User Access Configuration Guide for Role-based Access Control (RBAC)
How to use the User Access feature to configure RBAC for services hosted on the Red Hat Hybrid Cloud Console
Abstract
Chapter 1. User Access Configuration Guide for Role-based Access Control (RBAC)
The User Access feature is an implementation of role-based access control (RBAC) that controls user access to various services hosted on the Red Hat Hybrid Cloud Console. You configure the User Access feature to grant user access to services hosted on the Hybrid Cloud Console.
1.1. User Access and the Software as a Service (SaaS) access model
Red Hat customer accounts might have hundreds of authenticated users, yet not all users need the same level of access to the SaaS services available on the Red Hat Hybrid Cloud Console. With the User Access features, an Organization Administrator can manage user access to services hosted on the Red Hat Hybrid Cloud Console.
User Access does not manage OpenShift Cluster Manager permissions. For OpenShift Cluster Manager, all users in the organization can view information, but only an Organization Administrator and cluster owners can perform actions on clusters. See Configuring access to clusters in OpenShift Cluster Manager in the Openshift Cluster Manager documentation for details.
1.2. Who can use User Access
To initially view and manage User Access on the Red Hat Hybrid Cloud Console, you must be an Organization Administrator. This is because User Access requires user management capabilities that are designated from the Red Hat Customer Portal at Customer Portal. Those capabilities belong solely to the Organization Administrator.
The User Access administrator role is a special role that the Organization Administrator can assign. This role allows users who are not Organization Administrator users to manage User Access on the Red Hat Hybrid Cloud Console.
1.3. How to use User Access
The User Access feature is based on managing roles rather than by individually assigning permissions to specific users. In User Access, each role has a specific set of permissions. For example, a role might allow read permission for an application. Another role might allow write permission for an application.
You create groups that contain roles and, by extension, the permissions assigned to each role. You assign users (or service accounts) to groups. This means each user in a group is assigned the permissions of the roles in that group.
By creating different groups and adding or removing roles for that group, you control the permissions allowed for that group. When you add one or more users to a group, those users can perform all actions that are allowed for that group.
Red Hat provides two default access groups for User Access:
- Default admin access group. The Default admin access group is limited to Organization Administrator users in your organization. You cannot change or modify the roles in the Default admin access group.
Default access group. The Default access group contains all authenticated users in your organization. These users automatically inherit a selection of predefined roles.
NoteYou can make changes to the Default access group. However, when you do so, its name changes to Custom default access group.
Red Hat provides a set of predefined roles. Depending on the application, the predefined roles for each supported application might have different permissions that are tailored to the application.
1.3.1. The Default admin access group
The Default admin access group is provided by Red Hat on the Red Hat Hybrid Cloud Console. It contains a set of roles that are assigned to all users who have an Organization Administrator role on your system. The roles in this group are predefined in the Red Hat Hybrid Cloud Console.
The roles in the Default admin access group cannot be added to or modified. Because this group is provided by Red Hat, it is automatically updated when Red Hat assigns roles to the Default admin access group.
The benefit of the Default admin access group is that it allows roles to be assigned automatically to Organization Administrators.
See Predefined User Access roles, for the roles included in the Default admin access group.
1.3.2. The Default access group
The Default access group is provided by Red Hat on the Red Hat Hybrid Cloud Console. It contains a set of roles that are predefined in the Red Hat Hybrid Cloud Console. The Default access group includes all authenticated users in your organization. The Default access group is automatically updated when Default access group roles are added in the Red Hat Hybrid Cloud Console.
The Default access group contains a subset of all predefined roles. For more information, see section Predefined User Access roles, for the roles included in the Default admin access group.
As an Organization Administrator, you can add roles to and remove roles from the Default access group. When you do so, its name changes to Custom default access group. The changes you make to this group affect all authenticated users in your organization.
1.3.3. The Custom default access group
When you manually modify the Default access group, its name changes to Custom default access, which indicates it was modified. Moreover, it is no longer automatically updated from the Red Hat Hybrid Cloud Console.
From that point forward, an Organization Administrator is responsible for all updates and changes to the Custom default access group. The group is no longer managed or updated by the Red Hat Hybrid Cloud Console.
You cannot delete the Default access group or Custom default access group.
You can restore the Default access group, which removes the Custom default access group and any changes you made. See Restoring the Default access group.
1.3.4. User Access groups, roles, and permissions
User Access uses the following categories to determine the level of user access that an Organization Administrator can grant to the supported Red Hat Hybrid Cloud Console services. The access provided to any authorized user depends on the group that the user belongs to and the roles assigned to that group.
- Group: A collection of users belonging to an account which provides the mapping of roles to users. An Organization Administrator can use groups to assign one or more roles to a group and to include one or more users in a group. You can create a group with no roles and no users.
- Roles: A set of permissions that provide access to a given service, such as Insights. The permissions to perform certain operations are assigned to specific roles. Roles are assigned to groups. For example, you might have a read role and a write role for a service. Adding both roles to a group grants all members of that group read and write permissions to that service.
- Permissions: A discrete action that can be requested of a service. Permissions are assigned to roles.
An Organization Administrator adds or deletes roles, users, and service accounts to groups. The group can be a new group created by an Organization Administrator or the group can be an existing group. By creating a group that has one or more specific roles and then adding users to that group, you control how that group and its members interact with Red Hat Hybrid Cloud Console services.
When you add users to a group, they become members of that group. A group member inherits the roles of all other groups they belong to. The user interface lists users in the Members tab.
You can also use workspaces to configure access control to resources. Workspaces provide a way to easily organize systems in your inventory, apply access management rules to those systems, and restrict system access only to users who require it.
You can create and manage workspaces by navigating to RHEL > Inventory > Workspaces, or Identity & Access Management > Workspaces.
Using workspaces to configure access management is a preview feature in the Hybrid Cloud Console. See Previewing Hybrid Cloud Console features for information about using preview features.
1.3.5. Additive access
User access on the Red Hat Hybrid Cloud Console uses an additive model, which means that there are no deny roles. In other words, actions are only permitted. To control access, assign the appropriate roles with the desired permissions to groups, then add users to those groups. The access permitted to any individual user is a sum of all roles assigned to all groups to which that user belongs.
1.3.6. Access structure
The following points are a summary of the user access structure for User Access:
- Group: A user can be a member of one or many groups.
- Role: A role can be added to one or many groups.
- Permissions: One or more permissions can be assigned to a role.
In its initial default configuration, all User Access account users inherit the roles that are provided in the Default access group.
Any user added to a group must be an authenticated user for the organization account on the Red Hat Hybrid Cloud Console.
1.4. Access management with workspaces
For Red Hat Enterprise Linux (RHEL) systems, you can configure workspaces to organize systems in your inventory and apply access management rules to those systems. Use workspace configuration to restrict system access only to users who require it.
Configuring access management using workspaces is a preview feature in the Hybrid Cloud Console. See Previewing Hybrid Cloud Console features for information about using preview features.
Additional resources
- For more information about configuring inventory and workspaces for RHEL systems, see Viewing and managing system inventory in the Red Hat Insights documentation.
Chapter 2. Procedures for configuring User Access
As an Organization Administrator or User Access administrator, you can click
 > Identity & Access Management to view, configure, and modify the User Access groups, roles, and permissions.
> Identity & Access Management to view, configure, and modify the User Access groups, roles, and permissions.
2.1. Creating a User Access administrator
The User Access administrator is a special role that the Organization Administrator assigns to a group. All users in this group can perform User Access administration roles, such as adding, modifying, or deleting groups and roles. The User Access administrator role does not inherit the roles defined in the Default Admin Access group.
The User Access administrator role cannot create or modify a User Access administrator group. Only the Organization Administrator can create, modify, or delete a group that is assigned the User Access administrator role.
The User Access administrator role does not grant permission to view and approve customer Access Requests.
By having the User Access administrator role, users who are not the Organization Administrator can perform many of the Organization Administrator functions for managing the User Access features. The User Access administrator role does not inherit the roles of the Default admin access group. The roles in that group are restricted to the Organization Administrator.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Groups.
- Click Create group.
Follow the guided actions provided by the wizard to create the group and add users and roles.
- Name the group with a recognizable name: User Access Admin.
- Provide a meaningful description: User Access Organization Administrator permissions
- Click the Next button to add roles.
- Search for the User Access administrator role and click the selection box to add this role to the group. Optionally, select additional roles.
Click the Next button to add members to the group.
NoteAny member you add must be an active member of the organization account.
- After you select the members for the group, click the Next button to review the details.
- You can click the Back button to go back and make changes, or the Cancel button to cancel the action.
- Click the Submit button to complete the Create group wizard. The new group will appear in the Groups tab.
2.2. Viewing roles and permissions
You can view the roles and permissions for User Access at the Red Hat Hybrid Cloud Console. For a list of predefined roles provided by Red Hat, see section Predefined User Access roles.
You cannot modify a predefined role.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Roles. User Access roles are displayed. You can scroll through the list of all Roles.
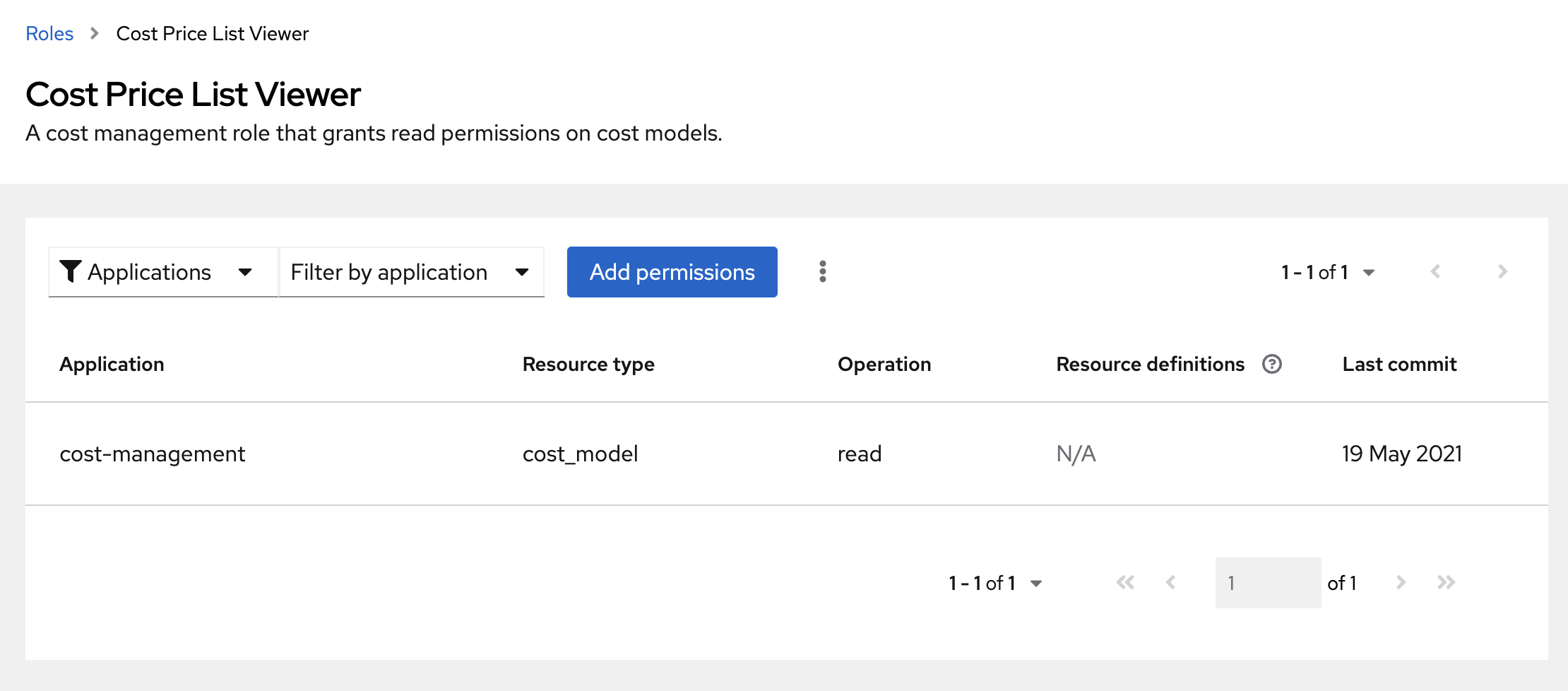
In the table, click either the role Name or the role Permissions to see details about the permissions assigned to the role. For example, if you click on the Cost Price List Viewer role, you see the following information.
An asterisk * indicates a wildcard permission. A wildcard permission grants access to all resource types and allows all operations for the applications in a role.
2.3. Viewing user permissions
You can view a user’s permissions and other access-related information from the user details page.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Users to view a list of users in your organization.
- Click a Username to view more details about that user.
On the user details page, you can view:
- If the user is an Organization Administrator in your organization
- The user’s email address
- The user’s username on the Hybrid Cloud Console (also known as a Red Hat login)
A list of roles associated with the user. To view more details about each role:
- Click the count in the Groups column to show the groups with this role assigned.
- Click the count in the Permissions column to show permissions the role provides.
If you are not an Organization Administrator, you can view your own permissions for different services by navigating to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > My User Access.
2.4. Managing group access with roles and members
You can manage group access by creating a group and adding roles, users, and service accounts to the group. The roles and their permissions determine the type of access granted to all members of the group.
The Members tab shows all users that you can add to the group. When you add users to a group, they become members of that group. A group member inherits the roles of all other groups they belong to.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
NoteOnly the Organization Administrator can assign the User Access administrator role to a group.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Groups to open the Groups page.
- Click Create group.
- Follow the guided actions provided by the wizard to add users and roles.
- To grant additional group access, edit the group and add additional roles.
2.4.1. Adding a role to a group
Add a role to an existing group to provide additional permissions to all members of that group. You can view user details to add roles to a group that the user belongs to.
You can add a role to a group from the Users page, or by editing a group from the Groups page. These steps show you how to edit the group from the user details page.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Users to open the Users list.
- Click the Username for a user to open the user details page.
Click the count in the Groups column for a role. This shows the groups the user is a member of that have this role assigned.
NoteYou can view the permissions a role provides by clicking the count in the Permissions column.
- Click Add role to this group next to the group name to add additional role(s) to the group. This opens the Add roles dialog.
- Select the checkbox for each role(s) you want to add to the group. (Only roles not yet associated with the group are listed.) Click Add to group.
- Reload the user details page to see the roles you added to the group.
The group now has these additional permissions in the console.
2.4.2. Adding a user to a group
Add a user to an existing group to provide that user with the permissions granted by the roles assigned to that group.
This can be useful when a new team member joins your organization and you want to provide them with all necessary permissions for their work.
You can add a user to a group from the Users page, or by editing a group from the Groups page. These steps show you how to add a user to a group from the user details page.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Users to open the Users list.
- Click the username for the user you want to edit.
- On the user details page, click Add user to a group. A dialog opens showing a list of groups the user is not a member of.
- Select the checkbox for one or more groups to add the user to and click Add to group.
- Reload the user details page to see the roles you added.
The user now has the permissions granted by the group(s) they were added to.
2.5. Restricting service access to a single user
You can create a new group that contains a single user and add a role to that group. The role you add provides the service access permissions you want that single user to have. If you add other users to the group, the added users will have the same group permissions.
The roles you add to the group can be from the predefined list of roles provided with User Access, from custom roles created by an Organization Administrator, or a combination of both.
For more information about predefined roles, see section Predefined User Access roles.
When you add a user to a new group, the user acquires the permissions of the new group and also inherits the permissions of all other groups they belong to. The permissions of the new group are added to their existing permissions.
In this procedure you modify the Default access group. Once modified, the Default access group name changes to Custom default access. The Custom default access group is no longer updated with changes pushed out by Red Hat from the Red Hat Hybrid Cloud Console.
You can restore the Default access group, which removes the Custom default access group and any changes you made. See Restoring the Default access group.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Groups. The Groups page is displayed.
Remove all roles from the Default access group.
Because all users in your organization belong to the Default access group, you cannot add or remove single users in Default access to create access control. By removing all roles, users do not inherit role permissions from Default access.
- Select the checkbox above the roles list to select all roles in the group.
- Click the more options icon (⋮) > Remove.
- Click Remove roles to confirm.
- Save the changes to Default access group. The name changes to Custom default access.
Create a new group that contains the users and roles for the allowed access permissions.
For example, create a group Security Admin that contains the users who will have full access to vulnerability service.
- Create a group Security Admin.
- Add one or several users to the group from the Members list.
Add the Vulnerability administrator role.
Each user you add to this group has full access to the vulnerability service.
If you want an Organization Administrator to have access, add the Organization Administrator user to the group.
2.6. Including an Organization Administrator in a group
You can include an Organization Administrator in a group. You add an Organization Administrator user to a group if you want an Organization Administrator to have the roles assigned to that group. An Organization Administrator does not inherit all available roles for all Red Hat Hybrid Cloud Console applications. Any roles not inherited by means of the Default access group or the Default admin access group must be assigned through group membership.
This procedure assumes that you want to modify an existing group and add an Organization Administrator to the group. Alternatively, you can add an Organization Administrator to a group when you create a new group.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
- Create a group if one does not exist. For more information, see Managing group access with roles and members.
- For information about how to configure notifications for behavior groups, see Configure notification behavior groups.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Groups. The Groups page displays.
- Click the group Name to display details about the group.
- On the group details page, click the Members tab to display a list of authorized users who are a member of the group.
- Click the Add member tab.
On the Add members to the group page that appears, find the Organization Administrator user name and click the check box next to the name.
For example, if the Organization Administrator user name is
smith-jones, find that name and click the check box next tosmith-jones. You can add additional names.- Verify the name list is complete and click the Add to group action.
Notification pop-ups appear when the action successfully completes.
2.7. Disabling group access
You can disable group access by removing roles from a group. Because the roles and their permissions determine the type of access granted to the group, removing roles disables group access for that role.
Prerequisite
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Groups. The Groups page is displayed.
- Click the Group Name that you want to modify.
- Click the Roles tab.
Click the check box next to roles Name that you want to remove.
You can click the check box at the top of the Name column to select all roles.
-
Click the more options menu icon
 that is next to the Add role tab, and then click Remove from group.
that is next to the Add role tab, and then click Remove from group.
- In the confirmation window that appears, click either Remove role or Cancel to complete the action.
Groups can contain no roles and no members and still be a valid group.
2.8. Granular permissions for User Access
Granular permissions allow an Organization Administrator to define role permissions for one or more applications. Many of the predefined roles provide wildcard permissions, which is equivalent to a super user role with full access to all actions.
By defining granular permissions, you can create (or modify) roles with limited permissions, such as read-only, or read and update but not delete.
As an example, compare the predefined roles of Cost Administrator and Cost Price List Viewer.
| Role | Application | Resource | Operation |
|---|---|---|---|
| Cost Administrator | cost-management | * (all) | * (all) |
| Cost Price List Viewer | cost-management | cost_model | read |
By creating a new role, you can define the applications, resources, and operations that are specific to that role.
2.8.1. Adding custom User Access roles
User Access provides a number of predefined roles that you can add to groups. In addition to using the predefined roles, you can create and manage custom User Access roles with granular permissions for one or more applications.
For a list of predefined roles provided by Red Hat, see section Predefined User Access roles.
The Default access group contains a subset of all predefined roles. For more information, see section Predefined User Access roles.
You cannot modify a predefined role.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
Procedure
A guided wizard leads you through the steps for adding a role.
The following steps describe how to use the Create role wizard.
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Roles. The Roles window appears.
- Click the Create role button. This starts the Create role wizard.
At this point in the wizard, you can create a role from scratch or copy an existing role.
2.8.2. Creating a role from scratch
Create a role from scratch when you want to create a role with specific granular permissions. For example, you can create a single role for your organization that provides read-only permissions across all resources for all available applications. By adding and managing this role in your default access group, you can change default access to read-only.
Prerequisites
- You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
- You started the Create role wizard.
Procedure
- In the Create role wizard, click the Create a role from scratch button.
- Enter a Role name, which is required.
- Optionally, enter a Role description.
- Click the Next button. If the role name already exists, you must provide a different name before you can proceed.
- Use the Add permissions window to select the application permissions to include in your role. By default, permissions are listed by application.
Optionally use the filter drop-down to to filter by Applications, Resources, or Operations.
TipUse the list at the top of the wizard page to view all the permissions added to the role. You can click a permission to delete it.
- Click the Next button to review details. You can click the Submit button to submit the role, the Back button to go back and make changes, or the Cancel button to cancel the action.
The role you created is available to add to a User Access group.
2.8.3. Copying an existing role
Copy an existing role when that role already contains many of the permissions you want to use and you need to change, add, or remove some permissions.
An existing role can be one of the predefined roles provided by Red Hat or it can be a previously created custom role.
For a list of predefined roles provided by Red Hat, see section Predefined User Access roles.
You cannot modify a predefined role.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
- You started the Create role wizard.
Procedure
- In the Create role wizard, click the Copy an existing role button.
- Click the button next to the role you want to copy.
- Click the Next button.
- The Name and description window shows a copy of the Role name and the existing Role description filled in. Make changes as needed.
- Click the Next button. If the role name already exists, you must provide a different name before you can proceed.
Use the Add permissions window to select the application permissions to include in your role. By default, permissions are listed by application.
TipCustom roles only support granular permissions. Wildcard permissions, such as
approval:*:*are not copied into a custom role.Optionally use the filter drop-down to to filter by Applications, Resources, or Operations.
TipUse the list at the top of the wizard page to view all the permissions added to the role. You can click a permission to delete it.
- Click the Next button to review details. You can click the Submit button to submit the role, the Back button to go back and make changes, or the Cancel button to cancel the action.
The role you created is available to add to a User Access group.
2.8.4. Creating a User Access group for service accounts
The Organization Administrator can create a new User Access group with roles or permissions that are specific to a service account. This group has the permissions that allow a service account to access services and applications on the Red Hat Hybrid Cloud Console. Any user can create a service account but only the Organization Administrator or a User Access administrator can add or create a new group for a service account.
In this example, you create a group that allows a service account to view automation analytics on the Red Hat Ansible Automation Platform.
Prerequisites
- You are logged in to the Red Hat Hybrid Cloud Console as the Organization Administrator or as a user with User Access administrator permissions.
- One or more service accounts are associated with your Red Hat organization account. See Creating and managing a service account.
You have access to the Client Secret information for the service account that you add to the User Access group.
NoteThe Client Secret information is displayed once when you create a new service account. You must copy and save that information. It is not displayed again.
Procedure
- From the Red Hat Hybrid Cloud Console, click the Settings menu and click User Access.
- Click the Groups tab and click Create Group.
- Add a Group name and a Group description. The description is optional.
- Click Next to add roles to the group. For this example, find Automation Analytics viewer and click the checkbox next to the role name.
- Click Next to display Add members. Because you are adding a service account and not a member, click Next. Add service accounts appears.
- Choose the service account you want to add and click the checkbox next to the name.
- Click Next, review the details and if no changes are needed, click Submit. The new group is created that contains the service account and the Automation Analytics viewer role and permissions.
2.8.5. Creating cost management application roles
You can create a role that is specific to the cost management application. When you create a cost management role, you define cost management resource definitions for that role. Other application roles do not provide that choice.
Prerequisites
Cost management operator is installed and configured.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
- A minimum of one cloud integration is configured for cost management.
- You started the Create role wizard.
Procedure
This procedure describes how to create roles with cost management permissions from scratch.
- In the Create role window, click on the radio button Create a role from scratch.
- Enter a Role name (required) and a Role description (optional).
- Click the Next button to display the Add permissions window.
-
Enter
costin the Filter by application field to display the cost management application and click on the cost-management check box. - When the Add permissions window appears, click on the check box for each cost management permission to include in this role.
- Click on the Next button to display the Define Cost Management resources window.
- You will see a drop-down list of available Resource definitions for each application permission you added to the role. You must click on the check box for at least one resource in each cost management permission.
- Click the Next button to review details. You can click the Submit button to submit the role, the Back button to go back and make changes, or the Cancel button to cancel the action.
2.8.5.1. Cost management example for creating a role from scratch
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
- A minimum of one cloud integration is configured for cost management.
- You started the Create role wizard.
Procedure
- Start the Create role wizard and click on Create a role from scratch.
-
Enter
AWS Org Unit Cost Viewerfor Role name and then click the Submit button. A description is not required. -
Enter
costin the Filter by application field to display the cost management application and click on the cost-management check box. -
Click the check box on the line that contains
aws.organizational_unitand then click the Next button to display a drop-down list of available Resource definitions for the permission. - Click on the check box for at least one resource listed in the Resource definitions list and then click the Next button to review details.
- After you review the details for this role, which show the Permissions and Resource definitions, click the Submit button to submit the role.
2.8.6. Editing custom role names
You can change the name of a custom role from the main roles page or from the Permissions page.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
- One or more custom role must exist.
Procedure
-
Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Roles. The Roles window appears. In the Roles window, a custom role has
 (more options) to the right of its name.
(more options) to the right of its name.
-
Click
 (more options).
(more options).
- Click on Edit to change the role name or description.
Click on Delete to remove the custom role.
TipYou can also click on the role name to open the Permissions window and then click on the
 (more options) to the right of the role name to access the Edit and Delete actions.
(more options) to the right of the role name to access the Edit and Delete actions.
- A confirmation window appears. After you confirm that this action cannot be undone, the custom role is deleted.
2.8.7. Removing permissions from a custom role
You can remove permissions from a custom role.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
- One or more custom role must exist.
Procedure
-
Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Roles. The Roles window appears. In the Roles window, a custom role has
 (more options) to the right of its name.
(more options) to the right of its name.
- Click on a custom role name to open the Permissions window.
-
In the Permissions list, click the
 (more options) to the right of an application permission name and click Remove.
(more options) to the right of an application permission name and click Remove.
- A confirmation window appears. Click Remove permission.
2.8.8. Restoring the Default access group
You can restore the Default access group to its state as provided by Red Hat services. When you do so, the Custom default access group is removed along with any changes made to that group.
There is no way to recover the Custom default access group when you restore the Default access group.
Reasons to restore the Default access group:
- You made changes to the Default access group that were not intended.
- You want to start over with the Default access group.
- You want to remove the Custom default access group.
- You want to pick up changes to the the Default access group pushed out by Red Hat services and abandon the Custom default access group.
One of the default groups, either the Default access group or the Custom default access group, always exists on your system.
Prerequisites
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- If you are not an Organization Administrator, you must be a member of a group that has the User Access administrator role assigned to it.
- The Custom default access group must exist.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Groups. The Groups page is displayed.
- Click Custom default access on the Groups page.
-
Click Restore to default and accept the caution message.
Default access appears on the Groups page.
2.9. Creating a workspace
Use workspaces in the Hybrid Cloud Console to organize Red Hat Enterprise Linux (RHEL) systems in your inventory and apply access management rules to them.
You can create workspaces and view systems assigned to a workspace from the Identity & Access Management area in the Hybrid Cloud Console.
Configuring access management using workspaces is a feature in development available in Hybrid Cloud Console preview. See Previewing Hybrid Cloud Console features for information about using preview features.
Configuring workspaces does not affect the settings you configured in User Access.
Prerequisites
- You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
- If you are not an Organization Administrator, you must be a member of a group that has the Workspace administrator role assigned to it.
Procedure
- Navigate to Identity & Access Management > User Access > Workspaces.
- Click Create workspace.
Enter a Workspace name.
NoteIn the current version of workspaces, you can only set the default workspace as a parent.
- Optional: Enter a Workspace description.
- Click Next.
- Click Submit to create the workspace. The workspace you created is available in the Workspaces list.
- Optional: To add systems to a workspace or remove them from a workspace, navigate to RHEL > Inventory > Systems.
Chapter 3. How to enable Red Hat account team access for customer support
When a customer has a question about their account on the Red Hat Hybrid Cloud Console, they can grant temporary access to their account to a Red Hat associate, usually a Red Hat Technical Account Manager (TAM) or a Red Hat Customer Experience and Engagement support engineer. After the customer grants account access, the Red Hat TAM or support engineer can log in to the customer account and access the account information on the Red Hat Hybrid Cloud Console as though they were a member of the customer’s account.
For more information about Red Hat support services, see Red Hat Service offerings.
When a Red Hat Technical Account Manager (TAM) or a Red Hat Customer Experience and Engagement support engineer requests access to a customer account, what they can see and do is limited by which user access roles are assigned to the access request and is also limited to customer account information that is available on the Red Hat Hybrid Cloud Console.
For more information about default user access roles, see reference section, Predefined User Access roles.
3.1. Using the access request feature to provide access to a customer account
Direct access to a customer account can help resolve issues when screen shots and remote viewing sessions are not successful. By using the access request feature, the Red Hat support team collaborates with the customer who consents to the level of access and the duration of access.
In a typical situation, the customer opens a support case with the Red Hat support team. The Red Hat support team works with the customer to arrange access to the customer’s account and log in to their Red Hat Hybrid Cloud Console.
Make sure to verify the following information before beginning any access request actions:
- The customer account number.
- The duration of the access which includes a maximum duration up to 12 months.
- The default user access roles the customer wants granted to the Red Hat support team.
With the access request feature, system access is always controlled by the customer. The customer can deny access permissions at any time.
Any access request action is associated with the unique username of the Red Hat associate on the support team who made the request. This means each Red Hat access request is visible only to the Red Hat associate who made the request, and only that associate can access the customer system. If a different Red Hat support engineer is brought into the support case and needs access, a new access request action is required for that unique Red Hat username.
3.1.1. Approving access to your account
As a customer and Organization Administrator, you grant access to your account by approving the Red Hat access request. An access request notification popup appears briefly when the Organization Administrator is logged in and receives a request.
You can view a list of all account access requests for your system and the status of each from the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Red Hat Access Requests.
Only the Organization Administrator can approve or deny an access request. The User Access administrator role does not provide permissions to approve or deny an access request.
Prerequisites
Collaborate with a Red Hat support engineer and provide the following information so that the support engineer can create an access request request for your approval.
You are logged in to the Red Hat Hybrid Cloud Console as a user who has Organization Administrator permission.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
- Your Red Hat customer account number.
- A start date for system access.
- An end date for system access.
- An understanding of which user access roles the access request will grant to the Red Hat support engineer.
Procedure
- Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Red Hat Access Requests. A list of all access requests is displayed.
- The recommended approach is that you click on the Request ID number, a string of hexadecimal digits.
- Carefully review the request details and the Roles requested.
- Click Approve to approve the request. The action is confirmed and the status changes to Approved.
- Use the edit function to change your response.
3.1.2. Denying access to your account
As a customer and Organization Administrator, you deny access to your account by denying the Red Hat access request.
You can view a list of all account access requests and their statuses from the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > Red Hat Access Requests.
Only the Organization Administrator can approve or deny an access request. The User Access administrator role does not provide permissions to approve or deny an access request.
Prerequisites
- A Red Hat support engineer created an access request.
- The access request appears in the Red Hat Account Requests list.
Procedure
-
Navigate to the Red Hat Hybrid Cloud Console > Settings > Identity & Access Management > User Access > Red Hat Access Requests window.
A list of all access requests is displayed. - The recommended approach is that you click on the Request ID number, a string of hexadecimal digits.
- Carefully review the request details and the Roles requested.
- Click Deny to approve the request. The action is confirmed and the status changes to Denied.
- Use the edit function to change your response.
3.1.3. Requesting access to a customer account (Red Hat support team)
A member of the Red Hat support team uses the access request feature to gain access to a customer’s account . After receiving the access request, the customer can approve or deny the request.
The access request feature is available only to Red Hat associates who have a validated Red Hat associate user account. The access request feature is not visible to a non-associate. This information is provided as an aid to Red Hat Technical Account Manager (TAM) or a Red Hat Customer Experience and Engagement support engineer, and to enhance the communications of requirements between the customer and the Red Hat support team member.
Prerequisites
Make sure to verify the following information before beginning any access request actions.
- The customer account number
- The customer organization ID
- The duration of the access which includes a maximum duration up to 12 months
- The user access roles the customer wants granted to the Red Hat support team
Procedure
Use one of the following methods to obtain the customer organization ID:
- Ask the customer to provide it.
On the Red Hat Subscription Admin page, search by the customer account number.
NoteYou must be a Red Hat associate on the Red Hat VPN to view the Red Hat Subscription Admin page.
- Log in to the Red Hat Hybrid Cloud Console.
- Click your user avatar in the upper right of the Red Hat Hybrid Cloud Console window. A drop-down list appears.
- On the drop-down list, click Internal.
- After the Internal window appears, click Access Requests.
- Click Create request. A wizard guides you through the steps.
- After you create an access request, and before the customer approves or denies the request, you can edit the request or cancel the request.
Verification
A list of accounts to which you have access appears in a context switcher in the masthead of your Red Hat Hybrid Cloud Console account. This list includes your personal account.
When you choose another account from the context switcher, a banner appears in your Red Hat Hybrid Cloud Console window, for example, "Viewing as account 654321."
The Access Requests window shows the status of all access requests that you submitted. Account requests are linked to your username and are unique to you. No other Red Hat associate can view or act on the requests that you created.
Chapter 4. Predefined User Access roles
The following table lists the predefined roles provided with User Access. Some of the predefined roles are included in the Default access group, which includes all authenticated users in your organization.
Only the Organization Administrator users in your organization inherit the roles in the Default admin access group. Because this group is provided by Red Hat, it is updated automatically when Red Hat assigns roles to the Default admin access group.
For more information about viewing predefined roles, see Chapter 2, Procedures for configuring User Access.
- NOTE
- Predefined roles are updated and modified by Red Hat and cannot be modified. The table might not contain all currently available predefined roles.
| Role name | Description | Default access group | Default admin access group |
|---|---|---|---|
| Ansible Lightspeed administrator | Perform read operations for Organization Administrators on all Lightspeed charts. | X | |
| Automation Analytics administrator | Perform any available operation on Automation Analytics resources. | ||
| Automation Analytics editor | Perform read and update operations on Automation Analytics resources. | X | |
| Automation Analytics viewer | Perform read operations on Automation Analytics resources. | ||
| Cloud administrator | Perform any available operation on any source. | X | |
| Compliance administrator | Perform any available operation on Compliance resources. | X | |
| Compliance viewer | Perform read operations on Compliance resources. | X | |
| Content Template administrator | Perform any available operation on any Content Template resource. | X | |
| Content Template viewer | Perform read-only operations on Content Template resources. | X | |
| Cost OpenShift viewer | Perform read operations on cost reports related to OpenShift sources. | ||
| Cost Price List administrator | Perform read and write operations on cost models. | ||
| Cost Price List viewer | Perform read operations on cost models. | ||
| Cost administrator | Perform any available operation on cost management resources. | X | |
| Cost cloud viewer | Perform read operations on cost reports related to cloud sources. | ||
| Directory and Domain Services administrator | Create, read, update and delete Directory and Domains Services registrations. | X | |
| Directory and Domain Services viewer | Read Directory and Domains Services registrations. | X | |
| Hybrid Committed Spend viewer | Perform read operations on any Hybrid Committed Spend report. | ||
| Inventory Hosts administrator | Perform read and update operations on Inventory Hosts data. | X | X |
| Inventory Hosts viewer | Perform read operations on Inventory Hosts data. | ||
| Inventory administrator | Perform any available operation on any Inventory resource. | ||
| Launch administrator | Perform read and update operations on launch reservation and related resources. | X | |
| Launch on AWS user | Perform update operations on AWS launch reservation and related resources. | ||
| Launch on Azure user | Perform update operations on Azure launch reservation and related resources. | ||
| Launch on Google Cloud user | Perform update operations on Google Cloud launch reservation and related resources. | ||
| Launch viewer | Perform read operations on launch reservation and related resources. | X | |
| Malware detection administrator | Perform any available operation on any malware-detection resource. | X | |
| Malware detection editor | Read any malware-detection resource as well as set malware acknowledgements. | ||
| Malware detection viewer | Perform read operations on any malware-detection resource. | ||
| Notifications administrator | Perform any available operation on notifications and integrations resources. | X | |
| Notifications viewer | Perform read operations on notifications and integrations resources. | X | |
| OCM IdP editor | Perform update operations on IdPs. | ||
| OCM Organization Administrator | Perform all available operations on the associated organization’s clusters. | ||
| OCM cluster autoscaler editor | Perform update operations on the cluster autoscaler. | ||
| OCM cluster editor | Perform update operations on clusters. | ||
| OCM cluster provisioner | Perform provision operations on clusters. | X | |
| OCM cluster viewer | Perform read operations on clusters. | X | |
| OCM machine pool editor | Perform update operations on machine pools. | ||
| OCP Advisor administrator | Perform any available operation on any OCP Advisor resource. | X | |
| Organization staleness and deletion administrator | Perform read and update operations on organization staleness and deletion data. | X | |
| Organization staleness and deletion viewer | Perform read operations on organization staleness and deletion data. | X | |
| Patch administrator | Perform any available operation on any Patch resource. | X | |
| Patch viewer | Perform read operations on any Patch resource. | X | |
| Policies administrator | Perform any available operation on any Policies resource. | X | |
| Policies viewer | Perform read operation on any Policies resource. | X | |
| RHC administrator | Perform any available operation on RHC manager resources. | X | |
| RHC user | Perform read operations on the current configurations on RHC manager and update actions to the activation keys. | X | |
| RHEL administrator | Grants full access to RHEL system configs, inventory, compliance, notifications, patch management, remediations, malware detection, and advisor. View/modify vulnerability settings. | ||
| RHEL operator | Grants read-only access to RHEL Insights. Users can view system configs, compliance reports, inventory data, patch info, vulnerabilities and more to observe the state of resources/activities, but can’t perform actions other than generating activation keys. | ||
| RHEL viewer | Grants read-only access to RHEL Insights. Users can view system configs, compliance reports, inventory data, patch info, vulnerabilities and more to observe the state of resources/activities, but can’t perform actions other than generating activation keys. | ||
| RHEL Advisor administrator | Perform any available operation on any RHEL advisor resource. | X | |
| RHEL Advisor viewer | Perform read operations on RHEL advisor data. | ||
| Remediations administrator | Perform any available operation on any Remediations resource | ||
| Remediations user | Perform create, read, update, delete operations on any Remediations resource. | X | |
| Repositories administrator | Perform any available operation on any repositories resource. | X | |
| Repositories uploader | Perform content upload to repositories. | ||
| Repositories viewer | Perform read operations on repositories resources. | X | |
| Resource Optimization administrator | Perform any available operation on any Resource Optimization resource. | X | |
| Resource Optimization user | Perform read operations on any Resource Optimization resource. | X | |
| Subscriptions administrator | Perform any available operation on any Subscriptions resource. | X | |
| Subscriptions viewer | Perform read operations on any Subscriptions resource. | X | assembly-insights-rbac-reference.adoc |
| Tasks administrator | Perform any available operation on any Tasks resource. | X | |
| User Access administrator | Perform any available operation for a non-Organization Administrator to configure and manage user access to services hosted on console.redhat.com. This role can only be viewed and assigned by Organization Administrators. | X | |
| User Access principal viewer | Perform read operations as a non-Organization Administrator on principals within user access. | ||
| Vulnerability administrator | Perform any available operation on any Vulnerability resource. | X | |
| Vulnerability viewer | Perform read operations on any Vulnerability resource. | X | |
| Workspace administrator | Perform read and update operations on Workspace data. | X | |
| Workspace viewer | Perform read operations on Workspace data. |
Providing feedback on Red Hat documentation
We appreciate your feedback on our documentation. Provide as much detail as possible so that your request can be addressed.
Prerequisites
- You have a Red Hat account.
You are logged in to your Red Hat account.
NoteYou cannot log in to the Hybrid Cloud Console with your email address unless your email address is the same as your Red Hat login. For more information, see Finding your login.
Procedure
- To provide your feedback, click the following link: Create Issue
- Describe the issue or enhancement in the Summary text box.
- Provide more details about the issue or enhancement in the Description text box.
- If your Red Hat user name does not automatically appear in the Reporter text box, enter it.
- Scroll to the bottom of the page and then click the Create button. A documentation issue is created and routed to the appropriate documentation team. Thank you for taking the time to provide feedback.