Este contenido no está disponible en el idioma seleccionado.
Chapter 16. Suspending applications
This guide explains how to disable all keys and access tokens for an application.
If an application is misusing your API and affecting other traffic, you may need to quickly suspend its operations before contacting the developer involved to ask them to amend their code or configuration.
16.1. Find the application
You can find the application from the Accounts or Applications tabs or by searching as described here.
16.2. Disable the application
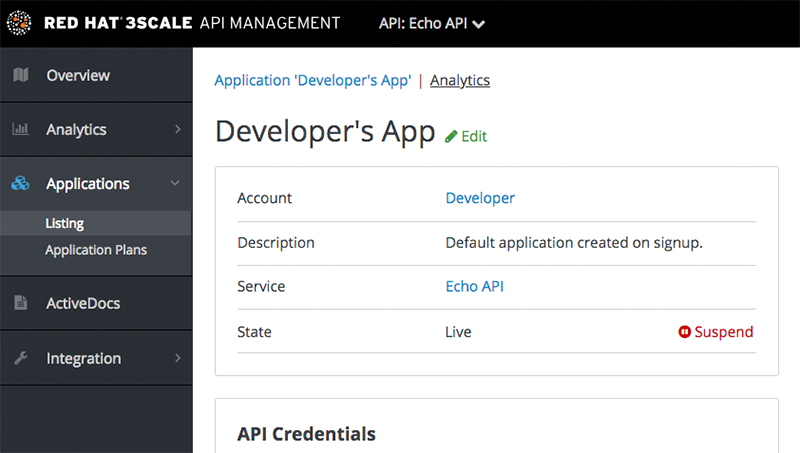
Once you have located the application and see the application summary page, click on the suspend icon next to the State value. This action will immediately disable the application from the API and suspend all keys from working. Calls with these application keys will be rejected by the control system.
The application can be unsuspended using the same button once the problematic behavior has been rectified.
If you use caching in your agents, suspension may not be immediate but require a short timeout.
16.3. Contact the developer
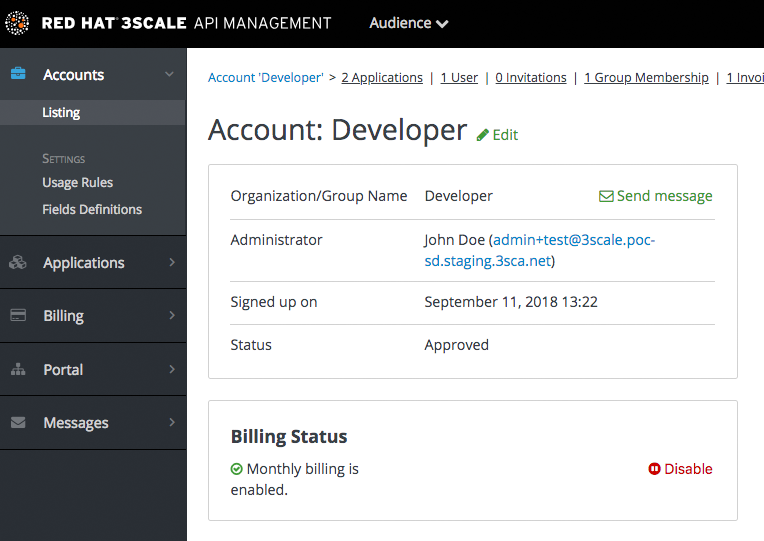
How you contact the developer of the application will depend on your workflow and policy. On the same page, you can click on the account name, which will take you to the account view where you can identify the key administrator of the account that owns the application. You can contact them either by email or by clicking on the send message button as shown, which will generate a dashboard message for the user.