Chapter 2. Common Vulnerabilities and Exposures (CVEs)
Common Vulnerabilities and Exposures (CVEs) are security vulnerabilities identified in publicly released software packages. CVEs are identified and listed by the National Cybersecurity FFRDC (NCF), the federally funded research and development center operated by the Mitre Corporation, with funding from the National Cyber Security Division of the United States Department of Homeland Security. The complete list of CVEs is available at https://cve.mitre.org.
By highlighting CVEs with publicly known exploits and security rules associated with CVEs, the vulnerability service surfaces enhanced threat intelligence to aid in determining which CVEs pose the greatest potential risk to RHEL environments, enabling our users to effectively prioritize and address their most critical issues first.
The vulnerability service does not contain every CVE included in the list of entries at https://cve.mitre.org. Only Red Hat CVEs, those CVEs for which Red Hat issues security advisories (RHSAs), are included in the vulnerability service.
The vulnerability service identifies CVEs impacting your RHEL systems, indicates the severity and enables you to efficiently triage the exposures that are most critical to resolve. The dashbar will alert you to the following types of CVEs:
- Known exploits
- Security rules
- Critical severity
- Important severity
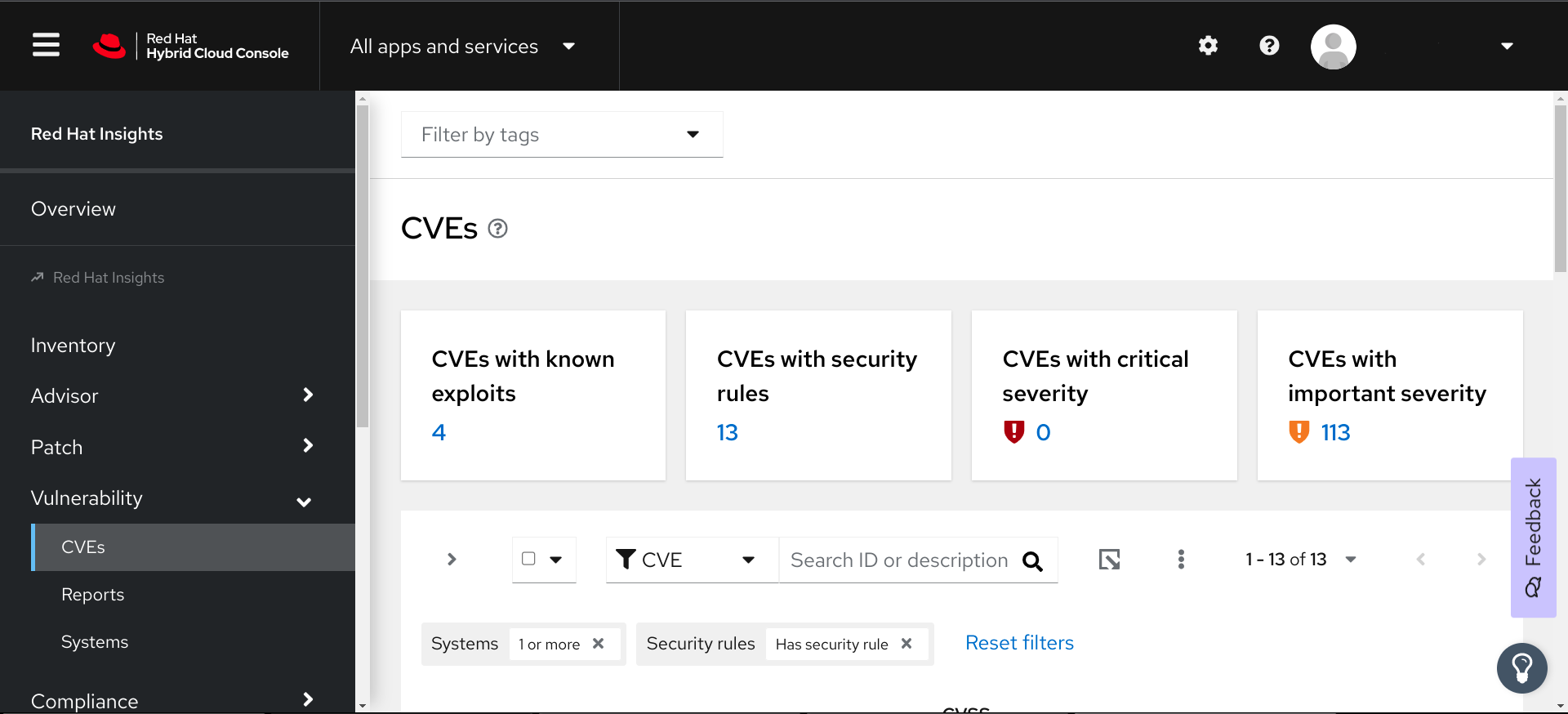
2.1. Red Hat Security Advisories (RHSAs)
Red Hat Security Advisory (RHSA) errata document security vulnerabilities in Red Hat products for which there are remediations or mitigations available. The Red Hat Insights for Red Hat Enterprise Linux vulnerability service displays the advisory identifier tied to each system exposed to a CVE.
View this information by selecting a CVE and selecting the Filter by affected systems link in the security rule card. If an advisory exists for the system, the RHSA ID is visible as a link next to the system in the Exposed systems list, Advisory column. When there are no such advisories, the Advisory column is not visible, or will show “Not available.”
When an advisory exists for a system, users can view more information about the RHSA, including a list of affected systems. In the patch service, users can select systems to create an Ansible Playbook to apply the remediation.
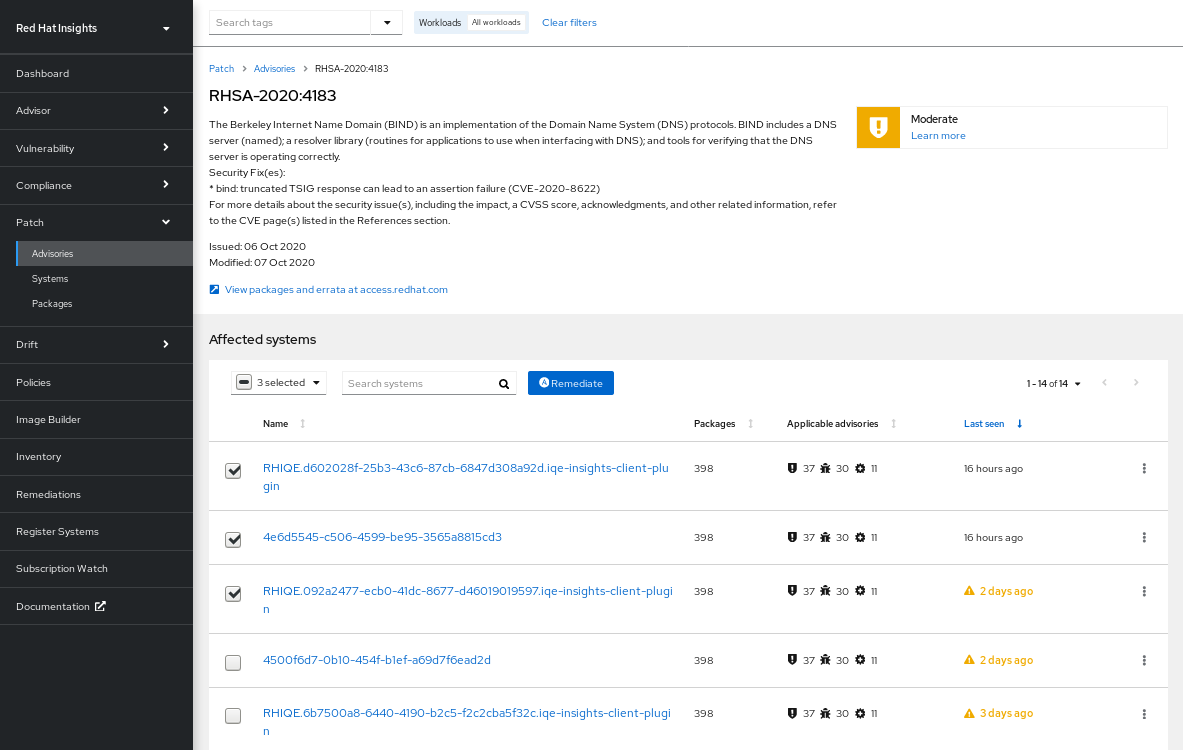
2.2. Security rules
Security rules are CVEs given additional visibility due to the elevated risk and exposure associated with them. These are security flaws that may receive significant media coverage and have been scrutinized by the Red Hat Product Security team, using the Product Security Incident Response Plan workflow to help determine your RHEL environment exposure. These security rules enable you to take the appropriate action to protect your organization.
Security rules provide deep threat intelligence, beyond analyzing the version of RHEL running on a system. Security rules are manually curated to determine whether you are susceptible to a security threat by analyzing system metadata collected by the Insights client. If the vulnerability service identifies a system as exposed to a security rule, there is the potential for elevated security risk and issues should be addressed with urgency.
Addressing security rules on exposed systems should be your highest priority.
Finally, not all systems exposed to a CVE are also exposed to a security rule associated with that CVE. Even though you may be running a vulnerable version of software, other environmental conditions may mitigate the threat; for example, a specific port is closed or if you are running SELinux.
2.2.1. Identifying security rules in the Insights for RHEL dashboard
Use the following steps to view your infrastructure exposure to security rules.
Procedure
Navigate to the Red Hat Insights for Red Hat Enterprise Linux dashboard.
NoteFor simplicity, panels for services not related to security vulnerability assessment are minimized in the following screenshot.
:
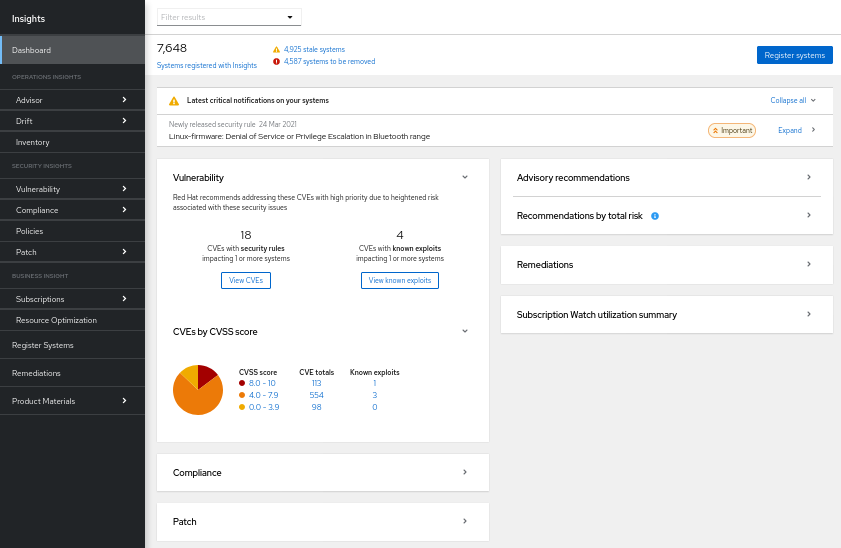
View the Latest critical notifications on your systems panel. These are security rules with an elevated severity rating of “Important” or “Critical.” These are potentially your most critical issues and should be prioritized for remediation.
To the right of each notification, click the Expand button to see associated CVEs and the number of systems exposed in your infrastructure.
NoteYou may see security rules in your critical notifications but have zero systems exposed. In this case, even though the CVE is present in your infrastructure, the security rule conditions may not exist.
- Below the name of the security rule, and under Associated CVEs, click the CVE ID link.
- View which of your systems is impacted by the security rule CVE and optionally select exposed systems to create playbooks.
Next, view the information in the vulnerability card.
Note the number of “CVEs with security rules impacting systems.” This number includes security rules of any severity impacting at least one system.
- Click View CVEs. Consider lesser-severity security rules your second highest priority for remediation, following high-severity security rules.
2.3. Known exploits
Red Hat analyzes Metasploit data to determine whether code exists publicly to exploit a CVE, or a CVE has already been exploited publicly. The vulnerability service applies the “Known exploits” label to CVEs that meet that criteria.
This enhanced threat assessment can help users identify and address those CVEs that pose the most critical risks first. Red Hat recommends users review any CVEs with the “Known exploit” label with high priority and work towards remediating those issues.
The vulnerability service makes you aware that the known-exploit CVE exists on systems in your infrastructure. The “Known exploits” label does not mean that the vulnerability was exploited on your RHEL systems; the vulnerability service does not make that determination.
2.4. Common Vulnerabilities and Exposures provide deep threat intelligence with triage feature
The vulnerability service provides you with data about individual Common Vulnerabilities and Exposures (CVEs) and their effect on your systems registered to Insights. CVEs are categorized as vulnerable or affected but not vulnerable. This level of threat intelligence is available for CVEs that have the Security Rule label or for those that have gone through Red Hat Product Security’s rigorous analysis.
This increased threat intelligence enables you to triage issues and address the most urgent ones first. When managing a large fleet of servers, this translates into expedited protection and significant efficiencies.
An affected but not vulnerable CVE status indicates that you are running software that has a vulnerability in it but is not currently exploitable. This system will need remediation but does not require immediate attention.
A vulnerable CVE status indicates flawed code with an open path to exploitation. An open path could be a port or an OS version that permits one of the following: confidential information to be leaked, the integrity of the system to be compromised or availability of the system to be hindered.
Let us look at an example of a vulnerable server versus an affected but not vulnerable server:
Suppose that Server A is running vulnerable software that allows root access to the system. Server A would be considered vulnerable and require immediate patching.
In contrast, suppose that Server B’s current configuration prevents the vulnerability from manifesting, even when present in the affected code. Server B would be considered affected but not vulnerable. This would mean that Server B could be relegated to the to-do list, so that the more immediate threat, Server A could be remediated.
You should patch Server B once Server A has been addressed since it is running potentially vulnerable code. Version updates and other events could render it vulnerable in the future.
2.4.1. Identifying known-exploit CVEs in the Red Hat Insights for RHEL dashboard
Use the following steps to identify known-exploit CVEs in the Insights for Red Hat Enterprise Linux dashboard vulnerability card.
Procedure
Navigate to the Red Hat Insights for Red Hat Enterprise Linux dashboard.
NoteFor simplicity, panels for services not related to security vulnerability assessment are minimized in the following screenshot.
:

- On the Vulnerability card, note the CVEs with Known exploits impacting 1 or more systems and the number displayed.
- Click View Known exploits.
- View the filtered list of Known-exploit CVEs in the CVEs list.