Red Hat Quay API guide
Preface
The Red Hat Quay application programming interface (API) provides a comprehensive, RESTful interface for managing and automating tasks within Red Hat Quay. Designed around the OAuth 2.0 protocol, this API enables secure, fine-grained access to Red Hat Quay resources, and allows administrators and users to perform such actions as creating repositories, managing images, setting permissions, and more.
Red Hat Quay follows Semantic Versioning (SemVer) principles, ensuring predictable API stability across releases, such as:
- Major releases: Introduce new capabilities. Might include breaking changes to API compatibility. For example, the API of Red Hat Quay 2.0 differs from Red Hat Quay 3.0.
- Minor releases: Add new functionality in a backward-compatible manner. For example, a 3.y release adds functionality to the version 3. release.
- Patch releases: Deliver bug fixes and improvements while preserving backward compatibility with minor releases, such as 3.y.z.
The following guide describes the Red Hat Quay API in more detail, and provides details on the following topics:
- OAuth 2 access tokens and how they compare to traditional API tokens and Red Hat Quay’s robot tokens
- Generating an OAuth 2 access token
- Best practices for token management
- OAuth 2 access token capabilities
- Using the Red Hat Quay API
- Red Hat Quay API configuration examples
Chapter 1. Introduction to Red Hat Quay OAuth 2.0 tokens
The Red Hat Quay OAuth 2 token system provides a secure, standards-based method for accessing Red Hat Quay’s API and other relevant resources. The OAuth 2 token-based approach provides a secure method for handling authentication and authorization for complex environments. Compared to more traditional API tokens, Red Hat Quay’s OAuth 2 token system offers the following enhancements:
- Standards-based security, which adheres to the OAuth 2.0 protocol.
- Revocable access by way of deleting the application in which the OAuth 2 token exists.
- Fine-grained access control, which allows Red Hat Quay administrators the ability to assign specific permissions to tokens.
- Delegated access, which allows third-party applications and services to act on behalf of a user.
- Future-proofing, which helps ensure that Red Hat Quay remains compatible with other services, platforms, and integrations.
Red Hat Quay primarily supports two types of tokens: OAuth 2 access tokens and robot account tokens. A third token type, an OCI referrers access token, that is required to list OCI referrers of a manifest under a repository, is also available when warranted.
The following chapters provide more details about each token type and how to generate each token type.
Chapter 2. OAuth 2 access tokens
OAuth 2 access tokens (considered "API tokens" for Red Hat Quay) enable user-authenticated access to the Red Hat Quay API, suitable for applications that require user identity verification. These tokens are obtained through an OAuth 2 authorization process, where a Red Hat Quay administrator generates a token on behalf of themselves or another user to access Red Hat Quay API endpoints. OAuth 2 tokens authorize actions on API endpoints based on the scopes defined for the token.
Although OAuth 2 tokens authorize actions on API endpoints based on the scopes defined for the token, access to the resources themselves is governed by Red Hat Quay’s role-based access control (RBAC) mechanisms. Actions can be created on a resource, for example, a repository, provided that you have the proper role (Admin or Creator) to do so for that namespace. This is true even if the API token was granted the repo:admin scope.
OAuth 2 access tokens can only be created by using the Red Hat Quay UI; there is no way to create an OAuth 2 access token by using the CLI. When creating an OAuth 2 token, the following options can be selected for a token holder:
- Administer Organization. When selected, allows the user to be able to administer organizations, including creating robots, creating teams, adjusting team membership, and changing billing settings.
- Administer Repositories. When selected, provides the user administrator access to all repositories to which the granting user has access.
- Create Repositories. When selected, provides the user the ability to create repositories in any namespaces that the granting user is allowed to create repositories.
- View all visible repositories. When selected, provides the user the ability to view and pull all repositories visible to the granting user.
- Read/Write to any accessible repositories. When selected, provides the user the ability to view, push and pull to all repositories to which the granting user has write access.
- Super User Access. When selected, provides the user the ability to administer your installation including managing users, managing organizations and other features found in the superuser panel.
- Administer User When selected, provides the user the ability to administer your account including creating robots and granting them permissions to your repositories.
- Read User Information. When selected, provides the user the ability to read user information such as username and email address.
Token distributors should be mindful of the permissions that they are granting when generating a token on behalf of a user, and should have absolute trust in a user before granting such permissions as Administer organization, Super User Access, and Administer User. Additionally, the access token is only revealed at the time of creation; they cannot be listed from the CLI, nor can they be found on the Red Hat Quay UI. If an access token is lost or forgotten, a new token must be created; a token cannot be recovered.
OAuth 2 access tokens are passed as a Bearer token in the Authorization header of an API call and, as a result, are used to provide authentication and authorization to the defined API endpoint, such as an image tag, a repository, an organization, and so on.
The API is available from the /api/v1 endpoint of your Red Hat Quay host. For example, https://<quay-server.example.com>/api/v1. It allows users to connect to endpoints through their browser to GET, POST, DELETE, and PUT Red Hat Quay settings by enabling the Swagger UI. The API can be accessed by applications that make API calls and use OAuth tokens, and it sends and receives data as JSON.
With Red Hat Quay, there is currently no way to rotate or to set an expiration time on an OAuth 2 access token, and the token lifespan is 10 years. Tokens can be deleted by deleting the applications in which they were created in the event that they are compromised, however, this deletes all tokens that were made within that specific application.
In practice, Red Hat Quay administrators could create a new OAuth application on the Applications page of their organization each time they wanted to create a new OAuth token for a user. This would ensure that a single application is not responsible for all OAuth tokens. As a result, in the event that a user’s token is compromised, the administrator would delete the application of the compromised token. This would help avoid disruption for other users whose tokens might be part of the same application.
The following sections shows you how to generate and reassign an OAuth 2 access token.
2.1. Creating an OAuth 2 access token
With Red Hat Quay, you must create an OAuth 2 access token before you can access the API endpoints of your organization. OAuth 2 access token can only be generated by using the Red Hat Quay UI; the CLI cannot be used to generate an OAuth 2 access token.
Use the following procedure to create an OAuth2 access token.
Prerequisites
- You have logged in to Red Hat Quay as an administrator.
- You have created an OAuth 2 application.
Procedure
- On the main page, select an Organization.
- In the navigation pane, select Applications.
- Click the name of your application, for example, Test application.
- In the navigation pane, select Generate Token.
Check the boxes for the following options:
- Administer Organization. When selected, allows the user to be able to administer organizations, including creating robots, creating teams, adjusting team membership, and changing billing settings.
- Administer Repositories. When selected, provides the user administrator access to all repositories to which the granting user has access.
- Create Repositories. When selected, provides the user the ability to create repositories in any namespaces that the granting user is allowed to create repositories.
- View all visible repositories. When selected, provides the user the ability to view and pull all repositories visible to the granting user.
- Read/Write to any accessible repositories. When selected, provides the user the ability to view, push and pull to all repositories to which the granting user has write access.
- Super User Access. When selected, provides the user the ability to administer your installation including managing users, managing organizations and other features found in the superuser panel.
- Administer User When selected, provides the user the ability to administer your account including creating robots and granting them permissions to your repositories.
- Read User Information. When selected, provides the user the ability to read user information such as username and email address.
- Click Generate Access Token. You are redirected to a new page.
- Review the permissions that you are allowing, then click Authorize Application. Confirm your decision by clicking Authorize Application.
You are redirected to the Access Token page. Copy and save the access token.
ImportantThis is the only opportunity to copy and save the access token. It cannot be reobtained after leaving this page.
2.2. Reassigning an OAuth access token
Organization administrators can assign OAuth API tokens to be created by other user’s with specific permissions. This allows the audit logs to be reflected accurately when the token is used by a user that has no organization administrative permissions to create an OAuth API token.
The following procedure only works on the current Red Hat Quay UI. It is not currently implemented in the Red Hat Quay v2 UI.
Prerequisites
You are logged in as a user with organization administrative privileges, which allows you to assign an OAuth API token.
NoteOAuth API tokens are used for authentication and not authorization. For example, the user that you are assigning the OAuth token to must have the
Adminteam role to use administrative API endpoints. For more information, see Managing access to repositories.
Procedure
Optional. If not already, update your Red Hat Quay
config.yamlfile to include theFEATURE_ASSIGN_OAUTH_TOKEN: truefield:# ... FEATURE_ASSIGN_OAUTH_TOKEN: true # ...
# ... FEATURE_ASSIGN_OAUTH_TOKEN: true # ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Optional. Restart your Red Hat Quay registry.
- Log in to your Red Hat Quay registry as an organization administrator.
- Click the name of the organization in which you created the OAuth token for.
- In the navigation pane, click Applications.
- Click the proper application name.
- In the navigation pane, click Generate Token.
- Click Assign another user and enter the name of the user that will take over the OAuth token.
Check the boxes for the desired permissions that you want the new user to have. For example, if you only want the new user to be able to create repositories, click Create Repositories.
ImportantPermission control is defined by the team role within an organization and must be configured regardless of the options selected here. For example, the user that you are assigning the OAuth token to must have the
Adminteam role to use administrative API endpoints.Solely checking the Super User Access box does not actually grant the user this permission. Superusers must be configured via the
config.yamlfile and the box must be checked here.Click Assign token. A popup box appears that confirms authorization with the following message and shows you the approved permissions:
This will prompt user <username> to generate a token with the following permissions: repo:create
This will prompt user <username> to generate a token with the following permissions: repo:createCopy to Clipboard Copied! Toggle word wrap Toggle overflow Click Assign token in the popup box. You are redirected to a new page that displays the following message:
Token assigned successfully
Token assigned successfullyCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
- After reassigning an OAuth token, the assigned user must accept the token to receive the bearer token, which is required to use API endpoints. Request that the assigned user logs into the Red Hat Quay registry.
- After they have logged in, they must click their username under Users and Organizations.
- In the navigation pane, they must click External Logins And Applications.
- Under Authorized Applications, they must confirm the application by clicking Authorize Application. They are directed to a new page where they must reconfirm by clicking Authorize Application.
- They are redirected to a new page that reveals their bearer token. They must save this bearer token, as it cannot be viewed again.
2.3. Deleting an OAuth 2 access token
Because OAuth 2 access tokens are created through the OAuth application, they cannot be rotated or renewed. In the event that a token is compromised, or you need to delete a token, you must deleted its associated application through the Red Hat Quay UI.
Deleting an application deletes all tokens that were made within that specific application. Use with caution.
Prerequisites
- You have created an OAuth 2 access token.
Procedure
- On the Red Hat Quay UI, click the name of the organization hosting the application. Then, in the navigation pane, click Applications.
- Click the application name, for example, Test application.
- In the navigation pane, click Delete Application. You are redirected to a new page. Click Delete application and confirm your decision.
Chapter 3. Robot account tokens
Robot account tokens are password-type credentials used to access a Red Hat Quay registry via normal Docker v2 endpoints; these are defined as tokens on the UI because the password itself is encrypted.
Robot account tokens are persistent tokens designed for automation and continuous integration workflows. By default, Red Hat Quay’s robot account tokens do not expire and do not require user interaction, which makes robot accounts ideal for non-interactive use cases.
Robot account tokens are automatically generated at the time of a robot’s creation and are non-user specific; that is, they are connected to the user and organization namespace where where they are created. for example, a robot named project_tools+<robot_name> is associated with the project_tools namespace.
Robot account tokens provide access without needing a user’s personal credentials. How the robot account is configured, for example, with one of READ, WRITE, or ADMIN permissions, ultimately defines the actions that the robot account can take.
Because robot account tokens are persistent and do not expire by default, they are ideal for automated workflows that require consistent access to Red Hat Quay without manual renewal. Despite this, robot account tokens can be easily re-generated by using the the UI. They can also be regenerated by using the proper API endpoint via the CLI. To enhance the security of your Red Hat Quay deployment, administrators should regularly refresh robot account tokens. Additionally, with the keyless authentication with robot accounts feature, robot account tokens can be exchanged for external OIDC tokens and leveraged so that they only last one hour, enhancing the security of your registry.
When a namespace gets deleted, or when the robot account is deleted itself, they are garbage collected when the collector is scheduled to run.
The following section shows you how to use the API to re-generate a robot account token for organization robots and user robots.
3.1. Regenerating a robot account token by using the Red Hat Quay UI
Use the following procedure to regenerate a robot account token by using the Red Hat Quay UI.
Prerequisites
- You have logged into Red Hat Quay.
Procedure
- Click the name of an Organization.
- In the navigation pane, click Robot accounts.
- Click the name of your robot account, for example, testorg3+test.
- Click Regenerate token in the popup box.
3.2. Regenerating a robot account token by using the Red Hat Quay API
Use the following procedure to regenerate a robot account token using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following command to regenerate a robot account token for an organization using the
POST /api/v1/organization/{orgname}/robots/{robot_shortname}/regenerateendpoint:curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<orgname>/robots/<robot_shortname>/regenerate"
$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<orgname>/robots/<robot_shortname>/regenerate"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "test-org+test", "created": "Fri, 10 May 2024 17:46:02 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}{"name": "test-org+test", "created": "Fri, 10 May 2024 17:46:02 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to regenerate a robot account token for the current user with the
POST /api/v1/user/robots/{robot_shortname}/regenerateendpoint:curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>/regenerate"
$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>/regenerate"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "quayadmin+test", "created": "Fri, 10 May 2024 14:12:11 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}{"name": "quayadmin+test", "created": "Fri, 10 May 2024 14:12:11 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 4. OCI referrers OAuth access token
In some cases, depending on the features that your Red Hat Quay deployment is configured to use, you might need to leverage an OCI referrers OAuth access token. OCI referrers OAuth access tokens are used to list OCI referrers of a manifest under a repository, and uses a curl command to make a GET request to the Red Hat Quay v2/auth endpoint.
These tokens are obtained via basic HTTP authentication, wherein the user provides a username and password encoded in Base64 to authenticate directly with the v2/auth API endpoint. As such, they are based directly on the user’s credentials aod do not follow the same detailed authorization flow as OAuth 2, but still allow a user to authorize API requests.
OCI referrers OAuth access tokens do not offer scope-based permissions and do not expire. They are solely used to list OCI referrers of a manifest under a repository.
Additional resource
4.1. Creating an OCI referrers OAuth access token
This OCI referrers OAuth access token is used to list OCI referrers of a manifest under a repository.
Procedure
Update your
config.yamlfile to include theFEATURE_REFERRERS_API: truefield. For example:# ... FEATURE_REFERRERS_API: true # ...
# ... FEATURE_REFERRERS_API: true # ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to Base64 encode your credentials:
echo -n '<username>:<password>' | base64
$ echo -n '<username>:<password>' | base64Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
abcdeWFkbWluOjE5ODlraWROZXQxIQ==
abcdeWFkbWluOjE5ODlraWROZXQxIQ==Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to use the base64 encoded string and modify the URL endpoint to your Red Hat Quay server:
curl --location '<quay-server.example.com>/v2/auth?service=<quay-server.example.com>&scope=repository:quay/listocireferrs:pull,push' --header 'Authorization: Basic <base64_username:password_encode_token>' -k | jq
$ curl --location '<quay-server.example.com>/v2/auth?service=<quay-server.example.com>&scope=repository:quay/listocireferrs:pull,push' --header 'Authorization: Basic <base64_username:password_encode_token>' -k | jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{ "token": "<example_secret> }{ "token": "<example_secret> }Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 5. Enabling and using the Red Hat Quay API
By leveraging the Red Hat Quay API, you can streamline container registry management, automate tasks, and integrate Red Hat Quay’s functionalities into your existing workflow. This can improve efficiency, offer enhanced flexibility (by way of repository management, user management, user permissions, image management, and so on), increase the stability of your organization, repository, or overall deployment, and more.
The following sections explain how to enable and use the Red Hat Quay API.
5.1. Configuring Red Hat Quay to accept API calls
Prior to using the Red Hat Quay API, you must disable BROWSER_API_CALLS_XHR_ONLY in your config.yaml file. This allows you to avoid such errors as API calls must be invoked with an X-Requested-With header if called from a browser.
Procedure
In your Red Hat Quay
config.yamlfile, setBROWSER_API_CALLS_XHR_ONLYtofalse. For example:# ... BROWSER_API_CALLS_XHR_ONLY: false # ...
# ... BROWSER_API_CALLS_XHR_ONLY: false # ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart your Red Hat Quay deployment.
5.2. Using the Red Hat Quay API
After you have created an application and generated an OAuth 2 access token with the desired settings, you can pass in the access token to GET, PUT, POST, or DELETE settings by using the API from the CLI. Generally, a Red Hat Quay API command looks similar to the following example:
curl -X GET -H "Authorization: Bearer <your_access_token>"
https://<quay-server.example.com>/api/v1/<example>/<endpoint>/
$ curl -X GET -H "Authorization: Bearer <your_access_token>"
https://<quay-server.example.com>/api/v1/<example>/<endpoint>/
All Red Hat Quay APIs are documented in the Application Programming Interface (API) chapter. Understanding how they are documented is crucial to successful invocation. Take, for example, the following entry for the createAppToken API endpoint:
- 1
- The name of the API endpoint.
- 2
- A brief description of the API endpoint.
- 3
- The API endpoint used for invocation.
- 4
- The authorizations required to use the API endpoint.
- 5
- The available paths to be used with the API endpoint. In this example,
titleis the only path to be used with thePOST /api/v1/user/apptokenendpoint. - 6
- The API responses for this endpoint.
In order to use an API endpoint, you pass in your access token and then include the appropriate fields depending on your needs. The following procedure shows you how to use the POST /api/v1/user/apptoken endpoint.
Prerequisites
- You have access to the Red Hat Quay API, which entails having already created an OAuth 2 access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Create a user application by entering the
POST /api/v1/user/apptokenAPI call:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"token": {"uuid": "6b5aa827-cee5-4fbe-a434-4b7b8a245ca7", "title": "MyAppToken", "last_accessed": null, "created": "Wed, 08 Jan 2025 19:32:48 -0000", "expiration": null, "token_code": "K2YQB1YO0ABYV5OBUYOMF9MCUABN12Y608Q9RHFXBI8K7IE8TYCI4WEEXSVH1AXWKZCKGUVA57PSA8N48PWED9F27PXATFUVUD9QDNCE9GOT9Q8ACYPIN0HL"}}{"token": {"uuid": "6b5aa827-cee5-4fbe-a434-4b7b8a245ca7", "title": "MyAppToken", "last_accessed": null, "created": "Wed, 08 Jan 2025 19:32:48 -0000", "expiration": null, "token_code": "K2YQB1YO0ABYV5OBUYOMF9MCUABN12Y608Q9RHFXBI8K7IE8TYCI4WEEXSVH1AXWKZCKGUVA57PSA8N48PWED9F27PXATFUVUD9QDNCE9GOT9Q8ACYPIN0HL"}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
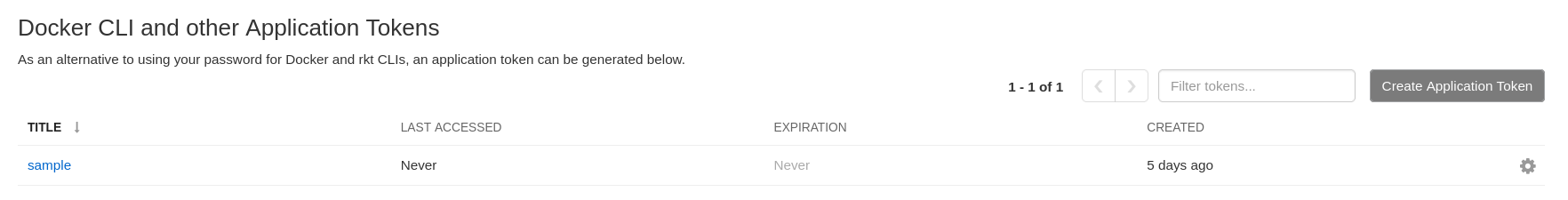
On the Red Hat Quay UI, click your username in the navigation pane → Account Settings. The name of your application appears under the Docker CLI and other Application Tokens heading. For example:
5.3. Automating Red Hat Quay processes by using the API
With the API, Red Hat Quay administrators and users with access to the API can automate repetitive tasks such as repository management or image pruning.
The following example shows you how you might use a Python script and a cron job to automate the deletion of OAuth 2 applications except the administrator’s token. This might be useful if you want to ensure an application associated with an OAuth 2 access token is cycled after a certain period of time.
Prerequisites
- You have access to the Red Hat Quay API, which entails having already created an OAuth 2 access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile. -
You have installed the Python
requestslibrary using. - You have enabled cron jobs on your machine.
- You have created several organization applications, including one that will not be deleted.
Procedure
Create a Python script that executes an API command. The following example is used to delete organization applications using the
DELETE /api/v1/organization/{orgname}/applications/{client_id}API endpoint.example.py file
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Save the script as
prune_applications.py. Create a cron job that automatically runs the script:
Open the crontab editor by running the following command:
crontab -e
$ crontab -eCopy to Clipboard Copied! Toggle word wrap Toggle overflow In the editor, add the cron job for running the script. The following example runs the script once per month:
0 0 1 * * sudo python /path/to/prune_images.py >> /var/log/prune_images.log 2>&1
0 0 1 * * sudo python /path/to/prune_images.py >> /var/log/prune_images.log 2>&1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 6. Red Hat Quay API examples
The remainder of this chapter provides Red Hat Quay API examples for the features in which they are available.
6.1. Managing a user application by using the API
Red Hat Quay users can create, list information about, and delete a user application that can be used as an alternative to using your password for Docker, Podman, or other service providers. User application tokens work like your username and password, but are encrypted and do not provide any information to third parties regarding who is accessing Red Hat Quay.
After creation via the CLI, the user application token is listed under User Settings of the Red Hat Quay UI. Note that this differs from an application token that is created under user settings, and should be considered a different application entirely.
Use the following procedure to create a user application token.
Prerequisites
- You have created an OAuth 2 access token.
Procedure
Create a user application by entering the
POST /api/v1/user/apptokenAPI call:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"token": {"uuid": "6b5aa827-cee5-4fbe-a434-4b7b8a245ca7", "title": "MyAppToken", "last_accessed": null, "created": "Wed, 08 Jan 2025 19:32:48 -0000", "expiration": null, "token_code": "K2YQB1YO0ABYV5OBUYOMF9MCUABN12Y608Q9RHFXBI8K7IE8TYCI4WEEXSVH1AXWKZCKGUVA57PSA8N48PWED9F27PXATFUVUD9QDNCE9GOT9Q8ACYPIN0HL"}}{"token": {"uuid": "6b5aa827-cee5-4fbe-a434-4b7b8a245ca7", "title": "MyAppToken", "last_accessed": null, "created": "Wed, 08 Jan 2025 19:32:48 -0000", "expiration": null, "token_code": "K2YQB1YO0ABYV5OBUYOMF9MCUABN12Y608Q9RHFXBI8K7IE8TYCI4WEEXSVH1AXWKZCKGUVA57PSA8N48PWED9F27PXATFUVUD9QDNCE9GOT9Q8ACYPIN0HL"}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can obtain information about your application, including when the application expires, by using the
GET /api/v1/user/apptokencommand. For example:curl -X GET \ -H "Authorization: Bearer <access_token>" \ "http://quay-server.example.com/api/v1/user/apptoken"
$ curl -X GET \ -H "Authorization: Bearer <access_token>" \ "http://quay-server.example.com/api/v1/user/apptoken"Copy to Clipboard Copied! Toggle word wrap Toggle overflow {"tokens": [{"uuid": "6b5aa827-cee5-4fbe-a434-4b7b8a245ca7", "title": "MyAppToken", "last_accessed": null, "created": "Wed, 08 Jan 2025 19:32:48 -0000", "expiration": null}], "only_expiring": null}{"tokens": [{"uuid": "6b5aa827-cee5-4fbe-a434-4b7b8a245ca7", "title": "MyAppToken", "last_accessed": null, "created": "Wed, 08 Jan 2025 19:32:48 -0000", "expiration": null}], "only_expiring": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can obtain information about a specific user application by entering the
GET /api/v1/user/apptoken/{token_uuid}command:curl -X GET \ -H "Authorization: Bearer <access_token>" \ "http://quay-server.example.com/api/v1/user/apptoken/<token_uuid>"
$ curl -X GET \ -H "Authorization: Bearer <access_token>" \ "http://quay-server.example.com/api/v1/user/apptoken/<token_uuid>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"token": {"uuid": "6b5aa827-cee5-4fbe-a434-4b7b8a245ca7", "title": "MyAppToken", "last_accessed": null, "created": "Wed, 08 Jan 2025 19:32:48 -0000", "expiration": null, "token_code": "K2YQB1YO0ABYV5OBUYOMF9MCUABN12Y608Q9RHFXBI8K7IE8TYCI4WEEXSVH1AXWKZCKGUVA57PSA8N48PWED9F27PXATFUVUD9QDNCE9GOT9Q8ACYPIN0HL"}}{"token": {"uuid": "6b5aa827-cee5-4fbe-a434-4b7b8a245ca7", "title": "MyAppToken", "last_accessed": null, "created": "Wed, 08 Jan 2025 19:32:48 -0000", "expiration": null, "token_code": "K2YQB1YO0ABYV5OBUYOMF9MCUABN12Y608Q9RHFXBI8K7IE8TYCI4WEEXSVH1AXWKZCKGUVA57PSA8N48PWED9F27PXATFUVUD9QDNCE9GOT9Q8ACYPIN0HL"}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can delete or revoke a user application token by using the
DELETE /api/v1/user/apptoken/{token_uuid}endpoint:curl -X DELETE \ -H "Authorization: Bearer <access_token>" \ "http://quay-server.example.com/api/v1/user/apptoken/<token_uuid>"
$ curl -X DELETE \ -H "Authorization: Bearer <access_token>" \ "http://quay-server.example.com/api/v1/user/apptoken/<token_uuid>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI. You can return a list of tokens by entering one of the aforementioned commands.
6.2. Discovering Red Hat Quay API endpoints
Red Hat Quay API endpoints are discoverable by using the API.
Use the following procedure to discover available API endpoints.
Prerequisites
- You have created an OAuth 2 access token.
Procedure
Enter the following
GET /api/v1/discoverycommand to list all of the API endpoints available in the swagger API format:curl -X GET "https://<quay-server.example.com>/api/v1/discovery?query=true" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/discovery?query=true" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
--- : "Manage the tags of a repository."}, {"name": "team", "description": "Create, list and manage an organization's teams."}, {"name": "trigger", "description": "Create, list and manage build triggers."}, {"name": "user", "description": "Manage the current user."}, {"name": "userfiles", "description": ""}]} ------ : "Manage the tags of a repository."}, {"name": "team", "description": "Create, list and manage an organization's teams."}, {"name": "trigger", "description": "Create, list and manage build triggers."}, {"name": "user", "description": "Manage the current user."}, {"name": "userfiles", "description": ""}]} ---Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3. Obtaining Red Hat Quay API error details
Red Hat Quay API error details are discoverable by using the API.
Use the following procedure to discover error details.
Prerequisites
- You have created an OAuth 2 access token.
Procedure
You can obtain error details of the API by entering the
GET /api/v1/error/{error_type}endpoint. Note that you must include one of the following error codes:Expand HTTP Code Description Schema 200
Successful invocation
400
Bad Request
401
Session required
403
Unauthorized access
404
Not found
curl -X GET "https://<quay-server.example.com>/api/v1/error/<error_type>" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/error/<error_type>" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
curl: (7) Failed to connect to quay-server.example.com port 443 after 0 ms: Couldn't connect to server
curl: (7) Failed to connect to quay-server.example.com port 443 after 0 ms: Couldn't connect to serverCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.4. Global messages
Global messages can be created, obtained, or deleted by using the Red Hat Quay API. Use the following procedure to create, obtain, or delete a global message.
Prerequisites
- You have created an OAuth 2 access token.
Procedure
Create a message by using the
POST /api/v1/messageendpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output.
Use the
GET /api/v1/messagescommand to return the list of global messages:curl -X GET "https://<quay-server.example.com>/api/v1/messages" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/messages" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"messages": [{"uuid": "ecababd4-3451-4458-b5db-801684137444", "content": "Hi", "severity": "info", "media_type": "text/plain"}]}{"messages": [{"uuid": "ecababd4-3451-4458-b5db-801684137444", "content": "Hi", "severity": "info", "media_type": "text/plain"}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Delete the global message by using the
DELETE /api/v1/message/{uuid}endpoint:curl -X DELETE "https://<quay-server.example.com>/api/v1/message/<uuid>" \ -H "Authorization: Bearer <access_token>"$ curl -X DELETE "https://<quay-server.example.com>/api/v1/message/<uuid>" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output.
6.5. Viewing usage logs by using the API
Logs can be viewed by Organization or repository by using the API. They can also be aggregated (grouped), or listed with more detailed. Logs can also be viewed by user, a specific date range, or by page.
6.5.1. Viewing aggregated logs
Aggregated logs can be viewed by Organization, repository, a specific user, or the current user. You can also pass in optional commands like performer, starttime/endtime, and next_page to filter results.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Use the
GET /api/v1/user/aggregatelogsAPI endpoint to return the aggregated (or grouped) logs for the current user:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "https://<quay-server.example.com>/api/v1/user/aggregatelogs"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "https://<quay-server.example.com>/api/v1/user/aggregatelogs"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"aggregated": [{"kind": "create_tag", "count": 1, "datetime": "Tue, 18 Jun 2024 00:00:00 -0000"}, {"kind": "manifest_label_add", "count": 1, "datetime": "Tue, 18 Jun 2024 00:00:00 -0000"}, {"kind": "push_repo", "count": 2, "datetime": "Tue, 18 Jun 2024 00:00:00 -0000"}, {"kind": "revert_tag", "count": 1, "datetime": "Tue, 18 Jun 2024 00:00:00 -0000"}]}{"aggregated": [{"kind": "create_tag", "count": 1, "datetime": "Tue, 18 Jun 2024 00:00:00 -0000"}, {"kind": "manifest_label_add", "count": 1, "datetime": "Tue, 18 Jun 2024 00:00:00 -0000"}, {"kind": "push_repo", "count": 2, "datetime": "Tue, 18 Jun 2024 00:00:00 -0000"}, {"kind": "revert_tag", "count": 1, "datetime": "Tue, 18 Jun 2024 00:00:00 -0000"}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can also pass in the
performerandstarttime/endtimequeries to obtain aggregated logs for a specific user between a specific time period. For example:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "<quay-server.example.com>/api/v1/user/aggregatelogs?performer=<username>&starttime=<MM/DD/YYYY>&endtime=<MM/DD/YYYY>"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "<quay-server.example.com>/api/v1/user/aggregatelogs?performer=<username>&starttime=<MM/DD/YYYY>&endtime=<MM/DD/YYYY>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Aggregated logs can also be viewed by Organization by using the
GET /api/v1/organization/{orgname}/aggregatelogs. For example:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "<quay-server.example.com>/api/v1/organization/{orgname}/aggregatelogs"$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "<quay-server.example.com>/api/v1/organization/{orgname}/aggregatelogs"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Aggregated logs can also be viewed by repository by using the
GET /api/v1/repository/{repository}/aggregatelogscommand. The following example includes thestarttime/endtimefields:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "<quay-server.example.com>/api/v1/repository/<repository_name>/<namespace>/aggregatelogs?starttime=2024-01-01&endtime=2024-06-18""
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "<quay-server.example.com>/api/v1/repository/<repository_name>/<namespace>/aggregatelogs?starttime=2024-01-01&endtime=2024-06-18""Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5.2. Viewing detailed logs
Detailed logs can be viewed by Organization, repository, a specific user, or the current user. You can also pass in optional fields like performer, starttime/endtime, and next_page to filter results.
Procedure
Use the
GET /api/v1/user/logsAPI endpoint to return a list of log entries for a user. For example:curl -X GET -H "Authorization: Bearer <bearer_token>" -H "Accept: application/json" "<quay-server.example.com>/api/v1/user/logs"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" -H "Accept: application/json" "<quay-server.example.com>/api/v1/user/logs"Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can also pass in the
performerandstartime/endtimequeries to obtain logs for a specific user between a specific time period. For example:curl -X GET -H "Authorization: Bearer <bearer_token>" -H "Accept: application/json" "http://quay-server.example.com/api/v1/user/logs?performer=quayuser&starttime=01/01/2024&endtime=06/18/2024"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" -H "Accept: application/json" "http://quay-server.example.com/api/v1/user/logs?performer=quayuser&starttime=01/01/2024&endtime=06/18/2024"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
--- {"start_time": "Mon, 01 Jan 2024 00:00:00 -0000", "end_time": "Wed, 19 Jun 2024 00:00:00 -0000", "logs": [{"kind": "revert_tag", "metadata": {"username": "quayuser", "repo": "busybox", "tag": "test-two", "manifest_digest": "sha256:57583a1b9c0a7509d3417387b4f43acf80d08cdcf5266ac87987be3f8f919d5d"}, "ip": "192.168.1.131", "datetime": "Tue, 18 Jun 2024 18:59:13 -0000", "performer": {"kind": "user", "name": "quayuser", "is_robot": false, "avatar": {"name": "quayuser", "hash": "b28d563a6dc76b4431fc7b0524bbff6b810387dac86d9303874871839859c7cc", "color": "#17becf", "kind": "user"}}}, {"kind": "push_repo", "metadata": {"repo": "busybox", "namespace": "quayuser", "user-agent": "containers/5.30.1 (github.com/containers/image)", "tag": "test-two", "username": "quayuser", } ------ {"start_time": "Mon, 01 Jan 2024 00:00:00 -0000", "end_time": "Wed, 19 Jun 2024 00:00:00 -0000", "logs": [{"kind": "revert_tag", "metadata": {"username": "quayuser", "repo": "busybox", "tag": "test-two", "manifest_digest": "sha256:57583a1b9c0a7509d3417387b4f43acf80d08cdcf5266ac87987be3f8f919d5d"}, "ip": "192.168.1.131", "datetime": "Tue, 18 Jun 2024 18:59:13 -0000", "performer": {"kind": "user", "name": "quayuser", "is_robot": false, "avatar": {"name": "quayuser", "hash": "b28d563a6dc76b4431fc7b0524bbff6b810387dac86d9303874871839859c7cc", "color": "#17becf", "kind": "user"}}}, {"kind": "push_repo", "metadata": {"repo": "busybox", "namespace": "quayuser", "user-agent": "containers/5.30.1 (github.com/containers/image)", "tag": "test-two", "username": "quayuser", } ---Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/organization/{orgname}/logsendpoint to return logs for a specified organization:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "http://<quay-server.example.com>/api/v1/organization/{orgname}/logs"$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "http://<quay-server.example.com>/api/v1/organization/{orgname}/logs"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/repository/{repository}/logsendpoint to return logs for a specified repository:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "http://<quay-server.example.com>/api/v1/repository/{repository}/logs"$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "http://<quay-server.example.com>/api/v1/repository/{repository}/logs"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.6. Exporting logs by using the API
Detailed logs can be exported to a callback URL or to an email address.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Use the
POST /api/v1/user/exportlogsendpoint to export logs for the current user:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"export_id": "6a0b9ea9-444c-4a19-9db8-113201c38cd4"}{"export_id": "6a0b9ea9-444c-4a19-9db8-113201c38cd4"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
POST /api/v1/organization/{orgname}/exportlogsendpoint to export logs for an Organization:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
POST /api/v1/repository/{repository}/exportlogsendpoint to export logs for a repository:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.7. Adding and managing labels by using the API
Red Hat Quay administrators can add and manage labels for tags with the API by using the following procedure.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Use the
GET /api/v1/repository/{repository}/manifest/{manifestref}command to retrieve the details of a specific manifest in a repository:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/repository/{repository}/manifest/{manifestref}/labelscommand to retrieve a list of labels for a specific manifest:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labelsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"labels": [{"id": "e9f717d2-c1dd-4626-802d-733a029d17ad", "key": "org.opencontainers.image.url", "value": "https://github.com/docker-library/busybox", "source_type": "manifest", "media_type": "text/plain"}, {"id": "2d34ec64-4051-43ad-ae06-d5f81003576a", "key": "org.opencontainers.image.version", "value": "1.36.1-glibc", "source_type": "manifest", "media_type": "text/plain"}]}{"labels": [{"id": "e9f717d2-c1dd-4626-802d-733a029d17ad", "key": "org.opencontainers.image.url", "value": "https://github.com/docker-library/busybox", "source_type": "manifest", "media_type": "text/plain"}, {"id": "2d34ec64-4051-43ad-ae06-d5f81003576a", "key": "org.opencontainers.image.version", "value": "1.36.1-glibc", "source_type": "manifest", "media_type": "text/plain"}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/repository/{repository}/manifest/{manifestref}/labels/{labelid}command to obtain information about a specific manifest:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels/<label_id>
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels/<label_id>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"id": "e9f717d2-c1dd-4626-802d-733a029d17ad", "key": "org.opencontainers.image.url", "value": "https://github.com/docker-library/busybox", "source_type": "manifest", "media_type": "text/plain"}{"id": "e9f717d2-c1dd-4626-802d-733a029d17ad", "key": "org.opencontainers.image.url", "value": "https://github.com/docker-library/busybox", "source_type": "manifest", "media_type": "text/plain"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can add an additional label to a manifest in a given repository with the
POST /api/v1/repository/{repository}/manifest/{manifestref}/labelscommand. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"label": {"id": "346593fd-18c8-49db-854f-4cb1fb76ff9c", "key": "example-key", "value": "example-value", "source_type": "api", "media_type": "text/plain"}}{"label": {"id": "346593fd-18c8-49db-854f-4cb1fb76ff9c", "key": "example-key", "value": "example-value", "source_type": "api", "media_type": "text/plain"}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can delete a label using the
DELETE /api/v1/repository/{repository}/manifest/{manifestref}/labels/{labelid}command:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels/<labelid>
$ curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels/<labelid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI. You can use one of the commands above to ensure that it was successfully removed.
6.8. Using the API to mirror a repository
Red Hat Quay administrators can mirror external repositories by using the API.
Prerequisites
-
You have set
FEATURE_REPO_MIRROR: truein yourconfig.yamlfile.
Procedure
Create a new repository mirror configuration by using the
POST /api/v1/repository/{repository}/mirrorendpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can return information about the mirror configuration by using the
GET /api/v1/repository/{repository}/mirrorendpoint:curl -X GET "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"is_enabled": true, "mirror_type": "PULL", "external_reference": "https://quay.io/repository/argoproj/argocd", "external_registry_username": null, "external_registry_config": {}, "sync_interval": 86400, "sync_start_date": "2025-01-15T12:00:00Z", "sync_expiration_date": null, "sync_retries_remaining": 3, "sync_status": "NEVER_RUN", "root_rule": {"rule_kind": "tag_glob_csv", "rule_value": ["*.latest*"]}, "robot_username": "quayadmin+mirror_robot"}{"is_enabled": true, "mirror_type": "PULL", "external_reference": "https://quay.io/repository/argoproj/argocd", "external_registry_username": null, "external_registry_config": {}, "sync_interval": 86400, "sync_start_date": "2025-01-15T12:00:00Z", "sync_expiration_date": null, "sync_retries_remaining": 3, "sync_status": "NEVER_RUN", "root_rule": {"rule_kind": "tag_glob_csv", "rule_value": ["*.latest*"]}, "robot_username": "quayadmin+mirror_robot"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can use the
POST /api/v1/repository/{repository}/mirror/sync-nowendpoint to sync the repositories. For example:curl -X POST "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror/sync-now" \ -H "Authorization: Bearer <access_token>"$ curl -X POST "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror/sync-now" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
Alternatively, you can cancel the sync with the
POST /api/v1/repository/{repository}/mirror/sync-cancelendpoint.For example:curl -X POST "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror/sync-cancel" \
$ curl -X POST "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror/sync-cancel" \Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
After creating a mirror configuration, you can make changes with the
PUT /api/v1/repository/{repository}/mirrorcommand. For example, you might choose to disable automatic synchronizations:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Disables automatic synchronization.
6.9. Establishing quota with the Red Hat Quay API
You can establish quota for an organization or users, and tailor quota policies to suit the needs of your registry.
The following sections show you how to establish quota for an organization, a user, and then how to modify those settings.
6.9.1. Managing organization quota with the Red Hat Quay API
When an organization is first created, it does not have an established quota. You can use the API to check, create, change, or delete quota limitations for an organization.
Prerequisites
- You have generated an OAuth access token.
Procedure
To set a quota for an organization, you can use the
POST /api/v1/organization/{orgname}/quotaendpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
"Created"
"Created"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/organization/{orgname}/quotacommand to return information about the policy, including the ID number, which is required for other organization quota endpoints. For example:curl -k -X GET -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' https://example-registry-quay-quay-enterprise.apps.docs.gcp.quaydev.org/api/v1/organization/testorg/quota | jq
$ curl -k -X GET -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' https://example-registry-quay-quay-enterprise.apps.docs.gcp.quaydev.org/api/v1/organization/testorg/quota | jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
[{"id": 1, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}][{"id": 1, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}]Copy to Clipboard Copied! Toggle word wrap Toggle overflow After you obtain the ID number, you can use the
GET /api/v1/organization/{orgname}/quota/{quota_id}command to list the quota policy. For example:curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"id": 1, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}{"id": 1, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can use the
PUT /api/v1/organization/{orgname}/quota/{quota_id}command to modify the existing quota limitation. Note that this requires the policy ID. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"id": 1, "limit_bytes": 21474836480, "limit": "20.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}{"id": 1, "limit_bytes": 21474836480, "limit": "20.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow An organization’s quota can be deleted with the
DELETE /api/v1/organization/{orgname}/quota/{quota_id}command. For example:curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>" \ -H "Authorization: Bearer <access_token>"$ curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output.
6.9.2. Setting quota limits for an organization with the Red Hat Quay API
You can set specific quota limits for an organization so that, when exceeded, a warning is returned, or the pushed image is denied altogether.
Procedure
Use the
POST /api/v1/organization/{orgname}/quota/{quota_id}/limitcommand to create a quota policy that rejects images if they exceeded the allotted quota. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
"Created"
"Created"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/organization/{orgname}/quota/{quota_id}/limitto obtain the ID of the quota limit. For example:curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>/limit" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>/limit" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
[{"id": 2, "type": "Reject", "limit_percent": 90}][{"id": 2, "type": "Reject", "limit_percent": 90}]Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Update the policy with the
PUT /api/v1/organization/{orgname}/quota/{quota_id}/limit/{limit_id}endpoint. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"id": 3, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [{"id": 2, "type": "Warning", "limit_percent": 80}], "default_config_exists": false}{"id": 3, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [{"id": 2, "type": "Warning", "limit_percent": 80}], "default_config_exists": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can delete the quota limit with the
DELETE /api/v1/organization/{orgname}/quota/{quota_id}/limit/{limit_id}endpoint:curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>/limit/<limit_id>" \ -H "Authorization: Bearer <access_token>"$ curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>/limit/<limit_id>" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output.
6.9.3. Obtaining quota limits for the user with the Red Hat Quay API
You can specify quota and limitations for users so that, when exceeded, a warning is returned, or the pushed image is denied altogether. Quota limits for users must be set on the Red Hat Quay UI. The following APIs can be used to view the quota limits for the user that is logged in.
Procedure
Use the
GET /api/v1/user/quotacommand to return information about the quota limitations:curl -X GET "https://<quay-server.example.com>/api/v1/user/quota" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/user/quota" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
[{"id": 4, "limit_bytes": 2199023255552, "limit": "2.0 TiB", "default_config": false, "limits": [], "default_config_exists": false}][{"id": 4, "limit_bytes": 2199023255552, "limit": "2.0 TiB", "default_config": false, "limits": [], "default_config_exists": false}]Copy to Clipboard Copied! Toggle word wrap Toggle overflow After you have received the quota ID, you can pass it in with the
GET /api/v1/user/quota/{quota_id}endpoint to return information about the limitation:curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"id": 4, "limit_bytes": 2199023255552, "limit": "2.0 TiB", "default_config": false, "limits": [], "default_config_exists": false}{"id": 4, "limit_bytes": 2199023255552, "limit": "2.0 TiB", "default_config": false, "limits": [], "default_config_exists": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow The limitations can be viewed by using the
GET /api/v1/user/quota/{quota_id}/limitendpoint. For example:curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}/limit" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}/limit" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
[{"id": 3, "type": "Reject", "limit_percent": 100}][{"id": 3, "type": "Reject", "limit_percent": 100}]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Additional information about the entire policy can be returned using the
GET /api/v1/user/quota/{quota_id}/limit/{limit_id}endpoint:curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}/limit/{limit_id}" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}/limit/{limit_id}" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"id": 4, "limit_bytes": 2199023255552, "limit": "2.0 TiB", "default_config": false, "limits": [{"id": 3, "type": "Reject", "limit_percent": 100}], "default_config_exists": false}{"id": 4, "limit_bytes": 2199023255552, "limit": "2.0 TiB", "default_config": false, "limits": [{"id": 3, "type": "Reject", "limit_percent": 100}], "default_config_exists": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.10. Establishing quota with the Red Hat Quay API
Organizations can be created and managed through API endpoints. With the Red Hat Quay API, you can create organizations, view organization information, create proxy caches for an organization, edit users with access to the organization, change organization details, delete organizations, and more.
6.10.1. Creating an organization by using the Red Hat Quay API
Use the following procedure to create a new organization using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following command to create a new organization using the
POST /api/v1/organization/endpoint:curl -X POST -H "Authorization: Bearer <bearer_token>" -H "Content-Type: application/json" -d '{ "name": "<new_organization_name>" }' "https://<quay-server.example.com>/api/v1/organization/"$ curl -X POST -H "Authorization: Bearer <bearer_token>" -H "Content-Type: application/json" -d '{ "name": "<new_organization_name>" }' "https://<quay-server.example.com>/api/v1/organization/"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
"Created"
"Created"Copy to Clipboard Copied! Toggle word wrap Toggle overflow After creation, organization details can be changed, such as adding an email address, with the
PUT /api/v1/organization/{orgname}command. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "test", "email": "new-contact@test-org.com", "avatar": {"name": "test", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "user"}, "is_admin": true, "is_member": true, "teams": {"owners": {"name": "owners", "description": "", "role": "admin", "avatar": {"name": "owners", "hash": "6f0e3a8c0eb46e8834b43b03374ece43a030621d92a7437beb48f871e90f8d90", "color": "#c7c7c7", "kind": "team"}, "can_view": true, "repo_count": 0, "member_count": 1, "is_synced": false}}, "ordered_teams": ["owners"], "invoice_email": true, "invoice_email_address": "billing@test-org.com", "tag_expiration_s": 1209600, "is_free_account": true, "quotas": [{"id": 2, "limit_bytes": 10737418240, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}]}], "quota_report": {"quota_bytes": 0, "configured_quota": 10737418240, "running_backfill": "complete", "backfill_status": "complete"}}{"name": "test", "email": "new-contact@test-org.com", "avatar": {"name": "test", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "user"}, "is_admin": true, "is_member": true, "teams": {"owners": {"name": "owners", "description": "", "role": "admin", "avatar": {"name": "owners", "hash": "6f0e3a8c0eb46e8834b43b03374ece43a030621d92a7437beb48f871e90f8d90", "color": "#c7c7c7", "kind": "team"}, "can_view": true, "repo_count": 0, "member_count": 1, "is_synced": false}}, "ordered_teams": ["owners"], "invoice_email": true, "invoice_email_address": "billing@test-org.com", "tag_expiration_s": 1209600, "is_free_account": true, "quotas": [{"id": 2, "limit_bytes": 10737418240, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}]}], "quota_report": {"quota_bytes": 0, "configured_quota": 10737418240, "running_backfill": "complete", "backfill_status": "complete"}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.10.2. Deleting an organization by using the Red Hat Quay API
Use the following procedure to delete an organization using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following command to delete an organization using the
DELETE /api/v1/organization/{orgname}endpoint:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay-server.example.com>/api/v1/organization/<organization_name>"
$ curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay-server.example.com>/api/v1/organization/<organization_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI does not return information when deleting an organization from the CLI. To confirm deletion, you can check the Red Hat Quay UI, or you can enter the
GET /api/v1/organization/{orgname}command to see if details are returned for the deleted organization:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"detail": "Not Found", "error_message": "Not Found", "error_type": "not_found", "title": "not_found", "type": "http://<quay-server.example.com>/api/v1/error/not_found", "status": 404}{"detail": "Not Found", "error_message": "Not Found", "error_type": "not_found", "title": "not_found", "type": "http://<quay-server.example.com>/api/v1/error/not_found", "status": 404}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.10.3. Retrieving organization member information by using the API
Information about organization members can be retrieved by using the Red Hat Quay API.
Procedure
Use the
GET /api/v1/organization/{orgname}/membersto return a list of organization members:curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/members" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/members" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"members": [{"name": "quayadmin", "kind": "user", "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}, "teams": [{"name": "owners", "avatar": {"name": "owners", "hash": "6f0e3a8c0eb46e8834b43b03374ece43a030621d92a7437beb48f871e90f8d90", "color": "#c7c7c7", "kind": "team"}}], "repositories": ["testrepo"]}, {"name": "testuser", "kind": "user", "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}, "teams": [{"name": "owners", "avatar": {"name": "owners", "hash": "6f0e3a8c0eb46e8834b43b03374ece43a030621d92a7437beb48f871e90f8d90", "color": "#c7c7c7", "kind": "team"}}], "repositories": []}]}{"members": [{"name": "quayadmin", "kind": "user", "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}, "teams": [{"name": "owners", "avatar": {"name": "owners", "hash": "6f0e3a8c0eb46e8834b43b03374ece43a030621d92a7437beb48f871e90f8d90", "color": "#c7c7c7", "kind": "team"}}], "repositories": ["testrepo"]}, {"name": "testuser", "kind": "user", "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}, "teams": [{"name": "owners", "avatar": {"name": "owners", "hash": "6f0e3a8c0eb46e8834b43b03374ece43a030621d92a7437beb48f871e90f8d90", "color": "#c7c7c7", "kind": "team"}}], "repositories": []}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can use the
GET /api/v1/organization/{orgname}/collaboratorsto return a list of organization collaborators:curl -X GET "https://<quay-server.example.com>/api/v1/organization/{orgname}/collaborators" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/{orgname}/collaborators" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"collaborators": [user-test]}{"collaborators": [user-test]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/organization/{orgname}/members/{membername}endpoint to obtain more specific information about a user:curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/members/<membername>" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/members/<membername>" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "quayadmin", "kind": "user", "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}, "teams": [{"name": "owners", "avatar": {"name": "owners", "hash": "6f0e3a8c0eb46e8834b43b03374ece43a030621d92a7437beb48f871e90f8d90", "color": "#c7c7c7", "kind": "team"}}], "repositories": ["testrepo"]}{"name": "quayadmin", "kind": "user", "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}, "teams": [{"name": "owners", "avatar": {"name": "owners", "hash": "6f0e3a8c0eb46e8834b43b03374ece43a030621d92a7437beb48f871e90f8d90", "color": "#c7c7c7", "kind": "team"}}], "repositories": ["testrepo"]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
DELETE /api/v1/organization/{orgname}/members/{membername}endpoint to delete a team member.curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/members/<membername>" \ -H "Authorization: Bearer <access_token>"
$ curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/members/<membername>" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output.
6.10.4. Creating an organization application by using the Red Hat Quay API
Organization applications can be created by using the Red Hat Quay UI.
Organization applications can be created by using the UI, however OAuth 2 access tokens must be created on the UI.
Procedure
Use the
POST /api/v1/organization/{orgname}/applicationsendpoint to create a new application for your organization. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "new-application", "description": "", "application_uri": "", "client_id": "E6GJSHOZMFBVNHTHNB53", "client_secret": "SANSWCWSGLVAUQ60L4Q4CEO3C1QAYGEXZK2VKJNI", "redirect_uri": "", "avatar_email": null}{"name": "new-application", "description": "", "application_uri": "", "client_id": "E6GJSHOZMFBVNHTHNB53", "client_secret": "SANSWCWSGLVAUQ60L4Q4CEO3C1QAYGEXZK2VKJNI", "redirect_uri": "", "avatar_email": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/organization/{orgname}/applicationsendpoint to return a list of all organization applications. For example:curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/applications" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/applications" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"applications": [{"name": "test", "description": "", "application_uri": "", "client_id": "MCJ61D8KQBFS2DXM56S2", "client_secret": "J5G7CCX5QCA8Q5XZLWGI7USJPSM4M5MQHJED46CF", "redirect_uri": "", "avatar_email": null}, {"name": "new-token", "description": "", "application_uri": "", "client_id": "IG58PX2REEY9O08IZFZE", "client_secret": "2LWTWO89KH26P2CO4TWFM7PGCX4V4SUZES2CIZMR", "redirect_uri": "", "avatar_email": null}, {"name": "second-token", "description": "", "application_uri": "", "client_id": "6XBK7QY7ACSCN5XBM3GS", "client_secret": "AVKBOUXTFO3MXBBK5UJD5QCQRN2FWL3O0XPZZT78", "redirect_uri": "", "avatar_email": null}, {"name": "new-application", "description": "", "application_uri": "", "client_id": "E6GJSHOZMFBVNHTHNB53", "client_secret": "SANSWCWSGLVAUQ60L4Q4CEO3C1QAYGEXZK2VKJNI", "redirect_uri": "", "avatar_email": null}]}{"applications": [{"name": "test", "description": "", "application_uri": "", "client_id": "MCJ61D8KQBFS2DXM56S2", "client_secret": "J5G7CCX5QCA8Q5XZLWGI7USJPSM4M5MQHJED46CF", "redirect_uri": "", "avatar_email": null}, {"name": "new-token", "description": "", "application_uri": "", "client_id": "IG58PX2REEY9O08IZFZE", "client_secret": "2LWTWO89KH26P2CO4TWFM7PGCX4V4SUZES2CIZMR", "redirect_uri": "", "avatar_email": null}, {"name": "second-token", "description": "", "application_uri": "", "client_id": "6XBK7QY7ACSCN5XBM3GS", "client_secret": "AVKBOUXTFO3MXBBK5UJD5QCQRN2FWL3O0XPZZT78", "redirect_uri": "", "avatar_email": null}, {"name": "new-application", "description": "", "application_uri": "", "client_id": "E6GJSHOZMFBVNHTHNB53", "client_secret": "SANSWCWSGLVAUQ60L4Q4CEO3C1QAYGEXZK2VKJNI", "redirect_uri": "", "avatar_email": null}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Applications can also be returned for a specific client using the
GET /api/v1/organization/{orgname}/applications/{client_id}endpoint. For example:curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/applications/<client_id>" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/applications/<client_id>" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "test", "description": "", "application_uri": "", "client_id": "MCJ61D8KQBFS2DXM56S2", "client_secret": "J5G7CCX5QCA8Q5XZLWGI7USJPSM4M5MQHJED46CF", "redirect_uri": "", "avatar_email": null}{"name": "test", "description": "", "application_uri": "", "client_id": "MCJ61D8KQBFS2DXM56S2", "client_secret": "J5G7CCX5QCA8Q5XZLWGI7USJPSM4M5MQHJED46CF", "redirect_uri": "", "avatar_email": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow After creation, organization applications can be updated, for example, if you want to add a redirect URI or a new description, using the
PUT /api/v1/organization/{orgname}/applications/{client_id}endpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow After creation, application information can be returned by using the
GET /api/v1/app/{client_id}endpoint:curl -X GET "https://<quay-server.example.com>/api/v1/app/<client_id>" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/app/<client_id>" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "new-application3", "description": "", "uri": "", "avatar": {"name": "new-application3", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "app"}, "organization": {"name": "test", "email": "new-contact@test-org.com", "avatar": {"name": "test", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "user"}, "is_admin": true, "is_member": true, "teams": {}, "ordered_teams": [], "invoice_email": true, "invoice_email_address": "billing@test-org.com", "tag_expiration_s": 1209600, "is_free_account": true, "quotas": [{"id": 2, "limit_bytes": 10737418240, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}]}], "quota_report": {"quota_bytes": 0, "configured_quota": 10737418240, "running_backfill": "complete", "backfill_status": "complete"}}}{"name": "new-application3", "description": "", "uri": "", "avatar": {"name": "new-application3", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "app"}, "organization": {"name": "test", "email": "new-contact@test-org.com", "avatar": {"name": "test", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "user"}, "is_admin": true, "is_member": true, "teams": {}, "ordered_teams": [], "invoice_email": true, "invoice_email_address": "billing@test-org.com", "tag_expiration_s": 1209600, "is_free_account": true, "quotas": [{"id": 2, "limit_bytes": 10737418240, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}]}], "quota_report": {"quota_bytes": 0, "configured_quota": 10737418240, "running_backfill": "complete", "backfill_status": "complete"}}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Organization applications can be deleted with the
DELETE /api/v1/organization/{orgname}/applications/{client_id}endpoint. For example:curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/{orgname}/applications/{client_id}" \ -H "Authorization: Bearer <access_token>"$ curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/{orgname}/applications/{client_id}" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output.
6.10.5. Configuring a proxy cache for an organization by using the Red Hat Quay API
Proxy caching for an organization can be configured by using the Red Hat Quay API.
Procedure
Use the
POST /api/v1/organization/{orgname}/proxycacheendpoint to create a proxy cache configuration for the organization.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
POST /api/v1/organization/{orgname}/validateproxycacheendpoint to validate the proxy configuration:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/organization/{orgname}/proxycacheendpoint to obtain information about the proxcy cache. For example:curl -X GET "https://<quay-server.example.com>/api/v1/organization/{orgname}/proxycache" \ -H "Authorization: Bearer <access_token>"$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/{orgname}/proxycache" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"upstream_registry": "quay.io", "expiration_s": 86400, "insecure": false}{"upstream_registry": "quay.io", "expiration_s": 86400, "insecure": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
DELETE /api/v1/organization/{orgname}/proxycacheendpoint tocurl -X DELETE "https://<quay-server.example.com>/api/v1/organization/{orgname}/proxycache" \ -H "Authorization: Bearer <access_token>"$ curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/{orgname}/proxycache" \ -H "Authorization: Bearer <access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
"Deleted"
"Deleted"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.11. Managing repository permissions by using the Red Hat Quay API
Repository permissions can be managed by using the Red Hat Quay API. For example, you can create, view, and delete user and team permissions.
The following procedures show you how to manage repository permissions by using the Red Hat Quay API.
6.11.1. Managing user permissions by using the Red Hat Quay API
Use the following procedure to manage user permissions by using the Red Hat Quay API.
Procedure
Use the
GET /api/v1/repository/{repository}/permissions/user/{username}endpoint to obtain repository permissions for a user. For example:curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<repository_path>/permissions/user/<username>"
$ curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<repository_path>/permissions/user/<username>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"role": "read", "name": "testuser", "is_robot": false, "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}, "is_org_member": false}$ {"role": "read", "name": "testuser", "is_robot": false, "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}, "is_org_member": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow All user permissions can be returned with the
GET /api/v1/repository/{repository}/permissions/user/endpoint:curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/user/"
$ curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/user/"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"permissions": {"quayadmin": {"role": "admin", "name": "quayadmin", "is_robot": false, "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}, "is_org_member": true}, "test+example": {"role": "admin", "name": "test+example", "is_robot": true, "avatar": {"name": "test+example", "hash": "3b03050c26e900500437beee4f7f2a5855ca7e7c5eab4623a023ee613565a60e", "color": "#a1d99b", "kind": "robot"}, "is_org_member": true}}}{"permissions": {"quayadmin": {"role": "admin", "name": "quayadmin", "is_robot": false, "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}, "is_org_member": true}, "test+example": {"role": "admin", "name": "test+example", "is_robot": true, "avatar": {"name": "test+example", "hash": "3b03050c26e900500437beee4f7f2a5855ca7e7c5eab4623a023ee613565a60e", "color": "#a1d99b", "kind": "robot"}, "is_org_member": true}}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can use the
GET /api/v1/repository/{repository}/permissions/user/{username}/transitiveendpoint to return only the repository permission for the user:curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<repository_path>/permissions/user/<username>/transitive"
$ curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<repository_path>/permissions/user/<username>/transitive"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"permissions": [{"role": "admin"}]}{"permissions": [{"role": "admin"}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can change the user’s permissions, such as making the user an
adminby using thePUT /api/v1/repository/{repository}/permissions/user/{username}endpoint. For example:curl -X PUT \ -H "Authorization: Bearer <access_token>" \ -H "Content-Type: application/json" \ -d '{"role": "<role>"}' \ "https://quay-server.example.com/api/v1/repository/<repository_path>/permissions/user/<username>"$ curl -X PUT \ -H "Authorization: Bearer <access_token>" \ -H "Content-Type: application/json" \ -d '{"role": "<role>"}' \ "https://quay-server.example.com/api/v1/repository/<repository_path>/permissions/user/<username>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"role": "admin", "name": "testuser", "is_robot": false, "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}, "is_org_member": false}{"role": "admin", "name": "testuser", "is_robot": false, "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}, "is_org_member": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow User permissions can be deleted by using the
DELETE /api/v1/repository/{repository}/permissions/user/{username}endpoint. For example:curl -X DELETE \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/user/<username>"
$ curl -X DELETE \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/user/<username>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output.
6.11.2. Managing team permissions by using the Red Hat Quay API
Use the following procedure to manage team permissions by using the Red Hat Quay API.
Permissions for a specified team can be returned by using the
GET /api/v1/repository/{repository}/permissions/team/{teamname}endpoint:curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"
$ curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"role": "write"}{"role": "write"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Permissions for all teams can be returned with the
GET /api/v1/repository/{repository}/permissions/team/endpoint. For example:curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/"
$ curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"permissions": {"ironmanteam": {"role": "read", "name": "ironmanteam", "avatar": {"name": "ironmanteam", "hash": "8045b2361613622183e87f33a7bfc54e100a41bca41094abb64320df29ef458d", "color": "#969696", "kind": "team"}}, "sillyteam": {"role": "read", "name": "sillyteam", "avatar": {"name": "sillyteam", "hash": "f275d39bdee2766d2404e2c6dbff28fe290969242e9fcf1ffb2cde36b83448ff", "color": "#17becf", "kind": "team"}}}}{"permissions": {"ironmanteam": {"role": "read", "name": "ironmanteam", "avatar": {"name": "ironmanteam", "hash": "8045b2361613622183e87f33a7bfc54e100a41bca41094abb64320df29ef458d", "color": "#969696", "kind": "team"}}, "sillyteam": {"role": "read", "name": "sillyteam", "avatar": {"name": "sillyteam", "hash": "f275d39bdee2766d2404e2c6dbff28fe290969242e9fcf1ffb2cde36b83448ff", "color": "#17becf", "kind": "team"}}}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Permissions for a specified team can be changed by using the
PUT /api/v1/repository/{repository}/permissions/team/{teamname}command. For example:curl -X PUT \ -H "Authorization: Bearer <access_token>" \ -H "Content-Type: application/json" \ -d '{"role": "<role>"}' \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"$ curl -X PUT \ -H "Authorization: Bearer <access_token>" \ -H "Content-Type: application/json" \ -d '{"role": "<role>"}' \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"role": "admin", "name": "superteam", "avatar": {"name": "superteam", "hash": "48cb6d114200039fed5c601480653ae7371d5a8849521d4c3bf2418ea013fc0f", "color": "#9467bd", "kind": "team"}}{"role": "admin", "name": "superteam", "avatar": {"name": "superteam", "hash": "48cb6d114200039fed5c601480653ae7371d5a8849521d4c3bf2418ea013fc0f", "color": "#9467bd", "kind": "team"}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Team permissions can be deleted with the
DELETE /api/v1/repository/{repository}/permissions/team/{teamname}command. For example:curl -X DELETE \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"
$ curl -X DELETE \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
6.12. Managing auto-prune policies by using the Red Hat Quay API
Auto-prune policies can be created, retrieved, changed, and delete for organizations, repositories, and users by using the Red Hat Quay API.
Procedure
Enter the following command to create a repository using the
POST /api/v1/repositoryendpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"namespace": "quayadmin", "name": "<new_repository_name>", "kind": "image"}{"namespace": "quayadmin", "name": "<new_repository_name>", "kind": "image"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can list a repositories with the
GET /api/v1/repositoryendpoint. For example:curl -X GET \ -H "Authorization: Bearer <ACCESS_TOKEN>" \ "https://quay-server.example.com/api/v1/repository?public=true&starred=false&namespace=<NAMESPACE>"
$ curl -X GET \ -H "Authorization: Bearer <ACCESS_TOKEN>" \ "https://quay-server.example.com/api/v1/repository?public=true&starred=false&namespace=<NAMESPACE>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"repositories": [{"namespace": "quayadmin", "name": "busybox", "description": null, "is_public": false, "kind": "image", "state": "MIRROR", "is_starred": false, "quota_report": {"quota_bytes": 2280675, "configured_quota": 2199023255552}}]}{"repositories": [{"namespace": "quayadmin", "name": "busybox", "description": null, "is_public": false, "kind": "image", "state": "MIRROR", "is_starred": false, "quota_report": {"quota_bytes": 2280675, "configured_quota": 2199023255552}}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Visibility can be changed from public to private with the
POST /api/v1/repository/{repository}/changevisibilityendpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"success": true}{"success": true}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can check the Red Hat Quay UI, or you can enter the following
GET /api/v1/repository/{repository}command to return details about a repository:curl -X GET -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"detail": "Not Found", "error_message": "Not Found", "error_type": "not_found", "title": "not_found", "type": "http://quay-server.example.com/api/v1/error/not_found", "status": 404}{"detail": "Not Found", "error_message": "Not Found", "error_type": "not_found", "title": "not_found", "type": "http://quay-server.example.com/api/v1/error/not_found", "status": 404}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Repository descriptions can be updated with the
PUT /api/v1/repository/{repository}endpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"success": true}{"success": true}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to delete a repository using the
DELETE /api/v1/repository/{repository}endpoint:curl -X DELETE -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"
$ curl -X DELETE -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
6.12.1. Creating an auto-prune policy for a namespace by using the Red Hat Quay API
You can use Red Hat Quay API endpoints to manage auto-pruning policies for an namespace.
Prerequisites
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile. - You have created an OAuth access token.
- You have logged into Red Hat Quay.
Procedure
Enter the following
POST /api/v1/organization/{orgname}/autoprunepolicy/command create a new policy that limits the number of tags allowed in an organization:curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags", "value": 10}' http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags", "value": 10}' http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can can set tags to expire for a specified time after their creation date:
curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{ "method": "creation_date", "value": "7d"}' http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{ "method": "creation_date", "value": "7d"}' http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"uuid": "73d64f05-d587-42d9-af6d-e726a4a80d6e"}{"uuid": "73d64f05-d587-42d9-af6d-e726a4a80d6e"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional. You can add an additional policy to an organization and pass in the
tagPatternandtagPatternMatchesfields to prune only tags that match the given regex pattern. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Setting
tagPatternMatchestotruemakes it so that tags that match the given regex pattern will be pruned. In this example, tags that match^v*are pruned.
Example output
{"uuid": "ebf7448b-93c3-4f14-bf2f-25aa6857c7b0"}{"uuid": "ebf7448b-93c3-4f14-bf2f-25aa6857c7b0"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can update your organization’s auto-prune policy by using the
PUT /api/v1/organization/{orgname}/autoprunepolicy/{policy_uuid}command. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output. Continue to the next step.
Check your auto-prune policy by entering the following command:
curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"policies": [{"uuid": "ebf7448b-93c3-4f14-bf2f-25aa6857c7b0", "method": "creation_date", "value": "4d", "tagPattern": "^v*", "tagPatternMatches": true}, {"uuid": "da4d0ad7-3c2d-4be8-af63-9c51f9a501bc", "method": "number_of_tags", "value": 10, "tagPattern": null, "tagPatternMatches": true}, {"uuid": "17b9fd96-1537-4462-a830-7f53b43f94c2", "method": "creation_date", "value": "7d", "tagPattern": "^v*", "tagPatternMatches": true}]}{"policies": [{"uuid": "ebf7448b-93c3-4f14-bf2f-25aa6857c7b0", "method": "creation_date", "value": "4d", "tagPattern": "^v*", "tagPatternMatches": true}, {"uuid": "da4d0ad7-3c2d-4be8-af63-9c51f9a501bc", "method": "number_of_tags", "value": 10, "tagPattern": null, "tagPatternMatches": true}, {"uuid": "17b9fd96-1537-4462-a830-7f53b43f94c2", "method": "creation_date", "value": "7d", "tagPattern": "^v*", "tagPatternMatches": true}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can delete the auto-prune policy for your organization by entering the following command. Note that deleting the policy requires the UUID.
curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/73d64f05-d587-42d9-af6d-e726a4a80d6e
$ curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/73d64f05-d587-42d9-af6d-e726a4a80d6eCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.12.2. Creating an auto-prune policy for a namespace for the current user by using the API
You can use Red Hat Quay API endpoints to manage auto-pruning policies for your account.
The use of /user/ in the following commands represents the user that is currently logged into Red Hat Quay.
Prerequisites
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile. - You have created an OAuth access token.
- You have logged into Red Hat Quay.
Procedure
Enter the following
POSTcommand create a new policy that limits the number of tags for the current user:curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags", "value": 10}' http://<quay-server.example.com>/api/v1/user/autoprunepolicy/$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags", "value": 10}' http://<quay-server.example.com>/api/v1/user/autoprunepolicy/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"uuid": "8c03f995-ca6f-4928-b98d-d75ed8c14859"}{"uuid": "8c03f995-ca6f-4928-b98d-d75ed8c14859"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check your auto-prune policy by entering the following command:
curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/user/autoprunepolicy/
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/user/autoprunepolicy/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can include the UUID:
curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/user/autoprunepolicy/8c03f995-ca6f-4928-b98d-d75ed8c14859
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/user/autoprunepolicy/8c03f995-ca6f-4928-b98d-d75ed8c14859Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"policies": [{"uuid": "8c03f995-ca6f-4928-b98d-d75ed8c14859", "method": "number_of_tags", "value": 10}]}{"policies": [{"uuid": "8c03f995-ca6f-4928-b98d-d75ed8c14859", "method": "number_of_tags", "value": 10}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can delete the auto-prune policy by entering the following command. Note that deleting the policy requires the UUID.
curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/user/autoprunepolicy/8c03f995-ca6f-4928-b98d-d75ed8c14859
$ curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/user/autoprunepolicy/8c03f995-ca6f-4928-b98d-d75ed8c14859Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"uuid": "8c03f995-ca6f-4928-b98d-d75ed8c14859"}{"uuid": "8c03f995-ca6f-4928-b98d-d75ed8c14859"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.12.3. Creating an auto-prune policy for a repository using the Red Hat Quay API
You can use Red Hat Quay API endpoints to manage auto-pruning policies for an repository.
Prerequisites
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile. - You have created an OAuth access token.
- You have logged into Red Hat Quay.
Procedure
Enter the following
POST /api/v1/repository/{repository}/autoprunepolicy/command create a new policy that limits the number of tags allowed in an organization:curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags","value": 2}' http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags","value": 2}' http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can can set tags to expire for a specified time after their creation date:
curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "creation_date", "value": "7d"}' http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "creation_date", "value": "7d"}' http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"uuid": "ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7"}{"uuid": "ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional. You can add an additional policy and pass in the
tagPatternandtagPatternMatchesfields to prune only tags that match the given regex pattern. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Setting
tagPatternMatchestofalsemakes it so that tags that all tags that do not match the given regex pattern are pruned. In this example, all tags but^test.are pruned.
Example output
{"uuid": "b53d8d3f-2e73-40e7-96ff-736d372cd5ef"}{"uuid": "b53d8d3f-2e73-40e7-96ff-736d372cd5ef"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can update your policy for the repository by using the
PUT /api/v1/repository/{repository}/autoprunepolicy/{policy_uuid}command and passing in the UUID. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output. Continue to the next step to check your auto-prune policy.
Check your auto-prune policy by entering the following command:
curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can include the UUID:
curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"policies": [{"uuid": "ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7", "method": "number_of_tags", "value": 10}]}{"policies": [{"uuid": "ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7", "method": "number_of_tags", "value": 10}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can delete the auto-prune policy by entering the following command. Note that deleting the policy requires the UUID.
curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7
$ curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"uuid": "ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7"}{"uuid": "ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.12.4. Creating an auto-prune policy on a repository for a user with the API
You can use Red Hat Quay API endpoints to manage auto-pruning policies on a repository for user accounts that are not your own, so long as you have admin privileges on the repository.
Prerequisites
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile. - You have created an OAuth access token.
- You have logged into Red Hat Quay.
-
You have
adminprivileges on the repository that you are creating the policy for.
Procedure
Enter the following
POST /api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/command create a new policy that limits the number of tags for the user:curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags","value": 2}' https://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags","value": 2}' https://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"uuid": "7726f79c-cbc7-490e-98dd-becdc6fefce7"}{"uuid": "7726f79c-cbc7-490e-98dd-becdc6fefce7"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional. You can add an additional policy for the current user and pass in the
tagPatternandtagPatternMatchesfields to prune only tags that match the given regex pattern. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"uuid": "b3797bcd-de72-4b71-9b1e-726dabc971be"}{"uuid": "b3797bcd-de72-4b71-9b1e-726dabc971be"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can update your policy for the current user by using the
PUT /api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/<policy_uuid>command. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Updating a policy does not return output in the CLI.
Check your auto-prune policy by entering the following command:
curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can include the UUID:
curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/7726f79c-cbc7-490e-98dd-becdc6fefce7
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/7726f79c-cbc7-490e-98dd-becdc6fefce7Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"uuid": "81ee77ec-496a-4a0a-9241-eca49437d15b", "method": "creation_date", "value": "7d", "tagPattern": "^v*", "tagPatternMatches": true}{"uuid": "81ee77ec-496a-4a0a-9241-eca49437d15b", "method": "creation_date", "value": "7d", "tagPattern": "^v*", "tagPatternMatches": true}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can delete the auto-prune policy by entering the following command. Note that deleting the policy requires the UUID.
curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/<policy_uuid>
$ curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/<policy_uuid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"uuid": "7726f79c-cbc7-490e-98dd-becdc6fefce7"}{"uuid": "7726f79c-cbc7-490e-98dd-becdc6fefce7"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.13. Creating and configuring repositories by using the Red Hat Quay API
Repositories can be created, retrieved, changed, and deleted by using the Red Hat Quay API.
6.13.1. Creating and configuring repositories by using the Red Hat Quay API
Repositories can be created, retrieved, changed, and deleted by using the Red Hat Quay API.
Procedure
Enter the following command to create a repository using the
POST /api/v1/repositoryendpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"namespace": "quayadmin", "name": "<new_repository_name>", "kind": "image"}{"namespace": "quayadmin", "name": "<new_repository_name>", "kind": "image"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can list a repositories with the
GET /api/v1/repositoryendpoint. For example:curl -X GET \ -H "Authorization: Bearer <ACCESS_TOKEN>" \ "https://quay-server.example.com/api/v1/repository?public=true&starred=false&namespace=<NAMESPACE>"
$ curl -X GET \ -H "Authorization: Bearer <ACCESS_TOKEN>" \ "https://quay-server.example.com/api/v1/repository?public=true&starred=false&namespace=<NAMESPACE>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"repositories": [{"namespace": "quayadmin", "name": "busybox", "description": null, "is_public": false, "kind": "image", "state": "MIRROR", "is_starred": false, "quota_report": {"quota_bytes": 2280675, "configured_quota": 2199023255552}}]}{"repositories": [{"namespace": "quayadmin", "name": "busybox", "description": null, "is_public": false, "kind": "image", "state": "MIRROR", "is_starred": false, "quota_report": {"quota_bytes": 2280675, "configured_quota": 2199023255552}}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Visibility can be changed from public to private with the
POST /api/v1/repository/{repository}/changevisibilityendpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"success": true}{"success": true}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can check the Red Hat Quay UI, or you can enter the following
GET /api/v1/repository/{repository}command to return details about a repository:curl -X GET -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"detail": "Not Found", "error_message": "Not Found", "error_type": "not_found", "title": "not_found", "type": "http://quay-server.example.com/api/v1/error/not_found", "status": 404}{"detail": "Not Found", "error_message": "Not Found", "error_type": "not_found", "title": "not_found", "type": "http://quay-server.example.com/api/v1/error/not_found", "status": 404}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Repository descriptions can be updated with the
PUT /api/v1/repository/{repository}endpoint:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"success": true}{"success": true}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to delete a repository using the
DELETE /api/v1/repository/{repository}endpoint:curl -X DELETE -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"
$ curl -X DELETE -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
6.13.2. Creating notifications by using the API
Use the following procedure to add notifications.
Prerequisites
- You have created a repository.
- You have administrative privileges for the repository.
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following
POST /api/v1/repository/{repository}/notificationcommand to create a notification on your repository:Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI. Instead, you can enter the following
GET /api/v1/repository/{repository}/notification/{uuid}command to obtain information about the repository notification:{"uuid": "240662ea-597b-499d-98bb-2b57e73408d6", "title": null, "event": "repo_push", "method": "quay_notification", "config": {"target": {"name": "quayadmin", "kind": "user", "is_robot": false, "avatar": {"name": "quayadmin", "hash": "b28d563a6dc76b4431fc7b0524bbff6b810387dac86d9303874871839859c7cc", "color": "#17becf", "kind": "user"}}}, "event_config": {}, "number_of_failures": 0}{"uuid": "240662ea-597b-499d-98bb-2b57e73408d6", "title": null, "event": "repo_push", "method": "quay_notification", "config": {"target": {"name": "quayadmin", "kind": "user", "is_robot": false, "avatar": {"name": "quayadmin", "hash": "b28d563a6dc76b4431fc7b0524bbff6b810387dac86d9303874871839859c7cc", "color": "#17becf", "kind": "user"}}}, "event_config": {}, "number_of_failures": 0}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can test your repository notification by entering the following
POST /api/v1/repository/{repository}/notification/{uuid}/testcommand:curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<repository>/notification/<uuid>/test
$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<repository>/notification/<uuid>/testCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{}{}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can reset repository notification failures to 0 by entering the following
POST /api/v1/repository/{repository}/notification/{uuid}command:curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<repository>/notification/<uuid>
$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<repository>/notification/<uuid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following
DELETE /api/v1/repository/{repository}/notification/{uuid}command to delete a repository notification:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>/notification/<uuid>
$ curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>/notification/<uuid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI. Instead, you can enter the following
GET /api/v1/repository/{repository}/notification/command to retrieve a list of all notifications:curl -X GET -H "Authorization: Bearer <bearer_token>" -H "Accept: application/json" https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>/notification
$ curl -X GET -H "Authorization: Bearer <bearer_token>" -H "Accept: application/json" https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>/notificationCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"notifications": []}{"notifications": []}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.14. Creating and configuring robot accounts by using the Red Hat Quay API
Robot accounts can be created, retrieved, changed, and deleted for both organizations and users by using the Red Hat Quay API.
6.14.1. Creating a robot account by using the Red Hat Quay API
Use the following procedure to create a robot account using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following command to create a new robot account for an organization using the
PUT /api/v1/organization/{orgname}/robots/{robot_shortname}endpoint:curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_name>"
$ curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "orgname+robot-name", "created": "Fri, 10 May 2024 15:11:00 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}{"name": "orgname+robot-name", "created": "Fri, 10 May 2024 15:11:00 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to create a new robot account for the current user with the
PUT /api/v1/user/robots/{robot_shortname}endpoint:curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/user/robots/<robot_name>"
$ curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/user/robots/<robot_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "quayadmin+robot-name", "created": "Fri, 10 May 2024 15:24:57 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}{"name": "quayadmin+robot-name", "created": "Fri, 10 May 2024 15:24:57 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.14.2. Obtaining robot account information by using the Red Hat Quay API
Robot account information, such as permissions, can be obtained for both organizations and users by using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Use the
GET /api/v1/organization/{orgname}/robots/{robot_shortname}API endpoint to return information for a robot for an organization:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/organization/<ORGNAME>/robots/<ROBOT_SHORTNAME>"
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/organization/<ORGNAME>/robots/<ROBOT_SHORTNAME>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "test+example", "created": "Mon, 25 Nov 2024 16:25:16 -0000", "last_accessed": null, "description": "", "token": "BILZ6YTVAZAKOGMD9270OKN3SOD9KPB7OLKEJQOJE38NBBRUJTIH7T5859DJL31Q", "unstructured_metadata": {}}{"name": "test+example", "created": "Mon, 25 Nov 2024 16:25:16 -0000", "last_accessed": null, "description": "", "token": "BILZ6YTVAZAKOGMD9270OKN3SOD9KPB7OLKEJQOJE38NBBRUJTIH7T5859DJL31Q", "unstructured_metadata": {}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/organization/{orgname}/robots/{robot_shortname}/permissionsendpoint to return the list of permissions for a specific organization robot:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/organization/<ORGNAME>/robots/<ROBOT_SHORTNAME>/permissions"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/organization/<ORGNAME>/robots/<ROBOT_SHORTNAME>/permissions"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"permissions": [{"repository": {"name": "testrepo", "is_public": true}, "role": "admin"}]}{"permissions": [{"repository": {"name": "testrepo", "is_public": true}, "role": "admin"}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/user/robots/{robot_shortname}API endpoint to return the user’s robot with the specified name:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/user/robots/<ROBOT_SHORTNAME>"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/user/robots/<ROBOT_SHORTNAME>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "quayadmin+mirror_robot", "created": "Wed, 15 Jan 2025 17:22:09 -0000", "last_accessed": null, "description": "", "token": "QBFYWIWZOS1I0P0R9N1JRNP1UZAOPUIR3EB4ASPZKK9IA1SFC12LTEF7OJHB05Z8", "unstructured_metadata": {}}{"name": "quayadmin+mirror_robot", "created": "Wed, 15 Jan 2025 17:22:09 -0000", "last_accessed": null, "description": "", "token": "QBFYWIWZOS1I0P0R9N1JRNP1UZAOPUIR3EB4ASPZKK9IA1SFC12LTEF7OJHB05Z8", "unstructured_metadata": {}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/user/robots/{robot_shortname}/permissionsAPI endpoint to return a list of permissions for the user robot:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/user/robots/<ROBOT_SHORTNAME>/permissions"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/user/robots/<ROBOT_SHORTNAME>/permissions"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"permissions": [{"repository": {"name": "busybox", "is_public": false}, "role": "write"}]}{"permissions": [{"repository": {"name": "busybox", "is_public": false}, "role": "write"}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.14.3. Deleting a robot account by using the Red Hat Quay API
Use the following procedure to delete a robot account using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following command to delete a robot account for an organization using the
DELETE /api/v1/organization/{orgname}/robots/{robot_shortname}endpoint:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_shortname>"
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI does not return information when deleting a robot account with the API. To confirm deletion, you can check the Red Hat Quay UI, or you can enter the following
GET /api/v1/organization/{orgname}/robotscommand to see if details are returned for the robot account:curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"robots": []}{"robots": []}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to delete a robot account for the current user with the
DELETE /api/v1/user/robots/{robot_shortname}endpoint:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"
$ curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI does not return information when deleting a robot account for the current user with the API. To confirm deletion, you can check the Red Hat Quay UI, or you can enter the following
GET /api/v1/user/robots/{robot_shortname}command to see if details are returned for the robot account:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"message":"Could not find robot with specified username"}{"message":"Could not find robot with specified username"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.15. Searching against registry context
You can use search API endpoints to perform searches against all registry context.
Procedure
Use the
GET /api/v1/find/repositoriesendpoint to get a list of apps and repositories that match the specified query:curl -X GET "https://quay-server.example.com/api/v1/find/repositories?query=<repo_name>&page=1&includeUsage=true" \ -H "Authorization: Bearer <bearer_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/find/repositories?query=<repo_name>&page=1&includeUsage=true" \ -H "Authorization: Bearer <bearer_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"results": [], "has_additional": false, "page": 2, "page_size": 10, "start_index": 10}{"results": [], "has_additional": false, "page": 2, "page_size": 10, "start_index": 10}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/find/allendpoint to get a list of entities and resources that match the specified query:curl -X GET "https://quay-server.example.com/api/v1/find/all?query=<mysearchterm>" \ -H "Authorization: Bearer <bearer_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/find/all?query=<mysearchterm>" \ -H "Authorization: Bearer <bearer_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"results": [{"kind": "repository", "title": "repo", "namespace": {"title": "user", "kind": "user", "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}, "name": "quayadmin", "score": 1, "href": "/user/quayadmin"}, "name": "busybox", "description": null, "is_public": false, "score": 4.0, "href": "/repository/quayadmin/busybox"}]}{"results": [{"kind": "repository", "title": "repo", "namespace": {"title": "user", "kind": "user", "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}, "name": "quayadmin", "score": 1, "href": "/user/quayadmin"}, "name": "busybox", "description": null, "is_public": false, "score": 4.0, "href": "/repository/quayadmin/busybox"}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/entities/{prefix}endpoint to get a list of entities that match the specified prefix.curl -X GET "https://quay-server.example.com/api/v1/entities/<prefix>?includeOrgs=<true_or_false>&includeTeams=<true_or_false>&namespace=<namespace>" \ -H "Authorization: Bearer <bearer_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/entities/<prefix>?includeOrgs=<true_or_false>&includeTeams=<true_or_false>&namespace=<namespace>" \ -H "Authorization: Bearer <bearer_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"results": [{"name": "quayadmin", "kind": "user", "is_robot": false, "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}}]}{"results": [{"name": "quayadmin", "kind": "user", "is_robot": false, "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.16. View Clair security scans by using the API
You can view Clair security scans by using the API.
Procedure
Use the
GET /api/v1/repository/{repository}/manifest/{manifestref}/securityendpoint to retrieve security information about a specific manifest in a repository. For example:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/manifest/<manifest_digest>/security?vulnerabilities=<true_or_false>"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/manifest/<manifest_digest>/security?vulnerabilities=<true_or_false>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"status": "queued", "data": null}{"status": "queued", "data": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.17. Managing your deployment as a superuser with the Red Hat Quay API
Through the Red Hat Quay UI, superusers have the ability to create, list, change, and delete aspects of the registry, such as users, service keys, a user’s quota, and more.
6.17.1. Creating a user account by using the Red Hat Quay API
Use the following procedure to create a new user for your Red Hat Quay repository by using the API.
Prerequisites
- You are logged into your Red Hat Quay deployment as a superuser.
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following command to create a new user using the
POST /api/v1/superuser/users/endpoint:curl -X POST -H "Authorization: Bearer <bearer_token>" -H "Content-Type: application/json" -d '{ "username": "newuser", "email": "newuser@example.com" }' "https://<quay-server.example.com>/api/v1/superuser/users/"$ curl -X POST -H "Authorization: Bearer <bearer_token>" -H "Content-Type: application/json" -d '{ "username": "newuser", "email": "newuser@example.com" }' "https://<quay-server.example.com>/api/v1/superuser/users/"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"username": "newuser", "email": "newuser@example.com", "password": "123456789", "encrypted_password": "<example_encrypted_password>/JKY9pnDcsw="}{"username": "newuser", "email": "newuser@example.com", "password": "123456789", "encrypted_password": "<example_encrypted_password>/JKY9pnDcsw="}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Navigate to your Red Hat Quay registry endpoint, for example,
quay-server.example.comand login with the username and password generated from the API call. In this scenario, the username isnewuserand the password is123456789. Alternatively, you can log in to the registry with the CLI. For example:podman login <quay-server.example.com>
$ podman login <quay-server.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
username: newuser password: 123456789
username: newuser password: 123456789Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional. You can obtain a list of all users, including superusers, by using the
GET /api/v1/superuser/users/endpoint:curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/superuser/users/"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/superuser/users/"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"users": [{"kind": "user", "name": "quayadmin", "username": "quayadmin", "email": "quay@quay.com", "verified": true, "avatar": {"name": "quayadmin", "hash": "b28d563a6dc76b4431fc7b0524bbff6b810387dac86d9303874871839859c7cc", "color": "#17becf", "kind": "user"}, "super_user": true, "enabled": true}, {"kind": "user", "name": "newuser", "username": "newuser", "email": "newuser@example.com", "verified": true, "avatar": {"name": "newuser", "hash": "f338a2c83bfdde84abe2d3348994d70c34185a234cfbf32f9e323e3578e7e771", "color": "#9edae5", "kind": "user"}, "super_user": false, "enabled": true}]}{"users": [{"kind": "user", "name": "quayadmin", "username": "quayadmin", "email": "quay@quay.com", "verified": true, "avatar": {"name": "quayadmin", "hash": "b28d563a6dc76b4431fc7b0524bbff6b810387dac86d9303874871839859c7cc", "color": "#17becf", "kind": "user"}, "super_user": true, "enabled": true}, {"kind": "user", "name": "newuser", "username": "newuser", "email": "newuser@example.com", "verified": true, "avatar": {"name": "newuser", "hash": "f338a2c83bfdde84abe2d3348994d70c34185a234cfbf32f9e323e3578e7e771", "color": "#9edae5", "kind": "user"}, "super_user": false, "enabled": true}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.17.2. Deleting a user by using the Red Hat Quay API
Use the following procedure to delete a user from Red Hat Quay using the API.
After deleting the user, any repositories that this user had in his private account become unavailable.
Prerequisites
- You are logged into your Red Hat Quay deployment as a superuser.
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following
DELETE /api/v1/superuser/users/{username}command to delete a user from the command line:curl -X DELETE -H "Authorization: Bearer <insert token here>" https://<quay-server.example.com>/api/v1/superuser/users/<username>
$ curl -X DELETE -H "Authorization: Bearer <insert token here>" https://<quay-server.example.com>/api/v1/superuser/users/<username>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI does not return information when deleting a user from the CLI. To confirm deletion, you can check the Red Hat Quay UI by navigating to Superuser Admin Panel → Users, or by entering the following
GET /api/v1/superuser/users/command. You can then check to see if they are present.curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/superuser/users/"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/superuser/users/"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.17.3. Managing organizations as a superuser with the Red Hat Quay API
Superusers have the ability to list, change, and delete organizations by using the Red Hat Quay API.
Procedure
Use the
GET /api/v1/superuser/organizationsendpoint to list all organizations:curl -L -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/organizations?name=<organization_name>"
$ curl -L -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/organizations?name=<organization_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"organizations": [{"name": "fed_test", "email": "fe11fc59-bd09-459a-a21c-b57692d151c9", "avatar": {"name": "fed_test", "hash": "e2ce1fb42ec2e0602362beb64b5ebd1e6ad291b710a0355f9296c16157bef3cb", "color": "#ff7f0e", "kind": "org"}, "quotas": [{"id": 3, "limit_bytes": 10737418240, "limits": []}], "quota_report": {"quota_bytes": 0, "configured_quota": 10737418240, "running_backfill": "complete", "backfill_status": "complete"}}, {"name": "test", "email": "new-contact@test-org.com", "avatar": {"name": "test", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "org"}, "quotas": [{"id": 2, "limit_bytes": 10737418240, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}]}], "quota_report": {"quota_bytes": 0, "configured_quota": 10737418240, "running_backfill": "complete", "backfill_status": "complete"}}]}{"organizations": [{"name": "fed_test", "email": "fe11fc59-bd09-459a-a21c-b57692d151c9", "avatar": {"name": "fed_test", "hash": "e2ce1fb42ec2e0602362beb64b5ebd1e6ad291b710a0355f9296c16157bef3cb", "color": "#ff7f0e", "kind": "org"}, "quotas": [{"id": 3, "limit_bytes": 10737418240, "limits": []}], "quota_report": {"quota_bytes": 0, "configured_quota": 10737418240, "running_backfill": "complete", "backfill_status": "complete"}}, {"name": "test", "email": "new-contact@test-org.com", "avatar": {"name": "test", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "org"}, "quotas": [{"id": 2, "limit_bytes": 10737418240, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}]}], "quota_report": {"quota_bytes": 0, "configured_quota": 10737418240, "running_backfill": "complete", "backfill_status": "complete"}}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
PUT /api/v1/superuser/organizations/{name}endpoint to change or update information for an organization:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "test", "email": "new-contact@test-org.com", "avatar": {"name": "test", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "org"}, "quotas": [{"id": 2, "limit_bytes": 10737418240, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}]}], "quota_report": {"quota_bytes": 0, "configured_quota": 10737418240, "running_backfill": "complete", "backfill_status": "complete"}}{"name": "test", "email": "new-contact@test-org.com", "avatar": {"name": "test", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "org"}, "quotas": [{"id": 2, "limit_bytes": 10737418240, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}]}], "quota_report": {"quota_bytes": 0, "configured_quota": 10737418240, "running_backfill": "complete", "backfill_status": "complete"}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
DELETE /api/v1/superuser/organizations/{name}endpoint to delete and organization:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/organizations/<organization_name>"
$ curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/organizations/<organization_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
6.17.4. Listing logs as a superuser with the Red Hat Quay API
Red Hat Quay superusers can list usage logs for the current system.
Procedure
Use the
GET /api/v1/superuser/logsendpoint to list the usage logs for the current system:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/logs?starttime=<start_time>&endtime=<end_time>&page=<page_number>&next_page=<next_page_token>"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/logs?starttime=<start_time>&endtime=<end_time>&page=<page_number>&next_page=<next_page_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"start_time": "Mon, 17 Feb 2025 19:29:14 -0000", "end_time": "Wed, 19 Feb 2025 19:29:14 -0000", "logs": [{"kind": "login_success", "metadata": {"type": "quayauth", "useragent": "Mozilla/5.0 (X11; Linux x86_64; rv:134.0) Gecko/20100101 Firefox/134.0"}, "ip": "192.168.1.131", "datetime": "Tue, 18 Feb 2025 19:28:15 -0000", "namespace": {"kind": "user", "name": "quayadmin", "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}}}], "next_page": "gAAAAABntN-KbPJDI0PpcHmWjRCmQTLiCprE_KXiOSidbGZ7Ireu8pVTgGUIstijNhmiLzlAv_S3HOsCrKWnuBmoQYZ3F53Uxg=="}{"start_time": "Mon, 17 Feb 2025 19:29:14 -0000", "end_time": "Wed, 19 Feb 2025 19:29:14 -0000", "logs": [{"kind": "login_success", "metadata": {"type": "quayauth", "useragent": "Mozilla/5.0 (X11; Linux x86_64; rv:134.0) Gecko/20100101 Firefox/134.0"}, "ip": "192.168.1.131", "datetime": "Tue, 18 Feb 2025 19:28:15 -0000", "namespace": {"kind": "user", "name": "quayadmin", "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}}}], "next_page": "gAAAAABntN-KbPJDI0PpcHmWjRCmQTLiCprE_KXiOSidbGZ7Ireu8pVTgGUIstijNhmiLzlAv_S3HOsCrKWnuBmoQYZ3F53Uxg=="}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/superuser/registrysize/end point to obtain information about the size of the registry:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/registrysize/"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/registrysize/"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"size_bytes": 0, "last_ran": null, "running": false, "queued": false}{"size_bytes": 0, "last_ran": null, "running": false, "queued": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
POST /api/v1/superuser/registrysize/end point to define registry size information:Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
6.17.5. Managing organization quota with the Red Hat Quay API
Quota can be managed with the Red Hat Quay API with superuser admin privileges. These endpoints allow superusers to manage quota policies for all organizations within the registry.
Procedure
Use the
POST /api/v1/superuser/organization/{namespace}/quotaAPI endpoint to create a quota policy for an organization:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
"Created"
"Created"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/superuser/organization/{namespace}/quotaAPI endpoint to obtain information about the policy, including the quota ID:curl -X GET "https://quay-server.example.com/api/v1/superuser/organization/<namespace>/quota" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X GET "https://quay-server.example.com/api/v1/superuser/organization/<namespace>/quota" \ -H "Authorization: Bearer <ACCESS_TOKEN>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
[{"id": 2, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}], "default_config_exists": false}][{"id": 2, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}], "default_config_exists": false}]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
PUT /api/v1/superuser/organization/{namespace}/quota/{quota_id}API endpoint to change the quota policy:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"id": 2, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}], "default_config_exists": false}{"id": 2, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [{"id": 1, "type": "Reject", "limit_percent": 90}], "default_config_exists": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
DELETE /api/v1/superuser/organization/{namespace}/quota/{quota_id}API endpoint tocurl -X DELETE "https://quay-server.example.com/api/v1/superuser/organization/<namespace>/quota/<quota_id>" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/superuser/organization/<namespace>/quota/<quota_id>" \ -H "Authorization: Bearer <ACCESS_TOKEN>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
6.17.6. Managing user quota with the Red Hat Quay API
As a superuser, you can manage user quota for specified organizations.
Procedure
Use the
POST /api/v1/superuser/users/{namespace}/quotaendpoint to create a quota policy for specific users within an organization:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
"Created"
"Created"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/superuser/users/{namespace}/quotaendpoint to return a list of a user’s allotted quota:curl -X GET "https://quay-server.example.com/api/v1/superuser/users/<username>/quota" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X GET "https://quay-server.example.com/api/v1/superuser/users/<username>/quota" \ -H "Authorization: Bearer <ACCESS_TOKEN>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
[{"id": 6, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}][{"id": 6, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
PUT /api/v1/superuser/users/{namespace}/quota/{quota_id}endpoint to adjust the user’s policy:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"id": 6, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}{"id": 6, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
DELETE /api/v1/superuser/users/{namespace}/quota/{quota_id}endpoint to delete a user’s policy:curl -X DELETE "https://quay-server.example.com/api/v1/superuser/users/<username>/quota/<quota_id>" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/superuser/users/<username>/quota/<quota_id>" \ -H "Authorization: Bearer <ACCESS_TOKEN>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
6.17.7. Retrieving build information with the Red Hat Quay API
As a superuser, you can retrieve information about builds with the Red Hat Quay API.
Procedure
Use the
GET /api/v1/superuser/{build_uuid}/buildendpoint to return information about a build:curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/build" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/build" \ -H "Authorization: Bearer <ACCESS_TOKEN>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/superuser/{build_uuid}/statusAPI endpoint to return the status for the builds specified by the build uuids:curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/status" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/status" \ -H "Authorization: Bearer <ACCESS_TOKEN>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/superuser/{build_uuid}/logsAPI endpoint to return the build logs for the build specified by the build uuid:curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/logs" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/logs" \ -H "Authorization: Bearer <ACCESS_TOKEN>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.17.8. Managing service keys as a superuser with the Red Hat Quay API
Superusers have the ability to create, list, change, and delete service keys by using the Red Hat Quay API.
Procedure
Use the
POST /api/v1/superuser/keysendpoint to create a service key:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"message":""}{"message":""}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
POST /api/v1/superuser/approvedkeys/{kid}endpoint to approved a service key:Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
Use the
GET /api/v1/superuser/keysendpoint to list service keys:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/keys"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/keys"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"keys":[{"approval":{"approval_type":"ServiceKeyApprovalType.AUTOMATIC","approved_date":"Mon, 20 Jan 2025 14:46:01 GMT","approver":null,"notes":""},"created_date":"Mon, 20 Jan 2025 14:46:01 GMT","expiration_date":"Wed, 05 Feb 2025 22:03:37 GMT","jwk":{"e":"AQAB","kid":"<example>","kty":"RSA","n":"<example>"},"kid":"7fr8soqXGgea8JqjwgItjjJT9GKlt-bMyMCDmvzy6WQ","metadata":{"created_by":"CLI tool"},"name":"http://quay-server.example.com:80","rotation_duration":null,"service":"quay"}]}{"keys":[{"approval":{"approval_type":"ServiceKeyApprovalType.AUTOMATIC","approved_date":"Mon, 20 Jan 2025 14:46:01 GMT","approver":null,"notes":""},"created_date":"Mon, 20 Jan 2025 14:46:01 GMT","expiration_date":"Wed, 05 Feb 2025 22:03:37 GMT","jwk":{"e":"AQAB","kid":"<example>","kty":"RSA","n":"<example>"},"kid":"7fr8soqXGgea8JqjwgItjjJT9GKlt-bMyMCDmvzy6WQ","metadata":{"created_by":"CLI tool"},"name":"http://quay-server.example.com:80","rotation_duration":null,"service":"quay"}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/superuser/keys/{kid}endpoint to retrieve information about a service account by its kid:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/keys/<kid>"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/keys/<kid>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"approval":{"approval_type":"ServiceKeyApprovalType.AUTOMATIC","approved_date":"Mon, 20 Jan 2025 14:46:01 GMT","approver":null,"notes":""},"created_date":"Mon, 20 Jan 2025 14:46:01 GMT","expiration_date":"Wed, 05 Feb 2025 22:03:37 GMT","jwk":{"e":"AQAB","kid":"7fr8soqXGgea8JqjwgItjjJT9GKlt-bMyMCDmvzy6WQ","kty":"RSA","n":"5iMX7RQ_4F_zdb1qonMsuWUDauCOqEyRpD8L_EhgnwDxrgMHuOlJ4_7sEOrOa3Jkx3QhwIW6LJCP69PR5X0wvz6vmC1DoWEaWv41bAq23Knzj7gUU9-N_fkZPZN9NQwZ-D-Zqg9L1c_cJF93Dy93py8_JswWFDj1FxMaThJmrX68wBwjhF-JLYqgCAGFyezzJ3oTpO-esV9v6R7skfkaqtx_cjLZk_0cKB4VKTtxiy2A8D_5nANTOSSbZLXNh2Vatgh3yrOmnTTNLIs0YO3vFIuylEkczHlln-40UMAzRB3HNspUySyzImO_2yGdrA762LATQrOzJN8E1YKCADx5CQ"},"kid":"7fr8soqXGgea8JqjwgItjjJT9GKlt-bMyMCDmvzy6WQ","metadata":{"created_by":"CLI tool"},"name":"http://quay-server.example.com:80","rotation_duration":null,"service":"quay"}{"approval":{"approval_type":"ServiceKeyApprovalType.AUTOMATIC","approved_date":"Mon, 20 Jan 2025 14:46:01 GMT","approver":null,"notes":""},"created_date":"Mon, 20 Jan 2025 14:46:01 GMT","expiration_date":"Wed, 05 Feb 2025 22:03:37 GMT","jwk":{"e":"AQAB","kid":"7fr8soqXGgea8JqjwgItjjJT9GKlt-bMyMCDmvzy6WQ","kty":"RSA","n":"5iMX7RQ_4F_zdb1qonMsuWUDauCOqEyRpD8L_EhgnwDxrgMHuOlJ4_7sEOrOa3Jkx3QhwIW6LJCP69PR5X0wvz6vmC1DoWEaWv41bAq23Knzj7gUU9-N_fkZPZN9NQwZ-D-Zqg9L1c_cJF93Dy93py8_JswWFDj1FxMaThJmrX68wBwjhF-JLYqgCAGFyezzJ3oTpO-esV9v6R7skfkaqtx_cjLZk_0cKB4VKTtxiy2A8D_5nANTOSSbZLXNh2Vatgh3yrOmnTTNLIs0YO3vFIuylEkczHlln-40UMAzRB3HNspUySyzImO_2yGdrA762LATQrOzJN8E1YKCADx5CQ"},"kid":"7fr8soqXGgea8JqjwgItjjJT9GKlt-bMyMCDmvzy6WQ","metadata":{"created_by":"CLI tool"},"name":"http://quay-server.example.com:80","rotation_duration":null,"service":"quay"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
PUT /api/v1/superuser/keys/{kid}endpoint to update your service key, such as the metadata:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"approval":{"approval_type":"ServiceKeyApprovalType.AUTOMATIC","approved_date":"Mon, 20 Jan 2025 14:46:01 GMT","approver":null,"notes":""},"created_date":"Mon, 20 Jan 2025 14:46:01 GMT","expiration_date":"Mon, 03 Mar 2025 10:40:00 GMT","jwk":{"e":"AQAB","kid":"7fr8soqXGgea8JqjwgItjjJT9GKlt-bMyMCDmvzy6WQ","kty":"RSA","n":"5iMX7RQ_4F_zdb1qonMsuWUDauCOqEyRpD8L_EhgnwDxrgMHuOlJ4_7sEOrOa3Jkx3QhwIW6LJCP69PR5X0wvz6vmC1DoWEaWv41bAq23Knzj7gUU9-N_fkZPZN9NQwZ-D-Zqg9L1c_cJF93Dy93py8_JswWFDj1FxMaThJmrX68wBwjhF-JLYqgCAGFyezzJ3oTpO-esV9v6R7skfkaqtx_cjLZk_0cKB4VKTtxiy2A8D_5nANTOSSbZLXNh2Vatgh3yrOmnTTNLIs0YO3vFIuylEkczHlln-40UMAzRB3HNspUySyzImO_2yGdrA762LATQrOzJN8E1YKCADx5CQ"},"kid":"7fr8soqXGgea8JqjwgItjjJT9GKlt-bMyMCDmvzy6WQ","metadata":{"created_by":"CLI tool","environment":"production"},"name":"quay-service-key-updated","rotation_duration":null,"service":"quay"}{"approval":{"approval_type":"ServiceKeyApprovalType.AUTOMATIC","approved_date":"Mon, 20 Jan 2025 14:46:01 GMT","approver":null,"notes":""},"created_date":"Mon, 20 Jan 2025 14:46:01 GMT","expiration_date":"Mon, 03 Mar 2025 10:40:00 GMT","jwk":{"e":"AQAB","kid":"7fr8soqXGgea8JqjwgItjjJT9GKlt-bMyMCDmvzy6WQ","kty":"RSA","n":"5iMX7RQ_4F_zdb1qonMsuWUDauCOqEyRpD8L_EhgnwDxrgMHuOlJ4_7sEOrOa3Jkx3QhwIW6LJCP69PR5X0wvz6vmC1DoWEaWv41bAq23Knzj7gUU9-N_fkZPZN9NQwZ-D-Zqg9L1c_cJF93Dy93py8_JswWFDj1FxMaThJmrX68wBwjhF-JLYqgCAGFyezzJ3oTpO-esV9v6R7skfkaqtx_cjLZk_0cKB4VKTtxiy2A8D_5nANTOSSbZLXNh2Vatgh3yrOmnTTNLIs0YO3vFIuylEkczHlln-40UMAzRB3HNspUySyzImO_2yGdrA762LATQrOzJN8E1YKCADx5CQ"},"kid":"7fr8soqXGgea8JqjwgItjjJT9GKlt-bMyMCDmvzy6WQ","metadata":{"created_by":"CLI tool","environment":"production"},"name":"quay-service-key-updated","rotation_duration":null,"service":"quay"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
DELETE /api/v1/superuser/keys/{kid}endpoint to delete a service key:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/keys/<kid>"
$ curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/keys/<kid>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
6.18. Managing tags with the Red Hat Quay API
Tags can be changed, restored, deleted, or listed by using the Red Hat Quay API.
Procedure
Use the
PUT /api/v1/repository/{repository}/tag/{tag}endpoint to change which image a tag points to or create a new tag:curl -X PUT "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/tag/<tag_name>" \ -H "Authorization: Bearer <ACCESS_TOKEN>" \ -H "Content-Type: application/json" \ -d '{"manifest_digest": "<MANIFEST_DIGEST>"}'$ curl -X PUT "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/tag/<tag_name>" \ -H "Authorization: Bearer <ACCESS_TOKEN>" \ -H "Content-Type: application/json" \ -d '{"manifest_digest": "<MANIFEST_DIGEST>"}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
"Updated"
"Updated"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
POST /api/v1/repository/{repository}/tag/{tag}/restoreendpoint to restore a repository tag back to a previous image in the repository:curl -X POST "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/tag/<tag_name>/restore" \ -H "Authorization: Bearer <your_access_token>" \ -H "Content-Type: application/json" \ -d '{"manifest_digest": "sha256:<your_manifest_digest>"}'$ curl -X POST "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/tag/<tag_name>/restore" \ -H "Authorization: Bearer <your_access_token>" \ -H "Content-Type: application/json" \ -d '{"manifest_digest": "sha256:<your_manifest_digest>"}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{}{}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/repository/{repository}/tag/endpoint to obtain a list of repository tags:curl -X GET "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/tag/" \ -H "Authorization: Bearer <your_access_token>" \ -H "Content-Type: application/json"
$ curl -X GET "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/tag/" \ -H "Authorization: Bearer <your_access_token>" \ -H "Content-Type: application/json"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"tags": [{"name": "test", "reversion": true, "start_ts": 1740496373, "manifest_digest": "sha256:d08334991a3dba62307016833083d6433f489ab0f7d36d0a4771a20b4569b2f6", "is_manifest_list": false, "size": 2280303, "last_modified": "Tue, 25 Feb 2025 15:12:53 -0000"}, {"name": "test", "reversion": false, "start_ts": 1740495442, "end_ts": 1740496373, "manifest_digest": "sha256:d08334991a3dba62307016833083d6433f489ab0f7d36d0a4771a20b4569b2f6", "is_manifest_list": false, "size": 2280303, "last_modified": "Tue, 25 Feb 2025 14:57:22 -0000", "expiration": "Tue, 25 Feb 2025 15:12:53 -0000"}, {"name": "test", "reversion": false, "start_ts": 1740495408, "end_ts": 1740495442, "manifest_digest": "sha256:d08334991a3dba62307016833083d6433f489ab0f7d36d0a4771a20b4569b2f6", "is_manifest_list": false, "size": 2280303, "last_modified": "Tue, 25 Feb 2025 14:56:48 -0000", "expiration": "Tue, 25 Feb 2025 14:57:22 -0000"}], "page": 1, "has_additional": false}{"tags": [{"name": "test", "reversion": true, "start_ts": 1740496373, "manifest_digest": "sha256:d08334991a3dba62307016833083d6433f489ab0f7d36d0a4771a20b4569b2f6", "is_manifest_list": false, "size": 2280303, "last_modified": "Tue, 25 Feb 2025 15:12:53 -0000"}, {"name": "test", "reversion": false, "start_ts": 1740495442, "end_ts": 1740496373, "manifest_digest": "sha256:d08334991a3dba62307016833083d6433f489ab0f7d36d0a4771a20b4569b2f6", "is_manifest_list": false, "size": 2280303, "last_modified": "Tue, 25 Feb 2025 14:57:22 -0000", "expiration": "Tue, 25 Feb 2025 15:12:53 -0000"}, {"name": "test", "reversion": false, "start_ts": 1740495408, "end_ts": 1740495442, "manifest_digest": "sha256:d08334991a3dba62307016833083d6433f489ab0f7d36d0a4771a20b4569b2f6", "is_manifest_list": false, "size": 2280303, "last_modified": "Tue, 25 Feb 2025 14:56:48 -0000", "expiration": "Tue, 25 Feb 2025 14:57:22 -0000"}], "page": 1, "has_additional": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
DELETE /api/v1/repository/{repository}/tag/{tag}endpoint to delete a tag from a repository:curl -X DELETE "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/tag/<tag_name>" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/tag/<tag_name>" \ -H "Authorization: Bearer <your_access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
6.19. Managing teams by using the API
Team can be managing by using the Red Hat Quay API.
6.19.1. Managing team members and repository permissions by using the API
Use the following procedures to add a member to a team (by direct invite or by email), or to remove a member from a team.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the
PUT /api/v1/organization/{orgname}/team/{teamname}/members/{membername}command to add or invite a member to an existing team:curl -X PUT \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members/<member_name>"
$ curl -X PUT \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members/<member_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "testuser", "kind": "user", "is_robot": false, "avatar": {"name": "testuser", "hash": "d51d17303dc3271ac3266fb332d7df919bab882bbfc7199d2017a4daac8979f0", "color": "#5254a3", "kind": "user"}, "invited": false}{"name": "testuser", "kind": "user", "is_robot": false, "avatar": {"name": "testuser", "hash": "d51d17303dc3271ac3266fb332d7df919bab882bbfc7199d2017a4daac8979f0", "color": "#5254a3", "kind": "user"}, "invited": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the
DELETE /api/v1/organization/{orgname}/team/{teamname}/members/{membername}command to remove a member of a team:curl -X DELETE \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members/<member_name>"
$ curl -X DELETE \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members/<member_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not an output in the CLI. To ensure that a member has been deleted, you can enter the
GET /api/v1/organization/{orgname}/team/{teamname}/memberscommand and ensure that the member is not returned in the output.curl -X GET \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members"
$ curl -X GET \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "owners", "members": [{"name": "quayadmin", "kind": "user", "is_robot": false, "avatar": {"name": "quayadmin", "hash": "b28d563a6dc76b4431fc7b0524bbff6b810387dac86d9303874871839859c7cc", "color": "#17becf", "kind": "user"}, "invited": false}, {"name": "test-org+test", "kind": "user", "is_robot": true, "avatar": {"name": "test-org+test", "hash": "aa85264436fe9839e7160bf349100a9b71403a5e9ec684d5b5e9571f6c821370", "color": "#8c564b", "kind": "robot"}, "invited": false}], "can_edit": true}{"name": "owners", "members": [{"name": "quayadmin", "kind": "user", "is_robot": false, "avatar": {"name": "quayadmin", "hash": "b28d563a6dc76b4431fc7b0524bbff6b810387dac86d9303874871839859c7cc", "color": "#17becf", "kind": "user"}, "invited": false}, {"name": "test-org+test", "kind": "user", "is_robot": true, "avatar": {"name": "test-org+test", "hash": "aa85264436fe9839e7160bf349100a9b71403a5e9ec684d5b5e9571f6c821370", "color": "#8c564b", "kind": "robot"}, "invited": false}], "can_edit": true}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can enter the
PUT /api/v1/organization/{orgname}/team/{teamname}/invite/{email}command to invite a user, by email address, to an existing team:curl -X PUT \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/invite/<email>"
$ curl -X PUT \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/invite/<email>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can enter the
DELETE /api/v1/organization/{orgname}/team/{teamname}/invite/{email}command to delete the invite of an email address to join a team. For example:curl -X DELETE \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/invite/<email>"
$ curl -X DELETE \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/invite/<email>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.19.2. Setting the role of a team within an organization by using the API
Use the following procedure to view and set the role a team within an organization using the API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following
GET /api/v1/organization/{orgname}/team/{teamname}/permissionscommand to return a list of repository permissions for the organization’s team. Note that your team must have been added to a repository for this command to return information.curl -X GET \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/permissions"
$ curl -X GET \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/permissions"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"permissions": [{"repository": {"name": "api-repo", "is_public": true}, "role": "admin"}]}{"permissions": [{"repository": {"name": "api-repo", "is_public": true}, "role": "admin"}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can create or update a team within an organization to have a specified role of admin, member, or creator using the
PUT /api/v1/organization/{orgname}/team/{teamname}command. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "testteam", "description": "", "can_view": true, "role": "creator", "avatar": {"name": "testteam", "hash": "827f8c5762148d7e85402495b126e0a18b9b168170416ed04b49aae551099dc8", "color": "#ff7f0e", "kind": "team"}, "new_team": false}{"name": "testteam", "description": "", "can_view": true, "role": "creator", "avatar": {"name": "testteam", "hash": "827f8c5762148d7e85402495b126e0a18b9b168170416ed04b49aae551099dc8", "color": "#ff7f0e", "kind": "team"}, "new_team": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.19.3. Deleting a team within an organization by using the API
Use the following procedure to delete a team within an organization by using the API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
You can delete a team within an organization by entering the
DELETE /api/v1/organization/{orgname}/team/{teamname}command:curl -X DELETE \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>"
$ curl -X DELETE \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
6.20. Managing builds by using the Red Hat Quay API
Builds can be managed by using the Red Hat Quay API.
Procedure
Use the
GET /api/v1/repository/{repository}/trigger/endpoint to list the triggers for the specified repository:curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/" \ -H "Authorization: Bearer <your_access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"triggers": [{"id": "32ca5eae-a29f-46c7-8f44-3221ca417c92", "service": "custom-git", "is_active": false, "build_source": null, "repository_url": null, "config": {}, "can_invoke": true, "enabled": true, "disabled_reason": null}]}{"triggers": [{"id": "32ca5eae-a29f-46c7-8f44-3221ca417c92", "service": "custom-git", "is_active": false, "build_source": null, "repository_url": null, "config": {}, "can_invoke": true, "enabled": true, "disabled_reason": null}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
POST /api/v1/repository/{repository}/trigger/{trigger_uuid}/activateendpoint to activate the specified build trigger.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
POST /api/v1/repository/{repository}/trigger/{trigger_uuid}/startendpoint to manually start the build from the specified trigger:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/repository/{repository}/trigger/{trigger_uuid}/buildsendpoint to list the builds started by the specified trigger:curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid/builds?limit=10" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid/builds?limit=10" \ -H "Authorization: Bearer <your_access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/repository/{repository}/trigger/{trigger_uuid}endpoint to get information for the specified build trigger:curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \ -H "Authorization: Bearer <your_access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
PUT /api/v1/repository/{repository}/trigger/{trigger_uuid}endpoint to update the specified build trigger:curl -X PUT "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \ -H "Authorization: Bearer <your_access_token>" \ -H "Content-Type: application/json" \ -d '{"enabled": true}'$ curl -X PUT "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \ -H "Authorization: Bearer <your_access_token>" \ -H "Content-Type: application/json" \ -d '{"enabled": true}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
DELETE /api/v1/repository/{repository}/trigger/{trigger_uuid}endpoint to delete the specified build trigger:curl -X DELETE "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \ -H "Authorization: Bearer <your_access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.21. Managing current user options by using the Red Hat Quay API
Some user options, like starring a repository, or getting information about your account, are available with the Red Hat Quay API.
Procedure
Use the
GET /api/v1/user/endpoint to get user information for the authenticated user.curl -X GET "https://quay-server.example.com/api/v1/user/" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/user/" \ -H "Authorization: Bearer <your_access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"anonymous": false, "username": "quayadmin", "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}, "can_create_repo": true, "is_me": true, "verified": true, "email": "test@gmil.com", "logins": [], "invoice_email": false, "invoice_email_address": null, "preferred_namespace": false, "tag_expiration_s": 1209600, "prompts": [], "company": null, "family_name": null, "given_name": null, "location": null, "is_free_account": true, "has_password_set": true, "quotas": [{"id": 4, "limit_bytes": 2199023255552, "limits": [{"id": 3, "type": "Reject", "limit_percent": 100}]}], "quota_report": {"quota_bytes": 2280675, "configured_quota": 2199023255552, "running_backfill": "complete", "backfill_status": "complete"}, "organizations": [{"name": "test", "avatar": {"name": "test", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "org"}, "can_create_repo": true, "public": false, "is_org_admin": true, "preferred_namespace": false}, {"name": "sample", "avatar": {"name": "sample", "hash": "ba560c68f1d26e8c6b911ac9b5d10d513e7e43e576cc2baece1b8a46f36a29a5", "color": "#b5cf6b", "kind": "org"}, "can_create_repo": true, "public": false, "is_org_admin": true, "preferred_namespace": false}], "super_user": true}{"anonymous": false, "username": "quayadmin", "avatar": {"name": "quayadmin", "hash": "6d640d802fe23b93779b987c187a4b7a4d8fbcbd4febe7009bdff58d84498fba", "color": "#f7b6d2", "kind": "user"}, "can_create_repo": true, "is_me": true, "verified": true, "email": "test@gmil.com", "logins": [], "invoice_email": false, "invoice_email_address": null, "preferred_namespace": false, "tag_expiration_s": 1209600, "prompts": [], "company": null, "family_name": null, "given_name": null, "location": null, "is_free_account": true, "has_password_set": true, "quotas": [{"id": 4, "limit_bytes": 2199023255552, "limits": [{"id": 3, "type": "Reject", "limit_percent": 100}]}], "quota_report": {"quota_bytes": 2280675, "configured_quota": 2199023255552, "running_backfill": "complete", "backfill_status": "complete"}, "organizations": [{"name": "test", "avatar": {"name": "test", "hash": "a15d479002b20f211568fd4419e76686d2b88a4980a5b4c4bc10420776c5f6fe", "color": "#aec7e8", "kind": "org"}, "can_create_repo": true, "public": false, "is_org_admin": true, "preferred_namespace": false}, {"name": "sample", "avatar": {"name": "sample", "hash": "ba560c68f1d26e8c6b911ac9b5d10d513e7e43e576cc2baece1b8a46f36a29a5", "color": "#b5cf6b", "kind": "org"}, "can_create_repo": true, "public": false, "is_org_admin": true, "preferred_namespace": false}], "super_user": true}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/users/{username}endpoint to get user information for the specified user.curl -X GET "https://quay-server.example.com/api/v1/users/example_user" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/users/example_user" \ -H "Authorization: Bearer <your_access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"anonymous": false, "username": "testuser", "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}, "super_user": false}{"anonymous": false, "username": "testuser", "avatar": {"name": "testuser", "hash": "f660ab912ec121d1b1e928a0bb4bc61b15f5ad44d5efdc4e1c92a25e99b8e44a", "color": "#6b6ecf", "kind": "user"}, "super_user": false}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
POST /api/v1/user/starredendpoint to star a repository:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"namespace": "test", "repository": "testrepo"}{"namespace": "test", "repository": "testrepo"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
GET /api/v1/user/starredendpoint to list all starred repositories:curl -X GET "https://quay-server.example.com/api/v1/user/starred?next_page=<next_page_token>" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/user/starred?next_page=<next_page_token>" \ -H "Authorization: Bearer <your_access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"repositories": [{"namespace": "test", "name": "testrepo", "description": "This repository is now under maintenance.", "is_public": true}]}{"repositories": [{"namespace": "test", "name": "testrepo", "description": "This repository is now under maintenance.", "is_public": true}]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
DELETE /api/v1/user/starred/{repository}endpoint to delete a star from a repository:curl -X DELETE "https://quay-server.example.com/api/v1/user/starred/namespace/repository-name" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/user/starred/namespace/repository-name" \ -H "Authorization: Bearer <your_access_token>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command does not return output in the CLI.
Chapter 7. Red Hat Quay Application Programming Interface (API)
This API allows you to perform many of the operations required to work with Red Hat Quay repositories, users, and organizations.
7.1. Authorization
oauth2_implicit
Scopes
The following scopes are used to control access to the API endpoints:
| Scope | Description |
|---|---|
| repo:read | This application will be able to view and pull all repositories visible to the granting user or robot account |
| repo:write | This application will be able to view, push and pull to all repositories to which the granting user or robot account has write access |
| repo:admin | This application will have administrator access to all repositories to which the granting user or robot account has access |
| repo:create | This application will be able to create repositories in to any namespaces that the granting user or robot account is allowed to create repositories |
| user:read | This application will be able to read user information such as username and email address. |
| org:admin | This application will be able to administer your organizations including creating robots, creating teams, adjusting team membership, and changing billing settings. You should have absolute trust in the requesting application before granting this permission. |
| super:user | This application will be able to administer your installation including managing users, managing organizations and other features found in the superuser panel. You should have absolute trust in the requesting application before granting this permission. |
| user:admin | This application will be able to administer your account including creating robots and granting them permissions to your repositories. You should have absolute trust in the requesting application before granting this permission. |
7.2. appspecifictokens
Manages app specific tokens for the current user.
7.2.1. createAppToken
Create a new app specific token for user.
POST /api/v1/user/apptoken
Authorizations: oauth2_implicit (user:admin)
Request body schema (application/json)
Description of a new token.
| Name | Description | Schema |
|---|---|---|
|
title | Friendly name to help identify the token | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.2.2. listAppTokens
Lists the app specific tokens for the user.
GET /api/v1/user/apptoken
Authorizations: oauth2_implicit (user:admin)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
expiring | If true, only returns those tokens expiring soon | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <access_token>" \ "http://quay-server.example.com/api/v1/user/apptoken"
$ curl -X GET \
-H "Authorization: Bearer <access_token>" \
"http://quay-server.example.com/api/v1/user/apptoken"7.2.3. getAppToken
Returns a specific app token for the user.
GET /api/v1/user/apptoken/{token_uuid}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
token_uuid | The uuid of the app specific token | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <access_token>" \ "http://quay-server.example.com/api/v1/user/apptoken/<token_uuid>"
$ curl -X GET \
-H "Authorization: Bearer <access_token>" \
"http://quay-server.example.com/api/v1/user/apptoken/<token_uuid>"7.2.4. revokeAppToken
Revokes a specific app token for the user.
DELETE /api/v1/user/apptoken/{token_uuid}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
token_uuid | The uuid of the app specific token | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <access_token>" \ "http://quay-server.example.com/api/v1/user/apptoken/<token_uuid>"
$ curl -X DELETE \
-H "Authorization: Bearer <access_token>" \
"http://quay-server.example.com/api/v1/user/apptoken/<token_uuid>"7.3. build
Create, list, cancel and get status/logs of repository builds.
7.3.1. getRepoBuildStatus
Return the status for the builds specified by the build uuids.
GET /api/v1/repository/{repository}/build/{build_uuid}/status
Authorizations: oauth2_implicit (repo:read)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
build_uuid | The UUID of the build | string |
Responses
7.3.2. getRepoBuildLogs
Return the build logs for the build specified by the build uuid.
GET /api/v1/repository/{repository}/build/{build_uuid}/logs
Authorizations: oauth2_implicit (repo:read)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
build_uuid | The UUID of the build | string |
Responses
7.3.3. getRepoBuild
Returns information about a build.
GET /api/v1/repository/{repository}/build/{build_uuid}
Authorizations: oauth2_implicit (repo:read)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
build_uuid | The UUID of the build | string |
Responses
7.3.4. cancelRepoBuild
Cancels a repository build.
DELETE /api/v1/repository/{repository}/build/{build_uuid}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
build_uuid | The UUID of the build | string |
Responses
7.3.5. requestRepoBuild
Request that a repository be built and pushed from the specified input.
POST /api/v1/repository/{repository}/build/
Authorizations: oauth2_implicit (repo:write)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
Description of a new repository build.
| Name | Description | Schema |
|---|---|---|
|
file_id | The file id that was generated when the build spec was uploaded | string |
|
archive_url | The URL of the .tar.gz to build. Must start with "http" or "https". | string |
|
subdirectory | Subdirectory in which the Dockerfile can be found. You can only specify this or dockerfile_path | string |
|
dockerfile_path | Path to a dockerfile. You can only specify this or subdirectory. | string |
|
context | Pass in the context for the dockerfile. This is optional. | string |
|
pull_robot | Username of a Quay robot account to use as pull credentials | string |
|
tags | The tags to which the built images will be pushed. If none specified, "latest" is used. |
array of string |
Responses
7.3.6. getRepoBuilds
Get the list of repository builds.
GET /api/v1/repository/{repository}/build/
Authorizations: oauth2_implicit (repo:read)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
since | Returns all builds since the given unix timecode | integer |
| query |
limit | The maximum number of builds to return | integer |
Responses
7.4. discovery
API discovery information.
7.4.1. discovery
List all of the API endpoints available in the swagger API format.
GET /api/v1/discovery
Authorizations:
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
internal | Whether to include internal APIs. | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/discovery?query=true" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/discovery?query=true" \
-H "Authorization: Bearer <access_token>"7.5. error
Error details API.
7.5.1. getErrorDescription
Get a detailed description of the error.
GET /api/v1/error/{error_type}
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
error_type | The error code identifying the type of error. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/error/<error_type>" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/error/<error_type>" \
-H "Authorization: Bearer <access_token>"7.6. globalmessages
Messages API.
7.6.1. createGlobalMessage
Create a message.
POST /api/v1/messages
Authorizations: oauth2_implicit (super:user)
Request body schema (application/json)
Create a new message
| Name | Description | Schema |
|---|---|---|
|
message | A single message | object |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.6.2. getGlobalMessages
Return a super users messages.
GET /api/v1/messages
Authorizations:
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/messages" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/messages" \
-H "Authorization: Bearer <access_token>"7.6.3. deleteGlobalMessage
Delete a message.
DELETE /api/v1/message/{uuid}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
uuid | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://<quay-server.example.com>/api/v1/message/<uuid>" \
-H "Authorization: Bearer <access_token>"
$ curl -X DELETE "https://<quay-server.example.com>/api/v1/message/<uuid>" \
-H "Authorization: Bearer <access_token>"7.7. logs
Access usage logs for organizations or repositories.
7.7.1. getAggregateUserLogs
Returns the aggregated logs for the current user.
GET /api/v1/user/aggregatelogs
Authorizations: oauth2_implicit (user:admin)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
performer | Username for which to filter logs. | string |
| query |
endtime | Latest time for logs. Format: "%m/%d/%Y" in UTC. | string |
| query |
starttime | Earliest time for logs. Format: "%m/%d/%Y" in UTC. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "<quay-server.example.com>/api/v1/user/aggregatelogs?performer=<username>&starttime=<MM/DD/YYYY>&endtime=<MM/DD/YYYY>"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
"<quay-server.example.com>/api/v1/user/aggregatelogs?performer=<username>&starttime=<MM/DD/YYYY>&endtime=<MM/DD/YYYY>"7.7.2. exportUserLogs
Returns the aggregated logs for the current user.
POST /api/v1/user/exportlogs
Authorizations: oauth2_implicit (user:admin)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
endtime | Latest time for logs. Format: "%m/%d/%Y" in UTC. | string |
| query |
starttime | Earliest time for logs. Format: "%m/%d/%Y" in UTC. | string |
Request body schema (application/json)
Configuration for an export logs operation
| Name | Description | Schema |
|---|---|---|
|
callback_url | The callback URL to invoke with a link to the exported logs | string |
|
callback_email | The e-mail address at which to e-mail a link to the exported logs | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.7.3. listUserLogs
List the logs for the current user.
GET /api/v1/user/logs
Authorizations: oauth2_implicit (user:admin)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
next_page | The page token for the next page | string |
| query |
performer | Username for which to filter logs. | string |
| query |
endtime | Latest time for logs. Format: "%m/%d/%Y" in UTC. | string |
| query |
starttime | Earliest time for logs. Format: "%m/%d/%Y" in UTC. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET -H "Authorization: Bearer <bearer_token>" -H "Accept: application/json" "<quay-server.example.com>/api/v1/user/logs"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" -H "Accept: application/json" "<quay-server.example.com>/api/v1/user/logs"7.7.4. getAggregateOrgLogs
Gets the aggregated logs for the specified organization.
GET /api/v1/organization/{orgname}/aggregatelogs
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
performer | Username for which to filter logs. | string |
| query |
endtime | Latest time for logs. Format: "%m/%d/%Y" in UTC. | string |
| query |
starttime | Earliest time for logs. Format: "%m/%d/%Y" in UTC. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
"<quay-server.example.com>/api/v1/organization/{orgname}/aggregatelogs"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
"<quay-server.example.com>/api/v1/organization/{orgname}/aggregatelogs"7.7.5. exportOrgLogs
Exports the logs for the specified organization.
POST /api/v1/organization/{orgname}/exportlogs
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
endtime | Latest time for logs. Format: "%m/%d/%Y" in UTC. | string |
| query |
starttime | Earliest time for logs. Format: "%m/%d/%Y" in UTC. | string |
Request body schema (application/json)
Configuration for an export logs operation
| Name | Description | Schema |
|---|---|---|
|
callback_url | The callback URL to invoke with a link to the exported logs | string |
|
callback_email | The e-mail address at which to e-mail a link to the exported logs | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.7.6. listOrgLogs
List the logs for the specified organization.
GET /api/v1/organization/{orgname}/logs
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
next_page | The page token for the next page | string |
| query |
performer | Username for which to filter logs. | string |
| query |
endtime | Latest time for logs. Format: "%m/%d/%Y" in UTC. | string |
| query |
starttime | Earliest time for logs. Format: "%m/%d/%Y" in UTC. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
"http://<quay-server.example.com>/api/v1/organization/{orgname}/logs"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
"http://<quay-server.example.com>/api/v1/organization/{orgname}/logs"7.7.7. getAggregateRepoLogs
Returns the aggregated logs for the specified repository.
GET /api/v1/repository/{repository}/aggregatelogs
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
endtime | Latest time for logs. Format: "%m/%d/%Y" in UTC. | string |
| query |
starttime | Earliest time for logs. Format: "%m/%d/%Y" in UTC. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "<quay-server.example.com>/api/v1/repository/<repository_name>/<namespace>/aggregatelogs?starttime=2024-01-01&endtime=2024-06-18""
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
"<quay-server.example.com>/api/v1/repository/<repository_name>/<namespace>/aggregatelogs?starttime=2024-01-01&endtime=2024-06-18""7.7.8. exportRepoLogs
Queues an export of the logs for the specified repository.
POST /api/v1/repository/{repository}/exportlogs
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
endtime | Latest time for logs. Format: "%m/%d/%Y" in UTC. | string |
| query |
starttime | Earliest time for logs. Format: "%m/%d/%Y" in UTC. | string |
Request body schema (application/json)
Configuration for an export logs operation
| Name | Description | Schema |
|---|---|---|
|
callback_url | The callback URL to invoke with a link to the exported logs | string |
|
callback_email | The e-mail address at which to e-mail a link to the exported logs | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.7.9. listRepoLogs
List the logs for the specified repository.
GET /api/v1/repository/{repository}/logs
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
next_page | The page token for the next page | string |
| query |
endtime | Latest time for logs. Format: "%m/%d/%Y" in UTC. | string |
| query |
starttime | Earliest time for logs. Format: "%m/%d/%Y" in UTC. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
"http://<quay-server.example.com>/api/v1/repository/{repository}/logs"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
"http://<quay-server.example.com>/api/v1/repository/{repository}/logs"7.8. manifest
Manage the manifests of a repository.
7.8.1. getManifestLabel
Retrieves the label with the specific ID under the manifest.
GET /api/v1/repository/{repository}/manifest/{manifestref}/labels/{labelid}
Authorizations: oauth2_implicit (repo:read)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
manifestref | The digest of the manifest | string |
| path |
labelid | The ID of the label | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels/<label_id>
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels/<label_id>7.8.2. deleteManifestLabel
Deletes an existing label from a manifest.
DELETE /api/v1/repository/{repository}/manifest/{manifestref}/labels/{labelid}
Authorizations: oauth2_implicit (repo:write)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
manifestref | The digest of the manifest | string |
| path |
labelid | The ID of the label | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels/<labelid>
$ curl -X DELETE \
-H "Authorization: Bearer <bearer_token>" \
https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels/<labelid>7.8.3. addManifestLabel
Adds a new label into the tag manifest.
POST /api/v1/repository/{repository}/manifest/{manifestref}/labels
Authorizations: oauth2_implicit (repo:write)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
manifestref | The digest of the manifest | string |
Request body schema (application/json)
Adds a label to a manifest
| Name | Description | Schema |
|---|---|---|
|
key | The key for the label | string |
|
value | The value for the label | string |
|
media_type | The media type for this label |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.8.4. listManifestLabels
GET /api/v1/repository/{repository}/manifest/{manifestref}/labels
Authorizations: oauth2_implicit (repo:read)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
manifestref | The digest of the manifest | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
filter | If specified, only labels matching the given prefix will be returned | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>/labels7.8.5. getRepoManifest
GET /api/v1/repository/{repository}/manifest/{manifestref}
Authorizations: oauth2_implicit (repo:read)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
manifestref | The digest of the manifest | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
https://<quay-server.example.com>/api/v1/repository/<repository>/manifest/<manifestref>7.9. mirror
7.9.1. syncCancel
Update the sync_status for a given Repository’s mirroring configuration.
POST /api/v1/repository/{repository}/mirror/sync-cancel
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror/sync-cancel" \
$ curl -X POST "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror/sync-cancel" \7.9.2. syncNow
Update the sync_status for a given Repository’s mirroring configuration.
POST /api/v1/repository/{repository}/mirror/sync-now
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror/sync-now" \
-H "Authorization: Bearer <access_token>"
$ curl -X POST "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror/sync-now" \
-H "Authorization: Bearer <access_token>"7.9.3. getRepoMirrorConfig
Return the Mirror configuration for a given Repository.
GET /api/v1/repository/{repository}/mirror
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/repository/<namespace>/<repo>/mirror" \
-H "Authorization: Bearer <access_token>"7.9.4. changeRepoMirrorConfig
Allow users to modifying the repository’s mirroring configuration.
PUT /api/v1/repository/{repository}/mirror
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
Update the repository mirroring configuration.
| Name | Description | Schema |
|---|---|---|
|
is_enabled | Used to enable or disable synchronizations. | boolean |
|
external_reference | Location of the external repository. | string |
|
external_registry_username | Username used to authenticate with external registry. | |
|
external_registry_password | Password used to authenticate with external registry. | |
|
sync_start_date | Determines the next time this repository is ready for synchronization. | string |
|
sync_interval | Number of seconds after next_start_date to begin synchronizing. | integer |
|
robot_username | Username of robot which will be used for image pushes. | string |
|
root_rule | A list of glob-patterns used to determine which tags should be synchronized. | object |
|
external_registry_config | object |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
- 1
- Disables automatic synchronization.
7.9.5. createRepoMirrorConfig
Create a RepoMirrorConfig for a given Repository.
POST /api/v1/repository/{repository}/mirror
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
Create the repository mirroring configuration.
| Name | Description | Schema |
|---|---|---|
|
is_enabled | Used to enable or disable synchronizations. | boolean |
|
external_reference | Location of the external repository. | string |
|
external_registry_username | Username used to authenticate with external registry. | |
|
external_registry_password | Password used to authenticate with external registry. | |
|
sync_start_date | Determines the next time this repository is ready for synchronization. | string |
|
sync_interval | Number of seconds after next_start_date to begin synchronizing. | integer |
|
robot_username | Username of robot which will be used for image pushes. | string |
|
root_rule | A list of glob-patterns used to determine which tags should be synchronized. | object |
|
external_registry_config | object |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.10. namespacequota
7.10.1. listUserQuota
GET /api/v1/user/quota
Authorizations: oauth2_implicit (user:admin)
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/user/quota" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/user/quota" \
-H "Authorization: Bearer <access_token>"7.10.2. getOrganizationQuotaLimit
GET /api/v1/organization/{orgname}/quota/{quota_id}/limit/{limit_id}
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string | |
| path |
limit_id | string | |
| path |
orgname | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>/limit/<limit_id>" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>/limit/<limit_id>" \
-H "Authorization: Bearer <access_token>"7.10.3. changeOrganizationQuotaLimit
PUT /api/v1/organization/{orgname}/quota/{quota_id}/limit/{limit_id}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string | |
| path |
limit_id | string | |
| path |
orgname | string |
Request body schema (application/json)
Description of changing organization quota limit
| Name | Description | Schema |
|---|---|---|
|
type | Type of quota limit: "Warning" or "Reject" | string |
|
threshold_percent | Quota threshold, in percent of quota | integer |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.10.4. deleteOrganizationQuotaLimit
DELETE /api/v1/organization/{orgname}/quota/{quota_id}/limit/{limit_id}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string | |
| path |
limit_id | string | |
| path |
orgname | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>/limit/<limit_id>" \
-H "Authorization: Bearer <access_token>"
$ curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>/limit/<limit_id>" \
-H "Authorization: Bearer <access_token>"7.10.5. createOrganizationQuotaLimit
POST /api/v1/organization/{orgname}/quota/{quota_id}/limit
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string | |
| path |
orgname | string |
Request body schema (application/json)
Description of a new organization quota limit
| Name | Description | Schema |
|---|---|---|
|
type | Type of quota limit: "Warning" or "Reject" | string |
|
threshold_percent | Quota threshold, in percent of quota | integer |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.10.6. listOrganizationQuotaLimit
GET /api/v1/organization/{orgname}/quota/{quota_id}/limit
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string | |
| path |
orgname | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>/limit" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>/limit" \
-H "Authorization: Bearer <access_token>"7.10.7. getUserQuotaLimit
GET /api/v1/user/quota/{quota_id}/limit/{limit_id}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string | |
| path |
limit_id | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}/limit/{limit_id}" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}/limit/{limit_id}" \
-H "Authorization: Bearer <access_token>"7.10.8. listUserQuotaLimit
GET /api/v1/user/quota/{quota_id}/limit
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}/limit" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}/limit" \
-H "Authorization: Bearer <access_token>"7.10.9. getOrganizationQuota
GET /api/v1/organization/{orgname}/quota/{quota_id}
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string | |
| path |
orgname | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>" \
-H "Authorization: Bearer <access_token>"S
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>" \
-H "Authorization: Bearer <access_token>"S7.10.10. changeOrganizationQuota
PUT /api/v1/organization/{orgname}/quota/{quota_id}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string | |
| path |
orgname | string |
Request body schema (application/json)
Description of a new organization quota
| Name | Description | Schema |
|---|---|---|
|
limit_bytes | Number of bytes the organization is allowed | integer |
|
limits |
Human readable storage capacity of the organization. Accepts SI units like Mi, Gi, or Ti, as well as non-standard units like GB or MB. Must be mutually exclusive with | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.10.11. deleteOrganizationQuota
DELETE /api/v1/organization/{orgname}/quota/{quota_id}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string | |
| path |
orgname | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>" \
-H "Authorization: Bearer <access_token>"
$ curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>" \
-H "Authorization: Bearer <access_token>"7.10.12. createOrganizationQuota
Create a new organization quota.
POST /api/v1/organization/{orgname}/quota
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | string |
Request body schema (application/json)
Description of a new organization quota
| Name | Description | Schema |
|---|---|---|
|
limit_bytes | Number of bytes the organization is allowed | integer |
|
limits |
Human readable storage capacity of the organization. Accepts SI units like Mi, Gi, or Ti, as well as non-standard units like GB or MB. Must be mutually exclusive with | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.10.13. listOrganizationQuota
GET /api/v1/organization/{orgname}/quota
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -k -X GET -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' https://<quay-server.example.com>/api/v1/organization/<organization_name>/quota
$ curl -k -X GET -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' https://<quay-server.example.com>/api/v1/organization/<organization_name>/quota7.10.14. getUserQuota
GET /api/v1/user/quota/{quota_id}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
quota_id | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/user/quota/{quota_id}" \
-H "Authorization: Bearer <access_token>"7.11. organization
Manage organizations, members and OAuth applications.
7.11.1. createOrganization
Create a new organization.
POST /api/v1/organization/
Authorizations: oauth2_implicit (user:admin)
Request body schema (application/json)
Description of a new organization.
| Name | Description | Schema |
|---|---|---|
|
name | Organization username | string |
|
email | Organization contact email | string |
|
recaptcha_response | The (may be disabled) recaptcha response code for verification | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST -H "Authorization: Bearer <bearer_token>" -H "Content-Type: application/json" -d '{
"name": "<new_organization_name>"
}' "https://<quay-server.example.com>/api/v1/organization/"
$ curl -X POST -H "Authorization: Bearer <bearer_token>" -H "Content-Type: application/json" -d '{
"name": "<new_organization_name>"
}' "https://<quay-server.example.com>/api/v1/organization/"7.11.2. validateProxyCacheConfig
POST /api/v1/organization/{orgname}/validateproxycache
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | string |
Request body schema (application/json)
Proxy cache configuration for an organization
| Name | Description | Schema |
|---|---|---|
|
upstream_registry | Name of the upstream registry that is to be cached | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 202 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.11.3. getOrganizationCollaborators
List outside collaborators of the specified organization.
GET /api/v1/organization/{orgname}/collaborators
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/organization/{orgname}/collaborators" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/{orgname}/collaborators" \
-H "Authorization: Bearer <access_token>"7.11.4. getOrganizationApplication
Retrieves the application with the specified client_id under the specified organization.
GET /api/v1/organization/{orgname}/applications/{client_id}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
client_id | The OAuth client ID | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/applications/<client_id>" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/applications/<client_id>" \
-H "Authorization: Bearer <access_token>"7.11.5. updateOrganizationApplication
Updates an application under this organization.
PUT /api/v1/organization/{orgname}/applications/{client_id}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
client_id | The OAuth client ID | string |
| path |
orgname | The name of the organization | string |
Request body schema (application/json)
Description of an updated application.
| Name | Description | Schema |
|---|---|---|
|
name | The name of the application | string |
|
redirect_uri | The URI for the application’s OAuth redirect | string |
|
application_uri | The URI for the application’s homepage | string |
|
description | The human-readable description for the application | string |
|
avatar_email | The e-mail address of the avatar to use for the application | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.11.6. deleteOrganizationApplication
Deletes the application under this organization.
DELETE /api/v1/organization/{orgname}/applications/{client_id}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
client_id | The OAuth client ID | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/{orgname}/applications/{client_id}" \
-H "Authorization: Bearer <access_token>"
$ curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/{orgname}/applications/{client_id}" \
-H "Authorization: Bearer <access_token>"7.11.7. createOrganizationApplication
Creates a new application under this organization.
POST /api/v1/organization/{orgname}/applications
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Request body schema (application/json)
Description of a new organization application.
| Name | Description | Schema |
|---|---|---|
|
name | The name of the application | string |
|
redirect_uri | The URI for the application’s OAuth redirect | string |
|
application_uri | The URI for the application’s homepage | string |
|
description | The human-readable description for the application | string |
|
avatar_email | The e-mail address of the avatar to use for the application | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.11.8. getOrganizationApplications
List the applications for the specified organization.
GET /api/v1/organization/{orgname}/applications
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/applications" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/applications" \
-H "Authorization: Bearer <access_token>"7.11.9. getProxyCacheConfig
Retrieves the proxy cache configuration of the organization.
GET /api/v1/organization/{orgname}/proxycache
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/organization/{orgname}/proxycache" \
-H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/{orgname}/proxycache" \
-H "Authorization: Bearer <access_token>"7.11.10. deleteProxyCacheConfig
Delete proxy cache configuration for the organization.
DELETE /api/v1/organization/{orgname}/proxycache
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/{orgname}/proxycache" \
-H "Authorization: Bearer <access_token>"
$ curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/{orgname}/proxycache" \
-H "Authorization: Bearer <access_token>"7.11.11. createProxyCacheConfig
Creates proxy cache configuration for the organization.
POST /api/v1/organization/{orgname}/proxycache
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Request body schema (application/json)
Proxy cache configuration for an organization
| Name | Description | Schema |
|---|---|---|
|
upstream_registry | Name of the upstream registry that is to be cached | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.11.12. getOrganizationMember
Retrieves the details of a member of the organization.
GET /api/v1/organization/{orgname}/members/{membername}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
membername | The username of the organization member | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/members/<membername>" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/members/<membername>" \
-H "Authorization: Bearer <access_token>"7.11.13. removeOrganizationMember
Removes a member from an organization, revoking all its repository priviledges and removing it from all teams in the organization.
DELETE /api/v1/organization/{orgname}/members/{membername}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
membername | The username of the organization member | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/members/<membername>" \ -H "Authorization: Bearer <access_token>"
$ curl -X DELETE "https://<quay-server.example.com>/api/v1/organization/<orgname>/members/<membername>" \
-H "Authorization: Bearer <access_token>"7.11.14. getOrganizationMembers
List the human members of the specified organization.
GET /api/v1/organization/{orgname}/members
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/members" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/organization/<orgname>/members" \
-H "Authorization: Bearer <access_token>"7.11.15. getOrganization
Get the details for the specified organization.
GET /api/v1/organization/{orgname}
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>"7.11.16. changeOrganizationDetails
Change the details for the specified organization.
PUT /api/v1/organization/{orgname}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Request body schema (application/json)
Description of updates for an existing organization
| Name | Description | Schema |
|---|---|---|
|
email | Organization contact email | string |
|
invoice_email | Whether the organization desires to receive emails for invoices | boolean |
|
invoice_email_address | The email address at which to receive invoices | |
|
tag_expiration_s | The number of seconds for tag expiration | integer |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X PUT \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>"
$ curl -X PUT \
-H "Authorization: Bearer <bearer_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>"7.11.17. deleteAdminedOrganization
Deletes the specified organization.
DELETE /api/v1/organization/{orgname}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>"7.11.18. getApplicationInformation
Get information on the specified application.
GET /api/v1/app/{client_id}
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
client_id | The OAuth client ID | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://<quay-server.example.com>/api/v1/app/<client_id>" \ -H "Authorization: Bearer <access_token>"
$ curl -X GET "https://<quay-server.example.com>/api/v1/app/<client_id>" \
-H "Authorization: Bearer <access_token>"7.12. permission
Manage repository permissions.
7.12.1. getUserTransitivePermission
Get the fetch the permission for the specified user.
GET /api/v1/repository/{repository}/permissions/user/{username}/transitive
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
username | The username of the user to which the permissions apply | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<repository_path>/permissions/user/<username>/transitive"
$ curl -X GET \
-H "Authorization: Bearer <access_token>" \
"https://quay-server.example.com/api/v1/repository/<repository_path>/permissions/user/<username>/transitive"7.12.2. getUserPermissions
Get the permission for the specified user.
GET /api/v1/repository/{repository}/permissions/user/{username}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
username | The username of the user to which the permission applies | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<repository_path>/permissions/user/<username>"
$ curl -X GET \
-H "Authorization: Bearer <access_token>" \
"https://quay-server.example.com/api/v1/repository/<repository_path>/permissions/user/<username>"7.12.3. changeUserPermissions
Update the perimssions for an existing repository.
PUT /api/v1/repository/{repository}/permissions/user/{username}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
username | The username of the user to which the permission applies | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
Description of a user permission.
| Name | Description | Schema |
|---|---|---|
|
role | Role to use for the user | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X PUT \
-H "Authorization: Bearer <bearer_token>" \
-H "Content-Type: application/json" \
-d '{"role": "admin"}' \
https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>
$ curl -X PUT \
-H "Authorization: Bearer <bearer_token>" \
-H "Content-Type: application/json" \
-d '{"role": "admin"}' \
https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>7.12.4. deleteUserPermissions
Delete the permission for the user.
DELETE /api/v1/repository/{repository}/permissions/user/{username}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
username | The username of the user to which the permission applies | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>
$ curl -X DELETE \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>7.12.5. getTeamPermissions
Fetch the permission for the specified team.
GET /api/v1/repository/{repository}/permissions/team/{teamname}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
teamname | The name of the team to which the permission applies | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"
$ curl -X GET \
-H "Authorization: Bearer <access_token>" \
"https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"7.12.6. changeTeamPermissions
Update the existing team permission.
PUT /api/v1/repository/{repository}/permissions/team/{teamname}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
teamname | The name of the team to which the permission applies | string |
Request body schema (application/json)
Description of a team permission.
| Name | Description | Schema |
|---|---|---|
|
role | Role to use for the team | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
curl -X PUT \
-H "Authorization: Bearer <access_token>" \
-H "Content-Type: application/json" \
-d '{"role": "<role>"}' \
"https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"
$ curl -X PUT \
-H "Authorization: Bearer <access_token>" \
-H "Content-Type: application/json" \
-d '{"role": "<role>"}' \
"https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"7.12.7. deleteTeamPermissions
Delete the permission for the specified team.
DELETE /api/v1/repository/{repository}/permissions/team/{teamname}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
teamname | The name of the team to which the permission applies | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"
$ curl -X DELETE \
-H "Authorization: Bearer <access_token>" \
"https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/<teamname>"7.12.8. listRepoTeamPermissions
List all team permission.
GET /api/v1/repository/{repository}/permissions/team/
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <access_token>" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/"
$ curl -X GET \
-H "Authorization: Bearer <access_token>" \
"https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/permissions/team/"7.12.9. listRepoUserPermissions
List all user permissions.
GET /api/v1/repository/{repository}/permissions/user/
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>/
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository>/permissions/user/<username>/7.13. policy
7.13.1. createOrganizationAutoPrunePolicy
Creates an auto-prune policy for the organization
POST /api/v1/organization/{orgname}/autoprunepolicy/
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Request body schema (application/json)
The policy configuration that is to be applied to the user namespace
| Name | Description | Schema |
|---|---|---|
|
method | The method to use for pruning tags (number_of_tags, creation_date) | string |
|
value | The value to use for the pruning method (number of tags e.g. 10, time delta e.g. 7d (7 days)) | |
|
tagPattern | Tags only matching this pattern will be pruned | string |
|
tagPatternMatches | Determine whether pruned tags should or should not match the tagPattern | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags", "value": 10}' http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/
$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags", "value": 10}' http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/7.13.2. listOrganizationAutoPrunePolicies
Lists the auto-prune policies for the organization
GET /api/v1/organization/{orgname}/autoprunepolicy/
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/organization/example_org/autoprunepolicy/" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/organization/example_org/autoprunepolicy/" \
-H "Authorization: Bearer <your_access_token>"7.13.3. getOrganizationAutoPrunePolicy
Fetches the auto-prune policy for the organization
GET /api/v1/organization/{orgname}/autoprunepolicy/{policy_uuid}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
policy_uuid | The unique ID of the policy | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/<policy_uuid>
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/<policy_uuid>7.13.4. deleteOrganizationAutoPrunePolicy
Deletes the auto-prune policy for the organization
DELETE /api/v1/organization/{orgname}/autoprunepolicy/{policy_uuid}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
policy_uuid | The unique ID of the policy | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://quay-server.example.com/api/v1/organization/example_org/autoprunepolicy/example_policy_uuid" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/organization/example_org/autoprunepolicy/example_policy_uuid" \
-H "Authorization: Bearer <your_access_token>"7.13.5. updateOrganizationAutoPrunePolicy
Updates the auto-prune policy for the organization
PUT /api/v1/organization/{orgname}/autoprunepolicy/{policy_uuid}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
policy_uuid | The unique ID of the policy | string |
| path |
orgname | The name of the organization | string |
Request body schema (application/json)
The policy configuration that is to be applied to the user namespace
| Name | Description | Schema |
|---|---|---|
|
method | The method to use for pruning tags (number_of_tags, creation_date) | string |
|
value | The value to use for the pruning method (number of tags e.g. 10, time delta e.g. 7d (7 days)) | |
|
tagPattern | Tags only matching this pattern will be pruned | string |
|
tagPatternMatches | Determine whether pruned tags should or should not match the tagPattern | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.13.6. createRepositoryAutoPrunePolicy
Creates an auto-prune policy for the repository
POST /api/v1/repository/{repository}/autoprunepolicy/
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
The policy configuration that is to be applied to the user namespace
| Name | Description | Schema |
|---|---|---|
|
method | The method to use for pruning tags (number_of_tags, creation_date) | string |
|
value | The value to use for the pruning method (number of tags e.g. 10, time delta e.g. 7d (7 days)) | |
|
tagPattern | Tags only matching this pattern will be pruned | string |
|
tagPatternMatches | Determine whether pruned tags should or should not match the tagPattern | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags","value": 2}' http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/
$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags","value": 2}' http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/7.13.7. listRepositoryAutoPrunePolicies
Lists the auto-prune policies for the repository
GET /api/v1/repository/{repository}/autoprunepolicy/
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/autoprunepolicy/" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/autoprunepolicy/" \
-H "Authorization: Bearer <your_access_token>"7.13.8. getRepositoryAutoPrunePolicy
Fetches the auto-prune policy for the repository
GET /api/v1/repository/{repository}/autoprunepolicy/{policy_uuid}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
policy_uuid | The unique ID of the policy | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/autoprunepolicy/123e4567-e89b-12d3-a456-426614174000" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/autoprunepolicy/123e4567-e89b-12d3-a456-426614174000" \
-H "Authorization: Bearer <your_access_token>"7.13.9. deleteRepositoryAutoPrunePolicy
Deletes the auto-prune policy for the repository
DELETE /api/v1/repository/{repository}/autoprunepolicy/{policy_uuid}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
policy_uuid | The unique ID of the policy | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/autoprunepolicy/123e4567-e89b-12d3-a456-426614174000" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/autoprunepolicy/123e4567-e89b-12d3-a456-426614174000" \
-H "Authorization: Bearer <your_access_token>"7.13.10. updateRepositoryAutoPrunePolicy
Updates the auto-prune policy for the repository
PUT /api/v1/repository/{repository}/autoprunepolicy/{policy_uuid}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
policy_uuid | The unique ID of the policy | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
The policy configuration that is to be applied to the user namespace
| Name | Description | Schema |
|---|---|---|
|
method | The method to use for pruning tags (number_of_tags, creation_date) | string |
|
value | The value to use for the pruning method (number of tags e.g. 10, time delta e.g. 7d (7 days)) | |
|
tagPattern | Tags only matching this pattern will be pruned | string |
|
tagPatternMatches | Determine whether pruned tags should or should not match the tagPattern | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.13.11. createUserAutoPrunePolicy
Creates the auto-prune policy for the currently logged in user
POST /api/v1/user/autoprunepolicy/
Authorizations: oauth2_implicit (user:admin)
Request body schema (application/json)
The policy configuration that is to be applied to the user namespace
| Name | Description | Schema |
|---|---|---|
|
method | The method to use for pruning tags (number_of_tags, creation_date) | string |
|
value | The value to use for the pruning method (number of tags e.g. 10, time delta e.g. 7d (7 days)) | |
|
tagPattern | Tags only matching this pattern will be pruned | string |
|
tagPatternMatches | Determine whether pruned tags should or should not match the tagPattern | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.13.12. listUserAutoPrunePolicies
Lists the auto-prune policies for the currently logged in user
GET /api/v1/user/autoprunepolicy/
Authorizations: oauth2_implicit (user:admin)
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/user/autoprunepolicy/" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/user/autoprunepolicy/" \
-H "Authorization: Bearer <your_access_token>"7.13.13. getUserAutoPrunePolicy
Fetches the auto-prune policy for the currently logged in user
GET /api/v1/user/autoprunepolicy/{policy_uuid}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
policy_uuid | The unique ID of the policy | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/user/autoprunepolicy/{policy_uuid}" \
-H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/user/autoprunepolicy/{policy_uuid}" \
-H "Authorization: Bearer <your_access_token>"7.13.14. deleteUserAutoPrunePolicy
Deletes the auto-prune policy for the currently logged in user
DELETE /api/v1/user/autoprunepolicy/{policy_uuid}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
policy_uuid | The unique ID of the policy | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://quay-server.example.com/api/v1/user/autoprunepolicy/<policy_uuid>" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/user/autoprunepolicy/<policy_uuid>" \
-H "Authorization: Bearer <your_access_token>"7.13.15. updateUserAutoPrunePolicy
Updates the auto-prune policy for the currently logged in user
PUT /api/v1/user/autoprunepolicy/{policy_uuid}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
policy_uuid | The unique ID of the policy | string |
Request body schema (application/json)
The policy configuration that is to be applied to the user namespace
| Name | Description | Schema |
|---|---|---|
|
method | The method to use for pruning tags (number_of_tags, creation_date) | string |
|
value | The value to use for the pruning method (number of tags e.g. 10, time delta e.g. 7d (7 days)) | |
|
tagPattern | Tags only matching this pattern will be pruned | string |
|
tagPatternMatches | Determine whether pruned tags should or should not match the tagPattern | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.14. prototype
Manage default permissions added to repositories.
7.14.1. updateOrganizationPrototypePermission
Update the role of an existing permission prototype.
PUT /api/v1/organization/{orgname}/prototypes/{prototypeid}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
prototypeid | The ID of the prototype | string |
| path |
orgname | The name of the organization | string |
Request body schema (application/json)
Description of a the new prototype role
| Name | Description | Schema |
|---|---|---|
|
role | Role that should be applied to the permission | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.14.2. deleteOrganizationPrototypePermission
Delete an existing permission prototype.
DELETE /api/v1/organization/{orgname}/prototypes/{prototypeid}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
prototypeid | The ID of the prototype | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/organization/<organization_name>/prototypes/<prototype_id>
curl -X DELETE \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
https://<quay-server.example.com>/api/v1/organization/<organization_name>/prototypes/<prototype_id>7.14.3. createOrganizationPrototypePermission
Create a new permission prototype.
POST /api/v1/organization/{orgname}/prototypes
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Request body schema (application/json)
Description of a new prototype
| Name | Description | Schema |
|---|---|---|
|
role | Role that should be applied to the delegate | string |
|
activating_user | Repository creating user to whom the rule should apply | object |
|
delegate | Information about the user or team to which the rule grants access | object |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.14.4. getOrganizationPrototypePermissions
List the existing prototypes for this organization.
GET /api/v1/organization/{orgname}/prototypes
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/organization/<organization_name>/prototypes
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
https://<quay-server.example.com>/api/v1/organization/<organization_name>/prototypes7.15. referrers
List v2 API referrers
7.15.1. getReferrers
List v2 API referrers of an image digest.
GET /v2/{organization_name}/{repository_name}/referrers/{digest}
Request body schema (application/json)
Referrers of an image digest.
| Type | Name | Description | Schema |
| path |
orgname | The name of the organization | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
referrers | Looks up the OCI referrers of a manifest under a repository. | string |
7.16. repository
List, create and manage repositories.
7.16.1. createRepo
Create a new repository.
POST /api/v1/repository
Authorizations: oauth2_implicit (repo:create)
Request body schema (application/json)
Description of a new repository
| Name | Description | Schema |
|---|---|---|
|
repository | Repository name | string |
|
visibility | Visibility which the repository will start with | string |
|
namespace | Namespace in which the repository should be created. If omitted, the username of the caller is used | string |
|
description | Markdown encoded description for the repository | string |
|
repo_kind | The kind of repository |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.16.2. listRepos
Fetch the list of repositories visible to the current user under a variety of situations.
GET /api/v1/repository
Authorizations: oauth2_implicit (repo:read)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
next_page | The page token for the next page | string |
| query |
repo_kind | The kind of repositories to return | string |
| query |
popularity | Whether to include the repository’s popularity metric. | boolean |
| query |
last_modified | Whether to include when the repository was last modified. | boolean |
| query |
public | Adds any repositories visible to the user by virtue of being public | boolean |
| query |
starred | Filters the repositories returned to those starred by the user | boolean |
| query |
namespace | Filters the repositories returned to this namespace | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <ACCESS_TOKEN>" \ "https://quay-server.example.com/api/v1/repository?public=true&starred=false&namespace=<NAMESPACE>"
$ curl -X GET \
-H "Authorization: Bearer <ACCESS_TOKEN>" \
"https://quay-server.example.com/api/v1/repository?public=true&starred=false&namespace=<NAMESPACE>"7.16.3. changeRepoVisibility
Change the visibility of a repository.
POST /api/v1/repository/{repository}/changevisibility
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
Change the visibility for the repository.
| Name | Description | Schema |
|---|---|---|
|
visibility | Visibility which the repository will start with | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example Command
7.16.4. changeRepoState
Change the state of a repository.
PUT /api/v1/repository/{repository}/changestate
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
Change the state of the repository.
| Name | Description | Schema |
|---|---|---|
|
state | Determines whether pushes are allowed. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.16.5. getRepo
Fetch the specified repository.
GET /api/v1/repository/{repository}
Authorizations: oauth2_implicit (repo:read)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
includeTags | Whether to include repository tags | boolean |
| query |
includeStats | Whether to include action statistics | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"7.16.6. updateRepo
Update the description in the specified repository.
PUT /api/v1/repository/{repository}
Authorizations: oauth2_implicit (repo:write)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
Fields which can be updated in a repository.
| Name | Description | Schema |
|---|---|---|
|
description | Markdown encoded description for the repository | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.16.7. deleteRepository
Delete a repository.
DELETE /api/v1/repository/{repository}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"
$ curl -X DELETE -H "Authorization: Bearer <bearer_token>" "<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>"7.17. repositorynotification
List, create and manage repository events/notifications.
7.17.1. testRepoNotification
Queues a test notification for this repository.
POST /api/v1/repository/{repository}/notification/{uuid}/test
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
uuid | The UUID of the notification | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<repository>/notification/<uuid>/test
$ curl -X POST \
-H "Authorization: Bearer <bearer_token>" \
https://<quay-server.example.com>/api/v1/repository/<repository>/notification/<uuid>/test7.17.2. getRepoNotification
Get information for the specified notification.
GET /api/v1/repository/{repository}/notification/{uuid}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
uuid | The UUID of the notification | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<repository>/notification/<uuid>
$ curl -X POST \
-H "Authorization: Bearer <bearer_token>" \
https://<quay-server.example.com>/api/v1/repository/<repository>/notification/<uuid>7.17.3. deleteRepoNotification
Deletes the specified notification.
DELETE /api/v1/repository/{repository}/notification/{uuid}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
uuid | The UUID of the notification | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>/notification/<uuid>
$ curl -X DELETE \
-H "Authorization: Bearer <bearer_token>" \
https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>/notification/<uuid>7.17.4. resetRepositoryNotificationFailures
Resets repository notification to 0 failures.
POST /api/v1/repository/{repository}/notification/{uuid}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
uuid | The UUID of the notification | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ https://<quay-server.example.com>/api/v1/repository/<repository>/notification/<uuid>
$ curl -X POST \
-H "Authorization: Bearer <bearer_token>" \
https://<quay-server.example.com>/api/v1/repository/<repository>/notification/<uuid>7.17.5. createRepoNotification
POST /api/v1/repository/{repository}/notification/
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
Information for creating a notification on a repository
| Name | Description | Schema |
|---|---|---|
|
event | The event on which the notification will respond | string |
|
method | The method of notification (such as email or web callback) | string |
|
config | JSON config information for the specific method of notification | object |
|
eventConfig | JSON config information for the specific event of notification | object |
|
title | The human-readable title of the notification | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.17.6. listRepoNotifications
List the notifications for the specified repository.
GET /api/v1/repository/{repository}/notification/
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET -H "Authorization: Bearer <bearer_token>" -H "Accept: application/json" https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>/notification
$ curl -X GET -H "Authorization: Bearer <bearer_token>" -H "Accept: application/json" https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>/notification7.18. robot
Manage user and organization robot accounts.
7.18.1. getUserRobots
List the available robots for the user.
GET /api/v1/user/robots
Authorizations: oauth2_implicit (user:admin)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
limit | If specified, the number of robots to return. | integer |
| query |
token | If false, the robot’s token is not returned. | boolean |
| query |
permissions | Whether to include repositories and teams in which the robots have permission. | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/user/robots?limit=10&token=false&permissions=true" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/user/robots?limit=10&token=false&permissions=true" \
-H "Authorization: Bearer <your_access_token>"7.18.2. getOrgRobotPermissions
Returns the list of repository permissions for the org’s robot.
GET /api/v1/organization/{orgname}/robots/{robot_shortname}/permissions
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
robot_shortname | The short name for the robot, without any user or organization prefix | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/organization/<ORGNAME>/robots/<ROBOT_SHORTNAME>/permissions"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
"https://quay-server.example.com/api/v1/organization/<ORGNAME>/robots/<ROBOT_SHORTNAME>/permissions"7.18.3. regenerateOrgRobotToken
Regenerates the token for an organization robot.
POST /api/v1/organization/{orgname}/robots/{robot_shortname}/regenerate
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
robot_shortname | The short name for the robot, without any user or organization prefix | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<orgname>/robots/<robot_shortname>/regenerate"
$ curl -X POST \
-H "Authorization: Bearer <bearer_token>" \
"<quay-server.example.com>/api/v1/organization/<orgname>/robots/<robot_shortname>/regenerate"7.18.4. getUserRobotPermissions
Returns the list of repository permissions for the user’s robot.
GET /api/v1/user/robots/{robot_shortname}/permissions
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
robot_shortname | The short name for the robot, without any user or organization prefix | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/user/robots/<ROBOT_SHORTNAME>/permissions"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
"https://quay-server.example.com/api/v1/user/robots/<ROBOT_SHORTNAME>/permissions"7.18.5. regenerateUserRobotToken
Regenerates the token for a user’s robot.
POST /api/v1/user/robots/{robot_shortname}/regenerate
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
robot_shortname | The short name for the robot, without any user or organization prefix | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>/regenerate"
$ curl -X POST \
-H "Authorization: Bearer <bearer_token>" \
"<quay-server.example.com>/api/v1/user/robots/<robot_shortname>/regenerate"7.18.6. getOrgRobot
Returns the organization’s robot with the specified name.
GET /api/v1/organization/{orgname}/robots/{robot_shortname}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
robot_shortname | The short name for the robot, without any user or organization prefix | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://quay-server.example.com/api/v1/organization/<ORGNAME>/robots/<ROBOT_SHORTNAME>"
curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
"https://quay-server.example.com/api/v1/organization/<ORGNAME>/robots/<ROBOT_SHORTNAME>"7.18.7. createOrgRobot
Create a new robot in the organization.
PUT /api/v1/organization/{orgname}/robots/{robot_shortname}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
robot_shortname | The short name for the robot, without any user or organization prefix | string |
| path |
orgname | The name of the organization | string |
Request body schema (application/json)
Optional data for creating a robot
| Name | Description | Schema |
|---|---|---|
|
description | Optional text description for the robot | string |
|
unstructured_metadata | Optional unstructured metadata for the robot | object |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_name>"
$ curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_name>"7.18.8. deleteOrgRobot
Delete an existing organization robot.
DELETE /api/v1/organization/{orgname}/robots/{robot_shortname}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
robot_shortname | The short name for the robot, without any user or organization prefix | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_shortname>"
curl -X DELETE \
-H "Authorization: Bearer <bearer_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_shortname>"7.18.9. getOrgRobots
List the organization’s robots.
GET /api/v1/organization/{orgname}/robots
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
orgname | The name of the organization | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
limit | If specified, the number of robots to return. | integer |
| query |
token | If false, the robot’s token is not returned. | boolean |
| query |
permissions | Whether to include repositories and teams in which the robots have permission. | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots"7.18.10. getUserRobot
Returns the user’s robot with the specified name.
GET /api/v1/user/robots/{robot_shortname}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
robot_shortname | The short name for the robot, without any user or organization prefix | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
"<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"7.18.11. createUserRobot
Create a new user robot with the specified name.
PUT /api/v1/user/robots/{robot_shortname}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
robot_shortname | The short name for the robot, without any user or organization prefix | string |
Request body schema (application/json)
Optional data for creating a robot
| Name | Description | Schema |
|---|---|---|
|
description | Optional text description for the robot | string |
|
unstructured_metadata | Optional unstructured metadata for the robot | object |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/user/robots/<robot_name>"
$ curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/user/robots/<robot_name>"7.18.12. deleteUserRobot
Delete an existing robot.
DELETE /api/v1/user/robots/{robot_shortname}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
robot_shortname | The short name for the robot, without any user or organization prefix | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"
$ curl -X DELETE \
-H "Authorization: Bearer <bearer_token>" \
"<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"7.18.13. Auth Federated Robot Token
Return an expiring robot token using the robot identity federation mechanism.
GET oauth2/federation/robot/token
Authorizations: oauth2_implicit (robot:auth)
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful authentication and token generation | { "token": "string" } |
| 401 | Unauthorized: missing or invalid authentication | { "error": "string" } |
Request Body
| Type | Name | Description | Schema |
|---|---|---|---|
| body |
auth_result | The result of the authentication process, containing information about the robot identity. | { "missing": "boolean", "error_message": "string", "context": { "robot": "RobotObject" } } |
Example command
curl -X GET "https://quay-server.example.com/oauth2/federation/robot/token" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/oauth2/federation/robot/token" \
-H "Authorization: Bearer <your_access_token>"7.18.14. createOrgRobotFederation
Create a federation configuration for the specified organization robot.
POST /api/v1/organization/{orgname}/robots/{robot_shortname}/federation
Retrieve the federation configuration for the specified organization robot.
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path | orgname + robot_shortnamerequired | The name of the organization and the short name for the robot, without any user or organization prefix | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access |
Example command
curl -X POST "https://quay-server.example.com/api/v1/organization/{orgname}/robots/{robot_shortname}/federation" \
-H "Authorization: Bearer <your_access_token>" \
-H "Content-Type: application/json"
$ curl -X POST "https://quay-server.example.com/api/v1/organization/{orgname}/robots/{robot_shortname}/federation" \
-H "Authorization: Bearer <your_access_token>" \
-H "Content-Type: application/json"7.19. search
Conduct searches against all registry context.
7.19.1. conductRepoSearch
Get a list of apps and repositories that match the specified query.
GET /api/v1/find/repositories
Authorizations:
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
includeUsage | Whether to include usage metadata | boolean |
| query |
page | The page. | integer |
| query |
query | The search query. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/find/repositories?query=<repo_name>&page=1&includeUsage=true" \ -H "Authorization: Bearer <bearer_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/find/repositories?query=<repo_name>&page=1&includeUsage=true" \
-H "Authorization: Bearer <bearer_token>"7.19.2. conductSearch
Get a list of entities and resources that match the specified query.
GET /api/v1/find/all
Authorizations: oauth2_implicit (repo:read)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
query | The search query. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/find/all?query=<mysearchterm>" \ -H "Authorization: Bearer <bearer_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/find/all?query=<mysearchterm>" \
-H "Authorization: Bearer <bearer_token>"7.19.3. getMatchingEntities
Get a list of entities that match the specified prefix.
GET /api/v1/entities/{prefix}
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
prefix | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
includeOrgs | Whether to include orgs names. | boolean |
| query |
includeTeams | Whether to include team names. | boolean |
| query |
namespace | Namespace to use when querying for org entities. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/entities/<prefix>?includeOrgs=<true_or_false>&includeTeams=<true_or_false>&namespace=<namespace>" \ -H "Authorization: Bearer <bearer_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/entities/<prefix>?includeOrgs=<true_or_false>&includeTeams=<true_or_false>&namespace=<namespace>" \
-H "Authorization: Bearer <bearer_token>"7.20. secscan
List and manage repository vulnerabilities and other security information.
7.20.1. getRepoManifestSecurity
GET /api/v1/repository/{repository}/manifest/{manifestref}/security
Authorizations: oauth2_implicit (repo:read)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
manifestref | The digest of the manifest | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
vulnerabilities | Include vulnerabilities informations | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/manifest/<manifest_digest>/security?vulnerabilities=<true_or_false>"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
"https://quay-server.example.com/api/v1/repository/<namespace>/<repository>/manifest/<manifest_digest>/security?vulnerabilities=<true_or_false>"7.21. superuser
Superuser API.
7.21.1. createInstallUser
Creates a new user.
POST /api/v1/superuser/users/
Authorizations: oauth2_implicit (super:user)
Request body schema (application/json)
Data for creating a user
| Name | Description | Schema |
|---|---|---|
|
username | The username of the user being created | string |
|
email | The email address of the user being created | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X POST -H "Authorization: Bearer <bearer_token>" -H "Content-Type: application/json" -d '{
"username": "newuser",
"email": "newuser@example.com"
}' "https://<quay-server.example.com>/api/v1/superuser/users/"
$ curl -X POST -H "Authorization: Bearer <bearer_token>" -H "Content-Type: application/json" -d '{
"username": "newuser",
"email": "newuser@example.com"
}' "https://<quay-server.example.com>/api/v1/superuser/users/"7.21.2. deleteInstallUser
Deletes a user.
DELETE /api/v1/superuser/users/{username}
Authorizations: oauth2_implicit (super:user)
Request body schema (application/json)
Data for deleting a user
| Name | Description | Schema |
|---|---|---|
|
username | The username of the user being deleted | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/superuser/users/{username}"
$ curl -X DELETE -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/superuser/users/{username}"7.21.3. listAllUsers
Returns a list of all users in the system.
GET /api/v1/superuser/users/
Authorizations: oauth2_implicit (super:user)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
next_page | The page token for the next page | string |
| query |
limit | Limit to the number of results to return per page. Max 100. | integer |
| query |
disabled | If false, only enabled users will be returned. | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/superuser/users/"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/superuser/users/"7.21.4. listAllLogs
List the usage logs for the current system.
GET /api/v1/superuser/logs
Authorizations: oauth2_implicit (super:user)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
next_page | The page token for the next page | string |
| query |
page | The page number for the logs | integer |
| query |
endtime | Latest time to which to get logs (%m/%d/%Y %Z) | string |
| query |
starttime | Earliest time from which to get logs (%m/%d/%Y %Z) | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/logs?starttime=<start_time>&endtime=<end_time>&page=<page_number>&next_page=<next_page_token>"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
"https://<quay_server>/api/v1/superuser/logs?starttime=<start_time>&endtime=<end_time>&page=<page_number>&next_page=<next_page_token>"7.21.5. listAllOrganizations
List the organizations for the current system.
GET /api/v1/superuser/organizations
Authorizations: oauth2_implicit (super:user)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
name | The name of the organization being managed | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/superuser/organizations/"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/superuser/organizations/"7.21.6. createServiceKey
POST /api/v1/superuser/keys
Authorizations: oauth2_implicit (super:user)
Request body schema (application/json)
Description of creation of a service key
| Name | Description | Schema |
|---|---|---|
|
service | The service authenticating with this key | string |
|
name | The friendly name of a service key | string |
|
metadata | The key/value pairs of this key’s metadata | object |
|
notes | If specified, the extra notes for the key | string |
|
expiration | The expiration date as a unix timestamp |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.21.7. listServiceKeys
GET /api/v1/superuser/keys
Authorizations: oauth2_implicit (super:user)
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/keys"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
"https://<quay_server>/api/v1/superuser/keys"7.21.8. changeUserQuotaSuperUser
PUT /api/v1/superuser/organization/{namespace}/quota/{quota_id}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
namespace | string | |
| path |
quota_id | string |
Request body schema (application/json)
Description of a new organization quota
| Name | Description | Schema |
|---|---|---|
|
limit_bytes | Number of bytes the organization is allowed | integer |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.21.9. deleteUserQuotaSuperUser
DELETE /api/v1/superuser/organization/{namespace}/quota/{quota_id}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
namespace | string | |
| path |
quota_id | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://quay-server.example.com/api/v1/superuser/organization/<namespace>/quota/<quota_id>" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/superuser/organization/<namespace>/quota/<quota_id>" \
-H "Authorization: Bearer <ACCESS_TOKEN>"7.21.10. createUserQuotaSuperUser
POST /api/v1/superuser/organization/{namespace}/quota
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
namespace | string |
Request body schema (application/json)
Description of a new organization quota
| Name | Description | Schema |
|---|---|---|
|
limit_bytes | Number of bytes the organization is allowed | integer |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.21.11. listUserQuotaSuperUser
GET /api/v1/superuser/organization/{namespace}/quota
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
namespace | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/superuser/organization/<namespace>/quota" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X GET "https://quay-server.example.com/api/v1/superuser/organization/<namespace>/quota" \
-H "Authorization: Bearer <ACCESS_TOKEN>"7.21.12. changeOrganizationQuotaSuperUser
PUT /api/v1/superuser/users/{namespace}/quota/{quota_id}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
namespace | string | |
| path |
quota_id | string |
Request body schema (application/json)
Description of a new organization quota
| Name | Description | Schema |
|---|---|---|
|
limit_bytes | Number of bytes the organization is allowed | integer |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.21.13. deleteOrganizationQuotaSuperUser
DELETE /api/v1/superuser/users/{namespace}/quota/{quota_id}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
namespace | string | |
| path |
quota_id | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://quay-server.example.com/api/v1/superuser/users/<username>/quota/<quota_id>" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/superuser/users/<username>/quota/<quota_id>" \
-H "Authorization: Bearer <ACCESS_TOKEN>"7.21.14. createOrganizationQuotaSuperUser
POST /api/v1/superuser/users/{namespace}/quota
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
namespace | string |
Request body schema (application/json)
Description of a new organization quota
| Name | Description | Schema |
|---|---|---|
|
limit_bytes | Number of bytes the organization is allowed | integer |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.21.15. listOrganizationQuotaSuperUser
GET /api/v1/superuser/users/{namespace}/quota
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
namespace | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/superuser/users/<username>/quota" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X GET "https://quay-server.example.com/api/v1/superuser/users/<username>/quota" \
-H "Authorization: Bearer <ACCESS_TOKEN>"7.21.16. changeOrganization
Updates information about the specified user.
PUT /api/v1/superuser/organizations/{name}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
name | The name of the organizaton being managed | string |
Request body schema (application/json)
Description of updates for an existing organization
| Name | Description | Schema |
|---|---|---|
|
email | Organization contact email | string |
|
invoice_email | Whether the organization desires to receive emails for invoices | boolean |
|
invoice_email_address | The email address at which to receive invoices | |
|
tag_expiration_s | The number of seconds for tag expiration | integer |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.21.17. deleteOrganization
Deletes the specified organization.
DELETE /api/v1/superuser/organizations/{name}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
name | The name of the organizaton being managed | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/organizations/<organization_name>"
$ curl -X DELETE \
-H "Authorization: Bearer <bearer_token>" \
"https://<quay_server>/api/v1/superuser/organizations/<organization_name>"7.21.18. approveServiceKey
POST /api/v1/superuser/approvedkeys/{kid}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
kid | The unique identifier for a service key | string |
Request body schema (application/json)
Information for approving service keys
| Name | Description | Schema |
|---|---|---|
|
notes | Optional approval notes | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.21.19. deleteServiceKey
DELETE /api/v1/superuser/keys/{kid}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
kid | The unique identifier for a service key | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/keys/<kid>"
$ curl -X DELETE \
-H "Authorization: Bearer <bearer_token>" \
"https://<quay_server>/api/v1/superuser/keys/<kid>"7.21.20. updateServiceKey
PUT /api/v1/superuser/keys/{kid}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
kid | The unique identifier for a service key | string |
Request body schema (application/json)
Description of updates for a service key
| Name | Description | Schema |
|---|---|---|
|
name | The friendly name of a service key | string |
|
metadata | The key/value pairs of this key’s metadata | object |
|
expiration | The expiration date as a unix timestamp |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.21.21. getServiceKey
GET /api/v1/superuser/keys/{kid}
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
kid | The unique identifier for a service key | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/keys/<kid>"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
"https://<quay_server>/api/v1/superuser/keys/<kid>"7.21.22. getRepoBuildStatusSuperUser
Return the status for the builds specified by the build uuids.
GET /api/v1/superuser/{build_uuid}/status
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
build_uuid | The UUID of the build | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/status" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/status" \
-H "Authorization: Bearer <ACCESS_TOKEN>"7.21.23. getRepoBuildSuperUser
Returns information about a build.
GET /api/v1/superuser/{build_uuid}/build
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
build_uuid | The UUID of the build | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/build" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/build" \
-H "Authorization: Bearer <ACCESS_TOKEN>"7.21.24. getRepoBuildLogsSuperUser
Return the build logs for the build specified by the build uuid.
GET /api/v1/superuser/{build_uuid}/logs
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
build_uuid | The UUID of the build | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/logs" \ -H "Authorization: Bearer <ACCESS_TOKEN>"
$ curl -X GET "https://quay-server.example.com/api/v1/superuser/<build_uuid>/logs" \
-H "Authorization: Bearer <ACCESS_TOKEN>"7.21.25. getRegistrySize
GET /api/v1/superuser/registrysize/
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
namespace | string |
Description of a image registry size
| Name | Description | Schema |
|---|---|---|
|
size_bytes* | Number of bytes the organization is allowed | integer |
| last_ran | integer | |
| queued | boolean | |
| running | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | CREATED | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "https://<quay_server>/api/v1/superuser/registrysize/"
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
"https://<quay_server>/api/v1/superuser/registrysize/"7.21.26. postRegistrySize
POST /api/v1/superuser/registrysize/
Authorizations: oauth2_implicit (super:user)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
namespace | string |
Request body schema (application/json)
Description of a image registry size
| Name | Description | Schema |
|---|---|---|
| last_ran | integer | |
| queued | boolean | |
| running | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | CREATED | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.22. tag
Manage the tags of a repository.
7.22.1. restoreTag
Restores a repository tag back to a previous image in the repository.
POST /api/v1/repository/{repository}/tag/{tag}/restore
Authorizations: oauth2_implicit (repo:write)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
tag | The name of the tag | string |
Request body schema (application/json)
Restores a tag to a specific image
| Name | Description | Schema |
|---|---|---|
|
manifest_digest | If specified, the manifest digest that should be used | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.22.2. changeTag
Change which image a tag points to or create a new tag.
PUT /api/v1/repository/{repository}/tag/{tag}
Authorizations: oauth2_implicit (repo:write)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
tag | The name of the tag | string |
Request body schema (application/json)
Makes changes to a specific tag
| Name | Description | Schema |
|---|---|---|
|
manifest_digest | (If specified) The manifest digest to which the tag should point | |
|
expiration | (If specified) The expiration for the image |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.22.3. deleteFullTag
Delete the specified repository tag.
DELETE /api/v1/repository/{repository}/tag/{tag}
Authorizations: oauth2_implicit (repo:write)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
| path |
tag | The name of the tag | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/tag/<tag_name>" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/tag/<tag_name>" \
-H "Authorization: Bearer <your_access_token>"7.22.4. listRepoTags
GET /api/v1/repository/{repository}/tag/
Authorizations: oauth2_implicit (repo:read)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
onlyActiveTags | Filter to only active tags. | boolean |
| query |
page | Page index for the results. Default 1. | integer |
| query |
limit | Limit to the number of results to return per page. Max 100. | integer |
| query |
filter_tag_name | Syntax: <op>:<name> Filters the tag names based on the operation.<op> can be 'like' or 'eq'. | string |
| query |
specificTag | Filters the tags to the specific tag. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ -H "Accept: application/json" \ https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>/tag/
$ curl -X GET \
-H "Authorization: Bearer <bearer_token>" \
-H "Accept: application/json" \
https://<quay-server.example.com>/api/v1/repository/<namespace>/<repository_name>/tag/7.23. team
Create, list and manage an organization’s teams.
7.23.1. getOrganizationTeamPermissions
Returns the list of repository permissions for the org’s team.
GET /api/v1/organization/{orgname}/team/{teamname}/permissions
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
teamname | The name of the team | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/permissions"
$ curl -X GET \
-H "Authorization: Bearer <your_access_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/permissions"7.23.2. updateOrganizationTeamMember
Adds or invites a member to an existing team.
PUT /api/v1/organization/{orgname}/team/{teamname}/members/{membername}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
teamname | The name of the team | string |
| path |
membername | The username of the team member | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X PUT \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members/<member_name>"
$ curl -X PUT \
-H "Authorization: Bearer <your_access_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members/<member_name>"7.23.3. deleteOrganizationTeamMember
Delete a member of a team.
If the user is merely invited to join the team, then the invite is removed instead.
If the user is merely invited to join the team, then the invite is removed instead.DELETE /api/v1/organization/{orgname}/team/{teamname}/members/{membername}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
teamname | The name of the team | string |
| path |
membername | The username of the team member | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members/<member_name>"
$ curl -X DELETE \
-H "Authorization: Bearer <your_access_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members/<member_name>"7.23.4. getOrganizationTeamMembers
Retrieve the list of members for the specified team.
GET /api/v1/organization/{orgname}/team/{teamname}/members
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
teamname | The name of the team | string |
| path |
orgname | The name of the organization | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
includePending | Whether to include pending members | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members"
$ curl -X GET \
-H "Authorization: Bearer <your_access_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/members"7.23.5. inviteTeamMemberEmail
Invites an email address to an existing team.
PUT /api/v1/organization/{orgname}/team/{teamname}/invite/{email}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
email | string | |
| path |
teamname | string | |
| path |
orgname | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X PUT \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/invite/<email>"
$ curl -X PUT \
-H "Authorization: Bearer <your_access_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/invite/<email>"7.23.6. deleteTeamMemberEmailInvite
Delete an invite of an email address to join a team.
DELETE /api/v1/organization/{orgname}/team/{teamname}/invite/{email}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
email | string | |
| path |
teamname | string | |
| path |
orgname | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
+
curl -X DELETE \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/invite/<email>"
$ curl -X DELETE \
-H "Authorization: Bearer <your_access_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>/invite/<email>"7.23.7. updateOrganizationTeam
Update the org-wide permission for the specified team.
This API is also used to create a team.
PUT /api/v1/organization/{orgname}/team/{teamname}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
teamname | The name of the team | string |
| path |
orgname | The name of the organization | string |
Request body schema (application/json)
Description of a team
| Name | Description | Schema |
|---|---|---|
|
role | Org wide permissions that should apply to the team | string |
|
description | Markdown description for the team | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -k -X PUT -H 'Accept: application/json' -H 'Content-Type: application/json' -H "Authorization: Bearer <bearer_token>" --data '{"role": "creator"}' https://<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>
$ curl -k -X PUT -H 'Accept: application/json' -H 'Content-Type: application/json' -H "Authorization: Bearer <bearer_token>" --data '{"role": "creator"}' https://<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>7.23.8. deleteOrganizationTeam
Delete the specified team.
DELETE /api/v1/organization/{orgname}/team/{teamname}
Authorizations: oauth2_implicit (org:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
teamname | The name of the team | string |
| path |
orgname | The name of the organization | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE \ -H "Authorization: Bearer <your_access_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>"
$ curl -X DELETE \
-H "Authorization: Bearer <your_access_token>" \
"<quay-server.example.com>/api/v1/organization/<organization_name>/team/<team_name>"7.24. trigger
Create, list and manage build triggers.
7.24.1. activateBuildTrigger
Activate the specified build trigger.
POST /api/v1/repository/{repository}/trigger/{trigger_uuid}/activate
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
trigger_uuid | The UUID of the build trigger | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
| Name | Description | Schema |
|---|---|---|
|
config | Arbitrary json. | object |
|
pull_robot | The name of the robot that will be used to pull images. | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.24.2. listTriggerRecentBuilds
List the builds started by the specified trigger.
GET /api/v1/repository/{repository}/trigger/{trigger_uuid}/builds
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
trigger_uuid | The UUID of the build trigger | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
limit | The maximum number of builds to return | integer |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid/builds?limit=10" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid/builds?limit=10" \
-H "Authorization: Bearer <your_access_token>"7.24.3. manuallyStartBuildTrigger
Manually start a build from the specified trigger.
POST /api/v1/repository/{repository}/trigger/{trigger_uuid}/start
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
trigger_uuid | The UUID of the build trigger | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
Optional run parameters for activating the build trigger
| Name | Description | Schema |
|---|---|---|
|
branch_name | (SCM only) If specified, the name of the branch to build. | string |
|
commit_sha | (Custom Only) If specified, the ref/SHA1 used to checkout a git repository. | string |
|
refs | (SCM Only) If specified, the ref to build. |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.24.4. getBuildTrigger
Get information for the specified build trigger.
GET /api/v1/repository/{repository}/trigger/{trigger_uuid}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
trigger_uuid | The UUID of the build trigger | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \
-H "Authorization: Bearer <your_access_token>"7.24.5. updateBuildTrigger
Updates the specified build trigger.
PUT /api/v1/repository/{repository}/trigger/{trigger_uuid}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
trigger_uuid | The UUID of the build trigger | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Request body schema (application/json)
Options for updating a build trigger
| Name | Description | Schema |
|---|---|---|
|
enabled | Whether the build trigger is enabled | boolean |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X PUT "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \
-H "Authorization: Bearer <your_access_token>" \
-H "Content-Type: application/json" \
-d '{"enabled": true}'
$ curl -X PUT "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \
-H "Authorization: Bearer <your_access_token>" \
-H "Content-Type: application/json" \
-d '{"enabled": true}'7.24.6. deleteBuildTrigger
Delete the specified build trigger.
DELETE /api/v1/repository/{repository}/trigger/{trigger_uuid}
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
trigger_uuid | The UUID of the build trigger | string |
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/example-trigger-uuid" \
-H "Authorization: Bearer <your_access_token>"7.24.7. listBuildTriggers
List the triggers for the specified repository.
GET /api/v1/repository/{repository}/trigger/
Authorizations: oauth2_implicit (repo:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/repository/example_namespace/example_repo/trigger/" \
-H "Authorization: Bearer <your_access_token>"7.25. user
Manage the current user.
7.25.1. createStar
Star a repository.
POST /api/v1/user/starred
Authorizations: oauth2_implicit (repo:read)
Request body schema (application/json)
| Name | Description | Schema |
|---|---|---|
|
namespace | Namespace in which the repository belongs | string |
|
repository | Repository name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 201 | Successful creation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
7.25.2. listStarredRepos
List all starred repositories.
GET /api/v1/user/starred
Authorizations: oauth2_implicit (user:admin)
Query parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| query |
next_page | The page token for the next page | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/user/starred?next_page=<next_page_token>" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/user/starred?next_page=<next_page_token>" \
-H "Authorization: Bearer <your_access_token>"7.25.3. getLoggedInUser
Get user information for the authenticated user.
GET /api/v1/user/
Authorizations: oauth2_implicit (user:read)
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/user/" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/user/" \
-H "Authorization: Bearer <your_access_token>"7.25.4. deleteStar
Removes a star from a repository.
DELETE /api/v1/user/starred/{repository}
Authorizations: oauth2_implicit (user:admin)
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
repository | The full path of the repository. e.g. namespace/name | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 204 | Deleted | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X DELETE "https://quay-server.example.com/api/v1/user/starred/namespace/repository-name" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X DELETE "https://quay-server.example.com/api/v1/user/starred/namespace/repository-name" \
-H "Authorization: Bearer <your_access_token>"7.25.5. getUserInformation
Get user information for the specified user.
GET /api/v1/users/{username}
Authorizations:
Path parameters
| Type | Name | Description | Schema |
|---|---|---|---|
| path |
username | string |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
| 200 | Successful invocation | |
| 400 | Bad Request | |
| 401 | Session required | |
| 403 | Unauthorized access | |
| 404 | Not found |
Example command
curl -X GET "https://quay-server.example.com/api/v1/users/example_user" \ -H "Authorization: Bearer <your_access_token>"
$ curl -X GET "https://quay-server.example.com/api/v1/users/example_user" \
-H "Authorization: Bearer <your_access_token>"7.26. Definitions
7.26.1. ApiError
| Name | Description | Schema |
|---|---|---|
|
status | Status code of the response. | integer |
|
type | Reference to the type of the error. | string |
|
detail | Details about the specific instance of the error. | string |
|
title | Unique error code to identify the type of error. | string |
|
error_message | Deprecated; alias for detail | string |
|
error_type | Deprecated; alias for detail | string |
7.26.2. UserView
| Name | Description | Schema |
|---|---|---|
|
verified | Whether the user’s email address has been verified | boolean |
|
anonymous | true if this user data represents a guest user | boolean |
|
email | The user’s email address | string |
|
avatar | Avatar data representing the user’s icon | object |
|
organizations | Information about the organizations in which the user is a member |
array of object |
|
logins | The list of external login providers against which the user has authenticated |
array of object |
|
can_create_repo | Whether the user has permission to create repositories | boolean |
|
preferred_namespace | If true, the user’s namespace is the preferred namespace to display | boolean |
7.26.3. ViewMirrorConfig
| Name | Description | Schema |
|---|---|---|
|
is_enabled | Used to enable or disable synchronizations. | boolean |
|
external_reference | Location of the external repository. | string |
|
external_registry_username | Username used to authenticate with external registry. | |
|
external_registry_password | Password used to authenticate with external registry. | |
|
sync_start_date | Determines the next time this repository is ready for synchronization. | string |
|
sync_interval | Number of seconds after next_start_date to begin synchronizing. | integer |
|
robot_username | Username of robot which will be used for image pushes. | string |
|
root_rule | A list of glob-patterns used to determine which tags should be synchronized. | object |
|
external_registry_config | object |
7.26.4. ApiErrorDescription
| Name | Description | Schema |
|---|---|---|
|
type | A reference to the error type resource | string |
|
title | The title of the error. Can be used to uniquely identify the kind of error. | string |
|
description | A more detailed description of the error that may include help for fixing the issue. | string |