Este contenido no está disponible en el idioma seleccionado.
16.3. Renewing Subsystem Certificates
There are two methods of renewing a certificate. Regenerating the certificate takes its original key and its original profile and request, and recreates an identical key with a new validity period and expiration date. Re-keying a certificate resubmits the initial certificate request to the original profile, but generates a new key pair. Administrator certificates can be renewed by being re-keyed.
16.3.1. Re-keying Certificates in the End-Entities Forms
Copiar enlaceEnlace copiado en el portapapeles!
Subsystem certificates can be renewed directly in the end user enrollment forms, using the serial number of the original certificate.
- Renew the certificates in the CA's end-entities forms, as described in Section 5.5, “Renewing Certificates”. This requires the serial number of the subsystem certificate being renewed.
- Import the certificate into the subsystem's database, as described in Section 16.6.1, “Installing Certificates in the Certificate System Database”. The certificate can be imported using
certutilor the console. For example:certutil -A -n "ServerCert cert-example" -t u,u,u -d /var/lib/pki/instance_name/alias -a -i /tmp/example.cert
certutil -A -n "ServerCert cert-example" -t u,u,u -d /var/lib/pki/instance_name/alias -a -i /tmp/example.certCopy to Clipboard Copied! Toggle word wrap Toggle overflow
16.3.2. Renewing Certificates in the Console
Copiar enlaceEnlace copiado en el portapapeles!
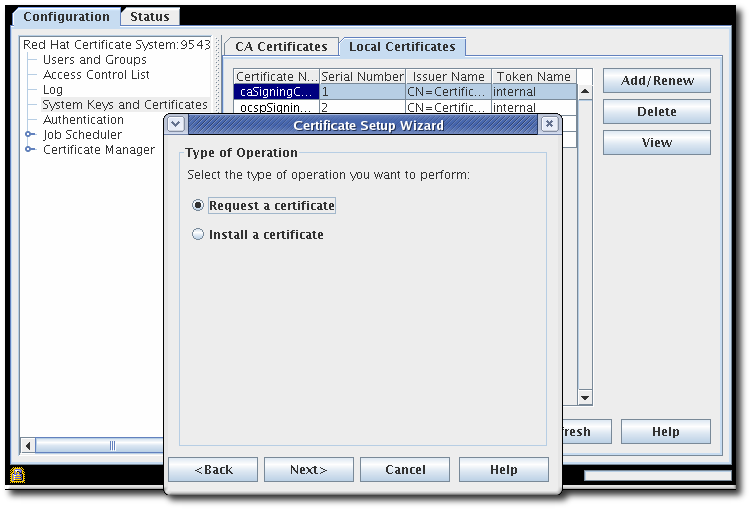
The Java subsystems can renew any of their subsystem certificates through their administrative console. The process is exactly the same as requesting new subsystem certificates (Section 16.2, “Requesting Certificates through the Console”), with one crucial difference: renewal uses an existing key pair rather than generating a new one.
Figure 16.1. Renewing Subsystem Certificate
After renewing a certificate, then delete the original certificate from the database (Section 16.6.3, “Deleting Certificates from the Database”).
16.3.3. Renewing Certificates Using certutil
Copiar enlaceEnlace copiado en el portapapeles!
certutil can be used to generate a certificate request using an existing key pair in the certificate database. The new certificate request can then be submitted through the regular profile pages for the CA to issue a renewed certificate.
Note
Encryption and signing certificates are created in a single step. However, the renewal process only renews one certificate at a time.
To renew both certificates in a certificate pair, each one has to be renewed individually.
- Get the password for the token database.
cat /var/lib/pki/instance_name/conf/password.conf internal=263163888660
cat /var/lib/pki/instance_name/conf/password.conf internal=263163888660Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Open the certificate database directory of the instance whose certificate is being renewed.
cd /var/lib/pki/instance_name/alias
cd /var/lib/pki/instance_name/aliasCopy to Clipboard Copied! Toggle word wrap Toggle overflow - List the key and nickname for the certificate being renewed. In order to renew a certificate, the key pairs used to generate and the subject name given to the new certificate must be the same as the one in the old certificate.
# certutil -K -d . certutil: Checking token "NSS Certificate DB" in slot "NSS User Private Key and Certificate Services" Enter Password or Pin for "NSS Certificate DB": < 0> rsa 69481646e38a6154dc105960aa24ccf61309d37d caSigningCert cert-pki-tomcat CA
# certutil -K -d . certutil: Checking token "NSS Certificate DB" in slot "NSS User Private Key and Certificate Services" Enter Password or Pin for "NSS Certificate DB": < 0> rsa 69481646e38a6154dc105960aa24ccf61309d37d caSigningCert cert-pki-tomcat CACopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the
aliasdirectory as a backup, then delete the original certificate from the certificate database. For example:certutil -D -n "ServerCert cert-example" -d .
certutil -D -n "ServerCert cert-example" -d .Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Run the
certutilcommand with the options set to the values in the existing certificate.certutil -d . -R -n "NSS Certificate DB:cert-pki-tomcat CA" -s "cn=CA Authority,o=Example Domain" -a -o example.req2.txt
certutil -d . -R -n "NSS Certificate DB:cert-pki-tomcat CA" -s "cn=CA Authority,o=Example Domain" -a -o example.req2.txtCopy to Clipboard Copied! Toggle word wrap Toggle overflow The difference between generating a new certificate and key pair and renewing the certificate is the value of the-noption. To generate an entirely new request and key pair, then-ksets the key type and is used with-g, which sets the bit length. For a renewal request, the-noption uses the certificate nickname to access the existing key pair stored in the security database.For further details about the parameters, see the certutil(1) man page. - Submit the certificate request and then retrieve it and install it, as described in Section 5.4, “Requesting and Receiving Certificates”.
16.3.4. Renewing System Certificates
Copiar enlaceEnlace copiado en el portapapeles!
Certificate System does not automatically renew system certificates online while the PKI server is running. However, if a system certificate expires, Certificate System will fail to start.
To renew system certificates:
- If the system certificate is expired:
- Create a temporary certificate:
pki-server cert-create sslserver --temp
# pki-server cert-create sslserver --tempCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Import the temporary certificate into Certificate System's Network Security Services (NSS) database:
pki-server cert-import sslserver
# pki-server cert-import sslserverCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Start Certificate System:
systemctl start pki-tomcatd@instance_name.service
# systemctl start pki-tomcatd@instance_name.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Display the certificates and note the ID of the expired system certificate:
pki-server cert-find
# pki-server cert-findCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Create the new permanent certificate:
pki-server cert-create certificate_ID
# pki-server cert-create certificate_IDCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Stop Certificate System:
systemctl stop pki-tomcatd@instance_name.service
# systemctl stop pki-tomcatd@instance_name.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Import the new certificate to replace the expired certificate:
pki-server cert-import certificate_ID
# pki-server cert-import certificate_IDCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Start Certificate System:
systemctl start pki-tomcatd@instance_name.service
# systemctl start pki-tomcatd@instance_name.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow