Este contenido no está disponible en el idioma seleccionado.
Chapter 22. Red Hat JBoss Data Grid Security: Authorization and Authentication
22.1. Red Hat JBoss Data Grid Security: Authorization and Authentication
Red Hat JBoss Data Grid is able to perform authorization on CacheManagers and Caches. JBoss Data Grid authorization is built on standard security features available in a JDK, such as JAAS and the SecurityManager.
If an application attempts to interact with a secured CacheManager and Cache, it must provide an identity which JBoss Data Grid’s security layer can validate against a set of required roles and permissions. Once validated, the client is issued a token for subsequent operations. Where access is denied, an exception indicating a security violation is thrown.
When a cache has been configured for with authorization, retrieving it returns an instance of SecureCache. SecureCache is a simple wrapper around a cache, which checks whether the "current user" has the permissions required to perform an operation. The "current user" is a Subject associated with the AccessControlContext.
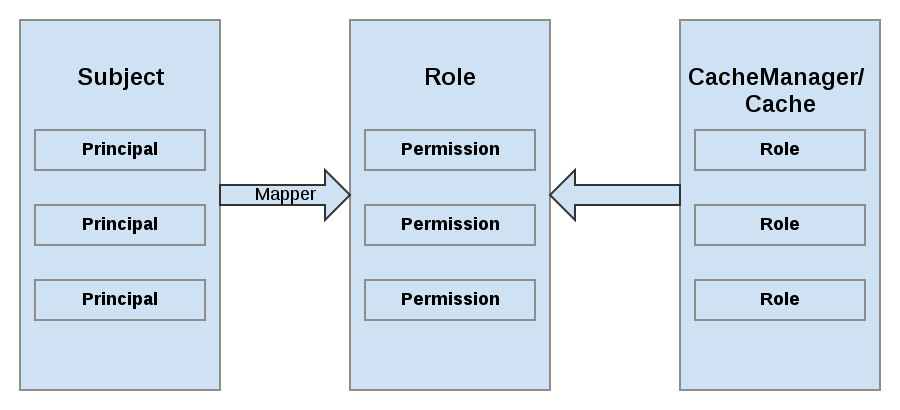
JBoss Data Grid maps Principals names to roles, which in turn, represent one or more permissions. The following diagram represents these relationships:
Figure 22.1. Roles and Permissions Mapping
22.2. Permissions
Access to a CacheManager or a Cache is controlled using a set of required permissions. Permissions control the type of action that is performed on the CacheManager or Cache, rather than the type of data being manipulated. Some of these permissions can apply to specifically name entities, such as a named cache. Different types of permissions are available depending on the entity.
| Permission | Function | Description |
|---|---|---|
| CONFIGURATION | defineConfiguration | Whether a new cache configuration can be defined. |
| LISTEN | addListener | Whether listeners can be registered against a cache manager. |
| LIFECYCLE | stop, start | Whether the cache manager can be stopped or started respectively. |
| ALL | A convenience permission which includes all of the above. |
| Permission | Function | Description |
|---|---|---|
| READ | get, contains | Whether entries can be retrieved from the cache. |
| WRITE | put, putIfAbsent, replace, remove, evict | Whether data can be written/replaced/removed/evicted from the cache. |
| EXEC | distexec, mapreduce | Whether code execution can be run against the cache. |
| LISTEN | addListener | Whether listeners can be registered against a cache. |
| BULK_READ | keySet, values, entrySet,query | Whether bulk retrieve operations can be executed. |
| BULK_WRITE | clear, putAll | Whether bulk write operations can be executed. |
| LIFECYCLE | start, stop | Whether a cache can be started / stopped. |
| ADMIN | getVersion, addInterceptor*, removeInterceptor, getInterceptorChain, getEvictionManager, getComponentRegistry, getDistributionManager, getAuthorizationManager, evict, getRpcManager, getCacheConfiguration, getCacheManager, getInvocationContextContainer, setAvailability, getDataContainer, getStats, getXAResource | Whether access to the underlying components/internal structures is allowed. |
| ALL | A convenience permission which includes all of the above. | |
| ALL_READ | Combines READ and BULK_READ. | |
| ALL_WRITE | Combines WRITE and BULK_WRITE. |
Some permissions may need to be combined with others in order to be useful. For example, EXEC with READ or with WRITE.
22.3. Role Mapping
In order to convert the Principals in a Subject into a set of roles used for authorization, a PrincipalRoleMapper must be specified in the global configuration. Red Hat JBoss Data Grid ships with three mappers, and also allows you to provide a custom mapper.
| Mapper Name | Java | XML | Description |
|---|---|---|---|
| IdentityRoleMapper | org.infinispan.security.impl.IdentityRoleMapper | <identity-role-mapper /> | Uses the Principal name as the role name. |
| CommonNameRoleMapper | org.infinispan.security.impl.CommonRoleMapper | <common-name-role-mapper /> |
If the Principal name is a Distinguished Name (DN), this mapper extracts the Common Name (CN) and uses it as a role name. For example the DN |
| ClusterRoleMapper | org.infinispan.security.impl.ClusterRoleMapper | <cluster-role-mapper /> |
Uses the |
| Custom Role Mapper | <custom-role-mapper class="a.b.c" /> |
Supply the fully-qualified class name of an implementation of |
22.4. Configuring Authentication and Role Mapping using Login Modules
When using the authentication login-module for querying roles from LDAP, you must implement your own mapping of Principals to Roles, as custom classes are in use. The following example demonstrates how to map a principal obtained from a login-module to a role. It maps user principal name to a role, performing a similar action to the IdentityRoleMapper:
Mapping a Principal
For information on configuring an LDAP server, or specifying users and roles in an LDAP server, refer to the Red Hat Directory Server Administration Guide .
22.5. Configuring Red Hat JBoss Data Grid for Authorization
Authorization is configured at two levels: the cache container (CacheManager), and at the single cache.
Each cache container determines:
- whether to use authorization.
- a class which will map principals to a set of roles.
- a set of named roles and the permissions they represent.
You can choose to use only a subset of the roles defined at the container level.
Roles
Roles may be applied on a cache-per-cache basis, using the roles defined at the cache-container level, as follows:
Any cache that is intended to require authentication must have a listing of roles defined; otherwise authentication is not enforced as the no-anonymous policy is defined by the cache’s authorization.
Programmatic CacheManager Authorization (Library Mode)
The following example shows how to set up the same authorization parameters for Library mode using programmatic configuration:
CacheManager Authorization Programmatic Configuration
The REST protocol is not supported for use with authorization, and any attempts to access a cache with authorization enabled will result in a SecurityException.
22.6. Data Security for Library Mode
22.6.1. Subject and Principal Classes
To authorize access to resources, applications must first authenticate the request’s source. The JAAS framework defines the term subject to represent a request’s source. The Subject class is the central class in JAAS. A Subject represents information for a single entity, such as a person or service. It encompasses the entity’s principals, public credentials, and private credentials. The JAAS APIs use the existing Java 2 java.security.Principal interface to represent a principal, which is a typed name.
During the authentication process, a subject is populated with associated identities, or principals. A subject may have many principals. For example, a person may have a name principal (John Doe), a social security number principal (123-45-6789), and a user name principal (johnd), all of which help distinguish the subject from other subjects. To retrieve the principals associated with a subject, two methods are available:
public Set getPrincipals() {...}
public Set getPrincipals(Class c) {...}
public Set getPrincipals() {...}
public Set getPrincipals(Class c) {...}
getPrincipals() returns all principals contained in the subject. getPrincipals(Class c) returns only those principals that are instances of class c or one of its subclasses. An empty set is returned if the subject has no matching principals.
The java.security.acl.Group interface is a sub-interface of java.security.Principal, so an instance in the principals set may represent a logical grouping of other principals or groups of principals.
22.6.2. Obtaining a Subject
In order to use a secured cache in Library mode, you must obtain a javax.security.auth.Subject. The Subject represents information for a single cache entity, such as a person or a service.
Red Hat JBoss Data Grid allows a JAAS Subject to be obtained either by using your container’s features, or by using a third-party library.
In JBoss containers, this can be done using the following:
Subject subject = SecurityContextAssociation.getSubject();
Subject subject = SecurityContextAssociation.getSubject();The Subject must be populated with a set of Principals, which represent the user and groups it belongs to in your security domain, for example, an LDAP or Active Directory.
The Java EE API allows retrieval of a container-set Principal through the following methods:
-
Servlets:
ServletRequest.getUserPrincipal() -
EJBs:
EJBContext.getCallerPrincipal() -
MessageDrivenBeans:
MessageDrivenContext.getCallerPrincipal()
The mapper is then used to identify the principals associated with the Subject and convert them into roles that correspond to those you have defined at the container level.
A Principal is only one of the components of a Subject, which is retrieved from the java.security.AccessControlContext. Either the container sets the Subject on the AccessControlContext, or the user must map the Principal to an appropriate Subject before wrapping the call to the JBoss Data Grid API using a Security.doAs() method.
Once a Subject has been obtained, the cache can be interacted with in the context of a PrivilegedAction.
Obtaining a Subject
The Security.doAs() method is in place of the typical Subject.doAs() method. Unless the AccessControlContext must be modified for reasons specific to your application’s security model, using Security.doAs() provides a performance advantage.
To obtain the current Subject, use Security.getSubject();, which will retrieve the Subject from either the JBoss Data Grid context, or from the AccessControlContext.
22.6.3. Subject Authentication
Subject Authentication requires a JAAS login. The login process consists of the following points:
-
An application instantiates a
LoginContextand passes in the name of the login configuration and aCallbackHandlerto populate theCallbackobjects, as required by the configurationLoginModules. -
The
LoginContextconsults aConfigurationto load all theLoginModulesincluded in the named login configuration. If no such named configuration exists theotherconfiguration is used as a default. -
The application invokes the
LoginContext.loginmethod. -
The login method invokes all the loaded
LoginModules. As eachLoginModuleattempts to authenticate the subject, it invokes the handle method on the associatedCallbackHandlerto obtain the information required for the authentication process. The required information is passed to the handle method in the form of an array ofCallbackobjects. Upon success, theLoginModules associate relevant principals and credentials with the subject. -
The
LoginContextreturns the authentication status to the application. Success is represented by a return from the login method. Failure is represented through a LoginException being thrown by the login method. -
If authentication succeeds, the application retrieves the authenticated subject using the
LoginContext.getSubjectmethod. -
After the scope of the subject authentication is complete, all principals and related information associated with the subject by the
loginmethod can be removed by invoking theLoginContext.logoutmethod.
The LoginContext class provides the basic methods for authenticating subjects and offers a way to develop an application that is independent of the underlying authentication technology. The LoginContext consults a Configuration to determine the authentication services configured for a particular application. LoginModule classes represent the authentication services. Therefore, you can plug different login modules into an application without changing the application itself. The following code shows the steps required by an application to authenticate a subject.
Developers integrate with an authentication technology by creating an implementation of the LoginModule interface. This allows an administrator to plug different authentication technologies into an application. You can chain together multiple LoginModules to allow for more than one authentication technology to participate in the authentication process. For example, one LoginModule may perform user name/password-based authentication, while another may interface to hardware devices such as smart card readers or biometric authenticators.
The life cycle of a LoginModule is driven by the LoginContext object against which the client creates and issues the login method. The process consists of two phases. The steps of the process are as follows:
-
The
LoginContextcreates each configuredLoginModuleusing its public no-arg constructor. -
Each
LoginModuleis initialized with a call to its initialize method. TheSubjectargument is guaranteed to be non-null. The signature of the initialize method is:public void initialize(Subject subject, CallbackHandler callbackHandler, Map sharedState, Map options) -
The
loginmethod is called to start the authentication process. For example, a method implementation might prompt the user for a user name and password and then verify the information against data stored in a naming service such as NIS or LDAP. Alternative implementations might interface to smart cards and biometric devices, or simply extract user information from the underlying operating system. The validation of user identity by eachLoginModuleis considered phase 1 of JAAS authentication. The signature of theloginmethod isboolean login() throws LoginException. ALoginExceptionindicates failure. A return value of true indicates that the method succeeded, whereas a return value of false indicates that the login module should be ignored. -
If the
LoginContext's overall authentication succeeds,commitis invoked on eachLoginModule. If phase 1 succeeds for aLoginModule, then the commit method continues with phase 2 and associates the relevant principals, public credentials, and/or private credentials with the subject. If phase 1 fails for aLoginModule, thencommitremoves any previously stored authentication state, such as user names or passwords. The signature of thecommitmethod is:boolean commit() throws LoginException. Failure to complete the commit phase is indicated by throwing aLoginException. A return of true indicates that the method succeeded, whereas a return of false indicates that the login module should be ignored. -
If the
LoginContext's overall authentication fails, then theabortmethod is invoked on eachLoginModule. Theabortmethod removes or destroys any authentication state created by the login or initialize methods. The signature of theabortmethod isboolean abort() throws LoginException. Failure to complete theabortphase is indicated by throwing aLoginException. A return of true indicates that the method succeeded, whereas a return of false indicates that the login module should be ignored. -
To remove the authentication state after a successful login, the application invokes
logouton theLoginContext. This in turn results in alogoutmethod invocation on eachLoginModule. Thelogoutmethod removes the principals and credentials originally associated with the subject during thecommitoperation. Credentials should be destroyed upon removal. The signature of thelogoutmethod is:boolean logout() throws LoginException. Failure to complete the logout process is indicated by throwing aLoginException. A return of true indicates that the method succeeded, whereas a return of false indicates that the login module should be ignored.
When a LoginModule must communicate with the user to obtain authentication information, it uses a CallbackHandler object. Applications implement the interface and pass it to the LoginContext, which send the authentication information directly to the underlying login modules.
Login modules use the CallbackHandler both to gather input from users, such as a password or smart card PIN, and to supply information to users, such as status information. By allowing the application to specify the CallbackHandler, underlying LoginModules remain independent from the different ways applications interact with users. For example, a CallbackHandler's implementation for a GUI application might display a window to solicit user input. On the other hand, a CallbackHandler implementation for a non-GUI environment, such as an application server, might simply obtain credential information by using an application server API. The interface has one method to implement:
void handle(Callback[] callbacks)
throws java.io.IOException,
UnsupportedCallbackException;
void handle(Callback[] callbacks)
throws java.io.IOException,
UnsupportedCallbackException;
The Callback interface is the last authentication class we will look at. This is a tagging interface for which several default implementations are provided, including the NameCallback and PasswordCallback used in an earlier example. A LoginModule uses a Callback to request information required by the authentication mechanism. LoginModules pass an array of Callbacks directly to the CallbackHandler.handle method during the authentication’s login phase. If a callbackhandler does not understand how to use a Callback object passed into the handle method, it throws an UnsupportedCallbackException to abort the login call.
22.7. Securing Interfaces
22.7.1. Securing Interfaces
While the Hot Rod interface may be secured programmatically, both the memcached and REST interfaces must be secured declaratively. Instructions for securing these interfaces are located in the JBoss Data Grid Administration and Configuration Guide .
22.7.2. Hot Rod Interface Security
22.7.2.1. Encryption of communication between Hot Rod Server and Hot Rod client
Hot Rod can be encrypted using TLS/SSL, and has the option to require certificate-based client authentication.
Use the following procedure to secure the Hot Rod connector using SSL.
Secure Hot Rod Using SSL/TLS
To prevent plain text passwords from appearing in configurations or source codes, plain text passwords should be changed to Vault passwords. For more information about how to set up Vault passwords, see the Password Vault section of the JBoss Enterprise Application Platform security documentation. .
22.7.2.2. Securing Hot Rod to LDAP Server using SSL
When connecting to an LDAP server with SSL enabled it may be necessary to specify a trust store or key store containing the appropriate certificates.
PLAIN authentication over SSL may be used for Hot Rod client authentication against an LDAP server. The Hot Rod client sends plain text credentials to the JBoss Data Grid server over SSL, and the server subsequently verifies the provided credentials against the specified LDAP server. In addition, a secure connection must be configured between the JBoss Data Grid server and the LDAP server. Refer to the JBoss Data Grid Administration and Configuration Guide for additional information on configuring the server to communicate to an LDAP backend. The example below demonstrates configuring PLAIN authentication over SSL on the Hot Rod client side:
Hot Rod Client Authentication to LDAP Server
To prevent plain text passwords from appearing in configurations or source codes, plain text passwords should be changed to Vault passwords. For more information about how to set up Vault passwords, see the Red Hat Enterprise Application Platform Security Guide .
22.7.2.3. User Authentication over Hot Rod Using SASL
22.7.2.3.1. User Authentication over Hot Rod Using SASL
User authentication over Hot Rod can be implemented using the following Simple Authentication and Security Layer (SASL) mechanisms:
-
PLAINis the least secure mechanism because credentials are transported in plain text format. However, it is also the simplest mechanism to implement. This mechanism can be used in conjunction with encryption (SSL) for additional security. -
DIGEST-MD5is a mechanism than hashes the credentials before transporting them. As a result, it is more secure than thePLAINmechanism. -
GSSAPIis a mechanism that uses Kerberos tickets. As a result, it requires a correctly configured Kerberos Domain Controller (for example, Microsoft Active Directory). -
EXTERNALis a mechanism that obtains the required credentials from the underlying transport (for example, from aX.509client certificate) and therefore requires client certificate encryption to work correctly.
22.7.2.3.2. Configure Hot Rod Authentication (GSSAPI/Kerberos)
Use the following steps to set up Hot Rod Authentication using the SASL GSSAPI/Kerberos mechanism:
Configure SASL GSSAPI/Kerberos Authentication - Client-side Configuration
- Ensure that the Server-Side configuration has been completed. As this is configured declaratively this configuration is found in the JBoss Data Grid Administration and Configuration Guide .
Define a login module in a login configuration file (gss.conf ) on the client side:
[source],options="nowrap"
GssExample {
com.sun.security.auth.module.Krb5LoginModule required client=TRUE;
};
GssExample {
com.sun.security.auth.module.Krb5LoginModule required client=TRUE;
};Set up the following system properties:
java.security.auth.login.config=gss.conf java.security.krb5.conf=/etc/krb5.conf
java.security.auth.login.config=gss.conf java.security.krb5.conf=/etc/krb5.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe krb5.conf file is dependent on the environment and must point to the Kerberos Key Distribution Center.
Implement the
CallbackHandler:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the Hot Rod Client, as seen in the below snippet:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
22.7.2.3.3. Configure Hot Rod Authentication (MD5)
Use the following steps to set up Hot Rod Authentication using the SASL using the MD5 mechanism:
- Ensure that the server has been configured for MD5 Authentication. Instructions for performing this configuration on the server are found in JBoss Data Grid’s Administration and Configuration Guide .
Implement the
CallbackHandler:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Connect the client to the configured Hot Rod connector as seen below:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
22.7.3. Hot Rod C++ Client Encryption
By default all communication with the remote server is unencrypted; however, TLS encryption may be enabled by defining the server’s key via the serverCAFile method on the SslConfigurationBuilder. Additionally, the client’s certificate may be defined with the clientCertificateFile, allowing for client authentication.
The following example demonstrates defining a server key with an optional client certificate:
Hot Rod C++ TLS Example
The client may also indicate which hostname it is attempting to connect to at the start of the TLS/SNI handshaking process by providing a value to the sniHostName function. For instance, the following could be used:
[...]
builder.ssl().enable().serverCAFile(argv[1]).sniHostName("sni");
[...]
[...]
builder.ssl().enable().serverCAFile(argv[1]).sniHostName("sni");
[...]22.7.4. Hot Rod C# Client Encryption
By default all communication with the remote server is unencrypted; however, TLS encryption may be enabled by defining the server’s key via the ServerCAFile method on the SslConfigurationBuilder. Additionally, the client’s certificate may be defined with the ClientCertificateFile, allowing for client authentication.
The following example demonstrates defining a server key with an optional client certificate:
Hot Rod C# TLS Example
The client may also indicate which hostname it is attempting to connect to at the start of the TLS/SNI handshaking process by providing a value to SniHostName. For instance, the following call could be included immediately after defining the ServerCAFile:
[...]
sslConfB.ServerCAFile("resources/infinispan-ca.pem").SniHostName("sni");
[...]
[...]
sslConfB.ServerCAFile("resources/infinispan-ca.pem").SniHostName("sni");
[...]22.7.5. Hot Rod Node.js Encryption
The Node.js client supports encryption via SSL/TLS with optional TLS/SNI support. To configure this on the client it is necessary to create a Java KeyStore (JKS) using the keytool application included in the JDK. The created keystore must contain the keys and certificates necessary for the JBoss Data Grid server to authorize connections, and the JBoss Data Grid server must be configured for encryption. For details on configuring the server for encryption, refer to the JBoss Data Grid Administration and Configuration Guide.
The Node.js client implementation of TLS/SSL does not allow self-signed certificates. It is recommended to either configure a local Certificate Authority to sign certificates, or to use a free, open Certificate Authority, if certificates were previously self-signed.
By defining the location of a trusted certificate the client connection may be authorized by the server:
In addition, the client may also read trusted certificates from PKCS#12 or PFX format key stores:
In addition, the client may be configured with encrypted authentication. To configure authentication it is necessary to provide the location of the private key, the passphrase, and the certificate key of the client:
The client may also indicate which hostname it is attempting to connect to at the start of the TLS/SNI handshaking process by including the sniHostName directive:
If no sniHostName is provided then the client will send localhost as the SNI parameter. If the server’s default realm does not match localhost an error will be thrown.
22.8. The Security Audit Logger
22.8.1. The Security Audit Logger
Red Hat JBoss Data Grid includes a logger to audit security logs for the cache, specifically whether a cache or a cache manager operation was allowed or denied for various operations.
The default audit logger is org.infinispan.security.impl.DefaultAuditLogger. This logger outputs audit logs using the available logging framework (for example, JBoss Logging) and provides results at the TRACE level and the AUDIT category.
To send the AUDIT category to either a log file, a JMS queue, or a database, use the appropriate log appender.
22.8.2. Configure the Security Audit Logger (Library Mode)
Use the following to configure the audit logger in Red Hat JBoss Data Grid:
GlobalConfigurationBuilder global = new GlobalConfigurationBuilder();
global.security()
.authorization()
.auditLogger(new DefaultAuditLogger());
GlobalConfigurationBuilder global = new GlobalConfigurationBuilder();
global.security()
.authorization()
.auditLogger(new DefaultAuditLogger());22.8.3. Custom Audit Loggers
Users can implement custom audit loggers in Red Hat JBoss Data Grid Library and Remote Client-Server Mode. The custom logger must implement the org.infinispan.security.AuditLogger interface. If no custom logger is provided, the default logger (DefaultAuditLogger) is used.