Chapter 7. System filtering and groups
Red Hat Insights for Red Hat Enterprise Linux enables you to filter systems in inventory, as well as by individual service. Insights for Red Hat Enterprise Linux also allows you to filter groups of systems by three criteria:
- Groups running SAP workloads
- Satellite host groups
- Custom filters that you define in a YAML file
As of Spring 2022, inventory, advisor, compliance, vulnerability, patch, drift, and policies enable filtering by groups and tags. Other services will follow.
Use the global Filter Results box to filter by SAP workloads, Satellite host groups, or custom filters added to the Insights client configuration and file filters added to the Insights client configuration file.
Prerequisites
- The Insights client is installed and registered on each system.
- Root-level permissions on the system.
7.1. SAP workloads
As Linux becomes the mandatory operating system for SAP ERP workloads in 2025, Red Hat Enterprise Linux and Red Hat Insights for Red Hat Enterprise Linux are working to make Insights for Red Hat Enterprise Linux the management tool of choice for SAP administrators.
As part of this ongoing effort, Insights for Red Hat Enterprise Linux automatically tags systems running SAP workloads and by SAP ID (SID), without any customization needed by administrators. To filter those workloads throughout the Insights for Red Hat Enterprise Linux application, use the global Filter Results drop-down menu.
7.2. Satellite host groups
Satellite host groups are configured in Satellite and automatically recognized by Insights for Red Hat Enterprise Linux.
7.3. Custom system tagging
You can apply custom grouping and tagging to your systems. This enables you to add contextual markers to individual systems, filter by those tags in the Insights for Red Hat Enterprise Linux application, and more easily focus on related systems. This functionality can be especially valuable when deploying Insights for Red Hat Enterprise Linux at scale, with many hundreds or thousands of systems under management.
In addition to the ability to add custom tags to several Insights for Red Hat Enterprise Linux services, you can add predefined tags. The advisor service can use these tags to create targeted recommendations for your systems that might require more attention, such as those systems that require a higher level of security.
7.3.1. Filter structure
Filters use a namespace=value or key=value paired structure.
-
Namespace. The namespace is the name of the ingestion point, insights-client. This value cannot be changed. The
tags.yamlfile is abstracted from the namespace, which is injected by the client before upload. - Key. You can create the key or use a predefined key from the system. You can use a mix of capitalization, letters, numbers, symbols and whitespace.
- Value. You can define your own descriptive string value. You can use a mix of capitalization, letters, numbers, symbols and whitespace.
7.3.2. Creating a custom group and the tags.yaml file
To create and add tags to /etc/insights-client/tags.yaml, use insights-client with the --group=<name-you-choose> option. This command option performs the following actions:
-
Creates the
etc/insights-client/tags.yamlfile -
Adds the
group=key and<name-you-choose>value totags.yaml - Uploads a fresh archive from the system to the Insights for Red Hat Enterprise Linux application making the new tag immediately visible along with your latest results
Prerequisites
- Root-level access to your system.
Procedure
Run the following command as root, adding your custom group name in place of
<name-you-choose>:[root@server ~]# insights-client --group=<name-you-choose>
-
Optional. To add additional tags, edit the
/etc/insights-client/tags.yamlfile. - Navigate to Inventory > Systems and log in if necessary.
- Click the Filter by tags drop-down menu. You can also use the search box to enter all or part of the tag’s name to automatically show systems with that text in the tags.
- Scroll up or down the list to locate the tag.
- Click the tag to filter by it.
Verify that your system is among the results on the advisor systems list.
- Navigate to Inventory > Systems and log in if necessary.
- Activate the Name filter and begin typing the system name until you see your system, then select it.
- The tag symbol is a darker color, and the number beside it shows the correct number of tags applied.
7.3.3. Editing tags.yaml to add or change tags
After you create the group tag, you can edit the contents of tags.yaml to add or modify tags.
The following procedure shows how to edit the /etc/insights-client/tags.yaml file, then verify the tag exists in the Red Hat Insights > RHEL > Inventory.
Prerequisites
- Root-level access to your system.
Procedure
Open the tag configuration file,
tags.yaml, in an editor.[root@server ~]# vim /etc/insights-client/tags.yaml
Edit the file contents or add additional
key=valuepairs. Add additionalkey=valuepairs if needed. Use a mix of capitalization, letters, numbers, symbols, and whitespace. The following example shows how to organizetags.yamlwhen adding more than one tag to a system.# tags --- group: _group-name-value_ location: _location-name-value_ description: - RHEL8 - SAP key 4: value
- Save your changes and close the editor.
Generate an upload to Insights for Red Hat Enterprise Linux.
[root@server ~]# insights-client
- Navigate to Inventory > Systems and log in if necessary.
In the Filter Results box, click the down arrow and select one of the filters or enter the name of the filter and select it.
NoteYou can search by the tag key or by its value.
- Find your system among the results.
- Verify that the filter icon is darkened and shows a number representing the number of filters applied to the system.
7.4. Using predefined system tags to get more accurate Red Hat Insights advisor service recommendations and enhanced security
Red Hat Insights advisor service recommendations treat every system equally. However, some systems might require more security than others, or require different networking performance levels. In addition to the ability to add custom tags, Red Hat Insights for Red Hat Enterprise Linux provides predefined tags that the advisor service can use to create targeted recommendations for your systems that might require more attention.
To opt in and get the extended security hardening and enhanced detection and remediation capabilities offered by predefined tags, you need to configure the tags. After configuration, the advisor service provides recommendations based on tailored severity levels, and preferred network performance that apply to your systems.
To configure the tags, use the /etc/insights-client/tags.yaml file to tag systems with predefined tags in a similar way that you might use it to tag systems in the inventory service. The predefined tags are configured using the same key=value structure used to create custom tags. Details about the Red Hat-predefined tags are in the following table.
| Key | Value | Note |
|---|---|---|
| security |
|
With the |
|
|
| The preferred network performance (either latency or throughput according to your business requirement) would affect the severity of an advisor service recommendation to a system. |
The predefined tag keys names are reserved. If you already use the key security, with a value that differs from one of the predefined values, you will not see a change in your recommendations. You will only see a change in recommendations if your existing key=value is the same as one of the predefined keys. For example, if you have a key=value of security: high, your recommendations will not change because of the Red Hat-predefined tags. If you currently have a key=value pair of security: strict, you will see a change in the recommendations for your systems.
Additional resources
7.4.1. Configuring predefined tags
You can use the Red Hat Insights for Red Hat Enterprise Linux advisor service’s predefined tags to adjust the behavior of recommendations for your systems to gain extended security hardening and enhanced detection and remediation capabilities. You can configure the predefined tags by following this procedure.
Prerequisites
- You have root-level access to your system
- You have Insights client installed
- You have systems registered within the Insights client
-
You have already created the
tags.yamlfile. See Creating a tags.yaml file and adding a custom group
Procedure
Using the command line, and your preferred editor, open
/etc/insights-client/tags.yaml. (The following example uses Vim.)[root@server ~]# vi /etc/insights-client/tags.yaml
Edit the
/etc/insights-client/tags.yamlfile to add the predefinedkey=valuepair for the tags. This example shows how to addsecurity: strictandnetwork_performance: latencytags.# cat /etc/insights-client/tags.yaml group: redhat location: Brisbane/Australia description: - RHEL8 - SAP security: strict network_performance: latency
- Save your changes.
- Close the editor.
Optional: Run the
insights-clientcommand to generate an upload to Red Hat Insights for Red Hat Enterprise Linux, or wait until the next scheduled Red Hat Insights upload.[root@server ~]# insights-client
Confirming that predefined tags are in your production area
After generating an upload to Red Hat Insights (or waiting for the next scheduled Insights upload), you can find out whether the tags are in the production environment by accessing Red Hat Insights > RHEL > Inventory. Find your system and look for the newly created tags. You see a table that shows:
- Name
- Value
- Tag Source (for example, insights-client).
The following image shows an example of what you see in inventory after creating the tag.
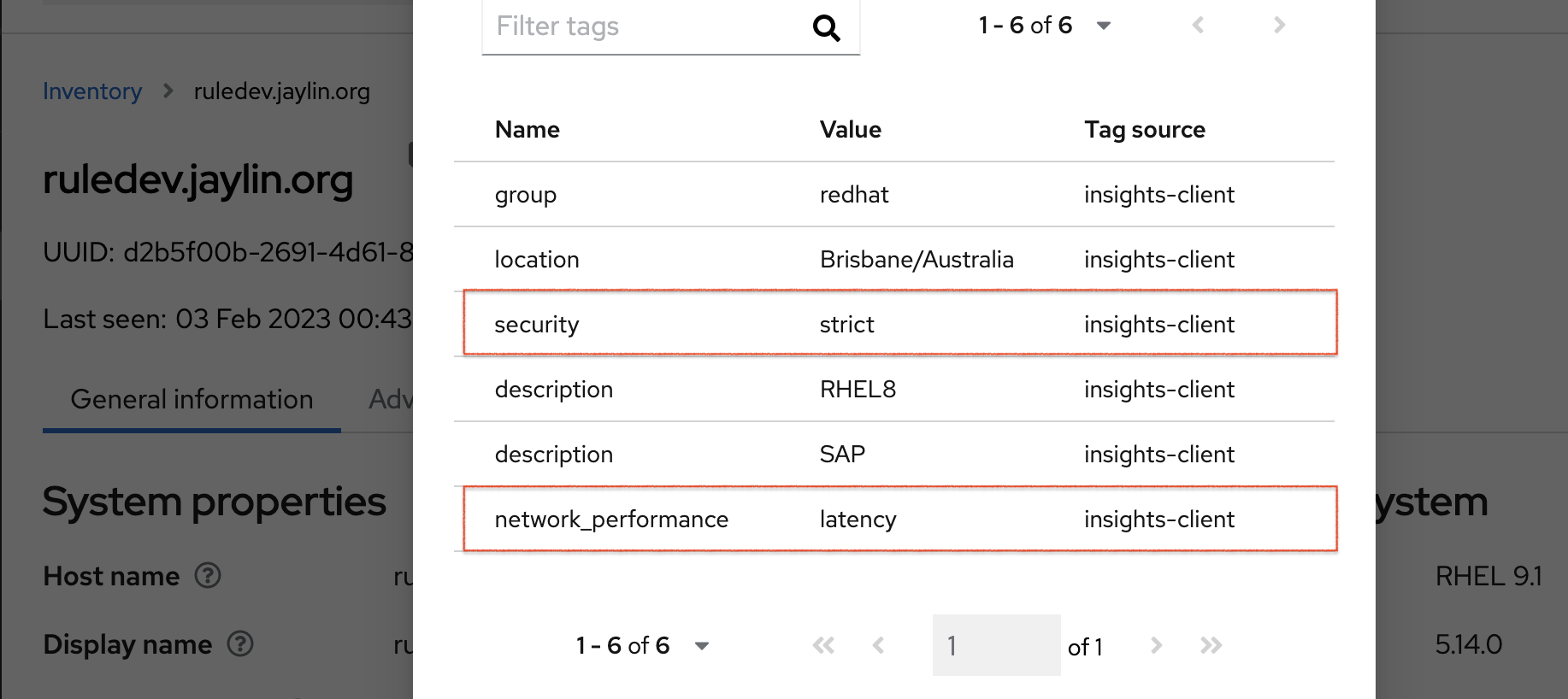
Example of recommendations after applying a predefined tag
The following image of the advisor service shows a system with the network_performance: latency tag configured.
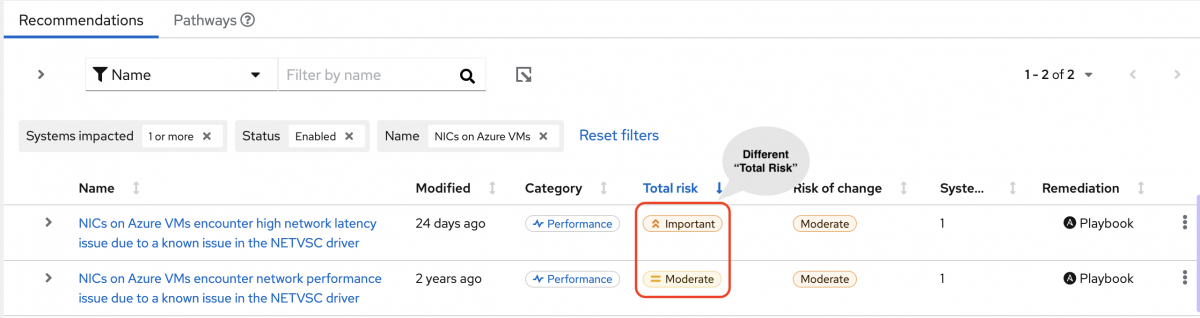
The system shows a recommendation with a higher Total Risk level of Important. The system without the network_performance: latency tag has a Total Risk of Moderate. You can make decisions about prioritizing the system with higher Total Risk.