Chapter 7. Viewing and exporting logs
Activity logs are gathered for all repositories and namespace in Quay.io.
Viewing usage logs of Quay.io. can provide valuable insights and benefits for both operational and security purposes. Usage logs might reveal the following information:
- Resource Planning: Usage logs can provide data on the number of image pulls, pushes, and overall traffic to your registry.
- User Activity: Logs can help you track user activity, showing which users are accessing and interacting with images in the registry. This can be useful for auditing, understanding user behavior, and managing access controls.
- Usage Patterns: By studying usage patterns, you can gain insights into which images are popular, which versions are frequently used, and which images are rarely accessed. This information can help prioritize image maintenance and cleanup efforts.
- Security Auditing: Usage logs enable you to track who is accessing images and when. This is crucial for security auditing, compliance, and investigating any unauthorized or suspicious activity.
- Image Lifecycle Management: Logs can reveal which images are being pulled, pushed, and deleted. This information is essential for managing image lifecycles, including deprecating old images and ensuring that only authorized images are used.
- Compliance and Regulatory Requirements: Many industries have compliance requirements that mandate tracking and auditing of access to sensitive resources. Usage logs can help you demonstrate compliance with such regulations.
- Identifying Abnormal Behavior: Unusual or abnormal patterns in usage logs can indicate potential security breaches or malicious activity. Monitoring these logs can help you detect and respond to security incidents more effectively.
- Trend Analysis: Over time, usage logs can provide trends and insights into how your registry is being used. This can help you make informed decisions about resource allocation, access controls, and image management strategies.
There are multiple ways of accessing log files:
- Viewing logs through the web UI.
- Exporting logs so that they can be saved externally.
- Accessing log entries using the API.
To access logs, you must have administrative privileges for the selected repository or namespace.
A maximum of 100 log results are available at a time via the API. To gather more results that that, you must use the log exporter feature described in this chapter.
7.1. Viewing logs using the UI
Use the following procedure to view log entries for a repository or namespace using the web UI.
Procedure
- Navigate to a repository or namespace for which you are an administrator of.
In the navigation pane, select Usage Logs.
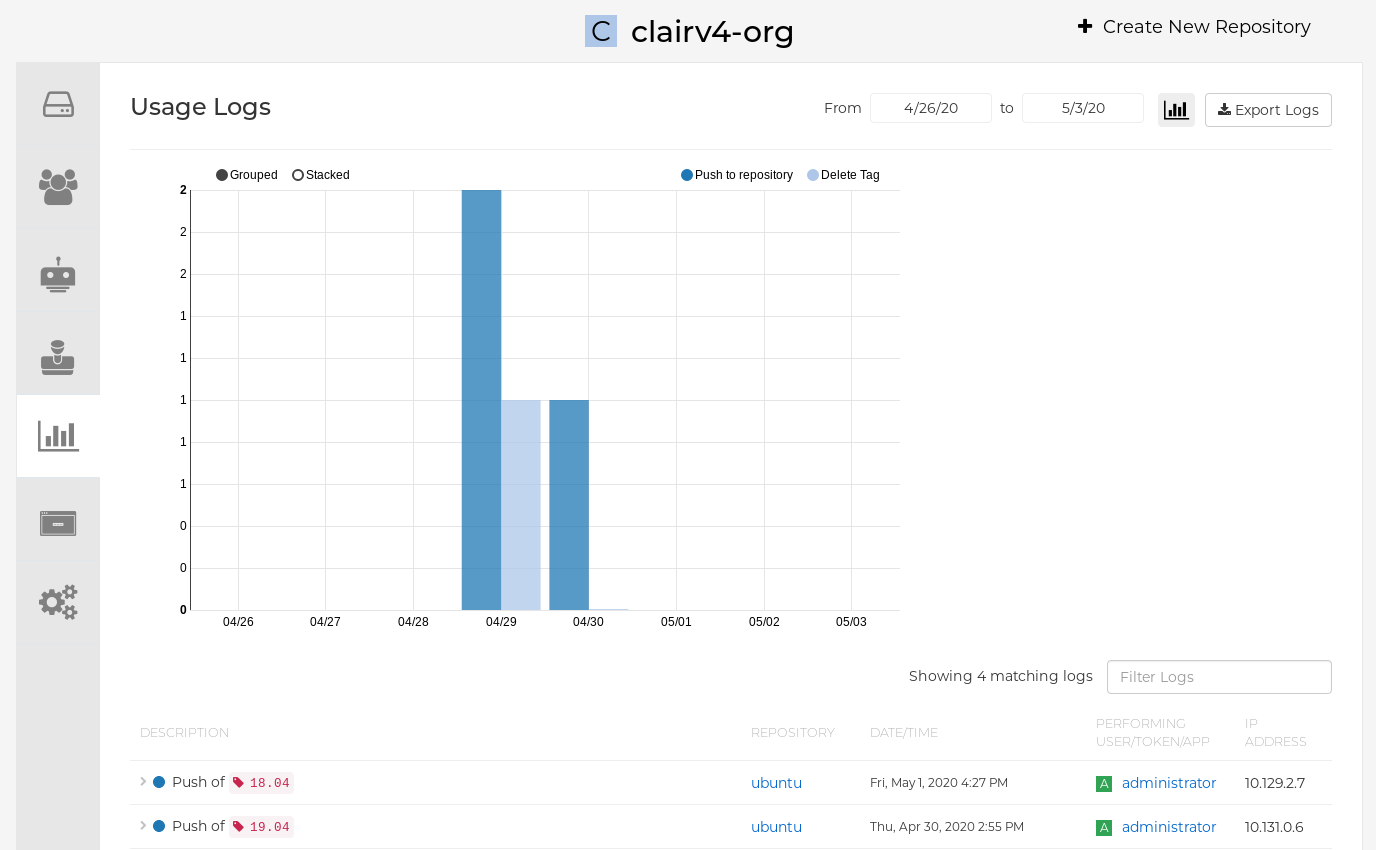
Optional. On the usage logs page:
- Set the date range for viewing log entries by adding dates to the From and to boxes. By default, the UI shows you the most recent week of log entries.
-
Type a string into the Filter Logs box to display log entries that of the specified keyword. For example, you can type
deleteto filter the logs to show deleted tags. - Under Description, toggle the arrow of a log entry to see more, or less, text associated with a specific log entry.
7.2. Exporting repository logs
You can obtain a larger number of log files and save them outside of Quay.io by using the Export Logs feature. This feature has the following benefits and constraints:
- You can choose a range of dates for the logs you want to gather from a repository.
- You can request that the logs be sent to you by an email attachment or directed to a callback URL.
- To export logs, you must be an administrator of the repository or namespace.
- 30 days worth of logs are retained for all users.
- Export logs only gathers log data that was previously produced. It does not stream logging data.
- When logs are gathered and made available to you, you should immediately copy that data if you want to save it. By default, the data expires after one hour.
Use the following procedure to export logs.
Procedure
- Select a repository for which you have administrator privileges.
- In the navigation pane, select Usage Logs.
- Optional. If you want to specify specific dates, enter the range in the From and to boxes.
Click the Export Logs button. An Export Usage Logs pop-up appears, as shown
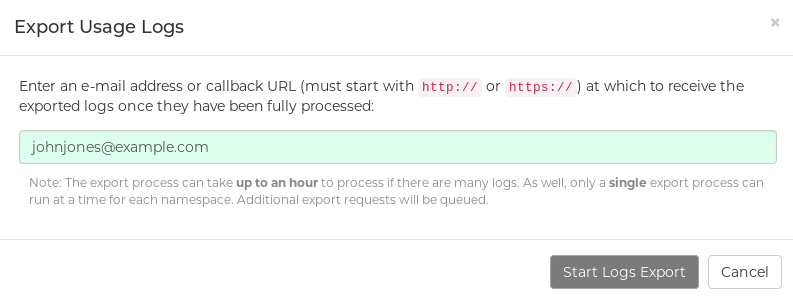
- Enter an email address or callback URL to receive the exported log. For the callback URL, you can use a URL to a specified domain, for example, <webhook.site>.
- Select Start Logs Export to start the process for gather the selected log entries. Depending on the amount of logging data being gathered, this can take anywhere from a few minutes to several hours to complete.
When the log export is completed, the one of following two events happens:
- An email is received, alerting you to the available of your requested exported log entries.
- A successful status of your log export request from the webhook URL is returned. Additionally, a link to the exported data is made available for you to delete to download the logs.