Este contenido no está disponible en el idioma seleccionado.
Chapter 5. Using Firewalls
5.1. Getting Started with firewalld
Copiar enlaceEnlace copiado en el portapapeles!
A firewall is a way to protect machines from any unwanted traffic from outside. It enables users to control incoming network traffic on host machines by defining a set of firewall rules. These rules are used to sort the incoming traffic and either block it or allow through.
firewalld is a firewall service daemon that provides a dynamic customizable host-based firewall with a D-Bus interface. Being dynamic, it enables creating, changing, and deleting the rules without the necessity to restart the firewall daemon each time the rules are changed.
firewalld uses the concepts of zones and services, that simplify the traffic management. Zones are predefined sets of rules. Network interfaces and sources can be assigned to a zone. The traffic allowed depends on the network your computer is connected to and the security level this network is assigned. Firewall services are predefined rules that cover all necessary settings to allow incoming traffic for a specific service and they apply within a zone.
Services use one or more ports or addresses for network communication. Firewalls filter communication based on ports. To allow network traffic for a service, its ports must be open.
firewalld blocks all traffic on ports that are not explicitly set as open. Some zones, such as trusted, allow all traffic by default.
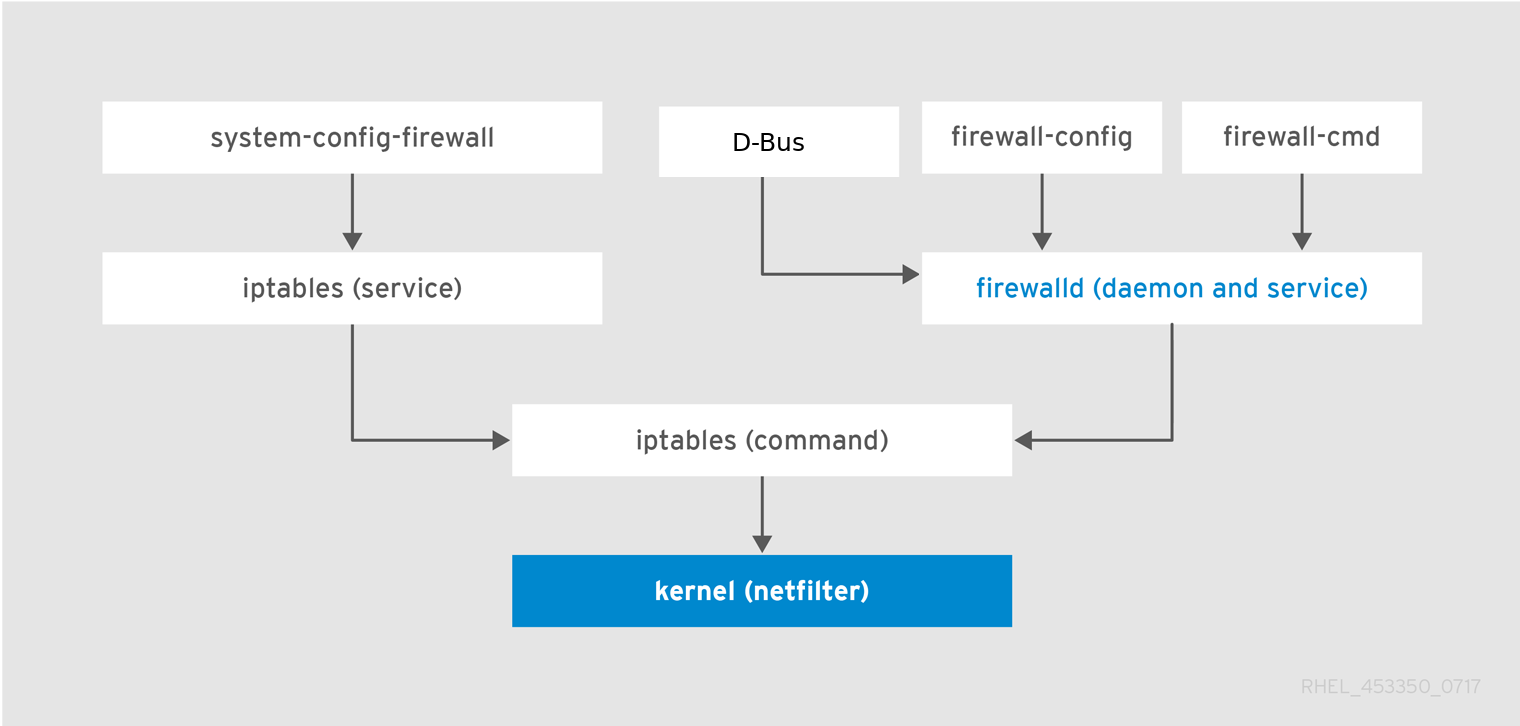
Figure 5.1. The Firewall Stack
5.1.1. Zones
Copiar enlaceEnlace copiado en el portapapeles!
firewalld can be used to separate networks into different zones according to the level of trust that the user has decided to place on the interfaces and traffic within that network. A connection can only be part of one zone, but a zone can be used for many network connections.
NetworkManager notifies
firewalld of the zone of an interface. You can assign zones to interfaces with NetworkManager, with the firewall-config tool, or the firewall-cmd command-line tool. The latter two only edit the appropriate NetworkManager configuration files. If you change the zone of the interface using firewall-cmd or firewall-config, the request is forwarded to NetworkManager and is not handled by firewalld.
The predefined zones are stored in the
/usr/lib/firewalld/zones/ directory and can be instantly applied to any available network interface. These files are copied to the /etc/firewalld/zones/ directory only after they are modified. The following table describes the default settings of the predefined zones:
block- Any incoming network connections are rejected with an icmp-host-prohibited message for
IPv4and icmp6-adm-prohibited forIPv6. Only network connections initiated from within the system are possible. dmz- For computers in your demilitarized zone that are publicly-accessible with limited access to your internal network. Only selected incoming connections are accepted.
-
drop - Any incoming network packets are dropped without any notification. Only outgoing network connections are possible.
external- For use on external networks with masquerading enabled, especially for routers. You do not trust the other computers on the network to not harm your computer. Only selected incoming connections are accepted.
home- For use at home when you mostly trust the other computers on the network. Only selected incoming connections are accepted.
internal- For use on internal networks when you mostly trust the other computers on the network. Only selected incoming connections are accepted.
public- For use in public areas where you do not trust other computers on the network. Only selected incoming connections are accepted.
trusted- All network connections are accepted.
work- For use at work where you mostly trust the other computers on the network. Only selected incoming connections are accepted.
One of these zones is set as the default zone. When interface connections are added to NetworkManager, they are assigned to the default zone. On installation, the default zone in
firewalld is set to be the public zone. The default zone can be changed.
Note
The network zone names have been chosen to be self-explanatory and to allow users to quickly make a reasonable decision. To avoid any security problems, review the default zone configuration and disable any unnecessary services according to your needs and risk assessments.
5.1.2. Predefined Services
Copiar enlaceEnlace copiado en el portapapeles!
A service can be a list of local ports, protocols, source ports, and destinations, as well as a list of firewall helper modules automatically loaded if a service is enabled. Using services saves users time because they can achieve several tasks, such as opening ports, defining protocols, enabling packet forwarding and more, in a single step, rather than setting up everything one after another.
Service configuration options and generic file information are described in the
firewalld.service(5) man page. The services are specified by means of individual XML configuration files, which are named in the following format: service-name.xml. Protocol names are preferred over service or application names in firewalld.
5.1.3. Runtime and Permanent Settings
Copiar enlaceEnlace copiado en el portapapeles!
Any changes committed in runtime mode only apply while
firewalld is running. When firewalld is restarted, the settings revert to their permanent values.
To make the changes persistent across reboots, apply them again using the
--permanent option. Alternatively, to make changes persistent while firewalld is running, use the --runtime-to-permanent firewall-cmd option.
If you set the rules while
firewalld is running using only the --permanent option, they do not become effective before firewalld is restarted. However, restarting firewalld closes all open ports and stops the networking traffic.
5.1.4. Modifying Settings in Runtime and Permanent Configuration using CLI
Copiar enlaceEnlace copiado en el portapapeles!
Using the CLI, you do not modify the firewall settings in both modes at the same time. You only modify either runtime or permanent mode. To modify the firewall settings in the permanent mode, use the
--permanent option with the firewall-cmd command.
firewall-cmd --permanent <other options>
~]# firewall-cmd --permanent <other options>
Without this option, the command modifies runtime mode.
To change settings in both modes, you can use two methods:
- Change runtime settings and then make them permanent as follows:
firewall-cmd <other options> firewall-cmd --runtime-to-permanent
~]# firewall-cmd <other options> ~]# firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Set permanent settings and reload the settings into runtime mode:
firewall-cmd --permanent <other options> firewall-cmd --reload
~]# firewall-cmd --permanent <other options> ~]# firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
The first method allows you to test the settings before you apply them to the permanent mode.
Note
It is possible, especially on remote systems, that an incorrect setting results in a user locking themselves out of a machine. To prevent such situations, use the
--timeout option. After a specified amount of time, any change reverts to its previous state. Using this options excludes the --permanent option.
For example, to add the
SSH service for 15 minutes:
firewall-cmd --add-service=ssh --timeout 15m
~]# firewall-cmd --add-service=ssh --timeout 15m