Este contenido no está disponible en el idioma seleccionado.
Chapter 3. Installing Ansible development tools
You have two options for installing Ansible development tools, so that you can choose the installation method that best suits your preferred operating system and development environment.
Red Hat provides two options for installing Ansible development tools.
- Installation on a RHEL container running inside VS Code. You can install this option on MacOS, Windows, and Linux systems.
Installation on your local RHEL 8 or RHEL 9 system using an RPM (Red Hat Package Manager) package.
NoteRPM installation is not supported on RHEL 10.
3.1. Requirements
To install and use Ansible development tools, you must meet the following requirements. Extra requirements for Windows installations and containerized installations are indicated in the procedures.
- Python 3.10 or later.
- VS Code (Visual Studio Code) with the Ansible extension added. See Installing VS Code.
- For containerized installations, the Microsoft Dev Containers VS Code extension. See Installing and configuring the Dev Containers extension.
A containerization platform, for example Podman, Podman Desktop, Docker, or Docker Desktop.
NoteThe installation procedure for Ansible development tools on Windows covers the use of Podman Desktop only. See Requirements for Ansible development tools on Windows.
-
You have a Red Hat account and you can log in to the Red Hat container registry at
registry.redhat.io. For information about logging in toregistry.redhat.io, see Authenticating with the Red Hat container registry.
3.1.1. Requirements for Ansible development tools on Windows
If you are installing Ansible development tools on a container in VS Code on Windows, there are extra requirements:
- Windows Subsystem for Linux(WSL2)
- Podman Desktop
Procedure
Install WSL2 without a distribution:
wsl --install --no-distribution
$ wsl --install --no-distributionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use
cgroupsv2by disablingcgroupsv1for WSL2:Edit the
%USERPROFILE%/wsl.conffile and add the following lines to forcecgroupv2usage:[wsl2] kernelCommandLine = cgroup_no_v1="all"
[wsl2] kernelCommandLine = cgroup_no_v1="all"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Install Podman Desktop. Follow the instructions in Installing Podman Desktop and Podman on Windows in the Podman Desktop documentation.
You do not need to change the default settings in the set-up wizard.
Ensure the podman machine is using
cgroupsv2:podman info | findstr cgroup
$ podman info | findstr cgroupCopy to Clipboard Copied! Toggle word wrap Toggle overflow Test Podman Desktop:
podman run hello
$ podman run helloCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the settings for Podman Desktop. Add a
%USERPROFILE%\bin\docker.batfile with the following content:@echo off podman %*
@echo off podman %*Copy to Clipboard Copied! Toggle word wrap Toggle overflow This avoids having to install Docker as required by the VS Code
Dev Containerextension.Add the
%USERPROFILE%\bindirectory to thePATH:- Select Settings and search for "Edit environment variables for your account" to display all of the user environment variables.
- Highlight "Path" in the top user variables box, click and add the path.
- Click to set the path for any new console that you open.
3.1.2. Authenticating with the Red Hat container registry
All container images available through the Red Hat container catalog are hosted on an image registry, registry.redhat.io. The registry requires authentication for access to images.
If you are planning to install the Ansible development tools on a container inside VS Code, you must log in to registry.redhat.io before launching VS Code so that VS Code can pull the devtools container from registry.redhat.io.
If you are running Ansible development tools on a container inside VS Code and you want to pull execution environments or the devcontainer to use as an execution environment, you must log in from a terminal prompt within the devcontainer from a terminal inside VS Code.
Prerequisites
- You have a Red Hat login. It is the same account that you use to log in to the Red Hat Customer Portal (access.redhat.com) and manage your Red Hat subscriptions.
Procedure
Check whether you are already logged in to the
registry.redhat.ioregistry:podman login --get-login registry.redhat.io
$ podman login --get-login registry.redhat.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command output displays your Red Hat login if you are logged in to
registry.redhat.io.If you are not logged in to
registry.redhat.io, use thepodman logincommand with your credentials to access content on the registry.podman login registry.redhat.io Username: my_redhat_username Password: ***********
$ podman login registry.redhat.io Username: my_redhat_username Password: ***********Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.1.3. Installing VS Code
Install VS Code by following the instructions found on the Download Visual Studio Code page in the official documentation.
Procedure
- To install VS Code, follow the instructions on the Download Visual Studio Code page in the Visual Studio Code documentation.
3.1.4. Installing the VS Code Ansible extension
The Ansible extension adds language support for Ansible to VS Code. It incorporates Ansible development tools to facilitate creating and running automation content.
For a full description of the Ansible extension, see the Visual Studio Code Marketplace.
Procedure
- Open VS Code.
-
Click the Extensions (
 ) icon in the Activity Bar, or click
) icon in the Activity Bar, or click , to display the Extensions view. -
In the search field in the Extensions view, type
Ansible Red Hat. - Select the Ansible extension and click .
Verification
When the language for a file is recognized as Ansible, the Ansible extension provides features such as auto-completion, hover, diagnostics, and goto. The language identified for a file is displayed in the Status bar at the bottom of the VS Code window.
The following files are assigned the Ansible language:
-
YAML files in a
/playbooksdirectory -
Files with the following double extension:
.ansible.ymlor.ansible.yaml -
Certain YAML names recognized by Ansible, for example
site.ymlorsite.yaml -
YAML files whose filename contains "playbook":
playbook.ymlorplaybook.yaml
Troubleshooting
If the extension does not identify the language for your playbook files as Ansible, follow the procedure in Associating the Ansible language to YAML files.
3.1.5. Configuring Ansible extension settings
The Ansible extension supports multiple configuration options.
You can configure the settings for the extension on a user level, on a workspace level, or for a particular directory. User-based settings are applied globally for any instance of VS Code that is opened. A VS Code workspace is a collection of one or more folders that you can open in a single VS Code window. Workspace settings are stored within your workspace and only apply when the current workspace is opened.
It is useful to configure settings for your workspace for the following reasons:
- If you define and maintain configurations specific to your playbook project, you can customize your Ansible development environment for individual projects without altering your preferred setup for other work. You can have different settings for a Python project, an Ansible project, and a C++ project, each optimized for the respective stack without the need to manually reconfigure settings each time you switch projects.
- If you include workspace settings when setting up version control for a project you want to share with your team, everyone uses the same configuration for that project.
Prerequisites
-
Open a workspace or folder, or create a new folder, in VS Code using the
menu. This is necessary because the file that stores settings preferences for workspaces is specific to a folder or workspace.
Procedure
Open the Ansible extension settings:
-
Click the
 Extensions icon in the activity bar.
Extensions icon in the activity bar.
Select the Ansible extension, and click the 'gear' icon and then Extension Settings to display the extension settings.
-
Alternatively, click
to open the Settings page.
-
Alternatively, click
-
Enter
Ansiblein the search bar to display the settings for the extension.
-
Click the
Select the Workspace tab to configure your settings for the current VS Code workspace.
-
If the Workspace tab is not displayed, open a folder or create a new folder using the
menu.
-
If the Workspace tab is not displayed, open a folder or create a new folder using the
The Ansible extension settings are pre-populated. Modify the settings to suit your requirements:
-
Check the
box to enable ansible-lint. -
Check the
Ansible Execution Environment: Enabledbox to use an execution environment. - Specify the execution environment image you want to use in the Ansible > Execution Environment: image field.
- To use Red Hat Ansible Lightspeed, check the Ansible > Lightspeed: Enabled box, and enter the URL for Lightspeed.
-
Check the
3.1.6. Installing and configuring the Dev Containers extension
If you are installing the containerized version of Ansible development tools, you must install the Microsoft Dev Containers extension in VS Code.
Procedure
- Open VS Code.
-
Click the Extensions (
 ) icon in the Activity Bar, or click
) icon in the Activity Bar, or click , to display the Extensions view. -
In the search field in the Extensions view, type
Dev Containers. Select the Dev Containers extension from Microsoft and click .
If you are using Podman or Podman Desktop as your containerization platform, you must modify the default settings in the
Dev Containersextension.Replace docker with podman in the
Dev Containersextension settings:- In VS Code, open the settings editor.
Search for
@ext:ms-vscode-remote.remote-containers.Alternatively, click the Extensions icon in the activity bar and click the gear icon for the
Dev Containersextension.
-
Set
Dev > Containers:Docker Pathtopodman. -
Set
Dev > Containers:Docker Compose Pathtopodman-compose.
3.2. Installing Ansible development tools on a container inside VS Code
The Dev Containers VS Code extension requires a .devcontainer file to store settings for your dev containers. You must use the Ansible extension to scaffold a config file for your dev container, and reopen your directory in a container in VS Code.
Prerequisites
- You have installed a containerization platform, for example Podman, Podman Desktop, Docker, or Docker Desktop.
-
You have a Red Hat login and you have logged in to the Red Hat registry at
registry.redhat.io. For information about logging in toregistry.redhat.io, see Authenticating with the Red Hat container registry. - You have installed VS Code.
- You have installed the Ansible extension in VS Code.
- You have installed the Microsoft Dev Containers extension in VS Code.
-
If you are installing Ansible development tools on Windows, launch VS Code and connect to the WSL machine. Click the
Remote( ) icon. In the dropdown menu that appears, select the option to connect to the WSL machine.
) icon. In the dropdown menu that appears, select the option to connect to the WSL machine.
Procedure
- In VS Code, navigate to your project directory.
- Click the Ansible icon in the VS Code activity bar to open the Ansible extension.
- In the Ansible Development Tools section of the Ansible extension, scroll down to the ADD option and select Devcontainer.
In the Create a devcontainer page, select the Downstream container image from the Container image options.
This action adds
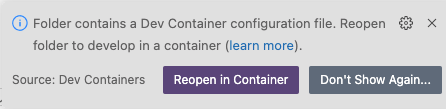
devcontainer.jsonfiles for both Podman and Docker in a.devcontainerdirectory.Reopen or reload the project directory:
If VS Code detects that your directory contains a
devcontainer.jsonfile, the following notification appears:Click Reopen in Container.
-
If the notification does not appear, click the
Remote( ) icon. In the dropdown menu that appears, select Reopen in Container.
) icon. In the dropdown menu that appears, select Reopen in Container.
Select the dev container for Podman or Docker according to the containerization platform you are using.
The Remote () status in the VS Code Status bar displays
opening Remoteand a notification indicates the progress in opening the container.
Verification
When the directory reopens in a container, the Remote () status displays Dev Container: ansible-dev-container.
The base image for the container is a Universal Base Image Minimal (UBI Minimal) image that uses microdnf as a package manager. The dnf and yum package managers are not available in the container.
For information about using microdnf in containers based on UBI Minimal images, see Adding software in a minimal UBI container in the Red Hat Enterprise Linux Building, running, and managing containers guide.
3.3. Installing Ansible development tools from a package on RHEL
Ansible development tools are bundled in the Ansible Automation Platform RPM (Red Hat Package Manager) package. Refer to the RPM installation documentation for information on installing Ansible Automation Platform.
Prerequisites
You have installed RHEL 8 or RHEL 9.
NoteRPM installation is not supported on RHEL 10.
- You have registered your system with Red Hat Subscription Manager.
- You have installed a containerization platform, for example Podman or Docker.
Procedure
Run the following command to check whether Simple Content Access (SCA) is enabled:
sudo subscription-manager status
$ sudo subscription-manager statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow If Simple Content Access is enabled, the output contains the following message:
Content Access Mode is set to Simple Content Access.
Content Access Mode is set to Simple Content Access.Copy to Clipboard Copied! Toggle word wrap Toggle overflow If Simple Content Access is not enabled, attach the Red Hat Ansible Automation Platform SKU:
sudo subscription-manager attach --pool=<sku-pool-id>
$ sudo subscription-manager attach --pool=<sku-pool-id>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Install Ansible development tools with the following command:
sudo dnf install --enablerepo=ansible-automation-platform-2.6-for-rhel-8-x86_64-rpms ansible-dev-tools
$ sudo dnf install --enablerepo=ansible-automation-platform-2.6-for-rhel-8-x86_64-rpms ansible-dev-toolsCopy to Clipboard Copied! Toggle word wrap Toggle overflow sudo dnf install --enablerepo=ansible-automation-platform-2.6-for-rhel-9-x86_64-rpms ansible-dev-tools
$ sudo dnf install --enablerepo=ansible-automation-platform-2.6-for-rhel-9-x86_64-rpms ansible-dev-toolsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the Ansible development tools components have been installed:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow On successful installation, you can view the help documentation for the
ansible-creatorutility:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.4. MCP server integration
An MCP server implements Model Context Protocol (MCP) for a specific backend such as REST API, various services, databases, and other external systems. The MCP server then exposes its operations as discoverable tools that AI agents or large language models (LLMs) can call.
MCP servers are integrated into Execution Environments (EEs) using a robust Ansible plugin framework. This setup allows Ansible playbooks to call MCP servers directly. A crucial design strategy is the ephemeral nature of these servers, meaning they exist only for the duration of the job execution.
The core requirement for enabling MCP support involves securely installing the required MCP server software into the Execution Environment during the build process, typically using the ansible-builder command.
You can configure MCP servers in two ways:
- For embedded (local) MCP servers: The EE image must explicitly include the MCP server binaries or libraries installed on the image path. This setup enables the Execution Environment to discover and start the specific embedded server required for the job.
For remote (external) MCP servers: The EE build process facilitates defining remote connection details in a manifest file contained within the EE. This manifest informs the core MCP collection plugin on how to connect, typically pointing to a specific remote URL using an HTTP connection.
- Supported MCP servers
To use MCP servers, you must specify the required MCP support information in your EE definitions. This configuration pulls the necessary dependencies into your EE YAML file. The following MCP servers are currently targeted for support:
- AWS Core MCP: Serves as a starting point for working across Amazon MCPs
- AWS Cloud Control API MCP: Provides the execution layer for AWS resource management
- GitHub MCP: Used for testing and validation, often targeting remote server connections
- Dependencies
- Dependencies are incorporated into the EE YAML when you create the definition files. For example, the demonstration jobs target scenarios like AWS EC2 and VPC management, GitHub repository, and Pull Request operations.
3.5. Implementing automation content for ephemeral MCP agents
You can create an Ansible playbook leveraging the Execution Environment (EE) setup so that ephemeral MCP servers are provisioned during Ansible Automation Platform (AAP) controller job creation. This way you can safely use AI as an operational assistant, which can take assigned actions in your enterprise platform.
Prerequisites
- You must securely store all access credentials necessary for MCP plugin use exclusively within AAP credential store.
- The Execution Environment (EE) image must be configured to include the necessary MCP server component, which is typically accomplished by selecting a collection with specialized roles during the EE build process.
Procedure
Create the
execution-environment.ymldefinition file, which specifies a step to install the MCP server components:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The example definition file above specifies the required MCP server, so that the necessary dependencies are pulled into the file.
During the EE build process the MCP server software is installed into the EE.
For embedded servers, include the MCP server binaries or libraries explicitly on the EE image path.
For remote servers, define remote connection details in a manifest file within the EE.
Write custom Ansible content:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The playbook syntax for invoking MCP plugins is intuitive and aligns with existing Ansible module patterns.
ImportantYou must configure the
ansible.mcp.mcpconnection plugin to use theansible.mcpcollection. For example, you should set theansible_mcp_server_namecustom-defined configuration variable to the name of a server in themcpserver.jsonmanifest file. Your playbook might use inventory variables, such as setting the connection plugin toansible_connection: ansible.mcp.mcp, along with required timeout values likeansible_connect_timeout: 30andansible_command_timeout: 30.Create and configure credentials in AAP:
The required credentials vary based on which MCP server you are using. For example, the Github MCP server requires a Github Personal Access Token, which should be set in the
MCP_BEARER_TOKENenvironment variable.To do this, first create a custom credential type in AAP:
Create a new credential and use the custom credential type you just created:
The examples above show how to set up the required credential structures in the AAP credential store. This includes defining the relevant fields and the injector configuration needed to pass the secret as an environment variable (for example,
MCP_BEARER_TOKEN: “{{ token }}”).
Create a new host and configure the connection variables:
- Launch the relevant job in the AAP controller GUI.
Troubleshooting
To manage the health of the MCP servers, the AAP environment emphasizes governance and auditability, allowing you to trace workflow success and failures.
All MCP plugin invocations and credential usage events are logged and auditable through AAP audit trail systems, including the job ID, user, and timestamp, along with Ansible eventstream data. This tracking supports governance requirements for enterprise compliance.
The system ensures that secrets are never hardcoded into playbooks or visible in execution logs; they are masked automatically. This robust auditing assists in identifying security issues or operational problems during task execution.
A successful operation relies on the strict, controlled lifecycle of the MCP agents. This ensures that upon job failure or completion, there are no residual data, services, or security artifacts remaining.