Este contenido no está disponible en el idioma seleccionado.
10.2. Design Example: A Multinational Enterprise and Its Extranet
10.2.1. Multinational Enterprise Data Design
- A messaging server is used to provide email routing, delivery, and reading services for most of Example Corp.'s sites. An enterprise server provides document publishing services. All servers run on Red Hat Enterprise Linux 7.
- Example Corp. needs to allow data to be managed locally. For example, the European site will be responsible for managing the Europe branch of the directory. This also means that Europe will be responsible for the main copy of its data.
- Because of the geographic distribution of Example Corp.'s offices, the directory needs to be available to users and applications 24 hours a day.
- Many of the data elements need to accommodate data values of several different languages.
Note
All data use the UTF-8 characterset; any other characterset violates LDAP standards.
- Parts suppliers need to log in to Example Corp.'s directory to manage their contracts with Example Corp. Parts suppliers depend on data elements used for authentication, such as name and user password.
- Example Corp.'s partners will use the directory to look up contact details of people in the partner network, such as email addresses and phone numbers.
10.2.2. Multinational Enterprise Schema Design
exampleSupplier object class and the examplePartner object class.
exampleSupplier object class allows one attribute, the exampleSupplierID attribute. This attribute contains the unique ID assigned by Example Corp. International to each automobile parts supplier with which it works.
examplePartner object class allows one attribute, the examplePartnerID attribute. This attribute contains the unique ID assigned by Example Corp. International to each trade partner.
10.2.3. Multinational Enterprise Directory Tree Design
- The root of the directory tree is the
dc=comsuffix. Under this suffix, Example Corp. creates two branches. One branch,dc=exampleCorp,dc=com, contains data internal to Example Corp. International. The other branch,dc=exampleNet,dc=com, contains data for the extranet. - The directory tree for the intranet (under
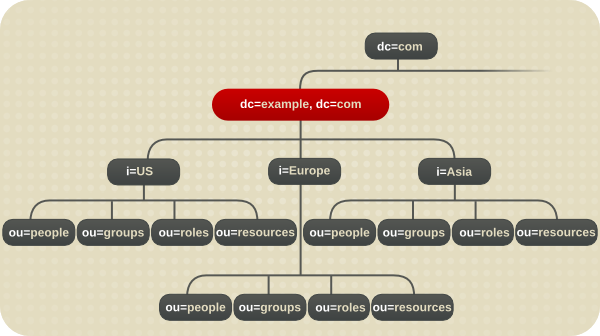
dc=exampleCorp,dc=com)has three main branches, each corresponding to one of the regions where Example Corp. has offices. These branches are identified using thel(locality) attribute. - Each main branch under
dc=exampleCorp,dc=commimics the original directory tree design of Example Corp. Under each locality, Example Corp. creates anou=people, anou=groups, anou=roles, and anou=resourcesbranch. See Figure 10.1, “Directory Tree for Example Corp.” for more information about this directory tree design. - Under the
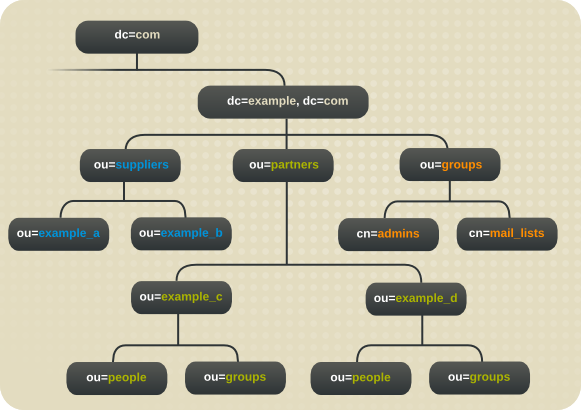
dc=exampleNet,dc=combranch, Example Corp. creates three branches. One branch for suppliers (o=suppliers), one branch for partners (o=partners), and one branch for groups (ou=groups). - The
ou=groupsbranch of the extranet contains entries for the administrators of the extranet as well as for mailing lists that partners subscribe to for up-to-date information on automobile parts manufacturing.
Figure 10.6. Basic Directory Tree for Example Corp. International
Figure 10.7. Directory Tree for Example Corp. International's Intranet
l=Asia entry appears in LDIF as follows:
Figure 10.8. Directory Tree for Example Corp. International's Extranet
10.2.4. Multinational Enterprise Topology Design
10.2.4.1. Database Topology
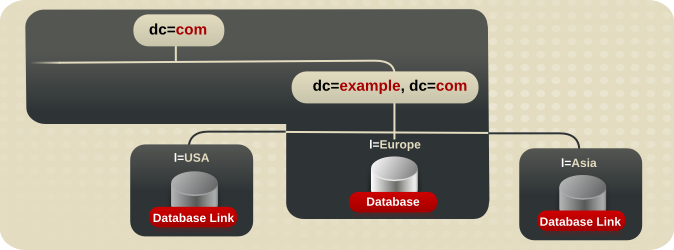
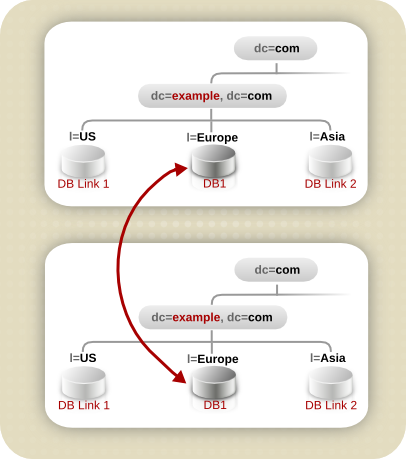
Figure 10.9. Database Topology for Example Corp. Europe
l=US branch are chained by a database link to a database on a server in Austin, Texas. For more information about database links and chaining, see Section 6.3.2, “Using Chaining”.
dc=exampleCorp,dc=com and the root entry, dc=com, is stored in the l=Europe database.
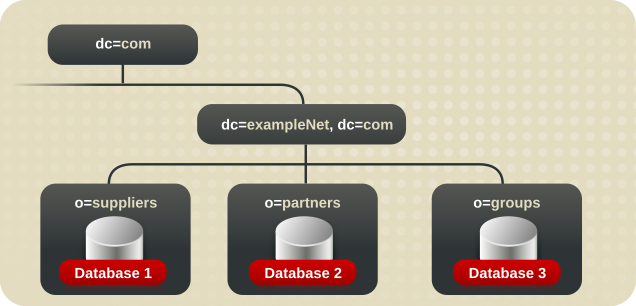
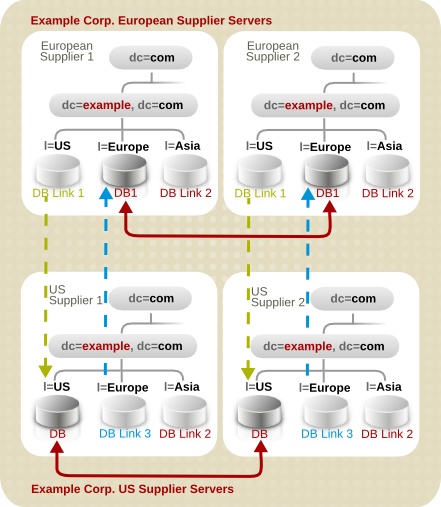
o=suppliers is stored in database one (DB1), that for o=partners is stored in database two (DB2), and that for ou=groups is stored in database three (DB3).
Figure 10.10. Database Topology for Example Corp. International's Extranet
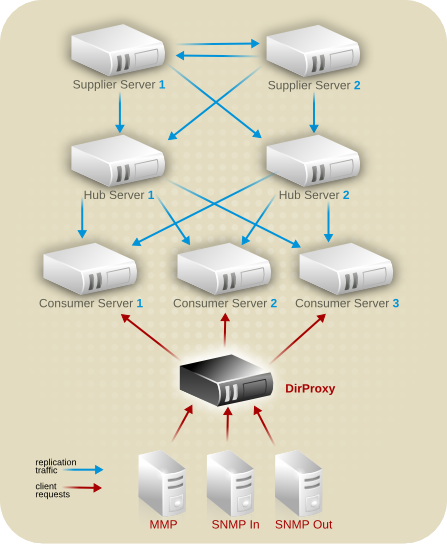
10.2.4.2. Server Topology
Figure 10.11. Server Topology for Example Corp. Europe
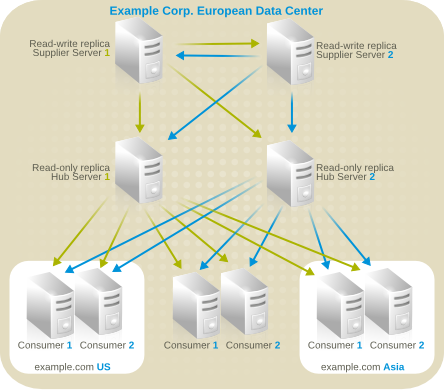
Figure 10.12. Server Topology for Example Corp. International's Extranet
10.2.5. Multinational Enterprise Replication Design
- Data will be managed locally.
- The quality of network connections varies from site to site.
- Database links will be used to connect data on remote servers.
- Hub servers that contain read-only copies of the data will be used to replicate data to consumer servers.
10.2.5.1. Supplier Architecture
dc=exampleCorp,dc=com and dc=com information:
Figure 10.13. Supplier Architecture for Example Corp. Europe
Figure 10.14. Multi-Supplier Replication Design for Example Corp. Europe and Example Corp. US
10.2.6. Multinational Enterprise Security Design
- Example Corp. adds general ACIs to the root of the intranet, creating more restrictive ACIs in each country and the branches beneath each country.
- Example Corp. decides to use macro ACIs to minimize the number of ACIs in the directory.Example Corp. uses a macro to represent a DN in the target or bind rule portion of the ACI. When the directory gets an incoming LDAP operation, the ACI macros are matched against the resource targeted by the LDAP operation. If there is a match, the macro is replaced by the value of the DN of the targeted resource.For more information about macro ACIs, see the Red Hat Directory Server Administrator's Guide.
- Example Corp. decides to use certificate-based authentication for all extranet activities. When people log in to the extranet, they need a digital certificate. The directory is used to store the certificates. Because the directory stores the certificates, users can send encrypted email by looking up public keys stored in the directory.
- Example Corp. creates an ACI that forbids anonymous access to the extranet. This protects the extranet from denial of service attacks.
- Example Corp. wants updates to the directory data to come only from an Example Corp. hosted application. This means that partners and suppliers using the extranet can only use the tools provided by Example Corp. Restricting extranet users to Example Corp.'s preferred tools allows Example Corp. administrators to use the audit logs to track the use of the directory and limits the types of problems that can be introduced by extranet users outside of Example Corp. International.