Este contenido no está disponible en el idioma seleccionado.
4.2. Configuring System Passwords Using authconfig
4.2.1. Password Security
Copiar enlaceEnlace copiado en el portapapeles!
If passwords are stored in plain text format, they are vulnerable to cracking, unauthorized access, or tampering. To prevent this, cryptographic hashing algorithms can be used to securely store password hash digests. The recommended (and also default) hashing algorithm supported in IdM is SHA-512, which uses 64-bit words and also salt and stretching for extra security. To ensure backward compatibility, the SHA-256, DES, BigCrypt, and MD5 hashing algorithms are also supported.
Important
If you do not need backward compatibility, only use SHA-512 as it is more secure.
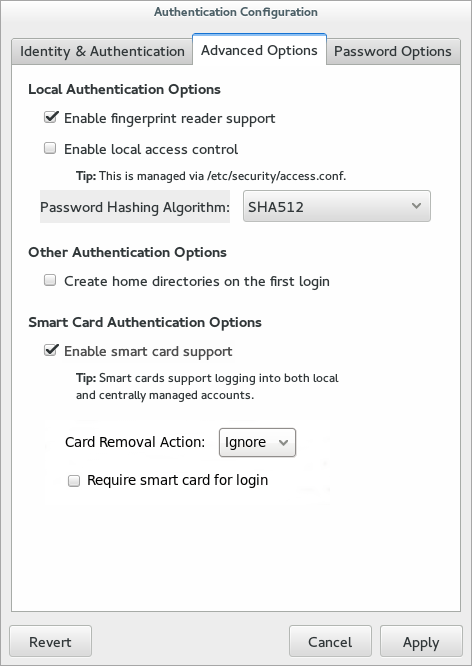
4.2.1.1. Configuring Password Hashing in the UI
Copiar enlaceEnlace copiado en el portapapeles!
The Local Authentication Options tab sets how local passwords are stored on the system. The Password Hashing Algorithm drop-down menu sets the algorithm to securely store passwords hashes.
- Open the
authconfigUI, as in Section 2.2.3, “Launching the authconfig UI”. - Open the Advanced Options tab.
- Select the algorithm to use in the Password Hashing Algorithm drop-down menu.
- Click the button.
4.2.1.2. Configuring Password Hashing on the Command Line
Copiar enlaceEnlace copiado en el portapapeles!
To set or change the hashing algorithm used to securely store user passwords digests, use the
--passalgo option and the short name for the algorithm. The following example uses the SHA-512 algorithm:
authconfig --passalgo=sha512 --update
[root@server ~]# authconfig --passalgo=sha512 --update4.2.2. Password Complexity
Copiar enlaceEnlace copiado en el portapapeles!
Password complexity sets how strong a password must be for it to be allowed to be set for a local user account. Complexity is a combination of length and a variation of character classes. One way to look at it is that there are two parts to setting policy for complex passwords: identifying what types of characters can be used in a password (such as upper and lower case letters and special characters) and how those characters can be used within the password (how long must it be and how often can those characters be repeated).
4.2.2.1. Configuring Password Complexity in the UI
Copiar enlaceEnlace copiado en el portapapeles!
- Open the
authconfigUI, as in Section 2.2.3, “Launching the authconfig UI”. - Open the Password Options tab.
- Set the minimum requirements for the password:
- The minimum length of the password
- The minimum number of character classes which must be used in the password.
- Enable characters classes which must be used for passwords. For example, an uppercase letter can be used with any password, but if the Uppercase check box is selected, then an uppercase letter must be used in every password.
- Set the number of times that a character or character class can be repeated consecutively. (If this is set to zero, then there is no repeat limit.)For the Same Character field, this sets how often a single letter or character can be repeated. If this is set to 2, for example, then ssecret is allowed but sssecret is rejected.Likewise, Same Class sets a limit on how many times any character from a character class (uppercase, number, special character) can be repeated. If this is set to 3, for example, secret!! is allowed but secret!!@ or secret1234 would be rejected.
- Click the button.
4.2.2.2. Configuring Password Complexity in the Command Line
Copiar enlaceEnlace copiado en el portapapeles!
When defining password complexity in the comment line, there are two halves to setting the requirements. The first is setting the requirements on how a password is constructed — its length, can characters be repeated, and how many different types of characters must be used:
- The minimum length (
--passminlen). - The minimum number of different types of characters which must be used (
--passminclass). - The number of times a character can be repeated consecutively (
--passmaxrepeat). Setting this to zero means there is no repeat limit. - The number of time the same type of character (such as a number) can be used in a row (
--passmaxclassrepeat). Setting this to zero means there is no repeat limit.
The second half is defining what types or classes of characters are allowed to be used for passwords. All character types are implicitly allowed; using the
--enablereqType option means that a given class is absolutely required or the password is rejected. (Conversely, types can be explicitly denied, as well.)
- Uppercase letters (
--enablerequpper) - Lowercase letters (
--enablereqlower) - Numbers (
--enablereqdigit) - Special characters (
--enablereqother)
For example, this sets a minimum length of nine characters, does not allow characters or classes to be repeated more than twice, and requires both uppercase and special characters.
authconfig --passminlen=9 --passminclass=3 --passmaxrepeat=2 -passmaxclassrepeat=2 --enablerequpper --enablereqother --update
[root@server ~]# authconfig --passminlen=9 --passminclass=3 --passmaxrepeat=2 -passmaxclassrepeat=2 --enablerequpper --enablereqother --update