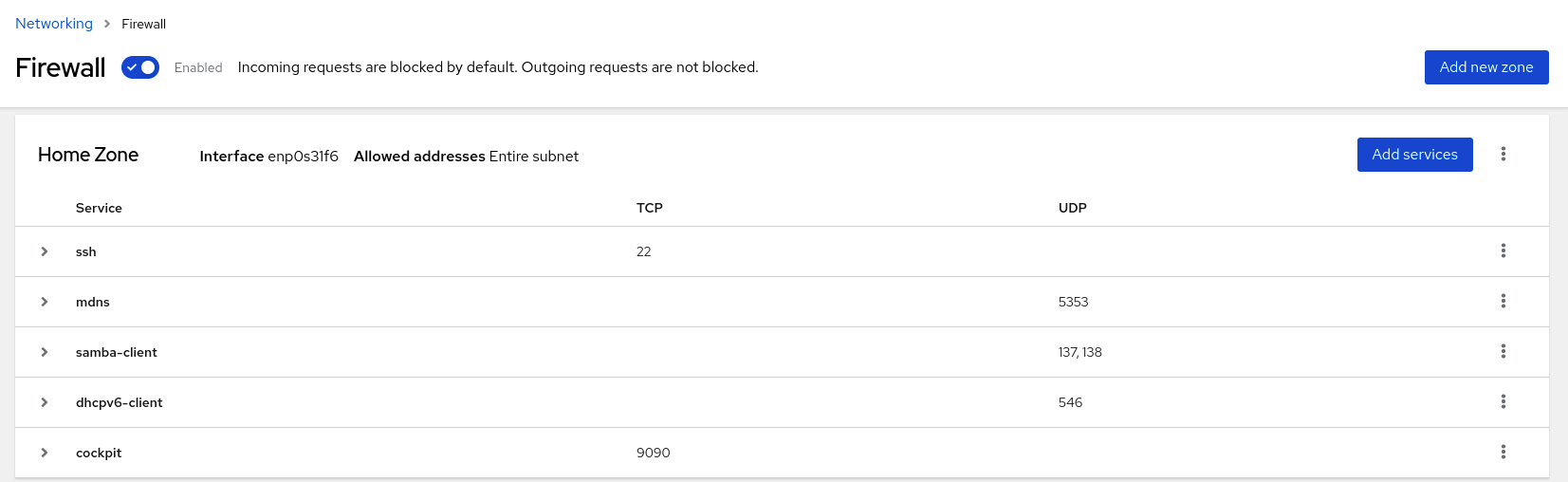
7.7.10. Disabling zones by using the web console
You can remove a firewall zone from your firewall configuration by using the web console.
Prerequisites
- You have installed the RHEL 8 web console.
- You have enabled the cockpit service.
Your user account is allowed to log in to the web console.
For instructions, see Installing and enabling the web console.
- You enabled administrative access in the web console.
-
The
firewalldservice is running.
Procedure
Log in to the RHEL 8 web console.
For details, see Logging in to the web console.
- Click Networking.
Click the button.

If you do not see the button, log in to the web console with the administrator privileges.
Click the Options icon at the zone you want to remove.
- Click Delete.
7.7.11. Using zone targets to set default behavior for incoming traffic
For every zone, you can set a default behavior that handles incoming traffic that is not further specified. Such behavior is defined by setting the target of the zone.
-
ACCEPT: Accepts all incoming packets except those disallowed by specific rules. -
REJECT: Rejects all incoming packets except those allowed by specific rules. Whenfirewalldrejects packets, the source machine is informed about the rejection. -
DROP: Drops all incoming packets except those allowed by specific rules. Whenfirewallddrops packets, the source machine is not informed about the packet drop. -
default: Similar behavior as forREJECT, but with special meanings in certain scenarios.
Prerequisites
-
The
firewalldservice is running.
Procedure
List the information for the specific zone to see the default target:
firewall-cmd --zone=zone-name --list-all
# firewall-cmd --zone=zone-name --list-allCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set a new target in the zone:
firewall-cmd --permanent --zone=zone-name --set-target=<default|ACCEPT|REJECT|DROP>
# firewall-cmd --permanent --zone=zone-name --set-target=<default|ACCEPT|REJECT|DROP>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.7.12. Configuring dynamic updates for allowlisting with IP sets
You can make near real-time updates to flexibly allow specific IP addresses or ranges in the IP sets even in unpredictable conditions.
These updates can be triggered by various events, such as detection of security threats or changes in the network behavior. Typically, such a solution leverages automation to reduce manual effort and improve security by responding quickly to the situation.
Prerequisites
-
The
firewalldservice is running.
Procedure
Create an IP set with a meaningful name:
firewall-cmd --permanent --new-ipset=allowlist --type=hash:ip
# firewall-cmd --permanent --new-ipset=allowlist --type=hash:ipCopy to Clipboard Copied! Toggle word wrap Toggle overflow The new IP set called
allowlistcontains IP addresses that you want your firewall to allow.Add a dynamic update to the IP set:
firewall-cmd --permanent --ipset=allowlist --add-entry=198.51.100.10
# firewall-cmd --permanent --ipset=allowlist --add-entry=198.51.100.10Copy to Clipboard Copied! Toggle word wrap Toggle overflow This configuration updates the
allowlistIP set with a newly added IP address that is allowed to pass network traffic by your firewall.Create a firewall rule that references the previously created IP set:
firewall-cmd --permanent --zone=public --add-source=ipset:allowlist
# firewall-cmd --permanent --zone=public --add-source=ipset:allowlistCopy to Clipboard Copied! Toggle word wrap Toggle overflow Without this rule, the IP set would not have any impact on network traffic. The default firewall policy would prevail.
Reload the firewall configuration to apply the changes:
firewall-cmd --reload
# firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
List all IP sets:
firewall-cmd --get-ipsets allowlist
# firewall-cmd --get-ipsets allowlistCopy to Clipboard Copied! Toggle word wrap Toggle overflow List the active rules:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
sourcessection of the command-line output provides insights to what origins of traffic (hostnames, interfaces, IP sets, subnets, and others) are permitted or denied access to a particular firewall zone. In this case, the IP addresses contained in theallowlistIP set are allowed to pass traffic through the firewall for thepubliczone.Explore the contents of your IP set:
cat /etc/firewalld/ipsets/allowlist.xml <?xml version="1.0" encoding="utf-8"?> <ipset type="hash:ip"> <entry>198.51.100.10</entry> </ipset>
# cat /etc/firewalld/ipsets/allowlist.xml <?xml version="1.0" encoding="utf-8"?> <ipset type="hash:ip"> <entry>198.51.100.10</entry> </ipset>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
-
Use a script or a security utility to fetch your threat intelligence feeds and update
allowlistaccordingly in an automated fashion.
7.8. Controlling network traffic using firewalld
The firewalld package installs a large number of predefined service files and you can add more or customize them. You can then use these service definitions to open or close ports for services without knowing the protocol and port numbers they use.
7.8.1. Controlling traffic with predefined services using the CLI
The most straightforward method to control traffic is to add a predefined service to firewalld. This opens all necessary ports and modifies other settings according to the service definition file.
Prerequisites
-
The
firewalldservice is running.
Procedure
Check that the service in
firewalldis not already allowed:firewall-cmd --list-services ssh dhcpv6-client
# firewall-cmd --list-services ssh dhcpv6-clientCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command lists the services that are enabled in the default zone.
List all predefined services in
firewalld:firewall-cmd --get-services RH-Satellite-6 amanda-client amanda-k5-client bacula bacula-client bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc ceph ceph-mon cfengine condor-collector ctdb dhcp dhcpv6 dhcpv6-client dns docker-registry ...
# firewall-cmd --get-services RH-Satellite-6 amanda-client amanda-k5-client bacula bacula-client bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc ceph ceph-mon cfengine condor-collector ctdb dhcp dhcpv6 dhcpv6-client dns docker-registry ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command displays a list of available services for the default zone.
Add the service to the list of services that
firewalldallows:firewall-cmd --add-service=<service_name>
# firewall-cmd --add-service=<service_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command adds the specified service to the default zone.
Make the new settings persistent:
firewall-cmd --runtime-to-permanent
# firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command applies these runtime changes to the permanent configuration of the firewall. By default, it applies these changes to the configuration of the default zone.
Verification
List all permanent firewall rules:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command displays complete configuration with the permanent firewall rules of the default firewall zone (
public).Check the validity of the permanent configuration of the
firewalldservice.firewall-cmd --check-config success
# firewall-cmd --check-config successCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the permanent configuration is invalid, the command returns an error with further details:
firewall-cmd --check-config Error: INVALID_PROTOCOL: 'public.xml': 'tcpx' not from {'tcp'|'udp'|'sctp'|'dccp'}# firewall-cmd --check-config Error: INVALID_PROTOCOL: 'public.xml': 'tcpx' not from {'tcp'|'udp'|'sctp'|'dccp'}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can also manually inspect the permanent configuration files to verify the settings. The main configuration file is
/etc/firewalld/firewalld.conf. The zone-specific configuration files are in the/etc/firewalld/zones/directory and the policies are in the/etc/firewalld/policies/directory.
7.8.2. Enabling services on the firewall by using the web console
By default, services are added to the default firewall zone. If you use more firewall zones on more network interfaces, you must select a zone first and then add the service with port.
The RHEL web console displays predefined firewalld services and you can add them to active firewall zones.
The RHEL 8 web console configures the firewalld service.
The web console does not allow generic firewalld rules that are not listed in the web console.
Prerequisites
- You have installed the RHEL 8 web console.
- You have enabled the cockpit service.
Your user account is allowed to log in to the web console.
For instructions, see Installing and enabling the web console.
- You enabled administrative access in the web console.
-
The
firewalldservice is running.
Procedure
Log in to the RHEL 8 web console.
For details, see Logging in to the web console.
- Click Networking.
Click the button.

If you do not see the button, log in to the web console with the administrator privileges.
In the Firewall section, select a zone for which you want to add the service and click Add Services.

- In the Add Services dialog box, find the service you want to enable in the firewall.
Enable services according to your scenario:
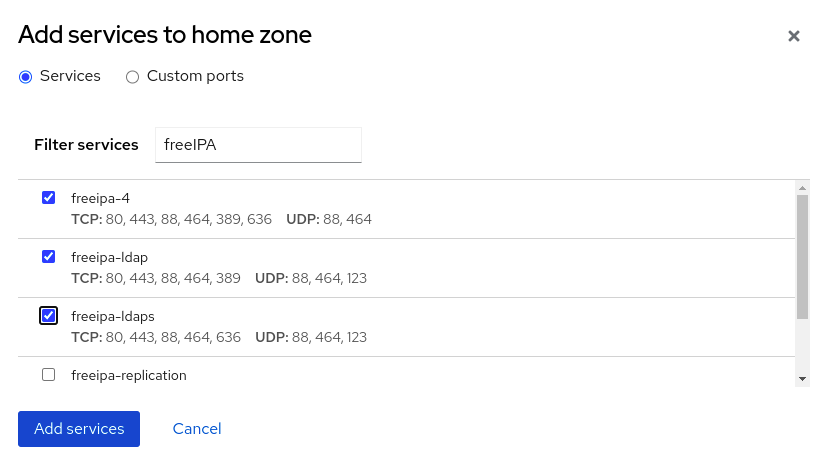
- Click Add Services.
7.8.3. Configuring custom ports by using the web console
You can add custom ports for services through the RHEL web console.
Prerequisites
- You have installed the RHEL 8 web console.
- You have enabled the cockpit service.
Your user account is allowed to log in to the web console.
For instructions, see Installing and enabling the web console.
-
The
firewalldservice is running.
Procedure
Log in to the RHEL 8 web console.
For details, see Logging in to the web console.
- Click Networking.
Click the button.

If you do not see the button, log in to the web console with the administrative privileges.
In the Firewall section, select a zone for which you want to configure a custom port and click Add Services.

- In the Add services dialog box, click the radio button.
In the TCP and UDP fields, add ports according to examples. You can add ports in the following formats:
- Port numbers such as 22
- Range of port numbers such as 5900-5910
- Aliases such as nfs, rsync
NoteYou can add multiple values into each field. You must separate values with a comma and without a space, for example: 8080,8081,http
After adding the port number in the TCP field, the UDP field, or both, verify the service name in the Name field.
The Name field displays the name of the service for which this port is reserved. You can rewrite the name if you are sure that this port is free to use and no server requires it to communicate on this port.
- In the Name field, add a name for the service including defined ports.
Click the button.
Verification
To verify the settings, go to the Firewall page and find the service in the list of zone’s Services.

7.9. Filtering forwarded traffic between zones
firewalld enables you to control the flow of network data between different firewalld zones. By defining rules and policies, you can manage how traffic is allowed or blocked when it moves between these zones.
The policy objects feature provides forward and output filtering in firewalld. You can use firewalld to filter traffic between different zones to allow access to locally hosted VMs to connect the host.
7.9.1. The relationship between policy objects and zones
Policy objects allow the user to attach firewalld’s primitives such as services, ports, and rich rules to the policy. You can apply the policy objects to traffic that passes between zones in a stateful and unidirectional manner.
firewall-cmd --permanent --new-policy myOutputPolicy firewall-cmd --permanent --policy myOutputPolicy --add-ingress-zone HOST firewall-cmd --permanent --policy myOutputPolicy --add-egress-zone ANY
# firewall-cmd --permanent --new-policy myOutputPolicy
# firewall-cmd --permanent --policy myOutputPolicy --add-ingress-zone HOST
# firewall-cmd --permanent --policy myOutputPolicy --add-egress-zone ANY
HOST and ANY are the symbolic zones used in the ingress and egress zone lists.
-
The
HOSTsymbolic zone allows policies for the traffic originating from or has a destination to the host running firewalld. -
The
ANYsymbolic zone applies policy to all the current and future zones.ANYsymbolic zone acts as a wildcard for all zones.
7.9.2. Using priorities to sort policies
Multiple policies can apply to the same set of traffic, therefore, priorities should be used to create an order of precedence for the policies that may be applied.
Procedure
Set a priority to sort the policies:
firewall-cmd --permanent --policy mypolicy --set-priority -500
# firewall-cmd --permanent --policy mypolicy --set-priority -500Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the above example -500 is a lower priority value but has higher precedence. Thus, -500 will execute before -100.
Lower numerical priority values have higher precedence and are applied first.
7.9.3. Using policy objects to filter traffic between locally hosted containers and a network physically connected to the host
The policy objects feature enables users to filter traffic between Podman and firewalld zones.
Red Hat recommends blocking all traffic by default and opening the selective services needed for the Podman utility.
Procedure
Create a new firewall policy:
firewall-cmd --permanent --new-policy podmanToAny
# firewall-cmd --permanent --new-policy podmanToAnyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Block all traffic from Podman to other zones and allow only necessary services on Podman:
firewall-cmd --permanent --policy podmanToAny --set-target REJECT firewall-cmd --permanent --policy podmanToAny --add-service dhcp firewall-cmd --permanent --policy podmanToAny --add-service dns firewall-cmd --permanent --policy podmanToAny --add-service https
# firewall-cmd --permanent --policy podmanToAny --set-target REJECT # firewall-cmd --permanent --policy podmanToAny --add-service dhcp # firewall-cmd --permanent --policy podmanToAny --add-service dns # firewall-cmd --permanent --policy podmanToAny --add-service httpsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a new Podman zone:
firewall-cmd --permanent --new-zone=podman
# firewall-cmd --permanent --new-zone=podmanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Define the ingress zone for the policy:
firewall-cmd --permanent --policy podmanToHost --add-ingress-zone podman
# firewall-cmd --permanent --policy podmanToHost --add-ingress-zone podmanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Define the egress zone for all other zones:
firewall-cmd --permanent --policy podmanToHost --add-egress-zone ANY
# firewall-cmd --permanent --policy podmanToHost --add-egress-zone ANYCopy to Clipboard Copied! Toggle word wrap Toggle overflow Setting the egress zone to ANY means that you filter from Podman to other zones. If you want to filter to the host, then set the egress zone to HOST.
Restart the firewalld service:
systemctl restart firewalld
# systemctl restart firewalldCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify the Podman firewall policy to other zones:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.9.4. Setting the default target of policy objects
You can specify --set-target options for policies.
The following targets are available:
-
ACCEPT- accepts the packet -
DROP- drops the unwanted packets -
REJECT- rejects unwanted packets with an ICMP reply -
CONTINUE(default) - packets will be subject to rules in following policies and zones.
Procedure
Set the default target:
firewall-cmd --permanent --policy mypolicy --set-target CONTINUE
# firewall-cmd --permanent --policy mypolicy --set-target CONTINUECopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify information about the policy
firewall-cmd --info-policy mypolicy
# firewall-cmd --info-policy mypolicyCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.10. Configuring NAT by using firewalld
With firewalld, you can configure the masquerading, destination NAT (DNAT), and redirect NAT types. With NAT, you can modify the source or destination IP address.
7.10.1. Network address translation types
If you require network address translation (NAT) in your network, it is important to understand the NAT types.
These are the different NAT types:
- Masquerading
Use this NAT type to change the source IP address of packets. For example, Internet Service Providers (ISPs) do not route private IP ranges, such as
10.0.0.0/8. If you use private IP ranges in your network and users should be able to reach servers on the internet, map the source IP address of packets from these ranges to a public IP address.Masquerading automatically uses the IP address of the outgoing interface. Therefore, use masquerading if the outgoing interface uses a dynamic IP address.
- Destination NAT (DNAT)
- Use this NAT type to rewrite the destination address and port of incoming packets. For example, if your web server uses an IP address from a private IP range and is, therefore, not directly accessible from the internet, you can set a DNAT rule on the router to redirect incoming traffic to this server.
- Redirect
- This type is a special case of DNAT that redirects packets to a different port on the local machine. For example, if a service runs on a different port than its standard port, you can redirect incoming traffic from the standard port to this specific port.
7.10.2. Configuring IP address masquerading
You can enable IP masquerading on your system. IP masquerading hides individual machines behind a gateway when accessing the internet.
Procedure
To check if IP masquerading is enabled (for example, for the
externalzone), enter the following command asroot:firewall-cmd --zone=external --query-masquerade
# firewall-cmd --zone=external --query-masqueradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command prints
yeswith exit status0if enabled. It printsnowith exit status1otherwise. Ifzoneis omitted, the default zone will be used.To enable IP masquerading, enter the following command as
root:firewall-cmd --zone=external --add-masquerade
# firewall-cmd --zone=external --add-masqueradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
To make this setting persistent, pass the
--permanentoption to the command. To disable IP masquerading, enter the following command as
root:firewall-cmd --zone=external --remove-masquerade
# firewall-cmd --zone=external --remove-masqueradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow To make this setting permanent, pass the
--permanentoption to the command.
7.10.3. Using DNAT to forward incoming HTTP traffic
You can use destination network address translation (DNAT) to direct incoming traffic from one destination address and port to another. Typically, this is useful for redirecting incoming requests from an external network interface to specific internal servers or services.
Prerequisites
-
The
firewalldservice is running.
Procedure
Forward incoming HTTP traffic:
firewall-cmd --zone=public --add-forward-port=port=80:proto=tcp:toaddr=198.51.100.10:toport=8080 --permanent
# firewall-cmd --zone=public --add-forward-port=port=80:proto=tcp:toaddr=198.51.100.10:toport=8080 --permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow The previous command defines a DNAT rule with the following settings:
-
--zone=public- The firewall zone for which you configure the DNAT rule. You can adjust this to whatever zone you need. -
--add-forward-port- The option that indicates you are adding a port-forwarding rule. -
port=80- The external destination port. -
proto=tcp- The protocol indicating that you forward TCP traffic. -
toaddr=198.51.100.10- The destination IP address. -
toport=8080- The destination port of the internal server. -
--permanent- The option that makes the DNAT rule persistent across reboots.
-
Reload the firewall configuration to apply the changes:
firewall-cmd --reload
# firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify the DNAT rule for the firewall zone that you used:
firewall-cmd --list-forward-ports --zone=public port=80:proto=tcp:toport=8080:toaddr=198.51.100.10
# firewall-cmd --list-forward-ports --zone=public port=80:proto=tcp:toport=8080:toaddr=198.51.100.10Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, view the corresponding XML configuration file:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.10.4. Redirecting traffic from a non-standard port to make the web service accessible on a standard port
You can use the redirect mechanism to make the web service that internally runs on a non-standard port accessible without requiring users to specify the port in the URL.
If you use redirect, the URLs are simpler and provide better browsing experience, while a non-standard port is still used internally or for specific requirements.
Prerequisites
-
The
firewalldservice is running.
Procedure
Create the NAT redirect rule:
firewall-cmd --zone=public --add-forward-port=port=<standard_port>:proto=tcp:toport=<non_standard_port> --permanent
# firewall-cmd --zone=public --add-forward-port=port=<standard_port>:proto=tcp:toport=<non_standard_port> --permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow The previous command defines the NAT redirect rule with the following settings:
-
--zone=public- The firewall zone, for which you configure the rule. You can adjust this to whatever zone you need. -
--add-forward-port=port=<non_standard_port>- The option that indicates you are adding a port-forwarding (redirecting) rule with source port on which you initially receive the incoming traffic. -
proto=tcp- The protocol indicating that you redirect TCP traffic. -
toport=<standard_port>- The destination port, to which the incoming traffic should be redirected after being received on the source port. -
--permanent- The option that makes the rule persist across reboots.
-
Reload the firewall configuration to apply the changes:
firewall-cmd --reload
# firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify the redirect rule for the firewall zone that you used:
firewall-cmd --list-forward-ports port=8080:proto=tcp:toport=80:toaddr=
# firewall-cmd --list-forward-ports port=8080:proto=tcp:toport=80:toaddr=Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, view the corresponding XML configuration file:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.11. Prioritizing rich rules
Rich rules provide a more advanced and flexible way to define firewall rules. Rich rules are particularly useful where services, ports, and so on are not enough to express complex firewall rules.
Concepts behind rich rules:
- granularity and flexibility
- You can define detailed conditions for network traffic based on more specific criteria.
- rule structure
A rich rule consists of a family (IPv4 or IPv6), followed by conditions and actions.
rule family="ipv4|ipv6" [conditions] [actions]
rule family="ipv4|ipv6" [conditions] [actions]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - conditions
- They allow rich rules to apply only when certain criteria are met.
- actions
- You can define what happens to network traffic that matches the conditions.
- combining multiple conditions
- You can create more specific and complex filtering.
- hierarchical control and reusability
- You can combine rich rules with other firewall mechanisms such as zones or services.
By default, rich rules are organized based on their rule action. For example, deny rules have precedence over allow rules. The priority parameter in rich rules provides administrators fine-grained control over rich rules and their execution order. When using the priority parameter, rules are sorted first by their priority values in ascending order. When more rules have the same priority, their order is determined by the rule action, and if the action is also the same, the order may be undefined.
7.11.1. How the priority parameter organizes rules into different chains
You can set the priority parameter in a rich rule to any number between -32768 and 32767, and lower numerical values have higher precedence.
The firewalld service organizes rules based on their priority value into different chains:
-
Priority lower than 0: the rule is redirected into a chain with the
_presuffix. -
Priority higher than 0: the rule is redirected into a chain with the
_postsuffix. -
Priority equals 0: based on the action, the rule is redirected into a chain with the
_log,_deny, or_allowthe action.
Inside these sub-chains, firewalld sorts the rules based on their priority value.
7.11.2. Setting the priority of a rich rule
You can use the priority parameter to log all traffic that is not allowed or denied by other rules. For example, you can use this feature to flag unexpected traffic.
Procedure
Add a rich rule with a very low precedence to log all traffic that has not been matched by other rules:
firewall-cmd --add-rich-rule='rule priority=32767 log prefix="UNEXPECTED: " limit value="5/m"'
# firewall-cmd --add-rich-rule='rule priority=32767 log prefix="UNEXPECTED: " limit value="5/m"'Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command additionally limits the number of log entries to
5per minute.
Verification
Display the
nftablesrule that the command in the previous step created:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.12. Enabling traffic forwarding between different interfaces or sources within a firewalld zone
Intra-zone forwarding is a firewalld feature that enables traffic forwarding between interfaces or sources within a firewalld zone.
7.12.1. The difference between intra-zone forwarding and zones with the default target set to ACCEPT
With intra-zone forwarding enabled, the traffic within a single firewalld zone can flow from one interface or source to another interface or source. The zone specifies the trust level of interfaces and sources. If the trust level is the same, the traffic stays inside the same zone.
Enabling intra-zone forwarding in the default zone of firewalld, applies only to the interfaces and sources added to the current default zone.
firewalld uses different zones to manage incoming and outgoing traffic. Each zone has its own set of rules and behaviors. For example, the trusted zone allows all forwarded traffic by default.
Other zones can have different default behaviors. In standard zones, forwarded traffic is typically dropped by default when the target of the zone is set to default.
To control how the traffic is forwarded between different interfaces or sources within a zone, make sure you understand and configure the target of the zone accordingly.
7.12.2. Using intra-zone forwarding to forward traffic between an Ethernet and Wi-Fi network
You can use intra-zone forwarding to forward traffic between interfaces and sources within the same firewalld zone.
This feature brings the following benefits:
-
Seamless connectivity between wired and wireless devices (you can forward traffic between an Ethernet network connected to
enp1s0and a Wi-Fi network connected towlp0s20) - Support for flexible work environments
- Shared resources that are accessible and used by multiple devices or users within a network (such as printers, databases, network-attached storage, and others)
- Efficient internal networking (such as smooth communication, reduced latency, resource accessibility, and others)
You can enable this functionality for individual firewalld zones.
Procedure
Enable packet forwarding in the kernel:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that interfaces between which you want to enable intra-zone forwarding are assigned only to the
internalzone:firewall-cmd --get-active-zones
# firewall-cmd --get-active-zonesCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the interface is currently assigned to a zone other than
internal, reassign it:firewall-cmd --zone=internal --change-interface=interface_name --permanent
# firewall-cmd --zone=internal --change-interface=interface_name --permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
enp1s0andwlp0s20interfaces to theinternalzone:firewall-cmd --zone=internal --add-interface=enp1s0 --add-interface=wlp0s20
# firewall-cmd --zone=internal --add-interface=enp1s0 --add-interface=wlp0s20Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable intra-zone forwarding:
firewall-cmd --zone=internal --add-forward
# firewall-cmd --zone=internal --add-forwardCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
-
Log in to a host that is on the same network as the
enp1s0interface of the host on which you enabled zone forwarding. Start an echo service with
ncatto test connectivity:ncat -e /usr/bin/cat -l 12345
# ncat -e /usr/bin/cat -l 12345Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Log in to a host that is in the same network as the
wlp0s20interface. Connect to the echo server running on the host that is in the same network as the
enp1s0:ncat <other_host> 12345
# ncat <other_host> 12345Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Type something and press . Verify the text is sent back.
7.13. Configuring firewalld by using RHEL system roles
RHEL system roles is a set of contents for the Ansible automation utility. This content together with the Ansible automation utility provides a consistent configuration interface to remotely manage multiple systems at once.
The rhel-system-roles package contains the rhel-system-roles.firewall RHEL system role. This role was introduced for automated configurations of the firewalld service.
With the firewall RHEL system role you can configure many different firewalld parameters, for example:
- Zones
- The services for which packets should be allowed
- Granting, rejection, or dropping of traffic access to ports
- Forwarding of ports or port ranges for a zone
7.13.1. Resetting the firewalld settings by using the firewall RHEL system role
The firewall RHEL system role supports automating a reset of firewalld settings to their defaults. This efficiently removes insecure or unintentional firewall rules and simplifies management.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
previous: replacedRemoves all existing user-defined settings and resets the
firewalldsettings to defaults. If you combine theprevious:replacedparameter with other settings, thefirewallrole removes all existing settings before applying new ones.For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.firewall/README.mdfile on the control node.
Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Run this command on the control node to remotely check that all firewall configuration on your managed node was reset to its default values:
ansible managed-node-01.example.com -m ansible.builtin.command -a 'firewall-cmd --list-all-zones'
# ansible managed-node-01.example.com -m ansible.builtin.command -a 'firewall-cmd --list-all-zones'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.13.2. Forwarding incoming traffic in firewalld from one local port to a different local port by using the firewall RHEL system role
You can use the firewall RHEL system role to remotely configure forwarding of incoming traffic from one local port to a different local port.
For example, if you have an environment where multiple services co-exist on the same machine and need the same default port, there are likely to become port conflicts. These conflicts can disrupt services and cause downtime. With the firewall RHEL system role, you can efficiently forward traffic to alternative ports to ensure that your services can run simultaneously without modification to their configuration.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
forward_port: 8080/tcp;443- Traffic coming to the local port 8080 using the TCP protocol is forwarded to port 443.
runtime: trueEnables changes in the runtime configuration. The default is set to
true.For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.firewall/README.mdfile on the control node.
Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
On the control node, run the following command to remotely check the forwarded-ports on your managed node:
ansible managed-node-01.example.com -m ansible.builtin.command -a 'firewall-cmd --list-forward-ports' managed-node-01.example.com | CHANGED | rc=0 >> port=8080:proto=tcp:toport=443:toaddr=
# ansible managed-node-01.example.com -m ansible.builtin.command -a 'firewall-cmd --list-forward-ports' managed-node-01.example.com | CHANGED | rc=0 >> port=8080:proto=tcp:toport=443:toaddr=Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.13.3. Configuring a firewalld DMZ zone by using the firewall RHEL system role
You can use the firewall RHEL system role to configure a zone to allow certain traffic. For example, you can configure that the dmz zone with the enp1s0 interface allows HTTPS traffic to enable external users to access your web servers.
Prerequisites
- You have prepared the control node and the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow For details about all variables used in the playbook, see the
/usr/share/ansible/roles/rhel-system-roles.firewall/README.mdfile on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
On the control node, run the following command to remotely check the information about the
dmzzone on your managed node:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 8. Getting started with nftables
If your scenario does not fall under typical packet-filtering cases covered by firewalld, or you want to have complete control of rules, you can use the nftables framework.
The nftables framework classifies packets, and it is the successor to the iptables, ip6tables, arptables, ebtables, and ipset utilities. It offers numerous improvements in convenience, features, and performance over previous packet-filtering tools, most notably:
- Built-in lookup tables instead of linear processing
-
A single framework for both the
IPv4andIPv6protocols - Updating the kernel rule set in place through transactions instead of fetching, updating, and storing the entire rule set
-
Support for debugging and tracing in the rule set (
nftrace) and monitoring trace events (in thenfttool) - More consistent and compact syntax, no protocol-specific extensions
- A Netlink API for third-party applications
The nftables framework uses tables to store chains. The chains contain individual rules for performing actions. The nft utility replaces all tools from the previous packet-filtering frameworks. You can use the libnftables library for low-level interaction with nftables Netlink API through the libnftnl library.
To display the effect of rule set changes, use the nft list ruleset command. To clear the kernel rule set, use the nft flush ruleset command. Note that this may also affect the rule set installed by the iptables-nft command, as it utilizes the same kernel infrastructure.
8.1. Creating and managing nftables tables, chains, and rules
You can display nftables rule sets and manage them.
8.1.1. Basics of nftables tables
A table in nftables is a namespace that contains a collection of chains, rules, sets, and other objects.
Each table must have an address family assigned. The address family defines the packet types that this table processes. You can set one of the following address families when you create a table:
-
ip: Matches only IPv4 packets. This is the default if you do not specify an address family. -
ip6: Matches only IPv6 packets. -
inet: Matches both IPv4 and IPv6 packets. -
arp: Matches IPv4 address resolution protocol (ARP) packets. -
bridge: Matches packets that pass through a bridge device. -
netdev: Matches packets from ingress.
If you want to add a table, the format to use depends on your firewall script:
In scripts in native syntax, use:
table <table_address_family> <table_name> { }table <table_address_family> <table_name> { }Copy to Clipboard Copied! Toggle word wrap Toggle overflow In shell scripts, use:
nft add table <table_address_family> <table_name>
nft add table <table_address_family> <table_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.1.2. Basics of nftables chains
Tables consist of chains which in turn are containers for rules. The following two rule types exists:
- Base chain: You can use base chains as an entry point for packets from the networking stack.
-
Regular chain: You can use regular chains as a
jumptarget to better organize rules.
If you want to add a base chain to a table, the format to use depends on your firewall script:
In scripts in native syntax, use:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In shell scripts, use:
nft add chain <table_address_family> <table_name> <chain_name> { type <type> hook <hook> priority <priority> \; policy <policy> \; }nft add chain <table_address_family> <table_name> <chain_name> { type <type> hook <hook> priority <priority> \; policy <policy> \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow To avoid that the shell interprets the semicolons as the end of the command, place the
\escape character in front of the semicolons.
Both examples create base chains. To create a regular chain, do not set any parameters in the curly brackets.
Chain types:
The following are the chain types and an overview with which address families and hooks you can use them:
| Type | Address families | Hooks | Description |
|---|---|---|---|
|
| all | all | Standard chain type |
|
|
|
| Chains of this type perform native address translation based on connection tracking entries. Only the first packet traverses this chain type. |
|
|
|
| Accepted packets that traverse this chain type cause a new route lookup if relevant parts of the IP header have changed. |
Chain priorities:
The priority parameter specifies the order in which packets traverse chains with the same hook value. You can set this parameter to an integer value or use a standard priority name.
The following matrix is an overview of the standard priority names and their numeric values, and with which address families and hooks you can use them:
| Textual value | Numeric value | Address families | Hooks |
|---|---|---|---|
|
|
|
| all |
|
|
|
| all |
|
|
|
|
|
|
|
|
| |
|
|
|
| all |
|
|
| all | |
|
|
|
| all |
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
Chain policies:
The chain policy defines whether nftables should accept or drop packets if rules in this chain do not specify any action. You can set one of the following policies in a chain:
-
accept(default) -
drop
8.1.3. Basics of nftables rules
Rules define actions to perform on packets that pass a chain that contains this rule. If the rule also contains matching expressions, nftables performs the actions only if all previous expressions apply.
If you want to add a rule to a chain, the format to use depends on your firewall script:
In scripts in native syntax, use:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In shell scripts, use:
nft add rule <table_address_family> <table_name> <chain_name> <rule>
nft add rule <table_address_family> <table_name> <chain_name> <rule>Copy to Clipboard Copied! Toggle word wrap Toggle overflow This shell command appends the new rule at the end of the chain. If you prefer to add a rule at the beginning of the chain, use the
nft insertcommand instead ofnft add.
8.1.4. Managing tables, chains, and rules by using nft commands
To manage an nftables firewall on the command line or in shell scripts, use the nft utility.
The commands in this procedure do not represent a typical workflow and are not optimized. This procedure only demonstrates how to use nft commands to manage tables, chains, and rules in general.
Procedure
Create a table named
nftables_svcwith theinetaddress family so that the table can process both IPv4 and IPv6 packets:nft add table inet nftables_svc
# nft add table inet nftables_svcCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a base chain named
INPUT, that processes incoming network traffic, to theinet nftables_svctable:nft add chain inet nftables_svc INPUT { type filter hook input priority filter \; policy accept \; }# nft add chain inet nftables_svc INPUT { type filter hook input priority filter \; policy accept \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow To avoid that the shell interprets the semicolons as the end of the command, escape the semicolons using the
\character.Add rules to the
INPUTchain. For example, allow incoming TCP traffic on port 22 and 443, and, as the last rule of theINPUTchain, reject other incoming traffic with an Internet Control Message Protocol (ICMP) port unreachable message:nft add rule inet nftables_svc INPUT tcp dport 22 accept nft add rule inet nftables_svc INPUT tcp dport 443 accept nft add rule inet nftables_svc INPUT reject with icmpx type port-unreachable
# nft add rule inet nftables_svc INPUT tcp dport 22 accept # nft add rule inet nftables_svc INPUT tcp dport 443 accept # nft add rule inet nftables_svc INPUT reject with icmpx type port-unreachableCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you enter the
nft add rulecommands as shown,nftadds the rules in the same order to the chain as you run the commands.Display the current rule set including handles:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Insert a rule before the existing rule with handle 3. For example, to insert a rule that allows TCP traffic on port 636, enter:
nft insert rule inet nftables_svc INPUT position 3 tcp dport 636 accept
# nft insert rule inet nftables_svc INPUT position 3 tcp dport 636 acceptCopy to Clipboard Copied! Toggle word wrap Toggle overflow Append a rule after the existing rule with handle 3. For example, to insert a rule that allows TCP traffic on port 80, enter:
nft add rule inet nftables_svc INPUT position 3 tcp dport 80 accept
# nft add rule inet nftables_svc INPUT position 3 tcp dport 80 acceptCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the rule set again with handles. Verify that the later added rules have been added to the specified positions:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the rule with handle 6:
nft delete rule inet nftables_svc INPUT handle 6
# nft delete rule inet nftables_svc INPUT handle 6Copy to Clipboard Copied! Toggle word wrap Toggle overflow To remove a rule, you must specify the handle.
Display the rule set, and verify that the removed rule is no longer present:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove all remaining rules from the
INPUTchain:nft flush chain inet nftables_svc INPUT
# nft flush chain inet nftables_svc INPUTCopy to Clipboard Copied! Toggle word wrap Toggle overflow Display the rule set, and verify that the
INPUTchain is empty:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Delete the
INPUTchain:nft delete chain inet nftables_svc INPUT
# nft delete chain inet nftables_svc INPUTCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can also use this command to delete chains that still contain rules.
Display the rule set, and verify that the
INPUTchain has been deleted:nft list table inet nftables_svc table inet nftables_svc { }# nft list table inet nftables_svc table inet nftables_svc { }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Delete the
nftables_svctable:nft delete table inet nftables_svc
# nft delete table inet nftables_svcCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can also use this command to delete tables that still contain chains.
NoteTo delete the entire rule set, use the
nft flush rulesetcommand instead of manually deleting all rules, chains, and tables in separate commands.
8.2. Migrating from iptables to nftables
If your firewall configuration still uses iptables rules, you can migrate your iptables rules to nftables.
8.2.1. When to use firewalld, nftables, or iptables
On RHEL 8, you can use the following packet-filtering utilities depending on your scenario:
-
firewalld: Thefirewalldutility simplifies firewall configuration for common use cases. -
nftables: Use thenftablesutility to set up complex and performance-critical firewalls, such as for a whole network. -
iptables: Theiptablesutility on Red Hat Enterprise Linux uses thenf_tableskernel API instead of thelegacyback end. Thenf_tablesAPI provides backward compatibility so that scripts that useiptablescommands still work on Red Hat Enterprise Linux. For new firewall scripts, usenftables.
To prevent the different firewall-related services (firewalld, nftables, or iptables) from influencing each other, run only one of them on a RHEL host, and disable the other services.
8.2.2. Concepts in the nftables framework
The nftables framework is a modern, efficient, and flexible alternative to iptables. It simplifies rule management and enhances performance, making it a better choice for complex, high-performance network environments.
- Tables and namespaces
-
In
nftables, tables represent organizational units or namespaces that group together related firewall chains, sets, flowtables, and other objects. Innftables, tables provide a more flexible way to structure firewall rules and related components. While iniptables, the tables were more rigidly defined with specific purposes. - Table families
-
Each table in
nftablesis associated with a specific family (ip,ip6,inet,arp,bridge, ornetdev). This association determines which packets the table can process. For example, a table in theipfamily handles only IPv4 packets. On the other hand,inetis a special case of table family. It offers a unified approach across protocols, because it can process both IPv4 and IPv6 packets. Another case of a special table family isnetdev, because it is used for rules that apply directly to network devices, enabling filtering at the device level. - Base chains
Base chains in
nftablesare highly configurable entry-points in the packet processing pipeline that enable users to specify the following:- Type of chain, for example, "filter"
- The hook point in the packet processing path, for example, "input", "output", "forward"
- Priority of the chain
This flexibility enables precise control over when and how the rules are applied to packets as they pass through the network stack. A special case of a chain is the
routechain, which is used to influence the routing decisions made by the kernel, based on packet headers.- Virtual machine for rule processing
The
nftablesframework uses an internal virtual machine to process rules. This virtual machine executes instructions that are similar to assembly language operations (loading data into registers, performing comparisons, and so on). Such a mechanism allows for highly flexible and efficient rule processing.Enhancements in
nftablescan be introduced as new instructions for that virtual machine. This typically requires a new kernel module and updates to thelibnftnllibrary and thenftcommand-line utility.Alternatively, you can introduce new features by combining existing instructions in innovative ways without a need for kernel modifications. The syntax of
nftablesrules reflects the flexibility of the underlying virtual machine. For example, the rulemeta mark set tcp dport map { 22: 1, 80: 2 }sets a packet’s firewall mark to 1 if the TCP destination port is 22, and to 2 if the port is 80. This demonstrates how complex logic can be expressed concisely.- Complex filtering and verdict maps
The
nftablesframework integrates and extends the functionality of theipsetutility, which is used iniptablesfor bulk matching on IP addresses, ports, other data types and, most importantly, combinations thereof. This integration makes it easier to manage large and dynamic sets of data directly withinnftables. Next,nftablesnatively supports matching packets based on multiple values or ranges for any data type, which enhances its capability to handle complex filtering requirements. Withnftablesyou can manipulate any field within a packet.In
nftables, sets can be either named or anonymous. The named sets can be referenced by multiple rules and modified dynamically. The anonymous sets are defined inline within a rule and are immutable. Sets can contain elements that are combinations of different types, for example IP address and port number pairs. This feature provides greater flexibility in matching complex criteria. To manage sets, the kernel can select the most appropriate backend based on the specific requirements (performance, memory efficiency, and others). Sets can also function as maps with key-value pairs. The value part can be used as data points (values to write into packet headers), or as verdicts or chains to jump to. This enables complex and dynamic rule behaviors, known as "verdict maps".- Flexible rule format
The structure of
nftablesrules is straightforward. The conditions and actions are applied sequentially from left to right. This intuitive format simplifies rule creating and troubleshooting.Conditions in a rule are logically connected (with the AND operator) together, which means that all conditions must be evaluated as "true" for the rule to match. If any condition fails, the evaluation moves to the next rule.
Actions in
nftablescan be final, such asdroporaccept, which stop further rule processing for the packet. Non-terminal actions, such ascounter log meta mark set 0x3, perform specific tasks (counting packets, logging, setting a mark, and others), but allow subsequent rules to be evaluated.
8.2.3. Concepts in the deprecated iptables framework
Similar to the actively-maintained nftables framework, the deprecated iptables framework enables you to perform a variety of packet filtering tasks, logging and auditing, NAT-related configuration tasks, and more.
The iptables framework is structured into multiple tables, where each table is designed for a specific purpose:
filter- The default table, ensures general packet filtering
nat- For Network Address Translation (NAT), includes altering the source and destination addresses of packets
mangle- For specific packet alteration, enables you to do modification of packet headers for advanced routing decisions
raw- For configurations that need to happen before connection tracking
These tables are implemented as separate kernel modules, where each table offers a fixed set of builtin chains such as INPUT, OUTPUT, and FORWARD. A chain is a sequence of rules that packets are evaluated against. These chains hook into specific points in the packet processing flow in the kernel. The chains have the same names across different tables, however their order of execution is determined by their respective hook priorities. The priorities are managed internally by the kernel to make sure that the rules are applied in the correct sequence.
Originally, iptables was designed to process IPv4 traffic. However, with the inception of the IPv6 protocol, the ip6tables utility needed to be introduced to provide comparable functionality (as iptables) and enable users to create and manage firewall rules for IPv6 packets. With the same logic, the arptables utility was created to process Address Resolution Protocol (ARP) and the ebtables utility was developed to handle Ethernet bridging frames. These tools ensure that you can apply the packet filtering abilities of iptables across various network protocols and provide comprehensive network coverage.
To enhance the functionality of iptables, the extensions started to be developed. The functionality extensions are typically implemented as kernel modules that are paired with user-space dynamic shared objects (DSOs). The extensions introduce "matches" and "targets" that you can use in firewall rules to perform more sophisticated operations. Extensions can enable complex matches and targets. For instance you can match on, or manipulate specific layer 4 protocol header values, perform rate-limiting, enforce quotas, and so on. Some extensions are designed to address limitations in the default iptables syntax, for example the "multiport" match extension. This extension allows a single rule to match multiple, non-consecutive ports to simplify rule definitions, and thereby reducing the number of individual rules required.
An ipset is a special kind of functionality extension to iptables. It is a kernel-level data structure that is used together with iptables to create collections of IP addresses, port numbers, and other network-related elements that you can match against packets. These sets significantly streamline, optimize, and accelerate the process of writing and managing firewall rules.
8.2.4. Converting iptables and ip6tables rule sets to nftables
Use the iptables-restore-translate and ip6tables-restore-translate utilities to translate iptables and ip6tables rule sets to nftables.
Prerequisites
-
The
nftablesandiptablespackages are installed. -
The system has
iptablesandip6tablesrules configured.
Procedure
Write the
iptablesandip6tablesrules to a file:iptables-save >/root/iptables.dump ip6tables-save >/root/ip6tables.dump
# iptables-save >/root/iptables.dump # ip6tables-save >/root/ip6tables.dumpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Convert the dump files to
nftablesinstructions:iptables-restore-translate -f /root/iptables.dump > /etc/nftables/ruleset-migrated-from-iptables.nft ip6tables-restore-translate -f /root/ip6tables.dump > /etc/nftables/ruleset-migrated-from-ip6tables.nft
# iptables-restore-translate -f /root/iptables.dump > /etc/nftables/ruleset-migrated-from-iptables.nft # ip6tables-restore-translate -f /root/ip6tables.dump > /etc/nftables/ruleset-migrated-from-ip6tables.nftCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Review and, if needed, manually update the generated
nftablesrules. To enable the
nftablesservice to load the generated files, add the following to the/etc/sysconfig/nftables.conffile:include "/etc/nftables/ruleset-migrated-from-iptables.nft" include "/etc/nftables/ruleset-migrated-from-ip6tables.nft"
include "/etc/nftables/ruleset-migrated-from-iptables.nft" include "/etc/nftables/ruleset-migrated-from-ip6tables.nft"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Stop and disable the
iptablesservice:systemctl disable --now iptables
# systemctl disable --now iptablesCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you used a custom script to load the
iptablesrules, ensure that the script no longer starts automatically and reboot to flush all tables.Enable and start the
nftablesservice:systemctl enable --now nftables
# systemctl enable --now nftablesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the
nftablesrule set:nft list ruleset
# nft list rulesetCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.2.5. Converting single iptables and ip6tables rules to nftables
Red Hat Enterprise Linux provides the iptables-translate and ip6tables-translate utilities to convert an iptables or ip6tables rule into the equivalent one for nftables.
Prerequisites
-
The
nftablespackage is installed.
Procedure
Use the
iptables-translateorip6tables-translateutility instead ofiptablesorip6tablesto display the correspondingnftablesrule, for example:iptables-translate -A INPUT -s 192.0.2.0/24 -j ACCEPT nft add rule ip filter INPUT ip saddr 192.0.2.0/24 counter accept
# iptables-translate -A INPUT -s 192.0.2.0/24 -j ACCEPT nft add rule ip filter INPUT ip saddr 192.0.2.0/24 counter acceptCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that some extensions lack translation support. In these cases, the utility prints the untranslated rule prefixed with the
#sign, for example:iptables-translate -A INPUT -j CHECKSUM --checksum-fill nft # -A INPUT -j CHECKSUM --checksum-fill
# iptables-translate -A INPUT -j CHECKSUM --checksum-fill nft # -A INPUT -j CHECKSUM --checksum-fillCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.2.6. Comparison of common iptables and nftables commands
The following is a comparison of common iptables and nftables commands.
Listing all rules:
Expand iptables nftables iptables-savenft list rulesetListing a certain table and chain:
Expand iptables nftables iptables -Lnft list table ip filteriptables -L INPUTnft list chain ip filter INPUTiptables -t nat -L PREROUTINGnft list chain ip nat PREROUTINGThe
nftcommand does not pre-create tables and chains. They exist only if a user created them manually.Listing rules generated by firewalld:
nft list table inet firewalld nft list table ip firewalld nft list table ip6 firewalld
# nft list table inet firewalld # nft list table ip firewalld # nft list table ip6 firewalldCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.3. Configuring NAT using nftables
With nftables, you can configure the masquerading, source (SNAT), destination NAT (DNAT), and redirect types. With NAT, you can modify the source or destination IP address.
You can only use real interface names in iifname and oifname parameters, and alternative names (altname) are not supported.
8.3.1. NAT types
The nftables framework supports different network address translation (NAT) types.
- Masquerading and source NAT (SNAT)
Use one of these NAT types to change the source IP address of packets. For example, Internet Service Providers (ISPs) do not route private IP ranges, such as
10.0.0.0/8. If you use private IP ranges in your network and users should be able to reach servers on the internet, map the source IP address of packets from these ranges to a public IP address.Masquerading and SNAT are very similar to one another. The differences are:
- Masquerading automatically uses the IP address of the outgoing interface. Therefore, use masquerading if the outgoing interface uses a dynamic IP address.
- SNAT sets the source IP address of packets to a specified IP and does not dynamically look up the IP of the outgoing interface. Therefore, SNAT is faster than masquerading. Use SNAT if the outgoing interface uses a fixed IP address.
- Destination NAT (DNAT)
- Use this NAT type to rewrite the destination address and port of incoming packets. For example, if your web server uses an IP address from a private IP range and is, therefore, not directly accessible from the internet, you can set a DNAT rule on the router to redirect incoming traffic to this server.
- Redirect
- This type is a special case of DNAT that redirects packets to the local machine depending on the chain hook. For example, if a service runs on a different port than its standard port, you can redirect incoming traffic from the standard port to this specific port.
8.3.2. Configuring masquerading using nftables
Masquerading enables a router to dynamically change the source IP of packets sent through an interface to the IP address of the interface. This means that if the interface gets a new IP assigned, nftables automatically uses the new IP when replacing the source IP.
Replace the source IP of packets leaving the host through the ens3 interface to the IP set on ens3.
Procedure
Create a table:
nft add table nat
# nft add table natCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
preroutingandpostroutingchains to the table:nft add chain nat postrouting { type nat hook postrouting priority 100 \; }# nft add chain nat postrouting { type nat hook postrouting priority 100 \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantEven if you do not add a rule to the
preroutingchain, thenftablesframework requires this chain to match incoming packet replies.Note that you must pass the
--option to thenftcommand to prevent the shell from interpreting the negative priority value as an option of thenftcommand.Add a rule to the
postroutingchain that matches outgoing packets on theens3interface:nft add rule nat postrouting oifname "ens3" masquerade
# nft add rule nat postrouting oifname "ens3" masqueradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.3.3. Configuring source NAT using nftables
On a router, Source NAT (SNAT) enables you to change the IP of packets sent through an interface to a specific IP address. The router then replaces the source IP of outgoing packets.
Procedure
Create a table:
nft add table nat
# nft add table natCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
preroutingandpostroutingchains to the table:nft add chain nat postrouting { type nat hook postrouting priority 100 \; }# nft add chain nat postrouting { type nat hook postrouting priority 100 \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantEven if you do not add a rule to the
postroutingchain, thenftablesframework requires this chain to match outgoing packet replies.Note that you must pass the
--option to thenftcommand to prevent the shell from interpreting the negative priority value as an option of thenftcommand.Add a rule to the
postroutingchain that replaces the source IP of outgoing packets throughens3with192.0.2.1:nft add rule nat postrouting oifname "ens3" snat to 192.0.2.1
# nft add rule nat postrouting oifname "ens3" snat to 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.3.4. Configuring destination NAT using nftables
Destination NAT (DNAT) enables you to redirect traffic on a router to a host that is not directly accessible from the internet.
For example, with DNAT the router redirects incoming traffic sent to port 80 and 443 to a web server with the IP address 192.0.2.1.
Procedure
Create a table:
nft add table nat
# nft add table natCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
preroutingandpostroutingchains to the table:nft -- add chain nat prerouting { type nat hook prerouting priority -100 \; } nft add chain nat postrouting { type nat hook postrouting priority 100 \; }# nft -- add chain nat prerouting { type nat hook prerouting priority -100 \; } # nft add chain nat postrouting { type nat hook postrouting priority 100 \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantEven if you do not add a rule to the
postroutingchain, thenftablesframework requires this chain to match outgoing packet replies.Note that you must pass the
--option to thenftcommand to prevent the shell from interpreting the negative priority value as an option of thenftcommand.Add a rule to the
preroutingchain that redirects incoming traffic to port80and443on theens3interface of the router to the web server with the IP address192.0.2.1:nft add rule nat prerouting iifname ens3 tcp dport { 80, 443 } dnat to 192.0.2.1# nft add rule nat prerouting iifname ens3 tcp dport { 80, 443 } dnat to 192.0.2.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow Depending on your environment, add either a SNAT or masquerading rule to change the source address for packets returning from the web server to the sender:
If the
ens3interface uses a dynamic IP addresses, add a masquerading rule:nft add rule nat postrouting oifname "ens3" masquerade
# nft add rule nat postrouting oifname "ens3" masqueradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the
ens3interface uses a static IP address, add a SNAT rule. For example, if theens3uses the198.51.100.1IP address:nft add rule nat postrouting oifname "ens3" snat to 198.51.100.1
# nft add rule nat postrouting oifname "ens3" snat to 198.51.100.1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Enable packet forwarding:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.3.5. Configuring a redirect using nftables
The redirect feature is a special case of destination network address translation (DNAT) that redirects packets to the local machine depending on the chain hook.
For example, you can redirect incoming and forwarded traffic sent to port 22 of the local host to port 2222.
Procedure
Create a table:
nft add table nat
# nft add table natCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
preroutingchain to the table:nft -- add chain nat prerouting { type nat hook prerouting priority -100 \; }# nft -- add chain nat prerouting { type nat hook prerouting priority -100 \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that you must pass the
--option to thenftcommand to prevent the shell from interpreting the negative priority value as an option of thenftcommand.Add a rule to the
preroutingchain that redirects incoming traffic on port22to port2222:nft add rule nat prerouting tcp dport 22 redirect to 2222
# nft add rule nat prerouting tcp dport 22 redirect to 2222Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.4. Writing and executing nftables scripts
The major benefit of using the nftables framework is that the execution of scripts is atomic. This means that the system either applies the whole script or prevents the execution if an error occurs. This guarantees that the firewall is always in a consistent state.
Additionally, with the nftables script environment, you can:
- Add comments
- Define variables
- Include other rule-set files
When you install the nftables package, Red Hat Enterprise Linux automatically creates *.nft scripts in the /etc/nftables/ directory. These scripts contain commands that create tables and empty chains for different purposes.
8.4.1. Supported nftables script formats
The nftables framework supports scripts in different formats.
You can use the following formats:
The same format as the
nft list rulesetcommand displays the rule set:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The same syntax as for
nftcommands:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.4.2. Running nftables scripts
You can run an nftables script either by passing it to the nft utility or by executing the script directly.
Procedure
To run an
nftablesscript by passing it to thenftutility, enter:nft -f /etc/nftables/<example_firewall_script>.nft
# nft -f /etc/nftables/<example_firewall_script>.nftCopy to Clipboard Copied! Toggle word wrap Toggle overflow To run an
nftablesscript directly:For the single time that you perform this:
Ensure that the script starts with the following shebang sequence:
#!/usr/sbin/nft -f
#!/usr/sbin/nft -fCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you omit the
-fparameter, thenftutility does not read the script and displays:Error: syntax error, unexpected newline, expecting string.Optional: Set the owner of the script to
root:chown root /etc/nftables/<example_firewall_script>.nft
# chown root /etc/nftables/<example_firewall_script>.nftCopy to Clipboard Copied! Toggle word wrap Toggle overflow Make the script executable for the owner:
chmod u+x /etc/nftables/<example_firewall_script>.nft
# chmod u+x /etc/nftables/<example_firewall_script>.nftCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Run the script:
/etc/nftables/<example_firewall_script>.nft
# /etc/nftables/<example_firewall_script>.nftCopy to Clipboard Copied! Toggle word wrap Toggle overflow If no output is displayed, the system executed the script successfully.
ImportantEven if
nftexecutes the script successfully, incorrectly placed rules, missing parameters, or other problems in the script can cause that the firewall behaves not as expected.
8.4.3. Using comments in nftables scripts
The nftables scripting environment interprets everything to the right of a # character to the end of a line as a comment.
Comments can start at the beginning of a line, or next to a command:
8.4.4. Using variables in nftables script
To define a variable in an nftables script, use the define keyword. You can store single values and anonymous sets in a variable. For more complex scenarios, use sets or verdict maps.
- Variables with a single value
The following example defines a variable named
INET_DEVwith the valueenp1s0:define INET_DEV = enp1s0
define INET_DEV = enp1s0Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can use the variable in the script by entering the
$sign followed by the variable name:... add rule inet example_table example_chain iifname $INET_DEV tcp dport ssh accept ...
... add rule inet example_table example_chain iifname $INET_DEV tcp dport ssh accept ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Variables that contain an anonymous set
The following example defines a variable that contains an anonymous set:
define DNS_SERVERS = { 192.0.2.1, 192.0.2.2 }define DNS_SERVERS = { 192.0.2.1, 192.0.2.2 }Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can use the variable in the script by writing the
$sign followed by the variable name:add rule inet example_table example_chain ip daddr $DNS_SERVERS accept
add rule inet example_table example_chain ip daddr $DNS_SERVERS acceptCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteCurly braces have special semantics when you use them in a rule because they indicate that the variable represents a set.
8.4.5. Including files in nftables scripts
In the nftables scripting environment, you can include other scripts by using the include statement.
If you specify only a file name without an absolute or relative path, nftables includes files from the default search path, which is set to /etc on Red Hat Enterprise Linux.
Example 8.1. Including files from the default search directory
To include a file from the default search directory:
include "example.nft"
include "example.nft"Example 8.2. Including all *.nft files from a directory
To include all files ending with *.nft that are stored in the /etc/nftables/rulesets/ directory:
include "/etc/nftables/rulesets/*.nft"
include "/etc/nftables/rulesets/*.nft"
Note that the include statement does not match files beginning with a dot.
8.4.6. Automatically loading nftables rules when the system boots
The nftables systemd service loads firewall scripts that are included in the /etc/sysconfig/nftables.conf file.
Prerequisites
-
The
nftablesscripts are stored in the/etc/nftables/directory.
Procedure
Edit the
/etc/sysconfig/nftables.conffile.-
If you modified the
*.nftscripts that were created in/etc/nftables/with the installation of thenftablespackage, uncomment theincludestatement for these scripts. If you wrote new scripts, add
includestatements to include these scripts. For example, to load the/etc/nftables/example.nftscript when thenftablesservice starts, add:include "/etc/nftables/_example_.nft"
include "/etc/nftables/_example_.nft"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
-
If you modified the
Optional: Start the
nftablesservice to load the firewall rules without rebooting the system:systemctl start nftables
# systemctl start nftablesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
nftablesservice.systemctl enable nftables
# systemctl enable nftablesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.5. Using sets in nftables commands
The nftables framework natively supports sets. You can use sets, for example, if a rule should match multiple IP addresses, port numbers, interfaces, or any other match criteria.
8.5.1. Using anonymous sets in nftables
An anonymous set contains comma-separated values enclosed in curly brackets, such as { 22, 80, 443 }, that you use directly in a rule. You can use anonymous sets also for IP addresses and any other match criteria.
The drawback of anonymous sets is that if you want to change the set, you must replace the rule. For a dynamic solution, use named sets as described in Using named sets in nftables.
Prerequisites
-
The
example_chainchain and theexample_tabletable in theinetfamily exist.
Procedure
For example, to add a rule to
example_chaininexample_tablethat allows incoming traffic to port22,80, and443:nft add rule inet example_table example_chain tcp dport { 22, 80, 443 } accept# nft add rule inet example_table example_chain tcp dport { 22, 80, 443 } acceptCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Display all chains and their rules in
example_table:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.5.2. Using named sets in nftables
The nftables framework supports mutable named sets. A named set is a list of ranges that you can use in multiple rules within a table. Another benefit over anonymous sets is that you can update a named set without replacing the rules that use the set.
When you create a named set, you must specify the type of elements the set contains. You can set the following types:
-
ipv4_addrfor a set that contains IPv4 addresses or ranges, such as192.0.2.1or192.0.2.0/24. -
ipv6_addrfor a set that contains IPv6 addresses or ranges, such as2001:db8:1::1or2001:db8:1::1/64. -
ether_addrfor a set that contains a list of media access control (MAC) addresses, such as52:54:00:6b:66:42. -
inet_protofor a set that contains a list of internet protocol types, such astcp. -
inet_servicefor a set that contains a list of internet services, such asssh. -
markfor a set that contains a list of packet marks. Packet marks can be any positive 32-bit integer value (0to2147483647).
Prerequisites
-
The
example_chainchain and theexample_tabletable exists.
Procedure
Create an empty set. The following examples create a set for IPv4 addresses:
To create a set that can store multiple individual IPv4 addresses:
nft add set inet example_table example_set { type ipv4_addr \; }# nft add set inet example_table example_set { type ipv4_addr \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow To create a set that can store IPv4 address ranges:
nft add set inet example_table example_set { type ipv4_addr \; flags interval \; }# nft add set inet example_table example_set { type ipv4_addr \; flags interval \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow
ImportantTo prevent the shell from interpreting the semicolons as the end of the command, you must escape the semicolons with a backslash.
Optional: Create rules that use the set. For example, the following command adds a rule to the
example_chainin theexample_tablethat will drop all packets from IPv4 addresses inexample_set.nft add rule inet example_table example_chain ip saddr @example_set drop
# nft add rule inet example_table example_chain ip saddr @example_set dropCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because
example_setis still empty, the rule has currently no effect.Add IPv4 addresses to
example_set:If you create a set that stores individual IPv4 addresses, enter:
nft add element inet example_table example_set { 192.0.2.1, 192.0.2.2 }# nft add element inet example_table example_set { 192.0.2.1, 192.0.2.2 }Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you create a set that stores IPv4 ranges, enter:
nft add element inet example_table example_set { 192.0.2.0-192.0.2.255 }# nft add element inet example_table example_set { 192.0.2.0-192.0.2.255 }Copy to Clipboard Copied! Toggle word wrap Toggle overflow When you specify an IP address range, you can alternatively use the Classless Inter-Domain Routing (CIDR) notation, such as
192.0.2.0/24in the above example.
8.5.3. Using dynamic sets to add entries from the packet path
Dynamic sets in nftables automatically add elements, such as IP addresses, ports, and MAC addresses from packet data. This enables real-time collection of data to create dynamic deny or ban lists, instantly reacting to security threats.
Prerequisites
-
The
example_chainchain and theexample_tabletable in theinetfamily exist.
Procedure
Create an empty set. The following examples create a set for IPv4 addresses:
To create a set that can store multiple individual IPv4 addresses:
nft add set inet example_table example_set { type ipv4_addr \; }# nft add set inet example_table example_set { type ipv4_addr \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow To create a set that can store IPv4 address ranges:
nft add set inet example_table example_set { type ipv4_addr \; flags interval \; }# nft add set inet example_table example_set { type ipv4_addr \; flags interval \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantTo prevent the shell from interpreting the semicolons as the end of the command, you must escape the semicolons with a backslash.
Create a rule for dynamically adding the source IPv4 addresses of incoming packets to the
example_setset:nft add rule inet example_table example_chain set add ip saddr @example_set
# nft add rule inet example_table example_chain set add ip saddr @example_setCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command creates a new rule within the
example_chainrule chain and theexample_tableto dynamically add the source IPv4 address of the packet to theexample_set.
Verification
Ensure the rule was added:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command displays the entire ruleset currently loaded in
nftables. It shows that IPs are actively triggering the rule, andexample_setis being updated with the relevant addresses.
Next steps
Once you have a dynamic set of IPs, you can use it for various security, filtering, and traffic control purposes. For example:
- block, limit, or log network traffic
- combine with allow-listing to avoid banning trusted users
- use automatic timeouts to prevent over-blocking
8.6. Using verdict maps in nftables commands
Verdict maps, which are also known as dictionaries, enable nft to perform an action based on packet information by mapping match criteria to an action.
8.6.1. Using anonymous maps in nftables
An anonymous map is a { match_criteria : action } statement that you use directly in a rule. The statement can contain multiple comma-separated mappings.
The drawback of an anonymous map is that if you want to change the map, you must replace the rule. For a dynamic solution, use named maps as described in Using named maps in nftables.
For example, you can use an anonymous map to route both TCP and UDP packets of the IPv4 and IPv6 protocol to different chains to count incoming TCP and UDP packets separately.
Procedure
Create a new table:
nft add table inet example_table
# nft add table inet example_tableCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
tcp_packetschain inexample_table:nft add chain inet example_table tcp_packets
# nft add chain inet example_table tcp_packetsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a rule to
tcp_packetsthat counts the traffic in this chain:nft add rule inet example_table tcp_packets counter
# nft add rule inet example_table tcp_packets counterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
udp_packetschain inexample_tablenft add chain inet example_table udp_packets
# nft add chain inet example_table udp_packetsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add a rule to
udp_packetsthat counts the traffic in this chain:nft add rule inet example_table udp_packets counter
# nft add rule inet example_table udp_packets counterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a chain for incoming traffic. For example, to create a chain named
incoming_trafficinexample_tablethat filters incoming traffic:nft add chain inet example_table incoming_traffic { type filter hook input priority 0 \; }# nft add chain inet example_table incoming_traffic { type filter hook input priority 0 \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add a rule with an anonymous map to
incoming_traffic:nft add rule inet example_table incoming_traffic ip protocol vmap { tcp : jump tcp_packets, udp : jump udp_packets }# nft add rule inet example_table incoming_traffic ip protocol vmap { tcp : jump tcp_packets, udp : jump udp_packets }Copy to Clipboard Copied! Toggle word wrap Toggle overflow The anonymous map distinguishes the packets and sends them to the different counter chains based on their protocol.
To list the traffic counters, display
example_table:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The counters in the
tcp_packetsandudp_packetschain display both the number of received packets and bytes.
8.6.2. Using named maps in nftables
The nftables framework supports named maps. You can use these maps in multiple rules within a table. Another benefit over anonymous maps is that you can update a named map without replacing the rules that use it.
When you create a named map, you must specify the type of elements:
-
ipv4_addrfor a map whose match part contains an IPv4 address, such as192.0.2.1. -
ipv6_addrfor a map whose match part contains an IPv6 address, such as2001:db8:1::1. -
ether_addrfor a map whose match part contains a media access control (MAC) address, such as52:54:00:6b:66:42. -
inet_protofor a map whose match part contains an internet protocol type, such astcp. -
inet_servicefor a map whose match part contains an internet services name port number, such assshor22. -
markfor a map whose match part contains a packet mark. A packet mark can be any positive 32-bit integer value (0to2147483647). -
counterfor a map whose match part contains a counter value. The counter value can be any positive 64-bit integer value. -
quotafor a map whose match part contains a quota value. The quota value can be any positive 64-bit integer value.
For example, you can allow or drop incoming packets based on their source IP address. Using a named map, you require only a single rule to configure this scenario while the IP addresses and actions are dynamically stored in the map.
Procedure
Create a table. For example, to create a table named
example_tablethat processes IPv4 packets:nft add table ip example_table
# nft add table ip example_tableCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a chain. For example, to create a chain named
example_chaininexample_table:nft add chain ip example_table example_chain { type filter hook input priority 0 \; }# nft add chain ip example_table example_chain { type filter hook input priority 0 \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantTo prevent the shell from interpreting the semicolons as the end of the command, you must escape the semicolons with a backslash.
Create an empty map. For example, to create a map for IPv4 addresses:
nft add map ip example_table example_map { type ipv4_addr : verdict \; }# nft add map ip example_table example_map { type ipv4_addr : verdict \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create rules that use the map. For example, the following command adds a rule to
example_chaininexample_tablethat applies actions to IPv4 addresses which are both defined inexample_map:nft add rule example_table example_chain ip saddr vmap @example_map
# nft add rule example_table example_chain ip saddr vmap @example_mapCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add IPv4 addresses and corresponding actions to
example_map:nft add element ip example_table example_map { 192.0.2.1 : accept, 192.0.2.2 : drop }# nft add element ip example_table example_map { 192.0.2.1 : accept, 192.0.2.2 : drop }Copy to Clipboard Copied! Toggle word wrap Toggle overflow This example defines the mappings of IPv4 addresses to actions. In combination with the rule created above, the firewall accepts packets from
192.0.2.1and drops packets from192.0.2.2.Optional: Enhance the map by adding another IP address and action statement:
nft add element ip example_table example_map { 192.0.2.3 : accept }# nft add element ip example_table example_map { 192.0.2.3 : accept }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Remove an entry from the map:
nft delete element ip example_table example_map { 192.0.2.1 }# nft delete element ip example_table example_map { 192.0.2.1 }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Display the rule set:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.7. Example: Protecting a LAN and DMZ using an nftables script
Use the nftables framework on a RHEL router to write and install a firewall script that protects the network clients in an internal LAN and a web server in a DMZ from unauthorized access from the internet and from other networks.
This example is only for demonstration purposes and describes a scenario with specific requirements.
Firewall scripts highly depend on the network infrastructure and security requirements. Use this example to learn the concepts of nftables firewalls when you write scripts for your own environment.
8.7.1. Network conditions
The network in this example has the following conditions.
The router is connected to the following networks:
-
The internet through interface
enp1s0 -
The internal LAN through interface
enp7s0 -
The DMZ through
enp8s0
-
The internet through interface
-
The internet interface of the router has both a static IPv4 address (
203.0.113.1) and IPv6 address (2001:db8:a::1) assigned. -
The clients in the internal LAN use only private IPv4 addresses from the range
10.0.0.0/24. Consequently, traffic from the LAN to the internet requires source network address translation (SNAT). -
The administrator PCs in the internal LAN use the IP addresses
10.0.0.100and10.0.0.200. -
The DMZ uses public IP addresses from the ranges
198.51.100.0/24and2001:db8:b::/56. -
The web server in the DMZ uses the IP addresses
198.51.100.5and2001:db8:b::5. - The router acts as a caching DNS server for hosts in the LAN and DMZ.
8.7.2. Security requirements to the firewall script
The following are the requirements to the nftables firewall in the example network.
The router must be able to:
- Recursively resolve DNS queries.
- Perform all connections on the loopback interface.
Clients in the internal LAN must be able to:
- Query the caching DNS server running on the router.
- Access the HTTPS server in the DMZ.
- Access any HTTPS server on the internet.
- The PCs of the administrators must be able to access the router and every server in the DMZ using SSH.
The web server in the DMZ must be able to:
- Query the caching DNS server running on the router.
- Access HTTPS servers on the internet to download updates.
Hosts on the internet must be able to:
- Access the HTTPS servers in the DMZ.
Additionally, the following security requirements exists:
- Connection attempts that are not explicitly allowed should be dropped.
- Dropped packets should be logged.
8.7.3. Configuring logging of dropped packets to a file
By default, systemd logs kernel messages, such as for dropped packets, to the journal. Additionally, you can configure the rsyslog service to log such entries to a separate file. To ensure that the log file does not grow infinitely, configure a rotation policy.
Prerequisites
-
The
rsyslogpackage is installed. -
The
rsyslogservice is running.
Procedure
Create the
/etc/rsyslog.d/nftables.conffile with the following content::msg, startswith, "nft drop" -/var/log/nftables.log & stop
:msg, startswith, "nft drop" -/var/log/nftables.log & stopCopy to Clipboard Copied! Toggle word wrap Toggle overflow Using this configuration, the
rsyslogservice logs dropped packets to the/var/log/nftables.logfile instead of/var/log/messages.Restart the
rsyslogservice:systemctl restart rsyslog
# systemctl restart rsyslogCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
/etc/logrotate.d/nftablesfile with the following content to rotate/var/log/nftables.logif the size exceeds 10 MB:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
maxage 30setting defines thatlogrotateremoves rotated logs older than 30 days during the next rotation operation.
8.7.4. Writing and activating the nftables script
This example is an nftables firewall script that runs on a RHEL router and protects the clients in an internal LAN and a web server in a DMZ.
For details about the network and the requirements for the firewall used in the example, see Network conditions and Security requirements to the firewall script.
This nftables firewall script is only for demonstration purposes. Do not use it without adapting it to your environments and security requirements.
Prerequisites
- The network is configured as described in Network conditions.
Procedure
Create the
/etc/nftables/firewall.nftscript with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Include the
/etc/nftables/firewall.nftscript in the/etc/sysconfig/nftables.conffile:include "/etc/nftables/firewall.nft"
include "/etc/nftables/firewall.nft"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable IPv4 forwarding:
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf sysctl -p /etc/sysctl.d/95-IPv4-forwarding.conf
# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/95-IPv4-forwarding.conf # sysctl -p /etc/sysctl.d/95-IPv4-forwarding.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable and start the
nftablesservice:systemctl enable --now nftables
# systemctl enable --now nftablesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Optional: Verify the
nftablesrule set:nft list ruleset ...
# nft list ruleset ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Try to perform an access that the firewall prevents. For example, try to access the router using SSH from the DMZ:
ssh router.example.com ssh: connect to host router.example.com port 22: Network is unreachable
# ssh router.example.com ssh: connect to host router.example.com port 22: Network is unreachableCopy to Clipboard Copied! Toggle word wrap Toggle overflow Depending on your logging settings, search:
The
systemdjournal for the blocked packets:journalctl -k -g "nft drop" Oct 14 17:27:18 router kernel: nft drop IN : IN=enp8s0 OUT= MAC=... SRC=198.51.100.5 DST=198.51.100.1 ... PROTO=TCP SPT=40464 DPT=22 ... SYN ...
# journalctl -k -g "nft drop" Oct 14 17:27:18 router kernel: nft drop IN : IN=enp8s0 OUT= MAC=... SRC=198.51.100.5 DST=198.51.100.1 ... PROTO=TCP SPT=40464 DPT=22 ... SYN ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
/var/log/nftables.logfile for the blocked packets:Oct 14 17:27:18 router kernel: nft drop IN : IN=enp8s0 OUT= MAC=... SRC=198.51.100.5 DST=198.51.100.1 ... PROTO=TCP SPT=40464 DPT=22 ... SYN ...
Oct 14 17:27:18 router kernel: nft drop IN : IN=enp8s0 OUT= MAC=... SRC=198.51.100.5 DST=198.51.100.1 ... PROTO=TCP SPT=40464 DPT=22 ... SYN ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.8. Using nftables to limit the amount of connections
You can use nftables to limit the number of connections or to block IP addresses that attempt to establish a given amount of connections to prevent them from using too many system resources.
8.8.1. Limiting the number of connections by using nftables
By using the ct count parameter of the nft utility, you can limit the number of simultaneous connections per IP address. For example, you can use this feature to configure that each source IP address can only establish two parallel SSH connections to a host.
Procedure
Create the
filtertable with theinetaddress family:nft add table inet filter
# nft add table inet filterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
inputchain to theinet filtertable:nft add chain inet filter input { type filter hook input priority 0 \; }# nft add chain inet filter input { type filter hook input priority 0 \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a dynamic set for IPv4 addresses:
nft add set inet filter limit-ssh { type ipv4_addr\; flags dynamic \;}# nft add set inet filter limit-ssh { type ipv4_addr\; flags dynamic \;}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add a rule to the
inputchain that allows only two simultaneous incoming connections to the SSH port (22) from an IPv4 address and rejects all further connections from the same IP:nft add rule inet filter input tcp dport ssh ct state new add @limit-ssh { ip saddr ct count over 2 } counter reject# nft add rule inet filter input tcp dport ssh ct state new add @limit-ssh { ip saddr ct count over 2 } counter rejectCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
- Establish more than two new simultaneous SSH connections from the same IP address to the host. Nftables refuses connections to the SSH port if two connections are already established.
Display the
limit-sshdynamic set:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
elementsentry displays addresses that currently match the rule. In this example,elementslists IP addresses that have active connections to the SSH port. Note that the output does not display the number of active connections or if connections were rejected.
8.8.2. Blocking IP addresses that attempt more than ten new incoming TCP connections within one minute
You can temporarily block hosts that are establishing more than ten IPv4 TCP connections within one minute.
Procedure
Create the
filtertable with theipaddress family:nft add table ip filter
# nft add table ip filterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
inputchain to thefiltertable:nft add chain ip filter input { type filter hook input priority 0 \; }# nft add chain ip filter input { type filter hook input priority 0 \; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add a rule that drops all packets from source addresses that attempt to establish more than ten TCP connections within one minute:
nft add rule ip filter input ip protocol tcp ct state new, untracked meter ratemeter { ip saddr timeout 5m limit rate over 10/minute } drop# nft add rule ip filter input ip protocol tcp ct state new, untracked meter ratemeter { ip saddr timeout 5m limit rate over 10/minute } dropCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
timeout 5mparameter defines thatnftablesautomatically removes entries after five minutes to prevent that the meter fills up with stale entries.
Verification
To display the meter’s content, enter:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.9. Debugging nftables rules
The nftables framework provides different options for administrators to debug rules and if packets match them.
8.9.1. Creating a rule with a counter
To identify if a rule is matched, you can use a counter.
Prerequisites
- The chain to which you want to add the rule exists.
Procedure
Add a new rule with the
counterparameter to the chain. The following example adds a rule with a counter that allows TCP traffic on port 22 and counts the packets and traffic that match this rule:nft add rule inet example_table example_chain tcp dport 22 counter accept
# nft add rule inet example_table example_chain tcp dport 22 counter acceptCopy to Clipboard Copied! Toggle word wrap Toggle overflow To display the counter values:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.9.2. Adding a counter to an existing rule
To identify if a rule is matched, you can use a counter.
Prerequisites
- The rule to which you want to add the counter exists.
Procedure
Display the rules in the chain including their handles:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the counter by replacing the rule but with the
counterparameter. The following example replaces the rule displayed in the previous step and adds a counter:nft replace rule inet example_table example_chain handle 4 tcp dport 22 counter accept
# nft replace rule inet example_table example_chain handle 4 tcp dport 22 counter acceptCopy to Clipboard Copied! Toggle word wrap Toggle overflow To display the counter values:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.9.3. Monitoring packets that match an existing rule
The tracing feature in nftables in combination with the nft monitor command enables administrators to display packets that match a rule. You can enable tracing for a rule and use it to monitor packets that match this rule.
Prerequisites
- The rule to which you want to add the counter exists.
Procedure
Display the rules in the chain including their handles:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the tracing feature by replacing the rule but with the
meta nftrace set 1parameters. The following example replaces the rule displayed in the previous step and enables tracing:nft replace rule inet example_table example_chain handle 4 tcp dport 22 meta nftrace set 1 accept
# nft replace rule inet example_table example_chain handle 4 tcp dport 22 meta nftrace set 1 acceptCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
nft monitorcommand to display the tracing. The following example filters the output of the command to display only entries that containinet example_table example_chain:nft monitor | grep "inet example_table example_chain" trace id 3c5eb15e inet example_table example_chain packet: iif "enp1s0" ether saddr 52:54:00:17:ff:e4 ether daddr 52:54:00:72:2f:6e ip saddr 192.0.2.1 ip daddr 192.0.2.2 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 49710 ip protocol tcp ip length 60 tcp sport 56728 tcp dport ssh tcp flags == syn tcp window 64240 trace id 3c5eb15e inet example_table example_chain rule tcp dport ssh nftrace set 1 accept (verdict accept) ...
# nft monitor | grep "inet example_table example_chain" trace id 3c5eb15e inet example_table example_chain packet: iif "enp1s0" ether saddr 52:54:00:17:ff:e4 ether daddr 52:54:00:72:2f:6e ip saddr 192.0.2.1 ip daddr 192.0.2.2 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 49710 ip protocol tcp ip length 60 tcp sport 56728 tcp dport ssh tcp flags == syn tcp window 64240 trace id 3c5eb15e inet example_table example_chain rule tcp dport ssh nftrace set 1 accept (verdict accept) ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningDepending on the number of rules with tracing enabled and the amount of matching traffic, the
nft monitorcommand can display a lot of output. Usegrepor other utilities to filter the output.
8.10. Backing up and restoring the nftables rule set
You can backup nftables rules to a file and later restoring them. Also, administrators can use a file with the rules to, for example, transfer the rules to a different server.
8.10.1. Backing up the nftables rule set to a file
You can use the nft utility to back up the nftables rule set to a file.
Procedure
To backup
nftablesrules:In a format produced by
nft list rulesetformat:nft list ruleset > file.nft
# nft list ruleset > file.nftCopy to Clipboard Copied! Toggle word wrap Toggle overflow In JSON format:
nft -j list ruleset > file.json
# nft -j list ruleset > file.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.10.2. Restoring the nftables rule set from a file
You can restore the nftables rule set from a file.
Procedure
To restore
nftablesrules:If the file to restore is in the format produced by
nft list rulesetor containsnftcommands directly:nft -f file.nft
# nft -f file.nftCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the file to restore is in JSON format:
nft -j -f file.json
# nft -j -f file.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 9. Securing network services
Red Hat Enterprise Linux 8 supports many different types of network servers. Their network services can expose the system security to risks of various types of attacks, such as denial of service attacks (DoS), distributed denial of service attacks (DDoS), script vulnerability attacks, and buffer overflow attacks.
To increase the system security against attacks, it is important to monitor active network services that you use. For example, when a network service is running on a machine, its daemon listens for connections on network ports, and this can reduce the security. To limit exposure to attacks over the network, all services that are unused should be turned off.
9.1. Securing the rpcbind service
The rpcbind service is a dynamic port-assignment daemon for remote procedure calls (RPC) services such as Network Information Service (NIS) and Network File System (NFS). Because it has weak authentication mechanisms and can assign a wide range of ports for the services it controls, it is important to secure rpcbind.
You can secure rpcbind by restricting access to all networks and defining specific exceptions using firewall rules on the server.
-
The
rpcbindservice is required onNFSv2andNFSv3servers. -
The
rpcbindservice is not required onNFSv4.
Prerequisites
-
The
rpcbindpackage is installed. -
The
firewalldpackage is installed and the service is running.
Procedure
Add firewall rules, for example:
Limit TCP connection and accept packages only from the
192.168.0.0/24host via the111port:firewall-cmd --add-rich-rule='rule family="ipv4" port port="111" protocol="tcp" source address="192.168.0.0/24" invert="True" drop'
# firewall-cmd --add-rich-rule='rule family="ipv4" port port="111" protocol="tcp" source address="192.168.0.0/24" invert="True" drop'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Limit TCP connection and accept packages only from local host via the
111port:firewall-cmd --add-rich-rule='rule family="ipv4" port port="111" protocol="tcp" source address="127.0.0.1" accept'
# firewall-cmd --add-rich-rule='rule family="ipv4" port port="111" protocol="tcp" source address="127.0.0.1" accept'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Limit UDP connection and accept packages only from the
192.168.0.0/24host via the111port:firewall-cmd --permanent --add-rich-rule='rule family="ipv4" port port="111" protocol="udp" source address="192.168.0.0/24" invert="True" drop'
# firewall-cmd --permanent --add-rich-rule='rule family="ipv4" port port="111" protocol="udp" source address="192.168.0.0/24" invert="True" drop'Copy to Clipboard Copied! Toggle word wrap Toggle overflow To make the firewall settings permanent, use the
--permanentoption when adding firewall rules.
Reload the firewall to apply the new rules:
firewall-cmd --reload
# firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
List the firewall rules:
firewall-cmd --list-rich-rule rule family="ipv4" port port="111" protocol="tcp" source address="192.168.0.0/24" invert="True" drop rule family="ipv4" port port="111" protocol="tcp" source address="127.0.0.1" accept rule family="ipv4" port port="111" protocol="udp" source address="192.168.0.0/24" invert="True" drop
# firewall-cmd --list-rich-rule rule family="ipv4" port port="111" protocol="tcp" source address="192.168.0.0/24" invert="True" drop rule family="ipv4" port port="111" protocol="tcp" source address="127.0.0.1" accept rule family="ipv4" port port="111" protocol="udp" source address="192.168.0.0/24" invert="True" dropCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.2. Securing the rpc.mountd service
The rpc.mountd daemon implements the server side of the NFS mount protocol. The NFS mount protocol is used by NFS version 2 (RFC 1904) and NFS version 3 (RFC 1813).
You can secure the rpc.mountd service by adding firewall rules to the server. You can restrict access to all networks and define specific exceptions using firewall rules.
Prerequisites
-
The
rpc.mountdpackage is installed. -
The
firewalldpackage is installed and the service is running.
Procedure
Add firewall rules to the server, for example:
Accept
mountdconnections from the192.168.0.0/24host:firewall-cmd --add-rich-rule 'rule family="ipv4" service name="mountd" source address="192.168.0.0/24" invert="True" drop'
# firewall-cmd --add-rich-rule 'rule family="ipv4" service name="mountd" source address="192.168.0.0/24" invert="True" drop'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Accept
mountdconnections from the local host:firewall-cmd --permanent --add-rich-rule 'rule family="ipv4" source address="127.0.0.1" service name="mountd" accept'
# firewall-cmd --permanent --add-rich-rule 'rule family="ipv4" source address="127.0.0.1" service name="mountd" accept'Copy to Clipboard Copied! Toggle word wrap Toggle overflow To make the firewall settings permanent, use the
--permanentoption when adding firewall rules.
Reload the firewall to apply the new rules:
firewall-cmd --reload
# firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
List the firewall rules:
firewall-cmd --list-rich-rule rule family="ipv4" service name="mountd" source address="192.168.0.0/24" invert="True" drop rule family="ipv4" source address="127.0.0.1" service name="mountd" accept
# firewall-cmd --list-rich-rule rule family="ipv4" service name="mountd" source address="192.168.0.0/24" invert="True" drop rule family="ipv4" source address="127.0.0.1" service name="mountd" acceptCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.3. Securing the NFS service
You can secure Network File System version 4 (NFSv4) by authenticating and encrypting all file system operations using Kerberos. When using NFSv4 with Network Address Translation (NAT) or a firewall, you can turn off the delegations by modifying the /etc/default/nfs file. Delegation is a technique by which the server delegates the management of a file to a client. In contrast, NFSv2 and NFSv3 do not use Kerberos for locking and mounting files.
The NFS service sends the traffic using TCP in all versions of NFS. The service supports Kerberos user and group authentication, as part of the RPCSEC_GSS kernel module.
NFS allows remote hosts to mount file systems over a network and interact with those file systems as if they are mounted locally. You can merge the resources on centralized servers and additionally customize NFS mount options in the /etc/nfsmount.conf file when sharing the file systems.
9.3.1. Export options for securing an NFS server
The NFS server determines a list structure of directories and hosts about which file systems to export to which hosts in the /etc/exports file.
You can use the following export options on the /etc/exports file:
ro- Exports the NFS volume as read-only.
rw-
Allows read and write requests on the NFS volume. Use this option cautiously because allowing write access increases the risk of attacks. If your scenario requires mounting the directories with the
rwoption, make sure they are not writable for all users to reduce possible risks. root_squash-
Maps requests from
uid/gid0 to the anonymousuid/gid. This does not apply to any otheruidsorgidsthat might be equally sensitive, such as thebinuser or thestaffgroup. no_root_squash-
Turns off root squashing. By default, NFS shares change the
rootuser to thenobodyuser, which is an unprivileged user account. This changes the owner of all therootcreated files tonobody, which prevents the uploading of programs with thesetuidbit set. When using theno_root_squashoption, remote root users can change any file on the shared file system and leave applications infected by trojans for other users. secure-
Restricts exports to reserved ports. By default, the server allows client communication only through reserved ports. However, it is easy for anyone to become a
rootuser on a client on many networks, so it is rarely safe for the server to assume that communication through a reserved port is privileged. Therefore the restriction to reserved ports is of limited value; it is better to rely on Kerberos, firewalls, and restriction of exports to particular clients.
Extra spaces in the syntax of the /etc/exports file can lead to major changes in the configuration.
In the following example, the /tmp/nfs/ directory is shared with the bob.example.com host and has read and write permissions.
/tmp/nfs/ bob.example.com(rw)
/tmp/nfs/ bob.example.com(rw)
The following example is the same as the previous one but shares the same directory to the bob.example.com host with read-only permissions and shares it to the world with read and write permissions due to a single space character after the hostname.
/tmp/nfs/ bob.example.com (rw)
/tmp/nfs/ bob.example.com (rw)
You can check the shared directories on your system by entering the showmount -e <hostname> command.
Additionally, consider the following best practices when exporting an NFS server:
- Exporting home directories is a risk because some applications store passwords in plain text or in a weakly encrypted format. You can reduce the risk by reviewing and improving the application code.
- Some users do not set passwords on SSH keys which again leads to risks with home directories. You can reduce these risks by enforcing the use of passwords or using Kerberos.
-
Restrict the NFS exports only to required clients. Use the
showmount -ecommand on the NFS server to review what the server is exporting. Do not export anything that is not specifically required. - Do not allow unnecessary users to log in to a server to reduce the risk of attacks. You can periodically check who and what can access the server.
Export an entire file system because exporting a subdirectory of a file system is not secure. An attacker might access the unexported part of a partially-exported file system.
9.3.2. Mount options for securing an NFS client
You can pass the following options to the mount command to increase the security of NFS-based clients:
nosuid-
Use the
nosuidoption to disable theset-user-identifierorset-group-identifierbits. This prevents remote users from gaining higher privileges by running asetuidprogram and you can use this option opposite tosetuidoption. noexec-
Use the
noexecoption to disable all executable files on the client. Use this to prevent users from accidentally executing files placed in the shared file system. nodev-
Use the
nodevoption to prevent the client’s processing of device files as a hardware device. resvport-
Use the
resvportoption to restrict communication to a reserved port and you can use a privileged source port to communicate with the server. The reserved ports are reserved for privileged users and processes such as therootuser. sec-
Use the
secoption on the NFS server to choose the RPCGSS security flavor for accessing files on the mount point. Valid security flavors arenone,sys,krb5,krb5i, andkrb5p.
The MIT Kerberos libraries provided by the krb5-libs package do not support the Data Encryption Standard (DES) algorithm in new deployments. DES is deprecated and disabled by default in Kerberos libraries because of security and compatibility reasons. Use newer and more secure algorithms instead of DES, unless your environment requires DES for compatibility reasons.
9.3.3. Securing NFS with firewall
To secure the firewall on an NFS server, keep only the required ports open. Do not use the NFS connection port numbers for any other service.
Prerequisites
-
The
nfs-utilspackage is installed. -
The
firewalldpackage is installed and running.
Procedure
-
On NFSv4, the firewall must open TCP port
2049. On NFSv3, open four additional ports with
2049:rpcbindservice assigns the NFS ports dynamically, which might cause problems when creating firewall rules. To simplify this process, use the/etc/nfs.conffile to specify which ports to use:-
Set TCP and UDP port for
mountd(rpc.mountd) in the[mountd]section inport=<value>format. -
Set TCP and UDP port for
statd(rpc.statd) in the[statd]section inport=<value>format.
-
Set TCP and UDP port for
Set the TCP and UDP port for the NFS lock manager (
nlockmgr) in the/etc/nfs.conffile:-
Set TCP port for
nlockmgr(rpc.statd) in the[lockd]section inport=valueformat. Alternatively, you can use thenlm_tcpportoption in the/etc/modprobe.d/lockd.conffile. -
Set UDP port for
nlockmgr(rpc.statd) in the[lockd]section inudp-port=valueformat. Alternatively, you can use thenlm_udpportoption in the/etc/modprobe.d/lockd.conffile.
-
Set TCP port for
Verification
List the active ports and RPC programs on the NFS server:
rpcinfo -p
$ rpcinfo -pCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.4. Securing the FTP service
You can use the File Transfer Protocol (FTP) to transfer files over a network. Because all FTP transactions with the server, including user authentication, are unencrypted, make sure it is configured securely.
RHEL 8 provides two FTP servers:
- Red Hat Content Accelerator (
tux) - A kernel-space web server with FTP capabilities.
- Very Secure FTP Daemon (
vsftpd) - A standalone, security-oriented implementation of the FTP service.
The following security guidelines are for setting up the vsftpd FTP service.
9.4.1. Securing the FTP greeting banner
When a user connects to the FTP service, FTP shows a greeting banner, which by default includes version information. Attackers might use this information to identify weaknesses in the system. You can hide this information by changing the default banner.
You can define a custom banner by editing the /etc/banners/ftp.msg file to either directly include a single-line message, or to refer to a separate file, which can contain a multi-line message.
Procedure
To define a single line message, add the following option to the
/etc/vsftpd/vsftpd.conffile:ftpd_banner=Hello, all activity on ftp.example.com is logged.
ftpd_banner=Hello, all activity on ftp.example.com is logged.Copy to Clipboard Copied! Toggle word wrap Toggle overflow To define a message in a separate file:
Create a
.msgfile which contains the banner message, for example/etc/banners/ftp.msg:######### Hello, all activity on ftp.example.com is logged. #########
######### Hello, all activity on ftp.example.com is logged. #########Copy to Clipboard Copied! Toggle word wrap Toggle overflow To simplify the management of multiple banners, place all banners into the
/etc/banners/directory.Add the path to the banner file to the
banner_fileoption in the/etc/vsftpd/vsftpd.conffile:banner_file=/etc/banners/ftp.msg
banner_file=/etc/banners/ftp.msgCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the modified banner:
ftp localhost Trying ::1… Connected to localhost (::1). Hello, all activity on ftp.example.com is logged.
$ ftp localhost Trying ::1… Connected to localhost (::1). Hello, all activity on ftp.example.com is logged.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.4.2. Preventing anonymous access and uploads in FTP
By default, installing the vsftpd package creates the /var/ftp/ directory and a directory tree for anonymous users with read-only permissions on the directories. Because anonymous users can access the data, do not store sensitive data in these directories.
To increase the security of the system, you can configure the FTP server to allow anonymous users to upload files to a specific directory and prevent anonymous users from reading data. In the following procedure, the anonymous user must be able to upload files in the directory owned by the root user but not change it.
Procedure
Create a write-only directory in the
/var/ftp/pub/directory:mkdir /var/ftp/pub/upload chmod 730 /var/ftp/pub/upload ls -ld /var/ftp/pub/upload drwx-wx---. 2 root ftp 4096 Nov 14 22:57 /var/ftp/pub/upload
# mkdir /var/ftp/pub/upload # chmod 730 /var/ftp/pub/upload # ls -ld /var/ftp/pub/upload drwx-wx---. 2 root ftp 4096 Nov 14 22:57 /var/ftp/pub/uploadCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the following lines to the
/etc/vsftpd/vsftpd.conffile:anon_upload_enable=YES anonymous_enable=YES
anon_upload_enable=YES anonymous_enable=YESCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Optional: If your system has SELinux enabled and enforcing, enable SELinux boolean attributes
allow_ftpd_anon_writeandallow_ftpd_full_access.
Allowing anonymous users to read and write in directories might lead to the server becoming a repository for stolen software.
9.4.3. Securing user accounts for FTP
FTP transmits usernames and passwords unencrypted over insecure networks for authentication. You can improve the security of FTP by denying system users access to the server from their user accounts.
Perform as many of the following steps as applicable for your configuration.
Procedure
Disable all user accounts in the
vsftpdserver, by adding the following line to the/etc/vsftpd/vsftpd.conffile:local_enable=NO
local_enable=NOCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Disable FTP access for specific accounts or specific groups of accounts, such as the
rootuser and users withsudoprivileges, by adding the usernames to the/etc/pam.d/vsftpdPAM configuration file. -
Disable user accounts, by adding the usernames to the
/etc/vsftpd/ftpusersfile.
9.5. Securing HTTP servers
9.5.1. Security enhancements in httpd.conf
You can enhance the security of the Apache HTTP server by configuring security options in the /etc/httpd/conf/httpd.conf file.
Always verify that all scripts running on the system work correctly before putting them into production.
Ensure that only the root user has write permissions to any directory containing scripts or Common Gateway Interfaces (CGI). To change the directory ownership to root with write permissions, enter the following commands:
chown root <directory_name> chmod 755 <directory_name>
# chown root <directory_name>
# chmod 755 <directory_name>
In the /etc/httpd/conf/httpd.conf file, you can configure the following options:
FollowSymLinks- This directive is enabled by default and follows symbolic links in the directory.
Indexes- This directive is enabled by default. Disable this directive to prevent visitors from browsing files on the server.
UserDir-
This directive is disabled by default because it can confirm the presence of a user account on the system. To activate user directory browsing for all user directories other than
/root/, use theUserDir enabledandUserDir disabledroot directives. To add users to the list of disabled accounts, add a space-delimited list of users on theUserDir disabledline. ServerTokensThis directive controls the server response header field which is sent back to clients. You can use the following parameters to customize the information:
ServerTokens FullProvides all available information such as web server version number, server operating system details, installed Apache modules, for example:
Apache/2.4.37 (Red Hat Enterprise Linux) MyMod/1.2
Apache/2.4.37 (Red Hat Enterprise Linux) MyMod/1.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow ServerTokens Full-ReleaseProvides all available information with release versions, for example:
Apache/2.4.37 (Red Hat Enterprise Linux) (Release 41.module+el8.5.0+11772+c8e0c271)
Apache/2.4.37 (Red Hat Enterprise Linux) (Release 41.module+el8.5.0+11772+c8e0c271)Copy to Clipboard Copied! Toggle word wrap Toggle overflow ServerTokens Prod / ServerTokens ProductOnlyProvides the web server name, for example:
Apache
ApacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow ServerTokens MajorProvides the web server major release version, for example:
Apache/2
Apache/2Copy to Clipboard Copied! Toggle word wrap Toggle overflow ServerTokens MinorProvides the web server minor release version, for example:
Apache/2.4
Apache/2.4Copy to Clipboard Copied! Toggle word wrap Toggle overflow ServerTokens Min/ServerTokens MinimalProvides the web server minimal release version, for example:
Apache/2.4.37
Apache/2.4.37Copy to Clipboard Copied! Toggle word wrap Toggle overflow ServerTokens OSProvides the web server release version and operating system, for example:
Apache/2.4.37 (Red Hat Enterprise Linux)
Apache/2.4.37 (Red Hat Enterprise Linux)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
ServerTokens Prodoption to reduce the risk of attackers gaining any valuable information about your system.
Do not remove the IncludesNoExec directive. By default, the Server Side Includes (SSI) module cannot execute commands. Changing this can allow an attacker to enter commands on the system.
Removing httpd modules
You can remove the httpd modules to limit the functionality of the HTTP server. To do so, edit configuration files in the /etc/httpd/conf.modules.d/ or /etc/httpd/conf.d/ directory. For example, to remove the proxy module:
echo '# All proxy modules disabled' > /etc/httpd/conf.modules.d/00-proxy.conf
echo '# All proxy modules disabled' > /etc/httpd/conf.modules.d/00-proxy.conf9.5.2. Securing the Nginx server configuration
Nginx is a high-performance HTTP and proxy server. You can harden your Nginx configuration with the following configuration options.
Procedure
To disable version strings, modify the
server_tokensconfiguration option:server_tokens off;
server_tokens off;Copy to Clipboard Copied! Toggle word wrap Toggle overflow This option stops displaying additional details such as server version number. This configuration displays only the server name in all requests served by Nginx, for example:
curl -sI http://localhost | grep Server Server: nginx
$ curl -sI http://localhost | grep Server Server: nginxCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add extra security headers that mitigate certain known web application vulnerabilities in specific
/etc/nginx/conf files:For example, the
X-Frame-Optionsheader option denies any page outside of your domain to frame any content served by Nginx, mitigating clickjacking attacks:add_header X-Frame-Options "SAMEORIGIN";
add_header X-Frame-Options "SAMEORIGIN";Copy to Clipboard Copied! Toggle word wrap Toggle overflow For example, the
x-content-typeheader prevents MIME-type sniffing in certain older browsers:add_header X-Content-Type-Options nosniff;
add_header X-Content-Type-Options nosniff;Copy to Clipboard Copied! Toggle word wrap Toggle overflow For example, the
X-XSS-Protectionheader enables Cross-Site Scripting (XSS) filtering, which prevents browsers from rendering potentially malicious content included in a response by Nginx:add_header X-XSS-Protection "1; mode=block";
add_header X-XSS-Protection "1; mode=block";Copy to Clipboard Copied! Toggle word wrap Toggle overflow
You can limit the services exposed to the public and limit what they do and accept from the visitors, for example:
limit_except GET { allow 192.168.1.0/32; deny all; }limit_except GET { allow 192.168.1.0/32; deny all; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow The snippet will limit access to all methods except
GETandHEAD.You can disable HTTP methods, for example:
# Allow GET, PUT, POST; return "405 Method Not Allowed" for all others. if ( $request_method !~ ^(GET|PUT|POST)$ ) { return 405; }# Allow GET, PUT, POST; return "405 Method Not Allowed" for all others. if ( $request_method !~ ^(GET|PUT|POST)$ ) { return 405; }Copy to Clipboard Copied! Toggle word wrap Toggle overflow - You can configure SSL to protect the data served by your Nginx web server, consider serving it over HTTPS only. Furthermore, you can generate a secure configuration profile for enabling SSL in your Nginx server using the Mozilla SSL Configuration Generator. The generated configuration ensures that known vulnerable protocols (for example, SSLv2 and SSLv3), ciphers, and hashing algorithms (for example, 3DES and MD5) are disabled. You can also use the SSL Server Test to verify that your configuration meets modern security requirements.
9.6. Securing PostgreSQL by limiting access to authenticated local users
PostgreSQL is an object-relational database management system (DBMS). In Red Hat Enterprise Linux, PostgreSQL is provided by the postgresql-server package.
You can reduce the risks of attacks by configuring client authentication. The pg_hba.conf configuration file stored in the database cluster’s data directory controls the client authentication. Follow the procedure to configure PostgreSQL for host-based authentication.
Procedure
Install PostgreSQL:
yum install postgresql-server
# yum install postgresql-serverCopy to Clipboard Copied! Toggle word wrap Toggle overflow Initialize a database storage area using one of the following options:
Using the
initdbutility:initdb -D /home/postgresql/db1/
$ initdb -D /home/postgresql/db1/Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
initdbcommand with the-Doption creates the directory you specify if it does not already exist, for example/home/postgresql/db1/. This directory then contains all the data stored in the database and also the client authentication configuration file.Using the
postgresql-setupscript:postgresql-setup --initdb
$ postgresql-setup --initdbCopy to Clipboard Copied! Toggle word wrap Toggle overflow By default, the script uses the
/var/lib/pgsql/data/directory. This script helps system administrators with basic database cluster administration.
To allow any authenticated local users to access any database with their usernames, modify the following line in the
pg_hba.conffile:local all all trust
local all all trustCopy to Clipboard Copied! Toggle word wrap Toggle overflow This can be problematic when you use layered applications that create database users and no local users. If you do not want to explicitly control all user names on the system, remove the
localline entry from thepg_hba.conffile.Restart the database to apply the changes:
systemctl restart postgresql
# systemctl restart postgresqlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The previous command updates the database and also verifies the syntax of the configuration file.
9.7. Securing the Memcached service
Memcached is an open source, high-performance, distributed memory object caching system. It can improve the performance of dynamic web applications by lowering database load.
Memcached is an in-memory key-value store for small chunks of arbitrary data, such as strings and objects, from results of database calls, API calls, or page rendering. Memcached allows assigning memory from underutilized areas to applications that require more memory.
In 2018, vulnerabilities of DDoS amplification attacks by exploiting Memcached servers exposed to the public internet were discovered. These attacks took advantage of Memcached communication using the UDP protocol for transport. The attack was effective because of the high amplification ratio where a request with the size of a few hundred bytes could generate a response of a few megabytes or even hundreds of megabytes in size.
In most situations, the memcached service does not need to be exposed to the public Internet. Such exposure may have its own security problems, allowing remote attackers to leak or modify information stored in Memcached.
9.7.1. Hardening Memcached against DDoS
To mitigate security risks, perform as many of the following steps as applicable for your configuration.
Procedure
Configure a firewall in your LAN. If your Memcached server should be accessible only in your local network, do not route external traffic to ports used by the
memcachedservice. For example, remove the default port11211from the list of allowed ports:firewall-cmd --remove-port=11211/udp firewall-cmd --runtime-to-permanent
# firewall-cmd --remove-port=11211/udp # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you use a single Memcached server on the same machine as your application, set up
memcachedto listen to localhost traffic only. Modify theOPTIONSvalue in the/etc/sysconfig/memcachedfile:OPTIONS="-l 127.0.0.1,::1"
OPTIONS="-l 127.0.0.1,::1"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable Simple Authentication and Security Layer (SASL) authentication:
Modify or add the
/etc/sasl2/memcached.conffile:sasldb_path: /path.to/memcached.sasldb
sasldb_path: /path.to/memcached.sasldbCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add an account in the SASL database:
saslpasswd2 -a memcached -c cacheuser -f /path.to/memcached.sasldb
# saslpasswd2 -a memcached -c cacheuser -f /path.to/memcached.sasldbCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that the database is accessible for the
memcacheduser and group:chown memcached:memcached /path.to/memcached.sasldb
# chown memcached:memcached /path.to/memcached.sasldbCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable SASL support in Memcached by adding the
-Svalue to theOPTIONSparameter in the/etc/sysconfig/memcachedfile:OPTIONS="-S"
OPTIONS="-S"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the Memcached server to apply the changes:
systemctl restart memcached
# systemctl restart memcachedCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the username and password created in the SASL database to the Memcached client configuration of your application.
Encrypt communication between Memcached clients and servers with TLS:
Enable encrypted communication between Memcached clients and servers with TLS by adding the
-Zvalue to theOPTIONSparameter in the/etc/sysconfig/memcachedfile:OPTIONS="-Z"
OPTIONS="-Z"Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Add the certificate chain file path in the PEM format using the
-o ssl_chain_certoption. -
Add a private key file path using the
-o ssl_keyoption.