Chapter 16. Red Hat Quay build enhancements
Prior to Red Hat Quay 3.7, Quay ran podman commands in virtual machines launched by pods. Running builds on virtual platforms requires enabling nested virtualization, which is not featured in Red Hat Enterprise Linux or OpenShift Container Platform. As a result, builds had to run on bare-metal clusters, which is an inefficient use of resources.
With Red Hat Quay 3.7., the bare-metal constraint required to run builds has been removed by adding an additional build option which does not contain the virtual machine layer. As a result, builds can be run on virtualized platforms. Backwards compatibility to run previous build configurations are also available.
16.1. Red Hat Quay enhanced build architecture
The preceding image shows the expected design flow and architecture of the enhanced build features:
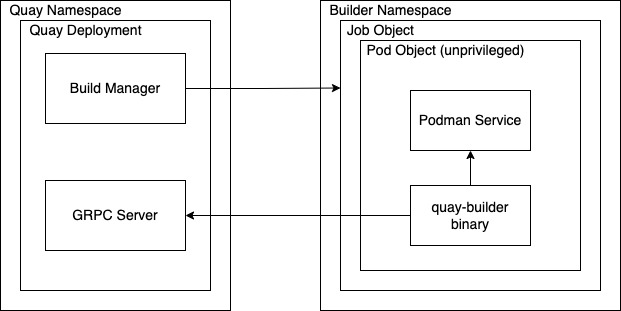
With this enhancement, the build manager first creates the Job Object. Then, the Job Object then creates a pod using the quay-builder-image. The quay-builder-image will contain the quay-builder binary and the Podman service. The created pod runs as unprivileged. The quay-builder binary then builds the image while communicating status and retrieving build information from the Build Manager.
16.2. Red Hat Quay build limitations
Running builds in Red Hat Quay in an unprivileged context might cause some commands that were working under the previous build strategy to fail. Attempts to change the build strategy could potentially cause performance issues and reliability with the build.
Running builds directly in a container will not have the same isolation as using virtual machines. Changing the build environment might also caused builds that were previously working to fail.
16.3. Creating a Red Hat Quay builders environment with OpenShift Container Platform
The procedures in this section explain how to create a Red Hat Quay virtual builders environment with OpenShift Container Platform.
16.3.1. OpenShift Container Platform TLS component
The tls component allows you to control TLS configuration.
Red Hat Quay 3.8 does not support builders when the TLS component is managed by the Operator.
If you set tls to unmanaged, you supply your own ssl.cert and ssl.key files. In this instance, if you want your cluster to support builders, you must add both the Quay route and the builder route name to the SAN list in the cert, or use a wildcard.
To add the builder route, use the following format:
[quayregistry-cr-name]-quay-builder-[ocp-namespace].[ocp-domain-name]:443
[quayregistry-cr-name]-quay-builder-[ocp-namespace].[ocp-domain-name]:44316.3.2. Using OpenShift Container Platform for Red Hat Quay builders
Builders require SSL/TLS certificates. For more information about SSL/TLS certificates, see Adding TLS certificates to the Red Hat Quay container.
If you are using Amazon Web Service (AWS) S3 storage, you must modify your storage bucket in the AWS console, prior to running builders. See "Modifying your AWS S3 storage bucket" in the following section for the required parameters.
16.3.2.1. Preparing OpenShift Container Platform for virtual builders
Use the following procedure to prepare OpenShift Container Platform for Red Hat Quay virtual builders.
- This procedure assumes you already have a cluster provisioned and a Quay Operator running.
- This procedure is for setting up a virtual namespace on OpenShift Container Platform.
Procedure
- Log in to your Red Hat Quay cluster using a cluster administrator account.
Create a new project where your virtual builders will be run, for example,
virtual-builders, by running the following command:oc new-project virtual-builders
$ oc new-project virtual-buildersCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
ServiceAccountin the project that will be used to run builds by entering the following command:oc create sa -n virtual-builders quay-builder
$ oc create sa -n virtual-builders quay-builderCopy to Clipboard Copied! Toggle word wrap Toggle overflow Provide the created service account with editing permissions so that it can run the build:
oc adm policy -n virtual-builders add-role-to-user edit system:serviceaccount:virtual-builders:quay-builder
$ oc adm policy -n virtual-builders add-role-to-user edit system:serviceaccount:virtual-builders:quay-builderCopy to Clipboard Copied! Toggle word wrap Toggle overflow Grant the Quay builder
anyuid sccpermissions by entering the following command:oc adm policy -n virtual-builders add-scc-to-user anyuid -z quay-builder
$ oc adm policy -n virtual-builders add-scc-to-user anyuid -z quay-builderCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThis action requires cluster admin privileges. This is required because builders must run as the Podman user for unprivileged or rootless builds to work.
Obtain the token for the Quay builder service account.
If using OpenShift Container Platform 4.10 or an earlier version, enter the following command:
oc sa get-token -n virtual-builders quay-builder
oc sa get-token -n virtual-builders quay-builderCopy to Clipboard Copied! Toggle word wrap Toggle overflow If using OpenShift Container Platform 4.11 or later, enter the following command:
oc create token quay-builder -n virtual-builders
$ oc create token quay-builder -n virtual-buildersCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
eyJhbGciOiJSUzI1NiIsImtpZCI6IldfQUJkaDVmb3ltTHZ0dGZMYjhIWnYxZTQzN2dJVEJxcDJscldSdEUtYWsifQ...
eyJhbGciOiJSUzI1NiIsImtpZCI6IldfQUJkaDVmb3ltTHZ0dGZMYjhIWnYxZTQzN2dJVEJxcDJscldSdEUtYWsifQ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Determine the builder route by entering the following command:
oc get route -n quay-enterprise
$ oc get route -n quay-enterpriseCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME HOST/PORT PATH SERVICES PORT TERMINATION WILDCARD ... example-registry-quay-builder example-registry-quay-builder-quay-enterprise.apps.docs.quayteam.org example-registry-quay-app grpc edge/Redirect None ...
NAME HOST/PORT PATH SERVICES PORT TERMINATION WILDCARD ... example-registry-quay-builder example-registry-quay-builder-quay-enterprise.apps.docs.quayteam.org example-registry-quay-app grpc edge/Redirect None ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Generate a self-signed SSL/TlS certificate with the .crt extension by entering the following command:
oc extract cm/kube-root-ca.crt -n openshift-apiserver
$ oc extract cm/kube-root-ca.crt -n openshift-apiserverCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
ca.crt
ca.crtCopy to Clipboard Copied! Toggle word wrap Toggle overflow Rename the
ca.crtfile toextra_ca_cert_build_cluster.crtby entering the following command:mv ca.crt extra_ca_cert_build_cluster.crt
$ mv ca.crt extra_ca_cert_build_cluster.crtCopy to Clipboard Copied! Toggle word wrap Toggle overflow Locate the secret for you configuration bundle in the Console, and select Actions
Edit Secret and add the appropriate builder configuration: Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The build route is obtained by running
oc get route -nwith the name of your OpenShift Operator’s namespace. A port must be provided at the end of the route, and it should use the following format:[quayregistry-cr-name]-quay-builder-[ocp-namespace].[ocp-domain-name]:443. - 2
- If the
JOB_REGISTRATION_TIMEOUTparameter is set too low, you might receive the following error:failed to register job to build manager: rpc error: code = Unauthenticated desc = Invalid build token: Signature has expired. It is suggested that this parameter be set to at least 240. - 3
- If your Redis host has a password or SSL/TLS certificates, you must update accordingly.
- 4
- Set to match the name of your virtual builders namespace, for example,
virtual-builders. - 5
- For early access, the
BUILDER_CONTAINER_IMAGEis currentlyquay.io/projectquay/quay-builder:3.7.0-rc.2. Note that this might change during the early access window. If this happens, customers are alerted. - 6
- The
K8S_API_SERVERis obtained by runningoc cluster-info. - 7
- You must manually create and add your custom CA cert, for example,
K8S_API_TLS_CA: /conf/stack/extra_ca_certs/build_cluster.crt. - 8
- Defaults to
5120Miif left unspecified. - 9
- For virtual builds, you must ensure that there are enough resources in your cluster. Defaults to
1000mif left unspecified. - 10
- Defaults to
3968Miif left unspecified. - 11
- Defaults to
500mif left unspecified. - 12
- Obtained when running
oc create sa.
Sample configuration
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
16.3.2.2. Manually adding SSL/TLS certificates
Due to a known issue with the configuration tool, you must manually add your custom SSL/TLS certificates to properly run builders. Use the following procedure to manually add custom SSL/TLS certificates.
For more information creating SSL/TLS certificates, see Adding TLS certificates to the Red Hat Quay container.
16.3.2.2.1. Creating and signing certificates
Use the following procedure to create and sign an SSL/TLS certificate.
Procedure
Create a certificate authority and sign a certificate. For more information, see Create a Certificate Authority and sign a certificate.
openssl.cnf
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Sample commands
openssl genrsa -out rootCA.key 2048 openssl req -x509 -new -nodes -key rootCA.key -sha256 -days 1024 -out rootCA.pem openssl genrsa -out ssl.key 2048 openssl req -new -key ssl.key -out ssl.csr openssl x509 -req -in ssl.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out ssl.cert -days 356 -extensions v3_req -extfile openssl.cnf
$ openssl genrsa -out rootCA.key 2048 $ openssl req -x509 -new -nodes -key rootCA.key -sha256 -days 1024 -out rootCA.pem $ openssl genrsa -out ssl.key 2048 $ openssl req -new -key ssl.key -out ssl.csr $ openssl x509 -req -in ssl.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out ssl.cert -days 356 -extensions v3_req -extfile openssl.cnfCopy to Clipboard Copied! Toggle word wrap Toggle overflow
16.3.2.2.2. Setting TLS to unmanaged
Use the following procedure to set king:tls to unmanaged.
Procedure
In your Red Hat Quay Registry YAML, set
kind: tlstomanaged: false:- kind: tls managed: false- kind: tls managed: falseCopy to Clipboard Copied! Toggle word wrap Toggle overflow On the Events page, the change is blocked until you set up the appropriate
config.yamlfile. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
16.3.2.2.3. Creating temporary secrets
Use the following procedure to create temporary secrets for the CA certificate.
Procedure
Create a secret in your default namespace for the CA certificate:
oc create secret generic -n quay-enterprise temp-crt --from-file extra_ca_cert_build_cluster.crt
$ oc create secret generic -n quay-enterprise temp-crt --from-file extra_ca_cert_build_cluster.crtCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a secret in your default namespace for the
ssl.keyandssl.certfiles:oc create secret generic -n quay-enterprise quay-config-ssl --from-file ssl.cert --from-file ssl.key
$ oc create secret generic -n quay-enterprise quay-config-ssl --from-file ssl.cert --from-file ssl.keyCopy to Clipboard Copied! Toggle word wrap Toggle overflow
16.3.2.2.4. Copying secret data to the configuration YAML
Use the following procedure to copy secret data to your config.yaml file.
Procedure
-
Locate the new secrets in the console UI at Workloads
Secrets. For each secret, locate the YAML view:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow Locate the secret for your Red Hat Quay registry configuration bundle in the UI, or through the command line by running a command like the following:
oc get quayregistries.quay.redhat.com -o jsonpath="{.items[0].spec.configBundleSecret}{'\n'}" -n quay-enterprise$ oc get quayregistries.quay.redhat.com -o jsonpath="{.items[0].spec.configBundleSecret}{'\n'}" -n quay-enterpriseCopy to Clipboard Copied! Toggle word wrap Toggle overflow In the OpenShift Container Platform console, select the YAML tab for your configuration bundle secret, and add the data from the two secrets you created:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Click Save.
Enter the following command to see if your pods are restarting:
oc get pods -n quay-enterprise
$ oc get pods -n quay-enterpriseCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow After your Red Hat Quay registry has reconfigured, enter the following command to check if the Red Hat Quay app pods are running:
oc get pods -n quay-enterprise
$ oc get pods -n quay-enterpriseCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In your browser, access the registry endpoint and validate that the certificate has been updated appropriately. For example:
Common Name (CN) example-registry-quay-quay-enterprise.apps.docs.quayteam.org Organisation (O) DOCS Organisational Unit (OU) QUAY
Common Name (CN) example-registry-quay-quay-enterprise.apps.docs.quayteam.org Organisation (O) DOCS Organisational Unit (OU) QUAYCopy to Clipboard Copied! Toggle word wrap Toggle overflow
16.3.2.3. Using the UI to create a build trigger
Use the following procedure to use the UI to create a build trigger.
Procedure
- Log in to your Red Hat Quay repository.
-
Click Create New Repository and create a new registry, for example,
testrepo. On the Repositories page, click the Builds tab on the navigation pane. Alternatively, use the corresponding URL directly:
https://example-registry-quay-quay-enterprise.apps.docs.quayteam.org/repository/quayadmin/testrepo?tab=builds
https://example-registry-quay-quay-enterprise.apps.docs.quayteam.org/repository/quayadmin/testrepo?tab=buildsCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIn some cases, the builder might have issues resolving hostnames. This issue might be related to the
dnsPolicybeing set todefaulton the job object. Currently, there is no workaround for this issue. It will be resolved in a future version of Red Hat Quay.-
Click Create Build Trigger
Custom Git Repository Push. Enter the HTTPS or SSH style URL used to clone your Git repository, then click Continue. For example:
https://github.com/gabriel-rh/actions_test.git
https://github.com/gabriel-rh/actions_test.gitCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Check Tag manifest with the branch or tag name and then click Continue.
-
Enter the location of the Dockerfile to build when the trigger is invoked, for example,
/Dockerfileand click Continue. -
Enter the location of the context for the Docker build, for example,
/, and click Continue. - If warranted, create a Robot Account. Otherwise, click Continue.
- Click Continue to verify the parameters.
- On the Builds page, click Options icon of your Trigger Name, and then click Run Trigger Now.
- Enter a commit SHA from the Git repository and click Start Build.
You can check the status of your build by clicking the commit in the Build History page, or by running
oc get pods -n virtual-builders. For example:oc get pods -n virtual-builders
$ oc get pods -n virtual-buildersCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME READY STATUS RESTARTS AGE f192fe4a-c802-4275-bcce-d2031e635126-9l2b5-25lg2 1/1 Running 0 7s
NAME READY STATUS RESTARTS AGE f192fe4a-c802-4275-bcce-d2031e635126-9l2b5-25lg2 1/1 Running 0 7sCopy to Clipboard Copied! Toggle word wrap Toggle overflow oc get pods -n virtual-builders
$ oc get pods -n virtual-buildersCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME READY STATUS RESTARTS AGE f192fe4a-c802-4275-bcce-d2031e635126-9l2b5-25lg2 1/1 Terminating 0 9s
NAME READY STATUS RESTARTS AGE f192fe4a-c802-4275-bcce-d2031e635126-9l2b5-25lg2 1/1 Terminating 0 9sCopy to Clipboard Copied! Toggle word wrap Toggle overflow oc get pods -n virtual-builders
$ oc get pods -n virtual-buildersCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
No resources found in virtual-builders namespace.
No resources found in virtual-builders namespace.Copy to Clipboard Copied! Toggle word wrap Toggle overflow When the build is finished, you can check the status of the tag under Tags on the navigation pane.
NoteWith early access, full build logs and timestamps of builds are currently unavailable.
16.3.2.4. Modifying your AWS S3 storage bucket
If you are using AWS S3 storage, you must change your storage bucket in the AWS console, prior to running builders.
Procedure
- Log in to your AWS console at s3.console.aws.com.
-
In the search bar, search for
S3and then click S3. -
Click the name of your bucket, for example,
myawsbucket. - Click the Permissions tab.
Under Cross-origin resource sharing (CORS), include the following parameters:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
16.3.2.5. Modifying your Google Cloud Platform object bucket
Use the following procedure to configure cross-origin resource sharing (CORS) for virtual builders.
Without CORS configuration, uploading a build Dockerfile fails.
Procedure
Use the following reference to create a JSON file for your specific CORS needs. For example:
cat gcp_cors.json
$ cat gcp_cors.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to update your GCP storage bucket:
gcloud storage buckets update gs://<bucket_name> --cors-file=./gcp_cors.json
$ gcloud storage buckets update gs://<bucket_name> --cors-file=./gcp_cors.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Updating Completed 1
Updating Completed 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can display the updated CORS configuration of your GCP bucket by running the following command:
gcloud storage buckets describe gs://<bucket_name> --format="default(cors)"
$ gcloud storage buckets describe gs://<bucket_name> --format="default(cors)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow