Ce contenu n'est pas disponible dans la langue sélectionnée.
Chapter 5. Configuring Microsoft Active Directory
Important
The domain details in this chapter differ from the domain details used in the rest of this guide.
To configure Active Directory to authenticate user through JBoss Negotiation you need to do the following:
- Create a server user account and configure it as a Service Principal Name (SPN) account: the user of the Service Principal Name account (SPN account) acts as a connection between the Kerberos server, the Active Directory and the JBoss web server.
- Generate a keytab file for the server user and export it to the application server. The application server uses the keytab to authenticate to KDC in AD.
Important
Make sure you are using an Active Directory domain controller. It is not possible to use a Windows machine with accounts managed locally.
Warning
Instructions in this guide apply to Windows 2003 and may differ from the instructions relevant for your Windows operating system.
5.1. User Account for the Application Server
Copier lienLien copié sur presse-papiers!
To configure an SPN account for the application server on the AD domain controller, you need Setspn and Ktpass. The command line utilities are part of Windows Server 2003 Support Tools and serve for mapping the server user name to the application server and its HTTP service.
The utilities are available on Microsoft web pages.
You need to create a regular user account for the server in the AD domain (make sure it is a user account, not a computer account) and map the account to the service account.
5.1.1. Creating Server User
Copier lienLien copié sur presse-papiers!
To create a new user for the server, do the following:
- Go to Start
- In the Active Directory Users and Computers window, go to
Figure 5.1. New User
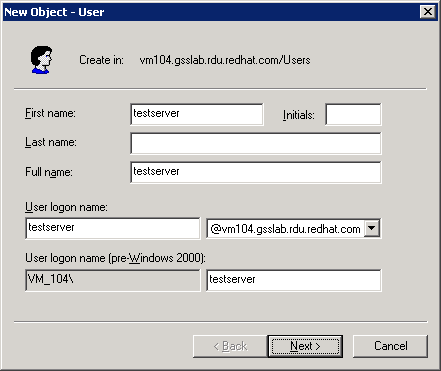
- In the New User window, enter the user details and click Next. Figure 5.1, “New User” uses the server
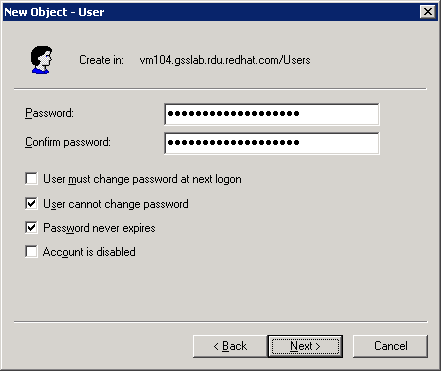
@vm104.gsslab.rdu.redhat.comand defines a user calledtestserver. - Enter the password for the user and select the User cannot change password and Password never expires.
Important
Make sure you have entered a valid password as changing the password later can invalidate the keytab file and break your JBoss installations.Figure 5.2. New User Password
- Click and .
Figure 5.3. New User Finish
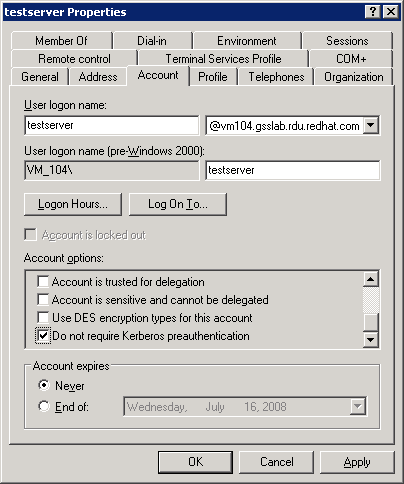
- In the Active Directory Users and Computers window, right-click the user and click .
- In the user properties window, click the Account tab and make sure the Do not require Kerberos preauthentication and Use DES encryption types for this account are selected under Account Options.
Figure 5.4. User Properties
Now you need to create and export the keytab file for the created user.