Managing access and permissions
Managing access and permissions
Abstract
Preface
Red Hat Quay offers a comprehensive permissions model, which allows administrators the ability to control who can access, manage, and modify repositories at a granular level. The following sections show you how to manage user access, define team roles, set permissions for users and robot accounts, and define the visibility of a repository. These guides include instructions using both the Red Hat Quay UI and the API.
The following topics are covered:
- Role-based access controls
- Adjusting repository visibility
- Creating and managing robot accounts
- Clair vulnerability reporting
Chapter 1. Red Hat Quay permissions model
Red Hat Quay’s permission model provides fine-grained access control over repositories and the content of those repositories, helping ensure secure collaboration and automation. Red Hat Quay administrators can grant users and robot accounts one of the following levels of access:
- Read: Allows users, robots, and teams to pull images.
- Write: Allows users, robots, and teams to push images.
- Admin: Provides users, robots, and teams administrative privileges.
Administrative users can delegate new permissions for existing users and teams, change existing permissions, and revoke permissions when necessary
Collectively, these levels of access provide users or robot accounts the ability to perform specific tasks, like pulling images, pushing new versions of an image into the registry, or managing the settings of a repository. These permissions can be delegated across the entire organization and on specific repositories. For example, Read permissions can be set to a specific team within the organization, while Admin permissions can be given to all users across all repositories within the organization.
1.1. Red Hat Quay teams overview
In Red Hat Quay a team is a group of users with shared permissions, allowing for efficient management and collaboration on projects. Teams can help streamline access control and project management within organizations and repositories. They can be assigned designated permissions and help ensure that members have the appropriate level of access to their repositories based on their roles and responsibilities.
1.1.1. Setting a team role by using the UI
After you have created a team, you can set the role of that team within the Organization.
Prerequisites
- You have created a team.
Procedure
- On the Red Hat Quay landing page, click the name of your Organization.
- In the navigation pane, click Teams and Membership.
Select the TEAM ROLE drop-down menu, as shown in the following figure:
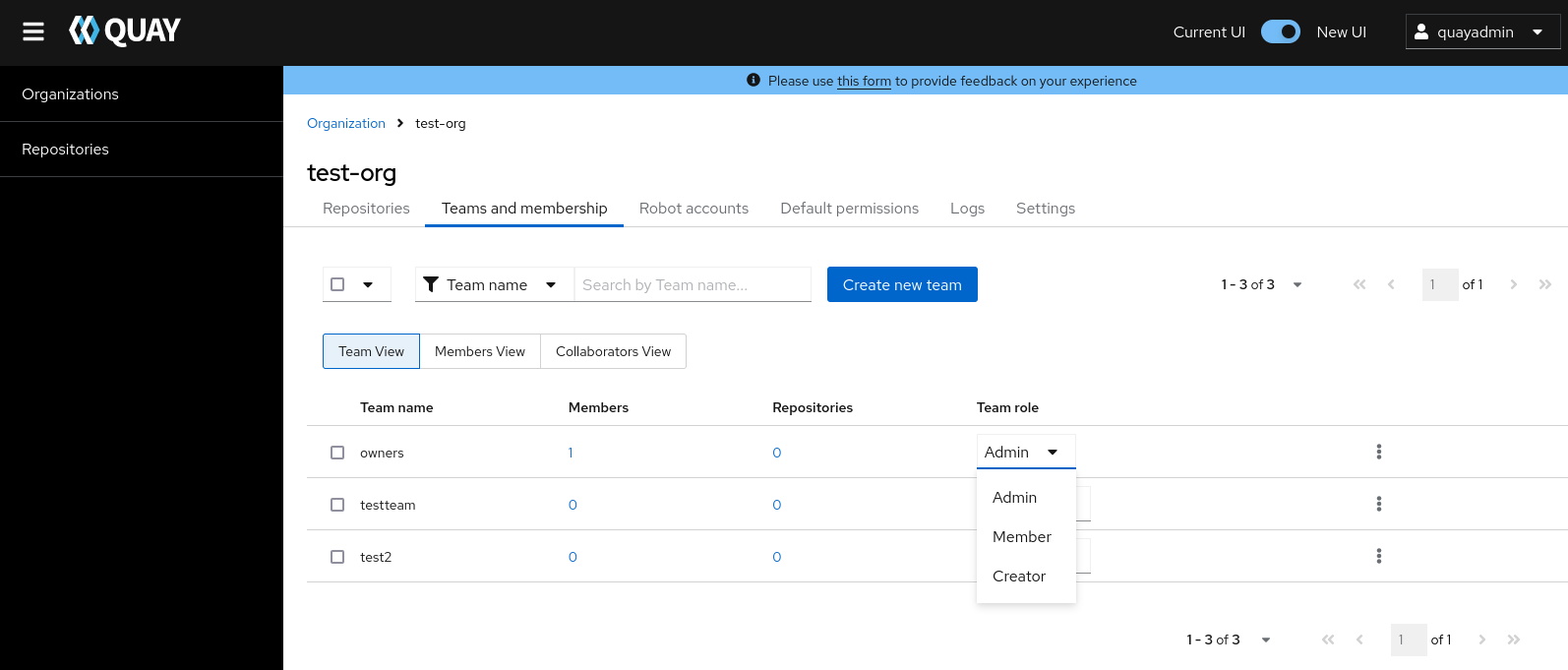
For the selected team, choose one of the following roles:
- Admin. Full administrative access to the organization, including the ability to create teams, add members, and set permissions.
- Member. Inherits all permissions set for the team.
- Creator. All member permissions, plus the ability to create new repositories.
1.1.1.1. Managing team members and repository permissions
Use the following procedure to manage team members and set repository permissions.
On the Teams and membership page of your organization, you can also manage team members and set repository permissions.
- Click the kebab menu, and select one of the following options:
- Manage Team Members. On this page, you can view all members, team members, robot accounts, or users who have been invited. You can also add a new team member by clicking Add new member.
Set repository permissions. On this page, you can set the repository permissions to one of the following:
- None. Team members have no permission to the repository.
- Read. Team members can view and pull from the repository.
- Write. Team members can read (pull) from and write (push) to the repository.
- Admin. Full access to pull from, and push to, the repository, plus the ability to do administrative tasks associated with the repository.
- Delete. This popup windows allows you to delete the team by clicking Delete.
1.1.2. Setting the role of a team within an organization by using the API
Use the following procedure to view and set the role a team within an organization using the API.
Prerequisites
- You have Created an OAuth access token.
Procedure
Enter the following
GET /api/v1/organization/{orgname}/team/{teamname}/permissionscommand to return a list of repository permissions for the organization’s team. Note that your team must have been added to a repository for this command to return information.curl -X GET \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/permissions"
$ curl -X GET \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/permissions"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"permissions": [{"repository": {"name": "api-repo", "is_public": true}, "role": "admin"}]}{"permissions": [{"repository": {"name": "api-repo", "is_public": true}, "role": "admin"}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can create or update a team within an organization to have a specified role of admin, member, or creator using the
PUT /api/v1/organization/{orgname}/team/{teamname}command. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "testteam", "description": "", "can_view": true, "role": "creator", "avatar": {"name": "testteam", "hash": "827f8c5762148d7e85402495b126e0a18b9b168170416ed04b49aae551099dc8", "color": "#ff7f0e", "kind": "team"}, "new_team": false}{"name": "testteam", "description": "", "can_view": true, "role": "creator", "avatar": {"name": "testteam", "hash": "827f8c5762148d7e85402495b126e0a18b9b168170416ed04b49aae551099dc8", "color": "#ff7f0e", "kind": "team"}, "new_team": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
1.2. Creating and managing default permissions by using the UI
Default permissions define permissions that should be granted automatically to a repository when it is created, in addition to the default of the repository’s creator. Permissions are assigned based on the user who created the repository.
Use the following procedure to create default permissions using the Red Hat Quay v2 UI.
Procedure
- Click the name of an organization.
- Click Default permissions.
- Click Create default permissions. A toggle drawer appears.
Select either Anyone or Specific user to create a default permission when a repository is created.
If selecting Anyone, the following information must be provided:
- Applied to. Search, invite, or add a user/robot/team.
- Permission. Set the permission to one of Read, Write, or Admin.
If selecting Specific user, the following information must be provided:
- Repository creator. Provide either a user or robot account.
- Applied to. Provide a username, robot account, or team name.
- Permission. Set the permission to one of Read, Write, or Admin.
- Click Create default permission. A confirmation box appears, returning the following alert: Successfully created default permission for creator.
1.3. Creating and managing default permissions by using the API
Use the following procedures to manage default permissions using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
Procedure
Enter the following command to create a default permission with the
POST /api/v1/organization/{orgname}/prototypesendpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"activating_user": {"name": "test-org+test", "is_robot": true, "kind": "user", "is_org_member": true, "avatar": {"name": "test-org+test", "hash": "aa85264436fe9839e7160bf349100a9b71403a5e9ec684d5b5e9571f6c821370", "color": "#8c564b", "kind": "robot"}}, "delegate": {"name": "testuser", "is_robot": false, "kind": "user", "is_org_member": false, "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}}, "role": "admin", "id": "977dc2bc-bc75-411d-82b3-604e5b79a493"}{"activating_user": {"name": "test-org+test", "is_robot": true, "kind": "user", "is_org_member": true, "avatar": {"name": "test-org+test", "hash": "aa85264436fe9839e7160bf349100a9b71403a5e9ec684d5b5e9571f6c821370", "color": "#8c564b", "kind": "robot"}}, "delegate": {"name": "testuser", "is_robot": false, "kind": "user", "is_org_member": false, "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}}, "role": "admin", "id": "977dc2bc-bc75-411d-82b3-604e5b79a493"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to update a default permission using the
PUT /api/v1/organization/{orgname}/prototypes/{prototypeid}endpoint, for example, if you want to change the permission type. You must include the ID that was returned when you created the policy.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"activating_user": {"name": "test-org+test", "is_robot": true, "kind": "user", "is_org_member": true, "avatar": {"name": "test-org+test", "hash": "aa85264436fe9839e7160bf349100a9b71403a5e9ec684d5b5e9571f6c821370", "color": "#8c564b", "kind": "robot"}}, "delegate": {"name": "testuser", "is_robot": false, "kind": "user", "is_org_member": false, "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}}, "role": "write", "id": "977dc2bc-bc75-411d-82b3-604e5b79a493"}{"activating_user": {"name": "test-org+test", "is_robot": true, "kind": "user", "is_org_member": true, "avatar": {"name": "test-org+test", "hash": "aa85264436fe9839e7160bf349100a9b71403a5e9ec684d5b5e9571f6c821370", "color": "#8c564b", "kind": "robot"}}, "delegate": {"name": "testuser", "is_robot": false, "kind": "user", "is_org_member": false, "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}}, "role": "write", "id": "977dc2bc-bc75-411d-82b3-604e5b79a493"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can delete the permission by entering the
DELETE /api/v1/organization/{orgname}/prototypes/{prototypeid}command:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/organization/<organization_name>/prototypes/<prototype_id>
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/organization/<organization_name>/prototypes/<prototype_id>Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return an output. Instead, you can obtain a list of all permissions by entering the
GET /api/v1/organization/{orgname}/prototypescommand:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/organization/<organization_name>/prototypes
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/organization/<organization_name>/prototypesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"prototypes": []}{"prototypes": []}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
1.4. Adjusting access settings for a repository by using the UI
Use the following procedure to adjust access settings for a user or robot account for a repository using the v2 UI.
Prerequisites
- You have created a user account or robot account.
Procedure
- Log into Red Hat Quay.
- On the v2 UI, click Repositories.
-
Click the name of a repository, for example,
quayadmin/busybox. - Click the Settings tab.
Optional. Click User and robot permissions. You can adjust the settings for a user or robot account by clicking the dropdown menu option under Permissions. You can change the settings to Read, Write, or Admin.
- Read. The User or Robot Account can view and pull from the repository.
- Write. The User or Robot Account can read (pull) from and write (push) to the repository.
- Admin. The User or Robot account has access to pull from, and push to, the repository, plus the ability to do administrative tasks associated with the repository.
1.5. Adjusting access settings for a repository by using the API
Use the following procedure to adjust access settings for a user or robot account for a repository by using the API.
Prerequisites
- You have created a user account or robot account.
- You have Created an OAuth access token.
Procedure
Enter the following
PUT /api/v1/repository/{repository}/permissions/user/{username}command to change the permissions of a user:curl -X PUT \ -H "Authorization: Bearer <bearer_token>" \ -H "Content-Type: application/json" \ -d '{"role": "admin"}' \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>$ curl -X PUT \ -H "Authorization: Bearer <bearer_token>" \ -H "Content-Type: application/json" \ -d '{"role": "admin"}' \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"role": "admin", "name": "quayadmin+test", "is_robot": true, "avatar": {"name": "quayadmin+test", "hash": "ca9afae0a9d3ca322fc8a7a866e8476dd6c98de543decd186ae090e420a88feb", "color": "#8c564b", "kind": "robot"}}{"role": "admin", "name": "quayadmin+test", "is_robot": true, "avatar": {"name": "quayadmin+test", "hash": "ca9afae0a9d3ca322fc8a7a866e8476dd6c98de543decd186ae090e420a88feb", "color": "#8c564b", "kind": "robot"}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow To delete the current permission, you can enter the
DELETE /api/v1/repository/{repository}/permissions/user/{username}command:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>
$ curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return any output in the CLI. Instead, you can check that the permissions were deleted by entering the
GET /api/v1/repository/{repository}/permissions/user/command:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>/
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"message":"User does not have permission for repo."}{"message":"User does not have permission for repo."}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 2. Registry-wide access management
The following sections provide information about adjusting registry-wide permissions for both users and superusers.
2.1. Managing restricted users
By default, all Red Hat Quay members part of a registry can create repositories and upload content to their own user account. For example, when user1 pushes an artifact tag such as /<user1>/<image>:<tag>, a repository of the name user1/image is created. Inside of that repository is information about the artifact tag.
With the FEATURE_RESTRICTED_USERS configuration field, Red Hat Quay administrators can restrict all users that are part of their registry from pushing images or artifacts to the registry. This configuration field effectively renders all users from creating new organizations or pushing content altogether unless they are already part of that organization and defined as a team member of that organization; that is, restricted users still have normal permissions in organizations based on the teams that they are members of.
For example, a Red Hat Quay administrator sets the FEATURE_RESTRICTED_USERS configuration field in their config.yaml file as follows:
FEATURE_RESTRICTED_USERS: true
FEATURE_RESTRICTED_USERS: true
When set as shown, user1 is unable to create a new organization by using the Red Hat Quay UI. Upon attempt, the following error message is returned: Unauthorized. Additionally, if user1 attempts to push an image to their own namespace by using the CLI (that is, /<user1>/<image>:<tag>), the following error message is returned: Error: writing blob: initiating layer upload to /v2/user1/<image>/blobs/uploads/ in <quay-server.example.com>: unauthorized: access to the requested resource is not authorized. However, if user1 is part of an organization’s team as defined by an administrator, they maintain the permissions capable of that team. For example, if user1 is added to an organization’s team and given the Admin role, they have administrative privileges for that organization. If they are given the
When FEATURE_RESTRICTED_USERS is leveraged with the RESTRICTED_USERS_WHITELIST configuration field, however, Red Hat Quay administrators can allow specified members the ability to continue to push to the registry or make organizations. In general, when FEATURE_RESTRICTED_USERS is set, Red Hat Quay administrators might also set RESTRICTED_USERS_WHITELIST, otherwise all members of the registry (with the exception of those defined by a team) are rendered incapable of doing basic tasks.
For example, a Red Hat Quay administrator sets the FEATURE_RESTRICTED_USERS and RESTRICTED_USERS_WHITELIST configuration fields in their config.yaml file as follows:
# ...
FEATURE_RESTRICTED_USERS: true
RESTRICTED_USERS_WHITELIST:
- user2
# ...
# ...
FEATURE_RESTRICTED_USERS: true
RESTRICTED_USERS_WHITELIST:
- user2
# ...
With this configuration, all users except user2 are restricted from pushing images or creating organizations. Other users part of a team will also have these privileges. Users part of the registry that are either not defined by the RESTRICTED_USERS_WHITELIST field or part of an organization’s team have no permissions within the registry, and will therefor be unable to perform basic tasks.
This feature works differently for LDAP deployment types. For more information, see LDAP authentication setup for Red Hat Quay.
2.2. Managing superuser access to organizations
When a user, for example, user1 creates an organization within a registry, they own the access and permissions to that organization. As such, they can create repositories, define teams and memberships, create robot accounts, set default permissions, view logs, and adjust other settings as warranted. It is, for all intents and purposes, the user’s organization.
By default, superusers do not have access to a user’s organization. However, Red Hat Quay administrators can use the FEATURE_SUPERUSERS_FULL_ACCESS configuration field to grant superusers the ability to read, write, and delete content from other repositories in namespaces or organizations that they do not own or have explicit permissions for.
- This feature is only available on the beta of the new UI. When enabled, it shows all organizations that the superuser has access to.
- When this field is enabled, the superuser cannot view the image repository of every organization at once. This is a known limitation and will be fixed in a future version of Red Hat Quay. As a temporary workaround, the superuser can view image repositories by navigating to them from the Organizations page.
To grant superusers full access to all organizations within the registry, you can use the following YAML configuration:
# ... FEATURE_SUPERUSERS_FULL_ACCESS: true # ...
# ...
FEATURE_SUPERUSERS_FULL_ACCESS: true
# ...
After sitting FEATURE_SUPERUSERS_FULL_ACCESS: true, all organizations will be visible on the superuser’s Organization page.
Chapter 3. Red Hat Quay repository overview
A repository provides a central location for storing a related set of container images. These images can be used to build applications along with their dependencies in a standardized format.
Repositories are organized by namespaces. Each namespace can have multiple repositories. For example, you might have a namespace for your personal projects, one for your company, or one for a specific team within your organization.
Private repositories provide control over the users that have access to your images by allowing you to define users or teams who can push to, or pull from, the repository, thereby enhancing the security of your registry.
3.1. Adjusting repository visibility by using the UI
You can adjust the visibility of a repository to make it either public of private by using the Red Hat Quay UI.
Procedure
- On the Red Hat Quay UI, click Repositories in the navigation pane.
- Click the name of a repository.
- Click Settings in the navigation pane.
- Click Repository visibility.
- Click Make private. The repository is made private, and only users on the permissions list can view and interact with it.
3.2. Adjusting repository visibility by using the API
The visibility of your repository can be set to private or public by using the POST /api/v1/repository/{repository}/changevisibility command.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile. - You have created a repository.
Procedure
You can change the visibility of your repository to public or private by specifying the desired option in the
visibilityschema. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"success": true}{"success": true}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 4. Red Hat Quay Robot Account overview
Robot Accounts are used to set up automated access to the repositories in your Red Hat Quay. registry. They are similar to OpenShift Container Platform service accounts.
Setting up a Robot Account results in the following:
- Credentials are generated that are associated with the Robot Account.
- Repositories and images that the Robot Account can push and pull images from are identified.
- Generated credentials can be copied and pasted to use with different container clients, such as Docker, Podman, Kubernetes, Mesos, and so on, to access each defined repository.
Robot Accounts can help secure your Red Hat Quay registry by offering various security advantages, such as the following:
- Specifying repository access.
-
Granular permissions, such as
Read(pull) orWrite(push) access. They can also be equipped withAdminpermissions if warranted. - Designed for CI/CD pipelines, system integrations, and other automation tasks, helping avoid credential exposure in scripts, pipelines, or other environment variables.
- Robot Accounts use tokens instead of passwords, which provides the ability for an administrator to revoke the token in the event that it is compromised.
Each Robot Account is limited to a single user namespace or Organization. For example, the Robot Account could provide access to all repositories for the user quayadmin. However, it cannot provide access to repositories that are not in the user’s list of repositories.
Robot Accounts can be created using the Red Hat Quay UI, or through the CLI using the Red Hat Quay API. After creation, Red Hat Quay administrators can leverage more advanced features with Robot Accounts, such as keyless authentication.
4.1. Creating a robot account by using the UI
Use the following procedure to create a robot account using the v2 UI.
Procedure
- On the v2 UI, click Organizations.
-
Click the name of the organization that you will create the robot account for, for example,
test-org. - Click the Robot accounts tab → Create robot account.
-
In the Provide a name for your robot account box, enter a name, for example,
robot1. The name of your Robot Account becomes a combination of your username plus the name of the robot, for example,quayadmin+robot1 Optional. The following options are available if desired:
- Add the robot account to a team.
- Add the robot account to a repository.
- Adjust the robot account’s permissions.
On the Review and finish page, review the information you have provided, then click Review and finish. The following alert appears: Successfully created robot account with robot name: <organization_name> + <robot_name>.
Alternatively, if you tried to create a robot account with the same name as another robot account, you might receive the following error message: Error creating robot account.
- Optional. You can click Expand or Collapse to reveal descriptive information about the robot account.
- Optional. You can change permissions of the robot account by clicking the kebab menu → Set repository permissions. The following message appears: Successfully updated repository permission.
Optional. You can click the name of your robot account to obtain the following information:
- Robot Account: Select this obtain the robot account token. You can regenerate the token by clicking Regenerate token now.
- Kubernetes Secret: Select this to download credentials in the form of a Kubernetes pull secret YAML file.
-
Podman: Select this to copy a full
podman logincommand line that includes the credentials. -
Docker Configuration: Select this to copy a full
docker logincommand line that includes the credentials.
4.2. Creating a robot account by using the Red Hat Quay API
Use the following procedure to create a robot account using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
Procedure
Enter the following command to create a new robot account for an organization using the
PUT /api/v1/organization/{orgname}/robots/{robot_shortname}endpoint:curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_name>"
$ curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "orgname+robot-name", "created": "Fri, 10 May 2024 15:11:00 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}{"name": "orgname+robot-name", "created": "Fri, 10 May 2024 15:11:00 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to create a new robot account for the current user with the
PUT /api/v1/user/robots/{robot_shortname}endpoint:curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/user/robots/<robot_name>"
$ curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/user/robots/<robot_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "quayadmin+robot-name", "created": "Fri, 10 May 2024 15:24:57 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}{"name": "quayadmin+robot-name", "created": "Fri, 10 May 2024 15:24:57 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.3. Bulk managing robot account repository access
Use the following procedure to manage, in bulk, robot account repository access by using the Red Hat Quay v2 UI.
Prerequisites
- You have created a robot account.
- You have created multiple repositories under a single organization.
Procedure
- On the Red Hat Quay v2 UI landing page, click Organizations in the navigation pane.
- On the Organizations page, select the name of the organization that has multiple repositories. The number of repositories under a single organization can be found under the Repo Count column.
- On your organization’s page, click Robot accounts.
- For the robot account that will be added to multiple repositories, click the kebab icon → Set repository permissions.
On the Set repository permissions page, check the boxes of the repositories that the robot account will be added to. For example:
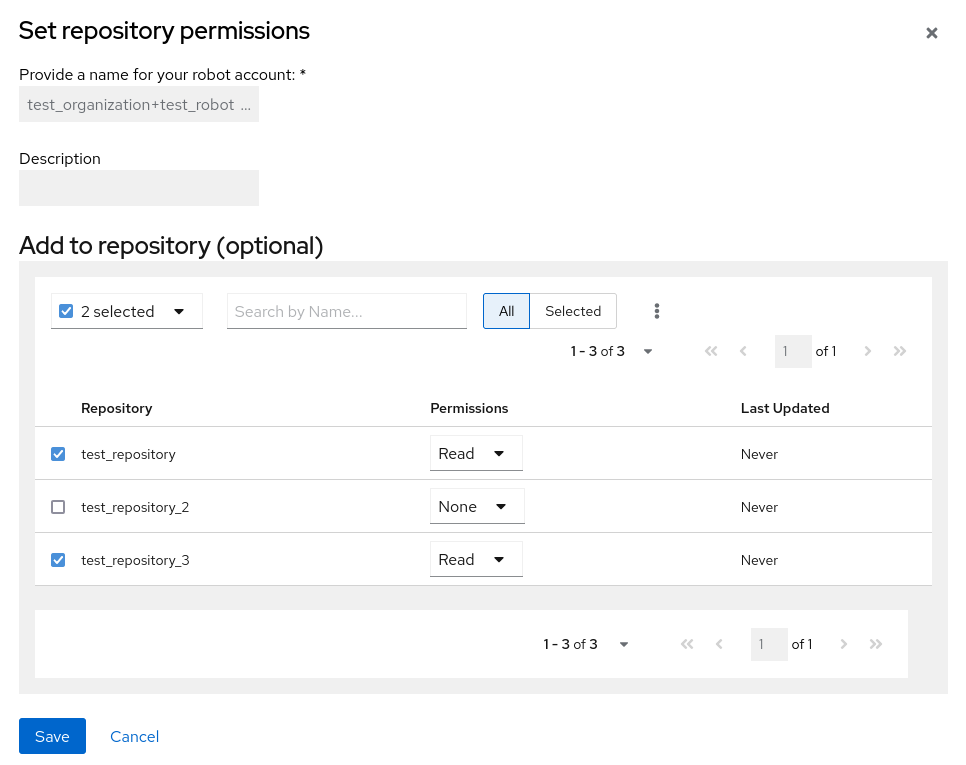
- Set the permissions for the robot account, for example, None, Read, Write, Admin.
- Click save. An alert that says Success alert: Successfully updated repository permission appears on the Set repository permissions page, confirming the changes.
- Return to the Organizations → Robot accounts page. Now, the Repositories column of your robot account shows the number of repositories that the robot account has been added to.
4.4. Disabling robot accounts by using the UI
Red Hat Quay administrators can manage robot accounts by disallowing users to create new robot accounts.
Robot accounts are mandatory for repository mirroring. Setting the ROBOTS_DISALLOW configuration field to True breaks mirroring configurations. Users mirroring repositories should not set ROBOTS_DISALLOW to True in their config.yaml file. This is a known issue and will be fixed in a future release of Red Hat Quay.
Use the following procedure to disable robot account creation.
Prerequisites
- You have created multiple robot accounts.
Procedure
Update your
config.yamlfield to add theROBOTS_DISALLOWvariable, for example:ROBOTS_DISALLOW: true
ROBOTS_DISALLOW: trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart your Red Hat Quay deployment.
Verification: Creating a new robot account
- Navigate to your Red Hat Quay repository.
- Click the name of a repository.
- In the navigation pane, click Robot Accounts.
- Click Create Robot Account.
-
Enter a name for the robot account, for example,
<organization-name/username>+<robot-name>. -
Click Create robot account to confirm creation. The following message appears:
Cannot create robot account. Robot accounts have been disabled. Please contact your administrator.
Verification: Logging into a robot account
On the command-line interface (CLI), attempt to log in as one of the robot accounts by entering the following command:
podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" <quay-server.example.com>
$ podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" <quay-server.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The following error message is returned:
Error: logging into "<quay-server.example.com>": invalid username/password
Error: logging into "<quay-server.example.com>": invalid username/passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can pass in the
log-level=debugflag to confirm that robot accounts have been deactivated:podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" --log-level=debug <quay-server.example.com>
$ podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" --log-level=debug <quay-server.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ... DEBU[0000] error logging into "quay-server.example.com": unable to retrieve auth token: invalid username/password: unauthorized: Robot accounts have been disabled. Please contact your administrator.
... DEBU[0000] error logging into "quay-server.example.com": unable to retrieve auth token: invalid username/password: unauthorized: Robot accounts have been disabled. Please contact your administrator.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.5. Regenerating a robot account token by using the Red Hat Quay API
Use the following procedure to regenerate a robot account token using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
Procedure
Enter the following command to regenerate a robot account token for an organization using the
POST /api/v1/organization/{orgname}/robots/{robot_shortname}/regenerateendpoint:curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<orgname>/robots/<robot_shortname>/regenerate"
$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<orgname>/robots/<robot_shortname>/regenerate"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "test-org+test", "created": "Fri, 10 May 2024 17:46:02 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}{"name": "test-org+test", "created": "Fri, 10 May 2024 17:46:02 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to regenerate a robot account token for the current user with the
POST /api/v1/user/robots/{robot_shortname}/regenerateendpoint:curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>/regenerate"
$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>/regenerate"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "quayadmin+test", "created": "Fri, 10 May 2024 14:12:11 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}{"name": "quayadmin+test", "created": "Fri, 10 May 2024 14:12:11 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.6. Deleting a robot account by using the UI
Use the following procedure to delete a robot account using the Red Hat Quay UI.
Procedure
- Log into your Red Hat Quay registry:
- Click the name of the Organization that has the robot account.
- Click Robot accounts.
- Check the box of the robot account to be deleted.
- Click the kebab menu.
- Click Delete.
-
Type
confirminto the textbox, then click Delete.
4.7. Deleting a robot account by using the Red Hat Quay API
Use the following procedure to delete a robot account using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
Procedure
Enter the following command to delete a robot account for an organization using the
DELETE /api/v1/organization/{orgname}/robots/{robot_shortname}endpoint:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_shortname>"
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI does not return information when deleting a robot account with the API. To confirm deletion, you can check the Red Hat Quay UI, or you can enter the following
GET /api/v1/organization/{orgname}/robotscommand to see if details are returned for the robot account:curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"robots": []}{"robots": []}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to delete a robot account for the current user with the
DELETE /api/v1/user/robots/{robot_shortname}endpoint:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"
$ curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI does not return information when deleting a robot account for the current user with the API. To confirm deletion, you can check the Red Hat Quay UI, or you can enter the following
GET /api/v1/user/robots/{robot_shortname}command to see if details are returned for the robot account:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"message":"Could not find robot with specified username"}{"message":"Could not find robot with specified username"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 5. Clair security scanner
Clair v4 (Clair) is an open source application that leverages static code analyses for parsing image content and reporting vulnerabilities affecting the content. Clair is packaged with Red Hat Quay and can be used in both standalone and Operator deployments. It can be run in highly scalable configurations, where components can be scaled separately as appropriate for enterprise environments.
For more information about Clair security scanner, see Vulnerability reporting with Clair on Red Hat Quay.